Security Analysis of Common Wireless Networking Implementations
|
|
|
- Vernon Reynolds
- 6 years ago
- Views:
Transcription
1 Security Analysis of Common Wireless Networking Implementations Brian Cavanagh CMPT /12/2005 The use of wireless networking to connect to the internet has grown by leaps and bounds in recent years. From the comfort of their own homes, or from the convenient setting of their local Starbucks, computer users are wirelessly connecting to the internet in staggering numbers. Of course, security implications abound when a wireless network is in use. This paper will analyze the current state of security surrounding wireless networks. Particular attention will be paid to the implementations of Wireless Access Points (WAPs). As we will see, although a WAP may come with the means to enable stringent wireless security, they are very rarely properly configured, and encryption is very often not even enabled. The most common means for securing a wireless network is WEP (Wired Equivalent Protocol) Encryption. This paper will examine WEP Encryption, showing different methods currently utilized to break this encryption. The role of the hardware manufacturer will also be discussed. By looking at the factory default settings on three common WAPs, we will gain insight into the level of care taken by hardware manufacturers to help ensure the privacy of their consumers. Growth of Wireless Networking Since its inception, wireless networking has seen staggering year over year growth. As the use of broadband internet access continues to rise, more consumers will purchase network routers to allow the sharing of broadband access throughout the household. As with all computer hardware, the cost of network routers continues to plummet. Additionally, many routers now come bundled with wireless access point capabilities. A user must simply purchase a cheap wireless network card in order to be able to access the internet from anywhere in their house. Wireless network cards for desktops computers (PCI) or notebook computers (PCMCIA) can now routinely be found for less than $25. The adoption of broadband internet access combined with a decline in price for the requisite hardware has led to steady growth. The two figures below depict two examples of this. Page 1 of 10
2 Figure 1 Growth of Wi-fi Hotspots Hotspots (thousands) Year Source: Telecommunications Industry Association Figure enabled Hardware Devices 50 Devices (millions) Year Source: In-Stat/MDR Page 2 of 10
3 As shown in Figure 1, it is projected that there will be 45,000 wireless hotspots available in This is up from less than 5,000 in A wireless hotspot is a wireless network that has been set up for public use. The type of service is now offered at many hotels, McDonald s and Starbucks (to name a few). Figure 2 depicts the growth in sales of wireless hardware, with an estimated 40 million wireless-enabled hardware devices estimated to be sold in This includes both wireless routers and wireless network cards. Obviously, as these numbers continue to rise, so will the number of more savvy computer users looking to take advantage of those that are wireless-enabled but not mindful of their wireless security. Typical Wireless Security Pitfalls As will be shown later in this paper, the common wireless network user does very little, if anything, to secure their wireless network from the outside world. While there is no way to guarantee that any wireless network won t be compromised, there are some very easy ways to at least make a wireless network less attractive to the casual hacker. Three typical pitfalls are discussed below: Default service set identifier (SSID) WAPs come set up with an SSID. This SSID is broadcast from the router to alert in-range users to its presence. There are two things that can be done to help make a network more secure. 1. Change the default SSID Hardware manufacturers generally use the same SSID for all of their equipment. They also use the same default password. If a user doesn t change the SSID and the corresponding password, a hacker can access the administration settings of the access point. 2. Turn off the SSID broadcast Many access points come equipped with the ability to not broadcast the SSID altogether. Although there are ways for a hacker to detect the network, turning off the SSID broadcast will help to make a network less appealing. WEP Encryption WEP Encryption is a security protocol developed for use with WAPs. Although not very strong (as will be seen below), having encryption turned on makes it much more difficult to break into a network. MAC Address Filtering Every piece of hardware that is produced comes with its own MAC (Media Access Control) address. A WAP can be configured to only allow access to certain MAC addresses. This way, the owner of the network can configure the WAP to only allow traffic from devices that he or she owns. Again, this method of security is not insurmountable to an accomplished hacker, but will help keep out the average over-curious neighbor. Page 3 of 10
4 WEP Encryption WEP Encryption is the most common wireless encryption method in use today. The overwhelming majority of WAPs available today come with WEP encryption available. WEP Encryption is based on the use of a symmetric key. Once WEP is enabled, all network devices wishing to gain access to the network must be able to supply the appropriate key. WEP keys are either 64-bit or 128-bit. However, for both the 64-bit and 128-bit key, 24 bits are reserved for what is calling the Initialization Vector (IV). (This will be important later as the cracking of WEP is discussed). Rather than requiring a user to actually type 40 or 104 bits (depending upon the key size), most WAPs ask the user for a pass-phrase. The WAP then uses an algorithm to transform the pass-phrase into a key. Based on the design of the algorithm, this could open the door to the possibility of a dictionary attack, as many users will chose an English word as the pass-phrase used to generate their key. (Again, this will be significant the cracking of WEP is discussed). Cracking WEP This paper will discuss two popular methods employed to crack WEP The FMS Attack and a dictionary attack. Although, there are a number of other methods available to crack WEP, the scope of this discussion is limited to these two. The FMS Attack The FMS Attack is the most common method for cracking WEP. It was conceived by Scott Fluhrer, Itsik Mantin, and Adi Shamir in their paper Weakness in the key scheduling algorithm of RC4. The basis for the FMS attack is that the WEP key generation can result in what are called weak IVs. As mentioned above, the IV is the first 24 bits of the key. The IV is also sent in the clear so it is available to anyone within range of the wireless network. Once a significant number of weak IVs have been captured by a potential hacker, they can be used to back in to the WEP key. Certain bits within the IV are essentially used to deduce the remaining bits in the key. In order to study this attack, I set out to attack my own home wireless network. Many tools have been developed that employ the FMS attack; for this test I used a Linux-based tool called Airsnort. The hardware employed for this test is shown below: WAP Linksys BEFW11S4v.2 D-Link 520+ PCI Card Compaq W110 PCMCIA Card The design of the attack was to sniff enough data on my wireless network so as to collect enough weak IVs to allow Airsnort to discover my key. In the interest of time, I Page 4 of 10
5 set my key to 64-bits as is shown in Figure 3 below. The pass-phrase I used was project. Figure 3 In order to collect enough packets to allow Airsnort to work, I began transferring a large (4GB) file wirelessly between 2 desktop computers on my network. Once this transfer began, Airsnort started collecting packets and analyzing the IVs. As can be seen from Figure 4 below, the key for my network was cracked in 2 hours and 15 minutes. Note: Airsnort labels weak IVs as Interesting Figure 4 Page 5 of 10
6 Obviously, in a real-world example, the hacker would not be able to initiate a file transfer in order to speed up the cracking process. There are, however, a variety of tools available that will ping the WAP with dummy data and force a response. Through these responses enough data can be obtained to ultimately crack WEP. Additionally, based on the locations of the network, a potential hacker could just wait until enough data was transmitted. Dictionary Attack As mentioned above, many WAPs use an algorithm in order to create the key. The user is first asked to enter a pass-phrase which is then used to generate the key. Obviously, with the genesis of the key being a user-entered string, this particular implementation of WEP is susceptible to a dictionary attack. A dictionary attack is the process of going through a file of words and testing each one to see if it matches the key. I used a Linux-based tool called Wepattack to test this vulnerability. The exact same hardware set up was used as in the FMS attack above. Before a dictionary attack can be run, a small amount of network traffic must be collected into a dump file. To create the dump file, I used another Linux-based tool called Gkismet. Once enough data had been collected with Gkismet, I used Wepattack to attempt to break the WEP encryption. Figure 5 below shows that WEP was broken once I typed in the correct pass-phrase on the command line. Figure 5 Page 6 of 10
