RSA NetWitness Logs. F5 Big-IP Advanced Firewall Manager. Event Source Log Configuration Guide. Last Modified: Friday, May 12, 2017
|
|
|
- Gregory Douglas
- 5 years ago
- Views:
Transcription
1 RSA NetWitness Logs Event Source Log Configuration Guide F5 Big-IP Advanced Firewall Manager Last Modified: Friday, May 12, 2017 Event Source Product Information: Vendor: F5 Event Source: Big-IP Advanced Firewall Manager Version: 11.5 RSA Product Information: Supported On: NetWitness Suite 10.0 and later Event Source Log Parser: bigipafm Collection Method: Syslog Event Source Class.Subclass: Security.Firewall
2 To configure the F5 Big-IP Advanced Firewall Manager event source, you must: I. Configure Syslog Output on F5 Big-IP Advanced Firewall Manager II. Configure NetWitness Suite for Syslog Collection 2
3 Configure Syslog Output on F5 Big-IP Advanced Firewall Manager Note: These instructions are taken from the BIG-IP Network Firewall: Policies and Implementations (Version 11.6) guide. In the following procedures, we discuss only the required parameter changes needed to get the Big-IP AFM event source to communicate with RSA NetWitness Suite. For all other parameters, please see the BIG-IP Network Firewall: Policies and Implementations (Version 11.6) guide for more details. To configure the Big-IP AFM event source, perform the following tasks: I. Create a pool of remote logging servers II. Create a remote high-speed log destination III. Create a publisher IV. Create a custom Network Firewall Logging profile V. Configure an LTM virtual server for Network Firewall event logging Create a pool of remote logging servers Before creating a pool of log servers, gather the IP addresses of the servers that you want to include in the pool. Ensure that the remote log servers are configured to listen to and receive log messages from the BIG-IP system. Create a pool of remote log servers to which the BIG-IP system can send log messages: 1. Open a browser window, an log onto the F5 Big-IP Configuration Utility. 2. On the Main tab, click Local Traffic > Pools. The Pool List screen opens. 3. Click Create. The New Pool screen opens. 4. In the Name field, type a unique name for the pool. 5. Using the New Members setting, add the IP address of your RSA NetWitness Suite Configure Syslog Output on F5 Big-IP Advanced Firewall Manager 3
4 Log Decoder or RSA NetWitness Suite Remote Log Collector. a. Type an IP address in the Address field, or select a node address from the Node List. b. Type a service number in the Service Port field, or select a service name from the list. Note: Typical remote logging servers require port 514. c. Click Add. 6. Click Finished. Create a remote high-speed log destination Before creating a remote high-speed log destination, ensure that at least one pool of remote log servers exists on the BIG-IP system. Create a log destination of the Remote High-Speed Log type to specify that log messages are sent to a pool of remote log servers: 1. On the Main tab, click System > Logs > Configuration > Log Destinations. The Log Destinations screen opens. 2. Click Create. 3. In the Name field, type a unique, identifiable name for this destination. 4. From the Type list, select Remote High-Speed Log. The BIG-IP system is configured to send an unformatted string of text to the log servers. 5. From the Pool Name list, select the pool of remote log servers to which you want the BIG-IP system to send log messages. 6. From the Protocol list, select protocol UDP. 7. Click Finished. Create a publisher Ensure that at least one destination associated with a pool of remote log servers exists on the BIG-IP system. 4 Create a remote high-speed log destination
5 Create a publisher to specify where the BIG-IP system sends log messages for specific resources: 1. On the Main tab, click System > Logs > Configuration > Log Publishers. The Log Publishers screen opens. 2. Click Create. 3. In the Name field, type a unique, identifiable name for this publisher. 4. For the Destinations setting, select a destination from the Available list, and click << to move the destination to the Selected list. 5. Click Finished. Create a custom Network Firewall Logging profile Create a custom Logging profile to log messages about BIG-IP system Network Firewall events: 1. On the Main tab, click Security > Event Logs > Logging Profiles. The Logging Profiles list screen opens. 2. Click Create. The New Logging Profile screen opens. 3. In the Name field, type a unique name for the profile. 4. Select the Network Firewall check box. 5. In the Network Firewall area, from the Publisher list, select the publisher the BIG- IP system uses to log Network Firewall events. 6. Set an Aggregate Rate Limit to define a rate limit for all combined network firewall log messages per second. Beyond this rate limit, log messages are not logged. 7. For the Log Rule Matches setting, select how the BIG-IP system logs packets that match ACL rules. You can select any or all of the options. When an option is selected, you can configure a rate limit for log messages of that type. Option Description Enables or disables logging of packets that match ACL rules configured with: Create a custom Network Firewall Logging profile 5
6 Option Accept Drop Reject Description action=accept action=drop action=reject 8. Select the Log IP Errors check box, to enable logging of IP error packets. When enabled, you can configure a rate limit for log messages of this type. 9. Select the Log TCP Errors check box, to enable logging of TCP error packets. When enabled, you can configure a rate limit for log messages of this type. 10. Select the Log TCP Events check box, to enable logging of open and close of TCP sessions. When enabled, you can configure a rate limit for log messages of this type. 11. Enable the Log Translation Fields setting to log both the original IP address and the NAT-translated IP address for Network Firewall log events. 12. Enable the Log Geolocation IP Address setting to specify that when a geolocation event causes a network firewall action, the associated IP address is logged. 13. From the Storage Format list, select how the BIG-IP system formats the log. Your choices are: Description Specifies the default format type in which the BIG-IP system logs messages to a remote Syslog server, for example: "management_ip_address","bigip_hostname","context_ type", "context_name","src_ip","dest_ip","src_port", "dest_port","vlan","protocol","route_domain", "acl_ rule_name","action","drop_reason This option allows you to: Select from a list, the fields to be included in the log. Specify the order the fields display in the log. Specify the delimiter that separates the content in the log. The default delimiter is the comma character. Option None Field- List User- Defined This option allows you to: Select from a list, the fields to be included in the log. 6 Create a custom Network Firewall Logging profile
