Be certain. MessageLabs Intelligence: May 2006
|
|
|
- Barbra Farmer
- 5 years ago
- Views:
Transcription
1 Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep you informed in the ongoing fight against viruses, spam and other unwelcome content. Global s & Content Analysis MessageLabs Anti-Spam and Anti-Virus Services focus on identifying and averting unwanted communications originating from unknown bad sources and which are addressed to valid recipients. Over the last few months, it has become increasingly apparent that as the technological arms race escalates, SMEs are now more than ever being confronted with the same security threats as larger enterprises, however, as the threats become more sophisticated, smaller companies are finding it more difficult to keep pace and safeguard their information systems. According to the latest Information Security Breaches Survey of 1,000 UK businesses and produced by the DTI and PricewaterhouseCoopers, nearly three times as many companies now have a security policy as did six years ago, and 98% of businesses have anti-virus software in place; 80% of which update their signatures every day. Although the number of companies infected has fallen, the average number of infections each company suffered rose to roughly one per day, with several businesses reporting hundreds of infections per day, with around a quarter of companies reporting a virus as their worst incident, causing major disruption. According to the same report, 86% of the companies surveyed also filtered incoming for spam. The report also noted that a quarter of UK businesses are not protected against spyware and 40% of businesses that allow instant messaging, have no controls in place over its use. In recent months, new issues such as Domain Kiting (or Disposable Domains ) and Spam Cannons have escalated to become much more of a serious threat than they were even a few months earlier. Disposable Domains was an issue first raised in the MessageLabs Intelligence 2005 End-of-Year report, but is now apparently being exploited by spammers via certain domain registrars using the controversial RFC 3915 Domain Registry Grace Period Mapping for the Extensible Provisioning Protocol loophole. Spyware has become intrinsic to the means by which bot technology has further converged with viruses, trojans and spam and the boundaries between them are almost impossible to distinguish. A traditional botnet may be likened with peas in a tube by pushing one pea in, another pea pops-out at the other end botnets provide this degree of anonymity, but are not often very scalable. However, the latest techniques use a mail-merge tactic that combines lists of harvested names and addresses with templates all downloaded from a control server on demand thus transforming the pea-shooters of old into a veritable spam cannon able to pump out millions of s per hour using mass-mailing, mail-merge technology. MessageLabs 2006
2 Skeptic Anti-Spam Protection: In May, the global ratio of spam in traffic from new and unknown bad sources, for which the recipient addresses were deemed valid, was (1 in 1.7), a decrease of 0.6% on the previous month. Spam rate 100 % 80% 60% 40% Peak: July % Avg. 59.8% 58.5% % Skeptic Anti-Virus and Trojan Protection: The global ratio of -borne viruses in traffic from new and previously unknown bad sources destined for valid recipients, was 1 in 67.1 (1.5%) in May, a decrease of 0.3% since April. Virus rate 1 in in in 0 1 in 20 1 in 40 1 in 60 1 in 80 1 in 100 Peak: Apr 04 1 in 10.4 Avg. 1 in in in 120 Phishing: May showed an increase of 0.03% in the proportion of phishing attacks compared with the previous month. One in (0.31%) s was a phishing attack. The number of phishing attacks also increased by 5.2% as a proportion of all -borne threats, now accounting for 20.8% of all malicious s intercepted by MessageLabs in May. Phishing 1 in in in 0 1 in in in in in 500 Peak: Jan 05 1 in 127 Avg. 1 in in in 600 2
3 Geographical Breakdown: Based on Targeted Countries By analyzing the geographical dispersal of traffic where possible, MessageLabs compiles data that shows the impact and vulnerability rates of spam and viruses for specific countries. The charts below reflect impact and ratios for May 2006: Spam rate by geography Hong Kong 67.9% Israel 64.0% United States 50.6% United Kingdom 49.9% Germany 47.2% Japan India % The country being on the receiving end of the greatest proportion of spam again is Hong Kong, dropping by only 1.4% on the previous month. The greatest increase was seen in Malaysia (ranked 18th in the list), where spam accounted for 20% of volume last month, but now accounts for 31%. The highest drop was seen in Canada (ranked 11th in the list), which fell by 7.8% to 40.3%. All of those in the top-5 decreased by an average of 2.1% compared with the April figures, with the exception of the UK, which bucked the trend with spam increasing by 2% on the previous month. Virus rate by geography India 1 in 9.6 Malaysia 1 in 15.1 Singapore 1 in 21.2 United Arab Emirates 1 in 21.6 Germany 1 in 32.6 Netherlands Sweden 1 in in Again, India continues to suffer as the most profusely affected country in the virus chart, the proportion of virus laden s decreasing by only 3.7% to 1 in 9.6, since April. The greatest increase in virus traffic was seen in Malaysia, where virus borne traffic rose by 4.5% on the previous month to 1 in
4 Vertical Industry Breakdown By analyzing the market distribution of traffic where possible, MessageLabs compiles data that shows the impact and vulnerability rates of spam and viruses specific to major industry sectors. The charts below reflect impacts and ratios for May 2006: Spam rate by vertical Chem/Pharm 61.4% Business Support Services 61.3% Recreation 58.6% Education IT Services 54.8% Virus rate by vertical Wholesale 1 in 21.5 Education 1 in 33.7 Manufacturing 1 in 39.9 Accom/Catering 1 in 43.8 Non-Profit 1 in 50.8 Accom/Catering Finance 38.5% 36.9% Finance Telcoms 1 in in The vertical most affected by spam is the Chemical & Pharmaceutical industry, with the greatest increase in the proportion of spam in traffic from the previous month. Increasing by 4.5% to 61.4% in May, the Chemical & Pharmaceutical sector ranks at number one in May. The greatest drop was within the Wholesale sector (ranked 12th this month), which saw spam traffic falling by 9% to 43.6%. The vertical most targeted in May, with 1 in 21.5 of containing a virus, was the Wholesale sector. Even with a slight fall of only 1.3% when compared with the previous month, it still manages to take the top spot from Business Support Services (now ranked 15th), which bore the greatest fall of 17.4% to now 0.9% (1 in 106.6). The Education sector witnessed the greatest rise in virus traffic, with 1 in s harboring a virus; this is an increase of 0.9% since April. Traffic Management (Protocol Level) Traffic Management continues to reduce the overall message volume through techniques operating at the protocol level. Unwanted senders are identified and connections to the mail server are slowed down using features embedded in the TCP protocol. Incoming volumes of known spam are significantly slowed, while ensuring legitimate is expedited. Connection Management Connection Management is particularly effective in stopping directory harvest, brute force and denial of service attacks, where unwanted senders send high volumes of messages to force spam into an organization or disrupt business communications. Connection Management works at the SMTP level using techniques that verify legitimate connections to the mail server, and is comprised of the following: SMTP Validation: Identifies unwanted originating from known spam and virus sending sources, where the source can unequivocally be identified as an open proxy or a botnet, and rejects the connection accordingly. In May, on average 6.1% of inbound messages were intercepted from botnets and other known malicious sources and rejected as a consequence. Registered User Address Validation: Reduces the overall volume of s for registered domains, by discarding connections for which the recipients are identified as invalid or non-existent. In May, on average 10.8% of recipient addresses were identified as invalid; these were attempted directory attacks upon domains that were therefore prevented. The table below details the current impact of connection management techniques on unwanted volume being 4
5 measured by MessageLabs Intelligence. Without these additional multiple layers of defense, spam traffic destined for MessageLabs clients in May would otherwise account for an average of 82.5% of global traffic. Region SMTP Validation (botnet sources) User Validation (directory attacks) USA 7.30% 11.20% UK 4.90% 10.10% Europe 5.40% 10.00% Asia Pacific 4.30% 15.40% Worldwide 6.10% 10.80% Effects of Connection Management Techniques MessageLabs is the world s leading provider of security and management services with more than 13,000 clients. MessageLabs Intelligence is a respected source of data and analysis for security issues, trends and statistics. MessageLabs provides a range of information on global security threats based on live data feeds from its control towers around the world. For further information on MessageLabs Intelligence, please visit and register to receive regular alerts and reports. NB: All figures mentioned in this report were correct at the time of going to press. 5
MessageLabs Intelligence: October 2006 Do you want spam with that spam?
