Payment Card Industry (PCI) Executive Report 11/07/2017
|
|
|
- Brendan Ellis
- 5 years ago
- Views:
Transcription
1 Payment Card Industry (PCI) Executive Report 11/07/2017 ASV Scan Report Attestation of Scan Compliance A1. Scan Customer Information A2. Approved Scanning Vendor Information Company: Allied Collection Services of CA Company: Qualys Contact Name: Susana G Job Title: Contact Name: Telephone: Business Address: Oakdale Avenue, Suite 205, susanag@acsca. com Qualys PCI ASV Support Job Title: Telephone: (650) Business Address: 1600 Bridge Parkway, Qualys PCI ASV Support support@qualys. com City: Chatsworth State/Province: California City: Redwood Shores State/Province: California ZIP/postal code: Country: United States of America ZIP/postal code: Country: United States of America URL: URL: A3. Scan Status Date scan completed 11/06/2017 Scan expiration date (90 days from date scan completed) 02/04/2018 Compliance Status Scan report type Full scan Number of unique in-scope components scanned 1 Number of identified failing vulnerabilities 0 Number of components found by ASV but not scanned because scan customer confirmed components were out of scope 7 A.4 Scan Customer Attestation Allied Collection Services of CA attests on 11/07/2017 at 18:07:44 GMT that this scan (either by itself or combined with multiple, partial, or failed scans/ rescans, as indicated in the above Section A.3, "Scan Status") includes all components which should be in scope for PCI DSS, any component considered out of scope for this scan is properly segmented from my cardholder data environment, and any evidence submitted to the ASV to resolve scan exceptions - including compensating controls if applicable- is accurate and complete. Allied Collection Services of CA also acknowledges 1) accurate and complete scoping of this external scan is my responsibility, and 2) this scan result only indicates whether or not my scanned systems are compliant with the external vulnerability scan requirement of PCI DSS; this scan result does not represent my overall compliance status with PCI DSS or provide any indication of compliance with other PCI DSS requirements. A.5 ASV Attestation This scan and report was prepared and conducted by Qualys under certificate number , according to internal processes that meet PCI DSS requirement and the ASV Program Guide. Qualys attests that the PCI DSS scan process was followed, including a manual or automated Quality Assurance process with customer boarding and scoping practices, review of results for anomalies, and review and correction of 1) disputed or incomplete results, 2) false positives, 3) compensating controls (if applicable), and 4) active scan interference. This report and any exceptions were reviewed by Qualys PCI ASV Support Payment Card Industry (PCI) Executive Report page 1
2 ASV Scan Report Summary Part 1. Scan Information Scan Customer Company: Allied Collection Services of CA ASV Company: Qualys Date scan was completed: 11/06/2017 Scan expiration date: 02/04/2018 Part 2. Component Compliance Summary IP Address: Part 2. Component Compliance Summary - (Hosts Not Current) Part 3a. Vulnerabilities Noted for each Component Component Vulnerabilities Noted per Component Severity Level CVSS Score Compliance Status Exceptions, False Positives, or Compensating Controls Noted by the ASV for this Vulnerability TCP Sequence Number Approximation Based Denial of Service CVE The vulnerability is purely a denial-of-service (DoS) vulnerability. Part 3b. Special Notes by Component Component Special Note Unknown services Remote Access Item Noted (remote access software, POS software, etc.) Open TCP Services List (TCP/IP)(..) Dell Remote Access Controller De(..) Scan customer's description of actions taken and declaration that software is either implemented securely or removed Yes - We will remediate. Yes - We will remediate. Part 3c. Special Notes Full Text Note Unknown services Note to Scan Customer : Unidentified services have been detected. Due to increased risk to the cardholder data environment, identify the service, then either 1) justify the business need for this service and confirm it is securely implememted, or 2) identify the service and confirm that it is disabled. Consult your ASV if you have questions about this Special Note. Remote Access Note to Scan Customer : Due to increased risk to the cardholder data environment when remote access software is present, please 1) justify the business need for this software to the ASV and 2) confirm it is either implemented securely or disabled/removed. Part 4a. Scope Submitted by Scan Customer for Discovery IP Addresses/ranges/subnets, domains, URLs, etc. IP Addresses/Ranges : Payment Card Industry (PCI) Executive Report page 2
3 Part 4b. Scan Customer Designated "In-Scope" Components (Scanned) IP Addresses/ranges/subnets, domains, URLs, etc. IP Addresses/Ranges : Part 4c. Scan Customer Designated "Out-of-Scope" Components (Not Scanned) IP Addresses/ranges/subnets, domains, URLs, etc. IP Addresses/Ranges : - (not active) Scan customer attests that this IP address is not issued/assigned to any physical or virtual host. ASV confirmed it is nonresponsive. Payment Card Industry (PCI) Executive Report page 3
4 Report Summary Company: Allied Collection Services of CA Hosts in Account: 1 Hosts Scanned: 1 Hosts Active: 1 Scan Date: 11/06/2017 at 17:52:56 GMT Report Date: 11/07/2017 at 18:07:55 GMT Report Title: Allied Collection Service PCI Certification Template Title: Payment Card Industry (PCI) Executive Report Summary of Vulnerabilities Vulnerabilities Total 13 Average Security Risk 2.0 by Severity Severity Confirmed Potential Information Gathered Total Total by PCI Severity PCI Severity Confirmed Potential Total High Medium Low Total Payment Card Industry (PCI) Executive Report page 4
5 Vulnerabilities by PCI Severity Potential Vulnerabilities by PCI Severity Payment Card Industry (PCI) Executive Report page 5
6 Vulnerabilities by Severity Potential Vulnerabilities by Severity Payment Card Industry (PCI) Executive Report page 6
7 Appendices Hosts Scanned Option Profile Scan Scanned TCP Ports: Full Scanned UDP Ports: Standard Scan Scan Dead Hosts: Off Load Balancer Detection: Off Password Brute Forcing: Standard Vulnerability Detection: Complete Windows Authentication: Disabled SSH Authentication: Disabled Oracle Authentication: Disabled SNMP Authentication: Disabled Perform 3-way Handshake: Off Advanced Hosts Discovery: TCP Standard Scan, UDP Standard Scan, ICMP On Ignore RST packets: Off Ignore firewall-generated SYN-ACK packets: Off Do not send ACK or SYN-ACK packets during host discovery: Off Payment Card Industry (PCI) Executive Report page 7
