GNU nano File: test.sh modified. #!/bin/sh. echo "Hello, World!" echo Hello, World! echo -n "the time is " date
|
|
|
- Peregrine Wilkerson
- 5 years ago
- Views:
Transcription
1 Chapter Shell Scripts in a Nutshell A shell script is a file of executable commands that has been stored in a text file. When the file is run, each command is executed. Shell scripts have access to all the commands of the shell, including logic. A script can therefore test for the presence of a file or look for particular output and change its behavior accordingly. You can build scripts to automate repetitive parts of your work, which frees your time and ensures consistency each time you use the script. For instance, if you run the same five commands every day, you can turn them into a shell script that reduces your work to one command. A script can be as simple as one command: echo Hello, World! The script, test.sh, consists of just one line that prints the string Hello, World! to the console. Running a script can be done either by passing it as an argument to your shell or by running it directly: sysadmin@localhost:$ sh test.sh Hello, World! sysadmin@localhost:$./test.sh -bash:./test.sh: Permission denied sysadmin@localhost:$ chmod +x./test.sh sysadmin@localhost:$./test.sh Hello, World! In the example above, first, the script is run as an argument to the shell. Next, the script is run directly from the shell. It is rare to have the current directory in the binary search path $PATH so the name is prefixed with./ to indicate it should be run out of the current directory. The error Permission denied means that the script has not been marked as executable. A quick chmod later and the script works. chmod is used to change the permissions of a file, which will be explained in detail in a later chapter. There are various shells with their own language syntax. Therefore, more complicated scripts will indicate a particular shell by specifying the absolute path to the interpreter as the first line, prefixed by #! as shown: #!/bin/sh echo Hello, World! or #!/bin/bash echo Hello, World! The two characters, #! are traditionally called the hash and the bang respectively, which leads to the shortened form of shebang when they re used at the beginning of a script. Incidentally, the shebang (or crunchbang) is used for traditional shell scripts and other text-based languages like Perl, Ruby, and Python. Any text file marked as executable will be run under the interpreter specified in the first line as long as the script is run directly. If the script is invoked directly as an argument to an interpreter, such as sh script or bash script, the given shell will be used no matter what s in the shebang line. It helps to become comfortable using a text editor before writing shell scripts, since you will need to create files in plain text. Traditional office tools like LibreOffice that output file formats containing formatting and other information are not appropriate for this task. 9.3 Editing Shell Scripts UNIX has many text editors, the merits of one over the other are often hotly debated. Two are specifically mentioned in the LPI Essentials syllabus: The GNU nano editor is a very simple editor well suited to editing small text files. The Visual Editor, vi, or its newer version, VI improved (vim), is a remarkably powerful editor but has a steep learning curve. We ll focus on nano. Type nano test.sh and you ll see a screen similar to this: GNU nano File: test.sh modified #!/bin/sh echo "Hello, World!" echo -n "the time is " date ^G Get Help ^O WriteOut ^R Read File ^Y Prev Page ^K Cut Text ^C Cur Po ^X Exit ^J Justify ^W Where Is ^V Next Page ^U UnCut Text^T To Spell The nano editor has few features to get in your way. You simply type with your keyboard, using the arrow keys to move around and the delete/backspace button to delete text. Along the bottom of the screen you can see some commands available to you, which are context sensitive and change depending on what you re doing. If you re directly on the Linux machine itself, as opposed to connecting over the network, you can also use the mouse to move the cursor and highlight text. To get familiar with the editor, start typing out a simple shell script while inside nano: GNU nano File: test.sh modified #!/bin/sh echo "Hello, World!" echo -n "the time is " date ^G Get Help ^O WriteOut ^R Read File ^Y Prev Page ^K Cut Text ^C Cur Po ^X Exit ^J Justify ^W Where Is ^V Next Page ^U UnCut Text^T To Spell Note that the bottom-left option is ^X Exit which means press control and X to exit. Press Ctrl and Xtogether and the bottom will change: Save modified buffer (ANSWERING "No" WILL DESTROY CHANGES)? Y Yes N No ^C Cancel At this point, you can exit the program without saving by pressing the N key, or save first by pressing Y to save. The default is to save the file with the current file name. You can press the Enter key to save and exit. You will be back at the shell prompt after saving. Return to the editor. This time press Ctrl and O together to save your work without exiting the editor. The prompts are largely the same, except that you re back in the editor.
2 This time use the arrow keys to move your cursor to the line that has "The time is. Press Control and K twice to cut the last two lines to the copy buffer. Move your cursor to the remaining line and press Control and U once to paste the copy buffer to the current position. This makes the script echo the current time before greeting you and saved you needing to re-type the lines. Other helpful commands you might need are: Command Ctrl + W Ctrl + W, then Control + R Ctrl + G Ctrl + Y/V Ctrl + C Description search the document search and replace show all the commands possible page up / down show the current position in the file and the file s size Variables Variables are a key part of any programming language. A very simple use of variables is shown here: #!/bin/bash ANIMAL="penguin" echo "My favorite animal is a $ANIMAL" After the shebang line is a directive to assign some text to a variable. The variable name is ANIMAL and the equals sign assigns the string penguin. Think of a variable like a box in which you can store things. After executing this line, the box called ANIMALcontains the word penguin. It is important that there are no spaces between the name of the variable, the equals sign, and the item to be assigned to the variable. If you have a space there, you will get an odd error such as command not found. Capitalizing the name of the variable is not necessary but it is a useful convention to separate variables from commands to be executed. Next, the script echos a string to the console. The string contains the name of the variable preceded by a dollar sign. When the interpreter sees that dollar sign it recognizes that it will be substituting the contents of the variable, which is called interpolation. The output of the script is then My favorite animal is a penguin. So remember this: To assign to a variable, just use the name of the variable. To access the contents of the variable, prefix it with a dollar sign. Here, we show a variable being assigned the contents of another variable! #!/bin/bash ANIMAL=penguin SOMETHING=$ANIMAL echo "My favorite animal is a $SOMETHING" ANIMAL contains the string penguin (as there are no spaces, the alternative syntax without using quotes is shown). SOMETHING is then assigned the contents of ANIMAL(because ANIMAL has the dollar sign in front of it). If you wanted, you could assign an interpolated string to a variable. This is quite common in larger scripts, as you can build up a larger command and execute it! Another way to assign to a variable is to use the output of another command as the contents of the variable by enclosing the command in back ticks: CURRENT_DIRECTORY=`pwd` echo "You are in $CURRENT_DIRECTORY" This pattern is often used to process text. You might take text from one variable or an input file and pass it through another command like sed or awk to extract certain parts and keep the result in a variable. It is possible to get input from the user of your script and assign it to a variable through the read command: #!/bin/bash echo -n "What is your name? " read NAME echo "Hello $NAME!" The read command can accept a string right from the keyboard or as part of command redirection like you learned in the last chapter. There are some special variables in addition to the ones you set. You can pass arguments to your script: #!/bin/bash echo "Hello $1" A dollar sign followed by a number N corresponds to the Nth argument passed to the script. If you call the example above with./test.sh the output will be Hello Linux. The $0 variable contains the name of the script itself. After a program runs, be it a binary or a script, it returns an exit code which is an integer between 0 and 255. You can test this through the $? variable to see if the previous command completed successfully. sysadmin@localhost:$ grep -q root /etc/passwd sysadmin@localhost:$ echo $? 0 sysadmin@localhost:$ grep -q slartibartfast /etc/passwd sysadmin@localhost:$ echo $? 1 The grep command was used to look for a string within a file with the q flag, which means quiet. The grep, while running in quiet mode, returns 0 if the string was found and 1 otherwise. This information can be used in a conditional to perform an action based on the output of another command. Likewise you can set the exit code of your own script with the exit command: #!/bin/bash # Something bad happened! exit 1 The example above shows a comment #. Anything after the hash mark is ignored which can be used to help the programmer leave notes. The exit 1 returns exit code 1 to the caller. This even works in the shell, if you run this script from the command line and then type echo $? you will see it returns 1. By convention, an exit code of 0 means everything is OK. Any exit codes greater than 0 mean some kind of error happened, which is specific to the program. Above you saw that grep uses 1 to mean the string was not found. #!/bin/bash
3 9.4.2 Conditionals Now that you can look at and set variables, it is time to make your script do different functions based on tests, called branching. The if statement is the basic operator to implement branching. A basic if statement looks like this: Command test 1 eq 1 o 2 eq 2 Description -o is OR: either can be the same if somecommand; then # do this if somecommand has an exit code of 0 fi The next example will run somecommand (actually, everything up to the semicolon) and if the exit code is 0 then the contents up until the closing fi will be run. Using what you know about grep, you can now write a script that does different things based on the presence of a string in the password file: #!/bin/bash if grep -q root /etc/passwd; then echo root is in the password file else echo root is missing from the password file fi From previous examples, you might remember that the exit code of grep is 0 if the string is found. The example above uses this in one line to print a message if root is in the password or a different message if it isn t. The difference here is that instead of an fi to close off the if block, there s an else. This lets you do one action if the condition is true, and another if the condition is false. The else block must still be closed with the fi keyword. Other common tasks are to look for the presence of a file or directory and to compare strings and numbers. You might initialize a log file if it doesn t exist, or compare the number of lines in a file to the last time you ran it. The if command is clearly the one to help here, but what command do you use to make the comparison? The test command gives you easy access to comparison and file test operators. For example: Command test f /dev/ttys0 Description 0 if the file exists test 1 eq 1 a 2 eq 2 -a is AND: both must be the same It is important to note that test looks at integer and string comparisons differently. 01and 1 are the same by numeric comparison, but not by string comparison. You must always be careful to remember what kind of input you expect. There are many more tests, such as gt for greater than, ways to test if one file is newer than the other, and many more. Consult the test man page for more. test is fairly verbose for a command that gets used so frequently, so there is an alias for it called [ (left square bracket). If you enclose your conditions in square brackets, it s the same as running test. So, these statements are identical. if test f /tmp/foo; then if [ -f /tmp/foo]; then While the latter form is most often used, it is important to understand that the square bracket is a command on its own that operates similarly to test except that it requires the closing square bracket. The if statement has a final form that lets you do multiple comparisons at one time using elif (short for else if). #!/bin/bash if [ "$1" = "hello" ]; then echo "hello yourself" elif [ "$1" = "goodbye" ]; then echo "nice to have met you" echo "I hope to see you again" else echo "I didn't understand that" fi test! f /dev/ttys0 test d /tmp test x `which ls` test 1 eq 1 test! 1 eq 1 test 1 ne 1 test a = a test a!= a 0 if the file doesn t exist 0 if the directory exists substitute the location of ls then test if the user can execute 0 if numeric comparison succeeds NOT 0 if the comparison fails Easier, test for numeric inequality 0 if the string comparison succeeds 0 if the strings are different The code above compares the first argument passed to the script. If it is hello, the first block is executed. If not, the script checks to see if it is goodbye and echos a different message if so. Otherwise, a third message is sent. Note that the $1 variable is quoted and the string comparison operator is used instead of the numeric version (- eq). The if/elif/else tests can become quite verbose and complicated. The casestatement provides a different way of making multiple tests easier. #!/bin/bash case "$1" in hello hi) echo "hello yourself" ;; goodbye) echo "nice to have met you" echo "I hope to see you again" ;; *) echo "I didn't understand that"
4 esac The case statement starts off with a description of the expression being tested: case EXPRESSION in. The expression here is the quoted $1. Next, each set of tests are executed as a pattern match terminated by a closing parenthesis. The previous example first looks for hello or hi; multiple options are separated by the vertical bar which is an OR operator in many programming languages. Following that are the commands to be executed if the pattern returns true, which are terminated by two semicolons. The pattern repeats. The * pattern is the same as an else because it matches anything. The behavior of the case statement is similar to the if/elif/else statement in that processing stops after the first match. If none of the other options matched the * ensures that the last one will match. With a solid understanding of conditionals you can have your scripts take actions only if necessary Loops Loops allow code to be executed repeatedly. They can be useful in numerous situations, such as when you want to run the same commands over each file in a directory, or repeat some action 100 times. There are two main loops in shell scripts: the for loop and the while loop. for loops are used when you have a finite collection over which you want to iterate, such as a list of files, or a list of server names: #!/bin/bash SERVERS="servera serverb serverc" for S in $SERVERS; do echo "Doing something to $S" done The script first sets a variable containing a space separated list of server names. The for statement then loops over the list of servers, each time it sets the S variable to the current server name. The choice of S was arbitrary, but note that the S has no dollar sign but the $SERVERS does, showing that $SERVERS will be expanded to the list of servers. The list does not have to be a variable. This example shows two more ways to pass a list. #!/bin/bash for NAME in Sean Jon Isaac David; do echo "Hello $NAME" done for S in *; do echo "Doing something to $S" done The first loop is functionally the same as the previous example, except that the list is passed to the for loop directly instead of using a variable. Using a variable helps the clarity of the script as someone can easily make changes to the variable rather than looking at a loop. The second loop uses a * which is a file glob. This gets expanded by the shell to all the files in the current directory. The other type of loop, a while loop, operates on a list of unknown size. Its job is to keep running and on each iteration perform a test to see if it should run another time. You can think of it as while some condition is true, do stuff. #!/bin/bash i=0 while [ $i -lt 10 ]; do echo $i i=$(( $i + 1)) done echo Done counting The example above shows a while loop that counts from 0 to 9. A counter variable, i, is initialized to 0. Then a while loop is run with the test being is $i less than 10? Note that the while loop uses the same notation as an if statement! Within the while loop the current value of i is echoed and then 1 is added to it through the $(( arithmetic )) command and assigned back into i. Once ibecomes 10 the while statement returns false and processing continues after the loop. Lab Basic Text Editing Most distributions of Linux have more than one text editor. These may include simple text-only editors, such as nano, or graphical editors, such as gedit. In this task, you will explore some of the basic text editing features of the vi editor. All distributions have some version of vi. The vi editor is a powerful text editor with a bit of a learning curve, but capable of performing a wide variety of text editing tasks. The vi editor has two modes: insert and command. In insert mode, you add text to a document. In command mode, operations can be performed such as navigation, searching, saving, and exiting the editor. Step 1 To create a new file, execute the following command: vi myfile Type an i to enter the insert mode of vi (more about this later). Then enter the following text: Welcome to the vi editor. It is a very powerful text editor. Then press the Esc key to leave insert mode. Type :wq to write the file to disk and quit. Note: Each of the previous commands will be covered in greater detail later in this lab. The purpose of the previous step was to create a file to work with during this lab. Step 2 Invoke the vi editor to modify the file you created. When vi is invoked,you are placed in command mode by default: vi myfile Your output should be similar to the following: Welcome to the vi editor. It is a very powerful text editor.
5 "myfile" 3 lines, 97 characters Notice in the bottom-left, the file name, the number of lines, and the number of characters in the file are displayed. Step 3 Press each of the following keys two times and observe how the cursor moves. Remember that you are in command mode: Key Function Key w e b Function Moves cursor to beginning of next word Moves cursor to end of word Moves cursor to beginning of previous word Warning: If you type any other keys then those listed above, you may end up in insert mode. Don't panic! Press the Esc key, then :q! + the Enter key. This should exit vi without saving any changes. Then execute vi myfile and you are back in the vi editor! Step 4 More vi cursor navigation: Press the following keys and observe how the cursor moves: Keys Function j k Moves cursor down one line (same as down arrow) Moves cursor up line (same as up arrow) $ Moves cursor to end of current line (same as End key) 0 (zero) Moves cursor beginning of current line (same as Home key) l Moves cursor to the right one character (same as right arrow) 3G Jumps to third line (ng jumps to the nth line) h Moves cursor to the left one character (same as left arrow) 1G Jumps to first line Shift+G Jumps to the last line Step 5 Move the cursor to the beginning of the word "very" by pressing the following keys: G k 8l (that's the number eight followed by the letter "l") The cursor should be on the letter v of the word "very" as shown below: Welcome to the vi editor. It is a very powerful text editor. Step 6 Delete the word very by issuing the command dw (delete word): dw Your screen should look similar to the following: Welcome to the vi editor. It is a powerful text editor. Step 7 Undo the last operation: u Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful text editor.
6 Step 8 Delete two words: 2dw Your screen should look similar to the following: Welcome to the vi editor. It is a text editor. Step 9 Undo the last operation: u Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful text editor. Step 10 Delete four characters, one at a time: xxxx Your screen should look similar to the following: Welcome to the vi editor. It is a powerful text editor. Step 11 Undo the last 4 operations and recover the deleted characters: 4u Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful text editor. Step 12 Delete 14 characters: 14x Your screen should look similar to the following: Welcome to the vi editor. It is a text editor. Step 13 Undo the last operation: u Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful text editor. Step 14 Delete the five characters to the left of the cursor (type 5 then Shift+x): 5X Your screen should look similar to the following: Welcome to the vi editor. It very powerful text editor. Step 15 Undo the last operation: u Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful text editor. Step 16 Delete the current line: dd Your screen should look similar to the following: Welcome to the vi editor. Step 17 Whatever was lasted deleted or yanked can be pasted. Paste the deleted lines below the current line: p Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful text editor. Step 18 Undo the last two operations: 2u Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful text editor. Step 19 Delete two lines, the current and the next: 2dd Your screen should look similar to the following: Welcome to the vi editor.
7 Step 20 Undo the last operation: u Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful text editor. Step 21 Move to the fourth word then delete from the current position to end of line Shift+D: 4w D Your screen should look similar to the following: Welcome to the vi editor. It is a very The command d$ also deletes to end of line. The $ character, as seen earlier, advances to end of line. Thus, d$ deletes to end of line. Step 22 Undo the last operation: u Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful text editor. Step 23 Join two lines, the current and the next by typing a capital J (Shift+J): J Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful text editor. Step 24 Undo the last operation: u Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful text editor. Step 25 Copy (or yank ) the current word: yw When you copy text, no change will take place on the screen. Step 26 Paste (or put ) the copied word before the current cursor: P Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful powerful text editor. Step 27 Undo the last operation: u Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful text editor. Step 28 Move to the first line, then join three lines: 1G 3J Welcome to the vi editor. It is a very powerful text editor. Especially fo r those who master it. Step 29 Undo the last operation: u Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful text editor. Step 30 Search for and delete the word text (add a space after the word text): :%s/text //g Your screen should look similar to the following: Welcome to the vi editor. It is a very powerful text editor. :%s/text //g
8 Step 31 Navigate to beginning of file, press i to enter insert mode to add text: Keys 1G i Hello and Function Go to beginning of file (Shift+G) Enter insert mode Hello and Welcome to the vi editor. It is a very powerful text editor. Add text to document with a space after and Step 32 Exit insert mode and return to command mode by pressing the Escape key: ESC Step 33 Move forward one space by pressing the lower case l to place the cursor on the W and toggle it to lower case by pressing the tilde (): Keys l Function Lowercase L moves forward one space Shift+` changes letter to lower case Hello and welcome to the vi editor. It is a very powerful text editor. Step 34 Save the file. Press the Esc key to ensure you are in command mode. Then type :w and the Enter key: :w Step 35 When you press Enter to commit the change: "myfile" 3 lines, 102 characters written Step 36 Navigate to the space between the word "powerful" and "editor" in the second line as shown in the image below. You could press j followed by 10l or use the arrow keys: Command j 10l Function/Keys Move down to second line 10 followed by the lowercase L Your screen should look similar to the following: Hello and welcome to the vi editor. It is a very powerful editor. Step 37 Append text to the right of the cursor by pressing the letter a. This moves the cursor to the right and enters insert mode. Type the word text followed by a space as shown in image below: Command a text Hello and welcome to the vi editor. It is a very powerful text editor. Function/Keys Enter insert mode. text followed by a space Step 38 Exit insert mode by pressing the Esc key. Step 39 Open a blank line below the current line by typing a lowercase letter o: o Your screen should look similar to the following: Hello and welcome to the vi editor. It is a very powerful text editor. _ Step 40 Enter the following text: This line added by pressing lowercase o. Your screen should look similar to the following: Hello and welcome to the vi editor. It is a very powerful text editor. This line was added by pressing lowercase o. Step 41 Exit insert mode by pressing the Esc key. Step 42 Open a blank line above the current line by pressing uppercase O: O Your screen should look similar to the following: Hello and welcome to the vi editor. It is a very powerful text editor. This line was added by pressing lowercase o. Step 43 Enter the following text: You just pressed O to open a line above. Your screen should look similar to the following: Hello and welcome to the vi editor. It is a very powerful text editor. You just pressed O to open a line above. This line was added by pressing lowercase o. Step 44 Exit insert mode by pressing the Esc key.
9 Step 45 Save the file and close the vi editor using any one of the following methods that saves changes: Command Function/Keys :x Will save and close the file. :wq :wq! ZZ :q! :e! :w! Will write to file and quit. Will write to a read-only file, if possible, and quit. Will save and close. Notice that no colon : is used in this case. Exit without saving changes Discard changes and reload file Write to read-only, if possible. Step 46 Once again open myfile using the vi editor: vi myfile Step 47 Navigate to the third line, delete the third and fourth lines: 3G 2dd Hello and welcome to the vi editor. It is a very powerful text editor. Step 48 Press the Esc key to confirm you are in command mode. Step 49 Quit the vi editor without saving your changes: :q! Step 50 Open myfile with the vi editor: vi myfile Notice that lines 3 and 4 are still present. Step 51 Search forward for the word line. You ll notice the cursor moves to the beginning of the first instance of the word line as shown in image below: /line Your screen should look similar to the following: Hello and welcome to the vi editor. It is a very powerful text editor. You just pressed O to open a line above. This line was added by pressing lowercase o. / line Step 52 Search for the next instance of the word line by pressing the letter n: n Your screen should look similar to the following: Hello and welcome to the vi editor. It is a very powerful text editor. You just pressed O to open a line above. This line was added by pressing lowercase o. / line Step 53 Search backward for the word line. You ll notice the cursor moves to the beginning of the previous instance of the word line as shown in image below:?line Your screen should look similar to the following: Hello and welcome to the vi editor. It is a very powerful text editor. You just pressed O to open a line above. This line was added by pressing lowercase o.?line
10 Step 54 Search for the previous instance of the word line by pressing the letter n. Since there are none in this, vi will wrap around document: n Hello and welcome to the vi editor. It is a very powerful text editor. You just pressed O to open a line above. This line was added by pressing lowercase o. search hit TOP, continuing at BOTTOM Step 60 Save your changes and exit vi: :x Step 55 You will replace the word line with the word entry. When you press cw the word line will disappear and you will be in insert mode: cw entry Your screen should look similar to the following: Hello and welcome to the vi editor. It is a very powerful text editor. You just pressed O to open a line above. This entry was added by pressing lowercase o. Step 56 Press Esc key to exit insert mode. Step 57 Add text at the beginning of a line. Enter insert mode again and add a line by pressing upper case i: I Your screen should look similar to the following: Hello and welcome to the vi editor. It is a very powerful text editor. 9.3 Basic Shell Scripting Shell scripting allows you to take a complex sequence of commands, place them into a file and then run the file as a program. This saves you the time of having to repeatedly type a long sequence of commands that you routinely use. This lab will focus on how to create simple shell scripts. For the purpose of this lab, it is assumed that you know how to use a text editor. Feel free to use the editor of your choice: vi, nano, gedit or any other editor that you like. Step 1 To create a simple shell script, you just need to create a text file and add commands. Create a file called sample.sh and add the following lines: echo "Hello there! Here is the calendar for this month:" cal echo "Hello there! Here is the calendar for this month:" cal You just pressed O to open a line above. This entry was added by pressing lowercase o. Insert modes include: i, I, a, A, o, and O. Step 58 Press the Esc key to return to command mode. Step 59 Add text at the end of a line (uppercase A). First move to the second line and add the phrase Indeed!: 2G A [Space]Indeed! Press the Esc key to return to command mode. Your screen should look similar to the following: Hello and welcome to the vi editor. It is a very powerful text editor. Indeed! You just pressed O to open a line above. This entry was added by pressing lowercase o. Step 2 To make it clear that this is a BASH shell script, you need to include a special line at the top of the file called a "shbang" (or "shebang"). This line starts with #! and then contains the path to the BASH shell executable. Add the following line at the top of the sample.sh file: #!/bin/bash #!/bin/bash echo "Hello there! Here is the calendar for this month:" cal Step 3 One way that you can run this program is by typing bash before the filename. Execute the following: bash sample.sh sysadmin@localhost:$ bash sample.sh Hello there! Here is the calendar for this month: April 2016 Su Mo Tu We Th Fr Sa
11 Step 4 You can avoid having to type bash in front of the filename by making the file "executable" for all users. Run the following commands: ls -l sample.sh chmod a+x sample.sh ls -l sample.sh./sample.sh sysadmin@localhost:$ ls -l sample.sh -rw-rw-r-- 1 sysadmin sysadmin 73 Apr 9 22:44 sample.sh sysadmin@localhost:$ chmod a+x sample.sh sysadmin@localhost:$./sample.sh Hello there! Here is the calendar for this month: April 2016 Su Mo Tu We Th Fr Sa Step 5 A common feature used in scripting is "backquoting". With this technique, you can run a shell command "within" another shell command. The outcome of the internal command will be returned as an argument to the external command. Add the following to the bottom of the sample.sh file: echo "Today is" `date +%A` Now execute it: cat sample.sh./sample.sh sysadmin@localhost:$ cat sample.sh #!/bin/bash echo "Hello there! Here is the calendar for this month:" cal echo "Today is" `date +%A` sysadmin@localhost:$./sample.sh Hello there! Here is the calendar for this month: April 2016 Su Mo Tu We Th Fr Sa Today is Friday Step 6 You have been using./ in front of the sample.sh filename to indicate that the file is in the current directory. Execute the following to see how the shell would fail to find the file if you don't use the./: sample.sh Your screen should look like the following: sysadmin@localhost:$ sample.sh -bash: sample.sh: command not found Step 7 Recall that the $PATH variable is used to search for commands that you type. Execute the following to see the $PATH variable for the sysadmin account: echo $PATH sysadmin@localhost:$ echo $PATH /home/sysadmin/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games Step 8 Note that /home/sysadmin/bin is one of the directories in the $PATH variable. This is a great place to put your shell scripts: mkdir bin mv sample.sh bin sample.sh sysadmin@localhost:$ mkdir bin sysadmin@localhost:$ mv sample.sh bin sysadmin@localhost:$ sample.sh Hello there! Here is the calendar for this month: April 2016 Su Mo Tu We Th Fr Sa Today is Friday 9.4 Conditional and Repetitive Execution Note that during this section examples that are more complex will be demonstrated. When doing so, you will be using a technique to describe what is happening in the program. The technique will look like the following: Enter this column into drive.sh echo "Please enter your age" read age This column describes the code (don't enter into the file) # print a prompt # read user input and place in $age variable When following the instructions provided, you are to enter the text from the left column into the specified file (drive.sh in the example above). The right column is used to describe specific lines in the program. The pound sign # character is used because in a shell script, you can place comments within your program by using a # character.
