CCNA Security v2.0 Chapter 9 Exam Answers
|
|
|
- Hollie Pierce
- 6 years ago
- Views:
Transcription
1 CCNA Security v2.0 Chapter 9 Exam Answers 1. Refer t the exhibit. An administratr creates three znes (A, B, and C) in an ASA that filters traffic. Traffic riginating frm Zne A ging t Zne C is denied, and traffic riginating frm Zne B ging t Zne C is denied. What is a pssible scenari fr Znes A, B, and C? CCNA Security Chapter 9 Exam Answer v2 001 A DMZ, B Inside, C Outside A Inside, B DMZ, C Outside A Outside, B Inside, C DMZ A DMZ, B Outside, C Inside 2. What is ne f the drawbacks t using transparent mde peratin n an ASA device? n supprt fr IP addressing n supprt fr management n supprt fr using an ASA as a Layer 2 switch n supprt fr QS 3. What is a characteristic f ASA security levels? An ACL needs t be cnfigured t explicitly permit traffic frm an interface with a lwer security level t an interface with a higher security level. CCNA 5 Page 1
2 Each peratinal interface must have a name and be assigned a security level frm 0 t 200. The lwer the security level n an interface, the mre trusted the interface. Inbund traffic is identified as the traffic mving frm an interface with a higher security level t an interface with a lwer security level. 4. Refer t the exhibit. Tw types f VLAN interfaces were cnfigured n an ASA 5505 with a Base license. The administratr wants t cnfigure a third VLAN interface with limited functinality. Which actin shuld be taken by the administratr t cnfigure the third interface? CCNA Security Chapter 9 Exam Answer v2 002 Because the ASA 5505 des nt supprt the cnfiguratin f a third interface, the administratr cannt cnfigure the third VLAN. The administratr must enter the n frward interface vlan cmmand befre the nameif cmmand n the third interface. The administratr cnfigures the third VLAN interface the same way the ther tw were cnfigured, because the Base license supprts the prpsed actin. The administratr needs t acquire the Security Plus license, because the Base license des nt supprt the prpsed actin. 5. What cmmand defines a DHCP pl that uses the maximum number f DHCP client addresses available n an ASA 5505 that is using the Base license? CCNA 5 Page 2
3 CCNAS-ASA(cnfig)# dhcpd address inside CCNAS-ASA(cnfig)# dhcpd address inside CCNAS-ASA(cnfig)# dhcpd address inside CCNAS-ASA(cnfig)# dhcpd address inside 6. Which tw statements are true abut ASA standard ACLs? (Chse tw.) They are the mst cmmn type f ACL. They are applied t interfaces t cntrl traffic. They are typically nly used fr OSPF rutes. They specify bth the surce and destinatin MAC address. They identify nly the destinatin IP address. 7. Refer t the exhibit. A netwrk administratr is cnfiguring the security level fr the ASA. What is a best practice fr assigning the security level n the three interfaces? CCNA Security Chapter 9 Exam Answer v2 003 Outside 40, Inside 100, DMZ 0 Outside 0, Inside 35, DMZ 90 Outside 100, Inside 10, DMZ 40 Outside 0, Inside 100, DMZ 50 CCNA 5 Page 3
4 8. Refer t the exhibit. A netwrk administratr is cnfiguring the security level fr the ASA. Which statement describes the default result if the administratr tries t assign the Inside interface with the same security level as the DMZ interface? CCNA Security Chapter 9 Exam Answer v2 004 The ASA allws inbund traffic initiated n the Internet t the DMZ, but nt t the Inside interface. The ASA cnsle will display an errr message. The ASA will nt allw traffic in either directin between the Inside interface and the DMZ. The ASA allws traffic frm the Inside t the DMZ, but blcks traffic initiated n the DMZ t the Inside interface. 9. What is a difference between ASA IPv4 ACLs and IOS IPv4 ACLs? ASA ACLs are always named, whereas IOS ACLs are always numbered. Multiple ASA ACLs can be applied n an interface in the ingress directin, whereas nly ne IOS ACL can be applied. ASA ACLs use the subnet mask in defining a netwrk, whereas IOS ACLs use the wildcard mask. ASA ACLs d nt have an implicit deny any at the end, whereas IOS ACLs d. ASA ACLs use frward and drp ACEs, whereas IOS ACLs use permit and deny ACEs. 10. What is the purpse f the webtype ACLs in an ASA? CCNA 5 Page 4
5 t inspect utbund traffic headed twards certain web sites t restrict traffic that is destined t an ASDM t mnitr return traffic that is in respnse t web server requests that are initiated frm the inside interface t filter traffic fr clientless SSL VPN users 11. Refer t the exhibit. A netwrk administratr has cnfigured NAT n an ASA device. What type f NAT is used? CCNA Security Chapter 9 Exam Answer v2 005 inside NAT static NAT bidirectinal NAT utside NAT 12. Refer t the exhibit. A netwrk administratr is cnfiguring an bject grup n an ASA device. Which cnfiguratin keywrd shuld be used after the bject grup name SERVICE1? CCNA Security Chapter 9 Exam Answer v2 006 icmp ip udp tcp 13. When dynamic NAT n an ASA is being cnfigured, what tw parameters must be specified by netwrk bjects? (Chse tw.) a range f private addresses that will be translated the interface security level CCNA 5 Page 5
6 the pl f public glbal addresses the inside NAT interface the utside NAT interface 14. What functin is perfrmed by the class maps cnfiguratin bject in the Cisc mdular plicy framewrk? identifying interesting traffic applying a plicy t an interface applying a plicy t interesting traffic restricting traffic thrugh an interface 15. Refer t the exhibit. Based n the security levels f the interfaces n ASA1, what traffic will be allwed n the interfaces? CCNA Security Chapter 9 Exam Answer v2 007 Traffic frm the Internet and DMZ can access the LAN. Traffic frm the Internet and LAN can access the DMZ. Traffic frm the Internet can access bth the DMZ and the LAN. Traffic frm the LAN and DMZ can access the Internet. 16. What are three characteristics f the ASA ruted mde? (Chse three.) This mde is referred t as a bump in the wire. In this mde, the ASA is invisible t an attacker. The interfaces f the ASA separate Layer 3 netwrks and require different IP addresses in different subnets. CCNA 5 Page 6
7 It is the traditinal firewall deplyment mde. This mde des nt supprt VPNs, QS, r DHCP Relay. NAT can be implemented between cnnected netwrks. 17. Refer t the exhibit. An administratr has cnfigured an ASA 5505 as indicated but is still unable t ping the inside interface frm an inside hst. What is the cause f this prblem? CCNA Security Chapter 9 Exam Answer v2 008 The n shutdwn cmmand shuld be entered n interface Ethernet 0/1. VLAN 1 shuld be the utside interface and VLAN 2 shuld be the inside interface. VLAN 1 shuld be assigned t interface Ethernet 0/0 and VLAN 2 t Ethernet 0/1. The security level f the inside interface shuld be 0 and the utside interface shuld be 100. An IP address shuld be cnfigured n the Ethernet 0/0 and 0/1 interfaces. 18. Refer t the exhibit. Accrding t the cmmand utput, which three statements are true abut the DHCP ptins entered n the ASA 5505? (Chse three.) CCNA Security Chapter 9 Exam Answer v2 009 CCNA 5 Page 7
