Using Network Based Application Recognition and ACLs for Blocking the "Code Red" Worm
|
|
|
- Piers Wright
- 5 years ago
- Views:
Transcription
1 Using Network Based Application Recognition and ACLs for Blocking the "Code Red" Worm Document ID: Contents Introduction Prerequisites Requirements Components Used Conventions How to Block the "Code Red" Worm Supported Platforms Detect the Infection Attempt in the IIS Web Logs Mark Inbound "Code Red" Hacks Using IOS Class Based Marking Feature Method A: Use an ACL Method B: Use Policy Based Routing (PBR) Method C: Use Class Based Policing NBAR Restrictions Known Issues Related Information Introduction This document provides a method for blocking the "Code Red" worm at network ingress points through Network Based Application Recognition (NBAR) and Access Control Lists (ACLs) within Cisco IOS Software on Cisco routers. This solution should be used in conjunction with the recommended patches for IIS servers from Microsoft. Note: This method does not work on Cisco 1600 series routers. Note: Some P2P traffic cannot be completely blocked due to the nature of its P2P protocol. These P2P protocols dynamically change their signatures to bypass any DPI engines trying to completely block their traffic. Therefore, it is recommended to limit the bandwidth instead of completely blocking them. Throttle the bandwidth for this traffic. Give much less bandwidth; however, let the connection go through. Prerequisites Requirements Cisco recommends that you have knowledge of these topics: Quality of Service (QoS) service policies using the commands of the modular QoS command line interface (CLI). NBAR ACLs Policy based routing
2 Components Used This document is not restricted to specific software and hardware versions. The configuration in this document was tested on the Cisco 3640 that runs Cisco IOS version 12.2(24a) The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command. Conventions Refer to Cisco Technical Tips Conventions for more information on document conventions. How to Block the "Code Red" Worm The first thing you should do to combat "Code Red" is apply the patch available from Microsoft (see links in section Method A: Use an ACL below). This protects vulnerable systems and removes the worm from an infected system. However, applying the patch to your servers only prevents the worm from infecting the servers, it does not stop the HTTP GET requests from hitting the servers. There is still the potential for the server to get bombarded with a flood of infection attempts. The solution detailed in this advisory is designed to work in conjunction with the Microsoft patch to block the "Code Red" HTTP GET requests at a network ingress point. This solution attempts to block the infection, however it will not cure problems caused by the buildup of large numbers of cache entries, adjacencies, and NAT/PAT entries, since the only way to analyze the contents of the HTTP GET request is following the establishment of a TCP connection. The following procedure will not help protect against a scan of the network. However, it will protect a site from infestation from an external network or reduce the number of infection attempts that a machine must service. In combination with inbound filtering, outbound filtering prevents infected clients from spreading the "Code Red" worm to the global Internet. Supported Platforms The solution described in this document requires the class based marking feature within Cisco IOS software. Specifically, the ability to match on any part of an HTTP URL uses the HTTP sub port classification feature within NBAR. The supported platforms and minimum Cisco IOS software requirements are summarized below: Platform Minimum Cisco IOS Software 12.2(8)T 12.2(8)T
3 (2)T Note: You need to enable Cisco Express Forwarding (CEF) in order to use NBAR. Class based marking and Distributed NBAR (DNBAR) are also available on the following platforms: 7500 Platform FlexWAN 12.1(6)E 12.1(6)E Minimum Cisco IOS Software Detect the Infection Attempt in the IIS Web Logs The initial infection attempt sends a large HTTP GET request to the target IIS server. The original "Code Red" footprint is shown below: :32: GET /default.ida NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN NNNNN%u9090%u6858%ucbd3%u7801%u9090%u6858%ucbd3%u7801%u9090%u6858%ucbd3%u 7801%u9090%u9090%u8190%u00c3%u0003%u8b00%u531b%u53ff%u0078%u0000%u00=a 403 The "Code Red" II footprint is shown below: :57: GET /default.ida XXXXXXXXXXX XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX%u9090 %u6858%ucbd3%u7801%u9090%u6858%ucbd3%u7801%u9090%u6858%ucbd3%u7801%u9090% u9090%u8190%u00c3%u0003%u8b00%u531b%u53ff%u0078%u0000%u00=a 403 Notice that the GET request is always looking for a file with an.ida extension. This is a common string in all infection attempts and can therefore be used as a match criteria with class based marking in IOS. The remainder of the GET request will not necessarily be consistent as it is just attempting to create a buffer overflow. This can be seen by comparing the two entries above. It is now being reported that the difference between these two signatures is due to a new strain of the "Code Red" worm, dubbed CodeRed.v3 or CodeRed.C. The original "Code Red" strain contains the "NNNNNNNN" string in the GET request, while the new strain contains "XXXXXXXX". Refer to the Symantec Advisory for more details. At 6:24PM EDT, 6 Aug 2001, we recorded a new footprint. We have since learned that this is the footprint that is left behind by the eeye vulnerability scanner :24: GET /x.ida AAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=X 403 HTTP/1.1 The technique for blocking "Code Red" provided in this advisory can also block these scanning attempts simply by tightening the class map definition as shown in the next section.
