Management. Software Quality. Dr. Stefan Wagner Technische Universität München. Garching 28 May 2010
|
|
|
- Theodore McCarthy
- 5 years ago
- Views:
Transcription
1 Technische Universität München Software Quality Management Dr. Stefan Wagner Technische Universität München Garching 28 May 2010 Some of these slides were adapted from the tutorial "Clone Detection in Practice" from F. Deissenbock, B. Hummel, and E. Jürgens given at ICSE'10. 1
2 Last QOT: On which quality attributes do reviews have the most direct influence? "Usability" "Readability" "Performance" Reviews might have an influence on usability, depending on what is actually reviewed. Reviews of GUI mock-ups, for example, might have a huge influence. 2 Readability is highly influenced in the case of code reviews. Performance problems are actually very hard to detect with reviews. New QOT: "Why is cloning a problem?"
3 Review alkthrough Inspection Review of last week's lecture 3
4 Metrics and Basics Product Quality Measurement Process Quality Quality Management Certification We are still in the part "Product Quality". 4
5 Code analysis Quality evaluation 5 This lecture covers code analysis, mostly bug pattern tools and clone detection, as well as an approach for quality evaluation.
6 Code analysis 6
7 Quality Assurance (QA) Constructive QA Process Standards Coding Guidelines Analytical QA Analysing Methods Testing Methods Verifying Methods Metrics Dynamic Test Formal Verification Anomaly Analysis Review/Inspection Model Checking Graphs and Tables Autom. Static Analysis With code analysis, I mainly refer to automatic static analysis. Dynamic analyses are not explicitly covered in the following. 7
8 Abstract Interpretation Control Flow and Data Flow Analysis Bug Pattern Style Checker (Coding Guidelines) Analysis of software by software But no execution of the analysed software Wide spectrum Efficient, but many false positives Examples Checkstyle FindBugs PMD Klockwork Coverity 8
9 Bug Pattern Tools On average 1/4 of faults during development 7 person-hours for configuration <0.5 person-hours per fault Empirical studies with Cirquent and o2 Germany Subset of defect types of reviews Different defects as tests Problem: High level of false positives, tends to improve 9
10 Example: FindBugs String input = textfield.content; if (input == expectedstring) {... int somemethod(int y) {...} if (a) {somemethod(b)}... A well-known and very usable example of Java analysis tools is FindBugs from the University of Maryland. The two code snippets are examples of bug patterns that FindBugs can detect: String comparison with == and missing usage of return value 10
11 Code cloning Class A Class B Code clones are parts of a source code that were copied and pasted. In principle, it is a normal, exploarative approach to look for code that does something similar as what you want to implement. You should, however, refactor common code to a method or class that is used in both places. If this refactoring step is omitted, we have clones in the code. 11
12 Code clone example Clone Sequence of normalized statements At least one other occurrence in the code 12 Exact clone Edit distance between clones = 0 Inconsistent clone Edit distance between clones > 0 & below given threshold (Inconsistent) Clone Group Set of clones at different positions (with at least 1 inconsistent clone) Semantic relationship between clones
13 Unnecessary size increase Class A Class C Class D Class E Class F Class G Class H The main and most direct problem of code clones is the unnecessary size increase. With many clone groups, which consist of several clones, the code is significantly larger than it needs to be. This additional, unnecessary code needs to be read, comprehended, changed, and tested. 13
14 Example: Inconsistent clones Furthermore, clones can become inconsistent if one of the clones is changed but not the others. This can be intended if one clone has to conform to different requirements. If this was not intended, however, it might be a real defect in the system. We analysed this in more detail with systems from Munich Re, LV 1871, and TUM. 14
15 Class A Class B These are two clones of a clone group. 15
16 Class A Class B Inconsistent? Unconscious? Defect? One of these clones was changed. In the study we then asked the developers: Was the change done conscious of the clone? Does the inconsistency constitute a clone? 16
17 Class B Inconsistent: 52% Unconscious: 28% Defect: 50% 17 Of all clones we found in the analysed systems, 52% contained inconsistencies. Of these inconsistent clones, 28% were changed unconscious of the copies. Of the inconsistent clones that were changed unconscious of the copies, 50% were real defects.
18 Every second unconsciously inconsistent change constitutes a fault. Jürgens et al., ICSE'09,
19 Group work Group 1: How do the types of defects found with automatic static analysis compare to defects found by tests or reviews? Group II: When in the development process should automatic static analysis be applied (e.g., before or after which other methods, how often)? 10 minutes, cards Short presentation Static analysis finds largely different defects than tests, but many defects also found in a review. If there is a good tool that finds a specific type of defect it often finds it more thoroughly than a review. Static analysis is mostly suitable for finding readability problems. 19 Static analysis should be applied as often as possible, e.g., in the nightly build or better directly in the IDE of the developer. It is a good entry criteria for a code inspection to save the inspectors the time for noting defects that a tool could detect cheaper.
20 Clone detection: Processing steps Storage load visualise tokenise & normalise find duplicates extract clones First, the code is loaded from the storage system. Second, the code separated into tokens and these tokens are normalised, e.g., identifier names are removed. Third, in the normalised tokens, duplicates are detected. Fourth, the duplicates that constitute clones are extracted. Fifth, the extracted clones are suitably visualised. 20
21 Normalisation example String readfileutf8(file file) { FileInputStream in = new FileInputStream(file); byte[] buffer = new byte[file.length()]; in.read(buffer); in.close(); return new String(buffer, UTF-8 ); } String readfileutf16(file file) { FileInputStream in = new FileInputStream(file); byte[] buffer = new byte[file.length()]; id0 id1(id2 id3) { id0 id2 = new id0(id4); } id0[] id1 = new id0[id2.id3()]; id0.id1(id2); id0.id3(); return new id0(id1, lit0); id0 id1(id2 id3) { id0 id2 = new id0(id4); } id0[] id1 = new id0[id2.id3()]; id0.id1(id2); id0.id3(); return new id0(id1, lit0); in.read(buffer); in.close(); return new String(buffer, UTF-16 ); } This examples shows why normalisation is necessary. Here the method that reads a UTF-8 file was copied and changed so that it reads UTF-16 files. In essence, this still is a copy and if there is a change in readfileutf8, there is a high probability that readfileutf16 also has to be changed. Hence, identifiers and literals are normalised to "id" and "lit" so that the duplication finder is still able to find them. 21
22 Normalisation example String readfileutf8(file file) { FileInputStream in = new FileInputStream(file); byte[] buffer = new byte[file.length()]; in.read(buffer); in.close(); return new String(buffer, UTF-8 ); } String readfileutf16(file file) { FileInputStream in = new FileInputStream(file); byte[] buffer = new byte[file.length()]; in.read(buffer); in.close(); return new String(buffer, UTF-16 ); id0 id1(id2 id3) { id0 id2 = new id0(id4); } id0[] id1 = new id0[id2.id3()]; id0.id1(id2); id0.id3(); return new id0(id1, lit0); id0 id1(id2 id3) { id0 id2 = new id0(id4); } id0[] id1 = new id0[id2.id3()]; id0.id1(id2); id0.id3(); return new id0(id1, lit0); } Clones contain similar but not necessarily identical code 22
23 Measures for cloning Number of clone groups/clone instances Size of largest clone/cardinality of most frequent clone Cloned Statements Number of statements in the system being part of at least one clone Clone Coverage #Cloned Statements / #Statements Probability of a randomly chosen statement to be part of a clone Redundancy Free Source Statements (RFSS) Size of system after (hypothetical) perfect clone removal Different measures for cloning are interesting for different goals. The number of clone groups and instances shows how many refactorings would be necessary. The size of the largest clone or the cardinality of the most frequent clone show the hot spots. Clone coverage gives a feeling how big the problem is over the whole system. RFSS shows the actual size of the system. 23
24 Measures example class Test { int dox (int a, int b) { if (a > b) { return 2*a; } return 2*b; } int doy (int a, int b) { return a+b; } Statements: 11 Cloned Statements: 8 Clone Coverage: 8/11 70% RFSS: 7 } int doz (int c, int d) { if (c > d) { return 2*c; } return 2*d; } 24
25 Visualisation of clone detection results Compare View (~20 LOC) Tree Maps (> LOC) Seesoft View (~400 LOC) Trends over Time 25 Depending on the the purpose of the analysis and the size of the part I want to look at, different visualisations are appropriate.
