INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT
|
|
|
- Lorin Morrison
- 5 years ago
- Views:
Transcription
1 INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT USER GUIDE: INSTALLING THE ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES VERSION 1.2 ECB-PUBLIC 24-Nov-2011
2 ECB - Unrestricted 2 USER GUIDE: INSTALLING THE ESCB-PKI ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES
3 ECB - Restricted TABLE OF CONTENTS 1. Introduction The ESCB-PKI certification hierarchy Installing the ESCB-PKI root and subordinate Certification Authorities Obtain the certificates for the root and subordinate Certification Authorities Install the root Certification Authority Install the subordinate Certification Authority USER GUIDE: INSTALLING THE ESCB-PKI ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES 3
4 ECB - Unrestricted Project name: ESCB-PKI Author: ESCB-PKI team File name: ESCB-PKI - Install Root and Subordinate CAs v.1.2.docx Version: 1.2 Date of issue: Status: Final Approved by: Distribution: RELEASE NOTES In order to follow the current status of this document, the following matrix is provided. The numbers mentioned in the column Release number refer to the current version of the document. Release number Status Date of issue Revisions 0.1 Draft Initial version. 1.0 Draft BdE Revision 1.1 Draft BdE Revision 1.2 Final Format 4 USER GUIDE: INSTALLING THE ESCB-PKI ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES
5 ECB - Restricted 1. INTRODUCTION This guide describes how to install the ESCB-PKI root and subordinate Certification Authorities. The screen shots are included only as a reference. Depending on the operating system version and web browser configuration used, the real screens could be slightly different. Note: The last version of this document can be found in the Support tab of the ESCB-PKI Website, along with other ESCB-PKI guides and manuals. USER GUIDE: INSTALLING THE ESCB-PKI ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES 5
6 ECB - Unrestricted 2. THE ESCB-PKI CERTIFICATION HIERARCHY The ESCB Public Key Infrastructure is based on the following certificate chain: Where: - Root CA: is the first-level Certification Authority. This CA only issues certificates for itself and its Subordinate CA. Its most significant data are: Subject Serial Number Issuer CN=ESCB-PKI ROOT CA, O=EUROPEAN SYSTEM OF CENTRAL BANKS, C=EU C5F 91E8 162F 4E00 73F6 6AB8 71D8 CN=ESCB-PKI ROOT CA, O=EUROPEAN SYSTEM OF CENTRAL BANKS, C=EU Validity From :35:34 to :35:34 Thumbprint (SHA-1) FBA FB19 BDBC A ED48 4D72 DD4B - Online CA: this second-level Certification Authority is subordinate to the Root CA. It is responsible for issuing certificates for the ESCB-PKI end entities. Its most significant data are: Subject Serial Number Issuer CN= ESCB-PKI ONLINE CA, O=EUROPEAN SYSTEM OF CENTRAL BANKS, C=EU 660C 9B12 9A0A 6C DD 54A0 ED2D CN=ESCB-PKI ROOT CA, O=EUROPEAN SYSTEM OF CENTRAL BANKS, C=EU Validity From :46:35 to :46:35 Thumbprint (SHA-1) E976 D216 4A5F 62DA C058 6BE0 EC10 EF24 36B8 12AC - End entities: they are the ESCB-PKI users that hold one or several digital certificates. Before using any ESCB-PKI certificate, it is required to install the root and subordinate CA certificates; otherwise the computer will not trust the certificate. 6 USER GUIDE: INSTALLING THE ESCB-PKI ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES
7 ECB - Restricted 3. INSTALLING THE ESCB-PKI ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES There are many technical possibilities to trust a Certificate Authority certificate. Check with your local Help Desk which options are available at your organisation. Below you can find the steps necessary to install the root and subordinate CA certificates in your computer for the Windows user account you use to log in. In case you require installing these certificates among several computers or for several user accounts, ask your local Help Desk OBTAIN THE CERTIFICATES FOR THE ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES These certificates can be downloaded at the ESCB-PKI website, INSTALL THE ROOT CERTIFICATION AUTHORITY - Double-click on the root CA certificate file (rootca.crt). You will see the following screen indicating that the certificate is not trusted: - In case the certificate is not tagged as not trusted, it means that your computer already trusts the certificate and you can skip the rest of the steps. USER GUIDE: INSTALLING THE ESCB-PKI ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES 7
8 ECB - Unrestricted - Click on the Details tab and check the most significant data against the certificate information provided in section 2: - If all the information matches, click on the General tab again and press the Install Certificate button. The Certificate Import wizard will start: 8 USER GUIDE: INSTALLING THE ESCB-PKI ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES
9 ECB - Restricted - Press Next. Select the Trusted Root Certification Authorities store: - Press Next. The following screen will be shown: USER GUIDE: INSTALLING THE ESCB-PKI ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES 9
10 ECB - Unrestricted - Press Finish. The following security warning will be shown: - Check the SHA-1 thumbprint against the one in section 2. Press Yes and then OK in the The import was successful pop-up message INSTALL THE SUBORDINATE CERTIFICATION AUTHORITY - Double-click on the subordinate CA certificate file (subca.crt). You will see the following screen: 10 USER GUIDE: INSTALLING THE ESCB-PKI ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES
11 ECB - Restricted - Click on the Details tab and check the most significant data against the certificate information provided in section 2: - Click on the Certification Path tab to make sure that the root CA certificate is properly installed in your computer (if that is not the case, install it again): USER GUIDE: INSTALLING THE ESCB-PKI ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES 11
12 ECB - Unrestricted - Click on the General tab again and press the Install Certificate button. The Certificate Import wizard will start: - Press Next. Select the Intermediate Certification Authorities store: 12 USER GUIDE: INSTALLING THE ESCB-PKI ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES
13 ECB - Restricted - Press Next. The following screen will be shown: - Press Finish and OK in the The import was successful screen. USER GUIDE: INSTALLING THE ESCB-PKI ROOT AND SUBORDINATE CERTIFICATION AUTHORITIES 13
DECISION OF THE EUROPEAN CENTRAL BANK
 L 74/30 Official Journal of the European Union 16.3.2013 DECISIONS DECISION OF THE EUROPEAN CENTRAL BANK of 11 January 2013 laying down the framework for a public key infrastructure for the European System
L 74/30 Official Journal of the European Union 16.3.2013 DECISIONS DECISION OF THE EUROPEAN CENTRAL BANK of 11 January 2013 laying down the framework for a public key infrastructure for the European System
INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT
 INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT ESCB-PKI REGISTRATION AUTHORITY APPLICATION MOST COMMON ERRORS VERSION 1.2 ECB-PUBLIC 15-November-2012 ESCB-PKI - Common errors v.1.2.docx Page 2 of 20
INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT ESCB-PKI REGISTRATION AUTHORITY APPLICATION MOST COMMON ERRORS VERSION 1.2 ECB-PUBLIC 15-November-2012 ESCB-PKI - Common errors v.1.2.docx Page 2 of 20
FedLine Web Customer Certificate Contingency Procedures
 FedLine Web Customer Certificate Contingency Procedures Version 2.0 Contents FedLine Web Certificate Contingency Procedures... 2 Certificate Export Procedures... 2 Certificate Import Procedures... 10 Installing
FedLine Web Customer Certificate Contingency Procedures Version 2.0 Contents FedLine Web Certificate Contingency Procedures... 2 Certificate Export Procedures... 2 Certificate Import Procedures... 10 Installing
INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT
 INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT SUBSCRIBER S GUIDE VERSION 1.3 ECB-PUBLIC 15-April-2014 ESCB-PKI - Subscriber's Procedures v.1.3.docx Page 2 of 26 TABLE OF CONTENTS GLOSSARY AND ACRONYMS...
INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT SUBSCRIBER S GUIDE VERSION 1.3 ECB-PUBLIC 15-April-2014 ESCB-PKI - Subscriber's Procedures v.1.3.docx Page 2 of 26 TABLE OF CONTENTS GLOSSARY AND ACRONYMS...
Banco de España electronic services
 Information Systems Department 03.09.2018 Banco de España electronic services Installation of Banco de España certification hierarchy CONTENTS 1 Introduction 1 2 Installation of the certification hierarchy
Information Systems Department 03.09.2018 Banco de España electronic services Installation of Banco de España certification hierarchy CONTENTS 1 Introduction 1 2 Installation of the certification hierarchy
Certificate Retrieval Procedures
 `` Certificate Retrieval Procedures Version 2.2 2018 Federal Reserve Banks Contents Federal Reserve Bank Certificate Retrieval Overview and Preparation Procedures... 2 Certificate Creation Procedures...
`` Certificate Retrieval Procedures Version 2.2 2018 Federal Reserve Banks Contents Federal Reserve Bank Certificate Retrieval Overview and Preparation Procedures... 2 Certificate Creation Procedures...
FedLine Web Certificate Retrieval Procedures
 Version 2.0 Contents Federal Reserve Bank Certificate Retrieval Overview and Preparation Procedures... 2 Certificate Creation Procedures... 3 Installing the Federal Reserve Banks Certificate Authority
Version 2.0 Contents Federal Reserve Bank Certificate Retrieval Overview and Preparation Procedures... 2 Certificate Creation Procedures... 3 Installing the Federal Reserve Banks Certificate Authority
Registration and Renewal procedure for Belfius Certificate
 Registration and Renewal procedure for Belfius Certificate GTU Environment Table of contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. CONTACT... 3 3. REGISTRATION PROCEDURE... 4 3.1 PRE-REQUISITES...
Registration and Renewal procedure for Belfius Certificate GTU Environment Table of contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. CONTACT... 3 3. REGISTRATION PROCEDURE... 4 3.1 PRE-REQUISITES...
Internet Explorer/ Edge/ Chrome/ Opera (Windows) Edition
 Internet Explorer/ Edge/ Chrome/ Opera (Windows) Edition Revision History Rev. Date (YYYY/MM/DD) Description Editor V.1.0 2015/4/1 First revision NII V.2.0 2018/2/26 Operating environment updates: Microsoft
Internet Explorer/ Edge/ Chrome/ Opera (Windows) Edition Revision History Rev. Date (YYYY/MM/DD) Description Editor V.1.0 2015/4/1 First revision NII V.2.0 2018/2/26 Operating environment updates: Microsoft
How to Digital Sign a PDF document With Nexus Personal software
 How to Digital Sign a PDF document With Nexus Personal software Version 1.1 Page 1 from 11 1. Introduction This document describes the procedure must be followed to digitally sign a PDF document using
How to Digital Sign a PDF document With Nexus Personal software Version 1.1 Page 1 from 11 1. Introduction This document describes the procedure must be followed to digitally sign a PDF document using
Registration and Renewal procedure for Belfius Certificate
 Registration and Renewal procedure for Belfius Certificate Table of contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. CONTACT... 3 3. CONFIGURATION... 3 4. REGISTRATION PROCEDURE... 4 4.1 PRE-REQUISITES...
Registration and Renewal procedure for Belfius Certificate Table of contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. CONTACT... 3 3. CONFIGURATION... 3 4. REGISTRATION PROCEDURE... 4 4.1 PRE-REQUISITES...
RPKI Trust Anchor. Geoff Huston APNIC
 RPKI Trust Anchor Geoff Huston APNIC Public Keys How can you trust a digital signature?? What if you have never met the signer and have no knowledge of them or their keys? One approach is transitive trust
RPKI Trust Anchor Geoff Huston APNIC Public Keys How can you trust a digital signature?? What if you have never met the signer and have no knowledge of them or their keys? One approach is transitive trust
Copyright
 This video will look at the different components that make up Active Directory Certificate Services and which services you should look at installing these components on. Which components to install where?
This video will look at the different components that make up Active Directory Certificate Services and which services you should look at installing these components on. Which components to install where?
