Lab I: Using tcpdump and Wireshark
|
|
|
- Hollie Lawson
- 5 years ago
- Views:
Transcription
1 Objectives To get the student familiar with basic network protocol analyzer, tools and equipment used in later labs, including tcpdump and Wireshark. Lab Readings Go to and read the manual pages of tcpdump command. Filter expression can be found at Go to and read about capture filters and display filters in wireshark. Alternatively, you can go to one of many Wireshark tutorial pages such as Read introduction part (pages 1-18) of the article Understanding IP Addressing: Everything You Ever Wanted to Know Prelab Questions 1. Write the tcpdump command that captures packets containing ICMP messages with a source or destination IP address Write the tcpdump syntax to capture packets whose source address is and it uses standard ssh port (either as source or destination port) 3. Write a Wireshark display filter expression that shows packets containing ICMP messages with a source or destination IP address and frame number between 15 and Write a Wireshark display filter expression that shows packets containing TCP traffic with a source or destination IP address and using ports 80, Equipment List Equipment Quantity Linux PC with one Ethernet card 3 Unmanaged switch 1 1 of 8
2 Introduction and Background Since this is the first lab that you have to configure the PCs and network configuration in Linux, a brief introduction to necessary commands will be given. Your Linux comes with graphical user interface, but in this lab (and most of other labs) you have to use console window (text mode). Most commands in Linux come with help. If you want to consult the command manual, use the command man. For example, man ping will show you how to use ping command. The content will be shown one page at a time. You can press space bar to scroll down or Ctrl-b to scroll up or q to quit to the shell prompt. Another useful shell feature is command/path completion to your save typing time. You can type a partial command string and then press the Tab key. If the string is a unique prefix of a command, the shell will fill out the rest for you. For example, you can type tcpd followed by Tab. The shell will complete tcpdump for you. If multiple commands match your partial string tcpd, the shell will list those commands. This technique also applies to path completion, which will save your time in typing the whole pathname. Another important command is Ping, which is a basic network utility for checking whether a target host is reachable or not. Ping sends an ICMP Echo Request message to the destination host, which will then return an ICMP Echo Reply message. For list of options, issue man ping ; or for brief parameter listing, try ping h. In Linux, Ethernet interfaces are named eth0 (first port), eth1, and so on. You can use command ifconfig to display current network interface configuration. Make sure that path /sbin/ is in your PATH environment variable by issuing the command echo $PATH If /sbin is not the list, add the path with the command export PATH=/sbin:$PATH You will also see interface lo. This is a loop back interface and will not be used in the lab. Wireshark is a network protocol analyzer with a graphical user interface. Originally, its name was Ethereal but was changed to Wireshark many years ago due to some legal problem. However, the interfaces and functionalities of Wireshark have not changed much since the last version of Ethereal. Therefore, you can safely use most of the Ethereal tutorials in Wireshark. Using Wireshark, you can interactively capture and examine network traffic, view summaries, and get detailed information for each packet. 2 of 8
3 Lab Procedures SW eth0 eth eth0 ` ` ` PC1 PC2 PC3 Figure 1.1 Network topology setup Part I: tcpdump Basic tcpdump is a console tool that allows you to capture traffic on a network and display the packet headers of the captured traffic 1. tcpdump can be used to identify network problems or to monitor network activities. To simultaneously view and save the output from tcpdump, you need to use the -l option of tcpdump together with the tee or tail commands. For example, tcpdump n l > filename & tail f filename tcpdump n l tee filename It may be necessary to hit Ctrl-C to terminate the tcpdump session. It may sometimes be best to simply redirect the output of tcpdump straight to a file (e.g., tcpdump > filename) and view it afterward with the more command or a text editor. Next we will use tcpdump to observe network traffic generated by issuing ping commands. 1. Basic tcpdump usage: Set up the network topology as shown in Figure 1.1. with default subnet mask, For example, to configure the IP address of PC2, typing the following commands at the terminal window: PC2% ifconfig eth netmask PC2% ifconfig eth0 up 2. At PC1, start tcpdump to monitor all packets containing the IP address of PC2 by typing PC1% tcpdump n host The tcpdump version for Microsoft Windows is windump. 3 of 8
4 3. Ping a single packet from PC1 to PC2 and then terminate tcpdump (by pressing Ctrl+c). To ping a single packet, open another terminal window and type the following at prompt: PC1% ping c Observe the tcpdump output and save it to a file. 4. At PC1, start tcpdump again by invoking command tcpdump n to capture packets. 5. Ping a single packet from PC1 to a non-existing IP address , and then ping two packets to a broadcast address Save the outputs of ping and tcpdump to a file. 7. Using filters in tcpdump: At PC1, ping five packets from PC1 to PC2, and use tcpdump to capture only ICMP packets that contain the IP address of PC2. Save the output of this tcpdump to a file. Lab report: 1.1 Include the tcpdump captured output in step 3 and explain the meaning of each field. 1.2 Include the tcpdump captured outputs in step 5 and explain what happens when pinging to a non-existing IP address and pinging to a broadcast address. How many of the Linux PCs responded to the broadcast ping? 1.3 Show the tcpdump command you used in Step 7 and include the tcpdump captured output. Part II: Wireshark Basic This part of the lab walks you through the steps of capturing and saving network traffic with Wireshark. The exercise is conducted on PC1. 1. On PC1, start Wireshark by typing PC1% wireshark & This displays the Wireshark main window on your desktop as shown in Figure of 8
5 Figure 1.2 Wireshark main window 2. Setting the capture options: Use the instructions in Figure 1.3 to set the options of Wireshark in preparation for capturing traffic. Basically, you need to set the proper interface and make sure that you capture packets in promiscuous mode. Note that the IP address and interface in the figure differ from your actual machine. Figure 1.3 General capture settings for wireshark 3. Starting the traffic capture by clicking Start button in the Capture Options window. You can also start the traffic capture by clicking Start a new live capture button (3 rd button from the left in the taskbar) once you properly set capture settings. 4. Generating traffic: In a separate terminal window on PC1, ping two packets to PC3. Observe the output of Wireshark in the main window. Click and highlight a captured packet in the Wireshark window and view the headers of the captured traffic. 5 of 8