12 Step 1 Scripts that are more complex may make use of conditional execution. A conditional expression, like the if statement, can make use of the outcome of a command called test. The teststatement compares two numbers (or two strings) for things like "equal to", "less than", etc. Create the following file (drive.sh) and make it executable to see how the if and teststatements work. Begin by placing the following in drive.sh: Enter this column into drive.sh This column describes the code (don't enter into the file) Verbally, you could read the if statement as "If $age is less than 16, then echo 'You are not old enough to drive', else echo 'You can drive!'". The fi ends the if statement. Note: $age must be an integer value. If not, the program will crash. Step 2 The test statement is automatically called when you place its arguments within square brackets [ ] surrounded by spaces. Modify the if line of drive.sh so it looks like the following: if [ $age -lt 16 ] #!/bin/bash echo "Please enter your age" # print a prompt Then run the program again: cat drive.sh./drive.sh read age if test $age -lt 16 then echo "You are not old enough to drive." else fi echo "You can drive!" Then make the file executable and run it: cat drive.sh chmod a+x drive.sh./drive.sh sysadmin@localhost:$ cat drive.sh #!/bin/bash echo "Please enter your age" read age if test $age -lt 16 then echo "You are not old enough to drive." else echo "You can drive!" fi sysadmin@localhost:$ chmod a+x drive.sh sysadmin@localhost:$./drive.sh Please enter your age 14 You are not old enough to drive. # read user input and place in the $age variable # test $age -lt 16 returns "true" if $age is numerically less then 16 # executes when test is true # executes when test is false # This ends the if statement Your screen should look like the following: sysadmin@localhost:$ cat drive.sh #!/bin/bash echo "Please enter your age" read age if [ $age -lt 16 ] then echo "You are not old enough to drive." else echo "You can drive!" fi sysadmin@localhost:$./drive.sh Please enter your age 21 You can drive! To see a full list of test conditions, run the command man test. Important: There must be spaces around the square brackets. [$age -lt 16] would fail, but [ $age -lt 16 ] would work. Step 3 You can also use the outcome of other shell commands as they all return "success" or "failure". For example, create and run the following program, which can be used to determine if a user account is on this system. Add the following to check.sh: #!/bin/bash echo "Enter a username to check: " read name if grep $name /etc/passwd > /dev/null then echo "$name is on this system" else echo "$name does not exist" fi Then run the following commands: chmod a+x check.sh./check.sh
13 When prompted for a username, give the value of "root". Execute the command again (./check.sh) and provide the value of "bobby". Your screen should look like the following: sysadmin@localhost:$ cat check.sh #!/bin/bash echo "Enter a username to check: " read name if grep $name /etc/passwd > /dev/null then echo "$name is on this system" else echo "$name does not exist" fi sysadmin@localhost:$ chmod a+x check.sh sysadmin@localhost:$./check.sh Enter a username to check: root root is on this system sysadmin@localhost:$./check.sh Enter a username to check: bobby bobby does not exist Step 4 Another common conditional statement is called the while loop. This statement is used to execute code repeatedly as long as a conditional check returns "true". Begin by placing the following in a file named num.sh: Enter this column into num.sh #!/bin/bash echo "Please enter a number greater than 100" read num while [ $num -le 100 ] do echo "$num is NOT greater than 100." echo "Please enter a number greater than 100" read num done echo "Finally, $num is greater than 100" This column describes the code (don't enter into the file) # Execute code from "do" to "done if test condition is true # This ends the done statement Then make the file executable and run it: chmod a+x num.sh./num.sh When prompted for a number, enter 25. When prompted again, enter 99. Finally, enter 101when prompted for a number the third time. Your screen should look like the following: sysadmin@localhost:$ cat num.sh #!/bin/bash echo "Please enter a number greater than 100" read num while [ $num -le 100 ] do echo "$num is NOT greater than 100." echo "Please enter a number greater than 100." read num done echo "Finally, $num is greater than 100" sysadmin@localhost:$ chmod a+x num.sh sysadmin@localhost:$./num.sh Please enter a number greater than is NOT greater than 100. Please enter a number greater than is NOT greater than 100. Please enter a number greater than Finally, 101 is greater than 100 If the conditional check for the while statement ( [ $num -le 100 ] ) returns true, then the statements between do and done are executed.once those statements have completed executing, the conditional check for the while statement is checked again. If true again, then again the statements between do and done are executed.this will continue repeating until the while condition returns false, or when value is greater than 100. Step 5 Scripting code is part of the BASH shell, which means you can use these statements on the command line just like you use them in a shell script. This can be useful for a statement like the for statement, a statement that will assign a list of values one at a time to a variable. This allows you to perform a set of operations on each value. For example, run the following on the command line: for name in /etc/passwd /etc/hosts /etc/group do wc $name done sysadmin@localhost:$ for name in /etc/passwd /etc/hosts /etc/group > do > wc $name > done /etc/passwd /etc/hosts /etc/group
14 Note that the wc command was run three times: once for /etc/passwd, once for /etc/hostsand once for /etc/group. Step 6 Often the seq command is used in conjunction with the for statement. The seq command can generate a list of integer values, for instance from 1 to 10. For example, run the following on the command line to create 12 files named test1, test2, test3, etc. (up to test12): ls for num in `seq 1 12` do touch test$num done ls sysadmin@localhost:$ ls Desktop Downloads Pictures Templates check.sh num.sh Documents Music Public Videos drive.sh sysadmin@localhost:$ for num in `seq 1 12` > do > touch test$num > done sysadmin@localhost:$ ls Desktop Music Templates drive.sh test10 test2 test5 test8 Documents Pictures Videos num.sh test11 test3 test6 test9 Downloads Public check.sh test1 test12 test4 test7 Chapter Introduction One of the many advantages of having so many different Linux distributions is that some of them are designed to run on specific hardware platforms. In fact, there is a Linux distribution specifically designed for just about all modern hardware platforms. Each of these hardware platforms has a great deal of variety in the hardware components that are available. In addition to several different types of hard drives, there are many different monitors and printers. With the popularity of USB devices, such as USB storage devices, cameras and cell phones, the number of available devices numbers in the thousands. In some cases, this poses problems as these hardware devices typically need some sort of software (called drivers or modules) that allows them to communicate with the installed operating system. Hardware manufactures often provide this software, but typically for Microsoft Windows, not Linux. The Linux mascot, Tux, is however starting to appear more often on hardware products, indicating Linux support. In addition to vendor support, there is a great deal of community support that strives to provide drivers for Linux systems. Although not all hardware has the necessary drivers, there is a good amount that does, making the challenge for Linux users and administrators to either find the correct drivers or choose hardware that has some level of support in Linux. In this chapter, you will learn about core hardware devices, including how to use Linux commands to display vital hardware device information Processors A Central Processing Unit (CPU or processor) is one of the most important hardware components of a computer. It performs the decision making as well as the calculations that need to be performed to properly run an operating system. The processor is essentially a computer chip. The processor is connected to the other hardware via a motherboard, also known as the system board. Motherboards are designed to work with specific types of processors. If a hardware system has more than one processor, the system is referred to as a multiprocessor. If more than one processor is combined into a single processor chip, then it is called multi-core. Although support is available for more types of processors in Linux than any other operating system, there are primarily just two types of processors used on desktop and server computers: x86 and x86_64. On an x86 system, the system processes data 32 bits at a time; on a x86_64 the system processes data 64 bits at a time. A x86_64 system is also capable of also processing data 32 bits at a time in a backward compatible mode. One of the main advantages to a 64 bit system is that the system is able to work with more memory. The x86 family of processors was originated by Intel in 1978 with the release of the 8086 processor. Since that time, Intel has produced many other processors that are improvements to the original 8086; they are known generically as x86 processors. These processors include the (also known as the i386), (i486), the Pentium series (i586) and the Pentium Pro series ( i686). In addition to Intel, other companies like AMD and Cyrix have also produced x86 compatible processors. While Linux is capable of supporting processors back to the i386 generation, many distributions limit their support to i686 or later. The x86_64 family of processors, including the 64 bit processors from Intel and AMD, have been in production since around the year As a result, most of the modern processors built today are x86_64. While the hardware has been available for over a decade now, the software to support this family of processors has been much slower to develop. Even as of 2013, there are many software packages that are available for the x86 architecture, but not the x86_64. You can see the family your CPU belongs to, using the arch command: sysadmin@localhost:$ arch x86_64
15 Another command you can use to identify the type of CPU in your system is the lscpu command: lscpu Architecture: x86_64 CPU op-mode(s): 32-bit, 64-bit Byte Order: Little Endian CPU(s): 4 On-line CPU(s) list: 0-3 Thread(s) per core: 1 Core(s) per socket: 4 Socket(s): 1 NUMA node(s): 1 Vendor ID: GenuineIntel CPU family: 6 Model: 44 Stepping: 2 CPU MHz: BogoMIPS: Virtualization: VT-x Hypervisor vendor: VMware Virtualization type: full L1d cache: 32K L1i cache: 32K L2 cache: 256K L3 cache: 12288K NUMA node0 CPU(s): 0-3 The first line of this output shows that the CPU is being used in a 32 bit mode, as the architecture reported is i686. The second line of output shows that the CPU is capable of operating in either a 32 or 64 bit mode, therefore it is actually a 64 bit CPU. The most detailed way of displaying information about your CPU(s) is viewing the /proc/cpuinfo file with the cat command: sysadmin@localhost:$ cat /proc/cpuinfo processor : 0 vendor_id : GenuineIntel cpu family : 6 model : 44 model name : Intel(R) Xeon(R) CPU 2.40GHz stepping : 2 microcode : 0x15 cpu MHz : cache size : KB physical id : 0 siblings : 4 core id : 0 cpu cores : 4 apicid : 0 initial apicid : 0 fpu : yes fpu_exception : yes cpuid level : 11 wp : yes flags : fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush dts mmx fxsr sse sse2 ss ht syscall nx rdtscp lm constant_ts arch_perfmon pebs bts nopl xtopology tsc_reliable nonstop_tsc aperfmperf pni pcl mulqdq vmx ssse3 cx16 sse4 _1 sse4_2 x2apic popcnt aes hypervisor lahf_lm ida arat dtherm tpr_shadow vnmi ept vpid While much of the output of the lscpu and the contents of the /proc/cpuinfo file appears to be the same, one benefit to viewing the /proc/cpuinfo file is that the flags of the CPU are displayed. The flags of a CPU are a very important component, since they indicate which features the CPU supports and the capabilities of the CPU. For example, the output from the previous example contains the flag lm (long mode), indicating that this CPU is 64-bit capable. There are also flags that indicated if the CPU is capable of supporting virtual machines (the ability to have multiple operating systems on a single computer) Motherboards and Buses The motherboard, or system board, is the main hardware board in the computer through which the CPU, Random Access Memory (RAM) and other components are all connected together. Some devices are attached directly to the motherboard, while other devices are connected via a bus to the motherboard dmidecode The system board of many computers contains what is known as Basic Input and Output System (BIOS).System Management BIOS (SMBIOS) is the standard that defines the data structures and how to communicate information about computer hardware. The dmidecode command is able to read and display the information from SMBIOS. For devices directly attached to the motherboard, an administrator can use the dmidecode command to view them. There is a great deal of information provided by the output of this command. The examples below provide you with a few ideas of what you can learn from the output of the dmidecode command. This command is not available within the virtual machine environment of this course. In the first example, you can see that the BIOS supports booting directly from the CD-ROM. This is important since operating system installs are often done by booting directly from the install CD: # dmidecode 2.11 SMBIOS 2.4 present. 364 structures occupying bytes. Table at 0x000E0010 Handle 0x0000, DMI type 0, 24 bytes BIOS Information Vendor: Phoenix Technologies LTD Version: 6.00 Release Date: 06/22/2012 Address: 0xEA0C0 Runtime Size: bytes ROM Size: 64 kb Characteristics: ISA is supported PCI is supported PC Card (PCMCIA) is supported PNP is supported APM is supported BIOS is upgradeable BIOS shadowing is allowed ESCD support is available Boot from CD is supported --More-- In the next example, you can see that a total of 2048 (about 2GB) of RAM is installed on the system:
16 Socket Designation: RAM socket #0 Bank Connections: None Current Speed: Unknown Type: EDO DIMM Installed Size: 2048 MB (Single-bank Connection) Enabled Size: 2048 MB (Single-bank Connection) Error Status: OK Random Access Memory The motherboard normally has slots where Random Access Memory (RAM) can be connected to the system. 32 bit architecture systems can use up to 4 gigabytes (GB) of RAM, while 64 bit architectures are capable of addressing and using far more RAM. In some cases, the RAM your system has might not be enough to handle all of the operating system requirements. Each program needs to store data in RAM and the programs themselves are loaded into RAM when they execute.to avoid having the system fail due to a lack of RAM, virtual RAM (or swap space) is utilized. Virtual RAM is hard drive space that is used to temporarily store RAM data when the system is running out of RAM. Data that is stored in RAM and that has not been used recently is copied on to the hard drive so currently active programs can use the RAM. If needed, this swapped data can be stored back into RAM at a later time. To view the amount of RAM in your system, including the virtual RAM, execute the free command. The free command has a -m option to force the output to be rounded to the nearest megabyte and a -g option to force the output to be rounded to the nearest gigabyte: sysadmin@localhost:$ free -m total used free shared buffers cached Mem: /+ buffers/cache: Swap: The output of executing this free command shows that the system it was executed on a system has a total of 1,894 megabytes and is currently using 356 megabytes.the amount of swap appears to be approximately 4 gigabytes, although none of it appears to be in use. This makes sense because so much of the physical RAM is free, so there is no need at this time for virtual RAM to be used Peripheral Devices The motherboard has buses that allow for multiple devices to connect to the system, including the Peripheral Component Interconnect (PCI) and Universal Serial Bus (USB). The motherboard also has connectors for monitors, keyboards and mice.in order to view all of the devices connected by the PCI bus, execute the lspci command. The following is a sample output of this command. As you can see below in the highlighted sections, this system has a VGA controller (a monitor connector), a SCSI storage controller (a type of hard drive) and an Ethernet controller (a network connector): The graphics below provide examples of using the lspci command. This command is not available within the virtual machine environment of this course. sysadmin@localhost:$ lspci 00:00.0 Host bridge: Intel Corporation 440BX/ZX/DX BX/ZX/DX Host bridge (rev 01) 00:01.0 PCI bridge: Intel Corporation 440BX/ZX/DX BX/ZX/DX AGP bridge (rev 01) 00:07.0 ISA bridge: Intel Corporation 82371AB/EB/MB PIIX4 ISA (rev 08) 00:07.1 IDE interface: Intel Corporation 82371AB/EB/MB PIIX4 IDE (rev 01) 00:07.3 Bridge: Intel Corporation 82371AB/EB/MB PIIX4 ACPI (rev 08) 00:07.7 System peripheral: VMware Virtual Machine Communication Interface (rev 10) 00:0f.0 VGA compatible controller: VMware SVGA II Adapter 03:00.0 Serial Attached SCSI controller: VMware PVSCSI SCSI Controller (rev 02 0b:00.0 Ethernet controller: VMware VMXNET3 Ethernet Controller (rev 01) Executing the lspci command with the -nn option shows both a numeric identifier for each device, as well as the original text description: sysadmin@localhost:$ lspci -nn 00:00.0 Host bridge [0600]: Intel Corporation 440BX/ZX/DX BX/ZX/DX Host bridge [8086:7190] (rev 01) 00:01.0 PCI bridge [0604]: Intel Corporation 440BX/ZX/DX BX/ZX/DX AGP bridge [8086:7191] (rev 01) 00:07.0 ISA bridge [0601]: Intel Corporation 82371AB/EB/MB PIIX4 ISA [8086:7110](rev 08) 00:07.1 IDE interface [0101]: Intel Corporation 82371AB/EB/MB PIIX4 IDE [8086:7111] (rev 01) 00:07.3 Bridge [0680]: Intel Corporation 82371AB/EB/MB PIIX4 ACPI [8086:7113](rev 08) 00:07.7 System peripheral [0880]: VMware Virtual Machine Communication Interface [15ad:0740] (rev 10) 00:0f.0 VGA compatible controller [0300]: VMware SVGA II Adapter [15ad:0405] 03:00.0 Serial Attached SCSI controller [0107]: VMware PVSCSI SCSI Controller [15ad:07c0] (rev 02) 0b:00.0 Ethernet controller [0200]: VMware VMXNET3 Ethernet Controller [15ad:07b0] (rev 01) The highlighted section, [15ad:07b0], is referred to as the [vendor:device] section. Using the [vendor:device] information can be useful for displaying detailed information about a specific device. By using the -d vendor:device option, you can select to view information about just one device. You can also view more detailed information by using either the -v, -vv or -vvv option. The more v characters, the more verbose the output will be. For example: sysadmin@localhost:$ lspci -d 15ad:07b0 -vvv 0b:00.0 Ethernet controller: VMware VMXNET3 Ethernet Controller (rev 01) Subsystem: VMware VMXNET3 Ethernet Controller Physical Slot: 192 Control: I/O+ Mem+ BusMaster+ SpecCycle- MemWINV- VGASnoop- ParErr- Step ping- SERR- FastB2B- DisINTx+ Status: Cap+ 66MHz- UDF- FastB2B- ParErr- DEVSEL=fast >TAbort- <TAbort- <MAbort- >SERR- <PERR- INTx- Latency: 0, Cache Line Size: 32 bytes Interrupt: pin A routed to IRQ 19 Region 0: Memory at fd4fb000 (32-bit, non-prefetchable) [size=4k] Region 1: Memory at fd4fc000 (32-bit, non-prefetchable) [size=4k] Region 2: Memory at fd4fe000 (32-bit, non-prefetchable) [size=8k] Region 3: I/O ports at 5000 [size=16] [virtual] Expansion ROM at fd [disabled] [size=64k] Capabilities: <access denied> Kernel driver in use: vmxnet3 Kernel modules: vmxnet3 The lspci command shows detailed information about devices connected to the system via the PCI bus. This information can be helpful to determine if the device is supported by the system, as indicated by a Kernel driver or Kernel module in use, as shown in the last couple of lines of output above Universal Serial Bus Devices While the PCI bus is used for many internal devices such as sound and network cards, many external devices (or peripherals) are connected to the computer via USB. Devices connected internally are usually cold-plug, meaning the system must be shut down in order to connect or disconnect a device. USB devices are hot-plug, meaning they can be connected or disconnected while the system is running. Note: The graphics below provide examples of using the lsusb command. This command is not available within the virtual machine environment of this course. To display the devices connected to the system via USB, execute the lsusb command:
17 lsusb Bus 001 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub The verbose option, -v, for the lsusb command shows a great amount of detail about each device: sysadmin@localhost:$ lsusb -v Bus 001 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub Couldn t open device, some information will be missing Device Descriptor: blength 18 bdescriptortype 1 bcdusb 1.10 bdeviceclass 9 Hub bdevicesubclass 0 Unused bdeviceprotocol 0 Full speed (or root) hub bmaxpacketsize0 64 idvendor 0x1d6b Linux Foundation idproduct 0x Linux Foundation bcdevice 2.06 imanufacturer 3 iproduct 2 iserial Hardware Abstraction Layer HAL is the Hardware Abstraction Layer. The daemon for HAL is hald, a process that gathers information about all devices connected to the system. When events occur that change the state of the connected devices, such as when a USB device is attached to the system, then haldbroadcasts this new information to any processes that have registered to be notified about new events. Note: The graphic below provides an example of using the lshal command. This command is not available within the virtual machine environment of this course. The lshal command allows you to view the devices detected by HAL. This command produces a huge amount of output; the following provides a small sample: 10.5 Disk Devices Disk devices (AKA, hard drives) may be attached to the system in a number of ways; the controller may be integrated into the motherboard, on a PCI (Peripheral Component Interconnect) card or a USB device. Hard drives are divided into partitions. A partition is a logical division of a hard drive, designed to take a large amount of available storage space and break it up into smaller "chunks". While it is common on Microsoft Windows to have a single partition for each hard drive, on Linux distributions, multiple partitions per hard drive is common. Some hard drives make use of a partitioning technology called Master Boot Record (MBR) while others make use of a partitioning type called GUID Partitioning Table (GPT). The MBR type of partitioning has been used since the early days of the Personal Computer (PC) and the GPT type has been available since the year An old term used to describe an internal hard disk is "fixed disk", as the disk is fixed (not removable). This term gave rise to several command names: the fdisk, cfdisk and sfdiskcommands, which are tools for working with the MBR partitioned disks. The GPT disks use a newer type of partitioning, which allows the user to divide the disk into more partitions than what MBR supports. GPT also allows having partitions which can be larger than two terabytes (MBR does not). The tools for managing GPT disks are named similar to the fdisk counterparts: gdisk, cgdisk, and sgdisk. There is also a family of tools that attempts to support both MBR and GPT type disks. This set of tools includes the parted command and the graphical gparted tool. Hard drives are associated with file names (called device files) that are stored in the /devdirectory. Different types of hard drives are given slightly different names: hd for IDE (Intelligent Drive Electronics) hard drives and sd for USB, SATA (Serial Advanced Technology Attachment) and SCSI (Small Computer System Interface) hard drives. Each hard drive is assigned a letter, for example, the first IDE hard drive would have a device file name of /dev/hda and the second IDE hard drive would have be associated with the /dev/hdb device file. Partitions are given unique numbers for each device. For example, if a USB hard drive had two partitions, they could be associated with the /dev/sda1 and /dev/sda2 device files. In the following output, you can see that this system has three sd devices: /dev/sda, /dev/sdb and /dev/sdc. Also, you can see there are two partitions on the first device (as evidenced by the /dev/sda1 and /dev/sda2 files) and one partition on the second device (as evidenced by the /dev/sdb1 file): root@localhost:$ ls /dev/sd* /dev/sda /dev/sda1 /dev/sda2 /dev/sdb /dev/sdb1 /dev/sdc root@localhost:$ In the following example, the fdisk command is used to display partition information on the first sd device. Note: The following command requires root access root@localhost:# fdisk -l /dev/sda Disk /dev/sda: 21.5 GB, bytes 255 heads, 63 sectors/track, 2610 cylinders, total sectors Units = sectors of 1 * 512 = 512 bytes Sector size (logical/physical): 512 bytes / 512 bytes I/O size (minimum/optimal): 512 bytes / 512 bytes Disk identifier: 0x000571a2 Device Boot Start End Blocks Id System /dev/sda1 * Linux /dev/sda Extended /dev/sda Linux swap / Solaris root@localhost:# Creating and modifying partitions is beyond the scope of this course Optical Disks Optical disks, often referred to as CD-ROMs, DVDs, or Blue-Ray are removable storage media. While some devices used with optical disks are read-only, others are capable of burning (writing to) disks, when using a writable type of disk. There are various standards for writable and rewritable disks, such as CD-R, CD+R, DVD+RW, and DVD-RW. These media standards go beyond the scope of the curriculum.
