Data Link Layer. Goals of This Lecture. Engineering Questions. Outline of the Class
|
|
|
- Mervin May
- 6 years ago
- Views:
Transcription
1 Data Link Layer Kuang Chiu Huang TCM NCKU Goals of This Lecture Through the lecture and in-class discussion, students are enabled to describe role and functions of the link layer, and compare different error control schemes. In addition, students can apply media access controls for different transmission media. 2 Outline of the Class Address resolution protocol Flow and error control Multiple access control Engineering Questions How can we associate link and network layer addressing? How can we transfer information reliably across a link? How can we control the throughput of a communications channel? How can we coordinate several accesses in one link? 3
2 Functions Systems Context End-to-end protocols Network layer protocol Link Layer Link Layer Link Layer What are the end to end protocols? What are the network layer protocols? How are network layer protocols different from link layer? Link Layer Addresses Physical delivery address Need only be locally unique Typically known as the MAC address Often physically embedded in Network Interface Card (NIC) Finding a Host on a Subnet Hosts are known to a subnet (eg. LAN) by their local attachment address (eg. Ethernet or MAC address) An IP address does not help deliver a packet
3 Finding a Host on a Subnet Address Resolution Protocol Solution: Make a table associating IP with network attachment addresses How? Broadcast unknown IP addresses to all hosts on a subnet Wait for a host to respond Address Resolution Protocol (ARP) Address Resolution Protocol Ethereal session transcript Source Destination Protocol Info Broadcast ARP Who has ? Tell Ethernet II, Src: 08:00:20:8f:70:66, Dst: ff:ff:ff:ff:ff:ff Address Resolution Protocol (request) Flow Control versus Error Control Flow control: Coordinates the amount of data can be sent before receiving an acknowledge The most important duty of this layer Process: some buffers on receiver side Error control: Error detection and correction Error detection: Parity check, VRC, CRC Error correction: ARQ and FEC Inform the sender any frames are lost or damaged and coordinates the retransmission
4 Types of errors Lost frames Damaged frames Causes of errors Bit errors Burst errors Error Control Strategies for Flow Control ARQ automatic repeat request Correct errors through retransmission Elements Use error detection Positive acknowledgement Retransmission after timeout NAK and retransmission Forward error correction Encode data so that errors can be detected and corrected Requires redundancy Use FEC when retransmission is impractical Long transmission channels Real time systems Error Detection Parity Vertical redundancy check Longitudinal redundancy check Still not that effective Cyclical redundancy check Based on polynomial division Much more effective than VRC and LRC Vertical and Longitudinal Redundancy Checks Character 1 Character 2 Character m Parity Bit 1 Bit 2 b 11 b 1m C 1 b 2m Bit n Parity b 21 b n1 R 1 b 12 b 22 b n2 R 2 C 2 C n C n+1 b nm R m LRC VRC
5 Types of ARQ Stop-and-Wait (Idle RQ) Sliding Window (Continuous RQ) Stop and Wait Transmitter sends a packet Receiver receives packet and checks for errors Transmitter must wait for ACK or NAK before sending additional messages Stop and Wait Stop and Wait (Long Channel) 1 Data 0 2 ACK 0 3 Data 1 4 NACK 1 5 Data ACK 7 Data 2 1 Data ACK 3 Data 1 4 ACK 1 Increasing bit rate 1 Data ACK 3 Data 4 4 ACK 4
6 Sliding Window Transmitter may transmit several messages before awaiting response The number of unacknowledged messages permitted is the Window Size Sliding Window If an error occurs Transmitter resends everything since the error (Go-Back-N) Only the errored packet (Selective Retransmission) Sliding Window (n>3) Sliding Window (Go-Back-N) 0 Data 0 1 Data 1 2 Data 2 3 ACK Data 4 5 Data 5 6 Data 6 7 NACK Data 4 9 Data 5 10 Data 6
7 U Performance Issues Stop and Wait Sliding Window (N=7) P=10-3 Performance Issues Stop and Wait Error free tt 1 1 U = = = t p 2tp + tt 2 1 2a 1 t + + With errors t Normalized Propagation Delay (a) U 1 P 1 P = = t 1+ 2 p 1 2a t + t Performance Issues Sliding window 1 N 2a+ 1 U = N N < 2a+ 1 ( 1 + 2a) where t a = t p t Medium Access Control Why is MAC necessary? What is the relationship between MAC and the link layer protocols we discussed?
8 Data link layer divided into two functionality-oriented sublayers Taxonomy of multiple-access protocols discussed in this class RANDOM ACCESS Frames in a pure ALOHA network In random access or contention methods, no station is superior to another station and none is assigned the control over another. No station permits, or does not permit, another station to send. At each instance, a station that has data to send uses a procedure defined by the protocol to make a decision on whether or not to send.
9 Procedure for pure ALOHA protocol Vulnerable time for pure ALOHA protocol Frames in a slotted ALOHA network Vulnerable time for slotted ALOHA protocol
10 Vulnerable time in CSMA Collision of the first bit in CSMA/CD Flow diagram for the CSMA/CD Energy level during transmission, idleness, or collision
11 Timing in CSMA/CA Note In CSMA/CA, if the station finds the channel busy, it does not restart the timer of the contention window; it stops the timer and restarts it when the channel becomes idle. Flow diagram for CSMA/CA CONTROLLED ACCESS In controlled access,, the stations consult one another to find which station has the right to send. A station cannot send unless it has been authorized by other stations. We discuss three popular controlled-access methods.
12 Reservation access method Polling Token Passing CHANNELIZATION Channelization is a multiple-access method in which the available bandwidth of a link is shared in time, frequency, or through code, between different stations. In this section, we discuss three channelization protocols.
13 Frequency-division multiple access (FDMA) Note In FDMA, the available bandwidth of the common channel is divided into bands that are separated by guard bands. Time-division multiple access (TDMA) Note In TDMA, the bandwidth is just one channel that is timeshared between different stations.
