Rhodes University Wireless Network
|
|
|
- Betty Blair
- 6 years ago
- Views:
Transcription
1 Rhodes University Wireless Network Like many organisations, Rhodes aims to secure its wireless network against unauthorised use. This document explains how this is achieved. Network Overview The University s wireless network consists of a number of different components that interoperate to provide secure, authenticated access to the network and Internet. The diagram below shows how the components of the network are interconnected. All components of the network must be functional for a user to successfully authenticate and connect. Rhodes Wireless Network Components Rhodes Network & the Internet Supplicant Wireless Access Points WPA-Enterprise Wireless Security Switch EAP RADIUS SSL edirectory The three dashed lines show the various secure (encrypted) tunnels that are established during the authentication process. The client initially establishes a tunnel to the University s RADIUS servers (blue, EAP) via a proxy on the wireless security switch. The RADIUS server then establishes a second tunnel (orange, SSL) to the University s edirectory (LDAP) servers. Together these two tunnels secure the user s credentials as they re transmitted over both the University s wireless and wired networks. Once authenticated, the client establishes a tunnel to the wireless security switch (green, WPA-Enterprise). This tunnel is then used for network traffic, and thus secures the user s communication over the wireless network. In practice many of the above components are redundant. Each wireless access point can automatically connect to either of two wireless security switches. These switches connect to a cluster of five RADIUS servers, any one of which is capable of handling authentication requests. The RADIUS servers load balance authentication requests between three edirectory replicas, with automatic failover. These wireless security protocols implemented by each of these components are explained in further detail in the sections below. 2009/02/07 1
2 Wireless Security Access to the wireless network is controlled by individual wireless access points in consultation with the wireless security switches they re connected to. These check that a particular device is authorised to use the network before allowing it to connect. We make use of devices that are certified under the WiFi-Protected Access (WPA) program, and utilise this standard for network authentication. Our access points will support the following protocols: Network Authentication: Data Encryption: WPA or WPA2 TKIP or AES The combination of WPA & TKIP is collectively known as WPA-Enterprise whilst WPA2 & AES combined form WPA2-Enterprise. Of these two, WPA2-Enterprise is the preferred method for doing network authentication as it is a newer standard and is known to be more secure than WPA-Enterprise. The other two combinations (WPA+AES & WPA2+TKIP) will work with Rhodes s wireless network infrastructure but they are not standards-based. The older, insecure Wired-Equivalency Protocol (WEP) is not supported in any form. Authentication Both versions of WPA-Enterprise make use of the Extensible Authentication Protocol (EAP) to authenticate and authorize particular users. As its name suggests, EAP provides for a number of different authentication methods. The following are supported at Rhodes: EAP-type: PEAP/MSCHAPv2 or TTLS/PAP or TTLS/MSCHAPv2 There s no preferred EAP type. Both PEAP and TTLS provide excellent security, and can be used interchangeably on our network. Each has their own pros and cons which might make them preferable in certain situations. TTLS/PAP is non-standard but is widely used and supported (for example by EDUROAM). WPA-Enterprise supports several other EAP authentication methods, most notably EAP-TLS (client certificates) and EAP-GTC (smart cards). Whilst some operating systems provide support for these EAP types, they re not widely used. Rhodes does not support any of these EAP types. The client part of EAP authentication (i.e. what s on the user s laptop) is called a supplicant. User Credentials EAP authentication is handled by the University s RADIUS servers, which in turn pass user credentials to the Novell edirectory (LDAP) servers for validation. These are the same servers that authenticate Rhodes users when they read , browse the Internet, etc. Users should therefore make use of their normal Rhodes username and password when connecting to the network. 2009/02/07 2
3 EAP and RADIUS support the concept of realms. A realm is used to provide routing information in environments where the same RADIUS servers handle authentication for several different organisations. Realms are often specified by appending sign and the realm to the person s username (e.g. username@ru.ac.za). Realms are unnecessary on the staff and student wireless networks, so users can leave any realm or domain field in their supplicant blank. If, however, they want to specify a realm, the correct one for staff and guests is ru.ac.za and the correct one for students is campus.ru.ac.za (i.e. the same as the domain in their address and the SSID of the wireless network they use). The TTLS EAP type requires an outer identity which it uses to route EAP messages correctly. When making use of TTLS, users should specify anonymous@ru.ac.za as their outer identity. In this context the realm is important; it cannot be left out. Operating System Support For reference, the following table shows which combinations of network authentication, data encryption and EAP type (as implemented by Rhodes network infrastructure) various operating systems are known to support: Security Options Operating System Windows XP (SP2 or later) Windows Vista Apple OSX Leopard Linux, *BSD, etc (wpa_supplicant 1 ) WPA + TKIP + PEAP WPA + TKIP + TTLS WPA + AES + PEAP? WPA + AES + TTLS? WPA2 + TKIP + PEAP? WPA2 + TKIP + TTLS? WPA2 + AES + PEAP WPA2 + AES + TTLS just works no yes yes no Key: Native operating system support Supported, but requires a third-party supplicant such as SecureW2 2 Not supported (conclusively known not to work)? Should be supported, but not able to test properly /02/07 3
4 The just works row of the table indicates how well the operating system concerned detects Rhodes wireless network and configures itself to make use of it. Operating systems with a yes here automatically detect a valid combination and thus work out-the-box with no specific user configuration (other than entering a username and password when prompted). Those with a no here require some level of user configuration before they ll connect. This could be as simple as selecting the right options, or could involve the installation of extra software such as a supplicant, drivers or a frontend. For example, installing KNetworkManager 3 in KDE 4 makes wpa_supplicant just work. Security Certificates The EAP methods Rhodes supports make use of X.509 certificates to secure user credentials as they re transmitted over the network. In order to work correctly, the wireless client needs to trust the certificate authorities that issue the certificates we use. Rhodes makes use of two different certificate authorities, and users of the wireless network should make sure that they trust both authorities. These are: Rhodes University CA (SHA1 fingerprint: 2b 47 db 5c a0 e4 c b b9 c d1 b4 ca a6 bd 5b) Thawte Premium Server CA (SHA1 fingerprint: 62 7f 8d d2 7d 7f c9 fe b3 f3 3e fa 9a) Rhodes CA certificate is available from Thawte s CA certificate is built into most operating systems and web browsers. Clients should not validate the certificate s CN (server name) because it s likely to change /02/07 4
