Clustering Techniques A Technical Whitepaper By Lorinda Visnick
|
|
|
- Dana Rose
- 6 years ago
- Views:
Transcription
1 Clustering Techniques A Technical Whitepaper By Lorinda Visnick 14 Oak Park Bedford, MA USA Phone:
2 Introduction Performance of a database can be greatly impacted by the manner in which data is loaded. This fact is true regardless of when the data is loaded; whether loaded before the application(s) begin accessing the data, or concurrently while the application(s) are accessing the data. This paper will present various strategies for locating data as it is loaded into the database and detail the performance implications of those strategies. Data Clustering, Working Sets, and Performance With ObjectStore access to persistent data can perform at in-memory speeds. In order to achieve inmemory speeds, one needs cache affinity. Cache affinity is the generic term that describes the degree to which data accessed within a program overlaps with data already retrieved on behalf of a previous request. Effective data clustering allows for better, if not optimal, cache affinity. Data density is defined as the proportion of objects within a given storage block that are accessed by a client during some scope of activation. Clustering is a technique to achieve high data density. The working set is defined as the set of database pages a client needs at a given time. ObjectStore is a pagebased architecture (see the ObjectStore Architecture Introductory technical paper at for a detailed review of the ObjectStore architecture) which performs best when the following goals are met: Minimize the number of pages transferred between the client and server Maximize the use of pages already in the cache In order to achieve these goals, the working set of the application should be optimal. The way to achieve an optimal working set is via data clustering. With good data clustering more data can be accessed in fewer pages; thus a high data density rate is obtained. A higher data density results in a smaller working set as well as a better chance of cache affinity. A smaller working set results in fewer page transfers. The following sections in this paper will explain several clustering patterns/techniques for achieving better performance via cache affinity, higher data density and a smaller working set. NOTE: clustering is used in this paper as a concept of locality of reference. The term is not being used to refer to the physical storage unit available in ObjectStore. ObjectStore does present the user with a choice for location of allocations: with the database, within a particular segment, within a particular cluster. For the remainder of this paper, the discussion of cluster is a conceptual one, not the ObjectStore physical one. Database Design Process Database design is one of the most important steps in designing and implementing an ObjectStore application. The following steps are pre-requisites for a database design: 1) Identify key use cases (ones which need to be fast and/or are run frequently) 2) Identify the object(s) used by the use cases called out in step 1 3) Identify the object(s) that are read or updated during the use cases called out in step 1 The focus of clustering efforts should be on the database objects which are used in the high priority use cases identified above. Begin to cluster based on one use case, and then validate with others. Copyright Progress Software Corporation. All rights reserved. Page 2 of 8
3 The database design strategies which lend themselves to achieving the optimal working set are: Clustering Partitioning There are several different types of techniques which result in data being well clustered: Isolate Index Pooling Object Modeling We will examine each of these in detail. Data Clustering Earlier in this paper we defined clustering as a technique to achieve high data density. Another definition of clustering is a grouping of objects together. If a use case requires objects A, B and C to operate, then those objects should be co-located for optimal data density. If upon loading the database, those objects are physically allocated close to one another, then we say we have clustered those objects. Assume that the size of the three objects combined is less than the size of a physical database page. The clustering leads to high data density because when we fetch the page with object A, we will also get objects B and C. In this particular case, we need just one page transfer to get all objects required for our use case. To accomplish good clustering, one must know the use cases and the objects involved in those use cases. Given that knowledge, the goals of clustering are: Cluster objects together which are accessed together Separate (de-cluster, or partition we will discuss partitioning in detail later in this paper) objects which are never accessed together. This includes separating frequently accessed data from rarely accessed data. Note: A change of object model may be required to accomplish the clustering goals. To that end, we will examine some object model change techniques as part of our discussion. Clustering Techniques: Isolate Index An index on a collection yields faster query performance. If the index is placed, as it is by default, in the same physical location as the collection itself and the items in the collection, then poor locality of reference for the index items is likely to occur. Restated, all the items which are related to the index should be placed in close proximity to one another. All items related to the collection (excluding the index) should be placed in close proximity to one another. The index items should not be interspersed with the collection nor the items contained within the collection. Therefore, if we cluster the index and all the index items together in an area that is physically distinct from the collection and/or the items in the collection, the index will be faster to fetch. If there are no non-index items interspersed with the index items, then fewer pages will be required to fetch the index to perform a query or update the index. Another side benefit of clustering index items in an isolated area is less fragmentation. Why? If the index were interspersed with the collection and items in the collection and then the index were dropped (most likely so that it could be regenerated) the physical locale where the index items had been would be fragmented. Fragmentation lowers data density. By definition, if you fetch a page and some space on that page is empty due to fragmentation, then you have lower data density. Copyright Progress Software Corporation. All rights reserved. Page 3 of 8
4 Clustering Techniques: Object Pooling Object pooling is a type of clustering that puts all instances of a certain type into one physical location. Imagine a scenario were an application expected to have 100 bank objects. An array, or pool, of 100 objects would be allocated at system startup. As bank objects were needed, a slot in the pool would be assigned for use by that particular bank. As banks are deleted, the slot is marked as available for reuse. This technique gives continuous storage for all objects of the type in the pool. Because deleted slots are reused, fragmentation is less likely. The lower fragmentation in combination with contiguous space leads to higher data density. Clustering Techniques: Object Modeling Object modeling is a technique that involves changes to the object model. In this category, we have four distinct methods: Head Body Split Data Member Ordering Collection Representations Virtual Keyword Let us examine each of these in detail. Head Body Split Recall that in clustering not only do we want to put data together which is accessed together, but we want to separate data that is not accessed together. Some objects have atttributes which are key and other attributes which are rarely accessed. Such objects are candidates for the technique called Head Body Split. Consider a person object with all the following attributes: First name Last name Social security number Gender Eye color Hair color Height Weight Home address Home phone Cell phone Employer Work phone Work address For most applications the only data that would be accessed from such a person object would be first name, last name and social security number. If all data were stored together, each person would consume a considerable amount of space. Then, a fetch of a database page would yield fewer people. Remember, one goal is fewer page transfers. Therefore, a larger person object is not desirable. However, a person is what it is all data is needed at some time. This is a perfect situation for the head/body split. In the head portion the items that are frequently accessed are placed: first name, last name, social security number. The remainder of the attributes are placed in the body. The head has a pointer to the body. The heads are physically allocated in close proximity to one another; therefore a page fetch returns many heads. The bodies are allocated in a location physically apart from the heads. The end result is higher data density, fewer page transfers, and thus a performance gain. Copyright Progress Software Corporation. All rights reserved. Page 4 of 8