7 Obviously, entering possible pass-phrases one at a time is not a viable solution for using this tool. However, when using a freely-available word list of English words, the WEP encryption was once again easily cracked. (Note: In order to ensure the test would finish quickly, I changed my pass-phrase to aardvark, as the word lists are in alphabetical order). Default Settings of Wireless Access Points We have learned that cracking WEP is a relatively easy process under the right conditions. However, from a hacker s point of view, it s quite a bit easier to break into a network with no security at all than into a network with WEP enabled. In that vein, I decided to look at WAPs currently offered by 3 of the large manufacturers of wireless networking equipment Linksys, Netgear, and D-Link. In order to execute this study, I downloaded the user manual for the WAP from the manufacturer s website. In particular, I looked at the 3 WAPs below: Linksys WRT54G Netgear WPN824 D-Link DI-634M In every case, the default setting was no wireless encryption. Why would this be? Doesn t the manufacturer care about the privacy of its consumers? The answer, in short, is that they care more about their bottom line. Enabling WEP by default on the router would require the end user to enable it on each of their network devices. Although relatively easy, this would invariably lead to more support calls for the manufacturer, with each call costing them money. Therefore, the consumer is left to make sure they ve turned on some sort of encryption for their network. Wardriving Wardriving is the activity of seeking out unprotected networks in order to find those networks with minimal security. Presumably the wardriver would either use the network for free internet access, or more deviously to break into the network for personal gain. Knowing that WAPs often have no security by default, I spent an evening driving around my town (Fair Lawn, NJ) to gather data on my neighbor s security practices. To do this I used a Windows-based tool called NetStumbler, which is able to detect wireless networks and report a good amount of details on them (MAC, SSID, Channel, Vendor, etc ). My results can be seen in Figure 6 below: Page 7 of 10
8 Figure 6 Those networks with some sort of encryption are denoted by the icon with a lock. It is immediately apparent that very few networks have any encryption at all. Of the 65 networks found, only 16 (25%) used encryption. Interestingly, 42 networks (65%) had changed the default SSID, which raises the question If the user is savvy enough to change the default SSID, why not enable WEP? It is possible that some networks are left intentionally open to allow sharing of a broadband connection between neighbors. Additionally, of the 12 users with the default SSID of linksys, 4 had not changed the password for their router configuration page, thereby allowing anyone in range to change their router settings. Finally, of the 16 users that did enable encryption, every single one used WEP. A stronger encryption method called WPA (Wi-fi Protected Access) is now available but was not seen in used at all. Note: WPA is outside the scope of this paper as it focuses on actual implementations of wireless security. As proved by this exercise, WPA is not nearly as prevalent as WEP. The results of the wardriving study are seen in Figures 7 10 below: Page 8 of 10
9 Figures 7-10: Conclusions We have seen that there are a great many flaws inherent in wireless security today. However, this is not to say that a wireless network cannot be secure enough to give a user piece of mind. Specifically, although it is not by any means unbreakable, just by enabling WEP, users will likely make themselves less likely to be attacked. Also, by following some simple guidelines changing the SSID, MAC address filtering, etc, a user can make their less-savvy neighbor a much more appealing target to would-be hacker. Those users that have highly sensitive data would be encouraged to employ other means of security. That is using WPA instead of WEP, using a Virtual Private Network (VPN), or investing in a wireless Intrusion Detection System (IDS). However, for those just looking to share their broadband internet access at home, simply being mindful of enabling the tools already available should be enough to allow for piece of mind. Page 9 of 10
10 Works Cited 1. Vladimirov, Andrew; Gavrilenko, Konstantin; Mikhailovsly, Andrei. Wi-Foo, The Secrets of Wireless Hacking. Addison Wesley Fluhrer, Scott; Mantin, Itsik; Shamir, Adi. Weakness in the key scheduling algorithm of RC Article on the proliferation of wireless networks: 4. Overview of WEP Encryption: Page 10 of 10
WPA SECURITY (Wi-Fi Protected Access) Presentation. Douglas Cheathem (csc Spring 2007)
 WPA SECURITY (Wi-Fi Protected Access) Presentation By Douglas Cheathem (csc 650.01 Spring 2007) OUTLINE Introduction Security Risk Vulnerabilities Prevention Conclusion Live Demo Q & A INTRODUCTION! WPA
WPA SECURITY (Wi-Fi Protected Access) Presentation By Douglas Cheathem (csc 650.01 Spring 2007) OUTLINE Introduction Security Risk Vulnerabilities Prevention Conclusion Live Demo Q & A INTRODUCTION! WPA
Wireless Attacks and Countermeasures
 Wireless Attacks and Countermeasures Wireless Network Technology Wireless network refers to any type of computer network which is wireless, and is commonly associated with a network whose interconnections
Wireless Attacks and Countermeasures Wireless Network Technology Wireless network refers to any type of computer network which is wireless, and is commonly associated with a network whose interconnections
5 Tips to Fortify your Wireless Network
 Article ID: 5035 5 Tips to Fortify your Wireless Network Objective Although Wi-Fi networks are convenient for you and your employees, there may be unwanted clients using up the bandwidth you pay for. In
Article ID: 5035 5 Tips to Fortify your Wireless Network Objective Although Wi-Fi networks are convenient for you and your employees, there may be unwanted clients using up the bandwidth you pay for. In
Wireless Attacks and Defense. By: Dan Schade. April 9, 2006
 Wireless Attacks and Defense By: Dan Schade April 9, 2006 Schade - 2 As more and more home and business users adapt wireless technologies because of their ease of use and affordability, these devices are
Wireless Attacks and Defense By: Dan Schade April 9, 2006 Schade - 2 As more and more home and business users adapt wireless technologies because of their ease of use and affordability, these devices are
An introduction to wireless security at home, on the road and on campus. Sherry Callahan and Kyle Crane
 Out of Thin Air! An introduction to wireless security at home, on the road and on campus Sherry Callahan and Kyle Crane University of Kansas Medical Center October 5, 2009 Wireless Networking at Home Sherry
Out of Thin Air! An introduction to wireless security at home, on the road and on campus Sherry Callahan and Kyle Crane University of Kansas Medical Center October 5, 2009 Wireless Networking at Home Sherry
Wireless Security Algorithms
 (NOTE: If you are using a virtual lab to run your attacks you will need an external Wi Fi attachment. The other option is to have a direct install on your computer. Virtual labs cannot access your wireless
(NOTE: If you are using a virtual lab to run your attacks you will need an external Wi Fi attachment. The other option is to have a direct install on your computer. Virtual labs cannot access your wireless
Analyzing Wireless Security in Columbia, Missouri
 Analyzing Wireless Security in Columbia, Missouri Matthew Chittum Clayton Harper John Mixon Johnathan Walton Abstract The current state of wireless security in most areas can be estimated based on trends
Analyzing Wireless Security in Columbia, Missouri Matthew Chittum Clayton Harper John Mixon Johnathan Walton Abstract The current state of wireless security in most areas can be estimated based on trends
Wireless LAN Security (RM12/2002)
 Information Technology in Education Project Reference Materials Wireless LAN Security (RM12/2002) Infrastructure Division Education Department The Government of HKSAR www.ited.ed.gov.hk December 2002 For
Information Technology in Education Project Reference Materials Wireless LAN Security (RM12/2002) Infrastructure Division Education Department The Government of HKSAR www.ited.ed.gov.hk December 2002 For
HW/Lab 4: IPSec and Wireless Security. CS 336/536: Computer Network Security DUE 11 am on 12/01/2014 (Monday)
 HW/Lab 4: IPSec and Wireless Security CS 336/536: Computer Network Security DUE 11 am on 12/01/2014 (Monday) This HW/Lab assignment covers Lectures 8 (IPSec) and 10 (Wireless Security). Please review these
HW/Lab 4: IPSec and Wireless Security CS 336/536: Computer Network Security DUE 11 am on 12/01/2014 (Monday) This HW/Lab assignment covers Lectures 8 (IPSec) and 10 (Wireless Security). Please review these
RouterCheck Installation and Usage
 RouterCheck Installation and Usage February 16, 2015 No part of this document may be reproduced, copied, or distributed in any fashion without the express written permission of Sericon Technology Inc.
