WHITE PAPER DECEMBER VMWARE vsphere VIRTUAL MACHINE ENCRYPTION. Virtual Machine Encryption Management
|
|
|
- Dominick Knight
- 6 years ago
- Views:
Transcription
1 WHITE PAPER DECEMBER 2017 VMWARE vsphere VIRTUAL MACHINE ENCRYPTION Virtual Machine Encryption Management
2 Contents Executive Summary Traditional Encryption Solutions In-Guest Encryption Infrastructure-Based Encryption Self-Encrypting Drives Array-Based Encryption... 5 Disadvantages to Disk- and Array-Based Encryption Fabric-Based Encryption Host Bus Adapter (HBA) Disadvantages to HBA Encryption Switch-Based Encryption... 6 Disadvantages to Switch-Based Encryption vsphere VM Encryption... 6 What Is Encrypted What Is Not Encrypted How Encryption Is Performed Key Management Server....7 vcenter Server....7 ESXi Hosts....7 Virtual Machine Keys....7 Roles and Permissions No Cryptography Administrator Least Privilege Host Encryption Mode Key Management Key Manager Availability KMS Cluster or Alias Policy-Based Enforcement Assurance and Attestation Advantages of vsphere Virtual Machine Encryption Conclusion WHITE PAPER 2
3 Executive Summary Virtual machine (VM) encryption has been around in different forms for many years and has met with various levels of success. The challenges of ensuring security versus running IT operations frequently led to solutions that, while secure, exponentially increased operational workload. The attempt to force existing rules onto a newer platform caused difficulties. By its very nature, virtualization changes the game. Rather than looking to that layer to provide security services, existing encryption solutions try to take the same approach one would take with a laptop or bare metal server. This requires modifications to the VM operating system (OS) or disk layout. VMware vsphere 6.5 addresses the operational and security challenges by leveraging the hypervisor to perform the encryption with no modification to the VM. The security architecture of VMware ESXi achieves this goal at the hypervisor layer, which yields the following benefits: No modification to VM OSs No changes to existing applications are required, providing a common method of encryption across any OS supported by vsphere. No specialized hardware or infrastructure required The encryption works with existing storage devices and storage fabrics. Policy-based enforcement that is supported by the vsphere SDK and tools such as VMware vsphere PowerCLI This provides easy integration into current and future provisioning solutions. In this document, we will elaborate on how the security architecture and controls of vsphere VM encryption address the concerns of the security team while providing the IT operations team with the necessary tools to minimize impact on day-to-day operations. This information is for both seasoned security specialists and experienced IT professionals. Some of the concepts herein might require a deeper understanding of hypervisor security. This is documented in the Security of the VMware vsphere Hypervisor technical white paper. Traditional Encryption Solutions Before describing the VMware solution for data encryption, we will discuss existing solutions by way of comparison. Generally speaking, there are two traditional approaches to encryption: in-guest and infrastructure-based. In-Guest Encryption In this scenario, encryption occurs within the guest VM. This is one of the more common methods of encryption outside of the virtualized data center. For example, many corporate laptops and desktops enforce the use of Microsoft Windows BitLocker, macos FileVault, or Linux dm-crypt. WHITE PAPER 3
4 This type of solution typically uses a preboot partition to control access to the encrypted partition. This involves custom partitioning of disks. The system boots from the preboot partition. Keys are retrieved via a hardware device or software control to enable the encrypted partition to boot. Each of these solutions requires additional setup and management. For example, it might be required to present a Trusted Platform Module (TPM) device to the VM. Multifactor authentication configuration might also be required. These solutions are OS specific in each case. The following are among the significant challenges with some of these solutions: There is no common encryption policy across Windows, Linux, and other OSs. Each is managed and configured separately. Encryption occurs in the context of the OS. Encryption takes place in the same context as potential malware. Encryption might require disabling to apply updates to the OS or applications. This adds to the operational burden and to the chances for error and misconfiguration. Changes in hardware configurations can lead to problems. This includes changes that might cause specialized investigation of encryption failures. All of these factors introduce large operational overhead costs. They all require individual configuration, management, and checking to ensure proper performance. Each environment has the capacity to run a unique number of VMs, beyond which operation becomes unwieldy and difficult to manage. Infrastructure-Based Encryption In this broad category, data is encrypted via the hardware deployed in the virtual environment. There are several points at which this encryption can occur. Self-Encrypting Drives Disk-based encryption is an approach by which the data is encrypted as it is written to disk. Self-encrypting drives (SEDs) have built-in hardware, which encrypts the stream of bits being written to an individual disk drive. Each drive is encrypted with a unique media encryption key (MEK), which is then encrypted with a key encryption key (KEK). If no KEK is used, no protection of the data is provided if the disk is moved to another system, even though the data is encrypted on the device via the MEK. From a hardware perspective, a SED without a KEK is essentially a normal disk. KEKs for SEDs can be managed in two ways. The first is via local key management. In this scenario, the server RAID adapter is configured with individual KEKs for each server. At boot time, the adapter loads the KEK into the respective SED, unlocking the drive. This requires keeping track of which KEK is configured in each server. In case of adapter failure, adapter reconfiguration with the recorded KEKs is necessary for data retrieval. In the second method, the HBA on the server interfaces with an external key manager provider, retrieves the KEK, and loads it into the SED. WHITE PAPER 4
5 Array-Based Encryption With array-based encryption, the controller in a storage array encrypts the data as it is written to the disks. Encryption can be performed via custom applicationspecific integrated circuits (ASICs) in hardware or in software. In both cases, key management can be achieved via an onboard key manager or through the use of an external Key Management Interoperability Protocol (KMIP) compliant key manager. Disadvantages to Disk- and Array-Based Encryption The main disadvantage of disk-based encryption is that data is not encrypted until just before it reaches the storage medium. This means that it travels in the clear from the application through the storage fabric or network. This might not be a concern when, for example, a SED is used for local storage on a server. But most data centers are architected with data generated or obtained by systems that are separate from the systems that store the data. This solution also lacks context of the workloads that are running, so it is not possible to manage workload granularity and multitenancy. For example, there is no easy way to enable different workloads to have different encryption keys. Although disk-based encryption might satisfy a strict definition for protecting data at rest, the physical stealing of a disk or array is the main threat it protects against. Moreover, in the case of array-based encryption, the entire disk array comes into scope for a compliance audit. The management plane of the array must be analyzed to identify the members of the storage team who have access to the data as well as their privileges to perform operations on it. Also, disk-based encryption can incur a significant cost. SEDs generally cost more than their standard counterparts, and arrays with encryption capabilities are usually high end and expensive. Fabric-Based Encryption Fabric-based encryption is possible when servers in a data center send their data to storage devices through a network that is usually dedicated to storage. The data is encrypted in the storage fabric as it leaves the physical server. There are two primary ways through which this is done. Host Bus Adapter (HBA) With the first method, data is encrypted by the server s host bus adapter (HBA) as it leaves the host and enters the storage network. For many HBA devices, key management occurs via existing external KMIP-based key managers. Because the encryption is handled at the host, data does not travel in the clear at all. Disadvantages to HBA Encryption The main drawback to HBA encryption is that it must be managed at the per-host level. This is not easy to scale up in large environments. It also greatly reduces workload portability: VMs encrypted on one host are not easily moved to another host. For this reason, it is also difficult to provide for multitenancy. WHITE PAPER 5
6 Switch-Based Encryption With the second method, the data leaves the host and travels in the clear until it reaches a switch, which then performs the encryption before sending the data on to the storage array. The switch might be a Fibre Channel switch or, in the case of NFS, a network switch. The switch typically also integrates with an external, KMIP-compliant key manager. Disadvantages to Switch-Based Encryption As mentioned, data is encrypted only after it has left the host and arrived at the switch. The switch presents array-based LUNs or NFS shares to each host, which in turn presents the LUN or share as a datastore. This limits the ability and flexibility to move a VM from datastore to datastore. Using a mix of Fibre Channel and NFS requires encryption at multiple fabric switches. There is significant overhead in setup, configuration, and orchestration of VM workloads and infrastructure. Multitenancy is limited to the datastore on which a VM resides, limiting operational efficiency. vsphere VM Encryption vsphere VM encryption enables creation of encrypted VMs and encrypts existing VMs. Because all VM files that contain sensitive information are encrypted, the entire VM is protected. Only administrators with encryption privileges can perform encryption and decryption tasks. What Is Encrypted vsphere VM encryption supports encryption of the following types of files: VM files Virtual disk files Host core dump files What Is Not Encrypted Some files associated with a VM are not encrypted or are partially encrypted because they don t contain sensitive information: Log files VM configuration files Virtual disk descriptor files How Encryption Is Performed To explain how encryption is performed, we first discuss the three major components used to encrypt: Key management server (KMS) VMware vcenter Server ESXi hosts WHITE PAPER 6
