Akamai: Turning Enterprise Security Inside Out
|
|
|
- Loreen Cannon
- 5 years ago
- Views:
Transcription
1 VENDOR PROFILE Akamai: Turning Enterprise Security Inside Out Christina Richmond Duncan Brown IDC OPINION Akamai is a leader in content delivery network (CDN) services. The company has built a web security portfolio that emphasizes scale, intelligence, and expertise, along with security services for cloud/internet-dependent enterprises. In addition: Akamai has experienced significant growth because its services address two challenging business issues. The first is maintaining uptime and preventing data loss through web services, which are essential to customer engagement and growth. The second is improving security for enterprise users that are increasingly mobile and outside of the traditional network perimeter. Akamai is adapting what it has done for outward-facing web applications and applying this inwardly for enterprises. This effort spans two divisions: the Web Business unit, which is focused on instant, secure access to applications and sites for all users and devices, and the new Enterprise Business unit, whose vision is to secure, optimize, and accelerate the enterprise as a service in the cloud. The business units' approach to thwarting attacks is timely and innovative, with a multipronged strategy encompassing web application firewall (WAF), DDoS mitigation, bot management, DNS, remote application access, threat protection, and branch network architectures. As a result of acquisitions and internal development, Akamai's portfolio of cloud security services is market leading, easy to use, and backed by high performance levels. IN THIS VENDOR PROFILE This IDC Vendor Profile analyzes Akamai's security services offerings. This Vendor Profile reviews key success factors including company strategy, service strategy, service offerings, and partnerships. SITUATION OVERVIEW Company Overview Akamai was founded in 1998 out of MIT as a better way to deliver internet content. The company has more than 230,000 servers in more than 130 countries within 3,500+ locations. The publicly traded company is headquartered in Cambridge, Massachusetts, and has offices throughout the United States, Canada, EMEA, and Asia/Pacific (APAC). The company's client list includes one-third of the Global 500, 96 of the top 100 online U.S. retailers, all branches of the U.S. military, the top 30 media and entertainment companies, 13 of the top 15 automobile manufacturers, and other high-profile companies and industries. Akamai says it can optimize web performance and availability for any web environment. May 2017, IDC #US
2 Akamai's solutions are organized into three divisions: Web, which delivers instant, secure access for "any device, anywhere" and personalized online experiences including dynamically generated rich content, with protections against applications and DDoS attacks (The platform, which distributes web content, enterprise applications, and video, sits between a company's infrastructure and the public internet. It monitors internet conditions and provides device-level detection as well as identifies, absorbs, and blocks security threats.) Media, which delivers high-end online experiences related to content produced by media, gaming, and software companies (Relevant capabilities include Adaptive Media Delivery, Predictive Content Delivery, Adaptive Media Player, and Media Analytics.) Enterprise, which facilitates remote access to internal applications, accelerates the applications, reduces bandwidth costs, and extends the internet and public clouds into private wide area networks (WANs) Akamai's annual revenue is $2.3 billion, with approximately $400 million coming from security services. Company Strategy Akamai's content delivery strategy is to be at the edge, distributing content close to end users. Similarly, Akamai addresses online threats closer to attackers instead of nearer to enterprise datacenters and web assets. This approach is enabled by Akamai's global platform, which provides visibility into attackers and their tactics before they hit enterprise infrastructures and facilitates the delivery of good traffic. Akamai wants to make it easier for organizations to remain secure. To this end, the enterprise security solutions focus on simplifying infrastructure for chief information officers (CIOs), even as more users, applications, and data leave the traditional confines of the enterprise network and datacenter. The solutions use the same security technology and platform used by other Akamai services but focus on requests going out from an enterprise instead of requests coming into the web infrastructure. Akamai's laudable goal is to augment and extend what enterprises are currently doing with their infrastructures, allowing them over time to shrink their infrastructures as they move "outside" into cloud and service provider environments. This evolution requires a fabric to link the inside and outside, and Akamai wants to be the fabric. The vision for the fabric is that it will contain necessary security controls such as threat protection, proxies, web gateway, and ultimately next-generation firewall. The Bloxx acquisition in 2015 is an essential part of this strategy because it brought deep packet inspection and application classification capabilities. Akamai delivers enterprise security services in three areas: Enterprise application access (EAA) to address the problem of remote access. EAA launched earlier this year based on the acquisition of Soha Systems in The service enables Akamai to simplify and improve remote and mobile access to enterprise information with cloud-based application access control. The service, which can be deployed in minutes, solves three security challenges: Moves infrastructure off the public internet and eliminates inbound network port access 2017 IDC #US
3 Enables an enterprise connector (a virtual machine) inside the infrastructure that only dials out and is fully managed in the cloud eliminating inbound holes in the firewall Isolates Layer 7 connectivity from users' browsers all the way back to the enterprise application, so the network is not open and users see only the applications exposed to them Threat protection by making DNS safe and preventing DDoS attacks. Akamai has built a new threat research team focused on DNS and is rolling out a cloud-based recursive DNS platform to customers and carrier partners to provide visibility on this side. Akamai already has visibility on the authoritative DNS side from its legacy business. With this approach, Akamai can improve security by preventing DNS-based data exfiltration, command and control callbacks, and access to malicious malware and phishing domains. Branch acceleration. Akamai Cloud Networking is designed to provide secure, reliable internet connectivity for branch and remote offices. Currently, the service is designed for network service and communication service providers and branch infrastructure vendors to incorporate into their offerings, covering IP-VPNs and cloud and SaaS applications. Cloud Networking services will provide: SLA-backed route optimization and packet delivery Caching, data deduplication, and quality-of-service optimization Secure web gateway functionality with cloud-based outbound web filtering and inbound malware protection with identity integration Web Security Product Strategy Akamai's cloud network and interconnected services provide expansive data that the company has turned into an information security and threat intelligence platform. The platform is augmented by a security operations center (SOC) and managed services function. Key web security offerings include: Automated WAF capability (Web Application Protector) for businesses that require protection from DDoS and compliance but don't have resident expertise or want to allocate resources elsewhere More robust WAF capability (Kona Site Defender) that provides automated rule updates and a managed services option Scalable DNS (Fast DNS) infrastructure to protect against volumetric attacks Network traffic routing protections (Prolexic) through scrubbing centers, where traffic is inspected by Akamai's SOC staff (Flow-based monitoring helps enterprises understand when to route traffic on and off this solution.) The aforementioned offerings can be augmented with additional solutions: Client reputation to address evolving threats that result from malware, spyware, and account takeovers SIEM integration to ensure that the existing analytics infrastructure is valuable and reliable Bot management related account takeover and, in the near future, credential abuse (This includes a means of aligning business objectives and IT/InfoSec concerns regarding bot management.) Partnerships Akamai has a robust partner program. Certain strategic alliances are notable for their potential to aid Akamai's growth. In early 2017, LAC, an information security company, augmented its portfolio with 2017 IDC #US