The cache is 4-way set associative, with 4-byte blocks, and 16 total lines
 Sample Problem 1 Assume the following memory setup: Virtual addresses are 20 bits wide Physical addresses are 15 bits wide The page size if 1KB (2 10 bytes) The TLB is 2-way set associative, with 8 total
Sample Problem 1 Assume the following memory setup: Virtual addresses are 20 bits wide Physical addresses are 15 bits wide The page size if 1KB (2 10 bytes) The TLB is 2-way set associative, with 8 total
Managing Certificates
 CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
4. Specifications and Additional Information
 4. Specifications and Additional Information AGX52004-1.0 8B/10B Code This section provides information about the data and control codes for Arria GX devices. Code Notation The 8B/10B data and control
4. Specifications and Additional Information AGX52004-1.0 8B/10B Code This section provides information about the data and control codes for Arria GX devices. Code Notation The 8B/10B data and control
PKI Contacts PKI for Fraunhofer Contacts
 Fraunhofer Competence Center PKI PKI Contacts PKI for Fraunhofer Contacts User manual for communication partners of the Fraunhofer-Gesellschaft Author[s]: Uwe Bendisch, Maximilian Gottwald As at: 03.02.2017
Fraunhofer Competence Center PKI PKI Contacts PKI for Fraunhofer Contacts User manual for communication partners of the Fraunhofer-Gesellschaft Author[s]: Uwe Bendisch, Maximilian Gottwald As at: 03.02.2017
CIS-331 Spring 2016 Exam 1 Name: Total of 109 Points Version 1
 Version 1 Instructions Write your name on the exam paper. Write your name and version number on the top of the yellow paper. Answer Question 1 on the exam paper. Answer Questions 2-4 on the yellow paper.
Version 1 Instructions Write your name on the exam paper. Write your name and version number on the top of the yellow paper. Answer Question 1 on the exam paper. Answer Questions 2-4 on the yellow paper.
QUALIFYING ATTESTATION LETTER
 TAYLLORCOX s.r.o. Member of TAYLLORCOX UK Ltd. 75 King William St., EC4N, London, UK TAYLLORCOX PCEB, certification body No. 3239, accredited in accordance with ČSN EN ISO/IEC 17065:2013 by Czech Accreditation
TAYLLORCOX s.r.o. Member of TAYLLORCOX UK Ltd. 75 King William St., EC4N, London, UK TAYLLORCOX PCEB, certification body No. 3239, accredited in accordance with ČSN EN ISO/IEC 17065:2013 by Czech Accreditation
FUJITSU Cloud Service S5 Certificate Management
 FUJITSU Cloud Service S5 Certificate Management This guide describes the process for reissuing, importing and exporting Certificates in the FUJITSU Cloud Service S5 How to Manage Certificates For security
FUJITSU Cloud Service S5 Certificate Management This guide describes the process for reissuing, importing and exporting Certificates in the FUJITSU Cloud Service S5 How to Manage Certificates For security
Verify certificate chain with OpenSSL
 Verify certificate chain with OpenSSL 1 / 5 Author : Tobias Hofmann Date : February 18, 2016 A good TLS setup includes providing a complete certificate chain to your clients. This means that your web server
Verify certificate chain with OpenSSL 1 / 5 Author : Tobias Hofmann Date : February 18, 2016 A good TLS setup includes providing a complete certificate chain to your clients. This means that your web server
PKI Configuration Examples
 PKI Configuration Examples Keywords: PKI, CA, RA, IKE, IPsec, SSL Abstract: The Public Key Infrastructure (PKI) is a general security infrastructure for providing information security through public key
PKI Configuration Examples Keywords: PKI, CA, RA, IKE, IPsec, SSL Abstract: The Public Key Infrastructure (PKI) is a general security infrastructure for providing information security through public key
Managing the SSL Certificate for the ESRS HTTPS Listener Service Technical Notes P/N Rev 01 July, 2012
 Managing the SSL Certificate for the ESRS HTTPS Listener Service Technical Notes P/N 300-013-818 Rev 01 July, 2012 This document contains information on these topics: Introduction... 2 Terminology... 2
Managing the SSL Certificate for the ESRS HTTPS Listener Service Technical Notes P/N 300-013-818 Rev 01 July, 2012 This document contains information on these topics: Introduction... 2 Terminology... 2
This document describes the configuration of Secure Sockets Layer (SSL) decryption on the FirePOWER Module using ASDM (On-Box Management).
 Contents Introduction Prerequisites Requirements Components Used Background Information Outbound SSL Decryption Inbound SSL Decryption Configuration for SSL Decryption Outbound SSL decryption (Decrypt
Contents Introduction Prerequisites Requirements Components Used Background Information Outbound SSL Decryption Inbound SSL Decryption Configuration for SSL Decryption Outbound SSL decryption (Decrypt
CIS-331 Fall 2013 Exam 1 Name: Total of 120 Points Version 1
 Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. NOTE: Router E should only be used for Internet traffic. Router A Router
Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. NOTE: Router E should only be used for Internet traffic. Router A Router
FBCA Cross-Certificate Remover 1.11 User Guide
 DoD Public Key Enablement (PKE) User Guide FBCA Cross-Certificate Remover Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke FBCA Cross-Certificate Remover 1.11 User Guide 12 February 2014 Version
DoD Public Key Enablement (PKE) User Guide FBCA Cross-Certificate Remover Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke FBCA Cross-Certificate Remover 1.11 User Guide 12 February 2014 Version
Certificate. Certificate number: Certified by EY CertifyPoint since: July 10, 2018
 Certificate Certificate number: 2018-016 Certified by EY CertifyPoint since: July 10, 2018 Based on certification examination in conformity with defined requirements in ISO/IEC 17065:2012 and ETSI EN 319