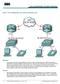
4 Mark Inbound "Code Red" Hacks Using IOS Class Based Marking Feature To block the "Code Red" worm, use one of the three methods described below. All three methods classify malicious traffic using the Cisco IOS MQC feature. This traffic is then dropped as described below. Method A: Use an ACL This method uses an ACL on the output interface to drop the marked "Code Red" packets. Let's use the following network diagram to illustrate the steps in this method: Here are the steps to configuring this method: 1. Classify inbound "Code Red" hacks with the class based marking feature in Cisco IOS software, as shown below: Router(config)#class map match any http hacks Router(config cmap)#match protocol http url "*default.ida*" Router(config cmap)#match protocol http url "*cmd.exe*" Router(config cmap)#match protocol http url "*root.exe*" The above class map looks inside of HTTP URLs and matches any of the specified strings. Notice that we have included other file names besides the default.ida of "Code Red". You can use this technique to block similar hack attempts, such as the Sadmind virus, which is explained in the following documents: asp 2. Build a policy and use the set command to mark inbound "Code Red" hacks with a policy map. This document uses a DSCP value of 1 (in decimal) since it is unlikely that any other network traffic is carrying this value. 3. Here we mark inbound "Code Red" hacks with a policy map named "mark inbound http hacks". Router(config)#policy map mark inbound http hacks Router(config pmap)#class http hacks Router(config pmap c)#set ip dscp 1 Apply the policy as an inbound policy on the input interface to mark arriving "Code Red" packets. Router(config)#interface serial 0/0 Router(config if)#service policy input mark inbound http hacks 4. Configure an ACL that matches on the DSCP value of 1, as set by the service policy. Router(config)#access list 105 deny ip any any dscp 1 Router(config)#access list 105 permit ip any any Note: Cisco IOS Software Releases 12.2(11) and 12.2(11)T introduce support for the log keyword on the ACL in defining on class maps for use with NBAR (CSCdv48172). If you are using an earlier
5 5. release, do not use the log keyword on the ACL. Doing so forces all packets to be process switched instead of CEF switched, and NBAR will not work since it requires CEF. Apply the ACL outbound on the output interface that connects to the target Web servers. Router(config)#interface ethernet 0/1 Router(config if)#ip access group 105 out 6. Verify that your solution works as expected. Execute the show access list command and ensure that the "matches" value for the deny statement is incrementing. Router#show access list 105 Extended IP access list 105 deny ip any any dscp 1 log (2406 matches) permit ip any any ( matches) In the configuration step, you can also disable sending IP unreachable messages with the no ip unreachable interface level command to avoid causing the router to expend excessive resources. This method is not recommended if you can policy route the DSCP=1 traffic to Null 0, as described in the Method B section. Method B: Use Policy Based Routing (PBR) This method uses policy based routing to block marked "Code Red" packets. You do not need to apply the commands in this method if methods A or C are already configured. Here are the steps to implementing this method: 1. Classify the traffic and mark it. Use the class map and policy map commands shown in method A. 2. Use the service policy command to apply the policy as an inbound policy on the input interface to mark arriving "Code Red" packets. See method A. 3. Create an extended IP ACL that matches on the marked "Code Red" packets. Router(config)#access list 106 permit ip any any dscp 1 4. Use the route map command to build a routing policy. 5. Router(config)#route map null_policy_route 10 Router(config route map)#match ip address 106 Router(config route map)#set interface Null0 Apply the route map to the input interface. Router(config)#interface serial 0/0 Router(config if)#ip policy route map null_policy_route 6. Verify your solution works as expected with the show access list command. If you are using output ACLs and have enabled ACL logging, you also can use the show log commands, as shown below: Router#show access list 106 Extended IP access list 106 permit ip any any dscp 1 (1506 matches) Router#show log Aug 4 13:25:20: %SEC 6 IPACCESSLOGP: list 105 denied tcp A.B.C.D.(0) > (0), 6 packets
6 Aug 4 13:26:32: %SEC 6 IPACCESSLOGP: list 105 denied tcp A.B.C.D.(0) > (0), 6 packets We are able to make the discard decision at the ingress interface of the router, rather than needing an output ACL on every egress interface. Again, we recommend disabling the sending IP unreachable messages with the command no ip unreachables command. Method C: Use Class Based Policing This method generally is the most scalable as it does not depend on either PBR or output ACLs. 1. Classify the traffic using the class map commands shown in method A. 2. Build a policy using the policy map command and use the police command to specify a drop action for this traffic. Router(config)#policy map drop inbound http hacks Router(config pmap)#class http hacks Router(config pmap c)#police conform action drop exceed action drop violate action drop 3. Use the service policy command to apply the policy as an inbound policy on the input interface to drop the "Code Red" packets. Router(config)#interface serial 0/0 Router(config if)#service policy input drop inbound http hacks 4. Verify that your solution works as expected with the show policy map interface command. Ensure that you see incrementing values for the class and the individual match criteria. Router#show policy map interface serial 0/0 Serial0/0 Service policy input: drop inbound http hacks Class map: http hacks (match any) 5 packets, 300 bytes 5 minute offered rate 0 bps, drop rate 0 bps Match: protocol http url "*default.ida*" 5 packets, 300 bytes 5 minute rate 0 bps Match: protocol http url "*cmd.exe*" 0 packets, 0 bytes 5 minute rate 0 bps Match: protocol http url "*root.exe*" 0 packets, 0 bytes 5 minute rate 0 bps police: bps, limit, extended limit conformed 5 packets, 300 bytes; action: drop exceeded 0 packets, 0 bytes; action: drop violated 0 packets, 0 bytes; action: drop conformed 0 bps, exceed 0 bps, violate 0 bps Class map: class default (match any) 5 packets, 300 bytes 5 minute offered rate 0 bps, drop rate 0 bps Match: any
7 NBAR Restrictions When using NBAR with the methods in this document, note that the following features are not supported by NBAR: More than 24 concurrent URLs, HOSTs or MIME type matches Matching beyond the first 400 bytes in a URL Non IP traffic Multicast and other non CEF switching modes Fragmented packets Pipelined persistent HTTP requests URL/HOST/MIME/ classification with secure HTTP Asymmetric flows with stateful protocols Packets originating from or destined to the router running NBAR You can't configure NBAR on the following logical interfaces: Fast EtherChannel Interfaces that use tunneling or encryption VLANs Dialer interfaces Multilink PPP Note: NBAR is configurable on VLANs as of Cisco IOS Release 12.1(13)E, but supported in the software switching path only. Since NBAR cannot be used to classify output traffic on a WAN link where tunneling or encryption is used, apply it instead to other interfaces on the router, such as the LAN interface, to perform input classification before the traffic is switched to the WAN link for output. For more NBAR information, see the links in the Related Information section below. Known Issues The "Code Red" worm exploits a vulnerability on unpatched servers within IIS that uses the Microsoft Indexing Service. The Internet Data Administration script file (default.ida) is installed by default on all IIS servers. "Code Red" relies on the presence of this file to carry out the exploit. Most systems do not use this service so the blocking method provided in this advisory will be effective. However, some servers may use this service within IIS. In this case, the blocking method proposed here could block legitimate requests to the IIS server. Related Information Dealing with mallocfail and High CPU Utilization Resulting From the "Code Red" Worm Using Cisco Secure IDS/NetRanger Custom String Match Signatures for "Code Red" Worm Remote Buffer Overflow in Microsoft Index Server ISAPI Extension in IIS 4.0 and 5.0 Technical Support & Documentation Cisco Systems Contacts & Feedback Help Site Map Cisco Systems, Inc. All rights reserved. Terms & Conditions Privacy Statement Cookie Policy Trademarks of Cisco Systems, Inc.