5 Appendix: PEAP on Windows XP Manually add a new wireless network with the following settings: On the Association tab: Network Name (SSID): ru.ac.za Network Authentication: WPA2 Data Encryption: AES On the Authentication tab: EAP type: Protected EAP (PEAP) Authenticate as computer: unticked (is ticked by default) Authenticate as guest: unticked Then click Properties to change the PEAP properties On the PEAP properties dialog: Validate server certificate: ticked Connect to these servers: unticked Do not prompt user to authorize...: unticked Authentication Method: EAP-MSCHAPv2 Fast reconnect: ticked (actually, untick if you have problems) Then click Configure... to change the MSCHAPv2 properties On the EAP-MSCHAPv2 properties dialog: Automatically use my Windows logon...: unticked (this can be left ticked if the user logs into Windows with exactly the same username and password as they use for , etc. the danger is that if the password is wrong they'll get intruder locked out when Windows re-trys authentication) 2009/02/07 5
6 Appendix: wpa_supplicant on Linux/FreeBSD Option 1: TTLS Put the following into your /etc/wpa_supplicant.conf network={ ssid="campus.ru.ac.za" key_mgmt=wpa-eap proto=rsn WPA eap=ttls password="xxxxxxxxxxxx" ca_cert="/path/to/thawte.cer" } replacing ssid with the correct SSID, username@campus.ru.ac.za with the correct username and realm and XXXXXXXXXXXX with your normal Rhodes password. (Leave the anonymous_identity as-is, it is important). You'll also need to download and save the Thawte Premium Server CA certificate, and then fix the path in the ca_cert line. Option 2: PEAP Use this instead of the network section above as an alternative. The CA certificate is not required. network={ ssid="ru.ac.za" key_mgmt=wpa-eap eap=peap identity="username" password="xxxxxxxxxxxxx" phase2="auth=pap" } replacing ssid with the correct SSID, username with the correct username (no realm) and XXXXXXXXXXXX with your normal Rhodes password. 2009/02/07 6
Eduroam wireless network - Mac OSX 10.5 Leopard
 Eduroam wireless network - Mac OSX 10.5 Leopard How to configure laptop computers and tablets to connect to the eduroam wireless network. Contents Introduction 1 Instructions for Mac OSX 10.5 Devices 2
Eduroam wireless network - Mac OSX 10.5 Leopard How to configure laptop computers and tablets to connect to the eduroam wireless network. Contents Introduction 1 Instructions for Mac OSX 10.5 Devices 2
simplifying... Wireless Access
 simplifying... Wireless Access Contents Introduction... 1 Android Devices... 1 Apple Devices... 4 ipad, iphone & ipod... 4 Macbook... 6 Windows Devices... 7 Windows 7... 7 Windows Vista... 9 Windows XP...
simplifying... Wireless Access Contents Introduction... 1 Android Devices... 1 Apple Devices... 4 ipad, iphone & ipod... 4 Macbook... 6 Windows Devices... 7 Windows 7... 7 Windows Vista... 9 Windows XP...
Your use of AirUWS-Lite is subject to the University s IT Acceptable Use of Resources Policy.
 AirUWS-Lite is the University s wireless network. This fact sheet describes connecting to AirUWS-Lite using a UWS laptop running Windows XP (SP3) and standard Windows network card drivers. AirUWS-Lite
AirUWS-Lite is the University s wireless network. This fact sheet describes connecting to AirUWS-Lite using a UWS laptop running Windows XP (SP3) and standard Windows network card drivers. AirUWS-Lite
Instructions for connecting to the FDIBA Wireless Network (Windows Vista)
 Instructions for connecting to the FDIBA Wireless Network (Windows Vista) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network (Windows Vista) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network. (Windows XP)
 Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
IMPORTANT INFORMATION FOR CURTIN WIRELESS ACCESS - STUDENT / WINDOWS XP -
 IMPORTANT INFORMATION FOR CURTIN WIRELESS ACCESS - STUDENT / WINDOWS XP - Information required for connection to the Curtin Wireless network: Wireless network names There are two wireless networks operating
IMPORTANT INFORMATION FOR CURTIN WIRELESS ACCESS - STUDENT / WINDOWS XP - Information required for connection to the Curtin Wireless network: Wireless network names There are two wireless networks operating
Connecting to the NJITSecure wireless network.
 Connecting to the NJITSecure wireless network. 1. Start by going to the Start menu and selecting Control Panel 2. Your control Panel will most likely be in Category view, you will need to change it to
Connecting to the NJITSecure wireless network. 1. Start by going to the Start menu and selecting Control Panel 2. Your control Panel will most likely be in Category view, you will need to change it to
Reference Card: How to connect Windows 7 to UniWireless
 Reference Card: How to connect Windows 7 to UniWireless Important Information Windows 7 is not supported by ITS. These instructions provided are only a guide and do not provide any troubleshooting assistance.
Reference Card: How to connect Windows 7 to UniWireless Important Information Windows 7 is not supported by ITS. These instructions provided are only a guide and do not provide any troubleshooting assistance.
Configuring the Client Adapter through the Windows XP Operating System
 APPENDIX E Configuring the Client Adapter through the Windows XP Operating System This appendix explains how to configure and use the client adapter with Windows XP. The following topics are covered in
APPENDIX E Configuring the Client Adapter through the Windows XP Operating System This appendix explains how to configure and use the client adapter with Windows XP. The following topics are covered in
Connecting to the Eduroam WiFi
 Connecting to the Eduroam WiFi The following guide illustrates the steps required to configure a Windows XP installation and internet browser ready for Eduroam use. Instructions for other versions of the
Connecting to the Eduroam WiFi The following guide illustrates the steps required to configure a Windows XP installation and internet browser ready for Eduroam use. Instructions for other versions of the
Wireless for Windows 7
 Wireless for Windows 7 The new CWSL wireless network consists of three different wireless networks CWSL Faculty-Staff - This network is for faculty and staff only. (uses WPA2-Enterprise encryption) CWSL
Wireless for Windows 7 The new CWSL wireless network consists of three different wireless networks CWSL Faculty-Staff - This network is for faculty and staff only. (uses WPA2-Enterprise encryption) CWSL
Internet access system through the Wireless Network of the University of Bologna (last update )
 Internet access system through the Wireless Network of the University of Bologna (last update 7.03.2012) Printable service summary document: the updated version is available online at the following address
Internet access system through the Wireless Network of the University of Bologna (last update 7.03.2012) Printable service summary document: the updated version is available online at the following address
How to connect to FVCC's WiFi
 Table of Contents Table of Contents How to connect to FVCC's WiFi Don't panic! Summary Caveats / Troubleshooting Removing a wifi profile Android iphone Windows 7 Windows 8 Windows 10 Other troubleshooting
Table of Contents Table of Contents How to connect to FVCC's WiFi Don't panic! Summary Caveats / Troubleshooting Removing a wifi profile Android iphone Windows 7 Windows 8 Windows 10 Other troubleshooting
How to connect to Wi-Fi
 41 How to connect to Wi-Fi LSBU uses the eduroam service to connect Wi-Fi devices. Once you are set up you will automatically be connected whenever you are in range. Wireless Internet access is available
41 How to connect to Wi-Fi LSBU uses the eduroam service to connect Wi-Fi devices. Once you are set up you will automatically be connected whenever you are in range. Wireless Internet access is available
Connecting to the eduroam Wireless Network. 1. If you are using a PC, move the. 2. Next Click or Tap the Settings. Help Sheet Windows 8.
