The Solution Requirements and considerations
|
|
|
- Alaina Lynch
- 6 years ago
- Views:
Transcription
1 Annex A TERMS OF REFERENCE Virtual Private Network (VPN) tunnel installation and Very Small Aperture Terminal (VSAT) internet connectivity for Migration Information and Data Analysis Systems (MIDAS) at ports of entry in Somalia Introduction Since 2007, the International Organization for Migration (IOM) has been assisting Somalia in strengthening its Immigration and border management in order to promote safe migration and mitigate security threats. In partnership with Departments of Immigration in Somalia, IOM has been supporting the upgrade of infrastructure and equipment at the various ports of entry, review of Immigration legislation and policy, organization capacity development, support to Inter-agency /regional cooperation and Border Information Management (BIM) through installation of Migration Information and Data Analysis Systems (MIDAS). The MIDAS Software has been designed by IOM to enable States with no or inadequate data capture system to equip themselves and have the operational means to take up the challenge of enhanced migration management. The system enables to collect, process and store travellers information, including bio-data, at entry and exit border points, for the purpose of idenfication, authentication, data collection and analysis. It contributes to better monitor border movements but also shape reactive migration and border management policies. To date thirteen ports of entry in Somalia have the system installed with an increased need to reach more ports OF entry thus, the need for enhanced connectivity at all the ports of entry to ensure timely and safe data exchange and back-up on central servers for maximum security at the ports of entry in Somalia thereby mitigating any security threats. To achieve this IOM, wishes to engage the services of a competent internet service provider /solutions company in Somalia with the right capacity to install a VPN tunnel and provide a VSAT internet for connectivity of the MIDAS at the various ports of entry with a readily available 24/7 technical client support services. Headquarters: 17 route des Morillons C.P. 71 CH-1211 Geneva 19 Switzerland Tel: Fax: hq@iom.int Internet:
2 2 Objective: To provide a VPN Connectivity and VSAT Internet Service to ports of entries with MIDAS in FGoS (Federal Government of Somalia) and Puntland state Departments of Immigration. Target: The project targets connectivity of 8 ports of entries in FGoS and Puntland state Immigration Departments already using MIDAS. The Proposed Technical Connectivity Solution The proposed solution should enhance reliable communications between Immigration headquarters and remote sites with maximum availability throughout using internet cloud with a remote VPN connection that provides remote access to the end users, through a private network, each remote user or station can directly access the headquarter network without any congestion or restriction using the internet cloud, secure VPN tunneling will encrypt all requests from the remote access point to provide encryption between the remote stations and the headquarter, the below approaches are vital: a) Either using a satellite VSAT connection for each remote site/port of entry b) Or an existing Internet infrastructure, depending on the bandwidth requirement for each station, many employees can access the VPN simultaneously. The Solution Requirements and considerations a) Firewall- Cisco IOS Firewall helps ensure your networks availability and the security of department's resources by protecting any network threats - and application-layer attacks. The VPN configuration and policies should be configured in the firewall to filter any packets outside and inside the network. Less resources of equipment will be used as the network scale is small and in the near future will be upgraded into medium and large scale infrastructure. b) Router- Cisco IOS router will be used at the HQ to provide any routing requirements inside the headquarter and enhance the packet forwarding between stations, this router can be eliminated using a layer 3 switch depending on the number of employees inside the headquarter, provide a full control of packet filtering and path selection to minimize the tcp/ip overhead. c) Switches- Layer 3 cisco switches will be used in each remote station for their local network to help increase the performance of packet forwarding, and more connection reliability to the VPN access, all the work stations will be connected to this switch and can simultaneously access the network without any delay.
3 3 Figure 1. On VPN Design topology using local ISP Connections The solution should be capable of the following in addition to the basic WAN connectivity and ability to access the headquarter but also provide: a) Extend geographical connectivity b) Reduce operational costs versus traditional WANs c) Reduce transit times and traveling costs for remote users d) Improve productivity e) Simplify network topology The features needed in a well-designed VPN should incorporate these items: a) Security b) Reliability c) Scalability d) Network Management e) Policy Management Based on the type of VPN (remote-access), you need to put in place certain components to build your VPN. These might include: a) Desktop software client for each remote user b) Dedicated hardware such as a Cisco VPN Concentrator or a Cisco Secure Firewall c) Dedicated VPN server for dial-up services / Firewall or router
4 Duties and Responsibilities: 4 Under the overall supervision of IOM Somalia Chief of Mission (COM) and the direct supervision of the IBM (Immigration and Border Management) Project Manager IBM (PM), the contracted firm will be responsible for the following duties and tasks. 1) Develop and create a VPN tunnel between the ports of entry locations and also provide a Support management of VPN Services. 2) The VPN must have a layer two tunnelling Protocol/Internet Protocol security (L2TP/IPSec) over an intermediate network. 3) All necessary hardware, cabling and software (if required for Internet service) should be provided and set up by the contractor 4) Free and unlimited technical support to the VPN system installed 5) Free and unlimited technical support to the VPN system installed 6) The selected contractor must provide weekly reports on network performance, utilization and usage analysis. 7) The contractor must undertake the responsibility of the Internet connection and also have an especial internet backup for the VPN connection, which will be used when there is no an Internet for whole. 8) Install site-to-site VPN connections to enable immigration departments have routed connections between separate offices or with one to another point of entry over a public network while helping to maintain secure communications. 9) Installation of VSAT connection for supporting the broadband internet connection between the points of entry for the immigration Departments in FGoS and Puntland 10) Establish a permanent monitoring system in conjunction with the technical supervisor on each site in order to ensure provision of a dedicated bandwidth required and a stable Internet connection; such system should be accessible. 11) Establish 2 or 3 technical repair teams, capable of a rapid intervention on any site at the ports of entry 12) Set up a help desk service available to the client 24/7 and provide all necessary information on such service. 13) Training of immigration IT officers and IOM-IT staff in each site with regards to the operation of the system and operational support arrangements. This training should take place as part of the installation of maintenance system. As an additional option, the contractor should also offer a more specialized training on the connectivity and VSAT solution, with a possibility of certifying IOM technical personnel in the VSAT and the connectivity system. 14) All administrative and logistics support involved with the maintenance of this network and connectivity will be responsibility of the service provider for the next six months after installation. 15) The Contractor is responsible for ensuring that all necessary items are appropriately insured against all risks including damage caused by fire, flood and lightning strikes in respect of its property and any equipment used in the execution of the service. 16) The Contractor must be a telecommunication company or Internet Service Provider who owns and operates the internet facilities starting from the local loop up to the internet gateway, and also can cover all areas in Somalia in FGoS and Puntland state.