26 Clone compare view 26 The clone compare view, here in Eclipse, shows the cloned parts of two classes next to each other. It allows a detailed inspection of the the clones.
27 Clone bars Displays cloning information in the IDE Helps when working with cloned code Clone bars are also shown in an IDE, but directly on the side of the code you work with. If you change existing code, this bar warns you that there are clones that you might have to change as well. 27
28 Tree map Visualisation of Structure Size Redundancy in a single picture The tree map is useful to get an overview of how cloning distributes over the whole system. The more red a square is, the higher the clone coverage in this class. 28
29 Apache Tomcat We use the source code of Apache Tomcat to show you tree map visualisation of cloning. 29
30 The top-level package in Tomcat is "org". 30
31 Below "org" there is the package "apache". 31
32 The "apache" package contains several further packages. 32
33 Which in turn contain further packages. 33
34 Which contain finally Java classes. 34
35 These Java classes are then overlayed with the degree of clone coverage they have. 35
36 Clones in models Deissenboeck et al., ICSE'08 36 Cloning is not only a problem in code. Also models contain copies. We analysed this at MAN Nutzfahrzeuge and their Simulink/Targetlink models. Simulink/TargetLink models with about 20,000 blocks in 71 files Identified: 139 clone classes after filtering Includes clones of library blocks 37% of relevant blocks are part of at least one clone group Most clones affect several files/transcend several hierarchies
37 Clones in requirements specifications Relative blow-up in percentage 129,6 60,6 Mean 13,5% 32,6 20,4 18,2 14,214,113,4 11,5 10,8 8,7 7 6,9 6,8 5,3 5 3, ,1 1 0,9 0,6 0,5 0,4 0,4 0 0 Jürgens et al., ICSE'10 Also requirements specifications are affected by cloning. The diagram shows results of a study we did with real world specifications. Each bar is the relative blow-up for a specification. The blow-up denotes how much larger the specification is than it would need to be without cloning. The maximum has a blow-up of 11,000 words! But there are specifications with no or almost no cloning. On average, an inspection of the requirements would need more than 2 additional person days because of cloning. 37
38 Cloning also in models and requirements specifications 38
39 Code analysis Quality evaluation 39
40 Quality evaluation 40
41 Group work What are useful measures for quality or specific quality attributes? 10 minutes Cards Short presentation The results of this group work will be reused in later lectures. 41
42 Example: Average maintenance effort 42 Quality evaluations will be discussed using the example of maintenance efforts. The average maintenance effort for the next year would be an interesting measure for maintainability. We use public data from the NASA system "CM1". Space craft instrument Developed in C To evaluate its quality, we use our existing maintainability model.
43 Bayesian nets P(C A,B) C P(A) P(B A) A B T = 0.6 F = 0.4 T F Low Med High Cause effect graphs Based on Bayesian inference Are therefore able to model uncertainty Node Probability Table (NPT) for each node N x M N states in the node M product of the cause node states 43
44 Quality model Maintenance Implementation Quality assurance Analysis Modification Testing Compr. Appropriateness of comments + Reading Regularity of implementation + Size of modules - This is the simplified model we use for the quality evaluation. It has a reduced activity tree that decomposes "maintenance" and the factors are simplified to just three. A realistic maintainability model contains more than hundred factors. 44
45 Transition to Bayesian net Maintenance Implementation Modification Quality assurance Testing Analysis Comprehension Appropriateness of comments Reading Size of modules Regularity of implementation The activity-based quality model can be directly transformed into a Bayesian net. The factors become nodes that influence the activities on which the have an impact. The activities than influence their higher-level activities until "maintenance" is reached. 45
46 Adding measures Maintenance Average change effort Implementation Analysis Quality assurance Modification Comprehension Testing Comment ratio Appropriateness of comments Regularity of implementation Reading Size of modules Average cyclomatic complexity Average module size The factors as well as the top-level activity need explicit measures. In the example, we only use automatically measureable measures, because these are available in the NASA data set. 46
47 This is the Bayesian net implemented in the tool AgenaRisk. The difficulty lies in defining suitable node probability tables for all nodes. With the final net, it is possible to set a desired average change effort and calculate the most probable explanation in comment ratio, average cyclomatic complexity, and average module size. Alternatively, we can set measured values for these and calculate the distribution of the average change effort. 47
48 Code analysis Quality evaluation 48
Software product quality control Dr. Stefan Wagner Dr. Florian Deißenböck Technische Universität München
 Tool-supported Software product quality control Dr. Stefan Wagner Dr. Florian Deißenböck Technische Universität München Google Developer Day Munich November 9, 2010 Continuous Quality Control Quality Model
Tool-supported Software product quality control Dr. Stefan Wagner Dr. Florian Deißenböck Technische Universität München Google Developer Day Munich November 9, 2010 Continuous Quality Control Quality Model
Three General Principles of QA. COMP 4004 Fall Notes Adapted from Dr. A. Williams
 Three General Principles of QA COMP 4004 Fall 2008 Notes Adapted from Dr. A. Williams Software Quality Assurance Lec2 1 Three General Principles of QA Know what you are doing. Know what you should be doing.
Three General Principles of QA COMP 4004 Fall 2008 Notes Adapted from Dr. A. Williams Software Quality Assurance Lec2 1 Three General Principles of QA Know what you are doing. Know what you should be doing.
Natural Language Processing Is No Free Lunch
 Natural Language Processing Is No Free Lunch STEFAN WAGNER UNIVERSITY OF STUTTGART, STUTTGART, GERMANY ntroduction o Impressive progress in NLP: OS with personal assistants like Siri or Cortan o Brief
Natural Language Processing Is No Free Lunch STEFAN WAGNER UNIVERSITY OF STUTTGART, STUTTGART, GERMANY ntroduction o Impressive progress in NLP: OS with personal assistants like Siri or Cortan o Brief
Software Quality Assurance. David Janzen
 Software Quality Assurance David Janzen What is quality? Crosby: Conformance to requirements Issues: who establishes requirements? implicit requirements Juran: Fitness for intended use Issues: Who defines
Software Quality Assurance David Janzen What is quality? Crosby: Conformance to requirements Issues: who establishes requirements? implicit requirements Juran: Fitness for intended use Issues: Who defines
Manuel Oriol, CHCRC-C, Software Testing ABB
 Manuel Oriol, CHCRC-C, 08.11.2017 Software Testing Slide 1 About me 1998 2004 2005 2008 2011 Slide 2 Introduction Why do we test? Did you have to deal with testing in the past? Slide 3 Ariane 5 http://www.youtube.com/watch?v=kyurqduyepi
Manuel Oriol, CHCRC-C, 08.11.2017 Software Testing Slide 1 About me 1998 2004 2005 2008 2011 Slide 2 Introduction Why do we test? Did you have to deal with testing in the past? Slide 3 Ariane 5 http://www.youtube.com/watch?v=kyurqduyepi
10. Software Testing Fundamental Concepts
 10. Software Testing Fundamental Concepts Department of Computer Science and Engineering Hanyang University ERICA Campus 1 st Semester 2016 Testing in Object-Oriented Point of View Error Correction Cost
10. Software Testing Fundamental Concepts Department of Computer Science and Engineering Hanyang University ERICA Campus 1 st Semester 2016 Testing in Object-Oriented Point of View Error Correction Cost
A Systematic Review of Bad Smells Metrics. Luiz Paulo Coelho Ferreira
 A Systematic Review of Bad Smells Metrics Luiz Paulo Coelho Ferreira Motivation One of the main goals in Software Engineering is to transform software development in a process predictable and controlled.
