Cisco SD-AVC User Guide, Release 1.1.0
|
|
|
- Quentin Mitchell
- 5 years ago
- Views:
Transcription
1 First Published: Last Modified: Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA USA Tel: NETS (6387) Fax:
2 2017 Cisco Systems, Inc. All rights reserved.
3 CONTENTS PART I Part: Introduction 1 CHAPTER 1 SD-AVC Overview 3 CHAPTER 2 Operation 5 SD-AVC Architecture 5 SD-AVC and Application Recognition 6 Collecting Application Data 6 Aggregating Application Data 6 CHAPTER 3 SD-AVC Features and Benefits 7 SD-AVC Features and Benefits 7 Using SD-AVC in an Asymmetric Routing Scenario 8 PART II CHAPTER 4 Part: Deployment 11 Installing or Upgrading the SD-AVC Network Service 13 Installation Overview 13 System Requirements: SD-AVC Network Service Host 14 Configuring Connectivity 15 Using SD-AVC with Cisco IWAN 16 Installing the SD-AVC Network Service 16 Upgrading the SD-AVC Network Service 20 CHAPTER 5 Unconfiguring or Uninstalling the SD-AVC Network Service 23 Unconfiguring the SD-AVC Network Service 23 Uninstalling the SD-AVC Network Service 23 iii
4 Contents CHAPTER 6 Configuring Network Devices 25 Configuring Network Devices to Use SD-AVC 25 System Requirements: Network Devices Using SD-AVC 25 Configuration Prerequisites: Network Devices Using SD-AVC 26 Activating the SD-AVC Agent 26 Deactivating the SD-AVC Agent 28 CHAPTER 7 SD-AVC High Availability 29 PART III Part: Usage 31 CHAPTER 8 Using SD-AVC 33 Using SD-AVC 33 Connectivity Page 34 Application Visibility Page 36 Application Rules Page 37 Asymmetric Sockets Page 37 Protocol Pack Update Page 37 Protocol Pack Repository Tab 38 Deploy Tab 39 Deployment Status Tab 39 Module Statistics Page 40 CHAPTER 9 SD-AVC Notes and Limitations 41 CHAPTER 10 Troubleshooting SD-AVC 43 APPENDIX A Operating the SD-AVC Network Service with Host Interface Attached to a VRF 45 APPENDIX B Configuring Secure Connectivity 47 Scenarios Requiring a Secure Connection 47 Securing Connection between Host and SD-AVC Network Service 48 Securing Connection between Agents and Network Service 49 Connectivity to the SD-AVC Dashboard 50 iv
5 Contents Connectivity: Complete Example 50 v
6 Contents vi
7 PART I Part: Introduction SD-AVC Overview, page 3 Operation, page 5 SD-AVC Features and Benefits, page 7
8
9 CHAPTER 1 SD-AVC Overview Cisco Software-Defined AVC (SD-AVC) is a component of Cisco Application Visibility and Control (AVC). It functions as a centralized network service, operating with specific participating devices in a network. As an SDN solution operating network-wide, Cisco SD-AVC complements solutions such as: Cisco Intelligent WAN (IWAN) Cisco EasyQoS Application Assurance Features and Benefits Some of the current features and benefits provided by SD-AVC: Network-level application recognition consistent across the network Improved application recognition in symmetric and asymmetric routing environments Improved first packet recognition Protocol Pack update at the network level Secure browser-based SD-AVC Dashboard over HTTPS for monitoring SD-AVC functionality and statistics, and for configuring Protocol Pack updates network-wide For details, see SD-AVC Features and Benefits, on page 7. No Change to Topology Deploying SD-AVC within an existing network does not require any changes to the network topology. 3
10 4
11 CHAPTER 2 Operation SD-AVC Architecture, page 5 SD-AVC and Application Recognition, page 6 SD-AVC Architecture SD-AVC architecture consists of two basic components: Centralized SD-AVC Network Service component operating on a host device SD-AVC Agent component running on each SD-AVC-enabled device in the network Figure 1: SD-AVC Network Service and Agents 5
12 SD-AVC and Application Recognition SD-AVC and Application Recognition Cisco AVC can recognize network applications, providing recognition of most enterprise network traffic. SD-AVC offers a controller-based approach that operates network-wide, aggregating application information collected across the network, and centralized deployment of Protocol Pack updates. SD-AVC improves application recognition, and offers a solution to challenges posed by complex networks that use a variety of routing devices and routing methods. Such challenges include asymmetric routing, first packet classification, encryption, and so on. Collecting Application Data Devices in the network running AVC analyze traffic and generate application data. If a device is connected to SD-AVC, the SD-AVC agent operating on the device receives this application data, and processes and caches the data. Periodically, the SD-AVC agent sends the latest application data to the centralized SD-AVC network service. As new servers are detected or as server addresses change, the agent continually discovers and validates these servers and updates the SD-AVC network service with the new information. The process of discovery and validation can take several minutes. Server addresses usually remain constant over time, but when they do change, the SD-AVC agent detects the changes and updates the network service. Aggregating Application Data The SD-AVC network service aggregates application data from multiple sources, producing an application rules pack from the composite data. This is made available to network devices using SD-AVC. Periodically, the network devices using SD-AVC request the application rules pack. Relying on devices to pull (request) the application rules pack on their own schedule improves efficiency and simplifies administration. The application rules pack contains the following type of information: ID, IP address, port, network protocol, VRF name, application name, and so on. Example: ID IP Address Port Protocol VRF-name App-Name ================================================================= TCP Mgt VNC 6
13 CHAPTER 3 SD-AVC Features and Benefits SD-AVC Features and Benefits, page 7 SD-AVC Features and Benefits The following table describes several SD-AVC features and benefits. Table 1: Features and Benefits Feature/Benefit Description Network-level application recognition consistent across the network The SD-AVC Network Service aggregates application data from multiple devices and sources, and provides that composite application information in return. Because SD-AVC operates at the network level, any application rule created by SD-AVC based on aggregated application data is shared and applied consistently across all participating network devices. Improved application recognition in symmetric and asymmetric routing environments Cisco SD-AVC further refines application recognition accuracy by helping numerous devices in a network SD-AVC aggregates application data shared by participating devices in the network, and analyzes the shared application data. It then provides this composite application information (in the form of an application rules pack) to the participating routers, improving application recognition. Because SD-AVC shares application rules across numerous network devices, devices that see only one direction of a flow can benefit from the information collected on the other direction of the same flow. See SD-AVC and Application Recognition, on page 6. Improved first packet recognition SD-AVC application rules are based on flow tuple (address and port) information. After a learning phase and sharing tuples among participating devices, the devices are able to identify new flows on the first packet, based on the tuple information 7
14 SD-AVC Features and Benefits Feature/Benefit Protocol Pack update at the network level SD-AVC Dashboard Description SD-AVC can assist in deploying Protocol Packs to numerous routers in the network. Download the Protocol Packs to deploy, store them on the centralized SD-AVC Network Service, then use the SD-AVC Dashboard to select which devices in the network will receive the Protocol Packs. See: Protocol Pack Update Page, on page 37. Secure browser-based SD-AVC Dashboard over HTTPS for monitoring SD-AVC functionality and statistics, and for configuring Protocol Pack updates network-wide. See: Using SD-AVC, on page 33 Using SD-AVC in an Asymmetric Routing Scenario The Challenge of Asymmetric Routing One of the challenges that SD-AVC addresses well is application recognition in asymmetric routing scenarios. While it is not the only situation in which SD-AVC offers improved results, asymmetric routing demonstrates one of the advantages of aggregating application data from many sources. Certain network configurations may produce "asymmetric routing" as an unintended effect. In asymmetric routing, the packets of a single two-way connection travel by different paths between network nodes. For example the downstream traffic from a server to a client might be routed through one path, while the upstream traffic from the client to the server might be through a different path. When this occurs, AVC operating on a hub router may see only a single direction of the traffic for that connection, posing a challenge to application recognition. Deep Packet Inspection and Asymmetry AVC deep packet inspection (DPI) operates best when it sees both directions of traffic. In symmetric routing, AVC operating on a single device that handles both directions of a flow can fully analyze metadata and other traffic attributes to help identify the application creating the flow. By contrast, an asymmetric scenario can limit the ability to recognize some types of traffic. This is especially true when AVC sees only to the downstream traffic for a particular flow. Asymmetric routing may occur for various reasons, including from intelligent path selection by Cisco IWAN. The issue particularly affects hub routers within an enterprise network with a hub/branch topology. 8
15 SD-AVC Features and Benefits Effects of Limited Application Recognition Limiting AVC application recognition can affect classification of traffic for QoS policy, visibility, and other functionality. Consequently, a solution that overcomes the limitations caused by asymmetric routing is especially helpful for maximum network efficiency. Figure 2: Asymmetric Routing Example Centralized Server Aggregating Application Data SD-AVC compiles and analyzes application data from multiple devices within the network, including devices that separately handle the downstream and upstream traffic for a single flow. Using data from multiple sources, SD-AVC synchronizes application information network-wide, overcoming the challenges of asymmetric routing. This strategy provides a major improvement to application recognition within networks, improving the effectiveness of application-based solutions. 9
16 SD-AVC Features and Benefits With the improved application recognition, AVC can apply application-based policies, such as QoS, path selection, and visibility more accurately. For example, with complete information about both streams of a flow, a path selection policy can direct the downstream path through the same route as the upstream. Figure 3: Asymmetric Routing and SD-AVC 10
17 PART II Part: Deployment Installing or Upgrading the SD-AVC Network Service, page 13 Unconfiguring or Uninstalling the SD-AVC Network Service, page 23 Configuring Network Devices, page 25 SD-AVC High Availability, page 29
18
19 CHAPTER 4 Installing or Upgrading the SD-AVC Network Service Installation Overview, page 13 System Requirements: SD-AVC Network Service Host, page 14 Configuring Connectivity, page 15 Using SD-AVC with Cisco IWAN, page 16 Installing the SD-AVC Network Service, page 16 Upgrading the SD-AVC Network Service, page 20 Installation Overview SD-AVC operates in a service/agent configuration. For details, see SD-AVC Architecture, on page 5. Network Service: The SD-AVC Network Service is installed as a virtualized component on a Cisco device service container, and operates on the device as a service. See: System Requirements: SD-AVC Network Service Host, on page 14 Agent: Other devices in the network are enabled as agents, and communicate with the SD-AVC Network Service. See: Configuring Network Devices to Use SD-AVC, on page 25 High Availability: SD-AVC supports a high availability (HA) configuration, using more than one SD-AVC Network Service. See: SD-AVC High Availability, on page 29 Connectivity: Operating SD-AVC requires connectivity between the SD-AVC Network Service and the SD-AVC agents that operate on devices in the network. See: Configuring Connectivity, on page 15 Summary of Setup The following table briefly describes the steps to set up SD-AVC: 13
