HAROLD BAELE MICROSOFT CLOUD TECHNICAL CONSULTANT MICROSOFT CERTIFIED TRAINER. New protection capabilities in Windows Server 2016
|
|
|
- Crystal Malone
- 5 years ago
- Views:
Transcription
1 HAROLD BAELE MICROSOFT CLOUD TECHNICAL CONSULTANT MICROSOFT CERTIFIED TRAINER New protection capabilities in Windows Server 2016
2 HAROLD BAELE MICROSOFT CLOUD TECHNICAL CONSULTANT AND MICROSOFT CERTIFIED Trainer since 2000 on Operating Systems, Networking, AD Exchange Office 365 PowerShell Azure IAAS Consultant since 2016 Azure IAAS Office 365 since 2015 in a Hybrid Cloud context ModernBiz - PPE s CSP Workshops
3 Security is a top priority for IT Increasing incidents Multiple motivations Bigger risk
4 Breaches cost a lot of money (Average $4M based on Ponemon Institute) Customers pay for your services Before $ $ $ $ After You pay customers compensation to keep them using your services Productivity Employees efficiently perform work activities Employees waste hours a day using manual processes $ Overspending Reflex Appropriately sized & dedicated IT Security team IT Security team exponentially increases in size and remediation efforts require new and expensive products
5 Attack timeline First host compromised Domain admin compromised Attack discovered hours Mean dwell time 150+ days (varies by industry)
6 Example attack scenario
7 Hard lessons The network is no longer the security perimeter (it hasn t been for some time) Entry we can t stop this from happening Identity is the (new) security perimeter People will be fooled, bribed, blackmailed, etc. Eliminating human error isn t possible Insider-attacks are a big problem Compliance is very important Prevention methods aren t always technical or architectural Phishing works and will continue to do so Anomalous activity monitoring helps in detection; limit access through identity management & isolation But compliance and security are not the same thing: compliant!= secure Many will be operational and that will impose some level of additional operational friction security has a price $$$
8 Managed privileged identities Secure virtualization Secure the OS
9 Help protect credentials and privileged access
10 Challenges in protecting credentials Social engineering leads to credential theft Most attacks involve gathering credentials (Pass-the-Hash attacks) Ben Mary Jake Admin Typical administrator Domain admin Administrative credentials typically provide unnecessary extra rights for unlimited time Capability Time
11 Helping protect privileged credentials Just Enough Administration (JEA) Just in Time Administration (JIT) Ben Mary Jake Admin JEA and JIT administration Domain admin Covered by Anthony Van Den Bossche in Identity: driving enterprise Mobility and Security Capability Capability and time needed Time
12 Helping protect privileged credentials Just Enough Administration (JEA) Just in Time Administration (JIT) Ben Mary Jake Admin Domain admin Credential Guard JEA and JIT administration Capability Capability and time needed Time
13 Helping protect privileged credentials Just Enough Administration (JEA) Just in Time Administration (JIT) Ben Mary Jake Admin Domain admin Credential Guard JEA and JIT administration Remote Credential Guard Capability Capability and time needed Time
14 VIRTUALISATION BASED SECURITY Credential process is doubled and running in Isolated User Mode Drivers or other kernel processes can access memory addresses where credentials hashes are stored LSALSO.exe is running in a separate zone, container based on virtualisation
15 ENABLING CREDENTIAL GUARD Using registry key Using Group Policy Using DISM (offline image servicing) 1. Add the virtualization-based security features by using Programs and Features 2. HKEY_LOCAL_MACHINE\System\ CurrentControlSet\Control\LSA\ LsaCfgFlags DWORD value = 1 (with UEFI lock) or 2 (without UEFI lock) 1. dism /image:<wim file name> /Enable- Feature /FeatureName:Microsoft-Hyper- V-Hypervisor 2. dism /image:<wim file name> /Enable- Feature /FeatureName:IsolatedUserMode
16 REQUIREMENTS WINDOWS 10 Windows 10 Enterprise Active Directory (any forest or domain level) UEFI firmware or higher Secure firmware update process Secure Boot Intel VT-x or AMD-V Intel VT-d or AMD-Vi I/O memory management unit Second Level Address Translation 64-bit CPU TPM 2.0
17 REQUIREMENTS SERVER 2016 Active Directory (any forest or domain level) UEFI firmware or higher Secure firmware update process Secure Boot Cannot be a domain controller
18 REQUIREMENTS FOR VIRTUAL MACHINES The Hyper-V host must have an IOMMU, input output memory management unit (IOMMU) is a memory management unit (MMU) that connects a direct-memory-access capable (DMA-capable) I/O bus to the main memory Host and guest must be running Windows Server 2016 or Windows 10 version The Hyper-V virtual machine must be Generation 2, have an enabled virtual TPM
19 USING HASHES & IMPLEMENTING CREDENTIAL GUARD MimiKatz Preparations: No antivirus running NewAdmin is domain administrator On Client local share with localadmin credentials created On client share for NewUser accessible only CMD with admin credentials GEN2DC NWTRADERS.LOCAL SECURESRV1 Using hash to connect to connect /24 Credential guard implemented using GPO W2016VM Win10VM
20 REMOTE CREDENTIAL GUARD No hash on remote session SSO with SSO One Identity checked at every connection aka Single Sign On Previous Identity check re-used aka Seamless Sign On
21 CONSIDERATIONS FOR REMOTE CREDENTIAL GUARD Active Directory Directory Services only. Remote Desktop Gateway is not compatible with RCG. No use of saved credentials. Needs the same domain or trusted domains. Forcing it: mstsc /remoteguard
22 LOGGING ON WITH REMOTE CREDENTIAL GUARD Preparation: GPO with remote credential guard From Gen2DC, RDP to Win10VM with current credentials
23 YOU ENABLED CREDENTIAL GUARD. WHAT CREDENTIALS ARE STILL IN THE OPEN? Software that manages credentials outside of Windows feature protection Local accounts and Microsoft Accounts The Directory database running on Windows Server 2016 domain controllers Credential input pipelines, such as Windows Server 2016 servers running Remote Desktop Gateway Key loggers Physical attacks Attacker with malware on the PC using the privileges associated with any credential Third-party security packages Digest and CredSSP credentials Supplied credentials for NTLM authentication are not protected Stored credentials
24 DISABLE CREDENTIAL (DEVICE) GUARD FROM OUTSIDE THE VM Credential guard and device guard rely on Virtualization Based Security From the host, you can disable this for a virtual machine: Set-VMSecurity -VMName <VMName> -VirtualizationBasedSecurityOptOut $true
25 Secure virtualization
26 Challenges protecting virtual machines Any compromised or malicious fabric administrators can access guest virtual machines. Health of hosts not taken into account before running VMs. Tenant s VMs are exposed to storage and network attacks. Virtual machines can t take advantage of hardwarerooted security capabilities such as TPMs.
