To get a feel for how to use the FIREWALL > Live page in NextGen Admin, watch the following video:
|
|
|
- Estella Bradley
- 6 years ago
- Views:
Transcription
1 Under the Live tab, you can view and filter real-time information for the traffic that passes through the Barracuda NextGen Firewall F-Series. You can also manage the traffic sessions. To access the Live page, open the FIREWALL tab and click the Live icon in the ribbon bar. Video To get a feel for how to use the FIREWALL > Live page in NextGen Admin, watch the following video: Viewing Session Details On the Live page, the details for all sessions are listed. You can view additional information for a specific session by double-clicking an entry. The following information is provided for each session: Click here to see more ID State Info IP Protocol Description The icons indicating the amount of traffic (Low to High...). The number provided is the unique access ID for the connection. The connection status (one-way traffic; connection established (TCP); two-way traffic (all other); connection could not be established; closing connection). The icon next to the status symbol indicates the application policy. The protocol that is used. For example, TCP, UDP, or ICMP. Application Context The context of the affected application. Application Content Rule The name of the affected application. The content of the affected application. The name of the affected firewall rule. 1 / 10
2 Type Interface Source Src. Port Destination Port User Bit/s Idle Total In Out Start SNAT DNAT Output-IF Policy QoS FWD Shape REV Shape Protocol Status Src. Geo Dst. Geo TI ID REV Shape URL Category The origin, as specified by the following abbreviations: LIN Local In. The incoming traffic on the box firewall. LOUT Local Out. The outgoing traffic from the box firewall. LB Loopback. The traffic via the loopback interface. FWD Forwarding. The outbound traffic via the Forwarding Firewall. IFWD Forwarding. The inbound traffic to the firewall. PXY Proxy. The outbound traffic via the proxy. IPXY Proxy. The inbound traffic via the proxy. TAP Transparent Application Proxying. The traffic via stream forwarding. The affected interface. The source IP address. The source port. The destination IP address. The destination port (or internal ICMP ID). The username of the affected user and group. The bits per second (during the last second). Time since the last data transfer. The total number of bytes that have been transferred over this connection. The total number of bytes that have been transferred over this connection from the source. The total number of bytes that have been transferred over this connection to the source. Time since the connection was established. The source NAT address. The destination NAT address. The outgoing interface. The affected policy. For descriptions of the available policies, see the Policy Overview section. QoS Band used by this session. The forward Traffic Shaping (IN/OUT). The shape connectors for ingress and egress shaping, respectively, in the forward direction. Ingress shaping takes place at the inbound interface. Egress shaping takes place at the outbound interface. The reverse Traffic Shaping (IN/OUT). The affected protocol. The status of the connection. For descriptions of the available status types, see Status Overview. The geographic source of the active connection. The geographic destination of the active connection. The transport rating setting (Bulk, Quality, or Fallback with IDs 0-7). For more information, see Traffic Shaping. The shape connectors for ingress and egress shaping, respectively, in the reverse direction. Ingress shaping takes place at the outbound interface. Egress shaping takes place at the inbound interface. Category of the destination URL. The general status of firewall connections is indicated by the following icons: Icon Transfer Rate Description UDP Session creating, connection not fully established (TCP) / one-way traffic (all other protocols) 2 / 10
3 Connection established (TCP) - Two-way traffic (all other protocols) UDP session failing Session one-sided down HA Synced Session IPS Scan App Scan Wan Optimization Session State: ACPF Slot Deny Filter Options You can filter the list of sessions by traffic type, status, and properties. The following filter settings are provided: Traffic Selection From the Traffic Selection list, you can select the following options to filter for certain traffic types: Forward Sessions handled by the Forwarding Firewall. Loopback System internal data exchanged by the loopback interface. Local In Incoming sessions handled by the box firewall. Local Out Outgoing sessions handled by the box firewall. IPv4 Show IPv4 sessions. IPv6 Show IPv6 sessions. Status Selection From the Status Selection list, you can select the following options to filter for certain traffic statuses: Closing Closing connections. Established Established connections. Failing Failed connections. Pending Connections that are currently being established. Application Shows the detected application. The filter section also allows you to add filters for very specific properties by clicking the + icon. Note that some fields allow the use of wildcards (*?;!*?). Example:!Amazon* excludes all entries starting with Amazon; Y* A* includes all entries starting with "Y" or "A". 3 / 10 IP Protocol Displays the IP protocol. Port Displays the port. Source The source IP address/range. Source/Destination IP address/range that matches either source or destination. Interface Displays the interface (for example eth0). User Displays the user. Destination The destination IP address/range. Output-IF The output interface. Application Name of the affected application. App Context Context of the affected application. Rule Displays the rule that affects the traffic. Any Interface Shows the forward or reverse interface. Idle Time [s] The time sessions are in idle state. If specified, the idle time and less (<) in seconds is implied. Entering < and > is possible. Protocol Shows the protocol.
4 File Content Shows the file type. User Agent User agent for HTTP- and HTTPS connections. URL Category Shows the URL category. Source Geo The source host's geographic location. Destination Geo The destination host's geographic location. Filter Icons Clicking the Open History with same filter icon on the top right of the ribbon bar above the filters allows you to switch to the History Page but with the same filters applied. Clicking the Save and Restore Filter and Column Settings icon in the ribbon bar will open a drop-down menu that lets you save, restore, or delete filter and column view settings. Managing Sessions You can control, copy, print, export, and organize the sessions that are listed on the Firewall > Live page. When you right-click a session, you are provided with the following options: Click here to see more 4 / 10 Option Terminate Session Ends the session. Description Abort Session (No TCP RST) Ends the session without a TCP request. Change QoS / Reverse QoS Change TI Settings Show Session Details Lets you change the QoS Band. For more information, see Traffic Shaping. Lets you change the Traffic Intelligent settings. For more information, see Traffic Intelligence. Displays the session details. Save Traffic Selection Policy Saves the traffic selection policy. Find Select / Deselect All Copy <...> to Clipboard Copy List to Clipboard Copy selected to Clipboard Export to File Print List Group by Interface Columns Work Processes Opens the search window at the top of the list. Selects or deselects all of the sessions. Copies the selected entry to the clipboard. Copies the list to the clipboard. Copies the selected row to the clipboard. Exports the selected entry to a text file. Prints the Firewall Live view. Groups access cache entries by their interface. Lets you select the columns to hide or show. The following options are also provided: Default Columns Offers the standard view. Optimize All Columns Adjusts the column size for best display. Adjust All Columns Displays all columns that are selected. In the lower left of the Live page, you can view and control firewall-related processes and workers. To access
