King Fahd University of Petroleum & Minerals Electrical Engineering Department EE 400, Experiment # 2
|
|
|
- Baldwin Stephens
- 5 years ago
- Views:
Transcription
1 King Fahd University of Petroleum & Minerals Electrical Engineering Department EE 400, Experiment # 2 IP Addressing and Subnetting: Establishing Elementary Networks using Hubs, Switches and Routers. Objectives: After this experiment, the students shall be able to explain the need and significance of assigning IP addresses statically or dynamically, its associated subnet mask, default gateway, and DNS servers. They shall be able to identify and use hubs, layer-2 switches, routers and layer-3 switches appropriately to establish an elementary network. IP addressing: Net ID First Host Last Host Net ID (bytes) Host ID (bytes) Class A 1 3 First Network Last Network Class B 2 2 First Network Last Network Class C 3 1 First Network Last Network Size of Net Huge # of Host, Less # of NW # of Host = # of NW Huge # f NW, Less # of Hosts 11
2 Class D: a multicast address. ( ) Class E: reserved for future use. ( ) Special forms of Internet Addresses For class C address, only 254 hosts can be supported because 0 is reserved for boot process 255 reserved for broadcast Default route 0.host_number - host on this net Limited broadcast (local net). net_number Directed broadcast for the specified net. (e.g broadcast to all hosts of the network.) 127.anything - Loop back test Given the above parameters, this system allows for the following combinations of valid Internet network and host addresses: To determine the number of possible networks or hosts, use the formula 2 n 2, where n is the number of bits in the network or host space. The subtraction of 2 is for the actual network and broadcast address. Class Possible Networks Possible Hosts A ,777,214 B 16,384 65,534 C 2,097, Several networks are reserved for private use and cannot be used on the Internet. They include: Class A B C Address Range 10.x.x.x x.x through x.x x.x These addresses are commonly used for corporate intranets and for testing. IP Subnetting (Refer to Appendix C for more reading) Subnetting is a Technique used to allow a single IP network address to span multiple physical networks. IP hosts should support subnetting. Subnetting is done by using some of the bits of the host-id part of the IP address as a physical network identifier. The subnet mask is used to 12
3 determine the bits of the network identifier. All hosts on the same network should have the same subnet mask. An example of Subnetting: The Class B network can be subnetted using the first 8 bits of the host-id, to span 254 different physical networks. The subnet mask for this case is The subnetworks are: , ,..., Each of the subnetworks can have up to 254 different hosts: X.1, X.2,..., X.254. If there is a need for less physical nets and more hosts in each one, less host-id bits can be used for subnetting. For example: With the subnet mask , 126 different subnets are available with up to 510 hosts in each one. Many Class A and B networks do not contain as many hosts as they could. This situation causes a lot of address space waste. Subnetting better utilizes the address space by dividing these big networks to smaller ones. IP Subnetting examples Class C subnetting example. In Host ID, 3 bits are used for subnet, 5 are used for Hosts Only (2 5 = 32) 2 = 30 Host are allowed for each subnet because 31 used for broadcast 0 used for bootup Only = 8 2 = 6 subnets are allowed because 0 is not allowed All 1 s are used for broadcast. Subnet mask for Host ID field will be ( ) b = (224) d Thus full Subnet mask will be Cabling Categories: Cable categories represent the amount of twist per unit length in the cable that results in better shielding effect in the cable thus increasing the capability of the cable to carry high speed data. 13
4 Category 1: suitable for voice only (1950s) Category 2: suitable for voice and low data rates (less than 4 Mbps). (1960s) Category 3: suited for voice and data rates up to 10 Mbps. Uses 4 twisted-pairs. Standard for most telephone installations. (1991) Category 4: consists of 4 twisted-pairs. Suitable for data rates up to 16 Mbps. Support fast Token Ring networks. (1993) Category 5: consists of 4 twisted-pairs. Suitable for data rates up to 100 Mbps. Supports 100Base-TX. (1994) Category 6: consists of 4 twisted-pairs. Suitable for data rates up to 1 Gbps. Supports 1000Base-TX. (1994) Straight-Through and Crossover Cable Pin outs: Cables ending in RJ45's may be wired up in two ways: straight through and crossover. A straight through cable connects pins N at both ends, whereas a crossover cable has the various pairs crossed over. Whether a straight through or crossover cable is required will depend on the types of network equipment and how they are interlinked. The schematics of crossover and straight-through cables are shown in below. Straight-Through Cable Schematic Crossover Cable Schematic MDI / MDI-X ports: Consider the connection between a hub (DCE) and a workstation (DTE), shown in the figure below There must be a point of crossover between the DCE and DTE for data to be successfully exchanged. Above figure shows a cable with the transmit and receive pairs crossed over. On a hub most of the ports will connect to DTE's (workstations, PCs etc.) and at some point a signals crossover must be affected. Equipment manufacturers are aware of this situation so the industry accepted standard is that all ports on hubs and switches which do not have a 14
5 media conversion capability have crossovers already built in. In such cases (the vast majority) only a straight-through cable is required to connect to a DTE. Figure below shows the DCE (hub) with a built in crossover port. Visually it is not easy to distinguish between straightthrough and crossover cables so it is preferable to avoid having both types of cable in an installation. Using hubs and switches with crossover ports built in is a way of eliminating the need for crossover cables altogether. Ports on such equipment are often marked MDI-X (Media Dependant Interface-Internally Crossed over). Uplink ports (e.g. 100BaseT) will not usually have built-in crossover and may be marked MDI (Media Dependant Interface). The connection between a DCE and DTE using a straight through cable because the port of the DCE is already crossed over internally. Many hubs and switches feature ports which are switchable between crossover for DTE connection and straight-through for cascading or uplinking, all others being MDI-X only, or unmarked. LAN Devices: Network Interface Card (For further reading on the subject, refer to Text book, sec 6.2) Network interface cards, commonly referred to as NICs, are used to connect a PC to a network. The NIC provides a physical connection between the networking cable and the computer's internal bus. NICs come in three basic varieties: 8-bit, 16-bit, and 32-bit. The larger the number of bits that can be transferred to the NIC, the faster the NIC can transfer data to the network cable. Many NIC adapters comply with Plug-n-Play specifications. On these systems, NICs are automatically configured without user intervention, while on non-plug-n-play systems, configuration is done manually through a setup program and/or DIP switches. Cards are available to support almost all networking standards, including the latest Fast Ethernet environment. Fast Ethernet NICs are often 10/100 capable, and will automatically set to the appropriate speed. Full duplex networking is another option, where a dedicated connection to a switch allows a NIC to operate at twice the speed. Repeater : A repeater is a device used to extend the network length and topology beyond what can be achieved by a single cable segment. It is used to re-time and amplify the individual signals and has no concept of packets. Repeaters, also called hubs or concentrators, are bit level devices. What this means that they do not examine the data packets that travel through them. They have no knowledge of addresses associated with the source or the destination. The basic operation of a repeater is to 15
