Deploying Performance Routing
|
|
|
- Sylvia Cox
- 5 years ago
- Views:
Transcription
1
2 Deploying Performance Routing KRST-2362 Jean-Marc Barozet Technical Leader Application Visibility and Control Network Operating Systems Technology Group
3 Introducing Performance Routing (PfR) Application Aware Adaptive Routing Internet (DMVPN) Branch VMs / Master Controller () Border Router () MPLS-VPN (IP-VPN) Path Video Path Full utilization of expensive WAN bandwidth Efficient distribution of traffic based upon load, circuit cost and path preference Improved Application Performance Per application best path based on delay, loss, jitter measurements Increased Application Availability Protection from carrier black holes and brownouts KRST
4 What is Application Visibility and Control (AVC) Enabled Technologies ISR G2 App Visibility & User Experience Report ISR G2 ASR1K ISR G2 ASR1K NFv9/IPFIX App BW Transaction Time SAP 3M 150 ms Sharepoint 10M 500 ms ASR1K High Med Low Reporting Tools Application Recognition Reporting Perf. Collection Tool & Exporting Management Tool Control NBAR2 Metadata Unified Monitoring - Traffic Statistics - Response Time - Voice/Video Monitoring - URL Collection Cisco Prime Infrastructure 3 rd Party Tools QoS (w/ NBAR2) PfR KRST
5 PERFORMANCE ROUTING 101
6 Performance Routing Components The Decision Maker: Master Controller () Apply policy, verification, reporting No packet forwarding/ inspection required The Forwarding Path: Border Router () Gain network visibility in forwarding path (Learn, measure) Enforce s decision (path enforcement) Optimize by: Reachability, Delay, Loss, Jitter, MOS, Throughput, Load, and/or $Cost WAN1 WAN2 KRST
7 Performance Routing Topologies Internet Edge ISP1 ISP2 Enterprise WAN Branch WAN1 (IP-VPN) / / WAN2 (IPVPN, DMVPN) Optimize by: Reachability, Loss, Delay, Jitter, MOS, Throughput, Load, and/or $Cost / KRST
8 Performance Routing Principles Learning Monitoring (Passive Active) Choosing Your Policies Enforcing the Path Get the Traffic Classes in the database Get the Traffic Classes Performance Metrics Check Delay, loss, threshold, Bandwidth and more Use a good performing path per Traffic Class KRST
9 Step #1 Learning PfR Operates on Traffic Classes PfR determines the traffic classes from the traffic flowing through the border routers Subsets of the total traffic must be identified, and these traffic subsets are named traffic classes Traffic Classes Voice, Video, Critical The Rest of the Traffic Dest. IP DSCP Delay Loss Jitter BW Prefixes /24-0 WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) or Applications (DSCP, ACL, well-known, NBAR) Dest. IP DSCP AppID Delay Loss Jitter BW /24 EF 0 Dest. IP DSCP AppID Delay Loss Jitter BW /24 AF31 0 / / / Default is to learn based on destination prefixes with aggregation mask /24 KRST
10 Learning Traffic Classes On a global basis internal Learn Global external WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) Global learning Aka Similar to the default class in QoS / / / KRST
11 Learning Traffic Classes Or Per Service Class Voice - Video Service Class Critical Application Rest of the Traffic Voice, Video, Critical The Rest of the Traffic Or define Service Classes Aka Similar to the class-map concept in QoS Allows to define: Specific policies per group Specific thresholds per group Specific monitoring mode per group WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) / / / KRST
12 Traffic Class Learning Using NetFlow on s Traffic Classes Destination Prefix DSCP App Id Delay Loss Ingress BW Egress BW Exit TNF Cache TNF Cache Traffic Classes Automatic Learning is enabled by default once you enable PfR and add the Border Routers commands s to learn Traffic Classes automatically enables Traditional NetFlow ingress NetFlow on internal and external interfaces WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) / / / KRST
13 Learning Traffic Classes Database Filled with TCs Destination Prefix DSCP App Id Delay Loss Ingress BW Egress BW Exit /32 EF 1 E0/ /24 AF31 2 E0/0 TNF Cache TNF Cache / E0/0 Traffic Classes s use their NetFlow cache Top Talkers based on throughput s aggregate based on the configured destination mask Send the reports to the every minute WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) / / / KRST
14 Step #2a Measurement Passive Monitoring Reachability Passive Delay Loss Traffic Classes Passive Performance Metrics Egress BW Ingress BW PfR Netflow Monitoring Flows Need not be symmetrical WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) / / / KRST
15 Measuring Passive Mode For Data, Best Effort Applications Destination Prefix DSCP App Id Delay Loss Ingress BW Egress BW Exit / Gi1/ /24 AF11 1 Gi1/2 0 2 Gi1/1 TNF Cache TNF Cache Traffic Classes Links Ingress Egress 1 2 Gig1/1 Gig1/2 WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) PfR uses NetFlow to collect and aggregate passive monitoring statistics on a per traffic class basis. / / / Instructs s to monitor the performance KRST
16 Measuring Passive Mode For Data, Best Effort Applications Destination Prefix DSCP App Id Delay Loss Ingress BW Egress BW Exit / Gi1/ /24 AF Gi1/ Gi1/1 TNF Cache TNF Cache Traffic Classes Links Ingress Egress 1 Gig1/ Gig1/ WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) Border routers collect and report passive monitoring statistics to the master controller approximately once per minute. s gather performance measurements using Netflow s report Performance Metrics for Traffic Classes to the Master Controller / / / KRST
17 Step #2b Measurement Active Mode Reachability Active Delay Loss Traffic Classes Probe active path Active Performance Metrics SLA IP SLA Responder Jitter MOS PfR enables IP SLA feature Probes sourced from ICMP probes learned or configured TCP, UDP, JITTER need ip sla responder WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) / / / KRST
18 Step #2b Measurement Active Hybrid Modes Fast Active probes on all path all the time Passive to measure BW only Traffic Classes Active Performance Metrics SLA Fast Mode Probe all paths Active Throughput Passive to measure BW only Active probing on current exit WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) / / / Fast Mode is used when fast failover is needed KRST
19 Measuring Active Mode For Voice, Video and Critical Apps SLA Destination Prefix DSCP App Id Delay Jitter Loss Ingress BW Egress /32 EF 1 Gi1/ /24 AF31 1 Gi1/2 0 2 Gi1/1 Traffic Classes BW Exit Active monitoring involves creating a stream of synthetic traffic (IP SLA probes) that replicates a traffic class as closely as possible. WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) / / / Instructs s to monitor the performance KRST
20 Measuring Active Mode For Voice, Video and Critical Apps SLA Destination Prefix DSCP App Id Delay Jitter Loss Ingress BW Egress /32 EF Gi1/ /24 AF Gi1/ Gi1/1 Traffic Classes BW Exit S gather performance measurements using IP SLA probes The performance metrics of the synthetic traffic are measured The results are applied to the traffic class entry in the Master Controller database s report Performance Metrics for Traffic Classes WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) / / / KRST
21 Step #3 Policy Definitions Choosing Your Policies Traffic Classes Link Load balancing Max utilization Link grouping $Cost Application Performance Reachability Delay Loss MOS Voice, Video, Critical WAN1 WAN2 Jitter (IP-VPN) (IPVPN, DMVPN) The Rest of the Traffic / / / KRST
22 Choosing Your Policies Resolvers per Group 1. Link-Group Voice - Video Critical Application 2. Loss 3. Jitter 4. Delay 1. Link-Group 2. Loss 4. Delay Voice, Video, Critical WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) The Rest of the Traffic Rest of the Traffic Load-Balancing Multiple resolvers can be assigned Set of Policies per Application Group Resolver Priority / / / KRST
23 Define Your Policy Thresholds Passive Mode Performance Metric Calculate Passive monitoring periods are defined as: Short-Term which consists of the last 5 minute results Long-Term which consists of the last 60 minute results KRST
24 Define Your Policy Thresholds Passive Mode Absolute vs. Relative The required characteristic can be represented in two ways Absolute Short Avg exceeds the threshold of N msec. Used for delay, loss, unreachable, jitter Relative Short Avg exceeds the Long Avg by X percent. Used for delay, loss, unreachable Short Term Avg (5 minutes) Delay Absolute Delay AbsoluteOOP Detected Short Avg is higher than the absolute threshold Threshold 35 ms KRST
25 Define Your Policy Thresholds Passive Mode Absolute vs. Relative The required characteristic can be represented in two ways Absolute Short Avg exceeds the threshold of N msec. Used for delay, loss, unreachable, jitter Relative Short Avg exceeds the Long Avg by X percent. Used for delay, loss, unreachable Short Term Avg (5 minutes) Delay Relative OOP Detected Delay Relative Short Avg is higher than Long Avg by X Percent Long Term Avg (60 minute) KRST
26 Define Your Policy Thresholds Active Mode Performance Metric Calculate Active probe monitoring periods are defined as: Short-Term which consists of the last 5 probe results Long-Term which consists of the last 60 probe results PfR short-term counter calculation is based on the last 5 samples Let s look at how it actually works KRST
27 Active Mode Example 1 Short-Term Delay OOP Detected Initial: 50 ms Threshold: 120 ms Problem: 150 ms T0 T1 T2 T3 T4 T5 Probe Freq Probe Results from s (last 5 samples) Short-term Delay KRST
28 Active Mode Example 2 Short-Term Delay OOP Detected Initial: 50 ms Threshold: 120 ms Problem: 300 ms T0 T1 T2 T3 T4 T5 Probe Freq Probe Results from s (last 5 samples) Short-term Delay KRST
29 Step #4 Enforce the Path Automatic or force P Destination Prefix Application BGP - Egress: route injection or Modifying the BGP Local Preference attribute - Ingress: BGP AS-PATH Prepend or AS Community EIGRP Route Control Static Route Injection Dynamic P NBAR/CCE Voice, Video, Critical WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) The Rest of the Traffic PIRO / / / KRST
30 Performance Routing Configuration Learning pfr master learn <learn-list> Monitoring (Passive Active) Choosing Your Policies pfr-map match <list> parameters policy definitions Enforcing the Path Automatic, Force P KRST
31 1. Provisioning (Decision Maker) (Forwarding Path) key chain pfr key 0 key-string cisco! pfr master! border key-chain pfr interface Ethernet0/0 internal interface Ethernet0/1 external border key-chain pfr interface Ethernet0/0 internal interface Ethernet0/1 external! learn throughput! max-range-utilization 15!! Load-Balancing enabled by default!! key chain pfr key 0 key-string cisco! pfr border local Ethernet0/0 master key-chain pfr! 1. Provisioning 2. Learning 3. Monitoring and Optimization WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) / / / Simplification Initiative with 15.2(3)T and XE 3.6 KRST
32 Provisioning What you Need to Enable PfR + WAAS WCCP establishes tunnels between router and WAAS device PfR needs to be aware of the WCCP Tunnel interfaces router#show tunnel groups 2 tunnel groups active WCCP : service group 317 in "Default", ver v2, assgnmnt: mask-value set intf: Tunnel0, locally sourced WCCP : service group 318 in "Default", ver v2, assgnmnt: mask-value set intf: Tunnel2, locally sourced PfR cannot control WAAS Express traffic which is sourced from the router Add both interfaces as PfR internal interfaces pfr master border key-chain pfr-keychain interface GigabitEthernet0/2 external max-xmit-utilization percentage 80 link-group secondary interface GigabitEthernet0/1.34 internal interface GigabitEthernet0/1.32 internal interface Tunnel0 internal interface Tunnel2 internal KRST
