Programming Assignment 3
|
|
|
- Moris Carson
- 5 years ago
- Views:
Transcription
1 UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Summer 2017 Programming Assignment 3 Introduction For this programming assignment you are to write a C, C++, Java, or Python program that demonstrates the processing of memory allocation and deallocation requests when the buddy algorithm is being used. The input to your program will give the amount of memory available, the size of the smallest possible allocation, and a sequence of allocation and deallocation requests. Details are provided later. In the buddy system each block of memory used to satisfy an allocation request has a size that is exactly a power of 2 storage units (for example, 512, 1024, 16384) 1. The memory management software (that is, your solution to this assignment!) will keep linked lists that identify the unused blocks of memory, which will have sizes that are a power of 2. The number of such lists depends on the amount of memory available to the system, and the size of the smallest allowable allocation. For example, suppose we have 1024 bytes in the system, and the smallest allowable allocation is for 128 bytes. We will need four lists of unused blocks: one for 128-byte blocks, one for 256-byte blocks, one for 512-byte blocks, and one for 1024-byte blocks. Obviously some of these may be empty lists. Each list entry will need to identify its size and its location (that is, its lowest or starting address). The size could be implied from the list on which the block appears (all blocks on the 256-byte block list should obviously be 256 bytes long), but you will likely find it better to explicitly record the size of the block in its list entry. The simulated memory used in this problem will begin at location 0. Note that there is no real memory being allocated in this problem, except, of course, for linked list entries and any other data structures used in your solution. For the example in the previous paragraph, where we have 1024 bytes of memory with a smallest block size of 128 bytes, all block addresses will be less than In fact, we can easily see that the only block addresses permitted are 0, 128, 256, 384, 512, 640, 768, and 896. Memory Management Requests There are two memory management request permitted in this assignment: allocation of a specified amount of memory, and deallocation of a pevious allocation. How your program is to handle each of these operations is described, in detail, in the following paragraphs. Allocation of R bytes 2 is performed by first rounding R up to the next power of 2, if it wasn t already a power of 2; assume this value is called K. The appropriate free list (that is, the free list for blocks of size K) is then checked to determine if a free block is available. If it is, then 1 Although most modern machines are byte addressable, many earlier machines could only address larger units of storage, like 16, 24, 36, or 60 bits. We will assume bytes as the units of allocation to avoid further use of stilted terms like units of storage. 2 You may assume that R will never be larger than the size of the memory.
2 that free block with the smallest address 3 is removed from the list and used to satisfy the request; the allocation is complete. If the free list for blocks of size K is empty, then the free list for blocks with the next larger size (2K) is examined. And if it doesn t have any entries, the program keeps looking in the free lists for larger and larger blocks (4K, 8K, ), until either a free block is found or the free lists for all the larger block sizes have been examined. If no free block of size K or a larger is found, the allocation request isn t discarded. Instead, it is deferred until sometime later when a suitable free block does become available 4. Deferring a request is done by saving the request at the end of a linked list of such deferred requests. An example of a deferred request will be given later. Of course, if a larger free block is found, then it is removed from its list and split into two smaller blocks (each half the size of the original), and these are placed on the appropriate free list. One of these blocks (we always choose the one with the smaller address 5 ) is then used to satisfy the request, either directly (if it is of size K), or indirectly, by splitting it again to yield two even smaller blocks which are handled in the same manner. Deallocation is almost the inverse of allocation. When a block B is deallocated, its buddy s address is first determined. If block B has address A and size K, we compute A / K, always yielding an integer result. If this value is even (that is, if the low-order bit in the binary representation of A / K is 0, or (A / K) mod 2 is 0), then the buddy s address is A + K; otherwise the buddy s address is A K. The free list for blocks with size K is examined for a free block with the buddy s address. If that block is not found, then an entry for B is added to the free list for size K blocks. Otherwise, B s buddy is removed from the free list for size K blocks and joined with block B to form a larger free block B'. This block has size 2K and an address that is the smaller of B and its buddy. We then continue as if we were trying to deallocate this larger block B'. The process is guaranteed to terminate. Once the deallocation is complete, we then need to determine if any of the deferred allocation requests can now be satisfied. This is done by considering each of the deferred requests, one at a time, in the same order the requests were submitted (that is, the deferred request queue is a FIFO queue). Each allocation request that can now be performed is removed from the deferred list, and is allocated the needed storage). An Example An illustration with real numbers will aid your understanding of these actions. Specifically, let s again assume we have a region with 1024 bytes to use in satisfying allocation requests, and that the smallest region we ll use to satisfy a request is 128 bytes. Assume we have the following allocation and deallocation requests to process, in the order given. Each allocation request is given a unique positive integer ID. Deallocation of the allocated memory will use the same ID. 3 This is done to guarantee that all correct solutions will yield the same output. 4 In a real system, the process making such a request might be blocked until sufficient storage becomes available to satisfy the request. 5 As before, this guarantees all correct solutions will yield the same output.
3 ID Action 1 Allocate 200 bytes 2 Allocate 399 bytes 3 Allocate 500 bytes 4 Allocate 100 bytes 5 Allocate 63 bytes 6 Allocate 75 bytes 4 Deallocate 5 Deallocate Initially all our free lists are empty except for the one for blocks of size 1024 bytes, which has a single entry for the region starting at address 0. The first request (ID 1, allocate 200 bytes, which is rounded up to 256 bytes) causes us to look first in the free list for 256 bytes (which is empty), then in the free list for 512 bytes (which is also empty), and finally the free list for 1024 bytes. This list has one entry for the free block at address 0. That entry is removed from the 1024-byte free list. Since it is larger than needed, it is split into two entries of size 512 (one at address 0 and one at address 512). The entry for address 512 is placed on the free list for size 512, and the one at address 0 is split again to give two free blocks of size 256, one at address 0 and one at address 256. The block at address 256 is added to the free list for size 256, and the one with address 0 is used to satisfy the current request. The second request (ID 2, allocate 399 bytes, rounded up to 512) is easily satisfied, since there is a single block of size 512 available. After that request is satisfied, a single free block, of size 256, at address 256, remains. The third request (ID 3, allocate 500 bytes, rounded up to 512) cannot be satisfied because there are no blocks on the free lists for 512 bytes and 1024 bytes. The request is therefore placed on the deferred list, and will be considered again after a deallocation. The fourth request (ID 4, allocate 100 bytes, rounded up to 128) can be satisfied after the free block of 256 bytes at address 256 is split into two 128 byte blocks. The 128 byte block at address 256 is used to satisfy the request, and the other 128 byte block at address 384, is placed on the free list for 128 byte blocks. The fifth request (ID 5, allocate 63 bytes, rounded up to 128, the minimum) is satisfied using the last free block in the system, at address 384. The sixth request (ID 6, allocate 75 bytes, rounded up to 128) cannot be satisfied immediately, so it is deferred, and placed after the first deferred request on the deferred list. The seventh request (ID 4, deallocate) indicates that the 128 byte block at address 256 is to be freed. Since its buddy (at address 384) is not free, the free block is placed on the 128 byte free list. Since there are deferred requests, we consider each of them in order. The first such deferred request (for 512 bytes) still cannot be satisfied, so it remains on the list. The second deferred request (for 128 bytes) can be satisfied using the single free block at address 256. We now have no free blocks, and one deferred request remains.