RouterCheck Installation and Usage February 16, 2015 No part of this document may be reproduced, copied, or distributed in any fashion without the express written permission of Sericon Technology Inc.
Expected Outcomes Able to design the network security for the entire network Able to develop and suggest the security plan and policy
 CHAPTER 9 DEVELOPING NETWORK SECURITY STRATEGIES Expected Outcomes Able to design the network security for the entire network Able to develop and suggest the security plan and policy Network Security Design
CHAPTER 9 DEVELOPING NETWORK SECURITY STRATEGIES Expected Outcomes Able to design the network security for the entire network Able to develop and suggest the security plan and policy Network Security Design
Digital Entertainment. Networking Made Easy
 Digital Entertainment 2003 by TiVo Inc. Reproduction in whole or in part without written permission is prohibited. All rights reserved. Printed in the USA. TiVo, TiVo Central, and TiVolution are registered
Digital Entertainment 2003 by TiVo Inc. Reproduction in whole or in part without written permission is prohibited. All rights reserved. Printed in the USA. TiVo, TiVo Central, and TiVolution are registered
Multi-Layered Security Framework for Metro-Scale Wi-Fi Networks
 Multi-Layered Security Framework for Metro-Scale Wi-Fi Networks A Security Whitepaper January, 2004 Photo courtesy of NASA Image exchange. Image use in no way implies endorsement by NASA of any of the
Multi-Layered Security Framework for Metro-Scale Wi-Fi Networks A Security Whitepaper January, 2004 Photo courtesy of NASA Image exchange. Image use in no way implies endorsement by NASA of any of the
Packet: Data can be broken into distinct pieces or packets and then reassembled after delivery. Computers on the Internet communicate via packets.
 Broadband Setup from A to Z Print out all the info below and get to work...have fun!! A word of caution! It is very important that you SECURE your wireless network using WEP or WPA encryption (password).
Broadband Setup from A to Z Print out all the info below and get to work...have fun!! A word of caution! It is very important that you SECURE your wireless network using WEP or WPA encryption (password).
What is a Wireless LAN? The wireless telegraph is not difficult to understand. The ordinary telegraph is like a very long cat. You pull the tail in Ne
 Introduction to Wireless Networking and Security Chino Information Technology Center Steve Siedschlag, Associate Professor What is a Wireless LAN? The wireless telegraph is not difficult to understand.
Introduction to Wireless Networking and Security Chino Information Technology Center Steve Siedschlag, Associate Professor What is a Wireless LAN? The wireless telegraph is not difficult to understand.
2013 Summer Camp: Wireless LAN Security Exercises JMU Cyber Defense Boot Camp
 2013 Summer Camp: Wireless LAN Security Exercises 2013 JMU Cyber Defense Boot Camp Questions Have you used a wireless local area network before? At home? At work? Have you configured a wireless AP before?
2013 Summer Camp: Wireless LAN Security Exercises 2013 JMU Cyber Defense Boot Camp Questions Have you used a wireless local area network before? At home? At work? Have you configured a wireless AP before?
CYBER ATTACKS EXPLAINED: WIRELESS ATTACKS
 CYBER ATTACKS EXPLAINED: WIRELESS ATTACKS Wireless networks are everywhere, from the home to corporate data centres. They make our lives easier by avoiding bulky cables and related problems. But with these
CYBER ATTACKS EXPLAINED: WIRELESS ATTACKS Wireless networks are everywhere, from the home to corporate data centres. They make our lives easier by avoiding bulky cables and related problems. But with these
Wireless Network Defensive Strategies
 Wireless Network Defensive Strategies Jay A. Crossler ECE 646 Analytical Project 12 Dec 2003 Topics Wireless Security Intrusion Experiment Initial Findings Attempted Attacks Results WEP Vulnerabilities
Wireless Network Defensive Strategies Jay A. Crossler ECE 646 Analytical Project 12 Dec 2003 Topics Wireless Security Intrusion Experiment Initial Findings Attempted Attacks Results WEP Vulnerabilities
How to connect to a Wi-Fi or Wireless Network
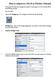 How to connect to a Wi-Fi or Wireless Network This guide will walk you through the steps of connecting to a Wi-Fi network that is broadcasting its name. Start the ipad. 1. Tap on the Settings app. The
How to connect to a Wi-Fi or Wireless Network This guide will walk you through the steps of connecting to a Wi-Fi network that is broadcasting its name. Start the ipad. 1. Tap on the Settings app. The
Smart speakers (like the Amazon Echo shown here), appliances, and equipment connect to the Internet, allowing you to access information using voice
 Smart speakers (like the Amazon Echo shown here), appliances, and equipment connect to the Internet, allowing you to access information using voice commands, or use your mobile device or computer as a
Smart speakers (like the Amazon Echo shown here), appliances, and equipment connect to the Internet, allowing you to access information using voice commands, or use your mobile device or computer as a
Security in IEEE Networks
 Security in IEEE 802.11 Networks Mário Nunes, Rui Silva, António Grilo March 2013 Sumário 1 Introduction to the Security Services 2 Basic security mechanisms in IEEE 802.11 2.1 Hidden SSID (Service Set
Security in IEEE 802.11 Networks Mário Nunes, Rui Silva, António Grilo March 2013 Sumário 1 Introduction to the Security Services 2 Basic security mechanisms in IEEE 802.11 2.1 Hidden SSID (Service Set
Wireless Network Security
 Wireless Network Security Why wireless? Wifi, which is short for wireless fi something, allows your computer to connect to the Internet using magic. -Motel 6 commercial 2 but it comes at a price Wireless
Wireless Network Security Why wireless? Wifi, which is short for wireless fi something, allows your computer to connect to the Internet using magic. -Motel 6 commercial 2 but it comes at a price Wireless
Main area: Security Additional areas: Digital Access, Information Literacy, Privacy and Reputation
 Public Wi Fi Created: March 2016 Last Updated: July 2018 Estimated time: Group or individual activity: Ages: 60 minutes [10 minutes] Activity #1 [15 minutes] Activity #2 [10 minutes] Activity #3 [10 minutes]