4 Akamai's internet-monitoring service for the purpose of protecting corporate websites. In late 2016, Akamai began training and certifying Singtel personnel to deliver professional and managed security services for web security solutions initially in Singapore and eventually in Asia/Pacific. FUTURE OUTLOOK Challenges and Opportunities The security landscape is a highly complex mix of technologies, services, and approaches. As adoption of digital transformation and 3rd Platform technologies (cloud, big data/analytics, mobile, and social) accelerates, new challenges arise related to where data resides, how data is accessed, and who owns security. With hybrid architectures and migration to cloud, applications, data, and users increasingly are outside the chief information officer's traditional domain, yet CIOs are responsible for security, visibility, control, and compliance. Security service providers can differentiate themselves first and foremost by simplifying the complex mix to make it more easily digestible for CIOs and other enterprise decision makers and decision influencers. Further, threat intelligence should be a decisive factor in the selection of vendors that offer security products and services. Threat intelligence, however, is evolving rapidly with the use of artificial intelligence and machine learning, and buyers may be confused about types of threat intelligence, what to buy, how to apply the intelligence, how to prioritize the threats, and how to prevent or mitigate threats. Market-leading service providers will offer: Complementary consulting services that provide customizable opportunities for customers to plan and enable their security journeys Flexible consumption models that match customer preferences for integrating a service provider's expertise, processes, and technology Cloud management capabilities that enable seamless hybrid implementations Pricing models that align with customer preferences Advanced detection and analytics capabilities, including advanced detection and response capabilities, threat intelligence, and big data, for infrastructure and endpoints Robust customer support, including incident response and forensics, to assist with recovery from breaches Managed security services, supported by security operations centers that have advanced methods of acquiring and retaining security talent The CAGR for the security services market is 8%, and the CAGR for the threat intelligence services market is 11.3%. Given these forecasts, there is significant opportunity for vendors and enterprises of all sizes. By engaging a vendor like Akamai, enterprises can implement security with a breach prevention emphasis that leverages cloud-based solutions, threat intelligence, and threat mitigation. Meanwhile, other challenges persist: Integrating threat intelligence into a business is a complex endeavor. Organizations must navigate their own technologies as well as those proposed by vendors, and they struggle with defining roles, responsibilities, communications, and processes IDC #US
5 Education must continue with board members and executives regarding the threat landscape, security strategies, threat intelligence options, detection and response options, integration, budgeting, and staffing. A shortage of security talent is a continuing problem, although service providers may have an advantage over enterprises in attracting and retaining staff because they can offer flexible career paths, cross-training, and rapid advancement. Enterprises are increasingly outsourcing security tasks because of the difficulties associated with staffing. ESSENTIAL GUIDANCE Advice for Akamai IDC believes that Akamai is exceptionally well positioned to continue its growth in security services. The company's innovative methods of protecting websites, infrastructures, and applications represent an important advancement in the delivery of security services. To support its continuing growth, Akamai should: Develop a customer journey story specific to targeted companies and verticals. A big part of this effort should be education about security basics and essentials, including services, technologies, expertise, and "what's next" to ensure cadence and encourage motion toward adoption. Akamai and its partners should be able to provide a wealth of security insights, recommendations, and use cases that can be used in an educational endeavor. Promote the "turning the enterprise inside out" message because it is fresh and spot on. This concept can give CIOs a framework for security education and business case development. Become a thought leader with respect to outcome-based customer engagements. The market is heading this way, and Akamai has an opportunity to position itself as a market leader and innovator. Akamai's core strength in network optimization and traffic analysis is increasingly being turned toward the company's security proposition. The logical extension of this is the "cloaking" of an organization's entire network, where access to and from the public internet is brokered by Akamai. Indeed, the company is already offering elements of this to selected clients. In this regard, Akamai is competing with SDN and segmentation approaches to compete directly with Unisys Stealth as well as VMware, Cisco, and Juniper. This "segmentation as a service" could be a precious nugget of differentiation as well as being attractive to companies under constant probes and attacks. LEARN MORE Related Research Worldwide Specialized Threat Analysis and Protection Forecast, : Enterprises Modernize Security Infrastructure (IDC #US , December 2016) Worldwide Web Security Forecast, : Extending Protection to Cloud Resources (IDC #US , December 2016) Worldwide Endpoint Security Forecast, (IDC #US , October 2016) Market Analysis Perspective: Worldwide Managed Security Services, 2016 (IDC #US , September 2016) 2017 IDC #US
6 Market Analysis Perspective: Worldwide Security Services, Security Services Grow Up (IDC #US , September 2016) Worldwide Threat Intelligence Security Services Forecast, : Strength in Numbers (IDC #US , March 2016) IDC's Worldwide Security Services Taxonomy, 2016 (IDC #US , March 2016) 2017 IDC #US
7 About IDC International Data Corporation (IDC) is the premier global provider of market intelligence, advisory services, and events for the information technology, telecommunications and consumer technology markets. IDC helps IT professionals, business executives, and the investment community make factbased decisions on technology purchases and business strategy. More than 1,100 IDC analysts provide global, regional, and local expertise on technology and industry opportunities and trends in over 110 countries worldwide. For 50 years, IDC has provided strategic insights to help our clients achieve their key business objectives. IDC is a subsidiary of IDG, the world's leading technology media, research, and events company. Global Headquarters 5 Speen Street Framingham, MA USA idc-insights-community.com Copyright Notice This IDC research document was published as part of an IDC continuous intelligence service, providing written research, analyst interactions, telebriefings, and conferences. Visit to learn more about IDC subscription and consulting services. To view a list of IDC offices worldwide, visit Please contact the IDC Hotline at , ext (or ) or sales@idc.com for information on applying the price of this document toward the purchase of an IDC service or for information on additional copies or web rights. Copyright 2017 IDC. Reproduction is forbidden unless authorized. All rights reserved.