8 Updated: Aug 02, 2006 Document ID: 27842
Control Plane Policing
 The feature allows you to configure a quality of service (QoS) filter that manages the traffic flow of control plane packets to protect the control plane of Cisco IOS XE routers and switches against reconnaissance
The feature allows you to configure a quality of service (QoS) filter that manages the traffic flow of control plane packets to protect the control plane of Cisco IOS XE routers and switches against reconnaissance
Q. What technologies does Cisco WAAS Express use to optimize traffic? A. Cisco WAAS Express optimizes WAN bandwidth using these technologies:
 Q&A Cisco WAAS Express General Q. What is Cisco Wide Area Application Services (WAAS) Express? A. Cisco WAAS Express extends the Cisco WAAS product portfolio with a small-footprint, cost-effective solution
Q&A Cisco WAAS Express General Q. What is Cisco Wide Area Application Services (WAAS) Express? A. Cisco WAAS Express extends the Cisco WAAS product portfolio with a small-footprint, cost-effective solution
NAT Support for Multiple Pools Using Route Maps
 NAT Support for Multiple Pools Using Route Maps Document ID: 13739 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Access List Approach Host 1 to Host
NAT Support for Multiple Pools Using Route Maps Document ID: 13739 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Access List Approach Host 1 to Host
Classifying Network Traffic
 Classifying Network Traffic Last Updated: December 2, 2011 Classifying network traffic allows you to organize traffic (that is, packets) into traffic classes or categories on the basis of whether the traffic
Classifying Network Traffic Last Updated: December 2, 2011 Classifying network traffic allows you to organize traffic (that is, packets) into traffic classes or categories on the basis of whether the traffic
Configuring Modular QoS Service Packet Classification
 Configuring Modular QoS Service Packet Classification This chapter covers these topics: Packet Classification Overview, page 1 Traffic Class Elements, page 2 Traffic Policy Elements, page 5 Traffic Policy
Configuring Modular QoS Service Packet Classification This chapter covers these topics: Packet Classification Overview, page 1 Traffic Class Elements, page 2 Traffic Policy Elements, page 5 Traffic Policy
EVC Quality of Service
 This document contains information about how to enable quality of service (QoS) features (such as traffic classification and traffic policing) for use on an Ethernet virtual circuit (EVC). An EVC as defined
This document contains information about how to enable quality of service (QoS) features (such as traffic classification and traffic policing) for use on an Ethernet virtual circuit (EVC). An EVC as defined
EVC Quality of Service
 First Published: March 28, 2011 Last Updated: March 28, 2011 This document contains information about how to enable quality of service (QoS) features (such as traffic classification and traffic policing)
First Published: March 28, 2011 Last Updated: March 28, 2011 This document contains information about how to enable quality of service (QoS) features (such as traffic classification and traffic policing)
Home Agent Quality of Service
 13 CHAPTER This chapter discusses concepts related to Quality of Service on the Cisco Mobile Wireless Home Agent, and provides details about how to configure this feature. This chapter includes the following
13 CHAPTER This chapter discusses concepts related to Quality of Service on the Cisco Mobile Wireless Home Agent, and provides details about how to configure this feature. This chapter includes the following
QoS Tunnel Marking for GRE Tunnels
 The feature introduces the capability to define and control the quality of service (QoS) for both incoming and outgoing customer traffic on the provider edge (PE) router in a service provider network.
The feature introduces the capability to define and control the quality of service (QoS) for both incoming and outgoing customer traffic on the provider edge (PE) router in a service provider network.
Understanding How Routing Updates and Layer 2 Control Packets Are Queued on an Interface with a QoS Service Policy
 Understanding How Routing Updates and Layer 2 Control Packets Are Queued on an Interface with a QoS Service Policy Document ID: 18664 Contents Introduction Prerequisites Requirements Components Used Conventions
Understanding How Routing Updates and Layer 2 Control Packets Are Queued on an Interface with a QoS Service Policy Document ID: 18664 Contents Introduction Prerequisites Requirements Components Used Conventions
EVC Quality of Service
 EVC Quality of Service Finding Feature Information EVC Quality of Service Last Updated: June 07, 2011 This document contains information about how to enable quality of service (QoS) features (such as traffic
EVC Quality of Service Finding Feature Information EVC Quality of Service Last Updated: June 07, 2011 This document contains information about how to enable quality of service (QoS) features (such as traffic
ASA Access Control. Section 3
 [ 39 ] CCNP Security Firewall 642-617 Quick Reference Section 3 ASA Access Control Now that you have connectivity to the ASA and have configured basic networking settings on the ASA, you can start to look
[ 39 ] CCNP Security Firewall 642-617 Quick Reference Section 3 ASA Access Control Now that you have connectivity to the ASA and have configured basic networking settings on the ASA, you can start to look
QoS: Policing and Shaping Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 920 Series)
 QoS: Policing and Shaping Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 920 Series) First Published: 2014-07-29 Last Modified: 2014-11-22 Americas Headquarters Cisco Systems, Inc. 170 West Tasman
QoS: Policing and Shaping Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 920 Series) First Published: 2014-07-29 Last Modified: 2014-11-22 Americas Headquarters Cisco Systems, Inc. 170 West Tasman
Per-Session QoS. Finding Feature Information
 The feature is one of two features bundled with the QoS: Broadband Aggregation Enhancements--Phase 1 feature. The feature provides the ability to apply quality of service (QoS) features (such as traffic
The feature is one of two features bundled with the QoS: Broadband Aggregation Enhancements--Phase 1 feature. The feature provides the ability to apply quality of service (QoS) features (such as traffic
Finding Support Information for Platforms and Cisco IOS and Catalyst OS Software Images
 First Published: March 20, 2006 Last Updated: March 22, 2011 The feature is one of two features bundled with the QoS: Broadband Aggregation Enhancements Phase 1 feature. The feature provides the ability
First Published: March 20, 2006 Last Updated: March 22, 2011 The feature is one of two features bundled with the QoS: Broadband Aggregation Enhancements Phase 1 feature. The feature provides the ability
Configuring Network-Based Application Recognition
 Configuring Network-Based Application Recognition This chapter describes the tasks for configuring the Network-Based Application Recognition (NBAR) feature. For complete conceptual information, see the