7 Option Description 14. Click Finished. Cut and paste, in a string of text, the order the fields display in the log. Assign this custom network firewall Logging profile to a virtual server. Configure an LTM virtual server for Network Firewall event logging Ensure that at least one log publisher exists on the BIG-IP system. Assign a custom Network Firewall Logging profile to a virtual server when you want the BIG-IP system to log Network Firewall events on the traffic that the virtual server processes: Note: These steps apply only to LTM -provisioned systems. 1. On the Main tab, click Local Traffic > Virtual Servers. The Virtual Server List screen opens. 2. Click the name of the virtual server you want to modify.. 3. On the menu bar, click Security > Policies. The screen displays firewall rule settings. 4. From the Log Profile list, select Enabled. Then, for the Profile setting, move the profiles that log specific events to specific locations from the Available list to the Selected list. Note: If you do not have a custom profile configured, select the predefined logging profile global-network to log Advanced Firewall Manager events. Note that to log global, self IP, and route domain contexts, you must enable a Publisher in the global-network profile. 5. Click Update to save the changes. Configure an LTM virtual server for Network Firewall event logging 7
8 Configure NetWitness Suite for Syslog Collection Note: You only need to configure Syslog collection the first time that you set up an event source that uses Syslog to send its output to NetWitness. You should configure either the Log Decoder or the Remote Log Collector for Syslog. You do not need to configure both. To configure the Log Decoder for Syslog collection: 1. In the NetWitness menu, select Administration > Services. 2. In the Services grid, select a Log Decoder, and from the Actions menu, choose View > System. 3. Depending on the icon you see, do one of the following: If you see, click the icon to start capturing Syslog. If you see, you do not need to do anything; this Log Decoder is already capturing Syslog. To configure the Remote Log Collector for Syslog collection: 1. In the NetWitness menu, select Administration > Services. 2. In the Services grid, select a Remote Log Collector, and from the Actions menu, choose View > Config > Event Sources. 3. Select Syslog/Config from the drop-down menu. The Event Categories panel displays the Syslog event sources that are configured, if any. 4. In the Event Categories panel toolbar, click +. The Available Event Source Types dialog is displayed. 5. Select either syslog-tcp or syslog-udp. You can set up either or both, depending on the needs of your organization. 8 Configure NetWitness Suite for Syslog Collection
9 6. Select the new type in the Event Categories panel and click + in the Sources panel toolbar. The Add Source dialog is displayed. 7. Enter 514 for the port, and select Enabled. Optionally, configure any of the Advanced parameters as necessary. Click OK to accept your changes and close the dialog box. Once you configure one or both syslog types, the Log Decoder or Remote Log Collector collects those types of messages from all available event sources. So, you can continue to add Syslog event sources to your system without needing to do any further configuration in NetWitness. Copyright 2017 EMC Corporation. All Rights Reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks or trademarks of EMC Corporation in the United States and/or other countries. All other trademarks used herein are the property of their respective owners. Configure NetWitness Suite for Syslog Collection 9
RSA NetWitness Logs. F5 Big-IP Application Security Manager. Event Source Log Configuration Guide. Last Modified: Friday, May 12, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide F5 Big-IP Application Security Manager Last Modified: Friday, May 12, 2017 Event Source Product Information: Vendor: F5 Event Source: F5 Big-IP
RSA NetWitness Logs Event Source Log Configuration Guide F5 Big-IP Application Security Manager Last Modified: Friday, May 12, 2017 Event Source Product Information: Vendor: F5 Event Source: F5 Big-IP
RSA NetWitness Logs. F5 Big-IP Access Policy Manager. Event Source Log Configuration Guide. Last Modified: Friday, May 12, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide F5 Big-IP Access Policy Manager Last Modified: Friday, May 12, 2017 Event Source Product Information: Vendor: F5 Event Source: Big-IP Access Policy
RSA NetWitness Logs Event Source Log Configuration Guide F5 Big-IP Access Policy Manager Last Modified: Friday, May 12, 2017 Event Source Product Information: Vendor: F5 Event Source: Big-IP Access Policy
RSA NetWitness Logs. Juniper Networks NetScreen Firewall Last Modified: Monday, October 9, Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide Juniper Networks NetScreen Firewall Last Modified: Monday, October 9, 2017 Event Source Product Information: Vendor: Juniper Networks Event Source:
RSA NetWitness Logs Event Source Log Configuration Guide Juniper Networks NetScreen Firewall Last Modified: Monday, October 9, 2017 Event Source Product Information: Vendor: Juniper Networks Event Source:
RSA NetWitness Logs. Bit9 Security Platform. Event Source Log Configuration Guide. Last Modified: Friday, May 05, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Bit9 Security Platform Last Modified: Friday, May 05, 2017 Event Source Product Information: Vendor: Bit9 Event Source: Bit9 Security Platform Versions:
RSA NetWitness Logs Event Source Log Configuration Guide Bit9 Security Platform Last Modified: Friday, May 05, 2017 Event Source Product Information: Vendor: Bit9 Event Source: Bit9 Security Platform Versions:
RSA NetWitness Logs. DenyAll Web Application Firewall. Event Source Log Configuration Guide. Last Modified: Thursday, November 2, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide DenyAll Web Application Firewall Last Modified: Thursday, November 2, 2017 Event Source Product Information: Vendor: DenyAll (formerly Bee Ware)
RSA NetWitness Logs Event Source Log Configuration Guide DenyAll Web Application Firewall Last Modified: Thursday, November 2, 2017 Event Source Product Information: Vendor: DenyAll (formerly Bee Ware)
RSA NetWitness Logs. EMC Data Domain. Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide EMC Data Domain Last Modified: Monday, January 16, 2017 Event Source Product Information: Vendor: EMC Event Source: Data Domain Versions: 5.1.0.4
RSA NetWitness Logs Event Source Log Configuration Guide EMC Data Domain Last Modified: Monday, January 16, 2017 Event Source Product Information: Vendor: EMC Event Source: Data Domain Versions: 5.1.0.4
RSA NetWitness Logs. Juniper Networks NetScreen ScreenOS Last Modified: Wednesday, November 8, Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide Juniper Networks NetScreen ScreenOS Last Modified: Wednesday, November 8, 2017 Event Source Product Information: Vendor: Juniper Networks Event
RSA NetWitness Logs Event Source Log Configuration Guide Juniper Networks NetScreen ScreenOS Last Modified: Wednesday, November 8, 2017 Event Source Product Information: Vendor: Juniper Networks Event
RSA NetWitness Logs. Imperva SecureSphere. Event Source Log Configuration Guide. Last Modified: Monday, May 22, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Imperva SecureSphere Last Modified: Monday, May 22, 2017 Event Source Product Information: Vendor: Imperva Event Source: SecureSphere Versions:
RSA NetWitness Logs Event Source Log Configuration Guide Imperva SecureSphere Last Modified: Monday, May 22, 2017 Event Source Product Information: Vendor: Imperva Event Source: SecureSphere Versions:
RSA NetWitness Logs. Cisco Meraki. Event Source Log Configuration Guide. Last Modified: Monday, November 13, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Cisco Meraki Last Modified: Monday, November 13, 2017 Event Source Product Information: Vendor: Cisco Event Source: Meraki Versions: MX60, GA 12.26
