Cisco WCS Server Hardening
|
|
|
- Gabriella Freeman
- 5 years ago
- Views:
Transcription
1 APPENDIXD This appendix provides an instructional checklist for hardening a WCS server. Ideally, the goal of a hardened server is to leave it exposed on the Internet without any other form of protection. This appendix describes the hardening of WCS, which requires some services and processes exposed to function properly. Think of it as WCS Best Practices. Hardening of WCS will involve disabling unnecessary services, removing and modifying registrykey entries, and applying appropriate restrictive permissions to files, services, and end points. This appendix contains the following sections:, page D-1 Tomcat Shutdown Prevention, page D-10 WCS Password Handling, page D-10 Setting Up SSL Certification, page D-11 Web servers provide data through an externally or publicly exposed interface, this is a well-known target for exploitation. Unprotected web servers provide an avenue for malicious activity, such as theft or the denial of service to an organization's resources. A Non-Privileged account allows you to work as a normal account and launching applications or tools using the credentials of a different account (most likely your administrator account). In Linux, you need not run WCS as a Non-Privileged Account as Linux starts as root to port 80 and then switches effective userid to nobody. Creating a Non-Privileged User To create a Non-Privileged User, follow these steps: Step 1 Create a new user by choosing Administrator Tools > Computer Management or right-click My Computer > Manage from the drop-down list. You will see the Computer Management window. (See Figure D-1) D-1
2 Figure D-1 Computer Management Step 2 Click Local users and Groups and click the Users folder. Right-click in the right pane and click "New User". (See Figure D-2) D-2
3 Figure D-2 Local Users and Groups Step 3 In the New User dialog box, type in your preferences for a new user name and password (this will be your secondary Administrator account). For example, use wcsuser is the username and wcsuser is the password. Click Create. (See Figure D-3) Figure D-3 New User D-3
4 Step 4 You need to add the new user to a group. Expand the Local Users and Groups option, right-click the groups and select the New Group option. Use wcsgroup as the groupname, and click Add, and select wcsuser.(see Figure D-4) Figure D-4 New Group Step 5 To provide permission for wcs group, you need to go to specific WCS installation path, add wcsgroup on the Security tab, and select permissions for wcsgroup. D-4
5 Figure D-5 Adding a group into security Step 6 Add Log on service rights for wcsgroup by running secpol.msc from start run command-line. That is, In the Local Security Settings window, select Local Policies > User Rights Assignment and double-click the Log on as as service policy. Add wcsgroup to this policy. (See Figure D-6) D-5
6 Figure D-6 Local Security Settings Step 7 Step 8 Edit the wrapper.conf file located at C:\Program Files\WCSx.xx.x\webnms\conf in your machine or appropriate directory in your setup: wrapper.ntservice.account=wcs-nms-1\wcsuser wrapper.ntservice.password=wcsuser Execute the below scripts for install services with new wcsuser account settings. (See Figure D-7): C:\Program Files\WCS \bin\UninstallService.bat C:\Program Files\WCS \bin\InstallService.bat D-6
7 Figure D-7 Install Services Step 9 Change the Properties of WCS Installation directories and files under it to wcsgroup on the Security tab for read, execute, and modify (See Figure D-8): Figure D-8 Security Tab for WCS Installation Folder D-7
8 Step 10 Open the registry editor from the run command-line and provide the permission for Javasoft directory to wcsgroup users to the read execute and write Javasoft directory (See Figure D-9): Figure D-9 Registry Editor Step 11 Open PackagingResources.properties file in <WCS_HOME>\webnms\classes\com\cisco\packaging directory, search for "NonPrivUser" attribute,and change it to true (See Figure D-11): D-8
9 Figure D-10 PackagingResources.properties Step 12 Restart the WCS server again from the services window (See Figure D-11): Figure D-11 Starting WCS Service D-9
10 Tomcat Shutdown Prevention Tomcat Shutdown Prevention On Windows, the file which controls the web service is the Server.xml file. Read and Write or Full Control access to this file is to be limited to the SA, Web Manager or Web Manager's designees. Tomcat can be shut down maliciously by any user with a browser. Tomcat uses port 8005 for its remote shutdown sequence command. So, the line Server port="8005" shutdown="shutdown" debug="0" in server.xml should be modified to have some other string than "SHUTDOWN". This string must be modifed to C15C0WC5. The File permissions for server.xml is the full control, read/write access is given to Administrator only. Others have only read and read/execute permissions. WCS Password Handling You can configure additional authentication by configuring the Local Password Policy parameters. Select the check boxes if you want the configurations to be enabled. Figure D-12 Local PAssword Policy D-10
11 Setting Up SSL Certification The following configurations are added for additional authentication: You can configure that the password cannot be reused until N number of new passwords are used. This figure is configurable. You can configure that the passoword cannot be changed for a minimum interval of 24 hours from last change. You can configure locking of an account if X number of attempts failed. The X figure is configurable. You can configure whether you want the account to be disabled or not if it is unused for 30 days. You can configure the expiry time of the password. This is confiurable and the unit is in days. You can configiure to enforce a user to change the password on first login. Setting Up SSL Certification The Secure Sockets Layer (SSL) Certification is to ensure secure transactions between a web server and the browsers. Installing the DoD Certificates will allow your Web browser to trust the identity and provide secure communications which are authenticated by Department of Defense (DoD). These certificates are used to validate the identity of the server or web site and are used to generate the encryption key used in the SSL. This encryption protects the information being passed between the server and the client. This section describes the SSL Certification and contains the following topics: Setting Up SSL Client Certification, page D-11 Setting Up SSL Server Certification, page D-12 Setting Up SSL Client Certification To setup the SSL Client Certificate Authentication using DoD certificates, follow these steps: As a prerequisite, to create the SSL Certificates, you would require KeyTool available in JDK. KeyTool is a command line tool to manage keystores and the certificates. Step 1 Create SSL Client Certificate using the following command: % keytool -genkey -keystore nmsclientkeystore -storetype pkcs12 -keyalg RSA -keysize alias nmsclient -dname "CN=nmsclient, OU=WNBU, O=Cisco, L=San Jose, ST=CA, C=US" -storepass nmskeystore Provide the Key Algorithm as RSA and KeySize as 1024 or Step 2 Generate the Certificate Signing Request (CSR) using the following command: % keytool -certreq -keyalg RSA -keysize alias nmsclient -keystore nmsclientkeystore -storetype pkcs12 -file <csrfilename> Provide the Key Algorithm as RSA and KeySize as 1024 or 2048 and provide a certificate file name. D-11