A Systematic Review of Bad Smells Metrics Luiz Paulo Coelho Ferreira Motivation One of the main goals in Software Engineering is to transform software development in a process predictable and controlled.
Program Partitioning - A Framework for Combining Static and Dynamic Analysis
 Program Partitioning - A Framework for Combining Static and Dynamic Analysis Pankaj Jalote, Vipindeep V, Taranbir Singh, Prateek Jain Department of Computer Science and Engineering Indian Institute of
Program Partitioning - A Framework for Combining Static and Dynamic Analysis Pankaj Jalote, Vipindeep V, Taranbir Singh, Prateek Jain Department of Computer Science and Engineering Indian Institute of
MONIKA HEINER.
 LESSON 1 testing, intro 1 / 25 SOFTWARE TESTING - STATE OF THE ART, METHODS, AND LIMITATIONS MONIKA HEINER monika.heiner@b-tu.de http://www.informatik.tu-cottbus.de PRELIMINARIES testing, intro 2 / 25
LESSON 1 testing, intro 1 / 25 SOFTWARE TESTING - STATE OF THE ART, METHODS, AND LIMITATIONS MONIKA HEINER monika.heiner@b-tu.de http://www.informatik.tu-cottbus.de PRELIMINARIES testing, intro 2 / 25
A Novel Ontology Metric Approach for Code Clone Detection Using FusionTechnique
 A Novel Ontology Metric Approach for Code Clone Detection Using FusionTechnique 1 Syed MohdFazalulHaque, 2 Dr. V Srikanth, 3 Dr. E. Sreenivasa Reddy 1 Maulana Azad National Urdu University, 2 Professor,
A Novel Ontology Metric Approach for Code Clone Detection Using FusionTechnique 1 Syed MohdFazalulHaque, 2 Dr. V Srikanth, 3 Dr. E. Sreenivasa Reddy 1 Maulana Azad National Urdu University, 2 Professor,
Large-Scale API Protocol Mining for Automated Bug Detection
 Large-Scale API Protocol Mining for Automated Bug Detection Michael Pradel Department of Computer Science ETH Zurich 1 Motivation LinkedList pinconnections =...; Iterator i = pinconnections.iterator();
Large-Scale API Protocol Mining for Automated Bug Detection Michael Pradel Department of Computer Science ETH Zurich 1 Motivation LinkedList pinconnections =...; Iterator i = pinconnections.iterator();
FOR0383 Software Quality Assurance
 This method seems much, much bigger than all the other methods. FOR0383 Software Quality Assurance Lecture 15 Code metrics "You cannot control what you cannot measure." Tom DeMarco 2/11/2009 Dr Andy Brooks
This method seems much, much bigger than all the other methods. FOR0383 Software Quality Assurance Lecture 15 Code metrics "You cannot control what you cannot measure." Tom DeMarco 2/11/2009 Dr Andy Brooks
Software Testing. Software Testing
 Software Testing Software Testing Error: mistake made by the programmer/ developer Fault: a incorrect piece of code/document (i.e., bug) Failure: result of a fault Goal of software testing: Cause failures
Software Testing Software Testing Error: mistake made by the programmer/ developer Fault: a incorrect piece of code/document (i.e., bug) Failure: result of a fault Goal of software testing: Cause failures
Black-box Testing Techniques
 T-76.5613 Software Testing and Quality Assurance Lecture 4, 20.9.2006 Black-box Testing Techniques SoberIT Black-box test case design techniques Basic techniques Equivalence partitioning Boundary value
T-76.5613 Software Testing and Quality Assurance Lecture 4, 20.9.2006 Black-box Testing Techniques SoberIT Black-box test case design techniques Basic techniques Equivalence partitioning Boundary value
Verification and Validation
 Verification and Validation Assuring that a software system meets a user's needs Ian Sommerville 2000 Software Engineering, 6th edition. Chapter 19 Slide 1 Objectives To introduce software verification
Verification and Validation Assuring that a software system meets a user's needs Ian Sommerville 2000 Software Engineering, 6th edition. Chapter 19 Slide 1 Objectives To introduce software verification
Verification and Validation. Assuring that a software system meets a user s needs. Verification vs Validation. The V & V Process
 Verification and Validation Assuring that a software system meets a user s needs Ian Sommerville 1995/2000 (Modified by Spiros Mancoridis 1999) Software Engineering, 6th edition. Chapters 19,20 Slide 1
Verification and Validation Assuring that a software system meets a user s needs Ian Sommerville 1995/2000 (Modified by Spiros Mancoridis 1999) Software Engineering, 6th edition. Chapters 19,20 Slide 1
Software Metrics based on Coding Standards Violations
 Software Metrics based on Coding Standards Violations Yasunari Takai, Takashi Kobayashi and Kiyoshi Agusa Graduate School of Information Science, Nagoya University Aichi, 464-8601, Japan takai@agusa.i.is.nagoya-u.ac.jp,
Software Metrics based on Coding Standards Violations Yasunari Takai, Takashi Kobayashi and Kiyoshi Agusa Graduate School of Information Science, Nagoya University Aichi, 464-8601, Japan takai@agusa.i.is.nagoya-u.ac.jp,
Analysis Tool Project
 Tool Overview The tool we chose to analyze was the Java static analysis tool FindBugs (http://findbugs.sourceforge.net/). FindBugs is A framework for writing static analyses Developed at the University
Tool Overview The tool we chose to analyze was the Java static analysis tool FindBugs (http://findbugs.sourceforge.net/). FindBugs is A framework for writing static analyses Developed at the University
Static and dynamic Testing
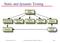 Static and dynamic Testing Static testing Requirements specification High-level design Formal specification Detailed design Program Prototype Dynamic testing Ian Sommerville 1995 Software Engineering,
Static and dynamic Testing Static testing Requirements specification High-level design Formal specification Detailed design Program Prototype Dynamic testing Ian Sommerville 1995 Software Engineering,
WHITE PAPER. 10 Reasons to Use Static Analysis for Embedded Software Development
 WHITE PAPER 10 Reasons to Use Static Analysis for Embedded Software Development Overview Software is in everything. And in many embedded systems like flight control, medical devices, and powertrains, quality
WHITE PAPER 10 Reasons to Use Static Analysis for Embedded Software Development Overview Software is in everything. And in many embedded systems like flight control, medical devices, and powertrains, quality
Software Engineering 2 A practical course in software engineering. Ekkart Kindler
 Software Engineering 2 A practical course in software engineering Quality Management Main Message Planning phase Definition phase Design phase Implem. phase Acceptance phase Mainten. phase 3 1. Overview
Software Engineering 2 A practical course in software engineering Quality Management Main Message Planning phase Definition phase Design phase Implem. phase Acceptance phase Mainten. phase 3 1. Overview
Static Analysis of C++ Projects with CodeSonar
 Static Analysis of C++ Projects with CodeSonar John Plaice, Senior Scientist, GrammaTech jplaice@grammatech.com 25 July 2017, Meetup C++ de Montréal Abstract Static program analysis consists of the analysis
Static Analysis of C++ Projects with CodeSonar John Plaice, Senior Scientist, GrammaTech jplaice@grammatech.com 25 July 2017, Meetup C++ de Montréal Abstract Static program analysis consists of the analysis
Verification Using Static Analysis
 Verification Using Static Analysis Outline Today we will discuss static analysis and how it differs from dynamic analysis We will also look at the different types of static analysis including: Control
Verification Using Static Analysis Outline Today we will discuss static analysis and how it differs from dynamic analysis We will also look at the different types of static analysis including: Control
Software Testing Prof. Rajib Mall Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur. Lecture 13 Path Testing
 Software Testing Prof. Rajib Mall Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 13 Path Testing Welcome to this session and we will discuss about path
Software Testing Prof. Rajib Mall Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 13 Path Testing Welcome to this session and we will discuss about path
Writeup for first project of CMSC 420: Data Structures Section 0102, Summer Theme: Threaded AVL Trees
 Writeup for first project of CMSC 420: Data Structures Section 0102, Summer 2017 Theme: Threaded AVL Trees Handout date: 06-01 On-time deadline: 06-09, 11:59pm Late deadline (30% penalty): 06-11, 11:59pm