5 5 17) The Connection should have a 24-hours-per-day, 7 days-per-week access. Deliverables: 1) An accurate assessment of the current capacity and structure and concrete recommendations to improve the connectivity system at the all ports of entry. 2) Install internet connectivity with VPN tunnels at the ports of entry in Puntland and FGoS 3) Install VSAT connection for supporting the broadband internet connection between the ports of entry 4) Set up a help desk service available to the client 24/7 and provide all necessary information on such service. 5) A perfect development of the current capacity and structure and concrete recommendations to improve the connectivity issues between the points of entry at FGoS and Puntland 6) Training of immigration IT officers and IOM-IT staff in each site with regards to the operation of the system and operational support arrangements 7) Provide technical support for regional networks and regional events Time schedules of Deliverables The company will be responsible for coordinating work with appointed technical team in order to achieve greater efficiency in the ports of entry connectivity system enhancement. 1) The installation of the VPN connectivity system to all ports of entry will be done after and up to within 30 days upon signature of the contract. 2) Installation of the VSAT internet services will be done at all the ports of entry to within and up to 45 days 3) All installation works should be accomplished and connection launched within 90 days days after the signing of the Contract. 4) The Connection should have a redundant connectivity which ensures 100% network availability. 5) Effective and efficient communication and connectivity/network design between 8 ports of entry completed within 90days
6 6 Hardware and Software Requirements for VPN Installation/Configuration No. Device Name Description Qty 1. Cisco Router CISCO2951-SEC/K9,Security Bundle w/sec license PAK 2 2. Cisco Switch (WS- Cisco Catalyst 3560-C Switch 8 GE, 2 x Dual Purpose 7 C3560CG-8TC-S ) Uplink, IP Base 3. Cisco Firewall Cisco ASA 5505; with Security bundle 2 4. VSAT 1.8M, Azimuth , elevation 1 0 ~80 0, Relative Humidity 100% 7 No. Tasks on Installation and Configurations Quantity 1. Installing Power Backups, inverters All Ports of Entry 2. Installing Cisco Router, Switch and Firewall. All Ports of Entry 3. Basic Configuration of Router, Switch and Firewall. All Ports of Entry 4. Installing and enabling security bundles in firewall and Cisco All Ports of Entry router. 5. Configuring VPN Tunnels for the remote users. All Ports of Entry 6. Configuring IP security to provide 3des 256 encryption key. All Ports of Entry 7. Configuring Remote VPN with Public IP Address. All Ports of Entry 8. Testing and verifying configurations All Ports of Entry 9. Installing VSAT All Ports of Entry 10. Training of IT technical staff All Ports of Entry For consulting firms/companies participating in the call for proposals, provide the following: Provide an outline of technical and financial proposal including proposed methodology, time schedule and work plan for the consultancy; Company Profile (including the names of owners, key officers, technical personnel attached to this project with their relevant CV s) Company's Articles of Incorporation, Partnership or Corporation, whichever is applicable, including amendments thereto, if any. Certificate of Registration from host country's Security & Exchange Commission or similar government agency/department/ministry Valid Government Permits/Licenses in Somalia Audited Financial/Bank Statements for the last 3 years Certificates from the Principals (e.g. Manufacturer's Authorization, Certificate of Exclusive Distributorship, Any certificate for the purpose, indicating name, complete address and contact details) List of contracts entered into for the last 3 years(indicate whether completed or ongoing) in related works Organizational Structure / Organogram CVs of Key technical Staff Detailed proposal for the work with clear implementation framework
7 7 A. Data, Local Services, Personnel and Facilities to be provided by IOM a) IOM Somalia Nairobi coordination offices will conduct a briefing to Service provider/consulting firm at the beginning of the contract. b) The payment to the service providers/consulting firms is all inclusive. The expenses shouldered if any by IOM, through facilitation of IOM for air travels to, local transport and accommodation in Somalia will be deducted from the final payment to the contracted firm.
CITY OF MONTEBELLO SYSTEMS MANAGER
 CITY OF MONTEBELLO 109A DEFINITION Under general administrative direction of the City Administrator, provides advanced professional support to departments with very complex computer systems, programs and
CITY OF MONTEBELLO 109A DEFINITION Under general administrative direction of the City Administrator, provides advanced professional support to departments with very complex computer systems, programs and
Cisco How Virtual Private Networks Work
 Table of Contents How Virtual Private Networks Work...1 Introduction...1 Before You Begin...1 Conventions...1 Prerequisites...1 Components Used...1 Background Information...1 What Makes a VPN?...2 Analogy:
Table of Contents How Virtual Private Networks Work...1 Introduction...1 Before You Begin...1 Conventions...1 Prerequisites...1 Components Used...1 Background Information...1 What Makes a VPN?...2 Analogy:
UNITED NATIONS DEVELOPMENT PROGRAMME TERMS OF REFERENCE
 UNITED NATIONS DEVELOPMENT PROGRAMME TERMS OF REFERENCE 1. Consultancy Information Title: Location: Application Deadline: Type of Contract: Languages Required: Duration of Contract: ICT Infrastructure
UNITED NATIONS DEVELOPMENT PROGRAMME TERMS OF REFERENCE 1. Consultancy Information Title: Location: Application Deadline: Type of Contract: Languages Required: Duration of Contract: ICT Infrastructure
SPECIFIC PROCUREMENT NOTICE IT SERVICES
 SPECIFIC PROCUREMENT NOTICE IT SERVICES Funding source: Sector: Asian Infrastructure Investment Bank (AIIB) Information Technology Project Name: On-site IT Security Service Project No. AIIB CP - 00043
SPECIFIC PROCUREMENT NOTICE IT SERVICES Funding source: Sector: Asian Infrastructure Investment Bank (AIIB) Information Technology Project Name: On-site IT Security Service Project No. AIIB CP - 00043
E-Commerce. Infrastructure I: Computer Networks
 E-Commerce Infrastructure I: Computer Networks Almost all computers today are networked or part of a distributed system. I will provide an overview of networking and a basic description of network technology.
E-Commerce Infrastructure I: Computer Networks Almost all computers today are networked or part of a distributed system. I will provide an overview of networking and a basic description of network technology.
IP VPn COMMITTED TO QUALITY
 IP VPn COMMITTED TO QUALITY Intraselect THE RIGHT SERVICE FOR ALL AND ANY REQUIREMENTS CONNECTIVITY TAILORED TO YOUR BUSINESS Businesses face an array of connectivity challenges. They need high bandwidth
IP VPn COMMITTED TO QUALITY Intraselect THE RIGHT SERVICE FOR ALL AND ANY REQUIREMENTS CONNECTIVITY TAILORED TO YOUR BUSINESS Businesses face an array of connectivity challenges. They need high bandwidth
VMware vcloud Air Accelerator Service
 DATASHEET AT A GLANCE The VMware vcloud Air Accelerator Service assists customers with extending their private VMware vsphere environment to a VMware vcloud Air public cloud. This Accelerator Service engagement
DATASHEET AT A GLANCE The VMware vcloud Air Accelerator Service assists customers with extending their private VMware vsphere environment to a VMware vcloud Air public cloud. This Accelerator Service engagement
ON-LINE EXPERT SUPPORT THROUGH VPN ACCESS
 ON-LINE EXPERT SUPPORT THROUGH VPN ACCESS P. Fidry, V. Rakotomanana, C. Ausanneau Pierre.fidry@alcatel-lucent.fr Alcatel-Lucent, Centre de Villarceaux, 91620, Nozay, France Abstract: As a consequence of
ON-LINE EXPERT SUPPORT THROUGH VPN ACCESS P. Fidry, V. Rakotomanana, C. Ausanneau Pierre.fidry@alcatel-lucent.fr Alcatel-Lucent, Centre de Villarceaux, 91620, Nozay, France Abstract: As a consequence of
RFP Annex A Terms of Reference UNHCR HQ Data Centre Colocation Service
 RFP 2017 845 Annex A Terms of Reference UNHCR HQ Data Centre Colocation Service Version 1 Contents Project objectives... 1 Background... 1 Scope... 1 Timeframe and Cost... 4 Stakeholders, roles and responsibilities...
