Mobile Ad Hoc Networks
|
|
|
- Reynold Day
- 6 years ago
- Views:
Transcription
1 Mobile Ad Hoc Networks Tutorial at CIT 2000 Bhubaneshwar, Dec Sridhar Iyer IIT Bombay
2 Acknowledgements Many figures, slides and reference citations are taken from Nitin Vaidya s MobiCom 2000 tutorial Nitin s tutorial is available online at
3 Introduction Medium Access Control Routing (unicast) Reactive Protocols Proactive Protocols Hybrid Protocols Transport Issues Summary and Conclusions Outline
4 Wireless Networks Need: Access computing and communication services, on the move Infrastructure based Networks traditional cellular systems (base station infrastructure) Wireless LANs Infrared (IrDA) or radio links (Wavelan) very flexible within the reception area; ad hoc networks possible low bandwidth compared to wired networks (1 10 Mbit/s) Ad hoc Networks useful when infrastructure not available, impractical, or expensive military applications, rescue, home networking
5 Cellular Wireless Single hop wireless connectivity to the wired world Space divided into cells A base station is responsible to communicate with hosts in its cell Mobile hosts can change cells while communicating Hand off occurs when a mobile host starts communicating via a new base station
6 Multi Hop Wireless May need to traverse multiple links to reach destination Mobility causes route changes
7 Mobile Ad Hoc Networks (MANET) Host movement frequent Topology change frequent A B A B No cellular infrastructure. Multi hop wireless links. Data must be routed via intermediate nodes.
8 Why Ad Hoc Networks? Setting up of fixed access points and backbone infrastructure is not always viable Infrastructure may not be present in a disaster area or war zone Infrastructure may not be practical for short range radios; Bluetooth (range ~ 10m) Ad hoc networks: Do not need backbone infrastructure support Are easy to deploy Useful when infrastructure is absent, destroyed or impractical
9 Many Applications Personal area networking cell phone, laptop, ear phone, wrist watch Military environments soldiers, tanks, planes Civilian environments taxi cab network meeting rooms sports stadiums boats, small aircraft Emergency operations search and rescue policing and fire fighting
10 Challenges in Mobile Environments Limitations of the Wireless Network packet loss due to transmission errors variable capacity links frequent disconnections/partitions limited communication bandwidth Broadcast nature of the communications Limitations Imposed by Mobility dynamically changing topologies/routes lack of mobility awareness by system/applications Limitations of the Mobile Computer short battery lifetime limited capacities
11 Effect of mobility on the protocol stack Application new applications and adaptations Transport congestion and flow control Network addressing and routing Link media access and handoff Physical transmission errors and interference
12 Medium Access Control in MANET
13 Motivation Can we apply media access methods from fixed networks? Example CSMA/CD Carrier Sense Multiple Access with Collision Detection send as soon as the medium is free, listen into the medium if a collision occurs (original method in IEEE 802.3) Medium access problems in wireless networks signal strength decreases proportional to the square of the distance sender would apply CS and CD, but the collisions happen at the receiver sender may not hear the collision, i.e., CD does not work CS might not work, e.g. if a terminal is hidden
14 Hidden and Exposed Terminals Hidden terminals A sends to B, C cannot receive A C wants to send to B, C senses a free medium (CS fails) collision at B, A cannot receive the collision (CD fails) A is hidden for C A B C Exposed terminals B sends to A, C wants to send to another terminal (not A or B) C senses carrier, finds medium in use and has to wait A is outside the radio range of C, therefore waiting is not necessary C is exposed to B
15 Multiple Access with Collision Avoidance (MACA) [Karn90] MACA uses signaling packets for collision avoidance RTS (request to send) sender request the right to send from a receiver with a short RTS packet before it sends a data packet CTS (clear to send) receiver grants the right to send as soon as it is ready to receive Signaling packets contain sender address receiver address packet size Variants of this method are used in IEEE
16 MACA Solutions [Karn90] MACA avoids the problem of hidden terminals A and C want to send to B A sends RTS first C waits after receiving CTS from B RTS A B C CTS CTS MACA avoids the problem of exposed terminals B wants to send to A, C to another terminal now C does not have RTS RTS to wait, as it cannot A B C CTS receive CTS from A
17 MAC: Reliability Wireless links are prone to errors. High packet loss rate is detrimental to transport layer performance. Solution: Use of acknowledgements When node B receives a data packet from node A, node B sends an Acknowledgement (Ack). If node A fails to receive an Ack, it will retransmit the packet This approach adopted in many protocols [Bharghavan94, IEEE ] IEEE Wireless MAC Distributed and centralized MAC components Distributed Coordination Function (DCF) Point Coordination Function (PCF) DCF suitable for multi hop ad hoc networking
18 IEEE DCF Uses RTS CTS exchange to avoid hidden terminal problem Any node overhearing a CTS cannot transmit for the duration of the transfer Uses ACK to achieve reliability Any node receiving the RTS cannot transmit for the duration of the transfer To prevent collision with ACK when it arrives at the sender When B is sending data to C, node A will keep quiet A B C
19 MAC: Collision Avoidance With half duplex radios, collision detection is not possible Collision avoidance: Once channel becomes idle, the node waits for a randomly chosen duration before attempting to transmit IEEE DCF When transmitting a packet, choose a backoff interval in the range [0,cw]; cw is contention window Count down the backoff interval when medium is idle Count down is suspended if medium becomes busy When backoff interval reaches 0, transmit RTS Time spent counting down backoff intervals is a part of MAC overhead large cw leads to larger backoff intervals small cw leads to larger number of collisions
20 MAC: Congestion Control IEEE DCF: Congestion control achieved by dynamically choosing the contention window cw Binary Exponential Backoff in DCF: When a node fails to receive CTS in response to its RTS, it increases the contention window cw is doubled (up to an upper bound) When a node successfully completes a data transfer, it restores cw to CWmin
21 MAC: Energy Conservation Proposals typically suggest turning the radio off when not needed Power Saving Mode in IEEE (Infrastructure Mode) An Access Point periodically transmits a beacon indicating which nodes have packets waiting for them Each power saving (PS) node wakes up periodically to receive the beacon If a node has a packet waiting, then it sends a PS Poll After waiting for a backoff interval in [0,CWmin] Access Point sends the data in response to PS poll
22 MAC Protocols: Summary Wireless medium is prone to hidden and exposed terminal problems Protocols are typically based on CSMA/CA RTS/CTS based signaling Acks for reliability Contention window is used for congestion control IEEE wireless LAN standard Fairness issues are still unclear
23 Routing Protocols
24 Traditional Routing A routing protocol sets up a routing table in routers A node makes a local choice depending on global topology
25 Distance vector & Link state Routing Both assume router knows address of each neighbor cost of reaching each neighbor Both allow a router to determine global routing information by talking to its neighbors Distance vector router knows cost to each destination Link state router knows entire network topology and computes shortest path
26 Distance Vector Routing: Example 2
27 Link State Routing: Example
28 Routing and Mobility Finding a path from a source to a destination Issues Frequent route changes amount of data transferred between route changes may be much smaller than traditional networks Route changes may be related to host movement Low bandwidth links Goal of routing protocols decrease routing related overhead find short routes find stable routes (despite mobility)
29 Mobile IP S MH Router 3 Router 1 Home agent Router 2
30 Mobile IP move S Router 3 Foreign agent MH Router 1 Home agent Router 2 Packets are tunneled using IP in IP
31 Routing in MANET
32 Unicast Routing Protocols Many protocols have been proposed Some specifically invented for MANET Others adapted from protocols for wired networks No single protocol works well in all environments some attempts made to develop adaptive/hybrid protocols Standardization efforts in IETF MANET, MobileIP working groups
33 Routing Protocols Proactive protocols Traditional distributed shortest path protocols Maintain routes between every host pair at all times Based on periodic updates; High routing overhead Example: DSDV (destination sequenced distance vector) Reactive protocols Determine route if and when needed Source initiates route discovery Example: DSR (dynamic source routing) Hybrid protocols Adaptive; Combination of proactive and reactive Example : ZRP (zone routing protocol)
34 Protocol Trade offs Proactive protocols Always maintain routes Little or no delay for route determination Consume bandwidth to keep routes up to date Maintain routes which may never be used Reactive protocols Lower overhead since routes are determined on demand Significant delay in route determination Employ flooding (global search) Control traffic may be bursty Which approach achieves a better trade off depends on the traffic and mobility patterns
35 Reactive Routing Protocols
36 Dynamic Source Routing (DSR) [Johnson96] When node S wants to send a packet to node D, but does not know a route to D, node S initiates a route discovery Source node S floods Route Request (RREQ) Each node appends own identifier when forwarding RREQ
37 Route Discovery in DSR Y Z S E A B H C I G F K J D M N L Represents a node that has received RREQ for D from S
38 Route Discovery in DSR Broadcast transmission Y [S] Z S E A B H C I G F K J D M N L Represents transmission of RREQ [X,Y] Represents list of identifiers appended to RREQ
39 Route Discovery in DSR Y S E [S,E] Z A B H C [S,C] I G F K J D M N L Node H receives packet RREQ from two neighbors: potential for collision
40 Route Discovery in DSR Y Z S E A B H C I G F [S,C,G] [S,E,F] K J D M N L Node C receives RREQ from G and H, but does not forward it again, because node C has already forwarded RREQ once
41 Route Discovery in DSR Y Z A B H S C I E G F [S,E,F,J] M J D K [S,C,G,K] N L Nodes J and K both broadcast RREQ to node D Since nodes J and K are hidden from each other, their transmissions may collide
42 Route Discovery in DSR Y Z A B H S C I E G F K J [S,E,F,J,M] M L D N Node D does not forward RREQ, because node D is the intended target of the route discovery
43 Route Discovery in DSR Destination D on receiving the first RREQ, sends a Route Reply (RREP) RREP is sent on a route obtained by reversing the route appended to received RREQ RREP includes the route from S to D on which RREQ was received by node D
44 Route Reply in DSR Y S E RREP [S,E,F,J,D] Z A B H C I G F K J M D N L Represents RREP control message
45 Dynamic Source Routing (DSR) Node S on receiving RREP, caches the route included in the RREP When node S sends a data packet to D, the entire route is included in the packet header hence the name source routing Intermediate nodes use the source route included in a packet to determine to whom a packet should be forwarded
46 Data Delivery in DSR Y DATA [S,E,F,J,D] Z S E A B H C I G F K J D M N L Packet header size grows with route length
47 DSR Optimization: Route Caching Each node caches a new route it learns by any means When node S finds route [S,E,F,J,D] to node D, node S also learns route [S,E,F] to node F When node K receives Route Request [S,C,G] destined for node, node K learns route [K,G,C,S] to node S When node F forwards Route Reply RREP [S,E,F,J,D], node F learns route [F,J,D] to node D When node E forwards Data [S,E,F,J,D] it learns route [E,F,J,D] to node D A node may also learn a route when it overhears Data Problem: Stale caches may increase overheads