14 Simple idea of communication with code Note In CDMA, one channel carries all transmissions simultaneously. Figure Chip sequences Figure Data representation in CDMA
15 Figure Sharing channel in CDMA Thank you! Q & A 58
Data Link Layer: Collisions
 Data Link Layer: Collisions 1 Multiple Access Data Link layer divided into two sublayers. The upper sublayer is responsible for datalink control, The lower sublayer is responsible for resolving access
Data Link Layer: Collisions 1 Multiple Access Data Link layer divided into two sublayers. The upper sublayer is responsible for datalink control, The lower sublayer is responsible for resolving access
Chapter 12 Multiple Access 12.1
 Chapter 12 Multiple Access 12.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 12.2 Figure 12.1 Data link layer divided into two functionality-oriented sublayers
Chapter 12 Multiple Access 12.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 12.2 Figure 12.1 Data link layer divided into two functionality-oriented sublayers
Data Link Layer -2- Network Access
 EITF25 Internet: Technology and Applications Data Link Layer -2- Network Access 2015, Lecture 03 Kaan Bür Previously on EITF25 Logical Link Control Sublayer Flow control Send data Wait for ACK Error control
EITF25 Internet: Technology and Applications Data Link Layer -2- Network Access 2015, Lecture 03 Kaan Bür Previously on EITF25 Logical Link Control Sublayer Flow control Send data Wait for ACK Error control
Data Link Layer -2- Network Access
 EITF25 Internet: Technology and Applications Data Link Layer -2- Network Access 2013, Lecture 03 Kaan Bür, Stefan Höst Previously on EITF25 Logical Link Control Sublayer Flow control Send data Wait for
EITF25 Internet: Technology and Applications Data Link Layer -2- Network Access 2013, Lecture 03 Kaan Bür, Stefan Höst Previously on EITF25 Logical Link Control Sublayer Flow control Send data Wait for
Data Link Layer: Overview, operations
 Data Link Layer: Overview, operations Chapter 3 1 Outlines 1. Data Link Layer Functions. Data Link Services 3. Framing 4. Error Detection/Correction. Flow Control 6. Medium Access 1 1. Data Link Layer
Data Link Layer: Overview, operations Chapter 3 1 Outlines 1. Data Link Layer Functions. Data Link Services 3. Framing 4. Error Detection/Correction. Flow Control 6. Medium Access 1 1. Data Link Layer
CHAPTER 7 MAC LAYER PROTOCOLS. Dr. Bhargavi Goswami Associate Professor & Head Department of Computer Science Garden City College
 CHAPTER 7 MAC LAYER PROTOCOLS Dr. Bhargavi Goswami Associate Professor & Head Department of Computer Science Garden City College MEDIUM ACCESS CONTROL - MAC PROTOCOLS When the two stations transmit data
CHAPTER 7 MAC LAYER PROTOCOLS Dr. Bhargavi Goswami Associate Professor & Head Department of Computer Science Garden City College MEDIUM ACCESS CONTROL - MAC PROTOCOLS When the two stations transmit data
Data Communications. Automatic Repeat Request Medium Access Control
 Data Communications Automatic Repeat Request Medium Access Control Handling Error Cases Automatic Repeat request(arq), also known as Automatic Repeat Query, is an error-control method ARQ uses acknowledgements
Data Communications Automatic Repeat Request Medium Access Control Handling Error Cases Automatic Repeat request(arq), also known as Automatic Repeat Query, is an error-control method ARQ uses acknowledgements
Topics. Link Layer Services (more) Link Layer Services LECTURE 5 MULTIPLE ACCESS AND LOCAL AREA NETWORKS. flow control: error detection:
 1 Topics 2 LECTURE 5 MULTIPLE ACCESS AND LOCAL AREA NETWORKS Multiple access: CSMA/CD, CSMA/CA, token passing, channelization LAN: characteristics, i basic principles i Protocol architecture Topologies
1 Topics 2 LECTURE 5 MULTIPLE ACCESS AND LOCAL AREA NETWORKS Multiple access: CSMA/CD, CSMA/CA, token passing, channelization LAN: characteristics, i basic principles i Protocol architecture Topologies
Problem Set Name the 7 OSI layers and give the corresponding functionalities for each layer.
 Problem Set 1 1. Why do we use layering in computer networks? 2. Name the 7 OSI layers and give the corresponding functionalities for each layer. 3. Compare the network performance of the 3 Multiple Access
Problem Set 1 1. Why do we use layering in computer networks? 2. Name the 7 OSI layers and give the corresponding functionalities for each layer. 3. Compare the network performance of the 3 Multiple Access
CS 4453 Computer Networks Winter
 CS 4453 Computer Networks Chapter 2 OSI Network Model 2015 Winter OSI model defines 7 layers Figure 1: OSI model Computer Networks R. Wei 2 The seven layers are as follows: Application Presentation Session
CS 4453 Computer Networks Chapter 2 OSI Network Model 2015 Winter OSI model defines 7 layers Figure 1: OSI model Computer Networks R. Wei 2 The seven layers are as follows: Application Presentation Session
Link layer, LANs: outline. Chapter 5-1 Link Layer. Link layer: introduction. Link layer services
 Chapter 5 Link Layer Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Link layer, LANs: outline 5.1 introduction, services 5.2 error detection, correction
Chapter 5 Link Layer Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Link layer, LANs: outline 5.1 introduction, services 5.2 error detection, correction
COMMUNICATION NETWORKS NETW 501
 COMMUNICATION NETWORKS NETW 501 TUTORIAL 6 Presented by: Eng. Hana Hesham Eng. Mohamed Atef Data Link Layer Data Link Layer is split into 2 sublayers which are the Logical Link Control (LLC) and the Medium
COMMUNICATION NETWORKS NETW 501 TUTORIAL 6 Presented by: Eng. Hana Hesham Eng. Mohamed Atef Data Link Layer Data Link Layer is split into 2 sublayers which are the Logical Link Control (LLC) and the Medium
EITF25 Internet Techniques and Applications L4: Network Access. Stefan Höst
 EITF25 Internet Techniques and Applications L4: Network Access Stefan Höst Repetition The link layer protocol should make sure that the data is correctly transmitted over the physical link using error
EITF25 Internet Techniques and Applications L4: Network Access Stefan Höst Repetition The link layer protocol should make sure that the data is correctly transmitted over the physical link using error
Link Layer and LANs 안상현서울시립대학교컴퓨터 통계학과.
 Link Layer and LANs 안상현서울시립대학교컴퓨터 통계학과 ahn@venus.uos.ac.kr Data Link Layer Goals: understand principles behind data link layer services: error detection, correction sharing a broadcast channel: multiple
Link Layer and LANs 안상현서울시립대학교컴퓨터 통계학과 ahn@venus.uos.ac.kr Data Link Layer Goals: understand principles behind data link layer services: error detection, correction sharing a broadcast channel: multiple
Multiple-access protocols
 Multiple Access Multiple-access protocols Random Access MA CSMA CSMA/CD CSMA/CA RANDOM ACCESS In a random access method, each station has the right to the medium without being controlled by any other station.
Multiple Access Multiple-access protocols Random Access MA CSMA CSMA/CD CSMA/CA RANDOM ACCESS In a random access method, each station has the right to the medium without being controlled by any other station.