6 repeat traffic. Any data arriving on one port will be amplified and repeated out all ports (except the port on which it was received). Repeaters were originally designed with only two ports and were used to increase the size of coax cable-based networks. This way, different lengths of coax cable coulds be attached to the repeater to extend the size of the network. This would allow the network to reach all areas of large or tall buildings. Data would be repeated from one cable segment to the other. When the coax cabling was replaced by concentrators or hubs, the concentrators were, in fact, just repeaters with many more ports. Now, data reeived on one port would be replicated anywhere from twice to hundreds of times and transmitted to attached stations. The repeater also had the ability to track how much traffic was crossing through it. Repeaters may also be linked together for even greater distances, but it is recommended that the data should not need to cross more than four repeaters. This is because each time the data gets repeated it may be slightly distorted. If there are too many distortions, original signal may be unreadable. A very important fact to note about hubs is that they only allow users to shared Ethernet. A network of hubs/repeaters is termed a "shared Ethernet," meaning that all members of the network are contending for transmission of data onto a single network (collision domain). This means that individual members of a shared network will only get a percentage of the available network bandwidth Repeaters support all standard LAN protocols and cabling types, and a repeater can translate between different cabling. Today, repeaters are being replaced called a bridge. Bridge and Layer-2 Switch: A bridge operates at layer 2 of the OSI model and offers several functions, including expansion of networks beyond normal physical limitation, overcoming station count limitations, packet storage and forwarding, and keeping local traffic local by building an address table (SAT) of where devices are located within the network. Bridges offer several advantages over repeaters, including: Expansion of network - because of regeneration issues, packets can only be repeated a limited number of times. Bridges eliminate the problem by copying and recreating new packets before forwarding them. Overcoming station count limitations - each type of LAN (Ethernet, token ring, FDDI) has a maximum number of users allowed on one segment. Bridges allows for the creation of multiple bridging segments. Packet storage and forwarding bridges receive the packet, examine it, and then determine where it needs to go. If there is other traffic on the destination port, the bridge buffers (stores) the packet until the port is able to accept more traffic. Keeping local traffic local the bridge s ability to read packets and identity addresses enables it to determine where a destination is located. This eliminates sending packets to segments that do not contain the destination. 16
7 Translating between different speeds bridges are required to interface between networks of different speeds (e.g., Ethernet s 10, 100, and 1000 Mbps) Translating traffic between LAN protocols bridges, acting as interpreters, have the ability to translate packets between other LAN protocols such as Ethernet, token ring, FDDI, and ATM. Bridges fit into the network in a similar fashion as repeaters and they support all the capabilities of repeaters (amplifications of signals, etc.). However, bridges have increased intelligence and can perform additional functions. The repeater repeats all traffic that goes through it, so if I had a 24-port repeater and a packet came in one port, it would be repeated out 23 other ports. This is because the repeater does not know where to send it. A bridge, though, is aware of the individual packets and the addressing that is used. A bridge that receives that same packet examines it and resends it only to the port that has the destination address attached to it. Obviously, this is a better way to handle traffic. Besides having the ability to examine packets and forward based on addresses, bridges have the ability to learn where the different addresses are located on the network. This means the bridge will learn which PC is located on which port, and it also keep track of this address if the PC is moved. Bridges can also be used to separate repeated networks. Bridges support all protocol and media types, and even have the ability to translate one LAN protocol to another. Routers : Routers perform their function at layer 3 of the OSI Model and are used to forward messages across an extended network based on network layer addresses (logical addressing), not MAC layer addresses. They route messages from end-station to end station, allowing multiple paths between them. Routeres can also be used to provide better traffic isolation and security by using access lists that control who can communicate through the router. Routers are used to forward traffic on the internet. Routers offers several advantages over repeaters and bridges. These include: Isolation of broadcast traffic routers prevent the flow of broadcast traffic from one LAN to another. Path selection routers can use the best path that physically exists between source and destination. Some routers allows for load balancing over redundant paths. Flexibility routers can support any desired protocol or network topology. the total size of the network interconnected with routers is, for all practical purposes, unlimited (e.g., the Internet) Routers supports layer 1,2,and 3 functionality. Note : Routers are more intelligent than bridges, but they are not plug-and-play routers must be configured by a human. Routers are designed to separate different parts of the network into what are called sub-nets, which are subdivisions of the the total network. This division of the network is done to 17
8 support the different requirements of the organization, and it allows a network manager to separate and control traffic in the different sub-nets. Routers are often used to separate the network for the purpose of security. Doing this allows a network manager to keep some traffic inside a sub-net and allows other traffic to cross sub-net boundaries. An example of using routers and sub-nets would be a large company that has divided their network up based on departments. Sales might be one sub-net, marketing on another sub-net, and engineering on another sub-net. All these sub-nets would form the complete network, and within each sub-net is a collection of users connected to bridges or repeaters. Routers support all the capabilities of bridges and repeaters along with network layer (layer3) protocols. Layer-3 Switches: Networks started as a collection of computers connected by a single cable. The next evolution of networks was the introduction of the repeater. The repeater allowed the larger networks (Distance and size) and eliminated the cable as a single point of failure. The problem was that traffic was flooded everywhere. The next evolution was the bridge. Originally, bridges were designed to separate networks into different sections, and this cut down on the amount of flooded traffic. Bridges could then used to interconnect groups of users connected to repeaters. Next came the router. With the routers, logical groupings could be defined, traffic could be better controlled. Now you had networks with users connected to repeaters, the repeater connected to bridges and the bridges connected to routers, with each network network device doing its own thing. A switch operates at layer 1, layer 2, and layer 3 (sometimes layer 4) and allows users to use a single device to support multiple capabilities. Now, using one device, some traffic can be repeated, some bridged, and some routed, all based on where the traffic needs to go. This is called switching. Switches combine the intelligence of repeaters, bridges, and routers into one networking device. Some of the advantages to using single box for all three functions are listed as follows: Save time one device to manage Single device required for spare Reconfigure instead of move/replace Single version of software need for upgrading network. Switches look like repeaters or bridges and allow direct connection to the PCs or to other switches, bridges, or routers, These devices are designed with much more intelligence built in, and the network manager can configure any port, or groups of ports, to act as repeaters, bridges, or routers. the idea here is that you do not need to purchase and manage three different types of devices in your network you can purchase one type of device and configure it the way you need it. 18