Predictive Insight, Automation and Expertise Drive Added Value for Managed Services
 Sponsored by: Cisco Services Author: Leslie Rosenberg December 2017 Predictive Insight, Automation and Expertise Drive Added Value for Managed Services IDC OPINION Competitive business leaders are challenging
Sponsored by: Cisco Services Author: Leslie Rosenberg December 2017 Predictive Insight, Automation and Expertise Drive Added Value for Managed Services IDC OPINION Competitive business leaders are challenging
IDC MarketScape: Worldwide Network Consulting Services 2017 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Network Consulting Services 2017 Vendor Assessment Leslie Rosenberg THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Network Consulting Services 2017 Vendor Assessment Leslie Rosenberg THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2016 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2016 Vendor Assessment Chad Huston Ali Zaidi THIS IDC MARKETSCAPE EXCERPT FEATURES: WIPRO IDC
IDC MarketScape IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2016 Vendor Assessment Chad Huston Ali Zaidi THIS IDC MARKETSCAPE EXCERPT FEATURES: WIPRO IDC
The Emerging Role of a CDN in Facilitating Secure Cloud Deployments
 White Paper The Emerging Role of a CDN in Facilitating Secure Cloud Deployments Sponsored by: Fastly Robert Ayoub August 2017 IDC OPINION The ongoing adoption of cloud services and the desire for anytime,
White Paper The Emerging Role of a CDN in Facilitating Secure Cloud Deployments Sponsored by: Fastly Robert Ayoub August 2017 IDC OPINION The ongoing adoption of cloud services and the desire for anytime,
IDC MarketScape: Worldwide Cloud Professional Services 2014 Vendor Analysis
 IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2014 Vendor Analysis Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2014 Vendor Analysis Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape: Worldwide Cloud Professional Services 2018 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2018 Vendor Assessment Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES DELL EMC IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2018 Vendor Assessment Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES DELL EMC IDC MARKETSCAPE FIGURE FIGURE 1 IDC
CloudGenix: Application-Centric SD-WAN
 Vendor Profile CloudGenix: Application-Centric SD-WAN Ksenia Efimova IDC OPINION The software-defined WAN (SD-WAN) market has started to mature as companies begin to understand the advantages of SD-WAN
Vendor Profile CloudGenix: Application-Centric SD-WAN Ksenia Efimova IDC OPINION The software-defined WAN (SD-WAN) market has started to mature as companies begin to understand the advantages of SD-WAN
Worldwide Datacenter Automation Software 2013 Vendor Shares
 COMPETITIVE ANALYSIS Worldwide Datacenter Automation Software 2013 Vendor Shares Mary Johnston Turner IDC OPINION In 2013, the worldwide datacenter automation software submarket of the workload scheduling
COMPETITIVE ANALYSIS Worldwide Datacenter Automation Software 2013 Vendor Shares Mary Johnston Turner IDC OPINION In 2013, the worldwide datacenter automation software submarket of the workload scheduling
IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2014 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2014 Vendor Assessment Ali Zaidi Gard Little THIS IDC MARKETSCAPE EXCERPT FEATURES: HCL IDC MARKETSCAPE
IDC MarketScape IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2014 Vendor Assessment Ali Zaidi Gard Little THIS IDC MARKETSCAPE EXCERPT FEATURES: HCL IDC MARKETSCAPE
IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment
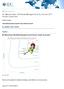 IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment Martha Vazquez THIS MARKETSCAPE EXCERPT WAS CREATED FOR BT IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide
IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment Martha Vazquez THIS MARKETSCAPE EXCERPT WAS CREATED FOR BT IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide
IDC MarketScape: Worldwide Mobile Threat Management Software Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Mobile Threat Management Software 2018 2019 Vendor Assessment Phil Hochmuth THIS IDC MARKETSCAPE EXCERPT FEATURES LOOKOUT IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape IDC MarketScape: Worldwide Mobile Threat Management Software 2018 2019 Vendor Assessment Phil Hochmuth THIS IDC MARKETSCAPE EXCERPT FEATURES LOOKOUT IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape: Worldwide Service Providers 2018 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Service Providers 2018 Vendor Assessment Courtney Munroe THIS IDC MARKETSCAPE EXCERPT FEATURES NTT COMMUNICATIONS IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Service Providers 2018 Vendor Assessment Courtney Munroe THIS IDC MARKETSCAPE EXCERPT FEATURES NTT COMMUNICATIONS IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
Optimizing Infrastructure Management with Predictive Analytics: The Red Hat Insights Approach
 White Paper Optimizing Infrastructure Management with Predictive Analytics: The Red Hat Insights Approach Sponsored by: Red Hat Tim Grieser January 2018 IN THIS WHITE PAPER This IDC White Paper discusses
White Paper Optimizing Infrastructure Management with Predictive Analytics: The Red Hat Insights Approach Sponsored by: Red Hat Tim Grieser January 2018 IN THIS WHITE PAPER This IDC White Paper discusses
Global Headquarters: 5 Speen Street Framingham, MA USA P F
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e D a t a c e
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e D a t a c e
IDC MarketScape: Worldwide Security Solutions and Services Hardcopy 2017 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Security Solutions and Services Hardcopy 2017 Vendor Assessment Robert Palmer Allison Correia THIS IDC MARKETSCAPE EXCERPT FEATURES: HP IDC MARKETSCAPE FIGURE
IDC MarketScape IDC MarketScape: Worldwide Security Solutions and Services Hardcopy 2017 Vendor Assessment Robert Palmer Allison Correia THIS IDC MARKETSCAPE EXCERPT FEATURES: HP IDC MARKETSCAPE FIGURE
Intent-Based Networking in the Limelight with Cisco's Launch of Catalyst 9000 Series Ethernet Switches
 MARKET NOTE Intent-Based Networking in the Limelight with Cisco's Launch of Catalyst 9000 Series Ethernet Switches Nolan Greene Rohit Mehra EXECUTIVE SNAPSHOT FIGURE 1 Executive Snapshot: Cisco Intent-Based
MARKET NOTE Intent-Based Networking in the Limelight with Cisco's Launch of Catalyst 9000 Series Ethernet Switches Nolan Greene Rohit Mehra EXECUTIVE SNAPSHOT FIGURE 1 Executive Snapshot: Cisco Intent-Based
Automated Infrastructure Management Powers Future-Ready Enterprise Clouds
 WHITE PAPER Automated Infrastructure Management Powers Future-Ready Enterprise Clouds Sponsored by: Dell Mary Johnston Turner April 2016 Richard L. Villars IDC OPINION Future-ready enterprises continually
WHITE PAPER Automated Infrastructure Management Powers Future-Ready Enterprise Clouds Sponsored by: Dell Mary Johnston Turner April 2016 Richard L. Villars IDC OPINION Future-ready enterprises continually
Global Headquarters: 5 Speen Street Framingham, MA USA P F
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e D a t a c e
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e D a t a c e
Atlantis Computing Adds the Ability to Address Classic Server Workloads
 FLASH Atlantis Computing Adds the Ability to Address Classic Server Workloads Eric Burgener Brett Waldman IN THIS FLASH This IDC Flash discusses Atlantis Computing's In-Memory Storage technology and how
FLASH Atlantis Computing Adds the Ability to Address Classic Server Workloads Eric Burgener Brett Waldman IN THIS FLASH This IDC Flash discusses Atlantis Computing's In-Memory Storage technology and how
Global Headquarters: 5 Speen Street Framingham, MA USA P F
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com INSIGHT VERITAS: Expanding the Storage Foundations and Building Utility Computing Rhoda Phillips Bill
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com INSIGHT VERITAS: Expanding the Storage Foundations and Building Utility Computing Rhoda Phillips Bill
AKAMAI CLOUD SECURITY SOLUTIONS
 AKAMAI CLOUD SECURITY SOLUTIONS Whether you sell to customers over the web, operate data centers around the world or in the cloud, or support employees on the road, you rely on the Internet to keep your
AKAMAI CLOUD SECURITY SOLUTIONS Whether you sell to customers over the web, operate data centers around the world or in the cloud, or support employees on the road, you rely on the Internet to keep your
IDC MarketScape: Worldwide Managed Security Services 2014 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2014 Vendor Assessment Christina Richmond THIS IDC MARKETSCAPE EXCERPT FEATURES: AT&T IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2014 Vendor Assessment Christina Richmond THIS IDC MARKETSCAPE EXCERPT FEATURES: AT&T IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
Cisco ACI Helps Integra Compete in Next-Generation Telecom Services Market
 IDC ExpertROI SPOTLIGHT Cisco ACI Helps Integra Compete in Next-Generation Telecom Services Market Sponsored by: Cisco Matthew Marden February 2016 Overview Brad Casemore Founded in 1996, Integra is one
IDC ExpertROI SPOTLIGHT Cisco ACI Helps Integra Compete in Next-Generation Telecom Services Market Sponsored by: Cisco Matthew Marden February 2016 Overview Brad Casemore Founded in 1996, Integra is one
Vendor Snapshot 2017: HP Inc. on Print and Document Security Services
 MARKET NOTE Vendor Snapshot 2017: HP Inc. on Print and Document Security Services Robert Palmer Allison Correia EXECUTIVE SNAPSHOT FIGURE 1 Executive Snapshot: Vendor Snapshot 2017 HP Inc. on Print and
MARKET NOTE Vendor Snapshot 2017: HP Inc. on Print and Document Security Services Robert Palmer Allison Correia EXECUTIVE SNAPSHOT FIGURE 1 Executive Snapshot: Vendor Snapshot 2017 HP Inc. on Print and
How your network can take on the cloud and win. Think beyond traditional networking toward a secure digital perimeter
 How your network can take on the cloud and win Think beyond traditional networking toward a secure digital perimeter Contents Introduction... 3 Reduce risk points with secure, contextualized access...