27 Helping protect virtual machines Shielded Virtual Machines Use BitLocker to encrypt the disk and state of virtual machines protecting secrets from compromised admins and malware. Building perimeter Computer room Hyper-V Hyper-V Host Guardian Service Attests to host health releasing the keys required to boot or migrate a Shielded VM only to healthy hosts. Generation 2 VMs Supports virtualized equivalents of hardware security technologies (e.g., TPMs) enabling BitLocker encryption for Shielded Virtual Machines. Physical machine Virtual machine Shielded virtual machine ` *
28 Demonstration video Shielded VMs
29 GUARDED FABRIC Shielded VM Virtual Secure Mode HYPER- V HOST 1 Hello, I m HOST1, can I have some keys, please? HOST GUARDIAN SERVICE (HGS) WINDOWS SERVER 2016 HYPER- V HOSTS HYPER- V HOST 2 Virtual Secure Mode Virtual Secure Mode HYPER- V HOST 3 Why certainly, I know you & I must say you re looking very healthy today! + KEY PROTECTION + HEALTH ATTESTATION
30 GUARDED FABRIC Shielded VM HOST GUARDIAN SERVICE (HGS) WINDOWS SERVER 2016 HYPER- V HOSTS HYPER- V HOST 1 HYPER- V HOST 2 Virtual Secure Mode Virtual Secure Mode Virtual Secure Mode HYPER- V HOST 3 OK, so I m healthy then! Can I have the keys now? Sure, your certificate of health authorizes me to release keys to you for 8 hours + KEY PROTECTION + HEALTH ATTESTATION
31 Shielded VMs Multiple levels of security
32 Shielded VMs Host Guardian Service
33 Shielded VMs Attestation mode types Attestation mode you choose for hosts Host assurances TPM-trusted attestation: Offers the strongest possible protections but also requires more configuration steps. Host hardware and firmware must include TPM 2.0 and UEFI with secure boot enabled. Admin-trusted attestation: Intended to support existing host hardware where TPM 2.0 is not available. Requires fewer configuration steps and is compatible with commonplace server hardware. Guarded hosts that can run shielded VMs are approved based on their TPM identity, measured boot sequence and code integrity policies so that you can ensure that these hosts are only running approved code. Guarded hosts that can run shielded VMs are approved by the Host Guardian Service based on membership in a designated Active Directory Domain Services (AD DS) security group.
34 Shielded VMs Trusted apps on trusted Hosts
35 Shielded VMs Trusted hardware check
36 Shielded VMs VHD protection using trusted VHD image
37 Shielded VMs shielding data
38 Shielded VMs - guardian
39
How Shielded VMs Protect Your Data
 How Shielded VMs Protect Your Data Jan Marek MVP MCC MCT MCSE MCSD Head of CDM & marek@kpcs.cz Architect @ KPCS CZ www.atom.ms www.kpcs.cz www.janmarek.eu Traditional Security Services (AD, MSSQL, ShP)
How Shielded VMs Protect Your Data Jan Marek MVP MCC MCT MCSE MCSD Head of CDM & marek@kpcs.cz Architect @ KPCS CZ www.atom.ms www.kpcs.cz www.janmarek.eu Traditional Security Services (AD, MSSQL, ShP)
Feature Comparison Summary
 Feature Comparison Summary,, and The cloud-ready operating system is the cloud-ready operating system that delivers new layers of security and Azure-inspired innovation for the applications and infrastructure
Feature Comparison Summary,, and The cloud-ready operating system is the cloud-ready operating system that delivers new layers of security and Azure-inspired innovation for the applications and infrastructure
Windows Server Security Guide
 Windows Server Security Guide August 2017 Contents Windows Server 2016 Security Guide... 3 Why is Windows Server 2016 security important?... 3 How does Windows Server 2016 help prevent and detect compromise?...
Windows Server Security Guide August 2017 Contents Windows Server 2016 Security Guide... 3 Why is Windows Server 2016 security important?... 3 How does Windows Server 2016 help prevent and detect compromise?...
Securing Windows Server 2016
 Course 20744C: Securing Windows Server 2016 Page 1 of 7 Securing Windows Server 2016 Course 20744C: 4 days; Instructor-Led Introduction This four-day, instructor-led course teaches IT professionals how
Course 20744C: Securing Windows Server 2016 Page 1 of 7 Securing Windows Server 2016 Course 20744C: 4 days; Instructor-Led Introduction This four-day, instructor-led course teaches IT professionals how
Feature Comparison Summary
 Feature Comparison Summary, and The cloud-ready operating system Thanks to cloud technology, the rate of change is faster than ever before, putting more pressure on IT. Organizations demand increased security,
Feature Comparison Summary, and The cloud-ready operating system Thanks to cloud technology, the rate of change is faster than ever before, putting more pressure on IT. Organizations demand increased security,
"Charting the Course... MOC C: Securing Windows Server Course Summary
 Course Summary Description This five-day, instructor-led course teaches IT professionals how they can enhance the security of the IT infrastructure that they administer. This course begins by emphasizing
Course Summary Description This five-day, instructor-led course teaches IT professionals how they can enhance the security of the IT infrastructure that they administer. This course begins by emphasizing
Microsoft Securing Windows Server 2016
 1800 ULEARN (853 276) www.ddls.com.au Length 5 days Microsoft 20744 - Securing Windows Server 2016 Price $4290.00 (inc GST) Version B Overview This five-day, instructor-led course teaches IT professionals
1800 ULEARN (853 276) www.ddls.com.au Length 5 days Microsoft 20744 - Securing Windows Server 2016 Price $4290.00 (inc GST) Version B Overview This five-day, instructor-led course teaches IT professionals
Microsoft. Exam Questions Securing Windows Server 2016
 Microsoft Exam Questions 70-744 Securing Windows Server 2016 NEW QUESTION 1 Note: The question is part of a series of questions th«present the same scenario. Each question In the series contains a unique
Microsoft Exam Questions 70-744 Securing Windows Server 2016 NEW QUESTION 1 Note: The question is part of a series of questions th«present the same scenario. Each question In the series contains a unique
Course Outline. Course Outline :: 20744A::
 Module Title : 20744A: Securing Windows Server 2016 Duration : 5 days Overview This five-day, instructor-led course teaches IT professionals how they can enhance the security of the IT infrastructure that
Module Title : 20744A: Securing Windows Server 2016 Duration : 5 days Overview This five-day, instructor-led course teaches IT professionals how they can enhance the security of the IT infrastructure that
Windows Server 2016 Tomorrow s operating system, today. Licensing & feature comparison guide.
