MITOCW watch?v=w_-sx4vr53m
|
|
|
- Jasper Sherman
- 5 years ago
- Views:
Transcription
1 MITOCW watch?v=w_-sx4vr53m The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make a donation or view additional materials from hundreds of MIT courses, visit MIT OpenCourseWare at ocw.mit.edu. All right. Let's get started. Today's topic would be distributed algorithms. We will look at two new algorithms. But they are similar to what you have seen in the lectures. So it will also be a review of some concepts in lectures. So our first example would be, again, [INAUDIBLE], the simplest example. But this time, the network and topology would be a ring. So in the lectures, the example we see is a click, meaning they are fully connected. Right. Every node can talk to every other node. There, if you remember, our solution for everyone to generate a UID or a random number. And if you are the maximum, then you output, you're the leader You can do that because, yeah, you are connected to everybody. So you immediately know what random number everybody generates. And you can compare whether you are the largest. Now, the idea is the same if we have a ring. So you want everyone to generate a ID or random number. I'll just say ID from now on. And you want to collect everyone else ID so that you know whether your ID is the largest among all of them. OK. [INAUDIBLE] Pardon? [INAUDIBLE] OK. The question is where did the comparison happen? So we first need some way to pass the numbers around such that everyone has everyone else's number. Right. You have the number of everyone, then you can compare whether the largest equals yours. OK. If the largest equals yours, then you know you are the largest. And you're going to output, I'm
2 the leader. OK. So the difficulty is just how to pass the numbers around so that everyone sees everyone else's number. Any ideas? Simple solution. Well, there's not much you can do. You are just connect to your two neighbors, the left one and the right one. So how do you propagate the information? Go ahead. You can take the maximum of your ID and neighbor's IDs and kind of broadcast that. OK. So what does broadcast mean here? Like tell your neighbors what the largest of your value [INAUDIBLE] OK. And yes. Let me call them A, B, C, E, F. Then, yes, C can tell D or can tell B, but how does C tell E? It waited around to I guess propagate the maximum. Yep. So it would be just, say, everyone talks to its right neighbor. And then B has A's IDs, C these B's ID, D has C's ID, and then continue and pass around next time. So just to make it perfect clear. Say they generate some random IDs that's 5, 10, 20. And then in the next round, A would send its ID to B, B would send its ID to C, C would send its ID to D. And in the next round, B would pass this information along to C. And C would pass the information to D. And just continue. And eventually everyone will have everyone else's ID. So how many rounds do we need? If they are in nodes in the system. I think probably in just one direction or two neighbors. I think you can do it either way. If you propagate both ways, it probably 2x faster, yeah. [INAUDIBLE] Yeah, correct. It's just O(n). But to keep it simple, let's say we just propagate in one direction. That's also fine. Still O(n). So how many messages are sent in total? n squared.
3 Pardon? n squared. n squared. Yep. Is that obvious to everyone? OK. Give an explanation. Yeah, at each round everyone sends a message to its neighbors. Yeah. Yeah. Every round, everyone sends a message. Or you can think of every message as propagated n times. And there are n messages in total. OK. Yeah. That's definitely a solution. Well, you can imagine, it's probably the naive solution. And can we do better than that? In this case, are we assuming they know that there are n of them? OK. Good question. So if they know there are n of them, yep, then they know how to terminate. So your question is how to terminate, right? If they don't, eventually you will receive your own ID on the other side. If we keep sending left, eventually you will receive it on the left port. And, yeah, that's an indication of termination. Question? Are we assuming the trajectory that these are unique? Yeah. We usually assume that, yeah. Either it's a unique user-- sorry, UID. What does U stand for by the way? Or if you generate random numbers in a large range, it's very unlikely that they collide. OK. So can we do better than that? You have some idea? Once something [INAUDIBLE] where you only pass it to the one that's bigger. Hm-mm. OK. I think you have two ideas. And binary search, we'll see how that works later. So you said only forward something that's larger? 0 Yeah, like only forward things are larger. OK, yeah, that's on the right track. So one obvious thing we can do is that so we actually don't care what all the IDs are, right. We only care whether a certain ID's the largest. So for example, in this case, when A send its ID 5 to B, B knows this 5 won't be the leader.
4 All right. Because 5 is too small. It's even smaller than his ID. So we can choose to drop this message. There's no point in passing that message further. Same thing for this message. C knows that 10 is too small. And it doesn't have to pass it along. [INAUDIBLE] Oh, the ID? It's just the integer each node chooses at random. See. Yeah, the only purpose of the ID is to break symmetry. So, yeah. Like we have seen the lecture, if they don't do this, if they don't have any unique identifier, they won't be able to select the leader. And when they have a unique number, then they can select, yeah, the largest one or smallest one in some way. OK. Does this optimization make sense? We can cut [INAUDIBLE] messages that have no chance of becoming the leader. What is the upper bound of it? Is it still n squared? Correct. Yeah. That's a very good question and very good answer, by the way. But how effective is this? Well in average case, we may be able to drop some messages. But there pathological case where it actually doesn't help at all. Say this is the ID we choose. Then when there's 20, it send around. B cannot drop it. Right, because it may be the largest. And when this 10 is sent to C, C cannot drop it. And when 20 comes along, it also cannot drop it. So no node can drop any message. Its worst case is still n square. OK. So let's think about the binary search equivalent, yeah, or how to binary search in this case. So binary is [INAUDIBLE] what? Yeah, good question. It's not very obvious binary searching to what. I Yeah, just some binary idea that will give us a n log end bound. So actually this is the better logarithm. But once you have a log n, you can probably get-- OK, go ahead. How about kind of merging, like instead of finding the [INAUDIBLE], finding like log maximum, then [INAUDIBLE].
