Delivery to the following recipient failed permanently:
|
|
|
- Brittney Miller
- 5 years ago
- Views:
Transcription
1
2 Delivery to the following recipient failed permanently: Original message DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=gmail.com; s= ; h=from:to:references:in-reply-to:subject:date:message-id:mime-version :content-type:x-mailer:thread-index:content-language; bh=elys+amdquskrx5q6km8oiuvz/d2gjvkaddv0tdwbqc=; b=ewb1mh4iksqjogfnzlmh0ei/sj9vcmodvppo9fozg3ddt/clq5tyo1a+iw2o+kbbhs ReMGDVBtmoThAhjpSeWSKlrPTqenkIbr1CfPutMg5JnCkl3HK754CS1Tcax6MAjrTCfk I4EFYcABuccB1p4mmZuErISgsCWdqyTGSOk1Uef1Sxq0Cuf7Y7/g6qY4NYwxfzcMlpfg Nvzqd1BiFpu7rsEQ3I5rIsALw9J620aulAEXb8jqeMU5Qq471EgwODAI07aw1pDZavjN otx1gcvbk6vocxasx1bbwpxxb0kxoqdpd9wiuvujskipzwhzba509rq5ww+pdmmiyfee H3/Q== Received: by with SMTP id hs12mr bkc ; Tue, 07 Aug :26: (PDT) Return-Path: Received: from MPC (cpe st3.cable.xnet.hr. [ ]) by mx.google.com with ESMTPS id 25sm bkx (version=tlsv1/sslv3 cipher=other); Tue, 07 Aug :26: (PDT) From: =?iso ?q?mirjana_pavi=e6?= To: References: l.com> In-Reply-To: Date: Tue, 7 Aug :26: Message-ID: <000f01cd7487$19b016f0$4d1044d0$@gmail.com> MIME-Version: 1.0 Content-Type: multipart/mixed; boundary="----=_nextpart_000_0010_01cd7497.dd4039f0" X-Mailer: Microsoft Outlook 14.0 Thread-Index: AQJaujHv2B6BJaU4+Wk7thp5V1UXEAMlNecsATmfLXkB/9/UBpYAocRw Content-Language: hr Poštovani gospodine Novokmet! Opetovano Vas molim da elektronskim putem potvrdite primitak niže dostavljenog a. Dostavljam Vam u attach. zakonske odredbe koje Vas obvezuju da potvrdite primitak elektroničke isprave a po zahtjevu pošiljaoca. Ukoliko ne potvrdite primitak, podnijeću tužbu protiv HRT i protiv Vas kao odgovorne osobe, sukladno Zakonu o elektroničkoj ispravi. S poštovanjem, Mirjana Pavić
3 From: Mirjana Pavić Sent: Monday, August 06, :58 PM To: Poštovani gospodine Novokmet! Već tri-četiri dana traje organizirana akcija raznih djelatnika HRT u smislu da blokiraju i brišu bez čitanja moje poruke. Također mi je vraćena poruka koju sam naslovila na Vas osobno. Zbog čega to rade Vaši djelatnici. Osobno se nadam da im Vi to niste naložili. Ljubazno Vas molim da mi potvrdite " na reply" da ste zaprimili ovaj . vkumbrija@hrt.hr Received: from tweety.hrt.hr ( ) by exhubcas2.hrt.hr ( ) with Microsoft SMTP Server (TLS) id ; Sun, 5 Aug :25: Received: from tom.hrt.hr (tom.hrt.hr [ ]) by tweety.hrt.hr (8.13.8/8.13.8) with SMTP id q75ep8xk for <hrt@hrt.hr>; Sun, 5 Aug :25: Received: from mail-wg0-f50.google.com (mail-wg0-f50.google.com [ ]) by tom.hrt.hr (8.13.8/8.13.8) with SMTP id q75eowol for <hrt@hrt.hr>; Sun, 5 Aug :25:
4 Received: by wgbds11 with SMTP id ds11so wgb.31 for Sun, 05 Aug :25: (PDT) DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=gmail.com; s= ; h=from:to:references:in-reply-to:subject:date:message-id:mime-version :content-type:x-mailer:thread-index:content-language; bh=ggx2ydm6jcq42fdyi/lcjvnfienb/hpdlo9fa1wm/d4=; b=wb10skdlstx8tcrqbpbxg+/wvicj69kdqvomv2qrxr46mydsvclkppe5b9pwkkmjd5 Di6b/XFsbKpm2GpLB3leiX4CX1GN4rh/L62JiO0SUxj54LtyxIPSWskywdg3ar/2/Rla tnwauqi2gkczt1odujnrrwrnf1uqeioimdqgcpthouitassuavvdndksudnb91afq7y1 KFb7RZORYF2ghneGBhDLu2PSLHsxR8z4XSGE+4GzlCieFhmAODAOEF1DCECs8J1fhCKb JHVUBAlUHbF/BkkWYomqcQ3fvqSj1Z3T5/eLdWCX2uyIRzVx8lmL4jpuILyyQmLzBtrJ M2Gw== Received: by with SMTP id q72mr wen ; Sun, 05 Aug :25: (PDT) Received: from MPC (cpe st.cable.xnet.hr. [ ]) by mx.google.com with ESMTPS id ep14sm wid (version=tlsv1/sslv3 cipher=other); Sun, 05 Aug :24: (PDT) From: =?iso ?q?mirjana_pavi=e6?= To: References: gmail.com> gmail.com> In-Reply-To: gmail.com> Date: Sun, 5 Aug :24: Message-ID: <001501cd7316$104d0450$30e70cf0$@gmail.com> MIME-Version: 1.0 Content-Type: multipart/mixed; boundary="----=_nextpart_000_0016_01cd7326.d3dba0b0" X-Mailer: Microsoft Outlook 14.0 Thread-Index: AQJaujHv2B6BJaU4+Wk7thp5V1UXEAMlNecsATmfLXkCXqABGJX6ynlA Content-Language: hr X-Virus-Scanned: by amavisd-new Return-Path: mir.pavic@gmail.com
5
59YHTgcmmrUbp965ht2TugQFZRjjak9Ckrp66CTxKEsgBZZJZqJvz462M3ePt5EGVcuL
 Delivered-To: bmackenty@gmail.com Received: by 10.79.136.130 with SMTP id k124csp2649542ivd; Mon, 7 Aug 2017 04:59:05-0700 (PDT) X-Received: by 10.84.231.194 with SMTP id g2mr312696pln. 5.1502107145823;
Delivered-To: bmackenty@gmail.com Received: by 10.79.136.130 with SMTP id k124csp2649542ivd; Mon, 7 Aug 2017 04:59:05-0700 (PDT) X-Received: by 10.84.231.194 with SMTP id g2mr312696pln. 5.1502107145823;
Delivery incomplete. Detected a bounce of message #36, list gbird (bounce type DSN)
 1 of 5 2/3/2018 6:03 PM Subject: Bounce detected (list gbird) from Toni.J.Piaggio@aphis.usda.gov From: mj2-owner@lists.ncsu.edu Date: 2/17/2017 12:06 PM To: gbird-owner@lists.ncsu.edu Detected a bounce
1 of 5 2/3/2018 6:03 PM Subject: Bounce detected (list gbird) from Toni.J.Piaggio@aphis.usda.gov From: mj2-owner@lists.ncsu.edu Date: 2/17/2017 12:06 PM To: gbird-owner@lists.ncsu.edu Detected a bounce
Advanced Introduction to Machine Learning CMU-10715
 Advanced Introduction to Machine Learning CMU-10715 MLE, MAP, Bayes classification Barnabás Póczos Sept 9, 2015 Outline Theory: Probabilities: Dependence, Independence, Conditional Independence Parameter
Advanced Introduction to Machine Learning CMU-10715 MLE, MAP, Bayes classification Barnabás Póczos Sept 9, 2015 Outline Theory: Probabilities: Dependence, Independence, Conditional Independence Parameter
Towards authentication
 Towards email authentication TLS SPF + DKIM + DMARC 2012/10/03 Roberto Innocente 1 Who adopted it? Hotmail.com Gmail.com AOL.com Verizon.com Ebay Paypal Yahoo.com 2012/10/03 Roberto Innocente 2 Tls/SPF/DKIM/DMARC
Towards email authentication TLS SPF + DKIM + DMARC 2012/10/03 Roberto Innocente 1 Who adopted it? Hotmail.com Gmail.com AOL.com Verizon.com Ebay Paypal Yahoo.com 2012/10/03 Roberto Innocente 2 Tls/SPF/DKIM/DMARC