4 The eighth and final request (ID 5, deallocate) frees the 128 byte block at address 384. Its buddy, at address 256, is not free, so we re done after placing the free block on the free list for 128 byte entries. The example given here and the additional example given later have all of the allocation requests first, followed by deallocation requests. This will not necessarily be the case in real data. You are certainly encouraged to use these to test your program, but you should also prepare additional test cases. Developing suitable test data is an essential part of any development activity. Input Data The input data will be read from the standard input. The first line of the input will contain two unsigned integers. The first of these, MSIZE, will indicate the total amount of memory available for allocation. The second integer, ASIZE, will indicate the size of the smallest block that can be used to satisfy a request. Each of these will be a power of 2, andasize MSIZE < Each remaining line will contain an allocation or deallocation request. Each request will begin with a positive integer ID, some whitespace (that is, blanks and/or tabs), and a '+' or '-'. '+' is used for an allocation request, and ' ' is used for a deallocation request. An allocation request will have the positive integer size of the allocation request specified after the '+' (separated by additional whitespace). The end of the input is indicated by the end of file. You may assume that all input is syntactically and semantically correct. Details and Limits You will need one free list for each power of 2 between (and including) ASIZE and MSIZE, a list to keep track of deferred allocation requests, and some way of recording information (ID, address, and size) for allocations that have been made but have not yet been deallocated. No two allocation requests will ever have the same ID, but each deallocation request must contain theid of a previously successful allocation. The input data used to test your solution will never attempt to deallocate an allocation that is currently deferred, but your solution should detect this case (if it should exist), since that would indicate either an error in the input data or, more troubling, an error in your solution! Although the IDs used in the earlier example were sequential, this need not be the case in actual test data. After reading each request, your program should display a line that indicates the request that is being processed; they should be similar to one of these: Request ID 52: allocate 73 bytes. Request ID 35: deallocate. Each line for an allocation request should be immediately followed by another line containing or Success; addr = 0x
5 as appropriate. Note that the address in the Success message should be the address at which the region allocated for the request begins. Also make certain that you always satisfy each allocation request with the free region that has the smallest address. (It will likely be appropriate to maintain the free lists in ascending address order to make this requirement easier to satsify.) After each deallocation request you should display a line that says Additionally, for each deferred request that can be successfully accommodated as a result of a deallocation, display a line that says Deferred request with ID 59 allocated; addr = 0x Of course, the IDs and address values in each of these are just an examples. But do note that the addresses in the output should be displayed as 8-digit hexadecimal numbers preceded by 0x (that is, they should be C/C++/Java-style hexadecimal constants). Keep in mind that the addresses used in the program for free blocks and allocations are not real memory addresses they are simulated memory addresses. Your program should not be doing dynamic memory allocation for blocks of the sizes used in the progam. Sample Input and Output The instructor s solution to this assignment and files containing sample input are available on Loki in the directory/home/stanw/csci4500. The instructor s solution is in the file named prog3. Like your solution should do, it reads input data from the standard input (file descriptor 0). You may also supply the option v on the command line to produce considerable additional output. After each input request has been completed, the program will display the status of all requests, the contents of the free lists, and the list of deferred requests. For deallocation, the calculation of buddy addresses and the joining of blocks on various free lists will be displayed. The first sample is the input used the earlier discussion, and is found in the fileprog3.input1 on Loki. Here s what it looks like: The expected output for this input is as follows: Request ID 1: allocate 200 bytes. Success; addr = 0x Request ID 2: allocate 399 bytes. Success; addr = 0x
6 Request ID 3: allocate 500 bytes. Request ID 4: allocate 100 bytes. Success; addr = 0x Request ID 5: allocate 63 bytes. Success; addr = 0x Request ID 6: allocate 75 bytes. Request ID 4: deallocate. Deferred request 6 allocated; addr = 0x Request ID 5: deallocate. The second sample is somewhat more ambitious, and is found in the file prog3.input2 on Loki. Here s what it contains: And here is the expected output: Request ID 1: allocate 500 bytes. Success; addr = 0x Request ID 2: allocate 250 bytes. Success; addr = 0x Request ID 3: allocate 100 bytes. Success; addr = 0x
7 Request ID 4: allocate 1025 bytes. Success; addr = 0x Request ID 5: allocate 390 bytes. Success; addr = 0x Request ID 6: allocate 200 bytes. Success; addr = 0x Request ID 7: allocate 1 byte. Success; addr = 0x Request ID 8: allocate 1200 bytes. Request ID 9: allocate 200 bytes. Request ID 10: allocate 2000 bytes. Request ID 11: allocate 2000 bytes. Request ID 4: deallocate. Deferred request 8 allocated; addr = 0x Request ID 3: deallocate. Deferred request 9 allocated; addr = 0x Request ID 2: deallocate. Request ID 1: deallocate. Request ID 9: deallocate. Request ID 7: deallocate. Request ID 5: deallocate. Request ID 6: deallocate. Deferred request 10 allocated; addr = 0x Request ID 8: deallocate. Deferred request 11 allocated; addr = 0x Request ID 10: deallocate. Request ID 11: deallocate. Three additional test cases, appropriately named, are also provided. The expected output for each test case can be obtained using the instructor s solution. Additional test cases may be provided in the future. If so, they ll be announced on the class web page, and will be given names similar to the samples already provided.
8 Requirements You must write (and test) a C, C++, Java or Python program that performs the tasks associated with the buddy system memory management system to perform the requests specifined in the input format described earlier. You should ideally have a single file of source code, appropriately named (that is, use prog3 as part of the name). That file (or multiple files, if necessary) should be located in a top-level directory named csci prog3 sometime before Wednesday, August 9, 2017 at 11:59 PM. At that time, the contents of that directory will be copied to the instructor s directory for grading. A template (partial solution) for a C solution to this assignment can be found in the csci4500 directory. It is namedprog3_temp.c. You are free to use this source code as the basis for your solution if you wish. You are not, however, required to use this partial solution. Locations in the code that are marked XXX WORK NEEDED obviously will require additional work. There may also be other modifications required to the code. You may work with one or two other students on this assignment that is, groups as large as three students are acceptable. If you work in a group with others, you should clearly indicate the names of all individuals in the group in a comment near the top of the source code (you should indicate the author of your code in all cases, even if you are working by yourself). You should also submit only one solution from the group for evaluation. Each individual in the group will receive the same evaluation. As always, please contact the instructor if you have questions, and periodically check the class web site for any additions or corrections to this assignment.
Programming Assignment 3
 UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Spring 2016 Programming Assignment 3 Introduction For this programming assignment you are to write a C, C++, Java, or Python
UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Spring 2016 Programming Assignment 3 Introduction For this programming assignment you are to write a C, C++, Java, or Python
UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Summer 2016 Programming Assignment 1 Introduction The purpose of this
 UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Summer 2016 Programming Assignment 1 Introduction The purpose of this programming assignment is to give you some experience
UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Summer 2016 Programming Assignment 1 Introduction The purpose of this programming assignment is to give you some experience
UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Fall Programming Assignment 1 (updated 9/16/2017)
 UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Fall 2017 Programming Assignment 1 (updated 9/16/2017) Introduction The purpose of this programming assignment is to give you
UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 4500/8506 Operating Systems Fall 2017 Programming Assignment 1 (updated 9/16/2017) Introduction The purpose of this programming assignment is to give you
Programming Assignment 3
 UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 3550 Section 002 Communication Networks Spring 2018 Programming Assignment 3 Introduction Having created a TCP client in programming assignment 2, it s
UNIVERSITY OF NEBRASKA AT OMAHA Computer Science 3550 Section 002 Communication Networks Spring 2018 Programming Assignment 3 Introduction Having created a TCP client in programming assignment 2, it s
Programming Standards: You must conform to good programming/documentation standards. Some specifics:
 CS3114 (Spring 2011) PROGRAMMING ASSIGNMENT #3 Due Thursday, April 7 @ 11:00 PM for 100 points Early bonus date: Wednesday, April 6 @ 11:00 PM for a 10 point bonus Initial Schedule due Thursday, March
CS3114 (Spring 2011) PROGRAMMING ASSIGNMENT #3 Due Thursday, April 7 @ 11:00 PM for 100 points Early bonus date: Wednesday, April 6 @ 11:00 PM for a 10 point bonus Initial Schedule due Thursday, March
CS Operating Systems
 CS 4500 - Operating Systems Module 9: Memory Management - Part 1 Stanley Wileman Department of Computer Science University of Nebraska at Omaha Omaha, NE 68182-0500, USA June 9, 2017 In This Module...