Configuring Network-Based Application Recognition This chapter describes the tasks for configuring the Network-Based Application Recognition (NBAR) feature. For complete conceptual information, see the
Classifying Network Traffic
 Classifying Network Traffic Last Updated: December 8, 2011 Classifying network traffic allows you to organize traffic (that is, packets) into traffic classes or categories on the basis of whether the traffic
Classifying Network Traffic Last Updated: December 8, 2011 Classifying network traffic allows you to organize traffic (that is, packets) into traffic classes or categories on the basis of whether the traffic
Implementing Access Lists and Prefix Lists
 An access control list (ACL) consists of one or more access control entries (ACE) that collectively define the network traffic profile. This profile can then be referenced by Cisco IOS XR softwarefeatures
An access control list (ACL) consists of one or more access control entries (ACE) that collectively define the network traffic profile. This profile can then be referenced by Cisco IOS XR softwarefeatures
Access Control List Enhancements on the Cisco Series Router
 Access Control List Enhancements on the Cisco 12000 Series Router Part Number, May 30, 2008 The Cisco 12000 series router filters IP packets using access control lists (ACLs) as a fundamental security
Access Control List Enhancements on the Cisco 12000 Series Router Part Number, May 30, 2008 The Cisco 12000 series router filters IP packets using access control lists (ACLs) as a fundamental security
Understanding and Configuring Switching Database Manager on Catalyst 3750 Series Switches
 Understanding and Configuring Switching Database Manager on Catalyst 3750 Series Switches Document ID: 44921 Contents Introduction Prerequisites Requirements Components Used Conventions Overview of the
Understanding and Configuring Switching Database Manager on Catalyst 3750 Series Switches Document ID: 44921 Contents Introduction Prerequisites Requirements Components Used Conventions Overview of the
Configuring Control Plane Policing
 21 CHAPTER This chapter describes how to configure control plane policing (CoPP) on the NX-OS device. This chapter includes the following sections: Information About CoPP, page 21-1 Guidelines and Limitations,
21 CHAPTER This chapter describes how to configure control plane policing (CoPP) on the NX-OS device. This chapter includes the following sections: Information About CoPP, page 21-1 Guidelines and Limitations,
Configuring Firewall Filters (J-Web Procedure)
 Configuring Firewall Filters (J-Web Procedure) You configure firewall filters on EX Series switches to control traffic that enters ports on the switch or enters and exits VLANs on the network and Layer
Configuring Firewall Filters (J-Web Procedure) You configure firewall filters on EX Series switches to control traffic that enters ports on the switch or enters and exits VLANs on the network and Layer
Quality of Service Commands match ip precedence. match ip precedence ip-precedence-value [ip-precedence-value ip-precedence-value
 match ip precedence match ip precedence To identify IP precedence values as match criteria, use the match ip precedence command in class-map configuration mode. To remove IP precedence values from a class
match ip precedence match ip precedence To identify IP precedence values as match criteria, use the match ip precedence command in class-map configuration mode. To remove IP precedence values from a class
QoS: Classification, Policing, and Marking on LAC Configuration Guide, Cisco IOS Release 12.4T
 QoS: Classification, Policing, and Marking on LAC Configuration Guide, Cisco IOS Release 12.4T Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
QoS: Classification, Policing, and Marking on LAC Configuration Guide, Cisco IOS Release 12.4T Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Sharing Bandwidth Fairly During Congestion
 CHAPTER 12 When no QoS policies exist, the router serves traffic with best effort service. The router makes no distinction between high and low priority traffic and makes no allowances for the needs of
CHAPTER 12 When no QoS policies exist, the router serves traffic with best effort service. The router makes no distinction between high and low priority traffic and makes no allowances for the needs of
Quality of Service (QoS) Configuration Guide, Cisco IOS XE Everest a (Catalyst 3850 Switches)
 Quality of Service (QoS) Configuration Guide, Cisco IOS XE Everest 16.5.1a (Catalyst 3850 Switches) First Published: 2017-05-31 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose,
Quality of Service (QoS) Configuration Guide, Cisco IOS XE Everest 16.5.1a (Catalyst 3850 Switches) First Published: 2017-05-31 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose,
Modular QoS CLI Three-Level Hierarchical Policer
 Modular QoS CLI Three-Level Hierarchical Policer The Modular QoS CLI (MQC) Three-Level Hierarchical Policer extends the traffic policing functionality by allowing you to configure traffic policing at three
Modular QoS CLI Three-Level Hierarchical Policer The Modular QoS CLI (MQC) Three-Level Hierarchical Policer extends the traffic policing functionality by allowing you to configure traffic policing at three
Nested Class Map Support for Zone-Based Policy Firewall
 Nested Class Map Support for Zone-Based Policy Firewall The Nested Class Map Support for Zone-Based Policy Firewall feature provides the Cisco IOS XE firewall the functionality to configure multiple traffic
Nested Class Map Support for Zone-Based Policy Firewall The Nested Class Map Support for Zone-Based Policy Firewall feature provides the Cisco IOS XE firewall the functionality to configure multiple traffic
Quality of Service. Understanding Quality of Service
 The following sections describe support for features on the Cisco ASR 920 Series Router. Understanding, page 1 Configuring, page 2 Global QoS Limitations, page 2 Classification, page 3 Marking, page 6
The following sections describe support for features on the Cisco ASR 920 Series Router. Understanding, page 1 Configuring, page 2 Global QoS Limitations, page 2 Classification, page 3 Marking, page 6
Using NetFlow Filtering or Sampling to Select the Network Traffic to Track
 Using NetFlow Filtering or Sampling to Select the Network Traffic to Track First Published: June 19, 2006 Last Updated: December 17, 2010 This module contains information about and instructions for selecting
Using NetFlow Filtering or Sampling to Select the Network Traffic to Track First Published: June 19, 2006 Last Updated: December 17, 2010 This module contains information about and instructions for selecting
Defining QoS for Multiple Policy Levels
 CHAPTER 13 In releases prior to Cisco IOS Release 12.0(22)S, you can specify QoS behavior at only one level. For example, to shape two outbound queues of an interface, you must configure each queue separately,
CHAPTER 13 In releases prior to Cisco IOS Release 12.0(22)S, you can specify QoS behavior at only one level. For example, to shape two outbound queues of an interface, you must configure each queue separately,
Provisioning: Working with Pre-Configuration