 Be certain MessageLabs Intelligence: October 2006 Do you want spam with that spam? Introduction Welcome to the October edition of the MessageLabs Intelligence monthly report. This report provides the latest
Be certain MessageLabs Intelligence: October 2006 Do you want spam with that spam? Introduction Welcome to the October edition of the MessageLabs Intelligence monthly report. This report provides the latest
MessageLabs Intelligence: August 2007 Storm botnet serves-up a diet of fast-flux spam
 Be certain MessageLabs Intelligence: August 2007 Storm botnet serves-up a diet of fast-flux spam Introduction Welcome to the August 2007 edition of the MessageLabs Intelligence monthly report. This report
Be certain MessageLabs Intelligence: August 2007 Storm botnet serves-up a diet of fast-flux spam Introduction Welcome to the August 2007 edition of the MessageLabs Intelligence monthly report. This report
May 2011 Intelligence Report
 Symantec.cloud MessageLabs Intelligence May 2011 Intelligence Report For the First Time, Spammers Establish Their Own Fake URL-Shortening Services; Spam Rate Rises by 2.9% Welcome to the May edition of
Symantec.cloud MessageLabs Intelligence May 2011 Intelligence Report For the First Time, Spammers Establish Their Own Fake URL-Shortening Services; Spam Rate Rises by 2.9% Welcome to the May edition of
IBM Express Managed Security Services for Security. Anti-Virus Administrator s Guide. Version 5.31
 IBM Express Managed Security Services for Email Security Anti-Virus Administrator s Guide Version 5.31 Table of Contents 1. Service overview...3 1.1 Welcome... 3 1.2 Anti-Virus (AV) features... 3 1.3 How
IBM Express Managed Security Services for Email Security Anti-Virus Administrator s Guide Version 5.31 Table of Contents 1. Service overview...3 1.1 Welcome... 3 1.2 Anti-Virus (AV) features... 3 1.3 How
Top 10 Global Threat Rank by Source
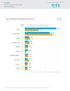 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Internet Security Threat Report Volume XIII. Patrick Martin Senior Product Manager Symantec Security Response October, 2008
 Internet Security Threat Report Volume XIII Patrick Martin Senior Product Manager Symantec Security Response October, 2008 Agenda 1 ISTR XIII Important Facts 2 ISTR XIII Key Messages 3 ISTR XIII Key Facts
Internet Security Threat Report Volume XIII Patrick Martin Senior Product Manager Symantec Security Response October, 2008 Agenda 1 ISTR XIII Important Facts 2 ISTR XIII Key Messages 3 ISTR XIII Key Facts
Israel Internet Security Threat Profile
 Israel Internet Security Threat Profile Worldwide Ranking.%.%.%.%.%.%.%.%.%.%.% Overall Average Spam Zombies Malicious Code Phishing Hosts Bots Network Attacking Countries Copyright Symantec Corporation.
Israel Internet Security Threat Profile Worldwide Ranking.%.%.%.%.%.%.%.%.%.%.% Overall Average Spam Zombies Malicious Code Phishing Hosts Bots Network Attacking Countries Copyright Symantec Corporation.
Securing Your Business Against the Diversifying Targeted Attacks Leonard Sim
 Securing Your Business Against the Diversifying Targeted Attacks Leonard Sim Manager, Client & Partner Services, Asia 1 Agenda 2010 Threats Targeted Attacks Defense Against Targeted Attacks Questions 2
Securing Your Business Against the Diversifying Targeted Attacks Leonard Sim Manager, Client & Partner Services, Asia 1 Agenda 2010 Threats Targeted Attacks Defense Against Targeted Attacks Questions 2
Intelligent and Secure Network
 Intelligent and Secure Network BIG-IP IP Global Delivery Intelligence v11.2 IP Intelligence Service Brian Boyan - b.boyan@f5.com Tony Ganzer t.ganzer@f5.com 2 Agenda Welcome & Intro Introduce F5 IP Intelligence
Intelligent and Secure Network BIG-IP IP Global Delivery Intelligence v11.2 IP Intelligence Service Brian Boyan - b.boyan@f5.com Tony Ganzer t.ganzer@f5.com 2 Agenda Welcome & Intro Introduce F5 IP Intelligence
Perimeter Defenses T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN
 T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN Perimeter Defenses Enterprises need to take their security strategy beyond stacking up layers of perimeter defenses to building up predictive
T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN Perimeter Defenses Enterprises need to take their security strategy beyond stacking up layers of perimeter defenses to building up predictive
SYMANTEC ENTERPRISE SECURITY. Symantec Internet Security Threat Report September 2005 Power and Energy Industry Data Sheet
 SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
Cisco Service Control Service Security: Outgoing Spam Mitigation Solution Guide, Release 4.1.x
 CISCO SERVICE CONTROL SOLUTION GUIDE Cisco Service Control Service Security: Outgoing Spam Mitigation Solution Guide, Release 4.1.x 1 Introduction and Scope 2 Functionality Overview 3 Mass-Mailing-Based
CISCO SERVICE CONTROL SOLUTION GUIDE Cisco Service Control Service Security: Outgoing Spam Mitigation Solution Guide, Release 4.1.x 1 Introduction and Scope 2 Functionality Overview 3 Mass-Mailing-Based
>MESSAGELABS END USER IT SECURITY GUIDE >WHAT STEPS CAN YOU TAKE TO KEEP YOURSELF, YOUR COLLEAGUES AND YOUR COMPANY SAFE ONLINE?