6 5. Stopping the traffic capture: Click Stop the running live capture button (4 th button from the left in the taskbar). 6. Saving captured traffic: Save the results of the captured traffic as a plain text file. This is done by selecting Print in the File menu. When the Print dialog pops up, select the Plain text-output to file option. You must check Packet summary line and Packet details with All expanded options. An example of print options is shown in Figure 1.4. Figure 1.4 Selecting print options Lab report: 2.1 In your lab report, include the file with the captured data and describe the differences between the files saved by tcpdump (in previous part) and by Wireshark (in this part). NOTE: In general, unless asked to do otherwise, always select Packet summary line option when you include saved data in the lab report. This will help keep the length of the lab report reasonably small. If detailed information is required, you will be asked to save details of the captured traffic. In this case, select the Packet details with All expanded option. If you select Save in the File menu, the captured data is saved in libpcap format. Both tcpdump and Wireshark can interpret this format. However, libpcap files are not plain text files and are not useful for preparing your report. 7. Setting display filters: In the Wireshark main window on PC1, type the desired display filter in the field next to the Filter button, as shown in Figure 1.5. Click the Clear button to clear any existing filter. Set a display filter so that it shows only datagrams with destination IP address The filter box background is green if 6 of 8
7 the syntax of the expression is correct and it turns to red if error occurs in the expression. Figure 1.5 Filter box for setting display filters Alternatively, you can click on Expression button, Wireshark will pop up Filter expression dialog, as shown in Figure 1.6, for assisting expression construction. Figure 1.6 Filter expression dialog 8. Save the displayed data in the lab report by selecting File:Print. However, only packets that are currently being displayed are saved this time. (You have to select Displayed button, instead of default Capture button in Figure 1.4) 9. Repeat Step 7 and 8 by changing the display filter to only datagrams with source IP More complex capture and display filters: At PC1, clear the display filter and start to capture traffic. 11. Start a telnet session from PC1 to PC2 and log in as root. While, logged in, ping five packets from PC1 to PC2 using another terminal window and ping one packet from PC2 to PC1 using the telneted session. Then logout after logging in successfully. 12. Stop the traffic capture of Wireshark. Lab report: 2.2 Set the display filter to ICMP messages with source or destination address of PC2 and include the data and filter expression to the report. 7 of 8
8 2.3 Set the display filter to TCP traffic with source address of PC2 with source port number 23 and include the data and filter expression to the report. 2.4 Include the statistic summary of captured session in the report. 8 of 8
Lab 1: Introduction to Linux Networking
 CMPE 150: Introduction to Computer Networks Fall 2011 http://courses.soe.ucsc.edu/courses/cmpe150/fall11/01/ Lab 1: Introduction to Linux Networking Materials: Please bring a USB drive to each lab section.
CMPE 150: Introduction to Computer Networks Fall 2011 http://courses.soe.ucsc.edu/courses/cmpe150/fall11/01/ Lab 1: Introduction to Linux Networking Materials: Please bring a USB drive to each lab section.
5. Write a capture filter for question 4.
 Pre-Lab 2: Single Segment IP Networks 1. Review Linux man pages for arp at www.linuxmanpages.com (in both Sections 7 and 8), the ARP RFC (RFC 826) at www.ietf.org, and Section 3.4 of the IBM Red Book.
Pre-Lab 2: Single Segment IP Networks 1. Review Linux man pages for arp at www.linuxmanpages.com (in both Sections 7 and 8), the ARP RFC (RFC 826) at www.ietf.org, and Section 3.4 of the IBM Red Book.
LAB THREE STATIC ROUTING
 LAB THREE STATIC ROUTING In this lab you will work with four different network topologies. The topology for Parts 1-4 is shown in Figure 3.1. These parts address router configuration on Linux PCs and a
LAB THREE STATIC ROUTING In this lab you will work with four different network topologies. The topology for Parts 1-4 is shown in Figure 3.1. These parts address router configuration on Linux PCs and a
Assignment 2 TCP/IP Vulnerabilities
 LEIC/MEIC - IST Alameda LEIC/MEIC/MERC IST Taguspark DEASegInf Network and Computer Security 2012/2013 Assignment 2 TCP/IP Vulnerabilities Goals Gather information about the machines in the network. Explore
LEIC/MEIC - IST Alameda LEIC/MEIC/MERC IST Taguspark DEASegInf Network and Computer Security 2012/2013 Assignment 2 TCP/IP Vulnerabilities Goals Gather information about the machines in the network. Explore
Instituto Superior Técnico, Universidade de Lisboa Network and Computer Security. Lab guide: Traffic analysis and TCP/IP Vulnerabilities
 Instituto Superior Técnico, Universidade de Lisboa Network and Computer Security Lab guide: Traffic analysis and TCP/IP Vulnerabilities Revised on 2016-10-18 Alpha version: This is an early version and
Instituto Superior Técnico, Universidade de Lisboa Network and Computer Security Lab guide: Traffic analysis and TCP/IP Vulnerabilities Revised on 2016-10-18 Alpha version: This is an early version and
ECE 4110 Internetwork Programming Lab 7: Configuring a Network Using RIP Routing Protocol. Prelab Questions
 ECE 4110 Internetwork Programming Lab 7: Configuring a Network Using RIP Routing Protocol Group Number: Member Names: Date Issued: March 26, 2013 Date Due: April 3, 2013 Last Edited: January 31, 2013 This
ECE 4110 Internetwork Programming Lab 7: Configuring a Network Using RIP Routing Protocol Group Number: Member Names: Date Issued: March 26, 2013 Date Due: April 3, 2013 Last Edited: January 31, 2013 This
Material for the Networking lab in EITF25 & EITF45
 Material for the Networking lab in EITF25 & EITF45 2016 Preparations In order to succeed with the lab, you must have understood some important parts of the course. Therefore, before you come to the lab
Material for the Networking lab in EITF25 & EITF45 2016 Preparations In order to succeed with the lab, you must have understood some important parts of the course. Therefore, before you come to the lab
COMPUTER NETWORKING LAB EXERCISES (TP) 4
 Name 1: Name 2: Group number: COMPUTER NETWORKING LAB EXERCISES (TP) 4 IPV6 December 14, 2009 Abstract In this TP you will revisit some of the basic networking tools that were introduced in TP1, only this
Name 1: Name 2: Group number: COMPUTER NETWORKING LAB EXERCISES (TP) 4 IPV6 December 14, 2009 Abstract In this TP you will revisit some of the basic networking tools that were introduced in TP1, only this
Use of the TCP/IP Protocols and the OSI Model in Packet Tracer
 Communication Networks [Netw501] Spring 2018 Tutorial 3 Packet Tracer Activity 3 Use of the TCP/IP Protocols and the OSI Model in Packet Tracer Introduction: In Packet Tracer simulation mode, detailed
Communication Networks [Netw501] Spring 2018 Tutorial 3 Packet Tracer Activity 3 Use of the TCP/IP Protocols and the OSI Model in Packet Tracer Introduction: In Packet Tracer simulation mode, detailed
Lab Using Wireshark to Examine Ethernet Frames
 Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Lab Capturing and Analyzing Network Traffic
 Lab 1.2.2 Capturing and Analyzing Network Traffic Host Name IP Address Fa0/0 Subnet Mask IP Address S0/0/0 Subnet Mask Default Gateway RouterA 172.17.0.1 255.255.0.0 192.168.1.1 (DCE) 255.255.255.0 N/A
Lab 1.2.2 Capturing and Analyzing Network Traffic Host Name IP Address Fa0/0 Subnet Mask IP Address S0/0/0 Subnet Mask Default Gateway RouterA 172.17.0.1 255.255.0.0 192.168.1.1 (DCE) 255.255.255.0 N/A
Lab Using Wireshark to Examine Ethernet Frames
 Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Lab - Using Wireshark to Examine TCP and UDP Captures
 Topology Part 1 (FTP) Part 1 will highlight a TCP capture of an FTP session. This topology consists of a PC with Internet access. Topology Part 2 (TFTP) Part 2 will highlight a UDP capture of a TFTP session.