5 Yeah. That's on the right track, yeah. Like clusters of some [INAUDIBLE]. Yeah. That's definitely the right idea. Let's detail it a little bit. How do you carry it out? Hm-mm. Divide the two parts. Like kind of the [INAUDIBLE]. And, OK, so then it's let them select their leader respectively and compare which one is larger. It's interesting thought. First, for example, A, B finds the maximum between these two, the C, D finds the maximum E [INAUDIBLE] maximum. Kind of merging, considering them as one node. I think the first difficulty I see is that if you cut it by half, it's no longer a ring, right. Also they can't cut themselves in half. Yeah. Yeah. Correct. Yeah, yeah. Yeah, it's definitely not an easy problem, not a easy algorithm. And the idea is to, well, you had the right idea. That we want to-- what's the word? Let the weak candidates shut up early. So what I mean by that is say we have several round, so this B and A and C. We will that B only propagate to A and C first. If B is the local maximum among A, B, C, then B will try to talk further. Increase its range. If B is not the local maximum of A, B, C, then, yeah, it can be quiet. Doesn't need to send messages anymore. If B succeeds in the next round, then you go further increase its range to try to talk to more people. OK. So how does it work in detail? Well so in round I, we will let a node send this message up to 2 raised to I hops. In this case, is 1 and in next round is 2 and then 4. If at any point some mode like along this range decides that you are not the local maximum, then they will reply that, yeah, you no longer need to send messages anymore. If this message successfully reaches this endpoint that 2 raised to I hops, then this guy will respond. And this guy, if it still thinks you are the local maximum, then it will respond the message while
6 saying, yeah, continue. OK. And if the sender receives the continue message on both sides, then they it continue into the next round. Otherwise, it will go inactive. Is the algorithm clear? If the problem reaches the next maximum, like next the node each has to send a message. Say that again. Like after receiving like don't sending it, like do you have to choose one node, which has to send the message? Oh, OK. In the first round, everyone send their messages. OK. Then some of them will go inactive because they learn they are not maximum. And the remaining, the surviving ones, will, yeah, continue sending messages. And then, yeah, half of them probably will die in the next round. And the surviving ones keep sending messages. Make sense? How do you return messages through I? Like if you [INAUDIBLE] its neighbor and not the node that do either. Yeah. So we will send the message of this form, say, well, some message. And then we will send the hop and the direction, either left or right. And this hop will initially be set to 2 raised to I, the number of round. Then when this guy receives the message, it will increment the hop count and pass it along. And every node when forwarding the message will decrease the that h by 1. And finally when it reaches here, that number becomes 0. And when a node sees a message with 0 hop count, it's going to reverse it, send it in the other direction. And, again, set it back to 2 raised to I. This message I should say ID. And at certain point, a certain node may decide this ID's too small. It doesn't have a chance. Then the I can directly send it in the opposite direction, replying a message saying, yeah, you are too small. OK. So any more questions on the algorithm itself? If not, what's the next step? Time. Yeah, time complexity. I already claimed it's n log n. Is it? This is round. This is message. This is also message complexity. OK. So why is it n log n?
7 The log n [INAUDIBLE]. Hm-mm. So we have a certain number of rounds. So how many rounds do we have? Two. Yeah, maybe. But, yeah, I'll just say log n. OK. Because you are increasing your hop length. And we're going to compute like how many nodes are still active each around and how many messages are sent in the round. So, well, the number of nodes active will just be this number if we start from 0. Why? Because the first time everyone is active. In the next time, only 1/3 of them will be active. But we said we are conservative here at we put 1/2. Right. Next round is actually 1/5. If it's local maximum, it means like these two and those two will go inactive. But we put this as a upper bound. So this is the number of nodes that are still active. And they will send the message up to this many hops. OK. And there are two directions. And you send a message back. And then, yeah-- sorry, send the message forward and someone will reply. But in the end, this is n log n. Yeah, and I think I got 8n log n. So my recitation note says it's 4 log n, not entirely sure what's going on. Yeah. But you can double check whether this is correct or the recitation note is correct. What is I again? I's the number of round in the I-th round. Yeah. This many nodes are still active. And each of them will send a message of this many hops. And I didn't mention whether the network is synchronous or asynchronous. And it turns out it doesn't care. Some of them can work for both synchronous and asynchronous. Apparently, it works for synchronous networks. If it's asynchronous, then what changes is that different nodes are in different rounds. A certain node may be far ahead than the others. But it's fine. Eventually, they will converge to the correct result. OK. So let's look at the second problem. Well, problem's defined even simpler. We just want to
8 So let's look at the second problem. Well, problem's defined even simpler. We just want to count how many nodes are out there. We want the algorithm to work both synchronously and asynchronously. By that I just mean we have a network. Well, say you have a lot of nodes after that. Just want to count how many nodes are there in this network. So I'll give you, say, one minutes to let's first come up with a high-level plan. Is the problem clear? In the worst case, [INAUDIBLE]. The worst case. OK. I haven't defined that. Let's not worry about complexity now for now. The complexity will depend on number of nodes and the number of edges, E. Let's just get it functionally correct. OK. Anyone share a high-level strategy? Go ahead. So each node will start like IDs of the other devices [INAUDIBLE]. So basically like it's going to send propagates [INAUDIBLE] sets of each node. On what edge? Furthest one. Yeah. It wasn't on both edges? Itself first. OK. So then maybe send the 1 here and send the 1 here there. Then this node will think it has a children, it as a child, right, which is this one. Let's just say this is the entire network. And what message does it send to this guy? Reinforced it. Well, you probably need send two here because you have one and this is possibly its child, right. But then we're double counting this node. See the problem? Do nodes have their IDs, like unique IDs? Oh, yeah. They have their IDs. We can't send the IDs instead of the IDs through the end node.
9 OK. We are going to send all the IDs. Yeah, neighbors. And after n steps, it's going to have the [INAUDIBLE]. OK. Yeah, that's an interesting thought. And then you may still need the root. And that will have everyone's ID. And then see how many unique I's are there. OK. Interesting. Does this algorithm work? Yeah, I don't see any problem. OK. But let me still repeat what our algorithm is because it's closer to what's in the lecture. So we're going to find a spanning tree of this network. A spanning tree means, well, like I have to cut one of these edges. If I have a tree, then I can have every child report to its parent. Like how many offsprings, including myself do I have. And this node will sum up all its children and report to its parent. Does everyone get that? So first, we'll find a spanning tree. And second, we'll have child reports to parent. How can we find the spanning tree? Good question. So in the lecture, we have seen algorithm that find BFS spanning tree for synchronous networks. OK. This is review of the lecture. How does it work? Each node will, say, we need to first choose a root. And our root will just send a message to its neighbor and, yeah, saying, you are my child, you are my child, you are my child. And then every node upon receiving this message from the parent will search among its neighbors. All right. So the neighbors that haven't got a parent will acknowledge this sender as the parent. OK. That's a little messy. So this node will search to the leaf node. But then it will also try to search for this guy. But this guy already had a parent, then, yeah, it will say I already got a parent and blah, blah, blah. This will give us a BFS spanning tree. What does it mean? It's a spanning tree found by BFS. Does it work for asynchronous network? Go ahead. This version doesn't. But there's a different version that contains an edge for relaxation
10 technique. Yeah. Correct. And so why does this version not work for a synchronous network? Because different nodes can be on a different round number so that a longer path could end up going to the node even. Yeah, exactly. So let me give a concrete example. What does asynchronous network mean? Is that, well, messages travel at different speed. Say this link for some reason is temporarily down. And this node doesn't receive the message from the root. And then this message travels very fast. And this message also travels very fast. So this message may reach this node earlier. And then this node will think of it as a child of this node. OK. And then this message comes along, finally. But this node says, yeah, I already have a parent. And I'm going to reject you. So it still makes a spanning tree? Yes. Good point. This is not a BFS spanning tree but it's still a spanning tree. All right. So in our problem, we're totally fine with it. Yeah. But you do have to know if you really want a BFS spanning tree in an asynchronous network, then you have to like record the distance and do the relaxation and so on and so forth. OK. So we will just use this algorithm, the BFS spanning tree algorithm, just run it asynchronously. It doesn't find the BFS spanning tree but it finds some spanning tree. OK. How does this algorithm work? We will have several variables. The first one is parent. We will initialize to this undefined single. OK. Then every node will pass around this search message. I'll use a slightly more shorthand notation than from the lecture. OK. Let's say the code I wrote is for a process u. OK. If we receive a message, a search message, from v to u, that means u-- sorry, v is trying to become a parent. OK. And if I do not have a parent yet, I should set the parent to v. OK. So what's the next step? Now, we got this search message from our parent. And we have to pass it along.