 2016 Tomorrow s operating system, today. Licensing & feature comparison guide. Contents 10 reasons you ll love 2016 4 Product overview 6 Feature differentiation and core-based pricing 7 Core-based licensing
2016 Tomorrow s operating system, today. Licensing & feature comparison guide. Contents 10 reasons you ll love 2016 4 Product overview 6 Feature differentiation and core-based pricing 7 Core-based licensing
Securing Privileged Access Securing High Value Assets Datacenter Security Information Protection Information Worker and Device Protection
 Securing Privileged Access Securing High Value Assets Datacenter Security Information Protection Information Worker and Device Protection Azure Active Directory 3 rd Party IaaS IaaS Rights Management Services
Securing Privileged Access Securing High Value Assets Datacenter Security Information Protection Information Worker and Device Protection Azure Active Directory 3 rd Party IaaS IaaS Rights Management Services
[MS20744]: Securing Windows Server 2016
![[MS20744]: Securing Windows Server 2016 [MS20744]: Securing Windows Server 2016](/thumbs/95/124187558.jpg) [MS20744]: Securing Windows Server 2016 Length : 5 Days Audience(s) : IT Professionals Level : 300 Technology : Windows Server Delivery Method : Instructor-led (Classroom) Course Overview This five-day,
[MS20744]: Securing Windows Server 2016 Length : 5 Days Audience(s) : IT Professionals Level : 300 Technology : Windows Server Delivery Method : Instructor-led (Classroom) Course Overview This five-day,
Consultant since many years. Mainly working with defense and public sector. MCSE on Windows Server 2000 security ;-)
 About Consultant since many years Mainly working with defense and public sector MCSE on Windows Server 2000 security ;-) CYBERCRIME: STATE OF THE UNION EVOLUTION OF ATTACKS Mischief Fraud and theft Damage
About Consultant since many years Mainly working with defense and public sector MCSE on Windows Server 2000 security ;-) CYBERCRIME: STATE OF THE UNION EVOLUTION OF ATTACKS Mischief Fraud and theft Damage
Securing Windows Server 2016
 Course 20744: Securing Windows Server 2016 Page 1 of 7 Securing Windows Server 2016 Course 20744: 4 days; Instructor-Led Introduction This four-day, instructor-led course teaches IT professionals how they
Course 20744: Securing Windows Server 2016 Page 1 of 7 Securing Windows Server 2016 Course 20744: 4 days; Instructor-Led Introduction This four-day, instructor-led course teaches IT professionals how they
Course Outline 20744B
 Course Outline 20744B Module 1: Attacks, breach detection, and Sysinternals tools In this module, students will learn about breach detection, attack types and vectors, cybercrime, and how you can analyse
Course Outline 20744B Module 1: Attacks, breach detection, and Sysinternals tools In this module, students will learn about breach detection, attack types and vectors, cybercrime, and how you can analyse
20744: Securing Windows Server Sobre o curso. Microsoft. Nível: Avançado Duração: 35h
 20744: Securing Windows Server 2016 Microsoft Nível: Avançado Duração: 35h Sobre o curso This five-day, instructor-led course teaches IT professionals how they can enhance the security of the IT infrastructure
20744: Securing Windows Server 2016 Microsoft Nível: Avançado Duração: 35h Sobre o curso This five-day, instructor-led course teaches IT professionals how they can enhance the security of the IT infrastructure
MODERN DESKTOP SECURITY
 MODERN DESKTOP SECURITY I M GOING TO BE HONEST. WE RE IN THE FIGHT OF OUR DIGITAL LIVES, AND WE ARE NOT WINNING! M I C H A E L M C C A U L, C H A I R M A N, U S H O M E L A N D S E C U R I T Y C O M M
MODERN DESKTOP SECURITY I M GOING TO BE HONEST. WE RE IN THE FIGHT OF OUR DIGITAL LIVES, AND WE ARE NOT WINNING! M I C H A E L M C C A U L, C H A I R M A N, U S H O M E L A N D S E C U R I T Y C O M M
Evolution of Cyber Security. Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa
 Evolution of Cyber Security Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa Nasser.Kettani@microsoft.com @nkettani MODERN SECURITY THREATS THERE ARE TWO KINDS OF BIG COMPANIES:
Evolution of Cyber Security Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa Nasser.Kettani@microsoft.com @nkettani MODERN SECURITY THREATS THERE ARE TWO KINDS OF BIG COMPANIES:
Windows 10 edition. Find out which. is right for you. Core features. Familar, and better than ever Home Pro Enterprise Education Mobile.
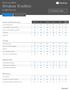 Core features Familar, and better than ever Home Pro Education Customizable Start Menu Windows Defender & Windows firewall N/A 1 N/A Fast start up with Hiberboot and InstantGo 2 N/A N/A TPM support 3 Battery
Core features Familar, and better than ever Home Pro Education Customizable Start Menu Windows Defender & Windows firewall N/A 1 N/A Fast start up with Hiberboot and InstantGo 2 N/A N/A TPM support 3 Battery
W11 Hyper-V security. Jesper Krogh.
 W11 Hyper-V security Jesper Krogh jesper_krogh@dell.com Jesper Krogh Speaker intro Senior Solution architect at Dell Responsible for Microsoft offerings and solutions within Denmark Specialities witin:
W11 Hyper-V security Jesper Krogh jesper_krogh@dell.com Jesper Krogh Speaker intro Senior Solution architect at Dell Responsible for Microsoft offerings and solutions within Denmark Specialities witin:
Windows 10 Security & Audit
 Windows 10 Security & Audit John Tannahill, CA, CISM, CGEIT, CRISC, CSX-P jtannahi@rogers.com Windows 10 Editions Home Pro Enterprise Education Mobile IoT Editions 1 Windows 10 Builds Windows 10 (initial
Windows 10 Security & Audit John Tannahill, CA, CISM, CGEIT, CRISC, CSX-P jtannahi@rogers.com Windows 10 Editions Home Pro Enterprise Education Mobile IoT Editions 1 Windows 10 Builds Windows 10 (initial
Enterprise Ransomware Mitigations
 打造數碼安全校園 Enterprise Ransomware Mitigations Windows 10, Edge Browser, Office ATP Enterprise Mobility Suite (EMS) ATP OneDrive for Business Azure Backup 3rd party Cloud Backup THE WINDOWS CLIENT DEFENSE
打造數碼安全校園 Enterprise Ransomware Mitigations Windows 10, Edge Browser, Office ATP Enterprise Mobility Suite (EMS) ATP OneDrive for Business Azure Backup 3rd party Cloud Backup THE WINDOWS CLIENT DEFENSE
Securing Windows Server 2016 (20744)
 Securing Windows Server 2016 (20744) Formato do curso: Presencial Localidade: Lisboa Data: 13 Mai. 2019 a 17 Mai. 2019 Preço: 1670 Horário: Laboral - das 09h30 às 17h30 Duração: 35 horas This five-day,
Securing Windows Server 2016 (20744) Formato do curso: Presencial Localidade: Lisboa Data: 13 Mai. 2019 a 17 Mai. 2019 Preço: 1670 Horário: Laboral - das 09h30 às 17h30 Duração: 35 horas This five-day,
Securing Windows Server 2016 (20744)
 Securing Windows Server 2016 (20744) Duration: 5 Days Price: $895 Delivery Option: Attend via MOC On-Demand Students Will Learn Securing Windows Server Protecting credentials and implement privileged access
Securing Windows Server 2016 (20744) Duration: 5 Days Price: $895 Delivery Option: Attend via MOC On-Demand Students Will Learn Securing Windows Server Protecting credentials and implement privileged access
Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting
 Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting Microsoft Cloud Evangelist at Patriot Consulting Principal Systems Architect with 17 Years of experience Technical certifications: MCSE, MCITP Office
Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting Microsoft Cloud Evangelist at Patriot Consulting Principal Systems Architect with 17 Years of experience Technical certifications: MCSE, MCITP Office
MD-101: Modern Desktop Administrator Part 2
 Days: 5 Description: This five-day course is for Desktop Administrators that deploy, configure, secure, manage, and monitor devices and client applications in an enterprise environment. As desktops has
Days: 5 Description: This five-day course is for Desktop Administrators that deploy, configure, secure, manage, and monitor devices and client applications in an enterprise environment. As desktops has
IMPLEMENTING MICROSOFT CREDENTIAL GUARD FOR ISO 27001, PCI, AND FEDRAMP
 IMPLEMENTING MICROSOFT CREDENTIAL GUARD FOR ISO 27001, PCI, AND FEDRAMP North America Latin America Europe 877.224.8077 info@coalfire.com coalfire.com Coalfire sm and CoalfireOne sm are registered service
IMPLEMENTING MICROSOFT CREDENTIAL GUARD FOR ISO 27001, PCI, AND FEDRAMP North America Latin America Europe 877.224.8077 info@coalfire.com coalfire.com Coalfire sm and CoalfireOne sm are registered service
Critical Hygiene for Preventing Major Breaches
 SESSION ID: CXO-F02 Critical Hygiene for Preventing Major Breaches Jonathan Trull Microsoft Enterprise Cybersecurity Group @jonathantrull Tony Sager Center for Internet Security @CISecurity Mark Simos
SESSION ID: CXO-F02 Critical Hygiene for Preventing Major Breaches Jonathan Trull Microsoft Enterprise Cybersecurity Group @jonathantrull Tony Sager Center for Internet Security @CISecurity Mark Simos
microsoft. Number: Passing Score: 800 Time Limit: 120 min.
