Authenticating SMTP Sessions Using Client Certificates
|
|
|
- Gabriel Houston
- 5 years ago
- Views:
Transcription
1 Authenticating SMTP Sessions Using Client Certificates This chapter contains the following sections: Overview of Certificates and SMTP Authentication, on page 1 Checking the Validity of a Client Certificate, on page 3 Authenticating a User Using an LDAP Directory, on page 3 Authenticating an SMTP Connection Over TLS Using a Client Certificate, on page 4 Establishing a TLS Connection from the Appliance, on page 5 Updating a List of Revoked Certificates, on page 5 Overview of Certificates and SMTP Authentication The Security appliance supports the use of client certificates to authenticate SMTP sessions between the Security appliance and users mail clients. The Security appliance can request a client certificate from a user s mail client when the application attempts to connect to the appliance to send messages. When the appliance receives the client certificate, it verifies that the certificate is valid, has not expired, and has not been revoked. If the certificate is valid, the Security appliance allows an SMTP connection from the mail application over TLS. Organizations that require their users to use a Common Access Card (CAC) for their mail clients can use this feature to configure the Security appliance to request a certificate that the CAC and ActivClient middleware application will provide to the appliance. You can configure the Security appliance to require users to provide a certificate when sending mail, but still allow exceptions for certain users. For these users, you can configure the appliance to use the SMTP authentication LDAP query to authenticate the user. Users must configure their mail client to send messages through a secure connection (TLS) and accept a server certificate from the appliance. 1
2 How to Authenticate a User with a Client Certificate How to Authenticate a User with a Client Certificate Table 1: How to Authenticate a User with a Client Certificate Do This Define a certificate query for your LDAP server. Create a certificate-based SMTP authentication profile. Configure a listener to use the certificate SMTP authentication profile. Modify the RELAYED mail flow policy to require TLS, a client certificate, and SMTP authentication. More Info Checking the Validity of a Client Certificate, on page 3 Authenticating an SMTP Connection Over TLS Using a Client Certificate, on page 4 Listening for Connection Requests by Creating a Listener Using Web Interface Establishing a TLS Connection from the Appliance, on page 5 How to Authenticate a User with an SMTP Authentication LDAP Query Table 2: How to Authenticate a User with an SMTP Authenticate LDAP Query Do This Define an SMTP authentication query for your server that uses an allowance query string and Bind for the authentication method. Create an LDAP-based SMTP authentication profile. Configure a listener to use the LDAP SMTP authentication profile. Modify the RELAYED mail flow policy to require TLS and SMTP authentication. More Info Authenticating a User Using an LDAP Directory, on page 3 Configuring AsyncOS for SMTP Authentication If the user is not allowed to use LDAP-based SMTP authentication for their connection, you can select whether the appliance rejects the connection or temporarily allows it while logging all activity. Establishing a TLS Connection from the Appliance, on page 5 How to Authenticate a User with an LDAP SMTP Authentication Query if the Client Certificate is Invalid Table 3: How to Authenticate a User with a Client Certificate or an LDAP SMTP Authentication Query Do This Define an SMTP authentication query for your server that uses an allowance query string and Bind for the authentication method. More Info Authenticating a User Using an LDAP Directory, on page 3 2
3 Checking the Validity of a Client Certificate Do This Define a certificate-based query for your LDAP server. Create a certificate-based SMTP authentication profile Create an LDAP SMTP authentication profile. Configure a listener to use the certificate SMTP authentication profile. 1. Modify the RELAYED mail flow policy to use the following settings: 2. TLS Preferred 3. SMTP authentication required 4. Require TLS for SMTP authentication More Info Checking the Validity of a Client Certificate, on page 3 Authenticating an SMTP Connection Over TLS Using a Client Certificate, on page 4 Configuring AsyncOS for SMTP Authentication Listening for Connection Requests by Creating a Listener Using Web Interface Establishing a TLS Connection from the Appliance, on page 5 Checking the Validity of a Client Certificate The Certificate Authentication LDAP query checks the validity of a client certificate in order to authenticate an SMTP session between the user s mail client and the Security appliance. When creating this query, you select a list of certificate fields for authentication, specify the User ID attribute (the default is uid ), and enter the query string. For example, a query string that searches for the certificate s common name and serial number may look like (&(objectclass-posixaccount)(caccn={cn})(cacserial={sn}). After you have created the query, you can use it in a Certificate SMTP Authentication Profile. This LDAP query supports OpenLDAP, Active Directory, and Oracle Directory. See LDAP Queries for more information on configuring LDAP servers. Select System Administration > LDAP. Create a new LDAP profile. See Creating LDAP Server Profiles to Store Information About the LDAP Server for more information. Check the Certificate Authentication Query checkbox. Enter the query name. Enter the query string to authenticate the user s certificate. For example, (&(objectclass=user)(cn={cn})). Enter the user ID attribute, such as samaccountname. Authenticating a User Using an LDAP Directory The SMTP Authentication LDAP query has an Allowance Query String that allows the Security appliance to check whether the user s mail client is allowed to send mail through the appliance based on the 3
4 Authenticating an SMTP Connection Over TLS Using a Client Certificate user s record in the LDAP directory. This allows users who don t have a client certificate to send mail as long as their record specifies that it s allowed. You can also filter out results based on other attributes. For example, the query string (&(uid={u})( (!(caccn=*))(cacexempt=*)(cacemergency>={t}))) checks to see if any of the following conditions are true for the user: CAC is not issued to the user ( caccn=* ) CAC is exempt ( cacexempt=* ) the time period that a user may temporarily send mail without a CAC expires in the future ( cacemergency>={t} ) See Configuring AsyncOS for SMTP Authenticationfor more information on using the SMTP Authentication query. Select System Administration > LDAP. Define an LDAP profile. See Creating LDAP Server Profiles to Store Information About the LDAP Server for more information. Define an SMTP authentication query for the LDAP profile. Check the SMTP Authentication Query checkbox. Enter the query name. Enter the string to query for the user s ID. For example, (uid={u}). Select LDAP BIND for the authentication method. Step 8 Enter an allowance query string. For example, (&(uid={u})( (!(caccn=*))(cacexempt=*)(cacemergency>={t}))). Step 9 Authenticating an SMTP Connection Over TLS Using a Client Certificate The certificate-based SMTP authentication profile allows the Security appliance to authenticate an SMTP connection over TLS using a client certificate. When creating the profile, you select the Certificate Authentication LDAP query to use for verifying the certificate. You can also specify whether the Security appliance falls back to the SMTP AUTH command to authenticate the user if a client certificate isn t available. For information on authenticating an SMTP connection by using LDAP, see Configuring AsyncOS for SMTP Authentication. Select Network > SMTP Authentication. Click Add Profile. Enter the name for the SMTP authentication profile. Select Certificate for the Profile Type. Click Next. Enter the profile name. 4