5 the status, simply click >> Show Proc on the lower left of the window. The entry Active displays the currently active worker processes. The feature Kill Selected is used for terminating single workers. The entry on the right of the Kill Selected button shows the status of the synchronization in case of active Transparent Failover (High Availability) and consists of the following possible states: Active Sync (UP) shown on active HA partner; synchronization works. Active Sync (DOWN) shown on active HA partner; sync would work, but Box Firewall is down. Passive Sync (UP) shown on passive HA partner; synchronization works. Passive Sync (DOWN) shown on passive HA partner; sync would work, but Box Firewall is down. The window provides the following information about the processes: PID System process ID. Connections Number of connections handled by worker. Bit/s Bytes per second (during the last second). Heartbeat Time in seconds the process stopped to answer. Should never be more than 2. PID System process ID; allows view on PID and fully extended description column. Description Role description of worker. Traffic Meter A traffic meter is integrated on the lower right of the page. The firewall engine samples the amount of traffic over 10 seconds and the traffic meter shows it based on the traffic origin (Forward, Loopback, Local, Total). Traffic can be displayed as Bits/sec, Bytes/sec or Packets/sec. The second available view is called TF Sync (click the Traffic drop-down arrow) and contains detailed information concerning the Transparent Failover function of an HA Forwarding Firewall. The pull-down menu for the statistics type (with the options Bits/sec, Bytes/sec and Packets/sec) has no function for this type of view. The display consists of the following entries: My Sync Addr IP address and connection port for synchronisation of this box. Partner Sync Addr IP address and connection port for synchronisation of the HA partner box. Synced Sessions Number of sessions successfully synchronized. Pending Sessions Number of pending sessions that are not synchronized. 5 / 10
6 Status Overview This table provides descriptions of the possible statuses that are displayed in the Status column for each session on the Firewall > Live page: Click here to see more Status Name Origin Description FWD-NEW FWD-FSYN-RCV FWD-RSYN-RSV FWD-EST FWD-RET FWD-FFIN-RCV FWD-RLACK FWD-RFIN-RCV FWD-FLACK FWD-WAIT FWD-TERM IFWD-NEW IFWD-SYN-SND IFWD-EST IFWD-RET IFWD-FFIN-RCV IFWD-RLACK IFWD-RFIN-RCV IFWD-FLACK IFWD-WAIT IFWD-TERM PXY-NEW 6 / 10 The session is validated by the firewall ruleset. Traffic has not The initial SYN packet received from the session source was forwarded. The session destination answered the SYN with a SYN/ACK packet. The SYN/ACK packet was acknowledged by the session source. The TCP session is established. Either source or destination are retransmitting packets. The connection might be dysfunctional. The session source sent a FIN datagram to terminate the session. The session destination answered the FIN packet with a FIN reply and awaits the last acknowledgement for this packet. The session destination sent a FIN datagram to terminate the session. The session source answered the FIN packet with a FIN reply and awaits the last acknowledgement for this packet. The session was reset by one of the two participants by sending a RST packet. During a wait period of five seconds, all packets belonging to the session will be discarded. The session is terminated and will be removed from the session list. A SYN packet was sent to the destination initiating the session. Note that the session with the source is already established. The destination replied to the SYN with a SYN/ACK. The session is established. Either source or destination are retransmitting packets. The connection might be dysfunctional. The session source sent a FIN datagram to terminate the session. The session destination answered the FIN packet with a FIN reply and awaits the last acknowledgement for this packet. The session destination sent a FIN datagram to terminate the session. The session source answered the FIN packet with a FIN reply and awaits the last acknowledgement for this packet. The session was reset by one of the two participants by sending a RST packet. During a wait period of five seconds, all packets belonging to the session will be discarded. The session is terminated and will be removed from the session list.
7 PXY-CONN PXY-ACC PXY-EST PXY-SRC-CLO PXY-DST-CLO PXY-SD-CLO PXY-TERM IPXY-NEW IPXY-ACC IPXY-CONN IPXY-EST IPXY-SRC-CLO IPXY-DST-CLO IPXY-SD-CLO IPXY-TERM UDP-NEW UDP-RECV UDP Forwarding UDP Forwarding A socket connection to the destination is being established. A socket connection to the source is being accepted. Two established TCP socket connections to the source and destination exist. The socket to the source is closed or is in the closing process. The socket to the destination is closed or is in the closing process. The source and the destination socket are closed or in the closing process. The session is terminated and will be removed from the session list. A socket connection to the source is being accepted. A socket connection to the destination is being established. Two established TCP socket connections to the source and destination exist. The socket to the source is closed or is in the closing process. The socket to the destination is closed or is in the closing process. The source and the destination socket are closed or in the closing process The session is terminated and will be removed from the session list. Traffic has been received from the source and was forwarded to the destination. UDP-REPL UDP Forwarding The destination replied to the traffic sent by the source. UDP-SENT UDP-FAIL ECHO-NEW ECHO-RECV UDP Forwarding UDP Forwarding ECHO Forwarding ECHO Forwarding The source transmitted more traffic after receiving a reply from the destination. The destination or a network component on the path to the destination sent an ICMP indicating that the request cannot be fulfilled. Traffic has been received from the source and forwarded to the destination. ECHO-REPL ECHO Forwarding The destination replied to the traffic sent by the source. ECHO-SENT ECHO-FAIL OTHER-NEW ECHO Forwarding ECHO Forwarding OTHER Protocols Forwarding The source sent more traffic after receiving a reply from the destination. The destination or a network component on the path to the destination sent an ICMP indicating that the request cannot be fulfilled. 7 / 10
8 OTHER-RECV OTHER-REPL OTHER-SENT OTHER-FAIL 8 / 10 OTHER Protocols Forwarding OTHER Protocols Forwarding OTHER Protocols Forwarding OTHER Protocols Forwarding Traffic has been received from the source and forwarded to the destination. The destination replied to the traffic sent by the source. The source sent more traffic after receiving a reply from the destination. The destination or a network component on the path to the destination sent an ICMP indicating that the request cannot be fulfilled. LOC-NEW Local TCP Traffic A local TCP session was granted by the local rule set. LOC-EST Local TCP Traffic The local TCP session is fully established. LOC-SYN-SND Local TCP Traffic A Local-Out TCP session is initiated by sending a SYN packet. LOC-SYN-RCV Local TCP Traffic A Local-In TCP session is initiated by receiving a SYN packet. LOC-FIN-WAIT1 LOC-FIN-WAIT2 Local TCP Traffic Local TCP Traffic LOC-TIME-WAIT Local TCP Traffic An established local TCP session started the closing process by sending a FIN packet. A local TCP session in the FIN-WAIT1 state received an ACK for the FIN packet. A local TCP session in the FIN-WAIT1 or in the FIN-WAIT2 state received a FIN packet. LOC-CLOSE Local TCP Traffic An established local TCP session is closed. LOC-CLOSE-WAIT Local TCP Traffic LOC-LAST-ACK Local TCP Traffic An established local TCP session received a FIN packet. Application holding an established TCP socket responded to a received FIN by closing the socket. A FIN is sent in return. LOC-LISTEN Local TCP Traffic A local socket awaits connection request (SYN packets). LOC-CLOSING Local TCP Traffic A local socket in the FIN_WAIT1 state received a FIN packet. LOC-FINISH Local TCP Traffic A local TCP socket was removed from the internal socket list. Policy Overview This table provides descriptions of the possible policies that you might see in the Policy column for each session on the Firewall > Live page: Click here to see more Policy NO_MATCH_IIF NO_MATCH_OIF INBOUND FWD_FILTER REV_FILTER TRACE NOTIFY_CONECT Description The received packet (Forward Direction) must NOT match initial input interface. The received packet (Reverse Direction) must NOT match initial output interface. The Accept Policy is used. The content filter is applied for forward traffic. The content filter is applied for reverse traffic. The session is traced. The Firewall Service is notified about successful or failing TCP establishment. These notifications are required for multiple redirection status. Source-Based NAT The bind IP address is determined by the routing table. NOLOG NOSTAT NOCACHE NONAGLE LOG_STATE OWN_LOG SRVSTAT Log file entries are not generated by the session. Statistics are not generated by the session. An access cache entry is not generated by the session. The Nagle algorithm is turned OFF. Every state change of this session is logged. The session will log to the firewall rule log file. The session resolves service object names when generating statistics.