20 System Requirements: SD-AVC Network Service Host Table 2: Setup 1 Setup Task Download the open virtual appliance (OVA) file for the SD-AVC Network Service, and install it on a host device accessible by other devices in the network. Section See: Installing the SD-AVC Network Service, on page 16 2 Enable the SD-AVC agent on Cisco devices in the network, pointing them to the SD-AVC Network Service set up in the previous step. (In a high availability setup, include more than one SD-AVC Network Service instance.) See: Configuring Network Devices, on page 25 3 Configure connectivity, or optionally, secure connectivity. See: Configuring Connectivity, on page 15, Configuring Secure Connectivity, on page 47 System Requirements: SD-AVC Network Service Host The following table describes platform requirements for hosting the SD-AVC Network Service. Table 3: SD-AVC Network Service Host Requirements Host Memory Storage OS CPU Cisco ASR1001-X M-ASR1001X-16GB NIM-SSD and SSD-SATA-400G Cisco IOS XE Everest or later Cisco ASR1002-X M-ASR1002X-16GB MASR1002X-HD-320G Cisco IOS XE Everest or later Cisco ISR4431 RAM: MEM GU16G Flash: MEM-FLASH-16G NIM-SSD and SSD-MSATA-400G Cisco IOS XE Everest or later Cisco ISR4451 RAM: MEM GU16G Flash: MEM-FLASH-16G NIM-SSD and SSD-MSATA-400G Cisco IOS XE Everest or later Cisco Cloud Services Router CSR1000V Minimum: 8 GB Recommended: 8 GB 20 GB Cisco IOS XE Everest or later 4 cores 14
21 Configuring Connectivity Configuring Connectivity Operating SD-AVC requires connectivity between various components. SD-AVC network service and host SD-AVC network service and agents Connectivity to the SD-AVC Dashboard This section describes the connectivity requirements. If secure connectivity is required, see: Configuring Secure Connectivity, on page 47 SD-AVC Network Service and Host Connectivity is required between the SD-AVC network service, which operates as a virtualized service, and the device hosting it. The host platform requires connectivity with the service through a virtual interface called VirtualPortGroup. The virtual service communicates with the host over this virtual interface, using SSH on TCP port 22. SD-AVC Network Service and Agents Network devices operating with SD-AVC use an SD-AVC agent, which operates in the background on the device, to communicate with the central SD-AVC network service. Connectivity is required between each of these network devices and the SD-AVC network service (more than one network service in SD-AVC high availability configurations). Ports Communication between agent and service uses the following protocols and ports: UDP: Port TCP: Ports 20, 21, Firewalls and Access Lists Ensure that communication is possible in both directions (agent to SD-AVC Network Service, SD-AVC Network Service to agent) on these ports for the relevant traffic. For example: Firewall policy must enable communication in both directions. If a network device has an access control list (ACL) configured, the ACL must permit communication between the SD-AVC Network Service and SD-AVC agents. Connectivity to the SD-AVC Dashboard Connecting to the SD-AVC Dashboard (see Using SD-AVC, on page 33) requires access to the device hosting the SD-AVC Network Service, and involves TCP traffic through port Ensure that network policy (firewall, ACL, and so on) permits this connectivity for devices requiring access to the SD-AVC Dashboard. 15
22 Using SD-AVC with Cisco IWAN Using SD-AVC with Cisco IWAN When operating SD-AVC in a Cisco IWAN environment, the SD-AVC Network Service may be hosted on the hub master controller (MC) or on a router dedicated for the purpose of hosting the service. In either case, verify that the host device meets the system requirements for hosting the SD-AVC Network Service (see System Requirements: SD-AVC Network Service Host, on page 14). For information about installing the SD-AVC Network Service, see Installing the SD-AVC Network Service, on page 16. Installing the SD-AVC Network Service The SD-AVC Network Service operates as a virtualized service on a Cisco router. It is installed as an open virtual appliance (OVA) virtual machine container, and requires a few steps of configuration on the host router. After configuration is complete, you can check service status using the browser-based SD-AVC Dashboard. Table 4: Overview of Installation Steps Task System requirements Installation Configuration Activation Verification Connecting to SD-AVC Dashboard Steps Step 1 Steps 2 to 4 Step 5 Step 6 Steps 7 to 10 Step 11 Examples follow the steps below. Installation Procedure The following procedure installs the SD-AVC Network Service as a virtualized service on a Cisco router. 1 Verify that the intended host device meets the system requirements. See System Requirements: SD-AVC Network Service Host, on page Download the OVA container for the SD-AVC Network Service from Cisco.com, using the Download Software tool. Specify a platform that supports hosting the SD-AVC virtual service, then navigate to software downloads for the platform. Select the "SD AVC Router Virtual Service" option to display available OVA files for SD-AVC. Example filename: iosxe-sd-avc ova 3 Copy the downloaded OVA file onto the device that will host the SD-AVC Network Service. Copy to one of the following locations, depending on the platform type: 16
23 Installing the SD-AVC Network Service CSR1000V: bootflash ASR1000 Series or ISR4000 Series: harddisk harddisk refers to the SSD or HD specified in the system requirements for the platform (System Requirements: SD-AVC Network Service Host, on page 14). 4 On the host device, execute the following command to extract the OVA package and install the SD-AVC Network Service. By default, it is installed on the same storage device where the OVA package was saved. service sd-avc install package disk-with-ova:ova-filename media location-for-ova-expansion Table 5: Command Details CLI keyword/argument disk-with-ova Description Specify one of the following, according to the platform type. The location refers to where the OVA was saved in a previous step. CSR: bootflash ASR1000 Series or ISR4000 Series: harddisk OVA-filename location-for-ova-expansion Downloaded OVA file. Specify one of the following, according to the platform type: CSR: bootflash ASR1000 Series or ISR4000 Series: harddisk Note On ASR1000 and ISR4000 platforms, the CLI may allow you to incorrectly specify the bootflash for the disk-with-ova, but for these platforms, specifying the bootflash as the location will cause this step to fail. On these platforms, specify only the hard disk for disk-with-ova location. Examples: For CSR1000V router: service sd-avc install package bootflash:iosxe-sd-avc ova media bootflash For ASR1000 Series or ISR4000 Series routers: service sd-avc install package harddisk:iosxe-sd-avc ova media harddisk 5 Configure the SD-AVC Network Service. Specify the router gateway interface that the virtualized service uses for external access. Specify a user-selected external-facing service IP address for the SD-AVC Network Service. This address must be within the same subnet as the gateway interface address. 17
24 Installing the SD-AVC Network Service This step accomplishes the following: Enables routers in the network to communicate with the SD-AVC Network Service. Enables access to the browser-based SD-AVC Dashboard. Note Use this command only in scenarios in which the gateway interface is not attached to a VRF. If the gateway interface is attached to a VRF, use the steps described in Operating the SD-AVC Network Service with Host Interface Attached to a VRF, on page 45. service sd-avc configure gateway interface interface service-ip service-ip-address [activate preview] Table 6: Command Details CLI keyword/argument activate preview Description Activates the service immediately. It is not typically recommended to use this option during this configuration step. Execute the activate option in a separate step, as shown below. Preview the configuration without configuring or activating the service. When using this option, the configuration is not sent to the device. Note: If the gateway interface is attached to a VRF, see Operating the SD-AVC Network Service with Host Interface Attached to a VRF, on page 45. Example output:! Virtual port configuration interface VirtualPortGroup31 description automatically created for sd-avc service by 'service sd-avc configure' exec command ip unnumbered gigabitethernet1 end! Virtual service configuration virtual-service SDAVC description automatically created for sd-avc service by 'service sd-avc configure' exec command vnic gateway VirtualPortGroup31 guest ip address exit end! Static route configuration ip route VirtualPortGroup31 interface Gateway interface: The device interface that the virtualized service uses for external access. Note: If the interface is attached to a VRF, see Operating the SD-AVC Network Service with Host Interface Attached to a VRF, on page 45 for instructions for configuring the gateway. 18
25 Installing the SD-AVC Network Service CLI keyword/argument service-ip-address Description External-facing IP address, must be in the same subnet as the IP of the gateway interface. Example: Gateway interface: service-ip-address: Example: service sd-avc configure gateway interface gigabitethernet1 service-ip Activate the service. service sd-avc activate Example: service sd-avc activate 7 Verify that the status of the SD-AVC Network Service is activated. service sd-avc status If installation and activation were successful, the displayed status is: SDAVC service is installed, configured and activated 8 Save the new configuration. copy running-config startup-config 9 Ping the service IP configured in a previous step to verify that it is reachable. 10 Verify that SSH is enabled on the host device. Details vary according to different scenarios, but the following is a helpful reference: ssh.html Example (uses SSH local authentication): aaa new-model! aaa authentication login default local username cisco privilege 15 password cisco ip domain name cisco.com crypto key generate rsa 11 Wait several minutes for the service to become fully active, then use a Chrome browser to access the browser-based SD-AVC Dashboard, at the following URL, which uses the service-ip configured in an earlier step and port The SD-AVC Dashboard uses the same authentication as the platform hosting the SD-AVC Network Service. Note Accessing the SD-AVC Dashboard requires connectivity from the PC you are using to access the SD-AVC interface. 19
26 Upgrading the SD-AVC Network Service Installation Example for CSR1000V Router The following is an example of the CLI steps used to install the SD-AVC Network Service on a Cisco CSR1000V Cloud Services Router. For this router, the first step includes bootflash as the location for extracting the OVA. service sd-avc install package harddisk:iosxe-sd-avc ova media bootflash service sd-avc configure gateway interface gigabitethernet1 service-ip service sd-avc activate service sd-avc status copy running-config startup-config Installation Example for ASR1000 Series or ISR4000 Series Routers The following is an example of the CLI steps used to install the SD-AVC Network Service on a Cisco ASR1000 Series or ISR4000 Series Router. For these routers, the first step includes harddisk as the location for extracting the OVA. service sd-avc install package harddisk:iosxe-sd-avc ova media harddisk service sd-avc configure gateway interface gigabitethernet1 service-ip service sd-avc activate service sd-avc status copy running-config startup-config Upgrading the SD-AVC Network Service Use the following procedure to upgrade the SD-AVC Network Service on the router hosting the service. 1 Deactivate the service. This step stops the service but does not erase the database of compiled application data. service sd-avc deactivate 2 Verify that the service has been deactivated. service sd-avc status The following output confirms that the service has been deactivated: Service SDAVC is installed, configured and deactivated 3 On the host router, execute the following command to extract and install the OVA package. By default, it is installed on the same storage device where the OVA package is stored. service sd-avc upgrade package disk-with-ova:ova-filename media location-for-ova-expansion Table 7: Command Details CLI keyword/argument disk-with-ova Description Specify one of the following, according to the platform type. The location refers to where the OVA was stored in a previous step. CSR: bootflash ASR1000 Series or ISR4000 Series: harddisk OVA-filename Downloaded OVA file. 20