Experiment No: Group A-6
 R (2) N (5) Oral (3) Total (10) Dated Sign Experiment No: Group A-6 Problem Definition: Write a program in C++ /Python to analyze email header. 6.1Prerequisite: Application Layer Protocols 6.2 Learning
R (2) N (5) Oral (3) Total (10) Dated Sign Experiment No: Group A-6 Problem Definition: Write a program in C++ /Python to analyze email header. 6.1Prerequisite: Application Layer Protocols 6.2 Learning
Subject: [Middle-east-structure] Fwd: IPT/Transmission - Progress Report: Sep 2017 From: Leon Mellul via Middle-east-structure
![Subject: [Middle-east-structure] Fwd: IPT/Transmission - Progress Report: Sep 2017 From: Leon Mellul via Middle-east-structure Subject: [Middle-east-structure] Fwd: IPT/Transmission - Progress Report: Sep 2017 From: Leon Mellul via Middle-east-structure](/thumbs/93/111272038.jpg) Subject: [Middle-east-structure] Fwd: IPT/Transmission - Progress Report: Sep 2017 From: Leon Mellul via Middle-east-structure Date: 1/10/2017 5:52 PM To: Middle East
Subject: [Middle-east-structure] Fwd: IPT/Transmission - Progress Report: Sep 2017 From: Leon Mellul via Middle-east-structure Date: 1/10/2017 5:52 PM To: Middle East
Naïve Bayes Classifier. Lecture 8: Aykut Erdem October 2017 Hacettepe University
 Naïve Bayes Classifier Lecture 8: Aykut Erdem October 2017 Hacettepe University Today Bayes rule - Naïve Bayes Classifier Application - Text classification - Mind reading = fmri data processing 2 Recap:
Naïve Bayes Classifier Lecture 8: Aykut Erdem October 2017 Hacettepe University Today Bayes rule - Naïve Bayes Classifier Application - Text classification - Mind reading = fmri data processing 2 Recap:
Over 99% of s are SPAM! Useless for mankind!
 Advanced Mail Introduction SPAM vs. non-spam Mail sent by spammer vs. non-spammer Problem of SPAM mail Over 99% of E-mails are SPAM! Useless for mankind! SPAM detection? Client-based detection These methods
Advanced Mail Introduction SPAM vs. non-spam Mail sent by spammer vs. non-spammer Problem of SPAM mail Over 99% of E-mails are SPAM! Useless for mankind! SPAM detection? Client-based detection These methods
BACKTRACING S. Michael Sonntag
 BACKTRACING E-MAILS Michael Sonntag SOURCE E-MAILS Source of E-Mails: My personal spam folder! real_viagra.eml Fake GMX E-Mail For comparison a real GMX messages: Beispielmail_GMX.eml As_lecture.eml A
BACKTRACING E-MAILS Michael Sonntag SOURCE E-MAILS Source of E-Mails: My personal spam folder! real_viagra.eml Fake GMX E-Mail For comparison a real GMX messages: Beispielmail_GMX.eml As_lecture.eml A
Forwarded conversation Subject: File: Comments -City Council & Board of Public Works & Gang Reduction Com.
 Adam Lid Fwd: Delivery Status Notification (Failure) 1 message Holly Wolcott To: Adam Lid Mon, Jun 27, 2016 at 9:09 AM --------- Forwarded
Adam Lid Fwd: Delivery Status Notification (Failure) 1 message Holly Wolcott To: Adam Lid Mon, Jun 27, 2016 at 9:09 AM --------- Forwarded
UPUTSTVO ZA KORIŠĆENJE NOVOG SPINTER WEBMAIL-a
 UPUTSTVO ZA KORIŠĆENJE NOVOG SPINTER WEBMAIL-a Webmail sistem ima podršku za SSL (HTTPS). Korištenjem ovog protokola sva komunikacija između Webmail sistema i vašeg Web čitača je kriptovana. Prilikom pristupa
UPUTSTVO ZA KORIŠĆENJE NOVOG SPINTER WEBMAIL-a Webmail sistem ima podršku za SSL (HTTPS). Korištenjem ovog protokola sva komunikacija između Webmail sistema i vašeg Web čitača je kriptovana. Prilikom pristupa
<OF1C8DBAB4.F6DD93FA ON852580F EA Mon, Mar 27, 2017 at 2:22 PM (Delivered after 239 seconds)
 Original Message Message ID Created at: From: To: Mon, Mar 27, 2017 at 2:22 PM (Delivered after 239 seconds) IBM Knowledge
Original Message Message ID Created at: From: To: Mon, Mar 27, 2017 at 2:22 PM (Delivered after 239 seconds) IBM Knowledge
bh=40lsbgolp7pbwmgrxdkxpu2gosgmm2ifbkmg6lw1jeu=; b=wmry1ugcb83u5xihbivsnolgzuj07gjvzmm+469p5b +8PzVhEWlQ1wqSjQBPAFHp6J
 Delivered-To: bmackenty@aswarsaw.org Received: by 10.55.80.139 with SMTP id e133csp463209qkb; Mon, 1 May 2017 03:07:15-0700 (PDT) X-Received: by 10.107.5.12 with SMTP id 12mr16189961iof. 186.1493633235602;
Delivered-To: bmackenty@aswarsaw.org Received: by 10.55.80.139 with SMTP id e133csp463209qkb; Mon, 1 May 2017 03:07:15-0700 (PDT) X-Received: by 10.107.5.12 with SMTP id 12mr16189961iof. 186.1493633235602;
Networking and the Internet
 ICS 101 Fall 2012 Networking and the Asst. Prof. Lipyeow Lim Information & Computer Science Department University of Hawaii at Manoa 9/4/2012 Lipyeow Lim -- University of Hawaii at Manoa 1 Problem Ancient
ICS 101 Fall 2012 Networking and the Asst. Prof. Lipyeow Lim Information & Computer Science Department University of Hawaii at Manoa 9/4/2012 Lipyeow Lim -- University of Hawaii at Manoa 1 Problem Ancient
s. has become a primary means of communication. can easily be forged. can be abused
 E-mails Email has become a primary means of communication. Email can easily be forged Email can be abused Spam Aid in committing a crime Threatening email, Challenges to E-mail Authenticity Origin & Sender
E-mails Email has become a primary means of communication. Email can easily be forged Email can be abused Spam Aid in committing a crime Threatening email, Challenges to E-mail Authenticity Origin & Sender
<deb61fd5 4d79 a Fri, Feb 17, 2017 at 4:08 PM (Delivered after 8 seconds) Bill MacKenty
 Original Message Message ID Created at: From: To: Subject: SPF: DKIM:
Original Message Message ID Created at: From: To: Subject: SPF: DKIM:
(b)(4) (b)(4) (b)(4) (b)(4) (b)(4) AMALG IND:000001
 AMALG IND:000001 AMALG IND:000002 AMALG IND:000003 November 16, 2010 Dear Applicant: RE: Amalgamated, Industrial and Toy & Novelty Workers of America Thank you for your application for the Waiver of the
AMALG IND:000001 AMALG IND:000002 AMALG IND:000003 November 16, 2010 Dear Applicant: RE: Amalgamated, Industrial and Toy & Novelty Workers of America Thank you for your application for the Waiver of the