5 Establishing a TLS Connection from the Appliance Step 8 Step 9 Select the certificate LDAP query you want to use with this SMTP authentication profile. Note Do not select the option to allow the SMTP AUTH command if a client certificate is not available. Click Finish. Establishing a TLS Connection from the Appliance The Verify Client Certificate option in the RELAYED mail flow policy directs the Security appliance to establish a TLS connection to the user s mail application if the client certificate is valid. If you select this option for the TLS Preferred setting, the appliance still allows a non-tls connection if the user doesn t have a certificate, but rejects a connection if the user has an invalid certificate. For the TLS Required setting, selecting this option requires the user to have a valid certificate in order for the appliance to allow the connection. To authenticate a user s SMTP session with a client certificate, select the following settings: TLS - Required Verify Client Certificate Require SMTP Authentication Note Although SMTP authentication is required, the Security appliance will not use the SMTP authentication LDAP query because it is using certificate authentication. To authenticate a user s SMTP session using the SMTP authentication query instead of a client certificate, select the following settings for the RELAYED mail flow policy: TLS - Required Require SMTP Authentication If you require the Security appliance to ask for a client certificate from certain users while allowing LDAP-based SMTP authentication from others, select the following settings for the RELAYED mail flow policy: TLS - Preferred Require SMTP Authentication Require TLS to Offer SMTP Authentication Updating a List of Revoked Certificates The Security appliance checks a list of revoked certificates (called a Certificate Revocation List) as part of its certificate verification to make sure that the user s certificate hasn t been revoked. You keep an up-to-date version of this list on a server and the Security appliance downloads it on a schedule that you create. Go to Network > CRL Sources. 5
6 Authenticating a User s SMTP Session With a Client Certificate Enable CRL checking for SMTP TLS connections: a) Click Edit Settings under Global Settings. b) (Optional) Select the Global Settings checkbox if you want to select all options: CRL check for inbound SMTP TLS. CRL check for outbound SMTP TLS CRL Check for Web Interface c) Select the checkbox for either CRL check for inbound SMTP TLS, CRL check for outbound SMTP TLS or CRL Check for Web Interface options. d) Submit your change. Step 8 Step 9 0 Click Add CRL Source. Enter a name for the CRL source. Select the file type. This can be either ASN.1 or PEM. Enter the URL for the primary source for the file, including the filename. For example, Optionally, enter the URL for a secondary source in case the appliance cannot contact the primary source. Specify a schedule for downloading the CRL source. Enable the CRL source. Authenticating a User s SMTP Session With a Client Certificate Go to System Administration > LDAP to configure an LDAP server profile.s Define a certificate query for the LDAP profile. a) Enter the query name. b) Choose the certificate fields to authenticate, such as the serial number and common name. c) Enter the query string. For example, (&(caccn={cn})(cacserial={sn})). d) Enter the user ID field, such as uid. Go to Network > SMTP Authentication to configure a Certificate SMTP authentication profile. a) Enter the profile name. b) Select the certificate LDAP query you want to use. c) Do not select the option to allow the SMTP AUTH command if a client certificate is not available. d) Submit your changes. Go to Network > Listeners to configure a listener to use the certificate SMTP authentication profile that you created. Modify the RELAYED mail flow policy to require TLS and a client certificate, as well as require SMTP authentication. Note Although SMTP authentication is required, the Security appliance will not use the SMTP AUTH command because it is using certificate authentication. The Security appliance will require a client certificate from the mail application to authenticate the user. 6
7 Authenticating a User s SMTP Session with the SMTP AUTH Command Authenticating a User s SMTP Session with the SMTP AUTH Command The Security appliance can use the SMTP AUTH command to authenticate a user s SMTP session instead of a client certificate. If you user is not allowed to use SMTP AUTH for their connection, you can select whether the appliance rejects the connection or temporarily allows it while logging all activity. Go to System Administration > LDAP to configure an LDAP server profile. Define an SMTP authentication query for the LDAP profile. a) Enter the query name. b) Enter the query string. For example, (uid={u}). c) Select LDAP Bind for the authentication method. d) Enter an allowance query string. For example, (&(uid={u})( (!(caccn=*))(cacexempt=*)(cacemergency>={t}))). Go to Network > SMTP Authentication to configure an LDAP SMTP authentication profile. a) Enter the profile name. b) Select the SMTP authentication LDAP query you want to use. c) Select the Check with LDAP if user is allowed to use SMTP AUTH Command and choose to monitor and report the user s activity. d) Submit your changes. Go to Network > Listeners to configure a listener to use the LDAP SMTP authentication profile that you created. Modify the RELAYED mail flow policy to require TLS and SMTP authentication. Authenticating a User s SMTP Session with Either a Client Certificate or SMTP AUTH This configuration requires the Security appliance to ask for a client certificate from users with a client certificate while allowing SMTP AUTH for users without one, or who cannot use one for sending . Any attempt to use the SMTP AUTH command by a user who is not allowed will be prohibited. Go to System Administration > LDAP to configure an LDAP server profile. Define an SMTP authentication query for the profile. a) Enter the query name. b) Enter the query string. For example, (uid={u}). c) Select LDAP Bind for the authentication method. d) Enter an allowance query string. For example, (&(uid={u})( (!(caccn=*))(cacexempt=*)(cacemergency>={t}))). 7
8 Authenticating a User s SMTP Session with Either a Client Certificate or SMTP AUTH Define a certificate query for the LDAP profile. a) Enter the query name. b) Choose the client certificate fields to authenticate, such as the serial number and common name. c) Enter the query string. For example, (&(caccn={cn})(cacserial={sn})). d) Enter the user ID field, such as uid. Go to Network > SMTP Authentication to configure an LDAP SMTP authentication profile. a) Enter the profile name. b) Select the SMTP authentication LDAP query you want to use. c) Select the Check with LDAP if user is allowed to use SMTP AUTH Command and choose to reject the connection. d) Enter a custom SMTP AUTH response. For example, 525, Dear user, please use your CAC to send . Configure a Certificate SMTP authentication profile. a) Enter the profile name. b) Select the certificate LDAP query you want to use. c) Select the option to allow the SMTP AUTH command if a client certificate is not available. d) Select your LDAP SMTP authentication profile for the appliance to use if the user does not have a client certificate. Go to Network > Listeners to configure a listener to use the certificate SMTP authentication profile you created. Modify the RELAYED mail flow policy to select the following options: TLS Preferred SMTP authentication required Require TLS for SMTP Authentication Step 8 8