How your network can take on the cloud and win Think beyond traditional networking toward a secure digital perimeter Contents Introduction... 3 Reduce risk points with secure, contextualized access...
I D C T E C H N O L O G Y S P O T L I G H T
 I D C T E C H N O L O G Y S P O T L I G H T P ow e ring Digital Transfor m a t i o n T h r ough the C l o u d - R e a d y E n t e r p rise September 2016 Adapted from Developing a Cloud Strategy for Digital
I D C T E C H N O L O G Y S P O T L I G H T P ow e ring Digital Transfor m a t i o n T h r ough the C l o u d - R e a d y E n t e r p rise September 2016 Adapted from Developing a Cloud Strategy for Digital
IDC MarketScape: Worldwide Datacenter Infrastructure Management 2015 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Datacenter Infrastructure Management 2015 Vendor Assessment Jennifer Koppy THIS IDC MARKETSCAPE EXCERPT FEATURES PANDUIT CORPORATION IDC MARKETSCAPE FIGURE FIGURE
IDC MarketScape IDC MarketScape: Worldwide Datacenter Infrastructure Management 2015 Vendor Assessment Jennifer Koppy THIS IDC MARKETSCAPE EXCERPT FEATURES PANDUIT CORPORATION IDC MARKETSCAPE FIGURE FIGURE
Cyber Group Deploys EMC ViPR for Next-Generation SaaS Application Infrastructure
 Buyer Case Study Cyber Group Deploys EMC ViPR for Next-Generation SaaS Application Infrastructure Laura DuBois IDC OPINION 3rd Platform computing has given rise to massive scale datacenters architected
Buyer Case Study Cyber Group Deploys EMC ViPR for Next-Generation SaaS Application Infrastructure Laura DuBois IDC OPINION 3rd Platform computing has given rise to massive scale datacenters architected
Assessing the Business Value of the Secured Datacenter
 IDC SOLUTION BRIEF Assessing the Business Value of the Secured Datacenter Sponsored by: Cisco Pete Lindstrom Matthew Marden December 2014 Richard L. Villars OVERVIEW The world of IT is in the midst of
IDC SOLUTION BRIEF Assessing the Business Value of the Secured Datacenter Sponsored by: Cisco Pete Lindstrom Matthew Marden December 2014 Richard L. Villars OVERVIEW The world of IT is in the midst of
Astrium Accelerates Research and Design with IHS Goldfire
 CASE STUDY Astrium Accelerates Research and Design with IHS Goldfire Sponsored by: IDC David Schubmehl Dan Vesset May 2014 IDC OPINION The challenges facing workers in most organizations today are immense.
CASE STUDY Astrium Accelerates Research and Design with IHS Goldfire Sponsored by: IDC David Schubmehl Dan Vesset May 2014 IDC OPINION The challenges facing workers in most organizations today are immense.
Oracle Autonomous Transaction Processing: Foolproofing the Database
 MARKET NOTE Oracle Autonomous Transaction Processing: Foolproofing the Database Carl W. Olofson EXECUTIVE SNAPSHOT FIGURE 1 Executive Snapshot: Oracle Autonomous Transaction Processing Announcement Source:
MARKET NOTE Oracle Autonomous Transaction Processing: Foolproofing the Database Carl W. Olofson EXECUTIVE SNAPSHOT FIGURE 1 Executive Snapshot: Oracle Autonomous Transaction Processing Announcement Source:
OpenText Magellan, Reborn Cloud, and Other Highlights from OpenText Enterprise World 2018
 IDC PERSPECTIVE OpenText Magellan, Reborn Cloud, and Other Highlights from OpenText Enterprise World 2018 Adelaide O'Brien EXECUTIVE SNAPSHOT FIGURE 1 Executive Snapshot: Highlights from OpenText Enterprise
IDC PERSPECTIVE OpenText Magellan, Reborn Cloud, and Other Highlights from OpenText Enterprise World 2018 Adelaide O'Brien EXECUTIVE SNAPSHOT FIGURE 1 Executive Snapshot: Highlights from OpenText Enterprise
Global Headquarters: 5 Speen Street Framingham, MA USA P F
 BUYER CASE STUDY INTRUST Implements F5 Networks BIG-IP Lucinda Borovick IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com One of the more
BUYER CASE STUDY INTRUST Implements F5 Networks BIG-IP Lucinda Borovick IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com One of the more
Text Messaging Helps Your Small Business Perform Big
 White Paper Text Messaging Helps Your Small Business Perform Big Sponsored by: AT&T Denise Lund August 2017 IN THIS WHITE PAPER This white paper introduces small businesses to the benefits of communicating
White Paper Text Messaging Helps Your Small Business Perform Big Sponsored by: AT&T Denise Lund August 2017 IN THIS WHITE PAPER This white paper introduces small businesses to the benefits of communicating
Acronis Backup 12.5: Transforming Data Protection with Blockchain Tech, Ransomware Protection, and Quick Insights
 MARKET NOTE Acronis Backup 12.5: Transforming Data Protection with Blockchain Tech, Ransomware Protection, and Quick Insights Archana Venkatraman EXECUTIVE SNAPSHOT FIGURE 1 Acronis Backup 12.5: Transforming
MARKET NOTE Acronis Backup 12.5: Transforming Data Protection with Blockchain Tech, Ransomware Protection, and Quick Insights Archana Venkatraman EXECUTIVE SNAPSHOT FIGURE 1 Acronis Backup 12.5: Transforming
Service Provider Consulting
 From Microsoft Services 1 Industry Overview More and more businesses are looking to outsource IT, decrease management requirements and ultimately save money. With worldwide public cloud spending expected
From Microsoft Services 1 Industry Overview More and more businesses are looking to outsource IT, decrease management requirements and ultimately save money. With worldwide public cloud spending expected
Securing Your Digital Transformation
 Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
Business Continuity & Disaster Recovery
 knowledge partner MARKET INSIGHT Business Continuity & Disaster Recovery Considerations for Saudi Organizations /mobily @MobilyBusiness 056 010 0901 I business.sales@mobily.com.sa About Us Mobily; the
knowledge partner MARKET INSIGHT Business Continuity & Disaster Recovery Considerations for Saudi Organizations /mobily @MobilyBusiness 056 010 0901 I business.sales@mobily.com.sa About Us Mobily; the
SD-WAN. Enabling the Enterprise to Overcome Barriers to Digital Transformation. An IDC InfoBrief Sponsored by Comcast
 SD-WAN Enabling the Enterprise to Overcome Barriers to Digital Transformation An IDC InfoBrief Sponsored by Comcast SD-WAN Is Emerging as an Important Driver of Business Results The increasing need for
SD-WAN Enabling the Enterprise to Overcome Barriers to Digital Transformation An IDC InfoBrief Sponsored by Comcast SD-WAN Is Emerging as an Important Driver of Business Results The increasing need for
Evolve Your Security Operations Strategy To Account For Cloud
 Evolve Your Security Operations Strategy To Account For Cloud GET STARTED The growth of cloud computing and proliferation of complex service delivery models continue to accelerate as companies recognize