sender) client-ip= ; dkim=pass
 Delivered-To: ryanlawhsv@gmail.com Received: by 10.129.162.146 with SMTP id z140csp2021593ywg; X-Received: by 10.200.36.81 with SMTP id d17mr24690451qtd.99.1487704818927; Return-Path:
Delivered-To: ryanlawhsv@gmail.com Received: by 10.129.162.146 with SMTP id z140csp2021593ywg; X-Received: by 10.200.36.81 with SMTP id d17mr24690451qtd.99.1487704818927; Return-Path:
bh=9f8/dl/qo6zqvut76gpsxonsryoygj7+iz3zai0nyty=; b=uzb/khk +qtkuju4s0ehm4kowgbvgoagiofkkbeqgxde79wrvtbe2kdtnqhenm+vnp1
 Delivered-To: bmackenty@aswarsaw.org Received: by 10.55.75.144 with SMTP id y138csp364924qka; Sat, 21 Jan 2017 01:28:46-0800 (PST) X-Received: by 10.157.54.139 with SMTP id h11mr10253536otc. 86.1484990925933;
Delivered-To: bmackenty@aswarsaw.org Received: by 10.55.75.144 with SMTP id y138csp364924qka; Sat, 21 Jan 2017 01:28:46-0800 (PST) X-Received: by 10.157.54.139 with SMTP id h11mr10253536otc. 86.1484990925933;
n Define active and passive footprinting n Identify methods and procedures in information gathering Chapter #2:
 Outline n Define active and passive footprinting n Identify methods and procedures in information gathering Chapter #2: n Understand the use of social networking, search engines, and Google hacking in
Outline n Define active and passive footprinting n Identify methods and procedures in information gathering Chapter #2: n Understand the use of social networking, search engines, and Google hacking in
Automatic Delivery Setup Guide
 for GuideSpark Communicate Cloud Table of Contents Summary: Working with Automatic Email Delivery... 1 What your IT department needs to know... 2 Prerequisite: Select a Targeted Audience... 3 Enable Automatic
for GuideSpark Communicate Cloud Table of Contents Summary: Working with Automatic Email Delivery... 1 What your IT department needs to know... 2 Prerequisite: Select a Targeted Audience... 3 Enable Automatic
Part 4: Message delivery protocols (POP and IMAP) Network News (Usenet News)
 4-1 *:96 Overheads Part 4: Message delivery protocols (POP and IMAP) Network News (Usenet News) More about this course about Internet application protocols can be found at URL: http://www.dsv.su.se/~jpalme/internet-course/int-app-prot-kurs.html
4-1 *:96 Overheads Part 4: Message delivery protocols (POP and IMAP) Network News (Usenet News) More about this course about Internet application protocols can be found at URL: http://www.dsv.su.se/~jpalme/internet-course/int-app-prot-kurs.html
Electronic mail security
 Electronic mail security Ola Flygt Växjö University, Sweden http://w3.msi.vxu.se/users/ofl/ Ola.Flygt@vxu.se +46 470 70 86 49 1 Outline Pretty Good Privacy (PGP) S/MIME 2 1 Pretty Good Privacy Philip R.
Electronic mail security Ola Flygt Växjö University, Sweden http://w3.msi.vxu.se/users/ofl/ Ola.Flygt@vxu.se +46 470 70 86 49 1 Outline Pretty Good Privacy (PGP) S/MIME 2 1 Pretty Good Privacy Philip R.
Forensic Analysis of Date and Time Spoofing
 Third International Conference on Computer and Communication Technology Forensic Analysis of E-mail and Spoofing Preeti Mishra, Emmanuel S. Pilli and R. C. Joshi Department of Computer Science & Engineering
Third International Conference on Computer and Communication Technology Forensic Analysis of E-mail and Spoofing Preeti Mishra, Emmanuel S. Pilli and R. C. Joshi Department of Computer Science & Engineering
Web Mail Check v 1.0
 Web Mail Check v 1.0 TABLE OF CONTENTS LAUNCHING WEB MAIL CHECK... 3 HOME PAGE... 4 LOG IN... 4 LANGUAGE... 5 DIRECTIONS... 5 READING MESSAGES... 8 HEADERS... 10 PRINTER FRIENDLY VERSION... 11 REPLYING
Web Mail Check v 1.0 TABLE OF CONTENTS LAUNCHING WEB MAIL CHECK... 3 HOME PAGE... 4 LOG IN... 4 LANGUAGE... 5 DIRECTIONS... 5 READING MESSAGES... 8 HEADERS... 10 PRINTER FRIENDLY VERSION... 11 REPLYING
Upute za postavljanje Outlook Expressa
 Upute za postavljanje Outlook Expressa Prije postavljanja klijenata morate obavezno obaviti prvu prijavu na web mail kako bi aktivirali vaš račun na novom sustavu. Ukoliko niste obavili prvu prijavu, nećete
Upute za postavljanje Outlook Expressa Prije postavljanja klijenata morate obavezno obaviti prvu prijavu na web mail kako bi aktivirali vaš račun na novom sustavu. Ukoliko niste obavili prvu prijavu, nećete
Overview of Economic Models
 Overview of Economic Models Richard Clayton richard.clayton@cl.cam.ac.uk ITAT 4 th December 2013 Why SHIM6 is likely to fail Richard Clayton richard.clayton@cl.cam.ac.uk WEIS June 2009 How is Internet
Overview of Economic Models Richard Clayton richard.clayton@cl.cam.ac.uk ITAT 4 th December 2013 Why SHIM6 is likely to fail Richard Clayton richard.clayton@cl.cam.ac.uk WEIS June 2009 How is Internet
International Journal of Advance Engineering and Research Development. Legalistic Evaluation of Headers Based on Address Spoofing
 Scientific Journal of Impact Factor (SJIF): 4.72 International Journal of Advance Engineering and Research Development Volume 5, Issue 01, January -2018 e-issn (O): 2348-4470 p-issn (P): 2348-6406 Legalistic
Scientific Journal of Impact Factor (SJIF): 4.72 International Journal of Advance Engineering and Research Development Volume 5, Issue 01, January -2018 e-issn (O): 2348-4470 p-issn (P): 2348-6406 Legalistic
SQL in a Server Environment (i)
 ICS 321 Fall 2012 SQL in a Server Environment (i) Asst. Prof. Lipyeow Lim Information & Computer Science Department University of Hawaii at Manoa 3/6/2013 Lipyeow Lim -- University of Hawaii at Manoa 1
ICS 321 Fall 2012 SQL in a Server Environment (i) Asst. Prof. Lipyeow Lim Information & Computer Science Department University of Hawaii at Manoa 3/6/2013 Lipyeow Lim -- University of Hawaii at Manoa 1
Objectives. What Is and How Does It Work? Objectives. and How Does It Work? and How Does It Work?