RFP 2017 845 Annex A Terms of Reference UNHCR HQ Data Centre Colocation Service Version 1 Contents Project objectives... 1 Background... 1 Scope... 1 Timeframe and Cost... 4 Stakeholders, roles and responsibilities...
Exam: : VPN/Security. Ver :
 Exam: Title : VPN/Security Ver : 03.20.04 QUESTION 1 A customer needs to connect smaller branch office locations to its central site and desires a more which solution should you recommend? A. V3PN solution
Exam: Title : VPN/Security Ver : 03.20.04 QUESTION 1 A customer needs to connect smaller branch office locations to its central site and desires a more which solution should you recommend? A. V3PN solution
Responsible Officer Approved by
 Responsible Officer Approved by Chief Information Officer Council Approved and commenced August, 2014 Review by August, 2017 Relevant Legislation, Ordinance, Rule and/or Governance Level Principle ICT
Responsible Officer Approved by Chief Information Officer Council Approved and commenced August, 2014 Review by August, 2017 Relevant Legislation, Ordinance, Rule and/or Governance Level Principle ICT
Connected Health Principles
 Version 2.1 Table of Contents 1 INTRODUCTION... 1 2 TERMINOLOGY... 1 3 CONNECTED HEALTH PRINCIPLES... 4 3.1 CONNECTED HEALTH FOUNDATION PRINCIPLES...5 3.2 CONNECTED HEALTH ARCHITECTURAL PRINCIPLES... 6
Version 2.1 Table of Contents 1 INTRODUCTION... 1 2 TERMINOLOGY... 1 3 CONNECTED HEALTH PRINCIPLES... 4 3.1 CONNECTED HEALTH FOUNDATION PRINCIPLES...5 3.2 CONNECTED HEALTH ARCHITECTURAL PRINCIPLES... 6
BREITKOM Network Sdn Bhd Corporate Profile
 BREITKOM Network Sdn Bhd Corporate Profile ICT Connectivity, Solutions and Provision 1 AGENDA BREITKOM Network Sdn Bhd Corporate Overview Our Products & Services Telco Products & Solutions Our Services
BREITKOM Network Sdn Bhd Corporate Profile ICT Connectivity, Solutions and Provision 1 AGENDA BREITKOM Network Sdn Bhd Corporate Overview Our Products & Services Telco Products & Solutions Our Services
Introduction to SURE
 Introduction to SURE Contents 1. Introduction... 3 2. What is SURE?... 4 3. Aim and objectives of SURE... 4 4. Overview of the facility... 4 5. SURE operations and design... 5 5.1 Logging on and authentication...
Introduction to SURE Contents 1. Introduction... 3 2. What is SURE?... 4 3. Aim and objectives of SURE... 4 4. Overview of the facility... 4 5. SURE operations and design... 5 5.1 Logging on and authentication...
Security
 Security +617 3222 2555 info@citec.com.au Security With enhanced intruder technologies, increasingly sophisticated attacks and advancing threats, your data has never been more susceptible to breaches from
Security +617 3222 2555 info@citec.com.au Security With enhanced intruder technologies, increasingly sophisticated attacks and advancing threats, your data has never been more susceptible to breaches from
INFORMATION SECURITY. One line heading. > One line subheading. A briefing on the information security controls at Computershare
 INFORMATION SECURITY A briefing on the information security controls at Computershare One line heading > One line subheading INTRODUCTION Information is critical to all of our clients and is therefore
INFORMATION SECURITY A briefing on the information security controls at Computershare One line heading > One line subheading INTRODUCTION Information is critical to all of our clients and is therefore
Policy. London School of Economics & Political Science. Remote Access Policy. IT Services. Jethro Perkins. Information Security Manager.
 London School of Economics & Political Science IT Services Policy Remote Access Policy Jethro Perkins Information Security Manager Summary This document outlines the controls from ISO27002 that relate
London School of Economics & Political Science IT Services Policy Remote Access Policy Jethro Perkins Information Security Manager Summary This document outlines the controls from ISO27002 that relate
Water Provider Relocates, Modernizes Data Center
 : mission-critical services and Cisco engaged to lead data of 260 servers and 60 community of employees and partners. The most vital are those associated service. It was important for us to maintain the
: mission-critical services and Cisco engaged to lead data of 260 servers and 60 community of employees and partners. The most vital are those associated service. It was important for us to maintain the
ITG. Information Security Management System Manual
 ITG Information Security Management System Manual This manual describes the ITG Information Security Management system and must be followed closely in order to ensure compliance with the ISO 27001:2005
ITG Information Security Management System Manual This manual describes the ITG Information Security Management system and must be followed closely in order to ensure compliance with the ISO 27001:2005
Guidelines. Technical and Financial Support. State Wide Area Network (SWAN)
 No. 1(3)/2004-EGD Guidelines For Technical and Financial Support For Establishment Of State Wide Area Network (SWAN) 20 th October, 2004 Department of Information Technology, Govt. of India, Electronics
No. 1(3)/2004-EGD Guidelines For Technical and Financial Support For Establishment Of State Wide Area Network (SWAN) 20 th October, 2004 Department of Information Technology, Govt. of India, Electronics
Cyber Security Requirements for Electronic Safety and Security
 This document is to provide suggested language to address cyber security elements as they may apply to physical and electronic security projects. Security consultants and specifiers should consider this
This document is to provide suggested language to address cyber security elements as they may apply to physical and electronic security projects. Security consultants and specifiers should consider this
AppPulse Point of Presence (POP)
 AppPulse Point of Presence Micro Focus AppPulse POP service is a remotely delivered solution that provides a managed environment of Application Performance Management. AppPulse POP service supplies real-time
AppPulse Point of Presence Micro Focus AppPulse POP service is a remotely delivered solution that provides a managed environment of Application Performance Management. AppPulse POP service supplies real-time
POSITION DESCRIPTION
 POSITION DESCRIPTION Engagement Manager Unit/Branch, Directorate: Location: Outreach & Engagement, Information Assurance and Cyber Security Directorate Auckland Salary range: H $77,711 - $116,567 Purpose
POSITION DESCRIPTION Engagement Manager Unit/Branch, Directorate: Location: Outreach & Engagement, Information Assurance and Cyber Security Directorate Auckland Salary range: H $77,711 - $116,567 Purpose
IT Managed Services. Schedule 1 Specification 11/07/18
 ` IT Managed Services Schedule 1 Specification 11/07/18 IT Managed Service ITT Schedule 1 Specification Table of Contents 1.0 Introduction... 2 1.1 Overview... 2 2.0 Scope... 2 3.0 Vendor Response Requirements...