9 DYNAMIC_PORT NOSYNC CLEAR_ECN The session is dynamically NAT'd. The outgoing source port will differ from the original client port. The session is not synchronized for transparent failover. The session clears any ECN bits in the IP header. 9 / 10
10 Figures 10 / 10
Status and Policy Entries
 The following article provides a list of all available status types and policies of firewall processes. The status is displayed in the Details dialog of the selected firewall status accessible via the
The following article provides a list of all available status types and policies of firewall processes. The status is displayed in the Details dialog of the selected firewall status accessible via the
Monitoring Active and Recent Connections
 To monitor network sessions or connections, view the following pages from the BASIC tab: Active Connections Lists all of the open and established sessions on the appliance. Recent Connections Lists all
To monitor network sessions or connections, view the following pages from the BASIC tab: Active Connections Lists all of the open and established sessions on the appliance. Recent Connections Lists all
History Page. Barracuda NextGen Firewall F
 The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
General Firewall Configuration
 To adjust resources used by your firewall service you can change the sizing parameters in the General Firewall Configuration (CONFIGURATION > Configuration Tree > Box > Infrastructure Services) of the
To adjust resources used by your firewall service you can change the sizing parameters in the General Firewall Configuration (CONFIGURATION > Configuration Tree > Box > Infrastructure Services) of the
Router and ACL ACL Filter traffic ACL: The Three Ps One ACL per protocol One ACL per direction One ACL per interface
 CCNA4 Chapter 5 * Router and ACL By default, a router does not have any ACLs configured and therefore does not filter traffic. Traffic that enters the router is routed according to the routing table. *
CCNA4 Chapter 5 * Router and ACL By default, a router does not have any ACLs configured and therefore does not filter traffic. Traffic that enters the router is routed according to the routing table. *
User Datagram Protocol
 Topics Transport Layer TCP s three-way handshake TCP s connection termination sequence TCP s TIME_WAIT state TCP and UDP buffering by the socket layer 2 Introduction UDP is a simple, unreliable datagram
Topics Transport Layer TCP s three-way handshake TCP s connection termination sequence TCP s TIME_WAIT state TCP and UDP buffering by the socket layer 2 Introduction UDP is a simple, unreliable datagram
Implementation Guide - VPN Network with Static Routing
 Implementation Guide - VPN Network with Static Routing This guide contains advanced topics and concepts. Follow the links in each section for step-by-step instructions on how to configure the following
Implementation Guide - VPN Network with Static Routing This guide contains advanced topics and concepts. Follow the links in each section for step-by-step instructions on how to configure the following
CCNA 1 Chapter 7 v5.0 Exam Answers 2013
 CCNA 1 Chapter 7 v5.0 Exam Answers 2013 1 A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the
CCNA 1 Chapter 7 v5.0 Exam Answers 2013 1 A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the
NGF0401 Instructor Slides
 Advanced Site to Site VPN Barracuda NextGen Firewall F VPN Tunnel Routing Separate routing table Default behavior Uses source based routing Creates separate premain routing tables for every VPN tunnel
Advanced Site to Site VPN Barracuda NextGen Firewall F VPN Tunnel Routing Separate routing table Default behavior Uses source based routing Creates separate premain routing tables for every VPN tunnel
 This is Google's cache of http://www.rigacci.org/wiki/lib/exe/fetch.php/doc/appunti/linux/sa/iptables/conntrack.html. It is a snapshot of the page as it appeared on 24 Oct 2012 08:53:12 GMT. The current
This is Google's cache of http://www.rigacci.org/wiki/lib/exe/fetch.php/doc/appunti/linux/sa/iptables/conntrack.html. It is a snapshot of the page as it appeared on 24 Oct 2012 08:53:12 GMT. The current
Load Balancing Technology White Paper
 Load Balancing Technology White Paper Keywords: Server, gateway, link, load balancing, SLB, LLB Abstract: This document describes the background, implementation, and operating mechanism of the load balancing
Load Balancing Technology White Paper Keywords: Server, gateway, link, load balancing, SLB, LLB Abstract: This document describes the background, implementation, and operating mechanism of the load balancing
Introduction to Network. Topics
 Introduction to Network Security Chapter 7 Transport Layer Protocols 1 TCP Layer Topics Responsible for reliable end-to-end transfer of application data. TCP vulnerabilities UDP UDP vulnerabilities DNS
Introduction to Network Security Chapter 7 Transport Layer Protocols 1 TCP Layer Topics Responsible for reliable end-to-end transfer of application data. TCP vulnerabilities UDP UDP vulnerabilities DNS
Lab Guide. Barracuda NextGen Firewall F-Series Microsoft Azure - NGF0501
 Barracuda NextGen Firewall F-Series Microsoft Azure - NGF0501 Lab Guide Official training material for Barracuda certified trainings and Authorized Training Centers. Edition 2018 Revision 1.0 campus.barracuda.com
Barracuda NextGen Firewall F-Series Microsoft Azure - NGF0501 Lab Guide Official training material for Barracuda certified trainings and Authorized Training Centers. Edition 2018 Revision 1.0 campus.barracuda.com
UDP and TCP. Introduction. So far we have studied some data link layer protocols such as PPP which are responsible for getting data
 ELEX 4550 : Wide Area Networks 2015 Winter Session UDP and TCP is lecture describes the two most common transport-layer protocols used by IP networks: the User Datagram Protocol (UDP) and the Transmission
ELEX 4550 : Wide Area Networks 2015 Winter Session UDP and TCP is lecture describes the two most common transport-layer protocols used by IP networks: the User Datagram Protocol (UDP) and the Transmission
How to Configure DNS Sinkholing in the Firewall
 UDP DNS traffic handled by the Firewall service is monitored and, if a domain is found that is considered to be malicious, the A and AAAA DNS response is replaced by fake IP addresses. An access rule blocks
UDP DNS traffic handled by the Firewall service is monitored and, if a domain is found that is considered to be malicious, the A and AAAA DNS response is replaced by fake IP addresses. An access rule blocks
How to Configure a Remote Management Tunnel for an F-Series Firewall
 How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
R (2) Implementation of following spoofing assignments using C++ multi-core Programming a) IP Spoofing b) Web spoofing.
 R (2) N (5) Oral (3) Total (10) Dated Sign Experiment No: 1 Problem Definition: Implementation of following spoofing assignments using C++ multi-core Programming a) IP Spoofing b) Web spoofing. 1.1 Prerequisite:
R (2) N (5) Oral (3) Total (10) Dated Sign Experiment No: 1 Problem Definition: Implementation of following spoofing assignments using C++ multi-core Programming a) IP Spoofing b) Web spoofing. 1.1 Prerequisite:
Double-clicking an entry opens a new window with detailed information about the selected VPN tunnel.