9 Exercise: 1. Students will distribute themselves in four groups A, B, C and D. 2. Connect computers in groups A and B to Hub 1 and Switch 1 respectively. 3. Connect computers in groups C and D to Switch 2 and Switch 3 respectively. Phase 1 4. Assign IP addresses and subnet masks of the computers in each group as depicted in the figure 2.1. Groups A and B belong to the one subnet and Groups C and D belong to other subnet. 5. Interconnect group A and group B by connecting Hub 1 and Switch 1 with the help of Straight cable. 6. Verify the end-to-end link between computers of group A and B by pinging each other. 7. Repeat steps 4, 5 and 6 for group C and D with Switch 2 and Switch 3. Phase 2 8. Assign IP addresses and subnet masks of the computers in each group as depicted in the figure Now interconnect group A and group C by connecting Hub1 and Switch 2 with the help of Straight cable. 10. Verify the inability of communication between computers of group A and C by pinging each other. 11. Repeat steps 8, 9 and 10 for group B and D. Phase Assign IP addresses and subnet masks of the computers in each group as depicted in the figure Interconnect group A and group C by connecting Hub 1 and Switch2 through Router1 interfaces FastEthernet0/0 and FastEthernet0/1 respectively. 14. Verify the end-to-end link between computers of group A and C by pinging each other. 15. Repeat steps 12, 13 and 14 for group B and D using Router2. 19
10 Figure 2.1: Phase 1 IP : X IP : X Hub 1 Switch 1 Group A Group B IP : X IP : X Switch 2 Switch 3 Group C Group D Where X = your computer number 20
11 Figure 2.2: Phase X X Group A Group C X X Group B Group D Where X = Your computer number 21
12 Figure 2.3: Phase X DG: Router X DG: FastEth 0/0 FastEth 0/1 Group A Group C X DG: Router X DG: FastEth 0/0 FastEth 0/1 Group B Group D Where X = Your computer number 22
13 23
Experiment # 2 Transmission Media & Networking Components
 Experiment # 2 Transmission Media & Networking Components Objectives: Study different types of networking cables, connectors and other network components. Transmission Media (refer to text book, sec 3.7)
Experiment # 2 Transmission Media & Networking Components Objectives: Study different types of networking cables, connectors and other network components. Transmission Media (refer to text book, sec 3.7)
Hubs. twisted pair. hub. 5: DataLink Layer 5-1
 Hubs Hubs are essentially physical-layer repeaters: bits coming from one link go out all other links at the same rate no frame buffering no CSMA/CD at : adapters detect collisions provides net management
Hubs Hubs are essentially physical-layer repeaters: bits coming from one link go out all other links at the same rate no frame buffering no CSMA/CD at : adapters detect collisions provides net management
A LAN is a high-speed data network that covers a relatively small geographic area. It typically connects workstations, personal computers, printers,
 CBCN4103 A LAN is a high-speed data network that covers a relatively small geographic area. It typically connects workstations, personal computers, printers, servers, and other devices. LANs offer computer
CBCN4103 A LAN is a high-speed data network that covers a relatively small geographic area. It typically connects workstations, personal computers, printers, servers, and other devices. LANs offer computer
Chapter 6 Connecting Device
 Computer Networks Al-Mustansiryah University Elec. Eng. Department College of Engineering Fourth Year Class Chapter 6 Connecting Device 6.1 Functions of network devices Separating (connecting) networks
Computer Networks Al-Mustansiryah University Elec. Eng. Department College of Engineering Fourth Year Class Chapter 6 Connecting Device 6.1 Functions of network devices Separating (connecting) networks
Chapter 4 NETWORK HARDWARE
 Chapter 4 NETWORK HARDWARE 1 Network Devices As Organizations grow, so do their networks Growth in number of users Geographical Growth Network Devices : Are products used to expand or connect networks.
Chapter 4 NETWORK HARDWARE 1 Network Devices As Organizations grow, so do their networks Growth in number of users Geographical Growth Network Devices : Are products used to expand or connect networks.
Internetworking is connecting two or more computer networks with some sort of routing device to exchange traffic back and forth, and guide traffic on
 CBCN4103 Internetworking is connecting two or more computer networks with some sort of routing device to exchange traffic back and forth, and guide traffic on the correct path across the complete network
CBCN4103 Internetworking is connecting two or more computer networks with some sort of routing device to exchange traffic back and forth, and guide traffic on the correct path across the complete network
Introduction to LAN Protocols
 CHAPTER 2 Introduction to LAN Protocols This chapter introduces the various media-access methods, transmission methods, topologies, and devices used in a local area network (LAN). Topics addressed focus
CHAPTER 2 Introduction to LAN Protocols This chapter introduces the various media-access methods, transmission methods, topologies, and devices used in a local area network (LAN). Topics addressed focus
6.1.2 Repeaters. Figure Repeater connecting two LAN segments. Figure Operation of a repeater as a level-1 relay
 6.1.2 Repeaters A single Ethernet segment can have a maximum length of 500 meters with a maximum of 100 stations (in a cheapernet segment it is 185m). To extend the length of the network, a repeater may
6.1.2 Repeaters A single Ethernet segment can have a maximum length of 500 meters with a maximum of 100 stations (in a cheapernet segment it is 185m). To extend the length of the network, a repeater may
2. LAN Topologies Gilbert Ndjatou Page 1
 2. LAN Topologies Two basic categories of network topologies exist, physical topologies and logical topologies. The physical topology of a network is the cabling layout used to link devices. This refers
2. LAN Topologies Two basic categories of network topologies exist, physical topologies and logical topologies. The physical topology of a network is the cabling layout used to link devices. This refers
More on LANS. LAN Wiring, Interface
 More on LANS Chapters 10-11 LAN Wiring, Interface Mostly covered this material already NIC = Network Interface Card Separate processor, buffers incoming/outgoing data CPU might not be able to keep up network
More on LANS Chapters 10-11 LAN Wiring, Interface Mostly covered this material already NIC = Network Interface Card Separate processor, buffers incoming/outgoing data CPU might not be able to keep up network
Introduction to LAN Protocols
 CHAPTER 2 Chapter Goals Learn about different LAN protocols. Understand the different methods used to deal with media contention. Learn about different LAN topologies. This chapter introduces the various
CHAPTER 2 Chapter Goals Learn about different LAN protocols. Understand the different methods used to deal with media contention. Learn about different LAN topologies. This chapter introduces the various
Introduction to Networking Devices
 Introduction to Networking Devices Objectives Explain the uses, advantages, and disadvantages of repeaters, hubs, wireless access points, bridges, switches, and routers Define the standards associated
Introduction to Networking Devices Objectives Explain the uses, advantages, and disadvantages of repeaters, hubs, wireless access points, bridges, switches, and routers Define the standards associated
NETWORKING COMPONENTS
 1) OBJECTIVES NETWORKING COMPONENTS The objectives of this chapter are to familiarize with the following: - i) The LAN components ii) iii) iv) Repeater Hub Bridge v) Router vi) Gateway 2) INTRODUCTION
1) OBJECTIVES NETWORKING COMPONENTS The objectives of this chapter are to familiarize with the following: - i) The LAN components ii) iii) iv) Repeater Hub Bridge v) Router vi) Gateway 2) INTRODUCTION
(Network Programming) Basic Networking Hardware