12 Setting Up SSL Certification Step 3 Send the generated CSR file to DoD. The DoD will issue the corresponding signed certificates. The CSR reply is through dod.p7b file. In addition you should also receive the root CA certificates. Please makes sure to retrieve the PKCS7 encoded certificates; Certificate Authorities provide an option to get the PKCS7 encoded certificates. Step 4 Step 5 Import the CSR reply in the Keystore using the command: % keytool -import dod.p7b -keystore nmsclientkeystore -storetype pkcs12 -storepass nmskeystore Check the formats of root CA certificates recieved, they must be base 64 encoded. If they are not base 64 encoded, use the OpenSSL command to convert them to base 64 encoded format. % openssl x509 -in rootca.cer -inform DER -outform PEM -outfile rootca.crt % openssl x509 -in DoD-sub.cer -inform DER -outform PEM -outfile rootca.crt Convert both root CA certificate and sub-ordinate certificates recieved. In case you recieved both root CA certificate and the sub-ordinate certificate, you must bundle them together using the below command: % cat DoD-sub.crt > ca-bundle.crt % cat DoD-rootCA.crt >> ca-bundle.crt Step 6 To setup SSL Client Authentication using these certificates, enable SSL Client Authentication in Apache in the ssl.conf file located in <WCS_Home>/webnms/apache/ssl/backup/ folder. SSLCACertificationPath conf/ssl.crt SSLCACertificationFile conf/ssl.crt/ca-bundle.crt SSLVerifyClient require SSLVerifyDepth 2 SSLVerifyDepth will depend of the level of Certificate Chain. In case you have only 1 root CA certificate, this should be set to 1. In case you have a certificate chain (root CA and subordinate CA), this should be set to 2. Step 7 Step 8 Install the DoD root CA certificates in WCS. Import the nmsclientkeystore in your browser. Setting Up SSL Server Certification To setup the SSL Server Certificate using DoD certificates, follow these steps: Step 1 Generate the Certificate Signing Request (CSR). % keyadmin -newdn genkey <csrfilename> D-12
13 Setting Up SSL Certification Step 2 Send the generated CSR file to DoD. The DoD will issue the corresponding signed certificates. The CSR reply is through dod.p7b file. In addition you should also receive the root CA certificates. Please makes sure to retrieve the PKCS7 encoded certificates; Certificate Authorities provide an option to get the PKCS7 encoded certificates. Step 3 Import the Signed Certificate using the below command in the Keytool: % keyadmin -importsignedcert <dod.p7> The certificate and the key are stored at <WCS_Home>/webnms/apache/conf/ssl.crt. D-13
14 Setting Up SSL Certification D-14
Configure the Prime Infrastructure Server
 View the Prime Infrastructure Server Configuration, page 2 Available System Settings, page 2 Secure the Connectivity of the Prime Infrastructure Server, page 9 MIB to Prime Infrastructure Alert/Event Mapping,
View the Prime Infrastructure Server Configuration, page 2 Available System Settings, page 2 Secure the Connectivity of the Prime Infrastructure Server, page 9 MIB to Prime Infrastructure Alert/Event Mapping,
Configure the Prime Infrastructure Server
 View the Prime Infrastructure Server Configuration, on page 1 Available System Settings, on page 2 Secure the Connectivity of the Prime Infrastructure Server, on page 7 MIB to Prime Infrastructure Alert/Event
View the Prime Infrastructure Server Configuration, on page 1 Available System Settings, on page 2 Secure the Connectivity of the Prime Infrastructure Server, on page 7 MIB to Prime Infrastructure Alert/Event
Public Key Enabling Oracle Weblogic Server
 DoD Public Key Enablement (PKE) Reference Guide Public Key Enabling Oracle Weblogic Server Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke URL: http://iase.disa.smil.mil/pki-pke Public Key Enabling
DoD Public Key Enablement (PKE) Reference Guide Public Key Enabling Oracle Weblogic Server Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke URL: http://iase.disa.smil.mil/pki-pke Public Key Enabling
SSL/TLS Certificate Generation
 SSL/TLS Certificate Generation Target: Lightstreamer Server v. 7.0 or greater Last updated: 16/02/2018 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion
SSL/TLS Certificate Generation Target: Lightstreamer Server v. 7.0 or greater Last updated: 16/02/2018 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion
SSL/TLS Certificate Generation
 SSL/TLS Certificate Generation Last updated: 11/01/2016 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion of an Existing Certificate Chain Available
SSL/TLS Certificate Generation Last updated: 11/01/2016 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion of an Existing Certificate Chain Available
SSL/TLS Certificate Generation
 SSL/TLS Certificate Generation Target: Lightstreamer Server v. 7.0 or greater Last updated: 08/03/2018 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion
SSL/TLS Certificate Generation Target: Lightstreamer Server v. 7.0 or greater Last updated: 08/03/2018 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion
FortiNAC. Analytics SSL Certificates. Version: 5.x Date: 8/28/2018. Rev: D
 FortiNAC Analytics SSL Certificates Version: 5.x Date: 8/28/2018 Rev: D 1 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET KNOWLEDGE BASE http://kb.fortinet.com
FortiNAC Analytics SSL Certificates Version: 5.x Date: 8/28/2018 Rev: D 1 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET KNOWLEDGE BASE http://kb.fortinet.com
Prepaid Online Vending System. XMLVend 2.1 Test Suite Setup Instructions
 Prepaid Online Vending System XMLVend 2.1 Test Suite Setup Instructions Contents SOFTWARE REQUIRED... 5 SETUP JAVA JDK... 5 TOMCAT SETUP FOR XML... 6 INTERCEPTOR... 8 SETTING UP SSL... 9 SETTING UP THE
Prepaid Online Vending System XMLVend 2.1 Test Suite Setup Instructions Contents SOFTWARE REQUIRED... 5 SETUP JAVA JDK... 5 TOMCAT SETUP FOR XML... 6 INTERCEPTOR... 8 SETTING UP SSL... 9 SETTING UP THE
IEA 2048 Bit Key Support for CSR on IEA Configuration Example
 IEA 2048 Bit Key Support for CSR on IEA Configuration Example Document ID: 117964 Contributed by Kishore Yerramreddy, Cisco TAC Engineer. Jul 16, 2014 Contents Introduction Configure Generate a Certificate
IEA 2048 Bit Key Support for CSR on IEA Configuration Example Document ID: 117964 Contributed by Kishore Yerramreddy, Cisco TAC Engineer. Jul 16, 2014 Contents Introduction Configure Generate a Certificate
GlobalForms SSL Installation Tech Brief
 127 Church Street, New Haven, CT 06510 O: (203) 789-0889 E: sales@square-9.com www.square-9.com GlobalForms SSL Installation Guide The following guide will give an overview of how to generate and install
127 Church Street, New Haven, CT 06510 O: (203) 789-0889 E: sales@square-9.com www.square-9.com GlobalForms SSL Installation Guide The following guide will give an overview of how to generate and install
Symantec Data Center Security Installation Guide. Version 6.5
 Symantec Data Center Security Installation Guide Version 6.5 Symantec Data Center Security Installation Guide Documentation version: 1.2 Legal Notice Copyright 2015 Symantec Corporation. All rights reserved.