 Connecting to the eduroam Wireless Network Help Sheet Windows 8 October 2013 This Help Sheet assists Windows 8 users to access the eduroam Wireless Network. 1. If you are using a PC, move the mouse to
Connecting to the eduroam Wireless Network Help Sheet Windows 8 October 2013 This Help Sheet assists Windows 8 users to access the eduroam Wireless Network. 1. If you are using a PC, move the mouse to
Aruba PEAP-GTC Supplicant Plug-In Guide
 Aruba PEAP-GTC Supplicant Plug-In Guide This document describes the installation and configuration of a supplicant plug-in which supports Protected Extensible Authentication Protocol (PEAP) with EAP-Generic
Aruba PEAP-GTC Supplicant Plug-In Guide This document describes the installation and configuration of a supplicant plug-in which supports Protected Extensible Authentication Protocol (PEAP) with EAP-Generic
IT Quick Reference Guides Connecting to SU-Secure using Windows 8
 IT Quick Reference Guides Connecting to SU-Secure using Windows 8 Windows Guides CONNECTING TO SU-SECURE WI-FI This document will give you instructions on how to connect your Windows 8 Computer to our
IT Quick Reference Guides Connecting to SU-Secure using Windows 8 Windows Guides CONNECTING TO SU-SECURE WI-FI This document will give you instructions on how to connect your Windows 8 Computer to our
Configuring the Client Adapter through Windows CE.NET
 APPENDIX E Configuring the Client Adapter through Windows CE.NET This appendix explains how to configure and use the client adapter with Windows CE.NET. The following topics are covered in this appendix:
APPENDIX E Configuring the Client Adapter through Windows CE.NET This appendix explains how to configure and use the client adapter with Windows CE.NET. The following topics are covered in this appendix:
Johns Hopkins
 Wireless Configuration Guide: Windows Vista Additional hopkins wireless network instructions and requirements for Windows 8, 7, XP, Mac OS X, Linux, and Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Wireless Configuration Guide: Windows Vista Additional hopkins wireless network instructions and requirements for Windows 8, 7, XP, Mac OS X, Linux, and Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Connect to eduroam WiFi
 Connect to eduroam WiFi List Procedure for Windows 10... 2 Procedure for Windows 8... 4 Procedure for Windows 7... 6 Procedure for Mac... 11 Procedure for iphone, ipod Touch and ipad... 15 Procedure for
Connect to eduroam WiFi List Procedure for Windows 10... 2 Procedure for Windows 8... 4 Procedure for Windows 7... 6 Procedure for Mac... 11 Procedure for iphone, ipod Touch and ipad... 15 Procedure for
Connecting Devices to the PSD-BYOD Network
 Connecting Devices to the PSD-BYOD Network Students and staff can use the PSD-BYOD (Bring Your Own Device) network for internet access. Below are directions for connecting different types of devices. Selecting
Connecting Devices to the PSD-BYOD Network Students and staff can use the PSD-BYOD (Bring Your Own Device) network for internet access. Below are directions for connecting different types of devices. Selecting
Wireless Setup Instructions for Windows 7
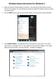 Wireless Setup Instructions for Windows 7 1. Make sure that your wireless feature is turned on. (You may need to flip a switch or press a button on your laptop.) On most laptops you should see a light
Wireless Setup Instructions for Windows 7 1. Make sure that your wireless feature is turned on. (You may need to flip a switch or press a button on your laptop.) On most laptops you should see a light
Configure Wireless for Windows 7
 Configure Wireless for Windows 7 There are two main procedures for configuring Windows 7 to access McGill's wireless network. You can also add the steps at the bottom if you don't want your username and
Configure Wireless for Windows 7 There are two main procedures for configuring Windows 7 to access McGill's wireless network. You can also add the steps at the bottom if you don't want your username and
Configuring 802.1X Authentication Client for Windows 8
 Configuring 802.1X Authentication Client for Windows 8 1. At the Metro Screen, press the windows key on your keyboard together with the alphabets x to go to the Control Panel. Page 1 1.1 In the Control
Configuring 802.1X Authentication Client for Windows 8 1. At the Metro Screen, press the windows key on your keyboard together with the alphabets x to go to the Control Panel. Page 1 1.1 In the Control
Protected EAP (PEAP) Application Note
 to users of Microsoft Windows 7: Cisco plug-in software modules such as EAP-FAST and PEAP are compatible with Windows 7. You do not need to upgrade these modules when you upgrade to Windows 7. This document
to users of Microsoft Windows 7: Cisco plug-in software modules such as EAP-FAST and PEAP are compatible with Windows 7. You do not need to upgrade these modules when you upgrade to Windows 7. This document
How to connect your device using eduroam
 How to connect your device using eduroam Banaras Hindu University is now fully covered under eduroam, a service with more than 70,000 member academic institutions worldwide. This service allows authorized
How to connect your device using eduroam Banaras Hindu University is now fully covered under eduroam, a service with more than 70,000 member academic institutions worldwide. This service allows authorized
802.1X: Deployment Experiences and Obstacles to Widespread Adoption
 802.1X: Deployment Experiences and Obstacles to Widespread Adoption Terry Simons University of Utah; open1x.org Terry.Simons@utah.edu Jon Snyder Portland State University jon@pdx.edu 802.1X Adoption Ratified
802.1X: Deployment Experiences and Obstacles to Widespread Adoption Terry Simons University of Utah; open1x.org Terry.Simons@utah.edu Jon Snyder Portland State University jon@pdx.edu 802.1X Adoption Ratified
BEFORE INSTALLATION: INSTALLATION:
 QUICK USER GUIDE INFORMATION TECHNOLOGY SERVICES SWINWIFI INSTALLATION GUIDE FOR WINDOWS XP BEFORE INSTALLATION: 1. Download Swinwifi installer to your desktop. You may download it from http://www.swinburne.edu.my/current_students.php.