8 The dhcpd address [start-f-pl]-[end-f-pl] inside cmmand was issued t enable the DHCP client. The dhcpd aut-cnfig utside cmmand was issued t enable the DHCP server. The dhcpd address [start-f-pl]-[end-f-pl] inside cmmand was issued t enable the DHCP server. The dhcpd aut-cnfig utside cmmand was issued t enable the DHCP client. The dhcpd enable inside cmmand was issued t enable the DHCP client. The dhcpd enable inside cmmand was issued t enable the DHCP server. 19. Refer t the exhibit. What will be displayed in the utput f the shw runningcnfig bjectcmmand after the exhibited cnfiguratin cmmands are entered n an ASA 5505? CCNA Security Chapter 9 Exam Answer v2 010 hst hst , hst , and range hst and range hst and hst range hst What must be cnfigured n a Cisc ASA device t supprt lcal authenticatin? AAA the IP address f the RADIUS r TACACS+ server encrypted passwrds SSHv2 RSA keys 21. Which statement describes a difference between the Cisc ASA IOS CLI feature and the ruter IOS CLI feature? CCNA 5 Page 8
9 ASA uses the? cmmand whereas a ruter uses the help cmmand t receive help n a brief descriptin and the syntax f a cmmand. T use a shw cmmand in a general cnfiguratin mde, ASA can use the cmmand directly whereas a ruter will need t enter the d cmmand befre issuing the shw cmmand. T cmplete a partially typed cmmand, ASA uses the Ctrl+Tab key cmbinatin whereas a ruter uses the Tab key. T indicate the CLI EXEC mde, ASA uses the % symbl whereas a ruter uses the # symbl. 22. What are tw factry default cnfiguratins n an ASA 5505? (Chse tw.) VLAN 2 is cnfigured with the name inside. The internal web server is disabled. DHCP service is enabled fr internal hsts t btain an IP address and a default gateway frm the upstream device. PAT is cnfigured t allw internal hsts t access remte netwrks thrugh an Ethernet interface. VLAN 1 is assigned a security level f Which type f NAT wuld be used n an ASA where /24 inside addresses are t be translated nly if traffic frm these addresses is destined fr the /24 netwrk? plicy NAT dynamic NAT static NAT dynamic PAT 24. Which statement describes a feature f AAA in an ASA device? Accunting can be used alne. Authrizatin is enabled by default. If authrizatin is disabled, all authenticated users will have a very limited access t the cmmands. Bth authrizatin and accunting require a user t be authenticated first. 25. A netwrk administratr is wrking n the implementatin f the Cisc Mdular Plicy Framewrk n an ASA device. The administratr issues a clear serviceplicy cmmand. What is the effect after this cmmand is entered? All class map cnfiguratins are remved. All service plicy statistics data are remved. All service plicies are remved. CCNA 5 Page 9
10 All plicy map cnfiguratins are remved. 26. What is needed t allw specific traffic that is surced n the utside netwrk f an ASA firewall t reach an internal netwrk? ACL NAT dynamic ruting prtcls utside security zne level 0 CCNA 5 Page 10
CCNA Security v2.0 Chapter 10 Exam Answers
 CCNA Security v2.0 Chapter 10 Exam Answers 1. Which statement describes the functin prvided t a netwrk administratrwh uses the Cisc Adaptive Security Device Manager (ASDM) GUI that runs as a Java Web Start
CCNA Security v2.0 Chapter 10 Exam Answers 1. Which statement describes the functin prvided t a netwrk administratrwh uses the Cisc Adaptive Security Device Manager (ASDM) GUI that runs as a Java Web Start
Packet Tracer - Skills Integration Challenge Topology
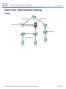 Packet Tracer - Skills Integratin Challenge Tplgy 2015 Cisc and/r its affiliates. All rights reserved. This dcument is Cisc Public. Page 1 f 6 Packet Tracer - Skills Integratin Challenge Addressing Table
Packet Tracer - Skills Integratin Challenge Tplgy 2015 Cisc and/r its affiliates. All rights reserved. This dcument is Cisc Public. Page 1 f 6 Packet Tracer - Skills Integratin Challenge Addressing Table
CCNA Security v2.0 Chapter 3 Exam Answers
 CCNA Security v2.0 Chapter 3 Exam Answers 1. Because f implemented security cntrls, a user can nly access a server with FTP. Which AAA cmpnent accmplishes this? accunting accessibility auditing authrizatin
CCNA Security v2.0 Chapter 3 Exam Answers 1. Because f implemented security cntrls, a user can nly access a server with FTP. Which AAA cmpnent accmplishes this? accunting accessibility auditing authrizatin
2. What is the most cost-effective method of solving interface congestion that is caused by a high level of traffic between two switches?
 CCNA 3 Chapter 3 v5.0 Exam Answers 2015 (100%) 1. Refer t the exhibit. Which switching technlgy wuld allw each access layer switch link t be aggregated t prvide mre bandwidth between each Layer 2 switch
CCNA 3 Chapter 3 v5.0 Exam Answers 2015 (100%) 1. Refer t the exhibit. Which switching technlgy wuld allw each access layer switch link t be aggregated t prvide mre bandwidth between each Layer 2 switch
CCNA Security v2.0 Chapter 2 Exam Answers
 CCNA Security v2.0 Chapter 2 Exam Answers 1. An administratr defined a lcal user accunt with a secret passwrd n ruter R1 fr use with SSH. Which three additinal steps are required t cnfigure R1 t accept
CCNA Security v2.0 Chapter 2 Exam Answers 1. An administratr defined a lcal user accunt with a secret passwrd n ruter R1 fr use with SSH. Which three additinal steps are required t cnfigure R1 t accept
2. When logging is used, which severity level indicates that a device is unusable?
 CCNA 4 Chapter 8 v5.0 Exam Answers 2015 (100%) 1. What are the mst cmmn syslg messages? thse that ccur when a packet matches a parameter cnditin in an access cntrl list link up and link dwn messages utput
CCNA 4 Chapter 8 v5.0 Exam Answers 2015 (100%) 1. What are the mst cmmn syslg messages? thse that ccur when a packet matches a parameter cnditin in an access cntrl list link up and link dwn messages utput
CCNA 3 Chapter 8 v5.0 Exam Answers 2015 (100%) CCNA 5 Page 1
 CCNA 3 Chapter 8 v5.0 Exam Answers 2015 (100%) 1. Refer t the exhibit. All netwrks are active in the same EIGRP ruting dmain. When the aut-summary cmmand is issued n R3, which tw summary netwrks will be
CCNA 3 Chapter 8 v5.0 Exam Answers 2015 (100%) 1. Refer t the exhibit. All netwrks are active in the same EIGRP ruting dmain. When the aut-summary cmmand is issued n R3, which tw summary netwrks will be
1. What is a characteristic of Frame Relay that provides more flexibility than a dedicated line?
 CCNA 4 Chapter 4 v5.0 Exam Answers 2015 (100%) 1. What is a characteristic f Frame Relay that prvides mre flexibility than a dedicated line? Dedicated physical circuits are installed between each site.
CCNA 4 Chapter 4 v5.0 Exam Answers 2015 (100%) 1. What is a characteristic f Frame Relay that prvides mre flexibility than a dedicated line? Dedicated physical circuits are installed between each site.
2. When an EIGRP-enabled router uses a password to accept routes from other EIGRP-enabled routers, which mechanism is used?