33 2. Traffic Class Learning Configuration Sample pfr master! learn throughput list seq 10 refname <CLASS_NAME_1> #1 traffic-class access-list <ACL1> filter <PREFIX_LIST1> aggregation-type prefix-length <LENGTH1> throughput WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) #2 list seq 20 refname <CLASS_NAME_2> traffic-class access-list <ACL2> filter <PREFIX_LIST2> aggregation-type prefix-length <LENGTH2> throughput / / / [Rest of the traffic] DEFAULT KRST
34 Traffic Class Learning Disable Global Learning (Optional) pfr master learn throughput traffic-class filter access-list DENY_GLOBAL_LEARN_LIST list seq 10 refname <CLASS_NAME_1> traffic-class access-list <ACL1> filter <PREFIX_LIST1> aggregation-type prefix-length <LENGTH1> throughput!! Access-list for disabling global learn.! ip access-list extended DENY_GLOBAL_LEARN_LIST deny ip any any Voice, Video, Critical WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) / / / When you want to use PfR for a subset of the traffic (ie Voice traffic only, rest is controlled by the routing protocol) KRST
35 3. Performance Routing Policies Global - Interface Global pfr master max-range-utilization percent 30 delay relative 200 loss threshold mode <monitor-mode> resolve delay resolve loss WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) Per Interface pfr master border interface Ethernet0/1 external max-xmit-utilization percentage 80 maximum utilization receive percentage 80 link-group WAN1 / / / KRST
36 Performance Routing Policies Per Service Class (pfr-map) #1 pfr-map MYMAP 10 match pfr learn list <CLASS_NAME_1> <Threshold definitions> <Monitoring mode definition> <Policy definitions> <Preferred Path and Fallback option> <Probe frequency> <Periodic timer definition> #2 pfr-map MYMAP 20 match pfr learn list <CLASS_NAME_2> <Threshold definitions> <Monitoring mode definition> <Policy definitions> <Preferred Path and Fallback option> <Probe frequency> <Periodic timer definition> WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) / / / pfr master policy-rules MYMAP KRST
37 PERFORMANCE ROUTING DOMAIN
38 Active Mode Issues Active Fast Active Throughput TCP, UDP, JITTER probe need IP SLA responder What s needed: Configure a pfr-map that matches prefixes or Remote-site1 Define the policies Define the jitter probes And REPEAT for each remote site pfr-map MYMAP 10 match pfr learn list LEARN_LIST_VIDEO_ANCH1 set periodic 90 set delay threshold 200 set loss threshold SLA set jitter threshold 30 set mode monitor fast set resolve loss priority 2 variance 5 set resolve jitter priority 3 variance 5 set resolve delay priority 4 variance 5 WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) IP SLA Responder no set resolve range no set resolve utilization set probe frequency 4 set active-probe jitter target-port 2000 / / / KRST
39 PfR Multisite System Evolution Peering & Discovery Enterprise Domain Multisite Peering Framework to Peering Framework can be used to exchange policies, services and feedback Remote Site Discovery Automatic discovery of branch routers Simplifies Configuration prefix and target discovery Probing Efficiency sharing of probe data across policies Enhance PfR remote site bandwidth discovery WAN1 (IP-VPN) SLA WAN2 (IPVPN, DMVPN) IP SLA Responder / / / IP SLA Responder KRST
40 PfR Domain Target Discovery Site Publish Each announces its inside prefixes, together with probe target address and site names Prefix H1, H2, H3 Responder H SLA WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) /B Site 1 R Publish Prefix A Responder 1 /B Site 2 R Publish Prefix B Responder 2 /B Site 3 R Publish Prefix C, D, E Responder 3, 4 IP SLA Responder KRST
41 PfR Domain Target Discovery Prefixes Responders BW Sites SLA Prefix A Responder1 1.2 Mbps Site 1 Prefix B Responder2 2.3 Mbps Site2 Prefix C, D, E Responder3, 4 10 Mbps Site3 Mapping table built on each site Allows automatic jitter probe configuration Allows automatic probe generation Remote Bandwidth discovery per remote site WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) / / / KRST
42 With Target Discovery Enabled pfr-map MAP-TEST3 10 match pfr learn list LEARN_LIST_ANCH1 set periodic 90 set mode route control set delay threshold 200 set loss threshold set jitter threshold 30 set mode monitor fast set resolve loss priority 2 variance 5 set resolve jitter priority 3 variance 5 set resolve delay priority 4 variance 5 no set resolve range no set resolve utilization set probe frequency 4 set active-probe jitter target-port pfr-map MAP-TEST pfr-map MAP-TEST3 15 match pfr-map learn MAP-TEST3 list 15 LEARN_LIST_ANCH2 match pfr-map learn MAP-TEST3 list 15 LEARN_LIST_ANCH2 set match pfr-map periodic 90 learn MAP-TEST3 list 15 LEARN_LIST_ANCH2 set match pfr-map periodic 90 learn MAP-TEST3 list 15 LEARN_LIST_ANCH2 set set match pfr-map delay periodic threshold 90 learn MAP-TEST3 list 15 LEARN_LIST_ANCH2 200 set set match pfr-map delay periodic threshold 90 learn MAP-TEST3 list 15 LEARN_LIST_ANCH2 200 set set set match pfr-map loss delay periodic threshold threshold 90 learn MAP-TEST3 list 15 LEARN_LIST_ANCH set set set match pfr-map loss delay periodic threshold threshold 90 learn MAP-TEST3 list 15 LEARN_LIST_ANCH set set set set match pfr-map jitter loss delay periodic threshold threshold 90 learn MAP-TEST3 list 15 LEARN_LIST_ANCH set set set set match pfr-map jitter loss delay periodic threshold threshold 90 learn MAP-TEST3 list 15 LEARN_LIST_ANCH set set set set set match mode jitter loss delay periodic pfr monitor threshold threshold 90 learn list LEARN_LIST_ANCH2 fast set set set set set match mode jitter loss delay periodic match pfr pfr monitor threshold threshold 90 learn learn list list LEARN_LIST_ANCH2 fast set set set set set set resolve mode jitter loss delay periodic loss monitor threshold threshold 90 priority fast variance 5 set set set set set set resolve mode jitter loss delay set periodic loss monitor threshold threshold priority fast variance 5 set set set set set set resolve resolve mode jitter loss delay jitter loss monitor threshold threshold priority fast variance 5 5 set set set set set set resolve resolve mode jitter loss set delay mode jitter loss monitor threshold threshold route priority fast control variance 5 5 set set set set set set resolve resolve resolve mode jitter loss delay jitter loss monitor threshold priority priority fast variance 3 2 variance set set set set set set resolve resolve resolve mode jitter set loss delay delay jitter loss monitor threshold priority priority fast variance 3 2 variance no set set set set set resolve resolve resolve mode jitter range delay jitter loss monitor threshold priority priority fast 30 4 variance 3 2 variance no set set set set set resolve resolve resolve mode set jitter loss range delay jitter loss monitor threshold priority priority fast variance 3 2 variance no set no set set set set resolve resolve resolve resolve mode utilization range delay loss monitor priority priority fast 4 variance 3 2 variance no set no set set set set resolve resolve resolve resolve set mode jitter utilization range delay jitter loss monitor threshold priority priority fast 30 4 variance 3 2 variance set no probe set no set set set frequency resolve resolve resolve resolve utilization range delay jitter loss priority priority 4 variance 3 2 variance set no probe set no set set set frequency resolve resolve resolve set resolve mode utilization range delay jitter monitor loss priority priority fast 4 variance 3 2 variance set set no active-probe set no set set frequency resolve resolve resolve utilization range delay jitter priority priority 4 variance 3 variance 5 5 jitter target-port 2000 set set no active-probe set no set set frequency resolve resolve set resolve utilization range delay jitter loss priority priority 4 variance 23 variance 5 5 jitter target-port 2000 set set no active-probe set no set frequency resolve resolve utilization range delay priority 4 variance 5 jitter target-port 2000 set set no active-probe set no set set frequency resolve resolve utilization range delay jitter priority priority 4 variance 3 variance 5 5 jitter target-port 2000 set set no active-probe set no set frequency resolve resolve utilization range jitter target-port 2000 set set no active-probe set no set set frequency resolve resolve utilization delay range priority 4 variance 5 jitter target-port 2000 set set no active-probe set frequency resolve utilization jitter target-port 2000 set set no active-probe no set set frequency resolve utilization range jitter target-port 2000 set set active-probe frequency jitter target-port 2000 set set active-probe no set resolve frequency jitter utilization target-port 2000 set active-probe jitter target-port 2000 KRST-2362 set set active-probe frequency jitter target-port Cisco and/or 2000 its affiliates. All rights reserved. set active-probe jitter target-port 2000 pfr master! policy-rules MYMAP mc-peer head-end Loopback1 target-discovery [SNIP] pfr-map MYMAP 10 match pfr learn list LEARN_LIST_ANCH set periodic 90 set delay threshold 200 set loss threshold set jitter threshold 30 set mode monitor fast set resolve loss priority 2 variance 5 set resolve jitter priority 3 variance 5 set resolve delay priority 4 variance 5 no set resolve range no set resolve utilization set probe frequency 4 42
43 PfR Domain Summary PfR is now multi-site aware to Peering Framework can be used to exchange policies, services and feedback Target Discovery is just the first feature running over this framework Automatic configuration and generation of all jitter probes Reduces IP SLA target configuration per destination and per policy. Improves IP SLA probing efficiency through the sharing of probe data across multiple policies Possible future features: Solving the Asymmetric Routing issue PfR Policies distribution QoS Policies distribution KRST
44 INTERNET EDGE USE CASE
45 Performance Routing Topologies Internet Edge ISP1 ISP2 Branch WAN1 (IP-VPN) / / WAN2 (IPVPN, DMVPN) / KRST
46 Ingress Egress Manual Traffic Engineering Overview Problem Statement Ingress/Egress path are under/over utilized Maximize bandwidth utilization (uplinks with different BW) ibgp Manual Solution Consider The Traffic Patterns of the Enterprise. Does the Enterprise Host Content? Does the Enterprise Access Content? Not Sure? Graph Interface Byte Count Use NetFlow Even better, use Flexible NetFlow In General, sites have a 80:20 traffic volume (in bytes) mix. Fix only the 80% Direction. 20% direction doesn t matter unless links are widely varying speeds. ebgp 1 2 GE FE ebgp ISP1 ISP2 ISP3 ISP5 ISP4 KRST
47 Manual Traffic Engineering BGP Policy Instruments Tool/Attribute Longest Match Local Preference AS_Path Communities Direction of Traffic Flow Affected Inbound and Outbound Outbound Inbound Inbound Implementation Static or Redistribution / Received Direction Applied: Inbound Direction Applied: Outbound Direction Applied: Outbound Direction Applied, works together with Route Maps KRST
48 Automatic Traffic Engineering Load-Balancing with PfR Solution: PfR used to load balance the traffic New default policies based on load-balancing Cisco ASR1k is typical / with terminating WAN connections BGP routing s must be ibgp peers Default routing or Partial routes or Full routes ebgp ibgp 1 2 GE FE ebgp ISP1 ISP2 ISP3 ISP5 ISP4 KRST