8 Report Legend Payment Card Industry (PCI) Status An overall PCI compliance status of PASSED indicates that all hosts in the report passed the PCI compliance standards. A PCI compliance status of PASSED for a single host/ip indicates that no vulnerabilities or potential vulnerabilities, as defined by the PCI DSS compliance standards set by the PCI Council, were detected on the host. An overall PCI compliance status of FAILED indicates that at least one host in the report failed to meet the PCI compliance standards. A PCI compliance status of FAILED for a single host/ip indicates that at least one vulnerability or potential vulnerability, as defined by the PCI DSS compliance standards set by the PCI Council, was detected on the host. Vulnerability Levels A Vulnerability is a design flaw or mis-configuration which makes your network (or a host on your network) susceptible to malicious attacks from local or remote users. Vulnerabilities can exist in several areas of your network, such as in your firewalls, FTP servers, Web servers, operating systems or CGI bins. Depending on the level of the security risk, the successful exploitation of a vulnerability can vary from the disclosure of information about the host to a complete compromise of the host. Severity Level Description 1 Minimal Intruders can collect information about the host (open ports, services, etc.) and may be able to use this information to find other vulnerabilities. 2 Medium Intruders may be able to collect sensitive information from the host, such as the precise version of software installed. With this information, intruders can easily exploit known vulnerabilities specific to software versions. 3 Serious Intruders may be able to gain access to specific information stored on the host, including security settings. This could result in potential misuse of the host by intruders. For example, vulnerabilities at this level may include partial disclosure of file contents, access to certain files on the host, directory browsing, disclosure of filtering rules and security mechanisms, denial of service attacks, and unauthorized use of services, such as mail-relaying. 4 Critical Intruders can possibly gain control of the host, or there may be potential leakage of highly sensitive information. For example, vulnerabilities at this level may include full read access to files, potential backdoors, or a listing of all the users on the host. 5 Urgent Intruders can easily gain control of the host, which can lead to the compromise of your entire network security. For example, vulnerabilities at this level may include full read and write access to files, remote execution of commands, and the presence of backdoors. Severity Level Description Low Medium High A vulnerability with a CVSS base score of 0.0 through 3.9. These vulnerabilities are not required to be fixed to pass PCI compliance. A vulnerability with a CVSS base score of 4.0 through 6.9. These vulnerabilities must be fixed to pass PCI compliance. A vulnerability with a CVSS base score of 7.0 through These vulnerabilities must be fixed to pass PCI compliance. Potential Vulnerability Levels A potential vulnerability is one which we cannot confirm exists. The only way to verify the existence of such vulnerabilities on your network would be to perform an intrusive scan, which could result in a denial of service. This is strictly against our policy. Instead, we urge you to investigate these potential vulnerabilities further. Severity Level Description 1 Minimal If this vulnerability exists on your system, intruders can collect information about the host (open ports, services, etc.) and may be able to use this information to find other vulnerabilities. 2 Medium If this vulnerability exists on your system, intruders may be able to collect sensitive information from the host, such as the precise version of software installed. With this information, intruders can easily exploit known vulnerabilities specific to software versions. 3 Serious If this vulnerability exists on your system, intruders may be able to gain access to specific information stored on the host, including security settings. This could result in potential misuse of the host by intruders. For example, vulnerabilities at this level may include partial disclosure of file contents, access to certain files on the host, directory browsing, disclosure of filtering rules and security mechanisms, denial of service attacks, and unauthorized use of services, such as mail-relaying. Payment Card Industry (PCI) Executive Report page 8
9 4 Critical If this vulnerability exists on your system, intruders can possibly gain control of the host, or there may be potential leakage of highly sensitive information. For example, vulnerabilities at this level may include full read access to files, potential backdoors, or a listing of all the users on the host. 5 Urgent If this vulnerability exists on your system, intruders can easily gain control of the host, which can lead to the compromise of your entire network security. For example, vulnerabilit es at this level may include full read and write access to files, remote execution of comma ds, and the presence of backdoors. Severity Level Description Low Medium High A potential vulnerability with a CVSS base score of 0.0 through 3.9. These vulnerabilities are not required to be fixed to pass PCI compliance. A potential vulnerability with a CVSS base score of 4.0 through 6.9. These vulnerabilities must be fixed to pass PCI compliance. A potential vulnerability with a CVSS base score of 7.0 through These vulnerabilities must be fixed to pass PCI compliance. Information Gathered Information Gathered includes visible information about the network related to the host, such as traceroute information, Internet Service Provider (ISP), or a list of reachable hosts. Information Gathered severity levels also include Network Mapping data, such as detected firewalls, SMTP banners, or a list of open TCP services. Severity Level Description 1 Minimal Intruders may be able to retrieve sensitive information related to the host, such as open UDP and TCP services lists, and detection of firewalls. 2 Medium Intruders may be able to determine the operating system running on the host, and view banner versions. 3 Serious Intruders may be able to detect highly sensitive data, such as global system user lists. Payment Card Industry (PCI) Executive Report page 9