CS 4500 - Operating Systems Module 9: Memory Management - Part 1 Stanley Wileman Department of Computer Science University of Nebraska at Omaha Omaha, NE 68182-0500, USA June 9, 2017 In This Module...
CS Operating Systems
 CS 4500 - Operating Systems Module 9: Memory Management - Part 1 Stanley Wileman Department of Computer Science University of Nebraska at Omaha Omaha, NE 68182-0500, USA June 9, 2017 In This Module...
CS 4500 - Operating Systems Module 9: Memory Management - Part 1 Stanley Wileman Department of Computer Science University of Nebraska at Omaha Omaha, NE 68182-0500, USA June 9, 2017 In This Module...
1. NUMBER SYSTEMS USED IN COMPUTING: THE BINARY NUMBER SYSTEM
 1. NUMBER SYSTEMS USED IN COMPUTING: THE BINARY NUMBER SYSTEM 1.1 Introduction Given that digital logic and memory devices are based on two electrical states (on and off), it is natural to use a number
1. NUMBER SYSTEMS USED IN COMPUTING: THE BINARY NUMBER SYSTEM 1.1 Introduction Given that digital logic and memory devices are based on two electrical states (on and off), it is natural to use a number
Computer Science 4500 Operating Systems
 Computer Science 4500 Operating Systems Module 6 Process Scheduling Methods Updated: September 25, 2014 2008 Stanley A. Wileman, Jr. Operating Systems Slide 1 1 In This Module Batch and interactive workloads
Computer Science 4500 Operating Systems Module 6 Process Scheduling Methods Updated: September 25, 2014 2008 Stanley A. Wileman, Jr. Operating Systems Slide 1 1 In This Module Batch and interactive workloads
COMPUTER SCIENCE 4500 OPERATING SYSTEMS
 Last update: 3/28/2017 COMPUTER SCIENCE 4500 OPERATING SYSTEMS 2017 Stanley Wileman Module 9: Memory Management Part 1 In This Module 2! Memory management functions! Types of memory and typical uses! Simple
Last update: 3/28/2017 COMPUTER SCIENCE 4500 OPERATING SYSTEMS 2017 Stanley Wileman Module 9: Memory Management Part 1 In This Module 2! Memory management functions! Types of memory and typical uses! Simple
CS 2604 Minor Project 1 Summer 2000
 RPN Calculator For this project, you will design and implement a simple integer calculator, which interprets reverse Polish notation (RPN) expressions. There is no graphical interface. Calculator input
RPN Calculator For this project, you will design and implement a simple integer calculator, which interprets reverse Polish notation (RPN) expressions. There is no graphical interface. Calculator input
Events, Memory Management
 Events, Memory Management Events, Memory Management 1. Call back, message pumps 2. Call backs vs messages 3. Memory management Callback Program registers and event handler program that is called whenever
Events, Memory Management Events, Memory Management 1. Call back, message pumps 2. Call backs vs messages 3. Memory management Callback Program registers and event handler program that is called whenever
3. When you process a largest recent earthquake query, you should print out:
 CS3114 (Fall 2013) PROGRAMMING ASSIGNMENT #1 Due Wednesday, September 18 @ 11:00 PM for 100 points Due Tuesday, September 17 @ 11:00 PM for 10 point bonus Updated: 9/11/2013 Assignment: This is the first
CS3114 (Fall 2013) PROGRAMMING ASSIGNMENT #1 Due Wednesday, September 18 @ 11:00 PM for 100 points Due Tuesday, September 17 @ 11:00 PM for 10 point bonus Updated: 9/11/2013 Assignment: This is the first
Chapter 2: Basic Elements of C++ Objectives. Objectives (cont d.) A C++ Program. Introduction
 Chapter 2: Basic Elements of C++ C++ Programming: From Problem Analysis to Program Design, Fifth Edition 1 Objectives In this chapter, you will: Become familiar with functions, special symbols, and identifiers
Chapter 2: Basic Elements of C++ C++ Programming: From Problem Analysis to Program Design, Fifth Edition 1 Objectives In this chapter, you will: Become familiar with functions, special symbols, and identifiers
CS 3204 Operating Systems Programming Project #2 Job / CPU Scheduling Dr. Sallie Henry Spring 2001 Due on February 27, 2001.
 CS 3204 Operating Systems Programming Project #2 Job / CPU Scheduling Dr. Sallie Henry Spring 2001 Due on February 27, 2001. 23:59:59 PM Design and implement a program that simulates some of the job scheduling,
CS 3204 Operating Systems Programming Project #2 Job / CPU Scheduling Dr. Sallie Henry Spring 2001 Due on February 27, 2001. 23:59:59 PM Design and implement a program that simulates some of the job scheduling,
CSCI 561: Foundations of Artificial Intelligence Instructor: Prof. Laurent Itti Homework 1: Uninformed Search Due on September 23rd at 11:59pm, 2015
 CSCI 561: Foundations of Artificial Intelligence Instructor: Prof. Laurent Itti Homework 1: Uninformed Search Due on September 23rd at 11:59pm, 2015 UNINFORMED SEARCH There is an old city that has an antique
CSCI 561: Foundations of Artificial Intelligence Instructor: Prof. Laurent Itti Homework 1: Uninformed Search Due on September 23rd at 11:59pm, 2015 UNINFORMED SEARCH There is an old city that has an antique
Fundamental Concepts: array of structures, string objects, searching and sorting. Static Inventory Maintenance Program
 Fundamental Concepts: array of structures, string objects, searching and sorting The point of this assignment is to validate your understanding of the basic concepts presented in CS 1044. If you have much
Fundamental Concepts: array of structures, string objects, searching and sorting The point of this assignment is to validate your understanding of the basic concepts presented in CS 1044. If you have much
Student Name: University of California at Berkeley College of Engineering Department of Electrical Engineering and Computer Science
 University of California at Berkeley College of Engineering Department of Electrical Engineering and Computer Science CS 162 Spring 2011 I. Stoica FIRST MIDTERM EXAMINATION Wednesday, March 9, 2011 INSTRUCTIONS
University of California at Berkeley College of Engineering Department of Electrical Engineering and Computer Science CS 162 Spring 2011 I. Stoica FIRST MIDTERM EXAMINATION Wednesday, March 9, 2011 INSTRUCTIONS
Objectives. Chapter 2: Basic Elements of C++ Introduction. Objectives (cont d.) A C++ Program (cont d.) A C++ Program
 Objectives Chapter 2: Basic Elements of C++ In this chapter, you will: Become familiar with functions, special symbols, and identifiers in C++ Explore simple data types Discover how a program evaluates
Objectives Chapter 2: Basic Elements of C++ In this chapter, you will: Become familiar with functions, special symbols, and identifiers in C++ Explore simple data types Discover how a program evaluates
Full file at
 Java Programming: From Problem Analysis to Program Design, 3 rd Edition 2-1 Chapter 2 Basic Elements of Java At a Glance Instructor s Manual Table of Contents Overview Objectives s Quick Quizzes Class
Java Programming: From Problem Analysis to Program Design, 3 rd Edition 2-1 Chapter 2 Basic Elements of Java At a Glance Instructor s Manual Table of Contents Overview Objectives s Quick Quizzes Class
CS 1044 Program 6 Summer I dimension ??????