Public Wi Fi Created: March 2016 Last Updated: July 2018 Estimated time: Group or individual activity: Ages: 60 minutes [10 minutes] Activity #1 [15 minutes] Activity #2 [10 minutes] Activity #3 [10 minutes]
Wi-Net Window and Rogue Access Points
 Wi-Net Window and Rogue Access Points The Wi-Net Window (WP150) has several features that make it ideal for detecting and locating rogue access points: A rogue access point is a wireless access point that
Wi-Net Window and Rogue Access Points The Wi-Net Window (WP150) has several features that make it ideal for detecting and locating rogue access points: A rogue access point is a wireless access point that
WIRELESS EVIL TWIN ATTACK
 WIRELESS EVIL TWIN ATTACK Prof. Pragati Goel Associate Professor, NCRD s Sterling Institute of Management Studies, Navi Mumbai Mr. Chetan Singh NCRD s Sterling Institute Of Management Studie, Navi Mumbai
WIRELESS EVIL TWIN ATTACK Prof. Pragati Goel Associate Professor, NCRD s Sterling Institute of Management Studies, Navi Mumbai Mr. Chetan Singh NCRD s Sterling Institute Of Management Studie, Navi Mumbai
Wireless Network Security
 Wireless Network Security By: Jose Rodriguez Table of Contents Wireless Network Security...1 Table of Contents...2 Introduction...3 Wireless Network Requirements...4 Wireless Network Protocols...5 Wireless
Wireless Network Security By: Jose Rodriguez Table of Contents Wireless Network Security...1 Table of Contents...2 Introduction...3 Wireless Network Requirements...4 Wireless Network Protocols...5 Wireless
Cryptanalysis. Ed Crowley
 Cryptanalysis Ed Crowley 1 Topics Cryptanalysis History Modern Cryptanalysis Characterization of Cryptanalysis Attacks Attack Types 2 Cryptanalysis Science of cracking ciphers and codes, decoding secrets,
Cryptanalysis Ed Crowley 1 Topics Cryptanalysis History Modern Cryptanalysis Characterization of Cryptanalysis Attacks Attack Types 2 Cryptanalysis Science of cracking ciphers and codes, decoding secrets,
Wireless Networking. Chapter The McGraw-Hill Companies, Inc. All rights reserved
 Wireless Networking Chapter 23 Overview In this chapter, you will learn how to Discuss wireless networking components Analyze and explain wireless networking standards Install and configure wireless networks
Wireless Networking Chapter 23 Overview In this chapter, you will learn how to Discuss wireless networking components Analyze and explain wireless networking standards Install and configure wireless networks
Wireless Security and Monitoring. Training materials for wireless trainers
 Wireless Security and Monitoring Training materials for wireless trainers Goals to understand which security issues are important to consider when designing WiFi networks to be introduced to encryption,
Wireless Security and Monitoring Training materials for wireless trainers Goals to understand which security issues are important to consider when designing WiFi networks to be introduced to encryption,
Karthik Pinnamaneni COEN 150 Wireless Network Security Dr. Joan Holliday 5/21/03
 Karthik Pinnamaneni COEN 150 Wireless Network Security Dr. Joan Holliday 5/21/03 Introduction Although a variety of wireless network technologies have or will soon reach the general business market, wireless
Karthik Pinnamaneni COEN 150 Wireless Network Security Dr. Joan Holliday 5/21/03 Introduction Although a variety of wireless network technologies have or will soon reach the general business market, wireless
Securing Wireless Networks by By Joe Klemencic Mon. Apr
 http://www.cymru.com/ Securing Wireless Networks by By Joe Klemencic (faz@home.com) Mon. Apr 30 2001 Many companies make attempts to embrace new technologies, but unfortunately, many of these new technologies
http://www.cymru.com/ Securing Wireless Networks by By Joe Klemencic (faz@home.com) Mon. Apr 30 2001 Many companies make attempts to embrace new technologies, but unfortunately, many of these new technologies
Ready Theatre Systems RTS POS
 Ready Theatre Systems RTS POS PCI PA-DSS Implementation Guide Revision: 2.0 September, 2010 Ready Theatre Systems, LLC - www.rts-solutions.com Table of Contents: Introduction to PCI PA DSS Compliance 2
Ready Theatre Systems RTS POS PCI PA-DSS Implementation Guide Revision: 2.0 September, 2010 Ready Theatre Systems, LLC - www.rts-solutions.com Table of Contents: Introduction to PCI PA DSS Compliance 2
Section 4 Cracking Encryption and Authentication
 Section 4 Cracking 802.11 Encryption and Authentication In the previous section we showed the vulnerabilities of Open Wireless LANs. In this section we ll show some of the techniques and tools used to
Section 4 Cracking 802.11 Encryption and Authentication In the previous section we showed the vulnerabilities of Open Wireless LANs. In this section we ll show some of the techniques and tools used to
Outline : Wireless Networks Lecture 10: Management. Management and Control Services : Infrastructure Reminder.
 Outline 18-759: Wireless Networks Lecture 10: 802.11 Management Peter Steenkiste Departments of Computer Science and Electrical and Computer Engineering Spring Semester 2016 http://www.cs.cmu.edu/~prs/wirelesss16/
Outline 18-759: Wireless Networks Lecture 10: 802.11 Management Peter Steenkiste Departments of Computer Science and Electrical and Computer Engineering Spring Semester 2016 http://www.cs.cmu.edu/~prs/wirelesss16/
Wireless technology Principles of Security
 Wireless technology Principles of Security 1 Wireless technologies 2 Overview This module provides an introduction to the rapidly evolving technology of wireless LANs (WLANs). WLANs redefine the way the
Wireless technology Principles of Security 1 Wireless technologies 2 Overview This module provides an introduction to the rapidly evolving technology of wireless LANs (WLANs). WLANs redefine the way the
Procedure: You can find the problem sheet on the Desktop of the lab PCs.
 University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Advance Networks Laboratory 907529 Lab.3 WLAN Security Objectives 1. Configure administrator accounts.
University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Advance Networks Laboratory 907529 Lab.3 WLAN Security Objectives 1. Configure administrator accounts.