49 Egress Load Balancing PfR Solution Used Learning Dest Prefixes (NetFlow) ibgp Monitoring Passive Global Egress BW ebgp % 45% ebgp Policies Load-Balancing (range) ISP1 ISP2 Path Enforcement BGP ISP3 Inject BGP Route ISP4 ISP5 BGP Local Pref KRST
50 Internet Presence Outbound Load Balancing Example Provisioning pfr master max-range-utilization percent 25 logging! border key-chain pfr interface Ethernet0/0 internal interface Ethernet0/1 external max-xmit-utilization percentage 90! border key-chain pfr interface Ethernet0/0 internal interface Ethernet0/1 external max-xmit-utilization percentage 90! Link Range Utilization Keep the usage on a set of exit links within a certain percentage range of each other Max Link Utilization Upper threshold on the amount of traffic a specific link can carry Simplification Initiative Default is now to load balance based on destination prefixes IOS 15.2(3)T, XE 3.6 KRST
51 Internet Presence Outbound Load Balancing Example Learning and Policies pfr master! learn monitoring-period 1 periodic-interval 1 prefixes 1000 applications 0 expire after time 300!! max prefix total learn exporter MYEXPORTER mode monitor passive periodic 600 Tune Learning Cycles as needed If high number of prefixes required Tune Number of Prefixes to learn Learn 1000 Prefixes per learning period Delete Prefix if not relearned in 60 Minutes Tune Max Prefixes Control Prefixes max Rest if under the routing protocol Global Policies Load Balancing enabled by default Link OOP if : % Util > Lowest + 10 % Util > 90 Revaluate Exit every 10 Minutes KRST
52 Path Enforcement BGP Egress Load Balancing R2#sh bgp [SNIP] Before PfR Network Next Hop Metric LocPrf Weight Path *>i i *>i I [SNIP] R2# BGP Path enforcement used Egress: Injecting more specific routes if needed Modifying the BGP Local Preference attribute Do NOT change the BGP configuration Ingress: BGP AS-PATH Prepend or AS Community KRST-2362 R2#sh bgp [SNIP] Network Next Hop Metric LocPrf Weight Path *>i I *>i i *>i / i *>i / i *>i / i *>i / i *>i / i *>i / i *>i I [SNIP] R2# After PfR 52
53 Ingress Load Balancing PfR Solution Used Learning Inside Prefixes (BGP) ibgp Monitoring Passive Global Ingress BW ebgp % 17% ebgp Policies Load-Balancing (range) ISP1 ISP2 Path Enforcement BGP ISP3 BGP AS-PATH Prepend ISP4 ISP5 BGP Community KRST
54 Internet Presence Inbound Load Balancing Learning Inside Prefix pfr master policy-rules MYMAP max-range-utilization percent 25 logging! [ PROVISIONNING]! learn inside bgp prefixes 1000 applications 0 expire after time 300! max prefix total learn max range receive percent 25 exporter MYEXPORTER mode monitor passive periodic 600 pfr-map MYMAP 10 match pfr learn inside Configuring Inside Prefix pfr master policy-rules MYMAP max-range-utilization percent 10 logging! [ PROVISIONNING]! learn prefixes 1000 expire after time 300! max prefix total learn max range receive percent 25 exporter MYEXPORTER mode monitor passive periodic 600! pfr-map MYMAP 10 match ip address prefix-list _PREFIX inside! ip prefix-list _PREFIX seq 5 permit /24 ip prefix-list _PREFIX seq 10 permit /24 ip prefix-list _PREFIX seq 15 permit /24 ip prefix-list _PREFIX seq 20 permit /24 Link Range Utilization - Ingress Keep the usage on a set of exit links within a certain percentage range of each other KRST
55 Internet Presence Downgrade Method AS-PATH PREPEND BGP Community Nothing required pfr master max-range-utilization percent 10 logging! border key-chain pfr interface Ethernet0/0 internal interface Ethernet0/1 external downgrade bgp community 3:100! border key-chain pfr interface Ethernet0/0 internal interface Ethernet0/1 external downgrade bgp community 4:200! Downgrade Community Specific value per Provider Check the following: Send-community enabled under bgp neighbor <ip> soft-reconfiguration inbound per neighbor max range receive percent X under pfr master KRST
56 PfR Master Controller Database Display Traffic Classes Performance Metrics #sh pfr master traffic-class OER Prefix Statistics: Pas - Passive, Act - Active, S - Short term, L - Long term, Dly - Delay (ms), P - Percentage below threshold, Jit - Jitter (ms), MOS - Mean Opinion Score Los - Packet Loss (packets-per-million), Un - Unreachable (flows-per-million), E - Egress, I - Ingress, Bw - Bandwidth (kbps), N - Not applicable U - unknown, * - uncontrolled, + - control more - active probe all # - Prefix monitor mode is Special, & - Blackholed Prefix % - Force Next-Hop, ^ - Prefix is denied DstPrefix Appl_ID Dscp Prot SrcPort DstPort SrcPrefix Flags State Time Curr CurrI/F Protocol PasSDly PasLDly PasSUn PasLUn PasSLos PasLLos EBw IBw ActSDly ActLDly ActSUn ActLUn ActSJit ActPMOS ActSLos ActLLos /24 N N N N N N INPOLICY Et0/1 BGP N N N N N N /24 N N N N N N INPOLICY Et0/1 BGP N N N N N N /24 N N N N N N INPOLICY Et0/1 BGP N N N N N N Passive Delay (from TCP Syn/Ack) No Active Delay Passive Mode used PfR has calculated the per traffic class (which is per /24 destination in this case) egress bandwidth usage as well as the ingress KRST
57 PfR Master Controller Database Traffic Class Performance NEW R3#sh pfr master traffic-class performance ip any /24 ============================================================================================== Traffic-class: Destination Prefix : /24 Source Prefix : N/A Destination Port : N/A Source Port : N/A DSCP : N Protocol : N/A Application Name: : N/A General: Control State : Controlled using BGP Traffic-class status : INPOLICY Current Exit : interface Et0/1, Tie breaker was load-balance criteria Time on current exit : 0d 0:12:57 Time remaining in current state seconds Traffic-class type : Learned Improper config : None Last Out-of-Policy event: No Out-of-Policy Event Average Passive Performance Current Exit: (Average for last 5 minutes) Unreachable : 0% -- Threshold: 50% Delay : 53% -- Threshold: 50% Loss : 0% -- Threshold: 10% Egress BW : 13 kbps Ingress BW : 1 kbps Time since last update : 0d 0:0:11 Average Active Performance Current Exit: (Average for last 5 minutes) Unreachable : 0% -- Threshold: 50% Delay : 51% -- Threshold: 50% ============================================================================================== R3# TC Performance Performance Details Last Resolver decisions Filter on any type of traffic KRST
58 PfR Master Controller Database Check Load-Balancing NEW #sh pfr master exits ============================================================================================== PfR Master Controller Exits: General Info: ============= E - External I - Internal N/A - Not Applicable Up/ ID Name Border Interface ifidx IP Address Mask Policy Type Down Et0/ Util E UP Et0/ Util E UP Global Exit Policy: =================== Cost: In Policy ebgp 1 ibgp 2 ebgp Exits Performance: ================== Egress Ingress ID Capacity MaxUtil Usage % RSVP POOL OOP Capacity MaxUtil Usage % OOP N/A N/A N/A N/A N/A N/A ISP1 ISP2 TC and BW Distribution: ======================= # of TCs BW (kbps) Probe Active Name/ID Current Controlled InPolicy Controlled Total Failed Unreach (count) (fpm) Exit Related TC Stats: ====================== Priority highest nth Number of TCs with range: 0 0 Number of TCs with util: 0 0 Number of TCs with cost: 0 0 ISP4 ISP3 ISP5 # Total number of TCs: 59 KRST
59 Internet Edge Scaling Max Number of Prefixes Recommended : ASR1k with RP2 ibgp PfR can actively manage up to 18k Prefixes concurrently with ASR1000-RP2 IOS-XE ebgp 1 2 ebgp ISP1 ISP2 ISP3 ISP4 ISP5 KRST
60 ENTERPRISE USE CASE
61 Performance Routing Topologies Enterprise WAN ISP1 ISP2 Branch WAN1 (IP-VPN) / / WAN2 (IPVPN, DMVPN) Voice - Video Critical Application Rest of the Traffic / KRST
62 Enterprise WAN Use Case Blackout and Brownout Problem Statement: Recent carrier routing problem cause a network outage (Blackout). Fluctuating performance over the WAN is causing intermittent application problems (Brownout) Secondary/Backup WAN path under utilized Solution: PfR Application based optimization Protect Voice and Video traffic: primary path, check delay, loss, jitter fallback secondary Protect Business Applications: primary path, check loss, utilization fallback secondary Best effort Applications Maximize bandwidth utilization: load balanced across SPs or use the secondary path Voice, Video, Critical WAN1 (IP-VPN) Voice - Video Critical Application Rest of the Traffic WAN2 (IPVPN, DMVPN) The Rest of the Traffic / / / KRST
63 Deployment With Target Discovery ISP-1 ISP-2 WAN1 (IP-VPN) / / Voice - Video Critical Application Rest of the Traffic WAN2 (IPVPN, DMVPN) / Multisite Peering Framework: to Peering Framework can be used to exchange policies, services and feedback Remote Site Discovery Simplifies Configuration prefix and target discovery Probing Efficiency sharing of probe data across policies KRST
64 Enabling Target Discovery Ease Configuration for Active Probing /16 R3 LISTEN The peering system must configure a source loopback interface with an IP address that is reachable (routed) through the network The Head-End is configured into unicast-listen mode and each of the Branch s will have a static unicast neighbor configuration with the Head- End peer address Voice, Video, Critical WAN1 (IP-VPN) SLA WAN2 (IPVPN, DMVPN) Shadow Router IP Sla Responder The Rest of the Traffic / / / ANCH SETUP The peering to the head-end / /16 KRST
65 Target Discovery Configuration Example /16! pfr master policy-rules MYMAP mc-peer head-end Loopback0 target-discovery <responder-list _TARGET> <insideprefixes _PREFIX> border key-chain pfr interface Ethernet0/0 internal interface Ethernet0/1 external link-group SP1! border key-chain pfr interface Ethernet0/0 internal interface Ethernet0/1 external link-group SP2! Voice, Video, Critical WAN1 (IP-VPN) SLA WAN2 (IPVPN, DMVPN) Shadow Router IP Sla Responder The Rest of the Traffic pfr master policy-rules MYMAP mc-peer Loopback0 target-discovery IOS 15.2(3)T / / / / /16 KRST
66 Target Discovery Hub Site /16 R3#sh pfr master target-discovery PfR Target-Discovery Services Mode: Static Domain: Responder list: _TARGET Inside-prefixes list: _PREFIX SvcRtg: client-handle: 7 sub-handle: 6 pub-seq: 1 PfR Target-Discovery Database (local) Voice, Video, Critical SLA Shadow Router IP Sla Responder The Rest of the Traffic Local-ID: Desc: R3 Target-list: , Prefix-list: /24, /24, /24, /24 PfR Target-Discovery Database (remote) WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) -peer: Target-list: Prefix-list: /16 -peer: Target-list: Prefix-list: /16 Desc: R10 Desc: R9 /B R /B R /B R R3# / /16 KRST
67 Target Discovery Branch /16 R10#sh pfr master target-discovery PfR Target-Discovery Services Mode: Dynamic Domain: SvcRtg: client-handle: 2 sub-handle: 1 pub-seq: 1 PfR Target-Discovery Database (local) Local-ID: Desc: R10 Target-list: Prefix-list: /16 PfR Target-Discovery Database (remote) Voice, Video, Critical WAN1 (IP-VPN) SLA WAN2 (IPVPN, DMVPN) Shadow Router IP Sla Responder The Rest of the Traffic -peer: Target-list: Prefix-list: /16 Desc: R9 -peer: Desc: R3 /B Target-list: , R Prefix-list: /24, /24, /24, /24 / / R10# / /16 KRST
68 Step1 Learning Traffic Defines your groups Traffic Classes Definition Prefixes Voice - Video Critical Application Rest of the Traffic Traffic Classes Voice, Video, Critical SLA The Rest of the Traffic Prefixes + DSCP Applications Check Prefixes and application/dscp per branch This will give an idea of the number of Traffic Classes EXAMPLE Critical Apps DSCP AF31 Mask TCs Mask 16 2 TCs WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) / / / Tune Aggregation Mask as needed KRST / / / /24 68