Topology Part 1 (FTP) Part 1 will highlight a TCP capture of an FTP session. This topology consists of a PC with Internet access. Topology Part 2 (TFTP) Part 2 will highlight a UDP capture of a TFTP session.
Intro to OpenFlow Tutorial
 GENIExperimenter/Tutorials/OpenFlowOVS-Floodlight GENI: geni Intro to OpenFlow Tutorial Overview: This is a simple OpenFlow tutorial that will guide you how to use the Floodlight Controller in conjunction
GENIExperimenter/Tutorials/OpenFlowOVS-Floodlight GENI: geni Intro to OpenFlow Tutorial Overview: This is a simple OpenFlow tutorial that will guide you how to use the Floodlight Controller in conjunction
To see how ARP (Address Resolution Protocol) works. ARP is an essential glue protocol that is used to join Ethernet and IP.
 Lab Exercise ARP Objective To see how ARP (Address Resolution Protocol) works. ARP is an essential glue protocol that is used to join Ethernet and IP. Requirements Wireshark: This lab uses the Wireshark
Lab Exercise ARP Objective To see how ARP (Address Resolution Protocol) works. ARP is an essential glue protocol that is used to join Ethernet and IP. Requirements Wireshark: This lab uses the Wireshark
521262S Computer Networks 2 (fall 2007) Laboratory exercise #2: Internetworking
 521262S Computer Networks 2 (fall 2007) Laboratory exercise #2: Internetworking Name Student ID Signature In this exercise we will connect our LANs made in first exercise with routers and build an internet.
521262S Computer Networks 2 (fall 2007) Laboratory exercise #2: Internetworking Name Student ID Signature In this exercise we will connect our LANs made in first exercise with routers and build an internet.
Spring 2017 Gabriel Kuri
 Lab 2 ECE 431L Spring 2017 Gabriel Kuri This lab is made up of two parts. Part 1 will consist of familiarizing yourself with the Raspberry Pi (RPi). It includes running Unix/Linux commands to become somewhat
Lab 2 ECE 431L Spring 2017 Gabriel Kuri This lab is made up of two parts. Part 1 will consist of familiarizing yourself with the Raspberry Pi (RPi). It includes running Unix/Linux commands to become somewhat
CCNA Access List Questions
 CCNA Access List Questions Here you will find answers to CCNA Access list questions Note: If you are not sure about how to use Access list, please read my Access list tutorial Question 1 Your boss is learning
CCNA Access List Questions Here you will find answers to CCNA Access list questions Note: If you are not sure about how to use Access list, please read my Access list tutorial Question 1 Your boss is learning
Introduction to the Packet Tracer Interface using a Hub Topology
 Introduction to Packet Tracer What is Packet Tracer? Packet Tracer is a protocol simulator developed by Dennis Frezzo and his team at Cisco Systems. Packet Tracer (PT) is a powerful and dynamic tool that
Introduction to Packet Tracer What is Packet Tracer? Packet Tracer is a protocol simulator developed by Dennis Frezzo and his team at Cisco Systems. Packet Tracer (PT) is a powerful and dynamic tool that
Exercises: Basics of Network Layer Experiential Learning Workshop
 Exercises: Basics of Network Layer Experiential Learning Workshop 1 General Guidelines 1. Make a team of two or three unless stated otherwise. 2. For each exercise, use wireshark capture to verify contents
Exercises: Basics of Network Layer Experiential Learning Workshop 1 General Guidelines 1. Make a team of two or three unless stated otherwise. 2. For each exercise, use wireshark capture to verify contents
Computer Networks A Simple Network Analyzer PART A undergraduates and graduates PART B graduate students only
 Computer Networks A Simple Network Analyzer PART A undergraduates and graduates PART B graduate students only Objectives The main objective of this assignment is to gain an understanding of network activities
Computer Networks A Simple Network Analyzer PART A undergraduates and graduates PART B graduate students only Objectives The main objective of this assignment is to gain an understanding of network activities
CCNA Semester 1 labs. Part 2 of 2 Labs for chapters 8 11
 CCNA Semester 1 labs Part 2 of 2 Labs for chapters 8 11 8.1.4.6 Lab - Calculating IPv4 Subnets 8.1.4.8 Lab - Designing and Implementing a Subnetted IPv4 Addressing Scheme 8.2.1.5 Lab - Designing and Implementing
CCNA Semester 1 labs Part 2 of 2 Labs for chapters 8 11 8.1.4.6 Lab - Calculating IPv4 Subnets 8.1.4.8 Lab - Designing and Implementing a Subnetted IPv4 Addressing Scheme 8.2.1.5 Lab - Designing and Implementing
Lab Configuring and Verifying Standard ACLs Topology
 Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Computer Networks A Simple Network Analyzer Decoding Ethernet and IP headers
 Computer Networks A Simple Network Analyzer Decoding Ethernet and IP headers Objectives The main objective of this assignment is to gain an understanding of network activities and network packet formats
Computer Networks A Simple Network Analyzer Decoding Ethernet and IP headers Objectives The main objective of this assignment is to gain an understanding of network activities and network packet formats
Lab - TCP Traffic Generator
 ECE4110 Fall Semester, 2010 Lab - TCP Traffic Generator Assigned: Sep 10, 2010 Due: Sep 20, 2010 Group Number: Member Names: Lab Goals 1. Finish a TCP sockets programs to transmit and receive TCP data.