WIRELESS N USB ADAPTER USER MANUAL
 WIRELESS N USB ADAPTER USER MANUAL MAN-525503/525534-UM-0413-01 INTRODUCTION Thank you for purchasing this Manhattan Wireless N USB Adapter. Because many netbooks and laptops (especially those more than
WIRELESS N USB ADAPTER USER MANUAL MAN-525503/525534-UM-0413-01 INTRODUCTION Thank you for purchasing this Manhattan Wireless N USB Adapter. Because many netbooks and laptops (especially those more than
USER GUIDE. Wireless-G Broadband Router. Model No: WRT54G2 V1
 USER GUIDE Wireless-G Broadband Router Model No: WRT54G2 V1 About This Guide About This Guide Icon Descriptions While reading through the User Guide you may see various icons that call attention to specific
USER GUIDE Wireless-G Broadband Router Model No: WRT54G2 V1 About This Guide About This Guide Icon Descriptions While reading through the User Guide you may see various icons that call attention to specific
BreezeACCESS VL Security
 BreezeACCESS VL Security Technical Paper Alvarion Ltd. All rights reserved. The material contained herein is proprietary. No part of this publication may be reproduced in any form without the express written
BreezeACCESS VL Security Technical Paper Alvarion Ltd. All rights reserved. The material contained herein is proprietary. No part of this publication may be reproduced in any form without the express written
How to Stay Safe on Public Wi-Fi Networks
 How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
THE 123 OF WIRELESS SECURITY AT HOME 家居 WIFI 保安 123
 THE 123 OF WIRELESS SECURITY AT HOME 家居 WIFI 保安 123 CONFIGURING YOUR HOME WIRELESS NETWORK Presented by: Au Shun Yi, Choi Kai San and Ngan Tsz Him of Hong Kong Institute of Vocational Education (Chai Wan)
THE 123 OF WIRELESS SECURITY AT HOME 家居 WIFI 保安 123 CONFIGURING YOUR HOME WIRELESS NETWORK Presented by: Au Shun Yi, Choi Kai San and Ngan Tsz Him of Hong Kong Institute of Vocational Education (Chai Wan)
Overview of Security
 Overview of 802.11 Security Bingdong Li Present for CPE 601 2/9/2011 Sources: 1 Jesse Walker (Intel) & 2. WinLab 1 Agenda Introduction 802.11 Basic Security Mechanisms What s Wrong? Major Risks Recommendations
Overview of 802.11 Security Bingdong Li Present for CPE 601 2/9/2011 Sources: 1 Jesse Walker (Intel) & 2. WinLab 1 Agenda Introduction 802.11 Basic Security Mechanisms What s Wrong? Major Risks Recommendations
and the Forensic Science CC Spring 2007 Prof. Nehru
 and the Introduction The Internet, (Information superhighway), has opened a medium for people to communicate and to access millions of pieces of information from computers located anywhere on the globe.
and the Introduction The Internet, (Information superhighway), has opened a medium for people to communicate and to access millions of pieces of information from computers located anywhere on the globe.
Basic Wireless Settings on the CVR100W VPN Router
 Basic Wireless Settings on the CVR100W VPN Router Objective A Wireless Local Area Network (WLAN) utilizes radio communication to connect wireless devices to a LAN. An example is a Wi-Fi hotspot at a cafe.
Basic Wireless Settings on the CVR100W VPN Router Objective A Wireless Local Area Network (WLAN) utilizes radio communication to connect wireless devices to a LAN. An example is a Wi-Fi hotspot at a cafe.
Cryptography ThreeB. Ed Crowley. Fall 08
 Cryptography ThreeB Ed Crowley Fall 08 Cryptanalysis History Modern Cryptanalysis Characterization of Cryptanalysis Attacks Attack Types Cryptanalysis. Science of cracking ciphers and codes, decoding secrets,
Cryptography ThreeB Ed Crowley Fall 08 Cryptanalysis History Modern Cryptanalysis Characterization of Cryptanalysis Attacks Attack Types Cryptanalysis. Science of cracking ciphers and codes, decoding secrets,
Wireless Fidelity Real Time Security System
 Wireless Fidelity Real Time Security System V.C.K.P Arul Oli 1 Assistant professor Dept. of Computer Application s Dhanalakshmi College of Engineering, Chennai. vckparuloli@yahoo.co.in Elayaraja Ponram
Wireless Fidelity Real Time Security System V.C.K.P Arul Oli 1 Assistant professor Dept. of Computer Application s Dhanalakshmi College of Engineering, Chennai. vckparuloli@yahoo.co.in Elayaraja Ponram
A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e. Chapter 10 Networking Essentials
 A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e Chapter 10 Networking Essentials Objectives Learn about hardware devices used for networking Learn about the different types of networks
A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e Chapter 10 Networking Essentials Objectives Learn about hardware devices used for networking Learn about the different types of networks
Improving Security in Wireless Networks
 Improving Security in Wireless Networks Introduction Wireless networking provides many advantages over conventional wired networks. For instance the ability to connect to your network resources without
Improving Security in Wireless Networks Introduction Wireless networking provides many advantages over conventional wired networks. For instance the ability to connect to your network resources without
Chapter 5 Local Area Networks. Computer Concepts 2013
 Chapter 5 Local Area Networks Computer Concepts 2013 5 Chapter Contents Section A: Network Building Blocks Section B: Wired and Wireless Technologies Section C: Network Setup Section D: Sharing Files Section
Chapter 5 Local Area Networks Computer Concepts 2013 5 Chapter Contents Section A: Network Building Blocks Section B: Wired and Wireless Technologies Section C: Network Setup Section D: Sharing Files Section
Cyber Security Guidelines for Securing Home and Small Office Routers
 Cyber Security Guidelines for Securing Home and Small Office Routers Author: CS Risk Management Section Document Published Date: March 2018 Document History: Version Description Date 1.0 Published V1.0
Cyber Security Guidelines for Securing Home and Small Office Routers Author: CS Risk Management Section Document Published Date: March 2018 Document History: Version Description Date 1.0 Published V1.0
Configuring Wireless Security Settings on the RV130W
 Article ID: 5021 Configuring Wireless Security Settings on the RV130W Objective Wireless networking operates by sending information over radio waves, which can be more vulnerable to intruders than a traditional
Article ID: 5021 Configuring Wireless Security Settings on the RV130W Objective Wireless networking operates by sending information over radio waves, which can be more vulnerable to intruders than a traditional
How To Make Belkin Wireless Router Password Protected
 How To Make Belkin Wireless Router Password Protected Wi-Fi Protected Access (WPA) is a type of wireless security which is dynamic in nature. This means Guidelines in creating a wireless password or passphrase
How To Make Belkin Wireless Router Password Protected Wi-Fi Protected Access (WPA) is a type of wireless security which is dynamic in nature. This means Guidelines in creating a wireless password or passphrase
Wireless MAXg Technology
 Wireless MAXg Technology MAXimizing range, performance, security and simplicity for 802.11g networks Technology Note Wireless technology has undoubtedly become a ubiquitous presence in our computing environment,
Wireless MAXg Technology MAXimizing range, performance, security and simplicity for 802.11g networks Technology Note Wireless technology has undoubtedly become a ubiquitous presence in our computing environment,