Certificate Certificate number: 2018-016 Certified by EY CertifyPoint since: July 10, 2018 Based on certification examination in conformity with defined requirements in ISO/IEC 17065:2012 and ETSI EN 319
ECC Certificate Addendum to the Comodo EV Certification Practice Statement v.1.03
 ECC Certificate Addendum to the Comodo EV Certification Practice Statement v.1.03 Comodo CA, Ltd. ECC Certificate Addendum to Comodo EV CPS v. 1.03 6 March 2008 3rd Floor, Office Village, Exchange Quay,
ECC Certificate Addendum to the Comodo EV Certification Practice Statement v.1.03 Comodo CA, Ltd. ECC Certificate Addendum to Comodo EV CPS v. 1.03 6 March 2008 3rd Floor, Office Village, Exchange Quay,
CIS-331 Exam 2 Spring 2016 Total of 110 Points Version 1
 Version 1 1. (20 Points) Given the class A network address 121.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 8,100 subnets? b. (5 Points) What is
Version 1 1. (20 Points) Given the class A network address 121.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 8,100 subnets? b. (5 Points) What is
QUALIFYING ATTESTATION LETTER
 TAYLLORCOX s.r.o. Member of TAYLLORCOX UK Ltd. 75 King William St., EC4N, London, UK TAYLLORCOX PCEB, certification body No. 3239, accredited in accordance with ČSN EN ISO/IEC 17065:2013 by Czech Accreditation
TAYLLORCOX s.r.o. Member of TAYLLORCOX UK Ltd. 75 King William St., EC4N, London, UK TAYLLORCOX PCEB, certification body No. 3239, accredited in accordance with ČSN EN ISO/IEC 17065:2013 by Czech Accreditation
CIS-331 Exam 2 Fall 2015 Total of 105 Points Version 1
 Version 1 1. (20 Points) Given the class A network address 117.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 4,000 subnets? b. (5 Points) What is
Version 1 1. (20 Points) Given the class A network address 117.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 4,000 subnets? b. (5 Points) What is
CDX Vendor Certificate Process
 CDX Vendor Certificate Process 10-June-2014 Version 0.03 Status: Draft CDX Vendor Certificate Process Page 1 of 17 Document Version Control Release Date Version Status / Comments 13 January 2014 0.01 Initial
CDX Vendor Certificate Process 10-June-2014 Version 0.03 Status: Draft CDX Vendor Certificate Process Page 1 of 17 Document Version Control Release Date Version Status / Comments 13 January 2014 0.01 Initial
Web CCaR Login Troubleshooting Guide
 Web CCaR Login Troubleshooting Guide Web CCaR Login Troubleshooting Guide ALTESS Implementation Copyright 2015 by Integrated Data Services, Inc. All rights reserved. No part of this copyrighted work may
Web CCaR Login Troubleshooting Guide Web CCaR Login Troubleshooting Guide ALTESS Implementation Copyright 2015 by Integrated Data Services, Inc. All rights reserved. No part of this copyrighted work may
AXIS Device Manager HTTPS certificate management
 HOW TO AXIS Device Manager AXIS Device Manager HTTPS certificate management Created: December 01, 2017 Last updated: December 01, 2017 Rev: 1.0 1 Please note that AXIS does not take any responsibility
HOW TO AXIS Device Manager AXIS Device Manager HTTPS certificate management Created: December 01, 2017 Last updated: December 01, 2017 Rev: 1.0 1 Please note that AXIS does not take any responsibility
ZN-DN312XE-M Quick User Guide
 ZN-DN312XE-M Quick User Guide This manual provides instructions for quick installation and basic configuration of your IP device. Step1. Connect cables to IP device Connect required cables to the device
ZN-DN312XE-M Quick User Guide This manual provides instructions for quick installation and basic configuration of your IP device. Step1. Connect cables to IP device Connect required cables to the device
Blue Coat ProxySG First Steps Solution for Controlling HTTPS SGOS 6.7
 Blue Coat ProxySG First Steps Solution for Controlling HTTPS SGOS 6.7 Legal Notice Copyright 2018 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the
Blue Coat ProxySG First Steps Solution for Controlling HTTPS SGOS 6.7 Legal Notice Copyright 2018 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the
The appendix to the certificate is part of the certificate and consists of 3 pages.
 The certification body of TÜV Informationstechnik GmbH hereby awards this certificate to the company Microsec Ltd. Záhony utca 7. H-1031 Budapest, Hungary to confirm that its trust service e-szignó Qualified
The certification body of TÜV Informationstechnik GmbH hereby awards this certificate to the company Microsec Ltd. Záhony utca 7. H-1031 Budapest, Hungary to confirm that its trust service e-szignó Qualified
AeroMACS Public Key Infrastructure (PKI) Users Overview
 AeroMACS Public Key Infrastructure (PKI) Users Overview WiMAX Forum Proprietary Copyright 2019 WiMAX Forum. All Rights Reserved. WiMAX, Mobile WiMAX, Fixed WiMAX, WiMAX Forum, WiMAX Certified, WiMAX Forum
AeroMACS Public Key Infrastructure (PKI) Users Overview WiMAX Forum Proprietary Copyright 2019 WiMAX Forum. All Rights Reserved. WiMAX, Mobile WiMAX, Fixed WiMAX, WiMAX Forum, WiMAX Certified, WiMAX Forum
Acquirer JCB EMV Test Card Set
 Acquirer JCB EMV Test Card Set July, 2017 Powered by Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available
Acquirer JCB EMV Test Card Set July, 2017 Powered by Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available
Guide Certificate Administration
 Version 1.4 Guide Certificate Administration Swish Certificate Management Datum: 2018/12/08 Table of content 1. Swish Certificate Management... 3 1.1. Background... 3 1.2. Certificate Administration...
Version 1.4 Guide Certificate Administration Swish Certificate Management Datum: 2018/12/08 Table of content 1. Swish Certificate Management... 3 1.1. Background... 3 1.2. Certificate Administration...