7 Key Management Server The vcenter Server instance requests keys from an external KMS. The KMS generates and stores KEKs and passes them to the vcenter Server instance for distribution. As a KMIP client, the vcenter Server system uses that protocol to facilitate use of the chosen KMS. vcenter Server The vcenter Server instance obtains keys from the KMS and transfers them to the ESXi hosts. It does not store or persist the KMS keys, but it keeps a list of key IDs. The vcenter Server system checks the privileges of users who perform cryptographic operations. VMware vsphere Web Client assigns cryptographic operation privileges and limits the users who can perform these operations. The vcenter Server system adds cryptography events to the list of events that can be viewed and exported from the vsphere Web Client event console. Each event includes the user, time, key ID, and cryptographic operation. ESXi Hosts The ESXi host is responsible for several aspects of the encryption workflow: Performs the encryption of VM disks Ensures that guest data for encrypted VMs is not sent over the network without encryption Encryption per se is performed by the industry-standard OpenSSL libraries and algorithms described in the following section. VM encryption does not impose any new hardware requirements, but using a processor that supports the AES-NI instruction set accelerates encryption and decryption operations. Virtual Machine Keys Two types of keys are used for VM encryption: Data encryption key (DEK): The ESXi host generates and uses internal keys to encrypt VMs and disks. These XTS-AES-256 keys are used as DEKs. Key encryption key (KEK): The vcenter Server instance requests AES-256 keys from the KMS. vcenter Server stores only the ID of each KEK, but not the key itself. The vcenter Server system transfers VM KEKs to an ESXi host when the host requires a key. The ESXi host uses the KEK to encrypt the DEK, and it stores the encrypted internal key on disk. The ESXi host does not store the KEK on disk. If a host reboots, the vcenter Server instance requests the KEK with the corresponding ID from the KMS and makes it available to the ESXi host. The ESXi host can then decrypt the DEKs as needed. Figure 1 illustrates the roles of the KEKs and DEKs. WHITE PAPER 7
8 KEK KMS-provided key encryption key Protected by customer s key management server DEK ESXi-generated data encryption key Protected by a KMS key encryption key VM VM Data Protected by an ESXi-generated DEK that is encrypted by the KMS-provided KEK Figure 1. Roles of Data Encryption Key and Key Encryption Key Roles and Permissions A new set of permissions has been added to vcenter Server to enable fine-grained permissions regarding VM encryption. These permissions fall under the banner of cryptographic operations. They enable the creation of custom roles that meet the business and security needs of a data center. For example, a custom role can be created to enable an administrator to encrypt a VM but not decrypt it. No Cryptography Administrator A new predefined role, no cryptography administrator, supports all administrator privileges except for the cryptographic operations privileges. This role enables standard administrator tasks such as powering on or migrating a VM via VMware vsphere vmotion. The following operations are not enabled: Encrypting a VM Decrypting a VM Allowing console access to an encrypted VM Downloading an encrypted VM Configuring key managers Least Privilege These permissions and the new no cryptography administrator role align with the industry movement toward least privilege management, which gives users only the privileges required to perform their roles. WHITE PAPER 8
9 The standard vcenter Server administrator role has all privileges, including encryption and decryption of VMs and configuration of key managers. Those adopting VM encryption are strongly encouraged to review which individuals have elevated privileges and whether they can be assigned roles with few capabilities. Host Encryption Mode Encrypted VMs can be encrypted or run only if host encryption mode is enabled for the ESXi host. Host encryption mode is often enabled automatically, but it also can be enabled explicitly. Users can check and explicitly set the current host encryption mode from the vsphere Web Client instance or by using the VMware vsphere Storage APIs. Automatic changes occur when encryption operations attempt to enable host encryption mode for example, when adding an encrypted VM to a host on which host encryption mode is not enabled. Encryption mode changes automatically to enabled when a user has the required privileges to complete the operation on the host. Key Management Setting up a trusted connection between the vcenter Server instance and a KMS is one element of initial configuration of vsphere VM encryption. The vcenter Server system can then retrieve keys from the KMS as needed. Key Manager Availability The biggest requirement of key management is availability. DNS provides a good comparison. Best practices discourage use of a single DNS server in an environment. A properly configured data center should have multiple replicating DNS servers in case something goes wrong. The same holds true for key management. Most modern KMS designs enable the use of replicating key managers. KMS Cluster or Alias In the context of vcenter Server, a KMS cluster or alias is essentially a list of replicating key manager FQDN or IP addresses grouped into a single namespace KMS Cluster, for example. In this example, multiple tenants, each with their respective key management infrastructures, can be named Tenant A KMS Cluster and Tenant B KMS Cluster. Policy-Based Enforcement Despite the sophistication of vsphere VM encryption, the actual task of encrypting a VM is quite straightforward. Encryption is essentially a storage policy that is applied to a VM, as with any other storage policy. After the policy has been applied, the VM is automatically encrypted. WHITE PAPER 9
10 The encryption policy can be applied on the Storage Policy screens in the vsphere Web Client instance. It can also be applied programmatically, via the vsphere Storage APIs or vsphere PowerCLI for example. This latter method enables encryption operations that can be performed across many VMs simultaneously, regardless of their OS type. Because of this policy-based enforcement, automation of VM encryption is simple, and it is very easy to integrate it with any overall provisioning workflow. Assurance and Attestation Regarding encryption, two concepts apply. The first is assurance: knowing that only verified code is being run during encryption operations and that any hardware is configured correctly. The second is attestation: the process by which the assurance can be measured. Another key term is remote attestation: out-of-band assurance measurement. A remote system determines the level of trust. With VM encryption, there is assurance of the device doing the encryption, in this case the ESXi hypervisor. This is accomplished in vsphere by enabling Secure Boot on the host that ensures that only digitally signed code is allowed to run. Remote attestation is another feature under consideration for the future. This will provide additional assurance that the hypervisor and underlying hardware have not been tampered with. HBAs, in-guest, fabric, SEDs, and arrays do not normally have a common method that provides for this level of remote attestation and certainly not one that is easy to consume at scale. Advantages of vsphere Virtual Machine Encryption The key difference between VM encryption and all other traditional solutions is ease of management. When VMs are treated as objects that can have a policy applied to them, there is no need to manage them individually. In addition, implementing encryption at the hypervisor eliminates the need for additional, specialized hardware to perform encryption. It also removes the need to bring into scope switches, drives, and all of the configuration requirements they introduce. This exponentially shrinks operational overhead and considerably reduces the chances of misconfiguration or abuse. If a security solution is too difficult, methods will be discovered to circumvent that solution. Traditional encryption solutions are difficult and time consuming to set up and manage. They also don t take into account the new rules that encryption at scale demands. These factors were the driving force behind the development of VM encryption in vsphere 6.5. It is easy to configure, easy to use, and also easy to report, so compliance objectives can be efficiently met. WHITE PAPER 10
11 Table 1 lists the major features that characterize encryption solutions and compares the abilities of the various methods. Feature VM Encryption HBA Switch SED In-Guest Multitenancy Yes No Maybe No Yes Guest OS Agnostic Yes Yes Yes Yes No Software Policy-Based Enforcement Yes No No No No Automation Yes No No No Maybe Additional Hardware No Yes Yes Yes Maybe Datastore Independent Yes No No No Yes No Access to Encryption Keys by the Guest Yes Yes Yes Yes No Table 1. Encryption Comparison Table Conclusion New technologies bring new rules. Encryption of data has a long history of being difficult to manage. Previous technologies struggle to keep up with the ever-increasing scale and the unique challenges that scale brings. Applying old rules to new technologies negatively impacts the ROI of these technologies. The increased burden of configuration, management, and attestation of hardwarebased solutions hinders IT operations, security, and compliance. With VMware vsphere, VMware has built one of the most secure and robust virtualization platforms. Encryption is now available via software policies that are independent of the operating system and applications while still maintaining operational efficiencies inherent in the vsphere platform, all while preserving the security of the virtual machine. WHITE PAPER 11
12 VMware, Inc Hillview Avenue Palo Alto CA USA Tel Fax Copyright 2017 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws. VMware products are covered by one or more patents listed at VMware is a registered trademark or trademark of VMware, Inc. and its subsidiaries in the United States and other jurisdictions. All other marks and names mentioned herein may be trademarks of their respective companies. Item No: VMW-WP-vSPHR-Virt-Mach-Encryp-USLET /17
What s New in VMware vsphere 5.1 Platform
 vsphere 5.1 Platform VMware vsphere 5.1 TECHNICAL MARKETING DOCUMENTATION V 2.0 / UPDATED JUNE 2012 Table of Contents Introduction.................................................................. 3 vsphere
vsphere 5.1 Platform VMware vsphere 5.1 TECHNICAL MARKETING DOCUMENTATION V 2.0 / UPDATED JUNE 2012 Table of Contents Introduction.................................................................. 3 vsphere
BUILDING SECURITY INTO YOUR DATA CENTER MODERNIZATION STRATEGY
 SOLUTION OVERVIEW BUILDING SECURITY INTO YOUR DATA CENTER MODERNIZATION STRATEGY Every organization is exploring how technology can help it disrupt current operating models, enabling it to better serve
SOLUTION OVERVIEW BUILDING SECURITY INTO YOUR DATA CENTER MODERNIZATION STRATEGY Every organization is exploring how technology can help it disrupt current operating models, enabling it to better serve
What s New in VMware vsphere 5.1 Platform
 vsphere 5.1 Platform VMware vsphere 5.1 TECHNICAL MARKETING DOCUMENTATION V 2.0 / UPDATED JUNE 2012 Table of Contents Introduction... 3 vsphere Platform Enhancements... 3 User Access... 3 Auditing....