Technology in Action. Chapter Topics. Participation Question. Participation Question 8/17/11. Chapter 7 Networking: Connecting Computing Devices
 Technology in Action Chapter 7 Networking: Connecting Computing Devices 1 2 Chapter Topics Networking fundamentals Network architecture Network components Peer-to-peer networks Ethernet networks Power-line
Technology in Action Chapter 7 Networking: Connecting Computing Devices 1 2 Chapter Topics Networking fundamentals Network architecture Network components Peer-to-peer networks Ethernet networks Power-line
Temporal Key Integrity Protocol: TKIP. Tim Fielder University of Tulsa Tulsa, Oklahoma
 Temporal Key Integrity Protocol: TKIP Tim Fielder University of Tulsa Tulsa, Oklahoma History IEEE released the first 802.11 specification back in 1997 The Wired Equivalent Privacy (WEP) authentication/encryption
Temporal Key Integrity Protocol: TKIP Tim Fielder University of Tulsa Tulsa, Oklahoma History IEEE released the first 802.11 specification back in 1997 The Wired Equivalent Privacy (WEP) authentication/encryption
NDSU Wireless. Bruce Curtis David Dahl Valerie Nordsletten
 NDSU Wireless Bruce Curtis David Dahl Valerie Nordsletten Wireless Security Acronyms WEP = Wired Equivalent Privacy WPA = Wi-Fi Protected Access WEP is broken WEP really means Won t Even Protect WPA is
NDSU Wireless Bruce Curtis David Dahl Valerie Nordsletten Wireless Security Acronyms WEP = Wired Equivalent Privacy WPA = Wi-Fi Protected Access WEP is broken WEP really means Won t Even Protect WPA is
Configuring your Home Wireless Network
 Configuring your Home Wireless Network Questions How many of you have more than one computer at home? How many of you connect to the Internet using broadband (Cable or DSL) How many already have a home
Configuring your Home Wireless Network Questions How many of you have more than one computer at home? How many of you connect to the Internet using broadband (Cable or DSL) How many already have a home
Wireless (Select Models Only) User Guide
 Wireless (Select Models Only) User Guide Copyright 2008 Hewlett-Packard Development Company, L.P. Windows is a U.S. registered trademark of Microsoft Corporation. Bluetooth is a trademark owned by its
Wireless (Select Models Only) User Guide Copyright 2008 Hewlett-Packard Development Company, L.P. Windows is a U.S. registered trademark of Microsoft Corporation. Bluetooth is a trademark owned by its
Wireless Setup Instructions
 Wireless Setup Instructions THESE INSTRUCTIONS ARE VERY IMPORTANT TO SECURE YOUR WIRELESS NETWORK The purpose of this procedure is to "lock" your router so other users can not access your network without
Wireless Setup Instructions THESE INSTRUCTIONS ARE VERY IMPORTANT TO SECURE YOUR WIRELESS NETWORK The purpose of this procedure is to "lock" your router so other users can not access your network without
WPA Passive Dictionary Attack Overview
 WPA Passive Dictionary Attack Overview TakehiroTakahashi This short paper presents an attack against the Pre-Shared Key version of the WPA encryption platform and argues the need for replacement. What
WPA Passive Dictionary Attack Overview TakehiroTakahashi This short paper presents an attack against the Pre-Shared Key version of the WPA encryption platform and argues the need for replacement. What
A Configuration Protocol for Embedded Devices on Secure Wireless Networks
 A Configuration Protocol for Embedded Devices on Secure Wireless Networks Larry Sanders lsanders@ittc.ku.edu 6 May 2003 Introduction Wi-Fi Alliance Formally Wireless Ethernet Compatibility Alliance (WECA)
A Configuration Protocol for Embedded Devices on Secure Wireless Networks Larry Sanders lsanders@ittc.ku.edu 6 May 2003 Introduction Wi-Fi Alliance Formally Wireless Ethernet Compatibility Alliance (WECA)
Key questions to ask before commissioning any web designer to build your website.
 Key questions to ask before commissioning any web designer to build your website. KEY QUESTIONS TO ASK Before commissioning a web designer to build your website. As both an entrepreneur and business owner,
Key questions to ask before commissioning any web designer to build your website. KEY QUESTIONS TO ASK Before commissioning a web designer to build your website. As both an entrepreneur and business owner,
LESSON 12: WI FI NETWORKS SECURITY
 LESSON 12: WI FI NETWORKS SECURITY Raúl Siles raul@taddong.com Founder and Security Analyst at Taddong Introduction to Wi Fi Network Security Wireless networks or Wi Fi networks IEEE 802.11 Standards Information
LESSON 12: WI FI NETWORKS SECURITY Raúl Siles raul@taddong.com Founder and Security Analyst at Taddong Introduction to Wi Fi Network Security Wireless networks or Wi Fi networks IEEE 802.11 Standards Information
CS-435 spring semester Network Technology & Programming Laboratory. Stefanos Papadakis & Manolis Spanakis
 CS-435 spring semester 2016 Network Technology & Programming Laboratory University of Crete Computer Science Department Stefanos Papadakis & Manolis Spanakis CS-435 Lecture preview 802.11 Security IEEE
CS-435 spring semester 2016 Network Technology & Programming Laboratory University of Crete Computer Science Department Stefanos Papadakis & Manolis Spanakis CS-435 Lecture preview 802.11 Security IEEE
تاثیرفناوری اطالعات برسازمان ومدیریت جلسه هشتم و نهم
 بنام خدا تاثیرفناوری اطالعات برسازمان ومدیریت جلسه هشتم و نهم امنیت بخشی به سیستمهای فناوری اطالعات Securing Information Systems 1 Learning Objectives Describe the business value of security and control.
بنام خدا تاثیرفناوری اطالعات برسازمان ومدیریت جلسه هشتم و نهم امنیت بخشی به سیستمهای فناوری اطالعات Securing Information Systems 1 Learning Objectives Describe the business value of security and control.
Chapter 11: Networks
 Chapter 11: Networks Devices in a Small Network Small Network A small network can comprise a few users, one router, one switch. A Typical Small Network Topology looks like this: Device Selection Factors
Chapter 11: Networks Devices in a Small Network Small Network A small network can comprise a few users, one router, one switch. A Typical Small Network Topology looks like this: Device Selection Factors
Add a Wireless Network to an Existing Wired Network using a Wireless Access Point (WAP)
 Add a Wireless Network to an Existing Wired Network using a Wireless Access Point (WAP) Objective A Wireless Access Point (WAP) is a networking device that allows wireless-capable devices to connect to
Add a Wireless Network to an Existing Wired Network using a Wireless Access Point (WAP) Objective A Wireless Access Point (WAP) is a networking device that allows wireless-capable devices to connect to
PASS4TEST. IT Certification Guaranteed, The Easy Way! We offer free update service for one year
 PASS4TEST IT Certification Guaranteed, The Easy Way! \ http://www.pass4test.com We offer free update service for one year Exam : GSLC Title : GIAC Security Leadership Certification (GSLC) Vendors : GIAC
PASS4TEST IT Certification Guaranteed, The Easy Way! \ http://www.pass4test.com We offer free update service for one year Exam : GSLC Title : GIAC Security Leadership Certification (GSLC) Vendors : GIAC
Chapter 3 Wireless Configuration
 Chapter 3 Wireless Configuration This chapter describes how to configure the wireless features of your WNR854T router. In planning your wireless network, you should consider the level of security required.
Chapter 3 Wireless Configuration This chapter describes how to configure the wireless features of your WNR854T router. In planning your wireless network, you should consider the level of security required.