48 Dynamic Source Routing: Advantages Routes maintained only between nodes who need to communicate reduces overhead of route maintenance Route caching can further reduce route discovery overhead A single route discovery may yield many routes to the destination, due to intermediate nodes replying from local caches
49 Dynamic Source Routing: Disadvantages Packet header size grows with route length due to source routing Flood of route requests may potentially reach all nodes in the network Potential collisions between route requests propagated by neighboring nodes insertion of random delays before forwarding RREQ Increased contention if too many route replies come back due to nodes replying using their local cache Route Reply Storm problem Stale caches will lead to increased overhead
50 Location Aided Routing (LAR) [Ko98Mobicom] Exploits location information to limit scope of route request flood Location information may be obtained using GPS Expected Zone is determined as a region that is expected to hold the current location of the destination Expected region determined based on potentially old location information, and knowledge of the destination s speed Route requests limited to a Request Zone that contains the Expected Zone and location of the sender node
51 Request Zone Define a Request Zone LAR is same as flooding, except that only nodes in request zone forward route request Smallest rectangle including S and expected zone for D Request Zone D Expected Zone x S Y
52 Location Aided Routing (LAR) Advantages reduces the scope of route request flood reduces overhead of route discovery Disadvantages Nodes need to know their physical locations Does not take into account possible existence of obstructions for radio transmissions
53 Ad Hoc On Demand Distance Vector Routing (AODV) [Perkins99Wmcsa] DSR includes source routes in packet headers Resulting large headers can sometimes degrade performance particularly when data contents of a packet are small AODV attempts to improve on DSR by maintaining routing tables at the nodes, so that data packets do not have to contain routes AODV retains the desirable feature of DSR that routes are maintained only between nodes which need to communicate
54 AODV Route Requests (RREQ) are forwarded in a manner similar to DSR When a node re broadcasts a Route Request, it sets up a reverse path pointing towards the source AODV assumes symmetric (bi directional) links When the intended destination receives a Route Request, it replies by sending a Route Reply (RREP) Route Reply travels along the reverse path set up when Route Request is forwarded
55 Route Requests in AODV Y Z S E A B H C I G F K J D M N L Represents a node that has received RREQ for D from S
56 Route Requests in AODV Broadcast transmission Y Z S E A B H C I G F K J D M N L Represents transmission of RREQ
57 Route Requests in AODV Y Z S E A B H C I G F K J D M N L Represents links on Reverse Path
58 Reverse Path Setup in AODV Y Z S E A B H C I G F K J D M N L Node C receives RREQ from G and H, but does not forward it again, because node C has already forwarded RREQ once
59 Reverse Path Setup in AODV Y Z S E A B H C I G F K J D M N L
60 Reverse Path Setup in AODV Y Z S E A B H C I G F K J D M N L Node D does not forward RREQ, because node D is the intended target of the RREQ
61 Forward Path Setup in AODV Y Z S E A B H C I G F K J D M N L Forward links are setup when RREP travels along the reverse path Represents a link on the forward path
62 Route Request and Route Reply Route Request (RREQ) includes the last known sequence number for the destination An intermediate node may also send a Route Reply (RREP) provided that it knows a more recent path than the one previously known to sender Intermediate nodes that forward the RREP, also record the next hop to destination A routing table entry maintaining a reverse path is purged after a timeout interval A routing table entry maintaining a forward path is purged if not used for a active_route_timeout interval
63 Link Failure A neighbor of node X is considered active for a routing table entry if the neighbor sent a packet within active_route_timeout interval which was forwarded using that entry Neighboring nodes periodically exchange hello message When the next hop link in a routing table entry breaks, all active neighbors are informed Link failures are propagated by means of Route Error (RERR) messages, which also update destination sequence numbers
64 Route Error When node X is unable to forward packet P (from node S to node D) on link (X,Y), it generates a RERR message Node X increments the destination sequence number for D cached at node X The incremented sequence number N is included in the RERR When node S receives the RERR, it initiates a new route discovery for D using destination sequence number at least as large as N When node D receives the route request with destination sequence number N, node D will set its sequence number to N, unless it is already larger than N
65 AODV: Summary Routes need not be included in packet headers Nodes maintain routing tables containing entries only for routes that are in active use At most one next hop per destination maintained at each node DSR may maintain several routes for a single destination Sequence numbers are used to avoid old/broken routes Sequence numbers prevent formation of routing loops Unused routes expire even if topology does not change
66 Other Protocols Many variations of using control packet flooding for route discovery Power Aware Routing [Singh98Mobicom] Assign a weight to each link: function of energy consumed when transmitting a packet on that link, as well as the residual energy level Modify DSR to incorporate weights and prefer a route with the smallest aggregate weight Associativity Based Routing (ABR) [Toh97] Only links that have been stable for some minimum duration are utilized Nodes increment the associativity ticks of neighbors by using periodic beacons Signal Stability Based Adaptive Routing (SSA) [Dube97] A node X re broadcasts a Route Request received from Y only if the (X,Y) link has a strong signal stability Signal stability is evaluated as a moving average of the signal strength of packets received on the link in recent past
67 Signal Stability Routing (SSA)
68 Signal Stability Routing (SSA)
69 Link Reversal Algorithm [Gafni81] A B F C E G D
70 Link Reversal Algorithm A B F Links are bi directional C E G But algorithm imposes logical directions on them D Maintain a directed acyclic graph (DAG) for each destination, with the destination being the only sink This DAG is for destination node D
71 Link Reversal Algorithm A B F C E G Link (G,D) broke D Any node, other than the destination, that has no outgoing links reverses all its incoming links. Node G has no outgoing links
72 Link Reversal Algorithm A B F C E G Represents a link that was reversed recently D Now nodes E and F have no outgoing links
73 Link Reversal Algorithm A B F C E G Represents a link that was reversed recently D Now nodes B and G have no outgoing links
74 Link Reversal Algorithm A B F C E G Represents a link that was reversed recently D Now nodes A and F have no outgoing links
75 Link Reversal Algorithm A B F C E G Represents a link that was reversed recently D Now all nodes (other than destination D) have an outgoing link
76 Link Reversal Algorithm A B F C E G D DAG has been restored with only the destination as a sink
77 Link Reversal Algorithm Attempts to keep link reversals local to where the failure occurred But this is not guaranteed When the first packet is sent to a destination, the destination oriented DAG is constructed The initial construction does result in flooding of control packets
78 Link Reversal Algorithm The previous algorithm is called a full reversal method since when a node reverses links, it reverses all its incoming links Partial reversal method [Gafni81]: A node reverses incoming links from only those neighbors who have not themselves reversed links previously If all neighbors have reversed links, then the node reverses all its incoming links Previously at node X means since the last link reversal done by node X
79 Link Reversal Methods Advantages Link reversal methods attempt to limit updates to routing tables at nodes in the vicinity of a broken link Partial reversal method tends to be better than full reversal method Each node may potentially have multiple routes to a destination Disadvantages Need a mechanism to detect link failure hello messages may be used If network is partitioned, link reversals continue indefinitely
80 Temporally Ordered Routing Algorithm (TORA) [Park97Infocom] Route optimality is considered of secondary importance; longer routes may be used At each node, a logically separate copy of TORA is run for each destination, that computes the height of the node with respect to the destination Height captures number of hops and next hop Route discovery is by using query and update packets TORA modifies the partial link reversal method to be able to detect partitions When a partition is detected, all nodes in the partition are informed, and link reversals in that partition cease
81 Asymmetric Algorithms Clusterhead Gateway Switch Routing (CGSR) All nodes within a cluster communicate with a clusterhead Routing uses a hierarchical clusterhead to gateway approach Core Extraction Distributed Ad Hoc Routing (CEDAR) [Sivakumar99] A subset of nodes in the network is identified as the core Each node in the network must be adjacent to at least one node in the core Each core node determines paths to nearby core nodes by means of a localized broadcast
82 CGSR
83 CEDAR A G H B C E D F S J K A core node Node E is the dominator for nodes D, F and K
84 Proactive Routing Protocols
85 Destination Sequenced Distance Vector (DSDV) [Perkins94Sigcomm] Each node maintains a routing table which stores next hop, cost metric towards each destination a sequence number that is created by the destination itself Each node periodically forwards routing table to neighbors Each node increments and appends its sequence number when sending its local routing table Each route is tagged with a sequence number; routes with greater sequence numbers are preferred Each node advertises a monotonically increasing even sequence number for itself When a node decides that a route is broken, it increments the sequence number of the route and advertises it with infinite metric Destination advertises new sequence number
86 Destination Sequenced Distance Vector (DSDV) When X receives information from Y about a route to Z Let destination sequence number for Z at X be S(X), S(Y) is sent from Y X Y Z If S(X) > S(Y), then X ignores the routing information received from Y If S(X) = S(Y), and cost of going through Y is smaller than the route known to X, then X sets Y as the next hop to Z If S(X) < S(Y), then X sets Y as the next hop to Z, and S(X) is updated to equal S(Y)
87 Optimized Link State Routing (OLSR) [Jacquet00ietf] Nodes C and E are multipoint relays of node A Multipoint relays of A are its neighbors such that each two hop neighbor of A is a one hop neighbor of one multipoint relay of A Nodes exchange neighbor lists to know their 2 hop neighbors and choose the multipoint relays B F J G C A D E H K Node that has broadcast state information from A
88 Optimized Link State Routing (OLSR) Nodes C and E forward information received from A Nodes E and K are multipoint relays for node H Node K forwards information received from H B F J G C A D E H K Node that has broadcast state information from A
89 Hybrid Routing Protocols
90 Zone Routing Protocol (ZRP) [Haas98] ZRP combines proactive and reactive approaches All nodes within hop distance at most d from a node X are said to be in the routing zone of node X All nodes at hop distance exactly d are said to be peripheral nodes of node X s routing zone Intra zone routing: Proactively maintain routes to all nodes within the source node s own zone. Inter zone routing: Use an on demand protocol (similar to DSR or AODV) to determine routes to outside zone.