11 Should we send it to the like add your child [INAUDIBLE]. Oh, yeah. Great. Yeah, we first need to respond by saying, OK, I'll use a shorter notation. Send these a cue that that's the message that will be sent to v at some point. The message we send is parent 1. Parent 2. This is a response to v saying, yeah, you are my parent. OK. Then else, we also have to respond by saying parent 0. You are not my parent because I already got some other parent. OK. Missing a step here. If we receive a search message. Go ahead. We send messages to all the other nodes. Yeah. We need to pass it to all my potential children. So I use this comma u, meaning the neighbors of u. And then I'll send them a message. What message? Search. OK. OK. So, well, naturally since we have a search message and we know how to deal with it, now we are sending this parent message with better deal with it. Right. So then the next chunk of code should be if we receive this parent message, I'll say parent b, meaning this message comes with either true or false. I received this message from some node w. OK. I'm still u here. Because I just send all the message to all the w's, to all my neighbors, and they should give me a response. OK. If b is 1 that means this particular w take me as its parent. Make sense? OK. So I'd better have a list of my children. I want to keep track of that. How? We will create a new variable for children. It's going to be initialized to what? Yeah, empty set. And now if this b is 1, then I'm going to put w in this children list. OK. I'm leaving some space here because our root should be slightly different. So every other node will send search messages when it receive a search message. We need someone to initiate. Make sense? So if u equals root, we say the root is v0.
12 So two things should happen. First, we should set its parent to some special value. Just say root. And then I should copy this blob of code to here. OK. It's a little crowded but I hope it's still legible. OK. This is already almost the correct algorithm, except that we don't know how to terminate. If we wait long enough, then everyone will receive all the responses and everyone will know its parent and this child list. But how do we terminate? After n rounds. Yeah, that's one way to do, after n rounds. But the whole point is we are trying to find what n is. We don't know how many nodes are there. If we receive reject for all, [INAUDIBLE]. Say again. For all the search, if we receive a reject. Oh, yeah. If you receive a response, either parent 0 or parent 1 from all your neighbors, then your job is pretty much done. But the others have not. All right. So you send a message very fast. They responded to you. And they are still working very hard. OK. So then we need to use the technique from the lecture that's called converge cast. So everyone will send a done signal when it is done and all its children are also done. OK. To do that, I'm going to define a new variable called searched. Searched means someone has responded. OK. In this case, w has responded. I'll put it into the search the list, no matter whether it accepts me as parent or reject. OK. Then naturally I need to define this variable here. OK. As a last step, If we search the list equals my neighbor list, that means everyone has responded and all my children are done, then I need a new variable called done. That's another list tracking who has finished and who has not. OK. So what's the first one?
13 Say again. What was the first one? This one? Searched means someone has responded to the search message. OK. Done means all its children are done. I haven't write how done is defined. Give me a minute. In this case, I'm going to send my parent a message. This is the step of converge cast. What do I send? I'm going to send them I'm done. OK. Then whenever we create a message, we should deal with that message. If we receive a message I'm done, what do we do? OK. From w, then we're going to mark that node as done. OK. There's this other point. So someone has to initiate the done signal. That's going to be our leaves, right. Because when this condition check, they don't have any children. Their children list is empty set. And their done list is also empty set. But they're going to send the I'm done signal first. And then in the median nodes, we'll send a done signal when all its children are done. All right. So this is the converged cast version. Only gives us a termination point of our spanning tree search. We haven't count the number of nodes in the network. But that's a small modification. We're just going to include that number in the I'm done signal. So then I need to define another variable called total that's initialized to 0. This variable will attract how many nodes do I have in my subtree, including me and all my children. Then when I send the I'm done signal, I'm going to send this-- sorry. That's not right way. When I'm sending the I'm done signal, I'm going to send my total number of offspring with it. And when I receive, one of my children reports that I do have t children. I need to increment my total by that amount. OK. I made a mistake again. Should be total plus 1. Right. Because I'm counting all my children and then I should include myself. So that's the complete algorithm. Yeah. One purpose is just to create a different angle to look at distributed algorithm. Usually just
14 draw that network graphs. But sometimes it's helpful to think about how the code actually works. OK. That's all for today.
MITOCW watch?v=zlohv4xq_ti
 MITOCW watch?v=zlohv4xq_ti The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
MITOCW watch?v=zlohv4xq_ti The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
MITOCW watch?v=zm5mw5nkzjg
 MITOCW watch?v=zm5mw5nkzjg The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=zm5mw5nkzjg The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=flgjisf3l78
 MITOCW watch?v=flgjisf3l78 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
MITOCW watch?v=flgjisf3l78 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
MITOCW watch?v=yarwp7tntl4
 MITOCW watch?v=yarwp7tntl4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free.
MITOCW watch?v=yarwp7tntl4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free.