 70-744 microsoft Number: 70-744 Passing Score: 800 Time Limit: 120 min Exam A QUESTION 1 This question is part of a series of question that use the same or similar answer choices. Your network contains
70-744 microsoft Number: 70-744 Passing Score: 800 Time Limit: 120 min Exam A QUESTION 1 This question is part of a series of question that use the same or similar answer choices. Your network contains
Securing Windows Server 2016
 Securing Windows Server 2016 Duration: 5 Days Course Code: M20744 Version: C Delivery Method: Elearning (Self-paced) Overview: This five-day, instructor-led course teaches IT professionals how they can
Securing Windows Server 2016 Duration: 5 Days Course Code: M20744 Version: C Delivery Method: Elearning (Self-paced) Overview: This five-day, instructor-led course teaches IT professionals how they can
Windows Server The operating system
 Windows Server 2019 The operating system that bridges onpremises and cloud By maximizing technology and infrastructure investments with Windows Server 2019, forward-facing businesses can capture direct
Windows Server 2019 The operating system that bridges onpremises and cloud By maximizing technology and infrastructure investments with Windows Server 2019, forward-facing businesses can capture direct
Přehled novinek v Hyper-V 2016 Kamil Roman
 Přehled novinek v Hyper-V 2016 Kamil Roman Mail: IT@KamilRT.net Twitter: @KamilRT blog: ITblog.KamilRT.net 1 2 3 Rising number of organizations suffer from breaches 1 1 2 2 3 3 3 4 Shielded VMs Shielded
Přehled novinek v Hyper-V 2016 Kamil Roman Mail: IT@KamilRT.net Twitter: @KamilRT blog: ITblog.KamilRT.net 1 2 3 Rising number of organizations suffer from breaches 1 1 2 2 3 3 3 4 Shielded VMs Shielded
Big and Bright - Security
 Big and Bright - Security Big and Bright Security Embedded Tech Trends 2018 Does this mean: Everything is Big and Bright our security is 100% effective? or There are Big security concerns but Bright solutions?
Big and Bright - Security Big and Bright Security Embedded Tech Trends 2018 Does this mean: Everything is Big and Bright our security is 100% effective? or There are Big security concerns but Bright solutions?
exam.72q.
 70-744.exam.72q Number: 70-744 Passing Score: 800 Time Limit: 120 min 70-744 Securing Windows Server 2016 Exam A QUESTION 1 Note: This question is part of a series of questions that present the same scenario.
70-744.exam.72q Number: 70-744 Passing Score: 800 Time Limit: 120 min 70-744 Securing Windows Server 2016 Exam A QUESTION 1 Note: This question is part of a series of questions that present the same scenario.
Securing Windows Server 2016
 Securing Windows Server 2016 Varighed: 5 Days Kursus Kode: M20744 Beskrivelse: This five-day, instructor-led course teaches IT professionals how they can enhance the security of the IT infrastructure that
Securing Windows Server 2016 Varighed: 5 Days Kursus Kode: M20744 Beskrivelse: This five-day, instructor-led course teaches IT professionals how they can enhance the security of the IT infrastructure that
Identity & Access Management
 Identity & Access Management THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY WITHOUT COMPROMISING SECURITY? S E C U R I T Y OR P R O D U C T I V I T Y On-premises THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY
Identity & Access Management THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY WITHOUT COMPROMISING SECURITY? S E C U R I T Y OR P R O D U C T I V I T Y On-premises THE PROBLEM: HOW DO WE ENABLE PRODUCTIVITY
Desktop features placemat
 Desktop features placemat Home Pro Enterprise Existing Differentiated Features in Win7 /Win8.1 Domain Join and Group Policy Management Existing Win7 / Win 8.1 Enterprise features Windows 10: Management
Desktop features placemat Home Pro Enterprise Existing Differentiated Features in Win7 /Win8.1 Domain Join and Group Policy Management Existing Win7 / Win 8.1 Enterprise features Windows 10: Management
UEFI, SecureBoot, DeviceGuard, TPM a WHB (un)related technologies
 GOLD PARTNER: Hlavní partner: Hlavní odborný partner: UEFI, SecureBoot, DeviceGuard, TPM a WHB (un)related technologies Ing. Ondřej Ševeček GOPAS a.s. MCSM:Directory MVP:Security CISA CISM CEH CHFI ondrej@sevecek.com
GOLD PARTNER: Hlavní partner: Hlavní odborný partner: UEFI, SecureBoot, DeviceGuard, TPM a WHB (un)related technologies Ing. Ondřej Ševeček GOPAS a.s. MCSM:Directory MVP:Security CISA CISM CEH CHFI ondrej@sevecek.com
Technical Feature Comparison Guide
 Technical Feature Comparison Guide,, and Contents How to use this comparison guide... 2 The cloud-ready operating system... 2 editions... 4 Security... 4 Identity... 10 Compute... 15 Storage... 20 Networking...
Technical Feature Comparison Guide,, and Contents How to use this comparison guide... 2 The cloud-ready operating system... 2 editions... 4 Security... 4 Identity... 10 Compute... 15 Storage... 20 Networking...