5 Strings Strings often represent a large percentage of a database. Therefore, an effective representation of strings can greatly reduce the database size. Smaller database size, fewer page transfers required to fetch data of interest. In addition to a smaller database size, some representations allow for fewer physical allocations. If allocations are reduced, then there is less overhead for the API calls for those allocations. In addition, an embedded string (one in which no separate allocation was required) has locality of reference to the parent object in which it resides. By definition, an embedded string is clustered with its parent object. Depending on the use cases for an application, it may be desirable to have embedded strings (clustered) or it may be desirable to have the strings allocated separately and placed in a different physical location (as with the head/body split). In general, strings can fit into one of three categories: Variable-length String Fixed-length String Symbol table Variable length strings are often represented via a char *. As mentioned above, this will cause an additional allocation to occur for space to be assigned to the string. If you wish for locality of reference, then you must take special care to allocate the new string in close proximity with the rest of the object. By default, one is not guaranteed locality of reference when a separate allocation is performed. If using a third party package such as Rogue Wave (RW) or some other STL implementation, be aware that variable length strings often have a large amount of overhead associated with them. Larger objects mean fewer objects per page, which means more page transfers. In the case of RW, a variable length string has at least 24 bytes of overhead associated with it. Therefore, one should not consider using such an implementation thinking that they are saving space. Fixed length strings can and should be used when locality of reference is desired. As mentioned above, an embedded string (char []) reduces the number of allocations and is guaranteed to be co-located with the rest of the object. If the fixed length string is large (for instance, the text of a paragraph or the list of ingredients on a label) then one might choose to use a char * representation (even though the string is of fixed length) instead of embedded string to achieve a head/body type of split. A symbol table is basically a reference table of strings. There is only one copy of each string that exists in the table in the entire database. This is useful for strings which are very common in the database. An example might be the names of the states, or zip codes. One important note about symbol tables is that it can be a concurrency bottleneck if some use cases are attempting to reference data in the table while other use cases are attempting to update the table. This bottleneck can be overcome by pre-creating the symbol table. Populate it with the data before the use cases begin to access it. Copyright Progress Software Corporation. All rights reserved. Page 5 of 8
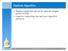
6 Data Member Ordering Different compilers have different object layout and alignment techniques. Some require that integers be 4 byte aligned, or that longs be 8 byte aligned. Because of these alignment regulations, a persistent object may have padding inserted between data members. This padding is wasted space. Consider the following object on a Tru64 platform: class example_part { private: char[2] small_string ; int my_int ; char[2] another_string ; long my_long ; }; Here is a pictorial representation of the above: The above class would be size 24 bytes on a Tru64 platform due to compiler alignment rules. The second data member, my_int could not be physically placed immediately after the first data member. Rather, the integer must be 4 byte aligned. Therefore, two bytes of space will exist between the first data member and the second. The long data type must be 8 byte aligned; therefore six bytes of space are wasted padding between the third data member and the fourth. A simple reordering of the class members can result in no space being wasted due to compiler alignment/padding. Here is the class reordered with no wasted space: Copyright Progress Software Corporation. All rights reserved. Page 6 of 8
7 class example_part { private: char[2] small_string ; char[2] another_string ; int my_int ; long my_long ; }; Again, wasted space due to padding from compiler alignment rules means larger objects. Larger objects mean fewer objects fit per physical page. Fewer objects per page means more page transfers which results in poorer performance. In the example above, we decreased our object from size 24 bytes to 16 bytes. Although 8 bytes may not seem like a lot, if you have thousands of instances of these objects, the overall savings will be great. Collection Representations If an application makes use of a large number of collections, then the collections themselves could account for a significant portion of the size of the database and/or the performance of the database application. Therefore, the choice of an appropriate collection representation is of utmost importance. For example, if a collection is being used to hold a class extent and it always has an index, then one should use an index only collection. If there is one primary key that is always queried, a dictionary (rather than a collection ) would provide for faster lookups. As mentioned before, if an index exists for a collection, isolation of that index will most likely help to improve performance. Virtual keyword If a database contains numerous small objects those objects should avoid having virtual functions if at all possible. The existence of a virtual function causes a class to have a virtual function table (vtbl) pointer. The additional pointer will increase the size of the object. Depending on how small the object was to start with, the addition of the vtbl pointer might add significant overhead to the database. Any derived classes will also incur the overhead of the vtbl pointer. Again, larger objects result in fewer objects per page. Fewer objects per page means more page transfers. More page transfers means more time for an application to execute. Therefore, use virtual functions only when necessary. Copyright Progress Software Corporation. All rights reserved. Page 7 of 8
8 Partitioning Partitioning is a strategy to isolate subsets of objects in different physical storage units. By definition, if two objects are in different partitions, they are de-clustered. The two goals of partitioning are to gain isolation and to increase data density. Isolation is desirable when concurrent access is required. The scope of this paper is not intended to cover concurrency. For that reason our discussion of partitioning will be rather brief. Although partitioning is intended for isolating objects, its use can improve data density. This may seem, by definition, to be counter intuitive. Let us use an example to illustrate. Imagine a grocery store. If you were in need of a box of cereal, you would go down the cereal aisle. If the grocer has done his job correctly, the aisle (or some number of shelves in the aisle) will be populated ONLY with boxes of cereal. Because other items have been located in their respective aisles/shelves, the entire cereal aisle is dense with cereal. If the grocer had not done the job correctly, a given section of a shelf might have (for instance) boxes of noodles, cans of vegetables, and bags of chips. In this scenario, the shelf does not have good data density for the goal of obtaining a box of cereal. Recall the definition of data density: the proportion of objects within a given storage block that are accessed by a client during some scope. Our scope is to obtain a box of cereal. Our storage block is the aisle or a shelf. If the shelf in question contains many items other than cereal, then we have poor data density. If, on the other hand, we partition the non-cereal items to be in different aisles, then the cereal aisle would contain only cereal and thus a high data density would be achieved. In the case of ObjectStore, a common area where partitioning can be used is with collections. The collection head can be placed in one physical location; the index in a separate physical location and the items themselves in a third separate location. Conclusion The way in which data is loaded into the database can have significant impact on the performance of an application. Careful analysis of the use cases for an application should allow key objects to be identified. Once key objects are identified, a clustering strategy can be planned. Several of the techniques presented here can allow for a clustering strategy that will boost performance far beyond any tuning that might be done after the database is loaded and the application delivered. It is often the case that several techniques can be combined; an application need not restrict itself to the use of just one technique. The goal of clustering is to reduce your working set size; yield higher data density; and reduce the number of pages which need to be transferred between the application and the ObjectStore server. ObjectStore is a registered trademark of Progress Software Corporation in the U.S. and other countries. Java and all Java-based marks are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. Any other trademarks or service marks contained herein are the property of their respective owners Copyright Progress Software Corporation. All rights reserved. Page 8 of 8