Configuring SSL. SSL Overview CHAPTER
 7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
Comprehensive Setup Guide for TLS on ESA
 Comprehensive Setup Guide for TLS on ESA Contents Introduction Prerequisites Requirements Components Used Background Information Functional Overview and Requirements Bring Your Own Certificate Update a
Comprehensive Setup Guide for TLS on ESA Contents Introduction Prerequisites Requirements Components Used Background Information Functional Overview and Requirements Bring Your Own Certificate Update a
Managing AON Security
 CHAPTER 4 This chapter describes AON functions relating to security, authentication, and authorization. It includes the following topics. Managing Keystores, page 4-1 Configuring Security Properties, page
CHAPTER 4 This chapter describes AON functions relating to security, authentication, and authorization. It includes the following topics. Managing Keystores, page 4-1 Configuring Security Properties, page
Create Decryption Policies to Control HTTPS Traffic
 Create Decryption Policies to Control HTTPS Traffic This chapter contains the following sections: Overview of Create Decryption Policies to Control HTTPS Traffic, page 1 Managing HTTPS Traffic through
Create Decryption Policies to Control HTTPS Traffic This chapter contains the following sections: Overview of Create Decryption Policies to Control HTTPS Traffic, page 1 Managing HTTPS Traffic through
Configuring SSL. SSL Overview CHAPTER
 CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
Integrating With LDAP
 This chapter contains the following sections: Overview, on page 1 Configuring LDAP to Work with the Spam Quarantine, on page 1 Creating the LDAP Server Profile, on page 2 Configuring LDAP Queries, on page
This chapter contains the following sections: Overview, on page 1 Configuring LDAP to Work with the Spam Quarantine, on page 1 Creating the LDAP Server Profile, on page 2 Configuring LDAP Queries, on page
Cisco Encryption
 This chapter contains the following sections: Overview of, page 1 How to Encrypt Messages with a Local Key Server, page 2 Encrypting Messages using the Email Security Appliance, page 3 Determining Which
This chapter contains the following sections: Overview of, page 1 How to Encrypt Messages with a Local Key Server, page 2 Encrypting Messages using the Email Security Appliance, page 3 Determining Which
FIPS Management. FIPS Management Overview. Configuration Changes in FIPS Mode
 This chapter contains the following sections: Overview, on page 1 Configuration Changes in FIPS Mode, on page 1 Switching the Appliance to FIPS Mode, on page 2 Encrypting Sensitive Data in FIPS Mode, on
This chapter contains the following sections: Overview, on page 1 Configuration Changes in FIPS Mode, on page 1 Switching the Appliance to FIPS Mode, on page 2 Encrypting Sensitive Data in FIPS Mode, on
Validating Recipients Using an SMTP Server
 This chapter contains the following sections: Overview of SMTP Call-Ahead Recipient Validation, page 1 SMTP Call-Ahead Recipient Validation Workflow, page 1 How to Validate Recipients Using an External
This chapter contains the following sections: Overview of SMTP Call-Ahead Recipient Validation, page 1 SMTP Call-Ahead Recipient Validation Workflow, page 1 How to Validate Recipients Using an External
ForeScout CounterACT. Configuration Guide. Version 6.3
 ForeScout CounterACT Authentication Module: User Directory Plugin Version 6.3 Table of Contents About the User Directory Plugin... 4 Endpoint User Details... 4 Endpoint Authentication... 5 User Directory
ForeScout CounterACT Authentication Module: User Directory Plugin Version 6.3 Table of Contents About the User Directory Plugin... 4 Endpoint User Details... 4 Endpoint Authentication... 5 User Directory
Managing Certificates
 CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
Cisco ISE Ports Reference
 Cisco ISE Infrastructure Cisco ISE Infrastructure, on page 1 Cisco ISE Administration Node Ports, on page 2 Cisco ISE Monitoring Node Ports, on page 4 Cisco ISE Policy Service Node Ports, on page 6 Cisco
Cisco ISE Infrastructure Cisco ISE Infrastructure, on page 1 Cisco ISE Administration Node Ports, on page 2 Cisco ISE Monitoring Node Ports, on page 4 Cisco ISE Policy Service Node Ports, on page 6 Cisco
ACCURATE STUDY GUIDES, HIGH PASSING RATE! Question & Answer. Dump Step. provides update free of charge in one year!
 DUMP STEP Question & Answer ACCURATE STUDY GUIDES, HIGH PASSING RATE! Dump Step provides update free of charge in one year! http://www.dumpstep.com Exam : 650-156 Title : ISPES Cisco IronPort Security
DUMP STEP Question & Answer ACCURATE STUDY GUIDES, HIGH PASSING RATE! Dump Step provides update free of charge in one year! http://www.dumpstep.com Exam : 650-156 Title : ISPES Cisco IronPort Security
LDAP Queries. Overview of LDAP Queries. Understanding LDAP Queries
 This chapter contains the following sections: Overview of, on page 1 Working with, on page 10 Using Acceptance Queries For Recipient Validation, on page 17 Using Routing Queries to Send Mail to Multiple
This chapter contains the following sections: Overview of, on page 1 Working with, on page 10 Using Acceptance Queries For Recipient Validation, on page 17 Using Routing Queries to Send Mail to Multiple
LDAP Queries. Overview of LDAP Queries. This chapter contains the following sections:
 This chapter contains the following sections: Overview of, page 1 Working with, page 11 Using Acceptance Queries For Recipient Validation, page 18 Using Routing Queries to Send Mail to Multiple Target
This chapter contains the following sections: Overview of, page 1 Working with, page 11 Using Acceptance Queries For Recipient Validation, page 18 Using Routing Queries to Send Mail to Multiple Target
Two factor authentication for Check Point appliances
 Two factor authentication for Check Point appliances logintc.com/docs/connectors/check-point.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged to run within
Two factor authentication for Check Point appliances logintc.com/docs/connectors/check-point.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged to run within
How to Configure Esva for Office365
 How to Configure Esva for Office365 This article addresses configuring Office 365 with Libra Esva as your inbound and/or outbound mail gateway. You can specify the appliance as an inbound mail gateway
How to Configure Esva for Office365 This article addresses configuring Office 365 with Libra Esva as your inbound and/or outbound mail gateway. You can specify the appliance as an inbound mail gateway
User Accounts for Management Access
 The Firepower Management Center and managed devices include a default admin account for management access. This chapter discusses how to create custom user accounts for supported models. See Logging into
The Firepower Management Center and managed devices include a default admin account for management access. This chapter discusses how to create custom user accounts for supported models. See Logging into
Configuring Gmail (G Suite) with Cisco Cloud Security
 Configuring Gmail (G Suite) with Cisco Cloud Email Security This document covers the steps required to integrate Cisco Cloud Email Security with Google G Suite for inbound and outbound email delivery.