Blue Coat Security First Steps Solution for Controlling HTTPS
 Solution for Controlling HTTPS SGOS 6.5 Legal Notice Copyright 2017 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat logo are trademarks
Solution for Controlling HTTPS SGOS 6.5 Legal Notice Copyright 2017 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the Blue Coat logo are trademarks
Access to RTE s Information System by software certificates under Microsoft Windows 7
 by software certificates under Microsoft Windows 7 PKI User guide Version 4, 01/01/2017 Programmes & SI (PSI) TOUR MARCHAND 41 RUE BERTHELOT - 92411 COURBEVOIE CEDEX TEL : 01.78.66.50.00 - FAX : 01.78.66.50.64
by software certificates under Microsoft Windows 7 PKI User guide Version 4, 01/01/2017 Programmes & SI (PSI) TOUR MARCHAND 41 RUE BERTHELOT - 92411 COURBEVOIE CEDEX TEL : 01.78.66.50.00 - FAX : 01.78.66.50.64
Instructions for connecting to the FDIBA Wireless Network (Windows Vista)
 Instructions for connecting to the FDIBA Wireless Network (Windows Vista) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network (Windows Vista) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
July Registration of a Cyrillic Character Set. Status of this Memo
 Network Working Group Request for Comments: 1489 A. Chernov RELCOM Development Team July 1993 Status of this Memo Registration of a Cyrillic Character Set This memo provides information for the Internet
Network Working Group Request for Comments: 1489 A. Chernov RELCOM Development Team July 1993 Status of this Memo Registration of a Cyrillic Character Set This memo provides information for the Internet
Guide Certifikatsadministration
 Version 1.0 Guide Certifikatsadministration Swish Certificate Management Datum: 2016/01/18 Table of content 1. Swish Certificate Management... 3 1.1. Background... 3 1.2. Certificate Administration...
Version 1.0 Guide Certifikatsadministration Swish Certificate Management Datum: 2016/01/18 Table of content 1. Swish Certificate Management... 3 1.1. Background... 3 1.2. Certificate Administration...
A certificate request and installation, can be performed by using the following tools:
 The ACBIS Business Intelligence Extraction Service (BiXtractor) version 3.2 uses certificates and now requires you to have a valid DoD issued certificate installed on your machine. This document will provide
The ACBIS Business Intelligence Extraction Service (BiXtractor) version 3.2 uses certificates and now requires you to have a valid DoD issued certificate installed on your machine. This document will provide
First Data Dual Interface EMV Test Card Set. Version 1.20
 First Data Dual Interface EMV Test Card Set August, 2016 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available
First Data Dual Interface EMV Test Card Set August, 2016 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available
How to Connect with SSL Network Extender using a Certificate
 How to Connect with SSL Network Extender using a Certificate 29 August 2011 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
How to Connect with SSL Network Extender using a Certificate 29 August 2011 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
First Data EMV Test Card Set. Version 1.30
 First Data EMV Test Card Set.30 January, 2018 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available from industry
First Data EMV Test Card Set.30 January, 2018 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available from industry
First Data EMV Test Card Set. Version 2.00
 First Data EMV Test Card Set.00 February, 2018 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available from industry
First Data EMV Test Card Set.00 February, 2018 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available from industry
Genesys Security Deployment Guide. What You Need
 Genesys Security Deployment Guide What You Need 12/27/2017 Contents 1 What You Need 1.1 TLS Certificates 1.2 Generating Certificates using OpenSSL and Genesys Security Pack 1.3 Generating Certificates
Genesys Security Deployment Guide What You Need 12/27/2017 Contents 1 What You Need 1.1 TLS Certificates 1.2 Generating Certificates using OpenSSL and Genesys Security Pack 1.3 Generating Certificates
egov & PKI By: Alaa Eldin Mahmoud Aly YOUR LOGO
 egov & PKI By: Alaa Eldin Mahmoud Aly YOUR LOGO e-government Survey 2014 United Nations Page 2 EGDI: E-Government Development Index National ID & Digital Signature Estonian Prime Minister Andrus Ansip
egov & PKI By: Alaa Eldin Mahmoud Aly YOUR LOGO e-government Survey 2014 United Nations Page 2 EGDI: E-Government Development Index National ID & Digital Signature Estonian Prime Minister Andrus Ansip
CIS-331 Fall 2014 Exam 1 Name: Total of 109 Points Version 1
 Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. Router A Router B Router C Router D Network Next Hop Next Hop Next Hop Next
Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. Router A Router B Router C Router D Network Next Hop Next Hop Next Hop Next
SAML-Based SSO Configuration
 Prerequisites, page 1 SAML SSO Configuration Task Flow, page 5 Reconfigure OpenAM SSO to SAML SSO Following an Upgrade, page 9 SAML SSO Deployment Interactions and Restrictions, page 9 Prerequisites NTP
Prerequisites, page 1 SAML SSO Configuration Task Flow, page 5 Reconfigure OpenAM SSO to SAML SSO Following an Upgrade, page 9 SAML SSO Deployment Interactions and Restrictions, page 9 Prerequisites NTP
Energy Trading System (ETS) Training Environment User Access Enrolment Procedures
 Energy Trading System (ETS) Training Environment User Access Enrolment Procedures Participants that require access to the Energy Trading System (ETS) Training Environment will need to apply for a digital
Energy Trading System (ETS) Training Environment User Access Enrolment Procedures Participants that require access to the Energy Trading System (ETS) Training Environment will need to apply for a digital
SECARDEO. certbox. Help-Manual. Secardeo GmbH Release:
 certbox Help-Manual Secardeo GmbH Release: 02.12.2014 certbox Help Manual 02.12.2014 Table of Contents 1 Search and retrieve Public Key Certificates... 1 1.1 Search by an e-mail address... 1 1.2 Download
certbox Help-Manual Secardeo GmbH Release: 02.12.2014 certbox Help Manual 02.12.2014 Table of Contents 1 Search and retrieve Public Key Certificates... 1 1.1 Search by an e-mail address... 1 1.2 Download
CIS-331 Exam 2 Fall 2014 Total of 105 Points. Version 1
 Version 1 1. (20 Points) Given the class A network address 119.0.0.0 will be divided into a maximum of 15,900 subnets. a. (5 Points) How many bits will be necessary to address the 15,900 subnets? b. (5
Version 1 1. (20 Points) Given the class A network address 119.0.0.0 will be divided into a maximum of 15,900 subnets. a. (5 Points) How many bits will be necessary to address the 15,900 subnets? b. (5
Your Guide to Merchant Online
 Your Guide to Merchant Online Merchant Online User Guide Contents 1 Introduction... 2 2 Using the Merchant Online Portal... 2 2.1 Signing In for the First Time... 2 2.2 Updating Your Information... 4 2.2.1
Your Guide to Merchant Online Merchant Online User Guide Contents 1 Introduction... 2 2 Using the Merchant Online Portal... 2 2.1 Signing In for the First Time... 2 2.2 Updating Your Information... 4 2.2.1
Wavecrest Certificate SHA-512
 Wavecrest InstallationGuide Wavecrest Certificate SHA-512 www.wavecrest.net Copyright Copyright 1996-2018, Wavecrest Computing, Inc. All rights reserved. Use of this product and this manual is subject
Wavecrest InstallationGuide Wavecrest Certificate SHA-512 www.wavecrest.net Copyright Copyright 1996-2018, Wavecrest Computing, Inc. All rights reserved. Use of this product and this manual is subject
Configuring Remote Access using the RDS Gateway
 Configuring Remote Access using the RDS Gateway Author: AC, SNE Contents Introduction... 3 Pre-requisites... 3 Supported Operating Systems... 3 Installing the I.T. Services Certificate Authority Root Certificate...