` IT Managed Services Schedule 1 Specification 11/07/18 IT Managed Service ITT Schedule 1 Specification Table of Contents 1.0 Introduction... 2 1.1 Overview... 2 2.0 Scope... 2 3.0 Vendor Response Requirements...
Cisco Data Center Accelerated Deployment Service for Nexus 9000 (ASF-DCV1-NEX-ADS)
 Page 1 of 6 Service Description: Advanced Services Fixed Price Cisco Data Center Accelerated Deployment Service for Nexus 9000 (ASF-DCV1-NEX-ADS) This document describes Advanced Services Fixed Price:
Page 1 of 6 Service Description: Advanced Services Fixed Price Cisco Data Center Accelerated Deployment Service for Nexus 9000 (ASF-DCV1-NEX-ADS) This document describes Advanced Services Fixed Price:
Campus Network Design
 Design Principles Campus Network Design 2003, Cisco Systems, Inc. All rights reserved. 2-1 2003, Cisco Systems, Inc. All rights reserved. BCMSN v2.0 2-2 Design Principles Task in Network Design Plan phase
Design Principles Campus Network Design 2003, Cisco Systems, Inc. All rights reserved. 2-1 2003, Cisco Systems, Inc. All rights reserved. BCMSN v2.0 2-2 Design Principles Task in Network Design Plan phase
NATO. 1. Course Title. DCIS ComS Foundation (Online) 2. Identification Number (ID) 3. Purpose of the Course
 Communications and 1. Course Title Version 1.0 dated 18 May 2016 DCIS ComS Foundation (Online) 2. Identification Number (ID) 964 3. Purpose of the Course The purpose of this blended distance learning course
Communications and 1. Course Title Version 1.0 dated 18 May 2016 DCIS ComS Foundation (Online) 2. Identification Number (ID) 964 3. Purpose of the Course The purpose of this blended distance learning course
Reaping the Benefits of Managed Services
 Figure 1. Converged Network with Managed Services These services complement each other when bundled together. For example, an IP VPN service makes managing an IP voice network simpler and more effective
Figure 1. Converged Network with Managed Services These services complement each other when bundled together. For example, an IP VPN service makes managing an IP voice network simpler and more effective
PASS4TEST. IT Certification Guaranteed, The Easy Way! We offer free update service for one year
 PASS4TEST IT Certification Guaranteed, The Easy Way! \ We offer free update service for one year Exam : 640-861 Title : CCDA Cisco Certified Design Associate Vendors : Cisco Version : DEMO Get Latest &
PASS4TEST IT Certification Guaranteed, The Easy Way! \ We offer free update service for one year Exam : 640-861 Title : CCDA Cisco Certified Design Associate Vendors : Cisco Version : DEMO Get Latest &
Call for Expressions of Interest
 Call for Expressions of Interest ENISA M/CEI/17/T01 Experts for assisting in the implementation of the annual ENISA Work Programme TECHNICAL DESCRIPTION CONTENTS TECHNICAL DESCRIPTION... 3 1. INTRODUCTION...
Call for Expressions of Interest ENISA M/CEI/17/T01 Experts for assisting in the implementation of the annual ENISA Work Programme TECHNICAL DESCRIPTION CONTENTS TECHNICAL DESCRIPTION... 3 1. INTRODUCTION...
Version 1/2018. GDPR Processor Security Controls
 Version 1/2018 GDPR Processor Security Controls Guidance Purpose of this document This document describes the information security controls that are in place by an organisation acting as a processor in
Version 1/2018 GDPR Processor Security Controls Guidance Purpose of this document This document describes the information security controls that are in place by an organisation acting as a processor in
Request for Proposal. I. Introduction. II. Scope of Work. IT Managed Services Support. IT Environment. Main Facility
 Request for Proposal IT Managed Services Support I. Introduction The Hoh Indian Tribe ( Tribe or Hoh Tribe ) is located in western Washington State in Jefferson County, 28 miles South of Forks, Washington.
Request for Proposal IT Managed Services Support I. Introduction The Hoh Indian Tribe ( Tribe or Hoh Tribe ) is located in western Washington State in Jefferson County, 28 miles South of Forks, Washington.
Automate sharing. Empower users. Retain control. Utilizes our purposebuilt cloud, not public shared clouds
 EXECUTIVE BRIEF SHAREBASE BY HYLAND Automate sharing. Empower users. Retain control. With ShareBase by Hyland, empower users with enterprise file sync and share (EFSS) technology and retain control over
EXECUTIVE BRIEF SHAREBASE BY HYLAND Automate sharing. Empower users. Retain control. With ShareBase by Hyland, empower users with enterprise file sync and share (EFSS) technology and retain control over
Service Description: CNS Federal High Touch Technical Support
 Page 1 of 1 Service Description: CNS Federal High Touch Technical Support This service description ( Service Description ) describes Cisco s Federal High Touch Technical support (CNS-HTTS), a tier 2 in
Page 1 of 1 Service Description: CNS Federal High Touch Technical Support This service description ( Service Description ) describes Cisco s Federal High Touch Technical support (CNS-HTTS), a tier 2 in
Community Development Commission of the County of Los Angeles
 VDI (Virtual Desktop Infrastructure) Implementation 2018 NACo Achievement Awards 1. Abstract of the Program. (~200 words or less). Summarize the program include the program description, the purpose, and
VDI (Virtual Desktop Infrastructure) Implementation 2018 NACo Achievement Awards 1. Abstract of the Program. (~200 words or less). Summarize the program include the program description, the purpose, and
ISO/IEC INTERNATIONAL STANDARD
 INTERNATIONAL STANDARD ISO/IEC 27006 Second edition 2011-12-01 Information technology Security techniques Requirements for bodies providing audit and certification of information security management systems
INTERNATIONAL STANDARD ISO/IEC 27006 Second edition 2011-12-01 Information technology Security techniques Requirements for bodies providing audit and certification of information security management systems
SERVICE DESCRIPTION DEDICATED SERVER
 Contents Service Overview.... 3 Key Features... 3 Implementation... 4 Validation... 4 Implementation Process.... 4 Internal Kick-Off... 4 Customer Kick-Off... 5 Provisioning & Testing.... 5 Billing....
Contents Service Overview.... 3 Key Features... 3 Implementation... 4 Validation... 4 Implementation Process.... 4 Internal Kick-Off... 4 Customer Kick-Off... 5 Provisioning & Testing.... 5 Billing....
Automating VPN Management
 Automating VPN Management By Scott Hilton, Vice President Product Management Assured Digital, Inc. Although many network managers, users and executives agree on the benefits of virtual private networking,
Automating VPN Management By Scott Hilton, Vice President Product Management Assured Digital, Inc. Although many network managers, users and executives agree on the benefits of virtual private networking,
CISCO QUAD Cisco CCENT/CCNA/CCDA/CCNA Security (QUAD)
 Our Learning Exclusive Custom exam prep software and materials Exam delivery in classroom with 98% success Course specific thinqtank Learning publications to promote fun exciting learning Extended hours
Our Learning Exclusive Custom exam prep software and materials Exam delivery in classroom with 98% success Course specific thinqtank Learning publications to promote fun exciting learning Extended hours
Service Description: Identity Services Engine Implementation-Subscription Service
 Page 1 of 6 Service Description: Identity Services Engine Implementation-Subscription Service Services Summary This document describes the Identity Services Engine Implementation. Subscription Service.