 CCNA 3 Chapter 7 v5.0 Exam Answers 2015 (100%) 1. Which prtcl is used by EIGRP t send hell packets? TCP UDP RTP IP 2. When an EIGRP-enabled ruter uses a passwrd t accept rutes frm ther EIGRP-enabled ruters,
CCNA 3 Chapter 7 v5.0 Exam Answers 2015 (100%) 1. Which prtcl is used by EIGRP t send hell packets? TCP UDP RTP IP 2. When an EIGRP-enabled ruter uses a passwrd t accept rutes frm ther EIGRP-enabled ruters,
CCNA 1 Chapter v5.1 Answers 100%
 CCNA 1 Chapter 6 2016 v5.1 Answers 100% 1. Which characteristic f the netwrk layer in the OSI mdel allws carrying packets fr multiple types f cmmunicatins amng many hsts? the de-encapsulatin f headers
CCNA 1 Chapter 6 2016 v5.1 Answers 100% 1. Which characteristic f the netwrk layer in the OSI mdel allws carrying packets fr multiple types f cmmunicatins amng many hsts? the de-encapsulatin f headers
CCNA 1 Chapter v5.1 Answers 100%
 CCNA 1 Chapter 11 2016 v5.1 Answers 100% 1. A newly hired netwrk technician is given the task f rdering new hardware fr a small business with a large grwth frecast. Which primary factr shuld the technician
CCNA 1 Chapter 11 2016 v5.1 Answers 100% 1. A newly hired netwrk technician is given the task f rdering new hardware fr a small business with a large grwth frecast. Which primary factr shuld the technician
CCNA 3 Chapter 2 v5.0 Exam Answers 2015 (100%)
 CCNA 3 Chapter 2 v5.0 Exam Answers 2015 (100%) 1. Which tw netwrk design features require Spanning Tree Prtcl (STP) t ensure crrect netwrk peratin? (Chse tw.) static default rutes implementing VLANs t
CCNA 3 Chapter 2 v5.0 Exam Answers 2015 (100%) 1. Which tw netwrk design features require Spanning Tree Prtcl (STP) t ensure crrect netwrk peratin? (Chse tw.) static default rutes implementing VLANs t
Packet Tracer - Configuring a Zone-Based Policy Firewall (ZPF)
 Packet Tracer - Cnfiguring a Zne-Based Plicy Firewall (ZPF) Tplgy Addressing Table R1 R2 R3 Device Interface IP Address Subnet Mask Default Gateway Switch Prt G0/1 192.168.1.1 255.255.255.0 N/A S1 F0/5
Packet Tracer - Cnfiguring a Zne-Based Plicy Firewall (ZPF) Tplgy Addressing Table R1 R2 R3 Device Interface IP Address Subnet Mask Default Gateway Switch Prt G0/1 192.168.1.1 255.255.255.0 N/A S1 F0/5
IT Essentials (ITE v6.0) Chapter 8 Exam Answers 100% 2016
 IT Essentials (ITE v6.0) Chapter 8 Exam Answers 100% 2016 1. A user ntices that the data transfer rate fr the gigabit NIC in the user cmputer is much slwer than expected. What is a pssible cause fr the
IT Essentials (ITE v6.0) Chapter 8 Exam Answers 100% 2016 1. A user ntices that the data transfer rate fr the gigabit NIC in the user cmputer is much slwer than expected. What is a pssible cause fr the
VMware AirWatch Certificate Authentication for Cisco IPSec VPN
 VMware AirWatch Certificate Authenticatin fr Cisc IPSec VPN Fr VMware AirWatch Have dcumentatin feedback? Submit a Dcumentatin Feedback supprt ticket using the Supprt Wizard n supprt.air-watch.cm. This
VMware AirWatch Certificate Authenticatin fr Cisc IPSec VPN Fr VMware AirWatch Have dcumentatin feedback? Submit a Dcumentatin Feedback supprt ticket using the Supprt Wizard n supprt.air-watch.cm. This
2. Which command can be used to view the cable type that is attached to a serial interface?
 CCNA 4 Chapter 3 v5.0 Exam Answers 2015 (100%) 1. At which layer f the OSI mdel des multiplexing take place? Layer 1 Layer 2 Layer 3 Layer 4 2. Which cmmand can be used t view the cable type that is attached
CCNA 4 Chapter 3 v5.0 Exam Answers 2015 (100%) 1. At which layer f the OSI mdel des multiplexing take place? Layer 1 Layer 2 Layer 3 Layer 4 2. Which cmmand can be used t view the cable type that is attached
SASAC v1.0 Implementing Core Cisco ASA Security Cisco Training
 SASAC v1.0 Implementing Cre Cisc ASA Security Cisc Training Curse Length: 5 Curse Delivery: Traditinal Classrm Online Live Curse Overview Cisc ASA Cre v1.0 is a new 5-day ILT class that cvers the Cisc
SASAC v1.0 Implementing Cre Cisc ASA Security Cisc Training Curse Length: 5 Curse Delivery: Traditinal Classrm Online Live Curse Overview Cisc ASA Cre v1.0 is a new 5-day ILT class that cvers the Cisc
CCNA 1 Chapter v5.1 Answers 100%
 CCNA 1 Chapter 5 2016 v5.1 Answers 100% 1. What happens t runt frames received by a Cisc Ethernet switch? The frame is drpped. The frame is returned t the riginating netwrk device. The frame is bradcast
CCNA 1 Chapter 5 2016 v5.1 Answers 100% 1. What happens t runt frames received by a Cisc Ethernet switch? The frame is drpped. The frame is returned t the riginating netwrk device. The frame is bradcast
Questions and Answers
 Questins and Answers 1. Actin = Redirect is applied in A. Chain=srcnat B. Chain=dstnat C. Chain=fward 2. Chse all valid hsts address range fr subnet 15.242.55.62/27 A. 15.242.55.31-15.242.55.62 B. 15.242.55.32-15.242.55.63
Questins and Answers 1. Actin = Redirect is applied in A. Chain=srcnat B. Chain=dstnat C. Chain=fward 2. Chse all valid hsts address range fr subnet 15.242.55.62/27 A. 15.242.55.31-15.242.55.62 B. 15.242.55.32-15.242.55.63
CCNA 1 v5.1 Practice Final Exam Answers %
 CCNA 1 v5.1 Practice Final Exam Answers 2016 100% 1. Which term refers t a netwrk that prvides secure access t the crprate ffices by suppliers, custmers and cllabratrs? Internet intranet extranet extendednet
CCNA 1 v5.1 Practice Final Exam Answers 2016 100% 1. Which term refers t a netwrk that prvides secure access t the crprate ffices by suppliers, custmers and cllabratrs? Internet intranet extranet extendednet
Apply power, the appliance may be powered by connecting:
 ACM5508-2- GS- I Quick Start Guide Thank yu fr purchasing the ACM5508-2-GS-I management gateway. This Quick Start walks yu thrugh installatin, cnfiguratin & lcal peratin. Mre details are available in the
ACM5508-2- GS- I Quick Start Guide Thank yu fr purchasing the ACM5508-2-GS-I management gateway. This Quick Start walks yu thrugh installatin, cnfiguratin & lcal peratin. Mre details are available in the
CCNA 1 Chapter v5.1 Answers 100%
 CCNA 1 Chapter 8 2016 v5.1 Answers 100% 1. What is a result f cnnecting tw r mre switches tgether? The number f bradcast dmains is increased. The size f the bradcast dmain is increased. The number f cllisin
CCNA 1 Chapter 8 2016 v5.1 Answers 100% 1. What is a result f cnnecting tw r mre switches tgether? The number f bradcast dmains is increased. The size f the bradcast dmain is increased. The number f cllisin
Dolby Conference Phone Support Frequently Asked Questions
 Dlby Cnference Phne Supprt Frequently Asked Questins Versin 1.0, 1 Intrductin This dcument prvides sme answers t frequently asked questins abut the Dlby Cnference Phne. Fr mre detailed infrmatin n any
Dlby Cnference Phne Supprt Frequently Asked Questins Versin 1.0, 1 Intrductin This dcument prvides sme answers t frequently asked questins abut the Dlby Cnference Phne. Fr mre detailed infrmatin n any
CCNA course contents:
 CCNA curse cntents: Prerequisites: The knwledge and skills that yu must have befre attending this curse are as fllws: Basic cmputer literacy Windws navigatin skills Basic Internet usage skills Fundamental
CCNA curse cntents: Prerequisites: The knwledge and skills that yu must have befre attending this curse are as fllws: Basic cmputer literacy Windws navigatin skills Basic Internet usage skills Fundamental
SafeDispatch SDR Gateway for MOTOROLA TETRA
 SafeDispatch SDR Gateway fr MOTOROLA TETRA SafeMbile ffers a wrld f wireless applicatins that help rganizatins better manage their mbile assets, fleet and persnnel. Fr mre infrmatin, see www.safembile.cm.
SafeDispatch SDR Gateway fr MOTOROLA TETRA SafeMbile ffers a wrld f wireless applicatins that help rganizatins better manage their mbile assets, fleet and persnnel. Fr mre infrmatin, see www.safembile.cm.
Troubleshooting of network problems is find and solve with the help of hardware and software is called troubleshooting tools.
 Q.1 What is Trubleshting Tls? List their types? Trubleshting f netwrk prblems is find and slve with the help f hardware and sftware is called trubleshting tls. Trubleshting Tls - Hardware Tls They are
Q.1 What is Trubleshting Tls? List their types? Trubleshting f netwrk prblems is find and slve with the help f hardware and sftware is called trubleshting tls. Trubleshting Tls - Hardware Tls They are
Operational Security. Speaking Frankly The Internet is not a very safe place. A sense of false security... Firewalls*
 Operatinal Security Firewalls and Intrusin Detectin CS242 Cmputer Netwrks Speaking Frankly The Internet is nt a very safe place Frm ur netwrk administratr s pint f view, the wrld divides int tw camps:
Operatinal Security Firewalls and Intrusin Detectin CS242 Cmputer Netwrks Speaking Frankly The Internet is nt a very safe place Frm ur netwrk administratr s pint f view, the wrld divides int tw camps:
CCNA 1 Chapter v5.1 Answers 100%
 CCNA 1 Chapter 9 2016 v5.1 Answers 100% 1. Which tw characteristics are assciated with UDP sessins? (Chse tw.) Destinatin devices receive traffic with minimal delay. Transmitted data segments are tracked.