 Objectives E-MAIL BASICS Evaluating Integrated Browser E-Mail Programs and a Web-Based E-Mail Service New Perspectives on THE INTERNET Learn about e-mail and how it works Configure and use two popular
Objectives E-MAIL BASICS Evaluating Integrated Browser E-Mail Programs and a Web-Based E-Mail Service New Perspectives on THE INTERNET Learn about e-mail and how it works Configure and use two popular
Network Working Group Request for Comments: 1844 Obsoletes: 1820 August 1995 Category: Informational
 Network Working Group E. Huizer Request for Comments: 1844 SURFnet bv Obsoletes: 1820 August 1995 Category: Informational Status of this Memo Multimedia E-mail (MIME) User Agent checklist This memo provides
Network Working Group E. Huizer Request for Comments: 1844 SURFnet bv Obsoletes: 1820 August 1995 Category: Informational Status of this Memo Multimedia E-mail (MIME) User Agent checklist This memo provides
Internet Engineering Task Force (IETF) Request for Comments: ISSN: November 2011
 Internet Engineering Task Force (IETF) K. Li Request for Comments: 6430 B. Leiba Category: Standards Track Huawei Technologies ISSN: 2070-1721 November 2011 Abstract Email Feedback Report Type Value: not-spam
Internet Engineering Task Force (IETF) K. Li Request for Comments: 6430 B. Leiba Category: Standards Track Huawei Technologies ISSN: 2070-1721 November 2011 Abstract Email Feedback Report Type Value: not-spam
Internet Technology. 03r. Application layer protocols: . Paul Krzyzanowski. Rutgers University. Spring 2016
 Internet Technology 03r. Application layer protocols: email Paul Krzyzanowski Rutgers University Spring 2016 1 Email: SMTP (Simple Mail Transfer Protocol) 2 Simple Mail Transfer Protocol (SMTP) Protocol
Internet Technology 03r. Application layer protocols: email Paul Krzyzanowski Rutgers University Spring 2016 1 Email: SMTP (Simple Mail Transfer Protocol) 2 Simple Mail Transfer Protocol (SMTP) Protocol
NORDUnet Nordic Infrastructure for Research & Education. Intro. SPAM-hantering på NUNOC och internt i SUNET
 Intro SPAM-hantering på NUNOC och internt i SUNET Intro Förkortningar som är bra att kunna: MTA MUA MDA Mail Transfer Agent ex. Sendmail, Postfix, Qmail Mail User Agent ex. Thunderbird, Eudora, Pine, mutt
Intro SPAM-hantering på NUNOC och internt i SUNET Intro Förkortningar som är bra att kunna: MTA MUA MDA Mail Transfer Agent ex. Sendmail, Postfix, Qmail Mail User Agent ex. Thunderbird, Eudora, Pine, mutt
& Online Evidence Collection
 Email & Online Evidence Collection Domestic violence offenders frequently misuse email and online spaces to stalk, abuse, terrorize, and monitor victims. Abusers may send messages from random email addresses
Email & Online Evidence Collection Domestic violence offenders frequently misuse email and online spaces to stalk, abuse, terrorize, and monitor victims. Abusers may send messages from random email addresses
Symantec ST Symantec Messaging Gateway Download Full Version :
 Symantec ST0-199 Symantec Messaging Gateway 10.0 Download Full Version : https://killexams.com/pass4sure/exam-detail/st0-199 QUESTION: 111 When configuring DKIM signing, how should the domain key generated
Symantec ST0-199 Symantec Messaging Gateway 10.0 Download Full Version : https://killexams.com/pass4sure/exam-detail/st0-199 QUESTION: 111 When configuring DKIM signing, how should the domain key generated
Outlook 2010 Common Tasks
 Outlook 2010 Common Tasks January 6, 2015 Table of Contents Creating a New Message... 2 Addressing the Message... 2 Using the Address Book... 2 Using the Check Names Icon... 5 Using AutoComplete... 7 Spell
Outlook 2010 Common Tasks January 6, 2015 Table of Contents Creating a New Message... 2 Addressing the Message... 2 Using the Address Book... 2 Using the Check Names Icon... 5 Using AutoComplete... 7 Spell
Computer Security Incident Response Team Slovakia CSIRT.SK
 Computer Security Incident Response Team Slovakia CSIRT.SK Martin Jurčík, CSIRT.SK CS Danube, 15 th March, 2016, Prague CS Danube (Cyber Security in Danube Region) project is part financed by the European
Computer Security Incident Response Team Slovakia CSIRT.SK Martin Jurčík, CSIRT.SK CS Danube, 15 th March, 2016, Prague CS Danube (Cyber Security in Danube Region) project is part financed by the European
SMTP. George Porter CSE 124 February 12, 2015
 SMTP George Porter CSE 124 February 12, 2015 Homework 2 out Announcements Project 2 checkpoint due Tuesday Traditional Applications Two of the most popular The World Wide Web and Email. Broadly speaking,
SMTP George Porter CSE 124 February 12, 2015 Homework 2 out Announcements Project 2 checkpoint due Tuesday Traditional Applications Two of the most popular The World Wide Web and Email. Broadly speaking,
Network Security (PhD Section)
 CSE508 Network Security (PhD Section) 4/7/2015 Email Michalis Polychronakis Stony Brook University 1 Email Overview MUA: Mail User Agent Thunderbird, webmail, Pine, MSA: Mail Submission Agent SMTP (port
CSE508 Network Security (PhD Section) 4/7/2015 Email Michalis Polychronakis Stony Brook University 1 Email Overview MUA: Mail User Agent Thunderbird, webmail, Pine, MSA: Mail Submission Agent SMTP (port
Employing VisNetic MailServer Security Features
 Employing VisNetic MailServer Security Features VisNetic MailServer p o w e r f u l email server VisNetic MailServer Security Features VisNetic MailServer includes a sophisticated and broad array of security
Employing VisNetic MailServer Security Features VisNetic MailServer p o w e r f u l email server VisNetic MailServer Security Features VisNetic MailServer includes a sophisticated and broad array of security
https://mail.google.com/mail/u/0/?ui=2&ik=4a9d5ab0fe&vi...