Configuring Remote Access using the RDS Gateway Author: AC, SNE Contents Introduction... 3 Pre-requisites... 3 Supported Operating Systems... 3 Installing the I.T. Services Certificate Authority Root Certificate...
Acquirer JCB Dual Interface EMV Test Card Set
 Acquirer JCB Dual Interface EMV Test Card Set.00 July, 2018 Powered by Disclaimer Information provided in this document describes capabilities available at the time of developing and delivering this document
Acquirer JCB Dual Interface EMV Test Card Set.00 July, 2018 Powered by Disclaimer Information provided in this document describes capabilities available at the time of developing and delivering this document
Gateway Ascii Command Protocol
 Gateway Ascii Command Protocol Table Of Contents Introduction....2 Ascii Commands.....3 Messages Received From The Gateway....3 Button Down Message.....3 Button Up Message....3 Button Maintain Message....4
Gateway Ascii Command Protocol Table Of Contents Introduction....2 Ascii Commands.....3 Messages Received From The Gateway....3 Button Down Message.....3 Button Up Message....3 Button Maintain Message....4
for Unclassified Systems
 DoD Public Key Enablement (PKE) Reference Guide InstallRoot 5.0 User Guide Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke InstallRoot 5.0 User Guide for Unclassified Systems 7 December 2015
DoD Public Key Enablement (PKE) Reference Guide InstallRoot 5.0 User Guide Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke InstallRoot 5.0 User Guide for Unclassified Systems 7 December 2015
IT Quick Reference Guides Connecting to SU-Secure using Windows 8
 IT Quick Reference Guides Connecting to SU-Secure using Windows 8 Windows Guides CONNECTING TO SU-SECURE WI-FI This document will give you instructions on how to connect your Windows 8 Computer to our
IT Quick Reference Guides Connecting to SU-Secure using Windows 8 Windows Guides CONNECTING TO SU-SECURE WI-FI This document will give you instructions on how to connect your Windows 8 Computer to our
Mitel MiVoice Connect Security Certificates
 Application Note - AN16036 MT App Note 16036 (AN 16036) May, 2018 Mitel MiVoice Connect Security Certificates Description: This Application Note describes the use of security certificates in Mitel MiVoice
Application Note - AN16036 MT App Note 16036 (AN 16036) May, 2018 Mitel MiVoice Connect Security Certificates Description: This Application Note describes the use of security certificates in Mitel MiVoice
The appendix to the certificate is part of the certificate and consists of 3 pages.
 The certification body of TÜV Informationstechnik GmbH hereby awards this certificate to the company Microsec Ltd. Záhony utca 7. H-1031 Budapest, Hungary to confirm that its trust service e-szignó Qualified
The certification body of TÜV Informationstechnik GmbH hereby awards this certificate to the company Microsec Ltd. Záhony utca 7. H-1031 Budapest, Hungary to confirm that its trust service e-szignó Qualified
esigntrust Qualified Certificate Installation
 esigntrust Qualified Certificate Installation For Microsoft Windows System & Internet Explorer User Equipment Installation Guide Version. 2017-01 Copyright Correios e Telecomunicações de Macau, 2017 All
esigntrust Qualified Certificate Installation For Microsoft Windows System & Internet Explorer User Equipment Installation Guide Version. 2017-01 Copyright Correios e Telecomunicações de Macau, 2017 All
Audit Attestation for AGENCE NATIONALE DE LA CERTIFICATION ELECTRONIQUE
 Conformity Assessment Body eidas Trust Service Providers ISO 27001 LA ISO 27001 LI ISO 27001 RM ISO 27005 Audit Attestation for AGENCE NATIONALE DE LA CERTIFICATION ELECTRONIQUE Siège: Parc Technologie
Conformity Assessment Body eidas Trust Service Providers ISO 27001 LA ISO 27001 LI ISO 27001 RM ISO 27005 Audit Attestation for AGENCE NATIONALE DE LA CERTIFICATION ELECTRONIQUE Siège: Parc Technologie
AirWatch Mobile Device Management
 RSA Ready Implementation Guide for 3rd Party PKI Applications Last Modified: November 26 th, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product Description
RSA Ready Implementation Guide for 3rd Party PKI Applications Last Modified: November 26 th, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product Description
ms-help://ms.technet.2004apr.1033/ad/tnoffline/prodtechnol/ad/windows2000/howto/mapcerts.htm
 Page 1 of 8 Active Directory Step-by-Step Guide to Mapping Certificates to User Accounts Introduction The Windows 2000 operating system provides a rich administrative model for managing user accounts.
Page 1 of 8 Active Directory Step-by-Step Guide to Mapping Certificates to User Accounts Introduction The Windows 2000 operating system provides a rich administrative model for managing user accounts.