RSA NetWitness Logs Event Source Log Configuration Guide Cisco Meraki Last Modified: Monday, November 13, 2017 Event Source Product Information: Vendor: Cisco Event Source: Meraki Versions: MX60, GA 12.26
RSA NetWitness Logs. Cisco Adaptive Security Appliance Last Modified: Wednesday, November 8, Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide Cisco Adaptive Security Appliance Last Modified: Wednesday, November 8, 2017 Event Source Product Information: Vendor: Cisco Event Source: Adaptive
RSA NetWitness Logs Event Source Log Configuration Guide Cisco Adaptive Security Appliance Last Modified: Wednesday, November 8, 2017 Event Source Product Information: Vendor: Cisco Event Source: Adaptive
RSA NetWitness Platform
 RSA NetWitness Platform Event Source Log Configuration Guide Palo Alto Panorama Management Server Last Modified: Friday, August 24, 2018 Event Source Product Information: Vendor: Palo Alto Event Source:
RSA NetWitness Platform Event Source Log Configuration Guide Palo Alto Panorama Management Server Last Modified: Friday, August 24, 2018 Event Source Product Information: Vendor: Palo Alto Event Source:
RSA NetWitness Platform
 RSA NetWitness Platform Event Source Log Configuration Guide Sophos UTM Last Modified: Wednesday, October 10, 2018 Event Source Product Information: Vendor: Sophos Event Source: UTM Version: 9.x, 17.x
RSA NetWitness Platform Event Source Log Configuration Guide Sophos UTM Last Modified: Wednesday, October 10, 2018 Event Source Product Information: Vendor: Sophos Event Source: UTM Version: 9.x, 17.x
RSA NetWitness Logs. Airtight Management Console. Event Source Log Configuration Guide. Last Modified: Thursday, May 04, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Airtight Management Console Last Modified: Thursday, May 04, 2017 Event Source Product Information: Vendor: AirTight Event Source: Airtight Management
RSA NetWitness Logs Event Source Log Configuration Guide Airtight Management Console Last Modified: Thursday, May 04, 2017 Event Source Product Information: Vendor: AirTight Event Source: Airtight Management
RSA NetWitness Platform
 RSA NetWitness Platform Event Source Log Configuration Guide Barracuda Spam Firewall Last Modified: Monday, May 21, 2018 Event Source Product Information: Vendor: Barracuda Networks Event Source: Spam
RSA NetWitness Platform Event Source Log Configuration Guide Barracuda Spam Firewall Last Modified: Monday, May 21, 2018 Event Source Product Information: Vendor: Barracuda Networks Event Source: Spam
Aruba Networks Mobility Controller
 Aruba Networks Mobility Controller Last Modified: Friday, July 6, 2018 Event Source Product Information: Vendor: Aruba Networks Event Source: Aruba Networks Mobility Controller Versions: ArubaOS 2.5.4.0,
Aruba Networks Mobility Controller Last Modified: Friday, July 6, 2018 Event Source Product Information: Vendor: Aruba Networks Event Source: Aruba Networks Mobility Controller Versions: ArubaOS 2.5.4.0,
RSA NetWitness Logs. IBM WebSphere DataPower. Event Source Log Configuration Guide. Last Modified: Friday, January 5, 2018
 RSA NetWitness Logs Event Source Log Configuration Guide IBM WebSphere DataPower Last Modified: Friday, January 5, 2018 Event Source Product Information: Vendor: IBM Event Source: WebSphere DataPower Versions:
RSA NetWitness Logs Event Source Log Configuration Guide IBM WebSphere DataPower Last Modified: Friday, January 5, 2018 Event Source Product Information: Vendor: IBM Event Source: WebSphere DataPower Versions:
RSA NetWitness Logs. Tripwire Enterprise. Event Source Log Configuration Guide. Last Modified: Friday, November 3, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Tripwire Enterprise Last Modified: Friday, November 3, 2017 Event Source Product Information: Vendor: Tripwire Event Source: Tripwire Enterprise
RSA NetWitness Logs Event Source Log Configuration Guide Tripwire Enterprise Last Modified: Friday, November 3, 2017 Event Source Product Information: Vendor: Tripwire Event Source: Tripwire Enterprise
RSA NetWitness Logs. RSA Web Threat Detection. Event Source Log Configuration Guide. Last Modified: Friday, April 14, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide RSA Web Threat Detection Last Modified: Friday, April 14, 2017 Event Source Product Information: Vendor: RSA Event Source: Web Threat Detection
RSA NetWitness Logs Event Source Log Configuration Guide RSA Web Threat Detection Last Modified: Friday, April 14, 2017 Event Source Product Information: Vendor: RSA Event Source: Web Threat Detection
RSA NetWitness Logs. Citrix Access Gateway Last Modified: Thursday, May 11, Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide Citrix Access Gateway Last Modified: Thursday, May 11, 2017 Event Source Product Information: Vendor: Citrix Event Source: Access Gateway Versions:
RSA NetWitness Logs Event Source Log Configuration Guide Citrix Access Gateway Last Modified: Thursday, May 11, 2017 Event Source Product Information: Vendor: Citrix Event Source: Access Gateway Versions:
RSA NetWitness Logs. Juniper Networks NetScreen-Security Manager Last Modified: Thursday, May 25, Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide Juniper Networks NetScreen-Security Manager Last Modified: Thursday, May 25, 2017 Event Source Product Information: Vendor: Juniper Networks Event
RSA NetWitness Logs Event Source Log Configuration Guide Juniper Networks NetScreen-Security Manager Last Modified: Thursday, May 25, 2017 Event Source Product Information: Vendor: Juniper Networks Event
RSA NetWitness Logs. Extreme Networks Switch Last Modified: Thursday, July 20, Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide Extreme Networks Switch Last Modified: Thursday, July 20, 2017 Event Source Product Information: Vendor: Extreme Networks Event Source: Extreme
RSA NetWitness Logs Event Source Log Configuration Guide Extreme Networks Switch Last Modified: Thursday, July 20, 2017 Event Source Product Information: Vendor: Extreme Networks Event Source: Extreme
RSA NetWitness Logs. Cisco Wireless LAN Controller. Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide Cisco Wireless LAN Controller Last Modified: Thursday, May 11, 2017 Event Source Product Information: Vendor: Cisco Event Source: Wireless LAN Controller
RSA NetWitness Logs Event Source Log Configuration Guide Cisco Wireless LAN Controller Last Modified: Thursday, May 11, 2017 Event Source Product Information: Vendor: Cisco Event Source: Wireless LAN Controller
RSA NetWitness Logs. Bind DNS. Event Source Log Configuration Guide. Last Modified: Thursday, October 19, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Bind DNS Last Modified: Thursday, October 19, 2017 Event Source Product Information: Vendor: Bind Event Source: Bind DNS Logs Versions: Bind DNS:
RSA NetWitness Logs Event Source Log Configuration Guide Bind DNS Last Modified: Thursday, October 19, 2017 Event Source Product Information: Vendor: Bind Event Source: Bind DNS Logs Versions: Bind DNS:
RSA NetWitness Logs. EMC Isilon. Event Source Log Configuration Guide. Last Modified: Tuesday, October 31, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide EMC Isilon Last Modified: Tuesday, October 31, 2017 Event Source Product Information: Vendor: EMC Event Source: Isilon Versions: 6.5.3.32, 6.5.5.7,
