Powerful and Frictionless Storage Administration
|
|
|
- Philippa Fox
- 6 years ago
- Views:
Transcription
1 Powerful and Frictionless Storage Administration Configuration Guide SoftNAS, LLC
2 Table of Contents Overview...3 Server Components...4 Kerberos Authentication...5 Prerequisites...6 Configuration Steps...9 Open LDAP Server Configuration...11 LDAP.conf...17 Client Setup...18 NFSv4 Configuration...21 Modify /etc/idmapd.conf...22 Modify /etc/sysconfig/nfs...23
3 Overview This document explains how to configure NFSv4 Server with Kerberos and LDAP authentication. Using Kerberos and/or LDAP with NFSv4 enables use of NFSv4 while maintaining each user's and user group's security rights for files and folders. The goal of this document is to describe how to setup a network to enable the following: User authentication is performed using a central Kerberos server (typically Active Directory) User information (UID/GID/home directories) is stored in a LDAP directory NFS automount information is stored in LDAP NFSv4 authentication using Kerberos is possible with support for legacy NFSv3 mounts.
4 Server Components NFS server V4 A Network File Server (NFS) is a client/server application that allows all network users to access shared files stored on computers of different types. NFS provides access to shared files through an interface called the Virtual File System (VFS) that runs on top of TCP/IP. Users can manipulate shared files as if they were stored locally on the user's own hard disk. Kerberos Authentication Kerberos is a secure method for authenticating a request for a service in a computer network. Kerberos lets a user request an encrypted "ticket" from an authentication process that can then be used to request a particular service from a server. The user's password does not have to pass through the network. LDAP Server The Lightweight Directory Access Protocol (LDAP) is an application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. Note: SoftNAS Cloud does not support installation of Open LDAP servers on the SoftNAS Cloud server itself. To use LDAP, typically an LDAP server would already be running separately in a network environment, and SoftNAS Cloud would be configured to reference that LDAP server. Refer to the vendor's LDAP server documentation or Open LDAP configuration and setup information (not included with SoftNAS Cloud).
5 Kerberos Authentication Kerberos is an industry-standard protocol with the ability to provide secure, mutual authentication in potentially insecure environments. Prerequisites Configuration Steps
6 Prerequisites The following prerequisites are required for a successful Kerberos install: Server packages Time synchronization Host Names Server Packages To begin using Kerberos, the following packages should be installed in the SoftNAS Cloud server. krb5-appl-servers krb5-appl-clients krb5-server krb5-workstation krb5-auth-dialog krb5-devel krb5-pkinit-openssl krb5-server-ldap yum install krb### ### yum -y install krb5-pkinit-openssl krb5-server-ldap Time Synchronization All machines that will participate in Kerberos authentication must have a reliable, synchronized time source. If the difference in time between systems varies by more than a small amount (usually five minutes), systems will not be able to authenticate. The following error will be displayed in this case, in a Red Hat Enterprise Linux 5 environment kadmin: GSS-API (or kerberos) error while initializing kadmin interface Resolution: To resolve this error, it is necessary to ensure that the time between the client and the KDC is synchronized. Host Names All hosts must have their hostname set to the fully qualified hostname as reported by DNS. Both forward and reverse mapping must work properly. If the host name does not match the reverse DNS lookup, Kerberos authentication will fail. To avoid this in the testing environment we have added the server name inside /etc/hosts file also in the clients hosts file nfsv4.nfstest.com nfsv4 nfstest.com
7 The above snapshot is the Kerberos Configuration for the configuration files. /etc/krb5.conf && /var/kerberos/krb5kdc/kdc.conf && /var/kerberos/krb5kdc/ kadm5.acl 1./etc/krb5.conf ============== [logging] default = FILE:/var/log/krb5libs.log kdc = FILE:/var/log/krb5kdc.log admin_server = FILE:/var/log/kadmind.log [libdefaults] default_realm = NFSTEST.COM dns_lookup_realm = false dns_lookup_kdc = false clockskew = 120 ticket_lifetime = 24h renew_lifetime = 7d forwardable = true [realms] NFSTEST.COM = { kdc = nfsv4.nfstest.com:88
8 admin_server = nfsv4.nfstest.com:749 default_domain = nfstest.com } [domain_realm].nfstest.com = NFSTEST.COM nfstest.com = NFSTEST.COM [appdefaults] pam = { debug = false ticket_lifetime = renew_lifetime = forwardable = true krb4_convert = false } kinit = { ticket_lifetime = renew_lifetime = forwardable = true } 2./var/kerberos/krb5kdc/kdc.conf ========================== [kdcdefaults] kdc_ports = 88 kdc_tcp_ports = 88 [realms] NFSTEST.COM = { acl_file = /var/kerberos/krb5kdc/kadm5.acl dict_file = /usr/share/dict/words admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab supported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmacsha1:normal des-cbc-md5:normal des-cbc-crc:normal } 3./var/kerberos/krb5kdc/kadm5.acl ======================== */admin@nfstest.com */
9 Configuration Steps After the Prerequisites have been met, continue with the following procedural steps: Create the Kerberos database Add administrative user Create host principal for the KDC (nfsv4) Setup the default policy Add normal users Perform firewall configuration Create Kerberos Database Create the database with the following command. kdb5_util create s The default password is nf$server. After primary access, change the password as per typical security best practices. Add the First Administrative User If administering as root, the first user defined should be root/admin. The default realm is appended automatically, so the command to use is as follows. [root@nfsv4] kadmin.local -q "addprinc root/admin" The default password is nf$server. After primary access, change the password as per typical security best practices. Create a Host Principal for the KDC (nfsv4) [root@nfsv4]# kadmin Authenticating as principal root/admin@nfsv4.nfstest.com with password. Password for root/admin@nfsv4.nfstest.com: kadmin: addprinc -randkey host/nfsv4.nfstest.com NOTICE: no policy specified for host/nfsv4.nfstest.com@nfstest.com; assigning "default" Principal "host/nfsv4.nfstest.com@nfstest.com " created. kadmin: ktadd host/nfsv4.nfstest.com Setup Default Policy You will want to create the default password policy at this point. All new accounts will have this policy enforced. [root@nfsv4] kadmin Authenticating as principal root/admin@nfstest.com with password. Password for root/admin@ nfstest.com: kadmin: add_policy -maxlife 180days -minlife 2days -minlength 8 minclasses 3 -history 10 default Add a Normal User
10 config]# kadmin.local -q "addprinc ahmed/users" Authenticating as principal with password. NOTICE: no policy specified for assigning "default" Enter password for principal Re-enter password for principal Principal created. Firewall Configuration Security best practices recommend using a firewall (e.g., iptables) to restrict access. For Kerberos to work, the following ports must be opened. Clients must be able to reach all KDCs on UDP port 88 (for authentication). Clients must be able to reach the primary KDC on TCP port 749 (for password management). The primary KDC must be able to reach the secondary KDCs on TCP port 754 (for replication).