91 Zone Routing Protocol (ZRP) Radius of routing zone = 2
92 Routing Summary Protocols Typically divided into proactive, reactive and hybrid Plenty of routing protocols. Discussion here is far from exhaustive Performance Studies Typically studied by simulations using ns, discrete event simulator Nodes (10 30) remains stationary for pause time seconds (0 900s) and then move to a random destination (1500m X300m space) at a uniform speed (0 20m/s). CBR traffic sources (4 30 packets/sec, bytes/packet) Attempt to estimate latency of route discovery, routing overhead Actual trade off depends a lot on traffic and mobility patterns Higher traffic diversity (more source destination pairs) increases overhead in on demand protocols Higher mobility will always increase overhead in all protocols
93 Transport in MANET
94 User Datagram Protocol (UDP) Studies comparing different routing protocols for MANET typically measure UDP performance Several performance metrics are used routing overhead per data packet packet delivery delay throughput/loss Many variables affect performance Traffic characteristics Mobility characteristics Node capabilities Difficult to identify a single scheme that will perform well in all environments Several relevant studies [Broch98Mobicom, Das9ic3n, Johansson99Mobicom, Das00Infocom, Jacquet00Inria]
95 Transmission Control Protocol (TCP) Reliable ordered delivery Reliability achieved by means of retransmissions if necessary End to end semantics Receiver sends cumulative acknowledgements for in sequence packets Receiver sends duplicate acknowledgements for out of sequence packets Implements congestion avoidance and control using sliding window Window size is minimum of receiver s advertised window determined by available buffer space at the receiver congestion window determined by the sender, based on feedback from the network Congestion window size bounds the amount of data that can be sent per round trip time
96 Detection of packet loss in TCP Retransmission timeout (RTO) sender sets retransmission timer for only one packet if Ack not received before timer expiry, the packet is assumed lost RTO dynamically calculated, doubles on each timeout Duplicate acks sender assumes packet loss if it receives three consecutive duplicate acknowledgements (dupacks) On detecting a packet loss, TCP sender assumes that network congestion has occurred and drastically reduces the congestion window
97 TCP in MANET Several factors affect TCP performance in MANET: Wireless transmission errors may cause fast retransmit, which results in retransmission of lost packet reduction in congestion window reducing congestion window in response to errors is unnecessary Multi hop routes on shared wireless medium Longer connections are at a disadvantage compared to shorter connections, because they have to contend for wireless access at each hop Route failures due to mobility
98 Impact of Multi hop Wireless Paths TCP throughput degrades with increase in number of hops Packet transmission can occur on at most one hop among three consecutive hops Increasing the number of hops from 1 to 2, 3 results in increased delay, and decreased throughput Increasing number of hops beyond 3 allows simultaneous transmissions on more than one link, however, degradation continues due to contention between TCP Data and Acks traveling in opposite directions When number of hops is large enough (>6), throughput stabilizes [Holland99]
99 Impact of Node Mobility TCP throughput degrades with increase in mobility but not always mobility causes link breakage, resulting in route failure Route is repaired TCP sender times out. Starts sending packets again No throughput No throughput despite route repair TCP data and acks en route discarded Larger route repair delays are especially harmful
100 Improved Throughput with Increased Mobility C D C D C D B A B A B A Low speed: (Route from A to D is broken for ~1.5 seconds) When TCP sender times after 1 second, route still broken. TCP times out after another 2 seconds, and only then resumes High speed: (Route from A to D is broken for ~0.75 seconds) When TCP sender times out after 1 second, route is repaired TCP timeout interval somewhat (not entirely) independent of speed Network state at higher speed may sometimes be more favorable than lower speed
101 Impact of Route Caching TCP performance typically degrades when caches are used for route repair When a route is broken, route discovery returns a cached route from local cache or from a nearby node After a time out, TCP sender transmits a packet on the new route. However, typically the cached route has also broken after it was cached timeout due to route failure timeout, cached route is broken timeout, second cached route also broken Another route discovery, and TCP time out interval Process repeats until a good route is found
102 Caching and TCP performance Caching can result in faster route repair Faster does not necessarily mean correct If incorrect repairs occur often enough, caching performs poorly If cache accuracy is not high enough, gains in routing overhead may be offset by loss of TCP performance due to multiple time outs Need mechanisms for determining when cached routes are stale
103 Impact of Acknowledgements TCP Acks (and link layer acks) share the wireless bandwidth with TCP data packets Data and Acks travel in opposite directions In addition to bandwidth usage, acks require additional receive send turnarounds, which also incur time penalty Reduction of contention between data and acks, and frequency of send receive turnaround Mitigation [Balakrishnan97] Piggybacking link layer acks with data Sending fewer TCP acks ack every d th packet (d may be chosen dynamically) Ack filtering Gateway may drop an older ack in the queue, if a new ack arrives
104 TCP Parameters after Route Repair Window Size after route repair Same as before route break: may be too optimistic Same as startup: may be too conservative Better be conservative than overly optimistic Reset window to small value; let TCP learn the window size Retransmission Timeout (RTO) after route repair Same as before route break: may be too small for long routes Same as TCP start up: may be too large and respond slowly to packet loss new RTO could be made a function of old RTO and route lengths
105 Improving TCP Throughput Network feedback Network knows best (why packets are lost) Need to modify transport & network layer to receive/send feedback Need mechanisms for information exchange between layers Inform TCP of route failure by explicit message Let TCP know when route is repaired Probing Explicit notification Better route caching mechanisms Reduces repeated TCP timeouts and backoff
106 In Conclusion Issues other than routing have received much less attention Other interesting problems: Applications for MANET Address assignment QoS issues Improving interaction between protocol layers
UCS-805 MOBILE COMPUTING Jan-May,2011 TOPIC 8. ALAK ROY. Assistant Professor Dept. of CSE NIT Agartala.
 Mobile Ad Hoc Networks: Routing TOPIC 8 UCS-805 MOBILE COMPUTING Jan-May,2011 ALAK ROY. Assistant Professor Dept. of CSE NIT Agartala Email-alakroy.nerist@gmail.com Mobile Ad Hoc Networks (MANET) Introduction
Mobile Ad Hoc Networks: Routing TOPIC 8 UCS-805 MOBILE COMPUTING Jan-May,2011 ALAK ROY. Assistant Professor Dept. of CSE NIT Agartala Email-alakroy.nerist@gmail.com Mobile Ad Hoc Networks (MANET) Introduction
ECS-087: Mobile Computing
 ECS-087: Mobile Computing Mobile Adhoc Networks and Routing in MANETS (most of the slides borrowed from Prof. Sridhar Iyer) Diwakar Yagyasen 1 Index Mobile Ad Hoc Networks (MANET) MAC in MANET MANET routing
ECS-087: Mobile Computing Mobile Adhoc Networks and Routing in MANETS (most of the slides borrowed from Prof. Sridhar Iyer) Diwakar Yagyasen 1 Index Mobile Ad Hoc Networks (MANET) MAC in MANET MANET routing
Wireless Networking & Mobile Computing
 Wireless Networking & Mobile Computing CS 752/852 - Spring 2012 Network Layer: Ad Hoc Routing Tamer Nadeem Dept. of Computer Science The OSI Communication Model Page 2 Spring 2012 CS 752/852 - Wireless
Wireless Networking & Mobile Computing CS 752/852 - Spring 2012 Network Layer: Ad Hoc Routing Tamer Nadeem Dept. of Computer Science The OSI Communication Model Page 2 Spring 2012 CS 752/852 - Wireless
Mobile Ad Hoc Networks: Routing, MAC and Transport Issues
 Mobile Ad Hoc Networks: Routing, MAC and Transport Issues Nitin H. Vaidya University of Illinois at Urbana-Champaign nhv@uiuc.edu http://www.crhc.uiuc.edu/~nhv 2004 Nitin Vaidya 1 Notes Names in brackets,
Mobile Ad Hoc Networks: Routing, MAC and Transport Issues Nitin H. Vaidya University of Illinois at Urbana-Champaign nhv@uiuc.edu http://www.crhc.uiuc.edu/~nhv 2004 Nitin Vaidya 1 Notes Names in brackets,
Mobile Ad-Hoc Networks & Routing Algorithms
 Mobile Ad-Hoc Networks & Routing Algorithms EMMANOUIL G. SPANAKIS, PhD. spanakis@csd.uoc.gr COLLABORATING RESEARCHER, COMPUTATIONAL BIOMEDICINE LABORATORY, FORTH-ICS VISITING LECTURER, COMPUTER SCIENCE
Mobile Ad-Hoc Networks & Routing Algorithms EMMANOUIL G. SPANAKIS, PhD. spanakis@csd.uoc.gr COLLABORATING RESEARCHER, COMPUTATIONAL BIOMEDICINE LABORATORY, FORTH-ICS VISITING LECTURER, COMPUTER SCIENCE
Politecnico di Milano Facoltà di Ingegneria dell Informazione. WI-7 Ad hoc networks. Wireless Internet Prof. Antonio Capone
 Politecnico di Milano Facoltà di Ingegneria dell Informazione WI-7 Ad hoc networks Wireless Internet Prof. Antonio Capone Acknowlegments o This class notes are mostly based on the teaching material of:
Politecnico di Milano Facoltà di Ingegneria dell Informazione WI-7 Ad hoc networks Wireless Internet Prof. Antonio Capone Acknowlegments o This class notes are mostly based on the teaching material of:
CMPE 257: Wireless and Mobile Networking
 CMPE 257: Wireless and Mobile Networking Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 5 CMPE 257 Winter'11 1 Announcements Project proposals. Student presentations. 10 students so
CMPE 257: Wireless and Mobile Networking Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 5 CMPE 257 Winter'11 1 Announcements Project proposals. Student presentations. 10 students so
CMPE 257: Wireless and Mobile Networking
 CMPE 257: Wireless and Mobile Networking Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 6 CMPE 257 Winter'11 1 Announcements Project proposals. Student presentations. 10 students so
CMPE 257: Wireless and Mobile Networking Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 6 CMPE 257 Winter'11 1 Announcements Project proposals. Student presentations. 10 students so
LECTURE 9. Ad hoc Networks and Routing
 1 LECTURE 9 Ad hoc Networks and Routing Ad hoc Networks 2 Ad Hoc Networks consist of peer to peer communicating nodes (possibly mobile) no infrastructure. Topology of the network changes dynamically links
1 LECTURE 9 Ad hoc Networks and Routing Ad hoc Networks 2 Ad Hoc Networks consist of peer to peer communicating nodes (possibly mobile) no infrastructure. Topology of the network changes dynamically links
Routing in Ad Hoc Wireless Networks PROF. MICHAEL TSAI / DR. KATE LIN 2014/05/14
 Routing in Ad Hoc Wireless Networks PROF. MICHAEL TSAI / DR. KATE LIN 2014/05/14 Routing Algorithms Link- State algorithm Each node maintains a view of the whole network topology Find the shortest path
Routing in Ad Hoc Wireless Networks PROF. MICHAEL TSAI / DR. KATE LIN 2014/05/14 Routing Algorithms Link- State algorithm Each node maintains a view of the whole network topology Find the shortest path
Content. 1. Introduction. 2. The Ad-hoc On-Demand Distance Vector Algorithm. 3. Simulation and Results. 4. Future Work. 5.