 Managing a simple array: Validating Array Indices Most interesting programs deal with considerable amounts of data, and must store much, or all, of that data on one time. The simplest effective means for
Managing a simple array: Validating Array Indices Most interesting programs deal with considerable amounts of data, and must store much, or all, of that data on one time. The simplest effective means for
6.172 Performance Engineering of Software Systems Spring Lecture 9. P after. Figure 1: A diagram of the stack (Image by MIT OpenCourseWare.
 6.172 Performance Engineering of Software Systems Spring 2009 Lecture 9 MIT OpenCourseWare Dynamic Storage Allocation Stack allocation: LIFO (last-in-first-out) Array and pointer A used unused P before
6.172 Performance Engineering of Software Systems Spring 2009 Lecture 9 MIT OpenCourseWare Dynamic Storage Allocation Stack allocation: LIFO (last-in-first-out) Array and pointer A used unused P before
CS 2604 Minor Project 1 DRAFT Fall 2000
 RPN Calculator For this project, you will design and implement a simple integer calculator, which interprets reverse Polish notation (RPN) expressions. There is no graphical interface. Calculator input
RPN Calculator For this project, you will design and implement a simple integer calculator, which interprets reverse Polish notation (RPN) expressions. There is no graphical interface. Calculator input
CS101 Lecture 04: Binary Arithmetic
 CS101 Lecture 04: Binary Arithmetic Binary Number Addition Two s complement encoding Briefly: real number representation Aaron Stevens (azs@bu.edu) 25 January 2013 What You ll Learn Today Counting in binary
CS101 Lecture 04: Binary Arithmetic Binary Number Addition Two s complement encoding Briefly: real number representation Aaron Stevens (azs@bu.edu) 25 January 2013 What You ll Learn Today Counting in binary
2018 Pummill Relay problem statement
 2018 Pummill Relays CS Problem: Minimum Spanning Tree Missouri State University For information about the Pummill Relays CS Problem, please contact: KenVollmar@missouristate.edu, 417-836-5789 Suppose there
2018 Pummill Relays CS Problem: Minimum Spanning Tree Missouri State University For information about the Pummill Relays CS Problem, please contact: KenVollmar@missouristate.edu, 417-836-5789 Suppose there
CSCI 4500 / 8506 Sample Questions for Quiz 5
 CSCI 4500 / 8506 Sample Questions for Quiz 5 1. Why might a system treat memory allocation requests from the operating system itself differently from those generated by an application? a. The OS typically
CSCI 4500 / 8506 Sample Questions for Quiz 5 1. Why might a system treat memory allocation requests from the operating system itself differently from those generated by an application? a. The OS typically
CS125 : Introduction to Computer Science. Lecture Notes #4 Type Checking, Input/Output, and Programming Style
 CS125 : Introduction to Computer Science Lecture Notes #4 Type Checking, Input/Output, and Programming Style c 2005, 2004, 2002, 2001, 2000 Jason Zych 1 Lecture 4 : Type Checking, Input/Output, and Programming
CS125 : Introduction to Computer Science Lecture Notes #4 Type Checking, Input/Output, and Programming Style c 2005, 2004, 2002, 2001, 2000 Jason Zych 1 Lecture 4 : Type Checking, Input/Output, and Programming
CS 374 Fall 2014 Homework 2 Due Tuesday, September 16, 2014 at noon
 CS 374 Fall 2014 Homework 2 Due Tuesday, September 16, 2014 at noon Groups of up to three students may submit common solutions for each problem in this homework and in all future homeworks You are responsible
CS 374 Fall 2014 Homework 2 Due Tuesday, September 16, 2014 at noon Groups of up to three students may submit common solutions for each problem in this homework and in all future homeworks You are responsible
CSE 410 Computer Systems. Hal Perkins Spring 2010 Lecture 12 More About Caches
 CSE 4 Computer Systems Hal Perkins Spring Lecture More About Caches Reading Computer Organization and Design Section 5. Introduction Section 5. Basics of Caches Section 5. Measuring and Improving Cache
CSE 4 Computer Systems Hal Perkins Spring Lecture More About Caches Reading Computer Organization and Design Section 5. Introduction Section 5. Basics of Caches Section 5. Measuring and Improving Cache
AP Computer Science Unit 1. Writing Programs Using BlueJ
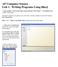 AP Computer Science Unit 1. Writing Programs Using BlueJ 1. Open up BlueJ. Click on the Project menu and select New Project. You should see the window on the right. Navigate to wherever you plan to save
AP Computer Science Unit 1. Writing Programs Using BlueJ 1. Open up BlueJ. Click on the Project menu and select New Project. You should see the window on the right. Navigate to wherever you plan to save
CS 261 Spring 2013 Midterm
 CS 261 Spring 2013 Midterm Name: Student ID: 1: 2: 3: 4: 5: 6: Total: 1. (20 points) Suppose that we implement a simplified version of the dynamic array data structure in which the amount of memory allocated
CS 261 Spring 2013 Midterm Name: Student ID: 1: 2: 3: 4: 5: 6: Total: 1. (20 points) Suppose that we implement a simplified version of the dynamic array data structure in which the amount of memory allocated
Number Systems (2.1.1)
 Number Systems (2.1.1) Concept of a register. Operations of register, Complementation, Ranges, Left and right shifts, Addition of two binary number, Numerical overflow, 2 s complement representation, Binary
Number Systems (2.1.1) Concept of a register. Operations of register, Complementation, Ranges, Left and right shifts, Addition of two binary number, Numerical overflow, 2 s complement representation, Binary
CS-245 Database System Principles
 CS-245 Database System Principles Midterm Exam Summer 2001 SOLUIONS his exam is open book and notes. here are a total of 110 points. You have 110 minutes to complete it. Print your name: he Honor Code
CS-245 Database System Principles Midterm Exam Summer 2001 SOLUIONS his exam is open book and notes. here are a total of 110 points. You have 110 minutes to complete it. Print your name: he Honor Code
Project: Visual Cache Simulator Input: Real Addresses Outputs: 1. Number of Hits 2. Number of Misses 3. Hit Ratio 4. Visual Representation of Cache
 Project: Visual Cache Simulator Input: Real Addresses Outputs: 1. Number of Hits 2. Number of Misses 3. Hit Ratio 4. Visual Representation of Cache including 4.1. Index or Index Set 4.2. Tag 4.3. Cache
Project: Visual Cache Simulator Input: Real Addresses Outputs: 1. Number of Hits 2. Number of Misses 3. Hit Ratio 4. Visual Representation of Cache including 4.1. Index or Index Set 4.2. Tag 4.3. Cache
The Program Specification:
 Reading to Input Failure, Decisions, Functions This programming assignment uses many of the ideas presented in sections 3 through 8 of the course notes, so you are advised to read those notes carefully
Reading to Input Failure, Decisions, Functions This programming assignment uses many of the ideas presented in sections 3 through 8 of the course notes, so you are advised to read those notes carefully
CSCI 204 Introduction to Computer Science II
 CSCI 204 Project 2 Maze Assigned: Wednesday 09/27/2017 First Phase (Recursion) Due Friday, 10/06/2017 Second Phase (Stack) Due Monday, 10/16/2017 1 Objective The purpose of this assignment is to give you