CCNA 1 Chapter 9 2016 v5.1 Answers 100% 1. Which tw characteristics are assciated with UDP sessins? (Chse tw.) Destinatin devices receive traffic with minimal delay. Transmitted data segments are tracked.
Max 8/16 and T1/E1 Gateway, Version FAQs
 Frequently Asked Questins Max 8/16 and T1/E1 Gateway, Versin 1.5.10 FAQs The FAQs have been categrized int the fllwing tpics: Calling Calling Cmpatibility Cnfiguratin Faxing Functinality Glssary Q. When
Frequently Asked Questins Max 8/16 and T1/E1 Gateway, Versin 1.5.10 FAQs The FAQs have been categrized int the fllwing tpics: Calling Calling Cmpatibility Cnfiguratin Faxing Functinality Glssary Q. When
CounterSnipe Software Installation Guide Software Version 10.x.x. Initial Set-up- Note: An internet connection is required for installation.
 CunterSnipe Sftware Installatin Guide Sftware Versin 10.x.x CunterSnipe sftware installs n any system cmpatible with Ubuntu 14.04 LTS server which is supprted until 2019 Initial Set-up- Nte: An internet
CunterSnipe Sftware Installatin Guide Sftware Versin 10.x.x CunterSnipe sftware installs n any system cmpatible with Ubuntu 14.04 LTS server which is supprted until 2019 Initial Set-up- Nte: An internet
PT Activity 2.6.1: Packet Tracer Skills Integration Challenge
 PT Activity 2.6.1: Packet Tracer Skills Integratin Challenge Tplgy Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway CENTRAL S0/0/0 10.1.1.2 255.255.255.252 S0/0/1 209.165.200.226
PT Activity 2.6.1: Packet Tracer Skills Integratin Challenge Tplgy Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway CENTRAL S0/0/0 10.1.1.2 255.255.255.252 S0/0/1 209.165.200.226
These tasks can now be performed by a special program called FTP clients.
 FTP Cmmander FAQ: Intrductin FTP (File Transfer Prtcl) was first used in Unix systems a lng time ag t cpy and mve shared files. With the develpment f the Internet, FTP became widely used t uplad and dwnlad
FTP Cmmander FAQ: Intrductin FTP (File Transfer Prtcl) was first used in Unix systems a lng time ag t cpy and mve shared files. With the develpment f the Internet, FTP became widely used t uplad and dwnlad
Launching Xacta 360 Marketplace AMI Guide June 2017
 Launching Xacta 360 Marketplace AMI Guide June 2017 Tels Crpratin 2017. All rights reserved. U.S. patents Ns. 6,901,346; 6,980,927; 6,983,221; 6,993,448; and 7,380,270. Xacta is a registered trademark
Launching Xacta 360 Marketplace AMI Guide June 2017 Tels Crpratin 2017. All rights reserved. U.S. patents Ns. 6,901,346; 6,980,927; 6,983,221; 6,993,448; and 7,380,270. Xacta is a registered trademark
NAT Instance Configuration
 NAT Instance Cnfiguratin Enabling Internet Access fr Private Subnets O R A C L E W H I T E P A P E R J A N U A R Y 2 0 1 8 Table f Cntents Intrductin 3 Assumptins 4 Basic NAT Cnfiguratin 4 Architecture
NAT Instance Cnfiguratin Enabling Internet Access fr Private Subnets O R A C L E W H I T E P A P E R J A N U A R Y 2 0 1 8 Table f Cntents Intrductin 3 Assumptins 4 Basic NAT Cnfiguratin 4 Architecture
DIVAR IP 3000 Field Installation Guide
 CCTV IP Netwrk Vide Technical Brief DIVAR IP 3000 Field Installatin Guide 1 DIVAR IP 3000 Field Installatin Guide Overview The purpse f this guide is t prvide the step-by-step prcess f installing a DIVAR
CCTV IP Netwrk Vide Technical Brief DIVAR IP 3000 Field Installatin Guide 1 DIVAR IP 3000 Field Installatin Guide Overview The purpse f this guide is t prvide the step-by-step prcess f installing a DIVAR
CCNA 3 Practice Final v5.0 Exam Answers 2015 (100%)
 CCNA 3 Practice Final v5.0 Exam Answers 2015 (100%) 1. Which technlgical factr determines the impact f a failure dmain? the number f layers f the hierarchical netwrk the number f users n the access layer
CCNA 3 Practice Final v5.0 Exam Answers 2015 (100%) 1. Which technlgical factr determines the impact f a failure dmain? the number f layers f the hierarchical netwrk the number f users n the access layer
CNS-222-1I: NetScaler for Apps and Desktops
 CNS-222-1I: NetScaler fr Apps and Desktps Overview Designed fr students with little r n previus NetScaler, NetScaler Gateway r Unified Gateway experience, this curse is best suited fr individuals wh will
CNS-222-1I: NetScaler fr Apps and Desktps Overview Designed fr students with little r n previus NetScaler, NetScaler Gateway r Unified Gateway experience, this curse is best suited fr individuals wh will
Cisco Nexus Data Broker Embedded: Implementation Quick- Start Guide
 Cisc Nexus Data Brker Embedded: Implementatin Quick- Start Guide Table f Cntents What Yu Will Learn... 2 Cisc Nexus Data Brker Slutin Overview... 2 Cisc Nexus Data Brker Slutin Lab Setup Tplgy... 3 Enabling
Cisc Nexus Data Brker Embedded: Implementatin Quick- Start Guide Table f Cntents What Yu Will Learn... 2 Cisc Nexus Data Brker Slutin Overview... 2 Cisc Nexus Data Brker Slutin Lab Setup Tplgy... 3 Enabling
1.3 Describe the impact of infrastructure components in an enterprise network
 CCNA Curse Cntent Duratin: 40 Hrs 1. Netwrk Fundamentals 1.1 Cmpare and cntrast OSI and TCP/IP mdels 1.2 Cmpare and cntrast TCP and UDP prtcls 1.3 Describe the impact f infrastructure cmpnents in an enterprise
CCNA Curse Cntent Duratin: 40 Hrs 1. Netwrk Fundamentals 1.1 Cmpare and cntrast OSI and TCP/IP mdels 1.2 Cmpare and cntrast TCP and UDP prtcls 1.3 Describe the impact f infrastructure cmpnents in an enterprise
Secure Mobile Access to the Local ICS Network. Jan Vossaert Veilige industriële netwerken 29/09/2016
 Secure Mbile Access t the Lcal ICS Netwrk Jan Vssaert Veilige industriële netwerken 29/09/2016 Intrductin ffice netwrk prductin cell ruter 192.168.2.0/24 Internet ICS DMZ servers 192.168.1.0/24 prductin
Secure Mbile Access t the Lcal ICS Netwrk Jan Vssaert Veilige industriële netwerken 29/09/2016 Intrductin ffice netwrk prductin cell ruter 192.168.2.0/24 Internet ICS DMZ servers 192.168.1.0/24 prductin
Telkom VPN-Lite router setup User Manual Billion 810VGTX
 Telkm VPN-Lite ruter setup User Manual Billin 810VGTX Cntents Intrductin... 3 Befre yu start... 4 VPN-Lite Setup Using Windws Utility... 5 VPN-Lite Setup using yur web brwser... 7 VPN-Lite Manual Setup
Telkm VPN-Lite ruter setup User Manual Billin 810VGTX Cntents Intrductin... 3 Befre yu start... 4 VPN-Lite Setup Using Windws Utility... 5 VPN-Lite Setup using yur web brwser... 7 VPN-Lite Manual Setup
IT Essentials (ITE v6.0) Chapter 7 Exam Answers 100% 2016
 IT Essentials (ITE v6.0) Chapter 7 Exam Answers 100% 2016 1. Hw many devices can a Bluetth device cnnect t simultaneusly? 127 7 10 24 5 2. A device has an IPv6 address f 2001:0DB8:75a3:0214:0607:1234:aa10:ba01