Triple DES and AES 192/256 Implementation Notes
 Triple DES and AES 192/256 Implementation Notes Sample Password-to-Key and KeyChange results of Triple DES and AES 192/256 implementation For InterWorking Labs customers who require detailed information
Triple DES and AES 192/256 Implementation Notes Sample Password-to-Key and KeyChange results of Triple DES and AES 192/256 implementation For InterWorking Labs customers who require detailed information
Certification Authority
 Certification Authority Overview Identifying CA Hierarchy Design Requirements Common CA Hierarchy Designs Documenting Legal Requirements Analyzing Design Requirements Designing a Hierarchy Structure Identifying
Certification Authority Overview Identifying CA Hierarchy Design Requirements Common CA Hierarchy Designs Documenting Legal Requirements Analyzing Design Requirements Designing a Hierarchy Structure Identifying
BACKUP APP V7 MICROSOFT EXCHANGE DATABASE BACKUP AND RESTORE GUIDE
 V7 MICROSOFT EXCHANGE DATABASE BACKUP AND RESTORE GUIDE Revision History Date Descriptions Type of modification 15 July 2016 First Draft New 3 February 2017 Added instructions and screen shots for Encryption
V7 MICROSOFT EXCHANGE DATABASE BACKUP AND RESTORE GUIDE Revision History Date Descriptions Type of modification 15 July 2016 First Draft New 3 February 2017 Added instructions and screen shots for Encryption
API Gateway Version September Validation Authority Interoperability Guide
 API Gateway Version 7.5.3 17 September 2018 Validation Authority Interoperability Guide Copyright 2018 Axway All rights reserved. This documentation describes the following Axway software: Axway API Gateway
API Gateway Version 7.5.3 17 September 2018 Validation Authority Interoperability Guide Copyright 2018 Axway All rights reserved. This documentation describes the following Axway software: Axway API Gateway
ECB E-TENDERING SUBMISSION OF A RESPONSE IN A PROCUREMENT PROCEDURE ( RFX )
 DG - Finance ECB-UNRESTRICTED 8 November 2016 ECB E-TENDERING SUBMISSION OF A RESPONSE IN A PROCUREMENT PROCEDURE ( RFX ) To submit a response in a procurement procedure (e.g. your (revised) Tender/Proposal,
DG - Finance ECB-UNRESTRICTED 8 November 2016 ECB E-TENDERING SUBMISSION OF A RESPONSE IN A PROCUREMENT PROCEDURE ( RFX ) To submit a response in a procurement procedure (e.g. your (revised) Tender/Proposal,
First Data DCC Test Card Set. Version 1.30
 First Data DCC Test Card Set.30 April, 2018 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available from industry
First Data DCC Test Card Set.30 April, 2018 Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information available from industry
The most common type of certificates are public key certificates. Such server has a certificate is a common shorthand for: there exists a certificate
 1 2 The most common type of certificates are public key certificates. Such server has a certificate is a common shorthand for: there exists a certificate signed by some certification authority, which certifies
1 2 The most common type of certificates are public key certificates. Such server has a certificate is a common shorthand for: there exists a certificate signed by some certification authority, which certifies
Regions Quick Deposit Administrator User Guide
 Regions Quick Deposit Administrator User Guide Revised 11.30.17 DRIVER INSTALLATION Do not connect the scanner before installing the correct scanner drive to the PC to be used with your Quick Deposit service.
Regions Quick Deposit Administrator User Guide Revised 11.30.17 DRIVER INSTALLATION Do not connect the scanner before installing the correct scanner drive to the PC to be used with your Quick Deposit service.
Setting up IMAP Mail in Outlook
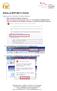 Setting up IMAP Mail in Outlook Setting up the Certificate in Internet Explorer 1. Open up Internet Explorer. Browse to https://intranet.yourschooldomain.school.nz. You will get a Certificate Error. Click
Setting up IMAP Mail in Outlook Setting up the Certificate in Internet Explorer 1. Open up Internet Explorer. Browse to https://intranet.yourschooldomain.school.nz. You will get a Certificate Error. Click
How to Configure SSL Interception in the Firewall
 Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted traffic to allow Application Control features (such as the Virus Scanner, ATD, URL Filter, Safe Search,
Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted traffic to allow Application Control features (such as the Virus Scanner, ATD, URL Filter, Safe Search,
Cryptography SSL/TLS. Network Security Workshop. 3-5 October 2017 Port Moresby, Papua New Guinea
 Cryptography SSL/TLS Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea 1 History Secure Sockets Layer was developed by Netscape in 1994 as a protocol which permitted persistent
Cryptography SSL/TLS Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea 1 History Secure Sockets Layer was developed by Netscape in 1994 as a protocol which permitted persistent
Product Support Notice
 PSN # PSN005110u Product Support Notice 2017 Avaya Inc. All Rights Reserved. Original publication date: 8 Dec. 2017. This is Issue #03, published date: 22 Dec. 2017 Severity/risk level High Urgency Immediately
PSN # PSN005110u Product Support Notice 2017 Avaya Inc. All Rights Reserved. Original publication date: 8 Dec. 2017. This is Issue #03, published date: 22 Dec. 2017 Severity/risk level High Urgency Immediately
FIS and DCS User Guide - Supplement
 FIS and DCS User Guide - Supplement Adobe Acrobat and Adobe Reader Configuration How to Digitally Sign PDF Documents with Adobe Acrobat and Adobe Reader Version 1.0 Exostar LLC September 2016 1 Table of
FIS and DCS User Guide - Supplement Adobe Acrobat and Adobe Reader Configuration How to Digitally Sign PDF Documents with Adobe Acrobat and Adobe Reader Version 1.0 Exostar LLC September 2016 1 Table of
Public Key Infrastructure
 Public Key Infrastructure Ed Crowley Summer 11 1 Topics Public Key Infrastructure Defined PKI Overview PKI Architecture Trust Models Components X.509 Certificates X.500 LDAP 2 Public Key Infrastructure
Public Key Infrastructure Ed Crowley Summer 11 1 Topics Public Key Infrastructure Defined PKI Overview PKI Architecture Trust Models Components X.509 Certificates X.500 LDAP 2 Public Key Infrastructure
Step-by-step installation guide for monitoring untrusted servers using Operations Manager
 Step-by-step installation guide for monitoring untrusted servers using Operations Manager Most of the time through Operations Manager, you may require to monitor servers and clients that are located outside
Step-by-step installation guide for monitoring untrusted servers using Operations Manager Most of the time through Operations Manager, you may require to monitor servers and clients that are located outside
Reference Card: How to connect Windows 7 to UniWireless
 Reference Card: How to connect Windows 7 to UniWireless Important Information Windows 7 is not supported by ITS. These instructions provided are only a guide and do not provide any troubleshooting assistance.