CSCI 204 Project 2 Maze Assigned: Wednesday 09/27/2017 First Phase (Recursion) Due Friday, 10/06/2017 Second Phase (Stack) Due Monday, 10/16/2017 1 Objective The purpose of this assignment is to give you
CS3114 (Fall 2013) PROGRAMMING ASSIGNMENT #2 Due Tuesday, October 11:00 PM for 100 points Due Monday, October 11:00 PM for 10 point bonus
 CS3114 (Fall 2013) PROGRAMMING ASSIGNMENT #2 Due Tuesday, October 15 @ 11:00 PM for 100 points Due Monday, October 14 @ 11:00 PM for 10 point bonus Updated: 10/10/2013 Assignment: This project continues
CS3114 (Fall 2013) PROGRAMMING ASSIGNMENT #2 Due Tuesday, October 15 @ 11:00 PM for 100 points Due Monday, October 14 @ 11:00 PM for 10 point bonus Updated: 10/10/2013 Assignment: This project continues
ENCE 3241 Data Lab. 60 points Due February 19, 2010, by 11:59 PM
 0 Introduction ENCE 3241 Data Lab 60 points Due February 19, 2010, by 11:59 PM The purpose of this assignment is for you to become more familiar with bit-level representations and manipulations. You ll
0 Introduction ENCE 3241 Data Lab 60 points Due February 19, 2010, by 11:59 PM The purpose of this assignment is for you to become more familiar with bit-level representations and manipulations. You ll
CSCI 4210 Operating Systems CSCI 6140 Computer Operating Systems Project 2 (document version 1.4) Contiguous and Non-contiguous Memory Management
 CSCI 4210 Operating Systems CSCI 6140 Computer Operating Systems Project 2 (document version 1.4) Contiguous and Non-contiguous Memory Management Overview This project is due by 11:59:59 PM on Wednesday,
CSCI 4210 Operating Systems CSCI 6140 Computer Operating Systems Project 2 (document version 1.4) Contiguous and Non-contiguous Memory Management Overview This project is due by 11:59:59 PM on Wednesday,
Chapter 2: Basic Elements of C++
 Chapter 2: Basic Elements of C++ Objectives In this chapter, you will: Become familiar with functions, special symbols, and identifiers in C++ Explore simple data types Discover how a program evaluates
Chapter 2: Basic Elements of C++ Objectives In this chapter, you will: Become familiar with functions, special symbols, and identifiers in C++ Explore simple data types Discover how a program evaluates
CSCI 4210 Operating Systems CSCI 6140 Computer Operating Systems Project 1 (document version 1.3) Process Simulation Framework
 CSCI 4210 Operating Systems CSCI 6140 Computer Operating Systems Project 1 (document version 1.3) Process Simulation Framework Overview This project is due by 11:59:59 PM on Thursday, October 20, 2016.
CSCI 4210 Operating Systems CSCI 6140 Computer Operating Systems Project 1 (document version 1.3) Process Simulation Framework Overview This project is due by 11:59:59 PM on Thursday, October 20, 2016.
CPSC 217 Assignment 3
 CPSC 217 Assignment 3 Due: Monday November 26, 2018 at 12:00 noon Weight: 7% Sample Solution Length: Approximately 120 lines, including blank lines, lots of comments and the provided code Individual Work:
CPSC 217 Assignment 3 Due: Monday November 26, 2018 at 12:00 noon Weight: 7% Sample Solution Length: Approximately 120 lines, including blank lines, lots of comments and the provided code Individual Work:
Introduction to Java Unit 1. Using BlueJ to Write Programs
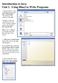 Introduction to Java Unit 1. Using BlueJ to Write Programs 1. Open up BlueJ. Click on the Project menu and select New Project. You should see the window on the right. Navigate to wherever you plan to save
Introduction to Java Unit 1. Using BlueJ to Write Programs 1. Open up BlueJ. Click on the Project menu and select New Project. You should see the window on the right. Navigate to wherever you plan to save
CMSC 341 Hashing. Based on slides from previous iterations of this course
 CMSC 341 Hashing Based on slides from previous iterations of this course Hashing Searching n Consider the problem of searching an array for a given value q If the array is not sorted, the search requires
CMSC 341 Hashing Based on slides from previous iterations of this course Hashing Searching n Consider the problem of searching an array for a given value q If the array is not sorted, the search requires
Objectives. In this chapter, you will:
 Objectives In this chapter, you will: Become familiar with functions, special symbols, and identifiers in C++ Explore simple data types Discover how a program evaluates arithmetic expressions Learn about
Objectives In this chapter, you will: Become familiar with functions, special symbols, and identifiers in C++ Explore simple data types Discover how a program evaluates arithmetic expressions Learn about
CS : Programming for Non-Majors, Fall 2018 Programming Project #5: Big Statistics Due by 10:20am Wednesday November
 CS 1313 010: Programming for Non-Majors, Fall 2018 Programming Project #5: Big Statistics Due by 10:20am Wednesday November 7 2018 This fifth programming project will give you experience writing programs
CS 1313 010: Programming for Non-Majors, Fall 2018 Programming Project #5: Big Statistics Due by 10:20am Wednesday November 7 2018 This fifth programming project will give you experience writing programs
Soda Machine Laboratory
 Soda Machine Laboratory Introduction This laboratory is intended to give you experience working with multiple queue structures in a familiar real-world setting. The given application models a soda machine
Soda Machine Laboratory Introduction This laboratory is intended to give you experience working with multiple queue structures in a familiar real-world setting. The given application models a soda machine
Lab 4: Super Sudoku Solver CSCI 2101 Fall 2017
 Due: Wednesday, October 18, 11:59 pm Collaboration Policy: Level 1 Group Policy: Pair-Optional Lab 4: Super Sudoku Solver CSCI 2101 Fall 2017 In this week s lab, you will write a program that can solve
Due: Wednesday, October 18, 11:59 pm Collaboration Policy: Level 1 Group Policy: Pair-Optional Lab 4: Super Sudoku Solver CSCI 2101 Fall 2017 In this week s lab, you will write a program that can solve
COP Programming Assignment #7
 1 of 5 03/13/07 12:36 COP 3330 - Programming Assignment #7 Due: Mon, Nov 21 (revised) Objective: Upon completion of this program, you should gain experience with operator overloading, as well as further
1 of 5 03/13/07 12:36 COP 3330 - Programming Assignment #7 Due: Mon, Nov 21 (revised) Objective: Upon completion of this program, you should gain experience with operator overloading, as well as further
Design Relationships, Indexes, Queries, & More (Individual/Team Of 2) Assignment 20 USE PENCIL
 Relationships-1-HW.docx CSCI 3321 Initials P a g e 1 If this lab is an Individual assignment, you must do all coded programs on your own. You may ask others for help on the language syntax, but you must
Relationships-1-HW.docx CSCI 3321 Initials P a g e 1 If this lab is an Individual assignment, you must do all coded programs on your own. You may ask others for help on the language syntax, but you must
COMPUTER SCIENCE Paper 2 (PRACTICAL)
 COMPUTER SCIENCE Paper 2 (PRACTICAL) (Maximum Marks: 30) (Time allowed: Three hours) (Candidates are allowed additional 15 minutes for only reading the paper. They must NOT start writing during this time.)