 The Barracuda NextGen Admin VPN tab provides information on all VPN connections that are configured on the Barracuda NextGen Firewall F-Series. Selecting the icons in the ribbon bar under the VPN tab takes
The Barracuda NextGen Admin VPN tab provides information on all VPN connections that are configured on the Barracuda NextGen Firewall F-Series. Selecting the icons in the ribbon bar under the VPN tab takes
Using Diagnostic Tools
 Using Diagnostic Tools The Tools System Diagnostics page on the INVESTIGATE view provides several diagnostic tools that help troubleshoot various kinds of network problems and process monitors. Tech Support
Using Diagnostic Tools The Tools System Diagnostics page on the INVESTIGATE view provides several diagnostic tools that help troubleshoot various kinds of network problems and process monitors. Tech Support
ICS 351: Networking Protocols
 ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
QUIZ: Longest Matching Prefix
 QUIZ: Longest Matching Prefix A router has the following routing table: 10.50.42.0 /24 Send out on interface Z 10.50.20.0 /24 Send out on interface A 10.50.24.0 /22 Send out on interface B 10.50.20.0 /22
QUIZ: Longest Matching Prefix A router has the following routing table: 10.50.42.0 /24 Send out on interface Z 10.50.20.0 /24 Send out on interface A 10.50.24.0 /22 Send out on interface B 10.50.20.0 /22
20-CS Cyber Defense Overview Fall, Network Basics
 20-CS-5155 6055 Cyber Defense Overview Fall, 2017 Network Basics Who Are The Attackers? Hackers: do it for fun or to alert a sysadmin Criminals: do it for monetary gain Malicious insiders: ignores perimeter
20-CS-5155 6055 Cyber Defense Overview Fall, 2017 Network Basics Who Are The Attackers? Hackers: do it for fun or to alert a sysadmin Criminals: do it for monetary gain Malicious insiders: ignores perimeter
Distributed Systems. 27. Firewalls and Virtual Private Networks Paul Krzyzanowski. Rutgers University. Fall 2013
 Distributed Systems 27. Firewalls and Virtual Private Networks Paul Krzyzanowski Rutgers University Fall 2013 November 25, 2013 2013 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive
Distributed Systems 27. Firewalls and Virtual Private Networks Paul Krzyzanowski Rutgers University Fall 2013 November 25, 2013 2013 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only.
 Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
This article explains how to configure NSRP-Lite for a NS50 firewall to a single WAN.
 This article explains how to configure NSRP-Lite for a NS50 firewall to a single WAN. Requirements: When configuring NSRP-Lite for the NS-50, confirm the following necessary requirements: The NS-25 or
This article explains how to configure NSRP-Lite for a NS50 firewall to a single WAN. Requirements: When configuring NSRP-Lite for the NS-50, confirm the following necessary requirements: The NS-25 or
BIG-IP Local Traffic Management: Basics. Version 12.1
 BIG-IP Local Traffic Management: Basics Version 12.1 Table of Contents Table of Contents Introduction to Local Traffic Management...7 About local traffic management...7 About the network map...7 Viewing
BIG-IP Local Traffic Management: Basics Version 12.1 Table of Contents Table of Contents Introduction to Local Traffic Management...7 About local traffic management...7 About the network map...7 Viewing
Avaya Port Matrix: Avaya Diagnostic Server 3.0
 Avaya Matrix: Avaya Diagnostic Server 3.0 Issue 2.0 February 208 ALL INFORMATION IS BELIEVED TO BE CORRECT AT THE TIME OF PUBLICATION AND IS PROVIDED "AS IS". AVAYA INC. DISCLAIMS ALL WARRANTIES, EITHER
Avaya Matrix: Avaya Diagnostic Server 3.0 Issue 2.0 February 208 ALL INFORMATION IS BELIEVED TO BE CORRECT AT THE TIME OF PUBLICATION AND IS PROVIDED "AS IS". AVAYA INC. DISCLAIMS ALL WARRANTIES, EITHER
Cisco IOS Firewall Intrusion Detection System Commands
 Cisco IOS Firewall Intrusion Detection System Commands This chapter describes the commands used to configure the integrated Intrusion Detection System (IDS) features in Cisco IOS Firewall. Intrusion detection
Cisco IOS Firewall Intrusion Detection System Commands This chapter describes the commands used to configure the integrated Intrusion Detection System (IDS) features in Cisco IOS Firewall. Intrusion detection
TCP /IP Fundamentals Mr. Cantu
 TCP /IP Fundamentals Mr. Cantu OSI Model and TCP/IP Model Comparison TCP / IP Protocols (Application Layer) The TCP/IP subprotocols listed in this layer are services that support a number of network functions:
TCP /IP Fundamentals Mr. Cantu OSI Model and TCP/IP Model Comparison TCP / IP Protocols (Application Layer) The TCP/IP subprotocols listed in this layer are services that support a number of network functions:
Firewalls N E T W O R K ( A N D D ATA ) S E C U R I T Y / P E D R O B R A N D Ã O M A N U E L E D U A R D O C O R R E I A
 Firewalls N E T W O R K ( A N D D ATA ) S E C U R I T Y 2 01 6 / 2 017 P E D R O B R A N D Ã O M A N U E L E D U A R D O C O R R E I A Slides are based on slides by Dr Lawrie Brown (UNSW@ADFA) for Computer
Firewalls N E T W O R K ( A N D D ATA ) S E C U R I T Y 2 01 6 / 2 017 P E D R O B R A N D Ã O M A N U E L E D U A R D O C O R R E I A Slides are based on slides by Dr Lawrie Brown (UNSW@ADFA) for Computer
Junos Security. Chapter 4: Security Policies Juniper Networks, Inc. All rights reserved. Worldwide Education Services
 Junos Security Chapter 4: Security Policies 2012 Juniper Networks, Inc. All rights reserved. www.juniper.net Worldwide Education Services Chapter Objectives After successfully completing this chapter,
Junos Security Chapter 4: Security Policies 2012 Juniper Networks, Inc. All rights reserved. www.juniper.net Worldwide Education Services Chapter Objectives After successfully completing this chapter,
Lecture 2-ter. 2. A communication example Managing a HTTP v1.0 connection. Managing a HTTP request. transport session. Step 1 - opening transport
 Lecture 2-ter. 2 A communication example Managing a HTTP v1.0 connection Managing a HTTP request User digits URL and press return (or clicks ). What happens (HTTP 1.0): 1. opens a TCP transport session
Lecture 2-ter. 2 A communication example Managing a HTTP v1.0 connection Managing a HTTP request User digits URL and press return (or clicks ). What happens (HTTP 1.0): 1. opens a TCP transport session
BIG-IQ Centralized Management: ADC. Version 5.0
 BIG-IQ Centralized Management: ADC Version 5.0 Table of Contents Table of Contents BIG-IQ Application Delivery Controller: Overview...5 What is Application Delivery Controller?...5 Managing Device Resources...7
BIG-IQ Centralized Management: ADC Version 5.0 Table of Contents Table of Contents BIG-IQ Application Delivery Controller: Overview...5 What is Application Delivery Controller?...5 Managing Device Resources...7
L41: Lab 4 - The TCP State Machine
 L41: Lab 4 - The TCP State Machine Dr Robert N. M. Watson 29 January 2016 Dr Robert N. M. Watson L41: Lab 4 - The TCP State Machine 29 January 2016 1 / 10 L41: Lab 4 - The TCP State Machine The TCP state