RSA NetWitness Logs Event Source Log Configuration Guide EMC Isilon Last Modified: Tuesday, October 31, 2017 Event Source Product Information: Vendor: EMC Event Source: Isilon Versions: 6.5.3.32, 6.5.5.7,
RSA NetWitness Logs. F5 Big-IP Local Traffic Manager. Event Source Log Configuration Guide. Last Modified: Friday, May 12, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide F5 Big-IP Local Traffic Manager Last Modified: Friday, May 12, 2017 Event Source Product Information: Vendor: F5 Event Source: Big-IP Local Traffic
RSA NetWitness Logs Event Source Log Configuration Guide F5 Big-IP Local Traffic Manager Last Modified: Friday, May 12, 2017 Event Source Product Information: Vendor: F5 Event Source: Big-IP Local Traffic
RSA NetWitness Logs. Symantec DLP Last Modified: Thursday, April 12, Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide Symantec DLP Last Modified: Thursday, April 12, 2018 Event Source Product Information: Vendor: Symantec Event Source: Data Loss Prevention Versions:
RSA NetWitness Logs Event Source Log Configuration Guide Symantec DLP Last Modified: Thursday, April 12, 2018 Event Source Product Information: Vendor: Symantec Event Source: Data Loss Prevention Versions:
RSA NetWitness Logs. Trend Micro InterScan Messaging Security Suite. Event Source Log Configuration Guide. Last Modified: Tuesday, April 25, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Trend Micro InterScan Messaging Security Suite Last Modified: Tuesday, April 25, 2017 Event Source Product Information: Vendor: Trend Micro Event
RSA NetWitness Logs Event Source Log Configuration Guide Trend Micro InterScan Messaging Security Suite Last Modified: Tuesday, April 25, 2017 Event Source Product Information: Vendor: Trend Micro Event
RSA NetWitness Logs. Oracle Audit Vault and Database Firewall. Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide Oracle Audit Vault and Database Firewall Last Modified: Thursday, June 29, 2017 Event Source Product Information: Vendor: Oracle Event Source: Oracle
RSA NetWitness Logs Event Source Log Configuration Guide Oracle Audit Vault and Database Firewall Last Modified: Thursday, June 29, 2017 Event Source Product Information: Vendor: Oracle Event Source: Oracle
RSA NetWitness Logs. McAfee Data Loss Prevention Endpoint. Event Source Log Configuration Guide. Last Modified: Thursday, May 25, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide McAfee Data Loss Prevention Endpoint Last Modified: Thursday, May 25, 2017 Event Source Product Information: Vendor: McAfee Event Source: Data Loss
RSA NetWitness Logs Event Source Log Configuration Guide McAfee Data Loss Prevention Endpoint Last Modified: Thursday, May 25, 2017 Event Source Product Information: Vendor: McAfee Event Source: Data Loss
RSA NetWitness Logs. Cisco IronPort Security Appliance. Event Source Log Configuration Guide. Last Modified: Thursday, January 19, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Cisco IronPort Email Security Appliance Last Modified: Thursday, January 19, 2017 Event Source Product Information: Vendor: Cisco Event Source:
RSA NetWitness Logs Event Source Log Configuration Guide Cisco IronPort Email Security Appliance Last Modified: Thursday, January 19, 2017 Event Source Product Information: Vendor: Cisco Event Source:
RSA NetWitness Logs. VMware NSX. Event Source Log Configuration Guide. Last Modified: Thursday, November 30, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide VMware NSX Last Modified: Thursday, November 30, 2017 Event Source Product Information: Vendor: VMware Event Source: VMware NSX Version: 6.x Note:
RSA NetWitness Logs Event Source Log Configuration Guide VMware NSX Last Modified: Thursday, November 30, 2017 Event Source Product Information: Vendor: VMware Event Source: VMware NSX Version: 6.x Note:
RSA NetWitness Logs. Trend Micro OfficeScan and Control Manager. Event Source Log Configuration Guide. Last Modified: Thursday, November 30, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Trend Micro OfficeScan and Control Manager Last Modified: Thursday, November 30, 2017 Event Source Product Information: Vendor: Trend Micro Event
RSA NetWitness Logs Event Source Log Configuration Guide Trend Micro OfficeScan and Control Manager Last Modified: Thursday, November 30, 2017 Event Source Product Information: Vendor: Trend Micro Event
RSA NetWitness Logs. EMC Symmetrix Solutions Enabler. Event Source Log Configuration Guide. Last Modified: Friday, April 21, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide EMC Symmetrix Solutions Enabler Last Modified: Friday, April 21, 2017 Event Source Product Information: Vendor: EMC Event Source: Symmetrix Solutions
RSA NetWitness Logs Event Source Log Configuration Guide EMC Symmetrix Solutions Enabler Last Modified: Friday, April 21, 2017 Event Source Product Information: Vendor: EMC Event Source: Symmetrix Solutions
RSA NetWitness Platform
 RSA NetWitness Platform Event Source Log Configuration Guide Cisco Sourcefire Defense Center (formerly Sourcefire Defense Center) Last Modified: Monday, November 5, 2018 Event Source Product Information:
RSA NetWitness Platform Event Source Log Configuration Guide Cisco Sourcefire Defense Center (formerly Sourcefire Defense Center) Last Modified: Monday, November 5, 2018 Event Source Product Information:
RSA NetWitness Logs. Microsoft Windows. Event Source Log Configuration Guide. Last Modified: Thursday, October 5, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Microsoft Windows Last Modified: Thursday, October 5, 2017 Event Source Product Information: Vendor: Microsoft Event Source: Windows Versions: SNARE
RSA NetWitness Logs Event Source Log Configuration Guide Microsoft Windows Last Modified: Thursday, October 5, 2017 Event Source Product Information: Vendor: Microsoft Event Source: Windows Versions: SNARE
RSA NetWitness Logs. Citrix XenApp. Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide Citrix XenApp Last Modified: Thursday, October 5, 2017 Event Source Product Information: Vendor: Citrix Event Source: XenApp Versions: 5 (for Windows
RSA NetWitness Logs Event Source Log Configuration Guide Citrix XenApp Last Modified: Thursday, October 5, 2017 Event Source Product Information: Vendor: Citrix Event Source: XenApp Versions: 5 (for Windows
RSA NetWitness Logs. IBM AIX Last Modified: Thursday, November 2, Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide IBM AIX Last Modified: Thursday, November 2, 2017 Event Source Product Information: Vendor: IBM Event Source: AIX Versions: 5L (Security and Authentication
RSA NetWitness Logs Event Source Log Configuration Guide IBM AIX Last Modified: Thursday, November 2, 2017 Event Source Product Information: Vendor: IBM Event Source: AIX Versions: 5L (Security and Authentication
RSA NetWitness Logs. Apache HTTP Server. Event Source Log Configuration Guide. Last Modified: Friday, November 3, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Apache HTTP Server Last Modified: Friday, November 3, 2017 Event Source Product Information: Vendor: Apache Event Source: HTTP Server Versions:
RSA NetWitness Logs Event Source Log Configuration Guide Apache HTTP Server Last Modified: Friday, November 3, 2017 Event Source Product Information: Vendor: Apache Event Source: HTTP Server Versions:
RSA NetWitness Logs. Microsoft Network Access Protection. Event Source Log Configuration Guide. Last Modified: Thursday, May 18, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Microsoft Network Access Protection Last Modified: Thursday, May 18, 2017 Event Source Product Information: Vendor: Microsoft Event Source: Network