Reference Card: How to connect Windows 7 to UniWireless Important Information Windows 7 is not supported by ITS. These instructions provided are only a guide and do not provide any troubleshooting assistance.
Report of Independent Accountants
 Report of Independent Accountants S.C. certsign S.A. B-dul Timisoara nr. 5A Sector 6, Bucharest, ZIP 061301, Romania We have examined the accompanying assertion 1 made by the management of S.C. certsign
Report of Independent Accountants S.C. certsign S.A. B-dul Timisoara nr. 5A Sector 6, Bucharest, ZIP 061301, Romania We have examined the accompanying assertion 1 made by the management of S.C. certsign
How to Install Enterprise Certificate Authority on a Windows 2008 Server
 AD CS is the backbone of Microsoft s Public Key Infrastructure (PKI) implementation. It will allow you to issue certificates for SSL/TTL user on websites or digitally sign your email. Now let s take a
AD CS is the backbone of Microsoft s Public Key Infrastructure (PKI) implementation. It will allow you to issue certificates for SSL/TTL user on websites or digitally sign your email. Now let s take a
Revit s Project Base Point
 Update your NLM! Revit s Project Base Point Autodesk Network License Manager (AdLM) FLEXnet Installation and Configuration Guide Single Server License Model Outline of installation and configuration actions:
Update your NLM! Revit s Project Base Point Autodesk Network License Manager (AdLM) FLEXnet Installation and Configuration Guide Single Server License Model Outline of installation and configuration actions:
OneDrive for Business: Basics
 OneDrive for Business: Basics DRAFT 2015. All Rights Reserved. California State University, Bakersfield September 21, 2015 REVISION CONTROL Document Title: Author: File Reference: O365 OneDrive for Business
OneDrive for Business: Basics DRAFT 2015. All Rights Reserved. California State University, Bakersfield September 21, 2015 REVISION CONTROL Document Title: Author: File Reference: O365 OneDrive for Business
L8: Public Key Infrastructure. Hui Chen, Ph.D. Dept. of Engineering & Computer Science Virginia State University Petersburg, VA 23806
 L8: Public Key Infrastructure Hui Chen, Ph.D. Dept. of Engineering & Computer Science Virginia State University Petersburg, VA 23806 9/21/2015 CSCI 451 - Fall 2015 1 Acknowledgement Many slides are from
L8: Public Key Infrastructure Hui Chen, Ph.D. Dept. of Engineering & Computer Science Virginia State University Petersburg, VA 23806 9/21/2015 CSCI 451 - Fall 2015 1 Acknowledgement Many slides are from
SWITCHpki Service Launch The SWITCHpki Team
 SWITCHpki Service Launch The SWITCHpki Team pki@switch.ch http://www.switch.ch/pki/ 2004 SWITCH Overview Introduction CA Structure Roles, Entities Service Options Example SwissSign Introduction Outlook:
SWITCHpki Service Launch The SWITCHpki Team pki@switch.ch http://www.switch.ch/pki/ 2004 SWITCH Overview Introduction CA Structure Roles, Entities Service Options Example SwissSign Introduction Outlook:
Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS)
 Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Audit Attestation for. Fabrica Nacional de Moneda y Timbre Real Casa. de la Moneda
 Space LOGO CAB Audit Attestation for Fabrica Nacional de Moneda y Timbre Real Casa de la Moneda Reference: AA2018041201 To whom it may concern, Essen, 12.04.2018 This is to confirm that TÜV Informationstechnik
Space LOGO CAB Audit Attestation for Fabrica Nacional de Moneda y Timbre Real Casa de la Moneda Reference: AA2018041201 To whom it may concern, Essen, 12.04.2018 This is to confirm that TÜV Informationstechnik
Automated Court Reporter Application. Digital Signatures
 Automated Court Reporter Application Digital Signatures Doc Version 1.5 December 1, 2010 Administrative Office of the U.S. Courts Revision History Date Version Description of Revision 2/10/2009 1.0 Initial
Automated Court Reporter Application Digital Signatures Doc Version 1.5 December 1, 2010 Administrative Office of the U.S. Courts Revision History Date Version Description of Revision 2/10/2009 1.0 Initial
Overview. SSL Cryptography Overview CHAPTER 1
 CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
Abila Nonprofit Online. Connection Guide
 Abila Nonprofit Online This is a publication of Abila, Inc. Version 1.x 2014 Abila, Inc. and its affiliated entities. All rights reserved. Abila, the Abila logos, and the Abila product and service names
Abila Nonprofit Online This is a publication of Abila, Inc. Version 1.x 2014 Abila, Inc. and its affiliated entities. All rights reserved. Abila, the Abila logos, and the Abila product and service names
DBK24. Isolated Digital Output Chassis. Overview
 DBK24 Isolated Digital Output Chassis Overview 1 Power Requirements 2 Hardware Setup 2 Card Connection 2 Card Configuration 3 DaqBook and DaqBoard Connection 4 DaqBoard/2000 Series Board Connection 5 DaqBook
DBK24 Isolated Digital Output Chassis Overview 1 Power Requirements 2 Hardware Setup 2 Card Connection 2 Card Configuration 3 DaqBook and DaqBoard Connection 4 DaqBoard/2000 Series Board Connection 5 DaqBook
Interac USA Interoperability EMV Test Card Set
 Interac USA Interoperability EMV Test Card Set.00 April, 2018 Powered by Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information
Interac USA Interoperability EMV Test Card Set.00 April, 2018 Powered by Disclaimer Information provided in this document describes capabilities available at the time of developing this document and information
The appendix to the certificate is part of the certificate and consists of 3 pages.
 The certification body of TÜV Informationstechnik GmbH hereby awards this certificate to the company FNMT Real Casa de la Moneda C/Jorge Juan, 106 28009 Madrid, Spain to confirm that its trust service
The certification body of TÜV Informationstechnik GmbH hereby awards this certificate to the company FNMT Real Casa de la Moneda C/Jorge Juan, 106 28009 Madrid, Spain to confirm that its trust service