69 Traffic Class Learning Configuration Example pfr master! learn throughput! list seq 10 refname LEARN_VOICE_VIDEO traffic-class access-list VOICE_VIDEO filter ANCH_PREFIX aggregation-type prefix-length <LENGTH> throughput! list seq 20 refname LEARN_CRITICAL traffic-class access-list CRITICAL filter ANCH_PREFIX aggregation-type prefix-length <LENGTH> throughput! [Rest of the traffic] Voice, Video, Critical WAN1 (IP-VPN) SLA WAN2 (IPVPN, DMVPN) The Rest of the Traffic / / / KRST
70 ! Traffic Class Learning Configuration Example ip access-list extended VOICE_VIDEO! permit ip any any dscp ef ip access-list extended CRITICAL! permit ip any any dscp af31 ip prefix-list ANCH_PREFIX seq 5 permit /16 ip prefix-list ANCH_PREFIX seq 10 permit /16! Access-List Automatically learn based on DSCP Traffic values for Voice, Video and Critical Classes Applications Rest of the Traffic falls under global learning (kind of default class) Voice, Video, Critical WAN1 (IP-VPN) SLA WAN2 (IPVPN, DMVPN) The Rest of the Traffic / / / Branch Prefixes Filters on remote prefixes KRST
71 Learning Traffic Classes Example #sh pfr master learn list Learn-List seq 10 refname LEARN_VOICE_VIDEO Configuration: Traffic-Class Access-list: VOICE_VIDEO Filter: ANCH_PREFIX Aggregation-type: prefix-length 32 Learn type: throughput Session count: 1000 Max count: 1000 Policies assigned: 10 Status: ACTIVE Stats: Traffic-Class Count: 2 Traffic-Class Learned: Appl Prefix /24 ef 256 Appl Prefix /24 ef 256 Learn-List seq 20 refname LEARN_CRITICAL Configuration: Traffic-Class Access-list: CRITICAL Filter: ANCH_PREFIX Aggregation-type: prefix-length 24 Learn type: throughput Session count: 50 Max count: 100 Policies assigned: 20 Status: ACTIVE Stats: Traffic-Class Count: 37 Traffic-Class Learned: Appl Prefix /24 af Appl Prefix /24 af Appl Prefix /24 af [SNIP] KRST-2362 Voice, Video, Critical WAN1 (IP-VPN) SLA WAN2 (IPVPN, DMVPN) The Rest of the Traffic / / / 71
72 Using NBAR2 Problem Statement Using NBAR2 to classify applications within PfR NBAR support in PfR is currently limited to a subset of all signatures Better to use NBAR2 with QoS marking on ingress. PfR Learning will be based on DSCP value Voice, Video, Critical WAN1 (IP-VPN) SLA WAN2 (IPVPN, DMVPN) The Rest of the Traffic / / / KRST
73 Using NBAR2 Workaround Using NBAR2 to classify applications NBAR support in PfR is currently limited to a subset of all signatures Better to use NBAR2 with QoS marking on ingress then configure PfR to classify based on DSCP But, needs: Workaround on ISR-G2 Disable NetFlow in PfR Border routers global configuration Enable NetFlow ingress/egress on the WAN interfaces IOS-XE 3.9 on ASR1k (workaround enabled by default no need to manually configure) KRST-2362 pfr border logging local Loopback0! master key-chain pfr no netflow Gi0/ Internal interface GigabitEthernet0/0.40 description LAN service-policy input marking-policy! class-map match-all marking-video interface GigabitEthernet0/1 match protocol rtp video description -- WAN class-map match-all marking-voice match protocol rtp audio ip address class-map match-all marking-critical ip flow ingress match protocol exchange ip flow egress policy-map marking-policy! class marking-voice set dscp ef Gig0/1 - External class marking-video set dscp af41 class marking-critical set dscp af21 73
74 Step2 Performance Measurement PfR Solution Used Monitoring TD Enabled tells the to configure and generate all Jitter probes needed Fast Voice/Video Fast Critical Apps Traffic Classes NetFlow Probes Shadow Router SLA IP Sla Responder NetFlow Probes Passive Rest Destination Prefix DSCP App Id Delay Jitter Loss Ingress BW Egress /24 EF Gi1/ /24 AF Gi1/2 EF Gi1/1 BW Exit WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) Destination Prefix DSCP App Id Delay Loss Ingress BW Egress / Gi1/ / Gi1/ Gi1/1 BW Exit / / / KRST
75 Step3 Policies Define your policies per group Policies 1. Link-Group Voice, Video, Critical SLA Shadow Router IP Sla Responder The Rest of the Traffic Voice - Video 2. Loss 3. Jitter 4. Delay WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) Critical Application 1. Link-Group 2. Loss 4. Delay / / / Rest of the Traffic Load-Balancing KRST
76 Configuration Sample Policies Voice and Video pfr-map MYMAP 10 match pfr learn list LEARN_VOICE_VIDEO set delay threshold 200 set loss threshold set jitter threshold 30 set mode monitor fast set resolve loss priority 2 variance 5 set resolve jitter priority 3 variance 5 set resolve delay priority 4 variance 5 set link-group SP1 fallback SP2 set probe frequency 4 set periodic 90 IOS 15.2(3)T Policies Thresholds Applied to the voice and video traffic Loss, delay and jitter Monitor mode fast Actively probe all exits to get performance metrics Policies Definition List all policies Assign priority Administrative policy: SP1 is the primary path, fallback to SP2 if OOP Jitter Probe Target Discovery is used No need to manually define the probe target KRST
77 Configuration Sample Policies Critical Applications pfr-map MYMAP 20 match pfr learn list LEARN_CRITICAL set delay threshold 120 set loss threshold set mode monitor fast set resolve delay priority 1 variance 20 set resolve loss priority 5 variance 10 set link-group SP1 fallback SP2 set probe frequency 4 set periodic 90 IOS 15.2(3)T Policies Thresholds Applied to the voice and video traffic Loss, delay and jitter Monitor mode fast Actively probe all exits to get performance metrics Policies Definition List all policies Assign priority Administrative policy: SP1 is the primary path, fallback to SP2 if OOP Active Probes Automatic configuration and generation of probes KRST
78 Configuration Sample Policies Rest of the Traffic! pfr master policy-rules MYMAP max-range-utilization percent 22! mc-peer head-end Loopback0 target-discovery! logging!! Default Policies! mode route protocol pbr! Link Range Utilization Keep the usage on a set of exit links within a certain percentage range of each other Global Policies Apply for the rest of the traffic Load Balancing enabled by default IOS 15.2(3)T KRST
79 Target Discovery Hub Site Jitter probes Generated /16 R3#sh pfr master active-probes target-discovery PfR Master Controller active-probes (TD) Border = Border Roter running this probe -Peer = Remote associated with this target Type = Probe Type Target = Target Address TPort = Target Port N - Not applicable Destination Site Peer Addresses: Voice, Video, Critical SLA Shadow Router IP Sla Responder The Rest of the Traffic -Peer Targets The following Probes are running: WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) Border Idx State -Peer Type Target TPort TD-Actv jitter TD-Actv jitter TD-Actv jitter /B TD-Actv jitter R TD-Actv jitter TD-Actv jitter R3# / /16 / /16 KRST
80 PfR Master Controller Database Traffic Classes Performance #sh pfr master traffic-class OER Prefix Statistics: Pas - Passive, Act - Active, S - Short term, L - Long term, Dly - Delay (ms), P - Percentage below threshold, Jit - Jitter (ms), MOS - Mean Opinion Score Los - Packet Loss (packets-per-million), Un - Unreachable (flows-per-million), E - Egress, I - Ingress, Bw - Bandwidth (kbps), N - Not applicable U - unknown, * - uncontrolled, + - control more - active probe all # - Prefix monitor mode is Special, & - Blackholed Prefix % - Force Next-Hop, ^ - Prefix is denied Passive Delay (from TCP Syn/Ack) DstPrefix Appl_ID Dscp Prot SrcPort DstPort SrcPrefix Flags State Time Curr CurrI/F Protocol PasSDly PasLDly PasSUn PasLUn PasSLos PasLLos EBw IBw ActSDly ActLDly ActSUn ActLUn ActSJit ActPMOS ActSLos ActLLos /24 N defa 256 N N /0 INPOLICY Et0/1 P N N N N Active Delay (from probes) /24 N ef 256 N N /0 INPOLICY Et0/1 P N N N N /24 N af N N /0 INPOLICY Et0/1 P N N N N KRST-2362 PfR has calculated the per traffic class (which is per /24 destination in this case) egress bandwidth usage as well as the ingress 80
81 PfR Master Controller Database Specific Traffic Class Performance #sh pfr master traffic-class performance ip any /24 dscp ef ============================================================================================== Traffic-class: Destination Prefix : /24 Source Prefix : /0 Destination Port : N Source Port : N DSCP : ef Protocol : 256 Application Name: : N/A General: Control State : Controlled using P Traffic-class status : INPOLICY Current Exit : interface Et0/1, Tie breaker was None Time on current exit : 0d 0:9:32 Time remaining in current state seconds Last uncontrol reason : Probe frequency changed Time since last uncontrol : 0d 1:12:1 Traffic-class type : Learned Improper config : None Last Out-of-Policy event: No Out-of-Policy Event Average Passive Performance Current Exit: (Average for last 5 minutes) Unreachable : 0% -- Threshold: 50% Loss : 0 ppm -- Threshold: ppm Delay : 52 msecs -- Threshold: 200 msecs Egress BW : 7 kbps Ingress BW : 5 kbps Time since last update : 0d 0:0:24 Average Active Performance Current Exit: (Average for last 5 minutes) Unreachable : 0% -- Threshold: 50% Loss : 0 ppm -- Threshold: ppm Jitter : 0 msec -- Threshold: 3000 msec Delay : 52 msec -- Threshold: 200 msec Last Resolver Decision: Interface Status Reason Performance Threshold Et0/1 Eliminated Link Group N/A N/A Et0/1 Best Exit Unreachable N/A N/A ============================================================================================== # TC Performance Performance Details Last Resolver decisions Filter on any type of traffic KRST
82 Enforcing the Path Dynamic P instructs s to apply Dynamic Route Maps on their inside interfaces Direct connection between s is needed Direct connection GRE/mGRE tunnel Voice, Video, Critical WAN1 (IP-VPN) WAN2 (IPVPN, DMVPN) The Rest of the Traffic / / / KRST
83 P Example Troubleshooting Path Enforcement R4#sh route-map dynamic route-map OER_INTERNAL_RMAP, permit, sequence 0, identifier Match clauses: ip address (access-lists): oer#1 Set clauses: ip next-hop interface Ethernet0/0 Policy routing matches: packets, bytes route-map OER_INTERNAL_RMAP, permit, sequence 1, identifier Match clauses: ip address (access-lists): oer#2 Set clauses: ip next-hop interface Ethernet0/1 Policy routing matches: packets, bytes Current active dynamic routemaps = 1 R4# R4#sh ip access-lists dynamic Extended IP access list oer# permit ip any dscp af31 (17981 matches) permit ip any dscp af31 (17984 matches) permit ip any dscp af31 (17975 matches) permit ip any dscp ef (17938 matches) permit ip any dscp ef (18002 matches) Extended IP access list oer# permit ip any dscp af31 (15000 matches) permit ip any dscp default (15034 matches) permit ip any dscp default (15958 matches) permit ip any dscp default (15937 matches) permit ip any dscp default (15966 matches) KRST-2362 R4# A dynamic route-map is created by PfR to enforce traffic to the chosen exit point Next hop = R5 A dynamic route-map is created by PfR to enforce traffic to the chosen exit point Next hop = WAN 83
84 Design Considerations Scalability on the Hub Number of remote sites Number of jitter probes CPU Impact on the Border Routers Probing Frequency Impact on the failover time CPU Impact on the Border Routers Probes WAN1 (IP-VPN) SLA WAN2 (IPVPN, DMVPN) Shadow Router IP Sla Responder Probes Number of Traffic Classes Number of Remote Sites Number of Prefixes per site Number of applications per site CPU Impact on the Master Controller / / / KRST
85 Test Results with Target Discovery ASR1006 with RP2 Branches TCs per Branch Traffic Classes Prefixes per branch CPU CPU Number of probes per branch: 2 Packets per probe: 60 Probe frequency: 4 KRST