Evolve Your Security Operations Strategy To Account For Cloud GET STARTED The growth of cloud computing and proliferation of complex service delivery models continue to accelerate as companies recognize
IT Consulting and Implementation Services
 PORTFOLIO OVERVIEW IT Consulting and Implementation Services Helping IT Transform the Way Business Innovates and Operates 1 2 PORTFOLIO OVERVIEW IT Consulting and Implementation Services IT is moving from
PORTFOLIO OVERVIEW IT Consulting and Implementation Services Helping IT Transform the Way Business Innovates and Operates 1 2 PORTFOLIO OVERVIEW IT Consulting and Implementation Services IT is moving from
How the WAN is Driving Digital Transformation. An IDC InfoBrief, Sponsored by
 How the WAN is Driving Digital Transformation Executive Summary Digital transformation needs to go hand in hand with an evolution of the wide area network (WAN). IDC has built a comparison framework to
How the WAN is Driving Digital Transformation Executive Summary Digital transformation needs to go hand in hand with an evolution of the wide area network (WAN). IDC has built a comparison framework to
Application Delivery Strategies for Today s Increasingly Mobile Workforce
 White Paper Application Delivery Strategies for Today s Increasingly Mobile Workforce Sponsored by: Parallels Avinash Kalyana Sundaram November 2016 IDC OPINION Organizations in Asia/Pacific are increasingly
White Paper Application Delivery Strategies for Today s Increasingly Mobile Workforce Sponsored by: Parallels Avinash Kalyana Sundaram November 2016 IDC OPINION Organizations in Asia/Pacific are increasingly
SOLUTION BRIEF RSA NETWITNESS EVOLVED SIEM
 RSA NETWITNESS EVOLVED SIEM OVERVIEW A SIEM is technology originally intended for compliance and log management. Later, as SIEMs became the aggregation points for security alerts, they began to be more
RSA NETWITNESS EVOLVED SIEM OVERVIEW A SIEM is technology originally intended for compliance and log management. Later, as SIEMs became the aggregation points for security alerts, they began to be more
Global Headquarters: 5 Speen Street Framingham, MA USA P F
 B U Y E R C A S E S T U D Y V M w a r e I m p r o v e s N e t w o r k U t i l i z a t i o n a n d B a c k u p P e r f o r m a n c e U s i n g A v a m a r ' s C l i e n t - S i d e D e d u p l i c a t i
B U Y E R C A S E S T U D Y V M w a r e I m p r o v e s N e t w o r k U t i l i z a t i o n a n d B a c k u p P e r f o r m a n c e U s i n g A v a m a r ' s C l i e n t - S i d e D e d u p l i c a t i
DIGITAL TRUST Making digital work by making digital secure
 Making digital work by making digital secure MARKET DRIVERS AND CHALLENGES THE ROLE OF IT SECURITY IN THE DIGITAL AGE 2 In today s digital age we see the impact of poor security controls everywhere. Bots
Making digital work by making digital secure MARKET DRIVERS AND CHALLENGES THE ROLE OF IT SECURITY IN THE DIGITAL AGE 2 In today s digital age we see the impact of poor security controls everywhere. Bots
Tegile Enters the All-Flash Array Market with Super Density Offering
 FLASH Tegile Enters the All-Flash Array Market with Super Density Offering Eric Burgener IN THIS FLASH This IDC Flash discusses the recent Tegile announcement, just prior to VMworld 2015 in San Francisco,
FLASH Tegile Enters the All-Flash Array Market with Super Density Offering Eric Burgener IN THIS FLASH This IDC Flash discusses the recent Tegile announcement, just prior to VMworld 2015 in San Francisco,
AKAMAI SOLUTION BROCHURE CLOUD SECURITY SOLUTIONS FAST RELIABLE SECURE.
 CLOUD SECURITY SOLUTIONS FAST RELIABLE SECURE. Threat > The number and size of cyberattacks are increasing rapidly Website availability and rapid performance are critical factors in determining the success
CLOUD SECURITY SOLUTIONS FAST RELIABLE SECURE. Threat > The number and size of cyberattacks are increasing rapidly Website availability and rapid performance are critical factors in determining the success
I D C T E C H N O L O G Y S P O T L I G H T. SD- W AN : M o m e n t u m B u i l d s as Early Ad o p t e r s
 I D C T E C H N O L O G Y S P O T L I G H T SD- W AN : M o m e n t u m B u i l d s as Early Ad o p t e r s E x p e r ience Tangible Benefits January 2018 Adapted from Worldwide SD-WAN Survey Special Report
I D C T E C H N O L O G Y S P O T L I G H T SD- W AN : M o m e n t u m B u i l d s as Early Ad o p t e r s E x p e r ience Tangible Benefits January 2018 Adapted from Worldwide SD-WAN Survey Special Report
Thin Clients as Attractive Solutions for Cost Effective, Secure Endpoint Management
 IDC Topline Sponsored by: IGEL Author: Michael Ceroici May 2018 Thin Clients as Attractive Solutions for Cost Effective, Secure Endpoint Management Situation Overview Managing IT endpoint infrastructure
IDC Topline Sponsored by: IGEL Author: Michael Ceroici May 2018 Thin Clients as Attractive Solutions for Cost Effective, Secure Endpoint Management Situation Overview Managing IT endpoint infrastructure
Server Workloads Forecasts and Analysis Study,
 EXCERPT Server Workloads Forecasts and Analysis Study, 2005-2010 Matthew Eastwood Michelle Bailey IN THIS EXCERPT Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015
EXCERPT Server Workloads Forecasts and Analysis Study, 2005-2010 Matthew Eastwood Michelle Bailey IN THIS EXCERPT Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015
MARKET PERSPECTIVE EXECUTIVE SNAPSHOT FIGURE 1
 MARKET PERSPECTIVE Commvault Launches HyperScale Software, HyperScale Appliance, and ScaleProtect with Cisco UCS to Meet Scale-Out, Software-Defined, Cloud-Ready Data Protection Needs Archana Venkatraman
MARKET PERSPECTIVE Commvault Launches HyperScale Software, HyperScale Appliance, and ScaleProtect with Cisco UCS to Meet Scale-Out, Software-Defined, Cloud-Ready Data Protection Needs Archana Venkatraman
SD-WAN: Aligning the Network with Digital Transformation, Cloud, and Customer Engagement
 White Paper SD-WAN: Aligning the Network with Digital Transformation, Cloud, and Customer Engagement Sponsored by: Windstream Brad Casemore November 2016 IDC OPINION Digital transformation is a growing,
White Paper SD-WAN: Aligning the Network with Digital Transformation, Cloud, and Customer Engagement Sponsored by: Windstream Brad Casemore November 2016 IDC OPINION Digital transformation is a growing,
TechValidate Survey Report: SaaS Application Trends and Challenges
 TechValidate Survey Report: SaaS Application Trends and Challenges TechValidate Survey Report: SaaS Application Trends and Challenges 2 The current growth rates and investments in SaaS are astounding.
TechValidate Survey Report: SaaS Application Trends and Challenges TechValidate Survey Report: SaaS Application Trends and Challenges 2 The current growth rates and investments in SaaS are astounding.