 CHAPTER 6 QPM provides you with Pre-Configuration feature to define certain values and features that will be used while working with policies. The following topics describe the macros used in QPM: Working
CHAPTER 6 QPM provides you with Pre-Configuration feature to define certain values and features that will be used while working with policies. The following topics describe the macros used in QPM: Working
How to Verify Cisco Express Forwarding Switching
 How to Verify Cisco Express Forwarding Switching Document ID: 47205 Contents Introduction Prerequisites Requirements Components Used Conventions What Is Cisco IOS Switching? Verification Steps Understand
How to Verify Cisco Express Forwarding Switching Document ID: 47205 Contents Introduction Prerequisites Requirements Components Used Conventions What Is Cisco IOS Switching? Verification Steps Understand
Configuring PFC QoS CHAPTER
 38 CHAPTER This chapter describes how to configure quality of service (QoS) as implemented on the Policy Feature Card 3B (PFC3B) on the Supervisor Engine 32 PISA. Note For complete syntax and usage information
38 CHAPTER This chapter describes how to configure quality of service (QoS) as implemented on the Policy Feature Card 3B (PFC3B) on the Supervisor Engine 32 PISA. Note For complete syntax and usage information
Quality of Service (QoS) Configuration Guide, Cisco IOS XE Fuji 16.8.x (Catalyst 3850 Switches)
 Quality of Service (QoS) Configuration Guide, Cisco IOS XE Fuji 16.8.x (Catalyst 3850 Switches) First Published: 2018-04-06 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA
Quality of Service (QoS) Configuration Guide, Cisco IOS XE Fuji 16.8.x (Catalyst 3850 Switches) First Published: 2018-04-06 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA
Configuring Cache Services Using the Web Cache Communication Protocol
 Configuring Cache Services Using the Web Cache Communication Protocol Finding Feature Information, page 1 Prerequisites for WCCP, page 1 Restrictions for WCCP, page 2 Information About WCCP, page 3 How
Configuring Cache Services Using the Web Cache Communication Protocol Finding Feature Information, page 1 Prerequisites for WCCP, page 1 Restrictions for WCCP, page 2 Information About WCCP, page 3 How
Regulating Packet Flow on a Per-Interface Basis Using Generic Traffic Shaping
 Regulating Packet Flow on a Per-Interface Basis Using Generic Traffic Shaping Packet flow on a network can be regulated using a traffic shaping mechanism. One such traffic shaping mechanism is a Cisco
Regulating Packet Flow on a Per-Interface Basis Using Generic Traffic Shaping Packet flow on a network can be regulated using a traffic shaping mechanism. One such traffic shaping mechanism is a Cisco
QoS: Child Service Policy for Priority Class
 QoS: Child Service Policy for Priority Class First Published: November, 2006 The QoS: Child Service Policy for Priority Class feature allows you to configure a child service policy with nonqueuing-based
QoS: Child Service Policy for Priority Class First Published: November, 2006 The QoS: Child Service Policy for Priority Class feature allows you to configure a child service policy with nonqueuing-based
Classifying and Marking MPLS EXP
 The QoS EXP Matching feature allows you to classify and mark network traffic by modifying the Multiprotocol Label Switching (MPLS) experimental bits (EXP) field in IP packets. This module contains conceptual
The QoS EXP Matching feature allows you to classify and mark network traffic by modifying the Multiprotocol Label Switching (MPLS) experimental bits (EXP) field in IP packets. This module contains conceptual
QoS: Per-Session Shaping and Queuing on LNS
 QoS: Per-Session Shaping and Queuing on LNS First Published: February 28, 2006 The QoS: Per-Session Shaping and Queuing on LNS feature provides the ability to shape (for example, transmit or drop) or queue
QoS: Per-Session Shaping and Queuing on LNS First Published: February 28, 2006 The QoS: Per-Session Shaping and Queuing on LNS feature provides the ability to shape (for example, transmit or drop) or queue
Protocol-Independent MAC ACL Filtering on the Cisco Series Internet Router
 Protocol-Independent MAC ACL Filtering on the Cisco 12000 Series Internet Router Part Number OL-142368-01 (Rev A0), January 19, 2006 The Protocol-Independent MAC ACL Filtering feature allows you to create
Protocol-Independent MAC ACL Filtering on the Cisco 12000 Series Internet Router Part Number OL-142368-01 (Rev A0), January 19, 2006 The Protocol-Independent MAC ACL Filtering feature allows you to create
Applying QoS Features Using the MQC
 QoS: Modular QoS Command-Line Interface Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 900 Series) First Published: November 30, 2012 Last Modified: March 31, 2014 This chapter discusses the Modular
QoS: Modular QoS Command-Line Interface Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 900 Series) First Published: November 30, 2012 Last Modified: March 31, 2014 This chapter discusses the Modular
QoS: Child Service Policy for Priority Class
 QoS: Child Service Policy for Priority Class First Published: November, 2006 Last Updated: March 2, 2009 The QoS: Child Service Policy for Priority Class feature allows you to configure a child service
QoS: Child Service Policy for Priority Class First Published: November, 2006 Last Updated: March 2, 2009 The QoS: Child Service Policy for Priority Class feature allows you to configure a child service
Troubleshooting High CPU Utilization Due to the IP Input Process
 Troubleshooting High CPU Utilization Due to the IP Input Process Document ID: 41160 Contents Introduction Prerequisites Requirements Components Used Conventions IP Input Sample IP Packet Debugging Session
Troubleshooting High CPU Utilization Due to the IP Input Process Document ID: 41160 Contents Introduction Prerequisites Requirements Components Used Conventions IP Input Sample IP Packet Debugging Session
Network Security Laboratory 23 rd May STATEFUL FIREWALL LAB
 Network Security Laboratory 23 rd May 2016. STATEFUL FIREWALL LAB 1 CONTENTS INTRODUCTION I. What is Stateful Firewall II. Difference between Stateful and Stateless III. Example of Stateful firewall IV.
Network Security Laboratory 23 rd May 2016. STATEFUL FIREWALL LAB 1 CONTENTS INTRODUCTION I. What is Stateful Firewall II. Difference between Stateful and Stateless III. Example of Stateful firewall IV.
Using NetFlow Filtering or Sampling to Select the Network Traffic to Track
 Using NetFlow Filtering or Sampling to Select the Network Traffic to Track Last Updated: December 7, 2011 This module contains information about and instructions for selecting the network traffic to track
Using NetFlow Filtering or Sampling to Select the Network Traffic to Track Last Updated: December 7, 2011 This module contains information about and instructions for selecting the network traffic to track
Configuring Web Cache Services By Using WCCP
 CHAPTER 44 Configuring Web Cache Services By Using WCCP This chapter describes how to configure your Catalyst 3560 switch to redirect traffic to wide-area application engines (such as the Cisco Cache Engine
CHAPTER 44 Configuring Web Cache Services By Using WCCP This chapter describes how to configure your Catalyst 3560 switch to redirect traffic to wide-area application engines (such as the Cisco Cache Engine