ECE4110 Fall Semester, 2010 Lab - TCP Traffic Generator Assigned: Sep 10, 2010 Due: Sep 20, 2010 Group Number: Member Names: Lab Goals 1. Finish a TCP sockets programs to transmit and receive TCP data.
CS356 Lab NIL (Lam) In this lab you will learn: Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore!
 CS356 Lab NIL (Lam) In this lab you will learn: PartA Time: 2 hrs 40 min Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore! Components used: 2 computers
CS356 Lab NIL (Lam) In this lab you will learn: PartA Time: 2 hrs 40 min Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore! Components used: 2 computers
CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists
 CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists Name: In this lab you will learn: PartA Cisco 2600 Router Configuration Static Routing PartB 20 min Dynamic
CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists Name: In this lab you will learn: PartA Cisco 2600 Router Configuration Static Routing PartB 20 min Dynamic
ECE 4110 Internetwork Programming Lab 2: TCP Traffic Generator. Lab Goals. Prelab
 ECE 4110 Internetwork Programming Lab 2: TCP Traffic Generator Group Number: Member Names: Date Issued: Tuesday January 22, 2013 Date Due: Wednesday, January 30, 2013 Last Edited: 1/21/2013 Lab Goals Finish
ECE 4110 Internetwork Programming Lab 2: TCP Traffic Generator Group Number: Member Names: Date Issued: Tuesday January 22, 2013 Date Due: Wednesday, January 30, 2013 Last Edited: 1/21/2013 Lab Goals Finish
SE 4C03 Winter Final Examination Answer Key. Instructor: William M. Farmer
 SE 4C03 Winter 2003 Final Examination Answer Key Instructor: William M. Farmer (1) [2 pts.] Both the source and destination IP addresses are used to route IP datagrams. Is this statement true or false?
SE 4C03 Winter 2003 Final Examination Answer Key Instructor: William M. Farmer (1) [2 pts.] Both the source and destination IP addresses are used to route IP datagrams. Is this statement true or false?
BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic. Topology. Objectives. Background / Scenario
 BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic Topology Objectives Part 1: (Optional) Download and Install Wireshark Part 2: Capture and Analyze Local ICMP Data in Wireshark
BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic Topology Objectives Part 1: (Optional) Download and Install Wireshark Part 2: Capture and Analyze Local ICMP Data in Wireshark
When does it work? Packet Sniffers. INFO Lecture 8. Content 24/03/2009
 Packet Sniffers INFO 404 - Lecture 8 24/03/2009 nfoukia@infoscience.otago.ac.nz Definition Sniffer Capabilities How does it work? When does it work? Preventing Sniffing Detection of Sniffing References
Packet Sniffers INFO 404 - Lecture 8 24/03/2009 nfoukia@infoscience.otago.ac.nz Definition Sniffer Capabilities How does it work? When does it work? Preventing Sniffing Detection of Sniffing References
Shortest Path First Example
 IP Exercises (Solutions in Class) 1 Shortest Path First Example Example: Received Set of Link State Update Packets (from Fig. 5-13, Computer Networks) Identity Sequence # Age List of Neighbors A 2021 60
IP Exercises (Solutions in Class) 1 Shortest Path First Example Example: Received Set of Link State Update Packets (from Fig. 5-13, Computer Networks) Identity Sequence # Age List of Neighbors A 2021 60
Lab Configuring and Verifying Standard IPv4 ACLs Topology
 Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Configuring Routes on the ACE
 CHAPTER2 This chapter describes how the ACE is considered a router hop in the network when it is in routed mode. In the Admin or user contexts, the ACE supports static routes only. The ACE supports up
CHAPTER2 This chapter describes how the ACE is considered a router hop in the network when it is in routed mode. In the Admin or user contexts, the ACE supports static routes only. The ACE supports up
COMP2330 Data Communications and Networking
 COMP2330 Data Communications and Networking Dr. Chu Xiaowen (Second semester, 2009-2010 academic year) Laboratory 3 Last update: Feb-3-2009 Use Wireshark to Analyze IP Packet Objectives: (1) Use Wireshark
COMP2330 Data Communications and Networking Dr. Chu Xiaowen (Second semester, 2009-2010 academic year) Laboratory 3 Last update: Feb-3-2009 Use Wireshark to Analyze IP Packet Objectives: (1) Use Wireshark
Lab Applying a Logical Layered Model to a Physical Network
 Lab 3.1.1 Applying a Logical Layered Model to a Physical Network Objective In this exercise, you will use various Cisco IOS commands and a protocol analyzer to map the layers in the OSI model to the encapsulated
Lab 3.1.1 Applying a Logical Layered Model to a Physical Network Objective In this exercise, you will use various Cisco IOS commands and a protocol analyzer to map the layers in the OSI model to the encapsulated
ICS 351: Networking Protocols
 ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
Lab 4: Network Packet Capture and Analysis using Wireshark
 Lab 4: Network Packet Capture and Analysis using Wireshark 4.1 Details Aim: To provide a foundation in network packet capture and analysis. You may be faced with network traffic analysis, from traffic
Lab 4: Network Packet Capture and Analysis using Wireshark 4.1 Details Aim: To provide a foundation in network packet capture and analysis. You may be faced with network traffic analysis, from traffic
Experiment 2: Wireshark as a Network Protocol Analyzer
 Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
Basics of GNS3 and Cisco IOS
 Lab00: Objectives: Basics of GNS3 and Cisco IOS IERG4090 Lab00 P.1 Upon completion of this lab, you will be able to: - Extract a given topology GNS3 archive - Start GNS3 - Open the given topology file
Lab00: Objectives: Basics of GNS3 and Cisco IOS IERG4090 Lab00 P.1 Upon completion of this lab, you will be able to: - Extract a given topology GNS3 archive - Start GNS3 - Open the given topology file
Classful Address Subnet Mask Number of Hosts per Subnet (2 x 2)
 LAB 1 Exercise 1- Subnetting exercises. Write the subnet, broadcast address, and valid host range for question 1 through question 6: 1. 192.168.100.25/30 2. 192.168.100.37/28 3. 192.168.100.66/27 4. 192.168.100.17/29
LAB 1 Exercise 1- Subnetting exercises. Write the subnet, broadcast address, and valid host range for question 1 through question 6: 1. 192.168.100.25/30 2. 192.168.100.37/28 3. 192.168.100.66/27 4. 192.168.100.17/29
Lab 4.2.5a Connectivity Tests Ping