27 Upgrading the SD-AVC Network Service CLI keyword/argument location-for-ova-expansion Description Specify one of the following, according to the platform type: CSR: bootflash ASR1000 Series or ISR4000 Series: harddisk Note On ASR1000 and ISR4000 platforms, the CLI may allow you to specify the bootflash for the disk-with-ova, but on these platforms, specifying the bootflash as the location will cause this step to fail. On these platforms, specify only the hard disk for disk-with-ova location. Examples: For Cisco CSR1000V router: service sd-avc upgrade package bootflash:iosxe-sd-avc ova media bootflash For Cisco ASR1000 Series or ISR4000 Series routers: service sd-avc upgrade package harddisk:iosxe-sd-avc ova media harddisk 4 (Optional) During the upgrade process, view the service status. service sd-avc status During the upgrade, the following output indicates that the service is being installed: Service SDAVC is installing..., configured and deactivated The following output indicates that the upgrade is complete: Service SDAVC is installed, configured and deactivated 5 Activate the service. service sd-avc activate Example: service sd-avc activate 6 Verify that the status of the SD-AVC Network Service is activated. service sd-avc status If upgrade and activation were successful, the displayed status is: SDAVC service is installed, configured and activated 21
28 Upgrading the SD-AVC Network Service 22
29 CHAPTER 5 Unconfiguring or Uninstalling the SD-AVC Network Service Unconfiguring the SD-AVC Network Service, page 23 Uninstalling the SD-AVC Network Service, page 23 Unconfiguring the SD-AVC Network Service Use the following procedure to unconfigure the SD-AVC Network Service on the router hosting the service. Unconfiguring the service is necessary before changing the SD-AVC Network Service configuration. 1 Deactivate the service. This step stops the service but does not erase the database of compiled application data. service sd-avc deactivate 2 Verify that the service has been deactivated. service sd-avc status The following output confirms that the service has been deactivated: Service SDAVC is installed, configured and deactivated 3 Unconfigure the service. service sd-avc unconfigure 4 Verify that the service has been unconfigured. service sd-avc status The following output confirms that the service has been unconfigured: Service SDAVC is installed, not configured and deactivated Uninstalling the SD-AVC Network Service Use the following procedure to uninstall the SD-AVC Network Service on the router hosting the service. 23
30 Uninstalling the SD-AVC Network Service 1 Deactivate and unconfigure the SD-AVC Network Service. Follow the full procedure in: Unconfiguring the SD-AVC Network Service, on page 23 2 Uninstall the service. This step deletes all information from the SD-AVC database for this SD-AVC Network Service. service sd-avc uninstall 3 Verify that the service has been uninstalled. service sd-avc status The following output confirms that the service has been uninstalled: Service SDAVC is uninstalled, not configured and deactivated 24
31 CHAPTER 6 Configuring Network Devices Configuring Network Devices to Use SD-AVC, page 25 System Requirements: Network Devices Using SD-AVC, page 25 Configuration Prerequisites: Network Devices Using SD-AVC, page 26 Activating the SD-AVC Agent, page 26 Deactivating the SD-AVC Agent, page 28 Configuring Network Devices to Use SD-AVC After the SD-AVC Network Service has been set up, use the information in this section to check the prerequisites for Cisco devices in the network to operate with the SD-AVC Network Service. Then activate and configure SD-AVC on the devices. This activates an SD-AVC agent that operates on the devices to communicate with the SD-AVC Network Service. After configuration is complete, verify the status of each device using the SD-AVC Dashboard. The SD-AVC Dashboard is a tool provided by the SD-AVC Network Service, and displays the details of participating devices, among other things (see Using SD-AVC, on page 33). For High Availability SD-AVC, which employs more than one SD-AVC Network Service, see SD-AVC High Availability, on page 29. System Requirements: Network Devices Using SD-AVC The following table describes the supported platforms and requirements for network devices to operate with SD-AVC. When operating with SD-AVC, network devices run the SD-AVC agent, which manages communication between the devices and the SD-AVC Network Service. Table 8: Network Device Requirements Platform OS Cisco ASR1001-X Cisco IOS XE Everest or later Cisco ASR1002-X Cisco IOS XE Everest or later 25
32 Configuration Prerequisites: Network Devices Using SD-AVC Platform Cisco ASR1001-HX Cisco ASR1002-HX Cisco ISR4000 Series: 4451, 4321, 4431 Cisco Cloud Services Router CSR1000V Cisco Route Processor RP2, operating on Cisco ASR1004, ASR1006, or ASR1013 Cisco Route Processor RP3, operating on Cisco ASR1004, ASR1006, or ASR1013 OS Cisco IOS XE Everest or later Cisco IOS XE Everest or later Cisco IOS XE Everest or later Cisco IOS XE Everest or later Cisco IOS XE Everest or later Cisco IOS XE Everest or later Connectivity For connectivity requirements and procedures, see Configuring Connectivity, on page 15. Configuration Prerequisites: Network Devices Using SD-AVC Network devices participating with SD-AVC run an SD-AVC agent (see SD-AVC Architecture, on page 5). SD-AVC functionality depends on receiving application statistics from each participating network device. Application statistics are collected on each interface (on participating devices) on which one of the following is enabled: Cisco Performance Monitor, Easy Performance Monitor (ezpm), PfR policy, or Protocol Discovery Depending on the Cisco solution in place, application statistics must be collected as follows: IWAN solution: (No additional user configuration required) Collection of application statistics is enabled by the use of Easy Performance Monitor (ezpm) and PfR policy. Application Assurance solution: (No additional user configuration required) Collection of application statistics is enabled by the use of Performance Monitor or Easy Performance Monitor (ezpm), and PfR policy. EasyQoS: (Requires user configuration) Configure Protocol Discovery on WAN-side interfaces. Activating the SD-AVC Agent Use the following procedure on a device in the network to activate the SD-AVC agent, enabling the device to communicate with the SD-AVC Network Service. Note See System Requirements for network devices operating with SD-AVC. 26
33 Activating the SD-AVC Agent Note The term, SD-AVC Network Service, refers to the virtual service that operates on a host device and performs SD-AVC functions, such as aggregating application data. The avc sd-service command used in this procedure does not refer to the SD-AVC Network Service. 1 Activate SD-AVC. avc sd-service Example: conft#avc sd-service 2 Configure the segment (group of devices that share the same purpose, such as routers within the same hub). segment cisco Example: (config-sd-service)#segment cisco 3 Enter controller mode to configure the agent to use the SD-AVC Network Service (not related to the avc sd-service command used in an earlier step). controller Example: (config-sd-service)#controller 4 Enter the service-ip used when the SD-AVC Network Service (running on a host device) was set up. address service-ip Note For a high availability (HA) configuration, more than one SD-AVC Network Service is specified in this step. See SD-AVC High Availability, on page 29 for details. Example: (config-sd-service-controller)#address Configure VRF. vrf vrf_mgmt Example: (config-sd-service-controller)#vrf vrf_mgmt The device is now configured to operate with SD-AVC, and begins: Sending collected application data to the SD-AVC Network Service Receiving application rules packs periodically from the SD-AVC Network Service 6 Using the SD-AVC Dashboard, in the Connectivity tab, confirm that the router appears in the hostname list, and that the Exporter Health column shows a green checkmark. Note If the tabs are hidden, click the menu button to display them. 27
34 Deactivating the SD-AVC Agent Configuration Example The following is an example of the CLI steps used to configure the SD-AVC agent on a device. conft#avc sd-service (config-sd-service)#segment cisco (config-sd-service)#controller (config-sd-service-controller)#address (config-sd-service-controller)#vrf vrf_mgmt Deactivating the SD-AVC Agent Use the following procedure on a device in the network to deactivate the SD-AVC agent and clear any SD-AVC agent configuration details that have been entered. This stops SD-AVC functionality on the device, and the device stops communicating with the SD-AVC network service. 1 Deactivate SD-AVC and remove SD-AVC agent configuration. no avc sd-service Example: conft#no avc sd-service 28
35 CHAPTER 7 SD-AVC High Availability SD-AVC supports a high availability (HA) configuration, using more than one SD-AVC network service. Each network device operating with SD-AVC, and consequently running the SD-AVC agent, designates a primary and secondary SD-AVC network service. If the primary SD-AVC network service becomes unavailable, the device fails over to the secondary service. In the event of failover, the secondary SD-AVC network service receives the application data (state) maintained by the SD-AVC agents on participating network devices. This provides SD-AVC a degree of resilience, enabling the secondary network service to receive previously aggregated data and resume operation where the primary network service left off. In addition, because each SD-AVC agent maintains its state locally, classification of traffic on each device continues seamlessly during the failover from primary to secondary network service. For all devices in the network that are operating with SD-AVC, it is recommended to use the same primary SD-AVC network service. Figure 4: Primary and Secondary SD-AVC Network Services in High Availability Configuration 29
36 Configuring High Availability SD-AVC SD-AVC Network Services Collect Application Data Separately Each SD-AVC network service collects application data from the devices that are using it as their active service. Multiple SD-AVC network services do not share application data with each other directly. So if the primary service becomes unavailable, the agents that were using it fail over to the secondary service, and that service begins collecting application data from the agents. Configuring High Availability SD-AVC, page 30 Configuring High Availability SD-AVC Setting up SD-AVC in a high availability configuration requires two steps that differ from a non-ha configuration. 1 Set up more than one SD-AVC Network Service. For information about setting up an SD-AVC Network Service, see Installation Overview, on page When configuring a device to use SD-AVC, specify primary and secondary SD-AVC Network Services with the address command. In other respects, configuring the device is identical to a non-ha configuration. For information about setting up a device, see Configuring Network Devices to Use SD-AVC, on page 25. The configuration commands are shown below. avc sd-service segment cisco controller address primary-network-service-ip secondary-network-service-ip vrf vrf_mgmt Example: conft#avc sd-service (config-sd-service)#segment cisco (config-sd-service)#controller (config-sd-service-controller)#address (config-sd-service-controller)#vrf vrf_mgmt 30
37 PART III Part: Usage Using SD-AVC, page 33 SD-AVC Notes and Limitations, page 41 Troubleshooting SD-AVC, page 43
38
39 CHAPTER 8 Using SD-AVC Using SD-AVC, page 33 Connectivity Page, page 34 Application Visibility Page, page 36 Application Rules Page, page 37 Asymmetric Sockets Page, page 37 Protocol Pack Update Page, page 37 Module Statistics Page, page 40 Using SD-AVC Use the SD-AVC Dashboard to monitor and control SD-AVC functionality and statistics, and to configure Protocol Pack updates. Specifically, the Dashboard: Provides information about devices operating with SD-AVC Provides detailed traffic analytics Enables setting up Protocol Pack deployment Connecting Using a Chrome browser with access to the device hosting the SD-AVC Network Service, open the SD-AVC Dashboard. The Dashboard is accessible using the service IP configured when setting up the SD-AVC Network Service, and port 8443, in the format: Example: 33
40 Connectivity Page Note The SD-AVC Dashboard uses the same authentication as the platform hosting the SD-AVC Network Service. The host platform may use locally configured usernames and passwords, or it may use other methods, such as an Authentication, Authorization, and Accounting (AAA) server. If prompted, enter the username and password used on the host platform. Connectivity Page The Connectivity page lists the devices in the network that are operating with the SD-AVC Network Service, and indicates the connectivity and health status for each device. Table 9: User Controls Control Menu button Description Display web interface tabs. Search field Home button Enter a string in the Search field to filter the display of devices. Open the main dashboard page. Refresh button Refresh display. Time button Display system time. Table 10: Information Provided in the SD-AVC Connectivity Page Field Hostname IP Segment Description Device hostname Device IP Network segment: A group of devices that share the same purpose, such as routers within the same hub. 34