Heap Management portion of the store lives indefinitely until the program explicitly deletes it C++ and Java new Such objects are stored on a heap
 Heap Management The heap is the portion of the store that is used for data that lives indefinitely, or until the program explicitly deletes it. While local variables typically become inaccessible when
Heap Management The heap is the portion of the store that is used for data that lives indefinitely, or until the program explicitly deletes it. While local variables typically become inaccessible when
Practice Exercises 449
 Practice Exercises 449 Kernel processes typically require memory to be allocated using pages that are physically contiguous. The buddy system allocates memory to kernel processes in units sized according
Practice Exercises 449 Kernel processes typically require memory to be allocated using pages that are physically contiguous. The buddy system allocates memory to kernel processes in units sized according
Hashing. Hashing Procedures
 Hashing Hashing Procedures Let us denote the set of all possible key values (i.e., the universe of keys) used in a dictionary application by U. Suppose an application requires a dictionary in which elements
Hashing Hashing Procedures Let us denote the set of all possible key values (i.e., the universe of keys) used in a dictionary application by U. Suppose an application requires a dictionary in which elements
FILE SYSTEMS. CS124 Operating Systems Winter , Lecture 23
 FILE SYSTEMS CS124 Operating Systems Winter 2015-2016, Lecture 23 2 Persistent Storage All programs require some form of persistent storage that lasts beyond the lifetime of an individual process Most
FILE SYSTEMS CS124 Operating Systems Winter 2015-2016, Lecture 23 2 Persistent Storage All programs require some form of persistent storage that lasts beyond the lifetime of an individual process Most
Virtual Memory. CSCI 315 Operating Systems Design Department of Computer Science
 Virtual Memory CSCI 315 Operating Systems Design Department of Computer Science Notice: The slides for this lecture have been largely based on those from an earlier edition of the course text Operating
Virtual Memory CSCI 315 Operating Systems Design Department of Computer Science Notice: The slides for this lecture have been largely based on those from an earlier edition of the course text Operating
Advanced Programming & C++ Language
 Advanced Programming & C++ Language ~6~ Introduction to Memory Management Ariel University 2018 Dr. Miri (Kopel) Ben-Nissan Stack & Heap 2 The memory a program uses is typically divided into four different
Advanced Programming & C++ Language ~6~ Introduction to Memory Management Ariel University 2018 Dr. Miri (Kopel) Ben-Nissan Stack & Heap 2 The memory a program uses is typically divided into four different
Chapter 5 Hashing. Introduction. Hashing. Hashing Functions. hashing performs basic operations, such as insertion,
 Introduction Chapter 5 Hashing hashing performs basic operations, such as insertion, deletion, and finds in average time 2 Hashing a hash table is merely an of some fixed size hashing converts into locations
Introduction Chapter 5 Hashing hashing performs basic operations, such as insertion, deletion, and finds in average time 2 Hashing a hash table is merely an of some fixed size hashing converts into locations
CS370 Operating Systems
 CS370 Operating Systems Colorado State University Yashwant K Malaiya Fall 2017 Lecture 23 Virtual memory Slides based on Text by Silberschatz, Galvin, Gagne Various sources 1 1 FAQ Is a page replaces when
CS370 Operating Systems Colorado State University Yashwant K Malaiya Fall 2017 Lecture 23 Virtual memory Slides based on Text by Silberschatz, Galvin, Gagne Various sources 1 1 FAQ Is a page replaces when
Memory Management. To improve CPU utilization in a multiprogramming environment we need multiple programs in main memory at the same time.
 Memory Management To improve CPU utilization in a multiprogramming environment we need multiple programs in main memory at the same time. Basic CPUs and Physical Memory CPU cache Physical memory
Memory Management To improve CPU utilization in a multiprogramming environment we need multiple programs in main memory at the same time. Basic CPUs and Physical Memory CPU cache Physical memory
Chapter 8 Virtual Memory
 Operating Systems: Internals and Design Principles Chapter 8 Virtual Memory Seventh Edition William Stallings Modified by Rana Forsati for CSE 410 Outline Principle of locality Paging - Effect of page
Operating Systems: Internals and Design Principles Chapter 8 Virtual Memory Seventh Edition William Stallings Modified by Rana Forsati for CSE 410 Outline Principle of locality Paging - Effect of page
Chapter 8 Virtual Memory
 Operating Systems: Internals and Design Principles Chapter 8 Virtual Memory Seventh Edition William Stallings Operating Systems: Internals and Design Principles You re gonna need a bigger boat. Steven
Operating Systems: Internals and Design Principles Chapter 8 Virtual Memory Seventh Edition William Stallings Operating Systems: Internals and Design Principles You re gonna need a bigger boat. Steven
Objectives and Functions Convenience. William Stallings Computer Organization and Architecture 7 th Edition. Efficiency
 William Stallings Computer Organization and Architecture 7 th Edition Chapter 8 Operating System Support Objectives and Functions Convenience Making the computer easier to use Efficiency Allowing better
William Stallings Computer Organization and Architecture 7 th Edition Chapter 8 Operating System Support Objectives and Functions Convenience Making the computer easier to use Efficiency Allowing better
Virtual Memory COMPSCI 386
 Virtual Memory COMPSCI 386 Motivation An instruction to be executed must be in physical memory, but there may not be enough space for all ready processes. Typically the entire program is not needed. Exception
Virtual Memory COMPSCI 386 Motivation An instruction to be executed must be in physical memory, but there may not be enough space for all ready processes. Typically the entire program is not needed. Exception
Operating System Support
 Operating System Support Objectives and Functions Convenience Making the computer easier to use Efficiency Allowing better use of computer resources Layers and Views of a Computer System Operating System
Operating System Support Objectives and Functions Convenience Making the computer easier to use Efficiency Allowing better use of computer resources Layers and Views of a Computer System Operating System
Caches Concepts Review
 Caches Concepts Review What is a block address? Why not bring just what is needed by the processor? What is a set associative cache? Write-through? Write-back? Then we ll see: Block allocation policy on
Caches Concepts Review What is a block address? Why not bring just what is needed by the processor? What is a set associative cache? Write-through? Write-back? Then we ll see: Block allocation policy on
Introduction. hashing performs basic operations, such as insertion, better than other ADTs we ve seen so far
 Chapter 5 Hashing 2 Introduction hashing performs basic operations, such as insertion, deletion, and finds in average time better than other ADTs we ve seen so far 3 Hashing a hash table is merely an hashing
Chapter 5 Hashing 2 Introduction hashing performs basic operations, such as insertion, deletion, and finds in average time better than other ADTs we ve seen so far 3 Hashing a hash table is merely an hashing
FILE SYSTEMS, PART 2. CS124 Operating Systems Fall , Lecture 24
 FILE SYSTEMS, PART 2 CS124 Operating Systems Fall 2017-2018, Lecture 24 2 Last Time: File Systems Introduced the concept of file systems Explored several ways of managing the contents of files Contiguous
FILE SYSTEMS, PART 2 CS124 Operating Systems Fall 2017-2018, Lecture 24 2 Last Time: File Systems Introduced the concept of file systems Explored several ways of managing the contents of files Contiguous
Operating System Concepts
 Chapter 9: Virtual-Memory Management 9.1 Silberschatz, Galvin and Gagne 2005 Chapter 9: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped
Chapter 9: Virtual-Memory Management 9.1 Silberschatz, Galvin and Gagne 2005 Chapter 9: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped
File System Interface and Implementation
 Unit 8 Structure 8.1 Introduction Objectives 8.2 Concept of a File Attributes of a File Operations on Files Types of Files Structure of File 8.3 File Access Methods Sequential Access Direct Access Indexed
Unit 8 Structure 8.1 Introduction Objectives 8.2 Concept of a File Attributes of a File Operations on Files Types of Files Structure of File 8.3 File Access Methods Sequential Access Direct Access Indexed
Chapter 9: Virtual Memory
 Chapter 9: Virtual Memory Chapter 9: Virtual Memory 9.1 Background 9.2 Demand Paging 9.3 Copy-on-Write 9.4 Page Replacement 9.5 Allocation of Frames 9.6 Thrashing 9.7 Memory-Mapped Files 9.8 Allocating
Chapter 9: Virtual Memory Chapter 9: Virtual Memory 9.1 Background 9.2 Demand Paging 9.3 Copy-on-Write 9.4 Page Replacement 9.5 Allocation of Frames 9.6 Thrashing 9.7 Memory-Mapped Files 9.8 Allocating
Server Memory Allocation White Paper VERSION 7.1. Copyright 2016 Jade Software Corporation Limited. All rights reserved.