 Delivered-To: bmackenty@aswarsaw.org Received: by 10.194.158.100 with SMTP id wt4csp1082891wjb; X-Received: by 10.55.50.149 with SMTP id y143mr16553555qky.86.1445001190398; Return-Path:
Delivered-To: bmackenty@aswarsaw.org Received: by 10.194.158.100 with SMTP id wt4csp1082891wjb; X-Received: by 10.55.50.149 with SMTP id y143mr16553555qky.86.1445001190398; Return-Path:
DomainKeys Identified Mail Overview (-01) Eric Allman Sendmail, Inc.
 DomainKeys Identified Mail Overview (-01) Eric Allman Sendmail, Inc. Overview of DKIM Cryptography-based protocol, signs selected header fields and message body Intended to: Enable reliable domain name
DomainKeys Identified Mail Overview (-01) Eric Allman Sendmail, Inc. Overview of DKIM Cryptography-based protocol, signs selected header fields and message body Intended to: Enable reliable domain name
COSC 301 Network Management. Lecture 14: Electronic Mail
 COSC 301 Network Management Lecture 14: Electronic Mail Zhiyi Huang Computer Science, University of Otago COSC301 Lecture 14: Electronic Mail 1 Today s Focus Electronic Mail -- How does it work? -- How
COSC 301 Network Management Lecture 14: Electronic Mail Zhiyi Huang Computer Science, University of Otago COSC301 Lecture 14: Electronic Mail 1 Today s Focus Electronic Mail -- How does it work? -- How
. SMTP, POP, and IMAP
 E-Mail SMTP, POP, and IMAP Scope How Email Appears to Work How Email Really Works Mail User Agent (MUA) Message Format Mail Delivery Agent (MDA)/ Mail Transfer Agent (MTA) Firewalls, Spam and Virus Filters
E-Mail SMTP, POP, and IMAP Scope How Email Appears to Work How Email Really Works Mail User Agent (MUA) Message Format Mail Delivery Agent (MDA)/ Mail Transfer Agent (MTA) Firewalls, Spam and Virus Filters
Symantec ST0-250 Exam
 Volume: 126 Questions Question No: 1 What is the recommended minimum hard-drive size for a virtual instance of Symantec Messaging Gateway 10.5? A. 80 GB B. 90 GB C. 160 GB D. 180 GB Answer: B Question
Volume: 126 Questions Question No: 1 What is the recommended minimum hard-drive size for a virtual instance of Symantec Messaging Gateway 10.5? A. 80 GB B. 90 GB C. 160 GB D. 180 GB Answer: B Question
BUT2 7day 11/4/07 11:07 PM Page 1. Introduction
 BUT2 7day 11/4/07 11:07 PM Page 1 Introduction This booklet will give you easy to follow instructions to allow you to set your BUT2 Timeswitch to the 7 Day, (different times every day) program. Contents
BUT2 7day 11/4/07 11:07 PM Page 1 Introduction This booklet will give you easy to follow instructions to allow you to set your BUT2 Timeswitch to the 7 Day, (different times every day) program. Contents
Automatic Delivery Setup Guide
 for GuideSpark Communicate Cloud Table of Contents Summary: Working with Automatic Email Delivery... 1 What your IT department needs to know... 2 Prerequisite: Select a Targeted Audience... 3 Enable Automatic
for GuideSpark Communicate Cloud Table of Contents Summary: Working with Automatic Email Delivery... 1 What your IT department needs to know... 2 Prerequisite: Select a Targeted Audience... 3 Enable Automatic
Error Sending Mail Message To Smtp Server. Return Code 552
 Error Sending Mail Message To Smtp Server. Return Code 552 The best mail server response code you can get. A 400-style message is usually returned when some sort of transient error is easing off the throttle
Error Sending Mail Message To Smtp Server. Return Code 552 The best mail server response code you can get. A 400-style message is usually returned when some sort of transient error is easing off the throttle
CSCE 463/612 Networks and Distributed Processing Spring 2018
 CSCE 463/612 Networks and Distributed Processing Spring 2018 Application Layer II Dmitri Loguinov Texas A&M University February 6, 2018 Original slides copyright 1996-2004 J.F Kurose and K.W. Ross 1 Chapter
CSCE 463/612 Networks and Distributed Processing Spring 2018 Application Layer II Dmitri Loguinov Texas A&M University February 6, 2018 Original slides copyright 1996-2004 J.F Kurose and K.W. Ross 1 Chapter
Internet Architecture
 Internet Architecture Lecture 10: How Email Work Assistant Teacher Samraa Adnan Al-Asadi 1 How Email Works Electronic mail, or email, might be the most heavily used feature of the Internet. You can use
Internet Architecture Lecture 10: How Email Work Assistant Teacher Samraa Adnan Al-Asadi 1 How Email Works Electronic mail, or email, might be the most heavily used feature of the Internet. You can use
https://exchange.billings.k12.mt.us Enter your username Enter your password
 https://exchange.billings.k12.mt.us Enter your username Enter your password Available folders This is the folder view. From here you can view your inbox, calendar, or any other folder shown on the left.
https://exchange.billings.k12.mt.us Enter your username Enter your password Available folders This is the folder view. From here you can view your inbox, calendar, or any other folder shown on the left.
eservices -processing
 eservices email-processing 9/17/2018 email-processing attachment-mngt autobot-agent-login-name autowar-detect-period autowar-max-reply-count autowar-scan-all-threads-ofcontact bcc-address cc-userdata-limit
eservices email-processing 9/17/2018 email-processing attachment-mngt autobot-agent-login-name autowar-detect-period autowar-max-reply-count autowar-scan-all-threads-ofcontact bcc-address cc-userdata-limit
Enterprise Chat and Administrator s Guide to Resources, Release 11.6(1)
 Enterprise Chat and Email Administrator s Guide to Email Resources, Release 11.6(1) For Unified Contact Center Enterprise First Published: August 2016 Last Updated: August 2017 Americas Headquarters Cisco
Enterprise Chat and Email Administrator s Guide to Email Resources, Release 11.6(1) For Unified Contact Center Enterprise First Published: August 2016 Last Updated: August 2017 Americas Headquarters Cisco
Backtracing s Computer Forensics
 Mag. iur. Dr. techn. Michael Sonntag Backtracing E-Mails Computer Forensics E-Mail: sonntag@fim.uni-linz.ac.at http://www.fim.uni-linz.ac.at/staff/sonntag.htm Institute for Information Processing and Microprocessor
Mag. iur. Dr. techn. Michael Sonntag Backtracing E-Mails Computer Forensics E-Mail: sonntag@fim.uni-linz.ac.at http://www.fim.uni-linz.ac.at/staff/sonntag.htm Institute for Information Processing and Microprocessor
From: Sent: To: Subject:
 From: Justin Michael Nelson Sent: Monday, December 12, 2016 10:21 PM To: s_huminski@live.com Subject: Hello from the OTHER SIDE! Hello, it's me. I was wondering if after
From: Justin Michael Nelson Sent: Monday, December 12, 2016 10:21 PM To: s_huminski@live.com Subject: Hello from the OTHER SIDE! Hello, it's me. I was wondering if after
Outline. Tools
 E-mail Tools 1 Outline Goals and Objectives Topics Headlines Introduction Communication Protocols Content, Attachments, and Etiquette Acronyms and Emoticons E-mail clients and Webbased E-mail Eudora Outlook
E-mail Tools 1 Outline Goals and Objectives Topics Headlines Introduction Communication Protocols Content, Attachments, and Etiquette Acronyms and Emoticons E-mail clients and Webbased E-mail Eudora Outlook
i-mscp OpenDKIM plugin
 2019/01/23 02:32 1/5 i-mscp OpenDKIM plugin Bear in mind that this documentation is for the last available version. If you use an older version, you must refer to the README.md file inside the plugin archive.