If you have multiple computers in the same place, you may find it convenient
 Chapter 1: Networking Your Macs In This Chapter Creating a wired network Creating a wireless network Setting up an Airport Extreme base station Connecting to a mobile phone or PDA If you have multiple
Chapter 1: Networking Your Macs In This Chapter Creating a wired network Creating a wireless network Setting up an Airport Extreme base station Connecting to a mobile phone or PDA If you have multiple
In the previous column (September
 Hal Berghel and Jacob Uecker Wireless Infidelity II: Airjacking Assessing the extent of the security risks involved in wireless networking technology by considering three possible scenarios demonstrating
Hal Berghel and Jacob Uecker Wireless Infidelity II: Airjacking Assessing the extent of the security risks involved in wireless networking technology by considering three possible scenarios demonstrating
PASS4TEST. IT Certification Guaranteed, The Easy Way! We offer free update service for one year
 PASS4TEST IT Certification Guaranteed, The Easy Way! \ http://www.pass4test.com We offer free update service for one year Exam : ECSS Title : EC-Council Certified Security Specialist Practice Test Vendors
PASS4TEST IT Certification Guaranteed, The Easy Way! \ http://www.pass4test.com We offer free update service for one year Exam : ECSS Title : EC-Council Certified Security Specialist Practice Test Vendors
Wireless LANs, Best Practices Session Two
 Wireless LANs, Best Practices Session Two David W. Borden, CISSP Senior Systems Engineer Lockheed Martin Corporation david.borden@lackland.af.mil dborden@gvtc.com August 4, 2004 David W. Borden 2004 Slide
Wireless LANs, Best Practices Session Two David W. Borden, CISSP Senior Systems Engineer Lockheed Martin Corporation david.borden@lackland.af.mil dborden@gvtc.com August 4, 2004 David W. Borden 2004 Slide
The Launch GDS can be updated via a wireless internet connection as well as by USB or cat5 cable.
 LAUNCH Wifi Setup Procedure The Launch GDS can be updated via a wireless internet connection as well as by USB or cat5 cable. If you are in a wifi hotspot or have an open network available simply choose
LAUNCH Wifi Setup Procedure The Launch GDS can be updated via a wireless internet connection as well as by USB or cat5 cable. If you are in a wifi hotspot or have an open network available simply choose
Internet of Things (IoT) Attacks. The Internet of Things (IoT) is based off a larger concept; the Internet of Things came
 Victoria Ellsworth Dr. Ping Li ICTN 4040 04/11/17 Internet of Things (IoT) Attacks The Internet of Things (IoT) is based off a larger concept; the Internet of Things came from idea of the Internet of Everything.
Victoria Ellsworth Dr. Ping Li ICTN 4040 04/11/17 Internet of Things (IoT) Attacks The Internet of Things (IoT) is based off a larger concept; the Internet of Things came from idea of the Internet of Everything.
FOR MORE INFORMATION: CALL VISIT telstrabusiness.com VISIT A TELSTRA BUSINESS CENTRE OR PARTNER
 FOR MORE INFORMATION: CALL 13 2000 VISIT telstrabusiness.com VISIT A TELSTRA BUSINESS CENTRE OR PARTNER GETTING TO KNOW YOUR TELSTRA ULTIMATE GATEWAY LET S GET THIS SHOW ON THE ROAD You must be excited
FOR MORE INFORMATION: CALL 13 2000 VISIT telstrabusiness.com VISIT A TELSTRA BUSINESS CENTRE OR PARTNER GETTING TO KNOW YOUR TELSTRA ULTIMATE GATEWAY LET S GET THIS SHOW ON THE ROAD You must be excited
Controlling Website Account Information. A recent survey done by Privacy Rights Clearinghouse shows that in the past five years
 Colson 1 Alex Colson Dr. Lunsford Information Security Management 10 July 2007 Controlling Website Account Information A recent survey done by Privacy Rights Clearinghouse shows that in the past five years
Colson 1 Alex Colson Dr. Lunsford Information Security Management 10 July 2007 Controlling Website Account Information A recent survey done by Privacy Rights Clearinghouse shows that in the past five years
Wireless LAN Security. Gabriel Clothier
 Wireless LAN Security Gabriel Clothier Timeline 1997: 802.11 standard released 1999: 802.11b released, WEP proposed [1] 2003: WiFi alliance certifies for WPA 2004: 802.11i released 2005: 802.11w task group
Wireless LAN Security Gabriel Clothier Timeline 1997: 802.11 standard released 1999: 802.11b released, WEP proposed [1] 2003: WiFi alliance certifies for WPA 2004: 802.11i released 2005: 802.11w task group
WarDriving. related fixed line attacks war dialing port scanning
 WarDriving slide 1 related fixed line attacks war dialing port scanning war driving drive through a metropolitan area looking for wireless access points software logs, latidute/longitude runs software
WarDriving slide 1 related fixed line attacks war dialing port scanning war driving drive through a metropolitan area looking for wireless access points software logs, latidute/longitude runs software
Wireless Network Security Fundamentals and Technologies
 Wireless Network Security Fundamentals and Technologies Rakesh V S 1, Ganesh D R 2, Rajesh Kumar S 3, Puspanathan G 4 1,2,3,4 Department of Computer Science and Engineering, Cambridge Institute of Technology
Wireless Network Security Fundamentals and Technologies Rakesh V S 1, Ganesh D R 2, Rajesh Kumar S 3, Puspanathan G 4 1,2,3,4 Department of Computer Science and Engineering, Cambridge Institute of Technology
Wi-Fi - Why for? A Word About Spectrum. I T I n f r a s t r u c t u r e S o l u t i o n s
 I T I n f r a s t r u c t u r e S o l u t i o n s Note: The following technical article was current at the time it was published. However, due to changing technologies and standards updates, some of the
I T I n f r a s t r u c t u r e S o l u t i o n s Note: The following technical article was current at the time it was published. However, due to changing technologies and standards updates, some of the
Fix Home Network. Thousands of satisfied users! Easy steps to setup Wireless router with Cable or DSL internet service provider.
 Fix Home Network Thousands of satisfied users! Easy steps to setup Wireless router with Cable or DSL internet service provider. Copyright, Legal Notice and Disclaimer: This publication is protected under
Fix Home Network Thousands of satisfied users! Easy steps to setup Wireless router with Cable or DSL internet service provider. Copyright, Legal Notice and Disclaimer: This publication is protected under
Table of Contents. Camera Anatomy... pg 1. Package Contents... pg 2. Camera Assembly... pg 3. Account Login... pg 5. Adding a New Camera...