L41: Lab 4 - The TCP State Machine Dr Robert N. M. Watson 29 January 2016 Dr Robert N. M. Watson L41: Lab 4 - The TCP State Machine 29 January 2016 1 / 10 L41: Lab 4 - The TCP State Machine The TCP state
IPv6 Commands: ipv6 h to ipv6 mi
 IPv6 Commands: ipv6 h to ipv6 mi ipv6 hello-interval eigrp, page 3 ipv6 hold-time eigrp, page 5 ipv6 hop-limit, page 7 ipv6 host, page 8 ipv6 icmp error-interval, page 10 ipv6 inspect, page 12 ipv6 inspect
IPv6 Commands: ipv6 h to ipv6 mi ipv6 hello-interval eigrp, page 3 ipv6 hold-time eigrp, page 5 ipv6 hop-limit, page 7 ipv6 host, page 8 ipv6 icmp error-interval, page 10 ipv6 inspect, page 12 ipv6 inspect
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
IPS Device Deployments and Configuration
 The following topics describe how to configure your device in an IPS deployment: Introduction to IPS Device Deployment and Configuration, page 1 Passive IPS Deployments, page 1 Inline IPS Deployments,
The following topics describe how to configure your device in an IPS deployment: Introduction to IPS Device Deployment and Configuration, page 1 Passive IPS Deployments, page 1 Inline IPS Deployments,
DEPLOYMENT GUIDE Version 1.1. DNS Traffic Management using the BIG-IP Local Traffic Manager
 DEPLOYMENT GUIDE Version 1.1 DNS Traffic Management using the BIG-IP Local Traffic Manager Table of Contents Table of Contents Introducing DNS server traffic management with the BIG-IP LTM Prerequisites
DEPLOYMENT GUIDE Version 1.1 DNS Traffic Management using the BIG-IP Local Traffic Manager Table of Contents Table of Contents Introducing DNS server traffic management with the BIG-IP LTM Prerequisites
A quick theorical introduction to network scanning. 23rd November 2005
 A quick theorical introduction to network ASBL CSRRT-LU (Computer Security Research and Response Team Luxembourg) http://www.csrrt.org/ 23rd November 2005 IP protocol ACK Network is not exact science When
A quick theorical introduction to network ASBL CSRRT-LU (Computer Security Research and Response Team Luxembourg) http://www.csrrt.org/ 23rd November 2005 IP protocol ACK Network is not exact science When
Configuring Virtual Servers, Maps, and Policies
 6 CHAPTER This chapter describes how to configure content switching and contains these sections: Configuring Virtual Servers, page 6-1 Configuring Maps, page 6-9 Configuring Policies, page 6-11 Configuring
6 CHAPTER This chapter describes how to configure content switching and contains these sections: Configuring Virtual Servers, page 6-1 Configuring Maps, page 6-9 Configuring Policies, page 6-11 Configuring
HP Load Balancing Module
 HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
NextGen Firewall F Foundation Complete
 Introducing the Barracuda NextGen Firewall F Barracuda NextGen Firewall F Supported Platforms The Barracuda NextGen Firewall F and NextGen Control Center are available as: Hardware appliances Virtual systems
Introducing the Barracuda NextGen Firewall F Barracuda NextGen Firewall F Supported Platforms The Barracuda NextGen Firewall F and NextGen Control Center are available as: Hardware appliances Virtual systems
TCP/IP Filtering. Main TCP/IP Filtering Dialog Box. Route Filters Button. Packet Filters Button CHAPTER
 CHAPTER 11 Main Dialog Box To access this dialog box (Figure 11-1), select Global/Filtering/ from the Device View. Figure 11-1 Main Configuration Dialog Box Route Filters Button This button brings up a
CHAPTER 11 Main Dialog Box To access this dialog box (Figure 11-1), select Global/Filtering/ from the Device View. Figure 11-1 Main Configuration Dialog Box Route Filters Button This button brings up a
Configuring Flood Protection
 Configuring Flood Protection NOTE: Control Plane flood protection is located on the Firewall Settings > Advanced Settings page. TIP: You must click Accept to activate any settings you select. The Firewall
Configuring Flood Protection NOTE: Control Plane flood protection is located on the Firewall Settings > Advanced Settings page. TIP: You must click Accept to activate any settings you select. The Firewall
A hacker in a hoodie with leather gloves tapping a glowing blue lock icon on a transparent touchscreen with ones and zeroes raining down in green
 A hacker in a hoodie with leather gloves tapping a glowing blue lock icon on a transparent touchscreen with ones and zeroes raining down in green onto a circuit board jason SYSTEMATIC NETWORK SECURITY
A hacker in a hoodie with leather gloves tapping a glowing blue lock icon on a transparent touchscreen with ones and zeroes raining down in green onto a circuit board jason SYSTEMATIC NETWORK SECURITY
Cisco CCIE Security Written.
 Cisco 400-251 CCIE Security Written http://killexams.com/pass4sure/exam-detail/400-251 QUESTION: 193 Which two of the following ICMP types and code should be allowed in a firewall to enable traceroute?
Cisco 400-251 CCIE Security Written http://killexams.com/pass4sure/exam-detail/400-251 QUESTION: 193 Which two of the following ICMP types and code should be allowed in a firewall to enable traceroute?
Portal configuration commands
 Contents Portal configuration commands 1 display portal acl 1 display portal connection statistics 5 display portal free-rule 7 display portal interface 9 display portal-roaming 11 display portal server
Contents Portal configuration commands 1 display portal acl 1 display portal connection statistics 5 display portal free-rule 7 display portal interface 9 display portal-roaming 11 display portal server
INBOUND AND OUTBOUND NAT
 INBOUND AND OUTBOUND NAT Network Address Translation Course # 2011 1 Overview! Network Address Translation (NAT)! Aliases! Static Address Mappings! Inbound Tunnels! Advanced Tunnel Option SYN Cookies Authentication
INBOUND AND OUTBOUND NAT Network Address Translation Course # 2011 1 Overview! Network Address Translation (NAT)! Aliases! Static Address Mappings! Inbound Tunnels! Advanced Tunnel Option SYN Cookies Authentication
Unit 4: Firewalls (I)
 Unit 4: Firewalls (I) What is a firewall? Types of firewalls Packet Filtering Statefull Application and Circuit Proxy Firewall services and limitations Writing firewall rules Example 1 Example 2 What is
Unit 4: Firewalls (I) What is a firewall? Types of firewalls Packet Filtering Statefull Application and Circuit Proxy Firewall services and limitations Writing firewall rules Example 1 Example 2 What is
CSC 4900 Computer Networks: Network Layer
 CSC 4900 Computer Networks: Network Layer Professor Henry Carter Fall 2017 Chapter 4: Network Layer 4. 1 Introduction 4.2 What s inside a router 4.3 IP: Internet Protocol Datagram format 4.4 Generalized
CSC 4900 Computer Networks: Network Layer Professor Henry Carter Fall 2017 Chapter 4: Network Layer 4. 1 Introduction 4.2 What s inside a router 4.3 IP: Internet Protocol Datagram format 4.4 Generalized
Firewalls and NAT. Firewalls. firewall isolates organization s internal net from larger Internet, allowing some packets to pass, blocking others.