Multiple Access. Data Communications and Networking
 Multiple Access In the previous part we discussed data link control, a mechanism which provides a link with reliable communication. In the protocols we described, we assumed that there is an available
Multiple Access In the previous part we discussed data link control, a mechanism which provides a link with reliable communication. In the protocols we described, we assumed that there is an available
The Link Layer and LANs. Chapter 6: Link layer and LANs
 The Link Layer and LANs EECS3214 2018-03-14 4-1 Chapter 6: Link layer and LANs our goals: understand principles behind link layer services: error detection, correction sharing a broadcast channel: multiple
The Link Layer and LANs EECS3214 2018-03-14 4-1 Chapter 6: Link layer and LANs our goals: understand principles behind link layer services: error detection, correction sharing a broadcast channel: multiple
Data Link Layer: Multi Access Protocols
 Digital Communication in the Modern World Data Link Layer: Multi Access Protocols http://www.cs.huji.ac.il/~com1 com1@cs.huji.ac.il Some of the slides have been borrowed from: Computer Networking: A Top
Digital Communication in the Modern World Data Link Layer: Multi Access Protocols http://www.cs.huji.ac.il/~com1 com1@cs.huji.ac.il Some of the slides have been borrowed from: Computer Networking: A Top
ECE 4450:427/527 - Computer Networks Spring 2017
 ECE 4450:427/527 - Computer Networks Spring 2017 Dr. Nghi Tran Department of Electrical & Computer Engineering Lecture 5.4: Multiple Access Protocols Dr. Nghi Tran (ECE-University of Akron) ECE 4450:427/527
ECE 4450:427/527 - Computer Networks Spring 2017 Dr. Nghi Tran Department of Electrical & Computer Engineering Lecture 5.4: Multiple Access Protocols Dr. Nghi Tran (ECE-University of Akron) ECE 4450:427/527
CS 43: Computer Networks. 27: Media Access Contd. December 3, 2018
 CS 43: Computer Networks 27: Media Access Contd. December 3, 2018 Last Class The link layer provides lots of functionality: addressing, framing, media access, error checking could be used independently
CS 43: Computer Networks 27: Media Access Contd. December 3, 2018 Last Class The link layer provides lots of functionality: addressing, framing, media access, error checking could be used independently
I. INTRODUCTION. each station (i.e., computer, telephone, etc.) directly connected to all other stations
 I. INTRODUCTION (a) Network Topologies (i) point-to-point communication each station (i.e., computer, telephone, etc.) directly connected to all other stations (ii) switched networks (1) circuit switched
I. INTRODUCTION (a) Network Topologies (i) point-to-point communication each station (i.e., computer, telephone, etc.) directly connected to all other stations (ii) switched networks (1) circuit switched
CS 455/555 Intro to Networks and Communications. Link Layer
 CS 455/555 Intro to Networks and Communications Link Layer Dr. Michele Weigle Department of Computer Science Old Dominion University mweigle@cs.odu.edu http://www.cs.odu.edu/~mweigle/cs455-s13 1 Link Layer
CS 455/555 Intro to Networks and Communications Link Layer Dr. Michele Weigle Department of Computer Science Old Dominion University mweigle@cs.odu.edu http://www.cs.odu.edu/~mweigle/cs455-s13 1 Link Layer
Links Reading: Chapter 2. Goals of Todayʼs Lecture. Message, Segment, Packet, and Frame
 Links Reading: Chapter 2 CS 375: Computer Networks Thomas Bressoud 1 Goals of Todayʼs Lecture Link-layer services Encoding, framing, and error detection Error correction and flow control Sharing a shared
Links Reading: Chapter 2 CS 375: Computer Networks Thomas Bressoud 1 Goals of Todayʼs Lecture Link-layer services Encoding, framing, and error detection Error correction and flow control Sharing a shared
CPE 448/548 Exam #1 (100 pts) February 14, Name Class: 448
 Name Class: 448 1) (14 pts) A message M = 11001 is transmitted from node A to node B using the CRC code. The CRC generator polynomial is G(x) = x 3 + x 2 + 1 ( bit sequence 1101) a) What is the transmitted
Name Class: 448 1) (14 pts) A message M = 11001 is transmitted from node A to node B using the CRC code. The CRC generator polynomial is G(x) = x 3 + x 2 + 1 ( bit sequence 1101) a) What is the transmitted
Data Link Layer. Learning Objectives. Position of the data-link layer. MCA 207, Data Communication & Networking
 Data Link Layer Bharati Vidyapeeth s Institute of Computer Applications and Management,New Delhi-63 by Vishal Jain U2. 1 Learning Objectives To introduce the design issues of data link layer. To discuss
Data Link Layer Bharati Vidyapeeth s Institute of Computer Applications and Management,New Delhi-63 by Vishal Jain U2. 1 Learning Objectives To introduce the design issues of data link layer. To discuss
Data Link Layer, Part 5. Medium Access Control
 CS 455 Medium Access Control, Page 1 Data Link Layer, Part 5 Medium Access Control These slides are created by Dr. Yih Huang of George Mason University. Students registered in Dr. Huang s courses at GMU
CS 455 Medium Access Control, Page 1 Data Link Layer, Part 5 Medium Access Control These slides are created by Dr. Yih Huang of George Mason University. Students registered in Dr. Huang s courses at GMU
12.2. Figure 12.1 Data link layer divided into two functionality-oriented sublayers
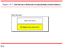 12.2 Figure 12.1 Data link layer divided into two functionality-oriented sublayers 12.3 Figure 12.2 Taxonomy of multiple-access protocols discussed in this chapter 12-1 RANDOM ACCESS 12.4 In random access
12.2 Figure 12.1 Data link layer divided into two functionality-oriented sublayers 12.3 Figure 12.2 Taxonomy of multiple-access protocols discussed in this chapter 12-1 RANDOM ACCESS 12.4 In random access
2.1 CHANNEL ALLOCATION 2.2 MULTIPLE ACCESS PROTOCOLS Collision Free Protocols 2.3 FDDI 2.4 DATA LINK LAYER DESIGN ISSUES 2.5 FRAMING & STUFFING
 UNIT-2 2.1 CHANNEL ALLOCATION 2.2 MULTIPLE ACCESS PROTOCOLS 2.2.1 Pure ALOHA 2.2.2 Slotted ALOHA 2.2.3 Carrier Sense Multiple Access 2.2.4 CSMA with Collision Detection 2.2.5 Collision Free Protocols 2.2.5.1
UNIT-2 2.1 CHANNEL ALLOCATION 2.2 MULTIPLE ACCESS PROTOCOLS 2.2.1 Pure ALOHA 2.2.2 Slotted ALOHA 2.2.3 Carrier Sense Multiple Access 2.2.4 CSMA with Collision Detection 2.2.5 Collision Free Protocols 2.2.5.1
Medium Access Control
 TC 3TCA NET Département Télécommunications Services & Usages Intervenant Razvan Stanica razvan.stanica@insa-lyon.fr. Ingénieur Télécom-Réseaux ENSEEIHT, promo 2008. Thèse sur le Contrôle de Congestion