18 Where these removable disks are mounted in the file system is an important consideration for a Linux administrator. Modern distributions often mount the disks under the /media folder, while older distributions typically mount them under the /mnt folder. Upon mounting, most GUI interfaces will prompt the user to take an action, such as open the contents of the disk in a file browser or start a media program. When the user is finished using the disk, it is prudent to unmount it using a menu or the eject command. While pressing the ejectbutton will open the disk tray, some programs will not realize that the disk is no longer mounted on the filesystem Video Display Devices In order to display video (output to the monitor), the computer system must have a video display device (AKA, video card) and a monitor. Video display devices are often directly attached to the motherboard, although they can also be connected through the PCI bus slots on the motherboard. Unfortunately, since the early days of the PC, no video standard has been approved by the major vendors, so each video display device usually requires a proprietary driver provided by the vendor. Drivers are software programs that allow the operating system to communicate with the device. Drivers must be written for the specific operating system, something that is commonly done for Microsoft Windows, but not always for Linux. Fortunately, the three largest video display vendors all now provide at least some level of Linux support. There are two types of video cables commonly used: the analog 15 pin Video Graphics Array (VGA) cable and the 29 pin Digital Visual Interface (DVI). In order for monitors to work properly with video display devices, they must be able to support the same resolution as the video display device. Normally, the software driving the video display device (commonly the X.org server) will normally be able to automatically detect the maximum resolution that the video display and monitor can both support and set the screen resolution to that value. Graphical tools are normally provided to change your resolution, as well as the maximum number of colors that can be displayed (known as the color depth) with your Linux distribution. For distributions using the X.org server, the /etc/x11/xorg.conf file can be used to change resolution, color depth and other settings Managing Devices In order for a device to be used in Linux, there may be several different kinds of software required. First of all there is the driver software. The driver could be compiled as part of the Linux kernel, loaded into the kernel as a module or loaded by a user command or application. Most devices have the driver either built-in to the kernel or have it loaded into the kernel, as the driver may require the low-level kind of access that the kernel has with devices. External devices, like scanners and printers, typically have their drivers loaded by an application and these drivers in turn communicate through the device via the kernel through an interface such as USB. In order to be successful in enabling devices in Linux, it is best to check the Linux distribution to see if the device is certified to work with that distribution. Commercial distributions like Red Hat and SUSE have web pages dedicated to listing hardware that is certified or approved to work with their software. Additional tips on being successful with connecting your devices: avoid brand new or highly specialized devices and check with the vendor of the device to see if they support Linux before making a purchase Power Supplies Power supplies are the devices that convert alternating current (120v, 240v) into direct current, which the computer uses at various voltages (3.3v, 5v, 12v, etc.). Power supplies are generally not programmable, however their proper function has a major impact on the rest of the system. Although they are not surge suppressors, these devices often protect the computer from fluctuations in voltage coming from the power source. It is wise for a network administrator to choose a power supply based on quality rather than price, since a failing power supply can result in major destruction to a computer system. Lab Step 1 In order to determine the type of CPU execute the lscpu command: lscpu Your output will be similar to the following: Being able to display CPU information can be important when trying to determine if more advanced Linux features can be used on your system. For even more details about your CPU(s), you can examine the /proc/cpuinfo file, especially "flags" that are listed that determine whether or not CPU has certain features Step 2 View the /proc/cpuinfo file: cat /proc/cpuinfo
19 Step 3 To discover how much RAM and swap space is being used, use the free command: free -m free -g The output shows the amount of memory in megabytes when the -m option is used and in gigabytes when the - g option is used: In the output above, you can see that the system has megabytes (roughly 15 gigabytes) of physical memory (RAM). Of that only 1066 megabytes are being used, a good sign that you have enough memory for your system's needs. In the event that you run out of memory, Swap is used. Swap is hard drive space that is used to temporarily store data that is supposed to be stored in RAM Step 4 To see what devices are connected to the PCI bus, use the lspci command: lspci Notice from the partial output below, that many of the devices connected to the system board are displayed: Step 6 Attempt to list the USB connected devices: lsusb The output of this command is unusual since no USB devices are detected: sysadmin@localhost:$ lsusb unable to initialize libusb: -99 Due to this system being virtualized, the USB devices do not appear as they normally would when executing the lsusb command. Normally, if USB devices are present, it would have shown something like this: sysadmin@localhost:$ lsusb Bus 001 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub HAL is the Hardware Abstraction Layer. The daemon for HAL is hald, which gathers information about devices connected to the system. When events occur that somehow change the state of the connected devices, then hald broadcasts this information to any processes that have registered for the events. On systems that use HAL, the lshal command will be able to list the devices of that system Step 7 For hardware to function, the Linux kernel usually loads a driver or module. Use the lsmodcommand to view the currently loaded modules: The output of the lspci command can be very important to identify devices that are not supported by the Linux kernel. Some devices like video cards may only provide basic functionality without installing proprietary driver software Step 5 Use the lspci command with the -k option to show devices along with the kernel driver and modules used: lsmod Partial output of the command is shown below. The first column is the module name, and the second is the amount of memory used by the module. The number in the "Used by" column indicates how many other modules are using the module. The names of the other modules using the module may also be listed in the "Used by" column, but is often incomplete:
20 Chapter Package Management Package management is a system by which software can be installed, updated, queried or removed from a filesystem. In Linux, there are many different software package management systems, but the two most popular are those from Debian and Red Hat Debian Package Management The Debian distribution and its derivatives such as Ubuntu and Mint, use the Debian package management system. At the heart of Debian-derived distributions package management are the software packages that are distributed as files ending in ".deb". The lowest level tool for managing these files is the dpkg command. This command can be tricky for novice Linux users, so the Advanced Package Tool, apt-get, a front-end program to the dpkg tool, makes management of packages even easier. There are other command line tools which serve as front-ends to dpkg, such as aptitude, as well as GUI front-ends like synaptic and software-center (shown below) Step 8 The system board of many computers contains what is known as BIOS, or a Basic Input and Output System. System Management BIOS, or SMBIOS, is a standard defining the data structures and how to communicate information about computer hardware. The dmidecode command is able to read and print the information from the SMBIOS of many systems. We will not demonstrate the command here, since it does not function properly within a virtual environment. The fdisk command can be used in two ways: interactively and non-interactively. When the -l option is used with fdisk, then the command will non-interactively list block devices, which includes disks (hard drives) and logical volumes. Without the -l option the fdisk command enters an interactive mode that is typically used to modify partitions on a disk device Step 9 Execute the fdisk command to list the disk devices non-interactively, in sectors, and without DOS compatibility warnings: fdisk -cul The partial output of this command below shows the first couple of disks, /dev/sda and /dev/sdb, and their partitions. The third disk, /dev/sdc, and the logical volumes that followed it have been omitted: The -u option causes the fdisk command to display units in sectors instead of cylinders. The -c option prevents the fdisk command from printing warnings that affect DOS compatibility Debian - Adding Packages The Debian repositories contain more than 65,000 different packages of software. To get an updated list from these Internet repositories, you can execute the sudo apt-get updatecommand. To search for keywords within these packages, you can use the sudo apt-cache search keyword command. Once you've found the package that you want to install, you can install it with the sudo apt-get install package command. Important: To execute these commands, your system will need access to the Internet. The apt-cache command searches repositories on the Internet for these software programs Debian - Updating Packages If you want to update an individual package, you perform the command to install that package: sudo apt-get install package
21 If an older version of the package is already installed, then it will be upgraded. Otherwise, a new installation would take place.if you want to update all possible packages, then you would execute the sudo apt-get upgrade command.users who log in with a graphical interface may have a message appear in the notification area from the update-manager indicating that updates are available, as shown below: RPM Package Management The Linux Standards Base, which is a Linux Foundation project, is designed to specify (through a consensus) a set of standards that increase the compatibility between conforming Linux systems. According to the Linux Standards Base, the standard package management system is RPM. RPM makes use of an.rpm file for each software package. This system is what Red Hat-derived distributions (like Red Hat, Centos, and Fedora) use to manage software. In addition, several other distributions that are not Red Hat-derived (such as SUSE, OpenSUSE and Mandriva) also use RPM. Note: RPM commands are not available within the virtual machine environment of this course. Like the Debian system, RPM Package Management systems track dependencies between packages. Tracking dependencies ensures that when you install a package, the system will also install any packages needed by that package to function correctly. Dependencies also ensure that software updates and removals are performed properly. The back-end tool most commonly used for RPM Package Management is the rpm command. While the rpm command can install, update, query and remove packages, the command line front end tools such as yum and up2date automate the process of resolving dependency issues. In addition, there are GUI-based front end tools such as yumex and gpk-application (shown below) that also make RPM package management easier Debian - Removing Packages Beware that removing one package of software may result in the removal of other packages. Due to the dependencies between packages, if you remove a package, then all packages that need, or depend on that package will be removed as well.if you want to remove all the files of a software package, except for the configuration files, then you can execute the sudo apt-get remove package command. If you want to remove all the files of a software package, including the configuration files, then you can execute the sudo apt-get --purge remove package command. You may want to keep the configuration files in the event that you plan to reinstall the software package at a later time Debian - Querying Packages There are several different kinds of queries that administrators need to use. To get a list of all the packages that are currently installed on the system, execute the dpkg -l command. To list the files that comprise a particular package, you can execute the dpkg -L packagecommand. To query a package for information, or its state, use the dpkg -s package command. To determine if a particular file was put on the filesystem as the result of installing a package, use the dpkg -S /path/to/file command. If the file was part of a package, then the package name could be provided. example: sysadmin@localhost:$ dpkg -S /usr/bin/who coreutils: /usr/bin/who The previous example shows the file /usr/bin/who is part of the coreutils package. You should note that the many of following commands will require root privileges. The rule of thumb is that if a command affects the state of a package, you will need to have administrative access. In other words, a regular user can perform a query or a search, but to add, update or remove a package requires the command be executed as the root user RPM - Adding Packages To search for a package from the configured repositories, execute the yum search keywordcommand. To install a package, along with its dependencies, execute the yum install package command. RPM commands are not available within the virtual machine environment of this course RPM - Updating Packages If you want to update an individual software package, you can execute the yum update package command. If you want to update all packages, you can execute the yum update command. If updates are available and the user is using the GUI, then the gpk-update-viewer may show a message in the notification area of the screen indicating that updates are available. RPM commands are not available within the virtual machine environment of this course.
22 The implementation of the Linux kernel includes many subsystems that are a part of the kernel itself and others that may be loaded in a modular fashion when needed. Some of the key functions of the Linux kernel include a system call interface, process management, memory management, virtual filesystem, networking, and device drivers. In a nutshell, the kernel accepts commands from the user and manages the processes that carry out those commands by giving them access to devices like memory, disks, network interfaces, keyboards, mice, monitors and more. The kernel provides access to information about running processes through a pseudo filesystemthat is visible under the /proc directory. Hardware devices are made available through special files under the /dev directory, while information about those devices can be found in another pseudo filesystem under the /sys directory. The/proc directory not only contains information about running processes, as its name would suggest (process), but it also contains information about the system hardware and the current kernel configuration. See an example output below: Keep in mind that the information displayed in the examples below will be different from what you may see within the virtual machine environment of this course RPM - Removing Packages As is the case with any package management system that tracks dependencies, if you want to remove one package, then you may end up removing more than one, due to the dependencies. The easiest way to automatically resolve the dependency issues is to use a yum command: yum remove package While you can remove software packages with the rpm command, it won't remove dependency packages automatically. RPM commands are not available within the virtual machine environment of this course RPM - Querying Packages Red Hat package management is similar to Debian package management when it comes to performing queries. It is best to use the back-end tool, rpm, instead of the front-end tool, yum. While front-end tools can perform some of these queries, performance suffers because these commands typically connect to multiple repositories across the network when executing any command. The rpm command performs its queries by connecting to a database that is local to the machine and doesn't connect over the network to any repositories. RPM commands are not available within the virtual machine environment of this course. To get a list of all the packages that are currently installed on the system, execute the rpm -qacommand. To list the files that comprise a particular package, execute the rpm -ql package command. To query a package for information, or its state, execute the rpm -qi package command. To determine if a particular file was put on the filesystem as the result of installing a package, execute the rpm - qf /path/to/file command Linux Kernel When most people refer to Linux, they are really referring to GNU/Linux, which defines the operating system. The Gnu's Not Unix (GNU) part of this combination is provided by a Free Software Foundation project. GNU is what provides the open source equivalents of many common UNIX commands, the bulk of the essential command line commands. The Linux part of this combination is the Linux kernel, which is core of the operating system. The kernel is loaded at boot time and stays loaded to manage every aspect of the running system. The output from executing ls /proc shows more than one hundred numbered directories. There is a numbered directory for each running process on the system, where the name of the directory matches the PID (process ID) for the running process. Because the /sbin/init process is always the first process, it has a PID of 1 and the information about the /sbin/init process can be found in the /proc/1 directory. As you will see later in this chapter, there are several commands that allow you to view information about running processes, so it is rarely necessary for users to have to view the files for each running process directly. You might also see that there are a number of regular files the /proc directory, such as /proc/cmdline, /proc/meminfo and /proc/modules. These files provide information about the running kernel: The /proc/cmdline file can be important because it contains all of the information that was passed to the kernel was first started. The /proc/meminfo file contains information about the use of memory by the kernel. The /proc/modules file holds a list of modules currently loaded into the kernel to add extra functionality.
23 Again, there is rarely a need to view these files directly, as other commands offer more "user friendly" output and an alternative way to view this information. While most of the "files" underneath the /proc directory cannot be modified, even by the root user, the "files" underneath the /proc/sys directory can be changed by the root user. Modifying these files will change the behavior of the Linux kernel. Direct modification of these files cause only temporary changes to the kernel. To make changes permanent, entries can be added to the /etc/sysctl.conf file. For example, the /proc/sys/net/ipv4 directory contains a file named icmp_echo_ignore_all. If that file contains a zero 0, as it normally does, then the system will respond to icmp requests. If that file contains a one 1, then the system will not respond to icmp requests: [user@localhost ]$ su - Password: [root@localhost ]# cat /proc/sys/net/ipv4/icmp_echo_ignore_all 0 [root@localhost ]# ping -c1 localhost PING localhost.localdomain ( ) 56(84) bytes of data. 64 bytes from localhost.localdomain ( ): icmp_seq=1 ttl=64 time=0.026 ms If you were to examine the parent and child processes relationship, using the output of the previous command, you could consider it to be like the following: --- localhost.localdomain ping statistics packets transmitted, 1 received, 0% packet loss, time 0ms rtt min/avg/max/mdev = 0.026/0.026/0.026/0.000 ms [root@localhost ]# echo 1 > /proc/sys/net/ipv4/icmp_echo_ignore_all [root@localhost ]# ping -c1 localhost PING localhost.localdomain ( ) 56(84) bytes of data. --- localhost.localdomain ping statistics packets transmitted, 0 received, 100% packet loss, time 10000ms 11.4 Process Hierarchy When the kernel finishes loading during the boot procedure, it starts the /sbin/init process and assigns it a Process Id (PID) of 1. This process then starts other system processes and each process is assigned a PID in sequential order. As the /sbin/init process starts up other processes, they in turn may start up processes, which may start up other processes, on and on. When one process starts another process, the process that performs the starting is called the parent process and the process that is started is called the child process. When viewing processes, the parent PID will be labeled PPID. When the system has been running for a long time, it will eventually reach the maximum PID value, which can be viewed and configured through the /proc/sys/kernel/pid_max file. Once the largest PID has been used, the system will "roll over" and resume by assigning PID values that are available at the bottom of the range. The graphics below provide an example and explanation of the pstree command. The output will vary from the results you will see if you enter the command in the virtual machine environment of this course. You can "map" processes into a family tree of parent and child couplings. If you want to view this tree, the command pstree will display it: 11.5 ps (Process) Command Another way of viewing processes is with the ps command. By default, the ps command will only show the current processes running in the current shell. Ironically, you will see ps running when you want to see what else is running in the current shell: sysadmin@localhost:$ ps PID TTY TIME CMD 6054? 00:00:00 bash 6070? 00:00:01 xeyes 6090? 00:00:01 firefox 6146? 00:00:00 ps Similar to the pstree command, if you run ps with the option --forest, then it will show lines indicating the parent and child relationship: sysadmin@localhost:$ ps --forest PID TTY TIME CMD 6054? 00:00:00 bash 6090? 00:00:02 \_ firefox 6180? 00:00:00 \_ dash 6181? 00:00:00 \_ xeyes 6188? 00:00:00 \_ ps
24 To be able to view all processes on the system you can execute either the ps aux command or the ps - ef command: sysadmin@localhost:$ ps aux head USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND root ? Ss 08:06 0:00 /sbin?? /ini syslog ? Sl 08:06 0:00 /usr/sbin/rsyslogd -c5 root ? Ss 08:06 0:00 /usr/sbin/cron root ? Ss 08:06 0:00 /usr/sbin/sshd bind ? Ssl 08:06 0:00 /usr/sbin/named -u bind root ? S 08:06 0:00 /bin/login -f sysadmin ? S 08:06 0:00 -bash sysadmin ? R+ 16:26 0:00 ps aux sysadmin ? D+ 16:26 0:00 -bash sysadmin@localhost:$ ps -ef head UID PID PPID C STIME TTY TIME CMD root :06? 00:00:00 /sbin?? /init syslog :06? 00:00:00 /usr/sbin/rsyslogd -c5 root :06? 00:00:00 /usr/sbin/cron root :06? 00:00:00 /usr/sbin/sshd bind :06? 00:00:00 /usr/sbin/named -u bind root :06? 00:00:00 /bin/login -f sysadmin :06? 00:00:00 -bash sysadmin :46? 00:00:00 ps -ef sysadmin :46? 00:00:00 head The output of all processes running on a system can definitely be overwhelming. In the example provided, the output of the ps command was filtered by the head command, so only the first ten processes were shown. If you don't filter the output of the ps command, then you are likely to have to scroll through hundreds of processes to find what might interest you. A common way to run the ps command is to use the grep command to filter the output display lines that match a keyword, such as the process name. For example, if you wanted to view the information about the firefox process, you may execute a command like: sysadmin@localhost:$ ps -e grep firefox 6090 pts/0 00:00:07 firefox By default, the output of the top command is sorted by the % of CPU time that each process is currently using, with the higher values listed first. This means processes that are "CPU hogs" are listed first: top - 16:58:13 up 26 days, 19:15, 1 user, load average: 0.60, 0.74, 0.60 Tasks: 8 total, 1 running, 7 sleeping, 0 stopped, 0 zombie Cpu(s): 6.0%us, 2.5%sy, 0.0%ni, 90.2%id, 0.0%wa, 1.1%hi, 0.2%si, 0.0%st Mem: k total, k used, k free, 4136k buffers Swap: 0k total, 0k used, 0k free, k cached PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND 1 root S :00.02 init 17 syslog m S :00.20 rsyslogd 21 root S :00.02 cron 23 root S :00.00 sshd 39 bind m 19m 6100 S :00.12 named 48 root S :00.00 login 60 sysadmin S :00.01 bash 127 sysadmin R :00.01 top There is an extensive list of commands that can be executed from within the running top program: Keys h or? l t m Meaning Help Toggle load statistics Toggle time statistics Toggle memory usage statistics < Move sorted column to the left > Move sorted column to the right As the root user, you may be more concerned about the processes of another user, than you are over your own processes. Because of the several styles of options that the ps command supports, there are different ways to view an individual user's processes. Using the traditional UNIX option, to view the processes of the sysadmin user, execute the following command: [root@localhost ]# ps -u username Or use the BSD style of options and execute: [root@localhost ]# ps u U username 11.6 top Command The ps command provides a "snapshot" of the processes running at the instant the command is executed, the top command that will regularly update the output of running processes. The top command is executed as follows: sysadmin@localhost:$ top F R P M k r Choose sorted field Toggle sort direction Sort by % CPU Sort by % memory used Kill a process (or send it a signal) Renice priority of a process
25 One of the advantages of the top command is that it can be left running to stay on "top" of processes for monitoring purposes. If a process begins to dominate, or "run away" with the system, then it will by default appear at the top of the list presented by the top command. An administrator that is running the top command can then take one of two actions: Terminate the "run away" process: Pressing the k key while the top command is running will prompt the user to provide the PID and then a signal number. Sending the default signal will request the process terminate, but sending signal number 9, the KILL signal, will force the process to terminate. Adjust the priority of the process: Pressing the r key while the top command is running will prompt the user for the process to renice, and then a niceness value. Niceness values can range from -20 to 19, and affect priority. Only the root user can use a niceness that is a lower number than the current niceness, or a negative niceness value, which causes the process to run with an increased priority. Any user can provide a niceness value that is higher than the current niceness value, which will cause the process to run with a lowered priority. Another advantage of the top command is that it is able to give you an overall representation of how busy the system is currently and the trend over time. The load averages shown in the first line of output from the top command indicate how busy the system has been during the last one, five and fifteen minutes. This information can also be viewed by executing the uptimecommand or directly by displaying the contents of the /proc/loadavg file: sysadmin@localhost:$ cat /proc/loadavg / The first three numbers in this file indicate the load average over the last one, five and fifteen minute intervals. The fourth value is a fraction which shows the number of processes currently executing code on the CPU 1 and the total number of processes 254. The fifth value is the last PID value that executed code on the CPU. The number reported as a load average is proportional to the number of CPU cores that are able to execute processes. On a single core CPU, a value of one would mean that the system is fully loaded. On a four core CPU, a value of one would mean that the system is only 1/4 or 25% loaded. Another reason administrators like to keep the top command running is the ability to monitor memory usage in real-time. Both the top and the free command display statistics for how overall memory is being used. The top command also has the ability to show the percent of memory used by each process, so a process that is consuming an inordinate amount of memory can quickly be identified free Command Executing the free command without any options provides a snapshot of the memory used at that moment. If you want to monitor memory usage over time with the free command, then you can execute it with the - s option and specify that number of seconds. For example, executing free -s 10would update the output every ten seconds. To make it easier to interpret what the free command is outputting the -m or -g options can be useful to show the output in either megabytes or gigabytes, respectively. Without these options, the output is displayed in bytes: sysadmin@localhost:$ free total used free shared buffers cached Mem: /+ buffers/cache: Swap: When reading the output of the free command: The first line is a descriptive header. The second line labeled Mem: is the statistics for the physical memory of the system. The third line represents the amount of physical memory after adjusting those values by not taking into account any memory that is in use by the kernel for buffers and caches. Technically, this "used" memory could be "reclaimed" if needed. The fourth line of output refers to Swap memory, also known as virtual memory. This is space on the hard disk that is used like physical memory when the amount of physical memory becomes low. Effectively, this makes it seem that the system has more memory than it really does, but using swap space can also slow down the system. If the amount of memory and swap that is available becomes very low, then the system will begin to automatically terminate processes. This is one reason why it is important to monitor the system's memory usage. An administrator that notices the system becoming low on free memory can use top or kill to terminate the processes of their own choice, rather than letting the system choose Log Files As the kernel and various processes run on the system, they produce output that describes how they are running. Some of this output is displayed in the terminal window where the process was executed, but some of this data is not sent to the screen, but instead it is written to various files. This is called "log data" or "log messages". These log files are very important for a number of reasons; they can be helpful in trouble-shooting problems and they can be used for determining whether or not unauthorized access has been attempted. Some processes are able to "log" their own data to these files, other processes rely on another process (a daemon) to handle these log data files. These logging daemons can vary from one distribution to another. For example, on some distributions, the daemons that run in the background to perform logging are called as syslogdand klogd. In other distributions, a single daemon such as rsyslogd in Red Hat and Centos or systemd-journald in the Fedora may serve this logging function. Regardless of what the daemon process is named, the log files themselves are almost always placed into the /var/log directory structure. Although some of the file names may vary, here are some of the more common files to be found in this directory: File boot.log cron dmesg maillog messages secure Xorg.0.log Contents Messages generated as services are started during the startup of the system. Messages generated by the crond daemon for jobs to be executed on a recurring basis. Messages generated by the kernel during system boot up. Messages produced by the mail daemon for messages sent or received Messages from the kernel and other processes that don't belong elsewhere. Sometimes named syslog instead of messages after the daemon that writes this file. Messages from processes that required authorization or authentication (such as the login process). Messages from the X windows (GUI) server. Log files are rotated, meaning older log files are renamed and replaced with newer log files. The file names that appear in the table above may have a numeric or date suffix added to them, for example: secure.0 or secure
26 Rotating a log file typically occurs on a regularly scheduled basis, for example, once a week. When a log file is rotated, the system stops writing to the log file and adds a suffix to it. Then a new file with the original name is created and the logging process continues using this new file. With the modern daemons, a date suffix is typically used. So, at the end of the week ending November 3, 2013, the logging daemon might stop writing to /var/log/messages, rename that file /var/log/messages , and then begin writing to a new /var/log/messages file. Although most log files contain text as their contents, which can be viewed safely with many tools, other files such as the /var/log/btmp and /var/log/wtmp files contain binary. By using the file command, you can check the file content type before you view it to make sure that it is safe to view. For the files that contain binary data, there are normally commands available that will read the files, interpret their contents and then output text. For example, the lastb and lastcommands can be used to view the /var/log/btmp and /var/log/wtmp files respectively. For security reasons, most of the files found are not readable by ordinary users, so be sure to execute commands that interact with these files with root privileges dmesg Command The /var/log/dmesg file contains the kernel messages that were produced during system startup. The /var/log/messages file will contain kernel messages that are produced as the system is running, but those messages will be mixed in with other messages from daemons or processes. Although the kernel doesn't have its own log file normally, one can be configured for them typically by modifying either the /etc/syslog.conf or the /etc/rsyslog.conf file. In addition, the dmesg command can be used to view the kernel ring buffer, which will hold a large number of messages that are generated by the kernel. On an active system, or one experiencing many kernel errors, the capacity of this buffer may be exceeded and some messages might be lost. The size of this buffer is set at the time the kernel is compiled, so it is not trivial to change. Executing the dmesg command can produce up to 512 kilobytes of text, so filtering the command with a pipe to another command like less or grep is recommended. For example, if you were troubleshooting problems with your USB device, then searching for the text "USB" with the grepcommand being case insensitive may be helpful: sysadmin@localhost:$ dmesg grep -i usb usbcore: registered new interface driver usbfs usbcore: registered new interface driver hub usbcore: registered new device driver usb ehci_hcd: USB 2.0 'Enhanced' Host Controller (EHCI) Driver ohci_hcd: USB 1.1 'Open' Host Controller (OHCI) Driver ohci_hcd 0000:00:06.0: new USB bus registered, assigned bus number 1 usb usb1: New USB device found, idvendor=1d6b, idproduct=0001 usb usb1: New USB device strings: Mfr=3, Product=2, SerialNumber=1 Lab The kernel and /proc In this task, you will explore the /proc directory and commands which communicate with the Linux kernel. The /proc directory appears to be an ordinary directory, like /usr or /etc, but it is not. Unlike /usr or /etc directories, which are usually written to a disk drive, the /procdirectory is a pseudo filesystem maintained in the memory of the computer. The /proc directory contains a subdirectory for each running process on the system. Programs such as ps and top read the information about running processes from these directories. The /proc directory also contains information about the operating system and its hardware in files like /proc/cpuinfo, /proc/meminfo and /proc/devices. The /proc/sys subdirectory contains pseudo files that can be used to alter the settings of the running kernel. As these files are not "real" files, an editor should not be used to change them; instead you should use either the echo or sysctl command to overwrite the contents of these files. For the same reason, do not attempt to view these files in an editor, but use the cat or sysctl command instead. For permanent configuration changes, the kernel uses the /etc/sysctl.conf file. Typically, this file is used by the kernel to make changes to the /proc files when the system is starting up Step 1 In this task, you will examine some of the files contained in the /proc directory: ls /proc Your output should be similar to the following: sysadmin@localhost:$ ls /proc 1 cpuinfo kallsyms mpt sysrq-trigger 19 crypto kcore mtrr sysvipc 23 devices key-users net thread-self 25 diskstats keys pagetypeinfo timer_list 41 dma kmsg partitions timer_stats 50 driver kpagecount sched_debug tty 62 execdomains kpageflags schedstat uptime 74 fb loadavg scsi version acpi filesystems locks self version_signature buddyinfo fs mdstat slabinfo vmallocinfo bus interrupts meminfo softirqs vmstat cgroups iomem misc stat zoneinfo cmdline ioports modules swaps consoles irq mounts sys Recall that the directories that have numbers for names represent running processes on the system. The first process is always /sbin/init, so the directory /proc/1 will contain files with information about the running init process. The cmdline file inside the process directory (/proc/1/cmdline, for example) will show the command that was executed. The order in which other processes are started varies greatly from system to system. Since the content of this file does not contain a new line character, an echocommand will be executed to cause the prompt to go to a new line Step 2 Use cat and then ps to view information about the /sbin/init process (Process IDentifier (PID) of 1): cat /proc/1/cmdline; echo ps -p 1 Your output should look something like this: sysadmin@localhost:$ cat /proc/1/cmdline; echo /sbin/init Note: The echo command in this example is executed immediately after the catcommand. Since it has no argument, it functions only to put the following command prompt on a new line. Execute the cat command alone to see the difference. sysadmin@localhost:$ ps -p 1 PID TTY TIME CMD 1? 00:00:00 init
27 The other files in the /proc directory contain information about the operating system. The following tasks will be used to view and modify these files Step 3 View the /proc/cmdline file to see what arguments were passed to the kernel at boot time: cat /proc/cmdline The output of the command should be similar to this: sysadmin@localhost:$ cat /proc/cmdline BOOT_IMAGE=/vmlinuz generic root=/dev/mapper/vlabs--vg-root ro cgroup_enable=memory swapacc ount=1 sysadmin@localhost:$ 11.3 Managing Processes In this task you will start and stop processes Step 1 From the terminal, type the following command: ping localhost > /dev/null Your output should be similar to the following: sysadmin@localhost:$ ping localhost > /dev/null The output of the ping is being redirected to the /dev/null file (which is commonly known as the bit bucket). Notice that the terminal appears to hang up at this command. This is due to running this command in the foreground. The system will continue to ping until the process is terminated or suspended by the user Step 2 Terminate the foreground process by pressing Ctrl-C. sysadmin@localhost:$ ping localhost > /dev/null ^C sysadmin@localhost:$ Step 3 Next, to start the same process in the background, type: ping localhost > /dev/null & Your output should be similar to the following: sysadmin@localhost:$ ping localhost > /dev/null & [1] 158 By adding the ampersand & to the end of the command, the process is started in the background allowing the user to maintain control of the terminal. An easier way to enter the above command would be to take advantage of the command history. You could have pressed the Up Arrow Key on the keyboard, add a Space and &to the end of the command and then pressed the Enter key. This is a time-saver when entering similar commands. Notice that the previous command returns the following information: [1] 158 This means that this process has a job number of 1 (as demonstrated by the output of [1]) and a Process ID (PID) of 158. Each terminal/shell will have unique job numbers. The PID is system-wide; each process has a unique ID number.this information is important when performing certain process manipulations, such as stopping processes or changing their priority value. Note: Your Process ID will likely be different than the one in the example Step 4 To see which commands are running in the current terminal, type the following command: jobs sysadmin@localhost:$ jobs [1]+ Running ping localhost > /dev/null & Step 5 Next, start another ping command in the background by typing the following: ping localhost > /dev/null & Your output should be similar to the following: sysadmin@localhost:$ ping localhost > /dev/null & [2] 100 Notice the different job number and process ID for this new command Step 6 Now, there should be two ping commands running in the background. To verify, issue the jobscommand again: jobs Your output should be similar to the following: sysadmin@localhost:$ jobs [1]- Running ping localhost > /dev/null & [2]+ Running ping localhost > /dev/null & Step 7 Once you have verified that two ping commands are running, bring the first command to the foreground by typing the following: fg %1 Your output should be similar to the following: sysadmin@localhost:$ fg %1 ping localhost > /dev/null Step 8 Notice that, once again, the ping command has taken control of the terminal. To suspend (pause) the process and regain control of the terminal, type Ctrl-Z: sysadmin@localhost:$ fg %1 ping localhost > /dev/null ^Z [1]+ Stopped ping localhost > /dev/null
28 Step 9 To have this process continue executing in the background, execute the following command: bg %1 Your output should be similar to the following: sysadmin@localhost:$ bg %1 [1]+ ping localhost > /dev/null & Step 10 Issue the jobs command again to verify two running processes : jobs Your output should be similar to the following: sysadmin@localhost:$ jobs [1]- Running ping localhost > /dev/null & [2]+ Running ping localhost > /dev/null & Step 11 Next, start one more ping command by typing the following: ping localhost > /dev/null & Your output should be similar to the following: sysadmin@localhost:$ ping localhost > /dev/null & [3] Step 12 Issue the jobs command again to verify three running processes : jobs sysadmin@localhost:$ jobs [1] Running ping localhost > /dev/null & [2]- Running ping localhost > /dev/null & [3]+ Running ping localhost > /dev/null & Step 13 Using the job number, stop the last ping command with the kill command and verify it was stopped executing the jobs command: kill %3 jobs Your output should be similar to the following: sysadmin@localhost:$ kill %3 sysadmin@localhost:$ jobs [1] Running ping localhost > /dev/null & [2]- Running ping localhost > /dev/null & [3]+ Terminated ping localhost > /dev/null Step 14 Finally, you can stop all of the ping commands with the killall command. After executing the killall command, wait a few moments, and then run the jobs command to verify that all processes have stopped: killall ping jobs Your output should be similar to the following: sysadmin@localhost:$ killall ping [1]- Terminated ping localhost > /dev/null [2]+ Terminated ping localhost > /dev/null sysadmin@localhost:$ jobs 11.4 Use Top to View Processes In this task, you will use the top command to work with processes. By default the top program sorts the processes in descending order of percentage of CPU usage, so the busiest programs will be at the top of its listing Step 1 From the terminal window, type the following commands: ping localhost > /dev/null & ping localhost > /dev/null & sysadmin@localhost:$ ping localhost > /dev/null & [1] 112 sysadmin@localhost:$ ping localhost > /dev/null & [2] 113 Make note of the PIDs output by the above commands! They will be different than the examples that we are providing. You will use the PIDs in subsequent steps Step 2 Next, start the top command by typing the following in the terminal: top top - 00:56:34 up 8:18, 1 user, load average: 0.09, 0.14, 0.20 Tasks: 10 total, 1 running, 9 sleeping, 0 stopped, 0 zombie Cpu(s): 2.1%us, 1.8%sy, 0.0%ni, 96.1%id, 0.0%wa, 0.0%hi, 0.0%si, 0.0%st Mem: k total, k used, k free, k buffers Swap: k total, 0k used, k free, k cached PID USER PR NIVIRT RES SHR S %CPU %MEM TIME+ COMMAND 1 root S :00.14 init 19 syslog m S :00.05 rsyslogd 23 root S :00.00 cron 25 root S :00.00 sshd 41 bind m 19m 5988 S :00.04 named 50 root S :00.00 login 62 sysadmin S :00.01 bash 112 sysadmin S :00.46 ping 113 sysadmin S :00.40 ping 114 sysadmin R :00.01 top Note: The output of the top command changes every 2 seconds.