Optimisation drives digital transformation
 January 2017 Executive summary Forward-thinking business leaders are challenging their organisations to achieve transformation by harnessing digital technologies with organisational, operational, and business
January 2017 Executive summary Forward-thinking business leaders are challenging their organisations to achieve transformation by harnessing digital technologies with organisational, operational, and business
2018 Trends in Hosting & Cloud Managed Services
 PREVIEW 2018 Trends in Hosting & Cloud Managed Services DEC 2017 Rory Duncan, Research Director, Managed Services & Hosting Penny Jones, Principal Analyst - MTDC & Managed Services Aaron Sherrill, Senior
PREVIEW 2018 Trends in Hosting & Cloud Managed Services DEC 2017 Rory Duncan, Research Director, Managed Services & Hosting Penny Jones, Principal Analyst - MTDC & Managed Services Aaron Sherrill, Senior
Singtel Investor Day Bill Chang, CEO, Group Enterprise and Country Chief Officer Singapore 13 June 2018
 Singtel Investor Day 2018 Bill Chang, CEO, Group Enterprise and Country Chief Officer Singapore 13 June 2018 Singtel Group Enterprise at a glance #1 International IPVPN in APeJ #1 EVPN and Eline in APeJ
Singtel Investor Day 2018 Bill Chang, CEO, Group Enterprise and Country Chief Officer Singapore 13 June 2018 Singtel Group Enterprise at a glance #1 International IPVPN in APeJ #1 EVPN and Eline in APeJ
Cisco Preparing Its Datacenters for the Next Generation of Virtualization and Hybrid Cloud with Its Application Centric Infrastructure
 IDC BUSINESS VALUE BRIEF: CISCO ACI Cisco Preparing Its Datacenters for the Next Generation of Virtualization and Hybrid Cloud with Its Application Centric Infrastructure Sponsored by: Cisco Matthew Marden
IDC BUSINESS VALUE BRIEF: CISCO ACI Cisco Preparing Its Datacenters for the Next Generation of Virtualization and Hybrid Cloud with Its Application Centric Infrastructure Sponsored by: Cisco Matthew Marden
Best Practices in Securing a Multicloud World
 Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
Sundaram Mutual Finds a Reliable Partner in HCL Services
 Buyer Case Study Sundaram Mutual Finds a Reliable Partner in HCL Services Sachin Chaturvedi Kannagi Shekhar IDC OPINION The India mutual fund industry is transforming to keep up with a number of changes
Buyer Case Study Sundaram Mutual Finds a Reliable Partner in HCL Services Sachin Chaturvedi Kannagi Shekhar IDC OPINION The India mutual fund industry is transforming to keep up with a number of changes
DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS. Security Without Compromise
 DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS Security Without Compromise CONTENTS INTRODUCTION 1 SECTION 1: STRETCHING BEYOND STATIC SECURITY 2 SECTION 2: NEW DEFENSES FOR CLOUD ENVIRONMENTS 5 SECTION
DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS Security Without Compromise CONTENTS INTRODUCTION 1 SECTION 1: STRETCHING BEYOND STATIC SECURITY 2 SECTION 2: NEW DEFENSES FOR CLOUD ENVIRONMENTS 5 SECTION
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE
 DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
IDC FutureScape: Worldwide Security Products and Services 2017 Predictions
 IDC FutureScape: Worldwide Security Products and Services 2017 Predictions Sean Pike, Program Vice President, Robert Ayoub, Research Director IDC Web Conference December, 7, 2016 Logistics Submit any questions
IDC FutureScape: Worldwide Security Products and Services 2017 Predictions Sean Pike, Program Vice President, Robert Ayoub, Research Director IDC Web Conference December, 7, 2016 Logistics Submit any questions
ATTIVO NETWORKS THREATDEFEND INTEGRATION WITH MCAFEE SOLUTIONS
 PARTNER BRIEF ATTIVO NETWORKS THREATDEFEND INTEGRATION WITH MCAFEE SOLUTIONS INTRODUCTION Attivo Networks has partnered with McAfee to detect real-time in-network threats and to automate incident response
PARTNER BRIEF ATTIVO NETWORKS THREATDEFEND INTEGRATION WITH MCAFEE SOLUTIONS INTRODUCTION Attivo Networks has partnered with McAfee to detect real-time in-network threats and to automate incident response
Comprehensive DDoS Attack Protection: Cloud-based, Enterprise Grade Mitigation F5 Silverline
 Comprehensive DDoS Attack Protection: Cloud-based, Enterprise Grade Mitigation F5 Silverline PRESENTED BY: RICH BIBLE, EMEA SILVERLINE SA November 22, 2018 1 2018 F5 NETWORKS DDoS and Application Attack
Comprehensive DDoS Attack Protection: Cloud-based, Enterprise Grade Mitigation F5 Silverline PRESENTED BY: RICH BIBLE, EMEA SILVERLINE SA November 22, 2018 1 2018 F5 NETWORKS DDoS and Application Attack
How Managed Service Providers Can Meet Market Growth with Maximum Uptime
 How Managed Service Providers Can Meet Market Growth with Maximum Uptime The managed services provider (MSP) sector is growing rapidly. Reports estimate the market to accumulate over $240 billion by 2021,
How Managed Service Providers Can Meet Market Growth with Maximum Uptime The managed services provider (MSP) sector is growing rapidly. Reports estimate the market to accumulate over $240 billion by 2021,
Cloud Services. Infrastructure-as-a-Service
 Cloud Services Infrastructure-as-a-Service Accelerate your IT and business transformation with our networkcentric, highly secure private and public cloud services - all backed-up by a 99.999% availability
Cloud Services Infrastructure-as-a-Service Accelerate your IT and business transformation with our networkcentric, highly secure private and public cloud services - all backed-up by a 99.999% availability
Hybrid WAN Operations: Extend Network Monitoring Across SD-WAN and Legacy WAN Infrastructure
 Hybrid WAN Operations: Extend Network Monitoring Across SD-WAN and Legacy WAN Infrastructure An ENTERPRISE MANAGEMENT ASSOCIATES (EMA ) White Paper Prepared for SevOne May 2017 IT & DATA MANAGEMENT RESEARCH,
Hybrid WAN Operations: Extend Network Monitoring Across SD-WAN and Legacy WAN Infrastructure An ENTERPRISE MANAGEMENT ASSOCIATES (EMA ) White Paper Prepared for SevOne May 2017 IT & DATA MANAGEMENT RESEARCH,
SECURITY SERVICES SECURITY
 SECURITY SERVICES SECURITY SOLUTION SUMMARY Computacenter helps organisations safeguard data, simplify compliance and enable users with holistic security solutions With users, data and devices dispersed
SECURITY SERVICES SECURITY SOLUTION SUMMARY Computacenter helps organisations safeguard data, simplify compliance and enable users with holistic security solutions With users, data and devices dispersed
The New Enterprise Network In The Era Of The Cloud. Rohit Mehra Director, Enterprise Communications Infrastructure IDC
 The New Enterprise Network In The Era Of The Cloud Rohit Mehra Director, Enterprise Communications Infrastructure IDC Agenda 1. Dynamics of the Cloud Era 2. Market Landscape 3. Implications for the new
The New Enterprise Network In The Era Of The Cloud Rohit Mehra Director, Enterprise Communications Infrastructure IDC Agenda 1. Dynamics of the Cloud Era 2. Market Landscape 3. Implications for the new
I D C T E C H N O L O G Y S P O T L I G H T. S e r ve r S e c u rity: V i r t u a l ization and Cloud C h a n g e s E ve r yt h i n g