WINDOWS 10 ENTERPRISE New Security Features
 WINDOWS 10 ENTERPRISE New Security Features J. Abernethy mindshift Technologies Josh Quinn mindshift Technologies #ILTALSS #LSS26 TODAY S AGENDA Windows 10 Security Fundamentals Managing Windows 10 Security
WINDOWS 10 ENTERPRISE New Security Features J. Abernethy mindshift Technologies Josh Quinn mindshift Technologies #ILTALSS #LSS26 TODAY S AGENDA Windows 10 Security Fundamentals Managing Windows 10 Security
Single Sign-On Showdown
 Single Sign-On Showdown ADFS vs Pass-Through Authentication Max Fritz Solutions Architect SADA Systems #ITDEVCONNECTIONS Azure AD Identity Sync & Auth Timeline 2009 2012 DirSync becomes Azure AD Sync 2013
Single Sign-On Showdown ADFS vs Pass-Through Authentication Max Fritz Solutions Architect SADA Systems #ITDEVCONNECTIONS Azure AD Identity Sync & Auth Timeline 2009 2012 DirSync becomes Azure AD Sync 2013
Windows Server Windows Server Windows Server 2008
 2003 2008 2012 Hardware Innovation X86 Symmetric Multi-Processor (SMP) s Affordable servers for the masses Software Innovation Window 2003 SQL 2005 Exchange 2003 Hardware Innovation X64 s Multi-Core s
2003 2008 2012 Hardware Innovation X86 Symmetric Multi-Processor (SMP) s Affordable servers for the masses Software Innovation Window 2003 SQL 2005 Exchange 2003 Hardware Innovation X64 s Multi-Core s
Cloud Customer Architecture for Securing Workloads on Cloud Services
 Cloud Customer Architecture for Securing Workloads on Cloud Services http://www.cloud-council.org/deliverables/cloud-customer-architecture-for-securing-workloads-on-cloud-services.htm Webinar April 19,
Cloud Customer Architecture for Securing Workloads on Cloud Services http://www.cloud-council.org/deliverables/cloud-customer-architecture-for-securing-workloads-on-cloud-services.htm Webinar April 19,
Technical Feature Comparison Guide
 Technical Feature Comparison Guide,, and Contents How to use this comparison guide... 2 The cloud-ready operating system... 2 editions... 4 Security... 4 Identity... 10 Compute... 15 Storage... 17 Networking...
Technical Feature Comparison Guide,, and Contents How to use this comparison guide... 2 The cloud-ready operating system... 2 editions... 4 Security... 4 Identity... 10 Compute... 15 Storage... 17 Networking...
News and Updates June 1, 2017
 Microsoft Azure News and Updates June 1, 2017 Azure Backup for Windows Server System State Modern Backup Storage with Azure Backup Server v2 vcenter/esxi 6.5 support for Azure Backup Server Larger Disk
Microsoft Azure News and Updates June 1, 2017 Azure Backup for Windows Server System State Modern Backup Storage with Azure Backup Server v2 vcenter/esxi 6.5 support for Azure Backup Server Larger Disk
Exam Questions Demo Microsoft. Exam Questions Securing Windows Server 2016.
 Microsoft Exam Questions 70-744 Securing Windows Server 2016 Version:Demo 1.. You are implementing Privileged Access Management (PAM) for an Active Directory forest named contoso.com. You install a bastion
Microsoft Exam Questions 70-744 Securing Windows Server 2016 Version:Demo 1.. You are implementing Privileged Access Management (PAM) for an Active Directory forest named contoso.com. You install a bastion
Pass-the-Hash Attacks
 Pass-the-Hash Attacks Mgr. Michael Grafnetter www.dsinternals.com Agenda PtH Attack Anatomy Mitigation Proactive Reactive Windows 10 + Windows Server 2016 Microsoft Advanced Threat Analytics PtH Attack
Pass-the-Hash Attacks Mgr. Michael Grafnetter www.dsinternals.com Agenda PtH Attack Anatomy Mitigation Proactive Reactive Windows 10 + Windows Server 2016 Microsoft Advanced Threat Analytics PtH Attack
ADC im Cloud - Zeitalter
 ADC im Cloud - Zeitalter Applikationsdienste für Hybrid-Cloud- und Microservice-Szenarien Ralf Sydekum, SE Manager DACH, F5 Networks GmbH Some of the Public Cloud Related Questions You May Have.. It s
ADC im Cloud - Zeitalter Applikationsdienste für Hybrid-Cloud- und Microservice-Szenarien Ralf Sydekum, SE Manager DACH, F5 Networks GmbH Some of the Public Cloud Related Questions You May Have.. It s
MU2b Authentication, Authorization and Accounting Questions Set 2
 MU2b Authentication, Authorization and Accounting Questions Set 2 1. You enable the audit of successful and failed policy changes. Where can you view entries related to policy change attempts? Lesson 2
MU2b Authentication, Authorization and Accounting Questions Set 2 1. You enable the audit of successful and failed policy changes. Where can you view entries related to policy change attempts? Lesson 2
Protecting Against Modern Attacks. Protection Against Modern Attack Vectors
 Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
PLATFORM CONVERGENCE JOURNEY
 Windows 10 Client PLATFORM CONVERGENCE JOURNEY Converged OS kernel Converged app model Windows 10 DEPLOYMENT CHOICES Wipe-and-Load In-Place Provisioning Traditional process Capture data and settings
Windows 10 Client PLATFORM CONVERGENCE JOURNEY Converged OS kernel Converged app model Windows 10 DEPLOYMENT CHOICES Wipe-and-Load In-Place Provisioning Traditional process Capture data and settings
CS 356 Operating System Security. Fall 2013
 CS 356 Operating System Security Fall 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter 5 Database
CS 356 Operating System Security Fall 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter 5 Database
Microsoft Securing Windows Server
 Microsoft 70-744 Securing Windows Server 2016 http://killexams.com/pass4sure/exam-detail/70-744 QUESTION: 53 Your network contains an Active Directory domain named contoso.com. All servers run Windows
Microsoft 70-744 Securing Windows Server 2016 http://killexams.com/pass4sure/exam-detail/70-744 QUESTION: 53 Your network contains an Active Directory domain named contoso.com. All servers run Windows
Planning for and Managing Devices in the Enterprise: Enterprise Management Suite (EMS) & On-Premises Tools
 Enterprise Management Suite (EMS) & On-Premises Tools Page 1 of 7 Planning for and Managing Devices in the Enterprise: Enterprise Management Suite (EMS) & On-Premises Tools Course 20398A: 4 days; Instructor-Led
Enterprise Management Suite (EMS) & On-Premises Tools Page 1 of 7 Planning for and Managing Devices in the Enterprise: Enterprise Management Suite (EMS) & On-Premises Tools Course 20398A: 4 days; Instructor-Led
Microsoft Configuring Windows 8.1
 1800 ULEARN (853 276) www.ddls.com.au Length 5 days Microsoft 20687 - Configuring Windows 8.1 Price $4290.00 (inc GST) Version D Overview Get expert instruction and hands-on practice administering and
1800 ULEARN (853 276) www.ddls.com.au Length 5 days Microsoft 20687 - Configuring Windows 8.1 Price $4290.00 (inc GST) Version D Overview Get expert instruction and hands-on practice administering and
Presented by. Steven Audis. Microsoft Education Technology Advisor
 Presented by Steven Audis Microsoft Education Technology Advisor More Pressure than Ever on IT Technology Change Regulatory Compliance Competition Security Cost Reduction Keep Business Up & Running Customer
Presented by Steven Audis Microsoft Education Technology Advisor More Pressure than Ever on IT Technology Change Regulatory Compliance Competition Security Cost Reduction Keep Business Up & Running Customer
Future Forests: Realistic Strategies for AD Security & Red Forest Architecture
 SESSION ID: STR-R02 Future Forests: Realistic Strategies for AD Security & Red Forest Architecture Katie Knowles Security Consultant MWR InfoSecurity @_sigil Introduction: Why AD Matters How AD is Targeted
SESSION ID: STR-R02 Future Forests: Realistic Strategies for AD Security & Red Forest Architecture Katie Knowles Security Consultant MWR InfoSecurity @_sigil Introduction: Why AD Matters How AD is Targeted
Course 20533B: Implementing Microsoft Azure Infrastructure Solutions
 Course 20533B: Implementing Microsoft Azure Infrastructure Solutions Course details Course Outline Module 1: Introduction to Azure This module explains cloud computing, and compares cloud computing and
Course 20533B: Implementing Microsoft Azure Infrastructure Solutions Course details Course Outline Module 1: Introduction to Azure This module explains cloud computing, and compares cloud computing and
Terra: A Virtual Machine-Based Platform for Trusted Computing by Garfinkel et al. (Some slides taken from Jason Franklin s 712 lecture, Fall 2006)
 Terra: A Virtual Machine-Based Platform for Trusted Computing by Garfinkel et al. (Some slides taken from Jason Franklin s 712 lecture, Fall 2006) Trusted Computing Hardware What can you do if you have
Terra: A Virtual Machine-Based Platform for Trusted Computing by Garfinkel et al. (Some slides taken from Jason Franklin s 712 lecture, Fall 2006) Trusted Computing Hardware What can you do if you have
Implementing Microsoft Azure Infrastructure Solutions
 Implementing Microsoft Azure Infrastructure Solutions OD20533C; On-Demand, Video-based Course Description This course is intended for IT professionals who are familiar with managing on-premises IT deployments
Implementing Microsoft Azure Infrastructure Solutions OD20533C; On-Demand, Video-based Course Description This course is intended for IT professionals who are familiar with managing on-premises IT deployments
Real-time Monitoring, Inventory and Change Tracking for. Track. Report. RESOLVE!