MITOCW watch?v=0jljzrnhwoi
 MITOCW watch?v=0jljzrnhwoi The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=0jljzrnhwoi The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
Formal Methods of Software Design, Eric Hehner, segment 24 page 1 out of 5
 Formal Methods of Software Design, Eric Hehner, segment 24 page 1 out of 5 [talking head] This lecture we study theory design and implementation. Programmers have two roles to play here. In one role, they
Formal Methods of Software Design, Eric Hehner, segment 24 page 1 out of 5 [talking head] This lecture we study theory design and implementation. Programmers have two roles to play here. In one role, they
The following content is provided under a Creative Commons license. Your support
 MITOCW Lecture 9 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make a donation
MITOCW Lecture 9 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make a donation
MITOCW watch?v=se4p7ivcune
 MITOCW watch?v=se4p7ivcune The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=se4p7ivcune The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=v3omvlzi0we
 MITOCW watch?v=v3omvlzi0we The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=v3omvlzi0we The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=9h6muyzjms0
 MITOCW watch?v=9h6muyzjms0 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=9h6muyzjms0 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
The following content is provided under a Creative Commons license. Your support
 MITOCW Recitation 4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make
MITOCW Recitation 4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make
The following content is provided under a Creative Commons license. Your support
 MITOCW Recitation 2 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make
MITOCW Recitation 2 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make
MITOCW watch?v=tkwnms5irbu
 MITOCW watch?v=tkwnms5irbu The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=tkwnms5irbu The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
The following content is provided under a Creative Commons license. Your support
 MITOCW Lecture 23 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free. To make a
MITOCW Lecture 23 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free. To make a
Hi everyone. I hope everyone had a good Fourth of July. Today we're going to be covering graph search. Now, whenever we bring up graph algorithms, we
 Hi everyone. I hope everyone had a good Fourth of July. Today we're going to be covering graph search. Now, whenever we bring up graph algorithms, we have to talk about the way in which we represent the
Hi everyone. I hope everyone had a good Fourth of July. Today we're going to be covering graph search. Now, whenever we bring up graph algorithms, we have to talk about the way in which we represent the
The following content is provided under a Creative Commons license. Your support
 MITOCW Recitation 1 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make
MITOCW Recitation 1 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make
MITOCW MIT6_172_F10_lec18_300k-mp4
 MITOCW MIT6_172_F10_lec18_300k-mp4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for
MITOCW MIT6_172_F10_lec18_300k-mp4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for
MITOCW watch?v=r6-lqbquci0
 MITOCW watch?v=r6-lqbquci0 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=r6-lqbquci0 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW ocw f99-lec07_300k
 MITOCW ocw-18.06-f99-lec07_300k OK, here's linear algebra lecture seven. I've been talking about vector spaces and specially the null space of a matrix and the column space of a matrix. What's in those
MITOCW ocw-18.06-f99-lec07_300k OK, here's linear algebra lecture seven. I've been talking about vector spaces and specially the null space of a matrix and the column space of a matrix. What's in those
The following content is provided under a Creative Commons license. Your support
 MITOCW Lecture 8 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make a donation
MITOCW Lecture 8 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make a donation
MITOCW watch?v=rvrkt-jxvko
 MITOCW watch?v=rvrkt-jxvko The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=rvrkt-jxvko The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
Post Experiment Interview Questions
 Post Experiment Interview Questions Questions about the Maximum Problem 1. What is this problem statement asking? 2. What is meant by positive integers? 3. What does it mean by the user entering valid
Post Experiment Interview Questions Questions about the Maximum Problem 1. What is this problem statement asking? 2. What is meant by positive integers? 3. What does it mean by the user entering valid
GIAN Course on Distributed Network Algorithms. Spanning Tree Constructions
 GIAN Course on Distributed Network Algorithms Spanning Tree Constructions Stefan Schmid @ T-Labs, 2011 Spanning Trees Attactive infrastructure : sparse subgraph ( loop-free backbone ) connecting all nodes.
GIAN Course on Distributed Network Algorithms Spanning Tree Constructions Stefan Schmid @ T-Labs, 2011 Spanning Trees Attactive infrastructure : sparse subgraph ( loop-free backbone ) connecting all nodes.
Distributed Algorithms 6.046J, Spring, 2015 Part 2. Nancy Lynch
 Distributed Algorithms 6.046J, Spring, 2015 Part 2 Nancy Lynch 1 This Week Synchronous distributed algorithms: Leader Election Maximal Independent Set Breadth-First Spanning Trees Shortest Paths Trees
Distributed Algorithms 6.046J, Spring, 2015 Part 2 Nancy Lynch 1 This Week Synchronous distributed algorithms: Leader Election Maximal Independent Set Breadth-First Spanning Trees Shortest Paths Trees
The following content is provided under a Creative Commons license. Your support
 MITOCW Recitation 5 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free. To make
MITOCW Recitation 5 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free. To make
So on the survey, someone mentioned they wanted to work on heaps, and someone else mentioned they wanted to work on balanced binary search trees.
 So on the survey, someone mentioned they wanted to work on heaps, and someone else mentioned they wanted to work on balanced binary search trees. According to the 161 schedule, heaps were last week, hashing
So on the survey, someone mentioned they wanted to work on heaps, and someone else mentioned they wanted to work on balanced binary search trees. According to the 161 schedule, heaps were last week, hashing
In our first lecture on sets and set theory, we introduced a bunch of new symbols and terminology.
 Guide to and Hi everybody! In our first lecture on sets and set theory, we introduced a bunch of new symbols and terminology. This guide focuses on two of those symbols: and. These symbols represent concepts
Guide to and Hi everybody! In our first lecture on sets and set theory, we introduced a bunch of new symbols and terminology. This guide focuses on two of those symbols: and. These symbols represent concepts
Distributed Algorithms 6.046J, Spring, Nancy Lynch
 Distributed Algorithms 6.046J, Spring, 205 Nancy Lynch What are Distributed Algorithms? Algorithms that run on networked processors, or on multiprocessors that share memory. They solve many kinds of problems:
Distributed Algorithms 6.046J, Spring, 205 Nancy Lynch What are Distributed Algorithms? Algorithms that run on networked processors, or on multiprocessors that share memory. They solve many kinds of problems:
The following content is provided under a Creative Commons license. Your support
 MITOCW Lecture 10 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make a
MITOCW Lecture 10 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make a
MITOCW watch?v=4dj1oguwtem
 MITOCW watch?v=4dj1oguwtem PROFESSOR: So it's time to examine uncountable sets. And that's what we're going to do in this segment. So Cantor's question was, are all sets the same size? And he gives a definitive
MITOCW watch?v=4dj1oguwtem PROFESSOR: So it's time to examine uncountable sets. And that's what we're going to do in this segment. So Cantor's question was, are all sets the same size? And he gives a definitive
Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi
 Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture 20 Priority Queues Today we are going to look at the priority
Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture 20 Priority Queues Today we are going to look at the priority
The following content is provided under a Creative Commons license. Your support
 MITOCW Lecture 2 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make a donation
MITOCW Lecture 2 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make a donation
MITOCW watch?v=kz7jjltq9r4
 MITOCW watch?v=kz7jjltq9r4 PROFESSOR: We're going to look at the most fundamental of all mathematical data types, namely sets, and let's begin with the definitions. So informally, a set is a collection
MITOCW watch?v=kz7jjltq9r4 PROFESSOR: We're going to look at the most fundamental of all mathematical data types, namely sets, and let's begin with the definitions. So informally, a set is a collection
In today s video I'm going show you how you can set up your own online business using marketing and affiliate marketing.
 Hey guys, Diggy here with a summary of part two of the four part free video series. If you haven't watched the first video yet, please do so (https://sixfigureinc.com/intro), before continuing with this
Hey guys, Diggy here with a summary of part two of the four part free video series. If you haven't watched the first video yet, please do so (https://sixfigureinc.com/intro), before continuing with this
GIAN Course on Distributed Network Algorithms. Spanning Tree Constructions
 GIAN Course on Distributed Network Algorithms Spanning Tree Constructions Stefan Schmid @ T-Labs, 2011 Spanning Trees Attactive infrastructure : sparse subgraph ( loop-free backbone ) connecting all nodes.