 Firews and NAT 1 Firews By conventional definition, a firew is a partition made of fireproof material designed to prevent the spread of fire from one part of a building to another. firew isolates organization
Firews and NAT 1 Firews By conventional definition, a firew is a partition made of fireproof material designed to prevent the spread of fire from one part of a building to another. firew isolates organization
Distributed Systems. 29. Firewalls. Paul Krzyzanowski. Rutgers University. Fall 2015
 Distributed Systems 29. Firewalls Paul Krzyzanowski Rutgers University Fall 2015 2013-2015 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive data & systems not accessible Integrity:
Distributed Systems 29. Firewalls Paul Krzyzanowski Rutgers University Fall 2015 2013-2015 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive data & systems not accessible Integrity:
Transport Layer. Application / Transport Interface. Transport Layer Services. Transport Layer Connections
 Application / Transport Interface Application requests service from transport layer Transport Layer Application Layer Prepare Transport service requirements Data for transport Local endpoint node address
Application / Transport Interface Application requests service from transport layer Transport Layer Application Layer Prepare Transport service requirements Data for transport Local endpoint node address
Computer and Network Security
 CIS 551 / TCOM 401 Computer and Network Security Spring 2009 Lecture 8 Announcements Plan for Today: Networks: TCP Firewalls Midterm 1: One week from Today! 2/17/2009 In class, short answer, multiple choice,
CIS 551 / TCOM 401 Computer and Network Security Spring 2009 Lecture 8 Announcements Plan for Today: Networks: TCP Firewalls Midterm 1: One week from Today! 2/17/2009 In class, short answer, multiple choice,
HP High-End Firewalls
 HP High-End Firewalls Access Control Configuration Guide Part number: 5998-2648 Software version: F1000-A-EI&F1000-S-EI: R3721 F5000: F3210 F1000-E: F3171 Firewall module: F3171 Document version: 6PW101-20120719
HP High-End Firewalls Access Control Configuration Guide Part number: 5998-2648 Software version: F1000-A-EI&F1000-S-EI: R3721 F5000: F3210 F1000-E: F3171 Firewall module: F3171 Document version: 6PW101-20120719
Avaya Port Matrix: Avaya Proprietary Use pursuant to the terms of your signed agreement or Avaya policy.
 Avaya Matrix: Release 3.0 Issue 2 April 2016 April 2016 Avaya Matrix: 3.0 1 ALL INFORMATION IS BELIEVED TO BE CORRECT AT THE TIME OF PUBLICATION AND IS PROVIDED "AS IS". AVAYA INC. DISCLAIMS ALL WARRANTIES,
Avaya Matrix: Release 3.0 Issue 2 April 2016 April 2016 Avaya Matrix: 3.0 1 ALL INFORMATION IS BELIEVED TO BE CORRECT AT THE TIME OF PUBLICATION AND IS PROVIDED "AS IS". AVAYA INC. DISCLAIMS ALL WARRANTIES,
How to Configure a Remote Management Tunnel for Barracuda NG Firewalls
 How to Configure a Remote Management Tunnel for Barracuda NG Firewalls If the managed NG Firewall can not directly reach the NG Control Center it must connect via a remote management tunnel. The remote
How to Configure a Remote Management Tunnel for Barracuda NG Firewalls If the managed NG Firewall can not directly reach the NG Control Center it must connect via a remote management tunnel. The remote
Monitoring and Analysis
 CHAPTER 3 Cisco Prime Network Analysis Module 5.1 has two types of dashboards: One type is the summary views found under the Monitor menu, and the other type is the over time views found under the Analyze
CHAPTER 3 Cisco Prime Network Analysis Module 5.1 has two types of dashboards: One type is the summary views found under the Monitor menu, and the other type is the over time views found under the Analyze
Firewalls. Firewall. means of protecting a local system or network of systems from network-based security threats creates a perimeter of defense
 FIREWALLS 3 Firewalls Firewall means of protecting a local system or network of systems from network-based security threats creates a perimeter of defense administered network public Internet firewall
FIREWALLS 3 Firewalls Firewall means of protecting a local system or network of systems from network-based security threats creates a perimeter of defense administered network public Internet firewall
HP Load Balancing Module
 HP Load Balancing Module Security Configuration Guide Part number: 5998-2686 Document version: 6PW101-20120217 Legal and notice information Copyright 2012 Hewlett-Packard Development Company, L.P. No part
HP Load Balancing Module Security Configuration Guide Part number: 5998-2686 Document version: 6PW101-20120217 Legal and notice information Copyright 2012 Hewlett-Packard Development Company, L.P. No part
Introduction to Firewalls using IPTables
 Introduction to Firewalls using IPTables The goal of this lab is to implement a firewall solution using IPTables, and to write and to customize new rules to achieve security. You will need to turn in your
Introduction to Firewalls using IPTables The goal of this lab is to implement a firewall solution using IPTables, and to write and to customize new rules to achieve security. You will need to turn in your
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
9th Slide Set Computer Networks
 Prof. Dr. Christian Baun 9th Slide Set Computer Networks Frankfurt University of Applied Sciences WS1718 1/49 9th Slide Set Computer Networks Prof. Dr. Christian Baun Frankfurt University of Applied Sciences
Prof. Dr. Christian Baun 9th Slide Set Computer Networks Frankfurt University of Applied Sciences WS1718 1/49 9th Slide Set Computer Networks Prof. Dr. Christian Baun Frankfurt University of Applied Sciences
Avaya Port Matrix: Avaya Aura Appliance Virtualization Platform 7.0
 Avaya Port Matrix: Avaya Aura Appliance Virtualization Platform 7.0 Issue 1.0 August 24, 2015 August 2015 Avaya Port Matrix: Avaya Aura Appliance Virtualization Platform 7.0 1 ALL INFORMATION IS BELIEVED
Avaya Port Matrix: Avaya Aura Appliance Virtualization Platform 7.0 Issue 1.0 August 24, 2015 August 2015 Avaya Port Matrix: Avaya Aura Appliance Virtualization Platform 7.0 1 ALL INFORMATION IS BELIEVED
CCNA Exploration Network Fundamentals. Chapter 04 OSI Transport Layer
 CCNA Exploration Network Fundamentals Chapter 04 OSI Transport Layer Updated: 05/05/2008 1 4.1 Roles of the Transport Layer 2 4.1 Roles of the Transport Layer The OSI Transport layer accept data from the
CCNA Exploration Network Fundamentals Chapter 04 OSI Transport Layer Updated: 05/05/2008 1 4.1 Roles of the Transport Layer 2 4.1 Roles of the Transport Layer The OSI Transport layer accept data from the
ACL Compliance Director Tutorial
 Abstract Copyright 2008 Cyber Operations, Inc. This is a tutorial on ACL Compliance Director intended to guide new users through the core features of the system. Table of Contents Introduction... 1 Login
Abstract Copyright 2008 Cyber Operations, Inc. This is a tutorial on ACL Compliance Director intended to guide new users through the core features of the system. Table of Contents Introduction... 1 Login
Firewall Policy. Edit Firewall Policy/ACL CHAPTER7. Configure a Firewall Before Using the Firewall Policy Feature
 CHAPTER7 The feature lets you view and modify firewall configurations access rules and CBAC inspection rules in the context of the interfaces whose traffic they filter. Using a graphical representation
CHAPTER7 The feature lets you view and modify firewall configurations access rules and CBAC inspection rules in the context of the interfaces whose traffic they filter. Using a graphical representation
Lab - Using Wireshark to Examine TCP and UDP Captures
 Topology Part 1 (FTP) Part 1 will highlight a TCP capture of an FTP session. This topology consists of a PC with Internet access. Topology Part 2 (TFTP) Part 2 will highlight a UDP capture of a TFTP session.