 Real-time Monitoring, Inventory and Change Tracking for Track. Report. RESOLVE! Powerful Monitoring Tool for Full Visibility over Your Hyper-V Environment VirtualMetric provides the most comprehensive
Real-time Monitoring, Inventory and Change Tracking for Track. Report. RESOLVE! Powerful Monitoring Tool for Full Visibility over Your Hyper-V Environment VirtualMetric provides the most comprehensive
Moving from Reactive to Proactive Security. Sami Laiho Adminize / Intility Senior Technical Fellow, MVP April 28 th New-York City
 Moving from Reactive to Proactive Security Sami Laiho Adminize / Intility Senior Technical Fellow, MVP April 28 th New-York City Thanks to our Organizers! Tome Tanasovski PowerShell MVP Blog: http://powertoe.wordpress.com/
Moving from Reactive to Proactive Security Sami Laiho Adminize / Intility Senior Technical Fellow, MVP April 28 th New-York City Thanks to our Organizers! Tome Tanasovski PowerShell MVP Blog: http://powertoe.wordpress.com/
Cloud Security, Mobility and Current Threats. Tristan Watkins, Head of Research and Innovation
 Cloud Security, Mobility and Current Threats Tristan Watkins, Head of Research and Innovation Threat Landscape Verizon Data Breach Investigations Report Verizon DBIR: Threat actors and actions Verizon
Cloud Security, Mobility and Current Threats Tristan Watkins, Head of Research and Innovation Threat Landscape Verizon Data Breach Investigations Report Verizon DBIR: Threat actors and actions Verizon
Planning for and Managing Devices in the Enterprise: Enterprise Mobility Suite (EMS) & On- Premises Tools
 Planning for and Managing Devices in the Enterprise: Enterprise Mobility Suite (EMS) & On- Premises Tools 20398BA - 5 Days - Instructor-led, Hands-on Introduction This five-day course teaches IT professionals
Planning for and Managing Devices in the Enterprise: Enterprise Mobility Suite (EMS) & On- Premises Tools 20398BA - 5 Days - Instructor-led, Hands-on Introduction This five-day course teaches IT professionals
Windows 10 and the Enterprise. Craig A. Brown Prepared for: GMIS
 Windows 10 and the Enterprise Craig A. Brown Prepared for: GMIS 11-2-2015 Introduction Craig A. Brown Microsoft Practice Leader Global Knowledge MCT, Since 1996 MCSA / MCSE / NT / 2000 / 2003 MCDST MCITP:
Windows 10 and the Enterprise Craig A. Brown Prepared for: GMIS 11-2-2015 Introduction Craig A. Brown Microsoft Practice Leader Global Knowledge MCT, Since 1996 MCSA / MCSE / NT / 2000 / 2003 MCDST MCITP:
Expert Reference Series of White Papers. BitLocker: Is It Really Secure? COURSES.
 Expert Reference Series of White Papers BitLocker: Is It Really Secure? 1-800-COURSES www.globalknowledge.com BitLocker: Is It Really Secure? Mark Mizrahi, Global Knowledge Instructor, MCSE, MCT, CEH Introduction:
Expert Reference Series of White Papers BitLocker: Is It Really Secure? 1-800-COURSES www.globalknowledge.com BitLocker: Is It Really Secure? Mark Mizrahi, Global Knowledge Instructor, MCSE, MCT, CEH Introduction:
Spring 2017 :: CSE 506. Introduction to. Virtual Machines. Nima Honarmand
 Introduction to Virtual Machines Nima Honarmand Virtual Machines & Hypervisors Virtual Machine: an abstraction of a complete compute environment through the combined virtualization of the processor, memory,
Introduction to Virtual Machines Nima Honarmand Virtual Machines & Hypervisors Virtual Machine: an abstraction of a complete compute environment through the combined virtualization of the processor, memory,
microsoft. Number: Passing Score: 800 Time Limit: 120 min.