IT Essentials (ITE v6.0) Chapter 7 Exam Answers 100% 2016 1. Hw many devices can a Bluetth device cnnect t simultaneusly? 127 7 10 24 5 2. A device has an IPv6 address f 2001:0DB8:75a3:0214:0607:1234:aa10:ba01
Telkom VPN-Lite router setup User Manual Billion 800VGT
 Telkm VPN-Lite ruter setup User Manual Billin 800VGT Cntents 1. Intrductin... 3 2. Befre yu start... 4 3. VPN-Lite Setup Using Windws Utility... 5 4. VPN-Lite Setup using yur web brwser... 7 5. VPN-Lite
Telkm VPN-Lite ruter setup User Manual Billin 800VGT Cntents 1. Intrductin... 3 2. Befre yu start... 4 3. VPN-Lite Setup Using Windws Utility... 5 4. VPN-Lite Setup using yur web brwser... 7 5. VPN-Lite
CCNA - Routing and Switching
 CCNA - Ruting and Switching The CCNA (Cisc Certified Netwrk Assciate) is meant fr engineers lking t get fthld in netwrking. This frms the base f the Cisc training pyramid and ffers different specializatins
CCNA - Ruting and Switching The CCNA (Cisc Certified Netwrk Assciate) is meant fr engineers lking t get fthld in netwrking. This frms the base f the Cisc training pyramid and ffers different specializatins
Exercise 1: Deploying Windows Server 2012
 Highlight Nte Lab Answer Key: Mdule 1: Deplying and Managing Windws Server 2012 Lab: Deplying and Managing Windws Server 201 2 Exercise 1: Deplying Windws Server 2012 10. In the Windws Setup Wizard, n
Highlight Nte Lab Answer Key: Mdule 1: Deplying and Managing Windws Server 2012 Lab: Deplying and Managing Windws Server 201 2 Exercise 1: Deplying Windws Server 2012 10. In the Windws Setup Wizard, n
Dear Milestone Customer,
 Dear Milestne Custmer, With the purchase f Milestne Xprtect Transact yu have chsen a very flexible ptin t yur Milestne Xprtect Business slutin. Milestne Xprtect Transact enables yu t stre a serial data
Dear Milestne Custmer, With the purchase f Milestne Xprtect Transact yu have chsen a very flexible ptin t yur Milestne Xprtect Business slutin. Milestne Xprtect Transact enables yu t stre a serial data
CCNA Voice ICOMM: (4 Day Course)
 CCNA Vice 640-461 ICOMM: (4 Day Curse) The CCNA Vice certificatin cnfirms that yu have the required skill set fr specialised jb rles in vice technlgies such as vice technlgies administratr, vice engineer,
CCNA Vice 640-461 ICOMM: (4 Day Curse) The CCNA Vice certificatin cnfirms that yu have the required skill set fr specialised jb rles in vice technlgies such as vice technlgies administratr, vice engineer,
Release Notes System Software
 Release Ntes System Sftware 10.2.5 Cntent Cntent... 1 1 Release 10.2.5.100... 2 1.1 New functins... 2 1.2 Changes... 3 1.3 Errr crrectins... 3 1.4 Knwn Restrictins... 5 Release Ntes 10.2.5 V. 1.0 20181220
Release Ntes System Sftware 10.2.5 Cntent Cntent... 1 1 Release 10.2.5.100... 2 1.1 New functins... 2 1.2 Changes... 3 1.3 Errr crrectins... 3 1.4 Knwn Restrictins... 5 Release Ntes 10.2.5 V. 1.0 20181220
EVALUATION GUIDE - OCTOBER 2018 VMWARE CLOUD ON AWS. Evaluation Guide
 EVALUATION GUIDE - OCTOBER 2018 VMWARE CLOUD ON AWS Evaluatin Guide Table f Cntents Intrductin 4 Intended Audience... 4 Assumptins... 4 User Interface Walkthrugh 4 Clud Cnsle Walkthrugh... 4 VMware Clud
EVALUATION GUIDE - OCTOBER 2018 VMWARE CLOUD ON AWS Evaluatin Guide Table f Cntents Intrductin 4 Intended Audience... 4 Assumptins... 4 User Interface Walkthrugh 4 Clud Cnsle Walkthrugh... 4 VMware Clud
ICND2 Lab Exercises Lesson Companion
 ICND2 Lab Exercises Lessn Cmpanin Je Rinehart MBA, CCIE #14256 CCNP/DP/VP Octber 11, 2014 Table f Cntents Intrductin... 5 The Overall Tplgy... 5 Purpse f the Lab Prject... 5 1.1 Packet Tracer Explratin...
ICND2 Lab Exercises Lessn Cmpanin Je Rinehart MBA, CCIE #14256 CCNP/DP/VP Octber 11, 2014 Table f Cntents Intrductin... 5 The Overall Tplgy... 5 Purpse f the Lab Prject... 5 1.1 Packet Tracer Explratin...
IPitomy IP1000 User Guide
 IPitmy IP1000 User Guide Table f Cntents INTRODUCTION...1 ABOUT THE IP1000...1 BENEFITS OF VOIP TECHNOLOGY...1 HOW THIS GUIDE WORKS...2 WEB-BASED SYSTEM SETUP...2 THE INSTALLATION WORKSHEET...2 PRODUCT
IPitmy IP1000 User Guide Table f Cntents INTRODUCTION...1 ABOUT THE IP1000...1 BENEFITS OF VOIP TECHNOLOGY...1 HOW THIS GUIDE WORKS...2 WEB-BASED SYSTEM SETUP...2 THE INSTALLATION WORKSHEET...2 PRODUCT
Please contact technical support if you have questions about the directory that your organization uses for user management.
 Overview ACTIVE DATA CALENDAR LDAP/AD IMPLEMENTATION GUIDE Active Data Calendar allws fr the use f single authenticatin fr users lgging int the administrative area f the applicatin thrugh LDAP/AD. LDAP
Overview ACTIVE DATA CALENDAR LDAP/AD IMPLEMENTATION GUIDE Active Data Calendar allws fr the use f single authenticatin fr users lgging int the administrative area f the applicatin thrugh LDAP/AD. LDAP
1. Which organization certifies vendors for adherence to the standards to improve interoperability of products?
 CCNA 3 Chapter 4 v5.0 Exam Answers 2015 (100%) 1. Which rganizatin certifies vendrs fr adherence t the 802.11 standards t imprve interperability f 802.11 prducts? FCC IEEE ITU-R Wi-Fi Alliance 2. Which
CCNA 3 Chapter 4 v5.0 Exam Answers 2015 (100%) 1. Which rganizatin certifies vendrs fr adherence t the 802.11 standards t imprve interperability f 802.11 prducts? FCC IEEE ITU-R Wi-Fi Alliance 2. Which
Competitor fills in. Expert fills in. Time: 6.75h 39 - IT Network Systems Administration Danny Meier, Florian Meier, Tobias Meier
 1/12 Time: 6.75h Trade: 39 - IT Netwrk Systems Administratin Experts: Danny Meier, Flrian Meier, Tbias Meier Cmpetitr fills in Name Date Signature Expert fills in Pints 2/12 Overview 1 EXAM... 3 1.1 CONTENTS...
1/12 Time: 6.75h Trade: 39 - IT Netwrk Systems Administratin Experts: Danny Meier, Flrian Meier, Tbias Meier Cmpetitr fills in Name Date Signature Expert fills in Pints 2/12 Overview 1 EXAM... 3 1.1 CONTENTS...
Pexip Infinity Secure Mode Deployment Guide
 Intrductin Pexip Infinity Secure Mde Deplyment Guide This guide cntains instructins fr deplying and using Pexip Infinity in a secure mde f peratin. Fr further infrmatin abut the deplyment instructins and
Intrductin Pexip Infinity Secure Mde Deplyment Guide This guide cntains instructins fr deplying and using Pexip Infinity in a secure mde f peratin. Fr further infrmatin abut the deplyment instructins and
1. Which IOS 12.4 software package integrates full features, including voice, security, and VPN capabilities, for all routing protocols?