86 Test Results with Target Discovery ASR1002-X Branches Traffic Classes Prefixes per branch Application per prefix Learn-list configured on CPU (avg/peak) CPU (Avg/Peak) /54 34/ /69 50/54 ASR1002-X XE 3.8 Probe Frequency: 20 sec Probe Packets: 20 KRST
87 NETWORK MANAGEMENT
88 PfR NetFlow v9 Export PfR NetFlow v9 Export The PfR NetFlow v9 Exporter resides on the PfR Master Controller Exports Passive Metrics, Active Metrics, Events, Configuration PfR SNMP MIB (Traps coming) TC as a row of cpfrtrafficclasstable TC Status as a row of cpfrtrafficclassstatustable performance metrics as a row of cpfrtrafficclassmetricstable NMS application vendors engaged! Cisco Prime Assurance engaged! WAN1 (IP-VPN) NetFlow SNMP Read WAN2 (IPVPN, DMVPN) / / / KRST
89 Configuration Templates For Your Reference Traffic Class Config Internal Interface Config Reason Config Encoded Traffic-Class ID, Source prefix, Source mask, Destination prefix, Destination mask, Protocol, DSCP, Source port min, Source port max, Destination port min, Destination port max, Application Name, Policy id address Internal interface id interface name External Interface Config Reason id Reason text Policy Config Policy id pfr-map name State Threshold Priority Variance MOS Link group Name address, External interface id, interface name, Link capacity, RSVP reserved bandwidth pool, Maximum ingress bandwidth, Maximum egress bandwidth, BGP Community Link group Name, Cost nickname, Cost type Cost discard rollup count KRST
90 Passive/Active Reports For Your Reference Passive Update Encoded Traffic-Class ID Address, External interface ID, Direction State First switched time Last switched time Sum of round-trip-time, Samples, Loss, Unreachable, Bytes, Packets, Flows, Next hop address Passive Performance Encoded Traffic-Class ID Address, External interface ID Direction Routing protocol State Reason ID Timestamp Left time Passive short-term unreachable Passive short-term loss Passive short-term round-trip-time Passive long-term unreachable Passive long-term loss Passive long-term round-trip-time Egress bandwidth Ingress bandwidth BGP Prepend BGP Community Active Update Encoded Traffic-Class ID Address External Interface ID State Average round-trip-time Minimum round-trip-time Maximum round-trip-time Sum of round-trip-time Unreachable Loss Jitter MOS below counts MOS total counts Initiations Completes Active Performance Encoded Traffic-Class ID Address External interface ID Routing protocol State Reason ID Timestamp Left time Active short-term unreachable Active short-term loss Active short-term round-trip-time Active short-term jitter Active Short-term MOS Active long-term unreachable Active long-term loss Active long-term round-trip-time KRST
91 Interface Update, Various For Your Reference External Interface Update Internal Interface Update Traffic Class Performance Cost Minimization Performance Address External interface ID State Reason ID Egress bandwidth Ingress bandwidth Cost target bandwidth RSVP bandwidth pool TC total counts Controlled TC counts In Policy TC counts Controlled bandwidth Address Internal interface ID State Reason ID Up/Down Alert address State Encoded Traffic-Class ID address External interface ID Direction Routing protocol State Reason ID Timestamp Left time BGP Prepend BGP Community Address External interface ID State Timestamp Counter of left rollup Ingress rollup bandwidth (kbps) Egress rollup bandwidth (kbps) k-th rollup bandwidth (kbps) k-th tier percentage (%) k-th fee KRST
92 Leverage NetFlow Partners Eco-system Traffic Analysis Denial of Service Billing More info: KRST
93 PfR Reporting Tools Plixer ActionPacked NetFlow Partners Plixer, ActionPacked Cisco Prime Infrastructure 2.x Future LiveAction KRST
94 CONCLUSION
95 PfR Platform Support Cisco ASR 1000 in IOS-XE in IOS-XE Cisco 1900 Cisco , 12.4T, Cisco 2900 Cisco , 12.4T 15M/T Cisco 3900 Cisco , 12.4T 15M/T Cisco 3900 Cisco , 12.4T 15M/T 15M/T Cisco (33)SXH (Deprecated) Cisco (33)SRB (Limited Support) Cisco 7200-NPE-G2, , 12.4T 15M/T KRST
96 PfR Software Packaging New Cisco ISR G2 Simplified Feature Sets New ISR-G2 1900, 2900, 3900 A single IOS Universal Image for all ISR Generation 2 ISR Platforms PfR is within the DATA package. Classic Cisco IOS Software Feature Sets Existing ISR 1800, 2800, 3800, 7200 PfR ASR 1000 Series ASR1001: Use Universal Image (U or UK9) with Advanced IP Services (AIS) or Advanced Enterprise Services (AES) technology package license All other ASR1000 (ASR1002-F, ASR1002, ASR1004, ASR1006, ASR1013): Use Advanced IP Services (AIS/AISK9) or Advanced Enterprise Services (AES/AESK9) images KRST
97 Technical References AVC Portal Docwiki Performance Routing Home Technology Overview, Solution Guides, Troubleshooting Guides, FAQ Performance Routing Technology Overview Performance Routing Solution Guides Performance Routing Troubleshooting Guide Configuration Understanding Performance Routing Basic Configuration Advanced Configuration KRST
98 Complete Your Online Session Evaluation Give us your feedback and you could win fabulous prizes. Winners announced daily. Receive 20 Cisco Daily Challenge points for each session evaluation you complete. Complete your session evaluation online now through either the mobile app or internet kiosk stations. Maximize your Cisco Live experience with your free Cisco Live 365 account. Download session PDFs, view sessions on-demand and participate in live activities throughout the year. Click the Enter Cisco Live 365 button in your Cisco Live portal to log in. KRST
Cisco recommends that you have basic knowledge of Performance Routing (PfR).
 Contents Introduction Prerequisites Requirements Components Used Background Information Passive Monitoring Active Monitoring Hybrid Mode Configure Network Diagram Relevant Configuration Verify Passive
Contents Introduction Prerequisites Requirements Components Used Background Information Passive Monitoring Active Monitoring Hybrid Mode Configure Network Diagram Relevant Configuration Verify Passive
Static Application Mapping Using Performance Routing
 Static Application Mapping Using Performance Routing The OER - Application Aware Routing with Static Application Mapping feature introduces the ability to configure standard applications using just one
Static Application Mapping Using Performance Routing The OER - Application Aware Routing with Static Application Mapping feature introduces the ability to configure standard applications using just one
Chapter H through R. loss (PfR), page 28. load-balance, page 23 local (PfR), page 24 logging (PfR), page 26
 Chapter H through R holddown (PfR), page 3 host-address (PfR), page 5 hub, page 7 inside bgp (PfR), page 8 interface (PfR), page 10 interface tunnel (global configuration), page 12 jitter (PfR), page 13
Chapter H through R holddown (PfR), page 3 host-address (PfR), page 5 hub, page 7 inside bgp (PfR), page 8 interface (PfR), page 10 interface tunnel (global configuration), page 12 jitter (PfR), page 13
set active-probe (PfR)
 set active-probe (PfR) set active-probe (PfR) To configure a Performance Routing (PfR) active probe with a forced target assignment within a PfR map, use the set active-probe command in PfR map configuration
set active-probe (PfR) set active-probe (PfR) To configure a Performance Routing (PfR) active probe with a forced target assignment within a PfR map, use the set active-probe command in PfR map configuration
Cisco Performance Routing
 Cisco Performance Routing As enterprise organizations grow their businesses, the demand for real-time application performance and a better application experience for users increases. For example, voice
Cisco Performance Routing As enterprise organizations grow their businesses, the demand for real-time application performance and a better application experience for users increases. For example, voice
BGP Inbound Optimization Using Performance Routing
 BGP Inbound Optimization Using Performance Routing The PfR BGP Inbound Optimization feature introduced support for the best entrance selection for traffic that originates from prefixes outside an autonomous
BGP Inbound Optimization Using Performance Routing The PfR BGP Inbound Optimization feature introduced support for the best entrance selection for traffic that originates from prefixes outside an autonomous
Performance Routing Version 3 Configuration Guide
 First Published: 2014-07-22 Last Modified: 2016-04-20 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
First Published: 2014-07-22 Last Modified: 2016-04-20 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
OER uses the following default value if this command is not configured or if the no form of this command is entered: timer: 300
 holddown holddown To configure the Optimized Edge Routing (OER) prefix route dampening timer to set the minimum period of time that a new exit must be used before an alternate exit can be selected, use
holddown holddown To configure the Optimized Edge Routing (OER) prefix route dampening timer to set the minimum period of time that a new exit must be used before an alternate exit can be selected, use
Configuring Basic Performance Routing
 Performance Routing (PfR) provides additional intelligence to classic routing technologies to track the performance of, or verify the quality of, a path between two devices over a Wide Area Networking
Performance Routing (PfR) provides additional intelligence to classic routing technologies to track the performance of, or verify the quality of, a path between two devices over a Wide Area Networking
Optimized Edge Routing Configuration Guide, Cisco IOS Release 15.1MT
 Optimized Edge Routing Configuration Guide, Cisco IOS Release 15.1MT Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800
Optimized Edge Routing Configuration Guide, Cisco IOS Release 15.1MT Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800
IWAN Under the Hood - Next Gen Performance Routing and DMVPN. David Prall, Communication Architect CCIE 6508 (R&S/SP/Security)
 IWAN Under the Hood - Next Gen Performance Routing and DMVPN David Prall, Communication Architect CCIE 6508 (R&S/SP/Security) dprall@cisco.com Agenda Introduction Intelligent Path Control PfRv3 Operations
IWAN Under the Hood - Next Gen Performance Routing and DMVPN David Prall, Communication Architect CCIE 6508 (R&S/SP/Security) dprall@cisco.com Agenda Introduction Intelligent Path Control PfRv3 Operations
Performance Routing Configuration Guide, Cisco IOS Release 15M&T
 First Published: November 29, 2012 Last Modified: March 25, 2013 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS
First Published: November 29, 2012 Last Modified: March 25, 2013 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS
PfRv3 Zero SLA Support
 The Performance Routing v3 (PfRv3) Zero SLA Support feature enables users to reduce probing frequency on various ISP links, such as 3G, 4G, and LTE When the Zero SLA (0-SLA) feature is configured on an
The Performance Routing v3 (PfRv3) Zero SLA Support feature enables users to reduce probing frequency on various ISP links, such as 3G, 4G, and LTE When the Zero SLA (0-SLA) feature is configured on an
PfRv3 Path of Last Resort
 The PfRv3 path of last resort feature allows the traffic to be routed to the path of last resort. Feature Information for, page 1 Restrictions for, page 2 Information About, page 2 How to Configure, page
The PfRv3 path of last resort feature allows the traffic to be routed to the path of last resort. Feature Information for, page 1 Restrictions for, page 2 Information About, page 2 How to Configure, page
Intelligent WAN 2.0 Traffic Independent Design and Intelligent Path Selection