 EEE 448 Computer Networks with (Network Programming) Basic Networking Hardware Lecture #2 Dept of Electrical and Electronics Engineering Çukurova University Agenda What is a network device? Network Media
EEE 448 Computer Networks with (Network Programming) Basic Networking Hardware Lecture #2 Dept of Electrical and Electronics Engineering Çukurova University Agenda What is a network device? Network Media
Prepared by Agha Mohammad Haidari Network Manager ICT Directorate Ministry of Communication & IT
 Network Basics Prepared by Agha Mohammad Haidari Network Manager ICT Directorate Ministry of Communication & IT E-mail :Agha.m@mcit.gov.af Cell:0700148122 After this lesson,you will be able to : Define
Network Basics Prepared by Agha Mohammad Haidari Network Manager ICT Directorate Ministry of Communication & IT E-mail :Agha.m@mcit.gov.af Cell:0700148122 After this lesson,you will be able to : Define
Full file at
 Guide to Networking Essentials, Sixth Edition 2-1 Chapter 2 Network Hardware Essentials At a Glance Instructor s Manual Table of Contents Overview Objectives Tips Quick Quizzes Class Discussion Topics
Guide to Networking Essentials, Sixth Edition 2-1 Chapter 2 Network Hardware Essentials At a Glance Instructor s Manual Table of Contents Overview Objectives Tips Quick Quizzes Class Discussion Topics
Introduction to Computer Science (I1100) Networks. Chapter 6
 Networks Chapter 6 501 Outline How does Networks and Internet Work? Networking devices Physical Network topology Types of Network Intranets - extranets Copper Media IP Address 502 How does Networks and
Networks Chapter 6 501 Outline How does Networks and Internet Work? Networking devices Physical Network topology Types of Network Intranets - extranets Copper Media IP Address 502 How does Networks and
Switching and Forwarding Reading: Chapter 3 1/30/14 1
 Switching and Forwarding Reading: Chapter 3 1/30/14 1 Switching and Forwarding Next Problem: Enable communication between hosts that are not directly connected Fundamental Problem of the Internet or any
Switching and Forwarding Reading: Chapter 3 1/30/14 1 Switching and Forwarding Next Problem: Enable communication between hosts that are not directly connected Fundamental Problem of the Internet or any
7010INT Data Communications Lecture 7 The Network Layer
 Introduction 7010INT Data Communications Lecture 7 The Layer Internetworking & Devices Connecting LANs Routing Backbone networks Virtual LANs Addressing Application Presentation Session Data Link Physical
Introduction 7010INT Data Communications Lecture 7 The Layer Internetworking & Devices Connecting LANs Routing Backbone networks Virtual LANs Addressing Application Presentation Session Data Link Physical
Summary of MAC protocols
 Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division, Code Division, Frequency Division Random partitioning (dynamic) ALOHA, S-ALOHA,
Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division, Code Division, Frequency Division Random partitioning (dynamic) ALOHA, S-ALOHA,
CH : 15 LOCAL AREA NETWORK OVERVIEW
 CH : 15 LOCAL AREA NETWORK OVERVIEW P. 447 LAN (Local Area Network) A LAN consists of a shared transmission medium and a set of hardware and software for interfacing devices to the medium and regulating
CH : 15 LOCAL AREA NETWORK OVERVIEW P. 447 LAN (Local Area Network) A LAN consists of a shared transmission medium and a set of hardware and software for interfacing devices to the medium and regulating
CCNA Exploration Network Fundamentals. Chapter 10 Planning and Cabling Networks
 CCNA Exploration Network Fundamentals Chapter 10 Planning and Cabling Networks Updated: 15/07/2008 1 10.0.1 Introduction 2 10.0.1 Introduction The following have been covered in previous chapters: considered
CCNA Exploration Network Fundamentals Chapter 10 Planning and Cabling Networks Updated: 15/07/2008 1 10.0.1 Introduction 2 10.0.1 Introduction The following have been covered in previous chapters: considered
Darshan Institute of Engineering & Technology for Diploma Studies
 1. Explain different network devices in detail. Or Explain NIC (Network Interface Card) in detail. Network interface cards are add on cards as hardware cards on the motherboard. This is additional hardware
1. Explain different network devices in detail. Or Explain NIC (Network Interface Card) in detail. Network interface cards are add on cards as hardware cards on the motherboard. This is additional hardware
Networking Fundamentals Tom Brett
 Networking Fundamentals Tom Brett Data Before we look at networking, it is important for us to understand what Data is and how it is stored and represented Data According to Webopedia, data is distinct
Networking Fundamentals Tom Brett Data Before we look at networking, it is important for us to understand what Data is and how it is stored and represented Data According to Webopedia, data is distinct
CN [Network Devices]
![CN [Network Devices] CN [Network Devices]](/thumbs/83/88538687.jpg) Q`.1 Explain Repeater. A repeater is a device that operates only at the PHYSICAL layer. A repeater can be used to increase the length of the network by put the effect on the signal. It connects two segments
Q`.1 Explain Repeater. A repeater is a device that operates only at the PHYSICAL layer. A repeater can be used to increase the length of the network by put the effect on the signal. It connects two segments
Lecture (04) Network Layer (Physical/Data link) 2
 Lecture (04) Network Layer (Physical/Data link) 2 By: Dr. Ahmed ElShafee ١ Dr. Ahmed elshafee, ACU : Spring 2018, CSE401 Computer Networks Agenda Ethernet standards 10 base 5 10 base 2 10 base T Fast Ethernet
Lecture (04) Network Layer (Physical/Data link) 2 By: Dr. Ahmed ElShafee ١ Dr. Ahmed elshafee, ACU : Spring 2018, CSE401 Computer Networks Agenda Ethernet standards 10 base 5 10 base 2 10 base T Fast Ethernet
Layer 2 functionality bridging and switching
 Layer 2 functionality bridging and switching BSAD 141 Dave Novak Sources: Network+ Guide to Networks, Dean 2013 Overview Layer 2 functionality Error detection Bridges Broadcast and collision domains How
Layer 2 functionality bridging and switching BSAD 141 Dave Novak Sources: Network+ Guide to Networks, Dean 2013 Overview Layer 2 functionality Error detection Bridges Broadcast and collision domains How
Appendix B Networks, Routing, and Firewall Basics
 Appendix B Networks, Routing, and Firewall Basics This appendix provides an overview of IP networks, routing, and firewalls. Related Publications As you read this document, you may be directed to various
Appendix B Networks, Routing, and Firewall Basics This appendix provides an overview of IP networks, routing, and firewalls. Related Publications As you read this document, you may be directed to various
Chapter Seven. Local Area Networks: Part 1. Data Communications and Computer Networks: A Business User s Approach Seventh Edition
 Chapter Seven Local Area Networks: Part 1 Data Communications and Computer Networks: A Business User s Approach Seventh Edition After reading this chapter, you should be able to: State the definition of
Chapter Seven Local Area Networks: Part 1 Data Communications and Computer Networks: A Business User s Approach Seventh Edition After reading this chapter, you should be able to: State the definition of
Networking Devices. Punch_down panels
 Networking Devices Punch_down panels Hubs Switches Bridges Routes Gateways Network Interface Cards (NICs) Wireless access points Modems 1 Punch_down panels Wiring closets Labeling schemes 2 1 Hubs The
Networking Devices Punch_down panels Hubs Switches Bridges Routes Gateways Network Interface Cards (NICs) Wireless access points Modems 1 Punch_down panels Wiring closets Labeling schemes 2 1 Hubs The
What is a Network? A connection of two or more computers so that they can share resources.
 NETWORKS What is a Network? A connection of two or more computers so that they can share resources. Network Benefits Remote access Sharing files & resources Communication Cost Maintenance Communication
NETWORKS What is a Network? A connection of two or more computers so that they can share resources. Network Benefits Remote access Sharing files & resources Communication Cost Maintenance Communication
1. What type of network cable is used between a terminal and a console port? cross-over straight-through rollover patch cable 2.