Symantec Data Center Security Installation Guide Version 6.5 Symantec Data Center Security Installation Guide Documentation version: 1.2 Legal Notice Copyright 2015 Symantec Corporation. All rights reserved.
Creating an authorized SSL certificate
 Creating an authorized SSL certificate for MeetingSphere Meeting Center Server MeetingSphere Meeting Center Server requires an authorized SSL certificate by which its Meeting center is identified, and
Creating an authorized SSL certificate for MeetingSphere Meeting Center Server MeetingSphere Meeting Center Server requires an authorized SSL certificate by which its Meeting center is identified, and
Certificate Properties File Realm
 Certificate Properties File Realm {scrollbar} This realm type allows you to configure Web applications to authenticate users against it. To get to that point, you will need to first configure Geronimo
Certificate Properties File Realm {scrollbar} This realm type allows you to configure Web applications to authenticate users against it. To get to that point, you will need to first configure Geronimo
Securing U2 Soap Server
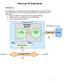 Securing U2 Soap Server Introduction To enable SSL on the Client(Consumer-to-U2SS side), we need a U2 soap server Certificate. There are three possible methods to obtain the Server Certificate: 1. Use
Securing U2 Soap Server Introduction To enable SSL on the Client(Consumer-to-U2SS side), we need a U2 soap server Certificate. There are three possible methods to obtain the Server Certificate: 1. Use
FileAudit Plus. Steps for Enabling SSL: The following steps will help you in the installation of SSL certificate in FileAudit Plus
 Steps for Enabling SSL: The following steps will help you in the installation of SSL certificate in Steps for Enabling SSL: The following steps will help you in the installation of SSL certificate in : Step
Steps for Enabling SSL: The following steps will help you in the installation of SSL certificate in Steps for Enabling SSL: The following steps will help you in the installation of SSL certificate in : Step
Using Certificates with HP Network Automation
 Using Certificates with HP Network Automation HP Network Automation / October 2010 This document provides an overview of how certificates are used within HP Network Automation (NA), including information
Using Certificates with HP Network Automation HP Network Automation / October 2010 This document provides an overview of how certificates are used within HP Network Automation (NA), including information
Tomcat SSL Certificate Deployment Guide (generate CSR by customer)
 Tomcat SSL Certificate Deployment Guide (generate CSR by customer) 沃通电子认证服务有限公司 WoSignCA Limited Content 1.Generate the CSR by customer... 3 1.1 Generate the private key files... 3 1.2 Generate CSR file...
Tomcat SSL Certificate Deployment Guide (generate CSR by customer) 沃通电子认证服务有限公司 WoSignCA Limited Content 1.Generate the CSR by customer... 3 1.1 Generate the private key files... 3 1.2 Generate CSR file...
SSL Configuration Oracle Banking Liquidity Management Release [April] [2017]
![SSL Configuration Oracle Banking Liquidity Management Release [April] [2017] SSL Configuration Oracle Banking Liquidity Management Release [April] [2017]](/thumbs/74/70574223.jpg) SSL Configuration Oracle Banking Liquidity Management Release 12.4.0.0.0 [April] [2017] Table of Contents 1. CONFIGURING SSL ON ORACLE WEBLOGIC... 1-1 1.1 INTRODUCTION... 1-1 1.2 SETTING UP SSL ON ORACLE
SSL Configuration Oracle Banking Liquidity Management Release 12.4.0.0.0 [April] [2017] Table of Contents 1. CONFIGURING SSL ON ORACLE WEBLOGIC... 1-1 1.1 INTRODUCTION... 1-1 1.2 SETTING UP SSL ON ORACLE
Configuring the RTP Server
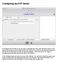 Configuring the RTP Server To configure the RTP Server you can click on the little cog in the lower right hand corner of the banner area at the top of the window (If the RTP Server is running you will
Configuring the RTP Server To configure the RTP Server you can click on the little cog in the lower right hand corner of the banner area at the top of the window (If the RTP Server is running you will
SafeNet KMIP and Google Drive Integration Guide
 SafeNet KMIP and Google Drive Integration Guide Documentation Version: 20130802 Table of Contents CHAPTER 1 GOOGLE DRIVE......................................... 2 Introduction...............................................................
SafeNet KMIP and Google Drive Integration Guide Documentation Version: 20130802 Table of Contents CHAPTER 1 GOOGLE DRIVE......................................... 2 Introduction...............................................................
Assuming you have Icinga 2 installed properly, and the API is not enabled, the commands will guide you through the basics:
 Icinga 2 Contents This page references the GroundWork Cloud Hub and the Icinga 2 virtualization environment. 1.0 Prerequisites 1.1 Enable the API The Icinga 2 system you run needs to have the API feature
Icinga 2 Contents This page references the GroundWork Cloud Hub and the Icinga 2 virtualization environment. 1.0 Prerequisites 1.1 Enable the API The Icinga 2 system you run needs to have the API feature
SAS Studio 3.6: Administrator s Guide
 SAS Studio 3.6: Administrator s Guide SAS Documentation March 7, 2018 The correct bibliographic citation for this manual is as follows: SAS Institute Inc. 2016. SAS Studio 3.6: Administrator s Guide. Cary,
SAS Studio 3.6: Administrator s Guide SAS Documentation March 7, 2018 The correct bibliographic citation for this manual is as follows: SAS Institute Inc. 2016. SAS Studio 3.6: Administrator s Guide. Cary,
DOCUMENT DESCRIPTION...