Lab Configuring Low Latency Queuing (LLQ)
 Lab 8.1.10.7 Configuring Low Latency Queuing (LLQ) Objective Scenario Low Latency Queuing (LLQ) enables the use of a single, strict priority queue within class-based weighted fair queuing (CBWFQ) at the
Lab 8.1.10.7 Configuring Low Latency Queuing (LLQ) Objective Scenario Low Latency Queuing (LLQ) enables the use of a single, strict priority queue within class-based weighted fair queuing (CBWFQ) at the
QoS: Regulating Packet Flow Configuration Guide, Cisco IOS Release 15S
 QoS: Regulating Packet Flow Configuration Guide, Cisco IOS Release 15S First Published: November 26, 2012 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
QoS: Regulating Packet Flow Configuration Guide, Cisco IOS Release 15S First Published: November 26, 2012 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Packet Classification Using the Frame Relay DLCI Number
 Packet Classification Using the Frame Relay DLCI Number The Packet Classification Using the Frame Relay DLCI Number feature allows customers to match and classify traffic on the basis of one or more Frame
Packet Classification Using the Frame Relay DLCI Number The Packet Classification Using the Frame Relay DLCI Number feature allows customers to match and classify traffic on the basis of one or more Frame
Configuring IP Version 6
 CHAPTER 24 Configuring IP Version 6 Internet Protocol version 6 (IPv6), formerly called IPng (next generation), is the latest version of IP. IPv6 offers many advantages over the previous version of IP,
CHAPTER 24 Configuring IP Version 6 Internet Protocol version 6 (IPv6), formerly called IPng (next generation), is the latest version of IP. IPv6 offers many advantages over the previous version of IP,
Using NetFlow Sampling to Select the Network Traffic to Track
 Using NetFlow Sampling to Select the Network Traffic to Track This module contains information about and instructions for selecting the network traffic to track through the use of NetFlow sampling. The
Using NetFlow Sampling to Select the Network Traffic to Track This module contains information about and instructions for selecting the network traffic to track through the use of NetFlow sampling. The
Sections Describing Standard Software Features
 27 CHAPTER This chapter describes how to configure quality of service (QoS) by using automatic-qos (auto-qos) commands or by using standard QoS commands. With QoS, you can give preferential treatment to
27 CHAPTER This chapter describes how to configure quality of service (QoS) by using automatic-qos (auto-qos) commands or by using standard QoS commands. With QoS, you can give preferential treatment to
Modular Quality of Service Overview on Cisco IOS XR Software
 Modular Quality of Service Overview on Cisco IOS XR Software Quality of Service (QoS) is the technique of prioritizing traffic flows and providing preferential forwarding for higher-priority packets. The
Modular Quality of Service Overview on Cisco IOS XR Software Quality of Service (QoS) is the technique of prioritizing traffic flows and providing preferential forwarding for higher-priority packets. The
Sections Describing Standard Software Features
 30 CHAPTER This chapter describes how to configure quality of service (QoS) by using automatic-qos (auto-qos) commands or by using standard QoS commands. With QoS, you can give preferential treatment to
30 CHAPTER This chapter describes how to configure quality of service (QoS) by using automatic-qos (auto-qos) commands or by using standard QoS commands. With QoS, you can give preferential treatment to
Configuring an IP ACL
 9 CHAPTER This chapter describes how to configure IP access control lists (ACLs). This chapter includes the following sections: Information About ACLs, page 9-1 Prerequisites for IP ACLs, page 9-5 Guidelines
9 CHAPTER This chapter describes how to configure IP access control lists (ACLs). This chapter includes the following sections: Information About ACLs, page 9-1 Prerequisites for IP ACLs, page 9-5 Guidelines
Configuring QoS. Finding Feature Information. Prerequisites for QoS
 Finding Feature Information, page 1 Prerequisites for QoS, page 1 Restrictions for QoS, page 3 Information About QoS, page 4 How to Configure QoS, page 28 Monitoring Standard QoS, page 80 Configuration
Finding Feature Information, page 1 Prerequisites for QoS, page 1 Restrictions for QoS, page 3 Information About QoS, page 4 How to Configure QoS, page 28 Monitoring Standard QoS, page 80 Configuration
Configuring QoS CHAPTER
 CHAPTER 34 This chapter describes how to use different methods to configure quality of service (QoS) on the Catalyst 3750 Metro switch. With QoS, you can provide preferential treatment to certain types
CHAPTER 34 This chapter describes how to use different methods to configure quality of service (QoS) on the Catalyst 3750 Metro switch. With QoS, you can provide preferential treatment to certain types
Quality of Service Configuration Guide, Cisco IOS XE Fuji 16.8.x (Catalyst 9300 Switches)
 Quality of Service Configuration Guide, Cisco IOS XE Fuji 16.8.x (Catalyst 9300 Switches) First Published: 2018-04-06 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706
Quality of Service Configuration Guide, Cisco IOS XE Fuji 16.8.x (Catalyst 9300 Switches) First Published: 2018-04-06 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706
Cisco 1000 Series Connected Grid Routers QoS Software Configuration Guide
 Cisco 1000 Series Connected Grid Routers QoS Software Configuration Guide January 17, 2012 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Cisco 1000 Series Connected Grid Routers QoS Software Configuration Guide January 17, 2012 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Contents. QoS overview 1
 Contents QoS overview 1 QoS service models 1 Best-effort service model 1 IntServ model 1 DiffServ model 1 QoS techniques overview 1 Deploying QoS in a network 2 QoS processing flow in a device 2 Configuring
Contents QoS overview 1 QoS service models 1 Best-effort service model 1 IntServ model 1 DiffServ model 1 QoS techniques overview 1 Deploying QoS in a network 2 QoS processing flow in a device 2 Configuring
Understanding Queuing and Scheduling QoS on Catalyst 4000 Supervisor III and IV
 Understanding Queuing and Scheduling QoS on Catalyst 4000 Supervisor III and IV Document ID: 21389 Contents Introduction Before You Begin Conventions Prerequisites Components Used Queuing Strict Priority
Understanding Queuing and Scheduling QoS on Catalyst 4000 Supervisor III and IV Document ID: 21389 Contents Introduction Before You Begin Conventions Prerequisites Components Used Queuing Strict Priority
WCCPv2 and WCCP Enhancements
 WCCPv2 and WCCP Enhancements Release 12.0(11)S June 20, 2000 This feature module describes the Web Cache Communication Protocol (WCCP) Enhancements feature and includes information on the benefits of the
WCCPv2 and WCCP Enhancements Release 12.0(11)S June 20, 2000 This feature module describes the Web Cache Communication Protocol (WCCP) Enhancements feature and includes information on the benefits of the
Configuring 4-Port Gigabit Ethernet WAN Optical Services Modules