 >MESSAGELABS END USER IT SECURITY GUIDE >WHAT STEPS CAN YOU TAKE TO KEEP YOURSELF, YOUR COLLEAGUES AND YOUR COMPANY SAFE ONLINE? >CONTENTS >WHAT IS MESSAGING AND WEB SECURITY? >P1 >EMAIL THREATS >P1 >VIRUSES
>MESSAGELABS END USER IT SECURITY GUIDE >WHAT STEPS CAN YOU TAKE TO KEEP YOURSELF, YOUR COLLEAGUES AND YOUR COMPANY SAFE ONLINE? >CONTENTS >WHAT IS MESSAGING AND WEB SECURITY? >P1 >EMAIL THREATS >P1 >VIRUSES
Phishing Activity Trends Report August, 2005
 Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection White Paper September 2017 www.cyren.com 1 White Paper September 2017 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
Fighting Spam, Phishing and Malware With Recurrent Pattern Detection White Paper September 2017 www.cyren.com 1 White Paper September 2017 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
Prolexic Attack Report Q4 2011
 Prolexic Attack Report Q4 2011 Prolexic believes the nature of DDoS attacks are changing: they are becoming more concentrated and damaging. Packet-per-second volume is increasing dramatically, while attack
Prolexic Attack Report Q4 2011 Prolexic believes the nature of DDoS attacks are changing: they are becoming more concentrated and damaging. Packet-per-second volume is increasing dramatically, while attack
Data Communication. Chapter # 5: Networking Threats. By: William Stalling
 Data Communication Chapter # 5: By: Networking Threats William Stalling Risk of Network Intrusion Whether wired or wireless, computer networks are quickly becoming essential to everyday activities. Individuals
Data Communication Chapter # 5: By: Networking Threats William Stalling Risk of Network Intrusion Whether wired or wireless, computer networks are quickly becoming essential to everyday activities. Individuals
UTM 5000 WannaCry Technote
 UTM 5000 WannaCry Technote The news is full of reports of the massive ransomware infection caused by WannaCry. Although these security threats are pervasive, and ransomware has been around for a decade,
UTM 5000 WannaCry Technote The news is full of reports of the massive ransomware infection caused by WannaCry. Although these security threats are pervasive, and ransomware has been around for a decade,
INSIDE. Symantec AntiVirus for Microsoft Internet Security and Acceleration (ISA) Server. Enhanced virus protection for Web and SMTP traffic
 Virus Protection & Content Filtering TECHNOLOGY BRIEF Symantec AntiVirus for Microsoft Internet Security and Acceleration (ISA) Server Enhanced virus protection for Web and SMTP traffic INSIDE The need
Virus Protection & Content Filtering TECHNOLOGY BRIEF Symantec AntiVirus for Microsoft Internet Security and Acceleration (ISA) Server Enhanced virus protection for Web and SMTP traffic INSIDE The need
Red Condor had. during. testing. Vx Technology high availability. AntiSpam,
 Lab Testing Summary Report July 21 Report 167 Product Category: Email Security Solution Vendors Tested: MessageLabs/Symantec MxLogic/McAfee SaaS Products Tested: - Cloudfilter; MessageLabs/Symantec Email
Lab Testing Summary Report July 21 Report 167 Product Category: Email Security Solution Vendors Tested: MessageLabs/Symantec MxLogic/McAfee SaaS Products Tested: - Cloudfilter; MessageLabs/Symantec Email
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
Cisco s Appliance-based Content Security: IronPort and Web Security
 Cisco s Appliance-based Content Security: IronPort E-mail and Web Security Hrvoje Dogan Consulting Systems Engineer, Security, Emerging Markets East 2010 Cisco and/or its affiliates. All rights reserved.
Cisco s Appliance-based Content Security: IronPort E-mail and Web Security Hrvoje Dogan Consulting Systems Engineer, Security, Emerging Markets East 2010 Cisco and/or its affiliates. All rights reserved.
McAfee Labs Threat Report
 McAfee Labs Threat Report December 217 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threat Report, December 217 The McAfee Labs count of new malware in Q3 reached an all-time
McAfee Labs Threat Report December 217 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threat Report, December 217 The McAfee Labs count of new malware in Q3 reached an all-time
Phishing Activity Trends Report August, 2006
 Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Second International Barometer of Security in SMBs
 1 2 Contents 1. Introduction. 3 2. Methodology.... 5 3. Details of the companies surveyed 6 4. Companies with security systems 10 5. Companies without security systems. 15 6. Infections and Internet threats.
1 2 Contents 1. Introduction. 3 2. Methodology.... 5 3. Details of the companies surveyed 6 4. Companies with security systems 10 5. Companies without security systems. 15 6. Infections and Internet threats.
MESSAGING SECURITY GATEWAY. Solution overview
 MESSAGING SECURITY GATEWAY Solution overview April 2017 CONTENTS Executive Summary...3 The case for email protection and privacy... 3 Privacy in email communication... 3 LinkedIn Phishing Sample...4 Messaging
MESSAGING SECURITY GATEWAY Solution overview April 2017 CONTENTS Executive Summary...3 The case for email protection and privacy... 3 Privacy in email communication... 3 LinkedIn Phishing Sample...4 Messaging
Global DDoS Threat Landscape
 DDOS REPORT Global DDoS Threat Landscape OVERVIEW Overview The number of network layer attacks continued to fall in, the fourth consecutive quarterly drop since peaking in Q2 2016. After reaching a record
DDOS REPORT Global DDoS Threat Landscape OVERVIEW Overview The number of network layer attacks continued to fall in, the fourth consecutive quarterly drop since peaking in Q2 2016. After reaching a record
Distributed Denial of Service (DDoS)
 Global Leader in DDoS Mitigation Threat Report Distributed Denial of Service (DDoS) Threat Report Q1 2017 456 Montgomery Street, Suite 800 San Francisco, CA 94104 USA +1 415 299 8550 Contents 1. Methodology...................