 Table of Contents Camera Anatomy... pg 1 Package Contents... pg 2 Camera Assembly... pg 3 Account Login... pg 5 Adding a New Camera... pg 6 Wireless Configuration... pg 9 WPS Enabled Routers... pg 13 Technical
Table of Contents Camera Anatomy... pg 1 Package Contents... pg 2 Camera Assembly... pg 3 Account Login... pg 5 Adding a New Camera... pg 6 Wireless Configuration... pg 9 WPS Enabled Routers... pg 13 Technical
Computers and Security
 The contents of this Supporting Material document have been prepared from the Eight units of study texts for the course M150: Date, Computing and Information, produced by The Open University, UK. Copyright
The contents of this Supporting Material document have been prepared from the Eight units of study texts for the course M150: Date, Computing and Information, produced by The Open University, UK. Copyright
NWD2705. User s Guide. Quick Start Guide. Dual-Band Wireless N450 USB Adapter. Version 1.00 Edition 1, 09/2012
 NWD2705 Dual-Band Wireless N450 USB Adapter Version 1.00 Edition 1, 09/2012 Quick Start Guide User s Guide www.zyxel.com Copyright 2012 ZyXEL Communications Corporation IMPORTANT! READ CAREFULLY BEFORE
NWD2705 Dual-Band Wireless N450 USB Adapter Version 1.00 Edition 1, 09/2012 Quick Start Guide User s Guide www.zyxel.com Copyright 2012 ZyXEL Communications Corporation IMPORTANT! READ CAREFULLY BEFORE
Configuring WEP and WEP Features
 CHAPTER 9 This chapter describes how to configure Wired Equivalent Privacy (WEP), Message Integrity Check (MIC), and Temporal Key Integrity Protocol (TKIP). This chapter contains these sections: Understanding
CHAPTER 9 This chapter describes how to configure Wired Equivalent Privacy (WEP), Message Integrity Check (MIC), and Temporal Key Integrity Protocol (TKIP). This chapter contains these sections: Understanding
The Honest Advantage
 The Honest Advantage READY TO CHALLENGE THE STATUS QUO GSA Security Policy and PCI Guidelines The GreenStar Alliance 2017 2017 GreenStar Alliance All Rights Reserved Table of Contents Table of Contents
The Honest Advantage READY TO CHALLENGE THE STATUS QUO GSA Security Policy and PCI Guidelines The GreenStar Alliance 2017 2017 GreenStar Alliance All Rights Reserved Table of Contents Table of Contents
CE Advanced Network Security Wireless Security
 CE 817 - Advanced Network Security Wireless Security Lecture 23 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially
CE 817 - Advanced Network Security Wireless Security Lecture 23 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially
A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e. Chapter 10 Networking Essentials
 A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e Chapter 10 Networking Essentials Objectives Learn about hardware devices used for networking Learn about the different types of networks
A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e Chapter 10 Networking Essentials Objectives Learn about hardware devices used for networking Learn about the different types of networks
Networks and Telecommunication
 Networks and Telecommunication Assignment R. C. A. Wijeratne 07/AS/CI/032 EP594 WI-Fi Technology Introduction Wi-Fi is a mechanism for wirelessly connecting electronic devices. A device enabled with Wi-Fi,
Networks and Telecommunication Assignment R. C. A. Wijeratne 07/AS/CI/032 EP594 WI-Fi Technology Introduction Wi-Fi is a mechanism for wirelessly connecting electronic devices. A device enabled with Wi-Fi,
Information Security in Corporation
 Information Security in Corporation System Vulnerability and Abuse Software Vulnerability Commercial software contains flaws that create security vulnerabilities. Hidden bugs (program code defects) Zero
Information Security in Corporation System Vulnerability and Abuse Software Vulnerability Commercial software contains flaws that create security vulnerabilities. Hidden bugs (program code defects) Zero
CS263: Wireless Communications and Sensor Networks
 CS263: Wireless Communications and Sensor Networks Matt Welsh Lecture 5: The 802.11 Standard October 7, 2004 2004 Matt Welsh Harvard University 1 All about 802.11 Today's Lecture CSMA/CD MAC and DCF WEP
CS263: Wireless Communications and Sensor Networks Matt Welsh Lecture 5: The 802.11 Standard October 7, 2004 2004 Matt Welsh Harvard University 1 All about 802.11 Today's Lecture CSMA/CD MAC and DCF WEP
Cyber Security Guidelines for Public Wi-Fi Networks
 Cyber Security Guidelines for Public Wi-Fi Networks Version: 1.0 Author: Cyber Security Policy and Standards Document Classification: PUBLIC Published Date: April 2018 Document History: Version Description
Cyber Security Guidelines for Public Wi-Fi Networks Version: 1.0 Author: Cyber Security Policy and Standards Document Classification: PUBLIC Published Date: April 2018 Document History: Version Description
Radiant Systems Wireless Point-of-Sale Security Requirements
 Abacus Business Solutions 15301 Roosevelt Blvd., Suite 303 Clearwater, FL 33760 P: (727) 524-0177 F: (727) 524-0188 www.abacuspos.com Radiant Systems Wireless Point-of-Sale Security Requirements This document
Abacus Business Solutions 15301 Roosevelt Blvd., Suite 303 Clearwater, FL 33760 P: (727) 524-0177 F: (727) 524-0188 www.abacuspos.com Radiant Systems Wireless Point-of-Sale Security Requirements This document
5 Steps Wifi Hacking Cracking WPA2 Password
 Advertise Here Contact Us Request Tutorial Write for Us Download» Hacking Knowledge Hacking News Hacking Tutorial Hacking Widget Online Tools» Tips and Trick Website» Phone Hacking Search 9,517 91 +525
Advertise Here Contact Us Request Tutorial Write for Us Download» Hacking Knowledge Hacking News Hacking Tutorial Hacking Widget Online Tools» Tips and Trick Website» Phone Hacking Search 9,517 91 +525
A Division of Cisco Systems, Inc. GHz g. Wireless-G. USB Network Adapter. User Guide WIRELESS WUSB54G. Model No.
 A Division of Cisco Systems, Inc. GHz 2.4 802.11g WIRELESS Wireless-G USB Network Adapter User Guide Model No. WUSB54G Copyright and Trademarks Specifications are subject to change without notice. Linksys
A Division of Cisco Systems, Inc. GHz 2.4 802.11g WIRELESS Wireless-G USB Network Adapter User Guide Model No. WUSB54G Copyright and Trademarks Specifications are subject to change without notice. Linksys
ECHONET Lite SPECIFICATION. ECHONET Lite System Design Guidelines 2011 (2012) ECHONET CONSORTIUM ALL RIGHTS RESERVED
 Part V ECHONET Lite System Design Guidelines i 2011 (2012) ALL RIGHTS RESERVED The specifications published by the ECHONET Consortium are established without regard to industrial property rights (e.g.,
Part V ECHONET Lite System Design Guidelines i 2011 (2012) ALL RIGHTS RESERVED The specifications published by the ECHONET Consortium are established without regard to industrial property rights (e.g.,
FAQ on Cisco Aironet Wireless Security
 FAQ on Cisco Aironet Wireless Security Document ID: 68583 Contents Introduction General FAQ Troubleshooting and Design FAQ Related Information Introduction This document provides information on the most
FAQ on Cisco Aironet Wireless Security Document ID: 68583 Contents Introduction General FAQ Troubleshooting and Design FAQ Related Information Introduction This document provides information on the most
How to Build a Wireless Home Network - Tutorial
 How to Build a Wireless Home Network - Tutorial Introduction to wireless computer networking By Bradley Mitchell, About.com wireless networking http://compnetworking.about.com/cs/wirelessproducts/a/howtobuildwlan.htm
How to Build a Wireless Home Network - Tutorial Introduction to wireless computer networking By Bradley Mitchell, About.com wireless networking http://compnetworking.about.com/cs/wirelessproducts/a/howtobuildwlan.htm
Networking. Prof. Abdul Hameed
 Networking Prof. Abdul Hameed http://informationtechnology.pk http://informationtechnology.pk 0 Chapter Topics Networking Fundamentals Network Architectures and Components Connecting to the Internet Installing
Networking Prof. Abdul Hameed http://informationtechnology.pk http://informationtechnology.pk 0 Chapter Topics Networking Fundamentals Network Architectures and Components Connecting to the Internet Installing