vsphere 5.1 Platform VMware vsphere 5.1 TECHNICAL MARKETING DOCUMENTATION V 2.0 / UPDATED JUNE 2012 Table of Contents Introduction... 3 vsphere Platform Enhancements... 3 User Access... 3 Auditing....
VMware vsphere Data Protection Evaluation Guide REVISED APRIL 2015
 VMware vsphere Data Protection REVISED APRIL 2015 Table of Contents Introduction.... 3 Features and Benefits of vsphere Data Protection... 3 Requirements.... 4 Evaluation Workflow... 5 Overview.... 5 Evaluation
VMware vsphere Data Protection REVISED APRIL 2015 Table of Contents Introduction.... 3 Features and Benefits of vsphere Data Protection... 3 Requirements.... 4 Evaluation Workflow... 5 Overview.... 5 Evaluation
What s New in VMware vsphere Storage Appliance 5.1 TECHNICAL MARKETING DOCUMENTATION V 1.0/UPDATED JULY 2012
 What s New in VMware vsphere TECHNICAL MARKETING DOCUMENTATION V 1.0/UPDATED JULY 2012 Table of Contents Introduction... 3 Support for Additional Disk Drives... 3 Maximum Storage per ESXi Host...4 Increase
What s New in VMware vsphere TECHNICAL MARKETING DOCUMENTATION V 1.0/UPDATED JULY 2012 Table of Contents Introduction... 3 Support for Additional Disk Drives... 3 Maximum Storage per ESXi Host...4 Increase
VMWARE VSPHERE FEATURE COMPARISON
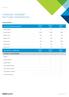 DATASHEET VMWARE VSPHERE FEATURE COMPARISON ACROSS VERSIONS KEY SCALE METRICS: MAXIMUMS Host per Cluster VMs per Cluster CPUs per Host RAM per Host VMs per Host vcpus per VM vram per VM 32 64 64 4000 8000
DATASHEET VMWARE VSPHERE FEATURE COMPARISON ACROSS VERSIONS KEY SCALE METRICS: MAXIMUMS Host per Cluster VMs per Cluster CPUs per Host RAM per Host VMs per Host vcpus per VM vram per VM 32 64 64 4000 8000
Storage Considerations for VMware vcloud Director. VMware vcloud Director Version 1.0
 Storage Considerations for VMware vcloud Director Version 1.0 T e c h n i c a l W H I T E P A P E R Introduction VMware vcloud Director is a new solution that addresses the challenge of rapidly provisioning
Storage Considerations for VMware vcloud Director Version 1.0 T e c h n i c a l W H I T E P A P E R Introduction VMware vcloud Director is a new solution that addresses the challenge of rapidly provisioning
vsphere Platform Security Update Day 2 Security Operations VMworld 2017 Content: Not for publication
 SER1848BU vsphere Platform Security Update Mike Foley #VMworld #SER1848BU vsphere Platform Security Update Day 2 Security Operations VMworld 2017 Content: Not for publication Current Issues Current Issues:
SER1848BU vsphere Platform Security Update Mike Foley #VMworld #SER1848BU vsphere Platform Security Update Day 2 Security Operations VMworld 2017 Content: Not for publication Current Issues Current Issues:
VMware vsphere 5.0 Evaluation Guide
 VMware vsphere 5.0 Evaluation Guide Auto Deploy TECHNICAL WHITE PAPER Table of Contents About This Guide.... 4 System Requirements... 4 Hardware Requirements.... 4 Servers.... 4 Storage.... 4 Networking....
VMware vsphere 5.0 Evaluation Guide Auto Deploy TECHNICAL WHITE PAPER Table of Contents About This Guide.... 4 System Requirements... 4 Hardware Requirements.... 4 Servers.... 4 Storage.... 4 Networking....
VMware vsphere Data Protection 5.8 TECHNICAL OVERVIEW REVISED AUGUST 2014
 VMware vsphere Data Protection 5.8 TECHNICAL OVERVIEW REVISED AUGUST 2014 Table of Contents Introduction.... 3 Features and Benefits of vsphere Data Protection... 3 Additional Features and Benefits of
VMware vsphere Data Protection 5.8 TECHNICAL OVERVIEW REVISED AUGUST 2014 Table of Contents Introduction.... 3 Features and Benefits of vsphere Data Protection... 3 Additional Features and Benefits of
DISASTER RECOVERY- AS-A-SERVICE FOR VMWARE CLOUD PROVIDER PARTNERS WHITE PAPER - OCTOBER 2017
 DISASTER RECOVERY- AS-A-SERVICE FOR VMWARE CLOUD PROVIDER PARTNERS WHITE PAPER - OCTOBER 2017 Table of Contents Executive Summary 3 Introduction 3 vsphere Replication... 3 VMware NSX for vsphere... 4 What
DISASTER RECOVERY- AS-A-SERVICE FOR VMWARE CLOUD PROVIDER PARTNERS WHITE PAPER - OCTOBER 2017 Table of Contents Executive Summary 3 Introduction 3 vsphere Replication... 3 VMware NSX for vsphere... 4 What
The Road to a Secure, Compliant Cloud
 The Road to a Secure, Compliant Cloud The Road to a Secure, Compliant Cloud Build a trusted infrastructure with a solution stack from Intel, IBM Cloud SoftLayer,* VMware,* and HyTrust Technology innovation
The Road to a Secure, Compliant Cloud The Road to a Secure, Compliant Cloud Build a trusted infrastructure with a solution stack from Intel, IBM Cloud SoftLayer,* VMware,* and HyTrust Technology innovation
Disclaimer This presentation may contain product features that are currently under development. This overview of new technology represents no commitme
 STO1960BU vsphere Encryption for Virtual Machines and vsan Encryption Deep Dive VMworld 2017 Content: Not for publication Jase McCarty & Mike Foley #VMworld #STO1960 Disclaimer This presentation may contain
STO1960BU vsphere Encryption for Virtual Machines and vsan Encryption Deep Dive VMworld 2017 Content: Not for publication Jase McCarty & Mike Foley #VMworld #STO1960 Disclaimer This presentation may contain
What s New in VMware vsphere Availability
 What s New in VMware vsphere 5.0 - Availability Technical WHITE PAPER v 1.0/Updated June 2011 Table of Contents Introduction.... 3 Management Availability.... 3 Manageability.... 3 Usability.... 4 Application
What s New in VMware vsphere 5.0 - Availability Technical WHITE PAPER v 1.0/Updated June 2011 Table of Contents Introduction.... 3 Management Availability.... 3 Manageability.... 3 Usability.... 4 Application
VMWARE EBOOK. Easily Deployed Software-Defined Storage: A Customer Love Story
 VMWARE EBOOK Easily Deployed Software-Defined Storage: A Customer Love Story TABLE OF CONTENTS The Software-Defined Data Center... 1 VMware Virtual SAN... 3 A Proven Enterprise Platform... 4 Proven Results:
VMWARE EBOOK Easily Deployed Software-Defined Storage: A Customer Love Story TABLE OF CONTENTS The Software-Defined Data Center... 1 VMware Virtual SAN... 3 A Proven Enterprise Platform... 4 Proven Results:
What s New in VMware vsphere 5.1 VMware vcenter Server
 What s New in VMware vsphere 5.1 VMware vsphere 5.1 TECHNICAL MARKETING DOCUMENTATION V 1.0/UPDATED JULY 2012 Table of Contents Introduction... 3 Key Components... 3 vcenter Single Sign-On Server.... 3
What s New in VMware vsphere 5.1 VMware vsphere 5.1 TECHNICAL MARKETING DOCUMENTATION V 1.0/UPDATED JULY 2012 Table of Contents Introduction... 3 Key Components... 3 vcenter Single Sign-On Server.... 3