Global Leader in DDoS Mitigation Threat Report Distributed Denial of Service (DDoS) Threat Report Q1 2017 456 Montgomery Street, Suite 800 San Francisco, CA 94104 USA +1 415 299 8550 Contents 1. Methodology...................
For example, if a message is both a virus and spam, the message is categorized as a virus as virus is higher in precedence than spam.
 About Anti-Spam NOTE: Anti-Spam is a separate, licensed feature that provides a quick, efficient, and effective way to add anti-spam, anti-phishing, and anti-virus capabilities to your existing firewall.
About Anti-Spam NOTE: Anti-Spam is a separate, licensed feature that provides a quick, efficient, and effective way to add anti-spam, anti-phishing, and anti-virus capabilities to your existing firewall.
Phishing: When is the Enemy
 Phishing: When E-mail is the Enemy Phishing, once only a consumer worry, is creating headaches for e-mail administrators as businesses become the next target. CONTENTS Understanding the Enemy 2 Three Things
Phishing: When E-mail is the Enemy Phishing, once only a consumer worry, is creating headaches for e-mail administrators as businesses become the next target. CONTENTS Understanding the Enemy 2 Three Things
CASE STUDY: REGIONAL BANK
 CASE STUDY: REGIONAL BANK Concerned about unauthorised network traffic, a regional bank in the MD/DC/VA area contracted GBMS Tech Ltd to monitor the banks various security systems. GBMS Tech Ltd uncovered
CASE STUDY: REGIONAL BANK Concerned about unauthorised network traffic, a regional bank in the MD/DC/VA area contracted GBMS Tech Ltd to monitor the banks various security systems. GBMS Tech Ltd uncovered
Marshal s Defense-in-Depth Anti-Spam Engine
 Marshal s Defense-in-Depth Anti-Spam Engine January 2008 Contents Overview 2 Features 3 Summary 6 This whitepaper explores the underlying anti-spam and anti-phishing defense technology in Marshal s world
Marshal s Defense-in-Depth Anti-Spam Engine January 2008 Contents Overview 2 Features 3 Summary 6 This whitepaper explores the underlying anti-spam and anti-phishing defense technology in Marshal s world
Office 365 Integration Guide Software Version 6.7
 rat Office 365 Integration Guide Software Version 6.7 Guide Version 6.7.061418 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction...3 1.1 Email Flow Explanation...3
rat Office 365 Integration Guide Software Version 6.7 Guide Version 6.7.061418 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction...3 1.1 Email Flow Explanation...3
The Mimecast Security Risk Assessment Quarterly Report May 2017
 The Mimecast Email Security Risk Assessment Quarterly Report May 2017 The Mimecast Email Security Risk Assessment Quarterly Report May 2017 Many organizations think their current email security systems
The Mimecast Email Security Risk Assessment Quarterly Report May 2017 The Mimecast Email Security Risk Assessment Quarterly Report May 2017 Many organizations think their current email security systems
VIETNAM CYBER-SAVVINESS REPORT 2015 CYBERSECURITY: USER KNOWLEDGE, BEHAVIOUR AND ATTITUDES IN VIETNAM
 VIETNAM CYBER-SAVVINESS REPORT 2015 CYBERSECURITY: USER KNOWLEDGE, BEHAVIOUR AND ATTITUDES IN VIETNAM 1. Why did ESET Undertake this Report? 2. Report Methodology 3. Key Highlights 4. How Many users in
VIETNAM CYBER-SAVVINESS REPORT 2015 CYBERSECURITY: USER KNOWLEDGE, BEHAVIOUR AND ATTITUDES IN VIETNAM 1. Why did ESET Undertake this Report? 2. Report Methodology 3. Key Highlights 4. How Many users in
2015 VORMETRIC INSIDER THREAT REPORT
 Research Conducted by Research Analyzed by 2015 VORMETRIC INSIDER THREAT REPORT Trends and Future Directions in Data Security GLOBAL EDITION #2015InsiderThreat EXECUTIVE PERSPECTIVE 1 INSIDER THREATS:
Research Conducted by Research Analyzed by 2015 VORMETRIC INSIDER THREAT REPORT Trends and Future Directions in Data Security GLOBAL EDITION #2015InsiderThreat EXECUTIVE PERSPECTIVE 1 INSIDER THREATS:
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Protecting DNS Critical Infrastructure Solution Overview. Radware Attack Mitigation System (AMS) - Whitepaper
 Protecting DNS Critical Infrastructure Solution Overview Radware Attack Mitigation System (AMS) - Whitepaper Table of Contents Introduction...3 DNS DDoS Attacks are Growing and Evolving...3 Challenges
Protecting DNS Critical Infrastructure Solution Overview Radware Attack Mitigation System (AMS) - Whitepaper Table of Contents Introduction...3 DNS DDoS Attacks are Growing and Evolving...3 Challenges
JPCERT/CC Incident Handling Report [January 1, March 31, 2018]
![JPCERT/CC Incident Handling Report [January 1, March 31, 2018] JPCERT/CC Incident Handling Report [January 1, March 31, 2018]](/thumbs/89/100577955.jpg) JPCERT-IR-2018-01 Issued: 2018-04-12 JPCERT/CC Incident Handling Report [January 1, 2018 - March 31, 2018] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
JPCERT-IR-2018-01 Issued: 2018-04-12 JPCERT/CC Incident Handling Report [January 1, 2018 - March 31, 2018] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
Franzes Francisco Manila IBM Domino Server Crash and Messaging
 Franzes Francisco Manila IBM Domino Server Crash and Messaging Topics to be discussed What is SPAM / email Spoofing? How to identify one? Anti-SPAM / Anti-email spoofing basic techniques Domino configurations
Franzes Francisco Manila IBM Domino Server Crash and Messaging Topics to be discussed What is SPAM / email Spoofing? How to identify one? Anti-SPAM / Anti-email spoofing basic techniques Domino configurations
PDF Spam: Spam Evolves, PDF becomes the Latest Threat
 PDF Spam: Spam Evolves, PDF becomes the Latest Threat A MessageLabs Whitepaper: August 2007 Nick Johnston, Anti-Spam Development at MessageLabs Table of Contents Introduction 3 The Beginning of PDF Spam
PDF Spam: Spam Evolves, PDF becomes the Latest Threat A MessageLabs Whitepaper: August 2007 Nick Johnston, Anti-Spam Development at MessageLabs Table of Contents Introduction 3 The Beginning of PDF Spam
Background. Threats. Present Status. Challenges and Strategies 9/30/2009 TRAI 2
 9/30/2009 TRAI 1 Background Threats Present Status Challenges and Strategies 9/30/2009 TRAI 2 Critical infrastructure means the computers, computer systems, and/or networks, whether physical or virtual,
9/30/2009 TRAI 1 Background Threats Present Status Challenges and Strategies 9/30/2009 TRAI 2 Critical infrastructure means the computers, computer systems, and/or networks, whether physical or virtual,
Advanced Threat Defense Certification Testing Report. Trend Micro Incorporated Trend Micro Deep Discovery Inspector
 Advanced Threat Defense Certification Testing Report Trend Micro Deep Discovery Inspector ICSA Labs Advanced Threat Defense July 12, 2016 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Advanced Threat Defense Certification Testing Report Trend Micro Deep Discovery Inspector ICSA Labs Advanced Threat Defense July 12, 2016 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
QUARTERLY TRENDS AND ANALYSIS REPORT
 September 1, 2007 Volume 2, Issue 3 QUARTERLY TRENDS AND ANALYSIS REPORT www.us-cert.gov Introduction This report summarizes and provides analysis of incident reports submitted to US-CERT during the U.S.