Configuring Gmail (G Suite) with Cisco Cloud Email Security This document covers the steps required to integrate Cisco Cloud Email Security with Google G Suite for inbound and outbound email delivery.
Network Communication Requirements for SecureAuth IdP
 Network Communication Requirements for SecureAuth IdP 9.1-9.2 Introduction This document lists the firewall ports that must be opened to ensure network connectivity of the SecureAuth IdP v9.1 - v9.2 appliance.
Network Communication Requirements for SecureAuth IdP 9.1-9.2 Introduction This document lists the firewall ports that must be opened to ensure network connectivity of the SecureAuth IdP v9.1 - v9.2 appliance.
Forescout. Server and Guest Management Configuration Guide. Version 6.4
 Forescout Authentication Module: User Directory Plugin Server and Guest Management Configuration Guide Version 6.4 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134
Forescout Authentication Module: User Directory Plugin Server and Guest Management Configuration Guide Version 6.4 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134
ACS 5.x: LDAP Server Configuration Example
 ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT
 INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT ESCB-PKI REGISTRATION AUTHORITY APPLICATION MOST COMMON ERRORS VERSION 1.2 ECB-PUBLIC 15-November-2012 ESCB-PKI - Common errors v.1.2.docx Page 2 of 20
INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT ESCB-PKI REGISTRATION AUTHORITY APPLICATION MOST COMMON ERRORS VERSION 1.2 ECB-PUBLIC 15-November-2012 ESCB-PKI - Common errors v.1.2.docx Page 2 of 20
ExtraHop 7.0 ExtraHop Trace Admin UI Guide
 ExtraHop 7.0 ExtraHop Trace Admin UI Guide 2018 ExtraHop Networks, Inc. All rights reserved. This manual in whole or in part, may not be reproduced, translated, or reduced to any machinereadable form without
ExtraHop 7.0 ExtraHop Trace Admin UI Guide 2018 ExtraHop Networks, Inc. All rights reserved. This manual in whole or in part, may not be reproduced, translated, or reduced to any machinereadable form without
Microsoft Dynamics CRM Integration with Bomgar Remote Support
 Microsoft Dynamics CRM Integration with Bomgar Remote Support 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown
Microsoft Dynamics CRM Integration with Bomgar Remote Support 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown
Using Centralized Security Reporting
 This chapter contains the following sections: Centralized Email Reporting Overview, on page 1 Setting Up Centralized Email Reporting, on page 2 Working with Email Report Data, on page 4 Understanding the
This chapter contains the following sections: Centralized Email Reporting Overview, on page 1 Setting Up Centralized Email Reporting, on page 2 Working with Email Report Data, on page 4 Understanding the
Accepting or Rejecting Connections Based on Domain Name or Recipient Address
 Accepting or Rejecting Connections Based on Domain Name or Recipient Address This chapter contains the following sections: Overview of Accepting or Rejecting Connections Based on the Recipient s Address,
Accepting or Rejecting Connections Based on Domain Name or Recipient Address This chapter contains the following sections: Overview of Accepting or Rejecting Connections Based on the Recipient s Address,
Technical Note: SecureSync LDAP AND RADIUS AUTHENTICATION WITH A SPECTRACOM SECURESYNC
 Technical Note: SecureSync LDAP AND RADIUS AUTHENTICATION WITH A SPECTRACOM SECURESYNC Purpose: The purpose of this document is to provide supplemental information regarding Radius and LDAP authentication
Technical Note: SecureSync LDAP AND RADIUS AUTHENTICATION WITH A SPECTRACOM SECURESYNC Purpose: The purpose of this document is to provide supplemental information regarding Radius and LDAP authentication
Deploying VMware Identity Manager in the DMZ. JULY 2018 VMware Identity Manager 3.2
 Deploying VMware Identity Manager in the DMZ JULY 2018 VMware Identity Manager 3.2 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Deploying VMware Identity Manager in the DMZ JULY 2018 VMware Identity Manager 3.2 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Managing External Identity Sources
 CHAPTER 5 The Cisco Identity Services Engine (Cisco ISE) integrates with external identity sources to validate credentials in user authentication functions, and to retrieve group information and other
CHAPTER 5 The Cisco Identity Services Engine (Cisco ISE) integrates with external identity sources to validate credentials in user authentication functions, and to retrieve group information and other
CounterACT User Directory Plugin
 Version 6.1.2 and Above Table of Contents About the User Directory Plugin... 3 Endpoint User Details... 3 Verify Endpoint Authentication... 3 User Directory Inventory... 4 HTTP Login Action... 5 HTTP Sign
Version 6.1.2 and Above Table of Contents About the User Directory Plugin... 3 Endpoint User Details... 3 Verify Endpoint Authentication... 3 User Directory Inventory... 4 HTTP Login Action... 5 HTTP Sign
Microsoft Dynamics CRM Integration with Remote Support
 Microsoft Dynamics CRM Integration with Remote Support 2003-2018 BeyondTrust, Inc. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust, Inc. Other trademarks are the property
Microsoft Dynamics CRM Integration with Remote Support 2003-2018 BeyondTrust, Inc. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust, Inc. Other trademarks are the property
Cisco ISE Ports Reference
 Cisco ISE Infrastructure Cisco ISE Infrastructure, on page 1 Cisco ISE Administration Node Ports, on page 2 Cisco ISE Monitoring Node Ports, on page 4 Cisco ISE Policy Service Node Ports, on page 5 Inline
Cisco ISE Infrastructure Cisco ISE Infrastructure, on page 1 Cisco ISE Administration Node Ports, on page 2 Cisco ISE Monitoring Node Ports, on page 4 Cisco ISE Policy Service Node Ports, on page 5 Inline
CSE 565 Computer Security Fall 2018
 CSE 565 Computer Security Fall 2018 Lecture 11: Public Key Infrastructure Department of Computer Science and Engineering University at Buffalo 1 Lecture Outline Public key infrastructure Certificates Trust
CSE 565 Computer Security Fall 2018 Lecture 11: Public Key Infrastructure Department of Computer Science and Engineering University at Buffalo 1 Lecture Outline Public key infrastructure Certificates Trust
How to Set Up External CA VPN Certificates
 To configure a client-to-site, or site-to-site VPN using s created by External CA, you must create the following VPN s for the VPN service to be able to authenticate Before you begin Use an external CA
To configure a client-to-site, or site-to-site VPN using s created by External CA, you must create the following VPN s for the VPN service to be able to authenticate Before you begin Use an external CA
Coding & Information Theory Lab.