 VERSION 7.1 Copyright 2016 Jade Software Corporation Limited. All rights reserved. Jade Software Corporation Limited cannot accept any financial or other responsibilities that may be the result of your
VERSION 7.1 Copyright 2016 Jade Software Corporation Limited. All rights reserved. Jade Software Corporation Limited cannot accept any financial or other responsibilities that may be the result of your
Virtual Memory Outline
 Virtual Memory Outline Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating Kernel Memory Other Considerations Operating-System Examples
Virtual Memory Outline Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating Kernel Memory Other Considerations Operating-System Examples
Main Memory and the CPU Cache
 Main Memory and the CPU Cache CPU cache Unrolled linked lists B Trees Our model of main memory and the cost of CPU operations has been intentionally simplistic The major focus has been on determining
Main Memory and the CPU Cache CPU cache Unrolled linked lists B Trees Our model of main memory and the cost of CPU operations has been intentionally simplistic The major focus has been on determining
Chapter 8: Virtual Memory. Operating System Concepts
 Chapter 8: Virtual Memory Silberschatz, Galvin and Gagne 2009 Chapter 8: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating
Chapter 8: Virtual Memory Silberschatz, Galvin and Gagne 2009 Chapter 8: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating
CS 536 Introduction to Programming Languages and Compilers Charles N. Fischer Lecture 11
 CS 536 Introduction to Programming Languages and Compilers Charles N. Fischer Lecture 11 CS 536 Spring 2015 1 Handling Overloaded Declarations Two approaches are popular: 1. Create a single symbol table
CS 536 Introduction to Programming Languages and Compilers Charles N. Fischer Lecture 11 CS 536 Spring 2015 1 Handling Overloaded Declarations Two approaches are popular: 1. Create a single symbol table
Chapter 9: Virtual Memory
 Chapter 9: Virtual Memory Background Demand Paging Chapter 9: Virtual Memory Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating Kernel Memory Other Considerations
Chapter 9: Virtual Memory Background Demand Paging Chapter 9: Virtual Memory Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating Kernel Memory Other Considerations
Unsupervised Learning : Clustering
 Unsupervised Learning : Clustering Things to be Addressed Traditional Learning Models. Cluster Analysis K-means Clustering Algorithm Drawbacks of traditional clustering algorithms. Clustering as a complex
Unsupervised Learning : Clustering Things to be Addressed Traditional Learning Models. Cluster Analysis K-means Clustering Algorithm Drawbacks of traditional clustering algorithms. Clustering as a complex
Oracle Berkeley DB. 12c Release 1
 Oracle Berkeley DB Writing In-Memory Applications 12c Release 1 (Library Version 12.1.6.2) Legal Notice This documentation is distributed under an open source license. You may review the terms of this
Oracle Berkeley DB Writing In-Memory Applications 12c Release 1 (Library Version 12.1.6.2) Legal Notice This documentation is distributed under an open source license. You may review the terms of this
Memory Management. Reading: Silberschatz chapter 9 Reading: Stallings. chapter 7 EEL 358
 Memory Management Reading: Silberschatz chapter 9 Reading: Stallings chapter 7 1 Outline Background Issues in Memory Management Logical Vs Physical address, MMU Dynamic Loading Memory Partitioning Placement
Memory Management Reading: Silberschatz chapter 9 Reading: Stallings chapter 7 1 Outline Background Issues in Memory Management Logical Vs Physical address, MMU Dynamic Loading Memory Partitioning Placement
Databasesystemer, forår 2005 IT Universitetet i København. Forelæsning 8: Database effektivitet. 31. marts Forelæser: Rasmus Pagh
 Databasesystemer, forår 2005 IT Universitetet i København Forelæsning 8: Database effektivitet. 31. marts 2005 Forelæser: Rasmus Pagh Today s lecture Database efficiency Indexing Schema tuning 1 Database
Databasesystemer, forår 2005 IT Universitetet i København Forelæsning 8: Database effektivitet. 31. marts 2005 Forelæser: Rasmus Pagh Today s lecture Database efficiency Indexing Schema tuning 1 Database
Chapter 8. Operating System Support. Yonsei University
 Chapter 8 Operating System Support Contents Operating System Overview Scheduling Memory Management Pentium II and PowerPC Memory Management 8-2 OS Objectives & Functions OS is a program that Manages the
Chapter 8 Operating System Support Contents Operating System Overview Scheduling Memory Management Pentium II and PowerPC Memory Management 8-2 OS Objectives & Functions OS is a program that Manages the
Multi-core processors are here, but how do you resolve data bottlenecks in native code?
 Multi-core processors are here, but how do you resolve data bottlenecks in native code? hint: it s all about locality Michael Wall October, 2008 part I of II: System memory 2 PDC 2008 October 2008 Session
Multi-core processors are here, but how do you resolve data bottlenecks in native code? hint: it s all about locality Michael Wall October, 2008 part I of II: System memory 2 PDC 2008 October 2008 Session
Introduction. Architecture Overview
 Performance and Sizing Guide Version 17 November 2017 Contents Introduction... 5 Architecture Overview... 5 Performance and Scalability Considerations... 6 Vertical Scaling... 7 JVM Heap Sizes... 7 Hardware
Performance and Sizing Guide Version 17 November 2017 Contents Introduction... 5 Architecture Overview... 5 Performance and Scalability Considerations... 6 Vertical Scaling... 7 JVM Heap Sizes... 7 Hardware
AN 831: Intel FPGA SDK for OpenCL
 AN 831: Intel FPGA SDK for OpenCL Host Pipelined Multithread Subscribe Send Feedback Latest document on the web: PDF HTML Contents Contents 1 Intel FPGA SDK for OpenCL Host Pipelined Multithread...3 1.1
AN 831: Intel FPGA SDK for OpenCL Host Pipelined Multithread Subscribe Send Feedback Latest document on the web: PDF HTML Contents Contents 1 Intel FPGA SDK for OpenCL Host Pipelined Multithread...3 1.1
Chapter 9: Virtual Memory. Chapter 9: Virtual Memory. Objectives. Background. Virtual-address address Space
 Chapter 9: Virtual Memory Chapter 9: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating Kernel Memory Other Considerations
Chapter 9: Virtual Memory Chapter 9: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating Kernel Memory Other Considerations
Embedded Systems Dr. Santanu Chaudhury Department of Electrical Engineering Indian Institute of Technology, Delhi
 Embedded Systems Dr. Santanu Chaudhury Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 13 Virtual memory and memory management unit In the last class, we had discussed
Embedded Systems Dr. Santanu Chaudhury Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 13 Virtual memory and memory management unit In the last class, we had discussed
Chapters 9 & 10: Memory Management and Virtual Memory
 Chapters 9 & 10: Memory Management and Virtual Memory Important concepts (for final, projects, papers) addressing: physical/absolute, logical/relative/virtual overlays swapping and paging memory protection
Chapters 9 & 10: Memory Management and Virtual Memory Important concepts (for final, projects, papers) addressing: physical/absolute, logical/relative/virtual overlays swapping and paging memory protection
Chapter 9: Virtual Memory
 Chapter 9: Virtual Memory Chapter 9: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating Kernel Memory Other Considerations
Chapter 9: Virtual Memory Chapter 9: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating Kernel Memory Other Considerations
Indexing Methods. Lecture 9. Storage Requirements of Databases
 Indexing Methods Lecture 9 Storage Requirements of Databases Need data to be stored permanently or persistently for long periods of time Usually too big to fit in main memory Low cost of storage per unit
Indexing Methods Lecture 9 Storage Requirements of Databases Need data to be stored permanently or persistently for long periods of time Usually too big to fit in main memory Low cost of storage per unit
TABLES AND HASHING. Chapter 13
 Data Structures Dr Ahmed Rafat Abas Computer Science Dept, Faculty of Computer and Information, Zagazig University arabas@zu.edu.eg http://www.arsaliem.faculty.zu.edu.eg/ TABLES AND HASHING Chapter 13
Data Structures Dr Ahmed Rafat Abas Computer Science Dept, Faculty of Computer and Information, Zagazig University arabas@zu.edu.eg http://www.arsaliem.faculty.zu.edu.eg/ TABLES AND HASHING Chapter 13
Lecture 17. Edited from slides for Operating System Concepts by Silberschatz, Galvin, Gagne
 Lecture 17 Edited from slides for Operating System Concepts by Silberschatz, Galvin, Gagne Page Replacement Algorithms Last Lecture: FIFO Optimal Page Replacement LRU LRU Approximation Additional-Reference-Bits
Lecture 17 Edited from slides for Operating System Concepts by Silberschatz, Galvin, Gagne Page Replacement Algorithms Last Lecture: FIFO Optimal Page Replacement LRU LRU Approximation Additional-Reference-Bits
MG4J: Managing Gigabytes for Java. MG4J - intro 1
 MG4J: Managing Gigabytes for Java MG4J - intro 1 Managing Gigabytes for Java Schedule: 1. Introduction to MG4J framework. 2. Exercitation: try to set up a search engine on a particular collection of documents.