 Rahem Abri Content 1. Introduction 2. The Ad-hoc On-Demand Distance Vector Algorithm Path Discovery Reverse Path Setup Forward Path Setup Route Table Management Path Management Local Connectivity Management
Rahem Abri Content 1. Introduction 2. The Ad-hoc On-Demand Distance Vector Algorithm Path Discovery Reverse Path Setup Forward Path Setup Route Table Management Path Management Local Connectivity Management
Mobile & Wireless Networking. Lecture 10: Mobile Transport Layer & Ad Hoc Networks. [Schiller, Section 8.3 & Section 9] [Reader, Part 8]
![Mobile & Wireless Networking. Lecture 10: Mobile Transport Layer & Ad Hoc Networks. [Schiller, Section 8.3 & Section 9] [Reader, Part 8] Mobile & Wireless Networking. Lecture 10: Mobile Transport Layer & Ad Hoc Networks. [Schiller, Section 8.3 & Section 9] [Reader, Part 8]](/thumbs/92/110300020.jpg) 192620010 Mobile & Wireless Networking Lecture 10: Mobile Transport Layer & Ad Hoc Networks [Schiller, Section 8.3 & Section 9] [Reader, Part 8] Geert Heijenk Outline of Lecture 10 Mobile transport layer
192620010 Mobile & Wireless Networking Lecture 10: Mobile Transport Layer & Ad Hoc Networks [Schiller, Section 8.3 & Section 9] [Reader, Part 8] Geert Heijenk Outline of Lecture 10 Mobile transport layer
Part I. Wireless Communication
 1 Part I. Wireless Communication 1.5 Topologies of cellular and ad-hoc networks 2 Introduction Cellular telephony has forever changed the way people communicate with one another. Cellular networks enable
1 Part I. Wireless Communication 1.5 Topologies of cellular and ad-hoc networks 2 Introduction Cellular telephony has forever changed the way people communicate with one another. Cellular networks enable
MANET TECHNOLOGY. Keywords: MANET, Wireless Nodes, Ad-Hoc Network, Mobile Nodes, Routes Protocols.
 MANET TECHNOLOGY Dharna 1, Varsha Saroha 2, R. B. Dubey 3 1,2,3 Department of Electronics and Communication Engineering, Hindu College of Engineering, Sonepat, Haryana,(India) ABSTRACT Wireless technology
MANET TECHNOLOGY Dharna 1, Varsha Saroha 2, R. B. Dubey 3 1,2,3 Department of Electronics and Communication Engineering, Hindu College of Engineering, Sonepat, Haryana,(India) ABSTRACT Wireless technology
ECS-087: Mobile Computing
 ECS-087: Mobile Computing TCP over wireless TCP and mobility Most of the Slides borrowed from Prof. Sridhar Iyer s lecture IIT Bombay Diwakar Yagyasen 1 Effect of Mobility on Protocol Stack Application:
ECS-087: Mobile Computing TCP over wireless TCP and mobility Most of the Slides borrowed from Prof. Sridhar Iyer s lecture IIT Bombay Diwakar Yagyasen 1 Effect of Mobility on Protocol Stack Application:
Outline. CS5984 Mobile Computing. Taxonomy of Routing Protocols AODV 1/2. Dr. Ayman Abdel-Hamid. Routing Protocols in MANETs Part I
 CS5984 Mobile Computing Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Part I Outline Routing Protocols for Ad hoc Networks Example of a reactive routing protocol AODV: Ad hoc On-demand
CS5984 Mobile Computing Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Part I Outline Routing Protocols for Ad hoc Networks Example of a reactive routing protocol AODV: Ad hoc On-demand
3. Evaluation of Selected Tree and Mesh based Routing Protocols
 33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
Chapter 7. Wireless Ad Hoc Networks. 7: Wireless Ad Hoc Networks 7-1
 Chapter 7 Wireless Ad Hoc Networks 7: Wireless Ad Hoc Networks 7-1 What is an Ad Hoc Network? Definitions: An ad-hoc network is one that comes together as needed, not necessarily with any assistance from
Chapter 7 Wireless Ad Hoc Networks 7: Wireless Ad Hoc Networks 7-1 What is an Ad Hoc Network? Definitions: An ad-hoc network is one that comes together as needed, not necessarily with any assistance from
Redes Inalámbricas Tema 4. Mobile Ad Hoc Networks
 Redes Inalámbricas Tema 4. Mobile Ad Hoc Networks A. Specific properties B. Flooding as a basic mechanism C. Basic routing protocols DSR AODV y DYMO OLSR y OLSRv2 D. Advanced protocols and techniques Acknowledgments
Redes Inalámbricas Tema 4. Mobile Ad Hoc Networks A. Specific properties B. Flooding as a basic mechanism C. Basic routing protocols DSR AODV y DYMO OLSR y OLSRv2 D. Advanced protocols and techniques Acknowledgments
CSE 461: Wireless Networks
 CSE 461: Wireless Networks Wireless IEEE 802.11 A physical and multiple access layer standard for wireless local area networks (WLAN) Ad Hoc Network: no servers or access points Infrastructure Network
CSE 461: Wireless Networks Wireless IEEE 802.11 A physical and multiple access layer standard for wireless local area networks (WLAN) Ad Hoc Network: no servers or access points Infrastructure Network
Wireless Mul*hop Ad Hoc Networks
 Wireless Mul*hop Guevara Noubir noubir@ccs.neu.edu Some slides are from Nitin Vaidya s tutorial. Infrastructure vs. Ad Hoc Wireless Networks Infrastructure networks: One or several Access- Points (AP)
Wireless Mul*hop Guevara Noubir noubir@ccs.neu.edu Some slides are from Nitin Vaidya s tutorial. Infrastructure vs. Ad Hoc Wireless Networks Infrastructure networks: One or several Access- Points (AP)
CIS 632 / EEC 687 Mobile Computing
 CIS 632 / EEC 687 Mobile Computing TCP in Mobile Networks Prof. Chansu Yu Contents Physical layer issues Communication frequency Signal propagation Modulation and Demodulation Channel access issues Multiple
CIS 632 / EEC 687 Mobile Computing TCP in Mobile Networks Prof. Chansu Yu Contents Physical layer issues Communication frequency Signal propagation Modulation and Demodulation Channel access issues Multiple
IEEE , Token Rings. 10/11/06 CS/ECE UIUC, Fall
 IEEE 802.11, Token Rings 10/11/06 CS/ECE 438 - UIUC, Fall 2006 1 Medium Access Control Wireless channel is a shared medium Need access control mechanism to avoid interference Why not CSMA/CD? 10/11/06
IEEE 802.11, Token Rings 10/11/06 CS/ECE 438 - UIUC, Fall 2006 1 Medium Access Control Wireless channel is a shared medium Need access control mechanism to avoid interference Why not CSMA/CD? 10/11/06
Page 1. EEC173B/ECS152C, Winter Link State Routing [Huitema95] Optimized Link State Routing (OLSR) MANET Unicast Routing. Proactive Protocols
![Page 1. EEC173B/ECS152C, Winter Link State Routing [Huitema95] Optimized Link State Routing (OLSR) MANET Unicast Routing. Proactive Protocols Page 1. EEC173B/ECS152C, Winter Link State Routing [Huitema95] Optimized Link State Routing (OLSR) MANET Unicast Routing. Proactive Protocols](/thumbs/92/108171170.jpg) 173/S152, Winter 2006 Proactive Protocols MNT Unicast Routing Proactive Protocols OLSR SV Hybrid Protocols Most of the schemes discussed so far are reactive Proactive schemes based on distance vector and
173/S152, Winter 2006 Proactive Protocols MNT Unicast Routing Proactive Protocols OLSR SV Hybrid Protocols Most of the schemes discussed so far are reactive Proactive schemes based on distance vector and
Ad Hoc Networks: Introduction
 Ad Hoc Networks: Introduction Module A.int.1 Dr.M.Y.Wu@CSE Shanghai Jiaotong University Shanghai, China Dr.W.Shu@ECE University of New Mexico Albuquerque, NM, USA 1 Ad Hoc networks: introduction A.int.1-2
Ad Hoc Networks: Introduction Module A.int.1 Dr.M.Y.Wu@CSE Shanghai Jiaotong University Shanghai, China Dr.W.Shu@ECE University of New Mexico Albuquerque, NM, USA 1 Ad Hoc networks: introduction A.int.1-2
Overview (Advantages and Routing Protocols) of MANET
 Advances in Computational Sciences and Technology ISSN 0973-6107 Volume 10, Number 5 (2017) pp. 855-861 Research India Publications http://www.ripublication.com Overview (Advantages and Routing Protocols)
Advances in Computational Sciences and Technology ISSN 0973-6107 Volume 10, Number 5 (2017) pp. 855-861 Research India Publications http://www.ripublication.com Overview (Advantages and Routing Protocols)
Unicast Routing in Mobile Ad Hoc Networks. Dr. Ashikur Rahman CSE 6811: Wireless Ad hoc Networks
 Unicast Routing in Mobile Ad Hoc Networks 1 Routing problem 2 Responsibility of a routing protocol Determining an optimal way to find optimal routes Determining a feasible path to a destination based on
Unicast Routing in Mobile Ad Hoc Networks 1 Routing problem 2 Responsibility of a routing protocol Determining an optimal way to find optimal routes Determining a feasible path to a destination based on