TC 3TCA NET Département Télécommunications Services & Usages Intervenant Razvan Stanica razvan.stanica@insa-lyon.fr. Ingénieur Télécom-Réseaux ENSEEIHT, promo 2008. Thèse sur le Contrôle de Congestion
CS 43: Computer Networks Media Access. Kevin Webb Swarthmore College November 30, 2017
 CS 43: Computer Networks Media Access Kevin Webb Swarthmore College November 30, 2017 Multiple Access Links & Protocols Two classes of links : point-to-point dial-up access link between Ethernet switch,
CS 43: Computer Networks Media Access Kevin Webb Swarthmore College November 30, 2017 Multiple Access Links & Protocols Two classes of links : point-to-point dial-up access link between Ethernet switch,
Lecture 8 The Data Link Layer part I. Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it
 Lecture 8 The Data Link Layer part I Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it Link Layer: setting the context two physically connected devices: host-router, router-router,
Lecture 8 The Data Link Layer part I Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it Link Layer: setting the context two physically connected devices: host-router, router-router,
Lecture 6. Data Link Layer (cont d) Data Link Layer 1-1
 Lecture 6 Data Link Layer (cont d) Data Link Layer 1-1 Agenda Continue the Data Link Layer Multiple Access Links and Protocols Addressing Data Link Layer 1-2 Multiple Access Links and Protocols Two types
Lecture 6 Data Link Layer (cont d) Data Link Layer 1-1 Agenda Continue the Data Link Layer Multiple Access Links and Protocols Addressing Data Link Layer 1-2 Multiple Access Links and Protocols Two types
Chapter 5 Data-Link Layer: Wired Networks
 Sungkyunkwan University Chapter 5 Data-Link Layer: Wired Networks Prepared by Syed M. Raza and H. Choo 2018-Fall Computer Networks Copyright 2000-2018 Networking Laboratory Chapter 5 Outline 5.1 Introduction
Sungkyunkwan University Chapter 5 Data-Link Layer: Wired Networks Prepared by Syed M. Raza and H. Choo 2018-Fall Computer Networks Copyright 2000-2018 Networking Laboratory Chapter 5 Outline 5.1 Introduction
COMPUTER NETWORKS UNIT 3
 COMPUTER NETWORKS UNIT 3 1. Illustrate about Reservation, Polling and Token Passing. [10 marks] Controlled access: In controlled access, the stations consult one another to find which station has the right
COMPUTER NETWORKS UNIT 3 1. Illustrate about Reservation, Polling and Token Passing. [10 marks] Controlled access: In controlled access, the stations consult one another to find which station has the right
SRI RAMAKRISHNA INSTITUTE OF TECHNOLOGY DEPARTMENT OF INFORMATION TECHNOLOGY COMPUTER NETWORKS UNIT - II DATA LINK LAYER
 SRI RAMAKRISHNA INSTITUTE OF TECHNOLOGY DEPARTMENT OF INFORMATION TECHNOLOGY COMPUTER NETWORKS UNIT - II DATA LINK LAYER 1. What are the responsibilities of data link layer? Specific responsibilities of
SRI RAMAKRISHNA INSTITUTE OF TECHNOLOGY DEPARTMENT OF INFORMATION TECHNOLOGY COMPUTER NETWORKS UNIT - II DATA LINK LAYER 1. What are the responsibilities of data link layer? Specific responsibilities of
Links. CS125 - mylinks 1 1/22/14
 Links 1 Goals of Today s Lecture Link-layer services Encoding, framing, and error detection Error correction and flow control Sharing a shared media Channel partitioning Taking turns Random access Shared
Links 1 Goals of Today s Lecture Link-layer services Encoding, framing, and error detection Error correction and flow control Sharing a shared media Channel partitioning Taking turns Random access Shared
CSC 401 Data and Computer Communications Networks
 CSC 401 Data and Computer Communications Networks Link Layer: Intro, Errors, Multiple Access Sec 6.1, 6.2, 6.3 Prof. Lina Battestilli Fall 2017 Chapter 6: Link layer Goals: understand principles behind
CSC 401 Data and Computer Communications Networks Link Layer: Intro, Errors, Multiple Access Sec 6.1, 6.2, 6.3 Prof. Lina Battestilli Fall 2017 Chapter 6: Link layer Goals: understand principles behind
CMPE 150/L : Introduction to Computer Networks. Chen Qian Computer Engineering UCSC Baskin Engineering Lecture 16
 CMPE 150/L : Introduction to Computer Networks Chen Qian Computer Engineering UCSC Baskin Engineering Lecture 16 1 Final project demo Please do the demo next week to the TAs. So basically you may need
CMPE 150/L : Introduction to Computer Networks Chen Qian Computer Engineering UCSC Baskin Engineering Lecture 16 1 Final project demo Please do the demo next week to the TAs. So basically you may need
Chapter 3. The Data Link Layer. Wesam A. Hatamleh
 Chapter 3 The Data Link Layer The Data Link Layer Data Link Layer Design Issues Error Detection and Correction Elementary Data Link Protocols Sliding Window Protocols Example Data Link Protocols The Data
Chapter 3 The Data Link Layer The Data Link Layer Data Link Layer Design Issues Error Detection and Correction Elementary Data Link Protocols Sliding Window Protocols Example Data Link Protocols The Data
CC451 Computer Networks
 CC451 Computer Networks Lecture 9 Link Layer 5: DataLink Layer 5-1 Chapter 5 Link Layer and LANs A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students,
CC451 Computer Networks Lecture 9 Link Layer 5: DataLink Layer 5-1 Chapter 5 Link Layer and LANs A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students,
Physical and Data Link layers
 Physical and Data Link layers Youki Kadobayashi Graduate School of Science Nara Institute of Science and Technology Physical Layer All rights reserved. 2 Types of transmission medium! Cables Optical fiber
Physical and Data Link layers Youki Kadobayashi Graduate School of Science Nara Institute of Science and Technology Physical Layer All rights reserved. 2 Types of transmission medium! Cables Optical fiber
Data Link Layer, Part 3 Medium Access Control. Preface
 Data Link Layer, Part 3 Medium Access Control These slides are created by Dr. Yih Huang of George Mason University. Students registered in Dr. Huang's courses at GMU can make a single machine-readable
Data Link Layer, Part 3 Medium Access Control These slides are created by Dr. Yih Huang of George Mason University. Students registered in Dr. Huang's courses at GMU can make a single machine-readable
Chapter 5: Link layer
 Chapter 5: Link layer our goals: v understand principles behind link layer services: error detection, correction sharing a broadcast channel: multiple access link layer addressing local area networks:
Chapter 5: Link layer our goals: v understand principles behind link layer services: error detection, correction sharing a broadcast channel: multiple access link layer addressing local area networks:
Outline: Connecting Many Computers
 Outline: Connecting Many Computers Last lecture: sending data between two computers This lecture: link-level network protocols (from last lecture) sending data among many computers 1 Review: A simple point-to-point