QUICK USER GUIDE INFORMATION TECHNOLOGY SERVICES SWINWIFI INSTALLATION GUIDE FOR WINDOWS XP BEFORE INSTALLATION: 1. Download Swinwifi installer to your desktop. You may download it from http://www.swinburne.edu.my/current_students.php.
Instructions for connecting to winthropsecure
 Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Windows 10 Quick Connect Windows 10 Wireless Set Up Apple Quick Connect Apple Settings Check Windows
Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Windows 10 Quick Connect Windows 10 Wireless Set Up Apple Quick Connect Apple Settings Check Windows
Johns Hopkins
 Wireless Configuration Guide: Windows 8 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, 7, Mac OS X, Linux, and other Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Wireless Configuration Guide: Windows 8 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, 7, Mac OS X, Linux, and other Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
PROTECTED EXTENSIBLE AUTHENTICATION PROTOCOL
 Q&A PROTECTED EXTENSIBLE AUTHENTICATION PROTOCOL This document answers questions about Protected Extensible Authentication Protocol. OVERVIEW Q. What is Protected Extensible Authentication Protocol? A.
Q&A PROTECTED EXTENSIBLE AUTHENTICATION PROTOCOL This document answers questions about Protected Extensible Authentication Protocol. OVERVIEW Q. What is Protected Extensible Authentication Protocol? A.
ONUnet ONU Setup Guide for Windows 7
 The steps below are designed to help Students, Faculty, and Staff connect to the wireless network at Olivet Nazarene University called ONU on Windows 7 (Guests should use ONUGuest). 1. Right click on the
The steps below are designed to help Students, Faculty, and Staff connect to the wireless network at Olivet Nazarene University called ONU on Windows 7 (Guests should use ONUGuest). 1. Right click on the
NT 0018 Instructions for Setting Up UoE_Secure (XP)
 Academic Services Information & Computing Services Division Network Team NT 0018 Instructions for Setting Up UoE_Secure (XP) Document reference: Document type: Document status: Review period: NT0018 Network
Academic Services Information & Computing Services Division Network Team NT 0018 Instructions for Setting Up UoE_Secure (XP) Document reference: Document type: Document status: Review period: NT0018 Network
Senate House Library Guide Connecting to wifi
 Senate House Library Guide Connecting to wifi senatehouselibrary.ac.uk Getting started Accessing our wifi As a member of Senate House Library you can use our wifi network to connect to the internet. The
Senate House Library Guide Connecting to wifi senatehouselibrary.ac.uk Getting started Accessing our wifi As a member of Senate House Library you can use our wifi network to connect to the internet. The
INFORMATION SYSTEMS SERVICE NETWORKS AND TELECOMMUNICATIONS SECTOR
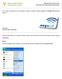 INFORMATION SYSTEMS SERVICE NETWORKS AND TELECOMMUNICATIONS SECTOR User Guide: Connecting to the University of Cyprus wireless network ucywifi for Windows XP operating systems ΥΠΣ ΕΔ/55 Last review date:
INFORMATION SYSTEMS SERVICE NETWORKS AND TELECOMMUNICATIONS SECTOR User Guide: Connecting to the University of Cyprus wireless network ucywifi for Windows XP operating systems ΥΠΣ ΕΔ/55 Last review date:
802.1X Deployment with SU1X
 802.1X Deployment with SU1X By Gareth Ayres Agenda 1.0 Quick Introduction 2.0 Wireless and Eduroam at Swansea 3.0 The Problems 4.0 The Solutions 5.0 Our solution: SU1X 6.0 SU1X Demo? 1.0 Quick Introduction
802.1X Deployment with SU1X By Gareth Ayres Agenda 1.0 Quick Introduction 2.0 Wireless and Eduroam at Swansea 3.0 The Problems 4.0 The Solutions 5.0 Our solution: SU1X 6.0 SU1X Demo? 1.0 Quick Introduction
Setting Up Cisco SSC. Introduction CHAPTER
 CHAPTER 2 This chapter provides an overview of the Cisco Secure Services Client and provides instructions for adding, configuring, and testing the user profiles. This chapter contains these sections: Introduction,
CHAPTER 2 This chapter provides an overview of the Cisco Secure Services Client and provides instructions for adding, configuring, and testing the user profiles. This chapter contains these sections: Introduction,
Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device
 Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device Prerequisites An activated MyID account is required to use ResNet s wireless network. If you have not activated your MyID account,
Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device Prerequisites An activated MyID account is required to use ResNet s wireless network. If you have not activated your MyID account,
Johns Hopkins
 Wireless Configuration Guide: Windows Vista Additional hopkins wireless network instructions and requirements for Windows XP, Mac OS X, and Linux can be found at: http://www.it.johnshopkins.edu/services/networking/wireless/
Wireless Configuration Guide: Windows Vista Additional hopkins wireless network instructions and requirements for Windows XP, Mac OS X, and Linux can be found at: http://www.it.johnshopkins.edu/services/networking/wireless/
Authentication and Security: IEEE 802.1x and protocols EAP based
 Authentication and Security: IEEE 802.1x and protocols EAP based Pietro Nicoletti Piero[at]studioreti.it 802-1-X-EAP-Eng - 1 P. Nicoletti: see note pag. 2 Copyright note These slides are protected by copyright
Authentication and Security: IEEE 802.1x and protocols EAP based Pietro Nicoletti Piero[at]studioreti.it 802-1-X-EAP-Eng - 1 P. Nicoletti: see note pag. 2 Copyright note These slides are protected by copyright
Campus Wi-Fi. Set up access to eduroam: the University Wi-Fi network
 Campus Wi-Fi Set up access to eduroam: the University Wi-Fi network Contents Before you get online... 2 Using eduroam... 3 Connect a phone/tablet... 3 Connect a PC/laptop... 4 Troubleshooting... 6 Help
Campus Wi-Fi Set up access to eduroam: the University Wi-Fi network Contents Before you get online... 2 Using eduroam... 3 Connect a phone/tablet... 3 Connect a PC/laptop... 4 Troubleshooting... 6 Help
Exam Questions CWSP-205
 Exam Questions CWSP-205 Certified Wireless Security Professional https://www.2passeasy.com/dumps/cwsp-205/ 1.. What is one advantage of using EAP-TTLS instead of EAP-TLS as an authentication mechanism
Exam Questions CWSP-205 Certified Wireless Security Professional https://www.2passeasy.com/dumps/cwsp-205/ 1.. What is one advantage of using EAP-TTLS instead of EAP-TLS as an authentication mechanism
The SSID to use and the credentials required to be used are listed below for each type of account: SSID TO CREDENTIALS TO BE USED:
 Installation Guides - Information required for connection to the Central Regional TAFE Kalgoorlie Campus Wireless Network Wireless Network Names and Credentials There are two wireless networks operating
Installation Guides - Information required for connection to the Central Regional TAFE Kalgoorlie Campus Wireless Network Wireless Network Names and Credentials There are two wireless networks operating
Eduroam network configuration using Linux
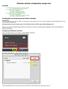 Contents Eduroam network configuration using Linux 1 Configuration by using the gnome network manager 1.1 Configuring the Eduroam connection 2 Configuration by using Kubuntu 10.10 2.1 Step 1: Installation
Contents Eduroam network configuration using Linux 1 Configuration by using the gnome network manager 1.1 Configuring the Eduroam connection 2 Configuration by using Kubuntu 10.10 2.1 Step 1: Installation
INFORMATION TECHNOLOGY
 INFORMATION TECHNOLOGY Configuring and connecting a Mac OS X 10.5x (Leopard) to the eduroam (802.1x) Wireless Service NOTE to Mac OSX 10.6x users: This information relates to configuring a Snow Leopard
INFORMATION TECHNOLOGY Configuring and connecting a Mac OS X 10.5x (Leopard) to the eduroam (802.1x) Wireless Service NOTE to Mac OSX 10.6x users: This information relates to configuring a Snow Leopard
HCC Wireless Instructions for Windows 10 (long version)
 HCC Wireless Instructions for Windows 10 (long version) TIP: If you are having trouble connecting to the wireless network, or if just need some friendly guidance, the Library staff and Technology Help
HCC Wireless Instructions for Windows 10 (long version) TIP: If you are having trouble connecting to the wireless network, or if just need some friendly guidance, the Library staff and Technology Help
Configuring the Client Adapter through the Windows XP Operating System
 APPENDIX E through the Windows XP Operating System This appendix explains how to configure and use the client adapter with Windows XP. The following topics are covered in this appendix: Overview, page
APPENDIX E through the Windows XP Operating System This appendix explains how to configure and use the client adapter with Windows XP. The following topics are covered in this appendix: Overview, page
Johns Hopkins
 Wireless Configuration Guide: Windows Vista Additional hopkins wireless network instructions and requirements for Windows XP, Mac OS X, and Linux can be found at: http://www.it.jhu.edu/networking/wireless/
Wireless Configuration Guide: Windows Vista Additional hopkins wireless network instructions and requirements for Windows XP, Mac OS X, and Linux can be found at: http://www.it.jhu.edu/networking/wireless/
UMDNJ Wireless Documentation Windows 7
 UMDNJ Wireless Documentation Windows 7 The following documentation will provide instructions for configuring the Microsoft Windows 7 native wireless client. There are wireless adapters that have 3 rd party
UMDNJ Wireless Documentation Windows 7 The following documentation will provide instructions for configuring the Microsoft Windows 7 native wireless client. There are wireless adapters that have 3 rd party
ResNet Guide. For the University of Redlands. Determine Your Operating System... 2 Windows 8 / 8.1 Wireless Connection Instructions...
 ResNet Guide For the University of Redlands Contents Determine Your Operating System... 2 Windows 8 / 8.1 Wireless Connection Instructions...4 Windows 7/ Wireless Connection Instructions... 8 Apple Lion
ResNet Guide For the University of Redlands Contents Determine Your Operating System... 2 Windows 8 / 8.1 Wireless Connection Instructions...4 Windows 7/ Wireless Connection Instructions... 8 Apple Lion
NCR. Wi-Fi Setup Assistant. User guide
 NCR Wi-Fi Setup Assistant User guide 15 Contents 1 Getting started... 3 1.1 Features... 3 1.2 System Requirements... 3 1.3 Installing Wi-Fi Setup Assistant... 4 2 Configuring a Wi-Fi Printer... 6 2.1 Setup
NCR Wi-Fi Setup Assistant User guide 15 Contents 1 Getting started... 3 1.1 Features... 3 1.2 System Requirements... 3 1.3 Installing Wi-Fi Setup Assistant... 4 2 Configuring a Wi-Fi Printer... 6 2.1 Setup
Manual UCSFwpa Configuration for Windows 7
 Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > Manual UCSFwpa Configuration for Windows 7 Manual UCSFwpa
Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > Manual UCSFwpa Configuration for Windows 7 Manual UCSFwpa
CaneNet_Wireless Documentation
 CaneNet_Wireless Documentation November 2018 Rev 1.0 CaneNet_Wireless Instructions What is CaneNet_Wireless? CaneNet_Wireless is a wireless network that provides encryption for your wireless communications
CaneNet_Wireless Documentation November 2018 Rev 1.0 CaneNet_Wireless Instructions What is CaneNet_Wireless? CaneNet_Wireless is a wireless network that provides encryption for your wireless communications
 Student Staff Device Zone INSTRUCTIONS FOR LAPTOP CONFIGURATION AND CONNECTION NOTE: To access the Wolf Creek Network (Wolfnet) you must agree to abide by the provisions of the Wolf Creek Acceptable Use
Student Staff Device Zone INSTRUCTIONS FOR LAPTOP CONFIGURATION AND CONNECTION NOTE: To access the Wolf Creek Network (Wolfnet) you must agree to abide by the provisions of the Wolf Creek Acceptable Use
Eduroam CAT. Stefan Winter, RESTENA TF-Mobility, Internetland, 30 june connect communicate collaborate
 Eduroam CAT Stefan Winter, RESTENA TF-Mobility, Internetland, 30 june 2011 What's the CAT? Configuration Assistant Tool Prerequisiste: IdP lets us know its configuration details: CA, certificate CN(s),
Eduroam CAT Stefan Winter, RESTENA TF-Mobility, Internetland, 30 june 2011 What's the CAT? Configuration Assistant Tool Prerequisiste: IdP lets us know its configuration details: CA, certificate CN(s),
Configuring WPA2 for Windows XP
 Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP Your wireless card must support 802.1x, AES, and WPA2. Your computer must have Windows XP service pack 2 installed and
Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP Your wireless card must support 802.1x, AES, and WPA2. Your computer must have Windows XP service pack 2 installed and
Windows 7 Configuration for ORU Wireless Networks
 Page 1 of 13 Windows 7 Configuration for ORU Wireless Networks Show hidden icons Wireless Signal Strength Indicator Figure 1 Windows 7 Documentation for the ORU- Employee wireless network Clicking the
Page 1 of 13 Windows 7 Configuration for ORU Wireless Networks Show hidden icons Wireless Signal Strength Indicator Figure 1 Windows 7 Documentation for the ORU- Employee wireless network Clicking the
For my installation, I created a VMware virtual machine with 128 MB of ram and a.1 GB hard drive (102 MB).