 I D C T E C H N O L O G Y S P O T L I G H T S e r ve r S e c u rity: V i r t u a l ization and Cloud C h a n g e s E ve r yt h i n g January 2016 Adapted from Worldwide Endpoint Security Market Share,
I D C T E C H N O L O G Y S P O T L I G H T S e r ve r S e c u rity: V i r t u a l ization and Cloud C h a n g e s E ve r yt h i n g January 2016 Adapted from Worldwide Endpoint Security Market Share,
Security-as-a-Service: The Future of Security Management
 Security-as-a-Service: The Future of Security Management EVERY SINGLE ATTACK THAT AN ORGANISATION EXPERIENCES IS EITHER ON AN ENDPOINT OR HEADING THERE 65% of CEOs say their risk management approach is
Security-as-a-Service: The Future of Security Management EVERY SINGLE ATTACK THAT AN ORGANISATION EXPERIENCES IS EITHER ON AN ENDPOINT OR HEADING THERE 65% of CEOs say their risk management approach is
Service. Sentry Cyber Security Gain protection against sophisticated and persistent security threats through our layered cyber defense solution
 Service SM Sentry Cyber Security Gain protection against sophisticated and persistent security threats through our layered cyber defense solution Product Protecting sensitive data is critical to being
Service SM Sentry Cyber Security Gain protection against sophisticated and persistent security threats through our layered cyber defense solution Product Protecting sensitive data is critical to being
Paper. Delivering Strong Security in a Hyperconverged Data Center Environment
 Paper Delivering Strong Security in a Hyperconverged Data Center Environment Introduction A new trend is emerging in data center technology that could dramatically change the way enterprises manage and
Paper Delivering Strong Security in a Hyperconverged Data Center Environment Introduction A new trend is emerging in data center technology that could dramatically change the way enterprises manage and
Analytics-as-a-Service Firm Chooses Cisco Hyperconverged Infrastructure as a More Cost-Effective Agile Development Platform Compared with Public Cloud
 IDC ExpertROI SPOTLIGHT Analytics-as-a-Service Firm Chooses Cisco Hyperconverged Infrastructure as a More Cost-Effective Agile Development Platform Compared with Public Cloud Sponsored by: Cisco Matthew
IDC ExpertROI SPOTLIGHT Analytics-as-a-Service Firm Chooses Cisco Hyperconverged Infrastructure as a More Cost-Effective Agile Development Platform Compared with Public Cloud Sponsored by: Cisco Matthew
Supporting the Cloud Transformation of Agencies across the Public Sector
 SOLUTION SERVICES Supporting the Cloud Transformation of Agencies across the Public Sector BRIEF Digital transformation, aging IT infrastructure, the Modernizing Government Technology (MGT) Act, the Datacenter
SOLUTION SERVICES Supporting the Cloud Transformation of Agencies across the Public Sector BRIEF Digital transformation, aging IT infrastructure, the Modernizing Government Technology (MGT) Act, the Datacenter
I D C T E C H N O L O G Y S P O T L I G H T
 I D C T E C H N O L O G Y S P O T L I G H T Ad va n c e d P e r s i s tent Threats: Movi n g f r o m D e t e c t i o n t o Preve n t i o n a n d R e s p o n s e October 2015 Adapted from Worldwide Specialized
I D C T E C H N O L O G Y S P O T L I G H T Ad va n c e d P e r s i s tent Threats: Movi n g f r o m D e t e c t i o n t o Preve n t i o n a n d R e s p o n s e October 2015 Adapted from Worldwide Specialized
National Bank Minimizes Security Risk and Supports New Business with McAfee Security Solutions
 IDC ExpertROI SPOTLIGHT National Bank Minimizes Security Risk and Supports New Business with McAfee Security Solutions Sponsored by: McAfee Matthew Marden February 2017 Overview Robert Ayoub As cyberattacks
IDC ExpertROI SPOTLIGHT National Bank Minimizes Security Risk and Supports New Business with McAfee Security Solutions Sponsored by: McAfee Matthew Marden February 2017 Overview Robert Ayoub As cyberattacks
AKAMAI WHITE PAPER. Enterprise Application Access Architecture Overview
 AKAMAI WHITE PAPER Enterprise Application Access Architecture Overview Enterprise Application Access Architecture Overview 1 Providing secure remote access is a core requirement for all businesses. Though
AKAMAI WHITE PAPER Enterprise Application Access Architecture Overview Enterprise Application Access Architecture Overview 1 Providing secure remote access is a core requirement for all businesses. Though
Gain Control Over Your Cloud Use with Cisco Cloud Consumption Professional Services
 Solution Overview Gain Control Over Your Cloud Use with Cisco Cloud Consumption Professional Services OPTIMIZE YOUR CLOUD SERVICES TO DRIVE BETTER BUSINESS OUTCOMES Reduce Cloud Business Risks and Costs
Solution Overview Gain Control Over Your Cloud Use with Cisco Cloud Consumption Professional Services OPTIMIZE YOUR CLOUD SERVICES TO DRIVE BETTER BUSINESS OUTCOMES Reduce Cloud Business Risks and Costs
REALIZE YOUR. DIGITAL VISION with Digital Private Cloud from Atos and VMware
 REALIZE YOUR DIGITAL VISION with Digital Private Cloud from Atos and VMware Today s critical business challenges and their IT impact Business challenges Maximizing agility to accelerate time to market
REALIZE YOUR DIGITAL VISION with Digital Private Cloud from Atos and VMware Today s critical business challenges and their IT impact Business challenges Maximizing agility to accelerate time to market
Cloud Computing: Making the Right Choice for Your Organization
 Cloud Computing: Making the Right Choice for Your Organization A decade ago, cloud computing was on the leading edge. Now, 95 percent of businesses use cloud technology, and Gartner says that by 2020,
Cloud Computing: Making the Right Choice for Your Organization A decade ago, cloud computing was on the leading edge. Now, 95 percent of businesses use cloud technology, and Gartner says that by 2020,
Capgemini Dynamic Services
 Capgemini Dynamic Services Evolution and dynamics of Copyright Capgemini 2015. All Rights Reserved 2 GEN 1 Simple IT GEN 2 Full Outsourcing GEN 3 Tower Sourcing GEN NEXT Micro Sourcing Business IT Interface
Capgemini Dynamic Services Evolution and dynamics of Copyright Capgemini 2015. All Rights Reserved 2 GEN 1 Simple IT GEN 2 Full Outsourcing GEN 3 Tower Sourcing GEN NEXT Micro Sourcing Business IT Interface
Flexible Network-Based, Enterprise-Class Software-Defined Solutions for Hybrid Public/Private Network Connectivity
 White Paper Flexible Network-Based, Enterprise-Class Software-Defined Solutions for Hybrid Public/Private Network Connectivity Sponsored by: Courtney Munroe June 2018 EXECUTIVE SUMMARY Today's enterprise
White Paper Flexible Network-Based, Enterprise-Class Software-Defined Solutions for Hybrid Public/Private Network Connectivity Sponsored by: Courtney Munroe June 2018 EXECUTIVE SUMMARY Today's enterprise
SOLUTION BRIEF RSA NETWITNESS SUITE 3X THE IMPACT WITH YOUR EXISTING SECURITY TEAM
 SOLUTION BRIEF RSA NETWITNESS SUITE 3X THE IMPACT WITH YOUR EXISTING SECURITY TEAM OVERVIEW The Verizon 2016 Data Breach Investigations Report highlights that attackers are regularly outpacing the defenders.