 Lab 4.2.5a Connectivity Tests Ping Objective Use the ping command to send ICMP datagrams to target host. Verify that the network layer between source and destination is working properly. Retrieve information
Lab 4.2.5a Connectivity Tests Ping Objective Use the ping command to send ICMP datagrams to target host. Verify that the network layer between source and destination is working properly. Retrieve information
SECURITY+ LAB SERIES. Lab 3: Protocols and Default Network Ports Connecting to a Remote System
 SECURITY+ LAB SERIES Lab 3: Protocols and Default Network Ports Connecting to a Remote System Document Version: 2015-09-24 otherwise noted, is licensed under the Creative Commons Attribution 3.0 Unported
SECURITY+ LAB SERIES Lab 3: Protocols and Default Network Ports Connecting to a Remote System Document Version: 2015-09-24 otherwise noted, is licensed under the Creative Commons Attribution 3.0 Unported
Lab - Examining Telnet and SSH in Wireshark
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A PC-A NIC 192.168.1.3 255.255.255.0 192.168.1.1 Part 1: Configure the Devices
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A PC-A NIC 192.168.1.3 255.255.255.0 192.168.1.1 Part 1: Configure the Devices
Intro to OpenFlow Tutorial
 5/24/2015 GENIExperimenter/Tutorials/OpenFlowOVS GENI: geni Intro to OpenFlow Tutorial Overview: This is a simple OpenFlow tutorial that will guide you through the writing of simple OpenFlow controllers
5/24/2015 GENIExperimenter/Tutorials/OpenFlowOVS GENI: geni Intro to OpenFlow Tutorial Overview: This is a simple OpenFlow tutorial that will guide you through the writing of simple OpenFlow controllers
Introduction to Firewalls using IPTables
 Introduction to Firewalls using IPTables The goal of this lab is to implement a firewall solution using IPTables, and to write and to customize new rules to achieve security. You will need to turn in your
Introduction to Firewalls using IPTables The goal of this lab is to implement a firewall solution using IPTables, and to write and to customize new rules to achieve security. You will need to turn in your
This is a sample Lab report from ECE 461 from previous years. L A B 6
 This is a sample Lab report from ECE 461 from previous years. L A B 6 Part 1 1. o the source and destination M A C/IP addresses change when a packet traverses a bridge? Provide an explanation and include
This is a sample Lab report from ECE 461 from previous years. L A B 6 Part 1 1. o the source and destination M A C/IP addresses change when a packet traverses a bridge? Provide an explanation and include
PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab)
 PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab) Name: UT EID: 1. Differentiate between Routers, Switches, and Hubs. 2. Explain subnet masks. 3. For this lab, where is subnet
PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab) Name: UT EID: 1. Differentiate between Routers, Switches, and Hubs. 2. Explain subnet masks. 3. For this lab, where is subnet
Assignment 3 Firewalls
 LEIC/MEIC - IST Alameda LEIC/MEIC IST Taguspark Network and Computer Security 2013/2014 Assignment 3 Firewalls Goal: Configure a firewall using iptables and fwbuilder. 1 Introduction This lab assignment
LEIC/MEIC - IST Alameda LEIC/MEIC IST Taguspark Network and Computer Security 2013/2014 Assignment 3 Firewalls Goal: Configure a firewall using iptables and fwbuilder. 1 Introduction This lab assignment
Lab Configuring and Verifying Standard IPv4 ACLs (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
1. Which OSI layers offers reliable, connection-oriented data communication services?
 CCNA 1 Practice Final Exam Answers v4.0 100% 1. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 2. Refer to the exhibit.
CCNA 1 Practice Final Exam Answers v4.0 100% 1. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 2. Refer to the exhibit.
2 nd SEE 6DISS Workshop Plovdiv June Host Configuration (Windows XP) Athanassios Liakopoulos
 2 nd SEE 6DISS Workshop Plovdiv 27-29 June 2007 Host Configuration (Windows XP) Athanassios Liakopoulos aliako@grnet.gr 1. Lab information Network Topology The network topology is shown in Figure 1. PCs
2 nd SEE 6DISS Workshop Plovdiv 27-29 June 2007 Host Configuration (Windows XP) Athanassios Liakopoulos aliako@grnet.gr 1. Lab information Network Topology The network topology is shown in Figure 1. PCs
ETHICAL HACKING LAB SERIES. Lab 15: Abusing SYSTEMS
 ETHICAL HACKING LAB SERIES Lab 15: Abusing SYSTEMS Certified Ethical Hacking Domain: Denial of Service Document Version: 2015-08-14 otherwise noted, is licensed under the Creative Commons Attribution 3.0
ETHICAL HACKING LAB SERIES Lab 15: Abusing SYSTEMS Certified Ethical Hacking Domain: Denial of Service Document Version: 2015-08-14 otherwise noted, is licensed under the Creative Commons Attribution 3.0
Network+ Guide to Networks 5 th Edition. Chapter 10 In-Depth TCP/IP Networking
 Network+ Guide to Networks 5 th Edition Chapter 10 In-Depth TCP/IP Networking Objectives Understand methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Network+ Guide to Networks 5 th Edition Chapter 10 In-Depth TCP/IP Networking Objectives Understand methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Network+ Guide to Networks 6 th Edition. Chapter 9 In-Depth TCP/IP Networking
 Network+ Guide to Networks 6 th Edition Chapter 9 In-Depth TCP/IP Networking Objectives Describe methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Network+ Guide to Networks 6 th Edition Chapter 9 In-Depth TCP/IP Networking Objectives Describe methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
ACL Compliance Director Tutorial
 Abstract Copyright 2008 Cyber Operations, Inc. This is a tutorial on ACL Compliance Director intended to guide new users through the core features of the system. Table of Contents Introduction... 1 Login
Abstract Copyright 2008 Cyber Operations, Inc. This is a tutorial on ACL Compliance Director intended to guide new users through the core features of the system. Table of Contents Introduction... 1 Login
Lab 8: Introduction to Pen Testing (HPING)
 Lab 8: Introduction to Pen Testing (HPING) Aim: To provide a foundation in understanding of email with a focus on hping to provide security assessments and in understanding the trails of evidence produced.
Lab 8: Introduction to Pen Testing (HPING) Aim: To provide a foundation in understanding of email with a focus on hping to provide security assessments and in understanding the trails of evidence produced.