PERFORMANCE CHARACTERIZATION OF MICROSOFT SQL SERVER USING VMWARE CLOUD ON AWS PERFORMANCE STUDY JULY 2018
 PERFORMANCE CHARACTERIZATION OF MICROSOFT SQL SERVER USING VMWARE CLOUD ON AWS PERFORMANCE STUDY JULY 2018 Table of Contents Executive Summary...3 Introduction...3 Test Environment... 4 Infrastructure
PERFORMANCE CHARACTERIZATION OF MICROSOFT SQL SERVER USING VMWARE CLOUD ON AWS PERFORMANCE STUDY JULY 2018 Table of Contents Executive Summary...3 Introduction...3 Test Environment... 4 Infrastructure
VMware vcloud Networking and Security Overview
 VMware vcloud Networking and Security Overview Efficient, Agile and Extensible Software-Defined Networks and Security WHITE PAPER Overview Organizations worldwide have gained significant efficiency and
VMware vcloud Networking and Security Overview Efficient, Agile and Extensible Software-Defined Networks and Security WHITE PAPER Overview Organizations worldwide have gained significant efficiency and
Achieving Digital Transformation: FOUR MUST-HAVES FOR A MODERN VIRTUALIZATION PLATFORM WHITE PAPER
 Achieving Digital Transformation: FOUR MUST-HAVES FOR A MODERN VIRTUALIZATION PLATFORM WHITE PAPER Table of Contents The Digital Transformation 3 Four Must-Haves for a Modern Virtualization Platform 3
Achieving Digital Transformation: FOUR MUST-HAVES FOR A MODERN VIRTUALIZATION PLATFORM WHITE PAPER Table of Contents The Digital Transformation 3 Four Must-Haves for a Modern Virtualization Platform 3
What s New in VMware Virtual SAN (VSAN) v 0.1c/AUGUST 2013
 What s New in VMware Virtual SAN (VSAN) Technical WHITE PAPER v 0.1c/AUGUST 2013 Table of Contents 1. Introduction.... 4 1.1 Software-Defined Datacenter.... 4 1.2 Software-Defined Storage.... 4 1.3 What
What s New in VMware Virtual SAN (VSAN) Technical WHITE PAPER v 0.1c/AUGUST 2013 Table of Contents 1. Introduction.... 4 1.1 Software-Defined Datacenter.... 4 1.2 Software-Defined Storage.... 4 1.3 What
VMWARE CLOUD FOUNDATION: THE SIMPLEST PATH TO THE HYBRID CLOUD WHITE PAPER AUGUST 2018
 VMWARE CLOUD FOUNDATION: THE SIMPLEST PATH TO THE HYBRID CLOUD WHITE PAPER AUGUST 2018 Table of Contents Executive Summary 3 A Single Architecture for Hybrid Cloud 4 Introducing VMware Cloud Foundation
VMWARE CLOUD FOUNDATION: THE SIMPLEST PATH TO THE HYBRID CLOUD WHITE PAPER AUGUST 2018 Table of Contents Executive Summary 3 A Single Architecture for Hybrid Cloud 4 Introducing VMware Cloud Foundation
CLOUD PROVIDER POD. for VMware. Release Notes. VMware Cloud Provider Pod January 2019 Check for additions and updates to these release notes
 VMware Cloud Provider Pod 1.1 31 January 2019 Check for additions and updates to these release notes Version 1.1 This document includes release details about VMware Cloud Provider Pod 1.1 What's in the
VMware Cloud Provider Pod 1.1 31 January 2019 Check for additions and updates to these release notes Version 1.1 This document includes release details about VMware Cloud Provider Pod 1.1 What's in the
Advanced Architecture Design for Cloud-Based Disaster Recovery WHITE PAPER
 Advanced Architecture Design for Cloud-Based Disaster Recovery WHITE PAPER Introduction Disaster Recovery (DR) is a fundamental tool for mitigating IT and business risks. But because it is perceived as
Advanced Architecture Design for Cloud-Based Disaster Recovery WHITE PAPER Introduction Disaster Recovery (DR) is a fundamental tool for mitigating IT and business risks. But because it is perceived as
WHITE PAPER SEPTEMBER VMWARE vsphere AND vsphere WITH OPERATIONS MANAGEMENT. Licensing, Pricing and Packaging
 WHITE PAPER SEPTEMBER 2017 VMWARE vsphere AND vsphere WITH OPERATIONS MANAGEMENT Licensing, Pricing and Packaging Table of Contents Executive Summary 3 VMware vsphere with Operations Management Overview
WHITE PAPER SEPTEMBER 2017 VMWARE vsphere AND vsphere WITH OPERATIONS MANAGEMENT Licensing, Pricing and Packaging Table of Contents Executive Summary 3 VMware vsphere with Operations Management Overview
VMWARE CLOUD FOUNDATION: INTEGRATED HYBRID CLOUD PLATFORM WHITE PAPER NOVEMBER 2017
 : INTEGRATED HYBRID CLOUD PLATFORM WHITE PAPER NOVEMBER 2017 Table of Contents Executive Summary 3 A Single Architecture for Hybrid Cloud 4 Introducing VMware Cloud Foundation 4 Deploying on Premises 6
: INTEGRATED HYBRID CLOUD PLATFORM WHITE PAPER NOVEMBER 2017 Table of Contents Executive Summary 3 A Single Architecture for Hybrid Cloud 4 Introducing VMware Cloud Foundation 4 Deploying on Premises 6
vsphere Security Modified on 21 JUN 2018 VMware vsphere 6.7 VMware ESXi 6.7 vcenter Server 6.7
 Modified on 21 JUN 2018 VMware vsphere 6.7 VMware ESXi 6.7 vcenter Server 6.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Modified on 21 JUN 2018 VMware vsphere 6.7 VMware ESXi 6.7 vcenter Server 6.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
3 Ways Businesses Use Network Virtualization. A Faster Path to Improved Security, Automated IT, and App Continuity
 3 Ways Businesses Use Network Virtualization A Faster Path to Improved Security, Automated IT, and App Continuity INTRODUCTION 2 Today s IT Environments Are Demanding Technology has made exciting leaps
3 Ways Businesses Use Network Virtualization A Faster Path to Improved Security, Automated IT, and App Continuity INTRODUCTION 2 Today s IT Environments Are Demanding Technology has made exciting leaps
What s New in VMware vcloud Automation Center 5.1
 What s New in VMware vcloud Automation Center 5.1 Feature Overview Technical White paper october 2012 Table of Contents vcloud Automation Center Overview.... 3 VMware vsphere 5.1 Support.... 3 VMware vcloud
What s New in VMware vcloud Automation Center 5.1 Feature Overview Technical White paper october 2012 Table of Contents vcloud Automation Center Overview.... 3 VMware vsphere 5.1 Support.... 3 VMware vcloud
Eliminate the Complexity of Multiple Infrastructure Silos
 SOLUTION OVERVIEW Eliminate the Complexity of Multiple Infrastructure Silos A common approach to building out compute and storage infrastructure for varying workloads has been dedicated resources based
SOLUTION OVERVIEW Eliminate the Complexity of Multiple Infrastructure Silos A common approach to building out compute and storage infrastructure for varying workloads has been dedicated resources based
DEPLOY MODERN APPS WITH KUBERNETES AS A SERVICE
 SOLUTION OVERVIEW DEPLOY MODERN APPS WITH KUBERNETES AS A SERVICE Cut Costs and Control Access with VMware Cloud PKS Digital transformation, the Internet of things, the growing popularity of public clouds,