41 Connectivity Page Field Connectivity Description Device connectivity with the SD-AVC Network Service. Connectivity messages are sent over UDP port Green checkmark: All connectivity messages are being received. Orange caution: Some connectivity messages have not been received. SD-AVC will monitor the device for restoration of connectivity. Wait a few minutes for the issue to resolve or escalate to red X. Red X: No messages are being received. Troubleshooting: Check connectivity on UDP port If no problem is found with connectivity, contact Cisco TAC. Update Health Status of updates from the SD-AVC Network Service to the device. Updates include application and configuration data, and are made by standard FTP connection. Green checkmark: The device has successfully accessed the SD-AVC Network Service and has installed any application data updates. Orange caution: Some messages are being received; some are missing. Wait a few minutes for the issue to resolve or escalate to red X. Red X: One of the following may have occurred: (a) No messages are being received. (b) The device has failed to install an application data update from the SD-AVC Network Service. Troubleshooting: Verfiy FTP connectivity on ports 20, 21. On the device, execute show tech-support nbar platform to display NBAR data useful for troubleshooting. Save the output for use by TAC if the problem persists. Exporter Health Status of device data export to the SD-AVC Network Service. Green checkmark: All messages are being received. Orange caution: Some messages are being received; some are missing. Wait a few minutes for the issue to resolve or escalate to red X. Red X: No messages are being received. Troubleshooting: Check FTP connectivity on UDP port If no problem is found with connectivity, contact Cisco TAC. 35
42 Application Visibility Page Field Traffic Health Description Traffic health status in the network indicates whether the device is processing traffic. Green checkmark: The NBAR2 component on the device is processing traffic. Requires: Connectivity between the SD-AVC Network Service and device NBAR2 is enabled. Device is processing traffic. Orange caution: The SD-AVC Network Service has not received some expected application data from the device. Wait a few minutes for the issue to resolve or escalate to red X. Red X: No application data is being received. Possible causes: Connection error. NBAR is not enabled. The device is not processing traffic. Troubleshooting: Check FTP connectivity on UDP port If no problem is found with connectivity, contact Cisco TAC. Classification Score Asymmetric Index Last measured classification quality score for the device. This indicates the degree of classification quality (specificity), calculated according to traffic volume. Higher score indicates better quality. Last measured degree of asymmetry seen by device. This is the ratio of asymmetric flows to total flows for TCP and DNS traffic. 0 is least asymmetry, and 10 is highest asymmetry. Application Visibility Page The Application Visibility page provides high-level information regarding the classification score of devices, and applications providing network traffic. Use the controls at the top to clear the statistics, filter by device, or select a time period (hours). The metrics and graphs displayed on the page are an average over the span of time indicated by the selected period. 36
43 Application Rules Page Table 11: Application Visibility page Metric Classification (over time) score First Packet classification ratio SD-AVC Coverage Ratio Business Relevancy chart Description Degree of classification quality (specificity), calculated according to traffic volume. Ratio of flows classified on the first packet, to total TCP/UDP flows. Ratio of flows covered by the SD-AVC application rules pack, to the total number of TCP/UDP flows. Traffic business relevance, over the period selected in the Period menu. Application Rules Page The Application Rules page lists application data compiled by SD-AVC, organized into rules ready for export to participating devices in the network. The information is sent when the devices request an Application Rules Pack from the SD-AVC Network Service. Asymmetric Sockets Page The Asymmetric Sockets page lists the asymmetric flows currently being tracked by SD-AVC. In networks that do not employ asymmetric routing, the list may be empty. Protocol Pack Update Page The Protocol Pack Update page enables deploying Protocol Packs to devices in the network that are are using SD-AVC. The page contains tabs for loading and scheduling deployment of Protocol Pack files, and checking status. Understanding Protocol Pack Files Cisco releases Protocol Packs on an ongoing basis. Each Protocol Pack release provides updates that expand and improve AVC application recognition. Typically, it is recommended to use the latest Protocol Pack compatible with the OS running on a device. The Protocol Library page indicates the latest Protocol Pack and provides compatibility information. Protocol Packs are available using the Cisco Download Software tool. When using the tool, specify a platform and then navigate to software downloads for the platform. Protocol Pack filenames have the following format: pp-adv-<platform-type>-<os>-<engine-id>-<protocol-pack-version>.pack Platform type may be, for example, asr1k, csr1000v, or isr4000. However, a Protocol Pack may be installed on any compatible device, even if that device is not indicated by the filename. 37
44 Protocol Pack Update Page How SD-AVC Determines which Devices are Compatible with a Protocol Pack The SD-AVC network service contains a Protocol Pack repository that stores specific Protocol Packs uploaded to the repository for deployment to devices in the network. The SD-AVC network service deploys a Protocol Pack in the repository to all compatible devices, at the time scheduled. To determine compatibility, the SD-AVC network service compares the IOS version and engine ID of a Protocol Pack in the repository to the IOS version and engine running on devices in the network. If a Protocol Pack in the repository is compatible with a device, then the SD-AVC network service deploys the Protocol Pack from the repository to the device. Deploying Protocol Packs Using SD-AVC Use the SD-AVC network service to deploy Protocol Packs to devices operating with the service, as follows: 1 Determine the Protocol Pack to deploy. The Protocol Library page provides compatibility information. 2 Download the Protocol Pack using the Cisco Download Software tool. In the filename of the downloaded Protocol Pack, note the engine ID. 3 In the SD-AVC Dashboard, use the Protocol Pack Update page to upload the Protocol Pack file into the Protocol Pack repository on the SD-AVC network service. SD-AVC determines which devices are compatible with the Protocol Packs in the repository. 4 On the Protocol Pack Update page, open the Deployment Status tab. The SD-AVC network service indicates the Protocol Packs ready for deployment to compatible devices. 5 On the Protocol Pack Update page, open the Deploy tab and schedule a time for deployment. At the specified time, the SD-AVC network service deploys the Protocol Pack to any compatible devices. If no time is scheduled, and if the Immediate option is not selected, then Protocol Pack deployment does not occur. Protocol Pack Repository Tab The Protocol Pack Repository is a collection of Protocol Pack files stored with the SD-AVC Network Service, for deployment to devices managed by the SD-AVC Network Service. The Protocol Pack Repository tab: Displays Protocol Pack files in the repository. Enables loading Protocol Pack files into the repository. Enables removal of Protocol Pack files from the repository. Table 12: Information in the Protocol Pack Repository Tab Column Name Engine-ID Description Protocol Pack filename. The engine ID is determined by the version of Cisco IOS XE. Protocol Pack files are compatible with specific engine ID versions. 38
45 Protocol Pack Update Page Column Latest Action Description A green checkmark in this column indicates that the Protocol Pack file is ready for deployment. To downgrade from a later Protocol Pack to an earlier Protocol Pack (for example to ), delete the later Protocol Pack from the repository, upload the earlier version (30.0.0), and then deploy. SD-AVC deploys the Protocol Pack to all compatible devices managed by the SD-AVC Network Service. Enables deleting a Protocol Pack file from the repository. Deploy Tab The Deploy tab enables scheduling a deployment time or selecting Immediate for immediate deployment. If no time is scheduled, the SD-AVC Network Service does not deploy any Protocol Packs. Deployment Status Tab The Deployment Status tab displays information about each device managed by the SD-AVC Network Service, as described in the following table. It indicates the current Protocol Pack, and any compatible Protocol Pack in the repository, if there is one. If a Protocol Pack file is listed in the Candidate column, and if it differs from the Active Protocol Pack, then the Candidate Protocol Pack will be deployed at the scheduled deployment time. Table 13: Information in the Deployment Status Tab Column Hostname IP Segment Active Pack Candidate Description Device hostname. Device IP. Network segment: A group of devices that share the same purpose, such as routers within the same hub. Protocol Pack currently installed on the device. A compatible Protocol Pack in the repository. Note: The latest Protocol Pack file in the repository compatible with the device may be an older Protocol Pack version, especially if the repository has not been kept up to date. 39
46 Module Statistics Page Column Current Status Last Status Description Green: The active Protocol Pack and the candidate are the same, so no Protocol Pack will be deployed to the device. Yellow/Orange: The candidate Protocol Pack is different from the active one, and it will be deployed at the scheduled time. Red: The candidate Protocol Pack is different from the active one, and a recent attempt to deploy a Protocol Pack failed. In this case the Last Status column indicates that a deployment failed. Indicates the status of the most recent attempt, if any, to deploy a Protocol Pack to the device. Module Statistics Page The Module Statistics page displays statistics for various types of packets, for each device. Each device reports raw data about packet handling to the SD-AVC Network Service, which compiles statistics for each device. The statistics may be useful for monitoring or troubleshooting. Click the X-icon to clear the module statistics. 40
47 CHAPTER 9 SD-AVC Notes and Limitations The following are limitations of SD-AVC: For the SD-AVC Network Service, running on a host device, if the host interface that is used as a gateway interface is attached to a VRF, see Operating the SD-AVC Network Service with Host Interface Attached to a VRF, on page 45 for configuration details. SD-AVC requires a few minutes to learn from the network traffic before the application data is sent to the SD-AVC Network Service and compiled at the network level. See SD-AVC and Application Recognition, on page 6. SD-AVC provides application classification for server-based applications. The SD-AVC application rules pack is less relevant for client-to-client traffic, which is more granular and dynamic. Client-to-client traffic is classified by NBAR running on each network element. In the case of a proxy or content delivery network (CDN), multiple applications may use the same IP/port combination. The network devices themselves classify such traffic fully. However, for these applications, the SD-AVC agent operating on a device may report application data to the SD-AVC network service with a lesser degree of detail: they may be reported with less detailed classification granularity or not at all. 41
48 42
49 CHAPTER 10 Troubleshooting SD-AVC This section provides information for troubleshooting SD-AVC problems. If this information does not provide a solution, contact Cisco TAC for assistance. Communication with Devices by TCP The SD-AVC Network Service uses TCP to communicate with the devices that it manages, over port In the SD-AVC Dashboard, if the Connectivity Page page shows any type of connectivity warning, check FTP connectivity on UDP port If no problem is found with connectivity, contact Cisco TAC. NBAR Activation on Interfaces On devices in the network that are using SD-AVC, the NBAR2 component must be active on any interface that processes network traffic, in order to report on traffic handled by the interface. For details, see Configuration Prerequisites: Network Devices Using SD-AVC, on page 26. Without this, the device will not report on any traffic on that interface. This can cause a red X icon warning in the SD-AVC Dashboard, on the Connectivity Page page, in the Traffic Health column. 43
50 44