 1. What type of network cable is used between a terminal and a console port? cross-over straight-through rollover patch cable 2. Refer to the exhibit. A network administrator has decided to use packet
1. What type of network cable is used between a terminal and a console port? cross-over straight-through rollover patch cable 2. Refer to the exhibit. A network administrator has decided to use packet
Chapter 10: Planning and Cabling Networks
 Chapter 10: Planning and Cabling Networks Before using an IP phone, accessing instant messaging, or conducting any number of other interactions over a data network, we must connect end devices and intermediary
Chapter 10: Planning and Cabling Networks Before using an IP phone, accessing instant messaging, or conducting any number of other interactions over a data network, we must connect end devices and intermediary
LAN Interconnection. different interconnecting devices, many approaches Vasile Dadarlat- Local Area Computer Networks
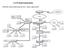 LAN Interconnection different interconnecting devices, many approaches 1 Need for ability to expand beyond single LAN; appears concept of Extended LAN, extending the number of attached stations and maximum
LAN Interconnection different interconnecting devices, many approaches 1 Need for ability to expand beyond single LAN; appears concept of Extended LAN, extending the number of attached stations and maximum
Network.... communication system for connecting end- systems. End-systems a.k.a. hosts PCs, workstations dedicated computers network components
 Networking 1 Network... communication system for connecting end- systems End-systems a.k.a. hosts PCs, workstations dedicated computers network components 2 Multiaccess vs.. Point-to-point Multiaccess
Networking 1 Network... communication system for connecting end- systems End-systems a.k.a. hosts PCs, workstations dedicated computers network components 2 Multiaccess vs.. Point-to-point Multiaccess
1: Review Of Semester Provide an overview of encapsulation.
 1: Review Of Semester 1 1.1.1.1. Provide an overview of encapsulation. Networking evolves to support current and future applications. By dividing and organizing the networking tasks into separate layers/functions,
1: Review Of Semester 1 1.1.1.1. Provide an overview of encapsulation. Networking evolves to support current and future applications. By dividing and organizing the networking tasks into separate layers/functions,
Medium Access Protocols
 Medium Access Protocols Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division,Code Division, Frequency Division Random partitioning
Medium Access Protocols Summary of MAC protocols What do you do with a shared media? Channel Partitioning, by time, frequency or code Time Division,Code Division, Frequency Division Random partitioning
10- and 100-Mbps Ethernet
 Ethernet Basics 10-Mbps Ethernet Three 10-Mbps Ethernet standards: 10BASE5 10BASE2 10BASE-T 10BASE2 and 10BASE5 were around more than 20 years and have been replaced by newer alternatives 10BASE-T s use
Ethernet Basics 10-Mbps Ethernet Three 10-Mbps Ethernet standards: 10BASE5 10BASE2 10BASE-T 10BASE2 and 10BASE5 were around more than 20 years and have been replaced by newer alternatives 10BASE-T s use
Network Devices,Frame Relay and X.25
 Network Devices,Frame Relay and X.25 Hardware/Networking Devices: Networking hardware may also be known as network equipment computer networking devices. Network Interface Card (NIC): NIC provides a physical
Network Devices,Frame Relay and X.25 Hardware/Networking Devices: Networking hardware may also be known as network equipment computer networking devices. Network Interface Card (NIC): NIC provides a physical
Chapter 2. Switch Concepts and Configuration. Part I
 Chapter 2 Switch Concepts and Configuration Part I CCNA3-1 Chapter 2-1 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor,
Chapter 2 Switch Concepts and Configuration Part I CCNA3-1 Chapter 2-1 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor,
3.5 CONNECTING DEVICES
 3.5 CONNECTING DEVICES LANs or WANs do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs and WANs together we use connecting devices. Connecting devices
3.5 CONNECTING DEVICES LANs or WANs do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs and WANs together we use connecting devices. Connecting devices
Objectives. Hexadecimal Numbering and Addressing. Ethernet / IEEE LAN Technology. Ethernet
 2007 Cisco Systems, Inc. All rights reserved. Cisco Public Objectives Ethernet Network Fundamentals Chapter 9 ITE PC v4.0 Chapter 1 1 Introduce Hexadecimal number system Describe the features of various
2007 Cisco Systems, Inc. All rights reserved. Cisco Public Objectives Ethernet Network Fundamentals Chapter 9 ITE PC v4.0 Chapter 1 1 Introduce Hexadecimal number system Describe the features of various
Data Link Layer. Our goals: understand principles behind data link layer services: instantiation and implementation of various link layer technologies
 Data Link Layer Our goals: understand principles behind data link layer services: link layer addressing instantiation and implementation of various link layer technologies 1 Outline Introduction and services
Data Link Layer Our goals: understand principles behind data link layer services: link layer addressing instantiation and implementation of various link layer technologies 1 Outline Introduction and services
CHAPTER -1. Introduction to Computer Networks
 CHAPTER -1 Introduction to Computer Networks PRELIMINARY DEFINITIONS computer network :: [Tanenbaum] a collection of autonomous computers interconnected by a single technology. communications network ::a
CHAPTER -1 Introduction to Computer Networks PRELIMINARY DEFINITIONS computer network :: [Tanenbaum] a collection of autonomous computers interconnected by a single technology. communications network ::a
Defining Networks with the OSI Model. Module 2
 Defining Networks with the OSI Model Module 2 Objectives Skills Concepts Objective Domain Description Objective Domain Number Understanding OSI Basics Defining the Communications Subnetwork Defining the
Defining Networks with the OSI Model Module 2 Objectives Skills Concepts Objective Domain Description Objective Domain Number Understanding OSI Basics Defining the Communications Subnetwork Defining the
IT 4504 Section 4.0. Network Architectures. 2008, University of Colombo School of Computing 1
 IT 4504 Section 4.0 Network Architectures 2008, University of Colombo School of Computing 1 Section 4.1 Introduction to Computer Networks 2008, University of Colombo School of Computing 2 Introduction
IT 4504 Section 4.0 Network Architectures 2008, University of Colombo School of Computing 1 Section 4.1 Introduction to Computer Networks 2008, University of Colombo School of Computing 2 Introduction
LAN Local Area Networks. CSMA/CD restriction. Bits on the Wire. PacketSize 2 * COMP476 Networked Computer Systems. Interconnecting
 Interconnecting s COMP476 ed Computer Systems LN Local rea s There is a Limit to the Maximum Length of a LN - Ethernet cables (segments) can be up to 500m. - The restrictions are due to power and propagation
Interconnecting s COMP476 ed Computer Systems LN Local rea s There is a Limit to the Maximum Length of a LN - Ethernet cables (segments) can be up to 500m. - The restrictions are due to power and propagation
Switched Ethernet Virtual LANs
 Switched Ethernet Virtual LANs Computer Networks Lecture 4 http://goo.gl/pze5o8 Switched Ethernet 2 LAN Switches Behave as bridges (operates in the logical tree topology) Switching is implemented by hardware
Switched Ethernet Virtual LANs Computer Networks Lecture 4 http://goo.gl/pze5o8 Switched Ethernet 2 LAN Switches Behave as bridges (operates in the logical tree topology) Switching is implemented by hardware
The following steps should be used when configuring a VLAN on the EdgeXOS platform:
 EdgeXOS VLANs VLAN Overview This document provides an overview of what a VLAN is and how it is configured on the EdgeXOS platform. Use the step-by-step guide below to configure a VLAN on the Edge appliance
EdgeXOS VLANs VLAN Overview This document provides an overview of what a VLAN is and how it is configured on the EdgeXOS platform. Use the step-by-step guide below to configure a VLAN on the Edge appliance
Principles behind data link layer services
 Data link layer Goals: Principles behind data link layer services Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control: Done!