Static routing lab KTH/CSC. Juniper version. Group Nr. Name 1. Name 2. Name 3. Name 4. Date. Grade. Instructor s Signature
 KTH/CSC Static routing lab Juniper version Group Nr Name 1 Name 2 Name 3 Name 4 Date Grade Instructor s Signature Table of Contents 1 Goals...3 2 Preparation questions...3 3 Host configuration...4 4 Static
KTH/CSC Static routing lab Juniper version Group Nr Name 1 Name 2 Name 3 Name 4 Date Grade Instructor s Signature Table of Contents 1 Goals...3 2 Preparation questions...3 3 Host configuration...4 4 Static
LARGE SCALE IP ROUTING
 Building ISP Networks Xantaro Page 1 / 18 TABLE OF CONTENTS 1. LAB ACCESS 4 1.1 Accessing the Jumphost... 4 1.2 Access to your routers... 4 1.3 Local Network Topology... 5 1.4 Global Network Topology...
Building ISP Networks Xantaro Page 1 / 18 TABLE OF CONTENTS 1. LAB ACCESS 4 1.1 Accessing the Jumphost... 4 1.2 Access to your routers... 4 1.3 Local Network Topology... 5 1.4 Global Network Topology...
Lab 6.7.1: Ping and Traceroute
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1-ISP R2-Central Eagle Server S0/0/0 10.10.10.6 255.255.255.252 N/A Fa0/0 192.168.254.253 255.255.255.0 N/A S0/0/0
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1-ISP R2-Central Eagle Server S0/0/0 10.10.10.6 255.255.255.252 N/A Fa0/0 192.168.254.253 255.255.255.0 N/A S0/0/0
Configuration and management of Networks LAB 1 Introduction to packet tracer
 LAB 1 Introduction to packet tracer Objectives: Learn Packet Tracer to design and simulate networks. Learn to create a simple LAN with two PCs using an Ethernet hub and two straight through cables to connect
LAB 1 Introduction to packet tracer Objectives: Learn Packet Tracer to design and simulate networks. Learn to create a simple LAN with two PCs using an Ethernet hub and two straight through cables to connect
Laboratory 2 Dynamic routing using RIP. Iptables. Part1. Dynamic Routing
 Introduction Laboratory 2 Dynamic routing using RIP. Iptables. Part1. Dynamic Routing Static routing has the advantage that it is simple, requires no computing power in router for determining routes (this
Introduction Laboratory 2 Dynamic routing using RIP. Iptables. Part1. Dynamic Routing Static routing has the advantage that it is simple, requires no computing power in router for determining routes (this
Packet Tracer: Novice Session 2007 Cisco Systems, Inc. All rights reserved. Cisco Public. Packet Tracer: Novice Session
 Packet Tracer: Novice Session Packet Tracer: Novice Session 1 How Can I Use Packet Tracer? Problem Scenario: Your students need to learn how to configure a router Ethernet interface and to verify connectivity
Packet Tracer: Novice Session Packet Tracer: Novice Session 1 How Can I Use Packet Tracer? Problem Scenario: Your students need to learn how to configure a router Ethernet interface and to verify connectivity
Experiment 3: Protocol Visualization with Packet Tracer
 Experiment 3: Protocol Visualization with Packet Tracer Learning Objectives: Explore Packet Tracer Real-time mode Explore the Logical Workspace Explore Packet Tracer operation Connect devices Examine a
Experiment 3: Protocol Visualization with Packet Tracer Learning Objectives: Explore Packet Tracer Real-time mode Explore the Logical Workspace Explore Packet Tracer operation Connect devices Examine a
Contrail Sandbox Tutorial Script
 Contrail Sandbox Tutorial Script Tutorial Flow Login to lab setup Add security rules Add IP address manager Add two networks Add network policy Add two VMs (can t ping) Add network policy to networks (VMs
Contrail Sandbox Tutorial Script Tutorial Flow Login to lab setup Add security rules Add IP address manager Add two networks Add network policy Add two VMs (can t ping) Add network policy to networks (VMs
Lab - Using Wireshark to Examine a UDP DNS Capture
 Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Packet Tracer: Novice Session. Packet Tracer: Novice Session 2007 Cisco Systems, Inc. All rights reserved. Cisco Public
 Packet Tracer: Novice Session Packet Tracer: Novice Session 1 How Can I Use Packet Tracer? Problem Scenario: Your students need to learn how to configure a router Ethernet interface and to verify connectivity
Packet Tracer: Novice Session Packet Tracer: Novice Session 1 How Can I Use Packet Tracer? Problem Scenario: Your students need to learn how to configure a router Ethernet interface and to verify connectivity
Lab #9: Basic Linux Networking
 CTEC1767 Data Communications & Networking 2017 Lab #9: Basic Linux Networking Understanding Linux networks starts with understanding Linux network commands and the information they provide. We will use
CTEC1767 Data Communications & Networking 2017 Lab #9: Basic Linux Networking Understanding Linux networks starts with understanding Linux network commands and the information they provide. We will use
LAN Setup Reflection
 LAN Setup Reflection After the LAN setup, ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other
LAN Setup Reflection After the LAN setup, ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other
Lab - Using Wireshark to Examine a UDP DNS Capture
 Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
King Fahd University of Petroleum & Minerals. Data Traffic Capture and Protocols Analysis using Sniffer Tool
 King Fahd University of Petroleum & Minerals Electrical Engineering Department EE 400, Experiment # 4 Data Traffic Capture and Protocols Analysis using Sniffer Tool Objectives: After this experiment, students
King Fahd University of Petroleum & Minerals Electrical Engineering Department EE 400, Experiment # 4 Data Traffic Capture and Protocols Analysis using Sniffer Tool Objectives: After this experiment, students
Introduction to SITL. Objective
 Introduction to SITL Objective This tutorial provides a quick introduction to System-in-the-Loop (SITL) functionality, which allows physical hardware and a simulation to interact as a unified system. It
Introduction to SITL Objective This tutorial provides a quick introduction to System-in-the-Loop (SITL) functionality, which allows physical hardware and a simulation to interact as a unified system. It
Laboration 2 Troubleshooting Switching and First-Hop Redundancy
 Laboration 2 Troubleshooting Switching and First-Hop Redundancy Topology All contents are Copyright 1992 2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1
Laboration 2 Troubleshooting Switching and First-Hop Redundancy Topology All contents are Copyright 1992 2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1
EXAMGOOD QUESTION & ANSWER. Accurate study guides High passing rate! Exam Good provides update free of charge in one year!