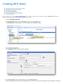
11 Open LDAP Server Configuration Initialize LDAP server and set up the configuration in the webmin-ldap-server Module. Build root DN for LDAP 1. Clear: *rm -rf /var/lib/ldap/* *rm -rf /etc/openldap/slapd.d/* * cp /usr/share/openldap-servers/db_config.example * chown -R ldap.ldap /var/lib/ldap/ /var/lib/ldap/ 2. In SoftNAS StorageCenter, configure Webmin LDAP module as shown in the screenshot below: 3. Click Save. The openldap server configuration page is displayed.
12 Create Tree Check the LDAP server to verify creation of cn=manger,dc=no-ip,dc=info. Create an Organization Unit An Organization Unit holds Groups and Users. Click Browse Database. Create Objects Click on Add new sub-object to create Groups and Users objects for LDAP users and Groups
13 For Users Review Settings After the above steps have been successfully completed, the environment should be similar to the screencap below.
14 Create Groups and Users elements Click on LDAP Users and Groups in the left Panel. Add New LDAP Group Add New User to NFSusers
15 Further Configuration The LDAP server must be configured to use Kerberos. If the LDAP server is on the same machine as the Kerberos KDC, then everything is automatically set up; otherwise, perform the following configuration: /etc/openlad/slapd.conf access to attr=loginshell by dn.regex="uid=.*/admin,cn=gssapi,cn=auth" write by self write by * read # Only the user can see their employeenumber access to attr=employeenumber
16 by dn.regex="uid=.*/admin,cn=gssapi,cn=auth" write by self read by * none # Default read access for everything else access to * by dn.regex="uid=.*/admin,cn=gssapi,cn=auth" write by * read
17 LDAP.conf This file needs to be propagated to each host, including the LDAP servers. Only the following lines need to be present: BASE URI dc=no-ip,dc=info ldaps://mycentosserver.no-ip.info This where all clients are going to point and look for an LDAP server.
18 Client Setup Copy Files Copy the following files from the KDC or LDAP server. /etc/krb5.conf /etc/openldap/ldap.conf /etc/openldap/cacerts/cacert.pem Create Kerberos Principals Run kadmin on the server and create the following principals. Replace qmail.no-ip.info with the fully qualified name of the client machine. If NFS is not in the network plan, adding the second principal is not crucial; however, if it is added at this point, it should not cause issues. kadmin Authenticating as principal with password. Password for kadmin: addprinc -randkey host/qmail.no-ip.info kadmin: addprinc -randkey nfs/qmail.no-ip.info Add Principal(s) to Keytab File Note: Ensure accuracy when adding the principal(s) in the steps shown above. This specific method is critical for a successful installation. [root@qmail ~]# kadmin Authenticating as principal root/admin@no-ip.info with password. Password for root/admin@no-ip.info: kadmin: ktadd host/qmial.no-ip.info kadmin: ktadd -e des-cbc-crc:normal nfs/qmail.no-ip.info
19 Enable Authentication Run the configuration tool by typing authconfig at the shell prompt. Check Use LDAP under User Information and Use Kerberos under Authentication. This error message may pop up. yum install pam_krb5
20 To view the contents, copy /etc/openldap/ldap. At this point the LDAP & Kerberos are configured to get information from LDAP and auth from Kerberos.
21 NFSv4 Configuration Creating Exports Share /home using /export/home to share all LDAP_USER_HOMEDIR. Configure the exports as needed against the screencaps below: NFS Exports
22 Modify /etc/idmapd.conf Change the domain listed to the current domain. Update the user mapping for nobody.
23 Modify /etc/sysconfig/nfs Enable Secure NFS Add the following line to /etc/sysconfig/nfs: SECURE_NFS=yes If the network includes NFSv3 and a firewall, add the following definitions as well. Choose ports that are appropriate to the environment, although the values listed below have been successful in our environments. STATD_PORT=4000 LOCKD_TCPPORT=4001 LOCKD_UDPPORT=4001 MOUNTD_PORT=4002 RQUOTAD_PORT=4003
Procedure to Kerberize HDP 3.1
 Procedure to Kerberize HDP 3.1 Below is the procedure to setup Kerberos on HDP 3.1.0.0 Fresh install all green To ensure successful install all the HDP components should be in good health.green Un-Kerberized
Procedure to Kerberize HDP 3.1 Below is the procedure to setup Kerberos on HDP 3.1.0.0 Fresh install all green To ensure successful install all the HDP components should be in good health.green Un-Kerberized
Configuring NFSv4 on SUSE Linux Enterprise 10
 Technical White Paper DATA CENTER www.novell.com Configuring NFSv4 on SUSE Linux Enterprise 10 Setup Guide Enhancing Client Performance for Narrow Data-sharing Applications on High-bandwidth Networks This
Technical White Paper DATA CENTER www.novell.com Configuring NFSv4 on SUSE Linux Enterprise 10 Setup Guide Enhancing Client Performance for Narrow Data-sharing Applications on High-bandwidth Networks This
Centralized Authentication with Kerberos 5, Part I
 1 of 8 6/18/2006 7:26 PM Centralized Authentication with Kerberos 5, Part I Alf Wachsmann Abstract Kerberos can solve your account administration woes. Account administration in a distributed UNIX/Linux
1 of 8 6/18/2006 7:26 PM Centralized Authentication with Kerberos 5, Part I Alf Wachsmann Abstract Kerberos can solve your account administration woes. Account administration in a distributed UNIX/Linux
Data, Avdeling for ingeniørutdanning, Høgskolen i Oslo
 Data, Avdeling for ingeniørutdanning, Text is Copyright 2010, Exponential Consulting, All rights reserved. These slides and the derived PDF file may be freely shared as long as they are unmodified and
Data, Avdeling for ingeniørutdanning, Text is Copyright 2010, Exponential Consulting, All rights reserved. These slides and the derived PDF file may be freely shared as long as they are unmodified and
HP Operations Orchestration Software
 HP Operations Orchestration Software Software Version: 7.50 Guide to Enabling Single Sign-on Document Release Date: March 2009 Software Release Date: March 2009 Legal Notices Warranty The only warranties
HP Operations Orchestration Software Software Version: 7.50 Guide to Enabling Single Sign-on Document Release Date: March 2009 Software Release Date: March 2009 Legal Notices Warranty The only warranties
NFS with Linux: Current and Future Efforts. Chuck Lever, Network Appliance, Inc Steve Dickson, Red Hat Red Hat Summit 2006
 NFS with Linux: Current and Future Efforts Chuck Lever, Network Appliance, Inc Steve Dickson, Red Hat Red Hat Summit 2006 Overview Linux NFS: Present Linux NFS: The Future Deploying Linux NFS Open Discussion
NFS with Linux: Current and Future Efforts Chuck Lever, Network Appliance, Inc Steve Dickson, Red Hat Red Hat Summit 2006 Overview Linux NFS: Present Linux NFS: The Future Deploying Linux NFS Open Discussion
setup cross realm trust between two MIT KDC to access and copy data of one cluster from another if the cross realm trust is setup correctly.