 HOWTO: ZeroShell WPA Enterprise by Paul Taylor ZeroShell can be obtained from: http://www.zeroshell.net/eng/ For my installation, I created a VMware virtual machine with 128 MB of ram and a.1 GB hard drive
HOWTO: ZeroShell WPA Enterprise by Paul Taylor ZeroShell can be obtained from: http://www.zeroshell.net/eng/ For my installation, I created a VMware virtual machine with 128 MB of ram and a.1 GB hard drive
Wireless Security Guide (for Windows XP, Windows Vista, Windows 7, Mac OSx)
 Wireless Security Guide (for Windows XP, Windows Vista, Windows 7, Mac OSx) Wireless Security Guide This guide will take you through the process of configuring, changing or checking the wireless security
Wireless Security Guide (for Windows XP, Windows Vista, Windows 7, Mac OSx) Wireless Security Guide This guide will take you through the process of configuring, changing or checking the wireless security
IEEE 802.1X workshop. Networkshop 34, 4 April Josh Howlett, JRS Technical Support, University of Bristol. Copyright JNT Association
 IEEE 802.1X workshop Networkshop 34, 4 April 2006. Josh Howlett, JRS Technical Support, University of Bristol. Copyright JNT Association 2005 1 Introduction Introduction (5 mins) Authentication overview
IEEE 802.1X workshop Networkshop 34, 4 April 2006. Josh Howlett, JRS Technical Support, University of Bristol. Copyright JNT Association 2005 1 Introduction Introduction (5 mins) Authentication overview
Securewireless Windows 7 Setup Guide
 Securewireless Windows 7 Setup Guide 1. Click on the wireless icon in the lower right-hand corner of the taskbar and then click on Open Network and Sharing Center. 2. From the Network and Sharing Center
Securewireless Windows 7 Setup Guide 1. Click on the wireless icon in the lower right-hand corner of the taskbar and then click on Open Network and Sharing Center. 2. From the Network and Sharing Center
Manually Configuring Windows 8 for Wireless PittNet
 Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 8 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 8 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Auburn Montgomery AUM Wi-Fi. Windows 7. User s Guide & System Documentation
 Auburn Montgomery AUM Wi-Fi Windows 7 User s Guide & System Documentation November 2018 WiFi Windows 7 For: Student Campus Fac Staff AUM WiFi // Windows 7 User s Guide Page 1 Table of Contents Overview
Auburn Montgomery AUM Wi-Fi Windows 7 User s Guide & System Documentation November 2018 WiFi Windows 7 For: Student Campus Fac Staff AUM WiFi // Windows 7 User s Guide Page 1 Table of Contents Overview
Install Certificate on the Cisco Secure ACS Appliance for PEAP Clients
 Install Certificate on the Cisco Secure ACS Appliance for PEAP Clients Document ID: 64067 Contents Introduction Prerequisites Requirements Components Used Conventions Microsoft Certificate Service Installation
Install Certificate on the Cisco Secure ACS Appliance for PEAP Clients Document ID: 64067 Contents Introduction Prerequisites Requirements Components Used Conventions Microsoft Certificate Service Installation
WZC Wireless Connection Method (Windows XP, Vista, 7) - 1 -
 WZC Wireless Connection Method (Windows XP, Vista, 7) - 1 - 1. Windows XP - 2 - Direction Confirm Wireless LanCard and on Service Normally, Before WZC Set-Up 1. Confirmation and Vitalization to Using Wireless
WZC Wireless Connection Method (Windows XP, Vista, 7) - 1 - 1. Windows XP - 2 - Direction Confirm Wireless LanCard and on Service Normally, Before WZC Set-Up 1. Confirmation and Vitalization to Using Wireless
ClearPass QuickConnect 2.0
 ClearPass QuickConnect 2.0 User Guide Copyright 2013 Aruba Networks, Inc. Aruba Networks trademarks include, Aruba Networks, Aruba Wireless Networks, the registered Aruba the Mobile Edge Company logo,
ClearPass QuickConnect 2.0 User Guide Copyright 2013 Aruba Networks, Inc. Aruba Networks trademarks include, Aruba Networks, Aruba Wireless Networks, the registered Aruba the Mobile Edge Company logo,
SecureW2 Enterprise Client
 RSA SecurID Ready Implementation Guide Partner Information Last Modified: January 16, 2015 Product Information Partner Name Web Site Product Name Version & Platform Product Description SecureW2 www.securew2.com
RSA SecurID Ready Implementation Guide Partner Information Last Modified: January 16, 2015 Product Information Partner Name Web Site Product Name Version & Platform Product Description SecureW2 www.securew2.com
Manually Configuring Windows 7 for Wireless PittNet
 Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 7 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 7 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Cisco EXAM Implementing Cisco Unified Wireless Networking Essentials (IUWNE) Buy Full Product.