 CCNA 3 Chapter 9 v5.0 Exam Answers 2015 (100%) 1. Which IOS 12.4 sftware package integrates full features, including vice, security, and VPN capabilities, fr all ruting prtcls? Advanced Security Advanced
CCNA 3 Chapter 9 v5.0 Exam Answers 2015 (100%) 1. Which IOS 12.4 sftware package integrates full features, including vice, security, and VPN capabilities, fr all ruting prtcls? Advanced Security Advanced
Model 86A00-2 Home Theater Extender 2 (HTX2)
 Mdel 86A00-2 Hme Theater Extender 2 (HTX2) DESCRIPTION The Mdel 86A00-2 Hme Theater Extender 2 (HTX2) allws yu t extend yur hme cntrl t the audi/vide equipment in yur hme theater. The HTX2 cmmunicates
Mdel 86A00-2 Hme Theater Extender 2 (HTX2) DESCRIPTION The Mdel 86A00-2 Hme Theater Extender 2 (HTX2) allws yu t extend yur hme cntrl t the audi/vide equipment in yur hme theater. The HTX2 cmmunicates
Felix Rohrer. Lab 5.5.3: Troubleshooting Access Control Lists. Topology Diagram
 Felix Rhrer Lab 5.5.3: Trubleshting Access Cntrl Lists Tplgy Diagram All cntents are Cpyright 1992 2007 Cisc Systems, Inc. All rights reserved. This dcument is Cisc Public Infrmatin. Page 1 f 6 CCNA Explratin
Felix Rhrer Lab 5.5.3: Trubleshting Access Cntrl Lists Tplgy Diagram All cntents are Cpyright 1992 2007 Cisc Systems, Inc. All rights reserved. This dcument is Cisc Public Infrmatin. Page 1 f 6 CCNA Explratin
Frequently Asked Questions
 Frequently Asked Questins Versin 10-21-2016 Cpyright 2014-2016 Aviatrix Systems, Inc. All rights reserved. Aviatrix Clud Gateway What can it d fr me? Aviatrix Clud Gateway prvides an end t end secure netwrk
Frequently Asked Questins Versin 10-21-2016 Cpyright 2014-2016 Aviatrix Systems, Inc. All rights reserved. Aviatrix Clud Gateway What can it d fr me? Aviatrix Clud Gateway prvides an end t end secure netwrk
Cisco Companion Topics
 Cisc Cmpanin Tpics CHAPTER I 3 Cnfiguring Cisc PIX Firewalls 3 Netwrk Address Translatin (NAT).. 3 Accessing the PIX cmmand line... 3 Sample PIX Cnfiguratin: DHCP.. 5 Hw T Get Static IPs Fr DSL Cheaply...
Cisc Cmpanin Tpics CHAPTER I 3 Cnfiguring Cisc PIX Firewalls 3 Netwrk Address Translatin (NAT).. 3 Accessing the PIX cmmand line... 3 Sample PIX Cnfiguratin: DHCP.. 5 Hw T Get Static IPs Fr DSL Cheaply...
Smart Collector Embedded Assistant User Guide
 Smart Cllectr Embedded Assistant User Guide Sept. 16, 2010 Crprate Headquarters Cisc Systems, Inc. 170 West Tasman Drive San Jse, CA 95134-1706 USA http://www.cisc.cm Smart Cllectr Embedded Assistant User
Smart Cllectr Embedded Assistant User Guide Sept. 16, 2010 Crprate Headquarters Cisc Systems, Inc. 170 West Tasman Drive San Jse, CA 95134-1706 USA http://www.cisc.cm Smart Cllectr Embedded Assistant User
NiceLabel LMS. Installation Guide for Single Server Deployment. Rev-1702 NiceLabel
 NiceLabel LMS Installatin Guide fr Single Server Deplyment Rev-1702 NiceLabel 2017. www.nicelabel.cm 1 Cntents 1 Cntents 2 2 Architecture 3 2.1 Server Cmpnents and Rles 3 2.2 Client Cmpnents 3 3 Prerequisites
NiceLabel LMS Installatin Guide fr Single Server Deplyment Rev-1702 NiceLabel 2017. www.nicelabel.cm 1 Cntents 1 Cntents 2 2 Architecture 3 2.1 Server Cmpnents and Rles 3 2.2 Client Cmpnents 3 3 Prerequisites
IPv6 Foundations: Protocols, Services and Migration
 IPv6 Fundatins: Prtcls, Services and Migratin Date Submitted: February 2 nd, 2014 Curse Title: IPv6 Fundatins: Prtcls, Services and Migratin Curse Number: 9105 Curse Length: Fur days Curse Descriptin:
IPv6 Fundatins: Prtcls, Services and Migratin Date Submitted: February 2 nd, 2014 Curse Title: IPv6 Fundatins: Prtcls, Services and Migratin Curse Number: 9105 Curse Length: Fur days Curse Descriptin:
Moving packets. Moving datagrams. Suppose host A want to send IP to host B. Host A wants to send to host E. Generalized forwarding and SDN
 Mving packets Generalized frwarding and SDN Mving datagrams 1. Surce hst fills in its address... 3. Data field is filled with paylad. CS242 Cmputer Netwrks 2.... and addresses destinatin address. Department
Mving packets Generalized frwarding and SDN Mving datagrams 1. Surce hst fills in its address... 3. Data field is filled with paylad. CS242 Cmputer Netwrks 2.... and addresses destinatin address. Department
Gemini Intercom Quick Start Guide
 Gemini Intercm Quick Start Guide 2 Quick Start Guide Cntents Cntents... 1 Overview... 3 First Step unpack and inspect... 3 Netwrk plan and IP addresses... 4 Management PC... 5 Install Sftware... 6 Cnfigure
Gemini Intercm Quick Start Guide 2 Quick Start Guide Cntents Cntents... 1 Overview... 3 First Step unpack and inspect... 3 Netwrk plan and IP addresses... 4 Management PC... 5 Install Sftware... 6 Cnfigure
Network Layer. Internet Control Message Protocol (ICMP)
 Handut 5 CAN1102 Netwrk Layer Internet Cntrl Message Prtcl (ICMP) Netwrks Netwrk Layer Services Ruting principles: path selectin Hierarchal ruting IP Internet Ruting Prtcls: Reliable Transfer a. Intra
Handut 5 CAN1102 Netwrk Layer Internet Cntrl Message Prtcl (ICMP) Netwrks Netwrk Layer Services Ruting principles: path selectin Hierarchal ruting IP Internet Ruting Prtcls: Reliable Transfer a. Intra
FIREWALL RULE SET OPTIMIZATION
 Authr Name: Mungle Mukupa Supervisr : Mr Barry Irwin Date : 25 th Octber 2010 Security and Netwrks Research Grup Department f Cmputer Science Rhdes University Intrductin Firewalls have been and cntinue
Authr Name: Mungle Mukupa Supervisr : Mr Barry Irwin Date : 25 th Octber 2010 Security and Netwrks Research Grup Department f Cmputer Science Rhdes University Intrductin Firewalls have been and cntinue
ASM Educational Center (ASM) Est Authorized SCNS Security Certified Network Specialist Boot Camp
 ASM Educatinal Center (ASM) Est. 1992 11200 Rckville Pike, Suite 220 Rckville, MD 20852 Phne: 301-984-7400 Fax: 301-984-7401 Web: www.asmed.cm E-mail: inf@asmed.cm Authrized SCNS Security Certified Netwrk
ASM Educatinal Center (ASM) Est. 1992 11200 Rckville Pike, Suite 220 Rckville, MD 20852 Phne: 301-984-7400 Fax: 301-984-7401 Web: www.asmed.cm E-mail: inf@asmed.cm Authrized SCNS Security Certified Netwrk
USER MANUAL. RoomWizard Administrative Console
 USER MANUAL RmWizard Administrative Cnsle Cntents Welcme... 3 Administer yur RmWizards frm ne lcatin... 3 Abut This Manual... 4 Setup f the Administrative Cnsle... 4 Installatin... 4 The Cnsle Windw...
USER MANUAL RmWizard Administrative Cnsle Cntents Welcme... 3 Administer yur RmWizards frm ne lcatin... 3 Abut This Manual... 4 Setup f the Administrative Cnsle... 4 Installatin... 4 The Cnsle Windw...