51 APPENDIX A Operating the SD-AVC Network Service with Host Interface Attached to a VRF In specific use cases, it may be necessary to operate the SD-AVC Network Service on a host device on which the host interface that is used by SD-AVC as its gateway interface may be attached to a VRF. In this case, the typical installation command described in Installing the SD-AVC Network Service, on page 16 cannot be used, and manual configuration is required, using the following guidelines: Ensure that the virtual port group and gateway interface(s) are not on the same subnet. Assign the virtual port group and gateway interface(s) to a VRF. Ensure that the IP address of the SD-AVC network service (guest IP in the configuration steps below) is on the virtual port group subnet. Example: ip vrf Mgt! interface VirtualPortGroup31 ip vrf forwarding Mgt ip address ! interface GigabitEthernet1 ip vrf forwarding Mgt ip address ! virtual-service SDAVC vnic gateway VirtualPortGroup31 guest ip address activate! 45
52 Operating the SD-AVC Network Service with Host Interface Attached to a VRF 46
53 APPENDIX B Configuring Secure Connectivity Scenarios Requiring a Secure Connection, page 47 Securing Connection between Host and SD-AVC Network Service, page 48 Securing Connection between Agents and Network Service, page 49 Connectivity to the SD-AVC Dashboard, page 50 Connectivity: Complete Example, page 50 Scenarios Requiring a Secure Connection For network scenarios that require a secure connection between a network device running the SD-AVC agent, and the SD-AVC Network Service, you can optionally encrypt the SD-AVC communication between agent 47
54 Securing Connection between Host and SD-AVC Network Service Configuring Secure Connectivity and Network Service using IPsec tunnels, and control device access using access control lists (ACL), as described in the sections that follow. Figure 5: IPsec Tunnels between Network Devices and SD-AVC Network Service Securing Connection between Host and SD-AVC Network Service The SD-AVC Network Service runs as a virtual service on a Cisco device serving as a host platform. The host platform requires connectivity with the service through a virtual interface called VirtualPortGroup. The virtual service communicates with the host over this virtual interface, using SSH on TCP port 22. Using ACL to Secure Connectivity between Host and SD-AVC Network Service The SD-AVC network service operates as a virtualized component on a host device. To secure the connection between the host device and the SD-AVC network service, use the following: interface VirtualPortGroup31 ip unnumbered GigabitEthernet1 ip access-group sd-avc-acl in 48
55 Configuring Secure Connectivity Securing Connection between Agents and Network Service ip access-list extended acl-name permit tcp host SD-AVC-virtual-service-IP host host-router-ip eq 22 permit tcp host host-router-ip eq 22 SD-AVC-virtual-service-IP Example using ACL: interface VirtualPortGroup31 ip unnumbered GigabitEthernet1 ip access-group sd-avc-acl in ip access-list extended sd-avc-acl!! Configure SSH connection between the sd-avc-network-service to the hosted router permit tcp host host eq 22 permit tcp host eq 22 host Securing Connection between Agents and Network Service Network devices operating with SD-AVC communicate with a central SD-AVC Network Service. Ensure that ports, firewall policy, and so on, are configured to enable communication between the SD-AVC agents and SD-AVC Network Service(s) (see Configuring Connectivity, on page 15). Using ACL to Secure Connection between Agent and Network Service On the device hosting the SD-AVC Network Service, configure the UDP and TCP access control lists, as follows. Note When using ACLs, only configured addresses will have access to the device hosting the SD-AVC Network Service. UDP The following syntax is presented for reference. For complete information about configuring ACL, see the documentation for your platform. permit udp [ host source-agent-ip source-agent-network source-wildcard ] host sd-avc-network-service-ip eq Example: Configuring port for UDP traffic for a range of devices ( to 255). permit udp host eq permit udp host eq TCP The following syntax is presented for reference. For complete information about configuring ACL, see the documentation for your platform. permit tcp [ host source-agent-ip source-agent-network source-wildcard ] host sd-avc-network-service-ip [eq port range port-range-start port-range-end] Example: Configuring required ports (20, 21, ) for TCP traffic for a range of devices ( to 255). permit tcp host eq 20 permit tcp host eq permit tcp host eq 21 permit tcp host eq
Installing or Upgrading the SD-AVC Network Service
 Installing or Upgrading the SD-AVC Network Service Installation Overview, page 1 System Requirements: SD-AVC Network Service Host, page 2 Configuring Connectivity, page 3 Using SD-AVC with Cisco IWAN,
Installing or Upgrading the SD-AVC Network Service Installation Overview, page 1 System Requirements: SD-AVC Network Service Host, page 2 Configuring Connectivity, page 3 Using SD-AVC with Cisco IWAN,
Lifecycle Management for Virtual Machine Applications Configuration Guide, Cisco IOS Everest 16.6
 Lifecycle Management for Virtual Machine Applications Configuration Guide, Cisco IOS Everest 16.6 IOx: Support 3rd Party Apps in KVMs 2 Information About IOx: Support 3rd Party Apps in KVMs 2 Configuring
Lifecycle Management for Virtual Machine Applications Configuration Guide, Cisco IOS Everest 16.6 IOx: Support 3rd Party Apps in KVMs 2 Information About IOx: Support 3rd Party Apps in KVMs 2 Configuring
Troubleshooting SD-AVC
 SD-AVC This section provides several SD-AVC troubleshooting scenarios. If this information does not provide a solution, contact Cisco TAC for assistance. Overview, page 1 SD-AVC Network Service Issues,
SD-AVC This section provides several SD-AVC troubleshooting scenarios. If this information does not provide a solution, contact Cisco TAC for assistance. Overview, page 1 SD-AVC Network Service Issues,
Configuring Application Visibility and Control for Cisco Flexible Netflow
 Configuring Application Visibility and Control for Cisco Flexible Netflow First published: July 22, 2011 This guide contains information about the Cisco Application Visibility and Control feature. It also
Configuring Application Visibility and Control for Cisco Flexible Netflow First published: July 22, 2011 This guide contains information about the Cisco Application Visibility and Control feature. It also
NBAR2 HTTP-Based Visibility Dashboard
 The NBAR2 HTTP-based Visibility Dashboard provides a web interface displaying network traffic data and related information. The information is presented in an intuitive, interactive graphical format. Finding
The NBAR2 HTTP-based Visibility Dashboard provides a web interface displaying network traffic data and related information. The information is presented in an intuitive, interactive graphical format. Finding
Guest Shell. Finding Feature Information. Information About Guest Shell. Guest Shell Overview
 Guestshell is a virtualized Linux-based environment, designed to run custom Linux applications, including Python for automated control and management of Cisco devices. It also includes the automated provisioning
Guestshell is a virtualized Linux-based environment, designed to run custom Linux applications, including Python for automated control and management of Cisco devices. It also includes the automated provisioning
Cisco Branch Routers Series Network Analysis Module (NME-NAM-120S) Installation and Configuration Note, 4.2
 Cisco Branch Routers Series Network Analysis Module (NME-NAM-120S) Installation and Configuration Note, 4.2 The Cisco Network Analysis Module (NAM) is an integrated module that enables network managers
Cisco Branch Routers Series Network Analysis Module (NME-NAM-120S) Installation and Configuration Note, 4.2 The Cisco Network Analysis Module (NAM) is an integrated module that enables network managers
Cisco IWAN Application on DNA Center Quick Start Guide, Release 1.1 Patch 1, Limited Availability
 Cisco IWAN Application on DNA Center Quick Start Guide, Release 1.1 Patch 1, Limited Availability First Published: 2017-12-22 Last Modified: 2017-12-22 Americas Headquarters Cisco Systems, Inc. 170 West
Cisco IWAN Application on DNA Center Quick Start Guide, Release 1.1 Patch 1, Limited Availability First Published: 2017-12-22 Last Modified: 2017-12-22 Americas Headquarters Cisco Systems, Inc. 170 West
Sun RPC ALG Support for Firewalls and NAT
 The feature adds support for the Sun Microsystems remote-procedure call (RPC) application-level gateway (ALG) on the firewall and Network Address Translation (NAT). Sun RPC is an application layer protocol
The feature adds support for the Sun Microsystems remote-procedure call (RPC) application-level gateway (ALG) on the firewall and Network Address Translation (NAT). Sun RPC is an application layer protocol
Sun RPC ALG Support for Firewalls and NAT
 The feature adds support for the Sun Microsystems remote-procedure call (RPC) application-level gateway (ALG) on the firewall and Network Address Translation (NAT). Sun RPC is an application layer protocol
The feature adds support for the Sun Microsystems remote-procedure call (RPC) application-level gateway (ALG) on the firewall and Network Address Translation (NAT). Sun RPC is an application layer protocol
Guest Shell. Finding Feature Information. Information About Guest Shell. Guest Shell Overview
 Guestshell is a virtualized Linux-based environment, designed to run custom Linux applications, including Python for automated control and management of Cisco devices. It also includes the automated provisioning
Guestshell is a virtualized Linux-based environment, designed to run custom Linux applications, including Python for automated control and management of Cisco devices. It also includes the automated provisioning
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM
 Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Cisco IWAN Application 2.2 on DNA Center, Quick Start Guide
 First Published: 2018-06-04 Last Modified: 2018-06-04 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
First Published: 2018-06-04 Last Modified: 2018-06-04 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Using NetFlow Sampling to Select the Network Traffic to Track
 Using NetFlow Sampling to Select the Network Traffic to Track Last Updated: September 17, 2012 This module contains information about and instructions for selecting the network traffic to track through
Using NetFlow Sampling to Select the Network Traffic to Track Last Updated: September 17, 2012 This module contains information about and instructions for selecting the network traffic to track through
Cisco Stealthwatch Learning Network License Virtual Service Quick Start Guide
 Cisco Stealthwatch Learning Network License Virtual Service Quick Start Guide Cisco Stealthwatch Learning Network License Quick Start Guide 2 Learning Network License Introduction 2 Installation Prerequisites
Cisco Stealthwatch Learning Network License Virtual Service Quick Start Guide Cisco Stealthwatch Learning Network License Quick Start Guide 2 Learning Network License Introduction 2 Installation Prerequisites
Cisco Prime Network Analysis Module (Cisco Prime NAM) for Nexus 1110 Installation and Configuration Guide
 Cisco Prime Network Analysis Module (Cisco Prime NAM) for Nexus 1110 Installation and Configuration Guide Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Cisco Prime Network Analysis Module (Cisco Prime NAM) for Nexus 1110 Installation and Configuration Guide Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Nested Class Map Support for Zone-Based Policy Firewall
 Nested Class Map Support for Zone-Based Policy Firewall The Nested Class Map Support for Zone-Based Policy Firewall feature provides the Cisco IOS XE firewall the functionality to configure multiple traffic
Nested Class Map Support for Zone-Based Policy Firewall The Nested Class Map Support for Zone-Based Policy Firewall feature provides the Cisco IOS XE firewall the functionality to configure multiple traffic
Cisco Cloud Services Platform 2100 Quick Start Guide, Release 2.2.0
 Cisco Cloud Services Platform 2100 Quick Start Guide, Release 2.2.0 First Published: 2017-03-15 Last Modified: 2017-08-03 Summary Steps Setting up your Cisco Cloud Services Platform 2100 (Cisco CSP 2100)
Cisco Cloud Services Platform 2100 Quick Start Guide, Release 2.2.0 First Published: 2017-03-15 Last Modified: 2017-08-03 Summary Steps Setting up your Cisco Cloud Services Platform 2100 (Cisco CSP 2100)
Fine-Grain NBAR for Selective Applications
 By default NBAR operates in the fine-grain mode, offering NBAR's full application recognition capabilities. Used when per-packet reporting is required, fine-grain mode offers a troubleshooting advantage.