GIAN Course on Distributed Network Algorithms Spanning Tree Constructions Stefan Schmid @ T-Labs, 2011 Spanning Trees Attactive infrastructure : sparse subgraph ( loop-free backbone ) connecting all nodes.
PROFESSOR: Last time, we took a look at an explicit control evaluator for Lisp, and that bridged the gap between
 MITOCW Lecture 10A [MUSIC PLAYING] PROFESSOR: Last time, we took a look at an explicit control evaluator for Lisp, and that bridged the gap between all these high-level languages like Lisp and the query
MITOCW Lecture 10A [MUSIC PLAYING] PROFESSOR: Last time, we took a look at an explicit control evaluator for Lisp, and that bridged the gap between all these high-level languages like Lisp and the query
CPSC 320 Sample Solution, Playing with Graphs!
 CPSC 320 Sample Solution, Playing with Graphs! September 23, 2017 Today we practice reasoning about graphs by playing with two new terms. These terms/concepts are useful in themselves but not tremendously
CPSC 320 Sample Solution, Playing with Graphs! September 23, 2017 Today we practice reasoning about graphs by playing with two new terms. These terms/concepts are useful in themselves but not tremendously
(Refer Slide Time: 06:01)
 Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture 28 Applications of DFS Today we are going to be talking about
Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture 28 Applications of DFS Today we are going to be talking about
MITOCW watch?v=ninwepprkdq
 MITOCW watch?v=ninwepprkdq The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=ninwepprkdq The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=qota76ga_fy
 MITOCW watch?v=qota76ga_fy The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=qota76ga_fy The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
Introduction to Programming in C Department of Computer Science and Engineering. Lecture No. #17. Loops: Break Statement
 Introduction to Programming in C Department of Computer Science and Engineering Lecture No. #17 Loops: Break Statement (Refer Slide Time: 00:07) In this session we will see one more feature that is present
Introduction to Programming in C Department of Computer Science and Engineering Lecture No. #17 Loops: Break Statement (Refer Slide Time: 00:07) In this session we will see one more feature that is present
Skill 1: Multiplying Polynomials
 CS103 Spring 2018 Mathematical Prerequisites Although CS103 is primarily a math class, this course does not require any higher math as a prerequisite. The most advanced level of mathematics you'll need
CS103 Spring 2018 Mathematical Prerequisites Although CS103 is primarily a math class, this course does not require any higher math as a prerequisite. The most advanced level of mathematics you'll need
MITOCW ocw f99-lec12_300k
 MITOCW ocw-18.06-f99-lec12_300k This is lecture twelve. OK. We've reached twelve lectures. And this one is more than the others about applications of linear algebra. And I'll confess. When I'm giving you
MITOCW ocw-18.06-f99-lec12_300k This is lecture twelve. OK. We've reached twelve lectures. And this one is more than the others about applications of linear algebra. And I'll confess. When I'm giving you
Formal Methods of Software Design, Eric Hehner, segment 1 page 1 out of 5
 Formal Methods of Software Design, Eric Hehner, segment 1 page 1 out of 5 [talking head] Formal Methods of Software Engineering means the use of mathematics as an aid to writing programs. Before we can
Formal Methods of Software Design, Eric Hehner, segment 1 page 1 out of 5 [talking head] Formal Methods of Software Engineering means the use of mathematics as an aid to writing programs. Before we can
MITOCW watch?v=ytpjdnlu9ug
 MITOCW watch?v=ytpjdnlu9ug The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality, educational resources for free.
MITOCW watch?v=ytpjdnlu9ug The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality, educational resources for free.
PROFESSOR: So far in this course we've been talking a lot about data abstraction. And remember the idea is that
 MITOCW Lecture 4B [MUSIC-- "JESU, JOY OF MAN'S DESIRING" BY JOHANN SEBASTIAN BACH] PROFESSOR: So far in this course we've been talking a lot about data abstraction. And remember the idea is that we build
MITOCW Lecture 4B [MUSIC-- "JESU, JOY OF MAN'S DESIRING" BY JOHANN SEBASTIAN BACH] PROFESSOR: So far in this course we've been talking a lot about data abstraction. And remember the idea is that we build
Close Your File Template
 In every sale there is always a scenario where I can t get someone to respond. No matter what I do. I can t get an answer from them. When people stop responding I use the Permission To. This is one of
In every sale there is always a scenario where I can t get someone to respond. No matter what I do. I can t get an answer from them. When people stop responding I use the Permission To. This is one of
(Refer Slide Time: 01.26)
 Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture # 22 Why Sorting? Today we are going to be looking at sorting.
Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture # 22 Why Sorting? Today we are going to be looking at sorting.
PROFESSOR: Well, now that we've given you some power to make independent local state and to model objects,
 MITOCW Lecture 5B PROFESSOR: Well, now that we've given you some power to make independent local state and to model objects, I thought we'd do a bit of programming of a very complicated kind, just to illustrate
MITOCW Lecture 5B PROFESSOR: Well, now that we've given you some power to make independent local state and to model objects, I thought we'd do a bit of programming of a very complicated kind, just to illustrate
MITOCW 2. IV: Consistency, Completeness, and Geometry
 MITOCW 2. IV: Consistency, Completeness, and Geometry The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational
MITOCW 2. IV: Consistency, Completeness, and Geometry The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational
MITOCW watch?v=sdw8_0rdzuw
 MITOCW watch?v=sdw8_0rdzuw PROFESSOR: Directed acyclic graphs are a special class of graphs that really have and warrant a theory of their own. Of course, "directed acyclic graphs" is lot of syllables,
MITOCW watch?v=sdw8_0rdzuw PROFESSOR: Directed acyclic graphs are a special class of graphs that really have and warrant a theory of their own. Of course, "directed acyclic graphs" is lot of syllables,
Binary Search Trees. Carlos Moreno uwaterloo.ca EIT https://ece.uwaterloo.ca/~cmoreno/ece250
 Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 https://ece.uwaterloo.ca/~cmoreno/ece250 Previously, on ECE-250... We discussed trees (the general type) and their implementations. We looked at traversals
Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 https://ece.uwaterloo.ca/~cmoreno/ece250 Previously, on ECE-250... We discussed trees (the general type) and their implementations. We looked at traversals
Week - 04 Lecture - 01 Merge Sort. (Refer Slide Time: 00:02)
 Programming, Data Structures and Algorithms in Python Prof. Madhavan Mukund Department of Computer Science and Engineering Indian Institute of Technology, Madras Week - 04 Lecture - 01 Merge Sort (Refer
Programming, Data Structures and Algorithms in Python Prof. Madhavan Mukund Department of Computer Science and Engineering Indian Institute of Technology, Madras Week - 04 Lecture - 01 Merge Sort (Refer
The following content is provided under a Creative Commons license. Your support
 MITOCW Lecture 11 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make a
MITOCW Lecture 11 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make a
Hi everyone. Starting this week I'm going to make a couple tweaks to how section is run. The first thing is that I'm going to go over all the slides
 Hi everyone. Starting this week I'm going to make a couple tweaks to how section is run. The first thing is that I'm going to go over all the slides for both problems first, and let you guys code them
Hi everyone. Starting this week I'm going to make a couple tweaks to how section is run. The first thing is that I'm going to go over all the slides for both problems first, and let you guys code them
Note: Please use the actual date you accessed this material in your citation.