MG4J: Managing Gigabytes for Java MG4J - intro 1 Managing Gigabytes for Java Schedule: 1. Introduction to MG4J framework. 2. Exercitation: try to set up a search engine on a particular collection of documents.
Representing Data Elements
 Representing Data Elements Week 10 and 14, Spring 2005 Edited by M. Naci Akkøk, 5.3.2004, 3.3.2005 Contains slides from 18.3.2002 by Hector Garcia-Molina, Vera Goebel INF3100/INF4100 Database Systems Page
Representing Data Elements Week 10 and 14, Spring 2005 Edited by M. Naci Akkøk, 5.3.2004, 3.3.2005 Contains slides from 18.3.2002 by Hector Garcia-Molina, Vera Goebel INF3100/INF4100 Database Systems Page
Optimal Algorithm. Replace page that will not be used for longest period of time Used for measuring how well your algorithm performs
 Optimal Algorithm Replace page that will not be used for longest period of time Used for measuring how well your algorithm performs page 1 Least Recently Used (LRU) Algorithm Reference string: 1, 2, 3,
Optimal Algorithm Replace page that will not be used for longest period of time Used for measuring how well your algorithm performs page 1 Least Recently Used (LRU) Algorithm Reference string: 1, 2, 3,
Computer Organization and Architecture. OS Objectives and Functions Convenience Making the computer easier to use
 Computer Organization and Architecture Chapter 8 Operating System Support 1. Processes and Scheduling 2. Memory Management OS Objectives and Functions Convenience Making the computer easier to use Efficiency
Computer Organization and Architecture Chapter 8 Operating System Support 1. Processes and Scheduling 2. Memory Management OS Objectives and Functions Convenience Making the computer easier to use Efficiency
Virtual Memory. Chapter 8
 Virtual Memory 1 Chapter 8 Characteristics of Paging and Segmentation Memory references are dynamically translated into physical addresses at run time E.g., process may be swapped in and out of main memory
Virtual Memory 1 Chapter 8 Characteristics of Paging and Segmentation Memory references are dynamically translated into physical addresses at run time E.g., process may be swapped in and out of main memory
Simultaneous Multithreading: a Platform for Next Generation Processors
 Simultaneous Multithreading: a Platform for Next Generation Processors Paulo Alexandre Vilarinho Assis Departamento de Informática, Universidade do Minho 4710 057 Braga, Portugal paulo.assis@bragatel.pt
Simultaneous Multithreading: a Platform for Next Generation Processors Paulo Alexandre Vilarinho Assis Departamento de Informática, Universidade do Minho 4710 057 Braga, Portugal paulo.assis@bragatel.pt
Virtual Memory. Reading: Silberschatz chapter 10 Reading: Stallings. chapter 8 EEL 358
 Virtual Memory Reading: Silberschatz chapter 10 Reading: Stallings chapter 8 1 Outline Introduction Advantages Thrashing Principal of Locality VM based on Paging/Segmentation Combined Paging and Segmentation
Virtual Memory Reading: Silberschatz chapter 10 Reading: Stallings chapter 8 1 Outline Introduction Advantages Thrashing Principal of Locality VM based on Paging/Segmentation Combined Paging and Segmentation
CS399 New Beginnings. Jonathan Walpole
 CS399 New Beginnings Jonathan Walpole Memory Management Memory Management Memory a linear array of bytes - Holds O.S. and programs (processes) - Each cell (byte) is named by a unique memory address Recall,
CS399 New Beginnings Jonathan Walpole Memory Management Memory Management Memory a linear array of bytes - Holds O.S. and programs (processes) - Each cell (byte) is named by a unique memory address Recall,
Advanced Database Systems
 Lecture IV Query Processing Kyumars Sheykh Esmaili Basic Steps in Query Processing 2 Query Optimization Many equivalent execution plans Choosing the best one Based on Heuristics, Cost Will be discussed
Lecture IV Query Processing Kyumars Sheykh Esmaili Basic Steps in Query Processing 2 Query Optimization Many equivalent execution plans Choosing the best one Based on Heuristics, Cost Will be discussed
Chapter 11: File System Implementation. Objectives
 Chapter 11: File System Implementation Objectives To describe the details of implementing local file systems and directory structures To describe the implementation of remote file systems To discuss block
Chapter 11: File System Implementation Objectives To describe the details of implementing local file systems and directory structures To describe the implementation of remote file systems To discuss block
CS6401- Operating System UNIT-III STORAGE MANAGEMENT
 UNIT-III STORAGE MANAGEMENT Memory Management: Background In general, to rum a program, it must be brought into memory. Input queue collection of processes on the disk that are waiting to be brought into
UNIT-III STORAGE MANAGEMENT Memory Management: Background In general, to rum a program, it must be brought into memory. Input queue collection of processes on the disk that are waiting to be brought into
Main Memory CHAPTER. Exercises. 7.9 Explain the difference between internal and external fragmentation. Answer:
 7 CHAPTER Main Memory Exercises 7.9 Explain the difference between internal and external fragmentation. a. Internal fragmentation is the area in a region or a page that is not used by the job occupying
7 CHAPTER Main Memory Exercises 7.9 Explain the difference between internal and external fragmentation. a. Internal fragmentation is the area in a region or a page that is not used by the job occupying
Chapter 6: Demand Paging
 ADRIAN PERRIG & TORSTEN HOEFLER ( 5-006-00 ) Networks and Operating Systems Chapter 6: Demand Paging Source: http://redmine.replicant.us/projects/replicant/wiki/samsunggalaxybackdoor If you miss a key
ADRIAN PERRIG & TORSTEN HOEFLER ( 5-006-00 ) Networks and Operating Systems Chapter 6: Demand Paging Source: http://redmine.replicant.us/projects/replicant/wiki/samsunggalaxybackdoor If you miss a key
Teradata Analyst Pack More Power to Analyze and Tune Your Data Warehouse for Optimal Performance
 Data Warehousing > Tools & Utilities Teradata Analyst Pack More Power to Analyze and Tune Your Data Warehouse for Optimal Performance By: Rod Vandervort, Jeff Shelton, and Louis Burger Table of Contents
Data Warehousing > Tools & Utilities Teradata Analyst Pack More Power to Analyze and Tune Your Data Warehouse for Optimal Performance By: Rod Vandervort, Jeff Shelton, and Louis Burger Table of Contents
TOPLink for WebLogic. Whitepaper. The Challenge: The Solution:
 Whitepaper The Challenge: Enterprise JavaBeans (EJB) represents a new standard in enterprise computing: a component-based architecture for developing and deploying distributed object-oriented applications
Whitepaper The Challenge: Enterprise JavaBeans (EJB) represents a new standard in enterprise computing: a component-based architecture for developing and deploying distributed object-oriented applications
Database performance becomes an important issue in the presence of
 Database tuning is the process of improving database performance by minimizing response time (the time it takes a statement to complete) and maximizing throughput the number of statements a database can
Database tuning is the process of improving database performance by minimizing response time (the time it takes a statement to complete) and maximizing throughput the number of statements a database can
Chapter 12: Indexing and Hashing. Basic Concepts
 Chapter 12: Indexing and Hashing! Basic Concepts! Ordered Indices! B+-Tree Index Files! B-Tree Index Files! Static Hashing! Dynamic Hashing! Comparison of Ordered Indexing and Hashing! Index Definition
Chapter 12: Indexing and Hashing! Basic Concepts! Ordered Indices! B+-Tree Index Files! B-Tree Index Files! Static Hashing! Dynamic Hashing! Comparison of Ordered Indexing and Hashing! Index Definition
File Directories Associated with any file management system and collection of files is a file directories The directory contains information about
 1 File Management 2 File Directories Associated with any file management system and collection of files is a file directories The directory contains information about the files, including attributes, location
1 File Management 2 File Directories Associated with any file management system and collection of files is a file directories The directory contains information about the files, including attributes, location
Last Class: Deadlocks. Where we are in the course
 Last Class: Deadlocks Necessary conditions for deadlock: Mutual exclusion Hold and wait No preemption Circular wait Ways of handling deadlock Deadlock detection and recovery Deadlock prevention Deadlock
Last Class: Deadlocks Necessary conditions for deadlock: Mutual exclusion Hold and wait No preemption Circular wait Ways of handling deadlock Deadlock detection and recovery Deadlock prevention Deadlock
Memory Management. Goals of Memory Management. Mechanism. Policies
 Memory Management Design, Spring 2011 Department of Computer Science Rutgers Sakai: 01:198:416 Sp11 (https://sakai.rutgers.edu) Memory Management Goals of Memory Management Convenient abstraction for programming
Memory Management Design, Spring 2011 Department of Computer Science Rutgers Sakai: 01:198:416 Sp11 (https://sakai.rutgers.edu) Memory Management Goals of Memory Management Convenient abstraction for programming
File Systems. CS170 Fall 2018
 File Systems CS170 Fall 2018 Table of Content File interface review File-System Structure File-System Implementation Directory Implementation Allocation Methods of Disk Space Free-Space Management Contiguous
File Systems CS170 Fall 2018 Table of Content File interface review File-System Structure File-System Implementation Directory Implementation Allocation Methods of Disk Space Free-Space Management Contiguous
Efficiency. Efficiency: Indexing. Indexing. Efficiency Techniques. Inverted Index. Inverted Index (COSC 488)
 Efficiency Efficiency: Indexing (COSC 488) Nazli Goharian nazli@cs.georgetown.edu Difficult to analyze sequential IR algorithms: data and query dependency (query selectivity). O(q(cf max )) -- high estimate-
Efficiency Efficiency: Indexing (COSC 488) Nazli Goharian nazli@cs.georgetown.edu Difficult to analyze sequential IR algorithms: data and query dependency (query selectivity). O(q(cf max )) -- high estimate-
Chapter 12: Indexing and Hashing
 Chapter 12: Indexing and Hashing Basic Concepts Ordered Indices B+-Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered Indexing and Hashing Index Definition in SQL
Chapter 12: Indexing and Hashing Basic Concepts Ordered Indices B+-Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered Indexing and Hashing Index Definition in SQL
CMSC 313 COMPUTER ORGANIZATION & ASSEMBLY LANGUAGE PROGRAMMING LECTURE 27, FALL 2012
 CMSC 313 COMPUTER ORGANIZATION & ASSEMBLY LANGUAGE PROGRAMMING LECTURE 27, FALL 2012 ANNOUNCEMENTS Need student input on Lecturer Search Max Morawski Lecture 2:30pm 3:15pm, Fri 12/7, ITE 217 Meet with
CMSC 313 COMPUTER ORGANIZATION & ASSEMBLY LANGUAGE PROGRAMMING LECTURE 27, FALL 2012 ANNOUNCEMENTS Need student input on Lecturer Search Max Morawski Lecture 2:30pm 3:15pm, Fri 12/7, ITE 217 Meet with
CS 405G: Introduction to Database Systems. Storage
 CS 405G: Introduction to Database Systems Storage It s all about disks! Outline That s why we always draw databases as And why the single most important metric in database processing is the number of disk
CS 405G: Introduction to Database Systems Storage It s all about disks! Outline That s why we always draw databases as And why the single most important metric in database processing is the number of disk
File Structures and Indexing
 File Structures and Indexing CPS352: Database Systems Simon Miner Gordon College Last Revised: 10/11/12 Agenda Check-in Database File Structures Indexing Database Design Tips Check-in Database File Structures
File Structures and Indexing CPS352: Database Systems Simon Miner Gordon College Last Revised: 10/11/12 Agenda Check-in Database File Structures Indexing Database Design Tips Check-in Database File Structures
Chapter 4. Advanced Pipelining and Instruction-Level Parallelism. In-Cheol Park Dept. of EE, KAIST
 Chapter 4. Advanced Pipelining and Instruction-Level Parallelism In-Cheol Park Dept. of EE, KAIST Instruction-level parallelism Loop unrolling Dependence Data/ name / control dependence Loop level parallelism
Chapter 4. Advanced Pipelining and Instruction-Level Parallelism In-Cheol Park Dept. of EE, KAIST Instruction-level parallelism Loop unrolling Dependence Data/ name / control dependence Loop level parallelism
Chapter 9: Virtual Memory
 Chapter 9: Virtual Memory Silberschatz, Galvin and Gagne 2013 Chapter 9: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating
Chapter 9: Virtual Memory Silberschatz, Galvin and Gagne 2013 Chapter 9: Virtual Memory Background Demand Paging Copy-on-Write Page Replacement Allocation of Frames Thrashing Memory-Mapped Files Allocating
Why do we care about parallel?