Topology Part 1 (FTP) Part 1 will highlight a TCP capture of an FTP session. This topology consists of a PC with Internet access. Topology Part 2 (TFTP) Part 2 will highlight a UDP capture of a TFTP session.
Linux Networking: tcp. TCP context and interfaces
 Linux Networking: tcp David Morgan TCP context and interfaces Computer A Computer B application process application process data data data data TCP process TCP process a network 1 TCP purposes and features
Linux Networking: tcp David Morgan TCP context and interfaces Computer A Computer B application process application process data data data data TCP process TCP process a network 1 TCP purposes and features
Configuring Access Rules
 Configuring Access Rules Rules > Access Rules About Access Rules Displaying Access Rules Specifying Maximum Zone-to-Zone Access Rules Changing Priority of a Rule Adding Access Rules Editing an Access Rule
Configuring Access Rules Rules > Access Rules About Access Rules Displaying Access Rules Specifying Maximum Zone-to-Zone Access Rules Changing Priority of a Rule Adding Access Rules Editing an Access Rule
Prof. Bill Buchanan Room: C.63
 Wireless LAN CO72047 Unit 7: Filtering Prof. Bill Buchanan Contact: w.buchanan@napier.ac.uk Room: C.63 Telephone: X2759 MSN Messenger: w_j_buchanan@hotmail.com WWW: http://www.dcs.napier.ac.uk/~bill http://buchananweb.co.uk
Wireless LAN CO72047 Unit 7: Filtering Prof. Bill Buchanan Contact: w.buchanan@napier.ac.uk Room: C.63 Telephone: X2759 MSN Messenger: w_j_buchanan@hotmail.com WWW: http://www.dcs.napier.ac.uk/~bill http://buchananweb.co.uk
Module 19 : Threats in Network What makes a Network Vulnerable?
 Module 19 : Threats in Network What makes a Network Vulnerable? Sharing Unknown path Many points of attack What makes a network vulnerable? Unknown perimeter Anonymity Complexity of system Categories of
Module 19 : Threats in Network What makes a Network Vulnerable? Sharing Unknown path Many points of attack What makes a network vulnerable? Unknown perimeter Anonymity Complexity of system Categories of
Network Control, Con t
 Network Control, Con t CS 161 - Computer Security Profs. Vern Paxson & David Wagner TAs: John Bethencourt, Erika Chin, Matthew Finifter, Cynthia Sturton, Joel Weinberger http://inst.eecs.berkeley.edu/~cs161/
Network Control, Con t CS 161 - Computer Security Profs. Vern Paxson & David Wagner TAs: John Bethencourt, Erika Chin, Matthew Finifter, Cynthia Sturton, Joel Weinberger http://inst.eecs.berkeley.edu/~cs161/
Network Security. Introduction to networks. Radboud University, The Netherlands. Autumn 2015
 Network Security Introduction to networks Radboud University, The Netherlands Autumn 2015 What is a (computer) network Definition A computer network is two or more computers that are connected, so that
Network Security Introduction to networks Radboud University, The Netherlands Autumn 2015 What is a (computer) network Definition A computer network is two or more computers that are connected, so that
Fundamentals of IP Networking 2017 Webinar Series Part 4 Building a Segmented IP Network Focused On Performance & Security
 Fundamentals of IP Networking 2017 Webinar Series Part 4 Building a Segmented IP Network Focused On Performance & Security Wayne M. Pecena, CPBE, CBNE Texas A&M University Educational Broadcast Services
Fundamentals of IP Networking 2017 Webinar Series Part 4 Building a Segmented IP Network Focused On Performance & Security Wayne M. Pecena, CPBE, CBNE Texas A&M University Educational Broadcast Services
Firepower Threat Defense Cluster for the Firepower 4100/9300
 Firepower Threat Defense Cluster for the Firepower 4100/9300 Clustering lets you group multiple Firepower Threat Defense units together as a single logical device. Clustering is only supported for the
Firepower Threat Defense Cluster for the Firepower 4100/9300 Clustering lets you group multiple Firepower Threat Defense units together as a single logical device. Clustering is only supported for the
ipv6 mobile home-agent (global configuration)
 ipv6 mobile home-agent (global configuration) ipv6 mobile home-agent (global configuration) To enter home agent configuration mode, use the ipv6 mobile home-agent command in global configuration mode.
ipv6 mobile home-agent (global configuration) ipv6 mobile home-agent (global configuration) To enter home agent configuration mode, use the ipv6 mobile home-agent command in global configuration mode.