10 Payment Card Industry (PCI) Executive Report page 10
Payment Card Industry (PCI) Executive Report 11/01/2016
 Payment Card Industry (PCI) Executive Report 11/01/2016 ASV Scan Report Attestation of Scan Compliance Scan Customer Information Approved Scanning Vendor Information Company: Rural Computer Consultants
Payment Card Industry (PCI) Executive Report 11/01/2016 ASV Scan Report Attestation of Scan Compliance Scan Customer Information Approved Scanning Vendor Information Company: Rural Computer Consultants
Payment Card Industry (PCI) Technical Report 11/07/2017
 Payment Card Industry (PCI) Technical Report 11/07/2017 ASV Scan Report Attestation of Scan Compliance A1. Scan Customer Information A2. Approved Scanning Vendor Information Company: Allied Collection
Payment Card Industry (PCI) Technical Report 11/07/2017 ASV Scan Report Attestation of Scan Compliance A1. Scan Customer Information A2. Approved Scanning Vendor Information Company: Allied Collection
Merchant Certificate of Compliance
 Merchant Certificate of Compliance Awarded To: Consolid S.R.L. (55504923) Self - Assessment Questionnaire Passed: SAQ D, v3.2r1.1 Date Awarded: 03/01/2018 Most Recent Scan Date: 06/04/2018 Certificate
Merchant Certificate of Compliance Awarded To: Consolid S.R.L. (55504923) Self - Assessment Questionnaire Passed: SAQ D, v3.2r1.1 Date Awarded: 03/01/2018 Most Recent Scan Date: 06/04/2018 Certificate
Scan Report Executive Summary. Part 2. Component Compliance Summary Component (IP Address, domain, etc.):
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 02/18/2018 Scan expiration date: 05/19/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 02/18/2018 Scan expiration date: 05/19/2018 Part 2. Component
Scan Report Executive Summary
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 11/20/2017 Scan expiration date: 02/18/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 11/20/2017 Scan expiration date: 02/18/2018 Part 2. Component
Scan Report Executive Summary
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 08/28/2017 Scan expiration date: 11/26/2017 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 08/28/2017 Scan expiration date: 11/26/2017 Part 2. Component
EFFECTIVE VULNERABILITY MANAGEMENT USING QUALYSGUARD 1
 EFFECTIVE VULNERABILITY MANAGEMENT USING QUALYSGUARD 1 EFFECTIVE VULNERABILITY MANAGEMENT USING QUALYSGUARD ICTN 6823 BOYD AARON SIGMON EAST CAROLINA UNIVERSITY EFFECTIVE VULNERABILITY MANAGEMENT USING
EFFECTIVE VULNERABILITY MANAGEMENT USING QUALYSGUARD 1 EFFECTIVE VULNERABILITY MANAGEMENT USING QUALYSGUARD ICTN 6823 BOYD AARON SIGMON EAST CAROLINA UNIVERSITY EFFECTIVE VULNERABILITY MANAGEMENT USING
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Merchants Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission This
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Merchants Version 3.0 February 2014 Section 1: Assessment Information Instructions for Submission This
PCI Compliance Assessment Module with Inspector
 Quick Start Guide PCI Compliance Assessment Module with Inspector Instructions to Perform a PCI Compliance Assessment Performing a PCI Compliance Assessment (with Inspector) 2 PCI Compliance Assessment
Quick Start Guide PCI Compliance Assessment Module with Inspector Instructions to Perform a PCI Compliance Assessment Performing a PCI Compliance Assessment (with Inspector) 2 PCI Compliance Assessment
Scan Results May 29, 2012
 Scan Results May 29, 2012 Report Summary User Name: Roberto Chana Login Name: sebyt-rc Company: SELLBYTEL GROUP S.A User Role: Manager Address: Guitard 43, 3ra planta City: Barcelona State: ne Zip: 08014
Scan Results May 29, 2012 Report Summary User Name: Roberto Chana Login Name: sebyt-rc Company: SELLBYTEL GROUP S.A User Role: Manager Address: Guitard 43, 3ra planta City: Barcelona State: ne Zip: 08014
PCI Compliance. Network Scanning. Getting Started Guide
 PCI Compliance Getting Started Guide Qualys PCI provides businesses, merchants and online service providers with the easiest, most cost effective and highly automated way to achieve compliance with the
PCI Compliance Getting Started Guide Qualys PCI provides businesses, merchants and online service providers with the easiest, most cost effective and highly automated way to achieve compliance with the
Scan Report Executive Summary
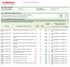 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire A-EP For use with PCI DSS Version 3.2.1 July 2018 Section 1: Assessment Information Instructions
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire A-EP For use with PCI DSS Version 3.2.1 July 2018 Section 1: Assessment Information Instructions
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire A For use with PCI DSS Version 3.2 Revision 1.1 January 2017 Section 1: Assessment Information
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire A For use with PCI DSS Version 3.2 Revision 1.1 January 2017 Section 1: Assessment Information
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance
 Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance Card-not-present Merchants, All Cardholder Data Functions Fully Outsourced For use with
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance Card-not-present Merchants, All Cardholder Data Functions Fully Outsourced For use with
Navigating the PCI DSS Challenge. 29 April 2011
 Navigating the PCI DSS Challenge 29 April 2011 Agenda 1. Overview of Threat and Compliance Landscape 2. Introduction to the PCI Security Standards 3. Payment Brand Compliance Programs 4. PCI DSS Scope
Navigating the PCI DSS Challenge 29 April 2011 Agenda 1. Overview of Threat and Compliance Landscape 2. Introduction to the PCI Security Standards 3. Payment Brand Compliance Programs 4. PCI DSS Scope
Scan Report Executive Summary. Part 2. Component Compliance Summary IP Address :
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 03/18/2015 Scan expiration date: 06/16/2015 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 03/18/2015 Scan expiration date: 06/16/2015 Part 2. Component
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 2006-2016 PCI Security Standards Council, LLC. All Rights Reserved.