SOLUTION OVERVIEW DEPLOY MODERN APPS WITH KUBERNETES AS A SERVICE Cut Costs and Control Access with VMware Cloud PKS Digital transformation, the Internet of things, the growing popularity of public clouds,
vsan Data Encryption at Rest January 18, 2018
 January 18, 2018 1 Table of Contents 1. Introduction 1.1.An introduction to Data at Rest Encryption 2. Overview 2.1.Common Terminologies 2.2.vSAN Data at Rest Encryption Specifics 3. Architecture of vsan
January 18, 2018 1 Table of Contents 1. Introduction 1.1.An introduction to Data at Rest Encryption 2. Overview 2.1.Common Terminologies 2.2.vSAN Data at Rest Encryption Specifics 3. Architecture of vsan
DEPLOY MODERN APPS WITH KUBERNETES AS A SERVICE
 SOLUTION OVERVIEW DEPLOY MODERN APPS WITH KUBERNETES AS A SERVICE Cut Costs and Control Access with VMware Kubernetes Engine Digital transformation, the Internet of things, the growing popularity of public
SOLUTION OVERVIEW DEPLOY MODERN APPS WITH KUBERNETES AS A SERVICE Cut Costs and Control Access with VMware Kubernetes Engine Digital transformation, the Internet of things, the growing popularity of public
VMware Cloud Provider Pod Designer User Guide. October 2018 Cloud Provider Pod 1.0
 VMware Cloud Provider Pod Designer User Guide October 2018 Cloud Provider Pod 1.0 Table of Contents About VMware Cloud Provider Pod 3 VMware Validated Design versus Advanced Design versus VMware Cloud
VMware Cloud Provider Pod Designer User Guide October 2018 Cloud Provider Pod 1.0 Table of Contents About VMware Cloud Provider Pod 3 VMware Validated Design versus Advanced Design versus VMware Cloud
VMware vcloud Air Accelerator Service
 DATASHEET AT A GLANCE The VMware vcloud Air Accelerator Service assists customers with extending their private VMware vsphere environment to a VMware vcloud Air public cloud. This Accelerator Service engagement
DATASHEET AT A GLANCE The VMware vcloud Air Accelerator Service assists customers with extending their private VMware vsphere environment to a VMware vcloud Air public cloud. This Accelerator Service engagement
VMWARE MICRO-SEGMENTATION AND SECURITY DEPLOY SERVICE
 DATASHEET VMWARE MICRO-SEGMENTATION AND SECURITY DEPLOY SERVICE AT A GLANCE VMware NSX for vsphere expands the power of virtualization and automation to the data center network, which is fully provisioned
DATASHEET VMWARE MICRO-SEGMENTATION AND SECURITY DEPLOY SERVICE AT A GLANCE VMware NSX for vsphere expands the power of virtualization and automation to the data center network, which is fully provisioned
Current Issues
 SER1848BE vsphere Platform Security Update Mike Foley Technical Market Architect vsphere Security Abhijat Singh Product Manager vsphere Security #VMworld #SER1848BE Current Issues Current Issues: SMB v1
SER1848BE vsphere Platform Security Update Mike Foley Technical Market Architect vsphere Security Abhijat Singh Product Manager vsphere Security #VMworld #SER1848BE Current Issues Current Issues: SMB v1
VMWARE PIVOTAL CONTAINER SERVICE
 DATASHEET VMWARE PIVOTAL CONTAINER SERVICE AT A GLANCE VMware Pivotal Container Service (PKS) is a production-grade Kubernetes-based container solution equipped with advanced networking, a private container
DATASHEET VMWARE PIVOTAL CONTAINER SERVICE AT A GLANCE VMware Pivotal Container Service (PKS) is a production-grade Kubernetes-based container solution equipped with advanced networking, a private container
CLOUD PROVIDER POD RELEASE NOTES
 VMware Cloud Provider Pod 1.0 18 October 2018 Check for additions and updates to these release notes Release Notes Version 1.0 This Release Notes document includes details about VMware Cloud Provider Pod
VMware Cloud Provider Pod 1.0 18 October 2018 Check for additions and updates to these release notes Release Notes Version 1.0 This Release Notes document includes details about VMware Cloud Provider Pod
TECHNICAL WHITE PAPER AUGUST 2017 REVIEWER S GUIDE FOR VIEW IN VMWARE HORIZON 7: INSTALLATION AND CONFIGURATION. VMware Horizon 7 version 7.
 TECHNICAL WHITE PAPER AUGUST 2017 REVIEWER S GUIDE FOR VIEW IN VMWARE HORIZON 7: INSTALLATION AND CONFIGURATION VMware Horizon 7 version 7.x Table of Contents Introduction.... 3 JMP Next-Generation Desktop
TECHNICAL WHITE PAPER AUGUST 2017 REVIEWER S GUIDE FOR VIEW IN VMWARE HORIZON 7: INSTALLATION AND CONFIGURATION VMware Horizon 7 version 7.x Table of Contents Introduction.... 3 JMP Next-Generation Desktop
VMWARE CLOUD TM ON AWS. Operations Model White Paper. November 2017
 WHITE PAPER - NOVEMBER 2017 VMWARE CLOUD TM ON AWS Operations Model White Paper November 2017 DISCLAIMER: Some features described in this paper have been released in preview to gather feedback, and may
WHITE PAPER - NOVEMBER 2017 VMWARE CLOUD TM ON AWS Operations Model White Paper November 2017 DISCLAIMER: Some features described in this paper have been released in preview to gather feedback, and may
Cloud Provider Pod Designer User Guide. November 2018 Cloud Provider Pod 1.0.1
 Cloud Provider Pod Designer User Guide November 2018 Cloud Provider Pod 1.0.1 Table of Contents About VMware Cloud Provider Pod 3 Cloud Provider Pod Designer Configuration Options 3 VMware Validated Design
Cloud Provider Pod Designer User Guide November 2018 Cloud Provider Pod 1.0.1 Table of Contents About VMware Cloud Provider Pod 3 Cloud Provider Pod Designer Configuration Options 3 VMware Validated Design
HARNESSING THE HYBRID CLOUD TO DRIVE GREATER BUSINESS AGILITY
 HARNESSING THE HYBRID CLOUD TO DRIVE GREATER BUSINESS AGILITY WHY DIGITAL TRANSFORMATION IS DRIVING ADOPTION OF MULTI-CLOUD STRATEGIES In the era of digital business, enterprises are increasingly using
HARNESSING THE HYBRID CLOUD TO DRIVE GREATER BUSINESS AGILITY WHY DIGITAL TRANSFORMATION IS DRIVING ADOPTION OF MULTI-CLOUD STRATEGIES In the era of digital business, enterprises are increasingly using
VMware vcloud Air. Enterprise IT Hybrid Data Center TECHNICAL MARKETING DOCUMENTATION
 TECHNICAL MARKETING DOCUMENTATION October 2014 Table of Contents Purpose and Overview.... 3 1.1 Background............................................................... 3 1.2 Target Audience...........................................................
TECHNICAL MARKETING DOCUMENTATION October 2014 Table of Contents Purpose and Overview.... 3 1.1 Background............................................................... 3 1.2 Target Audience...........................................................