 ####################################################### # How to setup cross realm trust between two MIT KDC ####################################################### setup cross realm trust between two
####################################################### # How to setup cross realm trust between two MIT KDC ####################################################### setup cross realm trust between two
Kerberos Administration Guide
 Kerberos Administration Guide Release 1.11.1 MIT CONTENTS 1 Installation guide 1 1.1 Contents................................................. 1 1.2 Additional references...........................................
Kerberos Administration Guide Release 1.11.1 MIT CONTENTS 1 Installation guide 1 1.1 Contents................................................. 1 1.2 Additional references...........................................
Configuring Hadoop Security with Cloudera Manager
 Configuring Hadoop Security with Cloudera Manager Important Notice (c) 2010-2015 Cloudera, Inc. All rights reserved. Cloudera, the Cloudera logo, Cloudera Impala, and any other product or service names
Configuring Hadoop Security with Cloudera Manager Important Notice (c) 2010-2015 Cloudera, Inc. All rights reserved. Cloudera, the Cloudera logo, Cloudera Impala, and any other product or service names
Nicolas Williams Staff Engineer Sun Microsystems, Inc.
 Deploying Secure NFS Nicolas Williams Staff Engineer Sun Microsystems, Inc. nicolas.williams@sun.com Page 1 of Secure NFS Background A Brief History Protocol In the beginning, no security AUTH_SYS, AUTH_NONE
Deploying Secure NFS Nicolas Williams Staff Engineer Sun Microsystems, Inc. nicolas.williams@sun.com Page 1 of Secure NFS Background A Brief History Protocol In the beginning, no security AUTH_SYS, AUTH_NONE
Setting Up Identity Management
 APPENDIX D Setting Up Identity Management To prepare for the RHCSA and RHCE exams, you need to use a server that provides Lightweight Directory Access Protocol (LDAP) and Kerberos services. The configuration
APPENDIX D Setting Up Identity Management To prepare for the RHCSA and RHCE exams, you need to use a server that provides Lightweight Directory Access Protocol (LDAP) and Kerberos services. The configuration
Novell Kerberos KDC 1.5 Quickstart. novdocx (en) 11 December Novell Kerberos KDC QUICK START.
 Novell Kerberos KDC 1.5 Quickstart Novell Kerberos KDC 1.5 April 8, 2008 QUICK START www.novell.com Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use
Novell Kerberos KDC 1.5 Quickstart Novell Kerberos KDC 1.5 April 8, 2008 QUICK START www.novell.com Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use
User Authentication C HAPTER Windows 2000
 C HAPTER 8 User Authentication Before we look at the interoperability of applications, we need to look at the issue of user authentication. We do so because most, if not all, of these applications require
C HAPTER 8 User Authentication Before we look at the interoperability of applications, we need to look at the issue of user authentication. We do so because most, if not all, of these applications require
NFS: The Next Generation. Steve Dickson Kernel Engineer, Red Hat Wednesday, May 4, 2011
 NFS: The Next Generation Steve Dickson Kernel Engineer, Red Hat Wednesday, May 4, 2011 Overview Time Line What is in RHEL6 HOWTOs Debugging tools Debugging scenarios Time Line NFS Version 2 NFS Version
NFS: The Next Generation Steve Dickson Kernel Engineer, Red Hat Wednesday, May 4, 2011 Overview Time Line What is in RHEL6 HOWTOs Debugging tools Debugging scenarios Time Line NFS Version 2 NFS Version
HP Operations Orchestration Software
 HP Operations Orchestration Software Software Version: 7.50 Administrator s Guide Document Release Date: November 2008 Software Release Date: November 2008 Legal Notices Warranty The only warranties for
HP Operations Orchestration Software Software Version: 7.50 Administrator s Guide Document Release Date: November 2008 Software Release Date: November 2008 Legal Notices Warranty The only warranties for
Red Hat Enterprise Linux 6
 Red Hat Enterprise Linux 6 Managing Single Sign-On and Smart Cards On Using the Enterprise Security Client Last Updated: 2017-10-20 Red Hat Enterprise Linux 6 Managing Single Sign-On and Smart Cards On
Red Hat Enterprise Linux 6 Managing Single Sign-On and Smart Cards On Using the Enterprise Security Client Last Updated: 2017-10-20 Red Hat Enterprise Linux 6 Managing Single Sign-On and Smart Cards On
4. Note: This example has NFS version 3, but other settings such as NFS version 4 may also work better in some environments.