 MIT OpenCourseWare http://ocw.mit.edu 6.046J Introduction to Algorithms, Fall 2005 Please use the following citation format: Erik Demaine and Charles Leiserson, 6.046J Introduction to Algorithms, Fall
MIT OpenCourseWare http://ocw.mit.edu 6.046J Introduction to Algorithms, Fall 2005 Please use the following citation format: Erik Demaine and Charles Leiserson, 6.046J Introduction to Algorithms, Fall
Note: Please use the actual date you accessed this material in your citation.
 MIT OpenCourseWare http://ocw.mit.edu 18.06 Linear Algebra, Spring 2005 Please use the following citation format: Gilbert Strang, 18.06 Linear Algebra, Spring 2005. (Massachusetts Institute of Technology:
MIT OpenCourseWare http://ocw.mit.edu 18.06 Linear Algebra, Spring 2005 Please use the following citation format: Gilbert Strang, 18.06 Linear Algebra, Spring 2005. (Massachusetts Institute of Technology:
PROFESSOR: Well, yesterday we learned a bit about symbolic manipulation, and we wrote a rather stylized
 MITOCW Lecture 4A PROFESSOR: Well, yesterday we learned a bit about symbolic manipulation, and we wrote a rather stylized program to implement a pile of calculus rule from the calculus book. Here on the
MITOCW Lecture 4A PROFESSOR: Well, yesterday we learned a bit about symbolic manipulation, and we wrote a rather stylized program to implement a pile of calculus rule from the calculus book. Here on the
MITOCW watch?v=hverxup4cfg
 MITOCW watch?v=hverxup4cfg PROFESSOR: We've briefly looked at graph isomorphism in the context of digraphs. And it comes up in even more fundamental way really for simple graphs where the definition is
MITOCW watch?v=hverxup4cfg PROFESSOR: We've briefly looked at graph isomorphism in the context of digraphs. And it comes up in even more fundamental way really for simple graphs where the definition is
9 R1 Get another piece of paper. We re going to have fun keeping track of (inaudible). Um How much time do you have? Are you getting tired?
 Page: 1 of 14 1 R1 And this is tell me what this is? 2 Stephanie x times y plus x times y or hm? 3 R1 What are you thinking? 4 Stephanie I don t know. 5 R1 Tell me what you re thinking. 6 Stephanie Well.
Page: 1 of 14 1 R1 And this is tell me what this is? 2 Stephanie x times y plus x times y or hm? 3 R1 What are you thinking? 4 Stephanie I don t know. 5 R1 Tell me what you re thinking. 6 Stephanie Well.
MITOCW mit-6-00-f08-lec16_300k
 MITOCW mit-6-00-f08-lec16_300k OPERATOR: The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources
MITOCW mit-6-00-f08-lec16_300k OPERATOR: The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources
lecture notes September 2, How to sort?
 .30 lecture notes September 2, 203 How to sort? Lecturer: Michel Goemans The task of sorting. Setup Suppose we have n objects that we need to sort according to some ordering. These could be integers or
.30 lecture notes September 2, 203 How to sort? Lecturer: Michel Goemans The task of sorting. Setup Suppose we have n objects that we need to sort according to some ordering. These could be integers or
How to Improve Your Campaign Conversion Rates
 How to Improve Your Email Campaign Conversion Rates Chris Williams Author of 7 Figure Business Models How to Exponentially Increase Conversion Rates I'm going to teach you my system for optimizing an email
How to Improve Your Email Campaign Conversion Rates Chris Williams Author of 7 Figure Business Models How to Exponentially Increase Conversion Rates I'm going to teach you my system for optimizing an email
MITOCW ocw lec24
 MITOCW ocw-6.046-lec24 -- week of 6.046. Woohoo! The topic of this final week, among our advanced topics, is cache oblivious algorithms. This is a particularly fun area, one dear to my heart because I've
MITOCW ocw-6.046-lec24 -- week of 6.046. Woohoo! The topic of this final week, among our advanced topics, is cache oblivious algorithms. This is a particularly fun area, one dear to my heart because I've
Autodesk University Step Up Your Game AutoCAD P&ID and SQL: Making Data Work for You Skill Level: All Levels
 Autodesk University Step Up Your Game AutoCAD P&ID and SQL: Making Data Work for You Skill Level: All Levels JULIAN CHAVEZ: Good afternoon, ladies and gentlemen. Last class of the last day and everybody's
Autodesk University Step Up Your Game AutoCAD P&ID and SQL: Making Data Work for You Skill Level: All Levels JULIAN CHAVEZ: Good afternoon, ladies and gentlemen. Last class of the last day and everybody's
P1_L3 Operating Systems Security Page 1
 P1_L3 Operating Systems Security Page 1 that is done by the operating system. systems. The operating system plays a really critical role in protecting resources in a computer system. Resources such as
P1_L3 Operating Systems Security Page 1 that is done by the operating system. systems. The operating system plays a really critical role in protecting resources in a computer system. Resources such as
Direct Variations DIRECT AND INVERSE VARIATIONS 19. Name
 DIRECT AND INVERSE VARIATIONS 19 Direct Variations Name Of the many relationships that two variables can have, one category is called a direct variation. Use the description and example of direct variation
DIRECT AND INVERSE VARIATIONS 19 Direct Variations Name Of the many relationships that two variables can have, one category is called a direct variation. Use the description and example of direct variation
Principles of Algorithm Design
 Principles of Algorithm Design When you are trying to design an algorithm or a data structure, it s often hard to see how to accomplish the task. The following techniques can often be useful: 1. Experiment
Principles of Algorithm Design When you are trying to design an algorithm or a data structure, it s often hard to see how to accomplish the task. The following techniques can often be useful: 1. Experiment
Binary Search Trees. Carlos Moreno uwaterloo.ca EIT https://ece.uwaterloo.ca/~cmoreno/ece250
 Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 https://ece.uwaterloo.ca/~cmoreno/ece250 Standard reminder to set phones to silent/vibrate mode, please! Previously, on ECE-250... We discussed trees (the
Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 https://ece.uwaterloo.ca/~cmoreno/ece250 Standard reminder to set phones to silent/vibrate mode, please! Previously, on ECE-250... We discussed trees (the
[key, Left subtree, Right subtree]
![[key, Left subtree, Right subtree] [key, Left subtree, Right subtree]](/thumbs/75/71756070.jpg) Project: Binary Search Trees A binary search tree is a method to organize data, together with operations on these data (i.e., it is a data structure). In particular, the operation that this organization
Project: Binary Search Trees A binary search tree is a method to organize data, together with operations on these data (i.e., it is a data structure). In particular, the operation that this organization
BEGINNER PHP Table of Contents
 Table of Contents 4 5 6 7 8 9 0 Introduction Getting Setup Your first PHP webpage Working with text Talking to the user Comparison & If statements If & Else Cleaning up the game Remembering values Finishing
Table of Contents 4 5 6 7 8 9 0 Introduction Getting Setup Your first PHP webpage Working with text Talking to the user Comparison & If statements If & Else Cleaning up the game Remembering values Finishing
Artificial Intelligence Prof. Deepak Khemani Department of Computer Science and Engineering Indian Institute of Technology, Madras
 Artificial Intelligence Prof. Deepak Khemani Department of Computer Science and Engineering Indian Institute of Technology, Madras (Refer Slide Time: 00:17) Lecture No - 10 Hill Climbing So, we were looking
Artificial Intelligence Prof. Deepak Khemani Department of Computer Science and Engineering Indian Institute of Technology, Madras (Refer Slide Time: 00:17) Lecture No - 10 Hill Climbing So, we were looking
MITOCW MIT6_172_F10_lec10_300k-mp4
 MITOCW MIT6_172_F10_lec10_300k-mp4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for
MITOCW MIT6_172_F10_lec10_300k-mp4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for
Linked Lists. What is a Linked List?