RSA NetWitness Logs Event Source Log Configuration Guide Microsoft Network Access Protection Last Modified: Thursday, May 18, 2017 Event Source Product Information: Vendor: Microsoft Event Source: Network
RSA NetWitness Logs. VMware vcenter Server. Event Source Log Configuration Guide. Last Modified: Thursday, November 30, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide VMware vcenter Server Last Modified: Thursday, November 30, 2017 Event Source Product Information: Vendor: VMware Event Source: VirtualCenter Server,
RSA NetWitness Logs Event Source Log Configuration Guide VMware vcenter Server Last Modified: Thursday, November 30, 2017 Event Source Product Information: Vendor: VMware Event Source: VirtualCenter Server,
RSA NetWitness Logs. Apache Tomcat Server. Event Source Log Configuration Guide. Last Modified: Friday, November 3, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Apache Tomcat Server Last Modified: Friday, November 3, 2017 Event Source Product Information: Vendor: Apache Event Source: Tomcat Server Versions:
RSA NetWitness Logs Event Source Log Configuration Guide Apache Tomcat Server Last Modified: Friday, November 3, 2017 Event Source Product Information: Vendor: Apache Event Source: Tomcat Server Versions:
RSA NetWitness Logs. ManageEngine NetFlow Analyzer. Event Source Log Configuration Guide. Last Modified: Monday, March 06, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide ManageEngine NetFlow Analyzer Last Modified: Monday, March 06, 2017 Event Source Product Information: Vendor: ManageEngine Event Source: NetFlow
RSA NetWitness Logs Event Source Log Configuration Guide ManageEngine NetFlow Analyzer Last Modified: Monday, March 06, 2017 Event Source Product Information: Vendor: ManageEngine Event Source: NetFlow
RSA NetWitness Logs. VMware ESX/ESXi. Event Source Log Configuration Guide. Last Modified: Tuesday, November 7, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide VMware ESX/ESXi Last Modified: Tuesday, November 7, 2017 Event Source Product Information: Vendor: VMware Event Source: ESX, ESXi, Embedded ESXi
RSA NetWitness Logs Event Source Log Configuration Guide VMware ESX/ESXi Last Modified: Tuesday, November 7, 2017 Event Source Product Information: Vendor: VMware Event Source: ESX, ESXi, Embedded ESXi
RSA NetWitness Logs. GlobalSCAPE Enhanced File Transfer (EFT) Server. Event Source Log Configuration Guide. Last Modified: Thursday, May 25, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide GlobalSCAPE Enhanced File Transfer (EFT) Server Last Modified: Thursday, May 25, 2017 Event Source Product Information: Vendor: GlobalSCAPE Event
RSA NetWitness Logs Event Source Log Configuration Guide GlobalSCAPE Enhanced File Transfer (EFT) Server Last Modified: Thursday, May 25, 2017 Event Source Product Information: Vendor: GlobalSCAPE Event
RSA NetWitness Logs. Linux. Event Source Log Configuration Guide. Last Modified: Thursday, October 12, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Linux Last Modified: Thursday, October 12, 2017 Event Source Product Information: Vendors: Red Hat Enterprise, Debian, Novell Event Source: Linux
RSA NetWitness Logs Event Source Log Configuration Guide Linux Last Modified: Thursday, October 12, 2017 Event Source Product Information: Vendors: Red Hat Enterprise, Debian, Novell Event Source: Linux
RSA NetWitness Logs. McAfee Web Gateway. Event Source Log Configuration Guide. Last Modified: Wednesday, October 11, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide McAfee Web Gateway Last Modified: Wednesday, October 11, 2017 Event Source Product Information: Vendor: McAfee Event Source: Web Gateway Versions:
RSA NetWitness Logs Event Source Log Configuration Guide McAfee Web Gateway Last Modified: Wednesday, October 11, 2017 Event Source Product Information: Vendor: McAfee Event Source: Web Gateway Versions:
RSA NetWitness Logs. Citrix XenMobile EMM Suite Last Modified: Wednesday, January 25, Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide Citrix XenMobile EMM Suite Last Modified: Wednesday, January 25, 2017 Event Source Product Information: Vendor: Citrix Event Source: Xenmobile Server
RSA NetWitness Logs Event Source Log Configuration Guide Citrix XenMobile EMM Suite Last Modified: Wednesday, January 25, 2017 Event Source Product Information: Vendor: Citrix Event Source: Xenmobile Server
RSA NetWitness Logs. Oracle Directory Server. Event Source Log Configuration Guide. Last Modified: Thursday, June 29, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Oracle Directory Server Last Modified: Thursday, June 29, 2017 Event Source Product Information: Vendor: Oracle Event Source: Oracle Directory Server
RSA NetWitness Logs Event Source Log Configuration Guide Oracle Directory Server Last Modified: Thursday, June 29, 2017 Event Source Product Information: Vendor: Oracle Event Source: Oracle Directory Server
RSA NetWitness Logs. MySQL Enterprise. Event Source Log Configuration Guide. Last Modified: Wednesday, November 15, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide MySQL Enterprise Last Modified: Wednesday, November 15, 2017 Event Source Product Information: Vendor: MySQL Event Source: MySQL Enterprise Versions:
RSA NetWitness Logs Event Source Log Configuration Guide MySQL Enterprise Last Modified: Wednesday, November 15, 2017 Event Source Product Information: Vendor: MySQL Event Source: MySQL Enterprise Versions:
RSA NetWitness Logs. EMC Ionix Unified Infrastructure Manager. Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide EMC Ionix Unified Infrastructure Manager Last Modified: Monday, March 06, 2017 Event Source Product Information: Vendor: EMC Event Source: EMC Ionix
RSA NetWitness Logs Event Source Log Configuration Guide EMC Ionix Unified Infrastructure Manager Last Modified: Monday, March 06, 2017 Event Source Product Information: Vendor: EMC Event Source: EMC Ionix
RSA NetWitness Logs. Symantec Critical Systems Protection. Event Source Log Configuration Guide
 RSA NetWitness Logs Symantec Critical Systems Protection Last Modified: Monday, July 24, 2017 Event Source Product Information: Vendor: Symantec Event Source: Critical Systems Protection, Data Center Security
RSA NetWitness Logs Symantec Critical Systems Protection Last Modified: Monday, July 24, 2017 Event Source Product Information: Vendor: Symantec Event Source: Critical Systems Protection, Data Center Security
RSA NetWitness Logs. IBM Tivoli Identity Manager. Event Source Log Configuration Guide. Last Modified: Monday, March 06, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide IBM Tivoli Identity Manager Last Modified: Monday, March 06, 2017 Event Source Product Information: Vendor: IBM Event Source: Tivoli Identity Manager
RSA NetWitness Logs Event Source Log Configuration Guide IBM Tivoli Identity Manager Last Modified: Monday, March 06, 2017 Event Source Product Information: Vendor: IBM Event Source: Tivoli Identity Manager
RSA NetWitness Logs. Cisco IronPort Web Security Appliance (WSA) Event Source Log Configuration Guide. Last Modified: Tuesday, January 9, 2018
 RSA NetWitness Logs Event Source Log Configuration Guide Cisco IronPort Web Security Appliance (WSA) Last Modified: Tuesday, January 9, 2018 Event Source Product Information: Vendor: Cisco Event Source:
RSA NetWitness Logs Event Source Log Configuration Guide Cisco IronPort Web Security Appliance (WSA) Last Modified: Tuesday, January 9, 2018 Event Source Product Information: Vendor: Cisco Event Source:
RSA NetWitness Logs. IBM ISS SiteProtector. Event Source Log Configuration Guide. Last Modified: Monday, May 22, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide IBM ISS SiteProtector Last Modified: Monday, May 22, 2017 Event Source Product Information: Vendor: IBM Event Source: Proventia Appliance, SiteProtector,
RSA NetWitness Logs Event Source Log Configuration Guide IBM ISS SiteProtector Last Modified: Monday, May 22, 2017 Event Source Product Information: Vendor: IBM Event Source: Proventia Appliance, SiteProtector,
RSA NetWitness Logs. Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide EMC VNX (formerly CLARiiON) Last Modified: Friday, May 12, 2017 Event Source Product Information: Vendor: EMC Event Source: VNX / CLARiiON Platforms/Versions:
RSA NetWitness Logs Event Source Log Configuration Guide EMC VNX (formerly CLARiiON) Last Modified: Friday, May 12, 2017 Event Source Product Information: Vendor: EMC Event Source: VNX / CLARiiON Platforms/Versions:
RSA NetWitness Logs. Radiator Radius Server. Event Source Log Configuration Guide. Last Modified: Thursday, November 2, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Radiator Radius Server Last Modified: Thursday, November 2, 2017 Event Source Product Information: Vendor: Radiator Event Source: Radius Server
RSA NetWitness Logs Event Source Log Configuration Guide Radiator Radius Server Last Modified: Thursday, November 2, 2017 Event Source Product Information: Vendor: Radiator Event Source: Radius Server
RSA NetWitness Logs. Tenable Nessus. Event Source Log Configuration Guide. Last Modified: Wednesday, August 09, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Tenable Nessus Last Modified: Wednesday, August 09, 2017 Event Source Product Information: Vendor: Tenable Event Source: Tenable Nessus Versions:
RSA NetWitness Logs Event Source Log Configuration Guide Tenable Nessus Last Modified: Wednesday, August 09, 2017 Event Source Product Information: Vendor: Tenable Event Source: Tenable Nessus Versions:
RSA NetWitness Logs. McAfee Endpoint Encryption. Event Source Log Configuration Guide. Last Modified: Friday, June 02, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide McAfee Endpoint Encryption Last Modified: Friday, June 02, 2017 Event Source Product Information: Vendor: McAfee Event Source: Endpoint Encryption
RSA NetWitness Logs Event Source Log Configuration Guide McAfee Endpoint Encryption Last Modified: Friday, June 02, 2017 Event Source Product Information: Vendor: McAfee Event Source: Endpoint Encryption
RSA NetWitness Logs. IBM Domino. Event Source Log Configuration Guide. Last Modified: Thursday, October 19, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide IBM Domino Last Modified: Thursday, October 19, 2017 Event Source Product Information: Vendor: IBM (Lotus) Event Source: Lotus Domino Versions:
RSA NetWitness Logs Event Source Log Configuration Guide IBM Domino Last Modified: Thursday, October 19, 2017 Event Source Product Information: Vendor: IBM (Lotus) Event Source: Lotus Domino Versions:
RSA NetWitness Platform
 RSA NetWitness Platform RSA SecurID Access Last Modified: Tuesday, January 29, 2019 Event Source Product Information: Vendor: RSA, The Security Division of Dell EMC Event Sources: Authentication Manager,
RSA NetWitness Platform RSA SecurID Access Last Modified: Tuesday, January 29, 2019 Event Source Product Information: Vendor: RSA, The Security Division of Dell EMC Event Sources: Authentication Manager,
RSA NetWitness Platform
 RSA NetWitness Platform Event Source Log Configuration Guide Check Point Security Suite, IPS-1 Last Modified: Wednesday, May 9, 2018 Event Source Product Information: Vendor: Check Point Event Source:
RSA NetWitness Platform Event Source Log Configuration Guide Check Point Security Suite, IPS-1 Last Modified: Wednesday, May 9, 2018 Event Source Product Information: Vendor: Check Point Event Source:
RSA NetWitness Logs. Microsoft Forefront Endpoint Protection. Event Source Log Configuration Guide. Last Modified: Monday, November 13, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Microsoft Forefront Endpoint Protection Last Modified: Monday, November 13, 2017 Event Source Product Information: Vendor: Microsoft Event Source:
RSA NetWitness Logs Event Source Log Configuration Guide Microsoft Forefront Endpoint Protection Last Modified: Monday, November 13, 2017 Event Source Product Information: Vendor: Microsoft Event Source:
RSA NetWitness Logs. Sophos Enterprise Console Last Modified: Friday, July 21, Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide Sophos Enterprise Console Last Modified: Friday, July 21, 2017 Event Source Product Information: Vendor: Sophos Event Source: Enterprise Console,
RSA NetWitness Logs Event Source Log Configuration Guide Sophos Enterprise Console Last Modified: Friday, July 21, 2017 Event Source Product Information: Vendor: Sophos Event Source: Enterprise Console,
RSA NetWitness Logs. Microsoft SharePoint Server. Event Source Log Configuration Guide. Last Modified: Friday, June 02, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Microsoft SharePoint Server Last Modified: Friday, June 02, 2017 Event Source Product Information: Vendor: Microsoft Event Source: SharePoint Server
RSA NetWitness Logs Event Source Log Configuration Guide Microsoft SharePoint Server Last Modified: Friday, June 02, 2017 Event Source Product Information: Vendor: Microsoft Event Source: SharePoint Server
RSA NetWitness Logs. Microsoft System Center Configuration Manager. Event Source Log Configuration Guide. Last Modified: Thursday, June 08, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Microsoft System Center Configuration Manager Last Modified: Thursday, June 08, 2017 Event Source Product Information: Vendor: Microsoft Event Source:
RSA NetWitness Logs Event Source Log Configuration Guide Microsoft System Center Configuration Manager Last Modified: Thursday, June 08, 2017 Event Source Product Information: Vendor: Microsoft Event Source:
RSA NetWitness Logs. Microsoft Network Policy Server. Event Source Log Configuration Guide. Last Modified: Thursday, June 08, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Microsoft Network Policy Server Last Modified: Thursday, June 08, 2017 Event Source Product Information: Vendor: Microsoft Event Source: Network
RSA NetWitness Logs Event Source Log Configuration Guide Microsoft Network Policy Server Last Modified: Thursday, June 08, 2017 Event Source Product Information: Vendor: Microsoft Event Source: Network
RSA NetWitness Logs SQUID. Event Source Log Configuration Guide. Last Modified: Thursday, October 12, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide SQUID Last Modified: Thursday, October 12, 2017 Event Source Product Information: Vendor: Open source Event Source: Squid Versions: 2.5.9, 2.7,
RSA NetWitness Logs Event Source Log Configuration Guide SQUID Last Modified: Thursday, October 12, 2017 Event Source Product Information: Vendor: Open source Event Source: Squid Versions: 2.5.9, 2.7,
RSA NetWitness Logs. Oracle iplanet Web Server. Event Source Log Configuration Guide. Last Modified: Tuesday, May 09, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Oracle iplanet Web Server Last Modified: Tuesday, May 09, 2017 Event Source Product Information: Vendor: Oracle Event Source: iplanet Web Server