SOLUTION BRIEF RSA NETWITNESS SUITE 3X THE IMPACT WITH YOUR EXISTING SECURITY TEAM OVERVIEW The Verizon 2016 Data Breach Investigations Report highlights that attackers are regularly outpacing the defenders.
MAKING THE CLOUD A SECURE EXTENSION OF YOUR DATACENTER
 MAKING THE CLOUD A SECURE EXTENSION OF YOUR DATACENTER Bret Hartman Cisco / Security & Government Group Session ID: SPO1-W25 Session Classification: General Interest 1 Mobility Cloud Threat Customer centric
MAKING THE CLOUD A SECURE EXTENSION OF YOUR DATACENTER Bret Hartman Cisco / Security & Government Group Session ID: SPO1-W25 Session Classification: General Interest 1 Mobility Cloud Threat Customer centric
Making hybrid IT simple with Capgemini and Microsoft Azure Stack
 Making hybrid IT simple with Capgemini and Microsoft Azure Stack The significant evolution of cloud computing in the last few years has encouraged IT leaders to rethink their enterprise cloud strategy.
Making hybrid IT simple with Capgemini and Microsoft Azure Stack The significant evolution of cloud computing in the last few years has encouraged IT leaders to rethink their enterprise cloud strategy.
Cloud Computing. January 2012 CONTENT COMMUNITY CONVERSATION CONVERSION
 Cloud Computing January 2012 CONTENT COMMUNITY CONVERSATION CONVERSION Purpose and Methodology Survey Sample Field Work December 20, 2011 January 9, 2012 Total Respondents 554 Margin of Error +/- 4.2%
Cloud Computing January 2012 CONTENT COMMUNITY CONVERSATION CONVERSION Purpose and Methodology Survey Sample Field Work December 20, 2011 January 9, 2012 Total Respondents 554 Margin of Error +/- 4.2%
IBM Cloud for VMware Solutions: Bringing VMware Environments to the Public Cloud
 White Paper IBM Cloud for VMware Solutions: Bringing VMware Environments to the Public Cloud Sponsored by: IBM Deepak Mohan August 2018 IDC OPINION Public cloud adoption is an enabler for digital transformation
White Paper IBM Cloud for VMware Solutions: Bringing VMware Environments to the Public Cloud Sponsored by: IBM Deepak Mohan August 2018 IDC OPINION Public cloud adoption is an enabler for digital transformation
Cisco Start. IT solutions designed to propel your business
 Cisco Start IT solutions designed to propel your business Small and medium-sized businesses (SMBs) typically have very limited resources to invest in new technologies. With every IT investment made, they
Cisco Start IT solutions designed to propel your business Small and medium-sized businesses (SMBs) typically have very limited resources to invest in new technologies. With every IT investment made, they
Run the business. Not the risks.
 Run the business. Not the risks. RISK-RESILIENCE FOR THE DIGITAL BUSINESS Cyber-attacks are a known risk to business. Today, with enterprises becoming pervasively digital, these risks have grown multifold.
Run the business. Not the risks. RISK-RESILIENCE FOR THE DIGITAL BUSINESS Cyber-attacks are a known risk to business. Today, with enterprises becoming pervasively digital, these risks have grown multifold.
Vendor: Cisco. Exam Code: Exam Name: Cisco Sales Expert. Version: Demo
 Vendor: Cisco Exam Code: 646-206 Exam Name: Cisco Sales Expert Version: Demo QUESTION 1 What are three current business factors that are influencing customer decisions in making technology investments?
Vendor: Cisco Exam Code: 646-206 Exam Name: Cisco Sales Expert Version: Demo QUESTION 1 What are three current business factors that are influencing customer decisions in making technology investments?
Unified Communications from West
 Unified Communications from West We Connect. We Deliver. Transforming the way your business works & improving its performance Delivering world-class service Uniting and deploying business technologies
Unified Communications from West We Connect. We Deliver. Transforming the way your business works & improving its performance Delivering world-class service Uniting and deploying business technologies
Datacenters: The Heart of the Digital Economy
 Technology Spotlight Datacenters: The Heart of the Digital Economy Sponsored by: Cogeco Peer 1 Mark Schrutt November 2016 David Senf TECHNOLOGY IS A KEY COMPETITIVE DIFFERENTIATOR The Trade Desk is in
Technology Spotlight Datacenters: The Heart of the Digital Economy Sponsored by: Cogeco Peer 1 Mark Schrutt November 2016 David Senf TECHNOLOGY IS A KEY COMPETITIVE DIFFERENTIATOR The Trade Desk is in
MATURE YOUR CYBER DEFENSE OPERATIONS with Accenture s SIEM Transformation Services
 MATURE YOUR CYBER DEFENSE OPERATIONS with Accenture s SIEM Transformation Services THE NEED FOR MATURE CYBER DEFENSE CAPABILITIES The average annual cost of cyber crime reached $11.7 million per organization
MATURE YOUR CYBER DEFENSE OPERATIONS with Accenture s SIEM Transformation Services THE NEED FOR MATURE CYBER DEFENSE CAPABILITIES The average annual cost of cyber crime reached $11.7 million per organization
I D C T E C H N O L O G Y S P O T L I G H T. SD- W AN : A C r i t i c al S t e p in Transforming the N e tw o r k for the Cloud Era
 I D C T E C H N O L O G Y S P O T L I G H T SD- W AN : A C r i t i c al S t e p in Transforming the N e tw o r k for the Cloud Era April 2017 Sponsored by GTT As the cloud era prevails in enterprise application
I D C T E C H N O L O G Y S P O T L I G H T SD- W AN : A C r i t i c al S t e p in Transforming the N e tw o r k for the Cloud Era April 2017 Sponsored by GTT As the cloud era prevails in enterprise application
Cisco Cloud Security. How to Protect Business to Support Digital Transformation
 Cisco Cloud Security How to Protect Business to Support Digital Transformation Dragan Novakovic Cybersecurity Consulting Systems Engineer January 2018. Security Enables Digitization Digital Disruption,
Cisco Cloud Security How to Protect Business to Support Digital Transformation Dragan Novakovic Cybersecurity Consulting Systems Engineer January 2018. Security Enables Digitization Digital Disruption,
NFV and SDN what does it mean to enterprises?
 OPINION NFV and SDN what does it mean to enterprises? By Clive Hamilton, VP Network Services, NTT Europe Rethinking the enterprise network The typical enterprise network now comprises hundreds or even
OPINION NFV and SDN what does it mean to enterprises? By Clive Hamilton, VP Network Services, NTT Europe Rethinking the enterprise network The typical enterprise network now comprises hundreds or even
TRUE SECURITY-AS-A-SERVICE
 TRUE SECURITY-AS-A-SERVICE To effectively defend against today s cybercriminals, organizations must look at ways to expand their ability to secure and maintain compliance across their evolving IT infrastructure.
TRUE SECURITY-AS-A-SERVICE To effectively defend against today s cybercriminals, organizations must look at ways to expand their ability to secure and maintain compliance across their evolving IT infrastructure.
Three Key Challenges Facing ISPs and Their Enterprise Clients
 Three Key Challenges Facing ISPs and Their Enterprise Clients GRC, enterprise services, and ever-evolving hybrid infrastructures are all dynamic and significant challenges to the ISP s enterprise clients.
Three Key Challenges Facing ISPs and Their Enterprise Clients GRC, enterprise services, and ever-evolving hybrid infrastructures are all dynamic and significant challenges to the ISP s enterprise clients.