 70-744 microsoft Number: 70-744 Passing Score: 800 Time Limit: 120 min Exam A QUESTION 1 This question is part of a series of question that use the same or similar answer choices. Your network contains
70-744 microsoft Number: 70-744 Passing Score: 800 Time Limit: 120 min Exam A QUESTION 1 This question is part of a series of question that use the same or similar answer choices. Your network contains
CSP 2017 Network Virtualisation and Security Scott McKinnon
 CSP 2017 Network Virtualisation and Security Scott McKinnon smckinnon@vmware.com Security Lead, Northern EMEA Network & Security, VMware Disclaimer This presentation may contain product features that are
CSP 2017 Network Virtualisation and Security Scott McKinnon smckinnon@vmware.com Security Lead, Northern EMEA Network & Security, VMware Disclaimer This presentation may contain product features that are
Securing the New Perimeter:
 Microsoft Future Decoded Securing the New Perimeter: Identity as the Keystone with Heathrow Airport 01/11/2018 Divider Title Slide Name Here Some Facts & Figures.. Passengers Team Heathrow Flights Size
Microsoft Future Decoded Securing the New Perimeter: Identity as the Keystone with Heathrow Airport 01/11/2018 Divider Title Slide Name Here Some Facts & Figures.. Passengers Team Heathrow Flights Size
Operating system hardening
 Operating system Comp Sci 3600 Security Outline 1 2 3 4 5 6 What is OS? Hardening process that includes planning, ation, uration, update, and maintenance of the operating system and the key applications
Operating system Comp Sci 3600 Security Outline 1 2 3 4 5 6 What is OS? Hardening process that includes planning, ation, uration, update, and maintenance of the operating system and the key applications
Securing Active Directory Administration
 Securing Active Directory Administration April 18, 2019 Sponsored by @BlackHatEvents / #BlackHatWebcasts Agenda On-Prem AD vs Azure AD Evolution of Administration Exploiting Typical Administration Methods
Securing Active Directory Administration April 18, 2019 Sponsored by @BlackHatEvents / #BlackHatWebcasts Agenda On-Prem AD vs Azure AD Evolution of Administration Exploiting Typical Administration Methods
Defense-in-Depth Against Malicious Software. Speaker name Title Group Microsoft Corporation
 Defense-in-Depth Against Malicious Software Speaker name Title Group Microsoft Corporation Agenda Understanding the Characteristics of Malicious Software Malware Defense-in-Depth Malware Defense for Client
Defense-in-Depth Against Malicious Software Speaker name Title Group Microsoft Corporation Agenda Understanding the Characteristics of Malicious Software Malware Defense-in-Depth Malware Defense for Client
Privilege Security & Next-Generation Technology. Morey J. Haber Chief Technology Officer
 Privilege Security & Next-Generation Technology Morey J. Haber Chief Technology Officer mhaber@beyondtrust.com Agenda The Next-Gen Threat Landscape o Infomatics, Breaches & the Attack Chain o Securing
Privilege Security & Next-Generation Technology Morey J. Haber Chief Technology Officer mhaber@beyondtrust.com Agenda The Next-Gen Threat Landscape o Infomatics, Breaches & the Attack Chain o Securing
70-410: Installing and Configuring Windows Server 2012
 70-410: Installing and Configuring Windows Server 2012 The following tables itemize changes to Exam 70-410. These changes will be made in January to include updates that relate to Windows Server 2012 R2
70-410: Installing and Configuring Windows Server 2012 The following tables itemize changes to Exam 70-410. These changes will be made in January to include updates that relate to Windows Server 2012 R2
Planning for and Managing Devices in the Enterprise: Enterprise Mobility Suite (EMS) & On-Premises Tools
 Planning for and Managing Devices in the Enterprise: Enterprise Mobility Suite (EMS) & On-Premises Tools OD20398B; On-Demand, Video-based Course Description This course teaches IT professionals how to
Planning for and Managing Devices in the Enterprise: Enterprise Mobility Suite (EMS) & On-Premises Tools OD20398B; On-Demand, Video-based Course Description This course teaches IT professionals how to
MCSA Windows 10. A Success Guide to Prepare- Installing and Configuring Windows 10. edusum.com
 70-698 MCSA Windows 10 A Success Guide to Prepare- Installing and Configuring Windows 10 edusum.com Table of Contents Introduction to 70-698 Exam on Installing and Configuring Windows 10... 2 Microsoft
70-698 MCSA Windows 10 A Success Guide to Prepare- Installing and Configuring Windows 10 edusum.com Table of Contents Introduction to 70-698 Exam on Installing and Configuring Windows 10... 2 Microsoft
Windows Devices. Device Capabilities. Premium. Entry
 Windows Devices $ Premium Entry Device Capabilities Windows 10 IoT $ Premium Windows 10 IoT Enterprise Desktop Shell, Win32 apps, Universal Windows Apps and Drivers 1 GB RAM, 16 GB Storage X86 Windows
Windows Devices $ Premium Entry Device Capabilities Windows 10 IoT $ Premium Windows 10 IoT Enterprise Desktop Shell, Win32 apps, Universal Windows Apps and Drivers 1 GB RAM, 16 GB Storage X86 Windows
CAN MICROSOFT HELP MEET THE GDPR
 CAN MICROSOFT HELP MEET THE GDPR REQUIREMENTS? Danny Uytgeerts Microsoft 365 TSP / P-Seller Privacy Consultant (certified DPO) Member of DPO-Pro (Professional association of Belgian DPOs) danny.uytgeerts@realdolmen.com
CAN MICROSOFT HELP MEET THE GDPR REQUIREMENTS? Danny Uytgeerts Microsoft 365 TSP / P-Seller Privacy Consultant (certified DPO) Member of DPO-Pro (Professional association of Belgian DPOs) danny.uytgeerts@realdolmen.com
Azure Webinar. Resilient Solutions March Sander van den Hoven Principal Technical Evangelist Microsoft
 Azure Webinar Resilient Solutions March 2017 Sander van den Hoven Principal Technical Evangelist Microsoft DX @svandenhoven 1 What is resilience? Client Client API FrontEnd Client Client Client Loadbalancer
Azure Webinar Resilient Solutions March 2017 Sander van den Hoven Principal Technical Evangelist Microsoft DX @svandenhoven 1 What is resilience? Client Client API FrontEnd Client Client Client Loadbalancer
Microsoft Azure Integration and Security. Course Code: AZ-101; Duration: 4 days; Instructorled
 Microsoft Azure Integration and Security Course Code: AZ-101; Duration: 4 days; Instructorled WHAT YOU WILL LEARN This course teaches IT professionals how to discover, assess, plan and implement a migration
Microsoft Azure Integration and Security Course Code: AZ-101; Duration: 4 days; Instructorled WHAT YOU WILL LEARN This course teaches IT professionals how to discover, assess, plan and implement a migration
Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering. Key Threats Internet was just growing Mail was on the verge
 Key Threats Internet was just growing Mail was on the verge Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering Key Threats Code Red and Nimda (2001), Blaster (2003), Slammer
Key Threats Internet was just growing Mail was on the verge Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering Key Threats Code Red and Nimda (2001), Blaster (2003), Slammer
Premediation. The Art of Proactive Remediation. Matthew McWhirt, Senior Manager Manfred Erjak, Principal Consultant OCTOBER 1 4, 2018 WASHINGTON, D.C.