September 1, 2007 Volume 2, Issue 3 QUARTERLY TRENDS AND ANALYSIS REPORT www.us-cert.gov Introduction This report summarizes and provides analysis of incident reports submitted to US-CERT during the U.S.
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of July, 2007 Summarization of July Report Findings For the first time recorded by the APWG, China has surpassed the United States as the country hosting the
Phishing Activity Trends Report for the Month of July, 2007 Summarization of July Report Findings For the first time recorded by the APWG, China has surpassed the United States as the country hosting the
Symantec Protection Suite Add-On for Hosted Security
 Symantec Protection Suite Add-On for Hosted Email Security Overview Malware and spam pose enormous risk to the health and viability of IT networks. Cyber criminal attacks are focused on stealing money
Symantec Protection Suite Add-On for Hosted Email Security Overview Malware and spam pose enormous risk to the health and viability of IT networks. Cyber criminal attacks are focused on stealing money
GFI MailSecurity 2011 for Exchange/SMTP. Administration & Configuration Manual
 GFI MailSecurity 2011 for Exchange/SMTP Administration & Configuration Manual http://www.gfi.com info@gfi.com The information and content in this document is provided for informational purposes only and
GFI MailSecurity 2011 for Exchange/SMTP Administration & Configuration Manual http://www.gfi.com info@gfi.com The information and content in this document is provided for informational purposes only and
Phishing Activity Trends Report. 3 rd Quarter Unifying the. Global Response To Cybercrime. July September 2012
 3 rd Quarter 2012 Unifying the Global Response To Cybercrime July September 2012 Published February 1, 2013 , Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member
3 rd Quarter 2012 Unifying the Global Response To Cybercrime July September 2012 Published February 1, 2013 , Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member
IBM Managed Security Services for Security
 Service Description 1. Scope of Services IBM Managed Security Services for E-mail Security IBM Managed Security Services for E-mail Security (called MSS for E-mail Security ) may include: a. E-mail Antivirus
Service Description 1. Scope of Services IBM Managed Security Services for E-mail Security IBM Managed Security Services for E-mail Security (called MSS for E-mail Security ) may include: a. E-mail Antivirus
New Zealand National Cyber Security Centre Incident Summary
 New Zealand National Cyber Security Centre 2013 Incident Summary National Cyber Security Centre 2013 Incident Summary Foreword The incidents summarised in this report reinforce that cyber security is truly
New Zealand National Cyber Security Centre 2013 Incident Summary National Cyber Security Centre 2013 Incident Summary Foreword The incidents summarised in this report reinforce that cyber security is truly
IBM Managed Security Services (Cloud Computing) hosted and Web security - express managed security
 IBM Managed Security Services (Cloud Computing) hosted e-mail and Web security - express managed e-mail security Z125-8581-01 12-2010 Page 1 of 15 Table of Contents 1. Scope of Services... 3 2. Definitions...
IBM Managed Security Services (Cloud Computing) hosted e-mail and Web security - express managed e-mail security Z125-8581-01 12-2010 Page 1 of 15 Table of Contents 1. Scope of Services... 3 2. Definitions...
Web Application Threat Trend Report
 Web Application Threat Trend Report Trends for 2017 Penta Security Systems Inc. Contents I. Overview II. Executive Summary III. 2017 Web Application Threat Trends 1. Overall Trends 2. Trends in Primary
Web Application Threat Trend Report Trends for 2017 Penta Security Systems Inc. Contents I. Overview II. Executive Summary III. 2017 Web Application Threat Trends 1. Overall Trends 2. Trends in Primary
Botnets: major players in the shadows. Author Sébastien GOUTAL Chief Science Officer
 Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
Security Gap Analysis: Aggregrated Results
 Email Security Gap Analysis: Aggregrated Results Average rates at which enterprise email security systems miss spam, phishing and malware attachments November 2017 www.cyren.com 1 Email Security Gap Analysis:
Email Security Gap Analysis: Aggregrated Results Average rates at which enterprise email security systems miss spam, phishing and malware attachments November 2017 www.cyren.com 1 Email Security Gap Analysis:
THE ACCENTURE CYBER DEFENSE SOLUTION
 THE ACCENTURE CYBER DEFENSE SOLUTION A MANAGED SERVICE FOR CYBER DEFENSE FROM ACCENTURE AND SPLUNK. YOUR CURRENT APPROACHES TO CYBER DEFENSE COULD BE PUTTING YOU AT RISK Cyber-attacks are increasingly
THE ACCENTURE CYBER DEFENSE SOLUTION A MANAGED SERVICE FOR CYBER DEFENSE FROM ACCENTURE AND SPLUNK. YOUR CURRENT APPROACHES TO CYBER DEFENSE COULD BE PUTTING YOU AT RISK Cyber-attacks are increasingly
Sales Training
 Sales Training Extensible Content Security 16.03.2010 2009 WatchGuard Technologies Market Opportunity Total Addressable Market, ($M) Total Addressable Market by Segment, ($M) 16,000 14,000 11.2% CAGR 16,000
Sales Training Extensible Content Security 16.03.2010 2009 WatchGuard Technologies Market Opportunity Total Addressable Market, ($M) Total Addressable Market by Segment, ($M) 16,000 14,000 11.2% CAGR 16,000
Radware Attack Mitigation Solution (AMS) Protect Online Businesses and Data Centers Against Emerging Application & Network Threats - Whitepaper
 Radware Attack Mitigation Solution (AMS) Protect Online Businesses and Data Centers Against Emerging Application & Network Threats - Whitepaper Table of Contents Abstract...3 Understanding Online Business
Radware Attack Mitigation Solution (AMS) Protect Online Businesses and Data Centers Against Emerging Application & Network Threats - Whitepaper Table of Contents Abstract...3 Understanding Online Business
Phishing Activity Trends Report January, 2005
 Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of June, 2007 Summarization of June Report Findings In the June 2007 report the APWG introduces a brand-domain pairs measurement (page 4) which combines the
Phishing Activity Trends Report for the Month of June, 2007 Summarization of June Report Findings In the June 2007 report the APWG introduces a brand-domain pairs measurement (page 4) which combines the
GFI product comparison: GFI MailEssentials vs Symantec Mail Security for Microsoft Exchange 7.5
 GFI product comparison: GFI MailEssentials vs Symantec Mail Security for Microsoft Exchange 7.5 Features GFI MailEssentials Symantec Mail Security for Microsoft Exchange 7.5 Integrates with Microsoft Exchange
GFI product comparison: GFI MailEssentials vs Symantec Mail Security for Microsoft Exchange 7.5 Features GFI MailEssentials Symantec Mail Security for Microsoft Exchange 7.5 Integrates with Microsoft Exchange
Building Resilience in a Digital Enterprise
 Building Resilience in a Digital Enterprise Top five steps to help reduce the risk of advanced targeted attacks To be successful in business today, an enterprise must operate securely in the cyberdomain.