 Cisco EXAM - 640-722 Implementing Cisco Unified Wireless Networking Essentials (IUWNE) Buy Full Product http://www.examskey.com/640-722.html Examskey Cisco 640-722 exam demo product is here for you to
Cisco EXAM - 640-722 Implementing Cisco Unified Wireless Networking Essentials (IUWNE) Buy Full Product http://www.examskey.com/640-722.html Examskey Cisco 640-722 exam demo product is here for you to
Who can use eduroam. Participating Organizations. How does eduroam work
 eduroam which stands for "Education Roaming" allows students, researchers and staff from participating institutions to access the wireless network at other participating organizations using their home
eduroam which stands for "Education Roaming" allows students, researchers and staff from participating institutions to access the wireless network at other participating organizations using their home
Configuring 802.1X Authentication Client for Windows 8
 Configuring 802.1X Authentication Client for Windows 8 1. At the Metro Screen, press the windows key on your keyboard together with the alphabets x to go to the Control Panel. Page 1 1.1 In the Control
Configuring 802.1X Authentication Client for Windows 8 1. At the Metro Screen, press the windows key on your keyboard together with the alphabets x to go to the Control Panel. Page 1 1.1 In the Control
EacStudent Wireless Access for Windows XP / 2000 Computers
 EacStudent Wireless Access for Windows XP / 2000 Computers These instructions will help you set up your wireless connection on campus. Before beginning, you need: An activated student account on Gila Hank
EacStudent Wireless Access for Windows XP / 2000 Computers These instructions will help you set up your wireless connection on campus. Before beginning, you need: An activated student account on Gila Hank
The SU1X 802.1X Configuration Deployment Tool
 Published on Jisc community (https://community.jisc.ac.uk) Home > Network and technology service docs > eduroam > Information for tech admins > The SU1X 802.1X Configuration Deployment Tool The SU1X 802.1X
Published on Jisc community (https://community.jisc.ac.uk) Home > Network and technology service docs > eduroam > Information for tech admins > The SU1X 802.1X Configuration Deployment Tool The SU1X 802.1X
Self Help Guide. APPLIES TO: F1PI241EGau
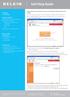 APPLIES TO: F1PI241EGau TABLE OF CONTENTS:- Enable Wireless on your Modem/Router 1 Setup Wireless Encryption 3 Wireless Security Information 3 64 Bit WEP 4 128 Bit WEP 6 WPA 8 Connecting to the Wireless
APPLIES TO: F1PI241EGau TABLE OF CONTENTS:- Enable Wireless on your Modem/Router 1 Setup Wireless Encryption 3 Wireless Security Information 3 64 Bit WEP 4 128 Bit WEP 6 WPA 8 Connecting to the Wireless
How to configure SecureW2
 How to configure SecureW2 Disclaimer The software described in this document is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Copyright Notice
How to configure SecureW2 Disclaimer The software described in this document is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Copyright Notice
Cisco Secure ACS for Windows v3.2 With PEAP MS CHAPv2 Machine Authentication
 Cisco Secure ACS for Windows v3.2 With PEAP MS CHAPv2 Machine Authentication Document ID: 43486 Contents Introduction Prerequisites Requirements Components Used Background Theory Conventions Network Diagram
Cisco Secure ACS for Windows v3.2 With PEAP MS CHAPv2 Machine Authentication Document ID: 43486 Contents Introduction Prerequisites Requirements Components Used Background Theory Conventions Network Diagram
802.1x Port Based Authentication
 802.1x Port Based Authentication Johan Loos Johan at accessdenied.be Who? Independent Information Security Consultant and Trainer Vulnerability Management and Assessment Wireless Security Next-Generation
802.1x Port Based Authentication Johan Loos Johan at accessdenied.be Who? Independent Information Security Consultant and Trainer Vulnerability Management and Assessment Wireless Security Next-Generation
ilight/gigapop eduroam Discussion Campus Network Engineering
 ilight/gigapop eduroam Discussion Campus Network Engineering By: James W. Dickerson Jr. May 10, 2017 What is eduroam?» eduroam (education roaming) is an international roaming service for users in research,
ilight/gigapop eduroam Discussion Campus Network Engineering By: James W. Dickerson Jr. May 10, 2017 What is eduroam?» eduroam (education roaming) is an international roaming service for users in research,
To Activate your Wireless Account
 To Activate your Wireless Account Access to the WVU Wireless network will require you to have an active WVU Active Directory account. Activation involves authenticating your account and setting a password.
To Activate your Wireless Account Access to the WVU Wireless network will require you to have an active WVU Active Directory account. Activation involves authenticating your account and setting a password.
Secure ACS for Windows v3.2 With EAP TLS Machine Authentication
 Secure ACS for Windows v3.2 With EAP TLS Machine Authentication Document ID: 43722 Contents Introduction Prerequisites Requirements Components Used Background Theory Conventions Network Diagram Configuring
Secure ACS for Windows v3.2 With EAP TLS Machine Authentication Document ID: 43722 Contents Introduction Prerequisites Requirements Components Used Background Theory Conventions Network Diagram Configuring
APP NOTES Onsight Rugged Smart Camera Wireless Network Configuration
 APP NOTES Onsight Rugged Smart Camera Wireless Network Configuration July 2016 Table of Contents 1. Overview... 4 1.1 Onsight Setup Wizard... 4 1.2 Onsight Wireless Manual Setup... 4 1.3 Hotspot Login...
APP NOTES Onsight Rugged Smart Camera Wireless Network Configuration July 2016 Table of Contents 1. Overview... 4 1.1 Onsight Setup Wizard... 4 1.2 Onsight Wireless Manual Setup... 4 1.3 Hotspot Login...
Postprocessing Verification Errors
 APPENDIXC Command Usage Errors Note Execution of the sscmanagementutility utility will result in either of the following: Success No return message. Output file created with processed content. Failure
APPENDIXC Command Usage Errors Note Execution of the sscmanagementutility utility will result in either of the following: Success No return message. Output file created with processed content. Failure
Cisco Exam Questions and Answers (PDF) Cisco Exam Questions BrainDumps
 Cisco 300-375 Dumps with Valid 300-375 Exam Questions PDF [2018] The Cisco 300-375 Securing Cisco Wireless Enterprise Networks (WISECURE) exam is an ultimate source for professionals to retain their credentials
Cisco 300-375 Dumps with Valid 300-375 Exam Questions PDF [2018] The Cisco 300-375 Securing Cisco Wireless Enterprise Networks (WISECURE) exam is an ultimate source for professionals to retain their credentials
Postprocessing Verification Errors
 APPENDIXC Command Usage Errors Note Execution of the sscconfigprocess utility will result in either of the following: Success No return message. Output file created with processed content. Failure Error
APPENDIXC Command Usage Errors Note Execution of the sscconfigprocess utility will result in either of the following: Success No return message. Output file created with processed content. Failure Error