29 Step 3 The top command is an interactive program, which means that you can issue commands within the program. You will use the top command to kill the ping processes. First type the letter k. Notice a prompt has appeared underneath Swap: top - 01:52:14 up 9:13, 1 user, load average: 0.04, 0.11, 0.19 Tasks: 10 total, 1 running, 9 sleeping, 0 stopped, 0 zombie Cpu(s): 4.2%us, 2.6%sy, 0.0%ni, 93.0%id, 0.1%wa, 0.0%hi, 0.1%si, 0.0%st Mem: k total, k used, k free, k buffers Swap: k total, 0k used, k free, k cached PID to kill: PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND 1 root S :00.14 init 19 syslog m S :00.07 rsyslogd 23 root S :00.00 cron 25 root S :00.00 sshd 41 bind m 19m 5988 S :00.07 named 50 root S :00.00 login 62 sysadmin S :00.01 bash 103 sysadmin S :00.96 ping 104 sysadmin S :00.85 ping 108 sysadmin R :01.03 top Step 4 At the PID to kill: prompt, type the PID of the first running ping process, then press Enter. Notice that the prompt changes as below: Consider This There are several different numeric values that can be sent to a process. These are predefined values, each with a different meaning. If you want to learn more about these values, type man kill in a terminal window. The prompt indicates that the default signal is the terminate signal indicated bysigterm or the number Step 6 Next, kill the remaining ping process as before, except this time, at the signal prompt Kill PID with signal [15]: prompt, use a value of 9 instead of accepting the default of 15. Press Enter to accept then entry Step 5 At the Kill PID with signal [15]: prompt, enter the signal to send to this process. In this case, just press the Enter key to use the default signal. Notice that the first ping command is removed and only one ping command remains in the listing (you may need to wait a few seconds as the top command refreshes): Consider This The kill signal 9 or SIGKILL is a "forceful" signal that cannot be ignored, unlike the default value of 15. Notice that all references to the ping command are now removed from top.
30 Step 7 Type q to exit the top command. The following screen reflects that both ping commands were terminated: [1]- Terminated ping localhost > /dev/null [2]+ Killed ping localhost > /dev/null 11.5 Use pkill and kill To Terminate Processes In this task, we will continue to work with processes. You will use pkill and kill to terminate processes Step 1 To begin, type the following commands in the terminal: sleep & sleep & sysadmin@localhost:$ sleep & [1] 85 sysadmin@localhost:$ sleep & [2] 86 sysadmin@localhost:$ The sleep command is typically used to pause a program (shell script) for a specific period of time. In this case it is used just to provide a command that will take a long time to run. Make sure to note the PIDs on your system of the sleep processes for the next steps! Your PIDs will be different than those demonstrated in the lab Step 2 Next, determine which jobs are currently running by typing: jobs sysadmin@localhost:$ jobs [1]- Running sleep & [2]+ Running sleep & sysadmin@localhost:$ Step 3 Now, use the kill command to stop the first instance of the sleep command by typing the following (substitute PID with the process id of your first sleep command).execute jobsto verify process has been stopped: kill PID jobs sysadmin@localhost:$ ps PID TTY TIME CMD 62? 00:00:00 bash 89? 00:00:00 sleep 90? 00:00:00 sleep 91? 00:00:00 ps sysadmin@localhost:$ kill 89 sysadmin@localhost:$ jobs [1]- Terminated sleep [2]+ Running sleep & sysadmin@localhost:$ Helpful Hint: If you can't remember the PID of the first process, just type the ps (process) command, as shown above Step 4 Next, use the pkill command to terminate the remaining sleep command, using the name of the program rather than the PID: pkill -15 sleep Your output should be similar to the following: sysadmin@localhost:$ pkill -15 sleep [2]+ Terminated sleep sysadmin@localhost:$ 11.6 Using ps to Select and Sort Processes The ps command can be used to view processes. By default, the ps command will only display the processes running in the current shell Step 1 Start up a background process using ping and view current processes using the ps command: ping localhost > /dev/null & ps Your output should be similar to the following: sysadmin@localhost:$ ping localhost > /dev/null & [1] 98 sysadmin@localhost:$ ps PID TTY TIME CMD 62? 00:00:00 bash 98? 00:00:00 ping 99? 00:00:00 ps Make note of the PID of the ping, you will use the PID in a subsequent step Step 2 Execute the ps command using the option -e, so all processes are displayed. ps -e Your output should be similar to the following: sysadmin@localhost:$ ps -e PID TTY TIME CMD 1? 00:00:00 init 19? 00:00:00 rsyslogd 23? 00:00:00 cron 25? 00:00:00 sshd 41? 00:00:00 named 50? 00:00:00 login 62? 00:00:00 bash 98? 00:00:00 ping 100? 00:00:00 ps Due to this environment being a virtualized operating system, there are far fewer processes than what would normally be shown with Linux running directly on hardware.
31 Step 3 Use the ps command with the -o option to specify which columns to output. ps -o pid,tty,time,%cpu,cmd Your output should be similar to the following: sysadmin@localhost:$ ps -o pid,tty,time,%cpu,cmd PID TT TIME %CPU CMD 62? 00:00: bash 98? 00:00: ping localhost 102? 00:00: ps -o pid,tty,time,%cpu,cmd Step 4 Use the --sort option to specify which column(s) to sort by. By default, a column specified for sorting will be in ascending order, this can be forced with placing a plus + symbol in front of the column name. To specify a descending sort, use the minus - symbol in front of the column name. Sort the output of ps by %mem: ps -o pid,tty,time,%mem,cmd --sort %mem sysadmin@localhost:$ ps -o pid,tty,time,%mem,cmd --sort %mem PID TT TIME %MEM CMD 103? 00:00: ps -o pid,tty,time,%mem,cmd --sort %mem 98? 00:00: ping localhost 62? 00:00: bash Step 5 While the ps command can show the percentage of memory that a process is using, the freecommand will show overall system memory usage: free Your output should be similar to the following: sysadmin@localhost:$ free total used free shared buffers cached Mem: /+ buffers/cache: Swap: Step 6 Stop the ping command with the following kill command and verify with the jobscommand: kill PID jobs Your output should be similar to the following: sysadmin@localhost:$ kill 98 sysadmin@localhost:$ jobs [1]+ Terminated ping localhost > /dev/null 11.7 Viewing System Logs System logs are critical for many tasks, including fixing operating system problems and ensuring that your system is secure. Knowing where the system log files are stored and how to maintain them is important for a system administrator. There are two daemons that handle log messages: the syslogd daemon and the klogddaemon. Typically you don't need to worry about klogd; it only handles kernel log messages and it sends its log information to the syslogd daemon. Messages that were generated by the kernel at boot time are stored in the /var/log/dmesgfile. The dmesg command allows viewing of current kernel messages, as well as providing control of whether those messages will appear in a terminal console window. The main log file that is written to by syslogd is /var/log/messages. In addition to the logging done by syslogd, many other processes perform their own logging. Some examples of processes that do their own logging include the Apache web server (log file resides in the /var/log/httpd directory), the Common Unix Printing System (/var/log/cups) and the auditd daemon (/var/log/audit). Note: On CentOS systems, the syslogd is called rsyslogd Step 1 Because the next few commands that you will run in this lab require superuser rights, use the sucommand to switch to the root account: su - root {Enter the password: netlab123} sysadmin@localhost:$ su - root Password: root@localhost:# Step 2 System logs are stored in the /var/log directory. List the files in this directory: ls /var/log root@localhost:# ls /var/log alternatives.log boot cron.log faillog lastlog news wtmp apt bootstrap.log dmesg fsck mail.err syslog auth.log btmp dpkg.log kern.log mail.log upstart root@localhost:# Step 3 Each log file represents a service or feature. For example, the auth.log file displays information regarding authorization or authentication, such as user login attempts. New data is stored at the bottom of the file. Execute the following commands to see an example: ssh localhost {At the first prompt, type yes} {At the second prompt, type abc} {At the third prompt, type abc} {At the fourth prompt, type abc} tail -5 /var/log/auth.log root@localhost:# ssh localhost The authenticity of host 'localhost (::1)' can't be established. ECDSA key fingerprint is 5f:e2:43:0f:f9:26:e5:d5:77:ba:9e:95:72:9e:ee:64. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'localhost' (ECDSA) to the list of known hosts. root@localhost's password:
32 Permission denied, please try again. password: Permission denied, please try again. password: Permission denied (publickey,password). tail -5 /var/log/auth.log Apr 8 20:25:13 localhost sshd[117]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=localhost user=root Apr 8 20:25:16 localhost sshd[117]: Failed password for root from ::1 port ssh2 Apr 8 20:25:28 sshd[117]: last message repeated 2 times Apr 8 20:25:28 localhost sshd[117]: Connection closed by ::1 [preauth] Apr 8 20:25:28 localhost sshd[117]: PAM 2 more authentication failures; logname= uid=0 euid=0 tty=ssh ruser= rhost=localhost user=root root@localhost:# The ssh command was used to generated data in the /var/log/auth.log file. Note the failed login attempts are logged in the /var/log/auth.log file Step 4 To see another example of log entries, execute the following commands: crontab -e Then add the following line to the document (recall that i will allow you to enter the insert mode) and then save and exit with ESC, :wq, Enter: 0 2 * * 0 who >> /tmp/whothere After you have completed the edits, view the log file for the crontab service: crontab -l tail -2 tail /var/log/cron.log root@localhost:# crontab -l tail -2 # m h dom mon dow command 0 2 * * 0 who >> /tmp/whothere root@localhost:# tail /var/log/cron.log Apr 8 17:33:32 localhost /usr/sbin/cron[22]: (CRON) INFO (pidfile fd = 3) Apr 8 17:33:32 localhost /usr/sbin/cron[23]: (CRON) STARTUP (fork ok) Apr 8 17:33:32 localhost /usr/sbin/cron[23]: (CRON) INFO jobs) Apr 8 18:17:01 localhost /USR/SBIN/CRON[79]: (root) CMD ( cd / && run-parts - -report /etc/cron.hourly) Apr 8 19:17:02 localhost /USR/SBIN/CRON[82]: (root) CMD ( cd / && run-parts - -report /etc/cron.hourly) Apr 8 20:17:01 localhost /USR/SBIN/CRON[99]: (root) CMD ( cd / && run-parts - -report /etc/cron.hourly) Apr 8 20:31:18 localhost crontab[121]: (root) BEGIN EDIT (root) Apr 8 20:32:42 localhost crontab[121]: (root) REPLACE (root) Apr 8 20:32:42 localhost crontab[121]: (root) END EDIT (root) Apr 8 20:33:19 localhost crontab[132]: (root) LIST (root) root@localhost:# tail -5 /var/log/dmesg dmesg tail -5 root@localhost:# tail -5 /var/log/dmesg [ ] type=1400 audit( :10): apparmor="status" operation="profile_load" name="/usr/ sbin/tcpdump" pid=848 comm="apparmor_parser" [ ] Bridge firewalling registered [ ] ip_tables: (C) Netfilter Core Team [ ] nf_conntrack version (16384 buckets, max) [ ] input: ImPS/2 Generic Wheel Mouse as /devices/platform/i8042/serio1/input/input2 root@localhost:# dmesg tail -5 [ ] device veth0pl17180 left promiscuous mode [ ] br998ad950-b830: port 1(veth0pl17180) entered disabled state [ ] bre2e b5e: port 1(veth0pl17664) entered disabled state [ ] device veth0pl17664 left promiscuous mode [ ] bre2e b5e: port 1(veth0pl17664) entered disabled state root@localhost:# Right about now you are likely thinking "what do all of these messages actually mean?". The answer to that question isn't a simple one, however the point behind this lesson isn't to explain the meaning of all of the log messages, but rather to learn where to find log messages. As you gain more experience in Linux, you will start to troubleshoot problems. In most cases the first place you want to look is the log files. In order to provide you a realistic troubleshooting example, follow the next set of tasks Step 6 Enter the following command to disable the ability of the sysadmin user from creating crontabentries and exit back to the sysadmin user: echo "sysadmin" > /etc/cron.deny exit root@localhost:# echo "sysadmin" > /etc/cron.deny root@localhost:# exit logout sysadmin@localhost:$ Step 7 Attempt to execute the following crontab command: crontab -e sysadmin@localhost:$ crontab -e You (sysadmin) are not allowed to use this program (crontab) See crontab(1) for more information sysadmin@localhost:$ Note: This command fails because of the entry in the /etc/cron.deny. If a username exists in this file, then that user can not use the crontab command Step 5 View the last five lines of the file /var/log/dmesg to see kernel messages from boot time and execute the dmesg command piped to the tail command to view the last five kernel messages:
33 Step 8 Instead of switching users to root with the su command, use sudo to execute the following command with root privileges: sudo tail -5 /var/log/cron.log {Enter the password: netlab123} sysadmin@localhost:$ sudo tail -5 /var/log/cron.log [sudo] password for sysadmin: Apr 8 20:31:18 localhost crontab[121]: (root) BEGIN EDIT (root) Apr 8 20:32:42 localhost crontab[121]: (root) REPLACE (root) Apr 8 20:32:42 localhost crontab[121]: (root) END EDIT (root) Apr 8 20:33:19 localhost crontab[132]: (root) LIST (root) Apr 8 20:47:06 localhost crontab[139]: (sysadmin) AUTH (crontab command not allowed) sysadmin@localhost:$ As you can see from the last line of the output of the tail command, the sysadmin user is not allowed to use the crontab command Shared Libraries Shared libraries are files that contain code that executable program files can link to in order to use that code. Because multiple programs often link to a single library file, this helps to reduce the amount of space needed for this code since each program does not have to have its own copy of the library code. These library files are most often stored in the /lib and /usr/lib directories. Additional directories can be added either by editing the configuration file, /etc/ld.so.conf. You can also create files with names ending in.conf and place them in the /etc/ld.so.conf.ddirectory. Finally, you can also set the LD_LIBRARY_PATH environment variable as well Step 1 When executed as the root user, the ldconfig command can be used to update the cache and the symbolic links for the shared libraries on the system. As an ordinary user, you will execute the ldconfig command to print the list of shared libraries: Chapter Basic Network Terminology Before setting up a network or accessing an existing network, it is important to know some key terms that are related to networking. This section explores the terms you should be aware of. Some of the terms are basic and you may already be familiar with them, however others are more advanced. Host: A host is basically a computer. However, many people have a more limited idea of what a computer is (like a desktop computer or a laptop). In reality, many other devices are also computers, such as cell phones, digital music players and many modern televisions. In networking terms, a host is any device that communicates with another device. Network: A network is a collection of two or more hosts (computers) that are able to communicate with each other. This communication can be via a wired connection or wireless. Internet: The Internet is an example of a network. It consists of a publically accessible network that connects millions of hosts throughout the world. Many people use the Internet to surf web pages and send/receive , but the Internet has many additional capabilities besides these activities. Wi-Fi: The term Wi-Fi refers to wireless networks. Server: A host that provides a service to another host or client is called a server. For example, a web server stores, processes and delivers web pages. An server receives incoming mail and delivers outgoing mail. Service: A feature being provided from a host is a service. An example of a service would be when a host provides web pages to another host. Client: A client is a host that is accessing a server. When you are working on a computer surfing the Internet, you are considered to be on a client host. Router: Also called a gateway, a router is a machine that connects hosts from one network to another network. For example, if you work in an office environment, the computers within the company can all communicate via the local network created by the administrators. To access the Internet, the computers would have to communicate with a router that would be used to forward network communications to the Internet. Typically when you communicate on a large network (like the Internet), there are several routers that are used before your communication reaches its final destination. The following diagram provides a visual reference for several of the terms discussed above: ldconfig -p less Remember to press q to quit the less pager Step 2 In order to view what libraries are linked to an executable, such as /bin/bash, execute the ldd command: ldd /bin/bash Your output should appear similar to the following: sysadmin@localhost:$ ldd /bin/bash linux-vdso.so.1 => (0x00007ffce6fbd000) libtinfo.so.5 => /lib/x86_64-linux-gnu/libtinfo.so.5 (0x00007fb32ae94000) libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007fb32ac90000) libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007fb32a8d1000) /lib64/ld-linux-x86-64.so.2 (0x ddfa4e000) 12.3 Networking Features Terminology In addition to the networking terms discussed in the last section, there are some additional terms that you should be aware of. These terms focus more on the different types of networking services that are commonly used as well as some of the techniques that are used to communicate between machines. Network packet: A network packet is used to send network communication between hosts. By breaking down communication into smaller chunks (packets), the data delivery method is much more efficient.