CS5984 Mobile Computing
 CS5984 Mobile Computing Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Part II 1 Outline Routing Protocols for Ad hoc Networks DSDV: Highly Dynamic Destination-Sequenced Distance- Vector
CS5984 Mobile Computing Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Part II 1 Outline Routing Protocols for Ad hoc Networks DSDV: Highly Dynamic Destination-Sequenced Distance- Vector
Ad Hoc Networks: Issues and Routing
 Ad Hoc Networks: Issues and Routing Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse574-08/
Ad Hoc Networks: Issues and Routing Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse574-08/
Wireless Mesh Networks
 Wireless Mesh Networks COS 463: Wireless Networks Lecture 6 Kyle Jamieson [Parts adapted from I. F. Akyildiz, B. Karp] Wireless Mesh Networks Describes wireless networks in which each node can communicate
Wireless Mesh Networks COS 463: Wireless Networks Lecture 6 Kyle Jamieson [Parts adapted from I. F. Akyildiz, B. Karp] Wireless Mesh Networks Describes wireless networks in which each node can communicate
AODV-PA: AODV with Path Accumulation
 -PA: with Path Accumulation Sumit Gwalani Elizabeth M. Belding-Royer Department of Computer Science University of California, Santa Barbara fsumitg, ebeldingg@cs.ucsb.edu Charles E. Perkins Communications
-PA: with Path Accumulation Sumit Gwalani Elizabeth M. Belding-Royer Department of Computer Science University of California, Santa Barbara fsumitg, ebeldingg@cs.ucsb.edu Charles E. Perkins Communications
AD HOC NETWORKS. RAJINI M 2 ND SEM M.Tech DECS PESIT
 AD HOC NETWORKS RAJINI M 2 ND SEM M.Tech DECS PESIT OUTLINE Introduction Features of Ad hoc network Types of ad hoc network MANETs Network architecture MAC protocols Routing protocols Denial of service
AD HOC NETWORKS RAJINI M 2 ND SEM M.Tech DECS PESIT OUTLINE Introduction Features of Ad hoc network Types of ad hoc network MANETs Network architecture MAC protocols Routing protocols Denial of service
Lecture 16: QoS and "
 Lecture 16: QoS and 802.11" CSE 123: Computer Networks Alex C. Snoeren HW 4 due now! Lecture 16 Overview" Network-wide QoS IntServ DifServ 802.11 Wireless CSMA/CA Hidden Terminals RTS/CTS CSE 123 Lecture
Lecture 16: QoS and 802.11" CSE 123: Computer Networks Alex C. Snoeren HW 4 due now! Lecture 16 Overview" Network-wide QoS IntServ DifServ 802.11 Wireless CSMA/CA Hidden Terminals RTS/CTS CSE 123 Lecture
A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols. Broch et al Presented by Brian Card
 A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols Broch et al Presented by Brian Card 1 Outline Introduction NS enhancements Protocols: DSDV TORA DRS AODV Evaluation Conclusions
A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols Broch et al Presented by Brian Card 1 Outline Introduction NS enhancements Protocols: DSDV TORA DRS AODV Evaluation Conclusions
Performance Evaluation of Route Failure Detection in Mobile Ad Hoc Networks
 Performance Evaluation of Route Failure Detection in Mobile Ad Hoc Networks Dimitri Marandin 4. Würzburger Workshop "IP Netzmanagement, IP Netzplanung und Optimierung" 27.-28. July 2004 www.ifn.et.tu-dresden.de/tk/
Performance Evaluation of Route Failure Detection in Mobile Ad Hoc Networks Dimitri Marandin 4. Würzburger Workshop "IP Netzmanagement, IP Netzplanung und Optimierung" 27.-28. July 2004 www.ifn.et.tu-dresden.de/tk/
Routing Protocols in MANETs
 Chapter 4 Routing Protocols in MANETs 4.1 Introduction The main aim of any Ad Hoc network routing protocol is to meet the challenges of the dynamically changing topology and establish a correct and an
Chapter 4 Routing Protocols in MANETs 4.1 Introduction The main aim of any Ad Hoc network routing protocol is to meet the challenges of the dynamically changing topology and establish a correct and an
Medium Access Control. IEEE , Token Rings. CSMA/CD in WLANs? Ethernet MAC Algorithm. MACA Solution for Hidden Terminal Problem
 Medium Access Control IEEE 802.11, Token Rings Wireless channel is a shared medium Need access control mechanism to avoid interference Why not CSMA/CD? 9/15/06 CS/ECE 438 - UIUC, Fall 2006 1 9/15/06 CS/ECE
Medium Access Control IEEE 802.11, Token Rings Wireless channel is a shared medium Need access control mechanism to avoid interference Why not CSMA/CD? 9/15/06 CS/ECE 438 - UIUC, Fall 2006 1 9/15/06 CS/ECE
Mohamed Khedr.
 Mohamed Khedr http://webmail.aast.edu/~khedr Tentatively Week 1 Week 2 Week 3 Week 4 Week 5 Week 6 Week 7 Week 8 Week 9 Week 10 Week 11 Week 12 Week 13 Week 14 Week 15 Overview Packet Switching IP addressing
Mohamed Khedr http://webmail.aast.edu/~khedr Tentatively Week 1 Week 2 Week 3 Week 4 Week 5 Week 6 Week 7 Week 8 Week 9 Week 10 Week 11 Week 12 Week 13 Week 14 Week 15 Overview Packet Switching IP addressing
A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols
 A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols By Josh Broch, David A. Maltz, David B. Johnson, Yih- Chun Hu, Jorjeta Jetcheva Presentation by: Michael Molignano Jacob
A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols By Josh Broch, David A. Maltz, David B. Johnson, Yih- Chun Hu, Jorjeta Jetcheva Presentation by: Michael Molignano Jacob
PERFORMANCE ANALYSIS OF AODV ROUTING PROTOCOL IN MANETS
 PERFORMANCE ANALYSIS OF AODV ROUTING PROTOCOL IN MANETS AMANDEEP University College of Engineering, Punjabi University Patiala, Punjab, India amandeep8848@gmail.com GURMEET KAUR University College of Engineering,
PERFORMANCE ANALYSIS OF AODV ROUTING PROTOCOL IN MANETS AMANDEEP University College of Engineering, Punjabi University Patiala, Punjab, India amandeep8848@gmail.com GURMEET KAUR University College of Engineering,
White Paper. Mobile Ad hoc Networking (MANET) with AODV. Revision 1.0
 White Paper Mobile Ad hoc Networking (MANET) with AODV Revision 1.0 This page is intentionally blank, or rather nearly blank. Table of Contents TABLE OF CONTENTS...3 TABLE OF FIGURES...4 WHAT IS MANET?...5
White Paper Mobile Ad hoc Networking (MANET) with AODV Revision 1.0 This page is intentionally blank, or rather nearly blank. Table of Contents TABLE OF CONTENTS...3 TABLE OF FIGURES...4 WHAT IS MANET?...5
2013, IJARCSSE All Rights Reserved Page 85
 Volume 3, Issue 12, December 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Overview of
Volume 3, Issue 12, December 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Overview of
15-441: Computer Networking. Wireless Networking
 15-441: Computer Networking Wireless Networking Outline Wireless Challenges 802.11 Overview Link Layer Ad-hoc Networks 2 Assumptions made in Internet Host are (mostly) stationary Address assignment, routing
15-441: Computer Networking Wireless Networking Outline Wireless Challenges 802.11 Overview Link Layer Ad-hoc Networks 2 Assumptions made in Internet Host are (mostly) stationary Address assignment, routing
CMPE 257: Wireless and Mobile Networking
 CMPE 257: Wireless and Mobile Networking Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 10 CMPE 257 Spring'15 1 Student Presentations Schedule May 21: Sam and Anuj May 26: Larissa
CMPE 257: Wireless and Mobile Networking Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 10 CMPE 257 Spring'15 1 Student Presentations Schedule May 21: Sam and Anuj May 26: Larissa
A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET
 ISSN: 2278 1323 All Rights Reserved 2016 IJARCET 296 A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET Dr. R. Shanmugavadivu 1, B. Chitra 2 1 Assistant Professor, Department of Computer
ISSN: 2278 1323 All Rights Reserved 2016 IJARCET 296 A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET Dr. R. Shanmugavadivu 1, B. Chitra 2 1 Assistant Professor, Department of Computer
Kapitel 5: Mobile Ad Hoc Networks. Characteristics. Applications of Ad Hoc Networks. Wireless Communication. Wireless communication networks types
 Kapitel 5: Mobile Ad Hoc Networks Mobilkommunikation 2 WS 08/09 Wireless Communication Wireless communication networks types Infrastructure-based networks Infrastructureless networks Ad hoc networks Prof.