 Creating NFS Share 1. Mounting the NFS Share from VMware vsphere Mounting from Windows NFS Clients NFS and Firewall Settings NFS Client Mount from Linux NFS v4 and Authentication Considerations Common
Creating NFS Share 1. Mounting the NFS Share from VMware vsphere Mounting from Windows NFS Clients NFS and Firewall Settings NFS Client Mount from Linux NFS v4 and Authentication Considerations Common
How to Connect to a Microsoft SQL Server Database that Uses Kerberos Authentication in Informatica 9.6.x
 How to Connect to a Microsoft SQL Server Database that Uses Kerberos Authentication in Informatica 9.6.x Copyright Informatica LLC 2015, 2017. Informatica Corporation. No part of this document may be reproduced
How to Connect to a Microsoft SQL Server Database that Uses Kerberos Authentication in Informatica 9.6.x Copyright Informatica LLC 2015, 2017. Informatica Corporation. No part of this document may be reproduced
Security Provider Integration Kerberos Authentication
 Security Provider Integration Kerberos Authentication 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are
Security Provider Integration Kerberos Authentication 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are
NFS Version 4 17/06/05. Thimo Langbehn
 NFS Version 4 17/06/05 Thimo Langbehn Operating System Services and Administration Seminar 2005 Hasso-Plattner-Institute for Software Systems Engineering thimo.langbehn@student.hpi.uni-potsdam.de Abstract
NFS Version 4 17/06/05 Thimo Langbehn Operating System Services and Administration Seminar 2005 Hasso-Plattner-Institute for Software Systems Engineering thimo.langbehn@student.hpi.uni-potsdam.de Abstract
The Evolution of the NFS Protocol:
 The Evolution of the NFS Protocol: NFSv4, NFSv4.1, NFSv4.2, Secure NFS Steve Dickson Red Hat, Inc 06.28.12 NFS Version 4.0 NFS version 3 most used! Why Change it??? Performance! Version 4 is now the default
The Evolution of the NFS Protocol: NFSv4, NFSv4.1, NFSv4.2, Secure NFS Steve Dickson Red Hat, Inc 06.28.12 NFS Version 4.0 NFS version 3 most used! Why Change it??? Performance! Version 4 is now the default
Part 1 : Getting Familiar with Linux. Hours. Part II : Administering Red Hat Enterprise Linux
 Part 1 : Getting Familiar with Linux Chapter 1 : Getting started with Red Hat Enterprise Linux Chapter 2 Finding Your Way on the Command Line Hours Part II : Administering Red Hat Enterprise Linux Linux,
Part 1 : Getting Familiar with Linux Chapter 1 : Getting started with Red Hat Enterprise Linux Chapter 2 Finding Your Way on the Command Line Hours Part II : Administering Red Hat Enterprise Linux Linux,
Pentaho, Linux, and Microsoft Active Directory Authentication with Kerberos
 Pentaho, Linux, and Microsoft Active Directory Authentication with Kerberos Change log (if you want to use it): Date Version Author Changes Contents Overview... 1 Before You Begin... 1 Setting Up the Domain
Pentaho, Linux, and Microsoft Active Directory Authentication with Kerberos Change log (if you want to use it): Date Version Author Changes Contents Overview... 1 Before You Begin... 1 Setting Up the Domain
Novell Kerberos Login Method for NMASTM
 Novell Kerberos Login Method for NMASTM 1.0 ADMINISTRATION GUIDE www.novell.com Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
Novell Kerberos Login Method for NMASTM 1.0 ADMINISTRATION GUIDE www.novell.com Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
Dell EMC Unity Family
 Dell EMC Unity Family Version 4.3 Configuring NFS File Sharing H16959 REV 01 Copyright 2018 Dell Inc. or its subsidiaries. All rights reserved. Published February 2018 Dell believes the information in
Dell EMC Unity Family Version 4.3 Configuring NFS File Sharing H16959 REV 01 Copyright 2018 Dell Inc. or its subsidiaries. All rights reserved. Published February 2018 Dell believes the information in
Managing Administrators
 This chapter explains how to set up network administrators at the local and regional clusters. The chapter also includes local and regional cluster tutorials for many of the administration features. Administrators,
This chapter explains how to set up network administrators at the local and regional clusters. The chapter also includes local and regional cluster tutorials for many of the administration features. Administrators,
US FEDERAL: Enabling Kerberos for Smartcard Authentication to Apache.
 US FEDERAL: Enabling Kerberos for Smartcard Authentication to Apache. Michael J, 2015-03-03 The following provides guidance on the configuration of BIG-IP Local Traffic Manager and Access Policy Manager
US FEDERAL: Enabling Kerberos for Smartcard Authentication to Apache. Michael J, 2015-03-03 The following provides guidance on the configuration of BIG-IP Local Traffic Manager and Access Policy Manager
Red Hat Enterprise Linux 5 Configuring Identity Management
 Red Hat Enterprise Linux 5 Configuring Identity Management Managing Identity and Authorization Policies for Linux-Based Infrastructures Edition 2.1.4 Landmann Red Hat Enterprise Linux 5 Configuring Identity
Red Hat Enterprise Linux 5 Configuring Identity Management Managing Identity and Authorization Policies for Linux-Based Infrastructures Edition 2.1.4 Landmann Red Hat Enterprise Linux 5 Configuring Identity
Hortonworks Data Platform
 Hortonworks Data Platform Apache Ambari Security (October 30, 2017) docs.hortonworks.com Hortonworks Data Platform: Apache Ambari Security Copyright 2012-2017 Hortonworks, Inc. All rights reserved. The
Hortonworks Data Platform Apache Ambari Security (October 30, 2017) docs.hortonworks.com Hortonworks Data Platform: Apache Ambari Security Copyright 2012-2017 Hortonworks, Inc. All rights reserved. The
HP Service Health Reporter Configuring SHR to use Windows AD Authentication
 Technical white paper HP Service Health Reporter Configuring SHR to use Windows AD Authentication For the Windows Operation System Software Version 9.3x Table of Contents Introduction... 2 Motivation...
Technical white paper HP Service Health Reporter Configuring SHR to use Windows AD Authentication For the Windows Operation System Software Version 9.3x Table of Contents Introduction... 2 Motivation...
2 SCANNING, PROBING, AND MAPPING VULNERABILITIES
 GL-550: Red Hat Linux Security Administration Course Length: 5 days Course Description: This highly technical course focuses on properly securing machines running the Linux operating systems. A broad range
GL-550: Red Hat Linux Security Administration Course Length: 5 days Course Description: This highly technical course focuses on properly securing machines running the Linux operating systems. A broad range
Configuring Kerberos
 Kerberos is a secret-key network authentication protocol, developed at the Massachusetts Institute of Technology (MIT), that uses the Data Encryption Standard (DES) cryptographic algorithm for encryption
Kerberos is a secret-key network authentication protocol, developed at the Massachusetts Institute of Technology (MIT), that uses the Data Encryption Standard (DES) cryptographic algorithm for encryption
How to Integrate an External Authentication Server
 How to Integrate an External Authentication Server Required Product Model and Version This article applies to the Barracuda Load Balancer ADC 540 and above, version 5.1 and above, and to all Barracuda
How to Integrate an External Authentication Server Required Product Model and Version This article applies to the Barracuda Load Balancer ADC 540 and above, version 5.1 and above, and to all Barracuda
White Paper. Fabasoft on Linux - Preparation Guide for Community ENTerprise Operating System. Fabasoft Folio 2017 R1 Update Rollup 1
 White Paper Fabasoft on Linux - Preparation Guide for Community ENTerprise Operating System Fabasoft Folio 2017 R1 Update Rollup 1 Copyright Fabasoft R&D GmbH, Linz, Austria, 2018. All rights reserved.
White Paper Fabasoft on Linux - Preparation Guide for Community ENTerprise Operating System Fabasoft Folio 2017 R1 Update Rollup 1 Copyright Fabasoft R&D GmbH, Linz, Austria, 2018. All rights reserved.
MIT Kerberos & Red Hat
 MIT Kerberos & Red Hat Past, Present and Future Dmitri Pal Sr. Engineering Manager, Red Hat Inc. October 2012 Agenda MIT Kerberos and Red Hat involvement Project details Future plans Context Red Hat has
MIT Kerberos & Red Hat Past, Present and Future Dmitri Pal Sr. Engineering Manager, Red Hat Inc. October 2012 Agenda MIT Kerberos and Red Hat involvement Project details Future plans Context Red Hat has
Single Sign On (SSO) with Polarion 17.3
 SIEMENS Single Sign On (SSO) with Polarion 17.3 POL007 17.3 Contents Configuring single sign-on (SSO)......................................... 1-1 Overview...........................................................