RSA NetWitness Logs Event Source Log Configuration Guide Oracle iplanet Web Server Last Modified: Tuesday, May 09, 2017 Event Source Product Information: Vendor: Oracle Event Source: iplanet Web Server
RSA NetWitness Logs. McAfee Network Security Platform. Event Source Log Configuration Guide. Last Modified: Thursday, March 8, 2018
 RSA NetWitness Logs Event Source Log Configuration Guide McAfee Network Security Platform Last Modified: Thursday, March 8, 2018 Event Source Product Information: Vendor: McAfee Event Source: Network Security
RSA NetWitness Logs Event Source Log Configuration Guide McAfee Network Security Platform Last Modified: Thursday, March 8, 2018 Event Source Product Information: Vendor: McAfee Event Source: Network Security
RSA NetWitness Logs. Microsoft Exchange Server. Event Source Log Configuration Guide. Last Modified: Thursday, November 2, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Microsoft Exchange Server Last Modified: Thursday, November 2, 2017 Event Source Product Information: Vendor: Microsoft Event Source: Exchange Server
RSA NetWitness Logs Event Source Log Configuration Guide Microsoft Exchange Server Last Modified: Thursday, November 2, 2017 Event Source Product Information: Vendor: Microsoft Event Source: Exchange Server
RSA NetWitness Logs IBM DB2. Event Source Log Configuration Guide. Last Modified: Friday, November 17, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide IBM DB2 Last Modified: Friday, November 17, 2017 Event Source Product Information: Vendor: IBM Event Source: DB2 Universal Database Versions: 7,8,
RSA NetWitness Logs Event Source Log Configuration Guide IBM DB2 Last Modified: Friday, November 17, 2017 Event Source Product Information: Vendor: IBM Event Source: DB2 Universal Database Versions: 7,8,
Deploying the BIG-IP LTM with IBM QRadar Logging
 Deployment Guide Deploying the BIG-IP LTM with IBM QRadar Logging Welcome to the F5 deployment guide for IBM Security QRadar SIEM and Log Manager. This guide shows administrators how to configure the BIG-IP
Deployment Guide Deploying the BIG-IP LTM with IBM QRadar Logging Welcome to the F5 deployment guide for IBM Security QRadar SIEM and Log Manager. This guide shows administrators how to configure the BIG-IP
RSA NetWitness Logs. Sybase Adaptive Server Enterprise. Event Source Log Configuration Guide. Last Modified: Wednesday, November 29, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Sybase Adaptive Server Enterprise Last Modified: Wednesday, November 29, 2017 Event Source Product Information: Vendor: Sybase Event Source: Sybase
RSA NetWitness Logs Event Source Log Configuration Guide Sybase Adaptive Server Enterprise Last Modified: Wednesday, November 29, 2017 Event Source Product Information: Vendor: Sybase Event Source: Sybase
Trademarks. License Agreement. Third-Party Licenses. Note on Encryption Technologies. Distribution
 Copyright 2017 EMC Corporation. All Rights Reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks or trademarks of EMC Corporation in the United States and/or other countries.
Copyright 2017 EMC Corporation. All Rights Reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks or trademarks of EMC Corporation in the United States and/or other countries.
BIG-IP System: Implementing a Passive Monitoring Configuration. Version 13.0
 BIG-IP System: Implementing a Passive Monitoring Configuration Version 13.0 Table of Contents Table of Contents Configuring the BIG-IP System for Passive Monitoring...5 Overview: Configuring the BIG-IP
BIG-IP System: Implementing a Passive Monitoring Configuration Version 13.0 Table of Contents Table of Contents Configuring the BIG-IP System for Passive Monitoring...5 Overview: Configuring the BIG-IP
BIG-IP Analytics: Implementations. Version 13.1
 BIG-IP Analytics: Implementations Version 13.1 Table of Contents Table of Contents Setting Up Application Statistics Collection...5 What is Analytics?...5 About HTTP Analytics profiles... 5 Overview:
BIG-IP Analytics: Implementations Version 13.1 Table of Contents Table of Contents Setting Up Application Statistics Collection...5 What is Analytics?...5 About HTTP Analytics profiles... 5 Overview:
RSA NetWitness Logs. Salesforce. Event Source Log Configuration Guide. Last Modified: Wednesday, February 14, 2018
 RSA NetWitness Logs Event Source Log Configuration Guide Salesforce Last Modified: Wednesday, February 14, 2018 Event Source Product Information: Vendor: Salesforce Event Source: CRM Versions: API v1.0
RSA NetWitness Logs Event Source Log Configuration Guide Salesforce Last Modified: Wednesday, February 14, 2018 Event Source Product Information: Vendor: Salesforce Event Source: CRM Versions: API v1.0
ForeScout CounterACT. Configuration Guide. Version 1.2
 ForeScout CounterACT Core Extensions Module: NetFlow Plugin Version 1.2 Table of Contents About NetFlow Integration... 3 How it Works... 3 Supported NetFlow Versions... 3 What to Do... 3 Requirements...
ForeScout CounterACT Core Extensions Module: NetFlow Plugin Version 1.2 Table of Contents About NetFlow Integration... 3 How it Works... 3 Supported NetFlow Versions... 3 What to Do... 3 Requirements...
BIG-IP Network Firewall: Policies and Implementations. Version 13.0
 BIG-IP Network Firewall: Policies and Implementations Version 13.0 Table of Contents Table of Contents About the Network Firewall...9 What is the BIG-IP Network Firewall?...9 About firewall modes... 9
BIG-IP Network Firewall: Policies and Implementations Version 13.0 Table of Contents Table of Contents About the Network Firewall...9 What is the BIG-IP Network Firewall?...9 About firewall modes... 9
RSA NetWitness Logs. Microsoft Azure NSG (Flow Logs) Event Source Log Configuration Guide. Last Modified: Monday, February 26, 2018
 RSA NetWitness Logs Event Source Log Configuration Guide Microsoft Azure NSG (Flow Logs) Last Modified: Monday, February 26, 2018 Event Source Product Information: Vendor: Microsoft Event Source: NSG (Flow
RSA NetWitness Logs Event Source Log Configuration Guide Microsoft Azure NSG (Flow Logs) Last Modified: Monday, February 26, 2018 Event Source Product Information: Vendor: Microsoft Event Source: NSG (Flow
Dell Storage Center Update Utility Administrator s Guide
 Dell Storage Center Update Utility Administrator s Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION indicates
Dell Storage Center Update Utility Administrator s Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION indicates
RSA NetWitness Platform
 RSA NetWitness Platform AWS CloudTrail Last Modified: Tuesday, May 1, 2018 Event Source Product Information: Vendor: Amazon Web Services Event Source: AWS CloudTrail Versions: all RSA Product Information:
RSA NetWitness Platform AWS CloudTrail Last Modified: Tuesday, May 1, 2018 Event Source Product Information: Vendor: Amazon Web Services Event Source: AWS CloudTrail Versions: all RSA Product Information:
UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0)
 UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0) Installation and Configuration Guide: UDP Director VE v6.9.0 2016 Cisco Systems, Inc. All rights reserved.
UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0) Installation and Configuration Guide: UDP Director VE v6.9.0 2016 Cisco Systems, Inc. All rights reserved.