 Contents 1 DOCUMENT DESCRIPTION... 1 1.1 OVERVIEW... 1 1.2 GLOSSARY... 1 1.3 PREREQUISITES... 3 2 CONFIGURATION... 4 2.1 CREATE WEBLOGIC DOMAIN... 4 2.2 CONFIGURE WEBLOGIC MANAGED DOMAIN... 12 2.3 INSTALLATION
Contents 1 DOCUMENT DESCRIPTION... 1 1.1 OVERVIEW... 1 1.2 GLOSSARY... 1 1.3 PREREQUISITES... 3 2 CONFIGURATION... 4 2.1 CREATE WEBLOGIC DOMAIN... 4 2.2 CONFIGURE WEBLOGIC MANAGED DOMAIN... 12 2.3 INSTALLATION
Practical Exercise: Smartcard-based authentication in HTTP
 MIECT: Security 2015-16 Practical Exercise: Smartcard-based authentication in HTTP November 24, 2015 Due date: no date Changelog v1.0 - Initial Version. 1 Introduction Smartcards can be used to authenticate
MIECT: Security 2015-16 Practical Exercise: Smartcard-based authentication in HTTP November 24, 2015 Due date: no date Changelog v1.0 - Initial Version. 1 Introduction Smartcards can be used to authenticate
Server software page. Certificate Signing Request (CSR) Generation. Software
 Server software page Certificate Signing Request (CSR) Generation Software Apache (mod_ssl and OpenSSL)... 2 cpanel and WHM... 3 Microsoft Exchange 2007... 8 Microsoft Exchange 2010... 9 F5 BigIP... 13
Server software page Certificate Signing Request (CSR) Generation Software Apache (mod_ssl and OpenSSL)... 2 cpanel and WHM... 3 Microsoft Exchange 2007... 8 Microsoft Exchange 2010... 9 F5 BigIP... 13
C O N F IGURIN G EN HA N C ED SEC U RITY O PTIONS F O R REMOTE C O N TROL
 C O N F IGURIN G EN HA N C ED SEC U RITY O PTIONS F O R REMOTE C O N TROL Avalanche Remote Control 4.1.3 can be configured to use AES encryption between the device and the server, and SSL encryption between
C O N F IGURIN G EN HA N C ED SEC U RITY O PTIONS F O R REMOTE C O N TROL Avalanche Remote Control 4.1.3 can be configured to use AES encryption between the device and the server, and SSL encryption between
MSE System and Appliance Hardening Guidelines
 MSE System and Appliance Hardening Guidelines This appendix describes the hardening of MSE, which requires some services and processes to be exposed to function properly. This is referred to as MSE Appliance
MSE System and Appliance Hardening Guidelines This appendix describes the hardening of MSE, which requires some services and processes to be exposed to function properly. This is referred to as MSE Appliance
Please select your version
 Installation Guide Please select your version Installation Instructions for Tomcat using PKCS#7 format Installation Instructions for Tomcat using X.509 format Installation Instructions for Tomcat using
Installation Guide Please select your version Installation Instructions for Tomcat using PKCS#7 format Installation Instructions for Tomcat using X.509 format Installation Instructions for Tomcat using
VIRTUAL GPU LICENSE SERVER VERSION , , AND 5.1.0
 VIRTUAL GPU LICENSE SERVER VERSION 2018.10, 2018.06, AND 5.1.0 DU-07754-001 _v7.0 through 7.2 March 2019 User Guide TABLE OF CONTENTS Chapter 1. Introduction to the NVIDIA vgpu Software License Server...
VIRTUAL GPU LICENSE SERVER VERSION 2018.10, 2018.06, AND 5.1.0 DU-07754-001 _v7.0 through 7.2 March 2019 User Guide TABLE OF CONTENTS Chapter 1. Introduction to the NVIDIA vgpu Software License Server...
VMware Horizon JMP Server Installation and Setup Guide. 13 DEC 2018 VMware Horizon 7 7.7
 VMware Horizon JMP Server Installation and Setup Guide 13 DEC 2018 VMware Horizon 7 7.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you
VMware Horizon JMP Server Installation and Setup Guide 13 DEC 2018 VMware Horizon 7 7.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you
Enabling Microsoft Outlook Calendar Notifications for Meetings Scheduled from the Cisco Unified MeetingPlace End-User Web Interface
 Enabling Microsoft Outlook Calendar Notifications for Meetings Scheduled from the Cisco Unified MeetingPlace End-User Web Interface Release 7.1 Revised: March 5, 2013 1:53 pm This document describes the
Enabling Microsoft Outlook Calendar Notifications for Meetings Scheduled from the Cisco Unified MeetingPlace End-User Web Interface Release 7.1 Revised: March 5, 2013 1:53 pm This document describes the
Provisioning Certificates
 CHAPTER 8 The Secure Socket Layer (SSL) protocol secures the network communication and allows data to be encrypted before transmission and provides security. Many application servers and web servers support
CHAPTER 8 The Secure Socket Layer (SSL) protocol secures the network communication and allows data to be encrypted before transmission and provides security. Many application servers and web servers support
VMware Identity Manager Connector Installation and Configuration (Legacy Mode)
 VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
Configure the Rational ClearQuest Web and Rational DOORS Web Access integration with SSL
 Configure the Rational ClearQuest Web and Rational DOORS Web Access integration with SSL Joan Morgan November 1, 2012 Page 1 of 33 INTRODUCTION...3 SUPPORTED FEATURES...4 PREPARATION FOR THE INTEGRATION...5
Configure the Rational ClearQuest Web and Rational DOORS Web Access integration with SSL Joan Morgan November 1, 2012 Page 1 of 33 INTRODUCTION...3 SUPPORTED FEATURES...4 PREPARATION FOR THE INTEGRATION...5
OpenAM Single Sign-On
 Single Sign-On Setup Task List, page 2 Single Sign-On Setup Preparation, page 4 Single Sign-On Setup and Management Tasks, page 6 Configuration and Administration of IM and Presence Service on Cisco Unified
Single Sign-On Setup Task List, page 2 Single Sign-On Setup Preparation, page 4 Single Sign-On Setup and Management Tasks, page 6 Configuration and Administration of IM and Presence Service on Cisco Unified
VMware Horizon JMP Server Installation and Setup Guide. Modified on 19 JUN 2018 VMware Horizon 7 7.5
 VMware Horizon JMP Server Installation and Setup Guide Modified on 19 JUN 2018 VMware Horizon 7 7.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware Horizon JMP Server Installation and Setup Guide Modified on 19 JUN 2018 VMware Horizon 7 7.5 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
HP AutoPass License Server
 HP AutoPass License Server Software Version: 9.0 Windows, Linux and CentOS operating systems Users Guide Document Release Date: October 2015 Software Release Date: October 2015 Page 2 of 144 Legal Notices
HP AutoPass License Server Software Version: 9.0 Windows, Linux and CentOS operating systems Users Guide Document Release Date: October 2015 Software Release Date: October 2015 Page 2 of 144 Legal Notices
Using Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS)