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 2006-2016 PCI Security Standards Council, LLC. All Rights Reserved.
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Attestation of Compliance for Onsite Assessments Service Providers
 Attestation of Compliance Service Providers Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 2.0 October 2010 Instructions for
Attestation of Compliance Service Providers Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 2.0 October 2010 Instructions for
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance
 Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance Card-not-present Merchants, All Cardholder Data Functions Fully Outsourced For use with
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance Card-not-present Merchants, All Cardholder Data Functions Fully Outsourced For use with
Business Address: City: Calabasas State/Province: California City: Seattle State/Province: Washington
 Payment Card Industry (PCI) Technical Report 05/19/2017 ASV Scan Report Attestation of Scan Compliance Scan Customer Information Approved Scanning Vendor Information Company: 1099 Pro, Inc. Company: Moss
Payment Card Industry (PCI) Technical Report 05/19/2017 ASV Scan Report Attestation of Scan Compliance Scan Customer Information Approved Scanning Vendor Information Company: 1099 Pro, Inc. Company: Moss
Section 1: Assessment Information
 Section 1: Assessment Information Instructions for Submission This document must be completed as a declaration of the results of the merchant s self-assessment with the Payment Card Industry Data Security
Section 1: Assessment Information Instructions for Submission This document must be completed as a declaration of the results of the merchant s self-assessment with the Payment Card Industry Data Security
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
ForeScout Extended Module for Qualys VM
 ForeScout Extended Module for Qualys VM Version 1.2.1 Table of Contents About the Qualys VM Integration... 3 Additional Qualys VM Documentation... 3 About This Module... 3 Components... 4 Considerations...
ForeScout Extended Module for Qualys VM Version 1.2.1 Table of Contents About the Qualys VM Integration... 3 Additional Qualys VM Documentation... 3 About This Module... 3 Components... 4 Considerations...
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire D Version 3.2 Section 1: Assessment Information Instructions for Submission This document
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire D Version 3.2 Section 1: Assessment Information Instructions for Submission This document
Scan Report Executive Summary
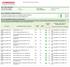 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 06/08/2018 Scan expiration date: 09/06/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 06/08/2018 Scan expiration date: 09/06/2018 Part 2. Component
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2.1 June 2018 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2.1 June 2018 Section 1: Assessment Information Instructions for Submission
INFORMATION SUPPLEMENT. Use of SSL/Early TLS for POS POI Terminal Connections. Date: June 2018 Author: PCI Security Standards Council
 Use of SSL/Early TLS for POS POI Terminal Connections Date: Author: PCI Security Standards Council Table of Contents Introduction...1 Executive Summary...1 What is the risk?...1 What is meant by Early
Use of SSL/Early TLS for POS POI Terminal Connections Date: Author: PCI Security Standards Council Table of Contents Introduction...1 Executive Summary...1 What is the risk?...1 What is meant by Early
PROTECTING INFORMATION ASSETS NETWORK SECURITY
 PROTECTING INFORMATION ASSETS NETWORK SECURITY PAUL SMITH 20 years of IT experience (desktop, servers, networks, firewalls.) 17 years of engineering in enterprise scaled networks 10+ years in Network Security
PROTECTING INFORMATION ASSETS NETWORK SECURITY PAUL SMITH 20 years of IT experience (desktop, servers, networks, firewalls.) 17 years of engineering in enterprise scaled networks 10+ years in Network Security
Scan Report Executive Summary. Part 2. Component Compliance Summary Component (IP Address, domain, etc.):ekk.worldtravelink.com
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Travolutionary ASV Company: Comodo CA Limited 10-03-2018 Scan expiration date: 01-01-2019 Part 2.
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Travolutionary ASV Company: Comodo CA Limited 10-03-2018 Scan expiration date: 01-01-2019 Part 2.