Data link layer Goals: Principles behind data link layer services Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control: Done!
LANs do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs, connecting devices are needed.
 LAN interconnecting devices INTRODUCTION LANs do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs, connecting devices are needed. Connecting devices
LAN interconnecting devices INTRODUCTION LANs do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs, connecting devices are needed. Connecting devices
Networking 101. Introduction to Ethernet networking basics; Network types, components, configurations. Routers. Switches. Servers.
 Switches Routers PCs Networking 101 Introduction to Ethernet networking basics; Network types, components, configurations Servers Hubs Protocols Cat-5 UTP NICs Page 1 July 28, 2000 Network Types LAN Local
Switches Routers PCs Networking 101 Introduction to Ethernet networking basics; Network types, components, configurations Servers Hubs Protocols Cat-5 UTP NICs Page 1 July 28, 2000 Network Types LAN Local
Bridging and Switching Basics
 CHAPTER 4 Bridging and Switching Basics This chapter introduces the technologies employed in devices loosely referred to as bridges and switches. Topics summarized here include general link-layer device
CHAPTER 4 Bridging and Switching Basics This chapter introduces the technologies employed in devices loosely referred to as bridges and switches. Topics summarized here include general link-layer device
CS 3201 Computer Networks 2014/2015 Handout: Lab 3
 Lab Content: - Network Devices - Ethernet Network - MAC Address Network Devices: - Hubs, MAU s, and Repeaters Hubs Hubs are one of the most important components of a network because they act as a central
Lab Content: - Network Devices - Ethernet Network - MAC Address Network Devices: - Hubs, MAU s, and Repeaters Hubs Hubs are one of the most important components of a network because they act as a central
Fundamentals of Networking Introduction to Networking Devices
 Fundamentals of Networking Introduction to Networking Devices Kuldeep Sonar 1 NIC (Network Interface Card) A network interface provides connectivity from an end-user PC or laptop to the public network.
Fundamentals of Networking Introduction to Networking Devices Kuldeep Sonar 1 NIC (Network Interface Card) A network interface provides connectivity from an end-user PC or laptop to the public network.
Introduction to LAN Topologies Cabling. 2000, Cisco Systems, Inc. 3-1
 Introduction to LAN Topologies Cabling 2000, Cisco Systems, Inc. 3-1 Objectives Upon completion of this chapter, you will be able to perform the following tasks: Media / Cabling Local Area Network Cabling
Introduction to LAN Topologies Cabling 2000, Cisco Systems, Inc. 3-1 Objectives Upon completion of this chapter, you will be able to perform the following tasks: Media / Cabling Local Area Network Cabling
Chapter 9. Ethernet. Part II
 Chapter 9 Ethernet Part II CCNA1-1 Chapter 9-2 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor, Ontario. Thanks must go
Chapter 9 Ethernet Part II CCNA1-1 Chapter 9-2 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor, Ontario. Thanks must go
Extending the LAN. Context. Info 341 Networking and Distributed Applications. Building up the network. How to hook things together. Media NIC 10/18/10
 Extending the LAN Info 341 Networking and Distributed Applications Context Building up the network Media NIC Application How to hook things together Transport Internetwork Network Access Physical Internet
Extending the LAN Info 341 Networking and Distributed Applications Context Building up the network Media NIC Application How to hook things together Transport Internetwork Network Access Physical Internet
CS610- Computer Network Solved Subjective From Midterm Papers
 Solved Subjective From Midterm Papers May 08,2012 MC100401285 Moaaz.pk@gmail.com Mc100401285@gmail.com PSMD01 CS610- Computer Network Midterm Examination - Fall 2011 1. Where are destination and source
Solved Subjective From Midterm Papers May 08,2012 MC100401285 Moaaz.pk@gmail.com Mc100401285@gmail.com PSMD01 CS610- Computer Network Midterm Examination - Fall 2011 1. Where are destination and source
INTRODUCTION. What You Need to Read. What this LANbook Covers
 Qwest DSLSM LANbook INTRODUCTION What You Need to Read If you are self-installing Qwest DSL on a local area network in your home or business, start with Chapter 1: Welcome to the Qwest DSL LANbook on page
Qwest DSLSM LANbook INTRODUCTION What You Need to Read If you are self-installing Qwest DSL on a local area network in your home or business, start with Chapter 1: Welcome to the Qwest DSL LANbook on page
THE OSI MODEL. Application Presentation Session Transport Network Data-Link Physical. OSI Model. Chapter 1 Review.
 THE OSI MODEL Application Presentation Session Transport Network Data-Link Physical OSI Model Chapter 1 Review By: Allan Johnson Table of Contents Go There! Go There! Go There! Go There! Go There! Go There!
THE OSI MODEL Application Presentation Session Transport Network Data-Link Physical OSI Model Chapter 1 Review By: Allan Johnson Table of Contents Go There! Go There! Go There! Go There! Go There! Go There!
Principles behind data link layer services:
 Data link layer Goals: Principles behind data link layer services: Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control Example
Data link layer Goals: Principles behind data link layer services: Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control Example
Principles behind data link layer services:
 Data link layer Goals: Principles behind data link layer services: Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control Example
Data link layer Goals: Principles behind data link layer services: Error detection, correction Sharing a broadcast channel: Multiple access Link layer addressing Reliable data transfer, flow control Example
Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs.