vcenter Server Installation and Setup Modified on 11 MAY 2018 VMware vsphere 6.7 vcenter Server 6.7
 vcenter Server Installation and Setup Modified on 11 MAY 2018 VMware vsphere 6.7 vcenter Server 6.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
vcenter Server Installation and Setup Modified on 11 MAY 2018 VMware vsphere 6.7 vcenter Server 6.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware vrealize Suite and vcloud Suite
 VMware vrealize Suite and vcloud Suite Licensing, Pricing, and Packaging WHITE PAPER Table of Contents Executive Summary.... 3 vrealize Suite Licensing Overview... 3 Multiple Components under a Single
VMware vrealize Suite and vcloud Suite Licensing, Pricing, and Packaging WHITE PAPER Table of Contents Executive Summary.... 3 vrealize Suite Licensing Overview... 3 Multiple Components under a Single
STREAMLINING THE DELIVERY, PROTECTION AND MANAGEMENT OF VIRTUAL DESKTOPS. VMware Workstation and Fusion. A White Paper for IT Professionals
 WHITE PAPER NOVEMBER 2016 STREAMLINING THE DELIVERY, PROTECTION AND MANAGEMENT OF VIRTUAL DESKTOPS VMware Workstation and Fusion A White Paper for IT Professionals Table of Contents Overview 3 The Changing
WHITE PAPER NOVEMBER 2016 STREAMLINING THE DELIVERY, PROTECTION AND MANAGEMENT OF VIRTUAL DESKTOPS VMware Workstation and Fusion A White Paper for IT Professionals Table of Contents Overview 3 The Changing
vsphere Upgrade Update 1 Modified on 4 OCT 2017 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5
 Update 1 Modified on 4 OCT 2017 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you
Update 1 Modified on 4 OCT 2017 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you
vsphere Installation and Setup Update 2 Modified on 10 JULY 2018 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5
 vsphere Installation and Setup Update 2 Modified on 10 JULY 2018 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5 You can find the most up-to-date technical documentation on the VMware website at:
vsphere Installation and Setup Update 2 Modified on 10 JULY 2018 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5 You can find the most up-to-date technical documentation on the VMware website at:
vsphere Security VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5 EN
 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To
VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To
What s New in VMware vsphere Flash Read Cache TECHNICAL MARKETING DOCUMENTATION
 What s New in VMware vsphere TECHNICAL MARKETING DOCUMENTATION v 0.1/September 2013 Table of Contents Introduction.... 3 1.1 Software-Defined Datacenter... 3 1.2 Software-Defined Storage... 3 1.3 What
What s New in VMware vsphere TECHNICAL MARKETING DOCUMENTATION v 0.1/September 2013 Table of Contents Introduction.... 3 1.1 Software-Defined Datacenter... 3 1.2 Software-Defined Storage... 3 1.3 What
vsphere Security Update 1 Modified 03 NOV 2017 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5
 Update 1 Modified 03 NOV 2017 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Update 1 Modified 03 NOV 2017 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
What s New with VMware vcloud Director 8.0
 Feature Overview TECHNICAL WHITE PAPER Table of Contents What s New with VMware....3 Support for vsphere 6.0 and NSX 6.1.4....4 VMware vsphere 6.0 Support...4 VMware NSX 6.1.4 Support....4 Organization
Feature Overview TECHNICAL WHITE PAPER Table of Contents What s New with VMware....3 Support for vsphere 6.0 and NSX 6.1.4....4 VMware vsphere 6.0 Support...4 VMware NSX 6.1.4 Support....4 Organization
CLOUD PROVIDER POD RELEASE NOTES
 VMware Cloud Provider Pod 1.0.1 20 November 2018 Check for additions and updates to these release notes Release Notes Version 1.0.1 This Release Notes document includes release details about VMware Cloud
VMware Cloud Provider Pod 1.0.1 20 November 2018 Check for additions and updates to these release notes Release Notes Version 1.0.1 This Release Notes document includes release details about VMware Cloud
STRATEGIC WHITE PAPER. Securing cloud environments with Nuage Networks VSP: Policy-based security automation and microsegmentation overview
 STRATEGIC WHITE PAPER Securing cloud environments with Nuage Networks VSP: Policy-based security automation and microsegmentation overview Abstract Cloud architectures rely on Software-Defined Networking
STRATEGIC WHITE PAPER Securing cloud environments with Nuage Networks VSP: Policy-based security automation and microsegmentation overview Abstract Cloud architectures rely on Software-Defined Networking
vsphere Security Update 2 Modified on 22 JUN 2018 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5
 Update 2 Modified on 22 JUN 2018 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you
Update 2 Modified on 22 JUN 2018 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you
Configuration Maximums VMware vsphere 5.0
 Topic VMware vsphere 5.0 When you select and configure your virtual and physical equipment, you must stay at or below the maximums supported by vsphere 5.0. The limits presented in the following tables
Topic VMware vsphere 5.0 When you select and configure your virtual and physical equipment, you must stay at or below the maximums supported by vsphere 5.0. The limits presented in the following tables
VMware vcloud Director for Service Providers
 Architecture Overview TECHNICAL WHITE PAPER Table of Contents Scope of Document....3 About VMware vcloud Director....3 Platform for Infrastructure Cloud...3 Architecture Overview....3 Constructs of vcloud
Architecture Overview TECHNICAL WHITE PAPER Table of Contents Scope of Document....3 About VMware vcloud Director....3 Platform for Infrastructure Cloud...3 Architecture Overview....3 Constructs of vcloud
Dedicated Hosted Cloud with vcloud Director
 VMware vcloud Architecture Toolkit for Service Providers Dedicated Hosted Cloud with vcloud Director Version 2.9 April 2018 Harold Simon 2017 VMware, Inc. All rights reserved. This product is protected
VMware vcloud Architecture Toolkit for Service Providers Dedicated Hosted Cloud with vcloud Director Version 2.9 April 2018 Harold Simon 2017 VMware, Inc. All rights reserved. This product is protected
VMware vsphere with ESX 6 and vcenter 6
 VMware vsphere with ESX 6 and vcenter 6 Course VM-06 5 Days Instructor-led, Hands-on Course Description This class is a 5-day intense introduction to virtualization using VMware s immensely popular vsphere
VMware vsphere with ESX 6 and vcenter 6 Course VM-06 5 Days Instructor-led, Hands-on Course Description This class is a 5-day intense introduction to virtualization using VMware s immensely popular vsphere
Table of Contents 1.1. Introduction. Overview of vsphere Integrated Containers 1.2
 Table of Contents Introduction Overview of vsphere Integrated Containers 1.1 1.2 2 Overview of vsphere Integrated Containers This document provides an overview of VMware vsphere Integrated Containers.
Table of Contents Introduction Overview of vsphere Integrated Containers 1.1 1.2 2 Overview of vsphere Integrated Containers This document provides an overview of VMware vsphere Integrated Containers.
Customer Onboarding with VMware NSX L2VPN Service for VMware Cloud Providers
 VMware vcloud Network VMware vcloud Architecture Toolkit for Service Providers Customer Onboarding with VMware NSX L2VPN Service for VMware Cloud Providers Version 2.8 August 2017 Harold Simon 2017 VMware,
VMware vcloud Network VMware vcloud Architecture Toolkit for Service Providers Customer Onboarding with VMware NSX L2VPN Service for VMware Cloud Providers Version 2.8 August 2017 Harold Simon 2017 VMware,
REFERENCE ARCHITECTURE. Rubrik and Nutanix
 REFERENCE ARCHITECTURE Rubrik and Nutanix TABLE OF CONTENTS INTRODUCTION - RUBRIK...3 INTRODUCTION - NUTANIX...3 AUDIENCE... 4 INTEGRATION OVERVIEW... 4 ARCHITECTURE OVERVIEW...5 Nutanix Snapshots...6
REFERENCE ARCHITECTURE Rubrik and Nutanix TABLE OF CONTENTS INTRODUCTION - RUBRIK...3 INTRODUCTION - NUTANIX...3 AUDIENCE... 4 INTEGRATION OVERVIEW... 4 ARCHITECTURE OVERVIEW...5 Nutanix Snapshots...6
vcenter Server Installation and Setup Update 1 Modified on 30 OCT 2018 VMware vsphere 6.7 vcenter Server 6.7
 vcenter Server Installation and Setup Update 1 Modified on 30 OCT 2018 VMware vsphere 6.7 vcenter Server 6.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
vcenter Server Installation and Setup Update 1 Modified on 30 OCT 2018 VMware vsphere 6.7 vcenter Server 6.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
HOW MIDSIZE ORGANIZATIONS CAN MEET COMPLIANCE REQUIREMENTS AND ENHANCE CYBERSECURITY WITH MICRO-SEGMENTATION WHITE PAPER FEBRUARY 2018
 HOW MIDSIZE ORGANIZATIONS CAN MEET COMPLIANCE REQUIREMENTS AND ENHANCE CYBERSECURITY WITH MICRO-SEGMENTATION WHITE PAPER FEBRUARY 2018 Table of Contents A short technology overview 3 How micro-segmentation
HOW MIDSIZE ORGANIZATIONS CAN MEET COMPLIANCE REQUIREMENTS AND ENHANCE CYBERSECURITY WITH MICRO-SEGMENTATION WHITE PAPER FEBRUARY 2018 Table of Contents A short technology overview 3 How micro-segmentation
What s New in VMware vsphere 4.1 Performance. VMware vsphere 4.1
 What s New in VMware vsphere 4.1 Performance VMware vsphere 4.1 T E C H N I C A L W H I T E P A P E R Table of Contents Scalability enhancements....................................................................
What s New in VMware vsphere 4.1 Performance VMware vsphere 4.1 T E C H N I C A L W H I T E P A P E R Table of Contents Scalability enhancements....................................................................
How to Use a Tomcat Stack on vcloud to Develop Optimized Web Applications. A VMware Cloud Evaluation Reference Document
 How to Use a Tomcat Stack on vcloud to Develop Optimized Web Applications A VMware Cloud Evaluation Reference Document Contents About Cloud Computing Cloud computing is an approach to computing that pools
How to Use a Tomcat Stack on vcloud to Develop Optimized Web Applications A VMware Cloud Evaluation Reference Document Contents About Cloud Computing Cloud computing is an approach to computing that pools
TECHNICAL WHITE PAPER AUGUST 2017 VMWARE APP VOLUMES 2.X DATABASE BEST PRACTICES. VMware App Volumes 2.x
 TECHNICAL WHITE PAPER AUGUST 2017 VMWARE APP VOLUMES 2.X DATABASE BEST PRACTICES VMware App Volumes 2.x Table of Contents Introduction.... 3 Database Sizing.... 4 Sizing Example 1.... 4 Sizing Example
TECHNICAL WHITE PAPER AUGUST 2017 VMWARE APP VOLUMES 2.X DATABASE BEST PRACTICES VMware App Volumes 2.x Table of Contents Introduction.... 3 Database Sizing.... 4 Sizing Example 1.... 4 Sizing Example
What s New in VMware vcloud Director 8.20
 What s New in VMware vcloud Director 8.20 Feature Overview TECHNICAL WHITE PAPER Table of Contents Introduction.... 3 Feature Updates.... 3 Advanced NSX Networking Features.... 3 Custom Role-Based Access
What s New in VMware vcloud Director 8.20 Feature Overview TECHNICAL WHITE PAPER Table of Contents Introduction.... 3 Feature Updates.... 3 Advanced NSX Networking Features.... 3 Custom Role-Based Access
WHITE PAPER SEPTEMBER 2017 VCLOUD DIRECTOR 9.0. What s New
 WHITE PAPER SEPTEMBER 2017 VCLOUD DIRECTOR 9.0 What s New Contents Summary 3 Features Update 3 Enhanced User Interface.................................................... 3 Multisite Management.......................................................