 Intelligent WAN 2.0 Traffic Independent Design and Intelligent Path Selection Tech-WAN Jaromír Pilař Consulting Systems Engineer, CCIE #2910 Cisco Intelligent WAN (IWAN) AVC Private Cloud ISR-AX 3G/4G-LTE
Intelligent WAN 2.0 Traffic Independent Design and Intelligent Path Selection Tech-WAN Jaromír Pilař Consulting Systems Engineer, CCIE #2910 Cisco Intelligent WAN (IWAN) AVC Private Cloud ISR-AX 3G/4G-LTE
Implementing Next Generation Performance Routing PfRv3
 Implementing Next Generation Performance Routing PfRv3 Jean-Marc Barozet Technical Leader IWAN Solution Group Agenda Business Trends PfRv3 Principles Monitoring Details The Life of a Packet Path Enforcement
Implementing Next Generation Performance Routing PfRv3 Jean-Marc Barozet Technical Leader IWAN Solution Group Agenda Business Trends PfRv3 Principles Monitoring Details The Life of a Packet Path Enforcement
Cloud Intelligent Network
 Dubrovnik, Croatia, South East Europe 20-22 May, 2013 Cloud Intelligent Network Mitko Vasilev CIN Lead Central Europe mitko@cisco.com 2011 2012 Cisco and/or its affiliates. All rights reserved. 1 New Application
Dubrovnik, Croatia, South East Europe 20-22 May, 2013 Cloud Intelligent Network Mitko Vasilev CIN Lead Central Europe mitko@cisco.com 2011 2012 Cisco and/or its affiliates. All rights reserved. 1 New Application
Pressures on the WAN
 IWAN Radek Boch, Systems Engineer, Cisco, rboch@cisco.com CCIE#7095 14.11.2013 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 1 The Application Landscape Is Changing Applications Are
IWAN Radek Boch, Systems Engineer, Cisco, rboch@cisco.com CCIE#7095 14.11.2013 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 1 The Application Landscape Is Changing Applications Are
Intelligent WAN : CVU update
 Intelligent WAN : CVU update Deliver enhanced mobile experience at the branch with Intelligent WAN Soren D. Andreasen (sandreas@cisco.com) Technical Solution Architect CCIE# 3252 Agenda IWAN 2.0/2.1 overview
Intelligent WAN : CVU update Deliver enhanced mobile experience at the branch with Intelligent WAN Soren D. Andreasen (sandreas@cisco.com) Technical Solution Architect CCIE# 3252 Agenda IWAN 2.0/2.1 overview
Setting Up OER Network Components
 Setting Up OER Network Components First Published: January 29, 2007 Last Updated: August 21, 2007 This module describes the concepts and tasks to help you set up the network components required for an
Setting Up OER Network Components First Published: January 29, 2007 Last Updated: August 21, 2007 This module describes the concepts and tasks to help you set up the network components required for an
PfR Voice Traffic Optimization Using Active Probes
 PfR Voice Traffic Optimization Using Active Probes This module documents a Performance Routing (PfR) solution that supports outbound optimization of voice traffic based on the voice metrics, jitter and
PfR Voice Traffic Optimization Using Active Probes This module documents a Performance Routing (PfR) solution that supports outbound optimization of voice traffic based on the voice metrics, jitter and
Intelligent WAN Multiple Data Center Deployment Guide
 Cisco Validated design Intelligent WAN Multiple Data Center Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deployment Details...1 Deploying
Cisco Validated design Intelligent WAN Multiple Data Center Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deployment Details...1 Deploying
PfR Performance Routing. Massimiliano Sbaraglia
 PfR Performance Routing Massimiliano Sbaraglia PfR advantage PfR abilita i processi di routing su base best path (non più su prefix-destination) basandosi su definite policy; PfR potenzia i tradizionali
PfR Performance Routing Massimiliano Sbaraglia PfR advantage PfR abilita i processi di routing su base best path (non più su prefix-destination) basandosi su definite policy; PfR potenzia i tradizionali
Intelligent WAN Multiple VRFs Deployment Guide
 Cisco Validated design Intelligent WAN Multiple VRFs Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deploying the Cisco IWAN Multiple VRFs...
Cisco Validated design Intelligent WAN Multiple VRFs Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deploying the Cisco IWAN Multiple VRFs...
OER Commands. November Cisco IOS Optimized Edge Routing Command Reference OER-3
 OER-3 active-probe active-probe To configure an Optimized Edge Routing (OER) active probe for a target prefix, use the active-probe command in OER master controller configuration mode. To disable the active
OER-3 active-probe active-probe To configure an Optimized Edge Routing (OER) active probe for a target prefix, use the active-probe command in OER master controller configuration mode. To disable the active
Cisco IOS Optimized Edge Routing Command Reference
 First Published: 2007-01-29 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE
First Published: 2007-01-29 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE
Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT
 Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT The Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT feature supports the forwarding of packets from a standby
Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT The Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT feature supports the forwarding of packets from a standby
SD-WAN Deployment Guide (CVD)
 SD-WAN Deployment Guide (CVD) All Cisco Meraki security appliances are equipped with SD-WAN capabilities that enable administrators to maximize network resiliency and bandwidth efficiency. This guide introduces
SD-WAN Deployment Guide (CVD) All Cisco Meraki security appliances are equipped with SD-WAN capabilities that enable administrators to maximize network resiliency and bandwidth efficiency. This guide introduces
Transport Diversity: Performance Routing (PfR) Design Guide
 Transport Diversity: Performance Routing (PfR) Design Guide Cisco Validated Design I February 11, 2008 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Transport Diversity: Performance Routing (PfR) Design Guide Cisco Validated Design I February 11, 2008 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Intelligent WAN Deployment Guide
 Cisco Validated design Intelligent WAN Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deployment Details...1 Configuring DMVPN Hub Router...2
Cisco Validated design Intelligent WAN Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deployment Details...1 Configuring DMVPN Hub Router...2
Cisco IOS Performance Routing Version 3 Command Reference
 First Published: 2017-04-07 Last Modified: 2017-04-07 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
First Published: 2017-04-07 Last Modified: 2017-04-07 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
ARCHIVED DOCUMENT. - The topics in the document are now covered by more recent content.
 ARCHIVED DOCUMENT This document is archived and should only be used as a historical reference and should not be used for new deployments for one of the following reasons: - The topics in the document are
ARCHIVED DOCUMENT This document is archived and should only be used as a historical reference and should not be used for new deployments for one of the following reasons: - The topics in the document are
PfRv3 Inter-DC Optimization
 The PfRv3-Inter-DC-Optimization feature provides support by routing traffic from a hub site to another for specific traffic types such as data, voice, video, etc. Feature Information for PfRv3-Inter-DC-Optimization,
The PfRv3-Inter-DC-Optimization feature provides support by routing traffic from a hub site to another for specific traffic types such as data, voice, video, etc. Feature Information for PfRv3-Inter-DC-Optimization,
Multihoming with BGP and NAT
 Eliminating ISP as a single point of failure www.noction.com Table of Contents Introduction 1. R-NAT Configuration 1.1 NAT Configuration 5. ISPs Routers Configuration 3 15 7 7 5.1 ISP-A Configuration 5.2
Eliminating ISP as a single point of failure www.noction.com Table of Contents Introduction 1. R-NAT Configuration 1.1 NAT Configuration 5. ISPs Routers Configuration 3 15 7 7 5.1 ISP-A Configuration 5.2
Q. What technologies does Cisco WAAS Express use to optimize traffic? A. Cisco WAAS Express optimizes WAN bandwidth using these technologies:
 Q&A Cisco WAAS Express General Q. What is Cisco Wide Area Application Services (WAAS) Express? A. Cisco WAAS Express extends the Cisco WAAS product portfolio with a small-footprint, cost-effective solution
Q&A Cisco WAAS Express General Q. What is Cisco Wide Area Application Services (WAAS) Express? A. Cisco WAAS Express extends the Cisco WAAS product portfolio with a small-footprint, cost-effective solution
Návrh inteligentní WAN sítě
 Návrh inteligentní WAN sítě EN2 Jaromír Pilař, CSE Agenda Úvod a základní pilíře inteligentní WAN sítě Tranport Independent Design Inteligentní výběr cesty Shrnutí Presentation Title: Intelligent WAN:
Návrh inteligentní WAN sítě EN2 Jaromír Pilař, CSE Agenda Úvod a základní pilíře inteligentní WAN sítě Tranport Independent Design Inteligentní výběr cesty Shrnutí Presentation Title: Intelligent WAN:
WAN Edge MPLSoL2 Service
 4 CHAPTER While Layer 3 VPN services are becoming increasing popular as a primary connection for the WAN, there are a much larger percentage of customers still using Layer 2 services such Frame-Relay (FR).
4 CHAPTER While Layer 3 VPN services are becoming increasing popular as a primary connection for the WAN, there are a much larger percentage of customers still using Layer 2 services such Frame-Relay (FR).
MPLS VPN--Inter-AS Option AB
 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service provider
The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service provider
Highly Available Wide Area Network Design
 Highly Available Wide Area Network Design David Prall, Communications Architect dprall@cisco.com Agenda Introduction Cisco IOS and IP Routing Convergence Techniques Design and Deployment Final Wrap Up
Highly Available Wide Area Network Design David Prall, Communications Architect dprall@cisco.com Agenda Introduction Cisco IOS and IP Routing Convergence Techniques Design and Deployment Final Wrap Up
BGP Cost Community. Prerequisites for the BGP Cost Community Feature
 The feature introduces the cost extended community attribute. The cost community is a non-transitive extended community attribute that is passed to internal BGP (ibgp) and confederation peers but not to
The feature introduces the cost extended community attribute. The cost community is a non-transitive extended community attribute that is passed to internal BGP (ibgp) and confederation peers but not to
Cisco recommends that you have basic knowledge of Performance Routing (PfR).
 Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations R3 Master Hub Router R4 Hub Border Router R5 Hub Border Router R9 Branch Master Router R10 Branch
Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations R3 Master Hub Router R4 Hub Border Router R5 Hub Border Router R9 Branch Master Router R10 Branch
Performance Routing (PfR) Master Controller Redundancy Configuration
 Performance Routing (PfR) Master Controller Redundancy Configuration This application note provides an overview on how to configure a Performance Routing (PfR) master controller in a redundant configuration.
Performance Routing (PfR) Master Controller Redundancy Configuration This application note provides an overview on how to configure a Performance Routing (PfR) master controller in a redundant configuration.