Outline: Connecting Many Computers Last lecture: sending data between two computers This lecture: link-level network protocols (from last lecture) sending data among many computers 1 Review: A simple point-to-point
CSC 4900 Computer Networks: The Link Layer
 CSC 4900 Computer Networks: The Link Layer Professor Henry Carter Fall 2017 Last Time We talked about intra-as routing protocols: Which routing algorithm is used in RIP? OSPF? What techniques allow OSPF
CSC 4900 Computer Networks: The Link Layer Professor Henry Carter Fall 2017 Last Time We talked about intra-as routing protocols: Which routing algorithm is used in RIP? OSPF? What techniques allow OSPF
Chapter 6 The Link Layer and LANs
 Chapter 6 The Link Layer and LANs A note on the use of these Powerpoint slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the
Chapter 6 The Link Layer and LANs A note on the use of these Powerpoint slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the
INSTITUTE OF AERONAUTICAL ENGINEERING (Autonomous) Dundigal, Hyderabad
 INSTITUTE OF AERONAUTICAL ENGINEERING (Autonomous) Dundigal, Hyderabad - 500 043 COMPUTER SCIENCE AND ENGINEERING TUTORIAL QUESTION BANK Name Code Class Branch COMPUTER NETWORKS A50515 Year 2016 17 Coordinator
INSTITUTE OF AERONAUTICAL ENGINEERING (Autonomous) Dundigal, Hyderabad - 500 043 COMPUTER SCIENCE AND ENGINEERING TUTORIAL QUESTION BANK Name Code Class Branch COMPUTER NETWORKS A50515 Year 2016 17 Coordinator
Chapter 5 Link Layer and LANs
 Chapter 5 Link Layer and LANs A note on the use of these ppt slides: All material copyright 1996-2007 J.F Kurose and K.W. Ross, All Rights Reserved Computer Networking: A Top Down Approach 4 th edition.
Chapter 5 Link Layer and LANs A note on the use of these ppt slides: All material copyright 1996-2007 J.F Kurose and K.W. Ross, All Rights Reserved Computer Networking: A Top Down Approach 4 th edition.
Multiple Access Links and Protocols
 Multiple Access Links and Protocols Two types of links : point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) old-fashioned Ethernet
Multiple Access Links and Protocols Two types of links : point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) old-fashioned Ethernet
Media Access Control. Networked Systems (H) Lecture 5
 Media Access Control Networked Systems (H) Lecture 5 Lecture Outline Controlling access to the channel Link contention Media access control protocols Contention-based protocols CSMA/CD Token ring Slotted
Media Access Control Networked Systems (H) Lecture 5 Lecture Outline Controlling access to the channel Link contention Media access control protocols Contention-based protocols CSMA/CD Token ring Slotted
1-1. Switching Networks (Fall 2010) EE 586 Communication and. November 8, Lecture 30
 EE 586 Communication and Switching Networks (Fall 2010) Lecture 30 November 8, 2010 1-1 Announcements Quiz on Wednesday Next Monday hands-on training on Contiki OS Bring your laptop 4-2 Multiple Access
EE 586 Communication and Switching Networks (Fall 2010) Lecture 30 November 8, 2010 1-1 Announcements Quiz on Wednesday Next Monday hands-on training on Contiki OS Bring your laptop 4-2 Multiple Access
Chapter 5 Link Layer and LANs
 Chapter 5 Link Layer and LANs Computer Networking: A Top Down Approach 4 th edition. Jim Kurose, Keith Ross Addison-Wesley, July 2007. All material copyright 1996-2007 J.F Kurose and K.W. Ross, All Rights
Chapter 5 Link Layer and LANs Computer Networking: A Top Down Approach 4 th edition. Jim Kurose, Keith Ross Addison-Wesley, July 2007. All material copyright 1996-2007 J.F Kurose and K.W. Ross, All Rights
Module 10 Data Link Layer CS655! 10-1!
 Module 10 Data Link Layer CS655! 10-1! Please note: Most of these slides come from this book. Note their copyright notice below! A note on the use of these ppt slides: We re making these slides freely
Module 10 Data Link Layer CS655! 10-1! Please note: Most of these slides come from this book. Note their copyright notice below! A note on the use of these ppt slides: We re making these slides freely
King Fahd University of Petroleum and Minerals College of Computer Sciences and Engineering Department of Computer Engineering
 Student Name: Section #: King Fahd University of Petroleum and Minerals College of Computer Sciences and Engineering Department of Computer Engineering COE 344 Computer Networks (T072) Final Exam Date
Student Name: Section #: King Fahd University of Petroleum and Minerals College of Computer Sciences and Engineering Department of Computer Engineering COE 344 Computer Networks (T072) Final Exam Date
Physical Layer. Medium Access Links and Protocols. Point-to-Point protocols. Modems: Signaling. Modems Signaling. Srinidhi Varadarajan
 P Physical Layer Srinidhi Varadarajan Medium Access Links and Protocols Three types of links : point-to-point (single wire, e.g. PPP, SLIP) broadcast (shared wire or medium; e.g, Ethernet, Wavelan, etc.)
P Physical Layer Srinidhi Varadarajan Medium Access Links and Protocols Three types of links : point-to-point (single wire, e.g. PPP, SLIP) broadcast (shared wire or medium; e.g, Ethernet, Wavelan, etc.)
Overview. Data Link Technology. Role of the data-link layer. Role of the data-link layer. Function of the physical layer
 Overview Data Link Technology Functions of the data link layer Technologies concept and design error control flow control fundamental protocols Suguru Yamaguchi Nara Institute of Science and Technology
Overview Data Link Technology Functions of the data link layer Technologies concept and design error control flow control fundamental protocols Suguru Yamaguchi Nara Institute of Science and Technology
Link Layer and LANs. CMPS 4750/6750: Computer Networks
 Link Layer and LANs CMPS 4750/6750: Computer Networks 1 Outline overview (6.1) multiple access (6.3) link addressing: ARP (6.4.1) a day in the life of a web request (6.7) 2 Link layer: introduction terminology:
Link Layer and LANs CMPS 4750/6750: Computer Networks 1 Outline overview (6.1) multiple access (6.3) link addressing: ARP (6.4.1) a day in the life of a web request (6.7) 2 Link layer: introduction terminology:
The MAC layer in wireless networks
 The MAC layer in wireless networks The wireless MAC layer roles Access control to shared channel(s) Natural broadcast of wireless transmission Collision of signal: a /space problem Who transmits when?
The MAC layer in wireless networks The wireless MAC layer roles Access control to shared channel(s) Natural broadcast of wireless transmission Collision of signal: a /space problem Who transmits when?