WHITE PAPER SEPTEMBER 2017 VCLOUD DIRECTOR 9.0 What s New Contents Summary 3 Features Update 3 Enhanced User Interface.................................................... 3 Multisite Management.......................................................
CASE STUDY INSIGHTS: MICRO-SEGMENTATION TRANSFORMS SECURITY. How Organizations Around the World Are Protecting Critical Data
 CASE STUDY INSIGHTS: MICRO-SEGMENTATION TRANSFORMS SECURITY How Organizations Around the World Are Protecting Critical Data The Growing Risk of Security Breaches Data center breaches are nothing new but
CASE STUDY INSIGHTS: MICRO-SEGMENTATION TRANSFORMS SECURITY How Organizations Around the World Are Protecting Critical Data The Growing Risk of Security Breaches Data center breaches are nothing new but
vsphere Upgrade Update 2 Modified on 4 OCT 2017 VMware vsphere 6.0 VMware ESXi 6.0 vcenter Server 6.0
 Update 2 Modified on 4 OCT 2017 VMware vsphere 6.0 VMware ESXi 6.0 vcenter Server 6.0 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you
Update 2 Modified on 4 OCT 2017 VMware vsphere 6.0 VMware ESXi 6.0 vcenter Server 6.0 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you
Mobile Secure Desktop Implementation with Pivot3 HOW-TO GUIDE
 Mobile Secure Desktop Implementation with Pivot3 HOW-TO GUIDE Solution Overview Purpose built to deliver a simple, scalable enterprise-class Virtual Desktop Infrastructure; Pivot3 vstac VDI appliances
Mobile Secure Desktop Implementation with Pivot3 HOW-TO GUIDE Solution Overview Purpose built to deliver a simple, scalable enterprise-class Virtual Desktop Infrastructure; Pivot3 vstac VDI appliances
VVD for Cloud Providers: Scale and Performance Guidelines. October 2018
 VVD for Cloud Providers: Scale and Performance Guidelines October 2018 2018 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws.
VVD for Cloud Providers: Scale and Performance Guidelines October 2018 2018 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws.
vrealize Production Test Upgrade Assessment Guide
 vrealize Production Test Upgrade Assessment Guide JUNE 2017 V E R S I O N 1.7. 1 Table of Contents Overview... 3 Supported Versions... 3 Prerequisites... 3 Installation... 3 Run the Full Suite of Tests
vrealize Production Test Upgrade Assessment Guide JUNE 2017 V E R S I O N 1.7. 1 Table of Contents Overview... 3 Supported Versions... 3 Prerequisites... 3 Installation... 3 Run the Full Suite of Tests
Introduction to Virtualization. From NDG In partnership with VMware IT Academy
 Introduction to Virtualization From NDG In partnership with VMware IT Academy www.vmware.com/go/academy Why learn virtualization? Modern computing is more efficient due to virtualization Virtualization
Introduction to Virtualization From NDG In partnership with VMware IT Academy www.vmware.com/go/academy Why learn virtualization? Modern computing is more efficient due to virtualization Virtualization
Migration. 22 AUG 2017 VMware Validated Design 4.1 VMware Validated Design for Software-Defined Data Center 4.1
 22 AUG 2017 VMware Validated Design 4.1 VMware Validated Design for Software-Defined Data Center 4.1 You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/
22 AUG 2017 VMware Validated Design 4.1 VMware Validated Design for Software-Defined Data Center 4.1 You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/
VMware vsphere 4. The Best Platform for Building Cloud Infrastructures
 Table of Contents Get the efficiency and low cost of cloud computing with uncompromising control over service levels and with the freedom of choice................ 3 Key Benefits........................................................
Table of Contents Get the efficiency and low cost of cloud computing with uncompromising control over service levels and with the freedom of choice................ 3 Key Benefits........................................................
VMware VMFS Volume Management VMware Infrastructure 3
 Information Guide VMware VMFS Volume Management VMware Infrastructure 3 The VMware Virtual Machine File System (VMFS) is a powerful automated file system that simplifies storage management for virtual
Information Guide VMware VMFS Volume Management VMware Infrastructure 3 The VMware Virtual Machine File System (VMFS) is a powerful automated file system that simplifies storage management for virtual
VMware Horizon FLEX 1.5 WHITE PAPER
 WHITE PAPER Table of Contents What Is VMware Horizon FLEX?... 3 Terminology for Horizon FLEX.... 4 Key Benefits of Horizon FLEX... 4 Deploying Horizon FLEX.... 5 Tested Host Operating Systems for Horizon
WHITE PAPER Table of Contents What Is VMware Horizon FLEX?... 3 Terminology for Horizon FLEX.... 4 Key Benefits of Horizon FLEX... 4 Deploying Horizon FLEX.... 5 Tested Host Operating Systems for Horizon
Hedvig as backup target for Veeam
 Hedvig as backup target for Veeam Solution Whitepaper Version 1.0 April 2018 Table of contents Executive overview... 3 Introduction... 3 Solution components... 4 Hedvig... 4 Hedvig Virtual Disk (vdisk)...
Hedvig as backup target for Veeam Solution Whitepaper Version 1.0 April 2018 Table of contents Executive overview... 3 Introduction... 3 Solution components... 4 Hedvig... 4 Hedvig Virtual Disk (vdisk)...