SIEMENS Single Sign On (SSO) with Polarion 17.3 POL007 17.3 Contents Configuring single sign-on (SSO)......................................... 1-1 Overview...........................................................
Red Hat Enterprise Linux 6 Managing Single Sign- On and Smart Cards
 Red Hat Enterprise Linux 6 Managing Single Sign- On and Smart Cards For Red Hat Enterprise Linux 6 Ella Deon Lackey Publication date: August 13, 2009 Managing Single Sign-On and Smart Cards Red Hat Enterprise
Red Hat Enterprise Linux 6 Managing Single Sign- On and Smart Cards For Red Hat Enterprise Linux 6 Ella Deon Lackey Publication date: August 13, 2009 Managing Single Sign-On and Smart Cards Red Hat Enterprise
LIP for Windows Server Infrastructure Automation Via Ansible Devops Tool
 LIP for Windows Server Infrastructure Automation Via Ansible Devops Tool This document provides the details about ansible automation for Windows server infrastructure. Author : Sangeetha Sangeetha@cloudnloud.com
LIP for Windows Server Infrastructure Automation Via Ansible Devops Tool This document provides the details about ansible automation for Windows server infrastructure. Author : Sangeetha Sangeetha@cloudnloud.com
Configuring Kerberos based SSO in Weblogic Application server Environment
 IBM Configuring Kerberos based SSO in Weblogic Application server Environment Kerberos configuration Saravana Kumar KKB 10/11/2013 Saravana, is working as a Staff Software Engineer (QA) for IBM Policy
IBM Configuring Kerberos based SSO in Weblogic Application server Environment Kerberos configuration Saravana Kumar KKB 10/11/2013 Saravana, is working as a Staff Software Engineer (QA) for IBM Policy
Spring Security Kerberos - Reference Documentation
 Spring Security Kerberos - Reference Documentation 1.0.1.RELEASE Janne Valkealahti Pivotal Copyright 2015 Pivotal Software, Inc. Copies of this document may be made for your own use and for distribution
Spring Security Kerberos - Reference Documentation 1.0.1.RELEASE Janne Valkealahti Pivotal Copyright 2015 Pivotal Software, Inc. Copies of this document may be made for your own use and for distribution
INUVIKA TECHNICAL GUIDE
 Version 1.6 December 13, 2018 Passing on or copying of this document, use and communication of its content not permitted without Inuvika written approval PREFACE This document describes how to integrate
Version 1.6 December 13, 2018 Passing on or copying of this document, use and communication of its content not permitted without Inuvika written approval PREFACE This document describes how to integrate
FreeIPA. Directory and authentication services the easy way. Christian Stankowic. Free and Open Source software Conference
 FreeIPA Directory and authentication services the easy way Christian Stankowic www.stankowic-development.net Free and Open Source software Conference 21.08.2016 whoami Christian Stankowic Messer Information
FreeIPA Directory and authentication services the easy way Christian Stankowic www.stankowic-development.net Free and Open Source software Conference 21.08.2016 whoami Christian Stankowic Messer Information
"Charting the Course... Enterprise Linux Security Administration Course Summary
 Course Summary Description This highly technical course focuses on properly securing machines running the Linux operating systems. A broad range of general security techniques such as user/group policies,
Course Summary Description This highly technical course focuses on properly securing machines running the Linux operating systems. A broad range of general security techniques such as user/group policies,
Lecture 08: Networking services: there s no place like
 Lecture 08: services: there s no place like 127.0.0.1 Hands-on Unix system administration DeCal 2012-10-15 1 / 22 About Common records Other records 2 / 22 About About Common records Other records Domain
Lecture 08: services: there s no place like 127.0.0.1 Hands-on Unix system administration DeCal 2012-10-15 1 / 22 About Common records Other records 2 / 22 About About Common records Other records Domain
FreeIPA - Control your identity
 FreeIPA - Control your identity LinuxAlt 2012 Martin Košek, Sr. Software Engineer, Red Hat Nov 3 rd, 2012 This work is licensed under the Creative Commons Attribution-NonCommercial-ShareAlike
FreeIPA - Control your identity LinuxAlt 2012 Martin Košek, Sr. Software Engineer, Red Hat Nov 3 rd, 2012 This work is licensed under the Creative Commons Attribution-NonCommercial-ShareAlike
Configuring Integrated Windows Authentication for JBoss with SAS 9.2 Web Applications
 Configuring Integrated Windows Authentication for JBoss with SAS 9.2 Web Applications Copyright Notice The correct bibliographic citation for this manual is as follows: SAS Institute Inc., Configuring
Configuring Integrated Windows Authentication for JBoss with SAS 9.2 Web Applications Copyright Notice The correct bibliographic citation for this manual is as follows: SAS Institute Inc., Configuring
Configuring Kerberos
 Configuring Kerberos Last Updated: January 26, 2012 Finding Feature Information, page 1 Information About Kerberos, page 1 How to Configure Kerberos, page 5 Kerberos Configuration Examples, page 13 Additional
Configuring Kerberos Last Updated: January 26, 2012 Finding Feature Information, page 1 Information About Kerberos, page 1 How to Configure Kerberos, page 5 Kerberos Configuration Examples, page 13 Additional
Integrating Red Hat Enterprise Linux 6 with Active Directory. Mark Heslin Principal Software Engineer
 Integrating Red Hat Enterprise Linux 6 with Active Directory Mark Heslin Principal Software Engineer Version 1.1 April 2012 1801 Varsity Drive Raleigh NC 27606-2072 USA Phone: +1 919 754 3700 Phone: 888
Integrating Red Hat Enterprise Linux 6 with Active Directory Mark Heslin Principal Software Engineer Version 1.1 April 2012 1801 Varsity Drive Raleigh NC 27606-2072 USA Phone: +1 919 754 3700 Phone: 888
Xcalar Installation Guide
 Xcalar Installation Guide Publication date: 2018-03-16 www.xcalar.com Copyright 2018 Xcalar, Inc. All rights reserved. Table of Contents Xcalar installation overview 5 Audience 5 Overview of the Xcalar
Xcalar Installation Guide Publication date: 2018-03-16 www.xcalar.com Copyright 2018 Xcalar, Inc. All rights reserved. Table of Contents Xcalar installation overview 5 Audience 5 Overview of the Xcalar
IBM i Version 7.2. Security Network authentication service IBM
 IBM i Version 7.2 Security Network authentication service IBM IBM i Version 7.2 Security Network authentication service IBM Note Before using this information and the product it supports, read the information
IBM i Version 7.2 Security Network authentication service IBM IBM i Version 7.2 Security Network authentication service IBM Note Before using this information and the product it supports, read the information
INUVIKA TECHNICAL GUIDE
 Version 1.7 July 10, 2018 Passing on or copying of this document, use and communication of its content not permitted without Inuvika written approval PREFACE This document explains the steps to implement
Version 1.7 July 10, 2018 Passing on or copying of this document, use and communication of its content not permitted without Inuvika written approval PREFACE This document explains the steps to implement
Linux with Active Directory
 Microsoft s Active Directory system provides centralized user management and single sign-on. If you re ready for a few manual steps, Linux can leverage this potential. BY WALTER NEU n many enterprises,
Microsoft s Active Directory system provides centralized user management and single sign-on. If you re ready for a few manual steps, Linux can leverage this potential. BY WALTER NEU n many enterprises,
HP CIFS Server and Kerberos
 HP CIFS Server and Kerberos Version 1.05 November, 2008 Version 1.02 August 2005: Added Microsoft Kerberos realm name identification in Chapter 4. Added clockskew in Common Problems section, Chapter 8.