The Link Layer II: Ethernet
 Monday Recap The Link Layer II: Ethernet q Link layer services q Principles for multiple access protocols q Categories of multiple access protocols CSC 249 March 24, 2017 1 2 Recap: Random Access Protocols
Monday Recap The Link Layer II: Ethernet q Link layer services q Principles for multiple access protocols q Categories of multiple access protocols CSC 249 March 24, 2017 1 2 Recap: Random Access Protocols
Lecture 6 The Data Link Layer. Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it
 Lecture 6 The Data Link Layer Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it Link Layer: setting the context two physically connected devices: host-router, router-router, host-host,
Lecture 6 The Data Link Layer Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it Link Layer: setting the context two physically connected devices: host-router, router-router, host-host,
MULTIPLE ACCESS PROTOCOLS 2. 1
 MULTIPLE ACCESS PROTOCOLS AND WIFI 1 MULTIPLE ACCESS PROTOCOLS 2. 1 MULTIPLE ACCESS LINKS, PROTOCOLS Two types of links : point-to-point broadcast (shared wire or medium) POINT-TO-POINT PPP for dial-up
MULTIPLE ACCESS PROTOCOLS AND WIFI 1 MULTIPLE ACCESS PROTOCOLS 2. 1 MULTIPLE ACCESS LINKS, PROTOCOLS Two types of links : point-to-point broadcast (shared wire or medium) POINT-TO-POINT PPP for dial-up
CCM 4300 Lecture 5 Computer Networks, Wireless and Mobile Communications. Dr Shahedur Rahman. Room: T115
 CCM 4300 Lecture 5 Computer Networks, Wireless and Mobile Communications Dr Shahedur Rahman s.rahman@mdx.ac.uk Room: T115 1 Recap of Last Session Described the physical layer Analogue and Digital signal
CCM 4300 Lecture 5 Computer Networks, Wireless and Mobile Communications Dr Shahedur Rahman s.rahman@mdx.ac.uk Room: T115 1 Recap of Last Session Described the physical layer Analogue and Digital signal
COMPUTER NETWORK Model Test Paper
 Model Test Paper Question no. 1 is compulsory. Attempt all parts. Q1. Each question carries equal marks. (5*5 marks) A) Difference between Transmission Control Protocol (TCP) and User Datagram Protocol.
Model Test Paper Question no. 1 is compulsory. Attempt all parts. Q1. Each question carries equal marks. (5*5 marks) A) Difference between Transmission Control Protocol (TCP) and User Datagram Protocol.
Link Layer and Ethernet
 Link Layer and Ethernet 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross traceroute Data Link Layer Multiple
Link Layer and Ethernet 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross traceroute Data Link Layer Multiple
Lecture 19. Principles behind data link layer services Framing Multiple access protocols
 Link Layer Lecture 19 Principles behind data link layer services Framing Multiple access protocols ALOHA *The slides are adapted from ppt slides (in substantially unaltered form) available from Computer
Link Layer Lecture 19 Principles behind data link layer services Framing Multiple access protocols ALOHA *The slides are adapted from ppt slides (in substantially unaltered form) available from Computer
Link Layer and Ethernet
 Link Layer and Ethernet 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross traceroute Data Link Layer Multiple
Link Layer and Ethernet 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross traceroute Data Link Layer Multiple
DATA LINK LAYER UNIT 7.
 DATA LINK LAYER UNIT 7 1 Data Link Layer Design Issues: 1. Service provided to network layer. 2. Determining how the bits of the physical layer are grouped into frames (FRAMING). 3. Dealing with transmission
DATA LINK LAYER UNIT 7 1 Data Link Layer Design Issues: 1. Service provided to network layer. 2. Determining how the bits of the physical layer are grouped into frames (FRAMING). 3. Dealing with transmission
Chapter 6 Medium Access Control Protocols and Local Area Networks
 Chapter 6 Medium Access Control Protocols and Local Area Networks Part I: Medium Access Control Part II: Local Area Networks CSE 3213, Winter 2010 Instructor: Foroohar Foroozan Chapter Overview Broadcast
Chapter 6 Medium Access Control Protocols and Local Area Networks Part I: Medium Access Control Part II: Local Area Networks CSE 3213, Winter 2010 Instructor: Foroohar Foroozan Chapter Overview Broadcast
Chapter 6 Local Area Networks and Media Access Control. School of Info. Sci. & Eng. Shandong Univ.
 Chapter 6 Local Area Networks and Media Access Control School of Info. Sci. & Eng. Shandong Univ. 6.1 MULTIPLE ACCESS COMMUNICATIONS FIGURE 6.1 Multiple access communications FIGURE 6.2 Approaches to sharing
Chapter 6 Local Area Networks and Media Access Control School of Info. Sci. & Eng. Shandong Univ. 6.1 MULTIPLE ACCESS COMMUNICATIONS FIGURE 6.1 Multiple access communications FIGURE 6.2 Approaches to sharing
Chapter 5 Link Layer. Computer Networking: A Top Down Approach. 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012
 Chapter 5 Link Layer A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the animations; and can
Chapter 5 Link Layer A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the animations; and can
Lecture 4: Wireless MAC Overview. Hung-Yu Wei National Taiwan University
 Lecture 4: Wireless MAC Overview Hung-Yu Wei National Taiwan University Medium Access Control Topology 3 Simplex and Duplex 4 FDMA TDMA CDMA DSSS FHSS Multiple Access Methods Notice: CDMA and spread spectrum
Lecture 4: Wireless MAC Overview Hung-Yu Wei National Taiwan University Medium Access Control Topology 3 Simplex and Duplex 4 FDMA TDMA CDMA DSSS FHSS Multiple Access Methods Notice: CDMA and spread spectrum
Outline. Introduction to Networked Embedded Systems - Embedded systems Networked embedded systems Embedded Internet - Network properties
 Outline Introduction to Networked Embedded Systems - Embedded systems Networked embedded systems Embedded Internet - Network properties Layered Network Architectures - OSI framework descriptions of layers
Outline Introduction to Networked Embedded Systems - Embedded systems Networked embedded systems Embedded Internet - Network properties Layered Network Architectures - OSI framework descriptions of layers
Lecture 8 Link Layer: functionality, error detection, media access algorithm
 Lecture 8 Link Layer: functionality, error detection, media access algorithm From Kurose & Ross Book slightly modified by Romaric Duvignau duvignau@chalmers.se Thanks and enjoy! JFK/KWR All material copyright
Lecture 8 Link Layer: functionality, error detection, media access algorithm From Kurose & Ross Book slightly modified by Romaric Duvignau duvignau@chalmers.se Thanks and enjoy! JFK/KWR All material copyright