Avaya Identity Engines Ignition CASE Administration. Avaya Identity Engines Ignition Server Release 8.0
 Avaya Identity Engines Ignition CASE Administration Release 8.0 Document Status: Standard Document Number: NN47280-603 Document Version: 01.01 Date: 2012 Avaya Inc. All Rights Reserved. Notices While reasonable
Avaya Identity Engines Ignition CASE Administration Release 8.0 Document Status: Standard Document Number: NN47280-603 Document Version: 01.01 Date: 2012 Avaya Inc. All Rights Reserved. Notices While reasonable
User Databases. ACS Internal Database CHAPTER
 CHAPTER 12 The Cisco Secure Access Control Server Release 4.2, hereafter referred to as ACS, authenticates users against one of several possible databases, including its internal database. You can configure
CHAPTER 12 The Cisco Secure Access Control Server Release 4.2, hereafter referred to as ACS, authenticates users against one of several possible databases, including its internal database. You can configure
Configuring EAP-FAST CHAPTER
 CHAPTER 3 This chapter explains how to configure EAP-FAST module settings, such as connection settings, user credentials, and authentication methods. The following topics are covered in this chapter: Accessing
CHAPTER 3 This chapter explains how to configure EAP-FAST module settings, such as connection settings, user credentials, and authentication methods. The following topics are covered in this chapter: Accessing
Wired Dot1x Version 1.05 Configuration Guide
 Wired Dot1x Version 1.05 Configuration Guide Document ID: 64068 Introduction Prerequisites Requirements Components Used Conventions Microsoft Certificate Services Installation Install the Microsoft Certificate
Wired Dot1x Version 1.05 Configuration Guide Document ID: 64068 Introduction Prerequisites Requirements Components Used Conventions Microsoft Certificate Services Installation Install the Microsoft Certificate
Intelligent IP-Enabled Access Control Solutions
 IP-Enabled Locks: Facts for IT Intelligent IP-Enabled Access Control Solutions The information sent over a site-wide 100 lock deployment in 24 hours is the size of a standard email message PoE and ESD
IP-Enabled Locks: Facts for IT Intelligent IP-Enabled Access Control Solutions The information sent over a site-wide 100 lock deployment in 24 hours is the size of a standard email message PoE and ESD
Introduction to eduroam
 Introduction to eduroam eduroam (education roaming) is the secure, world-wide roaming access service developed for the international research and education community. Poll Brief History eduroam initiative
Introduction to eduroam eduroam (education roaming) is the secure, world-wide roaming access service developed for the international research and education community. Poll Brief History eduroam initiative
ENHANCING PUBLIC WIFI SECURITY
 ENHANCING PUBLIC WIFI SECURITY A Technical Paper prepared for SCTE/ISBE by Ivan Ong Principal Engineer Comcast 1701 John F Kennedy Blvd Philadelphia, PA 19103 215-286-2493 Ivan_Ong@comcast.com 2017 SCTE-ISBE
ENHANCING PUBLIC WIFI SECURITY A Technical Paper prepared for SCTE/ISBE by Ivan Ong Principal Engineer Comcast 1701 John F Kennedy Blvd Philadelphia, PA 19103 215-286-2493 Ivan_Ong@comcast.com 2017 SCTE-ISBE
Cisco Securing Cisco Wireless Enterprise Networks (WISECURE) Download Full Version :
 Cisco 300-375 Securing Cisco Wireless Enterprise Networks (WISECURE) Download Full Version : https://killexams.com/pass4sure/exam-detail/300-375 QUESTION: 42 Which two considerations must a network engineer
Cisco 300-375 Securing Cisco Wireless Enterprise Networks (WISECURE) Download Full Version : https://killexams.com/pass4sure/exam-detail/300-375 QUESTION: 42 Which two considerations must a network engineer
Master Student IT Guidebook. Step by Step Guide to IT Success in Zayed University
 Master Student IT Guidebook Step by Step Guide to IT Success in Zayed University Contents Computing Services in Zayed University... 4 Configure Network Connection... 6 Window 7... 6 Mac... 14 ZU Network
Master Student IT Guidebook Step by Step Guide to IT Success in Zayed University Contents Computing Services in Zayed University... 4 Configure Network Connection... 6 Window 7... 6 Mac... 14 ZU Network
Using PEAP and WPA PEAP Authentication Security on a Zebra Wireless Tabletop Printer
 Using PEAP and WPA PEAP Authentication Security on a Zebra Wireless Tabletop Printer Q. What is PEAP? A. Protected Extensible Authentication Protocol is an IEEE 802.1x EAP security method that uses an
Using PEAP and WPA PEAP Authentication Security on a Zebra Wireless Tabletop Printer Q. What is PEAP? A. Protected Extensible Authentication Protocol is an IEEE 802.1x EAP security method that uses an
Protected EAP (PEAP) Application Note
 Revision 4.0 June 2004 Corporate Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 526-4100 Text Part
Revision 4.0 June 2004 Corporate Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 526-4100 Text Part
New Windows build with WLAN access
 New Windows build with WLAN access SecRep 24 17-18 May 2016 Ahmed Benallegue/Hassan El Ghouizy/Priyan Ariyansinghe ECMWF network_services@ecmwf.int ECMWF May 19, 2016 Introduction Drivers for the new WLAN
New Windows build with WLAN access SecRep 24 17-18 May 2016 Ahmed Benallegue/Hassan El Ghouizy/Priyan Ariyansinghe ECMWF network_services@ecmwf.int ECMWF May 19, 2016 Introduction Drivers for the new WLAN
LockView 5 / 5Pro CompX Database & Network Configuration & Installation Manual
 LockView 5 / 5Pro CompX Database & Network Configuration & Installation Manual TABLE OF CONTENTS CompX Database & Network Configuration & Installation Manual Introduction... 4 Installation Requirements...
LockView 5 / 5Pro CompX Database & Network Configuration & Installation Manual TABLE OF CONTENTS CompX Database & Network Configuration & Installation Manual Introduction... 4 Installation Requirements...
Server Certificate Validation
 Understanding Server Certificate Validation and 802.1X Update Kevin Koster Founder & Principal Cloudpath Networks Special Thanks To: Robert Hopley, RSA Chris Hessing, Cloudpath & OpenSEA Alex Sharaz, University
Understanding Server Certificate Validation and 802.1X Update Kevin Koster Founder & Principal Cloudpath Networks Special Thanks To: Robert Hopley, RSA Chris Hessing, Cloudpath & OpenSEA Alex Sharaz, University
eduroam for Windows Vista
 Please note: You must read the Wireless Network Fair Usage and Security Policy at the end of this guide. This ensures that you are aware of all the rules regarding Wireless services and prevent your internet
Please note: You must read the Wireless Network Fair Usage and Security Policy at the end of this guide. This ensures that you are aware of all the rules regarding Wireless services and prevent your internet
EacMonsterNet Wireless Access Windows XP Computers
 EacMonsterNet Wireless Access Windows XP Computers These instructions will help you set up your wireless connection on campus. Before beginning, you need: An activated student account on Gila Hank On-Line.
EacMonsterNet Wireless Access Windows XP Computers These instructions will help you set up your wireless connection on campus. Before beginning, you need: An activated student account on Gila Hank On-Line.