Writeup for first project of CMSC 420: Data Structures Section 0102, Summer 2017 Theme: Threaded AVL Trees Handout date: 06-01 On-time deadline: 06-09, 11:59pm Late deadline (30% penalty): 06-11, 11:59pm
White-Box Testing Techniques
 T-76.5613 Software Testing and Quality Assurance Lecture 3, 18.9.2006 White-Box Testing Techniques SoberIT Content What are white-box testing techniques Control flow testing Statement coverage Branch coverage
T-76.5613 Software Testing and Quality Assurance Lecture 3, 18.9.2006 White-Box Testing Techniques SoberIT Content What are white-box testing techniques Control flow testing Statement coverage Branch coverage
Cross-project defect prediction. Thomas Zimmermann Microsoft Research
 Cross-project defect prediction Thomas Zimmermann Microsoft Research Upcoming Events ICSE 2010: http://www.sbs.co.za/icse2010/ New Ideas and Emerging Results ACM Student Research Competition (SRC) sponsored
Cross-project defect prediction Thomas Zimmermann Microsoft Research Upcoming Events ICSE 2010: http://www.sbs.co.za/icse2010/ New Ideas and Emerging Results ACM Student Research Competition (SRC) sponsored
SE310 Analysis and Design of Software
 SE310 Analysis and Design of Software Lecture 14 REVIEW March 26, 2018 Sam Siewert Domain Models Use Case Details Complete a Design Provide Code Re-Use Candidate and PoC/Prototype Start Here! https://www.modelio.org/
SE310 Analysis and Design of Software Lecture 14 REVIEW March 26, 2018 Sam Siewert Domain Models Use Case Details Complete a Design Provide Code Re-Use Candidate and PoC/Prototype Start Here! https://www.modelio.org/
Important Points to Note
 Important Points to Note All Participating colleges are requested to mute your telephone lines during the webinar session. Participants are requested to make note of questions / responses to questions,
Important Points to Note All Participating colleges are requested to mute your telephone lines during the webinar session. Participants are requested to make note of questions / responses to questions,
Abstractness, Specificity, and Complexity in Software Design
 Abstractness, Specificity, and Complexity in Software Design Stefan Wagner and Florian Deißenböck Technische Universität München, Germany Florian Deißenböck ROA, 11.05.2008 Fakultät für Informatik Lehrstuhl
Abstractness, Specificity, and Complexity in Software Design Stefan Wagner and Florian Deißenböck Technische Universität München, Germany Florian Deißenböck ROA, 11.05.2008 Fakultät für Informatik Lehrstuhl
Toward Instant Gradeification
 Toward Instant Gradeification Daniel M. Zimmerman, Joseph R. Kiniry and Fintan Fairmichael University of Washington Tacoma, USA dmz@acm.org IT University of Copenhagen, Denmark kiniry@acm.org University
Toward Instant Gradeification Daniel M. Zimmerman, Joseph R. Kiniry and Fintan Fairmichael University of Washington Tacoma, USA dmz@acm.org IT University of Copenhagen, Denmark kiniry@acm.org University
SourcererCC -- Scaling Code Clone Detection to Big-Code
 SourcererCC -- Scaling Code Clone Detection to Big-Code What did this paper do? SourcererCC a token-based clone detector, that can detect both exact and near-miss clones from large inter project repositories
SourcererCC -- Scaling Code Clone Detection to Big-Code What did this paper do? SourcererCC a token-based clone detector, that can detect both exact and near-miss clones from large inter project repositories
Chapter 10. Testing and Quality Assurance
 Chapter 10 Testing and Quality Assurance Different styles of doing code review Human Reviewer Code Inspection with continuous integration infrastructure Pinger s testing set up Testing Related topics 1.
Chapter 10 Testing and Quality Assurance Different styles of doing code review Human Reviewer Code Inspection with continuous integration infrastructure Pinger s testing set up Testing Related topics 1.
Existing Model Metrics and Relations to Model Quality
 Existing Model Metrics and Relations to Model Quality Parastoo Mohagheghi, Vegard Dehlen WoSQ 09 ICT 1 Background In SINTEF ICT, we do research on Model-Driven Engineering and develop methods and tools:
Existing Model Metrics and Relations to Model Quality Parastoo Mohagheghi, Vegard Dehlen WoSQ 09 ICT 1 Background In SINTEF ICT, we do research on Model-Driven Engineering and develop methods and tools:
Static Analysis Techniques
 oftware Design (F28SD2): Static Analysis Techniques 1 Software Design (F28SD2) Static Analysis Techniques Andrew Ireland School of Mathematical and Computer Science Heriot-Watt University Edinburgh oftware
oftware Design (F28SD2): Static Analysis Techniques 1 Software Design (F28SD2) Static Analysis Techniques Andrew Ireland School of Mathematical and Computer Science Heriot-Watt University Edinburgh oftware
Context-Based Detection of Clone-Related Bugs. Lingxiao Jiang, Zhendong Su, Edwin Chiu University of California at Davis
 Context-Based Detection of Clone-Related Bugs Lingxiao Jiang, Zhendong Su, Edwin Chiu University of California at Davis 1 Outline Introduction and samples of cloning errors Definitions of inconsistencies
Context-Based Detection of Clone-Related Bugs Lingxiao Jiang, Zhendong Su, Edwin Chiu University of California at Davis 1 Outline Introduction and samples of cloning errors Definitions of inconsistencies
[ANALYSIS ASSIGNMENT 10]
![[ANALYSIS ASSIGNMENT 10] [ANALYSIS ASSIGNMENT 10]](/thumbs/83/88553425.jpg) 2009 Pidgin Carlos Simões Higino Silva João Carlos Almeida Miguel Graça Oliveira [ANALYSIS ASSIGNMENT 10] INTRODUCTION The purpose of this project is to evaluate a testing tool chosen by the team and provide
2009 Pidgin Carlos Simões Higino Silva João Carlos Almeida Miguel Graça Oliveira [ANALYSIS ASSIGNMENT 10] INTRODUCTION The purpose of this project is to evaluate a testing tool chosen by the team and provide
Objectives for this class meeting. 1. Conduct review of core concepts concerning contracts and pre/post conditions
 CSE1720 Click to edit Master Week text 01, styles Lecture 02 Second level Third level Fourth level Fifth level Winter 2015! Thursday, Jan 8, 2015 1 Objectives for this class meeting 1. Conduct review of
CSE1720 Click to edit Master Week text 01, styles Lecture 02 Second level Third level Fourth level Fifth level Winter 2015! Thursday, Jan 8, 2015 1 Objectives for this class meeting 1. Conduct review of
Objectives. Chapter 19. Verification vs. validation. Topics covered. Static and dynamic verification. The V&V process
 Objectives Chapter 19 Verification and Validation Assuring that a software system meets a user s need are to introduce software verification and validation (V&V) and to discuss the distinction between
Objectives Chapter 19 Verification and Validation Assuring that a software system meets a user s need are to introduce software verification and validation (V&V) and to discuss the distinction between
Lightweight Verification of Array Indexing
 Lightweight Verification of Array Indexing Martin Kellogg*, Vlastimil Dort**, Suzanne Millstein*, Michael D. Ernst* * University of Washington, Seattle ** Charles University, Prague The problem: unsafe
Lightweight Verification of Array Indexing Martin Kellogg*, Vlastimil Dort**, Suzanne Millstein*, Michael D. Ernst* * University of Washington, Seattle ** Charles University, Prague The problem: unsafe
Do You Know SQL? About Semantic Errors in SQL Queries. Christian Goldberg
 Do You Know SQL? About Semantic Errors in SQL Queries Christian Goldberg goldberg@informatik.uni-halle.de Institut für Informatik Martin-Luther-Universität Halle-Wittenberg TLAD 2009 Birmingham, 6th July
Do You Know SQL? About Semantic Errors in SQL Queries Christian Goldberg goldberg@informatik.uni-halle.de Institut für Informatik Martin-Luther-Universität Halle-Wittenberg TLAD 2009 Birmingham, 6th July
Association between JPL Coding Standard Violations and Software Faults: An Exploratory Study
 Association between JPL Coding Standard Violations and Software Faults: An Exploratory Study Bashar Q. Ahmed Computer Science Department Taiz University Taiz, Yemen Mahmoud O. Elish Computer Science Department
Association between JPL Coding Standard Violations and Software Faults: An Exploratory Study Bashar Q. Ahmed Computer Science Department Taiz University Taiz, Yemen Mahmoud O. Elish Computer Science Department
In this Lecture you will Learn: Testing in Software Development Process. What is Software Testing. Static Testing vs.