 Linked Lists Along with arrays, linked lists form the basis for pretty much every other data stucture out there. This makes learning and understand linked lists very important. They are also usually the
Linked Lists Along with arrays, linked lists form the basis for pretty much every other data stucture out there. This makes learning and understand linked lists very important. They are also usually the
How To Make 3-50 Times The Profits From Your Traffic
 1 How To Make 3-50 Times The Profits From Your Traffic by Chris Munch of Munchweb.com Copyright Munchweb.com. All Right Reserved. This work cannot be copied, re-published, or re-distributed. No re-sell
1 How To Make 3-50 Times The Profits From Your Traffic by Chris Munch of Munchweb.com Copyright Munchweb.com. All Right Reserved. This work cannot be copied, re-published, or re-distributed. No re-sell
Blog post on updates yesterday and today:
 Beta Bug Prioritization meeting IRC Transcript 12 November 2013 Meeting was held in IRC, on the #devmo channel. Meetings are weekly, every Tuesday at 17:00 UTC (10am PST) ok, everyone, we're ready to start
Beta Bug Prioritization meeting IRC Transcript 12 November 2013 Meeting was held in IRC, on the #devmo channel. Meetings are weekly, every Tuesday at 17:00 UTC (10am PST) ok, everyone, we're ready to start
Programming and Data Structure
 Programming and Data Structure Dr. P.P.Chakraborty Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture # 09 Problem Decomposition by Recursion - II We will
Programming and Data Structure Dr. P.P.Chakraborty Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture # 09 Problem Decomposition by Recursion - II We will
This lesson is part 5 of 5 in a series. You can go to Invoice, Part 1: Free Shipping if you'd like to start from the beginning.
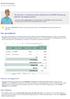 Excel Formulas Invoice, Part 5: Data Validation "Oh, hey. Um we noticed an issue with that new VLOOKUP function you added for the shipping options. If we don't type the exact name of the shipping option,
Excel Formulas Invoice, Part 5: Data Validation "Oh, hey. Um we noticed an issue with that new VLOOKUP function you added for the shipping options. If we don't type the exact name of the shipping option,
MITOCW ocw apr k
 MITOCW ocw-6.033-32123-06apr2005-220k Good afternoon. So we're going to continue our discussion about atomicity and how to achieve atomicity. And today the focus is going to be on implementing this idea
MITOCW ocw-6.033-32123-06apr2005-220k Good afternoon. So we're going to continue our discussion about atomicity and how to achieve atomicity. And today the focus is going to be on implementing this idea
Lesson 3 Transcript: Part 1 of 2 - Tools & Scripting
 Lesson 3 Transcript: Part 1 of 2 - Tools & Scripting Slide 1: Cover Welcome to lesson 3 of the db2 on Campus lecture series. Today we're going to talk about tools and scripting, and this is part 1 of 2
Lesson 3 Transcript: Part 1 of 2 - Tools & Scripting Slide 1: Cover Welcome to lesson 3 of the db2 on Campus lecture series. Today we're going to talk about tools and scripting, and this is part 1 of 2
The Stack, Free Store, and Global Namespace
 Pointers This tutorial is my attempt at clarifying pointers for anyone still confused about them. Pointers are notoriously hard to grasp, so I thought I'd take a shot at explaining them. The more information
Pointers This tutorial is my attempt at clarifying pointers for anyone still confused about them. Pointers are notoriously hard to grasp, so I thought I'd take a shot at explaining them. The more information
Out for Shopping-Understanding Linear Data Structures English
 Out for Shopping-Understanding Linear Data Structures English [MUSIC PLAYING] [MUSIC PLAYING] TANZEELA ALI: Hi, it's Tanzeela Ali. I'm a software engineer, and also a teacher at Superior University, which
Out for Shopping-Understanding Linear Data Structures English [MUSIC PLAYING] [MUSIC PLAYING] TANZEELA ALI: Hi, it's Tanzeela Ali. I'm a software engineer, and also a teacher at Superior University, which
(Refer Slide Time: 02.06)
 Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture 27 Depth First Search (DFS) Today we are going to be talking
Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture 27 Depth First Search (DFS) Today we are going to be talking
Constraint Satisfaction Problems: A Deeper Look
 Constraint Satisfaction Problems: A Deeper Look The last problem set covered the topic of constraint satisfaction problems. CSP search and solution algorithms are directly applicable to a number of AI
Constraint Satisfaction Problems: A Deeper Look The last problem set covered the topic of constraint satisfaction problems. CSP search and solution algorithms are directly applicable to a number of AI
1 Leaffix Scan, Rootfix Scan, Tree Size, and Depth
 Lecture 17 Graph Contraction I: Tree Contraction Parallel and Sequential Data Structures and Algorithms, 15-210 (Spring 2012) Lectured by Kanat Tangwongsan March 20, 2012 In this lecture, we will explore
Lecture 17 Graph Contraction I: Tree Contraction Parallel and Sequential Data Structures and Algorithms, 15-210 (Spring 2012) Lectured by Kanat Tangwongsan March 20, 2012 In this lecture, we will explore
1 GSW Bridging and Switching
 1 Sandwiched between the physical and media access layers of local area networking (such as Ethernet) and the routeing of the Internet layer of the IP protocol, lies the thorny subject of bridges. Bridges
1 Sandwiched between the physical and media access layers of local area networking (such as Ethernet) and the routeing of the Internet layer of the IP protocol, lies the thorny subject of bridges. Bridges
Instructor: Craig Duckett. Lecture 04: Thursday, April 5, Relationships
 Instructor: Craig Duckett Lecture 04: Thursday, April 5, 2018 Relationships 1 Assignment 1 is due NEXT LECTURE 5, Tuesday, April 10 th in StudentTracker by MIDNIGHT MID-TERM EXAM is LECTURE 10, Tuesday,
Instructor: Craig Duckett Lecture 04: Thursday, April 5, 2018 Relationships 1 Assignment 1 is due NEXT LECTURE 5, Tuesday, April 10 th in StudentTracker by MIDNIGHT MID-TERM EXAM is LECTURE 10, Tuesday,