IWAN APIC-EM Application Cisco Intelligent WAN
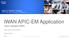 IWAN APIC-EM Application Cisco Intelligent WAN René og Per Cisco DK SE s Feb 23 th 2016 AVC MPLS Private Cloud 3G/4G-LTE Virtual Private Cloud Branch WAAS PfR Internet Public Cloud Control, Management,
IWAN APIC-EM Application Cisco Intelligent WAN René og Per Cisco DK SE s Feb 23 th 2016 AVC MPLS Private Cloud 3G/4G-LTE Virtual Private Cloud Branch WAAS PfR Internet Public Cloud Control, Management,
MPLS VPN Inter-AS Option AB
 First Published: December 17, 2007 Last Updated: September 21, 2011 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol
First Published: December 17, 2007 Last Updated: September 21, 2011 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol
Performance Routing Version 3 Commands
 Performance Routing Version 3 Commands advanced, page 3 bandwidth (interface configuration), page 4 border (VRF configuration), page 7 class (master controller configuration), page 8 collector, page 9
Performance Routing Version 3 Commands advanced, page 3 bandwidth (interface configuration), page 4 border (VRF configuration), page 7 class (master controller configuration), page 8 collector, page 9
CVP Enterprise Cisco SD-WAN Retail Profile (Hybrid WAN, Segmentation, Zone-Based Firewall, Quality of Service, and Centralized Policies)
 CVP CVP Enterprise Cisco SD-WAN Retail Profile (Hybrid WAN, Segmentation, Zone-Based Firewall, Quality of Service, and Centralized Policies) 2018 Cisco and/or its affiliates. All rights reserved. This
CVP CVP Enterprise Cisco SD-WAN Retail Profile (Hybrid WAN, Segmentation, Zone-Based Firewall, Quality of Service, and Centralized Policies) 2018 Cisco and/or its affiliates. All rights reserved. This
Intelligent WAN High Availability and Scalability Deployment Guide
 Cisco Validated design Intelligent WAN High Availability and Scalability Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deployment Details...1
Cisco Validated design Intelligent WAN High Availability and Scalability Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deployment Details...1
Technology Overview. Overview CHAPTER
 CHAPTER 2 Revised: July 29, 2013, This overview of AVC technology includes the following topics: Overview, page 2-1 AVC Features and Capabilities, page 2-2 AVC Architecture, page 2-4 Interoperability of
CHAPTER 2 Revised: July 29, 2013, This overview of AVC technology includes the following topics: Overview, page 2-1 AVC Features and Capabilities, page 2-2 AVC Architecture, page 2-4 Interoperability of
Monitoring and Analysis
 CHAPTER 3 Cisco Prime Network Analysis Module 5.1 has two types of dashboards: One type is the summary views found under the Monitor menu, and the other type is the over time views found under the Analyze
CHAPTER 3 Cisco Prime Network Analysis Module 5.1 has two types of dashboards: One type is the summary views found under the Monitor menu, and the other type is the over time views found under the Analyze
Connecting to a Service Provider Using External BGP
 Connecting to a Service Provider Using External BGP First Published: May 2, 2005 Last Updated: August 21, 2007 This module describes configuration tasks that will enable your Border Gateway Protocol (BGP)
Connecting to a Service Provider Using External BGP First Published: May 2, 2005 Last Updated: August 21, 2007 This module describes configuration tasks that will enable your Border Gateway Protocol (BGP)
IP SLAs Overview. Finding Feature Information. Information About IP SLAs. IP SLAs Technology Overview
 This module describes IP Service Level Agreements (SLAs). IP SLAs allows Cisco customers to analyze IP service levels for IP applications and services, to increase productivity, to lower operational costs,
This module describes IP Service Level Agreements (SLAs). IP SLAs allows Cisco customers to analyze IP service levels for IP applications and services, to increase productivity, to lower operational costs,
Performing Path Traces
 About Path Trace, page 1 Performing a Path Trace, page 13 Collecting QoS and Interface Statistics in a Path Trace, page 15 About Path Trace With Path Trace, the controller reviews and collects network
About Path Trace, page 1 Performing a Path Trace, page 13 Collecting QoS and Interface Statistics in a Path Trace, page 15 About Path Trace With Path Trace, the controller reviews and collects network
Borderless Networks. Tom Schepers, Director Systems Engineering
 Borderless Networks Tom Schepers, Director Systems Engineering Agenda Introducing Enterprise Network Architecture Unified Access Cloud Intelligent Network & Unified Services Enterprise Networks in Action
Borderless Networks Tom Schepers, Director Systems Engineering Agenda Introducing Enterprise Network Architecture Unified Access Cloud Intelligent Network & Unified Services Enterprise Networks in Action
Cisco Intelligent WAN
 Cisco Intelligent WAN Ľuboš Lontoš Systems Engineer SP/R&S ALEF NULA a.s. Agenda Cisco iwan Architecture Overview Tranport Independent Design Intelligent Path Control- PfRv3 Product PorMolio Tradi4onal
Cisco Intelligent WAN Ľuboš Lontoš Systems Engineer SP/R&S ALEF NULA a.s. Agenda Cisco iwan Architecture Overview Tranport Independent Design Intelligent Path Control- PfRv3 Product PorMolio Tradi4onal
Configuring AVC to Monitor MACE Metrics
 This feature is designed to analyze and measure network traffic for WAAS Express. Application Visibility and Control (AVC) provides visibility for various applications and the network to central network
This feature is designed to analyze and measure network traffic for WAAS Express. Application Visibility and Control (AVC) provides visibility for various applications and the network to central network
Configuring BGP community 43 Configuring a BGP route reflector 44 Configuring a BGP confederation 44 Configuring BGP GR 45 Enabling Guard route
 Contents Configuring BGP 1 Overview 1 BGP speaker and BGP peer 1 BGP message types 1 BGP path attributes 2 BGP route selection 6 BGP route advertisement rules 6 BGP load balancing 6 Settlements for problems
Contents Configuring BGP 1 Overview 1 BGP speaker and BGP peer 1 BGP message types 1 BGP path attributes 2 BGP route selection 6 BGP route advertisement rules 6 BGP load balancing 6 Settlements for problems
InterAS Option B. Information About InterAS. InterAS and ASBR
 This chapter explains the different InterAS option B configuration options. The available options are InterAS option B, InterAS option B (with RFC 3107), and InterAS option B lite. The InterAS option B
This chapter explains the different InterAS option B configuration options. The available options are InterAS option B, InterAS option B (with RFC 3107), and InterAS option B lite. The InterAS option B
cisco. Number: Passing Score: 800 Time Limit: 120 min.
 300-101.cisco Number: 300-101 Passing Score: 800 Time Limit: 120 min Exam A QUESTION 1 Examine the following output of the show ip ospf interface command. What would be the effect of executing the auto-cost
300-101.cisco Number: 300-101 Passing Score: 800 Time Limit: 120 min Exam A QUESTION 1 Examine the following output of the show ip ospf interface command. What would be the effect of executing the auto-cost
Implementing Cisco IP Routing
 ROUTE Implementing Cisco IP Routing Volume 3 Version 1.0 Student Guide Text Part Number: 97-2816-02 DISCLAIMER WARRANTY: THIS CONTENT IS BEING PROVIDED AS IS. CISCO MAKES AND YOU RECEIVE NO WARRANTIES
ROUTE Implementing Cisco IP Routing Volume 3 Version 1.0 Student Guide Text Part Number: 97-2816-02 DISCLAIMER WARRANTY: THIS CONTENT IS BEING PROVIDED AS IS. CISCO MAKES AND YOU RECEIVE NO WARRANTIES
BGP Commands: M through N
 match additional-paths advertise-set, on page 3 match as-path, on page 6 match community, on page 8 match extcommunity, on page 10 match local-preference, on page 12 match policy-list, on page 14 match
match additional-paths advertise-set, on page 3 match as-path, on page 6 match community, on page 8 match extcommunity, on page 10 match local-preference, on page 12 match policy-list, on page 14 match
Application Visibility and Control in Enterprise WAN
 Application Visibility and Control in Enterprise WAN Liad Ofek Manager, Technical Marketing Application Experience Services Enterprise Networking Group Cisco Emerging Branch Demands The Application Landscape
Application Visibility and Control in Enterprise WAN Liad Ofek Manager, Technical Marketing Application Experience Services Enterprise Networking Group Cisco Emerging Branch Demands The Application Landscape
BGP Link Bandwidth. Finding Feature Information. Prerequisites for BGP Link Bandwidth
 The Border Gateway Protocol (BGP) Link Bandwidth feature is used to advertise the bandwidth of an autonomous system exit link as an extended community. This feature is configured for links between directly
The Border Gateway Protocol (BGP) Link Bandwidth feature is used to advertise the bandwidth of an autonomous system exit link as an extended community. This feature is configured for links between directly
FlexVPN HA Dual Hub Configuration Example
 FlexVPN HA Dual Hub Configuration Example Document ID: 118888 Contributed by Piotr Kupisiewicz, Wen Zhang, and Frederic Detienne, Cisco TAC Engineers. Apr 08, 2015 Contents Introduction Prerequisites Requirements
FlexVPN HA Dual Hub Configuration Example Document ID: 118888 Contributed by Piotr Kupisiewicz, Wen Zhang, and Frederic Detienne, Cisco TAC Engineers. Apr 08, 2015 Contents Introduction Prerequisites Requirements
Quality of Service. Create QoS Policy CHAPTER26. Create QoS Policy Tab. Edit QoS Policy Tab. Launch QoS Wizard Button
 CHAPTER26 The (QoS) Wizard allows a network administrator to enable (QoS) on the router s WAN interfaces. QoS can also be enabled on IPSec VPN interfaces and tunnels. The QoS edit windows enables the administrator
CHAPTER26 The (QoS) Wizard allows a network administrator to enable (QoS) on the router s WAN interfaces. QoS can also be enabled on IPSec VPN interfaces and tunnels. The QoS edit windows enables the administrator
Using NetFlow Filtering or Sampling to Select the Network Traffic to Track
 Using NetFlow Filtering or Sampling to Select the Network Traffic to Track First Published: June 19, 2006 Last Updated: December 17, 2010 This module contains information about and instructions for selecting
Using NetFlow Filtering or Sampling to Select the Network Traffic to Track First Published: June 19, 2006 Last Updated: December 17, 2010 This module contains information about and instructions for selecting
IPv6 Switching: Provider Edge Router over MPLS
 Multiprotocol Label Switching (MPLS) is deployed by many service providers in their IPv4 networks. Service providers want to introduce IPv6 services to their customers, but changes to their existing IPv4
Multiprotocol Label Switching (MPLS) is deployed by many service providers in their IPv4 networks. Service providers want to introduce IPv6 services to their customers, but changes to their existing IPv4
BGP can also be used for carrying routing information for IPv6 prefix over IPv6 networks.
 This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Border Gateway Protocol (). About, page 1 Guidelines for, page
This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Border Gateway Protocol (). About, page 1 Guidelines for, page
Exam Questions Demo Cisco. Exam Questions CCIE SP CCIE Service Provider Written Exam
 Cisco Exam Questions 400-201 CCIE SP CCIE Service Provider Written Exam Version:Demo 1. Which is one difference between H-VPLS and VPLS? A. VPLS is a point-to-point Layer-2 services and H-VPLS is a multipoint
Cisco Exam Questions 400-201 CCIE SP CCIE Service Provider Written Exam Version:Demo 1. Which is one difference between H-VPLS and VPLS? A. VPLS is a point-to-point Layer-2 services and H-VPLS is a multipoint
Configuring Advanced BGP
 CHAPTER 6 This chapter describes how to configure advanced features of the Border Gateway Protocol (BGP) on the Cisco NX-OS switch. This chapter includes the following sections: Information About Advanced
CHAPTER 6 This chapter describes how to configure advanced features of the Border Gateway Protocol (BGP) on the Cisco NX-OS switch. This chapter includes the following sections: Information About Advanced
Chapter 17 BGP4 Commands
 Chapter 17 BGP4 Commands NOTE: This chapter describes commands in the BGP configuration level, which is present on HP devices that support IPv4 only. For information about BGP commands and configuration
Chapter 17 BGP4 Commands NOTE: This chapter describes commands in the BGP configuration level, which is present on HP devices that support IPv4 only. For information about BGP commands and configuration
Lab Guide CIERS1. Overview. Outline
 CIERS1 Lab Guide Overview Outline This guide presents the instructions and other information concerning the activities for this course. You can find the recommended solutions in the Answer Key. This guide
CIERS1 Lab Guide Overview Outline This guide presents the instructions and other information concerning the activities for this course. You can find the recommended solutions in the Answer Key. This guide
Chapter 13 Configuring BGP4
 Chapter 13 Configuring BGP4 This chapter provides details on how to configure Border Gateway Protocol version 4 (BGP4) on HP products using the CLI and the Web management interface. BGP4 is supported on
Chapter 13 Configuring BGP4 This chapter provides details on how to configure Border Gateway Protocol version 4 (BGP4) on HP products using the CLI and the Web management interface. BGP4 is supported on
Configuration prerequisites 45 Configuring BGP community 45 Configuring a BGP route reflector 46 Configuring a BGP confederation 46 Configuring BGP
 Contents Configuring BGP 1 Overview 1 BGP speaker and BGP peer 1 BGP message types 1 BGP path attributes 2 BGP route selection 6 BGP route advertisement rules 6 BGP load balancing 6 Settlements for problems
Contents Configuring BGP 1 Overview 1 BGP speaker and BGP peer 1 BGP message types 1 BGP path attributes 2 BGP route selection 6 BGP route advertisement rules 6 BGP load balancing 6 Settlements for problems
CertifyMe. CertifyMe
 CertifyMe Number: 642-661 Passing Score: 800 Time Limit: 120 min File Version: 7.6 http://www.gratisexam.com/ CertifyMe-642-661 Exam A QUESTION 1 Exhibit: Certkiller router#show ip route Codes: C - connected,
CertifyMe Number: 642-661 Passing Score: 800 Time Limit: 120 min File Version: 7.6 http://www.gratisexam.com/ CertifyMe-642-661 Exam A QUESTION 1 Exhibit: Certkiller router#show ip route Codes: C - connected,
Border Gateway Protocol - BGP
 BGP Fundamentals Border Gateway Protocol - BGP Runs over TCP (port 179) TCP connection required before BGP session Need to be reachable! Path vector routing protocol Best path selection based on path attributes
BGP Fundamentals Border Gateway Protocol - BGP Runs over TCP (port 179) TCP connection required before BGP session Need to be reachable! Path vector routing protocol Best path selection based on path attributes
Configuring Web Cache Services By Using WCCP
 CHAPTER 44 Configuring Web Cache Services By Using WCCP This chapter describes how to configure your Catalyst 3560 switch to redirect traffic to wide-area application engines (such as the Cisco Cache Engine
CHAPTER 44 Configuring Web Cache Services By Using WCCP This chapter describes how to configure your Catalyst 3560 switch to redirect traffic to wide-area application engines (such as the Cisco Cache Engine
BGP Support for Next-Hop Address Tracking
 The feature is enabled by default when a supporting Cisco software image is installed. BGP next-hop address tracking is event driven. BGP prefixes are automatically tracked as peering sessions are established.