Vulnerability Validation Tutorial
 Vulnerability Validation Tutorial Last updated 01/07/2014-4.8 Vulnerability scanning plays a key role in the vulnerability management process. It helps you find potential vulnerabilities so that you can
Vulnerability Validation Tutorial Last updated 01/07/2014-4.8 Vulnerability scanning plays a key role in the vulnerability management process. It helps you find potential vulnerabilities so that you can
PCI DSS 3.2 AWARENESS NOVEMBER 2017
 PCI DSS 3.2 AWARENESS NOVEMBER 2017 1 AGENDA PCI STANDARD OVERVIEW PAYMENT ENVIRONMENT 2ACTORS PCI ROLES AND RESPONSIBILITIES MERCHANTS COMPLIANCE PROGRAM PCI DSS 3.2 REQUIREMENTS 2 PCI STANDARD OVERVIEW
PCI DSS 3.2 AWARENESS NOVEMBER 2017 1 AGENDA PCI STANDARD OVERVIEW PAYMENT ENVIRONMENT 2ACTORS PCI ROLES AND RESPONSIBILITIES MERCHANTS COMPLIANCE PROGRAM PCI DSS 3.2 REQUIREMENTS 2 PCI STANDARD OVERVIEW
90% 191 Security Best Practices. Blades. 52 Regulatory Requirements. Compliance Report PCI DSS 2.0. related to this regulation
 Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on April 16, 2018 15:41 PM O verview 1 90% Compliance About PCI DSS 2.0 PCI-DSS is a legal obligation mandated not by government
Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on April 16, 2018 15:41 PM O verview 1 90% Compliance About PCI DSS 2.0 PCI-DSS is a legal obligation mandated not by government
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Document2 Section 1: Assessment Information Instructions for
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Document2 Section 1: Assessment Information Instructions for
IBM Managed Security Services - Vulnerability Scanning
 Service Description IBM Managed Security Services - Vulnerability Scanning This Service Description describes the Service IBM provides to Client. 1.1 Service IBM Managed Security Services - Vulnerability
Service Description IBM Managed Security Services - Vulnerability Scanning This Service Description describes the Service IBM provides to Client. 1.1 Service IBM Managed Security Services - Vulnerability
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire D Service Providers For use with PCI DSS Version 3.2 Revision 1.1 January 2017 Section 1:
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire D Service Providers For use with PCI DSS Version 3.2 Revision 1.1 January 2017 Section 1:
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire P2PE For use with PCI DSS Version 3.2.1 July 2018 Section 1: Assessment Information Instructions
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Self-Assessment Questionnaire P2PE For use with PCI DSS Version 3.2.1 July 2018 Section 1: Assessment Information Instructions
Comodo HackerGuardian. PCI Security Compliance The Facts. What PCI security means for your business
 Comodo HackerGuardian PCI Security Compliance The Facts What PCI security means for your business Overview The Payment Card Industry Data Security Standard (PCI DSS) is a set of 12 requirements intended
Comodo HackerGuardian PCI Security Compliance The Facts What PCI security means for your business Overview The Payment Card Industry Data Security Standard (PCI DSS) is a set of 12 requirements intended
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance
 Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance Card-not-present Merchants, All Cardholder Data Functions Fully Outsourced For use with
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance Card-not-present Merchants, All Cardholder Data Functions Fully Outsourced For use with
Tenable.io User Guide. Last Revised: November 03, 2017
 Tenable.io User Guide Last Revised: November 03, 2017 Table of Contents Tenable.io User Guide 1 Getting Started with Tenable.io 10 Tenable.io Workflow 12 System Requirements 15 Scanners and Agents 16 Link
Tenable.io User Guide Last Revised: November 03, 2017 Table of Contents Tenable.io User Guide 1 Getting Started with Tenable.io 10 Tenable.io Workflow 12 System Requirements 15 Scanners and Agents 16 Link
Network Vulnerability Scan
 Network Vulnerability Scan Aug 28, 2018 Ethnio, Inc. 6121 W SUNSET BLVD LOS angeles, CA 90028 Tel (888) 879-7439 ETHN.io Summary Ethnio conducts ongoing network vulnerability scans using both Qualys and
Network Vulnerability Scan Aug 28, 2018 Ethnio, Inc. 6121 W SUNSET BLVD LOS angeles, CA 90028 Tel (888) 879-7439 ETHN.io Summary Ethnio conducts ongoing network vulnerability scans using both Qualys and
PCI DSS COMPLIANCE 101
 PCI DSS COMPLIANCE 101 Pavel Kaminsky PCI QSA, CISSP, CISA, CEH, Head of Operations at Seven Security Group Information Security Professional, Auditor, Pentester SEVEN SECURITY GROUP PCI QSA Сompany Own
PCI DSS COMPLIANCE 101 Pavel Kaminsky PCI QSA, CISSP, CISA, CEH, Head of Operations at Seven Security Group Information Security Professional, Auditor, Pentester SEVEN SECURITY GROUP PCI QSA Сompany Own
Carbon Black PCI Compliance Mapping Checklist
 Carbon Black PCI Compliance Mapping Checklist The following table identifies selected PCI 3.0 requirements, the test definition per the PCI validation plan and how Carbon Black Enterprise Protection and
Carbon Black PCI Compliance Mapping Checklist The following table identifies selected PCI 3.0 requirements, the test definition per the PCI validation plan and how Carbon Black Enterprise Protection and
Hands-On Ethical Hacking and Network Defense
 Hands-On Ethical Hacking and Network Defense Chapter 2 TCP/IP Concepts Review Last modified 1-11-17 Objectives Describe the TCP/IP protocol stack Explain the basic concepts of IP addressing Explain the
Hands-On Ethical Hacking and Network Defense Chapter 2 TCP/IP Concepts Review Last modified 1-11-17 Objectives Describe the TCP/IP protocol stack Explain the basic concepts of IP addressing Explain the
PCI COMPLIANCE IS NO LONGER OPTIONAL
 PCI COMPLIANCE IS NO LONGER OPTIONAL YOUR PARTICIPATION IS MANDATORY To protect the data security of your business and your customers, the credit card industry introduced uniform Payment Card Industry
PCI COMPLIANCE IS NO LONGER OPTIONAL YOUR PARTICIPATION IS MANDATORY To protect the data security of your business and your customers, the credit card industry introduced uniform Payment Card Industry