 CHAPTER 2 Using Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) This chapter contains information on the following topics: HTTPS Overview, page 2-1 HTTPS for Cisco Unified IP Phone Services,
CHAPTER 2 Using Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) This chapter contains information on the following topics: HTTPS Overview, page 2-1 HTTPS for Cisco Unified IP Phone Services,
Application notes for supporting third-party certificate in Avaya Aura System Manager 6.3.x and 7.0.x. Issue 1.3. November 2017
 Application notes for supporting third-party certificate in Avaya Aura System Manager 6.3.x and 7.0.x Issue 1.3 November 2017 THE INFORMATION PROVIDED IN HEREIN IS PROVIDED AS IS WITHOUT ANY EXPRESS OR
Application notes for supporting third-party certificate in Avaya Aura System Manager 6.3.x and 7.0.x Issue 1.3 November 2017 THE INFORMATION PROVIDED IN HEREIN IS PROVIDED AS IS WITHOUT ANY EXPRESS OR
Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS)
 Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Managing Certificates
 CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
Configuring Cisco Unified MeetingPlace Web Conferencing Security Features
 Configuring Cisco Unified MeetingPlace Web Conferencing Security Features Release 7.1 Revised: February 15, 2012 3:42 pm How to Configure Restricted Meeting ID Patterns, page 1 How to Configure Secure
Configuring Cisco Unified MeetingPlace Web Conferencing Security Features Release 7.1 Revised: February 15, 2012 3:42 pm How to Configure Restricted Meeting ID Patterns, page 1 How to Configure Secure
SAML-Based SSO Configuration
 Prerequisites, page 1 SAML SSO Configuration Workflow, page 5 Reconfigure OpenAM SSO to SAML SSO After an Upgrade, page 9 Prerequisites NTP Setup In SAML SSO, Network Time Protocol (NTP) enables clock
Prerequisites, page 1 SAML SSO Configuration Workflow, page 5 Reconfigure OpenAM SSO to SAML SSO After an Upgrade, page 9 Prerequisites NTP Setup In SAML SSO, Network Time Protocol (NTP) enables clock
OpenAM Single Sign-On
 Single Sign-On Setup Task List, on page 1 Single Sign-On Setup Preparation, on page 3 Single Sign-On Setup and Management Tasks, on page 5 Single Sign-On Setup Task List The following figure provides the
Single Sign-On Setup Task List, on page 1 Single Sign-On Setup Preparation, on page 3 Single Sign-On Setup and Management Tasks, on page 5 Single Sign-On Setup Task List The following figure provides the
SAS Studio 3.7: Administrator s Guide
 SAS Studio 3.7: Administrator s Guide SAS Documentation March 7, 2018 The correct bibliographic citation for this manual is as follows: SAS Institute Inc. 2017. SAS Studio 3.7: Administrator s Guide. Cary,
SAS Studio 3.7: Administrator s Guide SAS Documentation March 7, 2018 The correct bibliographic citation for this manual is as follows: SAS Institute Inc. 2017. SAS Studio 3.7: Administrator s Guide. Cary,
HPE AutoPass License Server
 HPE AutoPass License Server Software Version: 9.2 Windows, Linux and CentOS operating systems User Guide Document Release Date: April 2016 Software Release Date: April 2016 Page 2 of 130 Legal Notices
HPE AutoPass License Server Software Version: 9.2 Windows, Linux and CentOS operating systems User Guide Document Release Date: April 2016 Software Release Date: April 2016 Page 2 of 130 Legal Notices
ADSelfService Plus: Guide to Install SSL Certificate. 1 P a g e
 ADSelfService Plus: Guide to Install SSL Certificate 1 P a g e Contents Document Summary:... 3 ADSelfService Plus Overview:... 3 Why do you need SSL Certification?... 3 Steps for Enabling SSL:... 4 Step
ADSelfService Plus: Guide to Install SSL Certificate 1 P a g e Contents Document Summary:... 3 ADSelfService Plus Overview:... 3 Why do you need SSL Certification?... 3 Steps for Enabling SSL:... 4 Step
Keytool and Certificate Management
 Keytool and Certificate Management A guide to utilizing keytool to assist with Certificates for emedny SOAP 2/16/2013 TABLE OF CONTENTS TABLE OF CONTENTS 1 Introduction... 3 2 Creating a Certificate Signing
Keytool and Certificate Management A guide to utilizing keytool to assist with Certificates for emedny SOAP 2/16/2013 TABLE OF CONTENTS TABLE OF CONTENTS 1 Introduction... 3 2 Creating a Certificate Signing
Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS)
 Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Director and Certificate Authority Issuance
 VMware vcloud Director and Certificate Authority Issuance Leveraging QuoVadis Certificate Authority with VMware vcloud Director TECHNICAL WHITE PAPER OCTOBER 2012 Table of Contents Introduction.... 3 Process
VMware vcloud Director and Certificate Authority Issuance Leveraging QuoVadis Certificate Authority with VMware vcloud Director TECHNICAL WHITE PAPER OCTOBER 2012 Table of Contents Introduction.... 3 Process
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE. 31 January 2017
 BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
Live Data Connection to SAP Universes
 Live Data Connection to SAP Universes You can create a Live Data Connection to SAP Universe using the SAP BusinessObjects Enterprise (BOE) Live Data Connector component deployed on your application server.
Live Data Connection to SAP Universes You can create a Live Data Connection to SAP Universe using the SAP BusinessObjects Enterprise (BOE) Live Data Connector component deployed on your application server.
Using SSL to Secure Client/Server Connections
 Using SSL to Secure Client/Server Connections Using SSL to Secure Client/Server Connections, page 1 Using SSL to Secure Client/Server Connections Introduction This chapter contains information on creating
Using SSL to Secure Client/Server Connections Using SSL to Secure Client/Server Connections, page 1 Using SSL to Secure Client/Server Connections Introduction This chapter contains information on creating
SSL or TLS Configuration for Tomcat Oracle FLEXCUBE Universal Banking Release [December] [2016]
![SSL or TLS Configuration for Tomcat Oracle FLEXCUBE Universal Banking Release [December] [2016] SSL or TLS Configuration for Tomcat Oracle FLEXCUBE Universal Banking Release [December] [2016]](/thumbs/74/70834213.jpg) SSL or TLS Configuration for Tomcat Oracle FLEXCUBE Universal Banking Release 12.3.0.0.0 [December] [2016] Table of Contents 1. SSL OR TLS CONFIGURATION... 1-1 1.1 INTRODUCTION... 1-1 1.2 REFERENCE SITES...
SSL or TLS Configuration for Tomcat Oracle FLEXCUBE Universal Banking Release 12.3.0.0.0 [December] [2016] Table of Contents 1. SSL OR TLS CONFIGURATION... 1-1 1.1 INTRODUCTION... 1-1 1.2 REFERENCE SITES...