UDP Director Virtual Edition
 UDP Director Virtual Edition (also known as FlowReplicator VE) Installation and Configuration Guide (for StealthWatch System v6.7.0) Installation and Configuration Guide: UDP Director VE v6.7.0 2015 Lancope,
UDP Director Virtual Edition (also known as FlowReplicator VE) Installation and Configuration Guide (for StealthWatch System v6.7.0) Installation and Configuration Guide: UDP Director VE v6.7.0 2015 Lancope,
<Partner Name> <Partner Product> RSA Ready Implementation Guide for
 RSA Ready Implementation Guide for Ixia Net Tool Optimizer 5288 FAL, RSA Partner Engineering Last Modified: 3/17/2016 Solution Summary The 5288 Series delivers performance
RSA Ready Implementation Guide for Ixia Net Tool Optimizer 5288 FAL, RSA Partner Engineering Last Modified: 3/17/2016 Solution Summary The 5288 Series delivers performance
Cisco Service Control Service Security: Outgoing Spam Mitigation Solution Guide, Release 4.1.x
 CISCO SERVICE CONTROL SOLUTION GUIDE Cisco Service Control Service Security: Outgoing Spam Mitigation Solution Guide, Release 4.1.x 1 Introduction and Scope 2 Functionality Overview 3 Mass-Mailing-Based
CISCO SERVICE CONTROL SOLUTION GUIDE Cisco Service Control Service Security: Outgoing Spam Mitigation Solution Guide, Release 4.1.x 1 Introduction and Scope 2 Functionality Overview 3 Mass-Mailing-Based
H3C Firewall and UTM Devices Log Management with IMC Firewall Manager Configuration Examples (Comware V5)
 H3C Firewall and UTM Devices Log Management with IMC Firewall Manager Configuration Examples (Comware V5) Copyright 2015 Hangzhou H3C Technologies Co., Ltd. All rights reserved. No part of this manual
H3C Firewall and UTM Devices Log Management with IMC Firewall Manager Configuration Examples (Comware V5) Copyright 2015 Hangzhou H3C Technologies Co., Ltd. All rights reserved. No part of this manual
RSA NetWitness Platform
 RSA NetWitness Platform Event Source Log Configuration Guide Microsoft Office 365 Last Modified: Thursday, June 7, 2018 Event Source Product Information: Vendor: Microsoft Event Source: Office 365 Versions:
RSA NetWitness Platform Event Source Log Configuration Guide Microsoft Office 365 Last Modified: Thursday, June 7, 2018 Event Source Product Information: Vendor: Microsoft Event Source: Office 365 Versions:
Cisco Stealthwatch. Proxy Log Configuration Guide 7.0
 Cisco Stealthwatch Proxy Log Configuration Guide 7.0 Table of Contents Introduction 3 Overview 3 Important Configuration Guidelines 3 Contacting Support 3 Configuring the Blue Coat Proxy Logs 5 Creating
Cisco Stealthwatch Proxy Log Configuration Guide 7.0 Table of Contents Introduction 3 Overview 3 Important Configuration Guidelines 3 Contacting Support 3 Configuring the Blue Coat Proxy Logs 5 Creating
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
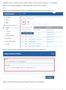 Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
BIG-IP Access Policy Manager : Application Access. Version 13.0
 BIG-IP Access Policy Manager : Application Access Version 13.0 Table of Contents Table of Contents Configuring App Tunnel Access... 5 What are app tunnels?...5 About ACLs to control access from app tunnels...
BIG-IP Access Policy Manager : Application Access Version 13.0 Table of Contents Table of Contents Configuring App Tunnel Access... 5 What are app tunnels?...5 About ACLs to control access from app tunnels...
SANmelody TRIAL Quick Start Guide
 Page 1 SANmelody TRIAL Quick Start Guide From Installation to Presenting Virtual Storage Download the trial software at: SANmelody Trial Software SANmelody TRIAL Quick Start Guide Change Summary August,
Page 1 SANmelody TRIAL Quick Start Guide From Installation to Presenting Virtual Storage Download the trial software at: SANmelody Trial Software SANmelody TRIAL Quick Start Guide Change Summary August,
Using ifix EGD I/O Driver and OPC Server v7.20 with Microsoft Windows XP Service Pack 2 WHITE PAPER
 Using ifix EGD I/O Driver and OPC Server v7.20 with Microsoft Windows XP Service Pack 2 WHITE PAPER Last Modified: September 16, 2004 Table of Contents Introduction... 1 Network Protection... 1 Windows
Using ifix EGD I/O Driver and OPC Server v7.20 with Microsoft Windows XP Service Pack 2 WHITE PAPER Last Modified: September 16, 2004 Table of Contents Introduction... 1 Network Protection... 1 Windows
ASA 8.X and later: Add or Modify an Access List through the ASDM GUI Configuration Example
 ASA 8.X and later: Add or Modify an Access List through the ASDM GUI Configuration Example Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
ASA 8.X and later: Add or Modify an Access List through the ASDM GUI Configuration Example Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
Intel Unite. Intel Unite Firewall Help Guide
 Intel Unite Intel Unite Firewall Help Guide September 2015 Legal Disclaimers & Copyrights All information provided here is subject to change without notice. Contact your Intel representative to obtain
Intel Unite Intel Unite Firewall Help Guide September 2015 Legal Disclaimers & Copyrights All information provided here is subject to change without notice. Contact your Intel representative to obtain
Deploying the BIG-IP System with Oracle Hyperion Applications
 Deployment Guide DOCUMENT VERSION.0 What s inside: Prerequisites and configuration notes Configuration example Preparation Worksheet Configuring the BIG-IP system for Hyperion Planning Workspace 5 Configuring
Deployment Guide DOCUMENT VERSION.0 What s inside: Prerequisites and configuration notes Configuration example Preparation Worksheet Configuring the BIG-IP system for Hyperion Planning Workspace 5 Configuring
NAT Support for Multiple Pools Using Route Maps
 NAT Support for Multiple Pools Using Route Maps Document ID: 13739 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Access List Approach Host 1 to Host
NAT Support for Multiple Pools Using Route Maps Document ID: 13739 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Access List Approach Host 1 to Host
Configuring Preferences
 Configuring Preferences CHAPTERS 1. Overview 2. IP Group Configuration 3. Time Range Configuration 4. VPN IP Pool Configuration 5. Service Type Configuration This guide applies to: TL-R470T+ v6 or above,
Configuring Preferences CHAPTERS 1. Overview 2. IP Group Configuration 3. Time Range Configuration 4. VPN IP Pool Configuration 5. Service Type Configuration This guide applies to: TL-R470T+ v6 or above,
IPv4 ACLs, identified by ACL numbers, fall into four categories, as shown in Table 1. Table 1 IPv4 ACL categories
 Table of Contents ACL Configuration 1 ACL Overview 1 IPv4 ACL Classification 1 IPv4 ACL Rule Order 1 Rule Numbering Step with IPv4 ACLs 3 Effective Time Period of an IPv4 ACL 3 IP Fragments Filtering with
Table of Contents ACL Configuration 1 ACL Overview 1 IPv4 ACL Classification 1 IPv4 ACL Rule Order 1 Rule Numbering Step with IPv4 ACLs 3 Effective Time Period of an IPv4 ACL 3 IP Fragments Filtering with
CounterACT NetFlow Plugin
 Version 1.1.0 and Above Table of Contents About NetFlow Integration... 3 How it Works... 3 Supported NetFlow Versions... 3 What to Do... 3 Requirements... 4 CounterACT Requirements... 4 Networking Requirements...
Version 1.1.0 and Above Table of Contents About NetFlow Integration... 3 How it Works... 3 Supported NetFlow Versions... 3 What to Do... 3 Requirements... 4 CounterACT Requirements... 4 Networking Requirements...