Managing Performance Variance of Applications Using Storage I/O Control
 Performance Study Managing Performance Variance of Applications Using Storage I/O Control VMware vsphere 4.1 Application performance can be impacted when servers contend for I/O resources in a shared storage
Performance Study Managing Performance Variance of Applications Using Storage I/O Control VMware vsphere 4.1 Application performance can be impacted when servers contend for I/O resources in a shared storage
REVISED 6 NOVEMBER 2018 COMPONENT DESIGN: UNIFIED ACCESS GATEWAY ARCHITECTURE
 REVISED 6 NOVEMBER 2018 COMPONENT DESIGN: UNIFIED ACCESS GATEWAY ARCHITECTURE Table of Contents Component Design: Unified Access Gateway Architecture Design Overview Network Deployment Options Authentication
REVISED 6 NOVEMBER 2018 COMPONENT DESIGN: UNIFIED ACCESS GATEWAY ARCHITECTURE Table of Contents Component Design: Unified Access Gateway Architecture Design Overview Network Deployment Options Authentication
VMware Virtual SAN Backup Using VMware vsphere Data Protection Advanced SEPTEMBER 2014
 VMware SAN Backup Using VMware vsphere Data Protection Advanced SEPTEMBER 2014 VMware SAN Backup Using VMware vsphere Table of Contents Introduction.... 3 vsphere Architectural Overview... 4 SAN Backup
VMware SAN Backup Using VMware vsphere Data Protection Advanced SEPTEMBER 2014 VMware SAN Backup Using VMware vsphere Table of Contents Introduction.... 3 vsphere Architectural Overview... 4 SAN Backup
vsphere Upgrade Guide
 ESX 4.0 ESXi 4.0 vcenter Server 4.0 vsphere Client 4.0 EN-000112-00 You can find the most up-to-date technical documentation on the VMware Web site at: http://www.vmware.com/support/ The VMware Web site
ESX 4.0 ESXi 4.0 vcenter Server 4.0 vsphere Client 4.0 EN-000112-00 You can find the most up-to-date technical documentation on the VMware Web site at: http://www.vmware.com/support/ The VMware Web site
CONFIDENTLY INTEGRATE VMWARE CLOUD ON AWS WITH INTELLIGENT OPERATIONS
 SOLUTION OVERVIEW CONFIDENTLY INTEGRATE VMWARE WITH INTELLIGENT OPERATIONS VMware Cloud TM on AWS brings VMware s enterprise class Software-Defined Data Center (SDDC) software to the AWS Cloud, with optimized
SOLUTION OVERVIEW CONFIDENTLY INTEGRATE VMWARE WITH INTELLIGENT OPERATIONS VMware Cloud TM on AWS brings VMware s enterprise class Software-Defined Data Center (SDDC) software to the AWS Cloud, with optimized
VMWARE PROTECTION WITH DELL EMC NETWORKER 9
 VMWARE PROTECTION WITH DELL EMC NETWORKER 9 Solution Overview ABSTRACT This white paper describes the integration of Dell EMC NetWorker with VMware vcenter. It also includes details on the NetWorker architecture
VMWARE PROTECTION WITH DELL EMC NETWORKER 9 Solution Overview ABSTRACT This white paper describes the integration of Dell EMC NetWorker with VMware vcenter. It also includes details on the NetWorker architecture
Microsoft E xchange 2010 on VMware
 : Microsoft E xchange 2010 on VMware Availability and R ecovery Options This product is protected by U.S. and international copyright and intellectual property laws. This product is covered by one or more
: Microsoft E xchange 2010 on VMware Availability and R ecovery Options This product is protected by U.S. and international copyright and intellectual property laws. This product is covered by one or more
Table of Contents 1.1. Overview. Containers, Docker, Registries vsphere Integrated Containers Engine
 Table of Contents Overview Containers, Docker, Registries vsphere Integrated Containers Engine Management Portal Registry Roles and Personas 1.1 1.1.1 1.1.2 1.1.2.1 1.1.2.2 1.1.2.3 1.1.2.4 2 Overview of
Table of Contents Overview Containers, Docker, Registries vsphere Integrated Containers Engine Management Portal Registry Roles and Personas 1.1 1.1.1 1.1.2 1.1.2.1 1.1.2.2 1.1.2.3 1.1.2.4 2 Overview of
10 QUESTIONS, 10 ANSWERS. Get to know VMware Cloud on AWS The Best-in-Class Hybrid Cloud Service
 10 QUESTIONS, 10 ANSWERS Get to know VMware Cloud on AWS The Best-in-Class Hybrid Cloud Service GET TO KNOW VMWARE CLOUD ON AWS: THE BEST-IN-CLASS HYBRID CLOUD SERVICE IT leaders focused on finding ways
10 QUESTIONS, 10 ANSWERS Get to know VMware Cloud on AWS The Best-in-Class Hybrid Cloud Service GET TO KNOW VMWARE CLOUD ON AWS: THE BEST-IN-CLASS HYBRID CLOUD SERVICE IT leaders focused on finding ways
Setup for Microsoft Cluster Service Update 1 Release for ESX Server 3.5, ESX Server 3i version 3.5, VirtualCenter 2.5
 Setup for Microsoft Cluster Service Update 1 Release for ESX Server 3.5, ESX Server 3i version 3.5, VirtualCenter 2.5 Setup for Microsoft Cluster Service Setup for Microsoft Cluster Service Revision: 041108
Setup for Microsoft Cluster Service Update 1 Release for ESX Server 3.5, ESX Server 3i version 3.5, VirtualCenter 2.5 Setup for Microsoft Cluster Service Setup for Microsoft Cluster Service Revision: 041108
8 TIPS FOR A SUCCESSFUL UPGRADE TO vsphere 6.5. Stay in the Know with These Expert Suggestions
 8 TIPS FOR A SUCCESSFUL UPGRADE TO vsphere 6.5 Stay in the Know with These Expert Suggestions The Digital Future Has Arrived Spurred by major advancements in technology and growing end-user demands, the
8 TIPS FOR A SUCCESSFUL UPGRADE TO vsphere 6.5 Stay in the Know with These Expert Suggestions The Digital Future Has Arrived Spurred by major advancements in technology and growing end-user demands, the
Debunking the Top 10 Cloud-Hosted Desktop Myths
 Debunking the Top 10 Cloud-Hosted Desktop Myths Page 1 Summary Desktops as a Service (DaaS) is the delivery of a virtual desktop offered as a hosted service by a service provider. DaaS has the potential
Debunking the Top 10 Cloud-Hosted Desktop Myths Page 1 Summary Desktops as a Service (DaaS) is the delivery of a virtual desktop offered as a hosted service by a service provider. DaaS has the potential
Certified Reference Design for VMware Cloud Providers
 VMware vcloud Architecture Toolkit for Service Providers Certified Reference Design for VMware Cloud Providers Version 2.5 August 2018 2018 VMware, Inc. All rights reserved. This product is protected by
VMware vcloud Architecture Toolkit for Service Providers Certified Reference Design for VMware Cloud Providers Version 2.5 August 2018 2018 VMware, Inc. All rights reserved. This product is protected by
Protecting Mission-Critical Workloads with VMware Fault Tolerance W H I T E P A P E R
 Protecting Mission-Critical Workloads with VMware Fault Tolerance W H I T E P A P E R Table of Contents Fault Tolerance and Virtualization... 3 Fault Tolerance in the Physical World... 3 VMware Fault Tolerance...
Protecting Mission-Critical Workloads with VMware Fault Tolerance W H I T E P A P E R Table of Contents Fault Tolerance and Virtualization... 3 Fault Tolerance in the Physical World... 3 VMware Fault Tolerance...
Setup for Failover Clustering and Microsoft Cluster Service
 Setup for Failover Clustering and Microsoft Cluster Service Update 1 ESXi 5.0 vcenter Server 5.0 This document supports the version of each product listed and supports all subsequent versions until the
Setup for Failover Clustering and Microsoft Cluster Service Update 1 ESXi 5.0 vcenter Server 5.0 This document supports the version of each product listed and supports all subsequent versions until the
TECHNICAL WHITE PAPER - MAY 2017 MULTI DATA CENTER POOLING WITH NSX WHITE PAPER
 TECHNICAL WHITE PAPER - MAY 2017 MULTI DATA CENTER POOLING WITH NSX WHITE PAPER Table of Contents Executive Summary 3 NSX with vsphere Metro Storage Cluster (vmsc) 4 Cross-VC NSX 6 Layer 2 VPN (L2VPN)
TECHNICAL WHITE PAPER - MAY 2017 MULTI DATA CENTER POOLING WITH NSX WHITE PAPER Table of Contents Executive Summary 3 NSX with vsphere Metro Storage Cluster (vmsc) 4 Cross-VC NSX 6 Layer 2 VPN (L2VPN)
Administering VMware vsphere and vcenter 5
 Administering VMware vsphere and vcenter 5 Course VM-05 5 Days Instructor-led, Hands-on Course Description This 5-day class will teach you how to master your VMware virtual environment. From installation,
Administering VMware vsphere and vcenter 5 Course VM-05 5 Days Instructor-led, Hands-on Course Description This 5-day class will teach you how to master your VMware virtual environment. From installation,
Understanding Data Locality in VMware Virtual SAN
 Understanding Data Locality in VMware Virtual SAN July 2014 Edition T E C H N I C A L M A R K E T I N G D O C U M E N T A T I O N Table of Contents Introduction... 2 Virtual SAN Design Goals... 3 Data
Understanding Data Locality in VMware Virtual SAN July 2014 Edition T E C H N I C A L M A R K E T I N G D O C U M E N T A T I O N Table of Contents Introduction... 2 Virtual SAN Design Goals... 3 Data
VMware - VMware vsphere: Install, Configure, Manage [V6.7]
![VMware - VMware vsphere: Install, Configure, Manage [V6.7] VMware - VMware vsphere: Install, Configure, Manage [V6.7]](/thumbs/93/112437773.jpg) VMware - VMware vsphere: Install, Configure, Manage [V6.7] Code: Length: URL: EDU-VSICM67 5 days View Online This five-day course features intensive hands-on training that focuses on installing, configuring,
VMware - VMware vsphere: Install, Configure, Manage [V6.7] Code: Length: URL: EDU-VSICM67 5 days View Online This five-day course features intensive hands-on training that focuses on installing, configuring,
VMWARE HORIZON CLOUD SERVICE HOSTED INFRASTRUCTURE ONBOARDING SERVICE SILVER
 DATASHEET VMWARE HORIZON CLOUD SERVICE HOSTED INFRASTRUCTURE ONBOARDING SERVICE SILVER AT A GLANCE The VMware Horizon Cloud Service Hosted Infrastructure Onboarding Service Silver provides basic assistance
DATASHEET VMWARE HORIZON CLOUD SERVICE HOSTED INFRASTRUCTURE ONBOARDING SERVICE SILVER AT A GLANCE The VMware Horizon Cloud Service Hosted Infrastructure Onboarding Service Silver provides basic assistance