Oracle Insurance Rules Palette
 Oracle Insurance Rules Palette Security Guide Version 10.2.0.0 Document Part Number: E62439-01 August, 2015 Copyright 2009, 2015, Oracle and/or its affiliates. All rights reserved. Trademark Notice Oracle
Oracle Insurance Rules Palette Security Guide Version 10.2.0.0 Document Part Number: E62439-01 August, 2015 Copyright 2009, 2015, Oracle and/or its affiliates. All rights reserved. Trademark Notice Oracle
Hortonworks DataFlow
 Hortonworks DataFlow Installing NiFi (February 28, 2018) docs.hortonworks.com Hortonworks DataFlow: Installing NiFi Copyright 2012-2018 Hortonworks, Inc. Some rights reserved. Except where otherwise noted,
Hortonworks DataFlow Installing NiFi (February 28, 2018) docs.hortonworks.com Hortonworks DataFlow: Installing NiFi Copyright 2012-2018 Hortonworks, Inc. Some rights reserved. Except where otherwise noted,
Unified Management Portal
 Unified Management Portal Secure Sockets Layer Implementation Guide 6.0 Document Revision History Document Version Date Changes Beta 05/01/2012 Beta release. 1.0 08/01/2012 Initial release. 1.1 09/15/2012
Unified Management Portal Secure Sockets Layer Implementation Guide 6.0 Document Revision History Document Version Date Changes Beta 05/01/2012 Beta release. 1.0 08/01/2012 Initial release. 1.1 09/15/2012
SSO Authentication with ADFS SAML 2.0. Ephesoft Transact Documentation
 SSO Authentication with ADFS SAML 2.0 Ephesoft Transact Documentation 2017 Table of Contents Prerequisites... 1 Tools Used... 1 Setup... 1 Generating Server Certificates to Set Up SSL/TLS... 1 Creating
SSO Authentication with ADFS SAML 2.0 Ephesoft Transact Documentation 2017 Table of Contents Prerequisites... 1 Tools Used... 1 Setup... 1 Generating Server Certificates to Set Up SSL/TLS... 1 Creating
HP Operations Orchestration Software
 HP Operations Orchestration Software Software Version: 7.50 Administrator s Guide Document Release Date: November 2008 Software Release Date: November 2008 Legal Notices Warranty The only warranties for
HP Operations Orchestration Software Software Version: 7.50 Administrator s Guide Document Release Date: November 2008 Software Release Date: November 2008 Legal Notices Warranty The only warranties for
Genesys Security Deployment Guide. What You Need
 Genesys Security Deployment Guide What You Need 12/27/2017 Contents 1 What You Need 1.1 TLS Certificates 1.2 Generating Certificates using OpenSSL and Genesys Security Pack 1.3 Generating Certificates
Genesys Security Deployment Guide What You Need 12/27/2017 Contents 1 What You Need 1.1 TLS Certificates 1.2 Generating Certificates using OpenSSL and Genesys Security Pack 1.3 Generating Certificates
Meteor Quick Setup Guide Version 1.11
 Steps for Setting Up Meteor 1. Download the Meteor Software from the Meteor page: www.meteornetwork.org in the User Documentation section 2. Install Java SDK (See Appendix A for instructions) o Add [Java
Steps for Setting Up Meteor 1. Download the Meteor Software from the Meteor page: www.meteornetwork.org in the User Documentation section 2. Install Java SDK (See Appendix A for instructions) o Add [Java
for Unclassified Systems
 DoD Public Key Enablement (PKE) Reference Guide InstallRoot 5.0 User Guide Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke InstallRoot 5.0 User Guide for Unclassified Systems 7 December 2015
DoD Public Key Enablement (PKE) Reference Guide InstallRoot 5.0 User Guide Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke InstallRoot 5.0 User Guide for Unclassified Systems 7 December 2015
Fabric Manager Web Server
 CHAPTER 7 With you can monitor Cisco MDS switch events, performance, and inventory from a remote location using a web browser. This chapter contains the following sections: Overview, page 7-1 Navigating
CHAPTER 7 With you can monitor Cisco MDS switch events, performance, and inventory from a remote location using a web browser. This chapter contains the following sections: Overview, page 7-1 Navigating
Symantec PKI Enterprise Gateway Deployment Guide. v8.15
 Symantec PKI Enterprise Gateway Deployment Guide v8.15 Legal Notice Copyright 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo and are trademarks or registered
Symantec PKI Enterprise Gateway Deployment Guide v8.15 Legal Notice Copyright 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo and are trademarks or registered
Prescription Monitoring Program Information Exchange. RxCheck State Routing Service. SRS Installation & Setup Guide
 Prescription Monitoring Program Information Exchange RxCheck State Routing Service SRS Installation & Setup Guide Delivery On: Version: July 2018 2.0 Prepared By: Sponsored By: IJIS Institute Tetrus Corp
Prescription Monitoring Program Information Exchange RxCheck State Routing Service SRS Installation & Setup Guide Delivery On: Version: July 2018 2.0 Prepared By: Sponsored By: IJIS Institute Tetrus Corp
Hitachi ID Systems Inc Identity Manager 8.2.6
 Systems Inc RSA SecurID Ready Implementation Guide Partner Information Last Modified: December 5, 2014 Product Information Partner Name Hitachi ID Systems Inc Web Site www.hitachi-id.com Product Name Identity
Systems Inc RSA SecurID Ready Implementation Guide Partner Information Last Modified: December 5, 2014 Product Information Partner Name Hitachi ID Systems Inc Web Site www.hitachi-id.com Product Name Identity
Fischer International Identity Fischer Identity Suite 4.2
 Fischer International Identity Fischer Identity Suite 4.2 RSA SecurID Ready Implementation Guide Partner Information Last Modified: June 16, 2010 Product Information Partner Name Web Site Product Name
Fischer International Identity Fischer Identity Suite 4.2 RSA SecurID Ready Implementation Guide Partner Information Last Modified: June 16, 2010 Product Information Partner Name Web Site Product Name
Troubleshooting Single Sign-On
 Security Trust Error Message, on page 1 "Invalid Profile Credentials" Message, on page 2 "Module Name Is Invalid" Message, on page 2 "Invalid OpenAM Access Manager (Openam) Server URL" Message, on page
Security Trust Error Message, on page 1 "Invalid Profile Credentials" Message, on page 2 "Module Name Is Invalid" Message, on page 2 "Invalid OpenAM Access Manager (Openam) Server URL" Message, on page
Implementing Secure User Access, page 3-2 Creating Secure Passwords, page 3-6 Configuring Prime Performance Manager User Account Levels, page 3-6
 3 CHAPTER Before you set up your server for discovering, monitoring, and configuring your Cisco network, you need to make some decisions about the level of security you need in your network monitoring.
3 CHAPTER Before you set up your server for discovering, monitoring, and configuring your Cisco network, you need to make some decisions about the level of security you need in your network monitoring.