Chapter 5: Vulnerability Analysis
 Chapter 5: Vulnerability Analysis Technology Brief Vulnerability analysis is a part of the scanning phase. In the Hacking cycle, vulnerability analysis is a major and important part. In this chapter, we
Chapter 5: Vulnerability Analysis Technology Brief Vulnerability analysis is a part of the scanning phase. In the Hacking cycle, vulnerability analysis is a major and important part. In this chapter, we
Basics of executing a penetration test
 Basics of executing a penetration test 25.04.2013, WrUT BAITSE guest lecture Bernhards Blumbergs, CERT.LV Outline Reconnaissance and footprinting Scanning and enumeration System exploitation Outline Reconnaisance
Basics of executing a penetration test 25.04.2013, WrUT BAITSE guest lecture Bernhards Blumbergs, CERT.LV Outline Reconnaissance and footprinting Scanning and enumeration System exploitation Outline Reconnaisance
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Question No: 1 After running a packet analyzer on the network, a security analyst has noticed the following output:
 Volume: 75 Questions Question No: 1 After running a packet analyzer on the network, a security analyst has noticed the following output: Which of the following is occurring? A. A ping sweep B. A port scan
Volume: 75 Questions Question No: 1 After running a packet analyzer on the network, a security analyst has noticed the following output: Which of the following is occurring? A. A ping sweep B. A port scan
Section 1: Assessment Information
 Section 1: Assessment Information Instructions for Submission This document must be completed as a declaration of the results of the merchant s self-assessment with the Payment Card Industry Data Security
Section 1: Assessment Information Instructions for Submission This document must be completed as a declaration of the results of the merchant s self-assessment with the Payment Card Industry Data Security
Qualified Integrators and Resellers (QIR) TM. QIR Implementation Statement, v2.0
 Qualified Integrators and Resellers (QIR) TM Implementation Statement For each Qualified Installation performed, the QIR Employee must complete this document and confirm whether the Validated Payment Application
Qualified Integrators and Resellers (QIR) TM Implementation Statement For each Qualified Installation performed, the QIR Employee must complete this document and confirm whether the Validated Payment Application
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0
 Payment Card Industry (PCI) Dataa Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 Section 1: Assessment Information Instructions for Submission This Attestation
Payment Card Industry (PCI) Dataa Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.0 Section 1: Assessment Information Instructions for Submission This Attestation
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2.1 June 2018 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2.1 June 2018 Section 1: Assessment Information Instructions for Submission
Payment Card Industry Data Security Standards Version 1.1, September 2006
 Payment Card Industry Data Security Standards Version 1.1, September 2006 Carl Grayson Agenda Overview of PCI DSS Compliance Levels and Requirements PCI DSS v1.1 in More Detail Discussion, Questions and
Payment Card Industry Data Security Standards Version 1.1, September 2006 Carl Grayson Agenda Overview of PCI DSS Compliance Levels and Requirements PCI DSS v1.1 in More Detail Discussion, Questions and
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2.1 June 2018 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2.1 June 2018 Section 1: Assessment Information Instructions for Submission
Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition. Chapter 3 Investigating Web Attacks
 Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition Chapter 3 Investigating Web Attacks Objectives After completing this chapter, you should be able to: Recognize the indications
Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition Chapter 3 Investigating Web Attacks Objectives After completing this chapter, you should be able to: Recognize the indications
Payment Card Industry (PCI) Data Security Standard. Summary of Changes from PCI DSS Version to 2.0
 Payment Card Industry (PCI) Data Security Standard Summary of s from PCI DSS Version 1.2.1 to 2.0 October 2010 General General Throughout Removed specific references to the Glossary as references are generally
Payment Card Industry (PCI) Data Security Standard Summary of s from PCI DSS Version 1.2.1 to 2.0 October 2010 General General Throughout Removed specific references to the Glossary as references are generally
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
User Interface. An Introductory Guide
 User Interface An Introductory Guide Last update: 18 May 2017 Index Introduction 3 Vulnerability Database 4 Overview 5 Targets 6 Findings 7 Vulnerability Details 8 Risk Acceptance 9 Network Interface Configuration
User Interface An Introductory Guide Last update: 18 May 2017 Index Introduction 3 Vulnerability Database 4 Overview 5 Targets 6 Findings 7 Vulnerability Details 8 Risk Acceptance 9 Network Interface Configuration
Offensive Technologies
 University of Amsterdam System and Network Engineering Offensive Technologies OS3 Network Security Assessment Students: Peter van Bolhuis Kim van Erkelens June 1, 2014 Executive Summary Being a security
University of Amsterdam System and Network Engineering Offensive Technologies OS3 Network Security Assessment Students: Peter van Bolhuis Kim van Erkelens June 1, 2014 Executive Summary Being a security
What are PCI DSS? PCI DSS = Payment Card Industry Data Security Standards
 PCI DSS What are PCI DSS? PCI DSS = Payment Card Industry Data Security Standards Definition: A multifaceted security standard that includes requirements for security management, policies, procedures,
PCI DSS What are PCI DSS? PCI DSS = Payment Card Industry Data Security Standards Definition: A multifaceted security standard that includes requirements for security management, policies, procedures,
ch02 True/False Indicate whether the statement is true or false.