HP CIFS Server and Kerberos Version 1.05 November, 2008 Version 1.02 August 2005: Added Microsoft Kerberos realm name identification in Chapter 4. Added clockskew in Common Problems section, Chapter 8.
CloudPlatform. Trial Installation Guide
 CloudPlatform (powered by Apache CloudStack) Trial Installation Guide For CloudPlatform Version 3.0.3-3.0.6 Revised December 19, 2012 3:22 PM Pacific 2011, 2012 Citrix Systems, Inc. All rights reserved.
CloudPlatform (powered by Apache CloudStack) Trial Installation Guide For CloudPlatform Version 3.0.3-3.0.6 Revised December 19, 2012 3:22 PM Pacific 2011, 2012 Citrix Systems, Inc. All rights reserved.
TIBCO Spotfire Connecting to a Kerberized Data Source
 TIBCO Spotfire Connecting to a Kerberized Data Source Introduction Use Cases for Kerberized Data Sources in TIBCO Spotfire Connecting to a Kerberized Data Source from a TIBCO Spotfire Client Connecting
TIBCO Spotfire Connecting to a Kerberized Data Source Introduction Use Cases for Kerberized Data Sources in TIBCO Spotfire Connecting to a Kerberized Data Source from a TIBCO Spotfire Client Connecting
WYDE Authorization Guide. (version 3.1)
 WYDE Authorization Guide (version 3.1) 2 Disclaimer THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS
WYDE Authorization Guide (version 3.1) 2 Disclaimer THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS
SSSD. Client side identity management. LinuxDays 2012 Jakub Hrozek
 SSSD Client side identity management LinuxDays 2012 Jakub Hrozek 20. října 2012 1 User login in Linux 2 Centralized user databases 3 SSSD Section 1 User login in Linux User login in Linux User login in
SSSD Client side identity management LinuxDays 2012 Jakub Hrozek 20. října 2012 1 User login in Linux 2 Centralized user databases 3 SSSD Section 1 User login in Linux User login in Linux User login in
HP Operations Orchestration Software
 HP Operations Orchestration Software Software Version: 9.00 Procedure and Technical Support Best Practices for Configuring SSO using Active Directory George Daflidis-Kotsis GSD OO Support - Hewlett-Packard
HP Operations Orchestration Software Software Version: 9.00 Procedure and Technical Support Best Practices for Configuring SSO using Active Directory George Daflidis-Kotsis GSD OO Support - Hewlett-Packard
ZENworks 11 Support Pack 4 User Source and Authentication Reference. October 2016
 ZENworks 11 Support Pack 4 User Source and Authentication Reference October 2016 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions,
ZENworks 11 Support Pack 4 User Source and Authentication Reference October 2016 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions,
Linux Administration
 Linux Administration This course will cover all aspects of Linux Certification. At the end of the course delegates will have the skills required to administer a Linux System. It is designed for professionals
Linux Administration This course will cover all aspects of Linux Certification. At the end of the course delegates will have the skills required to administer a Linux System. It is designed for professionals
Kerberos and Active Directory symmetric cryptography in practice COSC412
 Kerberos and Active Directory symmetric cryptography in practice COSC412 Learning objectives Understand the function of Kerberos Explain how symmetric cryptography supports the operation of Kerberos Summarise
Kerberos and Active Directory symmetric cryptography in practice COSC412 Learning objectives Understand the function of Kerberos Explain how symmetric cryptography supports the operation of Kerberos Summarise
Configuring Integrated Windows Authentication for Oracle WebLogic with SAS 9.2 Web Applications
 Configuring Integrated Windows Authentication for Oracle WebLogic with SAS 9.2 Web Applications Copyright Notice The correct bibliographic citation for this manual is as follows: SAS Institute Inc., Configuring
Configuring Integrated Windows Authentication for Oracle WebLogic with SAS 9.2 Web Applications Copyright Notice The correct bibliographic citation for this manual is as follows: SAS Institute Inc., Configuring
Windows AD Single Sign On
 Windows AD Single Sign On Firstly, let s define our server names and IPs (you must obviously adjust these and the commands below to reflect your server names and IPs: Step 1 Domain Name: DOMAIN (FQDN:
Windows AD Single Sign On Firstly, let s define our server names and IPs (you must obviously adjust these and the commands below to reflect your server names and IPs: Step 1 Domain Name: DOMAIN (FQDN:
User Security Configuration Guide, Cisco IOS XE Fuji 16.8.x (Cisco ASR 920 Routers)
 User Security Configuration Guide, Cisco IOS XE Fuji 16.8.x (Cisco ASR 920 Routers) Configuring Kerberos 2 Finding Feature Information 2 Prerequisites for Configuring Kerberos 2 Information About Configuring
User Security Configuration Guide, Cisco IOS XE Fuji 16.8.x (Cisco ASR 920 Routers) Configuring Kerberos 2 Finding Feature Information 2 Prerequisites for Configuring Kerberos 2 Information About Configuring
Advanced Network and System Administration
 Advanced Network and System Administration NFS Copyright@2009, HaiVDC 1 Topics 1. NFS Versions 2. Using NFS 3. NFS Services 4. Server and Client Configuration 5. Automounter 6. Security 7. Performance
Advanced Network and System Administration NFS Copyright@2009, HaiVDC 1 Topics 1. NFS Versions 2. Using NFS 3. NFS Services 4. Server and Client Configuration 5. Automounter 6. Security 7. Performance
Managing External Identity Sources
 CHAPTER 5 The Cisco Identity Services Engine (Cisco ISE) integrates with external identity sources to validate credentials in user authentication functions, and to retrieve group information and other
CHAPTER 5 The Cisco Identity Services Engine (Cisco ISE) integrates with external identity sources to validate credentials in user authentication functions, and to retrieve group information and other
Secure Unified Authentication for NFS
 Technical Report Secure Unified Authentication for NFS Kerberos, NFSv4, and LDAP in Clustered Data ONTAP Justin Parisi, NetApp July 2015 TR-4073 Abstract This document explains how to configure NetApp
Technical Report Secure Unified Authentication for NFS Kerberos, NFSv4, and LDAP in Clustered Data ONTAP Justin Parisi, NetApp July 2015 TR-4073 Abstract This document explains how to configure NetApp
ACS 5.x: LDAP Server Configuration Example
 ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
Securing BigInsights environments with kerberos authentication using Microsoft Active Directory and IBM WebSphere Application Server.