Kapitel 5: Mobile Ad Hoc Networks Mobilkommunikation 2 WS 08/09 Wireless Communication Wireless communication networks types Infrastructure-based networks Infrastructureless networks Ad hoc networks Prof.
Performance Comparison of Ad Hoc Routing Protocols over IEEE DCF and TDMA MAC Layer Protocols
 Performance Comparison of Ad Hoc Routing Protocols over IEEE 82.11 DCF and TDMA MAC Layer Protocols Govind. P. Gupta Computer Science Department R.K.G.I.T, Ghaziabad (India) er_gpgupta@yahoo.com A. K.
Performance Comparison of Ad Hoc Routing Protocols over IEEE 82.11 DCF and TDMA MAC Layer Protocols Govind. P. Gupta Computer Science Department R.K.G.I.T, Ghaziabad (India) er_gpgupta@yahoo.com A. K.
Performance Evaluation of MANET through NS2 Simulation
 International Journal of Electronic and Electrical Engineering. ISSN 0974-2174, Volume 7, Number 1 (2014), pp. 25-30 International Research Publication House http://www.irphouse.com Performance Evaluation
International Journal of Electronic and Electrical Engineering. ISSN 0974-2174, Volume 7, Number 1 (2014), pp. 25-30 International Research Publication House http://www.irphouse.com Performance Evaluation
CMPE 257: Wireless and Mobile Networking
 CMPE 257: Wireless and Mobile Networking Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 3 CMPE 257 Winter'11 1 Announcements Accessing secure part of the class Web page: User id: cmpe257.
CMPE 257: Wireless and Mobile Networking Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 3 CMPE 257 Winter'11 1 Announcements Accessing secure part of the class Web page: User id: cmpe257.
CHAPTER 2 LITERATURE REVIEW
 39 CHAPTER 2 LITERATURE REVIEW This chapter gives a brief summary of the MANET routing protocol types and their details. 2.1 ROUTING IN AD-HOC NETWORKS Routing is the act of moving information from source
39 CHAPTER 2 LITERATURE REVIEW This chapter gives a brief summary of the MANET routing protocol types and their details. 2.1 ROUTING IN AD-HOC NETWORKS Routing is the act of moving information from source
Analysis of Black-Hole Attack in MANET using AODV Routing Protocol
 Analysis of Black-Hole Attack in MANET using Routing Protocol Ms Neha Choudhary Electronics and Communication Truba College of Engineering, Indore India Dr Sudhir Agrawal Electronics and Communication
Analysis of Black-Hole Attack in MANET using Routing Protocol Ms Neha Choudhary Electronics and Communication Truba College of Engineering, Indore India Dr Sudhir Agrawal Electronics and Communication
Mobile Communications. Ad-hoc and Mesh Networks
 Ad-hoc+mesh-net 1 Mobile Communications Ad-hoc and Mesh Networks Manuel P. Ricardo Faculdade de Engenharia da Universidade do Porto Ad-hoc+mesh-net 2 What is an ad-hoc network? What are differences between
Ad-hoc+mesh-net 1 Mobile Communications Ad-hoc and Mesh Networks Manuel P. Ricardo Faculdade de Engenharia da Universidade do Porto Ad-hoc+mesh-net 2 What is an ad-hoc network? What are differences between
Wireless Local Area Network (IEEE )
 Wireless Local Area Network (IEEE 802.11) -IEEE 802.11 Specifies a single Medium Access Control (MAC) sublayer and 3 Physical Layer Specifications. Stations can operate in two configurations : Ad-hoc mode
Wireless Local Area Network (IEEE 802.11) -IEEE 802.11 Specifies a single Medium Access Control (MAC) sublayer and 3 Physical Layer Specifications. Stations can operate in two configurations : Ad-hoc mode
Wireless Challenges : Computer Networking. Overview. Routing to Mobile Nodes. Lecture 25: Wireless Networking
 Wireless Challenges 15-441: Computer Networking Lecture 25: Wireless Networking Force us to rethink many assumptions Need to share airwaves rather than wire Don t know what hosts are involved Host may
Wireless Challenges 15-441: Computer Networking Lecture 25: Wireless Networking Force us to rethink many assumptions Need to share airwaves rather than wire Don t know what hosts are involved Host may
Computer Communication III
 Computer Communication III Wireless Media Access IEEE 802.11 Wireless LAN Advantages of Wireless LANs Using the license free ISM band at 2.4 GHz no complicated or expensive licenses necessary very cost
Computer Communication III Wireless Media Access IEEE 802.11 Wireless LAN Advantages of Wireless LANs Using the license free ISM band at 2.4 GHz no complicated or expensive licenses necessary very cost
Lecture 4: Mobile Ad Hoc and Sensor Networks (I)
 Lecture 4: Mobile Ad Hoc and Sensor Networks (I) Ing-Ray Chen CS 6204 Mobile Computing Virginia Tech Courtesy of G.G. Richard III for providing some of the slides Mobile Ad Hoc Networks May need to traverse
Lecture 4: Mobile Ad Hoc and Sensor Networks (I) Ing-Ray Chen CS 6204 Mobile Computing Virginia Tech Courtesy of G.G. Richard III for providing some of the slides Mobile Ad Hoc Networks May need to traverse
ICE 1332/0715 Mobile Computing (Summer, 2008)
 ICE 1332/0715 Mobile Computing (Summer, 2008) Medium Access Control Prof. Chansu Yu http://academic.csuohio.edu/yuc/ Simplified Reference Model Application layer Transport layer Network layer Data link
ICE 1332/0715 Mobile Computing (Summer, 2008) Medium Access Control Prof. Chansu Yu http://academic.csuohio.edu/yuc/ Simplified Reference Model Application layer Transport layer Network layer Data link
Medium Access Control (MAC) Protocols for Ad hoc Wireless Networks -IV
 Medium Access Control (MAC) Protocols for Ad hoc Wireless Networks -IV CS: 647 Advanced Topics in Wireless Networks Drs. Baruch Awerbuch & Amitabh Mishra Department of Computer Science Johns Hopkins University
Medium Access Control (MAC) Protocols for Ad hoc Wireless Networks -IV CS: 647 Advanced Topics in Wireless Networks Drs. Baruch Awerbuch & Amitabh Mishra Department of Computer Science Johns Hopkins University
A Literature survey on Improving AODV protocol through cross layer design in MANET
 A Literature survey on Improving AODV protocol through cross layer design in MANET Nidhishkumar P. Modi 1, Krunal J. Panchal 2 1 Department of Computer Engineering, LJIET, Gujarat, India 2 Asst.Professor,
A Literature survey on Improving AODV protocol through cross layer design in MANET Nidhishkumar P. Modi 1, Krunal J. Panchal 2 1 Department of Computer Engineering, LJIET, Gujarat, India 2 Asst.Professor,
Location Awareness in Ad Hoc Wireless Mobile Neworks
 Location Awareness in Ad Hoc Wireless Mobile Neworks Lijuan Ai Wenyu Wang Yi Zhou 11/14/2001 Mobile Computing, Fall 2001 1 PART I INTRODUCTION TO MANET & LOCATION-AWARE COMPONENTS 11/14/2001 Mobile Computing,
Location Awareness in Ad Hoc Wireless Mobile Neworks Lijuan Ai Wenyu Wang Yi Zhou 11/14/2001 Mobile Computing, Fall 2001 1 PART I INTRODUCTION TO MANET & LOCATION-AWARE COMPONENTS 11/14/2001 Mobile Computing,
Media Access Control in Ad Hoc Networks
 Media Access Control in Ad Hoc Networks The Wireless Medium is a scarce precious resource. Furthermore, the access medium is broadcast in nature. It is necessary to share this resource efficiently and
Media Access Control in Ad Hoc Networks The Wireless Medium is a scarce precious resource. Furthermore, the access medium is broadcast in nature. It is necessary to share this resource efficiently and
ICE 1332/0715 Mobile Computing (Summer, 2008)
 ICE 1332/0715 Mobile Computing (Summer, 2008) TCP in Mobile Networks Prof. Chansu Yu http://academic.csuohio.edu/yuc/ c.yu91@csuohio.edu Contents Vinton Cerf and Robert Kahn s paper in 1973 introduces
ICE 1332/0715 Mobile Computing (Summer, 2008) TCP in Mobile Networks Prof. Chansu Yu http://academic.csuohio.edu/yuc/ c.yu91@csuohio.edu Contents Vinton Cerf and Robert Kahn s paper in 1973 introduces
Chapter-2 Routing Protocols of MANET
 Chapter-2 Routing Protocols of MANET Chapter 2 Routing Protocols of MANET Routing is an important function for any network, whether it is for wired or wireless. The protocols designed for routing in these
Chapter-2 Routing Protocols of MANET Chapter 2 Routing Protocols of MANET Routing is an important function for any network, whether it is for wired or wireless. The protocols designed for routing in these
Medium Access Control. MAC protocols: design goals, challenges, contention-based and contention-free protocols
 Medium Access Control MAC protocols: design goals, challenges, contention-based and contention-free protocols 1 Why do we need MAC protocols? Wireless medium is shared Many nodes may need to access the
Medium Access Control MAC protocols: design goals, challenges, contention-based and contention-free protocols 1 Why do we need MAC protocols? Wireless medium is shared Many nodes may need to access the
Arvind Krishnamurthy Fall 2003
 Ad-hoc Routing Arvind Krishnamurthy Fall 2003 Ad Hoc Routing Create multi-hop connectivity among set of wireless, possibly moving, nodes Mobile, wireless hosts act as forwarding nodes as well as end systems
Ad-hoc Routing Arvind Krishnamurthy Fall 2003 Ad Hoc Routing Create multi-hop connectivity among set of wireless, possibly moving, nodes Mobile, wireless hosts act as forwarding nodes as well as end systems