By default NBAR operates in the fine-grain mode, offering NBAR's full application recognition capabilities. Used when per-packet reporting is required, fine-grain mode offers a troubleshooting advantage.
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Enabling ALGs and AICs in Zone-Based Policy Firewalls
 Enabling ALGs and AICs in Zone-Based Policy Firewalls Zone-based policy firewalls support Layer 7 application protocol inspection along with application-level gateways (ALGs) and application inspection
Enabling ALGs and AICs in Zone-Based Policy Firewalls Zone-based policy firewalls support Layer 7 application protocol inspection along with application-level gateways (ALGs) and application inspection
Technology Overview. Overview CHAPTER
 CHAPTER 2 Revised: July 29, 2013, This overview of AVC technology includes the following topics: Overview, page 2-1 AVC Features and Capabilities, page 2-2 AVC Architecture, page 2-4 Interoperability of
CHAPTER 2 Revised: July 29, 2013, This overview of AVC technology includes the following topics: Overview, page 2-1 AVC Features and Capabilities, page 2-2 AVC Architecture, page 2-4 Interoperability of
Metadata Configuration Guide Cisco IOS Release 15M&T
 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 2014 Cisco Systems, Inc. All rights
Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 2014 Cisco Systems, Inc. All rights
Restrictions for Secure Copy Performance Improvement
 The Protocol (SCP) feature provides a secure and authenticated method for copying router configuration or router image files. SCP relies on Secure Shell (SSH), an application and a protocol that provide
The Protocol (SCP) feature provides a secure and authenticated method for copying router configuration or router image files. SCP relies on Secure Shell (SSH), an application and a protocol that provide
Software License Solution
 This document describes the software restructuring that the Cisco ASR 1000 Series Aggregation Services Routers has undergone to achieve consistency in software solution packaging across Enterprise Routing
This document describes the software restructuring that the Cisco ASR 1000 Series Aggregation Services Routers has undergone to achieve consistency in software solution packaging across Enterprise Routing
Upgrade Guide for Cisco Digital Media System Release 5.0
 Upgrade Guide for Cisco Digital Media System Release 5.0 Revised: December 12, 2008, This guide provides information about and instructions for upgrading your Cisco DMS appliances and Cisco Digital Media
Upgrade Guide for Cisco Digital Media System Release 5.0 Revised: December 12, 2008, This guide provides information about and instructions for upgrading your Cisco DMS appliances and Cisco Digital Media
IWAN APIC-EM Application Cisco Intelligent WAN
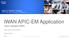 IWAN APIC-EM Application Cisco Intelligent WAN René og Per Cisco DK SE s Feb 23 th 2016 AVC MPLS Private Cloud 3G/4G-LTE Virtual Private Cloud Branch WAAS PfR Internet Public Cloud Control, Management,
IWAN APIC-EM Application Cisco Intelligent WAN René og Per Cisco DK SE s Feb 23 th 2016 AVC MPLS Private Cloud 3G/4G-LTE Virtual Private Cloud Branch WAAS PfR Internet Public Cloud Control, Management,
Monitoring WAAS Using WAAS Central Manager. Monitoring WAAS Network Health. Using the WAAS Dashboard CHAPTER
 CHAPTER 1 This chapter describes how to use WAAS Central Manager to monitor network health, device health, and traffic interception of the WAAS environment. This chapter contains the following sections:
CHAPTER 1 This chapter describes how to use WAAS Central Manager to monitor network health, device health, and traffic interception of the WAAS environment. This chapter contains the following sections:
Enabling ALGs and AICs in Zone-Based Policy Firewalls
 Enabling ALGs and AICs in Zone-Based Policy Firewalls Zone-based policy firewalls support Layer 7 application protocol inspection along with application-level gateways (ALGs) and application inspection
Enabling ALGs and AICs in Zone-Based Policy Firewalls Zone-based policy firewalls support Layer 7 application protocol inspection along with application-level gateways (ALGs) and application inspection
Fine-Grain NBAR for Selective Applications
 By default NBAR operates in the fine-grain mode, offering NBAR's full application recognition capabilities. Used when per-packet reporting is required, fine-grain mode offers a troubleshooting advantage.
By default NBAR operates in the fine-grain mode, offering NBAR's full application recognition capabilities. Used when per-packet reporting is required, fine-grain mode offers a troubleshooting advantage.
NBAR Protocol Pack Auto Update
 Cisco provides periodic updates of NBAR2 Protocol Packs for Cisco IOS releases designated as long-lived, to improve NBAR2 traffic recognition capabilities on an ongoing basis. The Protocol Pack Auto Update
Cisco provides periodic updates of NBAR2 Protocol Packs for Cisco IOS releases designated as long-lived, to improve NBAR2 traffic recognition capabilities on an ongoing basis. The Protocol Pack Auto Update
Sun RPC ALG Support for Firewall and NAT
 Sun RPC ALG Support for Firewall and NAT Last Updated: December 18, 2011 The Sun RPC ALG Support for Firewall and NAT feature adds support for the Sun Microsystems (Sun) Remote Procedure Call (RPC) Application
Sun RPC ALG Support for Firewall and NAT Last Updated: December 18, 2011 The Sun RPC ALG Support for Firewall and NAT feature adds support for the Sun Microsystems (Sun) Remote Procedure Call (RPC) Application
Configuring Support for Remote Management by the Cisco Prime Network Services Controller
 Configuring Support for Remote Management by the Cisco Prime Network Services Controller Configuring the Management Interface to Support Remote Management by the Cisco Prime Network Services Controller,
Configuring Support for Remote Management by the Cisco Prime Network Services Controller Configuring the Management Interface to Support Remote Management by the Cisco Prime Network Services Controller,
Remote Access MPLS-VPNs
 First Published: August 12, 2002 Last Updated: May 4, 2009 The feature allows the service provider to offer a scalable end-to-end Virtual Private Network (VPN) service to remote users. This feature integrates
First Published: August 12, 2002 Last Updated: May 4, 2009 The feature allows the service provider to offer a scalable end-to-end Virtual Private Network (VPN) service to remote users. This feature integrates
Optimizing Enterprise Networks through SD-AVC (Software Define Application Visibility and Control)
 BRKCRS-2502 Optimizing Enterprise Networks through SD-AVC (Software Define Application Visibility and Control) Guy Keinan Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after
BRKCRS-2502 Optimizing Enterprise Networks through SD-AVC (Software Define Application Visibility and Control) Guy Keinan Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after
Cisco Cloud Services Platform 2100 Quick Start Guide, Release 2.2.5
 Cisco Cloud Services Platform 2100 Quick Start Guide, Release 2.2.5 First Published: 2018-03-30 Summary Steps Setting up your Cisco Cloud Services Platform 2100 (Cisco CSP 2100) and creating services consists
Cisco Cloud Services Platform 2100 Quick Start Guide, Release 2.2.5 First Published: 2018-03-30 Summary Steps Setting up your Cisco Cloud Services Platform 2100 (Cisco CSP 2100) and creating services consists
Managing Site-to-Site VPNs: The Basics
 CHAPTER 21 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
CHAPTER 21 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
Managing Site-to-Site VPNs
 CHAPTER 21 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
CHAPTER 21 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
Performance Routing Version 3 Configuration Guide
 First Published: 2014-07-22 Last Modified: 2016-04-20 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
First Published: 2014-07-22 Last Modified: 2016-04-20 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
Identity Firewall. About the Identity Firewall
 This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
Converged Access CT 5760 AVC Deployment Guide, Cisco IOS XE Release 3.3
 Converged Access CT 5760 AVC Deployment Guide, Cisco IOS XE Release 3.3 Last Updated: November, 2013 Introduction This guide is designed to help you deploy and monitor new features introduced in the IOS
Converged Access CT 5760 AVC Deployment Guide, Cisco IOS XE Release 3.3 Last Updated: November, 2013 Introduction This guide is designed to help you deploy and monitor new features introduced in the IOS
SIP RFC 2782 Compliance with DNS SRV Queries
 SIP RFC 2782 Compliance with DNS SRV Last Updated: December 21, 2011 Effective with Cisco IOS XE Release 2.5, the Domain Name System Server (DNS SRV) query used to determine the IP address of the user
SIP RFC 2782 Compliance with DNS SRV Last Updated: December 21, 2011 Effective with Cisco IOS XE Release 2.5, the Domain Name System Server (DNS SRV) query used to determine the IP address of the user
Managing Site-to-Site VPNs: The Basics
 CHAPTER 23 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
CHAPTER 23 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
HTTP 1.1 Web Server and Client
 HTTP 1.1 Web Server and Client Last Updated: October 12, 2011 The HTTP 1.1 Web Server and Client feature provides a consistent interface for users and applications by implementing support for HTTP 1.1
HTTP 1.1 Web Server and Client Last Updated: October 12, 2011 The HTTP 1.1 Web Server and Client feature provides a consistent interface for users and applications by implementing support for HTTP 1.1
SSL Custom Application
 feature enables users to customize applications that run on any protocol over Secure Socket Layer (SSL), including HTTP over Secure Socket Layer (HTTPS), using the server name, if it exists in the Client
feature enables users to customize applications that run on any protocol over Secure Socket Layer (SSL), including HTTP over Secure Socket Layer (HTTPS), using the server name, if it exists in the Client
Configuring Data Export for Flexible NetFlow with Flow Exporters
 Configuring Data Export for Flexible NetFlow with Flow Exporters Last Updated: November 29, 2012 This document contains information about and instructions for configuring flow exporters to export Flexible