 01/09/2014 Securing BigInsights environments with kerberos authentication using Microsoft Active Directory and IBM WebSphere Application Server. Authors: Jeremy Langer Laser Nahoom Kabakov Roman Zeltser
01/09/2014 Securing BigInsights environments with kerberos authentication using Microsoft Active Directory and IBM WebSphere Application Server. Authors: Jeremy Langer Laser Nahoom Kabakov Roman Zeltser
Troubleshooting and Configuring Kerberos V5 Client Support
 Troubleshooting and Configuring Kerberos V5 Client Support Document ID: 13805 Contents Introduction Prerequisites Requirements Components Used Conventions Introduction to Kerberos Definitions Gotcha Cisco
Troubleshooting and Configuring Kerberos V5 Client Support Document ID: 13805 Contents Introduction Prerequisites Requirements Components Used Conventions Introduction to Kerberos Definitions Gotcha Cisco
Secure Unified Authentication
 Technical Report Secure Unified Authentication Kerberos, NFSv4, and LDAP in ONTAP Justin Parisi, NetApp August 2017 TR-4073 Abstract This document explains how to configure NetApp storage systems with
Technical Report Secure Unified Authentication Kerberos, NFSv4, and LDAP in ONTAP Justin Parisi, NetApp August 2017 TR-4073 Abstract This document explains how to configure NetApp storage systems with
CA SiteMinder Federation Standalone
 CA SiteMinder Federation Standalone Agent for Windows Authentication Guide r12.52 SP1 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred
CA SiteMinder Federation Standalone Agent for Windows Authentication Guide r12.52 SP1 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred
Installation and Configuration Guide Simba Technologies Inc.
 Simba Impala ODBC Driver with SQL Connector Installation and Configuration Guide Simba Technologies Inc. Version 1.2.16 October 31, 2017 Copyright 2017 Simba Technologies Inc. All Rights Reserved. Information
Simba Impala ODBC Driver with SQL Connector Installation and Configuration Guide Simba Technologies Inc. Version 1.2.16 October 31, 2017 Copyright 2017 Simba Technologies Inc. All Rights Reserved. Information
Red Hat Enterprise Linux 7 Windows Integration Guide
 Red Hat Enterprise Linux 7 Windows Integration Guide Integrating Linux Systems with Active Directory Environments Ella Deon Ballard Red Hat Enterprise Linux 7 Windows Integration Guide Integrating Linux
Red Hat Enterprise Linux 7 Windows Integration Guide Integrating Linux Systems with Active Directory Environments Ella Deon Ballard Red Hat Enterprise Linux 7 Windows Integration Guide Integrating Linux
IMPLEMENTING HTTPFS & KNOX WITH ISILON ONEFS TO ENHANCE HDFS ACCESS SECURITY
 IMPLEMENTING HTTPFS & KNOX WITH ISILON ONEFS TO ENHANCE HDFS ACCESS SECURITY Boni Bruno, CISSP, CISM, CGEIT Principal Solutions Architect DELL EMC ABSTRACT This paper describes implementing HTTPFS and
IMPLEMENTING HTTPFS & KNOX WITH ISILON ONEFS TO ENHANCE HDFS ACCESS SECURITY Boni Bruno, CISSP, CISM, CGEIT Principal Solutions Architect DELL EMC ABSTRACT This paper describes implementing HTTPFS and
Installing and Configuring VMware Identity Manager Connector (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.
 Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Integrating a directory server
 Integrating a directory server Knox Manage provides a directory service that integrates a client's directory server through a Lightweight Directory Access Protocol (LDAP)-based Active Directory service
Integrating a directory server Knox Manage provides a directory service that integrates a client's directory server through a Lightweight Directory Access Protocol (LDAP)-based Active Directory service
SAS High-Performance Analytics Infrastructure 3.5: Installation and Configuration Guide
 SAS High-Performance Analytics Infrastructure 3.5: Installation and Configuration Guide SAS Documentation The correct bibliographic citation for this manual is as follows: SAS Institute Inc. 2016. SAS
SAS High-Performance Analytics Infrastructure 3.5: Installation and Configuration Guide SAS Documentation The correct bibliographic citation for this manual is as follows: SAS Institute Inc. 2016. SAS
SAS High-Performance Analytics Infrastructure 3.6: Installation and Configuration Guide
 SAS High-Performance Analytics Infrastructure 3.6: Installation and Configuration Guide SAS Documentation June 2017 The correct bibliographic citation for this manual is as follows: SAS Institute Inc.
SAS High-Performance Analytics Infrastructure 3.6: Installation and Configuration Guide SAS Documentation June 2017 The correct bibliographic citation for this manual is as follows: SAS Institute Inc.
Identity Management In Red Hat Enterprise Linux. Dave Sirrine Solutions Architect
 Identity Management In Red Hat Enterprise Linux Dave Sirrine Solutions Architect Agenda Goals of the Presentation 2 Identity Management problem space What Red Hat Identity Management solution is about?
Identity Management In Red Hat Enterprise Linux Dave Sirrine Solutions Architect Agenda Goals of the Presentation 2 Identity Management problem space What Red Hat Identity Management solution is about?
If you have not successfully configured your DNS server in the previous tutorial, it is best to move on and return to it if you have time.
 Tutorial 2 From ACE Lab Team Name: Part 0 - DNS work around If you have not successfully configured your DNS server in the previous tutorial, it is best to move on and return to it if you have time. 1.
Tutorial 2 From ACE Lab Team Name: Part 0 - DNS work around If you have not successfully configured your DNS server in the previous tutorial, it is best to move on and return to it if you have time. 1.