Message, Segment, Packet, and Frame Link-layer services Encoding, framing, error detection, transmission control Error correction and flow control
 Links EE 122: Intro to Communication Networks Fall 2007 (WF 4-5:30 in Cory 277) Vern Paxson TAs: Lisa Fowler, Daniel Killebrew & Jorge Ortiz http://inst.eecs.berkeley.edu/~ee122/ Announcements Homework
Links EE 122: Intro to Communication Networks Fall 2007 (WF 4-5:30 in Cory 277) Vern Paxson TAs: Lisa Fowler, Daniel Killebrew & Jorge Ortiz http://inst.eecs.berkeley.edu/~ee122/ Announcements Homework
Lecture 7: Flow & Media Access Control"
 Lecture 7: Flow & Media Access Control" CSE 123: Computer Networks Alex C. Snoeren HW 2 due next Wednesday! Lecture 7 Overview" Flow control Go-back-N Sliding window Methods to share physical media: multiple
Lecture 7: Flow & Media Access Control" CSE 123: Computer Networks Alex C. Snoeren HW 2 due next Wednesday! Lecture 7 Overview" Flow control Go-back-N Sliding window Methods to share physical media: multiple
Data Link Control Layer, Error Detection, Error Correction, and Framing
 Data Link Control Layer, Error Detection, Error Correction, and Framing EEE 538, WEEK 2 Dr. Nail Akar Bilkent University Electrical and Electronics Engineering Department 1 Error Detection Techniques Used
Data Link Control Layer, Error Detection, Error Correction, and Framing EEE 538, WEEK 2 Dr. Nail Akar Bilkent University Electrical and Electronics Engineering Department 1 Error Detection Techniques Used
Aloha and slotted aloha
 CSMA 2/13/06 Aloha and slotted aloha Slotted aloha: transmissions are synchronized and only start at the beginning of a time slot. Aloha sender A sender B collision sender C t Slotted Aloha collision sender
CSMA 2/13/06 Aloha and slotted aloha Slotted aloha: transmissions are synchronized and only start at the beginning of a time slot. Aloha sender A sender B collision sender C t Slotted Aloha collision sender
Chapter 4. The Medium Access Control Sublayer
 Chapter 4 The Medium Access Control Sublayer The Channel Allocation Problem Static Channel Allocation in LANs and MANs Dynamic Channel Allocation in LANs and MANs Dynamic Channel Allocation in LANs and
Chapter 4 The Medium Access Control Sublayer The Channel Allocation Problem Static Channel Allocation in LANs and MANs Dynamic Channel Allocation in LANs and MANs Dynamic Channel Allocation in LANs and
CS 3640: Introduction to Networks and Their Applications
 CS 3640: Introduction to Networks and Their Applications Fall 2018, Lecture 7: The Link Layer II Medium Access Control Protocols Instructor: Rishab Nithyanand Teaching Assistant: Md. Kowsar Hossain 1 You
CS 3640: Introduction to Networks and Their Applications Fall 2018, Lecture 7: The Link Layer II Medium Access Control Protocols Instructor: Rishab Nithyanand Teaching Assistant: Md. Kowsar Hossain 1 You
Lecture 3: Data Link. (A. Pattavina, Chapter 4 and 15) Ilenia Tinnirello
 Lecture 3: Data Link (A. Pattavina, Chapter 4 and 15) Data Link Layer The main tasks of the data link layer are: Transfer data from the network layer of one machine to the network layer of another machine
Lecture 3: Data Link (A. Pattavina, Chapter 4 and 15) Data Link Layer The main tasks of the data link layer are: Transfer data from the network layer of one machine to the network layer of another machine
CPE 548 Exam #1 (50 pts) February 17, 2016
 Name Class: 548 All answers must have supporting work. Any answer without support will receive no credit 1) (4 pts) Answer the following short answer questions. a) Explain the stop and wait ARQ (automatic
Name Class: 548 All answers must have supporting work. Any answer without support will receive no credit 1) (4 pts) Answer the following short answer questions. a) Explain the stop and wait ARQ (automatic
LAN PROTOCOLS. Beulah A AP/CSE
 LAN PROTOCOLS Beulah A AP/CSE IEEE STANDARDS In 1985, the Computer Society of the IEEE started a project, called Project 802, to set standards to enable intercommunication among equipment from a variety
LAN PROTOCOLS Beulah A AP/CSE IEEE STANDARDS In 1985, the Computer Society of the IEEE started a project, called Project 802, to set standards to enable intercommunication among equipment from a variety
Computer Networks. Today. Principles of datalink layer services Multiple access links Adresavimas, ARP LANs Wireless LANs VU MIF CS 1/48 2/48
 Computer Networks VU MIF CS 1/48 Today Principles of datalink layer services Multiple access links Adresavimas, ARP LANs Wireless LANs 2/48 1 Link layer: introduction terminology: hosts and routers: nodes
Computer Networks VU MIF CS 1/48 Today Principles of datalink layer services Multiple access links Adresavimas, ARP LANs Wireless LANs 2/48 1 Link layer: introduction terminology: hosts and routers: nodes
LANs. Local Area Networks. via the Media Access Control (MAC) SubLayer. Networks: Local Area Networks
 LANs Local Area Networks via the Media Access Control (MAC) SubLayer 1 Local Area Networks Aloha Slotted Aloha CSMA (non-persistent, 1-persistent, p-persistent) CSMA/CD Ethernet Token Ring 2 Network Layer
LANs Local Area Networks via the Media Access Control (MAC) SubLayer 1 Local Area Networks Aloha Slotted Aloha CSMA (non-persistent, 1-persistent, p-persistent) CSMA/CD Ethernet Token Ring 2 Network Layer
INSTITUTE OF AERONAUTICAL ENGINEERING Autonomous Dundigal, Hyderabad
 INSTITUTE OF AERONAUTICAL ENGINEERING Autonomous Dundigal, Hyderabad - 500 043 COMPUTER SCIENCE AND ENGINEERING TUTORIAL QUESTION BANK Name Code Class Branch COMPUTER NETWORKS A50515 Year 2017 18 Coordinator
INSTITUTE OF AERONAUTICAL ENGINEERING Autonomous Dundigal, Hyderabad - 500 043 COMPUTER SCIENCE AND ENGINEERING TUTORIAL QUESTION BANK Name Code Class Branch COMPUTER NETWORKS A50515 Year 2017 18 Coordinator
Chapter 4 Data Link Layer
 Chapter 4 Data Link Layer Data Link Layer Objectives: understand principles behind data link layer services: error detection and correction ( by the receiver) reliable data transfer link access by sharing
Chapter 4 Data Link Layer Data Link Layer Objectives: understand principles behind data link layer services: error detection and correction ( by the receiver) reliable data transfer link access by sharing
Computer Networks Medium Access Control. Mostafa Salehi Fall 2008
 Computer Networks Medium Access Control Mostafa Salehi Fall 2008 2008 1 Outline Issues ALOHA Network Ethernet Token Ring Wireless 2 Main Issues Local Area Network (LAN) : Three or more machines are physically