 CHAPTER 4 Configuring 4-Port Gigabit Ethernet WAN Optical Services Modules This chapter provides an overview of the features supported on the 4-port Gigabit Ethernet WAN Optical Services Modules (OSM-2+4GE-WAN+
CHAPTER 4 Configuring 4-Port Gigabit Ethernet WAN Optical Services Modules This chapter provides an overview of the features supported on the 4-port Gigabit Ethernet WAN Optical Services Modules (OSM-2+4GE-WAN+
Three interface Router without NAT Cisco IOS Firewall Configuration
 Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Configuring Application Visibility and Control for Cisco Flexible Netflow
 Configuring Application Visibility and Control for Cisco Flexible Netflow First published: July 22, 2011 This guide contains information about the Cisco Application Visibility and Control feature. It also
Configuring Application Visibility and Control for Cisco Flexible Netflow First published: July 22, 2011 This guide contains information about the Cisco Application Visibility and Control feature. It also
Access Control Lists and IP Fragments
 Access Control Lists and IP Fragments Document ID: 8014 Contents Introduction Types of ACL Entries ACL Rules Flowchart How Packets Can Match an ACL Example 1 Example 2 fragments Keyword Scenarios Scenario
Access Control Lists and IP Fragments Document ID: 8014 Contents Introduction Types of ACL Entries ACL Rules Flowchart How Packets Can Match an ACL Example 1 Example 2 fragments Keyword Scenarios Scenario
Configuring Quality of Service
 CHAPTER 14 This chapter describes the Quality of Service (QoS) features built into your ML-Series card and how to map QoS scheduling at both the system and interface levels. This chapter contains the following
CHAPTER 14 This chapter describes the Quality of Service (QoS) features built into your ML-Series card and how to map QoS scheduling at both the system and interface levels. This chapter contains the following
Quality of Service Configuration Guide, Cisco IOS XE Everest 16.6.x (Catalyst 9300 Switches)
 Quality of Service Configuration Guide, Cisco IOS XE Everest 16.6.x (Catalyst 9300 Switches) First Published: 2017-07-31 Last Modified: 2017-11-03 Americas Headquarters Cisco Systems, Inc. 170 West Tasman
Quality of Service Configuration Guide, Cisco IOS XE Everest 16.6.x (Catalyst 9300 Switches) First Published: 2017-07-31 Last Modified: 2017-11-03 Americas Headquarters Cisco Systems, Inc. 170 West Tasman
IP Accounting C H A P T E R
 C H A P T E R 6 IP Accounting This chapter describes the IP Accounting features in Cisco IOS and enables you to distinguish the different IP Accounting functions and understand SNMP MIB details. This chapter
C H A P T E R 6 IP Accounting This chapter describes the IP Accounting features in Cisco IOS and enables you to distinguish the different IP Accounting functions and understand SNMP MIB details. This chapter
WCCP Network Integration with Cisco Catalyst 6500: Best Practice Recommendations for Successful Deployments
 WCCP Network Integration with Cisco Catalyst 6500: Best Practice Recommendations for Successful Deployments What You Will Learn This document is intended for network engineers deploying the Cisco Catalyst
WCCP Network Integration with Cisco Catalyst 6500: Best Practice Recommendations for Successful Deployments What You Will Learn This document is intended for network engineers deploying the Cisco Catalyst
Table of Contents. Cisco Quality of Service Options on GRE Tunnel Interfaces
 Table of Contents Quality of Service Options on GRE Tunnel Interfaces...1 Introduction...1 Before You Begin...1 Conventions...1 Prerequisites...1 Components Used...1 Overview of GRE...1 Cisco QoS for GRE
Table of Contents Quality of Service Options on GRE Tunnel Interfaces...1 Introduction...1 Before You Begin...1 Conventions...1 Prerequisites...1 Components Used...1 Overview of GRE...1 Cisco QoS for GRE
Understanding Packet Counters in show policy map interface Output
 Understanding Packet Counters in show policy map interface Output Document ID: 10107 Contents Introduction Prerequisites Requirements Components Used Conventions What Is Congestion? What Is the Difference
Understanding Packet Counters in show policy map interface Output Document ID: 10107 Contents Introduction Prerequisites Requirements Components Used Conventions What Is Congestion? What Is the Difference
Configuring Quality of Service
 CHAPTER 13 This chapter describes the Quality of Service (QoS) features built into your ML-Series card and how to map QoS scheduling at both the system and interface levels. This chapter contains the following
CHAPTER 13 This chapter describes the Quality of Service (QoS) features built into your ML-Series card and how to map QoS scheduling at both the system and interface levels. This chapter contains the following
Quality of Service Configuration Guide, Cisco IOS XE Everest 16.6.x (Catalyst 9300 Switches)
 Quality of Service Configuration Guide, Cisco IOS XE Everest 16.6.x (Catalyst 9300 Switches) First Published: 2017-07-31 Last Modified: 2017-11-03 Americas Headquarters Cisco Systems, Inc. 170 West Tasman
Quality of Service Configuration Guide, Cisco IOS XE Everest 16.6.x (Catalyst 9300 Switches) First Published: 2017-07-31 Last Modified: 2017-11-03 Americas Headquarters Cisco Systems, Inc. 170 West Tasman
Cisco - Catalyst G-L3 Series Switches and WS-X4232-L3 Layer 3 Modules QoS FAQ
 Page 1 of 7 Catalyst G-L3 Series Switches and WS-X4232-L3 Layer 3 Modules QoS FAQ Document ID: 19641 Questions Introduction Which QoS features do the Layer 3 (L3) Catalyst switches support? What is the
Page 1 of 7 Catalyst G-L3 Series Switches and WS-X4232-L3 Layer 3 Modules QoS FAQ Document ID: 19641 Questions Introduction Which QoS features do the Layer 3 (L3) Catalyst switches support? What is the
Sybex CCENT Chapter 12: Security. Instructor & Todd Lammle
 Sybex CCENT 100-101 Chapter 12: Security Instructor & Todd Lammle Chapter 12 Objectives The CCENT Topics Covered in this chapter include: IP Services Describe the types, features, and applications of ACLs
Sybex CCENT 100-101 Chapter 12: Security Instructor & Todd Lammle Chapter 12 Objectives The CCENT Topics Covered in this chapter include: IP Services Describe the types, features, and applications of ACLs
Configuring QoS Policy Actions and Rules
 CHAPTER 3 The second step in creating a QoS service policy is to define how you want the router to handle the packets that match the classification rules you defined in Chapter 2, Classifying Traffic.
CHAPTER 3 The second step in creating a QoS service policy is to define how you want the router to handle the packets that match the classification rules you defined in Chapter 2, Classifying Traffic.
Implementing Access Lists and Prefix Lists on Cisco ASR 9000 Series Routers
 Implementing Access Lists and Prefix Lists on Cisco ASR 9000 Series Routers An access control list (ACL) consists of one me access control entries (ACE) that collectively define the netwk traffic profile.
Implementing Access Lists and Prefix Lists on Cisco ASR 9000 Series Routers An access control list (ACL) consists of one me access control entries (ACE) that collectively define the netwk traffic profile.