34 IP address: An Internet Protocol (IP) address is a unique number assigned to a host on a network. Hosts use these numbers to "address" network communication. More discussion on IP addresses will occur later in this chapter. Network mask: Also called a netmask or mask, a network mask is a number system that can be used to define which IP addresses are considered to be within a single network. Because of how routers perform their functions, networks have to be clearly defined. Hostname: Each host on a network could have its own hostname. This makes it easier for humans to address network packets to another host because names are easier for humans to remember than numbers. Hostnames are translated into IP addresses before the network packet is sent on the network. DHCP: Hosts can be assigned hostnames, IP addresses and other network-related information by a DHCP (Dynamic Host Configuration Protocol) server. In the world of computers, a protocol is a well-defined set of rules. DHCP defines how network information is assigned to client hosts and the DHCP server is the machine that provides this information. While setting up a DHCP server is beyond the scope of this chapter, you will see how to configure a DHCP client machine later in this chapter. DNS: As mentioned previously, hostnames are translated into IP addresses, prior to the network packet being sent on the network. This means that your host needs to know the IP address of all of the other hosts that you are communicating with. When working on a large network (like the Internet), this can pose a challenge as there are so many hosts. A DNS (Domain Name Server) server provides the service of translating domain names into IP addresses. While setting up a DNS server is beyond the scope of this chapter, you will see how to configure a DNS client machine later in this chapter. Ethernet: In a wired network environment, Ethernet is the most common way to physically connect the hosts into a network. Ethernet cables are connected to network cards that support Ethernet connections. Ethernet cables and devices (such as routers) are specifically designed to support different speeds of communications, the lowest being 10 Mbps (10 Megabits per second) and the highest being 100 Gbps (100 gigabits per second). The most common speeds are 100 Mbps and 1 Gbps. TCP/IP: The Transmission Control Protocol/Internet Protocol (TCP/IP) is a fancy name for a collection of protocols (remember, protocol = set of rules) that are used to define how network communication should take place between hosts. While it isn't the only collection of protocols used to define network communication, it is the most often utilized one. As an example, TCP/IP includes the definition of how IP addresses and network masks work IP Addresses As previously mentioned, hosts "address" network packets by using the IP address of the destination machine. The network packet also includes a "return address", the IP address of the sending machine. There are, in fact, two different types of IP addresses: IPv4 and IPv6. To understand why there are two different types, you need to understand a brief bit of IP addressing history. For many years, the IP addressing technique that was used by all computers was IPv4 (IP version 4). In an IPv4 address, a total of four 8-bit (8-bit = numbers from 0 to 255) numbers are used to define the address. For example: Note, this is considered a 32-bit address (4 x 8-bit = 32). Each host on the Internet must have a unique IP address. In an IPv4 environment, there is a technical limit of about 4.3 billion IP addresses. However, many of these IP addresses are not really useable for various reasons. Also, IP addresses have been assigned to organizations that haven't fully made use of all of the IP addresses they had available. While it seems like there should be plenty of IP addresses to go around, various factors (the increasing number of hosts on the Internet, reserved private IP addresses, etc.) led to a problem: The Internet started running out of IP addresses. This, in part, encouraged the development of IPv6. IPv6 was officially "created" in In an IPv6 network the addresses are much larger, 128-bit addresses that look like this: 2001:0db8:85a3:0042:1000:8a2e:0370:7334. Essentially this provides for a much larger address pool, so large that running out of addresses any time in the near future is very unlikely. It is important to note the difference between IPv4 and IPv6 isn't just "more IP addresses". IPv6 has many other advanced features that address some of IPv4's limitations, including better speed, more advanced package management and more efficient data transportation. Considering all the advantages, you would think that by now all hosts would be using IPv6. This isn't the case at all. The majority of network-attached devices in the world still use IPv4 (something like 98-99% of all devices). So, why hasn't the world embraced the superior technology of IPv6? There are primarily two reasons: The invention of NAT: Invented to overcome the possibility of running out of IP addresses in an IPv4 environment, Net Address Translation (NAT) used a technique to provide more hosts access to the Internet. In a nutshell, a group of hosts are placed into a private network with no direct access to the Internet; a special router provides Internet access and only this one router needs an IP address to communicate on the Internet. In other words, a group of hosts share a single IP address, meaning a lot more computers can attach to the Internet. This feature means the need to move to IPv6 is less critical then before the invention of NAT. Porting issues: Porting is switching over from one technology to another. IPv6 has a lot of great new features, but all of the hosts need to be able to utilize these features. Getting everyone on the Internet (or even just some) to make these changes poses a challenge. Most experts agree that IPv6 will eventually replace IPv4, so understanding the basics of both is important for those who work in the IT industry Configuring Network Devices When you are configuring network devices, there are two initial questions that you need to ask: Wired or wireless? Configuring a wireless device will be slightly different than a wired device because of some of the additional features typically found on wireless devices (such as security). DHCP or static address? Recall that a DHCP server provides network information, such as your IP address and subnet mask. If you don't make use of a DHCP server, then you will need to manually provide this information to your host. This is called using a static IP address. Generally speaking, a desktop machine will use wired network, while a laptop will use wireless. Normally a wired machine uses a static IP address, but these can also often be assigned via a DHCP server. In almost all cases, wireless machines use DHCP since they are almost always mobile and attached to different networks Configuring the Network Using a GUI If you have access to a GUI (Graphical User Interface) environment, you will likely also have access to a GUIbased tool that will allow you to configure your network. These tools vary from one distribution to another. The following examples were performed on a CentOS machine. To start the network configuration tool, click on System in the menu bar, then Preferences > and then Network Connections:
35 The tool first lists all of the current network devices. In the example below, there is only a Wired device: Note that a full discussion of all network features is beyond the scope of this course. The focus on this section will be to change key network components. If you click on the IPv4 Settings tab, the following would be displayed: The network device itself is eth0. Network devices are named eth0, eth1, etc. To modify this network device, click on the device name and then click the Edit button: Recall that you can assign a static IP address or use a DHCP server (if one is available). This change can be made by clicking on the drop down list next to Method:
36 Configuring the Network Using Configuration Files There will be times when no GUI-based tool will be available. In those cases, it is helpful to know the configuration files that are used to store and modify network data. These files can vary depending on the distribution that you are working on. The following examples are provided for CENTOS systems Primary IPv4 Configuration File The primary configuration file for an IPv4 network interface is the /etc/sysconfig/network-scripts/ifcfg-eth0 file. The following demonstrates what this file looks like when configured for a static IP address: If you choose Manual, then you will be able to change the current address by clicking in the area where the address is currently specified: Note that if you choose Automatic (DHCP), then the Addresses location is "grayed out": root@localhost:# cat /etc/sysconfig/network-scripts/ifcfg-eth0 DEVICE="eth0" BOOTPROTO=none NM_CONTROLLED="yes" ONBOOT=yes TYPE="Ethernet" UUID="98cf38bf-d91c-49b3-bb1b-f48ae7f2d3b5" DEFROUTE=yes IPV4 _FAILURE_FATAL=yes IPV6INOT=no NAME="System eth0" IPADDR= PREFIX=24 GATEWAY= DNS1= HWADDR=00:50:56:90:18:18 LAST_CONNECT= If the device was configured to be a DHCP client, then the IPADDR, GATEWAY and DNS1values would not be set. Additionally, the BOOTPROTO value would be set to dhcp Primary IPv6 Configuration File On a CentOS system, the primary IPv6 configuration file is the same file where IPv4 configuration is stored: the /etc/sysconfig/network-scripts/ifcfg-eth0 file. If you want to have your system have a static IPv6 address, add the following to the configuration file: Important: If you switch from Automatic (DHCP) back to Manual, all of the previous data is "gone". By clicking the Cancel button and editing the eth0 device again, the data will reappear. Most GUI-based tools make changes take effect immediately after you save them. However, in some cases, you might need to either reboot the machine or run a command as the administrator to make the changes take effect. The following demonstrates the command that would need to be executed on a CentOS system: IPV6INIT=yes IPV6ADDR=<IPv6 IP Address> IPV6_DEFAULTGW=<IPv6 IP Gateway Address> If you want your system to be a DHCP IPv6 client, then add the following setting: DHCPV6C=yes You also need to add the following setting to the /etc/sysconfig/network file: NETWORKING_IPV6=yes Domain Name Service (DNS) When a computer is asked to access a website, such as it does not necessarily know what IP address to use. In order for the computer to associate an IP address with the URL or hostname request, the computer relies upon the DNS service of another computer. Often, the IP address of the DNS server is discovered during the DHCP request, while a computer is receiving important addressing information to communicate on the network. The address of the DNS server is stored in the /etc/resolv.conf file. A typical /etc/resolv.conf file is automatically generated and looks like the following:
37 cat /etc/resolv.conf nameserver The nameserver setting is often set to the IP address of the DNS server. The following example uses the host command discussed later in this chapter. Note that the example server is associated with the IP address by the DNS server: host example.com example.com has address It is also common to have multiple nameserver settings, in the event that one DNS server isn't responding /etc/resolv.conf File The file that holds the location of the DNS server is the /etc/resolv.conf file. A typical /etc/resolv.conf file looks like the following: The nameserver setting is set to the IP address of the DNS server. It is common to have multiple nameserver settings, in the event that one DNS server isn't responding Additional Network Configuration Files The following table describes additional network configuration files to be aware of. Although they are not specifically listed in the exam objectives, the objectives do include the general term Network configuration, so these files may in fact appear on the exam: Command /etc/hosts /etc/sysconfig/network /etc/nsswitch.conf Explanation This file contains a table of hostnames to IP addresses. It can be used to supplement a DNS server. This file has two settings. The NETWORK setting can determine if networking is turned on (yes) or off (no). The HOSTNAME setting defines the local machine's hostname. This file can be used to modify where hostname lookups occur. For example, the setting hosts: files dnswould have hostname lookups occur in the /etc/hostsfile first and then the DNS server second. If switched to hosts: dns files, the DNS server would be searched first Restarting the Network After changing a network configuration file (for example, the /etc/sysconfig/network-scripts/ifcfg-eth0 file or the /etc/resolv.conf file), you either need to reboot the machine or run a command as the administrator to make the changes take effect. The following example demonstrates the command that would need to be executed on a CentOS system: ifconfig Command The ifconfig command stands for "interface configuration" and is used to display network configuration information. Not all network settings are covered in this course, but it is important to note from the output below that the IP address of the primary network device (eth0) is and that the device is currently active (UP): root@localhost:# ifconfig eth0 Link encap:ethernet HWaddr b6:84:ab:e9:8f:0a inet addr: Bcast: Mask: inet6 addr: fe80::b484:abff:fee9:8f0a/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:95 errors:0 dropped:4 overruns:0 frame:0 TX packets:9 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:25306 (25.3 KB) TX bytes:690 (690.0 B) lo Link encap:local Loopback inet addr: Mask: inet6 addr: ::1/128 Scope:Host UP LOOPBACK RUNNING MTU:65536 Metric:1 RX packets:6 errors:0 dropped:0 overruns:0 frame:0 TX packets:6 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:460 (460.0 B) TX bytes:460 (460.0 B) root@localhost:# The lo device is referred to as the loopback device. It is a special network device used by the system when sending network-based data to itself. The ifconfig command can also be used to temporarily modify network settings. Typically these changes should be permanent, so using the ifconfig command to make such changes is fairly rare. The ifconfig command is becoming obsolete in some Linux distributions (deprecated) and is being replaced with a form of the ip command, specifically ip addr show. Note that the same information highlighted above can also be found using this command: root@localhost:# ip addr show 1: lo: <LOOPBACK,UP,LOWER_UP> mtu qdisc noqueue state UNKNOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet /8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever
38 6476: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codelstate UP qlen 1000 link/ether b6:84:ab:e9:8f:0a brd ff:ff:ff:ff:ff:ff inet /24 scope global eth0 valid_lft forever preferred_lft forever inet6 fe80::b484:abff:fee9:8f0a/64 scope link valid_lft forever preferred_lft forever route Command Recall that a router (or gateway) is a machine that will allow hosts from one network to communicate with another network. To view a table that describes where network packages are sent, use the route command: root@localhost:# route Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface * U eth0 default UG eth0 root@localhost:# The first red box in the example above indicates that any network package sent to a machine in the network is not sent to a gateway machine (the * indicates "no gateway"). The second red box indicates that all other network packets are sent to the host with the IP address of (the router). Some users prefer to display this information with numeric data only, by using the -noption to the route command. For example, look at the following and focus on where the output used to display default: root@localhost:# route -n Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface U eth UG eth0 root@localhost:# The refers to "all other machines", or the same as "default". The route command is becoming obsolete in some Linux distributions (deprecated) and is being replaced with a form of the ip command, specifically ip route show. Note that the same information highlighted above can also be found using this command: root@localhost:# ip route show default via dev eth0 proto static /24 dev eth0 proto kernel scope link src root@localhost:# ping Command The ping command can be used to determine if another machine is "reachable". If the ping command can send a network package to another machine and receive a response, then you should be able to connect to that machine. By default, the ping command will continue sending packages over and over. To limit how many pings to send, use the -c option. If the ping command is successful, you will see output like the following: root@localhost:# ping -c PING ( ) 56(84) bytes of data. 64 bytes from : icmp_req=1 ttl=64 time=0.051 ms 64 bytes from : icmp_req=2 ttl=64 time=0.064 ms 64 bytes from : icmp_req=3 ttl=64 time=0.050 ms 64 bytes from : icmp_req=4 ttl=64 time=0.043 ms ping statistics packets transmitted, 4 received, 0% packet loss, time 2999ms rtt min/avg/max/mdev = 0.043/0.052/0.064/0.007 ms root@localhost:# If the ping command fails, you will receive a message stating, Destination Host Unreachable: root@localhost:# ping -c PING ( ) 56(84) bytes of data. From icmp_seq=1 Destination Host Unreachable From icmp_seq=2 Destination Host Unreachable From icmp_seq=3 Destination Host Unreachable From icmp_seq=4 Destination Host Unreachable ping statistics packets transmitted, 0 received, +4 errors, 100% packet loss, time 2999ms pipe 4 root@localhost:# It is important to note that just because the ping command fails does not mean that the remote system is really unreachable. Some administrators configure their machines to not respond to ping requests. This is because a server can be attacked by something called a denial of service attack. In this sort of attack, a server is overwhelmed by a massive number of network packets. By ignoring ping requests, the server is less vulnerable. As a result, the ping command may be useful for checking the availability of local machines, but not always for machines outside of your own network netstat Command The netstat command is a powerful tool that provides a large amount of network information. It can be used to display information about network connections as well as display the routing table similar to the route command. For example, you may want to display statistics regarding network traffic. This can be accomplished by using the -i option to the netstat command: root@localhost:# netstat -i Kernel Interface table Iface MTU Met RX-OK RX-ERR RX-DRP RX-OVR TX-OK TX-ERR TX-DRP TX-OVR Flg eth BMRU lo LRU root@localhost:# The most important statistics from the output above are the TX-OK and TX-ERR. A high percentage of TX- ERR may indicate a problem on the network, such as too much network traffic. If you want to use the netstat command to display routing information, use the -roption: root@localhost:# netstat -r Kernel IP routing table Destination Gateway Genmask Flags MSS Window irtt Iface * U eth0 default UG eth0 root@localhost:#
39 The netstat command is also commonly used to display open ports. A port is a unique number that is associated with a service provided by a host. If the port is open, then the service is available for other hosts. For example, you can log into a host from another host using a service called SSH. The SSH service is assigned port #22. So, if port #22 is open, then the service is available to other hosts. It is important to note that the host also needs to have the services itself running; this means that the program that allows remote users to log in needs to be started (which it typically is, for most Linux distributions). To see a list of all currently open ports, you can use the following command: root@localhost:# netstat -tln Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp : :* LISTEN tcp : :* LISTEN tcp : :* LISTEN tcp : :* LISTEN tcp6 0 0 :::53 :::* LISTEN tcp6 0 0 :::22 :::* LISTEN tcp6 0 0 ::1:953 :::* LISTEN root@localhost:# As you can see from the output above, port #22 is "LISTENing", which means it is open. In the previous example, -t stands for TCP (recall this protocol from earlier in this chapter), -l stands for "listening" (which ports are listening) and -n stands for "show numbers, not names". Sometimes showing the names can be more useful. Just drop the -n option: root@localhost:# netstat -tl Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 cserver.example.:domain *:* LISTEN tcp 0 0 localhost:domain *:* LISTEN tcp 0 0 *:ssh *:* LISTEN tcp 0 0 localhost:953 *:* LISTEN tcp6 0 0 [::]:domain [::]:* LISTEN tcp6 0 0 [::]:ssh [::]:* LISTEN tcp6 0 0 localhost:953 [::]:* LISTEN root@localhost:# On some distributions you may see the following message in the man page of the netstat command: NOTE This program is obsolete. Replacement for netstat is ss. Replacement for netstat -r is ip route. Replacement for netstat -i is ip -s link. Replacement for netstat -g is ip maddr. While no further development is being done on the netstat command, it is still an excellent tool for displaying network information. The goal is to eventually replace the netstat command with commands such as the ss and ip commands. However, it is important to realize that this may take some time. The netstat command is covered in this course because it is available on all Linux distributions, still widely used and it is a Linux Essentials exam objective (the ss and ipcommands are not) dig Command There may be times when you need to test the functionality of the DNS server that your host is using. One way of doing this is to use the dig command. This command will perform queries on the DNS server to determine if the information needed is available on the server. In the following example, the dig command is used to determine the IP address of the example.com host: root@localhost:# dig example.com ; <<>> DiG P1 <<>> example.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 0 ;; QUESTION SECTION: ;example.com. IN A ;; ANSWER SECTION: example.com IN A ;; AUTHORITY SECTION: example.com IN NS example.com. ;; Query time: 0 msec ;; SERVER: #53( ) ;; WHEN: Tue Dec 8 17:54: ;; MSG SIZE rcvd: 59 root@localhost:# Note that the response included the IP address of , meaning that DNS server has the IP address to hostname translation information in its database. If your DNS server doesn't have the requested information, it is configured to ask other DNS servers. If none of them have the requested information, you will receive an error message: root@localhost:# dig sample.com ; <<>> DiG P1 <<>> sample.com ;; global options: +cmd ;; connection timed out; no servers could be reached root@localhost:# host Command In its most simple form, the host command works with DNS to associate a hostname with an IP address. As used in a previous example, example.com is associated with the IP address of : root@localhost:# host example.com example.com has address root@localhost:# The host command can also be used in reverse if an IP address is known, but the domain name is not. root@localhost:# host in-addr.arpa domain name pointer example.com in-addr.arpa domain name pointer cserver.example.com. root@localhost:# Other options exist to query the various aspects of a DNS such as a CNAME (canonical name -alias): root@localhost:# host -t CNAME example.com example.com has no CNAME record root@localhost:#
40 Since many DNS servers store a copy of example.com, SOA (Start of Authority) records indicate the primary server for the domain: root@localhost:# host -t SOA example.com example.com has SOA record example.com. cserver.example.com root@localhost:# A comprehensive list of DNS information regarding example.com can be found using the -a (all) option: root@localhost:# host -a example.com Trying "example.com" ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 3549 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1 ;; QUESTION SECTION: ;example.com. IN ANY ;; ANSWER SECTION: example.com IN SOA example.com. cserver.example.com example.com IN NS example.com. example.com IN A ;; ADDITIONAL SECTION: example.com IN A Received 119 bytes from #53 in 0 ms root@localhost:# ssh Command The ssh command will allow you to connect to another machine across the network, log in and then perform tasks on the remote machine. When you use the ssh command and only provide a machine name or IP address to log into, the command will assume you want to log in using the same username that you are currently logged in as. If you want to use a different username, use the syntax: username@hostname root@localhost:# ssh bob@test The authenticity of host test ( ) can t be established. RSA key fingerprint is c2:0d:ff:27:4c:f8:69:a9:c6:3e:13:da:2f:47:e4:c9. Are you sure you want to continue connection (yes/no)? yes Warning: Permanently added test (RSA) to the list of known hosts. bob@test s password: bob@test:$ Fri Oct 4 16:14:43 CDT 2013 bob@test:$ RSA Key Fingerprint The first prompt asks you to verify the identity of the machine you are logging into. In most cases, you are going to want to answer yes. While you can check with the administrator of the remote machine to make sure that the RSA key fingerprint is correct, this isn't really the purpose of this query. It is really designed for future log in attempts. After you answer yes, the RSA key fingerprint of the remote machine is stored on your local system. When you attempt to ssh to this same machine in the future, the RSA key fingerprint provided by the remote machine is compared to the copy stored on the local machine. If they match, then the username prompt appears. If they don't match, you will see an error like the following: sysadmin@localhost:$ @ WARNING: REMOTE HOST IDENTIFICATION @@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that the RSA host key has just been changed. The fingerprint for the RSA key sent by the remote host is c2:0d:ff:27:4c:f8:69:a9:c6:3e:13:da:2f:47:e4:c9. Please contact your system administrator. Add correct host key in /home/sysadmin/.ssh/known_hosts to get rid of this message. Offending key in /home/sysadmin/.ssh/known_hosts:1 RSA host key for test has changed and you have requested strict checking. Host key verification failed. This error could indicate that a rogue host has replaced the correct host. Check with the administrator of the remote system. If the system was recently reinstalled, it would have a new RSA key and that would be causing this error. In the event that this error message is due to a remote machine reinstall, you can remove the /.ssh/known_hosts file from your local system (or just remove the entry for that one machine) and try to connect again: sysadmin@localhost:$ cat /.ssh/known_hosts test ssh-rsa AAAAB3NzaC1yc2EAAAAmIwAAAQEAklOUpkDHrfHY17SbrmTIp/RZ0V4DTxgq9wzd+ohy006SWDSGPA +nafzlhdpow7vdi4mz5ew18kl4jw9jbhufrviqzm7xlelevf4h9lfx5qvkbpppsrg0cda3pbv7kodj/mtyblwxfcrh+ Cv3FXRitBqxiX1nKhXpHAZsMciLq8V6RjsNAQwdsdMFvSlVK/7BA t5faikoafncm1q8x3+2v0ww71/eifmb1zuufljhytprrx88xypndvjynby6vw/pb0rwprz/tn mzaw3ux+pntpi89zpmnbluxyrd2ce86z/il8b+gw3r3+1njotmikjn2so1d01qratlmqvssbx NrRFi9wrf+ghw== sysadmin@localhost:$ rm /.ssh/known_hosts sysadmin@localhost:$ ssh bob@test The authenticity of host test ( ) can t be established. RSA key fingerprint is c2:0d:ff:27:4c:f8:69:a9:c6:3e:13:da:2f:47:e4:c9. Are you sure you want to continue connection (yes/no)? yes Warning: Permanently added test (RSA) to the list of known hosts. bob@test s password: Last login: Fri Oct 4 16:14:39 CDT 2013 from localhost bob@test:$ Returning to the Local Machine To return back to the local machine, use the exit command: bob@test:$ exit logout Connection to test closed. Warning: Be careful, if you use the exit command too many times, you will close the terminal window that you are working in!
41 Lab Step 1 In order to determine your Internet Protocol (IP) address, execute the ifconfig command: sysadmin@localhost:$ ifconfig eth0 Link encap:ethernet HWaddr 3a:3b:65:10:f6:43 inet addr: Bcast: Mask: inet6 addr: fe80::383b:65ff:fe10:f643/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:15 errors:0 dropped:0 overruns:0 frame:0 TX packets:9 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:1206 (1.2 KB) TX bytes:690 (690.0 B) lo Link encap:local Loopback inet addr: Mask: inet6 addr: ::1/128 Scope:Host UP LOOPBACK RUNNING MTU:65536 Metric:1 RX packets:0 errors:0 dropped:0 overruns:0 frame:0 TX packets:0 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:0 (0.0 B) TX bytes:0 (0.0 B) The output shows two main blocks of information. The first block, indented by eth0, reflects information about your first Ethernet network card. The second block, indented by lo, reflects information about the loopback or internal network interface. The second line in each block contains the pertinent information for version 4 of the Internet Protocol (called IPv4) while the third line has the information for version 6 of the Internet Protocol (IPv6). IPv4 is an older method of identifying machines with a series of numbers. It is still widely used today despite the fact that the improved IPv6 method has been available for many years. The IPv4 addresses are displayed as four decimal numbers ranging from 0 to 255separated by periods. The IPv6 addresses are 128 bit numbers which are displayed as hexadecimal digits ranging from 0 to f. The hexadecimal digits are generally organized into groups of four digits separated by colons. If a number of consecutive hexadecimal digits have the value of zero, then they are replaced with two colons Step 2 Having an IP address will allow your system to communicate with other systems on the same network. With routing devices you are able to communicate with systems on other networks. To view the table of routing information, use the route command: route route -n sysadmin@localhost:$ route Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface * U eth0 sysadmin@localhost:$ route -n Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface U eth0 When connecting to other computers, either an IP address or a hostname may be used. Hostnames can be used if they are entered into the /etc/hosts file along with their associated IP address or if a Domain Name Server (DNS) provides IP address to host name translation. A couple of names that are commonly in the /etc/hosts file are localhost, and localhost.localdomain, both of which are used to refer to the current machine Step 3 Verify that the IP address has an entry in the /etc/hosts file: grep /etc/hosts The output should appear as follows, defining the localhost names: sysadmin@localhost:$ grep /etc/hosts localhost The ping command may be used to tell if a system is presently connected to a network. Sometimes, a system may be configured to not respond to ping requests. Therefore, the lack of a response to a ping command does not mean a system is not connected to a network. A quick response to a ping command does indicate, however that a system is connected to a network Step 4 Test to see if the localhost machine will respond to four ping requests: ping -c4 localhost sysadmin@localhost:$ ping -c4 localhost PING localhost ( ) 56(84) bytes of data. 64 bytes from localhost ( ): icmp_req=1 ttl=64 time=0.045 ms 64 bytes from localhost ( ): icmp_req=2 ttl=64 time=0.028 ms 64 bytes from localhost ( ): icmp_req=3 ttl=64 time=0.032 ms 64 bytes from localhost ( ): icmp_req=4 ttl=64 time=0.040 ms --- localhost ping statistics packets transmitted, 4 received, 0% packet loss, time 2998ms rtt min/avg/max/mdev = 0.028/0.036/0.045/0.007 ms Unlike the ping command that is available in the Microsoft Windows operating system, the Linux ping command does not stop making requests by default. If you forget to specify the -coption, then you will have to manually stop the command by holding the Control key and pressing C (CTRL+C). Hostnames can also be used if they are registered with a Domain Name Service (DNS) server. If your system is connected to a network with DNS servers, then the nameserver entry in the /etc/resolv.conf file configures your system to use these servers to resolve hostnames into IP addresses Step 5 View the /etc/resolv.conf file to see if any nameserver entries exists: cat /etc/resolv.conf The output should show one nameserver entry: sysadmin@localhost:$ cat /etc/resolv.conf nameserver Notice that the output of the first route command, names were provided for some items (like *). In the output of the second route command, numbers were provided in place of names, the result of using the -n option to the route command.
42 Step 6 Use the dig command to resolve the localhost.localdomain name to an IP address: dig localhost.localdomain sysadmin@localhost:$ dig localhost.localdomain ; <<>> DiG P1 <<>> localhost.localdomain ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 0 ;; QUESTION SECTION: ;localhost.localdomain. IN A ;; ANSWER SECTION: localhost.localdomain IN A ;; AUTHORITY SECTION: localdomain IN NS localhost.localdomain. ;; Query time: 803 msec ;; SERVER: #53( ) ;; WHEN: Mon Apr 11 13:33: ;; MSG SIZE rcvd: 69 Notice the output shows that the first nameserver that was listed in the /etc/resolv.conffile is the one that responded with the answer in the ANSWER SECTION of the output Step 7 You can use the dig command to resolve other fully qualified domain names. Use the digcommand to resolve the cserver.example.com hostname to an IP address: dig cserver.example.com sysadmin@localhost:$ dig cserver.example.com ; <<>> DiG P1 <<>> cserver.example.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1 ;; QUESTION SECTION: ;cserver.example.com. IN A ;; ANSWER SECTION: cserver.example.com IN A ;; AUTHORITY SECTION: example.com IN NS example.com. ;; ADDITIONAL SECTION: example.com IN A ;; Query time: 990 msec ;; SERVER: #53( ) ;; WHEN: Mon Apr 11 13:45: ;; MSG SIZE rcvd: 83 A fully qualified domain name (FQDN) includes not just the hostname, but also the domain that the hostname is "in". For the FQDN cserver.example.com, cserver is the hostname and example.com is the domain Step 8 Use the dig command to resolve the IP address to a hostname: dig -x sysadmin@localhost:$ dig -x ; <<>> DiG P1 <<>> -x ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 1, ADDITIONAL: 1 ;; QUESTION SECTION: ; in-addr.arpa. IN PTR ;; ANSWER SECTION: in-addr.arpa IN PTR cserver.example.com in-addr.arpa IN PTR example.com. ;; AUTHORITY SECTION: in-addr.arpa IN NS example.com. ;; ADDITIONAL SECTION: example.com IN A ;; Query time: 0 msec ;; SERVER: #53( ) ;; WHEN: Mon Apr 11 13:57: ;; MSG SIZE rcvd: Step 9 The netstat command performs a large variety of tasks related to networking. To get an idea of some of its capabilities, execute the command with the --help option: netstat --help sysadmin@localhost:$ netstat --help usage: netstat [-vweennccf] [<Af>] -r netstat {-V --version -h --help netstat [-vwnncaeol] [<Socket>...] netstat { [-vweennac] -i [-cwnne] -M -s } -r, --route display routing table -i, --interfaces display interface table -g, --groups display multicast group memberships -s, --statistics display networking statistics (like SNMP -M, --masquerade display masqueraded connections -v, --verbose -W, --wide -n, --numeric --numeric-hosts --numeric-ports --numeric-users -N, --symbolic -e, --extend -p, --programs be verbose don't truncate IP addresses don't resolve names don't resolve host names don't resolve port names don't resolve user names resolve hardware names display other/more information display PID/Program name for sockets
43 One of the common uses of netstat is to determine which services are listening to or waiting for an incoming connection. For example, a service that is used to allow users to perform remote or network logins is called Secure SHell or SSH. SSH normally will listen to TCP port 22. Well-known ports are the port numbers in the range of , typically used by system processes to provide network services. A list of service names and associated port numbers can be found in the /etc/services file Step 10 Use the netstat command to see if the TCP port for ssh, 22, has a process listening: netstat -tl netstat -tln sysadmin@localhost:$ netstat -tl Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 example.com:domain *:* LISTEN tcp 0 0 localhost:domain *:* LISTEN tcp 0 0 *:ssh *:* LISTEN tcp 0 0 localhost:953 *:* LISTEN tcp6 0 0 [::]:domain [::]:* LISTEN tcp6 0 0 [::]:ssh [::]:* LISTEN tcp6 0 0 localhost:953 [::]:* LISTEN Step 11 The -t option to the netstat command limits the listing to TCP ports; the -l option limits the output to ports with listening services; the -n shows the network addresses numerically: sysadmin@localhost:$ netstat -ltn Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp : :* LISTEN tcp : :* LISTEN tcp : :* LISTEN tcp : :* LISTEN tcp6 0 0 :::53 :::* LISTEN tcp6 0 0 :::22 :::* LISTEN tcp6 0 0 ::1:953 :::* LISTEN Chapter User Accounts There are several text files in the /etc directory that contain the account data of the users and groups that are defined on the system. For example, if you wanted to see if a specific user account has been defined on the system, then the place to check is the /etc/passwd file. The /etc/passwd file defines some of the account information for user accounts. Oddly enough, the passwords for the accounts are not stored in the /etc/passwd file, as the file name implies, but rather the /etc/shadow file /etc/passwd File Each line of the /etc/passwd file relates to a user account. The following graphic shows the first ten lines of a typical /etc/passwd file: sysadmin@localhost:$ head /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/bin/sh bin:x:2:2:bin:/bin:/bin/sh sys:x:3:3:sys:/dev:/bin/sh sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/bin/sh man:x:6:12:man:/var/cache/man:/bin/sh lp:x:7:7:lp:/var/spool/lpd:/bin/sh mail:x:8:8:mail:/var/mail:/bin/sh news:x:9:9:news:/var/spool/news:/bin/sh Each line is separated into fields by colon characters. The fields from left to right are as follows: name:password placeholder:user id:primary group id:comment:home directory:shell The following table describes each of these fields in detail, using the first line of the output of the previous graphic (root:x:0:0:root:/root:/bin/bash): Field Example Description name root This is the name of the account. This name is used by the person when they log in to the system and when file ownership is provided with the ls - l command. Typically, the system uses the user ID (see below) internally and the account name is provided to make it easiest for regular users to refer to the account. The root account is normally a special administrative account. However, it is important to note that not all systems have a root account and that it is really the user id of 0(zero) that provides administrative privileges on the system. password placeholder x At one time, the password for the user was actually stored in this location, but now it is stored in the/etc/shadow file. The x in the password placeholder field indicates to the system that the password is not stored here, but rather in the /etc/shadow file. user id 0 Each account is assigned a user ID (UID). The UID is what really defines the account as the user name is normally not directly used by the system. For example, files are owned by UIDs, not by user names. Some UIDs are special. For example, the UID of 0 provides that user account with administrative privileges.