Performance Evaluation of Various Routing Protocols in MANET
 208 Performance Evaluation of Various Routing Protocols in MANET Jaya Jacob 1,V.Seethalakshmi 2 1 II MECS,Sri Shakthi Institute of Science and Technology, Coimbatore, India 2 Associate Professor-ECE, Sri
208 Performance Evaluation of Various Routing Protocols in MANET Jaya Jacob 1,V.Seethalakshmi 2 1 II MECS,Sri Shakthi Institute of Science and Technology, Coimbatore, India 2 Associate Professor-ECE, Sri
Data Communications. Data Link Layer Protocols Wireless LANs
 Data Communications Data Link Layer Protocols Wireless LANs Wireless Networks Several different types of communications networks are using unguided media. These networks are generally referred to as wireless
Data Communications Data Link Layer Protocols Wireless LANs Wireless Networks Several different types of communications networks are using unguided media. These networks are generally referred to as wireless
Chapter 7 Routing Protocols for Ad Hoc Wireless Networks. Jang-Ping Sheu
 Chapter 7 Routing Protocols for Ad Hoc Wireless Networks Jang-Ping Sheu Introduction Routing protocols used in wired networks cannot be directly applied to ad hoc wireless networks Highly dynamic topology
Chapter 7 Routing Protocols for Ad Hoc Wireless Networks Jang-Ping Sheu Introduction Routing protocols used in wired networks cannot be directly applied to ad hoc wireless networks Highly dynamic topology
Performance Evaluation of AODV and DSR routing protocols in MANET
 Performance Evaluation of AODV and DSR routing protocols in MANET Naresh Dobhal Diwakar Mourya ABSTRACT MANETs are wireless temporary adhoc networks that are being setup with no prior infrastructure and
Performance Evaluation of AODV and DSR routing protocols in MANET Naresh Dobhal Diwakar Mourya ABSTRACT MANETs are wireless temporary adhoc networks that are being setup with no prior infrastructure and
Simulation & Performance Analysis of Mobile Ad-Hoc Network Routing Protocol
 Simulation & Performance Analysis of Mobile Ad-Hoc Network Routing Protocol V.S.Chaudhari 1, Prof.P.N.Matte 2, Prof. V.P.Bhope 3 Department of E&TC, Raisoni College of Engineering, Ahmednagar Abstract:-
Simulation & Performance Analysis of Mobile Ad-Hoc Network Routing Protocol V.S.Chaudhari 1, Prof.P.N.Matte 2, Prof. V.P.Bhope 3 Department of E&TC, Raisoni College of Engineering, Ahmednagar Abstract:-
REVIEW ON ROUTING PROTOCOLS FOR MOBILE AD HOC NETWORKS
 REVIEW ON ROUTING PROTOCOLS FOR MOBILE AD HOC NETWORKS G. Poornima 1, Mr. M. Rajasenathipathi 2, 1 Research Scholar, Department of Computer Science, NGM College, Pollachi 2 Assistant Professor, Department
REVIEW ON ROUTING PROTOCOLS FOR MOBILE AD HOC NETWORKS G. Poornima 1, Mr. M. Rajasenathipathi 2, 1 Research Scholar, Department of Computer Science, NGM College, Pollachi 2 Assistant Professor, Department
A Routing Protocol for Utilizing Multiple Channels in Multi-Hop Wireless Networks with a Single Transceiver
 1 A Routing Protocol for Utilizing Multiple Channels in Multi-Hop Wireless Networks with a Single Transceiver Jungmin So Dept. of Computer Science, and Coordinated Science Laboratory University of Illinois
1 A Routing Protocol for Utilizing Multiple Channels in Multi-Hop Wireless Networks with a Single Transceiver Jungmin So Dept. of Computer Science, and Coordinated Science Laboratory University of Illinois
The MAC layer in wireless networks
 The MAC layer in wireless networks The wireless MAC layer roles Access control to shared channel(s) Natural broadcast of wireless transmission Collision of signal: a /space problem Who transmits when?
The MAC layer in wireless networks The wireless MAC layer roles Access control to shared channel(s) Natural broadcast of wireless transmission Collision of signal: a /space problem Who transmits when?
A Survey - Energy Efficient Routing Protocols in MANET
 , pp. 163-168 http://dx.doi.org/10.14257/ijfgcn.2016.9.5.16 A Survey - Energy Efficient Routing Protocols in MANET Jyoti Upadhyaya and Nitin Manjhi Department of Computer Science, RGPV University Shriram
, pp. 163-168 http://dx.doi.org/10.14257/ijfgcn.2016.9.5.16 A Survey - Energy Efficient Routing Protocols in MANET Jyoti Upadhyaya and Nitin Manjhi Department of Computer Science, RGPV University Shriram
ROUTE STABILITY MODEL FOR DSR IN WIRELESS ADHOC NETWORKS
 ROUTE STABILITY MODEL FOR DSR IN WIRELESS ADHOC NETWORKS Ganga S 1, Binu Chandran R 2 1, 2 Mohandas College Of Engineering And Technology Abstract: Wireless Ad-Hoc Network is a collection of wireless mobile
ROUTE STABILITY MODEL FOR DSR IN WIRELESS ADHOC NETWORKS Ganga S 1, Binu Chandran R 2 1, 2 Mohandas College Of Engineering And Technology Abstract: Wireless Ad-Hoc Network is a collection of wireless mobile
Ad Hoc Networks. Advanced Mobile Communication Networks. Integrated Communication Systems Group Ilmenau University of Technology
 Ad Hoc Networks Advanced Mobile Communication Networks Integrated Communication Systems Group Ilmenau University of Technology Outline Introduction Medium Access Control (MAC) in Multi-Channel Scenario
Ad Hoc Networks Advanced Mobile Communication Networks Integrated Communication Systems Group Ilmenau University of Technology Outline Introduction Medium Access Control (MAC) in Multi-Channel Scenario
Introduction to Mobile Ad hoc Networks (MANETs)
 Introduction to Mobile Ad hoc Networks (MANETs) 1 Overview of Ad hoc Network Communication between various devices makes it possible to provide unique and innovative services. Although this inter-device
Introduction to Mobile Ad hoc Networks (MANETs) 1 Overview of Ad hoc Network Communication between various devices makes it possible to provide unique and innovative services. Although this inter-device
Mobile and Sensor Systems. Lecture 3: Infrastructure, Ad-hoc and Delay Tolerant Mobile Networks Dr Cecilia Mascolo
 Mobile and Sensor Systems Lecture 3: Infrastructure, Ad-hoc and Delay Tolerant Mobile Networks Dr Cecilia Mascolo In this lecture In this lecture we will describe the difference in infrastructure and ad
Mobile and Sensor Systems Lecture 3: Infrastructure, Ad-hoc and Delay Tolerant Mobile Networks Dr Cecilia Mascolo In this lecture In this lecture we will describe the difference in infrastructure and ad
Intelligent Transportation Systems. Medium Access Control. Prof. Dr. Thomas Strang
 Intelligent Transportation Systems Medium Access Control Prof. Dr. Thomas Strang Recap: Wireless Interconnections Networking types + Scalability + Range Delay Individuality Broadcast o Scalability o Range
Intelligent Transportation Systems Medium Access Control Prof. Dr. Thomas Strang Recap: Wireless Interconnections Networking types + Scalability + Range Delay Individuality Broadcast o Scalability o Range
[Kamboj* et al., 5(9): September, 2016] ISSN: IC Value: 3.00 Impact Factor: 4.116
![[Kamboj* et al., 5(9): September, 2016] ISSN: IC Value: 3.00 Impact Factor: 4.116 [Kamboj* et al., 5(9): September, 2016] ISSN: IC Value: 3.00 Impact Factor: 4.116](/thumbs/92/109489555.jpg) IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY NOVEL REVIEW OF MANET ROUTING PROTOCOLS Nippun Kamboj*, Dr. Munishwar Rai Department of Computer Applications Maharishi Markandeshwar
IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY NOVEL REVIEW OF MANET ROUTING PROTOCOLS Nippun Kamboj*, Dr. Munishwar Rai Department of Computer Applications Maharishi Markandeshwar
Example of TORA operations. From last time, this was the DAG that was built. A was the source and X was the destination.
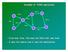 Example of TORA operations A Link 2 D Link 6 Y Link 1 Link 3 C Link 4 Link 8 B Link 5 E Link 7 X From last time, this was the DAG that was built. A was the source and X was the destination. Link 1 A B
Example of TORA operations A Link 2 D Link 6 Y Link 1 Link 3 C Link 4 Link 8 B Link 5 E Link 7 X From last time, this was the DAG that was built. A was the source and X was the destination. Link 1 A B
Routing Protocols in Mobile Ad-Hoc Network
 International Journal of Computer Science & Management Studies, Vol. 12, Issue 02, April 2012 Protocols in Mobile Ad-Hoc Network Sachin Minocha M. Tech Student, Vaish College of Engineering, Rohtak, Haryana
International Journal of Computer Science & Management Studies, Vol. 12, Issue 02, April 2012 Protocols in Mobile Ad-Hoc Network Sachin Minocha M. Tech Student, Vaish College of Engineering, Rohtak, Haryana
IEEE Medium Access Control. Medium Access Control
 IEEE 802.11 Medium Access Control EECS3214 3 April 2018 Medium Access Control reliable data delivery access control MAC layer covers three functional areas: security 2 1 MAC Requirements To avoid interference
IEEE 802.11 Medium Access Control EECS3214 3 April 2018 Medium Access Control reliable data delivery access control MAC layer covers three functional areas: security 2 1 MAC Requirements To avoid interference
SUMMARY OF ROUTING PROTOCOL MOBILE AD HOC NETWORKS. YI Jiazi. Polytechnic School of University of Nantes. Feb.