Building Resilience in a Digital Enterprise Top five steps to help reduce the risk of advanced targeted attacks To be successful in business today, an enterprise must operate securely in the cyberdomain.
Automating Security Response based on Internet Reputation
 Add Your Logo here Do not use master Automating Security Response based on Internet Reputation IP and DNS Reputation for the IPS Platform Anthony Supinski Senior Systems Engineer www.h3cnetworks.com www.3com.com
Add Your Logo here Do not use master Automating Security Response based on Internet Reputation IP and DNS Reputation for the IPS Platform Anthony Supinski Senior Systems Engineer www.h3cnetworks.com www.3com.com
ISO in the world today
 ISO 27001 in the world today 1 Agenda ISO 27001 worldwide Why ISO 27001 Framework to implement ISO 27001 2 ISO 27001 worldwide Source: ISO Annual Survey 3 ISO 27001 worldwide Number of Certificates Year
ISO 27001 in the world today 1 Agenda ISO 27001 worldwide Why ISO 27001 Framework to implement ISO 27001 2 ISO 27001 worldwide Source: ISO Annual Survey 3 ISO 27001 worldwide Number of Certificates Year
The Anatomy of IM Threats
 The Anatomy of IM Threats INTRODUCTION: INSTANT MESSAGING THREATS AT RECORD LEVELS While instant messaging (IM) has grown steadily in popularity over the past few years, the threats associated with IM
The Anatomy of IM Threats INTRODUCTION: INSTANT MESSAGING THREATS AT RECORD LEVELS While instant messaging (IM) has grown steadily in popularity over the past few years, the threats associated with IM
Spam Evolution Report: October 2009
 Spam Evolution Report: October 2009 Prepare by Kaspersky Lab,a leading manufacturer of secure content management solutions About Kaspersky Lab Kaspersky Lab delivers the world s most immediate protection
Spam Evolution Report: October 2009 Prepare by Kaspersky Lab,a leading manufacturer of secure content management solutions About Kaspersky Lab Kaspersky Lab delivers the world s most immediate protection
Seqrite Endpoint Security
 Enterprise Security Solutions by Quick Heal Integrated enterprise security and unified endpoint management console Enterprise Suite Edition Product Highlights Innovative endpoint security that prevents
Enterprise Security Solutions by Quick Heal Integrated enterprise security and unified endpoint management console Enterprise Suite Edition Product Highlights Innovative endpoint security that prevents
Phishing Activity Trends Report March, 2005
 Phishing Activity Trends Report March, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report March, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Basic Concepts in Intrusion Detection
 Technology Technical Information Services Security Engineering Roma, L Università Roma Tor Vergata, 23 Aprile 2007 Basic Concepts in Intrusion Detection JOVAN GOLIĆ Outline 2 Introduction Classification
Technology Technical Information Services Security Engineering Roma, L Università Roma Tor Vergata, 23 Aprile 2007 Basic Concepts in Intrusion Detection JOVAN GOLIĆ Outline 2 Introduction Classification
GFI product comparison: GFI MailEssentials vs. McAfee Security for Servers
 GFI product comparison: GFI MailEssentials vs. McAfee Security for Email Servers Features GFI MailEssentials McAfee Integrates with Microsoft Exchange Server 2003/2007/2010/2013 Scans incoming and outgoing
GFI product comparison: GFI MailEssentials vs. McAfee Security for Email Servers Features GFI MailEssentials McAfee Integrates with Microsoft Exchange Server 2003/2007/2010/2013 Scans incoming and outgoing
BOTNET-GENERATED SPAM
 BOTNET-GENERATED SPAM By Areej Al-Bataineh University of Texas at San Antonio MIT Spam Conference 2009 www.securitycartoon.com 3/27/2009 Areej Al-Bataineh - Botnet-generated Spam 2 1 Botnets: A Global
BOTNET-GENERATED SPAM By Areej Al-Bataineh University of Texas at San Antonio MIT Spam Conference 2009 www.securitycartoon.com 3/27/2009 Areej Al-Bataineh - Botnet-generated Spam 2 1 Botnets: A Global
ENDPOINT SECURITY WHITE PAPER. Endpoint Security and the Case For Automated Sandboxing
 WHITE PAPER Endpoint Security and the Case For Automated Sandboxing A World of Constant Threat We live in a world of constant threat. Every hour of every day in every country around the globe hackers are
WHITE PAPER Endpoint Security and the Case For Automated Sandboxing A World of Constant Threat We live in a world of constant threat. Every hour of every day in every country around the globe hackers are
JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015]
![JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015]](/thumbs/83/87837079.jpg) JPCERT-IR-2015-05 Issued: 2016-01-14 JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
JPCERT-IR-2015-05 Issued: 2016-01-14 JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
Korea Phishing Activity Trends Report
 Korea Phishing Activity Trends Report June, 2006 Issued by KrCERT/CC, Korea Internet Security Center Korea Phishing Activity Trends Report analyzes phishing attacks reported to KrCERT/CC via the organization
Korea Phishing Activity Trends Report June, 2006 Issued by KrCERT/CC, Korea Internet Security Center Korea Phishing Activity Trends Report analyzes phishing attacks reported to KrCERT/CC via the organization
GFI product comparison: GFI MailEssentials vs. Trend Micro ScanMail Suite for Microsoft Exchange
 GFI product comparison: GFI MailEssentials vs. Trend Micro ScanMail Suite for Microsoft Exchange Features GFI MailEssentials Trend Micro ScanMail Suite for Microsoft Exchange Integrates with Microsoft
GFI product comparison: GFI MailEssentials vs. Trend Micro ScanMail Suite for Microsoft Exchange Features GFI MailEssentials Trend Micro ScanMail Suite for Microsoft Exchange Integrates with Microsoft
Easy Activation Effortless web-based administration that can be activated in as little as one business day - no integration or migration necessary.