44 Field Example Description primary group id UIDs below 500 (on some Linux distributions 1,000) are reserved for system accounts. System accounts will be covered in more detail later in this chapter. 0 Each file and directory is owned by a user account. Normally the person who creates the account owns the file. In addition, each file is owned by a group, normally the user's primary group. Groups are assigned numeric IDs just like users are. When a user creates a file, the file is owned by the user's UID and also owned by a group id (GID), the user's primary GID. This field defines which GID is the user's primary GID. Besides, providing default group ownership on a file, this field also indicates that the user is a member of the group, which means the user will have special permissions on any file that is owned by this group. Permissions will be covered in detail in a later chapter. comment root This field can contain any information about the user, including their real (full) name and other useful information. This field is also called the GECOS (General Electric Comprehensive Operating System ) field. GECOS is a rarely used predefined format for this field that defines a comma-separated list of items, including the user's full name, office location, phone number and additional information. An administrator can modify GECOS information with the chfn command and users can display this information with the finger command. home directory /root This field defines the location of the user's home directory. For regular users, this would normally be /home/usernamewhere username is replaced with the user's username. For example, a username of bob would have a home directory of /home/bob. The root user normally has a different place for the home directory: /root. System accounts rarely have home directories as they typically are not used to create or store files. shell /bin/bash This is the location of the user's login shell. By default, the user is "placed in" this shell whenever the user logs into a command line environment or opens a terminal window. The user could then switch to a different shell by typing the name of the shell, for example: /bin/tcsh. The bash shell (/bin/bash) is the most common shell for Linux users. Note that while this chapter describes the contents of the user and group files, the next chapter will describe the commands and tools used to modify user and group account information /etc/shadow File As previously mentioned, the /etc/shadow file contains account information related to the user's password. A typical /etc/shadow file would look like the following graphic: root@localhost:# head /etc/shadow root:$6$4yga95h9$8hbxqsmeibtz0yomlmffycv9ve1sq4t2h3shxw41m02sqtfaddve9mqgp2hr20q.zuncjplywkywqdklsjys8.:16464:0:99999:7::: daemon:*:16463:0:99999:7::: bin:*:16463:0:99999:7::: sys:*:16463:0:99999:7::: sync:*:16463:0:99999:7::: games:*:16463:0:99999:7::: man:*:16463:0:99999:7::: lp:*:16463:0:99999:7::: mail:*:16463:0:99999:7::: news:*:16463:0:99999:7::: root@localhost:# The fields of the /etc/shadow file are: name:password:last change:min:max:warn:inactive:expire:reserved The following table describes the fields of the /etc/shadow file in more detail, using the following account that describes a typical user account: sysadmin:$6$ls6wj9o/fnmezrii$ko9nkrbjljjtlzd.l1dc2xwcuuyaywcts.gt4elijsqw8zdp6glyax.trnnpudagu XUrzDuAPsYs5YHZNAorI1:15020:5:30:7:60:15050: Field Example Description name sysadmin This is the name of the account, which matches the account name in the /etc/passwd file. password $6$...rI1 The password field contains the encrypted password for the account. This very long string (which was truncated in the example to the left of this cell) is a oneway encryption, meaning that it can't be "reversed" to determine the original password. While regular users have encrypted passwords in this field, system accounts will have an * character in this field. See more details about system accounts later in this chapter. last change This field contains a number that represents the last time the password was changed. The number is the number of days since January 1, 1970 (called the Epoch) and the last day the account password was changed. This value is automatically generated when the user's password is modified. This value is important as it is used by the password aging features provided by the rest of the fields of this file. min 5 This is one of the password aging fields; a non-zero value in this field indicates that after a user changes their password, the password can't be changed again for the specified number of days (5 days in this example). This field is important when the max field is used (see below). A value of zero in this field means the user can always change their password. max 5 This field is used to force users to change their passwords on a regular basis. A value of 30 in this field means the user must change their password at least every 30 days to avoid having their account "locked out". Note that if the min field is set to 0, the user may be able to immediately set their password back to the original value, defeating the purpose of forcing the
45 Field Example Description user to change their password every 30 days. So, if the maxfield is set, the min field is normally set as well. For example, a min:max of 5:60 means the user must change their password every 60 days and, after changing, the user must wait 5 days before they can change their password again. If the max field is set to 99999, the maximum possible value, then the user essentially never has to change their password (because days is approximately 274 years). warn 7 If the max field is set, the warn field indicates that the user would be "warned" when the max timeframe is approaching. For example, if warn is set to 7, then any time during the 7 days before the max timeframe is reached, the user would be warned to change their password during the login processes. The user is only warned at login, so some administrators have taken the approach to set the warn field to a higher value to provide a greater chance of having a warning issued. If the max timeframe is set to 99999, then the warnfield is essentially useless inactive 60 If the user ignores the warnings and they exceed the max password timeframe, their account will be locked out. In that case, the inactive field provides the user with a "grace" period in which their password can be changed, but only during the login process. If the inactive field is set to 60, the user has 60 grace days to change to a new password. If they fail to do so, then the administrator would be needed to reset the password for the user. expire This field represents the number of days from January 1, 1970 and the day the account will "expire". An expired account will be locked, not deleted, meaning the administrator can reset the password to unlock the account. Accounts with expiration dates are normally provided to temporary employees or contractors. The account will automatically expire after the user's last day of work. When an administrator sets this field, a tool is used to convert from a real date to an "Epoch" date. There are also several free converters available on the Internet. reserved Currently not used, this field is reserved for future use. Regular users can't view the contents of the /etc/shadow file for security reasons. In order to view the contents of this file, you must log in as the administrator (the root account) Viewing Account Information A good way to view account information from the /etc/passwd file is to use the grep command to output just the line containing the account that you are interested in. For example, to see the account information for the user name named sysadmin, use the grep sysadmin /etc/passwd command: sysadmin@localhost:$ grep sysadmin /etc/passwd sysadmin:x:1001:1001:system Administrator,,,,:/home/sysadmin:/bin/bash Another technique for retrieving user information that is normally contained in the /etc/passwdand /etc/shadow files is to use the getent command. One advantage to using the getentcommand is that it can retrieve account information that is defined locally (/etc/passwd and /etc/shadow) or on a network directory server. The general syntax of a getent command is: getent database record. For example, the getent passwd sysadmin command would retrieve the passwd account information for the sysadmin user: sysadmin@localhost:$ getent passwd sysadmin sysadmin:x:1001:1001:system Administrator,,,,:/home/sysadmin:/bin/bash Viewing Login Information When you log into different user accounts, it can be confusing as to who you are currently logged in as. To verify your identity (view whose account you are currently using) you can execute the idcommand. The id command will report the current identity, both by user name and user ID. In addition to providing the user account information, the group membership is also displayed. With no argument, the id command will display your identity. Given a user name as an argument, such as id root, the command will display other account information: sysadmin@localhost:$ id uid=1001(sysadmin) gid=1001(sysadmin) groups=1001(sysadmin),4(adm),27(sudo) context=unconfined_u:uncon fined_r:unconfined t:s0-s0:c0.c1023 sysadmin@localhost:$ sysadmin@localhost:$ id root uid=0(root) gid=0(root) groups=0(root) The output includes Security Enhanced Linux context (the context= part of the output), a topic which is beyond the scope of this course System Accounts Users will log into the system using regular user accounts. Typically, these accounts have UID values of greater than 500 (on some systems 1,000). The root user has special access to the system. As previously mentioned, this special access is actually provided to the account with a UID of 0. There are additional accounts that are not designed for users to log into. These accounts, typically from UID 1 to UID 499, are called system accounts and they are designed to provide accounts for services that are running on the system. System accounts have some fields in the /etc/passwd and /etc/shadow files that are different than other accounts. For example, in the /etc/passwd file, system accounts will have a non-login program in the "login shell" field: bin:x:1:1:bin:/bin:/sbin:/sbin/nologin In the /etc/shadow file, system accounts will typically have an * character in place of the password field: bin:*:15513:0:99999:7::: There are a few important things that you should remember about system accounts: Most are necessary for the system to function correctly. You should not delete a system account unless you are absolutely certain that removing the account won't cause problems. As you gain more experience, you should learn what each system account does. System administrators are tasked with ensuring the security on the system and that includes properly securing the system accounts.
46 13.3 Group Accounts Your level of access to a system is not determined solely by your user account. Each user can be a member of one or more groups, which can also affect your level of access to the system. Traditionally, UNIX systems limited users to belonging to no more than a total of sixteen groups, but the recent Linux kernels support users with over sixty-five thousand group memberships. As you have already seen, the /etc/passwd file defines the primary group membership for a user. Supplemental group membership (or secondary group membership), as well as the groups themselves, is defined in the /etc/group file. To view information about a specific group, either the grep or getent commands can be used. For example, the following commands will display the mail group account information: sysadmin@localhost:$ grep mail /etc/group mail:x:12:mail,postfix sysadmin@localhost:$ getent group mail mail:x:12:mail,postfix /etc/group File The /etc/group file is a colon delimited file with the following fields: group_name:password_placeholder:gid:user_list The following table describes the fields of the /etc/group file in more detail, using a line that describes a typical group account: mail:x:12:mail,postfix Field Example Description group_name mail This field contains the group name. As with user names, group names are easier for people to remember. The system typically uses Group IDs (GIDs) rather than group names. password_placeholder x While there are passwords for groups, they are rarely used in Linux. In the event that the administrator makes a group password, it would be stored in a different file (/etc/gshadow) because the group password is no longer stored in the /etc/group file. The x in this field is used to indicate that the password is not stored in this file. Group passwords are beyond the scope of this course. GID 12 Each group is associated with a unique Group ID (GID) which is placed in this field. user_list mail,postfix This last field is used to indicate who is a member of the group. While primary group membership is defined in the /etc/passwdfile, users who are assigned to additional groups would have their user name placed in this field of the /etc/group file. In this case, the mail and postfix users are secondary members of the mail group. Field Example Description It is very common for a user name to also appear as a group name. It is also common for a user to belong to a group with the same name Viewing Group Information Groups are primarily used for controlling access to files. By default, any new file that a user creates will be owned by the user's primary group. The id command can be used to verify the user's primary group: sysadmin@localhost:$ id -g 1001 Users can also access files and devices if they are members of secondary groups. The idcommand can also be used to verify the user's secondary group memberships: sysadmin@localhost:$ id -G Without passing any options to the command, id lists both primary and secondary group memberships: sysadmin@localhost:$ id uid=1001(sysadmin) gid=1001(sysadmin) groups=1001(sysadmin),4(adm),27(sudo) A username can be added to determine the groups of a specific user: sysadmin@localhost:$ id sysadmin uid=1001(sysadmin) gid=1001(sysadmin) groups=1001(sysadmin),4(adm),27(sudo) This aligns with the content of the /etc/group file, as a search for sysadmin reveals: sysadmin@localhost:$ cat /etc/group grep sysadmin adm:x:4:sysadmin sudo:x:27:sysadmin sysadmin:x:1001: Changing the Group Ownership of an Existing File To change the group owner of an existing file the chgrp group_name file command can be used. Users can only change the ownership of files that they own. The new group owner of the file must also be a group that the user is a member of: sysadmin@localhost:$ touch sample sysadmin@localhost:$ ls -l sample -rw-rw-r-- 1 sysadmin sysadmin 0 Dec 10 00:44 sample sysadmin@localhost:$ chgrp games sample -rw-rw-r--. 1 sysadmin games 0 Oct 23 22:12 sample To change the group ownership of all of the files of a directory structure, use the -R option to the chgrp command. For example, the chgrp -R games test_dir command would change the group ownership of the test_dir directory and all files and sub directories of the test_dirdirectory. There is also a chown command that can be used to change the user owner of a file or directory. However, this command can only be used by the root user. Regular users can't "give" their files to another user.
47 13.4 Logging In As Root There are many different ways to execute a command that requires administrative or root privileges. As already mentioned, logging in to the system as the root user allows you to execute commands as the administrator. This is potentially dangerous because you may forget that you are logged in as root and might run a command that could cause problems on the system. As a result, it is not recommended to login as the root user directly. Because using the root account is potentially dangerous, you should only execute commands as root if administrative privileges are needed. If the root account is disabled, as it is on the Ubuntu distribution, then administrative commands can be executed using the sudo command. If the root account is enabled, then a regular user can execute the su command to switch accounts to the root account. When you login to the system directly as root to execute commands, then everything about your session runs as the root user. If using the graphical environment, this is especially dangerous as the graphical login process is comprised of many different executables (programs that run during login). Each program that runs as the root user represents a greater threat than a process run as a standard user, as those programs would be allowed to do nearly anything, whereas standard user programs are very restricted in what they can do. The other potential danger with logging into the system as root is that a person that does this may forget to log out to do their non-administrative work. This means that programs such as browsers, clients, etc. would be run as the root user without restrictions on what they could do. The fact that several distributions of Linux, notably Ubuntu, do not allow users to login as the root user should be enough implication that this is not the preferred way to perform administrative tasks Using the su Command The su command allows you to run a shell as a different user. By default, if a user account is not specified, the su command will open a new shell as the root user. While switching to the root user is what the su command is used for most frequently, it can also switch to other users as well. One common option that is used with the su command is the -l option, which results in the new shell being a login shell. Using the su command with a login shell option is often important to ensuring that any commands executed will run correctly, as the login shell fully configures the new shell with the settings of the new user. A non-login shell essentially just changes the UID, but doesn't fully log the user in. The -l option can be abbreviated as simply - or spelled out as --login. Since the root account is used by default with the su command, the following two commands are equivalent ways to start a shell as the root user: su - root su - After pressing Enter to execute either one of these commands, the user must provide the password of the root user to start the shell as the root user. If you don't know the password of the account that you are shifting to, then the su command will fail. After using the shell started by the su command to perform the necessary administrative tasks, return to your original shell (and original user account) by using the exit command. sysadmin@localhost:$ su - Password: root@localhost:# id uid=0(root) gid=0(root) groups=0(root) root@localhost:# exit logout sysadmin@localhost:$ id uid=1001(sysadmin) gid=1001(sysadmin) groups=1001(sysadmin),4(adm),27(sudo) 13.6 Using the sudo Command In distributions that do not allow the root user to login directly or via the su command, the installation process automatically configures one user account to be able to use the sudocommand to execute commands as if they were executed by the root user. Like the su command, the sudo command assumes by default the root user account should be used to execute commands; to specify a different user account use the -u option. When using the sudo command to execute a command as the root user, the command will prompt for the user's own password (not that of the root user). This is a security feature that would prevent unauthorized root access if the user were to leave their computer unattended. The prompt for the password will not appear again as long as the user continues to execute sudo commands less than five minutes apart. Using the sudo command to execute an administrative command will result in an entry placed in a log file. This entry will include the user name who executed the command, the command that was executed and the date and time when the comment was executed. This allows for increased accountability, compared to a system where many users might know the root password and can either login directly as root or use the su command to execute commands as the root user. You can use the sudo command to execute a command that requires root privileges. For example, you need to be the root user in order to view the /etc/shadow file. The sudo head /etc/shadow command would run the head command as the root user: sysadmin@localhost:$ head /etc/shadow head: cannot open `/etc/shadow' for reading: Permission denied sysadmin@localhost:$ sudo head /etc/shadow [sudo] password for sysadmin: root:$6$4yga95h9$8hbxqsmeibtz0yomlmffycv9ve1sq4t2h3shxw41m02sqtfaddve9mqgp2hr20q.zuncjplywkywqdklsjys8.:16464:0:99999:7::: daemon:*:16463:0:99999:7::: bin:*:16463:0:99999:7::: sys:*:16463:0:99999:7::: sync:*:16463:0:99999:7::: games:*:16463:0:99999:7::: man:*:16463:0:99999:7::: lp:*:16463:0:99999:7::: mail:*:16463:0:99999:7::: news:*:16463:0:99999:7::: sysadmin@localhost:$ One big advantage to using sudo to execute administrative commands is that it reduces the risk that a user accidentally executes a command as root. The intention to execute a command is clear; the command is executed as root if prefixed with the sudo command. Otherwise, the command is executed as a regular user Setting Up the sudo Command If the sudo command is not automatically configured during installation, it can be configured to work manually post-install. Initially, this would require logging in as the root user (or using the sucommand to switch to the root account), but after it has been configured, specified users will be able to run sudo commands. You set up access to the sudo command by running the visudocommand. The visudo command will place you in an editor program, by default the vi (or vim) editor on most systems, which can be challenging for novice Linux users to use. To configure another editor, export the EDITOR variable with the value of the editor you would prefer. For example, to use the gedit editor instead of vi/vim, you would execute the export EDITOR=gedit command before you would execute the visudo command. Using the visudo command will open the /etc/sudoers configuration file for editing. Although advanced configurations of the sudo command are possible through this file, they are beyond the scope of this course. Basically, entries are made into this file to specify which user(s) on which machines can use the sudo command to execute commands as other users. This default entry... root ALL=(ALL) ALL
48 ...could be read as, "the root user can on ALL machines act as ALL users to execute ALL commands." To allow a user such as sysadmin to execute all commands as all users using the sudo command, an entry like the following could be added: sysadmin ALL=(ALL) ALL 13.7 Using the who Command The who command displays a list of users who are currently logged into the system, where they are logged in from and when they logged in. Through the use of options, this command is also able to display information such as the current run level (a functional state of the computer) and the time that the system was booted. For example: sysadmin@localhost:$ who root tty :00 sysadmin tty :58 (:0) sysadmin pts/ :59 (:0.0) sysadmin pts/ :00 (example.com) The following table describes the output of the who command: Column Example Description username root This column indicates the name of the user who is logged in. Note that by "logged in" we mean "any login process and any open terminal window". terminal tty2 This column indicates which terminal window the user is working in. If the terminal name starts with tty, then this is an indication of a local login, as this is a regular command line terminal. If the terminal name starts with pts, then this indicates the user is using a pseudo terminal or running a process that acts like a terminal. This can mean the user has a terminal application running in X Windows, such as gnome-terminal or xterm or they may have used a network protocol to connect to the system, such as ssh or telnet. date :00 (example.com) This indicates when the user logged in. After the date and time the user logged into the system, some location information may appear. If the location information contains a host name, domain name or IP address, then the user has logged in remotely. If there is a colon and a number, then this indicates that they have performed a local graphical login. If no location information is shown in the last column, then this means the user logged in via a local command line process. If you want to display system status information, the who command can do that by using several options. For example, the -b option will show the last time the system started (was booted) and the -r option will show the time the system reached a certain run-level: The w command provides a more detailed list about the users currently on the system than the who command. It also provides a summary of the system status. For example: sysadmin@localhost:$ w 10:44:03 up 50 min, 4 users, load average: 0.78, 0.44, 0.19 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT root tty2-10:00 43: s 0.01s -bash sysadmin tty1 :0 09:58 50: s 0.16s pam: gdm-password sysadmin pts/0 :0.0 09: s 0.14s 0.13s ssh sysadmin pts/1 example.com 10: s 0.03s 0.01s w The first line of output from the w command is identical to that of the uptime command. It shows the current time, how long the system has been running, the total number of current logins (users) and the load on the system averaged over the last 1, 5 and 15 minute time periods. Load average is CPU utilization where a value of 100 would mean full CPU usage during that period of time. The following table describes the rest of the output of the w command: Column Example Description USER root This column indicates the name of the user who is logged in. TTY tty2 This column indicates which terminal window the user is working in. FROM example.com Where the user logged in from. LOGIN@ 10:00 When the user logged in. IDLE 43:44 How long the user has been idle since the last command they ran. JCPU 0.01s The total cpu time (s=seconds) used by all processes (programs) run since login. PCPU 0.01s The total cpu time for the current process. WHAT -bash The current process that the user is running. sysadmin@localhost:$ who -b -r system boot :54 run-level : Using the w Command
49 Lab 13 User and system accounts are defined in the /etc/passwd and /etc/shadow files. View the first ten lines from the /etc/passwd file: head /etc/passwd Your output should be similar to the following: head /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/bin/sh bin:x:2:2:bin:/bin:/bin/sh sys:x:3:3:sys:/dev:/bin/sh sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/bin/sh man:x:6:12:man:/var/cache/man:/bin/sh lp:x:7:7:lp:/var/spool/lpd:/bin/sh mail:x:8:8:mail:/var/mail:/bin/sh news:x:9:9:news:/var/spool/news:/bin/sh Notice that this file contains a colon delimited database of all user and system accounts available on this system. User accounts are assigned to users, to allow them access to the operating system. The sysadmin account that you used to log in to the system is a typical user account. The root account is a special user account that has virtually unlimited access and control over the system. It is sometimes referred to as the "superuser" account. System accounts are used by the operating system or services running processes on it. By not having these services run as the root user, the system is kept more secure by limiting the damage that a comprised service account could cause. System accounts are never used directly by regular users Step 2 Use the grep command to view the record for your sysadmin account: grep sysadmin /etc/passwd sysadmin@localhost:$ grep sysadmin /etc/passwd sysadmin:x:1001:1001:system Administrator,,,,:/home/sysadmin:/bin/bash sysadmin@localhost:$ By using the grep command, the output only includes the account information for that one username. Another way to retrieve the account information for a user is by running the following command: getent passwd username. The getent command has the advantage over the grep command as it is also able to access user accounts that are not defined locally. In other words, the getent command is able to get user information for users who may be defined on network directory servers such as LDAP, NIS, Windows Domain, or Active Directory Domain servers Step 3 Use the getent command to retrieve the information about the sysadmin: getent passwd sysadmin sysadmin@localhost:$ getent passwd sysadmin sysadmin:x:1001:1001:system Administrator,,,,:/home/sysadmin:/bin/bash sysadmin@localhost:$ Note: In this case we don't have any network accounts, so the output displayed is just like looking at the /etc/passwd file Step 4 You can view the documentation of the fields in the /etc/passwd file with the following command: man 5 passwd Remember while viewing a man page, press Enter to move forward line by line, Spacepage by page and q to quit. The colon delimited /etc/passwd file has the following fields: account:password:uid:gid:gecos:directory:shell A breakdown of these fields: a. The account field is the username. b. This field was originally used to store the password, however, it is now typical for the password to be stored in the etc/shadow file. The x is serving as a placeholder. c. The UID is user's identification number. d. The GID is the user's primary group identification number. e. GECOS is the field that is typically used to store the full name of the user. f. The directory is the home directory of the user, where they are placed upon first logging into the system. g. The shell field defines the shell such as /bin/bash for a normal user, or /sbin/nologin for an account used by the system or a service Step 5 You can view account information for your account, or a specified user account, using the id command: id id root sysadmin@localhost:$ id uid=1001(sysadmin) gid=1001(sysadmin) groups=1001(sysadmin),4(adm),27(sudo sysadmin@localhost:$ id root uid=0(root) gid=0(root) groups=0(root) The output of the commands shows your user identity as a number and name: uid=1001(sysadmin). It also displays your primary group identity, gid=1001(sysadmin), and all the groups that you belong to, groups=1001(sysadmin), 4(adm) and 27(sudo). In this case, your user account only belongs to three groups. The file /etc/group, together with /etc/passwd, determines your group memberships. Your default primary group is determined by matching your GID found in /etc/passwd to the GID defined for a group in the /etc/group. Any secondary group memberships are defined in the /etc/group file. The format of entries in the /etc/group file for each line is: group_name:password:gid:user_list Step 6 The getent command can retrieve information about entries in the /etc/group file. Use getent to retrieve information about the sysadmin and adm groups: getent group sysadmin getent group adm sysadmin@localhost:$ getent group sysadmin sysadmin:x:1001: sysadmin@localhost:$ getent group adm adm:x:4:sysadmin
50 Groups are used for controlling access to files. By default any new file that you create will be owned by your primary group. To have any new files you create owned by one of your secondary groups, use the newgrp command. The basic format for this command is newgrp group_name. You must be a member of a group to use the newgrp command. The id command will then display that group_nameas your primary group. To change the group owner of one of the existing files that your user owns, you can use the chgrp command. The basic format for this command is chgrp group_name file_name You must be a member of a group to change a file group ownership to that group and you must own the file Step 7 Two commands with simple output for understanding your identity are whoami and groups. The groups command can also be used get the list of groups for another user. Use the whoami and groups command for your account and the groups command for the root user: whoami groups groups root sysadmin@localhost:$ whoami sysadmin sysadmin@localhost:$ groups sysadmin adm sudo sysadmin@localhost:$ groups root root : root sysadmin@localhost:$ Step 1 Use the who command to get the current list of users on the system: who sysadmin@localhost:$ who sysadmin tty Apr 11 14:32 sysadmin@localhost:$ The output of the who command has four columns: Username: the first column shows the name of the user (sysadmin in the example above). Terminal: the second column shows an identifier for a terminal type (tty in the example above). Each terminal has a separate name that is used by the superuser to control processes. Date/Time: the third column is the date and time that the login was initiated (Apr 11 14:32 in the first line of output in the example above). Host: although there is no output for the fourth column in this case, it can be the name or IP address of a local or remote host. The following forms indicate local logins: (:#) or (:#.#). Otherwise, a remote host may be shown by name (if resolvable) or by IP address Step 2 Use the w command to get a more detailed view of the users who are currently on your system: w Your output from the w command displays: sysadmin@localhost:$ w 15:17:08 up 6 days, 15 min, 1 user, load average: 0.39, 0.34, 0.37 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT sysadmin console 14: s 0.16s 0.00s w sysadmin@localhost:$ A summary of how long the system has been running, how many users are logged in and the system load averages for the past 1, 5, and 15 minutes. An entry for each user with their login name, tty name, host, login time, idle time, JCPU (CPU time used by background jobs), PCPU (CPU time used by the current process) and what is executing on the current command line The root user In this task, you will learn how to access the root user account in a couple of different ways. The account of the root user is special in Linux as it has a practically unlimited amount of control and access to the system. It's actually not the name of the user, but the UID with a value of zero that grants this authority. In general, it is not considered a good practice to login to the system as the root user. This is especially true of the graphical environment. To access the root user account, the su or sudo commands are normally used. The su command usually is used to switch users to start a new shell as another user; the default being the root user. The su command is normally used when a series of commands need to be executed as the root user. The sudo command is typically used to execute a single command as the root user by prefixing that command with sudo. The sudo command must be configured by the root user before an ordinary user can use it Step 1 To set up the sudo command for regular users, use the visudo command. This requires root access as the visudo command will fail when regular users execute the command. Attempt to configure access to the sudo command: visudo sysadmin@localhost:$ visudo visudo: /etc/sudoers: Permission denied visudo: /etc/sudoers: Permission denied sysadmin@localhost:$ The output shows that the visudo command failed because it attempts to modify the /etc/sudoers file, a file that regular users can't modify due to permissions. This file controls access to the sudo command and should never be modified directly, but rather with the visudo command Step 2 Switch users to the root user and provide the root password of netlab123 when prompted: su - netlab123 sysadmin@localhost:$ su - Password: root@localhost:# The dash or hyphen after the su command is an abbreviation for the option -l, which makes the login performed by su a complete login by executing the login scripts belonging to the root user. Without the -, or -l, the su command will switch your user identity, but it will not execute the login scripts of the new user. This can cause some problems, especially when switching to the root account. In most cases when you switch users you want a complete login to be performed so that environment variables, functions and aliases that are normally initialized for a user will be initialized Step 3 Now that you are logged in as the root user, you should be able to execute the command to configure sudo access: visudo root@localhost:# visudo