 통합인증시스템설계및구현 연세대학교전기 전자공학과정연식, 송홍엽 Coding & Information Theory Lab. Introduction Previous Works Contents Design and Implementation of Public-Key Infrastructure Design and Implementation of Single Sign-On
통합인증시스템설계및구현 연세대학교전기 전자공학과정연식, 송홍엽 Coding & Information Theory Lab. Introduction Previous Works Contents Design and Implementation of Public-Key Infrastructure Design and Implementation of Single Sign-On
Azure MFA Integration with NetScaler
 Azure MFA Integration with NetScaler This guide focuses on describing the configuration required for integrating Azure MFA (Multi-Factor Authentication) with NetScaler. Citrix.com 1 NetScaler is a world-class
Azure MFA Integration with NetScaler This guide focuses on describing the configuration required for integrating Azure MFA (Multi-Factor Authentication) with NetScaler. Citrix.com 1 NetScaler is a world-class
Pulse Secure Policy Secure
 Policy Secure RSA SecurID Ready Implementation Guide Last Modified: November 19, 2014 Partner Information Product Information Partner Name Pulse Secure Web Site http://www.pulsesecure.net/ Product Name
Policy Secure RSA SecurID Ready Implementation Guide Last Modified: November 19, 2014 Partner Information Product Information Partner Name Pulse Secure Web Site http://www.pulsesecure.net/ Product Name
Important Information
 May 2014 Important Information The following information applies to Proofpoint Essentials US1 data center only. User Interface Access https://usproofpointessentials.com MX Records mx1-usppe-hosted.com
May 2014 Important Information The following information applies to Proofpoint Essentials US1 data center only. User Interface Access https://usproofpointessentials.com MX Records mx1-usppe-hosted.com
Two factor authentication for Citrix NetScaler
 Two factor authentication for Citrix NetScaler logintc.com/docs/connectors/citrix-netscaler.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged to run within
Two factor authentication for Citrix NetScaler logintc.com/docs/connectors/citrix-netscaler.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged to run within
VMware Enterprise Systems Connector Guide for SaaS Customers ACC Installation and Integration for SaaS
 Connector Guide for SaaS Customers ACC Installation and Integration for SaaS Workspace ONE UEM v9.5 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard
Connector Guide for SaaS Customers ACC Installation and Integration for SaaS Workspace ONE UEM v9.5 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard
Novell OpenLDAP Configuration
 Novell OpenLDAP Configuration To access the GoPrint Novell e-directory LDAP Connector configuration screen navigate to: Accounts Authentication Connectors GoPrint provides two connector options, Standard
Novell OpenLDAP Configuration To access the GoPrint Novell e-directory LDAP Connector configuration screen navigate to: Accounts Authentication Connectors GoPrint provides two connector options, Standard
Version SurfControl RiskFilter - Administrator's Guide
 Version 5.2.4 SurfControl RiskFilter - E-mail Administrator's Guide CONTENTS Notices...i FINDING YOUR WAY AROUND...1 How RiskFilter works...2 Managing your messages with RiskFilter...2 Load balancing with
Version 5.2.4 SurfControl RiskFilter - E-mail Administrator's Guide CONTENTS Notices...i FINDING YOUR WAY AROUND...1 How RiskFilter works...2 Managing your messages with RiskFilter...2 Load balancing with
Defining Which Hosts Are Allowed to Connect Using the Host Access Table
 Defining Which Hosts Are Allowed to Connect Using the Host Access Table This chapter contains the following sections: Overview of Defining Which Hosts Are Allowed to Connect, page 1 Defining Remote Hosts
Defining Which Hosts Are Allowed to Connect Using the Host Access Table This chapter contains the following sections: Overview of Defining Which Hosts Are Allowed to Connect, page 1 Defining Remote Hosts
Validation Policy r tra is g e R ANF AC MALTA, LTD
 Maltese Registrar of Companies Number C75870 and VAT number MT ANF AC MALTA, LTD B2 Industry Street, Qormi, QRM 3000 Malta Telephone: (+356) 2299 3100 Fax:(+356) 2299 3101 Web: www.anfacmalta.com Security
Maltese Registrar of Companies Number C75870 and VAT number MT ANF AC MALTA, LTD B2 Industry Street, Qormi, QRM 3000 Malta Telephone: (+356) 2299 3100 Fax:(+356) 2299 3101 Web: www.anfacmalta.com Security
BIG-IP Access Policy Manager : Authentication and Single Sign-On. Version 13.1
 BIG-IP Access Policy Manager : Authentication and Single Sign-On Version 13.1 Table of Contents Table of Contents Authentication Concepts... 15 About AAA server support... 15 About AAA high availability
BIG-IP Access Policy Manager : Authentication and Single Sign-On Version 13.1 Table of Contents Table of Contents Authentication Concepts... 15 About AAA server support... 15 About AAA high availability
Elements of Cryptography and Computer and Network Security Computer Science 134 (COMPSCI 134) Fall 2016 Instructor: Karim ElDefrawy
 Elements of Cryptography and Computer and Network Security Computer Science 134 (COMPSCI 134) Fall 2016 Instructor: Karim ElDefrawy Homework 3 Due: Monday, 11/28/2016 at 11:55pm PT Solution: Will be posted
Elements of Cryptography and Computer and Network Security Computer Science 134 (COMPSCI 134) Fall 2016 Instructor: Karim ElDefrawy Homework 3 Due: Monday, 11/28/2016 at 11:55pm PT Solution: Will be posted
Displaying SSL Configuration Information and Statistics
 CHAPTER 7 Displaying SSL Configuration Information and Statistics This chapter describes the show commands available for displaying CSS SSL configuration information and statistics and an explanation of
CHAPTER 7 Displaying SSL Configuration Information and Statistics This chapter describes the show commands available for displaying CSS SSL configuration information and statistics and an explanation of
Defining Which Hosts Are Allowed to Connect Using the Host Access Table
 Defining Which Hosts Are Allowed to Connect Using the Host Access Table This chapter contains the following sections: Overview of Defining Which Hosts Are Allowed to Connect, on page 1 Defining Remote
Defining Which Hosts Are Allowed to Connect Using the Host Access Table This chapter contains the following sections: Overview of Defining Which Hosts Are Allowed to Connect, on page 1 Defining Remote
How to Configure SSL Interception in the Firewall
 Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted traffic to allow Application Control features (such as the Virus Scanner, ATD, URL Filter, Safe Search,
Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted traffic to allow Application Control features (such as the Virus Scanner, ATD, URL Filter, Safe Search,
provides several new features and enhancements, and resolves several issues reported by WatchGuard customers.