Computer Networks Medium Access Control Mostafa Salehi Fall 2008 2008 1 Outline Issues ALOHA Network Ethernet Token Ring Wireless 2 Main Issues Local Area Network (LAN) : Three or more machines are physically
Goals of Today s Lecture. Adaptors Communicating
 Goals of Today s Lecture EE 122: Link Layer Ion Stoica TAs: Junda Liu, DK Moon, David Zats http://inst.eecs.berkeley.edu/~ee122/ (Materials with thanks to Vern Paxson, Jennifer Rexford, and colleagues
Goals of Today s Lecture EE 122: Link Layer Ion Stoica TAs: Junda Liu, DK Moon, David Zats http://inst.eecs.berkeley.edu/~ee122/ (Materials with thanks to Vern Paxson, Jennifer Rexford, and colleagues
CS 716: Introduction to communication networks. - 9 th class; 19 th Aug Instructor: Sridhar Iyer IIT Bombay
 CS 716: Introduction to communication networks - 9 th class; 19 th Aug 2011 Instructor: Sridhar Iyer IIT Bombay Contention-based MAC: ALOHA Users transmit whenever they have data to send Collisions occur,
CS 716: Introduction to communication networks - 9 th class; 19 th Aug 2011 Instructor: Sridhar Iyer IIT Bombay Contention-based MAC: ALOHA Users transmit whenever they have data to send Collisions occur,
Chapter V: Link Layer
 Chapter V: Link Layer UG3 Computer Communications & Networks (COMN) Myungjin Lee myungjin.lee@ed.ac.uk Slides copyright of Kurose and Ross Link layer services framing, link access: encapsulate datagram
Chapter V: Link Layer UG3 Computer Communications & Networks (COMN) Myungjin Lee myungjin.lee@ed.ac.uk Slides copyright of Kurose and Ross Link layer services framing, link access: encapsulate datagram
Chapter 5 Link Layer. Computer Networking: A Top Down Approach. 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012
 Chapter 5 Link Layer Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 All material copyright 1996-2012 J.F Kurose and K.W. Ross, All Rights Reserved
Chapter 5 Link Layer Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 All material copyright 1996-2012 J.F Kurose and K.W. Ross, All Rights Reserved
The MAC layer in wireless networks
 The MAC layer in wireless networks The wireless MAC layer roles Access control to shared channel(s) Natural broadcast of wireless transmission Collision of signal: a time/space problem Who transmits when?
The MAC layer in wireless networks The wireless MAC layer roles Access control to shared channel(s) Natural broadcast of wireless transmission Collision of signal: a time/space problem Who transmits when?
QUESTION BANK EVEN SEMESTER
 Fatima Michael College of Engineering and Technology DEPARTMENT OF ELECTRONICS AND COMMUNICATION ENGINEERING QUESTION BANK EVEN SEMESTER SUB CODE & NAME: EC2352 COMPUTER NETWORKS YEAR / SEM: III / VI Staff
Fatima Michael College of Engineering and Technology DEPARTMENT OF ELECTRONICS AND COMMUNICATION ENGINEERING QUESTION BANK EVEN SEMESTER SUB CODE & NAME: EC2352 COMPUTER NETWORKS YEAR / SEM: III / VI Staff
Department of Computer and IT Engineering University of Kurdistan. Data Communication Netwotks (Graduate level) Data Link Layer
 Department of Computer and IT Engineering University of Kurdistan Data Communication Netwotks (Graduate level) Data Link Layer By: Dr. Alireza Abdollahpouri Data Link Layer 2 Data Link Layer Application
Department of Computer and IT Engineering University of Kurdistan Data Communication Netwotks (Graduate level) Data Link Layer By: Dr. Alireza Abdollahpouri Data Link Layer 2 Data Link Layer Application
Data Link Technology. Suguru Yamaguchi Nara Institute of Science and Technology Department of Information Science
 Data Link Technology Suguru Yamaguchi Nara Institute of Science and Technology Department of Information Science Agenda Functions of the data link layer Technologies concept and design error control flow
Data Link Technology Suguru Yamaguchi Nara Institute of Science and Technology Department of Information Science Agenda Functions of the data link layer Technologies concept and design error control flow
CS 716: Introduction to communication networks. - 8 th class; 17 th Aug Instructor: Sridhar Iyer IIT Bombay
 CS 716: Introduction to communication networks - 8 th class; 17 th Aug 2011 Instructor: Sridhar Iyer IIT Bombay Key points to consider for MAC Types/Modes of communication: Although the medium is shared,
CS 716: Introduction to communication networks - 8 th class; 17 th Aug 2011 Instructor: Sridhar Iyer IIT Bombay Key points to consider for MAC Types/Modes of communication: Although the medium is shared,
Redes de Computadores. Medium Access Control
 Redes de Computadores Medium Access Control Manuel P. Ricardo Faculdade de Engenharia da Universidade do Porto 1 » How to control the access of computers to a communication medium?» What is the ideal Medium
Redes de Computadores Medium Access Control Manuel P. Ricardo Faculdade de Engenharia da Universidade do Porto 1 » How to control the access of computers to a communication medium?» What is the ideal Medium
transferring datagram from one node data-link layer has responsibility of to adjacent node over a link 5-1 TDTS06 Computer networks
 TDTS06 Computer networks Lecture 7: The link layer I Link Layer: Introduction Some terminology: hosts and routers are nodes communication channels that connect adjacent nodes along communication path are
TDTS06 Computer networks Lecture 7: The link layer I Link Layer: Introduction Some terminology: hosts and routers are nodes communication channels that connect adjacent nodes along communication path are
Medium Access Control. MAC protocols: design goals, challenges, contention-based and contention-free protocols
 Medium Access Control MAC protocols: design goals, challenges, contention-based and contention-free protocols 1 Why do we need MAC protocols? Wireless medium is shared Many nodes may need to access the
Medium Access Control MAC protocols: design goals, challenges, contention-based and contention-free protocols 1 Why do we need MAC protocols? Wireless medium is shared Many nodes may need to access the
ERROR AND FLOW CONTROL. Lecture: 10 Instructor Mazhar Hussain
 ERROR AND FLOW CONTROL Lecture: 10 Instructor Mazhar Hussain 1 FLOW CONTROL Flow control coordinates the amount of data that can be sent before receiving acknowledgement It is one of the most important
ERROR AND FLOW CONTROL Lecture: 10 Instructor Mazhar Hussain 1 FLOW CONTROL Flow control coordinates the amount of data that can be sent before receiving acknowledgement It is one of the most important