Configuring Data Export for Flexible NetFlow with Flow Exporters Last Updated: November 29, 2012 This document contains information about and instructions for configuring flow exporters to export Flexible
IP Routing: ODR Configuration Guide, Cisco IOS Release 15M&T
 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION
Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION
Inspection of Router-Generated Traffic
 Inspection of Router-Generated Traffic The Inspection of Router-Generated Traffic feature allows Context-Based Access Control (CBAC) to inspect traffic that is originated by or destined to the router on
Inspection of Router-Generated Traffic The Inspection of Router-Generated Traffic feature allows Context-Based Access Control (CBAC) to inspect traffic that is originated by or destined to the router on
Using the Management Interfaces
 The following management interfaces are provided for external users and applications: Gigabit Ethernet Management Interface, page 1 SNMP, page 7 Gigabit Ethernet Management Interface Gigabit Ethernet Management
The following management interfaces are provided for external users and applications: Gigabit Ethernet Management Interface, page 1 SNMP, page 7 Gigabit Ethernet Management Interface Gigabit Ethernet Management
Upgrading the Cisco APIC-EM Deployment
 Review the following sections in this chapter for information about upgrading to the latest Cisco APIC-EM version and verification. Using the GUI to Upgrade Cisco APIC-EM, page 1 Using the CLI to Upgrade
Review the following sections in this chapter for information about upgrading to the latest Cisco APIC-EM version and verification. Using the GUI to Upgrade Cisco APIC-EM, page 1 Using the CLI to Upgrade
GSS Administration and Troubleshooting
 CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
QoS: Classification, Policing, and Marking on LAC Configuration Guide, Cisco IOS Release 12.4T
 QoS: Classification, Policing, and Marking on LAC Configuration Guide, Cisco IOS Release 12.4T Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
QoS: Classification, Policing, and Marking on LAC Configuration Guide, Cisco IOS Release 12.4T Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Guest Shell. Information About the Guest Shell. Guest Shell Overview
 Guestshell is a virtualized Linux-based environment, designed to run custom Linux applications, including Python for automated control and management of Cisco devices. It also includes the automated provisioning
Guestshell is a virtualized Linux-based environment, designed to run custom Linux applications, including Python for automated control and management of Cisco devices. It also includes the automated provisioning
Guest Shell. Information About the Guest Shell. Guest Shell Overview
 Guestshell is a virtualized Linux-based environment, designed to run custom Linux applications, including Python for automated control and management of Cisco devices. It also includes the automated provisioning
Guestshell is a virtualized Linux-based environment, designed to run custom Linux applications, including Python for automated control and management of Cisco devices. It also includes the automated provisioning
Cisco HyperFlex Upgrade Guide for Microsoft Hyper-V, Release 3.5
 First Published: 2018-10-16 Last Modified: 2018-11-19 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
First Published: 2018-10-16 Last Modified: 2018-11-19 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
Using NetFlow Sampling to Select the Network Traffic to Track
 Using NetFlow Sampling to Select the Network Traffic to Track This module contains information about and instructions for selecting the network traffic to track through the use of NetFlow sampling. The
Using NetFlow Sampling to Select the Network Traffic to Track This module contains information about and instructions for selecting the network traffic to track through the use of NetFlow sampling. The
Deploying IWAN Routers
 Deploying IWAN Routers Cisco Prime Infrastructure 3.1 Job Aid Copyright Page THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS,
Deploying IWAN Routers Cisco Prime Infrastructure 3.1 Job Aid Copyright Page THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS,
Cisco cbr Converged Broadband Routers High Availability Configuration Guide
 Cisco cbr Converged Broadband Routers High Availability Configuration Guide First Published: 2015-07-31 Last Modified: 2015-12-01 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose,
Cisco cbr Converged Broadband Routers High Availability Configuration Guide First Published: 2015-07-31 Last Modified: 2015-12-01 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose,
Configuring Application Visibility and Control
 Information About Application Visibility and Control, page 1 Restrictions for Application Visibility and Control, page 2 (GUI), page 3 (CLI), page 4 Configuring NetFlow, page 5 Information About Application
Information About Application Visibility and Control, page 1 Restrictions for Application Visibility and Control, page 2 (GUI), page 3 (CLI), page 4 Configuring NetFlow, page 5 Information About Application
IGMP Proxy. Finding Feature Information. Prerequisites for IGMP Proxy
 This module describes how to configure IGMP proxy to enable a device to send an IGMP report to a specified destination IP address. Finding Feature Information, page 1 Prerequisites for, page 1 Information
This module describes how to configure IGMP proxy to enable a device to send an IGMP report to a specified destination IP address. Finding Feature Information, page 1 Prerequisites for, page 1 Information
Configuring IP Multicast over Unidirectional Links
 Configuring IP Multicast over Unidirectional Links Last Updated: December 16, 2011 IP multicast requires bidirectional communication, yet some networks include broadcast satellite links, which are unidirectional.
Configuring IP Multicast over Unidirectional Links Last Updated: December 16, 2011 IP multicast requires bidirectional communication, yet some networks include broadcast satellite links, which are unidirectional.
HTTP 1.1 Web Server and Client
 The feature provides a consistent interface for users and applications by implementing support for HTTP 1.1 in Cisco IOS XE software-based devices. When combined with the HTTPS feature, the feature provides
The feature provides a consistent interface for users and applications by implementing support for HTTP 1.1 in Cisco IOS XE software-based devices. When combined with the HTTPS feature, the feature provides
Configuring the Cisco IOS XE DHCP Server
 Configuring the Cisco IOS XE DHCP Server Last Updated: December 20, 2011 Cisco routers running Cisco IOS XE software include Dynamic Host Configuration Protocol (DHCP) server and relay agent software.
Configuring the Cisco IOS XE DHCP Server Last Updated: December 20, 2011 Cisco routers running Cisco IOS XE software include Dynamic Host Configuration Protocol (DHCP) server and relay agent software.
Cisco Terminal Services (TS) Agent Guide, Version 1.1
 First Published: 2017-05-03 Last Modified: 2017-10-13 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
First Published: 2017-05-03 Last Modified: 2017-10-13 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
NetBrain OE System Quick Start Guide
 NetBrain Technologies Inc. NetBrain OE System Quick Start Guide For Operator Edition Administrators Table of Contents 1. Install NetBrain OE System... 3 1.1 Install Gateway Server... 4 1.2 Install Network
NetBrain Technologies Inc. NetBrain OE System Quick Start Guide For Operator Edition Administrators Table of Contents 1. Install NetBrain OE System... 3 1.1 Install Gateway Server... 4 1.2 Install Network
Setting up Microsoft Exchange Server 2016 with Avi
 Page 1 of 14 Setting up Microsoft Exchange Server 2016 with Avi Networks view online What is Exchange Server 2016 Microsoft Exchange Server 2016 is an e-mail server solution, with calendar and contact
Page 1 of 14 Setting up Microsoft Exchange Server 2016 with Avi Networks view online What is Exchange Server 2016 Microsoft Exchange Server 2016 is an e-mail server solution, with calendar and contact
Cisco Stealthwatch Learning Network License Virtual Service Installation Guide
 Cisco Stealthwatch Learning Network License Virtual Service Installation Guide First Published: July 13, 2016 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA
Cisco Stealthwatch Learning Network License Virtual Service Installation Guide First Published: July 13, 2016 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA
Lab Configuring and Verifying Extended ACLs Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Configuring Stateful Interchassis Redundancy
 The Stateful Interchassis Redundancy feature enables you to configure pairs of devices to act as backups for each other. This module describes conceptual information about and tasks for configuring stateful
The Stateful Interchassis Redundancy feature enables you to configure pairs of devices to act as backups for each other. This module describes conceptual information about and tasks for configuring stateful
Cisco Terminal Services (TS) Agent Guide, Version 1.1
 First Published: 2017-05-03 Last Modified: 2017-12-19 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
First Published: 2017-05-03 Last Modified: 2017-12-19 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
Forescout. Configuration Guide. Version 2.4
 Forescout Version 2.4 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 2.4 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Creating an IP Access List to Filter IP Options, TCP Flags, or Noncontiguous Ports
 Creating an IP Access List to Filter IP Options, TCP Flags, or Noncontiguous Ports First Published: August 18, 2006 Last Updated: July 31, 2009 This module describes how to use an IP access list to filter
Creating an IP Access List to Filter IP Options, TCP Flags, or Noncontiguous Ports First Published: August 18, 2006 Last Updated: July 31, 2009 This module describes how to use an IP access list to filter
User Security Configuration Guide, Cisco IOS Release 15MT
 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 2014 Cisco Systems, Inc. All rights
Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 2014 Cisco Systems, Inc. All rights
Implementing Traffic Filters for IPv6 Security
 Implementing Traffic Filters for IPv6 Security Last Updated: November 14, 2011 This module describes how to configure Cisco IOS XE IPv6 traffic filter and firewall features for your Cisco networking devices.