 WatchGuard XCS v9.2 Update 5 Release Notes WatchGuard XCS Build 130322 Revision Date March 28, 2013 Introduction WatchGuard is pleased to announce the release of WatchGuard XCS v9.2 Update 5. This update
WatchGuard XCS v9.2 Update 5 Release Notes WatchGuard XCS Build 130322 Revision Date March 28, 2013 Introduction WatchGuard is pleased to announce the release of WatchGuard XCS v9.2 Update 5. This update
The LDAP plugin for Fuel documentation
 The LDAP plugin for Fuel documentation Release 3.0-3.0.0-1 Mirantis Inc. July 07, 2016 CONTENTS 1 Plugin Guide 1 1.1 LDAP plugin for Fuel.......................................... 1 1.2 Release notes /
The LDAP plugin for Fuel documentation Release 3.0-3.0.0-1 Mirantis Inc. July 07, 2016 CONTENTS 1 Plugin Guide 1 1.1 LDAP plugin for Fuel.......................................... 1 1.2 Release notes /
Technical Trust Policy
 Technical Trust Policy Version 1.2 Last Updated: May 20, 2016 Introduction Carequality creates a community of trusted exchange partners who rely on each organization s adherence to the terms of the Carequality
Technical Trust Policy Version 1.2 Last Updated: May 20, 2016 Introduction Carequality creates a community of trusted exchange partners who rely on each organization s adherence to the terms of the Carequality
Ten Risks of PKI : What You re not Being Told about Public Key Infrastructure By Carl Ellison and Bruce Schneier
 Presented by Joshua Schiffman & Archana Viswanath Ten Risks of PKI : What You re not Being Told about Public Key Infrastructure By Carl Ellison and Bruce Schneier Trust Models Rooted Trust Model! In a
Presented by Joshua Schiffman & Archana Viswanath Ten Risks of PKI : What You re not Being Told about Public Key Infrastructure By Carl Ellison and Bruce Schneier Trust Models Rooted Trust Model! In a
Exinda How To Guide: SSL Acceleration. Exinda ExOS Version Exinda Networks, Inc.
 Exinda How To Guide: SSL Acceleration Exinda ExOS Version 7.4.3 2 Copyright All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or mechanical,
Exinda How To Guide: SSL Acceleration Exinda ExOS Version 7.4.3 2 Copyright All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or mechanical,
Sophos UTM Web Application Firewall For: Microsoft Exchange Services
 How to configure: Sophos UTM Web Application Firewall For: Microsoft Exchange Services This guide explains how to configure your Sophos UTM 9.3+ to allow access to the relevant Microsoft Exchange services
How to configure: Sophos UTM Web Application Firewall For: Microsoft Exchange Services This guide explains how to configure your Sophos UTM 9.3+ to allow access to the relevant Microsoft Exchange services
Realms and Identity Policies
 The following topics describe realms and identity policies: About, page 1 Create a Realm, page 8 Create an Identity Policy, page 14 Create an Identity Rule, page 15 Manage a Realm, page 17 Manage an Identity
The following topics describe realms and identity policies: About, page 1 Create a Realm, page 8 Create an Identity Policy, page 14 Create an Identity Rule, page 15 Manage a Realm, page 17 Manage an Identity
Barracuda Firewall Release Notes 6.6.X
 Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
StorageGRID Webscale 11.0 Tenant Administrator Guide
 StorageGRID Webscale 11.0 Tenant Administrator Guide January 2018 215-12403_B0 doccomments@netapp.com Table of Contents 3 Contents Administering a StorageGRID Webscale tenant account... 5 Understanding
StorageGRID Webscale 11.0 Tenant Administrator Guide January 2018 215-12403_B0 doccomments@netapp.com Table of Contents 3 Contents Administering a StorageGRID Webscale tenant account... 5 Understanding
Elements of Cryptography and Computer and Network Security Computer Science 134 (COMPSCI 134) Fall 2016 Instructor: Karim ElDefrawy
 Elements of Cryptography and Computer and Network Security Computer Science 134 (COMPSCI 134) Fall 2016 Instructor: Karim ElDefrawy Homework 3 Due: Monday, 11/28/2016 at 11:55pm PT Solution: Will be posted
Elements of Cryptography and Computer and Network Security Computer Science 134 (COMPSCI 134) Fall 2016 Instructor: Karim ElDefrawy Homework 3 Due: Monday, 11/28/2016 at 11:55pm PT Solution: Will be posted
Legacy of Heartbleed: MITM and Revoked Certificates. Alexey Busygin NeoBIT
 Legacy of Heartbleed: MITM and Revoked Certificates Alexey Busygin busygin@neobit.ru NeoBIT Notable Private Key Leaks 2010 DigiCert Sdn Bhd. issued certificates with 512-bit keys 2012 Trustwave issued
Legacy of Heartbleed: MITM and Revoked Certificates Alexey Busygin busygin@neobit.ru NeoBIT Notable Private Key Leaks 2010 DigiCert Sdn Bhd. issued certificates with 512-bit keys 2012 Trustwave issued
Two factor authentication for SSH using PAM RADIUS module
 Two factor authentication for SSH using PAM RADIUS module sandbox-logintc.com/docs/connectors/ssh.html Introduction LoginTC makes it easy for administrators to add multi-factor to SSH on their Unix systems.
Two factor authentication for SSH using PAM RADIUS module sandbox-logintc.com/docs/connectors/ssh.html Introduction LoginTC makes it easy for administrators to add multi-factor to SSH on their Unix systems.
JIRA Integration Guide
 JIRA Integration Guide 2018 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their respective
JIRA Integration Guide 2018 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their respective
Two factor authentication for Fortinet SSL VPN
 Two factor authentication for Fortinet SSL VPN logintc.com/docs/connectors/fortinet.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged to run within your
Two factor authentication for Fortinet SSL VPN logintc.com/docs/connectors/fortinet.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged to run within your
akkadian Global Directory 3.0 System Administration Guide
 akkadian Global Directory 3.0 System Administration Guide Updated July 19 th, 2016 Copyright and Trademarks: I. Copyright: This website and its content is copyright 2014 Akkadian Labs. All rights reserved.
akkadian Global Directory 3.0 System Administration Guide Updated July 19 th, 2016 Copyright and Trademarks: I. Copyright: This website and its content is copyright 2014 Akkadian Labs. All rights reserved.