COMPUTER SCIENCE Paper 2 (PRACTICAL) (Maximum Marks: 30) (Time allowed: Three hours) (Candidates are allowed additional 15 minutes for only reading the paper. They must NOT start writing during this time.)
CSCI 2212: Intermediate Programming / C Recursion
 ... 1/40 CSCI 2212: Intermediate Programming / C Recursion Alice E. Fischer November 13 and 16, 2015 ... 2/40 Outline What is Recursion? Recursively Defined Images What is a Recursive Function? How Does
... 1/40 CSCI 2212: Intermediate Programming / C Recursion Alice E. Fischer November 13 and 16, 2015 ... 2/40 Outline What is Recursion? Recursively Defined Images What is a Recursive Function? How Does
Integrated Projects for Presentations
 Integrated Projects for Presentations OUTLINING AND CREATING A PRESENTATION Outlining the Presentation Drafting a List of Topics Imagine that your supervisor has asked you to prepare and give a presentation.
Integrated Projects for Presentations OUTLINING AND CREATING A PRESENTATION Outlining the Presentation Drafting a List of Topics Imagine that your supervisor has asked you to prepare and give a presentation.
Chapter 2. Data Representation in Computer Systems
 Chapter 2 Data Representation in Computer Systems Chapter 2 Objectives Understand the fundamentals of numerical data representation and manipulation in digital computers. Master the skill of converting
Chapter 2 Data Representation in Computer Systems Chapter 2 Objectives Understand the fundamentals of numerical data representation and manipulation in digital computers. Master the skill of converting
Lab 03 - x86-64: atoi
 CSCI0330 Intro Computer Systems Doeppner Lab 03 - x86-64: atoi Due: October 1, 2017 at 4pm 1 Introduction 1 2 Assignment 1 2.1 Algorithm 2 3 Assembling and Testing 3 3.1 A Text Editor, Makefile, and gdb
CSCI0330 Intro Computer Systems Doeppner Lab 03 - x86-64: atoi Due: October 1, 2017 at 4pm 1 Introduction 1 2 Assignment 1 2.1 Algorithm 2 3 Assembling and Testing 3 3.1 A Text Editor, Makefile, and gdb
III Data Structures. Dynamic sets
 III Data Structures Elementary Data Structures Hash Tables Binary Search Trees Red-Black Trees Dynamic sets Sets are fundamental to computer science Algorithms may require several different types of operations
III Data Structures Elementary Data Structures Hash Tables Binary Search Trees Red-Black Trees Dynamic sets Sets are fundamental to computer science Algorithms may require several different types of operations
Rational Numbers CHAPTER Introduction
 RATIONAL NUMBERS Rational Numbers CHAPTER. Introduction In Mathematics, we frequently come across simple equations to be solved. For example, the equation x + () is solved when x, because this value of
RATIONAL NUMBERS Rational Numbers CHAPTER. Introduction In Mathematics, we frequently come across simple equations to be solved. For example, the equation x + () is solved when x, because this value of
MATH 353 Engineering mathematics III
 MATH 353 Engineering mathematics III Instructor: Francisco-Javier Pancho Sayas Spring 2014 University of Delaware Instructor: Francisco-Javier Pancho Sayas MATH 353 1 / 20 MEET YOUR COMPUTER Instructor:
MATH 353 Engineering mathematics III Instructor: Francisco-Javier Pancho Sayas Spring 2014 University of Delaware Instructor: Francisco-Javier Pancho Sayas MATH 353 1 / 20 MEET YOUR COMPUTER Instructor:
CPSC 121 Some Sample Questions for the Final Exam Tuesday, April 15, 2014, 8:30AM
 CPSC 121 Some Sample Questions for the Final Exam Tuesday, April 15, 2014, 8:30AM Name: Student ID: Signature: Section (circle one): George Steve Your signature acknowledges your understanding of and agreement
CPSC 121 Some Sample Questions for the Final Exam Tuesday, April 15, 2014, 8:30AM Name: Student ID: Signature: Section (circle one): George Steve Your signature acknowledges your understanding of and agreement
unused unused unused unused unused unused
 BCD numbers. In some applications, such as in the financial industry, the errors that can creep in due to converting numbers back and forth between decimal and binary is unacceptable. For these applications
BCD numbers. In some applications, such as in the financial industry, the errors that can creep in due to converting numbers back and forth between decimal and binary is unacceptable. For these applications
Review! Lecture 5 C Memory Management !
 CS61C L05 C Memory Management (1)! inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture 5 C Memory Management 2010-06-28!!! Instructor Paul Pearce! Symmetric multiprocessor! MIPS support for
CS61C L05 C Memory Management (1)! inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture 5 C Memory Management 2010-06-28!!! Instructor Paul Pearce! Symmetric multiprocessor! MIPS support for
CSCI 204 Introduction to Computer Science II Lab 7 Queue ADT
 CSCI 204 Introduction to Computer Science II Lab 7 Queue ADT 1. Objectives In this lab, you will practice the following: Implement the Queue ADT using a structure of your choice, e.g., array or linked
CSCI 204 Introduction to Computer Science II Lab 7 Queue ADT 1. Objectives In this lab, you will practice the following: Implement the Queue ADT using a structure of your choice, e.g., array or linked
CS 342 Software Design Spring 2018 Term Project Part III Saving and Restoring Exams and Exam Components
 CS 342 Software Design Spring 2018 Term Project Part III Saving and Restoring Exams and Exam Components Due: Wednesday 13 March. Electronic copy due at 3:30 P.M. Optional paper copy may be handed in during
CS 342 Software Design Spring 2018 Term Project Part III Saving and Restoring Exams and Exam Components Due: Wednesday 13 March. Electronic copy due at 3:30 P.M. Optional paper copy may be handed in during
Project #3: Dynamic Instruction Scheduling. Due: Wednesday, Dec. 4, 11:00 PM
 ECE 463/521: Fall 2002 Project #3: Dynamic Instruction Scheduling Due: Wednesday, Dec. 4, 11:00 PM Project rules 1. All students are encouraged to work in teams of two, using pair programming. Pair programming
ECE 463/521: Fall 2002 Project #3: Dynamic Instruction Scheduling Due: Wednesday, Dec. 4, 11:00 PM Project rules 1. All students are encouraged to work in teams of two, using pair programming. Pair programming
CS61C : Machine Structures
 inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture 5 C Memory Management 2010-06-28!!! Instructor Paul Pearce! Symmetric multiprocessor! MIPS support for Android MIPS Technologies (founded
inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture 5 C Memory Management 2010-06-28!!! Instructor Paul Pearce! Symmetric multiprocessor! MIPS support for Android MIPS Technologies (founded
12/22/11. Java How to Program, 9/e. Help you get started with Eclipse and NetBeans integrated development environments.