 In this Lecture you will Learn: Testing in Software Development Process Examine the verification and validation activities in software development process stage by stage Introduce some basic concepts of
In this Lecture you will Learn: Testing in Software Development Process Examine the verification and validation activities in software development process stage by stage Introduce some basic concepts of
Verification and Validation
 2014-2015 Verification and Validation Part I : Extended Static Analysis Burkhart Wolff Département Informatique Université Paris-Sud / Orsay Static Analysis! We have seen test methods, and proof methods.
2014-2015 Verification and Validation Part I : Extended Static Analysis Burkhart Wolff Département Informatique Université Paris-Sud / Orsay Static Analysis! We have seen test methods, and proof methods.
Is Power State Table Golden?
 Is Power State Table Golden? Harsha Vardhan #1, Ankush Bagotra #2, Neha Bajaj #3 # Synopsys India Pvt. Ltd Bangalore, India 1 dhv@synopsys.com 2 ankushb@synopsys.com 3 nehab@synopsys.com Abstract: Independent
Is Power State Table Golden? Harsha Vardhan #1, Ankush Bagotra #2, Neha Bajaj #3 # Synopsys India Pvt. Ltd Bangalore, India 1 dhv@synopsys.com 2 ankushb@synopsys.com 3 nehab@synopsys.com Abstract: Independent
CERT C++ COMPLIANCE ENFORCEMENT
 CERT C++ COMPLIANCE ENFORCEMENT AUTOMATED SOURCE CODE ANALYSIS TO MAINTAIN COMPLIANCE SIMPLIFY AND STREAMLINE CERT C++ COMPLIANCE The CERT C++ compliance module reports on dataflow problems, software defects,
CERT C++ COMPLIANCE ENFORCEMENT AUTOMATED SOURCE CODE ANALYSIS TO MAINTAIN COMPLIANCE SIMPLIFY AND STREAMLINE CERT C++ COMPLIANCE The CERT C++ compliance module reports on dataflow problems, software defects,
Principles of Software Construction: Objects, Design, and Concurrency (Part 2: Designing (Sub )Systems)
 Principles of Software Construction: Objects, Design, and Concurrency (Part 2: Designing (Sub )Systems) More Analysis for Functional Correctness Jonathan Aldrich Charlie Garrod School of Computer Science
Principles of Software Construction: Objects, Design, and Concurrency (Part 2: Designing (Sub )Systems) More Analysis for Functional Correctness Jonathan Aldrich Charlie Garrod School of Computer Science
Part I: Preliminaries 24
 Contents Preface......................................... 15 Acknowledgements................................... 22 Part I: Preliminaries 24 1. Basics of Software Testing 25 1.1. Humans, errors, and testing.............................
Contents Preface......................................... 15 Acknowledgements................................... 22 Part I: Preliminaries 24 1. Basics of Software Testing 25 1.1. Humans, errors, and testing.............................
Verifying source code
 Software and Systems Verification (VIMIMA01) Verifying source code Akos Hajdu, Istvan Majzik, Zoltan Micskei Budapest University of Technology and Economics Fault Tolerant Systems Research Group Budapest
Software and Systems Verification (VIMIMA01) Verifying source code Akos Hajdu, Istvan Majzik, Zoltan Micskei Budapest University of Technology and Economics Fault Tolerant Systems Research Group Budapest
Don t Judge Software by Its (Code) Coverage
 Author manuscript, published in "SAFECOMP 2013 - Workshop CARS (2nd Workshop on Critical Automotive applications : Robustness & Safety) of the 32nd International Conference on Computer Safety, Reliability
Author manuscript, published in "SAFECOMP 2013 - Workshop CARS (2nd Workshop on Critical Automotive applications : Robustness & Safety) of the 32nd International Conference on Computer Safety, Reliability
Specification-Based Testing 1
 Specification-Based Testing 1 Stuart Anderson Overview 1 Basic terminology A view of faults through failure Systematic versus randomised testing A systematic approach to specification-based testing A simple
Specification-Based Testing 1 Stuart Anderson Overview 1 Basic terminology A view of faults through failure Systematic versus randomised testing A systematic approach to specification-based testing A simple
Ian Sommerville 2006 Software Engineering, 8th edition. Chapter 22 Slide 1
 Verification and Validation Slide 1 Objectives To introduce software verification and validation and to discuss the distinction between them To describe the program inspection process and its role in V
Verification and Validation Slide 1 Objectives To introduce software verification and validation and to discuss the distinction between them To describe the program inspection process and its role in V
Higher-order Testing. Stuart Anderson. Stuart Anderson Higher-order Testing c 2011
 Higher-order Testing Stuart Anderson Defining Higher Order Tests 1 The V-Model V-Model Stages Meyers version of the V-model has a number of stages that relate to distinct testing phases all of which are
Higher-order Testing Stuart Anderson Defining Higher Order Tests 1 The V-Model V-Model Stages Meyers version of the V-model has a number of stages that relate to distinct testing phases all of which are
[IT6004-SOFTWARE TESTING] UNIT 2
![[IT6004-SOFTWARE TESTING] UNIT 2 [IT6004-SOFTWARE TESTING] UNIT 2](/thumbs/90/102012046.jpg) 1. List the two basic Testing strategies. UNIT 2 Black box testing. White box testing. 2. What are the knowledge sources for Black box testing? Requirements Document specification Domain knowledge Defect
1. List the two basic Testing strategies. UNIT 2 Black box testing. White box testing. 2. What are the knowledge sources for Black box testing? Requirements Document specification Domain knowledge Defect
Testing Theory. Agenda - What will you learn today? A Software Life-cycle Model Which part will we talk about today? Theory Lecture Plan
 heory Lecture Plan 2 esting heory Lecture 8 Software Engineering DDC88/DDC93 autumn 28 Department of Computer and Information Science Linköping University, Sweden L - Course Introduction and Overview L2
heory Lecture Plan 2 esting heory Lecture 8 Software Engineering DDC88/DDC93 autumn 28 Department of Computer and Information Science Linköping University, Sweden L - Course Introduction and Overview L2
Software Engineering 2 A practical course in software engineering. Ekkart Kindler
 Software Engineering 2 A practical course in software engineering I. Introduction Introduction Motivation: Software engineering & management Agile development The role of models in software engineering
Software Engineering 2 A practical course in software engineering I. Introduction Introduction Motivation: Software engineering & management Agile development The role of models in software engineering
MACHINE LEARNING BASED METHODOLOGY FOR TESTING OBJECT ORIENTED APPLICATIONS
 MACHINE LEARNING BASED METHODOLOGY FOR TESTING OBJECT ORIENTED APPLICATIONS N. Kannadhasan and B. Uma Maheswari Department of Master of Computer Applications St. Joseph s College of Engineering, Chennai,
MACHINE LEARNING BASED METHODOLOGY FOR TESTING OBJECT ORIENTED APPLICATIONS N. Kannadhasan and B. Uma Maheswari Department of Master of Computer Applications St. Joseph s College of Engineering, Chennai,
ARiSA First Contact Analysis
 ARiSA First Contact Analysis Applied Research In System Analysis - ARiSA You cannot control what you cannot measure Tom DeMarco Software Grail Version 1.3 Programming Language Java 1.4 Date 2 nd of December,
ARiSA First Contact Analysis Applied Research In System Analysis - ARiSA You cannot control what you cannot measure Tom DeMarco Software Grail Version 1.3 Programming Language Java 1.4 Date 2 nd of December,
By V-cubed Solutions, Inc. Page1. All rights reserved by V-cubed Solutions, Inc.