Page 1 of 6 Service Description: Identity Services Engine Implementation-Subscription Service Services Summary This document describes the Identity Services Engine Implementation. Subscription Service.
EVERYTHING YOU NEED TO KNOW ABOUT NETWORK FAILOVER
 WHITE PAPER EVERYTHING YOU NEED TO KNOW ABOUT NETWORK FAILOVER Overview Enterprises lose $700 billion from downtime; losses fall into three categories: lost revenue (17%), lost productivity (73%), and
WHITE PAPER EVERYTHING YOU NEED TO KNOW ABOUT NETWORK FAILOVER Overview Enterprises lose $700 billion from downtime; losses fall into three categories: lost revenue (17%), lost productivity (73%), and
Deploying Cisco SD-WAN on AWS
 How to Guide Deploying Cisco SD-WAN on AWS Introduction: Why use an SD-WAN solution for the cloud? Organizations leveraging branch office locations, IoT devices, and distributed network devices face a
How to Guide Deploying Cisco SD-WAN on AWS Introduction: Why use an SD-WAN solution for the cloud? Organizations leveraging branch office locations, IoT devices, and distributed network devices face a
SD-WAN. Managed Services. Expereo SD-WAN Managed Services Overview.
 SD-WAN Managed Services Expereo SD-WAN Managed Services Overview www.expereo.com/sd-wan Contents 1 SD-WAN MANAGED SERVICES DESCRIPTION... 3 1.1 Consult & Design... 4 1.2 Procurement & Logistics... 4 1.3
SD-WAN Managed Services Expereo SD-WAN Managed Services Overview www.expereo.com/sd-wan Contents 1 SD-WAN MANAGED SERVICES DESCRIPTION... 3 1.1 Consult & Design... 4 1.2 Procurement & Logistics... 4 1.3
RFP Questions Guideline For Data Center Buyers
 RFP Questions Guideline For Data Center Buyers Rev: 00W0052015 1 P a g e This guideline document is a supporting download for our webinar titled 5 RFP Questions Data Center Buyers Must Ask a Provider and
RFP Questions Guideline For Data Center Buyers Rev: 00W0052015 1 P a g e This guideline document is a supporting download for our webinar titled 5 RFP Questions Data Center Buyers Must Ask a Provider and
Dell helps you simplify IT
 Dell helps you simplify IT Workshops the first step. Reduce desktop and data center complexity. Improve productivity. Innovate. Dell IT Consulting Services New Edition 2011 Introduction Are you spending
Dell helps you simplify IT Workshops the first step. Reduce desktop and data center complexity. Improve productivity. Innovate. Dell IT Consulting Services New Edition 2011 Introduction Are you spending
NASCIO Recognition Award Nomination. Title: Central Issuance of State Drivers Licenses. Category: Digital Government Government to Citizen
 NASCIO Recognition Award Nomination Title: Central Issuance of State Drivers Licenses Category: Digital Government Government to Citizen State: North Carolina Executive Summary The NCDMV wanted to reduce
NASCIO Recognition Award Nomination Title: Central Issuance of State Drivers Licenses Category: Digital Government Government to Citizen State: North Carolina Executive Summary The NCDMV wanted to reduce
Commission for Environmental Cooperation (CEC) Sponsored Workshop on Environmental Assistance Programs and Resources for Automotive OEMs and Suppliers
 Commission for Environmental Cooperation (CEC) Sponsored Workshop on Environmental Assistance Programs and Resources for Automotive OEMs and Suppliers Ben Vickery Senior Technical Analyst NIST MEP September
Commission for Environmental Cooperation (CEC) Sponsored Workshop on Environmental Assistance Programs and Resources for Automotive OEMs and Suppliers Ben Vickery Senior Technical Analyst NIST MEP September
VMworld disclaimer This presentation may contain product features that are currently under development. This overview of new technology represents no
 LHC3296BUS OVH: Shields Up! Building a True Security Barrier in the Cloud Chris Romano, Principal Systems Engineer #VMworld #LHC3296BUS VMworld disclaimer This presentation may contain product features
LHC3296BUS OVH: Shields Up! Building a True Security Barrier in the Cloud Chris Romano, Principal Systems Engineer #VMworld #LHC3296BUS VMworld disclaimer This presentation may contain product features
ENISA s Position on the NIS Directive
 ENISA s Position on the NIS Directive 1 Introduction This note briefly summarises ENISA s position on the NIS Directive. It provides the background to the Directive, explains its significance, provides
ENISA s Position on the NIS Directive 1 Introduction This note briefly summarises ENISA s position on the NIS Directive. It provides the background to the Directive, explains its significance, provides
Unified Communications Networks Security and Platforms
 Unified Communications Networks Security and Platforms About Program Who May Apply? Learning Environment Program Overview Program Architecture Partnership with Industry Index Who is Who? 2 Index Introduction
Unified Communications Networks Security and Platforms About Program Who May Apply? Learning Environment Program Overview Program Architecture Partnership with Industry Index Who is Who? 2 Index Introduction
Portfolio Solution Story
 Portfolio Solution Story Private Data Networking Secure Gateway Services Secure Gateway Services provided by Verizon Business Services. All services may not be available in all areas. 2006 Verizon. All
Portfolio Solution Story Private Data Networking Secure Gateway Services Secure Gateway Services provided by Verizon Business Services. All services may not be available in all areas. 2006 Verizon. All
Trust Services Principles and Criteria
 Trust Services Principles and Criteria Security Principle and Criteria The security principle refers to the protection of the system from unauthorized access, both logical and physical. Limiting access
Trust Services Principles and Criteria Security Principle and Criteria The security principle refers to the protection of the system from unauthorized access, both logical and physical. Limiting access
Realiable and extensive solutions for your business #EmpoweringYourFuture
 connectivity Realiable and extensive solutions for your business #EmpoweringYourFuture Enhance your business coordination with Lintasarta Data Communication & Internet Services. Empowering Your Future
connectivity Realiable and extensive solutions for your business #EmpoweringYourFuture Enhance your business coordination with Lintasarta Data Communication & Internet Services. Empowering Your Future
Service Description: Advanced Services Fixed Price Cisco WebEx Advise and Implement Service (0-5,000 Users) (ASF- WBXS-UC-PDIBSE)
 Page 1 of 9 Service Description: Advanced Services Fixed Price Cisco WebEx Advise and Implement Service (0-5,000 Users) (ASF- WBXS-UC-PDIBSE) This document describes Advanced Services Fixed Price Cisco
Page 1 of 9 Service Description: Advanced Services Fixed Price Cisco WebEx Advise and Implement Service (0-5,000 Users) (ASF- WBXS-UC-PDIBSE) This document describes Advanced Services Fixed Price Cisco
Hosted Testing and Grading
 Hosted Testing and Grading Technical White Paper July 2010 www.lexmark.com Lexmark and Lexmark with diamond design are trademarks of Lexmark International, Inc., registered in the United States and/or
Hosted Testing and Grading Technical White Paper July 2010 www.lexmark.com Lexmark and Lexmark with diamond design are trademarks of Lexmark International, Inc., registered in the United States and/or