Modular Policy Framework. Class Maps SECTION 4. Advanced Configuration
 [ 59 ] Section 4: We have now covered the basic configuration and delved into AAA services on the ASA. In this section, we cover some of the more advanced features of the ASA that break it away from a
[ 59 ] Section 4: We have now covered the basic configuration and delved into AAA services on the ASA. In this section, we cover some of the more advanced features of the ASA that break it away from a
Configuring Cisco Performance Monitor
 This document contains information about and instructions for configuring Cisco Performance Monitor. Finding Feature Information, page 1 Information About Cisco Performance Monitor, page 1 Restrictions
This document contains information about and instructions for configuring Cisco Performance Monitor. Finding Feature Information, page 1 Information About Cisco Performance Monitor, page 1 Restrictions
Configuring Access Rules
 Configuring Access Rules Rules > Access Rules About Access Rules Displaying Access Rules Specifying Maximum Zone-to-Zone Access Rules Changing Priority of a Rule Adding Access Rules Editing an Access Rule
Configuring Access Rules Rules > Access Rules About Access Rules Displaying Access Rules Specifying Maximum Zone-to-Zone Access Rules Changing Priority of a Rule Adding Access Rules Editing an Access Rule
Quality of Service. Create QoS Policy CHAPTER26. Create QoS Policy Tab. Edit QoS Policy Tab. Launch QoS Wizard Button
 CHAPTER26 The (QoS) Wizard allows a network administrator to enable (QoS) on the router s WAN interfaces. QoS can also be enabled on IPSec VPN interfaces and tunnels. The QoS edit windows enables the administrator
CHAPTER26 The (QoS) Wizard allows a network administrator to enable (QoS) on the router s WAN interfaces. QoS can also be enabled on IPSec VPN interfaces and tunnels. The QoS edit windows enables the administrator
Configuring Destination Sensitive Services on the Optical Services Modules
 CHAPTER 10 on the Optical Services Modules This chapter describes how to configure Destination Sensitive Services (DSS) on the Optical Services Modules (OSMs). This chapter consists of these sections:
CHAPTER 10 on the Optical Services Modules This chapter describes how to configure Destination Sensitive Services (DSS) on the Optical Services Modules (OSMs). This chapter consists of these sections:
Securing Wireless LAN Controllers (WLCs)
 Securing Wireless LAN Controllers (WLCs) Document ID: 109669 Contents Introduction Prerequisites Requirements Components Used Conventions Traffic Handling in WLCs Controlling Traffic Controlling Management
Securing Wireless LAN Controllers (WLCs) Document ID: 109669 Contents Introduction Prerequisites Requirements Components Used Conventions Traffic Handling in WLCs Controlling Traffic Controlling Management
BCP Support on MLPPP
 , page 1 Finding Feature Information, page 1 Information About, page 1 How to Configure, page 3 Configuration Examples for, page 12 Additional References, page 20 Feature Information for, page 22 This
, page 1 Finding Feature Information, page 1 Information About, page 1 How to Configure, page 3 Configuration Examples for, page 12 Additional References, page 20 Feature Information for, page 22 This
Configuring Policy-Based Routing
 35 CHAPTER This chapter describes the tasks for configuring policy-based routing (PBR) on a router and includes these major sections: Overview of Policy-Based Routing, page 35-1 Policy-Based Routing Configuration
35 CHAPTER This chapter describes the tasks for configuring policy-based routing (PBR) on a router and includes these major sections: Overview of Policy-Based Routing, page 35-1 Policy-Based Routing Configuration
Configuring QoS CHAPTER
 CHAPTER 37 This chapter describes how to configure quality of service (QoS) by using automatic QoS (auto-qos) commands or by using standard QoS commands on the Catalyst 3750-E or 3560-E switch. With QoS,
CHAPTER 37 This chapter describes how to configure quality of service (QoS) by using automatic QoS (auto-qos) commands or by using standard QoS commands on the Catalyst 3750-E or 3560-E switch. With QoS,
Configuring Mutation Mapping
 CHAPTER 5 This chapter describes how to configure the mutation of packet values used to define traffic classes on the Cisco NX-OS device. This chapter includes the following sections: Information About
CHAPTER 5 This chapter describes how to configure the mutation of packet values used to define traffic classes on the Cisco NX-OS device. This chapter includes the following sections: Information About
Implementing QoS for IPv6
 Implementing QoS for IPv6 Last Updated: August 1, 2012 Finding Feature Information, page 1 Restrictions for Implementing QoS for IPv6, page 1 Information About Implementing QoS for IPv6, page 2 How to
Implementing QoS for IPv6 Last Updated: August 1, 2012 Finding Feature Information, page 1 Restrictions for Implementing QoS for IPv6, page 1 Information About Implementing QoS for IPv6, page 2 How to
Configuring QoS CHAPTER
 CHAPTER 36 This chapter describes how to configure quality of service (QoS) by using automatic QoS (auto-qos) commands or by using standard QoS commands on the Catalyst 3750 switch. With QoS, you can provide
CHAPTER 36 This chapter describes how to configure quality of service (QoS) by using automatic QoS (auto-qos) commands or by using standard QoS commands on the Catalyst 3750 switch. With QoS, you can provide
Configuring PPP over Ethernet with NAT
 CHAPTER 3 The Cisco Secure Router 520 Ethernet-to-Ethernet routers support Point-to-Point Protocol over Ethernet (PPPoE) clients and network address translation (NAT). Multiple PCs can be connected to
CHAPTER 3 The Cisco Secure Router 520 Ethernet-to-Ethernet routers support Point-to-Point Protocol over Ethernet (PPPoE) clients and network address translation (NAT). Multiple PCs can be connected to
Marking Network Traffic
 Marking network traffic allows you to set or modify the attributes for traffic (that is, packets) belonging to a specific class or category. When used in conjunction with network traffic classification,
Marking network traffic allows you to set or modify the attributes for traffic (that is, packets) belonging to a specific class or category. When used in conjunction with network traffic classification,
QoS v6.0. QoS v6.0 VGN
 QoS v6.0 Number: 642-642 Passing Score: 832 Time Limit: 90 min File Version: v1.0 http://www.gratisexam.com/ QoS 642-642 v6.0 by VGN Sections 1. Single Select 2. Multiple Select 3. Drag & Drop 4. Lab Exam
QoS v6.0 Number: 642-642 Passing Score: 832 Time Limit: 90 min File Version: v1.0 http://www.gratisexam.com/ QoS 642-642 v6.0 by VGN Sections 1. Single Select 2. Multiple Select 3. Drag & Drop 4. Lab Exam
QoS Group Match and Set for Classification and Marking
 QoS Group Match and Set for Classification and Marking This feature provides the capability of matching and classifying traffic on the basis of the QoS group value. Finding Feature Information, on page
QoS Group Match and Set for Classification and Marking This feature provides the capability of matching and classifying traffic on the basis of the QoS group value. Finding Feature Information, on page
Committed Access Rate
 Committed Access Rate Feature Summary The Committed Access Rate (CAR) feature performs the following functions: Limits the input or output transmission rate on an interface or subinterface based on a flexible
Committed Access Rate Feature Summary The Committed Access Rate (CAR) feature performs the following functions: Limits the input or output transmission rate on an interface or subinterface based on a flexible
Prioritizing Services
 CHAPTER 8 Voice, video, and data applications have differing quality of service needs. Voice applications, for example, require a small but guaranteed amount of bandwidth, are less tolerant of packet delay
CHAPTER 8 Voice, video, and data applications have differing quality of service needs. Voice applications, for example, require a small but guaranteed amount of bandwidth, are less tolerant of packet delay
Configuring Modular QoS Congestion Avoidance
 Congestion avoidance techniques monitor traffic flow in an effort to anticipate and avoid congestion at common network bottlenecks. Avoidance techniques are implemented before congestion occurs as compared
Congestion avoidance techniques monitor traffic flow in an effort to anticipate and avoid congestion at common network bottlenecks. Avoidance techniques are implemented before congestion occurs as compared
Configuring Control Plane Policing
 32 CHAPTER This chapter contains information on how to protect your Catalyst 4500 series switch using control plane policing (CoPP). The information covered in this chapter is unique to the Catalyst 4500
32 CHAPTER This chapter contains information on how to protect your Catalyst 4500 series switch using control plane policing (CoPP). The information covered in this chapter is unique to the Catalyst 4500
Configuring ACL Logging
 This chapter contains the following sections: Information About ACL Logging, page 1 Guidelines and Limitations for ACL Logging, page 2, page 2 Verifying ACL Logging Configuration, page 4 Configuration
This chapter contains the following sections: Information About ACL Logging, page 1 Guidelines and Limitations for ACL Logging, page 2, page 2 Verifying ACL Logging Configuration, page 4 Configuration