51 Step 4 To enable basic access to the use of the sudo command, an entry must be added to the /etc/sudoers file that you are now editing. Since you are in the vi editor by default, type the following to find this entry: What to Type G o sysadmin ALL=(ALL) ALL ESC :wq Meaning Go to the end of the file Open a new line below cursor The entry permitting sysadmin sudo access The Escape key returns to command mode Save changes and exit -rw-r root shadow 838 Mar 14 17:34 /etc/shadow Step 8 Use the sudo command to view the first few lines of /etc/shadow file: sudo head -3 /etc/shadow (provide the password of the sysadmin user: netlab123) sysadmin@localhost:$ sudo head -3 /etc/shadow [sudo] password for sysadmin: root:$6$t3w2rbrt$n/2jrt1ezq8tqovxwkyjepif3tcbpoyfwu7zyktoosxb4agmtb0.w6f8gb7vmihnj76yzeznpw MbTGoQFs5Kx1:16874:0:99999:7::: daemon:*:16863:0:99999:7::: bin:*:16863:0:99999:7 Important Note: The password that you provided was for your sysadmin account, not the root account. Once sudo has been configured for your account, you don't need to know the root password to run sudo commands as the root user. #includedir /etc/sudoers.d sysadmin ALL=(ALL) ALL -- INSERT -- If you type the data into the file correctly, you should be placed back at a shell prompt. However, if upon exiting the edit, you are presented with a prompt that says "What now?", then press Enter to see your choices. It is recommended that you type x to exit without saving changes to the sudoers file and repeat this step over Step 5 Return to the sysadmin account to verify that sudo provides root access by typing the following: exit root@localhost:# exit logout Step 6 Try to view the first few lines of /etc/shadow file, a file that contains the users' encrypted passwords and information about aging them: head -3 /etc/shadow sysadmin@localhost:$ head -3 /etc/shadow head: cannot open `/etc/shadow' for reading: Permission denied Notice the error message the head command displays. This is because the sysadminuser has no rights to view this file. The root user, however, can display this file Step 7 Notice that the permissions on the /etc/shadow file indicate that only members of the shadow group have permission to view the file: ls -l /etc/shadow Keep in mind that the root user can view any file. This is due to the root account having special privileges that transcend regular file permissions. sysadmin@localhost:$ ls -l /etc/shadow
52 Chapter Creating a Group The most common reason to create a group is to provide a way for users to share files. An example of this might be where there are several people who work together on the same project and need to be able to collaborate on documents stored in files for the project. In this scenario, the administrator can make these people members of a common group, change the directory ownership to the new group and set permissions on the directory that will only allow members of the group to access the files. After creating or modifying a group, you can verify the changes by viewing the group configuration information in the /etc/group file with the grep command. If working with network-based authentication services, then the getent command can show you both local and network-based groups. For local usage, these commands show the same result, in this case for the root group: root@localhost:# grep root /etc/group root:x:0: root@localhost:# getent group root root:x:0: The groupadd command can be executed by the root user to create a new group. The command requires only the name of the group to be created. The -g option can be used to specify a group id for the new group: root@localhost:# groupadd -g 506 research root@localhost:# grep research /etc/group research:x:506: If the -g option is not provided, the groupadd command will automatically provide a GID for the new group. To accomplish this, the groupadd command looks at the /etc/group file and uses a number that is one value higher than the current highest GID number. The execution of the following commands illustrates this: root@localhost:# grep research /etc/group research:x:506: root@localhost:# groupadd development root@localhost:# grep development /etc/group development:x:507: Group ID Considerations In some Linux distributions, particularly those based upon Red Hat, when a user ID (UID) is created, a user private group (UPG) is also created with that user as its only member. In these distributions, the user's UID and the private group id are supposed to match (be the same number). Therefore, you should avoid creating GIDs in the same numeric ranges where you expect to create user IDs (UIDs), in order to avoid a conflict between a GID you create vs. a UPG number that is created to match a UID. Recall that GIDs under 500 are reserved for system use. There may be times in which you want to assign a GID under 500. To accomplish this, use the -r. The -r option will assign the new group a GID that will be less than the lowest standard UID: root@localhost:# groupadd -r sales root@localhost:# getent group sales sales:x:491: Group Naming Considerations Following these guidelines for group names will help you to select a group name that will be portable (function correctly with other systems or services): The first character of the name should be either an underscore _ or a lower-case alphabetic character a-z. Up to 32 characters are allowed on most Linux distributions, but using more than 16 can be problematic as some distributions may not accept more than 16. After the first character, the remaining characters can be alphanumeric, the dash -or an underscore_. The last character should not be a hyphen -. Unfortunately, these guidelines are not always enforced. The problem isn't that the groupadd command will necessarily fail, but that other commands or system services may not work correctly Modifying a Group The groupmod command can be used to either change the name of the group (with the -n option) or change the GID (with the -g option) for the group. WARNING: Changing the name of the group may cause confusion for users who were familiar with the old name and haven't been informed of the new name. However, changing the group name won't cause any problems with accessing files, since the files are really owned by GIDs, not group names. For example: root@localhost:# ls -l index.html -rw-r root sales 0 Aug 1 13:21 index.html root@localhost:# groupmod -n clerks sales root@localhost:# ls -l index.html -rw-r root clerks 0 Aug 1 13:21 index.html After the previous groupmod command, the index.html file has a different group owner name. However, all users who were in the sales group are now in the clerks group, so all of those users can still access the index.html file. Again, this is because the group is defined by the GID, not the group name. On the other hand, if you change the GID for a group, then all files that were associated with that group will no longer be associated with that group. In fact, all files that were associated with that group will no longer be associated with any group name. Instead, these files will be owned by a GID only, as shown below: root@localhost:# groupmod -g clerks root@localhost:# ls -l index.html -rw-r root Aug 1 13:21 index.html These files with no group name are called "orphaned" files. As the root user, you may want to search for all files that are owned by just a GID (not associated with a group name). This can be accomplished with the - nogroup option to the find command: root@localhost:# find / -nogroup /root/index.html 14.4 Deleting a Group If you decide to delete a group with the groupdel command, be aware that any files that are owned by that group will become "orphaned". Only supplemental groups can be deleted, so if a group is the primary group for any user, it cannot be deleted. The administrator can modify which group is a user's primary group, so a group that was being used as a primary group can be made into a supplemental group and then can be deleted. As long as the group to be deleted is not a user's primary group, deleting the group is accomplished by using the groupdel command along with the name of the group: root@localhost:# groupdel clerks
53 14.5 /etc/default/useradd File Before you begin creating users for your system, you should verify or establish practical values that will be used by default with the useradd command. This can be accomplished by modifying settings in the configuration files that are used by the useradd command. Ensuring that the values in these configuration files are reasonable before adding users can help you to save time and the trouble of having to correct user account settings after adding the users. The -D option to the useradd command will allow you to view or change some of the default values used by the useradd command. The values shown by useradd -Dcan also be viewed or updated by manipulating the /etc/default/useradd file: useradd -D GROUP=100 HOME=/home INACTIVE=-1 EXPIRE= SHELL=/bin/bash SKEL=/etc/skel CREATE_MAIL_SPOOL=yes The following table describes each of these values: Field Example Description GROUP 100 In distributions not using UPG, this will be the default primary group for a new user, if one is not specified with the useradd command. This is normally the "users" group with a GID of 100. This setting affects the default setting of the /etc/passwd file highlighted below: bob:x:600:600:bob:/home/bob:/bin/bash The -g option to the useradd command allows you to use a different primary group than the default when creating a new user account. HOME /home The /home directory is the default base directory under which the user's new home directory will be created. This means that a user with an account name of bob would have a home directory of /home/bob. This setting affects the default setting of the /etc/passwd file highlighted below: bob:x:600:600:bob:/home/bob:/bin/bash The -b option to the useradd command allows you to use a different base directory group than the default when creating a new user account. INACTIVE -1 This value represents the number of days after the password expires that the account is disabled. A value of -1 means this feature is not enabled by default and no "inactive" value is provided for new accounts by default. This setting affects the default setting of the /etc/shadow file highlighted below in: bob:pw:15020:5:30:7:60:15050: Field Example Description EXPIRE The -f option to the useradd command allows you to use a different INACTIVE value than the default when creating a new user account. By default, there is no value set for the expiration date. Usually, an expiration date is set on an individual account, not all accounts by default. For example, if you had a contractor that was hired to work until the end of day on November 1, 2013, then you could ensure that they would be unable to login after that date by using the EXPIRE field. This setting affects the default setting of the /etc/shadow file highlighted below in red: bob:pw:15020:5:30:7:60:15050: The -e option to the useradd command allows you to use a different EXPIRE value than the default when creating a new user account. SHELL /bin/bash The SHELL setting indicates the default shell for user's when they login to the system. This setting affects the default setting of the /etc/passwd file highlighted below: bob:x:600:600:bob:/home/bob:/bin/bash The -s option to the useradd command allows you to use a different login shell than the default when creating a new user account. SKEL /etc/skel The SKEL value determines what "skeleton" directory will have its contents copied into the new users home directory. The contents of this directory are copied into the new user's home directory and the new user is given ownership of the new files. This provides administrators with an easy way to "populate" a new user account with key configuration files. The -k option to the useradd command allows you to use a different SKEL directory than the default when creating a new user account. CREATE_MAIL_SPOOL yes A "mail spool" is a file where incoming is placed. Currently the value for creating a mail spool is yes, which means that users by default are configured with the ability to receive and store local mail. If you are not planning on using local mail, then this value could be changed to no. To modify one of the useradd default values, the /etc/default/useradd file could be edited with a text editor. Another (safer) technique is to use the useradd -Dcommand. For example, if you wanted to allow users to have expired passwords that they could still login with for up to thirty days, then you could execute: root@localhost:# useradd -D -f 30 root@localhost:# useradd -D GROUP=100
54 HOME=/home INACTIVE=30 EXPIRE= SHELL=/bin/bash SKEL=/etc/skel CREATE_MAIL_SPOOL=yes 14.6 /etc/login.defs File The /etc/login.defs file also contains values that will be applied by default to new users you create with the useradd command. Unlike the /etc/default/useradd, which can be updated with the useradd -D command, the /etc/login.defs is usually edited directly by the administrator to alter its values. This file contains many comments and blank lines, so if you just want to view lines that are not comments or blank lines (the real configuration settings), then you can use the following grep command: grep -Ev '^# ^$' /etc/login.defs MAIL_DIR /var/spool/mail PASS_MAX_DAYS PASS_MIN_DAYS 0 PASS_MIN_LEN 5 PASS_WARN_AGE 7 UID_MIN 500 UID_MAX GID_MIN 500 GID_MAX CREATE_HOME yes UMASK 077 USERGROUPS_ENAB yes ENCRYPT_METHOD SHA512 MD5_CRYPT_ENAB no The above example represents a typical CentOS 6 distribution /etc/login.defs file with its values. The following table describes each of these values: Field Example Description MAIL_DIR /var/mail/spool The directory in which the user's mail spool file will be created. PASS_MAX_DAYS This setting determines the maximum number of days that a user can continue to use the same password. Since it defaults to days, or over 200 years, it effectively means users never have to change their password. Organizations with effective policies for maintaining secure passwords commonly change this value to 60 or 30 days. This setting affects the default setting of the /etc/shadow file highlighted below: bob:pw:15020:5:30:7:60:15050: PASS_MIN_DAYS 0 With this set to a default value of 0 (zero), the shortest time that a user is required to keep a password is zero days, which means that they can immediately change a password that they have just set. Field Example Description If the PASS_MIN_DAYS value was set to 3 days, then after setting a new password, the user would have to wait three days before they could change it again. This setting affects the default setting of the /etc/shadow file highlighted below: bob:pw:15020:3:30:7:60:15050: PASS_MIN_LEN 5 This indicates the minimum number of characters that a password must contain. PASS_WARN_AGE 7 This is the default for the warning field. As a user approaches the maximum number of days that they can use their password, the system will check to see if it is time to start warning the user about changing their password at login. This setting affects the default setting of the /etc/shadow file highlighted below: bob:pw:15020:3:30:7:60:15050: UID_MIN 500 The UID_MIN determines the first UID that will be assigned to an ordinary user. Any user with a UID that would be less than this value would either be for a system account or the root account. UID_MAX A UID technically could have a value of over four billion. For maximum compatibility it's recommended to leave it at its default value of GID _MIN 500 The GID _MIN determines the first GID that will be assigned to an ordinary group. Any group with a GID that would be less than this value would either be for a system group or the root group. GID _MAX A GID like a UID could have a value of over four billion. Whatever value you use for your UID_MAX, should be used for GID_MAX in order to support UPG. CREATE_HOME yes The value of this determines whether or not a new directory will be created for the user, when their account is created. UMASK 077 This UMASK works at the time the user home directory is being created; it will determine what the default permissions will be on this directory. Using the default value of 077 for UMASKmeans that only the user owner will have any kind of permission to access their directory. UMASK will be covered in more detail in a later chapter.
55 Field Example Description USERGROUPS_ENAB yes In distributions that feature a private group for each user, as this CentOS example shows, the USERGROUPS_ENAB will have a value of yes. If UPG is not used in the distribution, then this will have a value of no. ENCRYPT_METHOD SHA512 The encryption method that is used to encrypt the users' passwords in the /etc/shadow file. The ENCRYPT_METHOD setting overrides the MD5_CRYPT_ENAB setting (see next row). MD5_CRYPT_ENAB no This deprecated setting originally allowed the administrator to specify using MD5 encryption of passwords instead of the original DES encryption. It is now superseded by the setting of the ENCRYPT_METHOD Creating a User During the installation process, most installers will create a normal user and either give this user the permission to execute administrative commands with sudo or require the root user account password be configured as part of the installation process. This means that most Linux systems will be configured to allow for one unprivileged (non-root) user to login, as well as have the ability to effectively execute commands as the root user, either directly or indirectly. If the computer is to be used by only one person, then having only one regular user account might be sufficient. However, if a computer needs to be shared by multiple people, then it is desirable to have a separate account for each person who uses it. There are several advantages to individuals having their own separate accounts: Accounts can be used to grant selective access to files or services. For example, the user of each account has a separate home directory that is generally not accessible to the other users. The sudo command can be configured to grant the ability to execute select administrative commands. If users are required to use the sudo command to perform administrative commands, then the system will log when users perform these commands. Each account can have group memberships and rights associated with it allowing for greater management flexibility Account Considerations Creating a user account for use with a Linux system may require that you gather several pieces of information. While all that may be required is the account name, you may also want to plan the UID, the primary group, the supplementary groups, the home directory, the skeleton directory and the shell to be used. When planning these values, consider the following: user name: The only required argument for the useradd command is the name that you want the account to have. This name should follow the same guidelines discussed earlier in this chapter for group names. To summarize, it should be 32 characters or less, start with a lowercase letter or underscore and then should only contain lowercase letters, numbers, hyphens and underscores. If the user needs to access multiple systems, it is usually recommended to have the account name be the same on those systems. The account name must be unique for each user. user identifier (UID): Once you create a user with a specific UID, the system will generally just increment by one the UID for the next user that you create. If attached to a network with other systems, you may want to ensure that this UID is the same on all systems to help provide consistent access. The -u option to the useradd command allows you to specify the UID number. UIDs typically can range anywhere from zero to over four billion, but for greatest compatibility with older systems, the maximum recommended UID value is 60,000. As previously discussed, the root user has a user identifier (UID) of 0, which is what makes that account have special privileges. Any account with an UID of zero would effectively be able to act as the "administrator". System accounts are accounts generally used to run background services (called daemons). By not having services run as the root user, the amount of damage that can be done with a compromised service account is limited. System accounts used by services will generally use UIDs that are in the "reserved" range. One system account that is an exception to this rule is the user nfsnobody, which has an UID of The reserved range used for service accounts has expanded over time. Originally, it was for UIDs between 1 and 99. Then, it expanded to be between 1 and 499. The current trend among distributions is that system accounts will be any account that has a UID between 1 and 999, but the range is also still commonly used. If you are setting up a new system, it is a good practice to start your UIDs no lower than This also has the advantage of insuring you will have sufficient UIDs available for many system services and give you the ability to create many GIDs in the "reserved" range. primary group: In distributions which feature UPG, this group will be created automatically with a GID and group name that matches the UID and user name of the newly created user account. In distributions not using UPG, the primary group will ordinarily default to the "users" group with a GID of 100. To specify a primary group with the useradd command, use the -g option with either the name or GID of the group. supplementary group(s): If you want to make the user a member of one or more supplementary groups, the - G option can be used to specify a comma separated list of group names or numbers. home directory: By default, most distributions will create the user's home directory with the same name as the user account underneath the /home. For example, if creating a user account named sam, the user's new home directory would be /home/sam. There are several options for the useradd command that can affect creating the user's home directory: The -b option allows you to specify a different directory under which the user's home directory will be created. For example: -b /test would result in a home directory of /test/sam for a user account named sam. The -d option allows you to specify either an existing directory or a new home directory to create for the user. This should be a full path for the user's home directory. For example: -d /home/sam The -m option tells useradd to create the home directory; is not normally needed as this is the default behavior of the useradd command. However, when using the -k option (see below) to specify a different skeleton directory, then the -m option is needed. The -M option is used to specify to the useradd command that it should not create the home directory skeleton directory: By default, the contents of the /etc/skel directory are copied into the new user's home directory. The resulting files are also owned by the new user. By using the -k option with the useradd command, the contents of a different directory can be used to populate a new user's home directory. When specifying the skeleton directory with the -k option, the -m option must be used or else the useradd command will fail with an error stating, "-k flag is only allowed with the -mflag." shell: While the default shell is specified in the /etc/default/useradd file, it also can be overridden with the useradd -s option at the time of account creation. Later, the administrator can use the usermod -s option to change the shell or the user can change their shell with the chsh command. It is common to specify the /sbin/nologin shell for accounts to be used as system accounts. comment: The comment field, originally called the General Electric Comprehensive Operating System (GECOS) field, is typically used to hold the user's full name. Many graphical login programs display this field's value instead of the account name. The -coption of both useradd and usermod commands allows for the value of this field to be specified.
56 useradd Command Once you've verified what default values will be used and you've gathered the information about the user, then you are ready to create a user account. An example of a useradd command using a few options would look like the following: root@localhost:# useradd -u g users -G wheel,research -c 'Jane Doe' jane This example of the useradd command creates a user with a UID of 1000, a primary group of users, supplementary memberships in wheel and research groups, a comment of "Jane Doe" and an account name of jane. The information about the jane user account would be automatically added to the /etc/passwd and /etc/shadow files, while the information about jane's supplemental group access would be automatically added to the /etc/group and /etc/gshadow files. For example: root@localhost:# useradd -u g users -G wheel,research -c "Jane Doe" jane root@localhost:# grep jane /etc/passwd jane:x:1000:100:jane Doe:/home/jane:/bin/bash root@localhost:# grep jane /etc/shadow jane:!!:16003:0:99999:7::: root@localhost:# grep jane /etc/group wheel:x:10:jane research:x:2000:jane root@localhost:# grep jane /etc/gshadow wheel:::jane research:!::jane root@localhost:# Note that the account doesn't have a valid password yet! In addition, the mail spool file /var/spool/mail/jane would be created, the /home/jane directory would be created with permissions only permitting the janeuser access and the contents of the /etc/skel directory would be copied into the directory: root@localhost:# ls /var/spool/mail jane root rpc sysadmin root@localhost:# ls /home jane sysadmin root@localhost:# ls -a /home/jane....bash_logout.bashrc.profile.selected_editor root@localhost:# ls -a /etc/skel....bash_logout.bashrc.profile.selected_editor root@localhost:# 14.8 Choosing a Password Choosing a good password is not an easy task, but it is critical that it is done properly or the security of an account (perhaps the entire system) could be compromised. Picking a good password is only a start; you need to be very careful with your password so that it is not revealed to other people. You should never tell anyone your password and never let anyone see you type your password. If you do choose to write down your password, then you should store it securely in a place like a safe or safe deposit box. It's easy to make a bad password! If you use any information in your password that is related to you, then this information can also be known or discovered by others, resulting in your password being easily compromised. You password should never contain information about you or anyone you know, such as: first name middle name last name birthday phone pet names drivers license social security There are numerous factors to consider when you are trying to choose a password for an account: Length: The /etc/login.defs file allows the administrator to specify the minimum length of the password. While some believe that the longer the password, the better, this isn't really correct. The problem with passwords that are too long is that they are not easily remembered and, as a result, they are often written down in a place where they can easily be found and compromised. Composition: A good password should be composed of a combination of alphabetic, numeric and symbolic characters. Lifetime: The amount of time that a password can be used at maximum should be limited for several reasons: If an account is compromised and the time that the password is valid is limited, the intruder will ultimately lose access since the password will eventually become invalid. If an account is not being used, then it can automatically be disabled when the password is no longer valid. If attackers are attempting a "brute-force" attack by trying every possible password, then the password can be changed before the attack can succeed. However, requiring a user to change their password too often might pose security problems, including: The quality of the password the user chooses might suffer. The user may start writing their password on paper, increasing the possibility that the password may be discovered. Seldom used user accounts may become expired and require administrative attention to reset. Opinions vary about how often users should be forced to change their passwords. For highly sensitive accounts, it is recommended to change passwords more frequently, such as every 30 days. On the other hand, for noncritical accounts without any access to sensitive information, there is less need for frequent change. For accounts with minimal risk, having a duration of 90 days would be considered more reasonable Setting a User Password There are several ways for a user password to be changed: the user can execute the passwd command, the administrator can execute the passwd command providing the user name as an argument and graphical tools are also available. The administrator can use the passwd command to either set the initial password or change the password for the account. For example, if the administrator had created the account jane, then executing passwd jane will provide the administrator a prompt to set the password for the jane account. If completed successfully, then the /etc/shadow file will be updated with the user's new password. While regular users must follow many password rules, the root user only needs to follow one rule: the password cannot be left blank. All other password rules that the root user violates will simply result in a warning being printed to the screen and the rule not being enforced:
57 passwd jane Enter new UNIX password: BAD PASSWORD: it is WAY to short BAD PASSWORD: is too simple Retype new UNIX password: passwd: password updated successfully Assuming that the administrator has set a password for a user account, the user can then login with that account name and password. After the user opens a terminal they can execute the passwd command with no arguments to change their own password. They are prompted for their current password and then they are prompted to enter the new password twice. As an ordinary user, it may be difficult to set a valid password because all of the rules for the password must be followed. The user is normally allowed three attempts to provide a valid password before the passwd command exits with an error. Using the privileges of the root user, the encrypted passwords and other password related information can be viewed by viewing the /etc/shadow file. Recall that regular users cannot see the contents of this file Using the chage Command Although it's not listed as a command that you need to know in the Linux Essentials objectives, the chage command provides many options for managing the password aging information found in the /etc/shadow file. Here's a summary of the chage options: Short option Long option Description -l --list List the account aging information -d LAST_DAY --lastday LAST_DAY Set the date of the last password change to LAST_DAY root@localhost:# chage -M 60 jane Modifying a User Before you make changes to a user account, understand that some commands will not successfully modify a user account if the user is currently logged in (such as when changing the user's login name). Other changes that you might make won't be effective if the user is logged in, but will become effective as soon as the user logs out and then logs back in again. For example, if you are modifying group memberships, then the new memberships will be unavailable to the user until the next time the user logs in. In either case, it is helpful to know how to use the who, w and last commands, so you can be aware of who is logged into the system, as this may impact the changes that you want to make to a user. The who and w commands were discussed in a previous chapter. Both commands allow you to see who is currently logged into the system. The w command is actually the more verbose of the two, as it shows the system's uptime and load information as well as what process each user is running. The command last is slightly different from the who and w commands. By default, it also shows the user name, terminal, and login location, not just of the current login sessions, but previous sessions as well. Unlike the who and w commands, it will display the date/time the user logged into the system. If the user has logged off the system, then it will display the total time the user spent logged in or it will display "still logged in". The last command will read the entire login history from the /var/log/wtmp file and display all logins and reboot records by default. An interesting detail of the reboot records is that it displays the version of the Linux kernel that was booted instead of the login location. By providing a user name or a tty (terminal) name as an argument, the command will only show records that match that name. If you need to find out who was logged in as of a particular date and time, the last command can display that if you use the -t option to specify that date and time usermod Command The usermod command offers many options for modifying an existing user account. You should notice that most of these options are also available with the useraddcommand at the time you create the account. The following chart provides a summary of the usermod options: Short option Long option Description -E EXPIRE_DATE --expiredate EXPIRE_DATE Set account to expire on EXPIRE_DATE -c COMMENT Sets the value of the GECOS or comment field to COMMENT. -h --help Show the help for chage -d HOME_DIR --home HOME_DIR Sets a new home directory for the user. -I INACTIVE --inactive INACTIVE Set account to permit login for INACTIVE days after password expires -e EXPIRE_DATE --expiredate EXPIRE_DATE Set account expiration date to EXPIRE_DATE. -m MIN_DAYS --mindays MIN_DAYS Set the minimum number of days before password can be changed to MIN_DAYS -f INACTIVE --inactive INACTIVE Set account to permit login for INACTIVEdays after password expires. -M MAX_DAYS --maxdays MAX_DAYS Set the maximum number of days before a password should be changed to MAX_DAYS -g GROUP --gid GROUP Set GROUP as primary group. -G GROUPS --groups GROUPS Set supplementary groups to a list specified in GROUPS. -W WARN_DAYS --warndays WARN_DAYS Set the number of days before a password expires to start displaying a warning to WARN_DAYS A good example of the chage command would be to change the maximum number of days that an individual's password is valid to be 60 days: -a --append Append the user's supplemental groups with those specified by -G. -h --help Show the help for usermod.