 Internetworking Multiple networks are a fact of life: Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs. Fault isolation,
Internetworking Multiple networks are a fact of life: Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs. Fault isolation,
KIBABII UNIVERSITY COLLEGE DEPARTMENT COMPUTER SCIENCE & IT ANSWER ALL QUESTIONS IN SECTION A AND ANY TWO QUESTIONS IN SECTION B
 KIBABII UNIVERSITY COLLEGE DEPARTMENT COMPUTER SCIENCE & IT TITLE: DATACOMMUNICATION COURSE CODE: 223 SECTION A: 30 Marks ANSWER ALL QUESTIONS IN SECTION A AND ANY TWO QUESTIONS IN SECTION B TIME ALLOWED:
KIBABII UNIVERSITY COLLEGE DEPARTMENT COMPUTER SCIENCE & IT TITLE: DATACOMMUNICATION COURSE CODE: 223 SECTION A: 30 Marks ANSWER ALL QUESTIONS IN SECTION A AND ANY TWO QUESTIONS IN SECTION B TIME ALLOWED:
CCM 4300 Lecture 5 Computer Networks, Wireless and Mobile Communications. Dr Shahedur Rahman. Room: T115
 CCM 4300 Lecture 5 Computer Networks, Wireless and Mobile Communications Dr Shahedur Rahman s.rahman@mdx.ac.uk Room: T115 1 Recap of Last Session Described the physical layer Analogue and Digital signal
CCM 4300 Lecture 5 Computer Networks, Wireless and Mobile Communications Dr Shahedur Rahman s.rahman@mdx.ac.uk Room: T115 1 Recap of Last Session Described the physical layer Analogue and Digital signal
Lecture (04) Data link layer
 Lecture (04) Data link layer By: Dr. Ahmed ElShafee Standards Overview CSMA/CD Ethernet standards 10 base 5 10 base 2 10 base T Fast Ethernet Gigabit Ethernet ١ ٢ Standards Overview Like most protocols,
Lecture (04) Data link layer By: Dr. Ahmed ElShafee Standards Overview CSMA/CD Ethernet standards 10 base 5 10 base 2 10 base T Fast Ethernet Gigabit Ethernet ١ ٢ Standards Overview Like most protocols,
Local Area Network(LAN)
 Local Area Network() Sarawuth Chaimool ศราว ธ ช ยม ล jaounarak@hotmail.com Wireless Communications Research Group (WCR) Department of Electrical Engineering King Mongkut s Institute of Technology North
Local Area Network() Sarawuth Chaimool ศราว ธ ช ยม ล jaounarak@hotmail.com Wireless Communications Research Group (WCR) Department of Electrical Engineering King Mongkut s Institute of Technology North
Data Communications. Connecting Devices
 Data Communications Connecting Devices Connecting Devices Networks do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs, or segments of LANs, we use
Data Communications Connecting Devices Connecting Devices Networks do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs, or segments of LANs, we use
SYSTEMS ADMINISTRATION USING CISCO (315)
 Page 1 of 11 Contestant Number: Time: Rank: SYSTEMS ADMINISTRATION USING CISCO (315) REGIONAL 2016 Multiple Choice: Multiple Choice (50 @ 10 points each) TOTAL POINTS (500 points) (500 points) Failure
Page 1 of 11 Contestant Number: Time: Rank: SYSTEMS ADMINISTRATION USING CISCO (315) REGIONAL 2016 Multiple Choice: Multiple Choice (50 @ 10 points each) TOTAL POINTS (500 points) (500 points) Failure
King Fahd University of Petroleum & Minerals. LAN Extension by Bridges and WAN Connectivity by Routers using HDSL Links
 King Fahd University of Petroleum & Minerals Electrical Engineering Department EE 400, Experiment # 5 LAN Extension by Bridges and WAN Connectivity by Routers using H Links Objectives: In this experiment
King Fahd University of Petroleum & Minerals Electrical Engineering Department EE 400, Experiment # 5 LAN Extension by Bridges and WAN Connectivity by Routers using H Links Objectives: In this experiment
Some portions courtesy Srini Seshan or David Wetherall
 CSE 123 Computer Networks Fall 2009 Lecture 6: Data-Link III: Hubs, Bridges and Switches Some portions courtesy Srini Seshan or David Wetherall Misc Homework solutions have been posted I ll post a sample
CSE 123 Computer Networks Fall 2009 Lecture 6: Data-Link III: Hubs, Bridges and Switches Some portions courtesy Srini Seshan or David Wetherall Misc Homework solutions have been posted I ll post a sample
A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e. Chapter 10 Networking Essentials
 A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e Chapter 10 Networking Essentials Objectives Learn about hardware devices used for networking Learn about the different types of networks
A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e Chapter 10 Networking Essentials Objectives Learn about hardware devices used for networking Learn about the different types of networks
CHAPTER 2 - NETWORK DEVICES
 CHAPTER 2 - NETWORK DEVICES TRUE/FALSE 1. Repeaters can reformat, resize, or otherwise manipulate the data packet. F PTS: 1 REF: 30 2. Because active hubs have multiple inbound and outbound connections,
CHAPTER 2 - NETWORK DEVICES TRUE/FALSE 1. Repeaters can reformat, resize, or otherwise manipulate the data packet. F PTS: 1 REF: 30 2. Because active hubs have multiple inbound and outbound connections,
Local Area Network Overview
 Local Area Network Overview Chapter 15 CS420/520 Axel Krings Page 1 LAN Applications (1) Personal computer LANs Low cost Limited data rate Back end networks Interconnecting large systems (mainframes and
Local Area Network Overview Chapter 15 CS420/520 Axel Krings Page 1 LAN Applications (1) Personal computer LANs Low cost Limited data rate Back end networks Interconnecting large systems (mainframes and
Lesson 1: Network Communications
 Lesson 1: Network Communications This lesson introduces the basic building blocks of network communications and some of the structures used to construct data networks. There are many different kinds of
Lesson 1: Network Communications This lesson introduces the basic building blocks of network communications and some of the structures used to construct data networks. There are many different kinds of
Full file at
 ch02 True/False Indicate whether the statement is true or false. 1. The number of nodes on a network and the length of cable used influence the quality of communication on the network. 2. Repeaters and
ch02 True/False Indicate whether the statement is true or false. 1. The number of nodes on a network and the length of cable used influence the quality of communication on the network. 2. Repeaters and
Objectives. Learn how computers are connected. Become familiar with different types of transmission media
 Objectives Learn how computers are connected Become familiar with different types of transmission media Learn the differences between guided and unguided media Learn how protocols enable networking 2 Objectives
Objectives Learn how computers are connected Become familiar with different types of transmission media Learn the differences between guided and unguided media Learn how protocols enable networking 2 Objectives
Electrical Engineering Department EE 400, Experiment # 4 IP Addressing and Subnetting
 Electrical Engineering Department EE 400, Experiment # 4 IP Addressing and Subnetting Objectives: After this experiment, the students should be able to configure for networking, assign IP address, and
Electrical Engineering Department EE 400, Experiment # 4 IP Addressing and Subnetting Objectives: After this experiment, the students should be able to configure for networking, assign IP address, and
Chapter 3. Underlying Technology. TCP/IP Protocol Suite 1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display.
 Chapter 3 Underlying Technology TCP/IP Protocol Suite 1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. OBJECTIVES: To briefly discuss the technology of dominant
Chapter 3 Underlying Technology TCP/IP Protocol Suite 1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. OBJECTIVES: To briefly discuss the technology of dominant
Lecture (04) Network Access layer fundamentals I
 Lecture (04) Network Access layer fundamentals I By: Dr. Ahmed ElShafee Typical LAN Features for Physical layer Typical LAN Features for Data link layer Standards Overview 10BASE2 and 10BASE5 10BASE T
Lecture (04) Network Access layer fundamentals I By: Dr. Ahmed ElShafee Typical LAN Features for Physical layer Typical LAN Features for Data link layer Standards Overview 10BASE2 and 10BASE5 10BASE T
Lecture (04) Network Access layer fundamentals I
 Lecture (04) Network Access layer fundamentals I By: Dr. Ahmed ElShafee ١ Dr. Ahmed ElShafee, ACU : Fall 2014, Computer Networks II Typical LAN Features for Physical layer Typical LAN Features for Data
Lecture (04) Network Access layer fundamentals I By: Dr. Ahmed ElShafee ١ Dr. Ahmed ElShafee, ACU : Fall 2014, Computer Networks II Typical LAN Features for Physical layer Typical LAN Features for Data
Chapter 8: Subnetting IP Networks
 Chapter 8: Subnetting IP Networks Designing, implementing and managing an effective IP addressing plan ensures that networks can operate effectively and efficiently. This is especially true as the number
Chapter 8: Subnetting IP Networks Designing, implementing and managing an effective IP addressing plan ensures that networks can operate effectively and efficiently. This is especially true as the number
Unit 09 Computer Networks
 Unit 09 Computer Networks Gain a knowledge about network devices. Discuss what network devices are required to create a basic network Draw a bespoke network drawing using Visio 2 In order to setup a network
Unit 09 Computer Networks Gain a knowledge about network devices. Discuss what network devices are required to create a basic network Draw a bespoke network drawing using Visio 2 In order to setup a network
Interface The exit interface a packet will take when destined for a specific network.