2019/01/23 02:32 1/5 i-mscp OpenDKIM plugin Bear in mind that this documentation is for the last available version. If you use an older version, you must refer to the README.md file inside the plugin archive.
Based on material produced by among others: Sanjay Pol, Ashok Ramaswami, Jim Fenton and Eric Allman
 DKIM Patrik Fältström Based on material produced by among others: Sanjay Pol, Ashok Ramaswami, Jim Fenton and Eric Allman September 22, 2005 1 What is Domain Keys Identified Mail? Method of using cryptographic
DKIM Patrik Fältström Based on material produced by among others: Sanjay Pol, Ashok Ramaswami, Jim Fenton and Eric Allman September 22, 2005 1 What is Domain Keys Identified Mail? Method of using cryptographic
Filtering 7 April 2014
 Email Filtering 2014 Fortinet Inc. All rights reserved. The information contained herein is subject to change without notice. No part of this publication including text, examples, diagrams 1 or illustrations
Email Filtering 2014 Fortinet Inc. All rights reserved. The information contained herein is subject to change without notice. No part of this publication including text, examples, diagrams 1 or illustrations
Reading Headers with MX Tool Box By Matt Flederbach
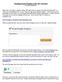 Reading Email Headers with MX Tool Box By Matt Flederbach Often times, you'll get a customer asking Why did it take so long for my email to be delivered? or Why was my email blocked? or even Why was this
Reading Email Headers with MX Tool Box By Matt Flederbach Often times, you'll get a customer asking Why did it take so long for my email to be delivered? or Why was my email blocked? or even Why was this
An Introduction to Protecting your (Mostly Online) Identity
 An Introduction to Protecting your (Mostly Online) Identity Carlos Jensen School of EECS Oregon State University cjensen@eecs... Overview Introduction to me & what I do Introduction/Background What is
An Introduction to Protecting your (Mostly Online) Identity Carlos Jensen School of EECS Oregon State University cjensen@eecs... Overview Introduction to me & what I do Introduction/Background What is
An analysis of patterns and causes over
 Downtime in digital hospitals: An analysis of patterns and causes over 33 months Jessica CHEN Ying WANG and Farah MAGRABI Graduate School of Biomedical Engineering, UNSW Centre for Health Informatics,
Downtime in digital hospitals: An analysis of patterns and causes over 33 months Jessica CHEN Ying WANG and Farah MAGRABI Graduate School of Biomedical Engineering, UNSW Centre for Health Informatics,
CompSci 356: Computer Network Architectures. Lecture 23: Application Layer Protocols Chapter 9.1. Xiaowei Yang
 CompSci 356: Computer Network Architectures Lecture 23: Application Layer Protocols Chapter 9.1 Xiaowei Yang xwy@cs.duke.edu The Internet Architecture Application layer Transport layer / Layer 4 Network
CompSci 356: Computer Network Architectures Lecture 23: Application Layer Protocols Chapter 9.1 Xiaowei Yang xwy@cs.duke.edu The Internet Architecture Application layer Transport layer / Layer 4 Network
ES Financials Tips & Techniques 14/03/2016
 THE AUSTRALIAN NATIONAL UNIVERSITY F&BS Business Solutions ES Financials Tips & Techniques 14/03/2016 Changes in Purchase Order Dispatch Methods Overview Note: Label "Vendor" in PS v9.1 is replaced with
THE AUSTRALIAN NATIONAL UNIVERSITY F&BS Business Solutions ES Financials Tips & Techniques 14/03/2016 Changes in Purchase Order Dispatch Methods Overview Note: Label "Vendor" in PS v9.1 is replaced with
Protecting the AXIGEN Messaging Solution with NOD32
 Protecting the AXIGEN Messaging Solution with NOD32 GECAD Technologies 10A Dimitrie Pompei Blvd., BUCHAREST 2, ROMANIA Tel.: +40 21 303 20 80 +40 21 303 20 81 http://www.axigen.com Last modified: 1/29/2007
Protecting the AXIGEN Messaging Solution with NOD32 GECAD Technologies 10A Dimitrie Pompei Blvd., BUCHAREST 2, ROMANIA Tel.: +40 21 303 20 80 +40 21 303 20 81 http://www.axigen.com Last modified: 1/29/2007
Uputstvo za podešavanje mail klijenta
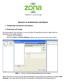 Uputstvo za podešavanje mail klijenta 1. Podešavanje Thunderbird mail klijenta 1.1 Dodavanje mail naloga Da biste podesili Vaš mail klijent (u ovom slučaju Thunderbird) da prima i šalje mail-ove potrebno
Uputstvo za podešavanje mail klijenta 1. Podešavanje Thunderbird mail klijenta 1.1 Dodavanje mail naloga Da biste podesili Vaš mail klijent (u ovom slučaju Thunderbird) da prima i šalje mail-ove potrebno
Envelope Journaling for Microsoft Exchange 2003 Version 1.0
 Barracuda Message Archiver Organizations using Microsoft Exchange 2003 can take advantage of its envelope journaling feature to send all messages along with all recipient information directly to the Barracuda
Barracuda Message Archiver Organizations using Microsoft Exchange 2003 can take advantage of its envelope journaling feature to send all messages along with all recipient information directly to the Barracuda
New Web Outlook. Look and Feel: You can personalize your Web Outlook by using Themes. Click on Options and select the desired Theme.