 Threads 11/15/16 CS31 teaches you How a computer runs a program. How the hardware performs computations How the compiler translates your code How the operating system connects hardware and software The
Threads 11/15/16 CS31 teaches you How a computer runs a program. How the hardware performs computations How the compiler translates your code How the operating system connects hardware and software The
SQL/MX UPDATE STATISTICS Enhancements
 SQL/MX UPDATE STATISTICS Enhancements Introduction... 2 UPDATE STATISTICS Background... 2 Tests Performed... 2 Test Results... 3 For more information... 7 Introduction HP NonStop SQL/MX Release 2.1.1 includes
SQL/MX UPDATE STATISTICS Enhancements Introduction... 2 UPDATE STATISTICS Background... 2 Tests Performed... 2 Test Results... 3 For more information... 7 Introduction HP NonStop SQL/MX Release 2.1.1 includes
Scalable Access to SAS Data Billy Clifford, SAS Institute Inc., Austin, TX
 Scalable Access to SAS Data Billy Clifford, SAS Institute Inc., Austin, TX ABSTRACT Symmetric multiprocessor (SMP) computers can increase performance by reducing the time required to analyze large volumes
Scalable Access to SAS Data Billy Clifford, SAS Institute Inc., Austin, TX ABSTRACT Symmetric multiprocessor (SMP) computers can increase performance by reducing the time required to analyze large volumes
Process size is independent of the main memory present in the system.
 Hardware control structure Two characteristics are key to paging and segmentation: 1. All memory references are logical addresses within a process which are dynamically converted into physical at run time.
Hardware control structure Two characteristics are key to paging and segmentation: 1. All memory references are logical addresses within a process which are dynamically converted into physical at run time.
CMSC 341 Hashing. Based on slides from previous iterations of this course
 CMSC 341 Hashing Based on slides from previous iterations of this course Hashing Searching n Consider the problem of searching an array for a given value q If the array is not sorted, the search requires
CMSC 341 Hashing Based on slides from previous iterations of this course Hashing Searching n Consider the problem of searching an array for a given value q If the array is not sorted, the search requires
Run-Time Environments/Garbage Collection
 Run-Time Environments/Garbage Collection Department of Computer Science, Faculty of ICT January 5, 2014 Introduction Compilers need to be aware of the run-time environment in which their compiled programs
Run-Time Environments/Garbage Collection Department of Computer Science, Faculty of ICT January 5, 2014 Introduction Compilers need to be aware of the run-time environment in which their compiled programs
Lecture Notes on Memory Layout
 Lecture Notes on Memory Layout 15-122: Principles of Imperative Computation Frank Pfenning André Platzer Lecture 11 1 Introduction In order to understand how programs work, we can consider the functions,
Lecture Notes on Memory Layout 15-122: Principles of Imperative Computation Frank Pfenning André Platzer Lecture 11 1 Introduction In order to understand how programs work, we can consider the functions,
CUDA. Schedule API. Language extensions. nvcc. Function type qualifiers (1) CUDA compiler to handle the standard C extensions.
 Schedule CUDA Digging further into the programming manual Application Programming Interface (API) text only part, sorry Image utilities (simple CUDA examples) Performace considerations Matrix multiplication
Schedule CUDA Digging further into the programming manual Application Programming Interface (API) text only part, sorry Image utilities (simple CUDA examples) Performace considerations Matrix multiplication
CS307: Operating Systems
 CS307: Operating Systems Chentao Wu 吴晨涛 Associate Professor Dept. of Computer Science and Engineering Shanghai Jiao Tong University SEIEE Building 3-513 wuct@cs.sjtu.edu.cn Download Lectures ftp://public.sjtu.edu.cn
CS307: Operating Systems Chentao Wu 吴晨涛 Associate Professor Dept. of Computer Science and Engineering Shanghai Jiao Tong University SEIEE Building 3-513 wuct@cs.sjtu.edu.cn Download Lectures ftp://public.sjtu.edu.cn
Chapter 6 Memory 11/3/2015. Chapter 6 Objectives. 6.2 Types of Memory. 6.1 Introduction
 Chapter 6 Objectives Chapter 6 Memory Master the concepts of hierarchical memory organization. Understand how each level of memory contributes to system performance, and how the performance is measured.
Chapter 6 Objectives Chapter 6 Memory Master the concepts of hierarchical memory organization. Understand how each level of memory contributes to system performance, and how the performance is measured.
ADRIAN PERRIG & TORSTEN HOEFLER Networks and Operating Systems ( ) Chapter 6: Demand Paging
 ADRIAN PERRIG & TORSTEN HOEFLER Networks and Operating Systems (5-006-00) Chapter 6: Demand Paging http://redmine.replicant.us/projects/replicant/wiki/samsunggalaxybackdoor (0) # Inverted page table One
ADRIAN PERRIG & TORSTEN HOEFLER Networks and Operating Systems (5-006-00) Chapter 6: Demand Paging http://redmine.replicant.us/projects/replicant/wiki/samsunggalaxybackdoor (0) # Inverted page table One
a. What is a lower bound on the number of page faults? b. What is an upper bound on the number of page faults?
 Virtual Memory 8 CHAPTER Practice Exercises 8.1 Under what circumstances do page faults occur? Describe the actions taken by the operating system when a page fault occurs. A page fault occurs when an access
Virtual Memory 8 CHAPTER Practice Exercises 8.1 Under what circumstances do page faults occur? Describe the actions taken by the operating system when a page fault occurs. A page fault occurs when an access
Memory Management Topics. CS 537 Lecture 11 Memory. Virtualizing Resources
 Memory Management Topics CS 537 Lecture Memory Michael Swift Goals of memory management convenient abstraction for programming isolation between processes allocate scarce memory resources between competing
Memory Management Topics CS 537 Lecture Memory Michael Swift Goals of memory management convenient abstraction for programming isolation between processes allocate scarce memory resources between competing
Oracle Berkeley DB. Writing In-Memory Applications
 . Oracle Berkeley DB Writing In-Memory Applications Legal Notice This documentation is distributed under an open source license. You may review the terms of this license at: http://www.oracle.com/technology/software/products/berkeley-db/htdocs/oslicense.html
. Oracle Berkeley DB Writing In-Memory Applications Legal Notice This documentation is distributed under an open source license. You may review the terms of this license at: http://www.oracle.com/technology/software/products/berkeley-db/htdocs/oslicense.html
MEMORY MANAGEMENT/1 CS 409, FALL 2013
 MEMORY MANAGEMENT Requirements: Relocation (to different memory areas) Protection (run time, usually implemented together with relocation) Sharing (and also protection) Logical organization Physical organization
MEMORY MANAGEMENT Requirements: Relocation (to different memory areas) Protection (run time, usually implemented together with relocation) Sharing (and also protection) Logical organization Physical organization
!! What is virtual memory and when is it useful? !! What is demand paging? !! When should pages in memory be replaced?
 Chapter 10: Virtual Memory Questions? CSCI [4 6] 730 Operating Systems Virtual Memory!! What is virtual memory and when is it useful?!! What is demand paging?!! When should pages in memory be replaced?!!
Chapter 10: Virtual Memory Questions? CSCI [4 6] 730 Operating Systems Virtual Memory!! What is virtual memory and when is it useful?!! What is demand paging?!! When should pages in memory be replaced?!!