 SUMMARY OF ROUTING PROTOCOL IN MOBILE AD HOC NETWORKS YI Jiazi Polytechnic School of University of Nantes yi.jiazi@gmail.com Feb. 2007 CONTENTS ABSTRACT...2 1. INTRODUCTION...2 2. UNI-PATH ROUTING PROTOCOL...2
SUMMARY OF ROUTING PROTOCOL IN MOBILE AD HOC NETWORKS YI Jiazi Polytechnic School of University of Nantes yi.jiazi@gmail.com Feb. 2007 CONTENTS ABSTRACT...2 1. INTRODUCTION...2 2. UNI-PATH ROUTING PROTOCOL...2
6367(Print), ISSN (Online) Volume 4, Issue 2, March April (2013), IAEME & TECHNOLOGY (IJCET)
 INTERNATIONAL International Journal of Computer JOURNAL Engineering OF COMPUTER and Technology ENGINEERING (IJCET), ISSN 0976- & TECHNOLOGY (IJCET) ISSN 0976 6367(Print) ISSN 0976 6375(Online) Volume 4,
INTERNATIONAL International Journal of Computer JOURNAL Engineering OF COMPUTER and Technology ENGINEERING (IJCET), ISSN 0976- & TECHNOLOGY (IJCET) ISSN 0976 6367(Print) ISSN 0976 6375(Online) Volume 4,
Ad Hoc Routing Protocols and Issues
 Ad Hoc Routing Protocols and Issues Stefano Basagni ECE Dept Northeastern University Boston, Jan 2003 Ad hoc (AD-HAHK or AD-HOKE)-Adjective a) Concerned with a particular end or purpose, and b) formed
Ad Hoc Routing Protocols and Issues Stefano Basagni ECE Dept Northeastern University Boston, Jan 2003 Ad hoc (AD-HAHK or AD-HOKE)-Adjective a) Concerned with a particular end or purpose, and b) formed
CS551 Ad-hoc Routing
 CS551 Ad-hoc Routing Bill Cheng http://merlot.usc.edu/cs551-f12 1 Mobile Routing Alternatives Why not just assume a base station? good for many cases, but not some (military, disaster recovery, sensor
CS551 Ad-hoc Routing Bill Cheng http://merlot.usc.edu/cs551-f12 1 Mobile Routing Alternatives Why not just assume a base station? good for many cases, but not some (military, disaster recovery, sensor
PERFORMANCE COMPARISON OF LINK, NODE AND ZONE DISJOINT MULTI-PATH ROUTING STRATEGIES AND MINIMUM HOP SINGLE PATH ROUTING FOR MOBILE AD HOC NETWORKS
 PERFORMANCE COMPARISON OF LINK, NODE AND ZONE DISJOINT MULTI-PATH ROUTING STRATEGIES AND MINIMUM HOP SINGLE PATH ROUTING FOR MOBILE AD HOC NETWORKS Natarajan Meghanathan Jackson State University, 1400
PERFORMANCE COMPARISON OF LINK, NODE AND ZONE DISJOINT MULTI-PATH ROUTING STRATEGIES AND MINIMUM HOP SINGLE PATH ROUTING FOR MOBILE AD HOC NETWORKS Natarajan Meghanathan Jackson State University, 1400
DSR: The Dynamic Source Routing Protocol for Multi-Hop Wireless Ad Hoc Networks
 DSR: The Dynamic Source Routing Protocol for Multi-Hop Wireless Ad Hoc Networks David B. Johnson David A. Maltz Josh Broch Computer Science Department Carnegie Mellon University Pittsburgh, PA 15213-3891
DSR: The Dynamic Source Routing Protocol for Multi-Hop Wireless Ad Hoc Networks David B. Johnson David A. Maltz Josh Broch Computer Science Department Carnegie Mellon University Pittsburgh, PA 15213-3891
Figure 1: Ad-Hoc routing protocols.
 Performance Analysis of Routing Protocols for Wireless Ad-Hoc Networks Sukhchandan Lally and Ljiljana Trajković Simon Fraser University Vancouver, British Columbia Canada E-mail: {lally, ljilja}@sfu.ca
Performance Analysis of Routing Protocols for Wireless Ad-Hoc Networks Sukhchandan Lally and Ljiljana Trajković Simon Fraser University Vancouver, British Columbia Canada E-mail: {lally, ljilja}@sfu.ca
Mobile Ad Hoc Networks Simulations Using Routing Protocols for Performance Comparisons
 Mobile Ad Hoc Networks Simulations Using Routing Protocols for Performance Comparisons Nadia Qasim, Fatin Said, Hamid Aghvami Abstract In this paper we have done performance comparisons of mobile ad hoc
Mobile Ad Hoc Networks Simulations Using Routing Protocols for Performance Comparisons Nadia Qasim, Fatin Said, Hamid Aghvami Abstract In this paper we have done performance comparisons of mobile ad hoc
Page 1. Mobile Ad Hoc Networks. EEC173B/ECS152C, Winter Mobile Ad Hoc Networks (MANET)
 173/152, Winter 2006 obile d oc etworks (T) obile d oc etworks (T) ntroduction Unicast Routing Properties ormed by wireless hosts which may be mobile Without (necessarily) using a pre existing infrastructure
173/152, Winter 2006 obile d oc etworks (T) obile d oc etworks (T) ntroduction Unicast Routing Properties ormed by wireless hosts which may be mobile Without (necessarily) using a pre existing infrastructure
Routing protocols in Mobile Ad Hoc Network
 Routing protocols in Mobile Ad Hoc Network Presented By :- Nitesh Jain Date:-26/10/2005 SCHOOL OF INFORMATION TECHNOLOGY INDIAN INSTITUTE OF TECHNOLOGY KHARAGPUR KHARAGPUR Types of Wireless Networks Infrastructure
Routing protocols in Mobile Ad Hoc Network Presented By :- Nitesh Jain Date:-26/10/2005 SCHOOL OF INFORMATION TECHNOLOGY INDIAN INSTITUTE OF TECHNOLOGY KHARAGPUR KHARAGPUR Types of Wireless Networks Infrastructure
The MAC layer in wireless networks
 The MAC layer in wireless networks The wireless MAC layer roles Access control to shared channel(s) Natural broadcast of wireless transmission Collision of signal: a time/space problem Who transmits when?
The MAC layer in wireless networks The wireless MAC layer roles Access control to shared channel(s) Natural broadcast of wireless transmission Collision of signal: a time/space problem Who transmits when?
MAC in /20/06
 MAC in 802.11 2/20/06 MAC Multiple users share common medium. Important issues: Collision detection Delay Fairness Hidden terminals Synchronization Power management Roaming Use 802.11 as an example to
MAC in 802.11 2/20/06 MAC Multiple users share common medium. Important issues: Collision detection Delay Fairness Hidden terminals Synchronization Power management Roaming Use 802.11 as an example to
Simulation and Comparative Analysis of AODV, DSR, DSDV and OLSR Routing Protocol in MANET Abstract Keywords:
 Volume-9 Number-1 Jan -June 2017 pp. 16-21 available online at www.csjournalss.com Simulation and Comparative Analysis of AODV, DSR, DSDV and OLSR Routing Protocol in MANET Sachin Lalar, Arun Kumar Yadav
Volume-9 Number-1 Jan -June 2017 pp. 16-21 available online at www.csjournalss.com Simulation and Comparative Analysis of AODV, DSR, DSDV and OLSR Routing Protocol in MANET Sachin Lalar, Arun Kumar Yadav
LECTURE PLAN. Script. Introduction about MAC Types o ALOHA o CSMA o CSMA/CD o CSMA/CA
 Course- B.Sc. Applied Physical Science (Computer Science) Year- IIIrd, Sem- Vth Subject Computer Science Paper- XVIIth, Computer Networks Lecture -11 Lecture Title- Medium Access Layer Script Today in
Course- B.Sc. Applied Physical Science (Computer Science) Year- IIIrd, Sem- Vth Subject Computer Science Paper- XVIIth, Computer Networks Lecture -11 Lecture Title- Medium Access Layer Script Today in
THE EXTENDED CLUSTERING AD HOC ROUTING PROTOCOL (ECRP)
 THE EXTENDED CLUSTERING AD HOC ROUTING PROTOCOL (P) 1 Buthayna Al-Sharaa 1 Department of Electrical Engineering, Al Balqa Applied University, Jordan buthayna74@hotmail.com Abstract Ad hoc networks are
THE EXTENDED CLUSTERING AD HOC ROUTING PROTOCOL (P) 1 Buthayna Al-Sharaa 1 Department of Electrical Engineering, Al Balqa Applied University, Jordan buthayna74@hotmail.com Abstract Ad hoc networks are
Mitigating Superfluous Flooding of Control Packets MANET
 Mitigating Superfluous Flooding of Control Packets MANET B.Shanmugha Priya 1 PG Student, Department of Computer Science, Park College of Engineering and Technology, Kaniyur, Coimbatore, India 1 Abstract:
Mitigating Superfluous Flooding of Control Packets MANET B.Shanmugha Priya 1 PG Student, Department of Computer Science, Park College of Engineering and Technology, Kaniyur, Coimbatore, India 1 Abstract:
A Comparative Study of Routing Protocols for Mobile Ad-Hoc Networks
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 11, November 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 11, November 2014,