 New Web Outlook Look and Feel: You can personalize your Web Outlook by using Themes. Click on Options and select the desired Theme. Reading Messages: You can double click to view an email message. Options
New Web Outlook Look and Feel: You can personalize your Web Outlook by using Themes. Click on Options and select the desired Theme. Reading Messages: You can double click to view an email message. Options
Password Change and Mail Client Configuration Guide for sltnet.lk/slt.lk Mail Server
 User Guide Password Change and Mail Client Configuration Guide for sltnet.lk/slt.lk Mail Server 2018/05/10 LEGAL INFORMATION Copyright 2018 Sri Lanka Telecom Plc All rights reserved. We reserve the right
User Guide Password Change and Mail Client Configuration Guide for sltnet.lk/slt.lk Mail Server 2018/05/10 LEGAL INFORMATION Copyright 2018 Sri Lanka Telecom Plc All rights reserved. We reserve the right
ESMTP Support for Cisco IOS Firewall
 ESMTP Support for Cisco IOS Firewall Finding Feature Information ESMTP Support for Cisco IOS Firewall Last Updated: June 14, 2011 The ESMTP Support for Cisco IOS Firewall feature enhances the Cisco IOS
ESMTP Support for Cisco IOS Firewall Finding Feature Information ESMTP Support for Cisco IOS Firewall Last Updated: June 14, 2011 The ESMTP Support for Cisco IOS Firewall feature enhances the Cisco IOS
12/2/2011. Integration of s into the Trial Master File. Russell Joyce. Heath Barrowcliff Consulting Ltd. Disclaimer
 Integration of emails into the Trial Master File Russell Joyce Director & Principal i Consultant t Heath Barrowcliff Consulting Ltd Disclaimer The views and opinions expressed in the following PowerPoint
Integration of emails into the Trial Master File Russell Joyce Director & Principal i Consultant t Heath Barrowcliff Consulting Ltd Disclaimer The views and opinions expressed in the following PowerPoint
SPAM UNDERSTANDING & AVOIDING
 SPAM UNDERSTANDING & AVOIDING Modified: March 8, 2016 SPAM UNDERSTANDING & AVOIDING... 5 What is Spam?... 6 How to avoid Spam... 6 How to view message headers... 8 Checking and emptying Junk E-mail...
SPAM UNDERSTANDING & AVOIDING Modified: March 8, 2016 SPAM UNDERSTANDING & AVOIDING... 5 What is Spam?... 6 How to avoid Spam... 6 How to view message headers... 8 Checking and emptying Junk E-mail...
Python easy mail library Documentation
 Python easy mail library Documentation Release 1.0.2 Alain Spineux Oct 31, 2017 Contents 1 Download and Install 3 2 Support for Python 3.x 5 3 Use pyzmail 7 4 Documentation 9 4.1 Articles..................................................
Python easy mail library Documentation Release 1.0.2 Alain Spineux Oct 31, 2017 Contents 1 Download and Install 3 2 Support for Python 3.x 5 3 Use pyzmail 7 4 Documentation 9 4.1 Articles..................................................
Request for Comments: 1652
 Network Working Group Request for Comments: 1652 Obsoletes: 1426 Category: Standards Track J. Klensin, WG Chair MCI N. Freed, Editor Innosoft M. Rose Dover Beach Consulting, Inc. E. Stefferud Network Management
Network Working Group Request for Comments: 1652 Obsoletes: 1426 Category: Standards Track J. Klensin, WG Chair MCI N. Freed, Editor Innosoft M. Rose Dover Beach Consulting, Inc. E. Stefferud Network Management
MPDS Configuration Sheet MS Outlook 2000 Mail Client
 Connecting Microsoft Outlook to a POP3 server. Pre-requisites: That the MPDS terminal is already connected to the Internet as described in previous integration documents, Microsoft Outlook is Installed,
Connecting Microsoft Outlook to a POP3 server. Pre-requisites: That the MPDS terminal is already connected to the Internet as described in previous integration documents, Microsoft Outlook is Installed,
Contents. Management. Client. Choosing One 1/20/17
 Contents Email Management CSCU9B2 Email clients choosing and using Email message header and content Emailing to lists of people In and out message management Mime attachments and HTML email SMTP, HTTP,
Contents Email Management CSCU9B2 Email clients choosing and using Email message header and content Emailing to lists of people In and out message management Mime attachments and HTML email SMTP, HTTP,
Milk Support Service Level Agreement
 Milk Support Service Level Agreement Document Owner: Milk (Student Planner System) Service Level Agreement (SLA) for: (CUSTOMER NAME) Revision History Version Date Contributor Modifications 1.0 May 2018
Milk Support Service Level Agreement Document Owner: Milk (Student Planner System) Service Level Agreement (SLA) for: (CUSTOMER NAME) Revision History Version Date Contributor Modifications 1.0 May 2018
Smtp Error My Code 554 Transaction Failed Data Reply
 Smtp Error My Code 554 Transaction Failed Data Reply Enter there the connection data to your SMTP server. Save your Return code: (SMTP 554 - Transaction failed.). My client would like to receive notification
Smtp Error My Code 554 Transaction Failed Data Reply Enter there the connection data to your SMTP server. Save your Return code: (SMTP 554 - Transaction failed.). My client would like to receive notification
09/25/2015 Functional Acknowledgment Table of Contents
 Table of Contents 997 Functional Acknowledgment....................................................................................... ... 1 ST Transaction Set.........................................................................................
Table of Contents 997 Functional Acknowledgment....................................................................................... ... 1 ST Transaction Set.........................................................................................
Design and Implementation of a DMARC Verification Result Notification System
 Proceedings of the APAN Research Workshop 2016 ISBN 978-4-9905448-6-7 Design and Implementation of a DMARC Verification Result Notification System Naoya Kitagawa, Toshiki Tanaka, Masami Fukuyama and Nariyoshi
Proceedings of the APAN Research Workshop 2016 ISBN 978-4-9905448-6-7 Design and Implementation of a DMARC Verification Result Notification System Naoya Kitagawa, Toshiki Tanaka, Masami Fukuyama and Nariyoshi
Motivation For Networking. Information access Interaction among cooperative application programs Resource sharing
 Motivation For Networking Information access Interaction among cooperative application programs Resource sharing CS422 -- PART 1 13 2003 Practical Results E-mail File transfer/access Web browsing Remote
Motivation For Networking Information access Interaction among cooperative application programs Resource sharing CS422 -- PART 1 13 2003 Practical Results E-mail File transfer/access Web browsing Remote
Re: Shirk Family Gift to BCPA Jim Mack to: Jo-Anna Ramsay
 Re: Shirk Family Gift to BCPA Mack to: 08/28/2018 03:48 PM I want to believe that by the end of the week of the City Council meeting in which it's approved, a check will be mailed. However, I'm hesitant
Re: Shirk Family Gift to BCPA Mack to: 08/28/2018 03:48 PM I want to believe that by the end of the week of the City Council meeting in which it's approved, a check will be mailed. However, I'm hesitant
Backtracing s. Mag. iur. Dr. techn. Michael Sonntag
 Mag. iur. Dr. techn. Michael Sonntag Backtracing E-Mails E-Mail: michael.sonntag@jku.at http://www.fim.uni-linz.ac.at/staff/sonntag.htm Institute for Information Processing and Microprocessor Technology