LDAP Directory Integration
 LDAP Server Name, Address, and Profile Configuration, page 1 with Cisco Unified Communications Manager Task List, page 1 for Contact Searches on XMPP Clients, page 6 LDAP Server Name, Address, and Profile
LDAP Server Name, Address, and Profile Configuration, page 1 with Cisco Unified Communications Manager Task List, page 1 for Contact Searches on XMPP Clients, page 6 LDAP Server Name, Address, and Profile
Click Studios. Passwordstate. Remote Session Launcher. Installation Instructions
 Passwordstate Remote Session Launcher Installation Instructions This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise
Passwordstate Remote Session Launcher Installation Instructions This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise
Troubleshooting Single Sign-On
 Security Trust Error Message, page 1 "Invalid Profile Credentials" Message, page 2 "Module Name Is Invalid" Message, page 2 "Invalid OpenAM Access Manager (Openam) Server URL" Message, page 2 Web Browser
Security Trust Error Message, page 1 "Invalid Profile Credentials" Message, page 2 "Module Name Is Invalid" Message, page 2 "Invalid OpenAM Access Manager (Openam) Server URL" Message, page 2 Web Browser
Manage Certificates. Certificates Overview
 Certificates Overview, page 1 Show Certificates, page 3 Download Certificates, page 4 Install Intermediate Certificates, page 4 Delete a Trust Certificate, page 5 Regenerate a Certificate, page 6 Upload
Certificates Overview, page 1 Show Certificates, page 3 Download Certificates, page 4 Install Intermediate Certificates, page 4 Delete a Trust Certificate, page 5 Regenerate a Certificate, page 6 Upload
ConnectUPS-X / -BD /-E How to use and install SSL, SSH
 ConnectUPS-X /-BD /-E product family Root CA Certificate installation Rev. B Page 1/16 Index 1. How to use and install SSL (Secure Socket Layer)...3 1.1. General Certificate warning message if not installed...3
ConnectUPS-X /-BD /-E product family Root CA Certificate installation Rev. B Page 1/16 Index 1. How to use and install SSL (Secure Socket Layer)...3 1.1. General Certificate warning message if not installed...3
Getting Started with the VQE Startup Configuration Utility
 CHAPTER 2 Getting Started with the VQE Startup Configuration Utility This chapter explains how to use the Cisco VQE Startup Configuration Utility to perform the initial configuration tasks needed to get
CHAPTER 2 Getting Started with the VQE Startup Configuration Utility This chapter explains how to use the Cisco VQE Startup Configuration Utility to perform the initial configuration tasks needed to get
SAS Event Stream Processing 5.2: Visualizing Event Streams with Streamviewer
 SAS Event Stream Processing 5.2: Visualizing Event Streams with Streamviewer Overview Streamviewer is a graphical user interface that visualizes events streaming through event stream processing models.
SAS Event Stream Processing 5.2: Visualizing Event Streams with Streamviewer Overview Streamviewer is a graphical user interface that visualizes events streaming through event stream processing models.
Client Authenticated SSL Server Setup Guide for Apache Webservers
 1 of 18 PROTECTID Client Authenticated SSL Server Setup Guide for Apache Webservers Document: MK UM 02180405 01 ProtectIDclientAuthSSLsetupApache.doc 2 of 18 Copyright 2005 Sentry Project Management All
1 of 18 PROTECTID Client Authenticated SSL Server Setup Guide for Apache Webservers Document: MK UM 02180405 01 ProtectIDclientAuthSSLsetupApache.doc 2 of 18 Copyright 2005 Sentry Project Management All
Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at
 Document Date: May 16, 2017 THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL
Document Date: May 16, 2017 THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL
Internet Script Editor
 ISE Application, page 1 ISE Functionality, page 1 ISE Requirements, page 2 TLS Requirements for ISE, page 2 ISE Installation and Upgrades, page 5 Troubleshooting Tools for, page 7 ISE Application You can
ISE Application, page 1 ISE Functionality, page 1 ISE Requirements, page 2 TLS Requirements for ISE, page 2 ISE Installation and Upgrades, page 5 Troubleshooting Tools for, page 7 ISE Application You can
Creating and Installing SSL Certificates (for Stealthwatch System v6.10)
 Creating and Installing SSL Certificates (for Stealthwatch System v6.10) Copyrights and Trademarks 2017 Cisco Systems, Inc. All rights reserved. NOTICE THE SPECIFICATIONS AND INFORMATION REGARDING THE
Creating and Installing SSL Certificates (for Stealthwatch System v6.10) Copyrights and Trademarks 2017 Cisco Systems, Inc. All rights reserved. NOTICE THE SPECIFICATIONS AND INFORMATION REGARDING THE
SAS Event Stream Processing 4.3: Visualizing Event Streams with Streamviewer
 SAS Event Stream Processing 4.3: Visualizing Event Streams with Streamviewer Overview Streamviewer provides a user interface that enables you to subscribe to window event streams from one or more event
SAS Event Stream Processing 4.3: Visualizing Event Streams with Streamviewer Overview Streamviewer provides a user interface that enables you to subscribe to window event streams from one or more event
ZENworks 2017 ZENworks Appliance Deployment and Administration Reference. December 2016
 ZENworks 2017 ZENworks Appliance Deployment and Administration Reference December 2016 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions,
ZENworks 2017 ZENworks Appliance Deployment and Administration Reference December 2016 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions,
Managing vrealize Automation. 15 March 2018 vrealize Automation 7.3
 Managing vrealize Automation 15 March 2018 vrealize Automation 7.3 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about
Managing vrealize Automation 15 March 2018 vrealize Automation 7.3 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about
Configuring SAML-based Single Sign-on for Informatica Web Applications
 Configuring SAML-based Single Sign-on for Informatica Web Applications Copyright Informatica LLC 2017. Informatica LLC. Informatica, the Informatica logo, Informatica Big Data Management, and Informatica
Configuring SAML-based Single Sign-on for Informatica Web Applications Copyright Informatica LLC 2017. Informatica LLC. Informatica, the Informatica logo, Informatica Big Data Management, and Informatica
eroaming platform Secure Connection Guide
 eroaming platform Secure Connection Guide Contents 1. Revisions overview... 3 2. Abbrevations... 4 3. Preconditions... 5 3.1. OpenSSL... 5 3.2. Requirements for your PKCS10 CSR... 5 3.3. Java Keytool...
eroaming platform Secure Connection Guide Contents 1. Revisions overview... 3 2. Abbrevations... 4 3. Preconditions... 5 3.1. OpenSSL... 5 3.2. Requirements for your PKCS10 CSR... 5 3.3. Java Keytool...