 Security Solutions Our security suite protects against email spam, viruses, web-based threats and spyware while delivering disaster recovery, giving you peace of mind so you can focus on what matters most:
Security Solutions Our security suite protects against email spam, viruses, web-based threats and spyware while delivering disaster recovery, giving you peace of mind so you can focus on what matters most:
Security report Usuario de Test
 Security report Usuario de Test Servidor Cloud Period: 2018/MAY/13-2018/MAY/20 INDEX SUMMARY 2 Overview 3 Comparison with other users 5 Services and IPs included in this report 6 Traffic 7 Inbound and
Security report Usuario de Test Servidor Cloud Period: 2018/MAY/13-2018/MAY/20 INDEX SUMMARY 2 Overview 3 Comparison with other users 5 Services and IPs included in this report 6 Traffic 7 Inbound and
JPCERT/CC Internet Threat Monitoring Report [July 1, September 30, 2014]
![JPCERT/CC Internet Threat Monitoring Report [July 1, September 30, 2014] JPCERT/CC Internet Threat Monitoring Report [July 1, September 30, 2014]](/thumbs/85/91527925.jpg) JPCERT-IA-2014-03 Issued: 2014-10-28 JPCERT/CC Internet Threat Monitoring Report [July 1, 2014 - September 30, 2014] 1 Overview JPCERT/CC has placed multiple sensors across the Internet for monitoring
JPCERT-IA-2014-03 Issued: 2014-10-28 JPCERT/CC Internet Threat Monitoring Report [July 1, 2014 - September 30, 2014] 1 Overview JPCERT/CC has placed multiple sensors across the Internet for monitoring
Detecting Spammers with SNARE: Spatio-temporal Network-level Automatic Reputation Engine
 Detecting Spammers with SNARE: Spatio-temporal Network-level Automatic Reputation Engine Shuang Hao, Nadeem Ahmed Syed, Nick Feamster, Alexander G. Gray, Sven Krasser Motivation Spam: More than Just a
Detecting Spammers with SNARE: Spatio-temporal Network-level Automatic Reputation Engine Shuang Hao, Nadeem Ahmed Syed, Nick Feamster, Alexander G. Gray, Sven Krasser Motivation Spam: More than Just a
Samu Konttinen, CEO, F-Secure WE ARE F-SECURE. 1 F-Secure
 Samu Konttinen, CEO, F-Secure WE ARE F-SECURE 1 F-SECURE A FRONT RUNNER IN CYBER SECURITY We are the largest European single source of cyber security services and detection and response solutions for companies,
Samu Konttinen, CEO, F-Secure WE ARE F-SECURE 1 F-SECURE A FRONT RUNNER IN CYBER SECURITY We are the largest European single source of cyber security services and detection and response solutions for companies,
MX Control Console. Administrative User Manual
 MX Control Console Administrative User Manual This Software and Related Documentation are proprietary to MX Logic, Inc. Copyright 2003 MX Logic, Inc. The information contained in this document is subject
MX Control Console Administrative User Manual This Software and Related Documentation are proprietary to MX Logic, Inc. Copyright 2003 MX Logic, Inc. The information contained in this document is subject
Phishing Activity Trends Report. 3 rd Quarter Committed to Wiping Out Internet Scams and Fraud
 3 rd Quarter 2009 Committed to Wiping Out Internet Scams and Fraud July September 2009 Phishing Report Scope The quarterly APWG analyzes phishing attacks reported to the APWG by its member companies, its
3 rd Quarter 2009 Committed to Wiping Out Internet Scams and Fraud July September 2009 Phishing Report Scope The quarterly APWG analyzes phishing attacks reported to the APWG by its member companies, its
IC B01: Internet Security Threat Report: How to Stay Protected
 IC B01: Internet Security Threat Report: How to Stay Protected Piero DePaoli Director, Product Marketing IC B01: Internet Security Threat Report: How to Stay Protected 1 Topics 1 Targeted Attacks 2 Spam
IC B01: Internet Security Threat Report: How to Stay Protected Piero DePaoli Director, Product Marketing IC B01: Internet Security Threat Report: How to Stay Protected 1 Topics 1 Targeted Attacks 2 Spam
FRANKFORT PLANT BOARD CABLE MODEM INTERNET BROADBAND INTERNET SERVICE DISCLOSURES
 FRANKFORT PLANT BOARD CABLE MODEM INTERNET BROADBAND INTERNET SERVICE DISCLOSURES Consistent with FCC 1 regulations, Frankfort Plant Board (FPB) provides this information about our broadband Internet access
FRANKFORT PLANT BOARD CABLE MODEM INTERNET BROADBAND INTERNET SERVICE DISCLOSURES Consistent with FCC 1 regulations, Frankfort Plant Board (FPB) provides this information about our broadband Internet access
Protecting against tomorrow s threats today proactive security from SophosLabs
 Protecting against tomorrow s threats today proactive security from SophosLabs Constantly looking for new vulnerabilities to exploit, today s cybercriminals are using fastchanging, low-profile threats
Protecting against tomorrow s threats today proactive security from SophosLabs Constantly looking for new vulnerabilities to exploit, today s cybercriminals are using fastchanging, low-profile threats
VERISIGN DISTRIBUTED DENIAL OF SERVICE TRENDS REPORT
 VERISIGN DISTRIBUTED DENIAL OF SERVICE TRENDS REPORT VOLUME 4, ISSUE 1 1ST QUARTER 2017 Complimentary report supplied by CONTENTS EXECUTIVE SUMMARY 3 VERISIGN-OBSERVED DDoS ATTACK TRENDS: Q1 2017 4 DDoS
VERISIGN DISTRIBUTED DENIAL OF SERVICE TRENDS REPORT VOLUME 4, ISSUE 1 1ST QUARTER 2017 Complimentary report supplied by CONTENTS EXECUTIVE SUMMARY 3 VERISIGN-OBSERVED DDoS ATTACK TRENDS: Q1 2017 4 DDoS
NYMBLE INTERNET ACCESS SERVICE DISCLOSURES
 NYMBLE INTERNET ACCESS SERVICE DISCLOSURES Consistent with FCC regulations, Nymble Internet Service provides this information about our Internet access services ( Nymble or Nymble services ). We welcome
NYMBLE INTERNET ACCESS SERVICE DISCLOSURES Consistent with FCC regulations, Nymble Internet Service provides this information about our Internet access services ( Nymble or Nymble services ). We welcome
Panda Security 2010 Page 1
 Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
Cybersecurity. Anna Chan, Marketing Director, Akamai Technologies