ASA AnyConnect Double Authentication with Certificate Validation, Mapping, and Pre Fill Configuration Guide
 ASA AnyConnect Double Authentication with Certificate Validation, Mapping, and Pre Fill Configuration Guide Document ID: 116111 Contributed by Michal Garcarz, Cisco TAC Engineer. Jun 13, 2013 Contents
ASA AnyConnect Double Authentication with Certificate Validation, Mapping, and Pre Fill Configuration Guide Document ID: 116111 Contributed by Michal Garcarz, Cisco TAC Engineer. Jun 13, 2013 Contents
Configuring Secure Socket Layer HTTP
 Finding Feature Information, page 1 Information about Secure Sockets Layer (SSL) HTTP, page 1 How to Configure Secure HTTP Servers and Clients, page 4 Monitoring Secure HTTP Server and Client Status, page
Finding Feature Information, page 1 Information about Secure Sockets Layer (SSL) HTTP, page 1 How to Configure Secure HTTP Servers and Clients, page 4 Monitoring Secure HTTP Server and Client Status, page
VSP16. Venafi Security Professional 16 Course 04 April 2016
 VSP16 Venafi Security Professional 16 Course 04 April 2016 VSP16 Prerequisites Course intended for: IT Professionals who interact with Digital Certificates Also appropriate for: Enterprise Security Officers
VSP16 Venafi Security Professional 16 Course 04 April 2016 VSP16 Prerequisites Course intended for: IT Professionals who interact with Digital Certificates Also appropriate for: Enterprise Security Officers
Realms and Identity Policies
 The following topics describe realms and identity policies: About, page 1 Create a Realm, page 8 Create an Identity Policy, page 15 Create an Identity Rule, page 15 Manage a Realm, page 20 Manage an Identity
The following topics describe realms and identity policies: About, page 1 Create a Realm, page 8 Create an Identity Policy, page 15 Create an Identity Rule, page 15 Manage a Realm, page 20 Manage an Identity
Installing and Configuring VMware Identity Manager Connector (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.
 Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Cisco ISE Ports Reference
 Cisco ISE Infrastructure, page 1 Cisco ISE Administration Node Ports, page 2 Cisco ISE Monitoring Node Ports, page 3 Cisco ISE Policy Service Node Ports, page 4 Cisco ISE pxgrid Service Ports, page 8 OCSP
Cisco ISE Infrastructure, page 1 Cisco ISE Administration Node Ports, page 2 Cisco ISE Monitoring Node Ports, page 3 Cisco ISE Policy Service Node Ports, page 4 Cisco ISE pxgrid Service Ports, page 8 OCSP
Deploying VMware Identity Manager in the DMZ. SEPT 2018 VMware Identity Manager 3.3
 Deploying VMware Identity Manager in the DMZ SEPT 2018 VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Deploying VMware Identity Manager in the DMZ SEPT 2018 VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
User ID Service. How to integrate Forcepoint User ID Service with other Forcepoint products 1.1. Revision A
 User ID Service How to integrate Forcepoint User ID Service with other Forcepoint products 1.1 Revision A Contents Introduction on page 2 Requirements on page 3 Installation overview on page 4 Obtain installation
User ID Service How to integrate Forcepoint User ID Service with other Forcepoint products 1.1 Revision A Contents Introduction on page 2 Requirements on page 3 Installation overview on page 4 Obtain installation
Cisco ISE Ports Reference
 Cisco ISE Infrastructure, page 1 Cisco ISE Administration Node Ports, page 2 Cisco ISE Monitoring Node Ports, page 4 Cisco ISE Policy Service Node Ports, page 5 Cisco ISE pxgrid Service Ports, page 10
Cisco ISE Infrastructure, page 1 Cisco ISE Administration Node Ports, page 2 Cisco ISE Monitoring Node Ports, page 4 Cisco ISE Policy Service Node Ports, page 5 Cisco ISE pxgrid Service Ports, page 10
Citrix Exam 1Y0-351 Citrix NetScaler 10.5 Essentials and Networking Version: 7.0 [ Total Questions: 178 ]
![Citrix Exam 1Y0-351 Citrix NetScaler 10.5 Essentials and Networking Version: 7.0 [ Total Questions: 178 ] Citrix Exam 1Y0-351 Citrix NetScaler 10.5 Essentials and Networking Version: 7.0 [ Total Questions: 178 ]](/thumbs/77/76355722.jpg) s@lm@n Citrix Exam 1Y0-351 Citrix NetScaler 10.5 Essentials and Networking Version: 7.0 [ Total Questions: 178 ] Question No : 1 A network engineer notes that a high availability pair (HA) is NOT synchronizing
s@lm@n Citrix Exam 1Y0-351 Citrix NetScaler 10.5 Essentials and Networking Version: 7.0 [ Total Questions: 178 ] Question No : 1 A network engineer notes that a high availability pair (HA) is NOT synchronizing
Two factor authentication for F5 BIG-IP APM
 Two factor authentication for F5 BIG-IP APM logintc.com/docs/connectors/f5.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged to run within your corporate
Two factor authentication for F5 BIG-IP APM logintc.com/docs/connectors/f5.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged to run within your corporate
Two factor authentication for OpenVPN Access Server
 Two factor authentication for OpenVPN Access Server logintc.com/docs/connectors/openvpn-as.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged to run within
Two factor authentication for OpenVPN Access Server logintc.com/docs/connectors/openvpn-as.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged to run within
RSA Identity Governance and Lifecycle Collector Data Sheet For Open LDAP
 RSA Identity Governance and Lifecycle Collector Data Sheet For Open LDAP Version 1.1 July 2017 Table of Contents RSA Identity Governance and Lifecycle Collector Datasheet for Open LDAP Purpose... 4 Supported
RSA Identity Governance and Lifecycle Collector Data Sheet For Open LDAP Version 1.1 July 2017 Table of Contents RSA Identity Governance and Lifecycle Collector Datasheet for Open LDAP Purpose... 4 Supported
Two factor authentication for SonicWALL SRA Secure Remote Access
 Two factor authentication for SonicWALL SRA Secure Remote Access logintc.com/docs/connectors/sonicwall-sra.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged
Two factor authentication for SonicWALL SRA Secure Remote Access logintc.com/docs/connectors/sonicwall-sra.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged
Entrust Connector (econnector) Venafi Trust Protection Platform
 Entrust Connector (econnector) For Venafi Trust Protection Platform Installation and Configuration Guide Version 1.0.5 DATE: 17 November 2017 VERSION: 1.0.5 Copyright 2017. All rights reserved Table of
Entrust Connector (econnector) For Venafi Trust Protection Platform Installation and Configuration Guide Version 1.0.5 DATE: 17 November 2017 VERSION: 1.0.5 Copyright 2017. All rights reserved Table of
PKI Services. Text PKI Definition. PKI Definition #1. Public Key Infrastructure. What Does A PKI Do? Public Key Infrastructures
 Public Key Infrastructures Public Key Infrastructure Definition and Description Functions Components Certificates 1 2 PKI Services Security Between Strangers Encryption Integrity Non-repudiation Key establishment
Public Key Infrastructures Public Key Infrastructure Definition and Description Functions Components Certificates 1 2 PKI Services Security Between Strangers Encryption Integrity Non-repudiation Key establishment