 ch02 True/False Indicate whether the statement is true or false. 1. No matter what medium connects computers on a network copper wires, fiber-optic cables, or a wireless setup the same protocol must be
ch02 True/False Indicate whether the statement is true or false. 1. No matter what medium connects computers on a network copper wires, fiber-optic cables, or a wireless setup the same protocol must be
CSE 565 Computer Security Fall 2018
 CSE 565 Computer Security Fall 2018 Lecture 19: Intrusion Detection Department of Computer Science and Engineering University at Buffalo 1 Lecture Outline Intruders Intrusion detection host-based network-based
CSE 565 Computer Security Fall 2018 Lecture 19: Intrusion Detection Department of Computer Science and Engineering University at Buffalo 1 Lecture Outline Intruders Intrusion detection host-based network-based
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance
 Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance No Electronic Storage, Processing, or Transmission of Cardholder Data Version 1.2 October
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance No Electronic Storage, Processing, or Transmission of Cardholder Data Version 1.2 October
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
University of Maine System Payment Card Industry Data Security Standard (PCI DSS) Guide for Completing Self Assessment Questionnaire (SAQ) SAQ C
 University of Maine System Payment Card Industry Data Security Standard (PCI DSS) Guide for Completing Self Assessment Questionnaire (SAQ) SAQ C All university merchant departments accepting credit cards
University of Maine System Payment Card Industry Data Security Standard (PCI DSS) Guide for Completing Self Assessment Questionnaire (SAQ) SAQ C All university merchant departments accepting credit cards
Site Data Protection (SDP) Program Update
 Advanced Payments October 9, 2006 Site Data Protection (SDP) Program Update Agenda Security Landscape PCI Security Standards Council SDP Program October 9, 2006 SDP Program Update 2 Security Landscape
Advanced Payments October 9, 2006 Site Data Protection (SDP) Program Update Agenda Security Landscape PCI Security Standards Council SDP Program October 9, 2006 SDP Program Update 2 Security Landscape
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.1 April 2015 Section 1: Assessment Information Instructions for Submission
PCI DSS v3. Justin
 PCI DSS v3 Justin Leapline justin.leapline@giftcards.com @jmleapline My Experience With PCI Just to lay the groundwork Currently work at Largest ecommerce in Pittsburgh My experience includes: QSA Acquirer
PCI DSS v3 Justin Leapline justin.leapline@giftcards.com @jmleapline My Experience With PCI Just to lay the groundwork Currently work at Largest ecommerce in Pittsburgh My experience includes: QSA Acquirer
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Your guide to the Payment Card Industry Data Security Standard (PCI DSS) banksa.com.au
 Your guide to the Payment Card Industry Data Security Standard (PCI DSS) 1 13 13 76 banksa.com.au CONTENTS Page Contents 1 Introduction 2 What are the 12 key requirements of PCIDSS? 3 Protect your business
Your guide to the Payment Card Industry Data Security Standard (PCI DSS) 1 13 13 76 banksa.com.au CONTENTS Page Contents 1 Introduction 2 What are the 12 key requirements of PCIDSS? 3 Protect your business
Blueprint for PCI Compliance with Network Detective
 Blueprint for PCI Compliance with Network Detective WHITEPAPER by Win Pham, RapidFire Tools VP Development Copyright 2017 RapidFire Tools, Inc. All rights reserved. Table of Contents Target Audience...
Blueprint for PCI Compliance with Network Detective WHITEPAPER by Win Pham, RapidFire Tools VP Development Copyright 2017 RapidFire Tools, Inc. All rights reserved. Table of Contents Target Audience...
PrecisionAccess Trusted Access Control
 Data Sheet PrecisionAccess Trusted Access Control Defeats Cyber Attacks Credential Theft: Integrated MFA defeats credential theft. Server Exploitation: Server isolation defeats server exploitation. Compromised
Data Sheet PrecisionAccess Trusted Access Control Defeats Cyber Attacks Credential Theft: Integrated MFA defeats credential theft. Server Exploitation: Server isolation defeats server exploitation. Compromised
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments - Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments - Service Providers Version 3.2 April 2016 Section 1: Assessment Information Instructions for Submission
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Requirements and Security Assessment Procedures Version 2.0 October 2010 Document Changes Date Version Description Pages October 2008 July 2009 October
Payment Card Industry (PCI) Data Security Standard Requirements and Security Assessment Procedures Version 2.0 October 2010 Document Changes Date Version Description Pages October 2008 July 2009 October
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire C-VT and Attestation of Compliance
 Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire C-VT and Attestation of Compliance Merchants with Web-Based Virtual Payment Terminals No Electronic Cardholder Data Storage
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire C-VT and Attestation of Compliance Merchants with Web-Based Virtual Payment Terminals No Electronic Cardholder Data Storage
PCI DSS Compliance. Verba SOLUTION GUIDE. Introduction. Verba and the Payment Card Industry Data Security Standard
 Introduction Verba provides a complete compliance solution for merchants and service providers who accept and/or process payment card data over the telephone. Secure and compliant handling of a customer
Introduction Verba provides a complete compliance solution for merchants and service providers who accept and/or process payment card data over the telephone. Secure and compliant handling of a customer
Cogeco Peer 1 PCI DSS Compliance. Overview
 Cogeco Peer 1 PCI DSS Compliance Overview Cogeco Peer 1 provides Payment Card Industry Data Security Standards (PCI DSS) compliant Managed Hosting in select datacenters, facilitated by the availability