Computer Caches. Lab 1. Caching
 Lab 1 Computer Caches Lab Objective: Caches play an important role in computational performance. Computers store memory in various caches, each with its advantages and drawbacks. We discuss the three main
Lab 1 Computer Caches Lab Objective: Caches play an important role in computational performance. Computers store memory in various caches, each with its advantages and drawbacks. We discuss the three main
CMSC 313 COMPUTER ORGANIZATION & ASSEMBLY LANGUAGE PROGRAMMING LECTURE 27, SPRING 2013
 CMSC 313 COMPUTER ORGANIZATION & ASSEMBLY LANGUAGE PROGRAMMING LECTURE 27, SPRING 2013 CACHING Why: bridge speed difference between CPU and RAM Modern RAM allows blocks of memory to be read quickly Principle
CMSC 313 COMPUTER ORGANIZATION & ASSEMBLY LANGUAGE PROGRAMMING LECTURE 27, SPRING 2013 CACHING Why: bridge speed difference between CPU and RAM Modern RAM allows blocks of memory to be read quickly Principle
CSE 410 Computer Systems. Hal Perkins Spring 2010 Lecture 12 More About Caches
 CSE 4 Computer Systems Hal Perkins Spring Lecture More About Caches Reading Computer Organization and Design Section 5. Introduction Section 5. Basics of Caches Section 5. Measuring and Improving Cache
CSE 4 Computer Systems Hal Perkins Spring Lecture More About Caches Reading Computer Organization and Design Section 5. Introduction Section 5. Basics of Caches Section 5. Measuring and Improving Cache
Operating Systems. Memory Management. Lecture 9 Michael O Boyle
 Operating Systems Memory Management Lecture 9 Michael O Boyle 1 Memory Management Background Logical/Virtual Address Space vs Physical Address Space Swapping Contiguous Memory Allocation Segmentation Goals
Operating Systems Memory Management Lecture 9 Michael O Boyle 1 Memory Management Background Logical/Virtual Address Space vs Physical Address Space Swapping Contiguous Memory Allocation Segmentation Goals
Sustainable Memory Use Allocation & (Implicit) Deallocation (mostly in Java)
 COMP 412 FALL 2017 Sustainable Memory Use Allocation & (Implicit) Deallocation (mostly in Java) Copyright 2017, Keith D. Cooper & Zoran Budimlić, all rights reserved. Students enrolled in Comp 412 at Rice
COMP 412 FALL 2017 Sustainable Memory Use Allocation & (Implicit) Deallocation (mostly in Java) Copyright 2017, Keith D. Cooper & Zoran Budimlić, all rights reserved. Students enrolled in Comp 412 at Rice
Memory management. Requirements. Relocation: program loading. Terms. Relocation. Protection. Sharing. Logical organization. Physical organization
 Requirements Relocation Memory management ability to change process image position Protection ability to avoid unwanted memory accesses Sharing ability to share memory portions among processes Logical
Requirements Relocation Memory management ability to change process image position Protection ability to avoid unwanted memory accesses Sharing ability to share memory portions among processes Logical
Chapter 9: Virtual-Memory
 Chapter 9: Virtual-Memory Management Chapter 9: Virtual-Memory Management Background Demand Paging Page Replacement Allocation of Frames Thrashing Other Considerations Silberschatz, Galvin and Gagne 2013
Chapter 9: Virtual-Memory Management Chapter 9: Virtual-Memory Management Background Demand Paging Page Replacement Allocation of Frames Thrashing Other Considerations Silberschatz, Galvin and Gagne 2013
Model-Based Design for Large High Integrity Systems: A Discussion Regarding Model Architecture
 Model-Based Design for Large High Integrity Systems: A Discussion Regarding Model Architecture By Mike Anthony and Jon Friedman MathWorks Inc, Natick, MA, 01760 INTRODUCTION From complex controls problems
Model-Based Design for Large High Integrity Systems: A Discussion Regarding Model Architecture By Mike Anthony and Jon Friedman MathWorks Inc, Natick, MA, 01760 INTRODUCTION From complex controls problems
CSE 351. Virtual Memory
 CSE 351 Virtual Memory Virtual Memory Very powerful layer of indirection on top of physical memory addressing We never actually use physical addresses when writing programs Every address, pointer, etc
CSE 351 Virtual Memory Virtual Memory Very powerful layer of indirection on top of physical memory addressing We never actually use physical addresses when writing programs Every address, pointer, etc
Chapter 9: Virtual Memory
 Chapter 9: Virtual Memory Chapter 9: Virtual Memory Background Demand Paging Process Creation Page Replacement Allocation of Frames Thrashing Demand Segmentation Operating System Examples 9.2 Background
Chapter 9: Virtual Memory Chapter 9: Virtual Memory Background Demand Paging Process Creation Page Replacement Allocation of Frames Thrashing Demand Segmentation Operating System Examples 9.2 Background
B.H.GARDI COLLEGE OF ENGINEERING & TECHNOLOGY (MCA Dept.) Parallel Database Database Management System - 2
 Introduction :- Today single CPU based architecture is not capable enough for the modern database that are required to handle more demanding and complex requirements of the users, for example, high performance,
Introduction :- Today single CPU based architecture is not capable enough for the modern database that are required to handle more demanding and complex requirements of the users, for example, high performance,
Multiprocessors II: CC-NUMA DSM. CC-NUMA for Large Systems
 Multiprocessors II: CC-NUMA DSM DSM cache coherence the hardware stuff Today s topics: what happens when we lose snooping new issues: global vs. local cache line state enter the directory issues of increasing
Multiprocessors II: CC-NUMA DSM DSM cache coherence the hardware stuff Today s topics: what happens when we lose snooping new issues: global vs. local cache line state enter the directory issues of increasing
CMSC 341 Lecture 16/17 Hashing, Parts 1 & 2
 CMSC 341 Lecture 16/17 Hashing, Parts 1 & 2 Prof. John Park Based on slides from previous iterations of this course Today s Topics Overview Uses and motivations of hash tables Major concerns with hash
CMSC 341 Lecture 16/17 Hashing, Parts 1 & 2 Prof. John Park Based on slides from previous iterations of this course Today s Topics Overview Uses and motivations of hash tables Major concerns with hash
Multidimensional Clustering (MDC) Tables in DB2 LUW. DB2Night Show. January 14, 2011
 Multidimensional Clustering (MDC) Tables in DB2 LUW DB2Night Show January 14, 2011 Pat Bates, IBM Technical Sales Professional, Data Warehousing Paul Zikopoulos, Director, IBM Information Management Client
Multidimensional Clustering (MDC) Tables in DB2 LUW DB2Night Show January 14, 2011 Pat Bates, IBM Technical Sales Professional, Data Warehousing Paul Zikopoulos, Director, IBM Information Management Client
The Art and Science of Memory Allocation
 Logical Diagram The Art and Science of Memory Allocation Don Porter CSE 506 Binary Formats RCU Memory Management Memory Allocators CPU Scheduler User System Calls Kernel Today s Lecture File System Networking
Logical Diagram The Art and Science of Memory Allocation Don Porter CSE 506 Binary Formats RCU Memory Management Memory Allocators CPU Scheduler User System Calls Kernel Today s Lecture File System Networking