Troubleshooting Grid authentication from the client side
 Troubleshooting Grid authentication from the client side By Adriaan van der Zee RP1 presentation 2009-02-04 Contents The Grid @NIKHEF The project Grid components and interactions X.509 certificates, proxies
Troubleshooting Grid authentication from the client side By Adriaan van der Zee RP1 presentation 2009-02-04 Contents The Grid @NIKHEF The project Grid components and interactions X.509 certificates, proxies
CertAgent. Certificate Authority Guide
 CertAgent Certificate Authority Guide Version 6.0.0 December 12, 2013 Information in this document is subject to change without notice and does not represent a commitment on the part of Information Security
CertAgent Certificate Authority Guide Version 6.0.0 December 12, 2013 Information in this document is subject to change without notice and does not represent a commitment on the part of Information Security
Integrate HEAT Software with Bomgar Remote Support
 Integrate HEAT Software with Bomgar Remote Support 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the
Integrate HEAT Software with Bomgar Remote Support 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the
Two factor authentication for Cisco ASA IPSec VPN Alternative
 Two factor authentication for Cisco ASA IPSec VPN Alternative logintc.com/docs/connectors/cisco-asa-ipsec-alt.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged
Two factor authentication for Cisco ASA IPSec VPN Alternative logintc.com/docs/connectors/cisco-asa-ipsec-alt.html The LoginTC RADIUS Connector is a complete two-factor authentication virtual machine packaged
Odette CA Help File and User Manual
 How to Order and Install Odette Certificates For a German version of this file please follow this link. Odette CA Help File and User Manual 1 Release date 31.05.2016 Contents Preparation for Ordering an
How to Order and Install Odette Certificates For a German version of this file please follow this link. Odette CA Help File and User Manual 1 Release date 31.05.2016 Contents Preparation for Ordering an
Certificate Renewal on Cisco Identity Services Engine Configuration Guide
 Certificate Renewal on Cisco Identity Services Engine Configuration Guide Document ID: 116977 Contributed by Roger Nobel, Cisco TAC Engineer. Jun 26, 2015 Contents Introduction Prerequisites Requirements
Certificate Renewal on Cisco Identity Services Engine Configuration Guide Document ID: 116977 Contributed by Roger Nobel, Cisco TAC Engineer. Jun 26, 2015 Contents Introduction Prerequisites Requirements
Mail Assure. Quick Start Guide
 Mail Assure Quick Start Guide Last Updated: Wednesday, November 14, 2018 ----------- 2018 CONTENTS Firewall Settings 2 Accessing Mail Assure 3 Application Overview 4 Navigating Mail Assure 4 Setting up
Mail Assure Quick Start Guide Last Updated: Wednesday, November 14, 2018 ----------- 2018 CONTENTS Firewall Settings 2 Accessing Mail Assure 3 Application Overview 4 Navigating Mail Assure 4 Setting up
HEAT Software Integration with Remote Support
 HEAT Software Integration with Remote Support 2003-2018 BeyondTrust, Inc. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust, Inc. Other trademarks are the property of their
HEAT Software Integration with Remote Support 2003-2018 BeyondTrust, Inc. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust, Inc. Other trademarks are the property of their
Oracle9iAS Unified Messaging
 Oracle9iAS Unified Messaging Release Notes Release 9.0.2 for UNIX April 2002 Part No. A95819-01 This document summarizes the differences between Oracle9iAS Unified Messaging and its documented functionality.
Oracle9iAS Unified Messaging Release Notes Release 9.0.2 for UNIX April 2002 Part No. A95819-01 This document summarizes the differences between Oracle9iAS Unified Messaging and its documented functionality.
Understanding HTTPS CRL and OCSP
 Understanding HTTPS CRL and OCSP Santhosh J PKI Body of Knowledge: Development & Dissemination Centre for Development of Advanced Computing (C-DAC) Bangalore Under the Aegis of Controller of Certifying
Understanding HTTPS CRL and OCSP Santhosh J PKI Body of Knowledge: Development & Dissemination Centre for Development of Advanced Computing (C-DAC) Bangalore Under the Aegis of Controller of Certifying
Forescout. Plugin. Configuration Guide. Version 2.2.4
 Forescout Core Extensions Module: External Classifier Plugin Version 2.2.4 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/
Forescout Core Extensions Module: External Classifier Plugin Version 2.2.4 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/
Script.byu.edu SharePoint Instructions
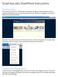 Script.byu.edu SharePoint Instructions Site Actions Menu Go to script.byu.edu, click on Authenticate at the bottom of page, you will be prompted to enter a username and password, use your netid and password
Script.byu.edu SharePoint Instructions Site Actions Menu Go to script.byu.edu, click on Authenticate at the bottom of page, you will be prompted to enter a username and password, use your netid and password
VMware Workspace ONE UEM VMware AirWatch Cloud Connector
 VMware AirWatch Cloud Connector VMware Workspace ONE UEM 1811 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this
VMware AirWatch Cloud Connector VMware Workspace ONE UEM 1811 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this
Steel Belted Radius. Release Notes SBR 6.24 Build 1. Release, Build Published Document Version Build 1 May,
 Steel Belted Radius Release Notes SBR 6.24 Build 1 Release, Build Published Document Version 6.24 Build 1 May, 2017 2.0 Contents Steel-Belted Radius Release - 6.2 Release Notes... 3 System Requirements...
Steel Belted Radius Release Notes SBR 6.24 Build 1 Release, Build Published Document Version 6.24 Build 1 May, 2017 2.0 Contents Steel-Belted Radius Release - 6.2 Release Notes... 3 System Requirements...
HTTPS--HTTP Server and Client with SSL 3.0
 The feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS XE software. SSL provides server authentication, encryption, and message
The feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS XE software. SSL provides server authentication, encryption, and message
This PDF Document was generated for free by the Aloaha PDF Suite If you want to learn how to make your own PDF Documents visit:
 INSTALLING AND CONFIGURING A WINDOWS SERVER 2003 ENTERPRISE CERTIFICATION AUTHORITY Certification Authorities can issue certificates to users and computers for a variety of purposes. In the context of
INSTALLING AND CONFIGURING A WINDOWS SERVER 2003 ENTERPRISE CERTIFICATION AUTHORITY Certification Authorities can issue certificates to users and computers for a variety of purposes. In the context of
CA Service Desk Integration with Remote Support
 CA Service Desk Integration with Remote Support 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are the
CA Service Desk Integration with Remote Support 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are the