 Grow revenue opportunities with fast, personalized web experiences and manage complexity from peak demand, mobile Business devices and Continuity data collection. & Cybersecurity Anna Chan, Marketing Director,
Grow revenue opportunities with fast, personalized web experiences and manage complexity from peak demand, mobile Business devices and Continuity data collection. & Cybersecurity Anna Chan, Marketing Director,
Cyber War Chronicles Stories from the Virtual Trenches
 Cyber War Chronicles Stories from the Virtual Trenches Ron Winward Security Evangelist Radware, Inc. March 17, 2016 Background on the Radware Report Key Cyber Attack Trends for 2015-2016 Case Study: Look
Cyber War Chronicles Stories from the Virtual Trenches Ron Winward Security Evangelist Radware, Inc. March 17, 2016 Background on the Radware Report Key Cyber Attack Trends for 2015-2016 Case Study: Look
Computer Security. Solutions
 Computer Security Solutions What is the Problem? In general, the security issues we are trying to prevent include: illegal or unwanted access to your computer access to your personal information loss or
Computer Security Solutions What is the Problem? In general, the security issues we are trying to prevent include: illegal or unwanted access to your computer access to your personal information loss or
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR UAE
 EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR UAE 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
EMC GLOBAL DATA PROTECTION INDEX KEY FINDINGS & RESULTS FOR UAE 1 THE DATA PROTECTION LANDSCAPE ARE YOU ON SOLID GROUND? 2 GLOBAL KEY FINDINGS GLOBALLY, ENTERPRISES ARE LOSING AS MUCH AS $1.7 TRILLION
Spam Filtering Works Better With a Management Policy
 Select Q&A, M. Grey, A. Hallawell Research Note 22 September 2003 Spam Filtering Works Better With a Management Policy A deployment of spam-filtering technology that does not consider business issues will
Select Q&A, M. Grey, A. Hallawell Research Note 22 September 2003 Spam Filtering Works Better With a Management Policy A deployment of spam-filtering technology that does not consider business issues will
Training UNIFIED SECURITY. Signature based packet analysis
 Training UNIFIED SECURITY Signature based packet analysis At the core of its scanning technology, Kerio Control integrates a packet analyzer based on Snort. Snort is an open source IDS/IPS system that
Training UNIFIED SECURITY Signature based packet analysis At the core of its scanning technology, Kerio Control integrates a packet analyzer based on Snort. Snort is an open source IDS/IPS system that
2015 DDoS Attack Trends and 2016 Outlook
 CDNetworks 2015 DDoS Attack Trends and 2016 Outlook 2016, January CDNetworks Security Service Team Table of Contents 1. Introduction... 3 2. Outline... 3 3. DDoS attack trends... 4 4. DDoS attack outlook
CDNetworks 2015 DDoS Attack Trends and 2016 Outlook 2016, January CDNetworks Security Service Team Table of Contents 1. Introduction... 3 2. Outline... 3 3. DDoS attack trends... 4 4. DDoS attack outlook
ADVANCED THREAT PREVENTION FOR ENDPOINT DEVICES 5 th GENERATION OF CYBER SECURITY
 ADVANCED THREAT PREVENTION FOR ENDPOINT DEVICES 5 th GENERATION OF CYBER SECURITY OUTLINE Advanced Threat Landscape (genv) Why is endpoint protection essential? Types of attacks and how to prevent them
ADVANCED THREAT PREVENTION FOR ENDPOINT DEVICES 5 th GENERATION OF CYBER SECURITY OUTLINE Advanced Threat Landscape (genv) Why is endpoint protection essential? Types of attacks and how to prevent them
INSIDE. Integrated Security: Creating the Secure Enterprise. Symantec Enterprise Security
 Symantec Enterprise Security WHITE PAPER Integrated Security: Creating the Secure Enterprise INSIDE Evolving IT and business environments The impact of network attacks on business The logical solution
Symantec Enterprise Security WHITE PAPER Integrated Security: Creating the Secure Enterprise INSIDE Evolving IT and business environments The impact of network attacks on business The logical solution
Technical Brochure F-SECURE THREAT SHIELD
 Technical Brochure F-SECURE THREAT SHIELD F-SECURE THREATSHIELD F-Secure ThreatShield is a gateway-level security solution for protecting email and web traffic, with built-in network sandboxing technology.
Technical Brochure F-SECURE THREAT SHIELD F-SECURE THREATSHIELD F-Secure ThreatShield is a gateway-level security solution for protecting email and web traffic, with built-in network sandboxing technology.
GFI product comparison: GFI MailEssentials vs. Barracuda Spam Firewall
 GFI product comparison: GFI MailEssentials vs. Barracuda Spam Firewall Features GFI MailEssentials Barracuda Spam Firewall Integrates with Microsoft Exchange Server 2007/2010/2013 Scans incoming and outgoing
GFI product comparison: GFI MailEssentials vs. Barracuda Spam Firewall Features GFI MailEssentials Barracuda Spam Firewall Integrates with Microsoft Exchange Server 2007/2010/2013 Scans incoming and outgoing
THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION BREACH & ATTACK SIMULATION
 BREACH & ATTACK SIMULATION THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION Cymulate s cyber simulation platform allows you to test your security assumptions, identify possible security gaps and receive
BREACH & ATTACK SIMULATION THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION Cymulate s cyber simulation platform allows you to test your security assumptions, identify possible security gaps and receive
Creating Threat Prevention Connection Rules
 Creating Threat Prevention Connection Rules The Threat Prevention feature runs a connection rules script each time a client tries to connect to eprism. The script determines whether to accept or reject
Creating Threat Prevention Connection Rules The Threat Prevention feature runs a connection rules script each time a client tries to connect to eprism. The script determines whether to accept or reject