 The Network Layer The Network layer (also called layer 3) manages device addressing, tracks the location of devices on the network, and determines the best way to move data, which means that the Network
The Network Layer The Network layer (also called layer 3) manages device addressing, tracks the location of devices on the network, and determines the best way to move data, which means that the Network
Lecture (04 & 05) Data link layer fundamental
 Lecture (04 & 05) Data link layer fundamental Dr. Ahmed M. ElShafee ١ Agenda Foundation Topics Typical LAN Features for OSI Layer 1 Typical LAN Features for OSI Layer 2 Standards Overview 10BASE2 and 10BASE5
Lecture (04 & 05) Data link layer fundamental Dr. Ahmed M. ElShafee ١ Agenda Foundation Topics Typical LAN Features for OSI Layer 1 Typical LAN Features for OSI Layer 2 Standards Overview 10BASE2 and 10BASE5
CCENT Study Guide. Chapter 2 Ethernet Networking and Data Encapsulation
 CCENT Study Guide Chapter 2 Ethernet Networking and Data Encapsulation Chapter 2 Objectives The CCENT Topics Covered in this chapter include: Network Fundamentals 1.6 Select the appropriate cabling type
CCENT Study Guide Chapter 2 Ethernet Networking and Data Encapsulation Chapter 2 Objectives The CCENT Topics Covered in this chapter include: Network Fundamentals 1.6 Select the appropriate cabling type
Modern Ethernet. Chapter 6
 Modern Ethernet Chapter 6 Contents Define the characteristics, cabling, and connectors used in 10BaseT and 10BaseFL Explain how to connect multiple Ethernet segments Define the characteristics, cabling,
Modern Ethernet Chapter 6 Contents Define the characteristics, cabling, and connectors used in 10BaseT and 10BaseFL Explain how to connect multiple Ethernet segments Define the characteristics, cabling,
ECE 333: Introduction to Communication Networks Fall Lecture 19: Medium Access Control VII
 ECE : Introduction to Communication Networks Fall 2002 Lecture 9: Medium Access Control VII More on token ring networks LAN bridges and switches. More on token rings In the last lecture we began discussing
ECE : Introduction to Communication Networks Fall 2002 Lecture 9: Medium Access Control VII More on token ring networks LAN bridges and switches. More on token rings In the last lecture we began discussing
Cisco Cisco Certified Network Associate (CCNA)
 Cisco 200-125 Cisco Certified Network Associate (CCNA) http://killexams.com/pass4sure/exam-detail/200-125 Question: 769 Refer to exhibit: Which destination addresses will be used by Host A to send data
Cisco 200-125 Cisco Certified Network Associate (CCNA) http://killexams.com/pass4sure/exam-detail/200-125 Question: 769 Refer to exhibit: Which destination addresses will be used by Host A to send data
Different network topologies
 Network Topology Network topology is the arrangement of the various elements of a communication network. It is the topological structure of a network and may be depicted physically or logically. Physical
Network Topology Network topology is the arrangement of the various elements of a communication network. It is the topological structure of a network and may be depicted physically or logically. Physical
Although the CCNA certification exams test you on some difficult and in-depth networking
 Chapter 1 Networking Devices, Technologies, and Models Although the CCNA certification exams test you on some difficult and in-depth networking issues, the ICND1 exam also tests you on basic networking
Chapter 1 Networking Devices, Technologies, and Models Although the CCNA certification exams test you on some difficult and in-depth networking issues, the ICND1 exam also tests you on basic networking
Comp277 Assignment 1 Fall 2011 Due 20 th December 2011 at 11:00am
 Question 1 1. Which of the following are related to two crucial tasks of a network interface cards? a. Establishes and manages the computer s network connection b. Connect the different parts of a motherboard
Question 1 1. Which of the following are related to two crucial tasks of a network interface cards? a. Establishes and manages the computer s network connection b. Connect the different parts of a motherboard
RMIT University. Data Communication and Net-Centric Computing COSC 1111/2061/1110. Lecture 8. Medium Access Control Methods & LAN
 RMIT University Data Communication and Net-Centric Computing COSC 1111/2061/1110 Medium Access Control Methods & LAN Technology Slide 1 Lecture Overview During this lecture, we will Look at several Multiple
RMIT University Data Communication and Net-Centric Computing COSC 1111/2061/1110 Medium Access Control Methods & LAN Technology Slide 1 Lecture Overview During this lecture, we will Look at several Multiple
Data Communication. Introduction of Communication. Data Communication. Elements of Data Communication (Communication Model)
 Data Communication Introduction of Communication The need to communicate is part of man s inherent being. Since the beginning of time the human race has communicated using different techniques and methods.
Data Communication Introduction of Communication The need to communicate is part of man s inherent being. Since the beginning of time the human race has communicated using different techniques and methods.
VLANS and Other Hardware
 VLANS and Other Hardware CS442 First, a review problem Subnet mask: 255.255.255.0 Examples: Client in A wants to contact server in A or B 1 Other Network Devices Brouters are devices that combine the functions
VLANS and Other Hardware CS442 First, a review problem Subnet mask: 255.255.255.0 Examples: Client in A wants to contact server in A or B 1 Other Network Devices Brouters are devices that combine the functions
Switching & ARP Week 3
 Switching & ARP Week 3 Module : Computer Networks Lecturer: Lucy White lbwhite@wit.ie Office : 324 Many Slides courtesy of Tony Chen 1 Ethernet Using Switches In the last few years, switches have quickly
Switching & ARP Week 3 Module : Computer Networks Lecturer: Lucy White lbwhite@wit.ie Office : 324 Many Slides courtesy of Tony Chen 1 Ethernet Using Switches In the last few years, switches have quickly
5/8-Port 10/100Mbps Fast Ethernet Desktop Switch
 5/8-Port 10/100Mbps Fast Ethernet Desktop Switch A02-F5P A02-F8P USER S MANUAL A02-F5(8)P_ME01 Copyright The Atlantis Land logo is a registered trademark of Atlantis Land SpA. All other names mentioned
5/8-Port 10/100Mbps Fast Ethernet Desktop Switch A02-F5P A02-F8P USER S MANUAL A02-F5(8)P_ME01 Copyright The Atlantis Land logo is a registered trademark of Atlantis Land SpA. All other names mentioned
The SpeedTouch and Ethernet Connectivity
 The SpeedTouch and Ethernet Connectivity Author: Mark Van Wambeke Date: May 2003 Version: v1.0 Abstract: Applicability: Updates: This application note provides technical Ethernet information and how this
The SpeedTouch and Ethernet Connectivity Author: Mark Van Wambeke Date: May 2003 Version: v1.0 Abstract: Applicability: Updates: This application note provides technical Ethernet information and how this
ET4254 Communications and Networking 1
 Topic 10:- Local Area Network Overview Aims:- LAN topologies and media LAN protocol architecture bridges, hubs, layer 2 & 3 switches 1 LAN Applications (1) personal computer LANs low cost limited data
Topic 10:- Local Area Network Overview Aims:- LAN topologies and media LAN protocol architecture bridges, hubs, layer 2 & 3 switches 1 LAN Applications (1) personal computer LANs low cost limited data