 Java How to Program, 9/e Education, Inc. All Rights Reserved. } Java application programming } Use tools from the JDK to compile and run programs. } Videos at www.deitel.com/books/jhtp9/ Help you get started
Java How to Program, 9/e Education, Inc. All Rights Reserved. } Java application programming } Use tools from the JDK to compile and run programs. } Videos at www.deitel.com/books/jhtp9/ Help you get started
1. Overview This project will help you understand address spaces and virtual memory management.
 Project 2--Memory Worth: 12 points Assigned: Due: 1. Overview This project will help you understand address spaces and virtual memory management. In this project, you will implement an external pager,
Project 2--Memory Worth: 12 points Assigned: Due: 1. Overview This project will help you understand address spaces and virtual memory management. In this project, you will implement an external pager,
Kaltura Blackboard Building Block - KAF
 Kaltura Blackboard Building Block - KAF I. Introduction a. The Kaltura Building Block allows us to add powerful media tools to Blackboard, combing the best features of video sharing, webcam recording,
Kaltura Blackboard Building Block - KAF I. Introduction a. The Kaltura Building Block allows us to add powerful media tools to Blackboard, combing the best features of video sharing, webcam recording,
EECS 311: Data Structures and Data Management Program 1 Assigned: 10/21/10 Checkpoint: 11/2/10; Due: 11/9/10
 EECS 311: Data Structures and Data Management Program 1 Assigned: 10/21/10 Checkpoint: 11/2/10; Due: 11/9/10 1 Project: Scheme Parser. In many respects, the ultimate program is an interpreter. Why? Because
EECS 311: Data Structures and Data Management Program 1 Assigned: 10/21/10 Checkpoint: 11/2/10; Due: 11/9/10 1 Project: Scheme Parser. In many respects, the ultimate program is an interpreter. Why? Because
Machine Problem 1: A Simple Memory Allocator. 100 points Due date: To Be Announced
 Machine Problem 1: A Simple Memory Allocator Introduction 100 points Due date: To Be Announced In this machine problem, you are to develop a simple memory allocator that implements the functions my malloc()
Machine Problem 1: A Simple Memory Allocator Introduction 100 points Due date: To Be Announced In this machine problem, you are to develop a simple memory allocator that implements the functions my malloc()
Final Programming Project
 Due Thursday, Dec. 7, at 5:00 pm Logistics This assignment should be completed in groups of 3. This is not optional -- you are not allowed to complete it on your own, or in groups of any other size. I
Due Thursday, Dec. 7, at 5:00 pm Logistics This assignment should be completed in groups of 3. This is not optional -- you are not allowed to complete it on your own, or in groups of any other size. I
UNIVERSITY OF TORONTO FACULTY OF APPLIED SCIENCE AND ENGINEERING
 UNIVERSITY OF TORONTO FACULTY OF APPLIED SCIENCE AND ENGINEERING APS 105 - Computer Fundamentals Final Examination April 21, 2017 2:00 p.m. - 4:30 p.m. (150 minutes) Examiners: B. Li, J. Rose and M. Stumm
UNIVERSITY OF TORONTO FACULTY OF APPLIED SCIENCE AND ENGINEERING APS 105 - Computer Fundamentals Final Examination April 21, 2017 2:00 p.m. - 4:30 p.m. (150 minutes) Examiners: B. Li, J. Rose and M. Stumm
CS 2704 Project 2: Elevator Simulation Fall 1999
 Elevator Simulation Consider an elevator system, similar to the one on McBryde Hall. At any given time, there may be zero or more elevators in operation. Each operating elevator will be on a particular
Elevator Simulation Consider an elevator system, similar to the one on McBryde Hall. At any given time, there may be zero or more elevators in operation. Each operating elevator will be on a particular
UNIVERSITY OF WISCONSIN MADISON
 CS/ECE 252: INTRODUCTION TO COMPUTER ENGINEERING UNIVERSITY OF WISCONSIN MADISON Prof. Gurindar Sohi TAs: Lisa Ossian, Minsub Shin, Sujith Surendran Midterm Examination 1 In Class (50 minutes) Wednesday,
CS/ECE 252: INTRODUCTION TO COMPUTER ENGINEERING UNIVERSITY OF WISCONSIN MADISON Prof. Gurindar Sohi TAs: Lisa Ossian, Minsub Shin, Sujith Surendran Midterm Examination 1 In Class (50 minutes) Wednesday,
CaGBC Design and Construction Split Review Option
 1 2 3 4 5 6 Let s begin with an overview of what the Split Review process is and how it works. 7 If we were to try and capture what a Split Review is in one sentence, we might state that it is a certification
1 2 3 4 5 6 Let s begin with an overview of what the Split Review process is and how it works. 7 If we were to try and capture what a Split Review is in one sentence, we might state that it is a certification
Lecture 8: September 30
 CMPSCI 377 Operating Systems Fall 2013 Lecture 8: September 30 Lecturer: Prashant Shenoy Scribe: Armand Halbert 8.1 Semaphores A semaphore is a more generalized form of a lock that can be used to regulate
CMPSCI 377 Operating Systems Fall 2013 Lecture 8: September 30 Lecturer: Prashant Shenoy Scribe: Armand Halbert 8.1 Semaphores A semaphore is a more generalized form of a lock that can be used to regulate
HW 3: Malloc CS 162. Due: Monday, March 28, 2016
 CS 162 Due: Monday, March 28, 2016 1 Introduction Your task in this assignment is to implement your own memory allocator from scratch. This will expose you to POSIX interfaces, force you to reason about
CS 162 Due: Monday, March 28, 2016 1 Introduction Your task in this assignment is to implement your own memory allocator from scratch. This will expose you to POSIX interfaces, force you to reason about
Phase One: Process and Semaphore Queue Modules
 CSCI 320 (GOLDWEBER) Handout 4 Fall 00 8/30/00 Phase One: Process and Semaphore Queue Modules Due Date: Friday September 22, 2000. 1 Introduction In this phase you will write two simple modules to create
CSCI 320 (GOLDWEBER) Handout 4 Fall 00 8/30/00 Phase One: Process and Semaphore Queue Modules Due Date: Friday September 22, 2000. 1 Introduction In this phase you will write two simple modules to create
CSC258: Computer Organization. Memory Systems
 CSC258: Computer Organization Memory Systems 1 Summer Independent Studies I m looking for a few students who will be working on campus this summer. In addition to the paid positions posted earlier, I have
CSC258: Computer Organization Memory Systems 1 Summer Independent Studies I m looking for a few students who will be working on campus this summer. In addition to the paid positions posted earlier, I have
GCSE Computer Science
 GCSE Computer Science 4512/2 Computing Fundamentals Report on the Examination 4512 Summer 2015 Version: 1.0 Further copies of this Report are available from aqa.org.uk Copyright 2015 AQA and its licensors.
GCSE Computer Science 4512/2 Computing Fundamentals Report on the Examination 4512 Summer 2015 Version: 1.0 Further copies of this Report are available from aqa.org.uk Copyright 2015 AQA and its licensors.
CSCI 1100L: Topics in Computing Lab Lab 11: Programming with Scratch
 CSCI 1100L: Topics in Computing Lab Lab 11: Programming with Scratch Purpose: We will take a look at programming this week using a language called Scratch. Scratch is a programming language that was developed
CSCI 1100L: Topics in Computing Lab Lab 11: Programming with Scratch Purpose: We will take a look at programming this week using a language called Scratch. Scratch is a programming language that was developed
ECE 2020B Fundamentals of Digital Design Spring problems, 6 pages Exam Two 26 February 2014
 Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand and I will come to you. Please work the exam in pencil and do not separate
Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand and I will come to you. Please work the exam in pencil and do not separate
Slide 1 CS 170 Java Programming 1 Expressions Duration: 00:00:41 Advance mode: Auto
 CS 170 Java Programming 1 Expressions Slide 1 CS 170 Java Programming 1 Expressions Duration: 00:00:41 What is an expression? Expression Vocabulary Any combination of operators and operands which, when
CS 170 Java Programming 1 Expressions Slide 1 CS 170 Java Programming 1 Expressions Duration: 00:00:41 What is an expression? Expression Vocabulary Any combination of operators and operands which, when
CS ) PROGRAMMING ASSIGNMENT 11:00 PM 11:00 PM
 CS3114 (Fall 2017) PROGRAMMING ASSIGNMENT #4 Due Thursday, December 7 th @ 11:00 PM for 100 points Due Tuesday, December 5 th @ 11:00 PM for 10 point bonus Last updated: 11/13/2017 Assignment: Update:
CS3114 (Fall 2017) PROGRAMMING ASSIGNMENT #4 Due Thursday, December 7 th @ 11:00 PM for 100 points Due Tuesday, December 5 th @ 11:00 PM for 10 point bonus Last updated: 11/13/2017 Assignment: Update:
ECE 2035 Programming HW/SW Systems Fall problems, 4 pages Exam Three 14 November Your Name (please PRINT clearly) Signed.