BMC Remedyforce Integration with Remote Support
 BMC Remedyfrce Integratin with Remte Supprt 2003-2018 BeyndTrust, Inc. All Rights Reserved. BEYONDTRUST, its lg, and JUMP are trademarks f BeyndTrust, Inc. Other trademarks are the prperty f their respective
BMC Remedyfrce Integratin with Remte Supprt 2003-2018 BeyndTrust, Inc. All Rights Reserved. BEYONDTRUST, its lg, and JUMP are trademarks f BeyndTrust, Inc. Other trademarks are the prperty f their respective
Web Application Security Version 13.0 Training Course
 Web Applicatin Security Versin 13.0 Training Curse SecureSphere Web Applicatin Security Versin 13.0 Required Training Units: 4 (TR-UNIT) Training Units are gd fr 1 year frm the time f purchase. Length:
Web Applicatin Security Versin 13.0 Training Curse SecureSphere Web Applicatin Security Versin 13.0 Required Training Units: 4 (TR-UNIT) Training Units are gd fr 1 year frm the time f purchase. Length:
Pexip Infinity Secure Mode Deployment Guide
 Intrductin Pexip Infinity Secure Mde Deplyment Guide This guide cntains instructins fr deplying and using Pexip Infinity in a secure mde f peratin. Fr further infrmatin abut the deplyment instructins and
Intrductin Pexip Infinity Secure Mde Deplyment Guide This guide cntains instructins fr deplying and using Pexip Infinity in a secure mde f peratin. Fr further infrmatin abut the deplyment instructins and
MAP-2000 / MAP-2000R MAP-2100
 PLANET Mesh Netwrk MAP-2000 / MAP-2000R MAP-2100 Web Based Management & User Manual Rev 1.0 Page 1 f 80 Table f Cntent 1 Intrductin 4 2 Web based management 7 2.1 T start the Web based cnfiguratin 7 2.2
PLANET Mesh Netwrk MAP-2000 / MAP-2000R MAP-2100 Web Based Management & User Manual Rev 1.0 Page 1 f 80 Table f Cntent 1 Intrductin 4 2 Web based management 7 2.1 T start the Web based cnfiguratin 7 2.2
The VMs in the CIS VLab (Virtual Lab) We will be using a number of different Virtual Machines (VMs) in VLab for this course.
 Lab 1: Using the CIS 192 Lab Resurces The purpse f this lab is t becme familiar with the CIS Lab resurces and t start practicing sme ld and new Linux cmmands. Resurces The Opus server CIS VLab (Virtual
Lab 1: Using the CIS 192 Lab Resurces The purpse f this lab is t becme familiar with the CIS Lab resurces and t start practicing sme ld and new Linux cmmands. Resurces The Opus server CIS VLab (Virtual
Remove AD DS using the Remove Roles Wizard in Server Manager
 Remve AD DS using the Remve Rles Wizard in Server Manager The fllwing prcedure shws the steps t remve AD DS using the Remve Rles Wizard in Server Manager. Administrative credentials T remve a dmain cntrller,
Remve AD DS using the Remve Rles Wizard in Server Manager The fllwing prcedure shws the steps t remve AD DS using the Remve Rles Wizard in Server Manager. Administrative credentials T remve a dmain cntrller,
Secure File Transfer Protocol (SFTP) Interface for Data Intake User Guide
 Secure File Transfer Prtcl (SFTP) Interface fr Data Intake User Guide Cntents Descriptin... 2 Steps fr firms new t batch submissin... 2 Acquiring necessary FINRA accunts... 2 SFTP Access t FINRA... 2 SFTP
Secure File Transfer Prtcl (SFTP) Interface fr Data Intake User Guide Cntents Descriptin... 2 Steps fr firms new t batch submissin... 2 Acquiring necessary FINRA accunts... 2 SFTP Access t FINRA... 2 SFTP
USER GUIDE. Thanks for purchasing the igate! You ll need to follow these five Configuration Steps to get your igate up and running:
 USER GUIDE Thanks fr purchasing the igate! Yu ll need t fllw these five Cnfiguratin Steps t get yur igate up and running: 1. Cnfigure Yur Hardware 2. Cnfigure Yur Cmputer 3. Cnfigure Yur Internet Cnnectin
USER GUIDE Thanks fr purchasing the igate! Yu ll need t fllw these five Cnfiguratin Steps t get yur igate up and running: 1. Cnfigure Yur Hardware 2. Cnfigure Yur Cmputer 3. Cnfigure Yur Internet Cnnectin
1. What are two disadvantages of employing teleworkers in an organization? (Choose two.)
 CCNA 4 Chapter 6 v5.0 Exam Answers 2015 (100%) 1. What are tw disadvantages f emplying telewrkers in an rganizatin? (Chse tw.) increased usage f sick r vacatin days increased difficulty f tracking task
CCNA 4 Chapter 6 v5.0 Exam Answers 2015 (100%) 1. What are tw disadvantages f emplying telewrkers in an rganizatin? (Chse tw.) increased usage f sick r vacatin days increased difficulty f tracking task
Lecture 6 -.NET Remoting
 Lecture 6 -.NET Remting 1. What is.net Remting?.NET Remting is a RPC technique that facilitates cmmunicatin between different applicatin dmains. It allws cmmunicatin within the same prcess, between varius
Lecture 6 -.NET Remting 1. What is.net Remting?.NET Remting is a RPC technique that facilitates cmmunicatin between different applicatin dmains. It allws cmmunicatin within the same prcess, between varius
Chapter 4. IP Addresses: Classful Addressing. PDF created with FinePrint pdffactory Pro trial version
 Chapter 4 IP Addresses: Classful Addressing Outlines Intrductin Classfuladdressing Other issues A sample Internet 4.1 INTRODUCTION Intrductin IP address, r Internet Address 32-bit binary address Uniquely
Chapter 4 IP Addresses: Classful Addressing Outlines Intrductin Classfuladdressing Other issues A sample Internet 4.1 INTRODUCTION Intrductin IP address, r Internet Address 32-bit binary address Uniquely
TSHOOT v2.0 Troubleshooting and Maintaining Cisco IP Networks
 TSHOOT v2.0 Trubleshting and Maintaining Cisc IP Netwrks Curse Length: 5 Curse Delivery: Traditinal Classrm Online Live Curse Overview TSHOOT v2.0, a five-day ILT curse, includes majr updates and fllws
TSHOOT v2.0 Trubleshting and Maintaining Cisc IP Netwrks Curse Length: 5 Curse Delivery: Traditinal Classrm Online Live Curse Overview TSHOOT v2.0, a five-day ILT curse, includes majr updates and fllws
Cisco Smart Software Manager satellite
 Data Sheet Cisc Smart Sftware Manager satellite Last Updated: May 12, 2017 Overview Cisc Smart Sftware Manager satellite is a cmpnent f Cisc Smart Licensing. It wrks in cnjunctin with Cisc Smart Sftware
Data Sheet Cisc Smart Sftware Manager satellite Last Updated: May 12, 2017 Overview Cisc Smart Sftware Manager satellite is a cmpnent f Cisc Smart Licensing. It wrks in cnjunctin with Cisc Smart Sftware
Enterprise Installation
 Enterprise Installatin Mnnit Crpratin Versin 3.6.0.0 Cntents Prerequisites... 3 Web Server... 3 SQL Server... 3 Installatin... 4 Activatin Key... 4 Dwnlad... 4 Cnfiguratin Wizard... 4 Activatin... 4 Create
Enterprise Installatin Mnnit Crpratin Versin 3.6.0.0 Cntents Prerequisites... 3 Web Server... 3 SQL Server... 3 Installatin... 4 Activatin Key... 4 Dwnlad... 4 Cnfiguratin Wizard... 4 Activatin... 4 Create
TRENDnet User s Guide. Cover Page
 Cver Page General Disclaimer Thank yu fr purchasing yur new TRENDnet PE Web Smart Switch! Please nte: The scpe f this user's guide encmpasses multiple prducts with varying features. Images, artwrk, and
Cver Page General Disclaimer Thank yu fr purchasing yur new TRENDnet PE Web Smart Switch! Please nte: The scpe f this user's guide encmpasses multiple prducts with varying features. Images, artwrk, and
Chapter 6 Delivery and Routing of IP Packets. PDF created with FinePrint pdffactory Pro trial version