SOLUTIONS BRIEF GOGO AIRBORNE SECURITY SUMMARY 2017 Q3 RELEASE
 SOLUTIONS BRIEF GOGO AIRBORNE SECURITY SUMMARY 2017 Q3 RELEASE SECURE AIRBORNE CONNECTIVITY: OVERVIEW Gogo Business Aviation realizes the ever-pressing need to be vigilant in staying ahead of potential
SOLUTIONS BRIEF GOGO AIRBORNE SECURITY SUMMARY 2017 Q3 RELEASE SECURE AIRBORNE CONNECTIVITY: OVERVIEW Gogo Business Aviation realizes the ever-pressing need to be vigilant in staying ahead of potential
enalyzer enalyzer security
 enalyzer enalyzer security A documentation that provides an in depth description, that can be read as is, or forwarded to IT departments demanding more technical information. Copenhagen, May 2018 www.enalyzer.com
enalyzer enalyzer security A documentation that provides an in depth description, that can be read as is, or forwarded to IT departments demanding more technical information. Copenhagen, May 2018 www.enalyzer.com
DIGITAL APPRENTICESHIPS
 DIGITAL Networking, Infrastructure Technician, Unified Communication Technician and Software & Web Development Technician - Advanced and Higher Apprenticeships WHY CHOOSE US? OVERVIEW OF PROGRAMMES ESTABLISHED
DIGITAL Networking, Infrastructure Technician, Unified Communication Technician and Software & Web Development Technician - Advanced and Higher Apprenticeships WHY CHOOSE US? OVERVIEW OF PROGRAMMES ESTABLISHED
Figure 1: Summary Status of Actions Recommended in June 2016 Committee Report. Status of Actions Recommended # of Actions Recommended
 Chapter 3 Section 3.05 Metrolinx Regional Transportation Planning Standing Committee on Public Accounts Follow-Up on Section 4.08, 2014 Annual Report In November 2015, the Standing Committee on Public
Chapter 3 Section 3.05 Metrolinx Regional Transportation Planning Standing Committee on Public Accounts Follow-Up on Section 4.08, 2014 Annual Report In November 2015, the Standing Committee on Public
How Cisco ASR 1000 Enables Cisco Business Strategies by Providing Capacity and Resiliency for Collaborative Applications
 Cisco IT Case Study How Cisco ASR 1000 Enables Cisco Business Strategies by Providing Capacity and Resiliency for Collaborative Applications Cisco ASR 1000 Routers support company shift toward virtualized
Cisco IT Case Study How Cisco ASR 1000 Enables Cisco Business Strategies by Providing Capacity and Resiliency for Collaborative Applications Cisco ASR 1000 Routers support company shift toward virtualized
PassReview. PassReview - IT Certification Exams Pass Review
 PassReview http://www.passreview.com PassReview - IT Certification Exams Pass Review Exam : 640-863 Title : Designing for Cisco Internetwork Solutions Vendors : Cisco Version : DEMO Get Latest & Valid
PassReview http://www.passreview.com PassReview - IT Certification Exams Pass Review Exam : 640-863 Title : Designing for Cisco Internetwork Solutions Vendors : Cisco Version : DEMO Get Latest & Valid
Digital Advisory Services Professional Service Description SIP SBC with Field Trial Endpoint Deployment Model
 Digital Advisory Services Professional Service Description SIP SBC with Field Trial Endpoint Deployment Model 1. Description of Services. 1.1 SIP SBC with Field Trial Endpoint Deployment Verizon will assist
Digital Advisory Services Professional Service Description SIP SBC with Field Trial Endpoint Deployment Model 1. Description of Services. 1.1 SIP SBC with Field Trial Endpoint Deployment Verizon will assist
Networking Services. This is IBM Cloud the DNA way.
 Networking Services This is IBM Cloud the DNA way DNA IT Solutions have been chosen as one of just a few IBM Partners in Ireland. Selected based on our experience and expertise in providing customer solutions
Networking Services This is IBM Cloud the DNA way DNA IT Solutions have been chosen as one of just a few IBM Partners in Ireland. Selected based on our experience and expertise in providing customer solutions
Managed Services Rely on us to manage your business services
 Managed Services Rely on us to manage your business services Your business relies on a number of interconnected systems used by different departments from HR, Marketing, Sales and IT. Keeping all these
Managed Services Rely on us to manage your business services Your business relies on a number of interconnected systems used by different departments from HR, Marketing, Sales and IT. Keeping all these
Page 2 Skype Connect Requirements Guide
 Thinking about implementing Skype Connect? Read this guide first. Skype Connect provides connectivity between your business and the Skype community. By adding Skype Connect to your existing SIP-enabled
Thinking about implementing Skype Connect? Read this guide first. Skype Connect provides connectivity between your business and the Skype community. By adding Skype Connect to your existing SIP-enabled
Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications
 Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications Product Overview Cisco Dynamic Multipoint VPN (DMVPN) is a Cisco IOS Software-based security solution for building scalable
Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications Product Overview Cisco Dynamic Multipoint VPN (DMVPN) is a Cisco IOS Software-based security solution for building scalable
MASERGY S MANAGED SD-WAN
 MASERGY S MANAGED New Performance Options for Hybrid Networks Business Challenges WAN Ecosystem Features and Benefits Use Cases INTRODUCTION Organizations are leveraging technology to transform the way
MASERGY S MANAGED New Performance Options for Hybrid Networks Business Challenges WAN Ecosystem Features and Benefits Use Cases INTRODUCTION Organizations are leveraging technology to transform the way
DISTRICT OF COLUMBIA WATER AND SEWER AUTHORITY DEPARTMENT OF PROCUREMENT
 DISTRICT OF COLUMBIA WATER AND SEWER AUTHORITY DEPARTMENT OF PROCUREMENT REQUEST FOR PROPOSALS (RFP) for An Independent Review of Architectural and Engineering Consultant Overhead Rates RFP NUMBER: 17-PR-DETS-45
DISTRICT OF COLUMBIA WATER AND SEWER AUTHORITY DEPARTMENT OF PROCUREMENT REQUEST FOR PROPOSALS (RFP) for An Independent Review of Architectural and Engineering Consultant Overhead Rates RFP NUMBER: 17-PR-DETS-45
SD-WAN Transform Your Agency
 Federal SD-WAN Transform Your Agency 1 Overview Is your agency facing network traffic challenges? Is migration to the secured cloud hogging scarce bandwidth? How about increased mobile computing that is
Federal SD-WAN Transform Your Agency 1 Overview Is your agency facing network traffic challenges? Is migration to the secured cloud hogging scarce bandwidth? How about increased mobile computing that is
SERVICE DEFINITION G-CLOUD 7 THALES PSN REMOTE ACCESS. Classification: Open
 SERVICE DEFINITION G-CLOUD 7 THALES PSN REMOTE ACCESS Classification: Open Classification: Open ii MDS Technologies Ltd 2015. Other than for the sole purpose of evaluating this Response, no part of this
SERVICE DEFINITION G-CLOUD 7 THALES PSN REMOTE ACCESS Classification: Open Classification: Open ii MDS Technologies Ltd 2015. Other than for the sole purpose of evaluating this Response, no part of this
W H I T E P A P E R : O P E N. V P N C L O U D. Implementing A Secure OpenVPN Cloud
 W H I T E P A P E R : O P E N. V P N C L O U D Implementing A Secure OpenVPN Cloud Platform White Paper: OpenVPN Cloud Platform Implementing OpenVPN Cloud Platform Content Introduction... 3 The Problems...