 By V-cubed Solutions, Inc. Page1 Purpose of Document This document will demonstrate the efficacy of CODESCROLL CODE INSPECTOR, CONTROLLER TESTER, and QUALITYSCROLL COVER, which has been developed by V-cubed
By V-cubed Solutions, Inc. Page1 Purpose of Document This document will demonstrate the efficacy of CODESCROLL CODE INSPECTOR, CONTROLLER TESTER, and QUALITYSCROLL COVER, which has been developed by V-cubed
Duplication de code: un défi pour l assurance qualité des logiciels?
 Duplication de code: un défi pour l assurance qualité des logiciels? Foutse Khomh S.W.A.T http://swat.polymtl.ca/ 2 JHotDraw 3 Code duplication can be 4 Example of code duplication Duplication to experiment
Duplication de code: un défi pour l assurance qualité des logiciels? Foutse Khomh S.W.A.T http://swat.polymtl.ca/ 2 JHotDraw 3 Code duplication can be 4 Example of code duplication Duplication to experiment
Programming. Dr Ben Dudson University of York
 Programming Dr Ben Dudson University of York Outline Last lecture covered the basics of programming and IDL This lecture will cover More advanced IDL and plotting Fortran and C++ Programming techniques
Programming Dr Ben Dudson University of York Outline Last lecture covered the basics of programming and IDL This lecture will cover More advanced IDL and plotting Fortran and C++ Programming techniques
Software Testing part II (white box) Lecturer: Giuseppe Santucci
 Software Testing part II (white box) Lecturer: Giuseppe Santucci 4. White box testing White-box (or Glass-box) testing: general characteristics Statement coverage Decision coverage Condition coverage Decision
Software Testing part II (white box) Lecturer: Giuseppe Santucci 4. White box testing White-box (or Glass-box) testing: general characteristics Statement coverage Decision coverage Condition coverage Decision
COMPARISON AND EVALUATION ON METRICS
 COMPARISON AND EVALUATION ON METRICS BASED APPROACH FOR DETECTING CODE CLONE D. Gayathri Devi 1 1 Department of Computer Science, Karpagam University, Coimbatore, Tamilnadu dgayadevi@gmail.com Abstract
COMPARISON AND EVALUATION ON METRICS BASED APPROACH FOR DETECTING CODE CLONE D. Gayathri Devi 1 1 Department of Computer Science, Karpagam University, Coimbatore, Tamilnadu dgayadevi@gmail.com Abstract
Analysiss of Software Artifacts
 Analysiss of Software Artifacts : Tool Project 6 th April 2009 The Mappers António Alvim Filipe Pontes Paulo Casanova Pedro Mota Pedro Saraiva Tool Project 1 Introduction...... 3 Tool...... 4 Projects......
Analysiss of Software Artifacts : Tool Project 6 th April 2009 The Mappers António Alvim Filipe Pontes Paulo Casanova Pedro Mota Pedro Saraiva Tool Project 1 Introduction...... 3 Tool...... 4 Projects......
Introduction to Dynamic Analysis
 Introduction to Dynamic Analysis Reading assignment Gary T. Leavens, Yoonsik Cheon, "Design by Contract with JML," draft paper, http://www.eecs.ucf.edu/~leavens/jml//jmldbc.pdf G. Kudrjavets, N. Nagappan,
Introduction to Dynamic Analysis Reading assignment Gary T. Leavens, Yoonsik Cheon, "Design by Contract with JML," draft paper, http://www.eecs.ucf.edu/~leavens/jml//jmldbc.pdf G. Kudrjavets, N. Nagappan,
Fault Tolerant Computing CS 530 Software Reliability: Static Factors. Yashwant K. Malaiya Colorado State University
 Fault Tolerant Computing CS 530 Software Reliability: Static Factors Yashwant K. Malaiya Colorado State University 1 Class Notes Project Proposal due 3/2/2018 Midterm 3/8/2018, Thurs OC (+ local distance):
Fault Tolerant Computing CS 530 Software Reliability: Static Factors Yashwant K. Malaiya Colorado State University 1 Class Notes Project Proposal due 3/2/2018 Midterm 3/8/2018, Thurs OC (+ local distance):
Compiler Construction I
 TECHNISCHE UNIVERSITÄT MÜNCHEN FAKULTÄT FÜR INFORMATIK Compiler Construction I Dr. Michael Petter SoSe 2015 1 / 58 Organizing Master or Bachelor in the 6th Semester with 5 ECTS Prerequisites Informatik
TECHNISCHE UNIVERSITÄT MÜNCHEN FAKULTÄT FÜR INFORMATIK Compiler Construction I Dr. Michael Petter SoSe 2015 1 / 58 Organizing Master or Bachelor in the 6th Semester with 5 ECTS Prerequisites Informatik
Chapter 11, Testing. Using UML, Patterns, and Java. Object-Oriented Software Engineering
 Chapter 11, Testing Using UML, Patterns, and Java Object-Oriented Software Engineering Outline Terminology Types of errors Dealing with errors Quality assurance vs Testing Component Testing! Unit testing!
Chapter 11, Testing Using UML, Patterns, and Java Object-Oriented Software Engineering Outline Terminology Types of errors Dealing with errors Quality assurance vs Testing Component Testing! Unit testing!