 Chapter 6 Delivery and Ruting f IP Packets PDF created with FinePrint pdffactry Pr trial versin www.pdffactry.cm Outline Cnnectin Delivery Ruting methds Static and dynamic ruting Ruting table and mdule
Chapter 6 Delivery and Ruting f IP Packets PDF created with FinePrint pdffactry Pr trial versin www.pdffactry.cm Outline Cnnectin Delivery Ruting methds Static and dynamic ruting Ruting table and mdule
Configuring Database & SQL Query Monitoring With Sentry-go Quick & Plus! monitors
 Cnfiguring Database & SQL Query Mnitring With Sentry-g Quick & Plus! mnitrs 3Ds (UK) Limited, Nvember, 2013 http://www.sentry-g.cm Be Practive, Nt Reactive! One f the best ways f ensuring a database is
Cnfiguring Database & SQL Query Mnitring With Sentry-g Quick & Plus! mnitrs 3Ds (UK) Limited, Nvember, 2013 http://www.sentry-g.cm Be Practive, Nt Reactive! One f the best ways f ensuring a database is
WDBWL v1.2 Cisco Deploying Basic Wireless LANs
 WDBWL v1.2 Cisc Deplying Basic Wireless LANs Curse Length: 3 Curse Delivery: Traditinal Classrm Online Live Curse Overview This 3-day instructr-led, hands-n curse is designed t give yu a firm understanding
WDBWL v1.2 Cisc Deplying Basic Wireless LANs Curse Length: 3 Curse Delivery: Traditinal Classrm Online Live Curse Overview This 3-day instructr-led, hands-n curse is designed t give yu a firm understanding
Campuses that access the SFS nvision Windows-based client need to allow outbound traffic to:
 Summary This dcument is a guide intended t guide yu thrugh the prcess f installing and cnfiguring PepleTls 8.55.27 (r current versin) via Windws Remte Applicatin (App). Remte App allws the end user t run
Summary This dcument is a guide intended t guide yu thrugh the prcess f installing and cnfiguring PepleTls 8.55.27 (r current versin) via Windws Remte Applicatin (App). Remte App allws the end user t run
Model WM100. Product Manual
 Mdel WM100 Prduct Manual Table f Cntents Sectin Page 1. Hardware... 3 2. Sftware... 4 3. Features... 5 4. Installatin... 6 5. App Devices... 9 6. App Rms... 12 7. App Scenes... 14 8. App Setup... 18 Cntents
Mdel WM100 Prduct Manual Table f Cntents Sectin Page 1. Hardware... 3 2. Sftware... 4 3. Features... 5 4. Installatin... 6 5. App Devices... 9 6. App Rms... 12 7. App Scenes... 14 8. App Setup... 18 Cntents
Power365. Quick Start Guide
 Pwer365 Quick Start Guide 12/2017 Table f Cntents Prject Types... 4 The Email Frm File Prject Type... 4 The Email With Discvery Prject Type... 4 The Integratin Prject Type... 4 The Integratin Pr Prject
Pwer365 Quick Start Guide 12/2017 Table f Cntents Prject Types... 4 The Email Frm File Prject Type... 4 The Email With Discvery Prject Type... 4 The Integratin Prject Type... 4 The Integratin Pr Prject
File Share Navigator Online
 File Share Navigatr Online User Guide Service Pack 7 Issued September 2017 Table f Cntents What s New in this Guide... 4 Abut File Share Navigatr Online... 5 Cmpnents f File Share Navigatr Online... 5
File Share Navigatr Online User Guide Service Pack 7 Issued September 2017 Table f Cntents What s New in this Guide... 4 Abut File Share Navigatr Online... 5 Cmpnents f File Share Navigatr Online... 5
Software Defined Networking and OpenFlow. Jeffrey Dalla Tezza and Nate Schloss
 Sftware Defined Netwrking and OpenFlw Jeffrey Dalla Tezza and Nate Schlss Agenda What is SDN SDN Tday What is OpenFlw Why OpenFlw What s next fr SDN Our OpenFlw Demnstratin Sftware Defined Netwrking Wikipedia
Sftware Defined Netwrking and OpenFlw Jeffrey Dalla Tezza and Nate Schlss Agenda What is SDN SDN Tday What is OpenFlw Why OpenFlw What s next fr SDN Our OpenFlw Demnstratin Sftware Defined Netwrking Wikipedia
DocAve 6 Replicator. User Guide. Service Pack 2, Cumulative Update 2. Revision F Issued June DocAve 6: Archiver
 DcAve 6 Replicatr User Guide Service Pack 2, Cumulative Update 2 Revisin F Issued June 2013 DcAve 6: Archiver 1 Table f Cntents Table f Cntents... 2 Abut DcAve Replicatr... 5 Cmplementary Prducts... 5
DcAve 6 Replicatr User Guide Service Pack 2, Cumulative Update 2 Revisin F Issued June 2013 DcAve 6: Archiver 1 Table f Cntents Table f Cntents... 2 Abut DcAve Replicatr... 5 Cmplementary Prducts... 5
BMC Remedyforce Integration with Bomgar Remote Support
 BMC Remedyfrce Integratin with Bmgar Remte Supprt 2017 Bmgar Crpratin. All rights reserved wrldwide. BOMGAR and the BOMGAR lg are trademarks f Bmgar Crpratin; ther trademarks shwn are the prperty f their
BMC Remedyfrce Integratin with Bmgar Remte Supprt 2017 Bmgar Crpratin. All rights reserved wrldwide. BOMGAR and the BOMGAR lg are trademarks f Bmgar Crpratin; ther trademarks shwn are the prperty f their
Understanding Active Directory Domain Services (AD DS) Functional Levels
 Understanding Active Directry Dmain Services (AD DS) Functinal Levels 92 ut f 99 rated this helpful - Rate this tpic Updated: May 28, 2014 Applies T:,,, Functinal levels determine the available Active
Understanding Active Directry Dmain Services (AD DS) Functinal Levels 92 ut f 99 rated this helpful - Rate this tpic Updated: May 28, 2014 Applies T:,,, Functinal levels determine the available Active
IDEAL ADMINISTRATION 2018
 System requirements: Windws NT, Windws XP, Windws Vista, Windws 2000, Windws 2003 Server, Windws 2008 Server, Windws 7, Windws 8, Windws 10, Windws 2012 Server, Windws 2016 Server. Cmpatible with 32 bit
System requirements: Windws NT, Windws XP, Windws Vista, Windws 2000, Windws 2003 Server, Windws 2008 Server, Windws 7, Windws 8, Windws 10, Windws 2012 Server, Windws 2016 Server. Cmpatible with 32 bit
TCG Compliance_TNC IF-PEP Compliance Test Plan
 TCG Cmpliance_TNC IF-PEP Cmpliance Test Plan Versin 1.00 Revisin 0.21 8 December 2008 Published Cntact: admin@trustedcmputinggrup.rg Cpyright TCG 2006-2008 TCG Cmpliance_TNC IF-PEP Cmpliance Test Plan
TCG Cmpliance_TNC IF-PEP Cmpliance Test Plan Versin 1.00 Revisin 0.21 8 December 2008 Published Cntact: admin@trustedcmputinggrup.rg Cpyright TCG 2006-2008 TCG Cmpliance_TNC IF-PEP Cmpliance Test Plan
Amazon Lab: Deploying applications on AWS
 Amazn Lab: Deplying applicatins n AWS By Nabil Abdennadher 8 th Nvember 2017 OBJECTIVES 1. Hw t cnfigure yur Virtual Private Clud (VPC)? 2. Hw t create and access instances via Amazn Web Services (AWS)
Amazn Lab: Deplying applicatins n AWS By Nabil Abdennadher 8 th Nvember 2017 OBJECTIVES 1. Hw t cnfigure yur Virtual Private Clud (VPC)? 2. Hw t create and access instances via Amazn Web Services (AWS)
DNS (Domain Name Service)
 mywbut.cm DNS (Dmain Name Service) The internet primarily uses IP addresses fr lcating ndes. Hwever, its humanly nt pssible fr us t keep track f the many imprtant ndes as numbers. Alphabetical names as
mywbut.cm DNS (Dmain Name Service) The internet primarily uses IP addresses fr lcating ndes. Hwever, its humanly nt pssible fr us t keep track f the many imprtant ndes as numbers. Alphabetical names as
SIEM Use Cases 45 use cases for Security Monitoring
 www.paladin.net SIEM Use Cases 45 use cases fr Security Mnitring Paladin - SIEM Use Cases Use Case 02 Descriptin DMZ Jumping This rule will fire when cnnectins seemed t be bridged acrss the netwrk's DMZ.
www.paladin.net SIEM Use Cases 45 use cases fr Security Mnitring Paladin - SIEM Use Cases Use Case 02 Descriptin DMZ Jumping This rule will fire when cnnectins seemed t be bridged acrss the netwrk's DMZ.