W H I T E P A P E R : O P E N. V P N C L O U D Implementing A Secure OpenVPN Cloud Platform White Paper: OpenVPN Cloud Platform Implementing OpenVPN Cloud Platform Content Introduction... 3 The Problems...
LANCOM Techpaper Advanced Routing and Forwarding (ARF)
 IP network virtualization An ever increasing number of business applications such as telephony, remote maintenance and similar are using the advantages of IP networks. With its Advanced Routing and Forwarding
IP network virtualization An ever increasing number of business applications such as telephony, remote maintenance and similar are using the advantages of IP networks. With its Advanced Routing and Forwarding
Draft Applicant Guidebook, v3
 Draft Applicant Guidebook, v3 Module 5 Please note that this is a discussion draft only. Potential applicants should not rely on any of the proposed details of the new gtld program as the program remains
Draft Applicant Guidebook, v3 Module 5 Please note that this is a discussion draft only. Potential applicants should not rely on any of the proposed details of the new gtld program as the program remains
Kuh-ke-nah Network and Services Page 1 - January 2004
 Kuh-ke-nah Network and Services Page 1 - January 2004 The map of Canada shows the urban sites with video conferencing connections and facilities that now have Quality of Service (QoS) for their video and
Kuh-ke-nah Network and Services Page 1 - January 2004 The map of Canada shows the urban sites with video conferencing connections and facilities that now have Quality of Service (QoS) for their video and
Campus Network Design. 2003, Cisco Systems, Inc. All rights reserved. 2-1
 Campus Network Design 2003, Cisco Systems, Inc. All rights reserved. 2-1 Design Objective Business Requirement Why do you want to build a network? Too often people build networks based on technological,
Campus Network Design 2003, Cisco Systems, Inc. All rights reserved. 2-1 Design Objective Business Requirement Why do you want to build a network? Too often people build networks based on technological,
Telecommunications RFP 02. for. North Country Telemedicine Project (NCTP) Network
 Telecommunications RFP 02 for North Country Telemedicine Project (NCTP) Network TABLE OF CONTENTS 1. PROJECT OVERVIEW 2. PROJECT ADMINISTRATION 3. TECHNICAL REQUIREMENTS 4. PROJECT MANAGEMENT REQUIREMENTS
Telecommunications RFP 02 for North Country Telemedicine Project (NCTP) Network TABLE OF CONTENTS 1. PROJECT OVERVIEW 2. PROJECT ADMINISTRATION 3. TECHNICAL REQUIREMENTS 4. PROJECT MANAGEMENT REQUIREMENTS
How does your organization manage Privileged Users?
 How does your organization manage Privileged Users? A GOVERNMENT & MILITARY SOLUTION GUIDE IONsales@apitech.com www.apitech.com Tel: +1 908-546-3900 Who is ION Networks? ION Networks The most trusted name
How does your organization manage Privileged Users? A GOVERNMENT & MILITARY SOLUTION GUIDE IONsales@apitech.com www.apitech.com Tel: +1 908-546-3900 Who is ION Networks? ION Networks The most trusted name
Accessing CharityMaster data from another location
 Accessing CharityMaster data from another location When all of your computers are on the same Local Area Network (LAN), you can place the back end files (including your data and the Word templates) onto
Accessing CharityMaster data from another location When all of your computers are on the same Local Area Network (LAN), you can place the back end files (including your data and the Word templates) onto
Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications
 Data Sheet Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications Product Overview Cisco Dynamic Multipoint VPN (DMVPN) is a Cisco IOS Software-based security solution for building
Data Sheet Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications Product Overview Cisco Dynamic Multipoint VPN (DMVPN) is a Cisco IOS Software-based security solution for building
Campus Network Design
 Modular Network Design Campus Network Design Modules are analogous to building blocks of different shapes and sizes; when creating a building, each block has different functions Designing one of these
Modular Network Design Campus Network Design Modules are analogous to building blocks of different shapes and sizes; when creating a building, each block has different functions Designing one of these
CND Exam Blueprint v2.0
 EC-Council C ND Certified Network Defende r CND Exam Blueprint v2.0 CND Exam Blueprint v2.0 1 Domains Objectives Weightage Number of Questions 1. Computer Network and Defense Fundamentals Understanding
EC-Council C ND Certified Network Defende r CND Exam Blueprint v2.0 CND Exam Blueprint v2.0 1 Domains Objectives Weightage Number of Questions 1. Computer Network and Defense Fundamentals Understanding
Connecticut Department of Department of Administrative Services and the Broadband Technology Opportunity Program (BTOP) 8/20/2012 1
 Connecticut Department of Department of Administrative Services and the Broadband Technology Opportunity Program (BTOP) 8/20/2012 1 Presentation Overview What is BTOP? Making BTOP work for our state What
Connecticut Department of Department of Administrative Services and the Broadband Technology Opportunity Program (BTOP) 8/20/2012 1 Presentation Overview What is BTOP? Making BTOP work for our state What
Defining IT Security Requirements for Federal Systems and Networks
 Defining IT Security Requirements for Federal Systems and Networks Employing Common Criteria Profiles in Key Technology Areas Dr. Ron Ross 1 The Fundamentals Building more secure systems depends on the
Defining IT Security Requirements for Federal Systems and Networks Employing Common Criteria Profiles in Key Technology Areas Dr. Ron Ross 1 The Fundamentals Building more secure systems depends on the
QuickBooks Online Security White Paper July 2017
 QuickBooks Online Security White Paper July 2017 Page 1 of 6 Introduction At Intuit QuickBooks Online (QBO), we consider the security of your information as well as your customers and employees data a
QuickBooks Online Security White Paper July 2017 Page 1 of 6 Introduction At Intuit QuickBooks Online (QBO), we consider the security of your information as well as your customers and employees data a
Registration of Suppliers
 Registration of Suppliers - 2018 Applications are invited from recognized Manufacturers, Brand agents and other Business establishments,who are interested to register with the Colombo Stock Exchange to
Registration of Suppliers - 2018 Applications are invited from recognized Manufacturers, Brand agents and other Business establishments,who are interested to register with the Colombo Stock Exchange to
Agenda. TÜV Secure it GmbH short introduction. Risk Analysis Case Study. Certification Procedure. w w w. t u v. c o m 2/ 18. TÜV Secure it GmbH 2003
 Agenda TÜV Secure it GmbH short introduction Risk Analysis Case Study Certification Procedure 2/ 18 Let TÜV Secure it Be Your Guide Who we are. Subsidiary of TÜV Rheinland Group TÜV Secure it: Specialists