 Premediation The Art of Proactive Remediation Matthew McWhirt, Senior Manager Manfred Erjak, Principal Consultant OCTOBER 1 4, 2018 WASHINGTON, D.C. Overview Case Study Remediation Overview Premediation
Premediation The Art of Proactive Remediation Matthew McWhirt, Senior Manager Manfred Erjak, Principal Consultant OCTOBER 1 4, 2018 WASHINGTON, D.C. Overview Case Study Remediation Overview Premediation
BUILDING A PRIVATE CLOUD. By Mark Black Jay Muelhoefer Parviz Peiravi Marco Righini
 BUILDING A PRIVATE CLOUD By Mark Black Jay Muelhoefer Parviz Peiravi Marco Righini HOW PLATFORM COMPUTING'S PLATFORM ISF AND INTEL'S TRUSTED EXECUTION TECHNOLOGY CAN HELP 24 loud computing is a paradigm
BUILDING A PRIVATE CLOUD By Mark Black Jay Muelhoefer Parviz Peiravi Marco Righini HOW PLATFORM COMPUTING'S PLATFORM ISF AND INTEL'S TRUSTED EXECUTION TECHNOLOGY CAN HELP 24 loud computing is a paradigm
Microsoft EXAM Securing Windows Server 2016 (beta) m/ Product: Demo. For More Information:
 Page No 1 https://www.dumpsplanet.com m/ Microsoft 70-744 EXAM Securing Windows Server 2016 (beta) Product: Demo For More Information: 70-744-dumps Page No 2 Question: 1 HOTSPOT You have 100 computers
Page No 1 https://www.dumpsplanet.com m/ Microsoft 70-744 EXAM Securing Windows Server 2016 (beta) Product: Demo For More Information: 70-744-dumps Page No 2 Question: 1 HOTSPOT You have 100 computers
Pasiruoškite ateičiai: modernus duomenų centras. Laurynas Dovydaitis Microsoft Azure MVP
 Pasiruoškite ateičiai: modernus duomenų centras Laurynas Dovydaitis Microsoft Azure MVP 2016-05-17 Tension drives change The datacenter today Traditional datacenter Tight coupling between infrastructure
Pasiruoškite ateičiai: modernus duomenų centras Laurynas Dovydaitis Microsoft Azure MVP 2016-05-17 Tension drives change The datacenter today Traditional datacenter Tight coupling between infrastructure
Mobile Field Worker Security Advocate Series: Customer Conversation Guide. Research by IDC, 2015
 Mobile Field Worker Security Advocate Series: Customer Conversation Guide Research by IDC, 2015 Agenda 1. Security Requirements for Mobile Field Workers 2. Key Mobile Security Challenges Companies Face
Mobile Field Worker Security Advocate Series: Customer Conversation Guide Research by IDC, 2015 Agenda 1. Security Requirements for Mobile Field Workers 2. Key Mobile Security Challenges Companies Face
GSE/Belux Enterprise Systems Security Meeting
 MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION. 1 In the news Microsoft Exposes Scope of Botnet Threat By Tony Bradley, October 15, 2010 Microsoft's
MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION. 1 In the news Microsoft Exposes Scope of Botnet Threat By Tony Bradley, October 15, 2010 Microsoft's
COMP6511A: Large-Scale Distributed Systems. Windows Azure. Lin Gu. Hong Kong University of Science and Technology Spring, 2014
 COMP6511A: Large-Scale Distributed Systems Windows Azure Lin Gu Hong Kong University of Science and Technology Spring, 2014 Cloud Systems Infrastructure as a (IaaS): basic compute and storage resources
COMP6511A: Large-Scale Distributed Systems Windows Azure Lin Gu Hong Kong University of Science and Technology Spring, 2014 Cloud Systems Infrastructure as a (IaaS): basic compute and storage resources
Citrix XenMobile and Windows 10
 White Paper Citrix XenMobile and Windows 10 Citrix XenMobile and Windows 10 With version 10, Windows has moved the once desktop operating system firmly into the era of the mobility and the cloud. Windows
White Paper Citrix XenMobile and Windows 10 Citrix XenMobile and Windows 10 With version 10, Windows has moved the once desktop operating system firmly into the era of the mobility and the cloud. Windows
Hybrid Identity de paraplu in de cloud
 EXPERTS LIVE SUMMER NIGHT Hybrid Identity de paraplu in de cloud Robbert van der Zwan TSP EM+S Netherlands EXPERTS LIVE SUMMER NIGHT Robbert van der Zwan Robbert works as an Enterprise Mobility and Security
EXPERTS LIVE SUMMER NIGHT Hybrid Identity de paraplu in de cloud Robbert van der Zwan TSP EM+S Netherlands EXPERTS LIVE SUMMER NIGHT Robbert van der Zwan Robbert works as an Enterprise Mobility and Security
Security Challenges: Integrating Apple Computers into Windows Environments
 Integrating Apple Computers into Windows Environments White Paper Parallels Mac Management for Microsoft SCCM 2018 Presented By: Table of Contents Environments... 3 Requirements for Managing Mac Natively
Integrating Apple Computers into Windows Environments White Paper Parallels Mac Management for Microsoft SCCM 2018 Presented By: Table of Contents Environments... 3 Requirements for Managing Mac Natively
Securing Cloud Computing
 Securing Cloud Computing NLIT Summit, May 2018 PRESENTED BY Jeffrey E. Forster jeforst@sandia.gov Lucille Forster lforste@sandia.gov Sandia National Laboratories is a multimission laboratory managed and
Securing Cloud Computing NLIT Summit, May 2018 PRESENTED BY Jeffrey E. Forster jeforst@sandia.gov Lucille Forster lforste@sandia.gov Sandia National Laboratories is a multimission laboratory managed and
What s really new in Windows 10?
 Sami Laiho Senior Technical Fellow, MVP Adminize.com / Win-fu.com sami@adminize.com BLOG.WIN-FU.COM @samilaiho What s really new in Windows 10? Configuration Manager Forgive my English When most get Administrator
Sami Laiho Senior Technical Fellow, MVP Adminize.com / Win-fu.com sami@adminize.com BLOG.WIN-FU.COM @samilaiho What s really new in Windows 10? Configuration Manager Forgive my English When most get Administrator
MCSA Windows Server 2012 Installation and Configuration
 MCSA Windows Server 2012 Installation and Configuration Session 1 Section A: Plan Windows Server Installation Server Installation Scenario Server Editions Server Requirements Plan Roles for Servers Section
MCSA Windows Server 2012 Installation and Configuration Session 1 Section A: Plan Windows Server Installation Server Installation Scenario Server Editions Server Requirements Plan Roles for Servers Section
MCSA Windows Server A Success Guide to Prepare- Microsoft Installing and Configuring Windows Server edusum.com
 70-410 MCSA Windows Server 2012 A Success Guide to Prepare- Microsoft Installing and Configuring Windows Server 2012 edusum.com Table of Contents Introduction to 70-410 Exam on Installing and Configuring
70-410 MCSA Windows Server 2012 A Success Guide to Prepare- Microsoft Installing and Configuring Windows Server 2012 edusum.com Table of Contents Introduction to 70-410 Exam on Installing and Configuring
Mobility Windows 10 Bootcamp
 Mobility Windows 10 Bootcamp Length: 8 days Format: Bootcamp Time: Day About This Course This boot camp is designed to provide students with the knowledge and skills required to install and configure Windows
Mobility Windows 10 Bootcamp Length: 8 days Format: Bootcamp Time: Day About This Course This boot camp is designed to provide students with the knowledge and skills required to install and configure Windows
Bromium: Virtualization-Based Security
 Bromium: Virtualization-Based Security TAG-Cyber Briefing Presented by Simon Crosby CTO, Co-Founder of Bromium Bromium 2016 2 Bromium 2016 3 Real-time Detection & Analysis Malware manifest Bromium 2016
Bromium: Virtualization-Based Security TAG-Cyber Briefing Presented by Simon Crosby CTO, Co-Founder of Bromium Bromium 2016 2 Bromium 2016 3 Real-time Detection & Analysis Malware manifest Bromium 2016
Crash course in Azure Active Directory
 Crash course in Azure Active Directory Crash course in Azure Active Directory Competing today requires a focus on digital transformation and empowering everyone to be creative and work together securely.
Crash course in Azure Active Directory Crash course in Azure Active Directory Competing today requires a focus on digital transformation and empowering everyone to be creative and work together securely.
The security challenge in a mobile world
 The security challenge in a mobile world Contents Executive summary 2 Executive summary 3 Controlling devices and data from the cloud 4 Managing mobile devices - Overview - How it works with MDM - Scenario
The security challenge in a mobile world Contents Executive summary 2 Executive summary 3 Controlling devices and data from the cloud 4 Managing mobile devices - Overview - How it works with MDM - Scenario