 EXAMGOOD QUESTION & ANSWER Exam Good provides update free of charge in one year! Accurate study guides High passing rate! http://www.examgood.com Exam : 3X0-103 Title : Linux Networking (Level 1) Version
EXAMGOOD QUESTION & ANSWER Exam Good provides update free of charge in one year! Accurate study guides High passing rate! http://www.examgood.com Exam : 3X0-103 Title : Linux Networking (Level 1) Version
ETHICAL HACKING LAB SERIES. Lab 19: Using Certificates to Encrypt
 ETHICAL HACKING LAB SERIES Lab 19: Using Certificates to Encrypt Email Certified Ethical Hacking Domain: Cryptography Document Version: 2015-08-14 otherwise noted, is licensed under the Creative Commons
ETHICAL HACKING LAB SERIES Lab 19: Using Certificates to Encrypt Email Certified Ethical Hacking Domain: Cryptography Document Version: 2015-08-14 otherwise noted, is licensed under the Creative Commons
Homework 2 TCP/IP Network Monitoring and Management
 Homework 2 TCP/IP Network Monitoring and Management Hw 2 Assigned on 2015/9/1, Due 2015/9/15 Hand-In Requirement Prepare a activity/laboratory report (name it Hw4-WebSys-YourName.docx) using the ECET Lab
Homework 2 TCP/IP Network Monitoring and Management Hw 2 Assigned on 2015/9/1, Due 2015/9/15 Hand-In Requirement Prepare a activity/laboratory report (name it Hw4-WebSys-YourName.docx) using the ECET Lab
Exercises: Basics of Networking II Experiential Learning Workshop
 Exercises: Basics of Networking II Experiential Learning Workshop 1 General Guidelines 1. Make a team of two or three unless stated otherwise. 2. For each exercise, use wireshark capture to verify contents
Exercises: Basics of Networking II Experiential Learning Workshop 1 General Guidelines 1. Make a team of two or three unless stated otherwise. 2. For each exercise, use wireshark capture to verify contents
Lab: RIP v2 with VLSM
 Lab: RIP v2 with VLSM Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP PC1 PC2 PC3 PC4 PC5 Lo1 S0/0/0 Lo1 S0/0/0 S0/0/1 S/0/0/1 Learning Objectives
Lab: RIP v2 with VLSM Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP PC1 PC2 PC3 PC4 PC5 Lo1 S0/0/0 Lo1 S0/0/0 S0/0/1 S/0/0/1 Learning Objectives
Access Switch VLAN Y Y.1 /24
 Topology: Fa 0/1 VNC Server Fa 0/0 Port B Access Router Trunk VLAN X Access Switch VLAN Y Backbone Router 141.85.Y.1 /24 28.0.0.42 OSPF X.0.0.0/8 Port A 27.45.67.89 Work Station DHCP Server The Goal: Connect
Topology: Fa 0/1 VNC Server Fa 0/0 Port B Access Router Trunk VLAN X Access Switch VLAN Y Backbone Router 141.85.Y.1 /24 28.0.0.42 OSPF X.0.0.0/8 Port A 27.45.67.89 Work Station DHCP Server The Goal: Connect
CompTIA Network+ Lab Series Network Concepts. Lab 3: TCP/IP Utilities
 CompTIA Network+ Lab Series Network Concepts Lab 3: TCP/IP Utilities Objective 1.5: Identify common TCP and UDP default ports Objective 1.6: Explain the function of common networking protocols Objective
CompTIA Network+ Lab Series Network Concepts Lab 3: TCP/IP Utilities Objective 1.5: Identify common TCP and UDP default ports Objective 1.6: Explain the function of common networking protocols Objective
Lab 1: Packet Sniffing and Wireshark
 Lab 1: Packet Sniffing and Wireshark Fengwei Zhang Wayne State University Course: Cyber Security Practice 1 Packet Sniffer Packet sniffer is a basic tool for observing network packet exchanges in a computer
Lab 1: Packet Sniffing and Wireshark Fengwei Zhang Wayne State University Course: Cyber Security Practice 1 Packet Sniffer Packet sniffer is a basic tool for observing network packet exchanges in a computer
Let us ping! First we will learn the Hello World of a networked machine.
 AN INTRODUCTION TO LINUX NETWORKING In this article, we ll explore networking under GNU/Linux. You ll find it interesting to manage the entire network through certain valid keystrokes known as commands.
AN INTRODUCTION TO LINUX NETWORKING In this article, we ll explore networking under GNU/Linux. You ll find it interesting to manage the entire network through certain valid keystrokes known as commands.
Introduction to Wireshark
 Introduction to Wireshark CS3C03/SE4C03 Jason Jaskolka Department of Computing and Software Faculty of Engineering McMaster University Hamilton, Ontario, Canada jaskolj@mcmaster.ca Winter 2013 Jason Jaskolka
Introduction to Wireshark CS3C03/SE4C03 Jason Jaskolka Department of Computing and Software Faculty of Engineering McMaster University Hamilton, Ontario, Canada jaskolj@mcmaster.ca Winter 2013 Jason Jaskolka
Practical Networking. Introduction
 Practical Networking Introduction Interfaces, network connections Netstat tool Tcpdump: Popular network debugging tool Used to intercept and display packets transmitted/received on a network Filters used
Practical Networking Introduction Interfaces, network connections Netstat tool Tcpdump: Popular network debugging tool Used to intercept and display packets transmitted/received on a network Filters used
Vorlesung Kommunikationsnetze
 Picture 15 13 Vorlesung Kommunikationsnetze Prof. Dr. H. P. Großmann mit B. Wiegel sowie A. Schmeiser und M. Rabel Sommersemester 2009 Institut für Organisation und Management von Informationssystemen
Picture 15 13 Vorlesung Kommunikationsnetze Prof. Dr. H. P. Großmann mit B. Wiegel sowie A. Schmeiser und M. Rabel Sommersemester 2009 Institut für Organisation und Management von Informationssystemen
Network Security Laboratory 23 rd May STATEFUL FIREWALL LAB
 Network Security Laboratory 23 rd May 2016. STATEFUL FIREWALL LAB 1 CONTENTS INTRODUCTION I. What is Stateful Firewall II. Difference between Stateful and Stateless III. Example of Stateful firewall IV.