Netlink2 as ForCES protocol (update)
 57 th IETF, Juy 14 th, 2003 Netlink2 as ForCES protocol (update) draft-jhsrha-forces-netlink2-01.txt presentation available online at http://www.zurich.ibm.com/~rha/netlink2-1.pdf Robert Haas, IBM Research
57 th IETF, Juy 14 th, 2003 Netlink2 as ForCES protocol (update) draft-jhsrha-forces-netlink2-01.txt presentation available online at http://www.zurich.ibm.com/~rha/netlink2-1.pdf Robert Haas, IBM Research
Configuring IP Services
 CHAPTER 8 Configuring IP Services This chapter describes how to configure optional IP services supported by the Cisco Optical Networking System (ONS) 15304. For a complete description of the commands in
CHAPTER 8 Configuring IP Services This chapter describes how to configure optional IP services supported by the Cisco Optical Networking System (ONS) 15304. For a complete description of the commands in
7. TCP 최양희서울대학교컴퓨터공학부
 7. TCP 최양희서울대학교컴퓨터공학부 1 TCP Basics Connection-oriented (virtual circuit) Reliable Transfer Buffered Transfer Unstructured Stream Full Duplex Point-to-point Connection End-to-end service 2009 Yanghee Choi
7. TCP 최양희서울대학교컴퓨터공학부 1 TCP Basics Connection-oriented (virtual circuit) Reliable Transfer Buffered Transfer Unstructured Stream Full Duplex Point-to-point Connection End-to-end service 2009 Yanghee Choi
Configuring Answers and Answer Groups
 CHAPTER 6 Configuring Answers and Answer Groups This chapter describes how to create and configure answers and answer groups for your GSS network. It contains the following major sections: Configuring
CHAPTER 6 Configuring Answers and Answer Groups This chapter describes how to create and configure answers and answer groups for your GSS network. It contains the following major sections: Configuring
Configuring Answers and Answer Groups
 CHAPTER 6 This chapter describes how to create and configure answers and answer groups for your GSS network. It contains the following major sections: Configuring and Modifying Answers Configuring and
CHAPTER 6 This chapter describes how to create and configure answers and answer groups for your GSS network. It contains the following major sections: Configuring and Modifying Answers Configuring and
Configuring Commonly Used IP ACLs
 Configuring Commonly Used IP ACLs Document ID: 26448 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a
Configuring Commonly Used IP ACLs Document ID: 26448 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a
DevCentral Basics: Application Delivery Services PRESENTED BY:
 DevCentral Basics: Application Delivery Services PRESENTED BY: Networking Concepts Physical/Virtual NICs VLANs and VLAN Groups Untagged and Tagged Interfaces Self IPs (local / floating) Routes are just
DevCentral Basics: Application Delivery Services PRESENTED BY: Networking Concepts Physical/Virtual NICs VLANs and VLAN Groups Untagged and Tagged Interfaces Self IPs (local / floating) Routes are just
How to Configure a Dynamic Mesh VPN with the GTI Editor
 How to Configure a Dynamic Mesh VPN with the GTI Editor The GTI editor greatly simplifies creating a dynamic mesh VPN network with a large number of NextGen F- Series Firewalls. You can enable dynamic
How to Configure a Dynamic Mesh VPN with the GTI Editor The GTI editor greatly simplifies creating a dynamic mesh VPN network with a large number of NextGen F- Series Firewalls. You can enable dynamic
WatchGuard System Manager Fireware Configuration Guide. WatchGuard Fireware Pro v8.1
 WatchGuard System Manager Fireware Configuration Guide WatchGuard Fireware Pro v8.1 Notice to Users Information in this guide is subject to change without notice. Companies, names, and data used in examples
WatchGuard System Manager Fireware Configuration Guide WatchGuard Fireware Pro v8.1 Notice to Users Information in this guide is subject to change without notice. Companies, names, and data used in examples
Configuring Transparent Redirection for Standalone Content Engines
 CHAPTER 6 Configuring Transparent Redirection for Standalone Content Engines This chapter discusses the following methods for transparently redirecting content requests to standalone Content Engines: Web
CHAPTER 6 Configuring Transparent Redirection for Standalone Content Engines This chapter discusses the following methods for transparently redirecting content requests to standalone Content Engines: Web
Configure FTD Interfaces in Inline-Pair Mode
 Configure FTD Interfaces in Inline-Pair Mode Contents Introduction Prerequisites Requirements Components Used Background Information Configure Inline Pair Interface on FTD Network Diagram Verify Verify
Configure FTD Interfaces in Inline-Pair Mode Contents Introduction Prerequisites Requirements Components Used Background Information Configure Inline Pair Interface on FTD Network Diagram Verify Verify
Connecting DataCenters with OverLapping Private IP Addresses & Hiding Real Server IP For Security.
 Connecting DataCenters with OverLapping Private IP Addresses & Hiding Real Server IP For Security. Overview Connecting Multiple Data-Centers or Remote Branches to Centralized or Hub Sites is very common
Connecting DataCenters with OverLapping Private IP Addresses & Hiding Real Server IP For Security. Overview Connecting Multiple Data-Centers or Remote Branches to Centralized or Hub Sites is very common
CISCO EXAM QUESTIONS & ANSWERS
 CISCO 642-618 EXAM QUESTIONS & ANSWERS Number: 642-618 Passing Score: 800 Time Limit: 120 min File Version: 39.6 http://www.gratisexam.com/ CISCO 642-618 EXAM QUESTIONS & ANSWERS Exam Name: Deploying Cisco
CISCO 642-618 EXAM QUESTIONS & ANSWERS Number: 642-618 Passing Score: 800 Time Limit: 120 min File Version: 39.6 http://www.gratisexam.com/ CISCO 642-618 EXAM QUESTIONS & ANSWERS Exam Name: Deploying Cisco
Broadcast Infrastructure Cybersecurity - Part 2
 SBE Webinar Series - 2018 Broadcast Infrastructure Cybersecurity - Part 2 Wayne M. Pecena, CPBE, CBNE Texas A&M University Educational Broadcast Services KAMU FM-TV Broadcast Infrastructure Cybersecurity
SBE Webinar Series - 2018 Broadcast Infrastructure Cybersecurity - Part 2 Wayne M. Pecena, CPBE, CBNE Texas A&M University Educational Broadcast Services KAMU FM-TV Broadcast Infrastructure Cybersecurity
CSE/EE 461 Lecture 13 Connections and Fragmentation. TCP Connection Management
 CSE/EE 461 Lecture 13 Connections and Fragmentation Tom Anderson tom@cs.washington.edu Peterson, Chapter 5.2 TCP Connection Management Setup assymetric 3-way handshake Transfer sliding window; data and
CSE/EE 461 Lecture 13 Connections and Fragmentation Tom Anderson tom@cs.washington.edu Peterson, Chapter 5.2 TCP Connection Management Setup assymetric 3-way handshake Transfer sliding window; data and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
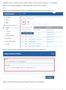 Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
WCCPv2 and WCCP Enhancements
 WCCPv2 and WCCP Enhancements Release 12.0(11)S June 20, 2000 This feature module describes the Web Cache Communication Protocol (WCCP) Enhancements feature and includes information on the benefits of the
WCCPv2 and WCCP Enhancements Release 12.0(11)S June 20, 2000 This feature module describes the Web Cache Communication Protocol (WCCP) Enhancements feature and includes information on the benefits of the
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Make the Client IP Address Available to the Back-end Server
 How to Make the Client IP Address Available to the Back-end Server For Layer 4 - UDP and Layer 4 - TCP services, the actual client IP address is passed to the server in the TCP header. No further configuration
How to Make the Client IP Address Available to the Back-end Server For Layer 4 - UDP and Layer 4 - TCP services, the actual client IP address is passed to the server in the TCP header. No further configuration
Configuring IPv6 ACLs
 CHAPTER 37 When the Cisco ME 3400 Ethernet Access switch is running the metro IP access image, you can filter IP Version 6 (IPv6) traffic by creating IPv6 access control lists (ACLs) and applying them
CHAPTER 37 When the Cisco ME 3400 Ethernet Access switch is running the metro IP access image, you can filter IP Version 6 (IPv6) traffic by creating IPv6 access control lists (ACLs) and applying them
IPv6 Access Control Lists
 Access lists determine what traffic is blocked and what traffic is forwarded at device interfaces and allow filtering of traffic based on source and destination addresses, and inbound and outbound traffic
Access lists determine what traffic is blocked and what traffic is forwarded at device interfaces and allow filtering of traffic based on source and destination addresses, and inbound and outbound traffic
Internet Security: Firewall
 Internet Security: Firewall What is a Firewall firewall = wall to protect against fire propagation More like a moat around a medieval castle restricts entry to carefully controlled points restricts exits
Internet Security: Firewall What is a Firewall firewall = wall to protect against fire propagation More like a moat around a medieval castle restricts entry to carefully controlled points restricts exits
ipv6 hello-interval eigrp
 ipv6 hello-interval eigrp ipv6 hello-interval eigrp To configure the hello interval for the Enhanced Interior Gateway Routing Protocol (EIGRP) for IPv6 routing process designated by an autonomous system
ipv6 hello-interval eigrp ipv6 hello-interval eigrp To configure the hello interval for the Enhanced Interior Gateway Routing Protocol (EIGRP) for IPv6 routing process designated by an autonomous system