Cogeco Peer 1 PCI DSS Compliance Overview Cogeco Peer 1 provides Payment Card Industry Data Security Standards (PCI DSS) compliant Managed Hosting in select datacenters, facilitated by the availability
Easy-to-Use PCI Kit to Enable PCI Compliance Audits
 Easy-to-Use PCI Kit to Enable PCI Compliance Audits Version 2.0 and Above Table of Contents Executive Summary... 3 About This Guide... 3 What Is PCI?... 3 ForeScout CounterACT... 3 PCI Requirements Addressed
Easy-to-Use PCI Kit to Enable PCI Compliance Audits Version 2.0 and Above Table of Contents Executive Summary... 3 About This Guide... 3 What Is PCI?... 3 ForeScout CounterACT... 3 PCI Requirements Addressed
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire B and Attestation of Compliance
 Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire B and Attestation of Compliance Merchants with Only Imprint Machines or Only Standalone, Dial-out Terminals Electronic Cardholder
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire B and Attestation of Compliance Merchants with Only Imprint Machines or Only Standalone, Dial-out Terminals Electronic Cardholder
Self-Assessment Questionnaire A
 Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance All cardholder data functions outsourced. No Electronic Storage, Processing, or Transmission
Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire A and Attestation of Compliance All cardholder data functions outsourced. No Electronic Storage, Processing, or Transmission
VANGUARD WHITE PAPER VANGUARD INSURANCE INDUSTRY WHITEPAPER
 VANGUARD INSURANCE INDUSTRY WHITEPAPER Achieving PCI DSS Compliance with Vanguard Integrity Professionals Software & Professional Services Vanguard is the industry leader in z/os Mainframe Software to
VANGUARD INSURANCE INDUSTRY WHITEPAPER Achieving PCI DSS Compliance with Vanguard Integrity Professionals Software & Professional Services Vanguard is the industry leader in z/os Mainframe Software to
Security Assessment. Prepared For: Prospect Or Customer Prepared By: Your Company Name
 Security Assessment Prepared For: Prospect Or Customer Prepared By: Your Company Name Agenda Security - External & Outbound - Policy Compliance Risk and Issue Score Issue Review Next Steps Security - External
Security Assessment Prepared For: Prospect Or Customer Prepared By: Your Company Name Agenda Security - External & Outbound - Policy Compliance Risk and Issue Score Issue Review Next Steps Security - External
Certified Vulnerability Assessor
 Certified Vulnerability Assessor COURSE BENEFITS Course Title:Certified Vulnerability Assessor Duration: 3Day Language: English Class Format Options: Instructor-led classroom Live Online Training Prerequisites:
Certified Vulnerability Assessor COURSE BENEFITS Course Title:Certified Vulnerability Assessor Duration: 3Day Language: English Class Format Options: Instructor-led classroom Live Online Training Prerequisites:
EC-Council Certified Network Defender (CND) Duration: 5 Days Method: Instructor-Led
 EC-Council Certified Network Defender (CND) Duration: 5 Days Method: Instructor-Led Certification: Certified Network Defender Exam: 312-38 Course Description This course is a vendor-neutral, hands-on,
EC-Council Certified Network Defender (CND) Duration: 5 Days Method: Instructor-Led Certification: Certified Network Defender Exam: 312-38 Course Description This course is a vendor-neutral, hands-on,
Network Security. Kitisak Jirawannakool Electronics Government Agency (public organisation)
 1 Network Security Kitisak Jirawannakool Electronics Government Agency (public organisation) A Brief History of the World 2 OSI Model vs TCP/IP suite 3 TFTP & SMTP 4 ICMP 5 NAT/PAT 6 ARP/RARP 7 DHCP 8
1 Network Security Kitisak Jirawannakool Electronics Government Agency (public organisation) A Brief History of the World 2 OSI Model vs TCP/IP suite 3 TFTP & SMTP 4 ICMP 5 NAT/PAT 6 ARP/RARP 7 DHCP 8
WHITE PAPERS. INSURANCE INDUSTRY (White Paper)
 (White Paper) Achieving PCI DSS Compliance with Vanguard Integrity Professionals Software & Professional Services Vanguard is the industry leader in z/os Mainframe Software to ensure enterprise compliance
(White Paper) Achieving PCI DSS Compliance with Vanguard Integrity Professionals Software & Professional Services Vanguard is the industry leader in z/os Mainframe Software to ensure enterprise compliance
Scanning. Course Learning Outcomes for Unit III. Reading Assignment. Unit Lesson UNIT III STUDY GUIDE
 UNIT III STUDY GUIDE Course Learning Outcomes for Unit III Upon completion of this unit, students should be able to: 1. Recall the terms port scanning, network scanning, and vulnerability scanning. 2.
UNIT III STUDY GUIDE Course Learning Outcomes for Unit III Upon completion of this unit, students should be able to: 1. Recall the terms port scanning, network scanning, and vulnerability scanning. 2.
Firewall Configuration and Management Policy
 Firewall Configuration and Management Policy Version Date Change/s Author/s Approver/s 1.0 01/01/2013 Initial written policy. Kyle Johnson Dean of Information Services Executive Director for Compliance
Firewall Configuration and Management Policy Version Date Change/s Author/s Approver/s 1.0 01/01/2013 Initial written policy. Kyle Johnson Dean of Information Services Executive Director for Compliance
Specialized Security Services, Inc. REDUCE RISK WITH CONFIDENCE. s3security.com
 Specialized Security Services, Inc. REDUCE RISK WITH CONFIDENCE s3security.com Security Professional Services S3 offers security services through its Security Professional Services (SPS) group, the security-consulting
Specialized Security Services, Inc. REDUCE RISK WITH CONFIDENCE s3security.com Security Professional Services S3 offers security services through its Security Professional Services (SPS) group, the security-consulting
Customer Compliance Portal. User Guide V2.0
 Customer Compliance Portal User Guide V2.0 0 Copyright 2016 Merchant Preservation Services, LLC. All rights reserved. CampusGuard, the Merchant Preservation Services logo, and the CampusGuard logo are
Customer Compliance Portal User Guide V2.0 0 Copyright 2016 Merchant Preservation Services, LLC. All rights reserved. CampusGuard, the Merchant Preservation Services logo, and the CampusGuard logo are