Recitation #3. September 14, 2018
 18-642 Recitation #3 September 14, 2018 Homework: Updates Homeworks through #6 graded on canvas Homeworks #9/10/11 due Wednesday night Homework grading Points are mostly for good faith effort (no single
18-642 Recitation #3 September 14, 2018 Homework: Updates Homeworks through #6 graded on canvas Homeworks #9/10/11 due Wednesday night Homework grading Points are mostly for good faith effort (no single
Software Testing 2. OOD and Testability. White box vs Black box Testing. Software Testing 2 Semester 1, 2006
 Software Testing 2 Jens Dietrich OOD and Testability Component based design and component based unit testing. Design that isolates component that are difficult to test (automatically) (such as user interfaces).
Software Testing 2 Jens Dietrich OOD and Testability Component based design and component based unit testing. Design that isolates component that are difficult to test (automatically) (such as user interfaces).
Testing! Prof. Leon Osterweil! CS 520/620! Spring 2013!
 Testing Prof. Leon Osterweil CS 520/620 Spring 2013 Relations and Analysis A software product consists of A collection of (types of) artifacts Related to each other by myriad Relations The relations are
Testing Prof. Leon Osterweil CS 520/620 Spring 2013 Relations and Analysis A software product consists of A collection of (types of) artifacts Related to each other by myriad Relations The relations are
Code Analysis Via Version Control History
 Code Analysis Via Version Control History Justin Mclean Class Software Email: justin@classsoftware.com Twitter: @justinmclean Blog: http://blog.classsoftware.com Who am I? Freelance Developer Programming
Code Analysis Via Version Control History Justin Mclean Class Software Email: justin@classsoftware.com Twitter: @justinmclean Blog: http://blog.classsoftware.com Who am I? Freelance Developer Programming
Learning outcomes. Systems Engineering. Debugging Process. Debugging Process. Review
 Systems Engineering Lecture 9 System Verification II Dr. Joanna Bryson Dr. Leon Watts University of Bath Department of Computer Science 1 Learning outcomes After both lectures and doing the reading, you
Systems Engineering Lecture 9 System Verification II Dr. Joanna Bryson Dr. Leon Watts University of Bath Department of Computer Science 1 Learning outcomes After both lectures and doing the reading, you
ExMAn: A Generic and Customizable Framework for Experimental Mutation Analysis 1
 ExMAn: A Generic and Customizable Framework for Experimental Mutation Analysis 1 Jeremy S. Bradbury, James R. Cordy, Juergen Dingel School of Computing, Queen s University Kingston, Ontario, Canada {bradbury,
ExMAn: A Generic and Customizable Framework for Experimental Mutation Analysis 1 Jeremy S. Bradbury, James R. Cordy, Juergen Dingel School of Computing, Queen s University Kingston, Ontario, Canada {bradbury,
Why testing and analysis. Software Testing. A framework for software testing. Outline. Software Qualities. Dependability Properties
 Why testing and analysis Software Testing Adapted from FSE 98 Tutorial by Michal Young and Mauro Pezze Software is never correct no matter what developing testing technique is used All software must be
Why testing and analysis Software Testing Adapted from FSE 98 Tutorial by Michal Young and Mauro Pezze Software is never correct no matter what developing testing technique is used All software must be
Analyzing Robustness of UML State Machines
 Analyzing Robustness of UML State Machines Reinhard von Hanxleden Department of Computer Science and Applied Mathematics Real-Time Systems and Embedded Systems Group Christian-Albrecht Universität zu Kiel
Analyzing Robustness of UML State Machines Reinhard von Hanxleden Department of Computer Science and Applied Mathematics Real-Time Systems and Embedded Systems Group Christian-Albrecht Universität zu Kiel
Static Code Analysis to Find Bugs. Wright.edu CS7140 Spring 2013 (Slides collected from many sources)
 Static Code Analysis to Find Bugs Wright.edu CS7140 Spring 2013 (Slides collected from many sources) Comparison of Defect-Detection Approaches Inspections? The combination of design and code inspections
Static Code Analysis to Find Bugs Wright.edu CS7140 Spring 2013 (Slides collected from many sources) Comparison of Defect-Detection Approaches Inspections? The combination of design and code inspections
Towards Better Understanding of Software Quality Evolution Through Commit Impact Analysis
 Towards Better Understanding of Software Quality Evolution Through Commit Impact Analysis Sponsor: DASD(SE) By Mr. Pooyan Behnamghader 5 th Annual SERC Doctoral Students Forum November 7, 2017 FHI 360
Towards Better Understanding of Software Quality Evolution Through Commit Impact Analysis Sponsor: DASD(SE) By Mr. Pooyan Behnamghader 5 th Annual SERC Doctoral Students Forum November 7, 2017 FHI 360
QTEP: Quality-Aware Test Case Prioritization
 QTEP: Quality-Aware Test Case Prioritization {song.wang,jc.nam,lintan}@uwaterloo.ca Electrical and Computer Engineering, University of Waterloo Waterloo, ON, Canada ABSTRACT Test case prioritization (TCP)
QTEP: Quality-Aware Test Case Prioritization {song.wang,jc.nam,lintan}@uwaterloo.ca Electrical and Computer Engineering, University of Waterloo Waterloo, ON, Canada ABSTRACT Test case prioritization (TCP)
Testing. ECE/CS 5780/6780: Embedded System Design. Why is testing so hard? Why do testing?
 Testing ECE/CS 5780/6780: Embedded System Design Scott R. Little Lecture 24: Introduction to Software Testing and Verification What is software testing? Running a program in order to find bugs (faults,
Testing ECE/CS 5780/6780: Embedded System Design Scott R. Little Lecture 24: Introduction to Software Testing and Verification What is software testing? Running a program in order to find bugs (faults,
Compiler Construction I
 TECHNISCHE UNIVERSITÄT MÜNCHEN FAKULTÄT FÜR INFORMATIK Compiler Construction I Dr. Michael Petter, Dr. Axel Simon SoSe 2014 1 / 59 Organizing Master or Bachelor in the 6th Semester with 5 ECTS Prerequisites
TECHNISCHE UNIVERSITÄT MÜNCHEN FAKULTÄT FÜR INFORMATIK Compiler Construction I Dr. Michael Petter, Dr. Axel Simon SoSe 2014 1 / 59 Organizing Master or Bachelor in the 6th Semester with 5 ECTS Prerequisites
Darshan Institute of Engineering & Technology Unit : 9
 1) Explain software testing strategy for conventional software architecture. Draw the spiral diagram showing testing strategies with phases of software development. Software Testing: Once source code has
1) Explain software testing strategy for conventional software architecture. Draw the spiral diagram showing testing strategies with phases of software development. Software Testing: Once source code has
Finding Extract Method Refactoring Opportunities by Analyzing Development History
 2017 IEEE 41st Annual Computer Software and Applications Conference Finding Extract Refactoring Opportunities by Analyzing Development History Ayaka Imazato, Yoshiki Higo, Keisuke Hotta, and Shinji Kusumoto
2017 IEEE 41st Annual Computer Software and Applications Conference Finding Extract Refactoring Opportunities by Analyzing Development History Ayaka Imazato, Yoshiki Higo, Keisuke Hotta, and Shinji Kusumoto
Experience Report: Error Distribution in Safety-Critical Software and Software Risk Analysis Based on Unit Tests
 Experience Report: Error Distribution in Safety-Critical Software and Software Risk Analysis Based on Unit Tests Stephan Ramberger, Thomas Gruber, Wolfgang Herzner Division Information Technologies ARC
Experience Report: Error Distribution in Safety-Critical Software and Software Risk Analysis Based on Unit Tests Stephan Ramberger, Thomas Gruber, Wolfgang Herzner Division Information Technologies ARC
COMPLEX SYSTEMS. Today. Complex Systems. Kinds of Systems. Embedded Systems. Software Engineering. Lectures 20: Engineering Complex Systems
 Chair of Software Engineering Today Software Engineering Prof. Dr. Bertrand Meyer Dr. Manuel Oriol Dr. Bernd Schoeller Lectures 20: Engineering Complex Systems Complex Systems What is it? Examples Technologies
Chair of Software Engineering Today Software Engineering Prof. Dr. Bertrand Meyer Dr. Manuel Oriol Dr. Bernd Schoeller Lectures 20: Engineering Complex Systems Complex Systems What is it? Examples Technologies
MTAT : Software Testing
 MTAT.03.159: Software Testing Lecture 04: Static Testing (Inspection) and Defect Estimation (Textbook Ch. 10 & 12) Spring 2013 Dietmar Pfahl email: dietmar.pfahl@ut.ee Lecture Reading Chapter 10: Reviews
MTAT.03.159: Software Testing Lecture 04: Static Testing (Inspection) and Defect Estimation (Textbook Ch. 10 & 12) Spring 2013 Dietmar Pfahl email: dietmar.pfahl@ut.ee Lecture Reading Chapter 10: Reviews
Verification and Validation. Ian Sommerville 2004 Software Engineering, 7th edition. Chapter 22 Slide 1
 Verification and Validation Ian Sommerville 2004 Software Engineering, 7th edition. Chapter 22 Slide 1 Verification vs validation Verification: "Are we building the product right?. The software should
Verification and Validation Ian Sommerville 2004 Software Engineering, 7th edition. Chapter 22 Slide 1 Verification vs validation Verification: "Are we building the product right?. The software should
Rubicon: Scalable Bounded Verification of Web Applications
 Joseph P. Near Research Statement My research focuses on developing domain-specific static analyses to improve software security and reliability. In contrast to existing approaches, my techniques leverage
Joseph P. Near Research Statement My research focuses on developing domain-specific static analyses to improve software security and reliability. In contrast to existing approaches, my techniques leverage
EmpAnADa Project. Christian Lange. June 4 th, Eindhoven University of Technology, The Netherlands.