Configuring Integrated Windows Authentication for IBM WebSphere with SAS 9.2 Web Applications
 Configuring Integrated Windows Authentication for IBM WebSphere with SAS 9.2 Web Applications Copyright Notice The correct bibliographic citation for this manual is as follows: SAS Institute Inc., Configuring
Configuring Integrated Windows Authentication for IBM WebSphere with SAS 9.2 Web Applications Copyright Notice The correct bibliographic citation for this manual is as follows: SAS Institute Inc., Configuring
"Charting the Course... RHCE Rapid Track Course. Course Summary
 Course Summary Description This course is carefully designed to match the topics found in the Red Hat RH299 exam prep course but also features the added benefit of an entire extra day of comprehensive
Course Summary Description This course is carefully designed to match the topics found in the Red Hat RH299 exam prep course but also features the added benefit of an entire extra day of comprehensive
Identity Management Scaling Out and Up
 Identity Management Scaling Out and Up Jan Pazdziora Principal Software Engineer Identity Management Engineering, Red Hat jpazdziora@redhat.com 15 th October 2014 Identity Users; user groups. Hosts; host
Identity Management Scaling Out and Up Jan Pazdziora Principal Software Engineer Identity Management Engineering, Red Hat jpazdziora@redhat.com 15 th October 2014 Identity Users; user groups. Hosts; host
Unit 2: Manage Files Graphically with Nautilus Objective: Manage files graphically and access remote systems with Nautilus
 Linux system administrator-i Unit 1: Get Started with the GNOME Graphical Desktop Objective: Get started with GNOME and edit text files with gedit Unit 2: Manage Files Graphically with Nautilus Objective:
Linux system administrator-i Unit 1: Get Started with the GNOME Graphical Desktop Objective: Get started with GNOME and edit text files with gedit Unit 2: Manage Files Graphically with Nautilus Objective:
Persistent key, value storage
 Persistent key, value storage In programs, often use hash tables - E.g., Buckets are an array of pointers, collision chaining For persistant data, minimize # disk accesses - Traversing linked lists is
Persistent key, value storage In programs, often use hash tables - E.g., Buckets are an array of pointers, collision chaining For persistant data, minimize # disk accesses - Traversing linked lists is
Grandstream Networks, Inc. LDAP Configuration Guide
 Grandstream Networks, Inc. Table of Contents INTRODUCTION... 4 LDAP SERVER CONFIGURATION... 5 LDAP PHONEBOOK... 6 Access the Default Phonebook DN... 6 Add a New Phonebook DN... 7 Add contacts to Phonebook
Grandstream Networks, Inc. Table of Contents INTRODUCTION... 4 LDAP SERVER CONFIGURATION... 5 LDAP PHONEBOOK... 6 Access the Default Phonebook DN... 6 Add a New Phonebook DN... 7 Add contacts to Phonebook
White Paper. Fabasoft on Linux - Fabasoft Folio Web Management. Fabasoft Folio 2017 R1 Update Rollup 1
 White Paper Fabasoft on Linux - Fabasoft Folio Web Management Fabasoft Folio 2017 R1 Update Rollup 1 Copyright Fabasoft R&D GmbH, Linz, Austria, 2018. All rights reserved. All hardware and software names
White Paper Fabasoft on Linux - Fabasoft Folio Web Management Fabasoft Folio 2017 R1 Update Rollup 1 Copyright Fabasoft R&D GmbH, Linz, Austria, 2018. All rights reserved. All hardware and software names
Red Hat Enterprise Linux 7
 Red Hat Enterprise Linux 7 Windows Integration Guide Integrating Linux Systems with Active Directory Environments Last Updated: 2018-06-25 Red Hat Enterprise Linux 7 Windows Integration Guide Integrating
Red Hat Enterprise Linux 7 Windows Integration Guide Integrating Linux Systems with Active Directory Environments Last Updated: 2018-06-25 Red Hat Enterprise Linux 7 Windows Integration Guide Integrating
TIBCO ActiveMatrix BPM Single Sign-On
 TIBCO ActiveMatrix BPM Single Sign-On Software Release 4.1 May 2016 Two-Second Advantage 2 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED OR BUNDLED
TIBCO ActiveMatrix BPM Single Sign-On Software Release 4.1 May 2016 Two-Second Advantage 2 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED OR BUNDLED
MIT KDC integration. Andreas Schneider Günther Deschner May 21th, Red Hat
 Andreas Schneider Günther Deschner May 21th, 2015 Who we are? We both are Samba Team members work for on Samba love rock climbing and love Frankonian beer (an important part
Andreas Schneider Günther Deschner May 21th, 2015 Who we are? We both are Samba Team members work for on Samba love rock climbing and love Frankonian beer (an important part
Kerberos and NFS4 on Linux. isginf Workshop
 Kerberos and NFS4 on Linux isginf Workshop Stefan Walter 13.03.18 1 Welcome First workshop we organize! Background info and three practical labs Goal is to show you how to get NFS4 with Kerberos working
Kerberos and NFS4 on Linux isginf Workshop Stefan Walter 13.03.18 1 Welcome First workshop we organize! Background info and three practical labs Goal is to show you how to get NFS4 with Kerberos working
VMware Identity Manager Cloud Deployment. DEC 2017 VMware AirWatch 9.2 VMware Identity Manager
 VMware Identity Manager Cloud Deployment DEC 2017 VMware AirWatch 9.2 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware Identity Manager Cloud Deployment DEC 2017 VMware AirWatch 9.2 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware Identity Manager Cloud Deployment. Modified on 01 OCT 2017 VMware Identity Manager
 VMware Identity Manager Cloud Deployment Modified on 01 OCT 2017 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The
VMware Identity Manager Cloud Deployment Modified on 01 OCT 2017 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The
VMware Identity Manager Administration
 VMware Identity Manager Administration VMware Identity Manager 2.4 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
VMware Identity Manager Administration VMware Identity Manager 2.4 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Overview of Kerberos(I)
 Overview of Kerberos(I) Network Authentication Protocol for C/S application based on symmetric cryptosystem TTP authentication service Based on secret key, single login Part of MIT's project Athena (public
Overview of Kerberos(I) Network Authentication Protocol for C/S application based on symmetric cryptosystem TTP authentication service Based on secret key, single login Part of MIT's project Athena (public
NoMachine Authentication Guide
 NoMachine Authentication Guide Page 1 of 28 Table of Contents 1. NoMachine ntegration with Various Authorization Methods 1.1 Document Convention and mportant Notices 1.2 Resources on the Web 2. Authorization
NoMachine Authentication Guide Page 1 of 28 Table of Contents 1. NoMachine ntegration with Various Authorization Methods 1.1 Document Convention and mportant Notices 1.2 Resources on the Web 2. Authorization
Setting Up Resources in VMware Identity Manager
 Setting Up Resources in VMware Identity Manager VMware Identity Manager 2.7 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
Setting Up Resources in VMware Identity Manager VMware Identity Manager 2.7 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
Installation Prerequisites
 This chapter includes the following sections: Supported Platforms, page 1 Supported Web Browsers, page 2 Required Ports, page 2 System Requirements, page 5 Important Prerequisites for Installing Cisco
This chapter includes the following sections: Supported Platforms, page 1 Supported Web Browsers, page 2 Required Ports, page 2 System Requirements, page 5 Important Prerequisites for Installing Cisco
VMware Identity Manager Connector Installation and Configuration (Legacy Mode)
 VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