Implementing Traffic Filters for IPv6 Security Last Updated: November 14, 2011 This module describes how to configure Cisco IOS XE IPv6 traffic filter and firewall features for your Cisco networking devices.
Release Notes for Cisco Application Policy Infrastructure Controller Enterprise Module, Release x
 Release s for Cisco Application Policy Infrastructure Controller Enterprise Module, Release 1.3.3.x First Published: 2017-02-10 Release s for Cisco Application Policy Infrastructure Controller Enterprise
Release s for Cisco Application Policy Infrastructure Controller Enterprise Module, Release 1.3.3.x First Published: 2017-02-10 Release s for Cisco Application Policy Infrastructure Controller Enterprise
Configuring Secure Shell
 Configuring Secure Shell Last Updated: October 24, 2011 The Secure Shell (SSH) feature is an application and a protocol that provides a secure replacement to the Berkeley r-tools. The protocol secures
Configuring Secure Shell Last Updated: October 24, 2011 The Secure Shell (SSH) feature is an application and a protocol that provides a secure replacement to the Berkeley r-tools. The protocol secures
SD-WAN Deployment Guide (CVD)
 SD-WAN Deployment Guide (CVD) All Cisco Meraki security appliances are equipped with SD-WAN capabilities that enable administrators to maximize network resiliency and bandwidth efficiency. This guide introduces
SD-WAN Deployment Guide (CVD) All Cisco Meraki security appliances are equipped with SD-WAN capabilities that enable administrators to maximize network resiliency and bandwidth efficiency. This guide introduces
IMC Network Traffic Analyzer 7.2 (E0401P04) Copyright 2016 Hewlett Packard Enterprise Development LP
 Network Traffic Analyzer 7.2 (E0401P04) Copyright 2016 Hewlett Packard Enterprise Development LP Table of Contents 1. What's New in this Release 2. Problems Fixed in this Release 3. Software Distribution
Network Traffic Analyzer 7.2 (E0401P04) Copyright 2016 Hewlett Packard Enterprise Development LP Table of Contents 1. What's New in this Release 2. Problems Fixed in this Release 3. Software Distribution
VII. Corente Services SSL Client
 VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
Configuring Template ACLs
 Configuring Template ACLs First Published: June 19, 2009 Last Updated: June 19, 2009 When user profiles are configured using RADIUS Attribute 242 or vendor-specific attribute (VSA) Cisco-AVPairs, similar
Configuring Template ACLs First Published: June 19, 2009 Last Updated: June 19, 2009 When user profiles are configured using RADIUS Attribute 242 or vendor-specific attribute (VSA) Cisco-AVPairs, similar
Upgrading the Cisco IOS XE Software
 Prerequisites for the Software Upgrade Process, page 1 Saving Backup Copies of Your Old System Image and Configuration, page 2 Using TFTP or Remote Copy Protocol to Copy the System Image into Boot Flash
Prerequisites for the Software Upgrade Process, page 1 Saving Backup Copies of Your Old System Image and Configuration, page 2 Using TFTP or Remote Copy Protocol to Copy the System Image into Boot Flash
Installing the Cisco CSR 1000v in VMware ESXi Environments
 Installing the Cisco CSR 1000v in VMware ESXi Environments VMware ESXi Support Information, page 1 VMware Requirements Cisco IOS XE Fuji 16.7, page 2 Supported VMware Features and Operations, page 3 Deploying
Installing the Cisco CSR 1000v in VMware ESXi Environments VMware ESXi Support Information, page 1 VMware Requirements Cisco IOS XE Fuji 16.7, page 2 Supported VMware Features and Operations, page 3 Deploying
Using NetFlow Filtering or Sampling to Select the Network Traffic to Track
 Using NetFlow Filtering or Sampling to Select the Network Traffic to Track First Published: June 19, 2006 Last Updated: December 17, 2010 This module contains information about and instructions for selecting
Using NetFlow Filtering or Sampling to Select the Network Traffic to Track First Published: June 19, 2006 Last Updated: December 17, 2010 This module contains information about and instructions for selecting
User Workspace Management
 Access the Interface, page 1 User Management Workspace User Types, page 4 Projects (Admin User), page 5 Users (Admin User), page 9 CML Server (Admin User), page 11 Connectivity, page 30 Using the VM Control
Access the Interface, page 1 User Management Workspace User Types, page 4 Projects (Admin User), page 5 Users (Admin User), page 9 CML Server (Admin User), page 11 Connectivity, page 30 Using the VM Control
Cisco Nexus Data Broker for Network Traffic Monitoring and Visibility
 Guide Cisco Nexus Data Broker for Network Traffic Monitoring and Visibility Solution Implementation Guide 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.
Guide Cisco Nexus Data Broker for Network Traffic Monitoring and Visibility Solution Implementation Guide 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.
Branch Repeater :51:35 UTC Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement
 Branch Repeater 6.0 2013-07-22 14:51:35 UTC 2013 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents Branch Repeater 6.0... 3 Branch Repeater 6.0... 4 Release Notes
Branch Repeater 6.0 2013-07-22 14:51:35 UTC 2013 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents Branch Repeater 6.0... 3 Branch Repeater 6.0... 4 Release Notes
Release Notes for Cisco Insight Reporter, v3.1
 November 2011 This document describes the operating environment and the defects and caveats that were identified as part of internal testing and during the live trials. It assumes the reader has a good
November 2011 This document describes the operating environment and the defects and caveats that were identified as part of internal testing and during the live trials. It assumes the reader has a good
Deploying VMware Identity Manager in the DMZ. JULY 2018 VMware Identity Manager 3.2
 Deploying VMware Identity Manager in the DMZ JULY 2018 VMware Identity Manager 3.2 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Deploying VMware Identity Manager in the DMZ JULY 2018 VMware Identity Manager 3.2 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Deploying VMware Identity Manager in the DMZ. SEPT 2018 VMware Identity Manager 3.3
 Deploying VMware Identity Manager in the DMZ SEPT 2018 VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Deploying VMware Identity Manager in the DMZ SEPT 2018 VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Bulk Logging and Port Block Allocation
 The feature allocates a block of ports for translation instead of allocating individual ports. This feature is supported only in carrier-grade Network Address Translation (CGN) mode. This module provides
The feature allocates a block of ports for translation instead of allocating individual ports. This feature is supported only in carrier-grade Network Address Translation (CGN) mode. This module provides
Configuring AVC to Monitor MACE Metrics
 This feature is designed to analyze and measure network traffic for WAAS Express. Application Visibility and Control (AVC) provides visibility for various applications and the network to central network
This feature is designed to analyze and measure network traffic for WAAS Express. Application Visibility and Control (AVC) provides visibility for various applications and the network to central network
LiveNX 7.4 QUICK START GUIDE (QSG) LiveAction, Inc WEST BAYSHORE ROAD PALO ALTO, CA LIVEACTION, INC.
 LIVEACTION, INC. LiveNX 7.4 QUICK START GUIDE (QSG) LiveAction, Inc. 3500 WEST BAYSHORE ROAD PALO ALTO, CA 94303 1-1 LiveNX 7.4 Quick Start Guide (QSG) Introduction This LiveNX 7.4 Quick Start Guide will
LIVEACTION, INC. LiveNX 7.4 QUICK START GUIDE (QSG) LiveAction, Inc. 3500 WEST BAYSHORE ROAD PALO ALTO, CA 94303 1-1 LiveNX 7.4 Quick Start Guide (QSG) Introduction This LiveNX 7.4 Quick Start Guide will
Application Firewall-Instant Message Traffic Enforcement
 Application Firewall-Instant Message Traffic Enforcement Last Updated: September 24, 2012 The Application Firewall--Instant Message Traffic Enforcement feature enables users to define and enforce a policy
Application Firewall-Instant Message Traffic Enforcement Last Updated: September 24, 2012 The Application Firewall--Instant Message Traffic Enforcement feature enables users to define and enforce a policy
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
LiveNX 8.0 QUICK START GUIDE (QSG) LiveAction, Inc WEST BAYSHORE ROAD PALO ALTO, CA LIVEACTION, INC.
 LIVEACTION, INC. LiveNX 8.0 QUICK START GUIDE (QSG) LiveAction, Inc. 3500 WEST BAYSHORE ROAD PALO ALTO, CA 94303 1-1 LiveNX 8.0 Quick Start Guide (QSG) Introduction This LiveNX 8.0 Quick Start Guide will
LIVEACTION, INC. LiveNX 8.0 QUICK START GUIDE (QSG) LiveAction, Inc. 3500 WEST BAYSHORE ROAD PALO ALTO, CA 94303 1-1 LiveNX 8.0 Quick Start Guide (QSG) Introduction This LiveNX 8.0 Quick Start Guide will
Cisco Terminal Services (TS) Agent Guide, Version 1.0
 First Published: 2016-08-29 Last Modified: 2018-01-30 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
First Published: 2016-08-29 Last Modified: 2018-01-30 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
Configuring Port to Application Mapping
 Configuring Port to Application Mapping Last Updated: January 19, 2012 This chapter describes the Cisco IOS Firewall Port to Application Mapping (PAM) feature. PAM enables CBAC-supported applications to
Configuring Port to Application Mapping Last Updated: January 19, 2012 This chapter describes the Cisco IOS Firewall Port to Application Mapping (PAM) feature. PAM enables CBAC-supported applications to
IPsec Anti-Replay Window: Expanding and Disabling
 IPsec Anti-Replay Window: Expanding and Disabling First Published: February 28, 2005 Last Updated: March 24, 2011 Cisco IP security (IPsec) authentication provides anti-replay protection against an attacker
IPsec Anti-Replay Window: Expanding and Disabling First Published: February 28, 2005 Last Updated: March 24, 2011 Cisco IP security (IPsec) authentication provides anti-replay protection against an attacker
Deploying Cisco Nexus Data Broker Embedded for OpenFlow
 Deploying Cisco Nexus Data Broker Embedded for OpenFlow This chapter contains the following sections: Obtaining the Cisco Nexus Data Broker Embedded Software for OpenFlow, page 1 Upgrading to Release 3.2.2,
Deploying Cisco Nexus Data Broker Embedded for OpenFlow This chapter contains the following sections: Obtaining the Cisco Nexus Data Broker Embedded Software for OpenFlow, page 1 Upgrading to Release 3.2.2,