The feature is enabled by default when a supporting Cisco software image is installed. BGP next-hop address tracking is event driven. BGP prefixes are automatically tracked as peering sessions are established.
Configuring BGP on Cisco Routers Volume 1
 Volume 1 I. Course Introduction A. Overview/Learner Skills and Knowledge B. Course Flow C. Additional References 1. Cisco Glossary of Terms D. Your Training Curriculum II. BGP Overview III. Introducing
Volume 1 I. Course Introduction A. Overview/Learner Skills and Knowledge B. Course Flow C. Additional References 1. Cisco Glossary of Terms D. Your Training Curriculum II. BGP Overview III. Introducing
Cisco Service Advertisement Framework Deployment Guide
 Cisco Service Advertisement Framework Deployment Guide What You Will Learn Cisco Service Advertisement Framework (SAF) is a network-based, scalable, bandwidth-efficient approach to service advertisement
Cisco Service Advertisement Framework Deployment Guide What You Will Learn Cisco Service Advertisement Framework (SAF) is a network-based, scalable, bandwidth-efficient approach to service advertisement
Troubleshooting High CPU Caused by the BGP Scanner or BGP Router Process
 Troubleshooting High CPU Caused by the BGP Scanner or BGP Router Process Document ID: 107615 Contents Introduction Before You Begin Conventions Prerequisites Components Used Understanding BGP Processes
Troubleshooting High CPU Caused by the BGP Scanner or BGP Router Process Document ID: 107615 Contents Introduction Before You Begin Conventions Prerequisites Components Used Understanding BGP Processes
Configuring Data Export for Flexible NetFlow with Flow Exporters
 Configuring Data Export for Flexible NetFlow with Flow Exporters Last Updated: November 29, 2012 This document contains information about and instructions for configuring flow exporters to export Flexible
Configuring Data Export for Flexible NetFlow with Flow Exporters Last Updated: November 29, 2012 This document contains information about and instructions for configuring flow exporters to export Flexible
CCIE Routing and Switching (v5.0)
 400-101 - CCIE Routing and Switching (v5.0) 1. Which two statements about MAC ACLs are true? (Choose two.) A. They support only inbound filtering. B. They support both inbound and outbound filtering. C.
400-101 - CCIE Routing and Switching (v5.0) 1. Which two statements about MAC ACLs are true? (Choose two.) A. They support only inbound filtering. B. They support both inbound and outbound filtering. C.
Contents. BGP commands 1
 Contents BGP commands 1 address-family ipv4 1 address-family ipv6 2 address-family link-state 3 advertise-rib-active 4 aggregate 5 balance 7 balance as-path-neglect 9 bestroute as-path-neglect 10 bestroute
Contents BGP commands 1 address-family ipv4 1 address-family ipv6 2 address-family link-state 3 advertise-rib-active 4 aggregate 5 balance 7 balance as-path-neglect 9 bestroute as-path-neglect 10 bestroute
Configuring Performance Routing Cost Policies
 Configuring Performance Routing Cost Policies Last Updated: October 10, 2011 This module describes how to configure and apply Cisco IOS Performance Routing (PfR) cost policies. Performance Routing is an
Configuring Performance Routing Cost Policies Last Updated: October 10, 2011 This module describes how to configure and apply Cisco IOS Performance Routing (PfR) cost policies. Performance Routing is an
MPLS VPN Carrier Supporting Carrier Using LDP and an IGP
 MPLS VPN Carrier Supporting Carrier Using LDP and an IGP Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) Carrier Supporting Carrier (CSC) enables one MPLS VPN-based service provider
MPLS VPN Carrier Supporting Carrier Using LDP and an IGP Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) Carrier Supporting Carrier (CSC) enables one MPLS VPN-based service provider
Configuring Cisco IOS IP SLAs Operations
 CHAPTER 50 This chapter describes how to use Cisco IOS IP Service Level Agreements (SLAs) on the switch. Cisco IP SLAs is a part of Cisco IOS software that allows Cisco customers to analyze IP service
CHAPTER 50 This chapter describes how to use Cisco IOS IP Service Level Agreements (SLAs) on the switch. Cisco IP SLAs is a part of Cisco IOS software that allows Cisco customers to analyze IP service
Implementing Cisco IP Routing (ROUTE)
 Implementing Cisco IP Routing (ROUTE) Foundation Learning Guide Foundation learning for the ROUTE 642-902 Exam Diane Teare Cisco Press 800 East 96th Street Indianapolis, IN 46240 Implementing Cisco IP
Implementing Cisco IP Routing (ROUTE) Foundation Learning Guide Foundation learning for the ROUTE 642-902 Exam Diane Teare Cisco Press 800 East 96th Street Indianapolis, IN 46240 Implementing Cisco IP
Configuring Cache Services Using the Web Cache Communication Protocol
 Configuring Cache Services Using the Web Cache Communication Protocol Finding Feature Information, page 1 Prerequisites for WCCP, page 1 Restrictions for WCCP, page 2 Information About WCCP, page 3 How
Configuring Cache Services Using the Web Cache Communication Protocol Finding Feature Information, page 1 Prerequisites for WCCP, page 1 Restrictions for WCCP, page 2 Information About WCCP, page 3 How
Configuring Cisco IOS IP SLA Operations
 CHAPTER 58 This chapter describes how to use Cisco IOS IP Service Level Agreements (SLA) on the switch. Cisco IP SLA is a part of Cisco IOS software that allows Cisco customers to analyze IP service levels
CHAPTER 58 This chapter describes how to use Cisco IOS IP Service Level Agreements (SLA) on the switch. Cisco IP SLA is a part of Cisco IOS software that allows Cisco customers to analyze IP service levels
Configuring BGP. Cisco s BGP Implementation
 Configuring BGP This chapter describes how to configure Border Gateway Protocol (BGP). For a complete description of the BGP commands in this chapter, refer to the BGP s chapter of the Network Protocols
Configuring BGP This chapter describes how to configure Border Gateway Protocol (BGP). For a complete description of the BGP commands in this chapter, refer to the BGP s chapter of the Network Protocols
MPLS VPN C H A P T E R S U P P L E M E N T. BGP Advertising IPv4 Prefixes with a Label
 7 C H A P T E R S U P P L E M E N T This online supplement of Chapter 7 focuses on two important developments. The first one is Inter-Autonomous. Inter-Autonomous is a concept whereby two service provider
7 C H A P T E R S U P P L E M E N T This online supplement of Chapter 7 focuses on two important developments. The first one is Inter-Autonomous. Inter-Autonomous is a concept whereby two service provider
BGP Route-Map Continue
 The feature introduces the continue clause to BGP route-map configuration. The continue clause allows for more programmable policy configuration and route filtering and introduces the capability to execute
The feature introduces the continue clause to BGP route-map configuration. The continue clause allows for more programmable policy configuration and route filtering and introduces the capability to execute
BGP Commands on Cisco ASR 9000 Series Router
 This module describes the commands used to configure and monitor Border Gateway Protocol (BGP) on Cisco ASR 9000 Series Aggregation Services Routers using Cisco IOS XR software. The commands in this module
This module describes the commands used to configure and monitor Border Gateway Protocol (BGP) on Cisco ASR 9000 Series Aggregation Services Routers using Cisco IOS XR software. The commands in this module
CCIE Routing & Switching
 CCIE Routing & Switching Cisco Certified Internetwork Expert Routing and Switching (CCIE Routing and Switching) certifies the skills required of expert-level network engineers to plan, operate and troubleshoot
CCIE Routing & Switching Cisco Certified Internetwork Expert Routing and Switching (CCIE Routing and Switching) certifies the skills required of expert-level network engineers to plan, operate and troubleshoot
Cisco IOS Optimized Edge Routing Command Reference
 Cisco IOS Optimized Edge Routing Command Reference Release 12.4T Corporate Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800
Cisco IOS Optimized Edge Routing Command Reference Release 12.4T Corporate Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800
Intelligent WAN NetFlow Monitoring Deployment Guide
 Cisco Validated design Intelligent WAN NetFlow Monitoring Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deployment Details...1 Deploying NetFlow
Cisco Validated design Intelligent WAN NetFlow Monitoring Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deployment Details...1 Deploying NetFlow
MPLS VPN Explicit Null Label Support with BGP. BGP IPv4 Label Session
 MPLS VPN Explicit Null Label Support with BGP IPv4 Label Session The MPLS VPN Explicit Null Label Support with BGP IPv4 Label Session feature provides a method to advertise explicit null in a Border Gateway
MPLS VPN Explicit Null Label Support with BGP IPv4 Label Session The MPLS VPN Explicit Null Label Support with BGP IPv4 Label Session feature provides a method to advertise explicit null in a Border Gateway
DE-CIX Academy: BGP Introduction. Notice of Liability. BGP Configuration Examples. Network Diagram for all examples. Links and Examples
 Notice of Liability Despite careful checking of content, we accept no liability for the content of external links. Content on linked sites is exclusively the responsibility of the respective website operator.
Notice of Liability Despite careful checking of content, we accept no liability for the content of external links. Content on linked sites is exclusively the responsibility of the respective website operator.
Cisco ASR 1000 Series Aggregation Services Routers: QoS Architecture and Solutions
 Cisco ASR 1000 Series Aggregation Services Routers: QoS Architecture and Solutions Introduction Much more bandwidth is available now than during the times of 300-bps modems, but the same business principles
Cisco ASR 1000 Series Aggregation Services Routers: QoS Architecture and Solutions Introduction Much more bandwidth is available now than during the times of 300-bps modems, but the same business principles
Protecting an EBGP peer when memory usage reaches level 2 threshold 66 Configuring a large-scale BGP network 67 Configuring BGP community 67
 Contents Configuring BGP 1 Overview 1 BGP speaker and BGP peer 1 BGP message types 1 BGP path attributes 2 BGP route selection 6 BGP route advertisement rules 6 BGP load balancing 6 Settlements for problems
Contents Configuring BGP 1 Overview 1 BGP speaker and BGP peer 1 BGP message types 1 BGP path attributes 2 BGP route selection 6 BGP route advertisement rules 6 BGP load balancing 6 Settlements for problems