802.1AS Fast Master Clock Selection
 802.1AS Fast Master Clock Selection Moving 802.1AS closer to RSTP Version 2 Norman Finn Cisco Systems 1 Introduction 2 Introduction IEEE 1588 networks that contain transparent clocks and the current draft
802.1AS Fast Master Clock Selection Moving 802.1AS closer to RSTP Version 2 Norman Finn Cisco Systems 1 Introduction 2 Introduction IEEE 1588 networks that contain transparent clocks and the current draft
/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Sorting lower bound and Linear-time sorting Date: 9/19/17
 601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Sorting lower bound and Linear-time sorting Date: 9/19/17 5.1 Introduction You should all know a few ways of sorting in O(n log n)
601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Sorting lower bound and Linear-time sorting Date: 9/19/17 5.1 Introduction You should all know a few ways of sorting in O(n log n)
Who am I? I m a python developer who has been working on OpenStack since I currently work for Aptira, who do OpenStack, SDN, and orchestration
 Who am I? I m a python developer who has been working on OpenStack since 2011. I currently work for Aptira, who do OpenStack, SDN, and orchestration consulting. I m here today to help you learn from my
Who am I? I m a python developer who has been working on OpenStack since 2011. I currently work for Aptira, who do OpenStack, SDN, and orchestration consulting. I m here today to help you learn from my
Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute
 Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute Module 07 Lecture - 38 Divide and Conquer: Closest Pair of Points We now look at another divide and conquer algorithm,
Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute Module 07 Lecture - 38 Divide and Conquer: Closest Pair of Points We now look at another divide and conquer algorithm,
(Refer Slide Time: 05:25)
 Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering IIT Delhi Lecture 30 Applications of DFS in Directed Graphs Today we are going to look at more applications
Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering IIT Delhi Lecture 30 Applications of DFS in Directed Graphs Today we are going to look at more applications
A lot of people make repeated mistakes of not calling their functions and getting errors. Make sure you're calling your functions.
 Handout 2 Functions, Lists, For Loops and Tuples [ ] Functions -- parameters/arguments, "calling" functions, return values, etc. Please make sure you understand this example: def square(x): return x *
Handout 2 Functions, Lists, For Loops and Tuples [ ] Functions -- parameters/arguments, "calling" functions, return values, etc. Please make sure you understand this example: def square(x): return x *
Transcriber(s): Aboelnaga, Eman Verifier(s): Yedman, Madeline Date Transcribed: Fall 2010 Page: 1 of 9
 Page: 1 of 9 0:00 1 R1 The color s not going to show a little bit, but okay. Okay. So, um, a plus b quantity cubed, you said, means Stephanie a plus b times a plus b times a plus b /R1 3 R1 Okay, so you
Page: 1 of 9 0:00 1 R1 The color s not going to show a little bit, but okay. Okay. So, um, a plus b quantity cubed, you said, means Stephanie a plus b times a plus b times a plus b /R1 3 R1 Okay, so you
(Refer Slide Time: 00:51)
 Programming, Data Structures and Algorithms Prof. Shankar Balachandran Department of Computer Science and Engineering Indian Institute Technology, Madras Module 10 E Lecture 24 Content Example: factorial
Programming, Data Structures and Algorithms Prof. Shankar Balachandran Department of Computer Science and Engineering Indian Institute Technology, Madras Module 10 E Lecture 24 Content Example: factorial
Binary Trees
 Binary Trees 4-7-2005 Opening Discussion What did we talk about last class? Do you have any code to show? Do you have any questions about the assignment? What is a Tree? You are all familiar with what
Binary Trees 4-7-2005 Opening Discussion What did we talk about last class? Do you have any code to show? Do you have any questions about the assignment? What is a Tree? You are all familiar with what
Leader Election in Rings
 Leader Election Arvind Krishnamurthy Fall 2003 Leader Election in Rings Under different models: Synchronous vs. asynchronous Anonymous vs. non-anonymous (knowledge of unique id) Knowledge of n (non-uniform)
Leader Election Arvind Krishnamurthy Fall 2003 Leader Election in Rings Under different models: Synchronous vs. asynchronous Anonymous vs. non-anonymous (knowledge of unique id) Knowledge of n (non-uniform)
CS144 Final Review. Dec 4th, 2009 Tom Wiltzius
 CS144 Final Review Dec 4th, 2009 Tom Wiltzius Topics Topics In narrative format! Let's follow Packy as he traverses the Internet! Packy comes into being to help Compy the Computer load a web page Compy
CS144 Final Review Dec 4th, 2009 Tom Wiltzius Topics Topics In narrative format! Let's follow Packy as he traverses the Internet! Packy comes into being to help Compy the Computer load a web page Compy
It Might Be Valid, But It's Still Wrong Paul Maskens and Andy Kramek
 Seite 1 von 5 Issue Date: FoxTalk July 2000 It Might Be Valid, But It's Still Wrong Paul Maskens and Andy Kramek This month, Paul Maskens and Andy Kramek discuss the problems of validating data entry.
Seite 1 von 5 Issue Date: FoxTalk July 2000 It Might Be Valid, But It's Still Wrong Paul Maskens and Andy Kramek This month, Paul Maskens and Andy Kramek discuss the problems of validating data entry.
Algorithm 23 works. Instead of a spanning tree, one can use routing.
 Chapter 5 Shared Objects 5.1 Introduction Assume that there is a common resource (e.g. a common variable or data structure), which different nodes in a network need to access from time to time. If the
Chapter 5 Shared Objects 5.1 Introduction Assume that there is a common resource (e.g. a common variable or data structure), which different nodes in a network need to access from time to time. If the