 Your Name (please PRINT clearly) Your Student Number (9 digit) This exam will be conducted according to the Georgia Tech Honor Code. I pledge to neither give nor receive unauthorized assistance on this
Your Name (please PRINT clearly) Your Student Number (9 digit) This exam will be conducted according to the Georgia Tech Honor Code. I pledge to neither give nor receive unauthorized assistance on this
Welcome to CS 135 (Winter 2018)
 Welcome to CS 135 (Winter 2018) Instructors: Sandy Graham, Paul Nijjar Other course personnel: see website for details ISAs (Instructional Support Assistants) IAs (Instructional Apprentices) ISC (Instructional
Welcome to CS 135 (Winter 2018) Instructors: Sandy Graham, Paul Nijjar Other course personnel: see website for details ISAs (Instructional Support Assistants) IAs (Instructional Apprentices) ISC (Instructional
CSE 143: Computer Programming II Summer 2017 HW5: Anagrams (due Thursday, August 3, :30pm)
 CSE 143: Computer Programming II Summer 2017 HW5: Anagrams (due Thursday, August 3, 2017 11:30pm) This assignment focuses on recursive backtracking. Turn in the following files using the link on the course
CSE 143: Computer Programming II Summer 2017 HW5: Anagrams (due Thursday, August 3, 2017 11:30pm) This assignment focuses on recursive backtracking. Turn in the following files using the link on the course
Comparing Algorithms. Example Access Control System. Unsorted lists new record. Unsorted lists search records. Cycle Counts
 CSCI 1900 Discrete Structures Complexity Reading: Kolman, Sections 4.6, 5.2, and 5.3 This presentation uses an example to present the material from the following three sections of our text book. Section
CSCI 1900 Discrete Structures Complexity Reading: Kolman, Sections 4.6, 5.2, and 5.3 This presentation uses an example to present the material from the following three sections of our text book. Section
Homework Assignment #3
 CS 540-2: Introduction to Artificial Intelligence Homework Assignment #3 Assigned: Monday, February 20 Due: Saturday, March 4 Hand-In Instructions This assignment includes written problems and programming
CS 540-2: Introduction to Artificial Intelligence Homework Assignment #3 Assigned: Monday, February 20 Due: Saturday, March 4 Hand-In Instructions This assignment includes written problems and programming
CS50 Supersection (for those less comfortable)
 CS50 Supersection (for those less comfortable) Friday, September 8, 2017 3 4pm, Science Center C Maria Zlatkova, Doug Lloyd Today s Topics Setting up CS50 IDE Variables and Data Types Conditions Boolean
CS50 Supersection (for those less comfortable) Friday, September 8, 2017 3 4pm, Science Center C Maria Zlatkova, Doug Lloyd Today s Topics Setting up CS50 IDE Variables and Data Types Conditions Boolean
Here is a C function that will print a selected block of bytes from such a memory block, using an array-based view of the necessary logic:
 Pointer Manipulations Pointer Casts and Data Accesses Viewing Memory The contents of a block of memory may be viewed as a collection of hex nybbles indicating the contents of the byte in the memory region;
Pointer Manipulations Pointer Casts and Data Accesses Viewing Memory The contents of a block of memory may be viewed as a collection of hex nybbles indicating the contents of the byte in the memory region;
Customizing the Navigation Menu
 Customizing the Navigation Menu New course shells in Blackboard all start out with the same navigation menu. You can customize this navigation menu to give your Blackboard course site a unique look and
Customizing the Navigation Menu New course shells in Blackboard all start out with the same navigation menu. You can customize this navigation menu to give your Blackboard course site a unique look and
CSCI 4210 Operating Systems CSCI 6140 Computer Operating Systems Project 2 (document version 1.4) CPU Scheduling Algorithms
 CSCI 4210 Operating Systems CSCI 6140 Computer Operating Systems Project 2 (document version 14) CPU Scheduling Algorithms Overview This project is due by 11:59:59 PM on Monday, October 5, 2015 Projects
CSCI 4210 Operating Systems CSCI 6140 Computer Operating Systems Project 2 (document version 14) CPU Scheduling Algorithms Overview This project is due by 11:59:59 PM on Monday, October 5, 2015 Projects
Computer Science 385 Design and Analysis of Algorithms Siena College Spring Lab 8: Search Trees Due: Start of your next lab session
 Computer Science 385 Design and Analysis of Algorithms Siena College Spring 2018 Lab 8: Search Trees Due: Start of your next lab session You will be assigned a partner to work with on this lab. Only one
Computer Science 385 Design and Analysis of Algorithms Siena College Spring 2018 Lab 8: Search Trees Due: Start of your next lab session You will be assigned a partner to work with on this lab. Only one
Intro. Scheme Basics. scm> 5 5. scm>
 Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
CS 3330 Exam 2 Fall 2017 Computing ID:
 S 3330 Fall 2017 Exam 2 Variant page 1 of 8 Email I: S 3330 Exam 2 Fall 2017 Name: omputing I: Letters go in the boxes unless otherwise specified (e.g., for 8 write not 8 ). Write Letters clearly: if we
S 3330 Fall 2017 Exam 2 Variant page 1 of 8 Email I: S 3330 Exam 2 Fall 2017 Name: omputing I: Letters go in the boxes unless otherwise specified (e.g., for 8 write not 8 ). Write Letters clearly: if we
ECE 2035 A Programming HW/SW Systems Spring problems, 5 pages Exam Three 13 April Your Name (please print clearly)
 Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand; do not leave your seat. Please work the exam in pencil and do not separate
Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand; do not leave your seat. Please work the exam in pencil and do not separate
Worst-case running time for RANDOMIZED-SELECT
 Worst-case running time for RANDOMIZED-SELECT is ), even to nd the minimum The algorithm has a linear expected running time, though, and because it is randomized, no particular input elicits the worst-case
Worst-case running time for RANDOMIZED-SELECT is ), even to nd the minimum The algorithm has a linear expected running time, though, and because it is randomized, no particular input elicits the worst-case
CS61B Lecture #14: Integers
 Announcement: CS61B Lecture #14: Integers Project #0 due Tuesday night. Programming contest SATURDAY! You can still sign up at https://inst.eecs.berkeley.edu/~ctest/contest/register. Test #1 will be Tuesday,
Announcement: CS61B Lecture #14: Integers Project #0 due Tuesday night. Programming contest SATURDAY! You can still sign up at https://inst.eecs.berkeley.edu/~ctest/contest/register. Test #1 will be Tuesday,
AP Computer Science Unit 1. Writing Programs Using BlueJ
 AP Computer Science Unit 1. Writing Programs Using BlueJ 1. Open up BlueJ. Click on the Project menu and select New Project. You should see the window on the right. Navigate to wherever you plan to save
AP Computer Science Unit 1. Writing Programs Using BlueJ 1. Open up BlueJ. Click on the Project menu and select New Project. You should see the window on the right. Navigate to wherever you plan to save