Network Security Laboratory 23 rd May 2016. STATEFUL FIREWALL LAB 1 CONTENTS INTRODUCTION I. What is Stateful Firewall II. Difference between Stateful and Stateless III. Example of Stateful firewall IV.
Lab IP Addresses and Network Communication
 Lab 3.5.2 IP Addresses and Network Communication Objectives Build a simple peer-to-peer network and verify physical connectivity. Assign various IP addresses to hosts and observe the effects on network
Lab 3.5.2 IP Addresses and Network Communication Objectives Build a simple peer-to-peer network and verify physical connectivity. Assign various IP addresses to hosts and observe the effects on network
1/18/13. Network+ Guide to Networks 5 th Edition. Objectives. Chapter 10 In-Depth TCP/IP Networking
 Network+ Guide to Networks 5 th Edition Chapter 10 In-Depth TCP/IP Networking Objectives Understand methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Network+ Guide to Networks 5 th Edition Chapter 10 In-Depth TCP/IP Networking Objectives Understand methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Packet Capturing with TCPDUMP command in Linux
 Packet Capturing with TCPDUMP command in Linux In this tutorial we will be looking into a very well known tool in Linux system administrators tool box. Some times during troubleshooting this tool proves
Packet Capturing with TCPDUMP command in Linux In this tutorial we will be looking into a very well known tool in Linux system administrators tool box. Some times during troubleshooting this tool proves
521262S Computer Networks 2 (fall 2007) Laboratory exercise #4: Multimedia, QoS and testing
 521262S Computer Networks 2 (fall 2007) Laboratory exercise #4: Multimedia, QoS and testing Name Student ID Signature In this exercise we will take a little look at the multimedia and Quality of Service
521262S Computer Networks 2 (fall 2007) Laboratory exercise #4: Multimedia, QoS and testing Name Student ID Signature In this exercise we will take a little look at the multimedia and Quality of Service
The Assignment is divided into preparation, practical part, and documentation.
 EINTE LAB EXERCISES LAB EXERCISE #4 IGP ROUTING PURPOSE AND GOALS This lab assignment will give you a hands-on experience in configuring and managing routers and particularly in setting up IP routing protocols.
EINTE LAB EXERCISES LAB EXERCISE #4 IGP ROUTING PURPOSE AND GOALS This lab assignment will give you a hands-on experience in configuring and managing routers and particularly in setting up IP routing protocols.
CCNA Discovery 3 Chapter 8 Reading Organizer
 Name Date Chapter 8 Reading Organizer After completion of this chapter, you should be able to: Describe traffic filtering and explain how Access Control Lists (ACLs) can filter traffic at router interfaces.
Name Date Chapter 8 Reading Organizer After completion of this chapter, you should be able to: Describe traffic filtering and explain how Access Control Lists (ACLs) can filter traffic at router interfaces.
CHAPTER 2 ACTIVITY
 CHAPTER 2 ACTIVITY 2.1.1.1 1. CLI stands for 2. GUI stands for 3. Write the step you used to go to CLI interface on Windows 4. The OS, normally loads from a disk drive, into RAM. 5. The portion of the
CHAPTER 2 ACTIVITY 2.1.1.1 1. CLI stands for 2. GUI stands for 3. Write the step you used to go to CLI interface on Windows 4. The OS, normally loads from a disk drive, into RAM. 5. The portion of the
CIS 76 VLab Pod Setup
 CIS 76 VLab Pod Setup Last updated 9/4/2017 Status on setup instructions: 1. pfsense (2.3.1, 64 bit) pfsense-ce-2.3.4-release-amd64 - DONE for Fa17 2. Kali (2017.1, 64 bit) kali-linux-2017.1-amd64.iso
CIS 76 VLab Pod Setup Last updated 9/4/2017 Status on setup instructions: 1. pfsense (2.3.1, 64 bit) pfsense-ce-2.3.4-release-amd64 - DONE for Fa17 2. Kali (2017.1, 64 bit) kali-linux-2017.1-amd64.iso
Basic Cisco Router Configuration: Multiple Routers
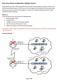 Basic Cisco Router Configuration: Multiple Routers Routers rarely exist alone. Most organizations have several to several dozens of routers. In this Lab, we will study two different ways in which routers
Basic Cisco Router Configuration: Multiple Routers Routers rarely exist alone. Most organizations have several to several dozens of routers. In this Lab, we will study two different ways in which routers
Practical Exercises in Computer Networks
 Practical Exercises in Computer Networks IP forwarding between directly connected stations, ARP and ICMP (WIP) 2015, José María Foces Morán. All rights reserved. Internet is composed of a large number
Practical Exercises in Computer Networks IP forwarding between directly connected stations, ARP and ICMP (WIP) 2015, José María Foces Morán. All rights reserved. Internet is composed of a large number
COMPUTER NETWORKING LAB EXERCISES (TP) 1 BASIC CONFIGURATION AND TOOLS FOR EVERYBODY:
 Name 1: Name 2: Group number: COMPUTER NETWORKING LAB EXERCISES (TP) 1 BASIC CONFIGURATION AND TOOLS FOR EVERYBODY: PING(6), DIG, TRACEROUTE(6), NETSTAT September 24, 2012 Abstract In this TP you will
Name 1: Name 2: Group number: COMPUTER NETWORKING LAB EXERCISES (TP) 1 BASIC CONFIGURATION AND TOOLS FOR EVERYBODY: PING(6), DIG, TRACEROUTE(6), NETSTAT September 24, 2012 Abstract In this TP you will
CS 716: Introduction to communication networks. Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay
 CS 716: Introduction to communication networks - 16 th class; 28 th Sept 2011 Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay What is IP address An identifier for a computer or device on a TCP/IP
CS 716: Introduction to communication networks - 16 th class; 28 th Sept 2011 Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay What is IP address An identifier for a computer or device on a TCP/IP
Lab - Configure the Firewall in Windows 8
 Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected over the network Windows 8 installed
Introduction In this lab, you will explore the Windows Firewall and configure some advanced settings. Recommended Equipment Two computers directly connected or connected over the network Windows 8 installed
The Addressing of Data Link Layer
 The Addressing of Data Link Layer Outline Unicast Addressing Broadcast Addressing Multicast Addressing Promiscuous Mode Summary Appendix 2 mac_addressing.xtpl 3 Unicast Addressing 4 Fill
The Addressing of Data Link Layer Outline Unicast Addressing Broadcast Addressing Multicast Addressing Promiscuous Mode Summary Appendix 2 mac_addressing.xtpl 3 Unicast Addressing 4 Fill