Agenda TÜV Secure it GmbH short introduction Risk Analysis Case Study Certification Procedure 2/ 18 Let TÜV Secure it Be Your Guide Who we are. Subsidiary of TÜV Rheinland Group TÜV Secure it: Specialists
Campus IT Modernization OPERATIONAL CONTINUITY FLEXIBLE TECHNOLOGY MODERNIZED SYSTEMS
 Campus IT Modernization OPERATIONAL CONTINUITY FLEXIBLE TECHNOLOGY MODERNIZED SYSTEMS Managing the Complexity of IT Modernization Constructing and modernizing a new campus is a complex undertaking, requiring
Campus IT Modernization OPERATIONAL CONTINUITY FLEXIBLE TECHNOLOGY MODERNIZED SYSTEMS Managing the Complexity of IT Modernization Constructing and modernizing a new campus is a complex undertaking, requiring
Corporate Private Networks Applications
 Corporate communication networks are critical in ensuring day-to-day business operations flow smoothly. With deficiencies in telephone networks and terrestrial infrastructure in developing regions, a modern,
Corporate communication networks are critical in ensuring day-to-day business operations flow smoothly. With deficiencies in telephone networks and terrestrial infrastructure in developing regions, a modern,
ECSA Assessment Report
 ECSA Assessment Report Company Test Cloud Company Name of the cloudservice textcloud.com Website of the cloudservice 11.textcloud.com Project number #10652 Projectname Dummyproject Print date 2015-12-01
ECSA Assessment Report Company Test Cloud Company Name of the cloudservice textcloud.com Website of the cloudservice 11.textcloud.com Project number #10652 Projectname Dummyproject Print date 2015-12-01
Level 1 Technical Firewall Traversal & Security. Level 1 Technical. Firewall Traversal & Security. V2 Page 1 of 16
 Level 1 Technical Firewall Traversal & Security V2 Page 1 of 16 Contents 1 - Introduction... 3 Introduction... Error! Bookmark not defined. Available Resources... 8 2 - Overview... 4 Level 1 Recap... Error!
Level 1 Technical Firewall Traversal & Security V2 Page 1 of 16 Contents 1 - Introduction... 3 Introduction... Error! Bookmark not defined. Available Resources... 8 2 - Overview... 4 Level 1 Recap... Error!
ITG. Information Security Management System Manual
 ITG Information Security Management System Manual This manual describes the ITG Information Security Management system and must be followed closely in order to ensure compliance with the ISO 27001:2005
ITG Information Security Management System Manual This manual describes the ITG Information Security Management system and must be followed closely in order to ensure compliance with the ISO 27001:2005
Realiable and extensive solutions for your business #EmpoweringYourFuture
 it services Realiable and extensive solutions for your business #EmpoweringYourFuture Invest your business IT system with Lintasarta IT Services. Empowering Your Future it services Lintasarta IT Services
it services Realiable and extensive solutions for your business #EmpoweringYourFuture Invest your business IT system with Lintasarta IT Services. Empowering Your Future it services Lintasarta IT Services
Exam: Title : VPN/Security. Ver :
 Exam: Title : VPN/Security Ver : 04.21.04 QUESTION 1 You are a technician at Certkiller. Certkiller has its headquarters in New York. The company has just established two branch offices located in Baltimore
Exam: Title : VPN/Security Ver : 04.21.04 QUESTION 1 You are a technician at Certkiller. Certkiller has its headquarters in New York. The company has just established two branch offices located in Baltimore
Digital Advisory Services Professional Service Description SIP Centralized IP Trunk with Field Trial Model
 Digital Advisory Services Professional Service Description SIP Centralized IP Trunk with Field Trial Model 1. Description of Services. 1.1 SIP Centralized IP Trunk with Field Trial Verizon will assist
Digital Advisory Services Professional Service Description SIP Centralized IP Trunk with Field Trial Model 1. Description of Services. 1.1 SIP Centralized IP Trunk with Field Trial Verizon will assist
Customer Managed Connectivity - Milan
 Customer Managed Connectivity - Milan Service and Technical Description June 2017 Version 2 Table of Contents 1.0 Document Scope 3 1.1 1.2 1.3 1.4 Structure of this document 3 Version History 4 Use of
Customer Managed Connectivity - Milan Service and Technical Description June 2017 Version 2 Table of Contents 1.0 Document Scope 3 1.1 1.2 1.3 1.4 Structure of this document 3 Version History 4 Use of
Mobility+ Computing Deployment and Management. Course Outline. Mobility+ Computing Deployment and Management. 07 Apr
 Course Outline Mobility+ Computing Deployment and Management 07 Apr 2019 Contents 1. Course Objective 2. Pre-Assessment 3. Exercises, Quizzes, Flashcards & Glossary Number of Questions 4. Expert Instructor-Led
Course Outline Mobility+ Computing Deployment and Management 07 Apr 2019 Contents 1. Course Objective 2. Pre-Assessment 3. Exercises, Quizzes, Flashcards & Glossary Number of Questions 4. Expert Instructor-Led
Kuh-ke-nah Network and Services Page 1 - April 2005
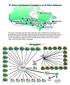 Kuh-ke-nah Network and Services Page 1 - April 2005 The map of Canada shows the urban sites with video conferencing connections and facilities that now have Quality of Service (QoS) for their video and
Kuh-ke-nah Network and Services Page 1 - April 2005 The map of Canada shows the urban sites with video conferencing connections and facilities that now have Quality of Service (QoS) for their video and
Position Title: IT Security Specialist
 Position Title: IT Security Specialist SASRIA SOC LIMITED Sasria, a state-owned company, is the only short-term insurer in South Africa that provides affordable voluntary cover against special risks such
Position Title: IT Security Specialist SASRIA SOC LIMITED Sasria, a state-owned company, is the only short-term insurer in South Africa that provides affordable voluntary cover against special risks such
Background Note on Possible arrangements for a Technology Facilitation Mechanism and other science, technology and innovation issues
 Background Note on Possible arrangements for a Technology Facilitation Mechanism and other science, technology and innovation issues Introduction This background note outlines, in a non-exhaustive manner,
Background Note on Possible arrangements for a Technology Facilitation Mechanism and other science, technology and innovation issues Introduction This background note outlines, in a non-exhaustive manner,
Truffle Broadband Bonding Network Appliance
 Truffle Broadband Bonding Network Appliance Reliable high throughput data connections with low-cost & diverse transport technologies PART I Truffle in standalone installation for a single office. Executive
Truffle Broadband Bonding Network Appliance Reliable high throughput data connections with low-cost & diverse transport technologies PART I Truffle in standalone installation for a single office. Executive