Mag. iur. Dr. techn. Michael Sonntag Backtracing E-Mails E-Mail: michael.sonntag@jku.at http://www.fim.uni-linz.ac.at/staff/sonntag.htm Institute for Information Processing and Microprocessor Technology
BEST PRACTICES FOR PERSONAL Security
 BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
E-POST OFFICE USER SUPPORT
 E-POST OFFICE USER SUPPORT Issued November 2017 1 E-Post Office CONTENTS 1 Service description 3 2 Registration 4 3 E-Post Office in the portal 5 3.1 Home 5 3.2 E-letter 5 3.2.1 Archive folder structure
E-POST OFFICE USER SUPPORT Issued November 2017 1 E-Post Office CONTENTS 1 Service description 3 2 Registration 4 3 E-Post Office in the portal 5 3.1 Home 5 3.2 E-letter 5 3.2.1 Archive folder structure
Internet Engineering Task Force (IETF) Request for Comments: 6591 April 2012 Category: Standards Track ISSN:
 Internet Engineering Task Force (IETF) H. Fontana Request for Comments: 6591 April 2012 Category: Standards Track ISSN: 2070-1721 Authentication Failure Reporting Using the Abuse Reporting Format Abstract
Internet Engineering Task Force (IETF) H. Fontana Request for Comments: 6591 April 2012 Category: Standards Track ISSN: 2070-1721 Authentication Failure Reporting Using the Abuse Reporting Format Abstract
Internet Engineering Task Force (IETF) Request for Comments: 6522 STD: 73 January 2012 Obsoletes: 3462 Category: Standards Track ISSN:
 Internet Engineering Task Force (IETF) M. Kucherawy, Ed. Request for Comments: 6522 Cloudmark STD: 73 January 2012 Obsoletes: 3462 Category: Standards Track ISSN: 2070-1721 Abstract The Multipart/Report
Internet Engineering Task Force (IETF) M. Kucherawy, Ed. Request for Comments: 6522 Cloudmark STD: 73 January 2012 Obsoletes: 3462 Category: Standards Track ISSN: 2070-1721 Abstract The Multipart/Report
SMTP Simple Mail Transfer Protocol
 SMTP Simple Mail Transfer Protocol What is SMTP? SMTP stands for Simple Mail Transfer Protocol. This protocol allows transmitting electronic mail over the Internet or any other network. The protocol itself
SMTP Simple Mail Transfer Protocol What is SMTP? SMTP stands for Simple Mail Transfer Protocol. This protocol allows transmitting electronic mail over the Internet or any other network. The protocol itself
Content Filters. Overview of Content Filters. How Content Filters Work. This chapter contains the following sections:
 This chapter contains the following sections: Overview of, page 1 How Work, page 1 Content Filter Conditions, page 2 Content Filter Actions, page 9 How to Filter Messages Based on Content, page 17 Overview
This chapter contains the following sections: Overview of, page 1 How Work, page 1 Content Filter Conditions, page 2 Content Filter Actions, page 9 How to Filter Messages Based on Content, page 17 Overview
BUP2 5/2 12/4/07 12:49 AM Page 1. Introduction
 BUP2 5/2 12/4/07 12:49 AM Page 1 Introduction This booklet will give you easy to follow instructions to allow you to set your BUP2 Programmer to the Weekday/Weekend, (same times Monday - Friday, different
BUP2 5/2 12/4/07 12:49 AM Page 1 Introduction This booklet will give you easy to follow instructions to allow you to set your BUP2 Programmer to the Weekday/Weekend, (same times Monday - Friday, different
FIPS Management. FIPS Management Overview. Configuration Changes in FIPS Mode
 This chapter contains the following sections: Overview, on page 1 Configuration Changes in FIPS Mode, on page 1 Switching the Appliance to FIPS Mode, on page 2 Encrypting Sensitive Data in FIPS Mode, on
This chapter contains the following sections: Overview, on page 1 Configuration Changes in FIPS Mode, on page 1 Switching the Appliance to FIPS Mode, on page 2 Encrypting Sensitive Data in FIPS Mode, on
Case 3:09-cv F Document Filed 04/07/11 Page 17 of 23 PageID 16514
 Case 3:09-cv-00988-F Document 440-1 Filed 04/07/11 Page 17 of 23 PageID 16514 To: "'Elizabeth M. Schurig'" , "'jeffbaron1@gmail.com'" , "Michelle Rosenblatt" ,
Case 3:09-cv-00988-F Document 440-1 Filed 04/07/11 Page 17 of 23 PageID 16514 To: "'Elizabeth M. Schurig'" , "'jeffbaron1@gmail.com'" , "Michelle Rosenblatt" ,
Microsoft Outlook Tips and Tricks
 Microsoft Outlook Tips and Tricks Signatures 1. Click on File at the top left and click Options on the left side menu. 2. Click on Mail on the left and then click on the Signatures button. 3. Create your
Microsoft Outlook Tips and Tricks Signatures 1. Click on File at the top left and click Options on the left side menu. 2. Click on Mail on the left and then click on the Signatures button. 3. Create your
E-POST OFFICE USER SUPPORT
 E-POST OFFICE USER SUPPORT Issued November 2018 CONTENTS 1 Service description 3 2 Registration 4 3 E-Post Office in the portal 5 3.1 Archive (homepage) 5 3.2 E-letter 5 3.2.1 Archive folder structure
E-POST OFFICE USER SUPPORT Issued November 2018 CONTENTS 1 Service description 3 2 Registration 4 3 E-Post Office in the portal 5 3.1 Archive (homepage) 5 3.2 E-letter 5 3.2.1 Archive folder structure
Anti-Spoofing. Inbound SPF Settings
 Anti-Spoofing SonicWall Hosted Email Security solution allows you to enable and configure settings to prevent illegitimate messages from entering your organization. Spoofing consists of an attacker forging
Anti-Spoofing SonicWall Hosted Email Security solution allows you to enable and configure settings to prevent illegitimate messages from entering your organization. Spoofing consists of an attacker forging
Oracle Communications Messaging Server
 Oracle Communications Messaging Server MTA Developer's Reference Release 8.0 July 2015 Oracle Communications Messaging Server MTA Developer's Reference, Release 8.0 Copyright 2007, 2015, Oracle and/or
Oracle Communications Messaging Server MTA Developer's Reference Release 8.0 July 2015 Oracle Communications Messaging Server MTA Developer's Reference, Release 8.0 Copyright 2007, 2015, Oracle and/or
anti-spam techniques beyond Bayesian filters
 anti-spam techniques beyond Bayesian filters Plain Old SMTP protocol overview Grey-Listing save resources on receiver side Authentication of Senders Sender ID Framework DomainKeys signingbased IP-based
anti-spam techniques beyond Bayesian filters Plain Old SMTP protocol overview Grey-Listing save resources on receiver side Authentication of Senders Sender ID Framework DomainKeys signingbased IP-based
Mail Protocol, Postfix and Mail security
 Mail Protocol, Postfix and Mail security How Email Appears to Works How Email Really Works Message Format Envelop Routing information for the "postman" Message Header Sender Recipients (simple, lists,
Mail Protocol, Postfix and Mail security How Email Appears to Works How Email Really Works Message Format Envelop Routing information for the "postman" Message Header Sender Recipients (simple, lists,
TRACS Tenant Informational Message Codes... F-2
 Appendix F:... F-2 August 2014 F-1 AD001 Insufficient street address information for mail delivery by the USPS. Resubmit MAT15 update (tran type 3) with valid street address. AD002 Multiple matching addresses
Appendix F:... F-2 August 2014 F-1 AD001 Insufficient street address information for mail delivery by the USPS. Resubmit MAT15 update (tran type 3) with valid street address. AD002 Multiple matching addresses