Configuring Oracle Java CAPS for SSL Support
 Configuring Oracle Java CAPS for SSL Support Part No: 821 2544 March 2011 Copyright 2008, 2011, Oracle and/or its affiliates. All rights reserved. License Restrictions Warranty/Consequential Damages Disclaimer
Configuring Oracle Java CAPS for SSL Support Part No: 821 2544 March 2011 Copyright 2008, 2011, Oracle and/or its affiliates. All rights reserved. License Restrictions Warranty/Consequential Damages Disclaimer
X-road MISP2 installation and configuration guide. Version 1.20
 X-road MISP2 installation and configuration guide Version 1.20 Contents 1. Introduction... 3 2. Environment requirements... 3 3.MISP2 Installation... 3 3.1. Java... 3 3.2. PostgreSQL... 3 3.3. Apache Tomcat
X-road MISP2 installation and configuration guide Version 1.20 Contents 1. Introduction... 3 2. Environment requirements... 3 3.MISP2 Installation... 3 3.1. Java... 3 3.2. PostgreSQL... 3 3.3. Apache Tomcat
VMware vrealize Operations for Horizon Security. 20 SEP 2018 VMware vrealize Operations for Horizon 6.6
 VMware vrealize Operations for Horizon Security 20 SEP 2018 VMware vrealize Operations for Horizon 6.6 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware vrealize Operations for Horizon Security 20 SEP 2018 VMware vrealize Operations for Horizon 6.6 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Scenarios for Setting Up SSL Certificates for View. VMware Horizon 6 6.0
 Scenarios for Setting Up SSL Certificates for View VMware Horizon 6 6.0 Scenarios for Setting Up SSL Certificates for View You can find the most up-to-date technical documentation on the VMware Web site
Scenarios for Setting Up SSL Certificates for View VMware Horizon 6 6.0 Scenarios for Setting Up SSL Certificates for View You can find the most up-to-date technical documentation on the VMware Web site
User Account Manager
 CHAPTER 4 Note User accounts can be accessed only when operating in Internal Directory mode. To access User tasks, log in to the system (see Logging In section on page 2-1). Then, from the Home page, click
CHAPTER 4 Note User accounts can be accessed only when operating in Internal Directory mode. To access User tasks, log in to the system (see Logging In section on page 2-1). Then, from the Home page, click
OneClick. Administration Guide. Document 5166
 OneClick Administration Guide Document 5166 Notice This documentation (the "Documentation") and related computer software program (the "Software") (hereinafter collectively referred to as the "Product")
OneClick Administration Guide Document 5166 Notice This documentation (the "Documentation") and related computer software program (the "Software") (hereinafter collectively referred to as the "Product")
Oracle Oracle Identity Manager 11g
 RSA SecurID Ready Implementation Guide Partner Information Last Modified: August 24, 2014 Product Information Partner Name Web Site Product Name Version & Platform Product Description Oracle www.oracle.com
RSA SecurID Ready Implementation Guide Partner Information Last Modified: August 24, 2014 Product Information Partner Name Web Site Product Name Version & Platform Product Description Oracle www.oracle.com
Let s Encrypt Apache Tomcat * * Full disclosure: Tomcat will not actually be encrypted.
 Let s Encrypt Apache Tomcat * * Full disclosure: Tomcat will not actually be encrypted. Christopher Schultz Chief Technology Officer Total Child Health, Inc. * Slides available on the Linux Foundation
Let s Encrypt Apache Tomcat * * Full disclosure: Tomcat will not actually be encrypted. Christopher Schultz Chief Technology Officer Total Child Health, Inc. * Slides available on the Linux Foundation
Cisco SSL Encryption Utility
 About SSL Encryption Utility, page 1 About SSL Encryption Utility Unified ICM web servers are configured for secure access (HTTPS) using SSL. Cisco provides an application called the SSL Encryption Utility
About SSL Encryption Utility, page 1 About SSL Encryption Utility Unified ICM web servers are configured for secure access (HTTPS) using SSL. Cisco provides an application called the SSL Encryption Utility
McAfee Cloud Identity Manager Installation Guide For McAfee Cloud Identity Manager v3.1 August 2012
 McAfee Cloud Identity Manager Installation Guide For McAfee Cloud Identity Manager v3.1 August 2012 Order Number: 326712-005US COPYRIGHT Copyright 2012 McAfee, Inc. Do not copy without permission. TRADEMARK
McAfee Cloud Identity Manager Installation Guide For McAfee Cloud Identity Manager v3.1 August 2012 Order Number: 326712-005US COPYRIGHT Copyright 2012 McAfee, Inc. Do not copy without permission. TRADEMARK
Deploy In-Memory Parallel Graph Analytics (PGX) to Oracle Java Cloud Service (JCS)
 Deploy In-Memory Parallel Graph Analytics (PGX) to Oracle Java Cloud Service (JCS) Overview This document provides detailed steps required to deploy PGX to Java Cloud Service Instance. This exercise is
Deploy In-Memory Parallel Graph Analytics (PGX) to Oracle Java Cloud Service (JCS) Overview This document provides detailed steps required to deploy PGX to Java Cloud Service Instance. This exercise is
Installation 1. DLM Installation. Date of Publish:
 1 DLM Installation Date of Publish: 2018-05-18 http://docs.hortonworks.com Contents Installation overview...3 Setting Up the Local Repository for Your DLM Installation... 3 Set up a local repository for
1 DLM Installation Date of Publish: 2018-05-18 http://docs.hortonworks.com Contents Installation overview...3 Setting Up the Local Repository for Your DLM Installation... 3 Set up a local repository for
Managing Security Certificates in Cisco Unified Operating System
 CHAPTER 5 Managing Security Certificates in Cisco Unified Operating System June 11, 2009 The operating system security options enable you to manage security certificates in these two ways: Certificate
CHAPTER 5 Managing Security Certificates in Cisco Unified Operating System June 11, 2009 The operating system security options enable you to manage security certificates in these two ways: Certificate
Administration Guide Configuration and Operation
 Title page Nortel Application Gateway 1000/2000 Nortel Application Gateway Release 6.1 Administration Guide Configuration and Operation Document Number: NN42360-600 Document Release: Standard 01.07 Date:
Title page Nortel Application Gateway 1000/2000 Nortel Application Gateway Release 6.1 Administration Guide Configuration and Operation Document Number: NN42360-600 Document Release: Standard 01.07 Date:
HP Enterprise Integration Module for SAP Solution Manager
 HP Enterprise Integration Module for SAP Solution Manager Software Version: 12.01 User Guide Document Release Date: March 2015 Software Release Date: March 2015 Legal Notices Warranty The only warranties
HP Enterprise Integration Module for SAP Solution Manager Software Version: 12.01 User Guide Document Release Date: March 2015 Software Release Date: March 2015 Legal Notices Warranty The only warranties