 EmpAnADa Project C.F.J.Lange@tue.nl June 4 th, 2004 Eindhoven University of Technology, The Netherlands Outline EmpAnADa introduction Part I Completeness and consistency in detail Part II Background UML
EmpAnADa Project C.F.J.Lange@tue.nl June 4 th, 2004 Eindhoven University of Technology, The Netherlands Outline EmpAnADa introduction Part I Completeness and consistency in detail Part II Background UML
Flexible Architecture Conformance Assessment with ConQAT
 Flexible Architecture Conformance Assessment with ConQAT Florian Deissenboeck, Lars Heinemann, Benjamin Hummel, Elmar Juergens Technische Universität München ICSE 2010 Cape Town Software Architecture Software
Flexible Architecture Conformance Assessment with ConQAT Florian Deissenboeck, Lars Heinemann, Benjamin Hummel, Elmar Juergens Technische Universität München ICSE 2010 Cape Town Software Architecture Software
Object Oriented Mutation Applied in Java Application programming Interface and C++ Classes
 Object Oriented Mutation Applied in Java Application programming Interface and C++ Classes Titu Singh Arora 1, Ravindra Gupta 2 M.Tech Scholar, Department of Computer Science, SSSIST Sehore, India 1 Professor
Object Oriented Mutation Applied in Java Application programming Interface and C++ Classes Titu Singh Arora 1, Ravindra Gupta 2 M.Tech Scholar, Department of Computer Science, SSSIST Sehore, India 1 Professor
Verification and Validation of High-Integrity Systems
 Verification and Validation of High-Integrity Systems Chethan CU, MathWorks Vaishnavi HR, MathWorks 2015 The MathWorks, Inc. 1 Growing Complexity of Embedded Systems Emergency Braking Body Control Module
Verification and Validation of High-Integrity Systems Chethan CU, MathWorks Vaishnavi HR, MathWorks 2015 The MathWorks, Inc. 1 Growing Complexity of Embedded Systems Emergency Braking Body Control Module
Lecture 9 Dynamic Compilation
 Lecture 9 Dynamic Compilation I. Motivation & Background II. Overview III. Compilation Policy IV. Partial Method Compilation V. Partial Dead Code Elimination VI. Escape Analysis VII. Results Partial Method
Lecture 9 Dynamic Compilation I. Motivation & Background II. Overview III. Compilation Policy IV. Partial Method Compilation V. Partial Dead Code Elimination VI. Escape Analysis VII. Results Partial Method
Measurement. Joseph Spring. Based on Software Metrics by Fenton and Pfleeger
 Measurement Joseph Spring Based on Software Metrics by Fenton and Pfleeger Discussion Measurement Direct and Indirect Measurement Measurements met so far Measurement Scales and Types of Scale Measurement
Measurement Joseph Spring Based on Software Metrics by Fenton and Pfleeger Discussion Measurement Direct and Indirect Measurement Measurements met so far Measurement Scales and Types of Scale Measurement
<Name of the project> Software Requirement Specification
 Software Requirement Specification Project Code: Document Code: v RECORD OF CHANGE *A -
Software Requirement Specification Project Code: Document Code: v RECORD OF CHANGE *A -
Lecture 15 Software Testing
 Lecture 15 Software Testing Includes slides from the companion website for Sommerville, Software Engineering, 10/e. Pearson Higher Education, 2016. All rights reserved. Used with permission. Topics covered
Lecture 15 Software Testing Includes slides from the companion website for Sommerville, Software Engineering, 10/e. Pearson Higher Education, 2016. All rights reserved. Used with permission. Topics covered
Static Analysis methods and tools An industrial study. Pär Emanuelsson Ericsson AB and LiU Prof Ulf Nilsson LiU
 Static Analysis methods and tools An industrial study Pär Emanuelsson Ericsson AB and LiU Prof Ulf Nilsson LiU Outline Why static analysis What is it Underlying technology Some tools (Coverity, KlocWork,
Static Analysis methods and tools An industrial study Pär Emanuelsson Ericsson AB and LiU Prof Ulf Nilsson LiU Outline Why static analysis What is it Underlying technology Some tools (Coverity, KlocWork,
Evaluating Bug Finders
 Evaluating Bug Finders Test and Measurement of Static Code Analyzers Aurelien DELAITRE Bertrand STIVALET http://samate.nist.gov ICSE - COUFLESS 2015 May 23, 2015 Authors Aurelien DELAITRE West Virginia
Evaluating Bug Finders Test and Measurement of Static Code Analyzers Aurelien DELAITRE Bertrand STIVALET http://samate.nist.gov ICSE - COUFLESS 2015 May 23, 2015 Authors Aurelien DELAITRE West Virginia
Requirements Validation and Negotiation
 REQUIREMENTS ENGINEERING LECTURE 2015/2016 Eddy Groen Requirements Validation and Negotiation AGENDA Fundamentals of Requirements Validation Fundamentals of Requirements Negotiation Quality Aspects of
REQUIREMENTS ENGINEERING LECTURE 2015/2016 Eddy Groen Requirements Validation and Negotiation AGENDA Fundamentals of Requirements Validation Fundamentals of Requirements Negotiation Quality Aspects of
Simulink Verification and Validation
 Simulink Verification and Validation Mark Walker MathWorks 7 th October 2014 2014 The MathWorks, Inc. 1 V Diagrams 3 When to Stop? A perfectly tested design would never be released Time spent on V&V is
Simulink Verification and Validation Mark Walker MathWorks 7 th October 2014 2014 The MathWorks, Inc. 1 V Diagrams 3 When to Stop? A perfectly tested design would never be released Time spent on V&V is