58 Short option Long option Description -l NEW_LOGIN --login NEW_LOGIN Change the user's login name. -L --lock Lock the user account. -s SHELL --shell SHELL Specify the login shell for the account. -u NEW_UID --uid NEW_UID Specify the user's UID to be NEW_UID. -U --unlock Unlock the user account. Several of these options are worthy of discussion because of how they impact user management. It can be very problematic to change the user's UID with the -u option, as any files owned by the user will be orphaned. On the other hand, specifying a new login name for the user with -l does not cause the files to be orphaned. Deleting a user with the userdel command (see the next section) can either orphan or remove the user's files on the system. Instead of deleting the account, another choice is to lock the account with the -L option for the usermod command. Locking an account prevents the account from being used, but ownership of the files remains. There are some important things to know about managing the supplementary groups. If you use the -G option without the -a option, then you must list all the groups to which the user would belong. Using the -G option alone can lead to accidentally removing a user from all the former supplemental groups that the user belonged to. If you use the -a option with -G then you only have to list the new groups to which the user would belong. For example, if the user jane currently belongs to the wheeland research groups, then to add her account to the development group, execute the following command: root@localhost:# usermod -ag development jane Delete a User When you delete a user account, you also need to decide whether to delete the user's home directory. The user's files may be important for your organization and you may even have legal requirements to keep the data for a certain amount of time, so be careful not to make this decision lightly. Also, unless you've made backup copies of the data, once you've executed the command to delete the user and their files, there is no reversing the action. To delete the user jane without deleting the user's home directory (/home/jane), you could execute: root@localhost:# userdel jane Beware that deleting a user without deleting their home directory means that user's home directory's files will now be orphaned and these files will be owned solely by their former UID and GID. To delete the user jane and delete the /home/jane directory as well, use the -roption: root@localhost:# userdel -r jane WARNING: The above command will only delete the user's files in their home directory and their mail spool. If the user owns other files outside of their home directory, then those files will continue to exist as orphaned files. Lab Creating Users and Groups In this task, you will create group and user accounts. Group accounts can be helpful to be able to assign permissions on files shared by a group of users. User accounts in Linux distributions based upon Red Hat, like the CentOS distribution, start with the first User ID (UID) at 500, the next UID given at 501, and so on. The current trend followed by many other distributions is to have the first UID be 1000, the second to be 1001, and so on. If managing accounts for multiple systems, then it is desirable to have a network-based authentication server, where accounts can be created once, but used on many machines. Otherwise, managing multiple accounts on multiple machines can be challenging as it can be difficult to ensure that the user, and all the groups they belong to all have the same UIDs and GIDs on all machines. Another issue with multiple machine accounts that can be difficult is trying to keep the passwords to each account synchronized across all machines. Managing accounts for local users is still useful for individual machines, even if they have access to a networkbased authentication server. In this lab, you will manage local group and user accounts Step 1 In order to administer the user and group accounts, you will want to switch users to the root account with the following command: su - (Provide the root password "netlab123" when prompted) sysadmin@localhost:$ su - Password: root@localhost:# Step 2 Use the groupadd command to create a group called "research": groupadd -r research root@localhost:# groupadd -r research root@localhost:# The research group that was just added was added in the reserved range (between 1-999) because the -r option was used. Group Identifiers (GIDs) are automatically assigned with a value of less than the lowest normal user UID with this option. The groupadd command modifies the /etc/group file where group account information is stored. The groupmod command could be used with a -n option to change the name of this group or the -g option in order to change the GID for this group. The groupdel command can be used to delete this group, as long as it has not been made the primary group for a user Step 3 Use a getent command to retrieve information about the new group: getent group research Your output should appear similar to the following, although the GID that was assigned may be different: root@localhost:# getent group research research:x:999: root@localhost:# Now that the research group has been created, existing or new users can be made a member of this group. The usermod option -G must have a comma separated list of all secondary groups the user is to belong.
59 When usermod is used with the -a and -G options, then only the new group will need to be specified and it will be added to the existing secondary group memberships Step 4 Use the usermod command to add the research group as a secondary group for the sysadmin user: usermod -ag research sysadmin root@localhost:# usermod -ag research sysadmin root@localhost:# Users who are actively logged into the system will not be able to use any new group memberships until the next time they log into the system Step 5 There are several commands that could be used to verify the new group membership. Use the groups, id and getent commands to verify the sysadmin's membership: groups sysadmin id sysadmin getent group research The output of the previous commands should appear similar to: root@localhost:# groups sysadmin sysadmin : sysadmin adm sudo research root@localhost:# id sysadmin uid=1001(sysadmin) gid=1001(sysadmin) groups=1001(sysadmin),4(adm),27(sudo),999(research) root@localhost:# getent group research research:x:999:sysadmin root@localhost:# The useradd command will create a new user account and, in Red Hat-based distributions, a new group for that user. This new group will be named after the user and that will be their primary group. Red Hat-based distributions use what is known as "User Private Groups", or UPG, each user is a primary member of their own private group. For distributions that do not use UPG, all new users belong to the users group as their primary group Step 6 Create a new user named student who is a secondary member of the researchgroup and a primary member of their own private group. Use a comment of Linux Student that will appear as the full name of the user when they do a graphical login. Make sure that their home directory will be created by specifying the -moption: useradd -G research -c 'Linux Student' -m student root@localhost:# useradd -G research -c 'Linux Student' -m student root@localhost:# The user's account information is stored in the /etc/passwd and /etc/shadowfiles. The user's group information can be found in /etc/passwd and /etc/group file Step 7 Using the getent command, view the research group members again, but also use getent to show the student group, and the passwd and shadowdatabases for the student user: getent group research getent group student getent passwd student getent shadow student root@localhost:# getent group research research:x:999:sysadmin,student root@localhost:# getent group student student:x:1002: root@localhost:# getent passwd student student:x:1002:1002:linux Student:/home/student:/bin/sh root@localhost:# getent shadow student student:!:16902:0:99999:7::: root@localhost:# The output should now show that both sysadmin and student are secondary members of the research group. The GID of the student group matches the fourth field of the passwd information. This is what makes the student a primary member of the student group. Finally, the! appearing in the password field (second field) of the shadow file, shows that the password for the student has not been set Step 8 Use the passwd command to set the password, netlab123 for the student user and view the shadow file entry for the student user again: passwd student (type the same password twice) getent shadow student The output from the /etc/shadow file now shows an encrypted password in the second field: root@localhost:# passwd student Enter new UNIX password: Retype new UNIX password: passwd: password updated successfully root@localhost:# getent shadow student student:$6$pieedvax$gbo0beyhojl3/vdrop2uaqr6uvcwmzxxmpqimrejww/5or2wttm6dh3h83vjrmg6hg d9ux2i9fqfwqltg3/:16902:0:99999:7::: root@localhost:# Step 9 Just because a user has a password doesn't mean that they have ever logged into the system. Use the last command to see if the student has ever logged in: last last student The output of the last command should show that the sysadmin user has logged in before, but not the student user: root@localhost:# last sysadmin console Mon Apr 11 19:08 still logged in sysadmin console Mon Apr 11 19:08-19:08 (00:00) wtmp begins Mon Apr 11 18:25: root@localhost:# last student wtmp begins Mon Apr 11 18:25: root@localhost:#
60 There is also a lastb command, which works similar to the last command except that it shows "bad" or failed log in attempts. If you no longer wanted the student user to have access to the system, then the usermod -L student command could be used to "lock" the account. The account could be unlocked with the usermod -U student command. A more permanent solution to preventing access to the student account would be to delete the account with either the userdel student or userdel -r studentcommands. Using the -r option with the userdel command removes the user's home directory and mail, in addition to deleting the user's account Step 10 Delete the student account and remove the user's home directory: userdel -r student Executing the command should look like this: root@localhost:# userdel -r student root@localhost:# Chapter File Ownership By default, users will own the files that they create. While this ownership can be changed, this function requires administrative privileges. Although, most commands will usually show the user owner as a name, the operating system is actually associating the user ownership with the UID for that user name. Every file also has a group owner. In the previous chapter on creating users and groups, the user's primary group was discussed. By default, the primary group of the user who creates the file will be the group owner of any new files. Users are allowed to change the group owner of a file to any group that they belong. Similar to user ownership, the association of a file with a group is not actually done internally by the operating system by name, but by the GID of the group. Since ownership is actually determined by the UID and GID associated with a file, changing the UID of a user (or deleting the user) has the effect of making a file that was originally owned by that user have no real user owner. When there is no UID in the /etc/passwd file that matches the UID of the owner of the file, then the UID (the number) will be displayed as the user owner of the file instead of the user name (which no longer exists). The same occurs for groups. The id command can be useful for verifying which user account you are using and which groups you have available to use. By viewing the output of this command, you can see the user's identity information expressed both as a number and as a name. The output of the id command displays the UID and user account name of the current user followed by the GID and group name of the primary group and the GIDs and group names of all group memberships: sysadmin@localhost:$ id uid=500(sysadmin) gid=500(sysadmin) groups=500(sysadmin),10001(research),10002(development) context=un confined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 The above example shows the user has a UID of 500 for the user account sysadmin. It shows the primary group for this user has a GID of 500 for the group sysadmin. Because the user account and primary group account have the same numeric identifier and same name, this indicates that this user is in a User Private Group (UPG). In addition, the user belongs to two supplemental groups: the research group with a GID of and the development group with a GID of When a file is created it will belong to the current user and their current primary group. If the user from the above example were to execute a command like touch to create a file and then view the file details, the output would look like the following: sysadmin@localhost:$ touch /tmp/filetest1 sysadmin@localhost:$ ls -l /tmp/filetest1 -rw-rw-r--. 1 sysadmin sysadmin 0 Oct 21 10:18 /tmp/filetest1 The user owner of the file is sysadmin and the group owner sysadmin newgrp and groups Commands If you know that the file you are about to create should belong to a group different from your current primary group, then you can use the newgrp command to change your current primary group. As shown previously, the id command will list your identity information, including your group memberships. If you are only interested in knowing what groups you belong to, then you can execute the groups command: sysadmin@localhost:$ groups sysadmin research development The groups output may not be as detailed as the output of the id command, but if all you need to know is what groups you can switch to by using the newgrp command, then the groups command provides the information that you need. The id command output does show your current primary group, so it is useful for verifying that the newgrp command succeeded.
61 For example, if the sysadmin user was planning on having a file owned by the group research, but that wasn't the user's primary group, then the user could use the newgrpcommand and then verify the correct primary group with the id command before creating the new file: sysadmin@localhost:$ id uid=502(sysadmin) gid=503(sysadmin) groups=503(sysadmin),10001(research),10002(development) context=un confined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 sysadmin@localhost:$ newgrp research sysadmin@localhost:$ id uid=502(sysadmin) gid=10001(research) groups=503(sysadmin),10001(research),10002(development) context=u nconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 From the output of the previous commands, you see initially the user's GID is 503 for the sysadmin user, then the newgrp research command is executed, and then the user's primary GID is 10001, the research group. After these commands were executed, if the user was to create another file and view its details, the new file would be owned by the research group: sysadmin@localhost:$ touch /tmp/filetest2 sysadmin@localhost:$ ls -l /tmp/filetest2 -rw-r--r--. 1 sysadmin research 0 Oct 21 10:53 /tmp/filetest2 The newgrp command opens a new shell; as long as the user stays in that shell, the primary group won't change. To switch the primary group back to the original, the user could leave the new shell by running the exit command. For example: sysadmin@localhost:$ id uid=502(sysadmin) gid=10001(research) groups=503(sysadmin),10001(research),10002(development) context=u nconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 sysadmin@localhost:$ exit exit sysadmin@localhost:$ id uid=502(sysadmin) gid=503(sysadmin) groups=503(sysadmin),10001(research),10002(development) context=un confined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 Administrative privileges are required in order to permanently change the primary group of the user. The root user would execute the usermod -g groupname username command chgrp and stat Commands If you need to change the group ownership of an existing file, then you can use the chgrpcommand. As a user without administrative privileges, the chgrp command can only be used to change the group owner of the file to a group that the user is already a member. As the root user, the chgrp command can be used to change the group owner of any file to any group.while you can view the ownership of a file with the -l option to the ls command, the system provides another command that is useful when viewing ownership and file permissions: the stat command. The stat command displays more detailed information about a file, including providing the group ownership both by group name and GID number: sysadmin@localhost:$ stat /tmp/filetest1 File: `/tmp/filetest1' Size: 0 Blocks: 0 IO Block: 4096 regular empty file Device: fd00h/64768d Inode: Links: 1 Access: (0664/-rw-rw-r--) Uid: ( 502/sysadmin) Gid: ( 503/sysadmin) Access: :18: Modify: :18: Change: :18: The stat command will also be useful later in this chapter when file permissions are covered, as it provides more detail than the ls -l command provides. The following graphic illustrates the sysadmin user changing the group ownership of a file that the user owns: sysadmin@localhost:$ chgrp development /tmp/filetest1 sysadmin@localhost:$ stat /tmp/filetest1 File: `/tmp/filetest1' Size: 0 Blocks: 0 IO Block: 4096 regular empty file Device: fd00h/64768d Inode: Links: 1 Access: (0664/-rw-rw-r--) Uid: ( 500/sysadmin) Gid: ( 502/development) Access: :18: Modify: :18: Change: :18: If a user attempts to modify the group ownership of a file that the user doesn't own, they will receive an error message: sysadmin@localhost:$ chgrp development /etc/passwd chgrp: changing group of '/etc/passwd': Operation not permitted Sometimes you want to be able to not only change the files in your current directory, but also the files in subdirectories. When executed with the -R (recursive) option, the chgrp command will operate not only on the current directory, but all directories that may be nested underneath the specified directory. The operation will also affect all files in the subdirectories, not just the directories themselves. The following graphic illustrates the use of the -R option: sysadmin@localhost:$ cp -r /etc/sound. sysadmin@localhost:$ ls -ld sound drwxr-xr-x 1 sysadmin sysadmin 0 Dec 11 02:02 sound sysadmin@localhost:$ls -lr sound sound: total 4 drwxr-xr-x. 2 sysadmin sysadmin 4096 Oct 28 13:06 events sound/events: total 48 -rw-r--r--. 1 sysadmin sysadmin Oct 28 13:06 gnome-2.soundlist -rw-r--r--. 1 sysadmin sysadmin Oct 28 13:06 gtk-events-2.soundlist sysadmin@localhost:$ chgrp -R development sound sysadmin@localhost:$ ls -ld sound drwxr-xr-x. 3 sysadmin development 4096 Oct 28 13:06 sound ls -lr sound sound: total 4 drwxr-xr-x. 2 sysadmin development 4096 Oct 28 13:06 events sound/events: -rw-r--r--. 1 sysadmin development Oct 28 13:06 gnome-2.soundlist -rw-r--r--. 1 sysadmin development Oct 28 13:06 gtk-events-2.soundlist 15.5 chown Command The chown command allows the root user to change the user ownership of files and directories. A regular user cannot use this command to change the user owner of a file, even to give the ownership of one of their own files to another user. However, the chown command also permits changing group ownership, which can be accomplished by either root or the owner of the file.
62 There are three different ways the chown command can be executed. The first method is used to change just the user owner of the file. For example, if the root user wanted to change the user ownership of the abc.txt file to the user ted, then the following command could be executed: chown ted abc.txt The second method is to change both the user and the group; this also requires root privileges. To accomplish this, you separate the user and group by either a colon or a period character. For example: root@localhost:# chown user:group /path/to/file root@localhost:# chown user.group /path/to/file Character c p Type of the File A character file is one that relates to a character hardware device where data is read one byte at a time. A pipe file works similar to the pipe symbol, allowing for the output of one process to communicate to another process through the pipe file, where the output of the one process is used as input for the other process. If a user doesn't have root privileges, they can use the third method to change the group owner of a file just like the chgrp command. To use chown to only change the group ownership of the file, use a colon or a period as a prefix to the group name: root@localhost:# chown :group /path/to/file root@localhost:# chown.group /path/to/file 15.6 Permissions When you execute the ls -l command, the resulting output displays ten characters at the beginning of each line, which indicate the type of file and the permissions of the file: The first character indicates the file type. Characters 2-4 indicate the permissions for the user that owns the file. Characters 5-7 indicate the permissions for the group that owns the file. Characters 8-10 indicate the permissions for "others" or what is sometimes referred to as the world's permissions. This would include all users who are not the file owner or a member of the file's group. For example, consider the output of the following command: root@localhost:# ls -l /etc/passwd -rw-r--r--. 1 root root 4135 May 27 21:08 /etc/passwd Based on the previous command output, the first ten characters could be described by the following table: The following table describes the possible values for the file type. Recall that these types were covered in a previous chapter: Character Type of the File - A regular file which may be empty, contain text or binary data. d A directory file which contains the names of other files and links to them. s A socket file allows two processes to communicate, where both processes are allowed to either send or receive data. Although all the file types are listed in the table above, most likely you will never encounter anything but regular, directory and link files unless you explore the /dev directory. The characters in the permissions part of the output have the following meanings: r stands for read permission w stands for write permission x stands for execute permission The permissions set on these files determine the level of access that a user will have on the file. When a user runs a program and the program accesses a file, then the permissions are checked to determine if the user has the correct access rights to the file. The permissions themselves are deceptively simple and have a different meaning depending on whether they are applied to a file or a directory: Permission Meaning on a file Meaning on a directory r w x The process can read the contents of the file, meaning the contents can be viewed and copied. The file can be written to by the process, so changes to a file can be saved. Note that w permission really requires r permission on the file to work correctly. The file can be executed or run as a process. File names in the directory can be listed, but other details are not available. Files can be added to or removed from the directory. Note that w permission requires x permission on the directory to work correctly. The user can use the cd command to "get into" the directory and use the directory in a pathname to access files and, potentially, subdirectories under this directory. l b A symbolic link is a file name that refers (points) to another file. A block file is one that relates to a block hardware device where data is read in blocks of data.
63 Understanding Permissions While the chart on the previous page can be a handy reference, by itself it doesn't provide a clear description of how permissions work. To better understand how permissions work, consider the following scenarios. To understand these scenarios, you should first understand the following diagram: Scenario #2 - Viewing Directory Contents Question: Based on the following diagram, who can use the ls command to display the contents of the /data directory (ls /data)? The important information is highlighted. The first box represents the / directory, with a user owner of root, a group owner of root and permissions of rwxr-xr-x. The second box represents the /data directory, a directory that is under the / directory. The third box represents the abc.txt file, which is stored in the /data directory. You should also understand that if you are the owner of the file/directory, then only the user owner permissions are used to determine access to that file/directory. If you are not the owner, but are a member of the group that owns the file/directory, then only group owner permissions are used to determine access to that file/directory. If you aren't the owner and not a member of the file/directory group, then your permissions would be others" Scenario #1 - The importance of Directory Access Question: Based on the following diagram, what access would the user bob have on the file abc.txt? Answer: All users Explanation: All that is required to be able to view a directory's contents is r permission on the directory (and the ability to access the parent directories). The x permission for all users in the / directory means all users can use / as part of a path, so everyone is able to get through the / directory to get to the /data directory. The r permission for all users in the /datadirectory means all users can use the ls command to view the contents.this includes hidden files, so the ls -a command will also work on this directory. However, note that in order to see file details (ls -l) would also require x permission on the directory. So while the root user and members of the root group have this access on the /datadirectory, no other users would be able to execute ls -l /data. Lesson learned: The r permission allows a user to view a listing of the directory Scenario #3 - Deleting Directory Contents Question: Based on the following diagram, who can delete the /data/abc.txt file? Answer: None Explanation: Initially it would appear that the user bob can view the contents of the abc.txtfile as well as copy the file, modify its contents and run it like a program. This erroneous conclusion would be the result of looking solely at the file's permissions (rwx for the user bobin this case). However, in order to do anything with the file, the user must first "get into" the /data directory. The permissions for bob for the /data directory are the permissions for "others" (r--), which means bob can't even use the cd command to get into the directory. If the execute permission (--x) was set for the directory, then the user bob would be able to "get into" the directory, meaning the permissions of the file itself would apply. Lesson learned: The permissions of all parent directories must be considered before considering the permissions on a specific file. Answer: Only the root user Explanation: A user needs no permissions at all on the file itself to delete a file. The w permission on the directory that the file is stored in is required to delete a file in a directory. Based on that, it would seem that all users could delete the /data/abc.txt file, since everyone has w permission on the directory. However, to delete a file, you must also be able to "get into" the directory. Since only the root user has x permission on the /data directory, only root can "get into" that directory in order to delete files in this directory. Lesson learned: The w permission allows a user to delete files from a directory, but only if the user also has x permission on the directory.
9.2 Linux Essentials Exam Objectives
 9.2 Linux Essentials Exam Objectives This chapter will cover the topics for the following Linux Essentials exam objectives: Topic 3: The Power of the Command Line (weight: 10) 3.3: Turning Commands into
9.2 Linux Essentials Exam Objectives This chapter will cover the topics for the following Linux Essentials exam objectives: Topic 3: The Power of the Command Line (weight: 10) 3.3: Turning Commands into
Install Cisco ISE on a Linux KVM
 KVM Hypervisor Support, on page 1 Obtain the Cisco ISE Evaluation Software, on page 4 Install Cisco ISE on KVM, on page 4 KVM Hypervisor Support Cisco ISE supports KVM hypervisor on Red Hat Enterprise
KVM Hypervisor Support, on page 1 Obtain the Cisco ISE Evaluation Software, on page 4 Install Cisco ISE on KVM, on page 4 KVM Hypervisor Support Cisco ISE supports KVM hypervisor on Red Hat Enterprise
Install Cisco ISE on a Linux KVM
 KVM Hypervisor Support, page 1 Obtain the Cisco ISE Evaluation Software, page 3 Install Cisco ISE on KVM, page 4 KVM Hypervisor Support Cisco ISE supports KVM hypervisor on Red Hat Enterprise Linux (RHEL)
KVM Hypervisor Support, page 1 Obtain the Cisco ISE Evaluation Software, page 3 Install Cisco ISE on KVM, page 4 KVM Hypervisor Support Cisco ISE supports KVM hypervisor on Red Hat Enterprise Linux (RHEL)
Install Cisco ISE on a Linux KVM
 KVM Hypervisor Support, on page 1 Obtain the Cisco ISE Evaluation Software, on page 8 Install Cisco ISE on KVM, on page 8 KVM Hypervisor Support Cisco ISE supports KVM hypervisor on Red Hat Enterprise
KVM Hypervisor Support, on page 1 Obtain the Cisco ISE Evaluation Software, on page 8 Install Cisco ISE on KVM, on page 8 KVM Hypervisor Support Cisco ISE supports KVM hypervisor on Red Hat Enterprise
Install Cisco ISE on a Linux KVM
 KVM Hypervisor Support, page 1 Obtain the Cisco ISE Evaluation Software, page 7 Install Cisco ISE on KVM, page 8 KVM Hypervisor Support Cisco ISE supports KVM hypervisor on Red Hat Enterprise Linux (RHEL)
KVM Hypervisor Support, page 1 Obtain the Cisco ISE Evaluation Software, page 7 Install Cisco ISE on KVM, page 8 KVM Hypervisor Support Cisco ISE supports KVM hypervisor on Red Hat Enterprise Linux (RHEL)
A shell can be used in one of two ways:
 Shell Scripting 1 A shell can be used in one of two ways: A command interpreter, used interactively A programming language, to write shell scripts (your own custom commands) 2 If we have a set of commands
Shell Scripting 1 A shell can be used in one of two ways: A command interpreter, used interactively A programming language, to write shell scripts (your own custom commands) 2 If we have a set of commands
A Big Step. Shell Scripts, I/O Redirection, Ownership and Permission Concepts, and Binary Numbers
 A Big Step Shell Scripts, I/O Redirection, Ownership and Permission Concepts, and Binary Numbers Copyright 2006 2009 Stewart Weiss What a shell really does Here is the scoop on shells. A shell is a program
A Big Step Shell Scripts, I/O Redirection, Ownership and Permission Concepts, and Binary Numbers Copyright 2006 2009 Stewart Weiss What a shell really does Here is the scoop on shells. A shell is a program
LING 408/508: Computational Techniques for Linguists. Lecture 5
 LING 408/508: Computational Techniques for Linguists Lecture 5 Last Time Installing Ubuntu 18.04 LTS on top of VirtualBox Your Homework 2: did everyone succeed? Ubuntu VirtualBox Host OS: MacOS or Windows
LING 408/508: Computational Techniques for Linguists Lecture 5 Last Time Installing Ubuntu 18.04 LTS on top of VirtualBox Your Homework 2: did everyone succeed? Ubuntu VirtualBox Host OS: MacOS or Windows
Scripting. Shell Scripts, I/O Redirection, Ownership and Permission Concepts, and Binary Numbers
 Scripting Shell Scripts, I/O Redirection, Ownership and Permission Concepts, and Binary Numbers Adapted from Practical Unix and Programming Hunter College Copyright 2006 2009 Stewart Weiss What a shell
Scripting Shell Scripts, I/O Redirection, Ownership and Permission Concepts, and Binary Numbers Adapted from Practical Unix and Programming Hunter College Copyright 2006 2009 Stewart Weiss What a shell
Unix Shell scripting. Dr Alun Moon 7th October Introduction. Notation. Spaces
 Unix Shell scripting Dr Alun Moon 7th October 2017 Introduction Shell scripts in Unix are a very powerfull tool, they form much of the standard system as installed. What are these good for? So many file
Unix Shell scripting Dr Alun Moon 7th October 2017 Introduction Shell scripts in Unix are a very powerfull tool, they form much of the standard system as installed. What are these good for? So many file
Chapter 12. Virtualization
 Chapter 12 Virtualization Virtualization is used in many contexts in computer systems In Operating Systems (already covered in the lecture): Virtualization of memory Virtualization of block devices (or
Chapter 12 Virtualization Virtualization is used in many contexts in computer systems In Operating Systems (already covered in the lecture): Virtualization of memory Virtualization of block devices (or
Shell Scripting. Todd Kelley CST8207 Todd Kelley 1
 Shell Scripting Todd Kelley kelleyt@algonquincollege.com CST8207 Todd Kelley 1 If we have a set of commands that we want to run on a regular basis, we could write a script A script acts as a Linux command,
Shell Scripting Todd Kelley kelleyt@algonquincollege.com CST8207 Todd Kelley 1 If we have a set of commands that we want to run on a regular basis, we could write a script A script acts as a Linux command,
Scripting. More Shell Scripts. Adapted from Practical Unix and Programming Hunter College
 Scripting More Shell Scripts Adapted from Practical Unix and Programming Hunter College Copyright 2006 2009 Stewart Weiss Back to shell scripts Now that you've learned a few commands and can edit files,
Scripting More Shell Scripts Adapted from Practical Unix and Programming Hunter College Copyright 2006 2009 Stewart Weiss Back to shell scripts Now that you've learned a few commands and can edit files,
Week Overview. Unix file system File types and file naming Basic file system commands: pwd,cd,ls,mkdir,rmdir,mv,cp,rm man pages
 ULI101 Week 02 Week Overview Unix file system File types and file naming Basic file system commands: pwd,cd,ls,mkdir,rmdir,mv,cp,rm man pages Text editing Common file utilities: cat,more,less,touch,file,find
ULI101 Week 02 Week Overview Unix file system File types and file naming Basic file system commands: pwd,cd,ls,mkdir,rmdir,mv,cp,rm man pages Text editing Common file utilities: cat,more,less,touch,file,find
vi Primer Adapted from:
 Adapted from: http://courses.knox.edu/cs205/205tutorials/viprimer.html vi Primer This document is designed to introduce you to the standard UNIX screen editor, vi (short for "visual"). Vi can be used to
Adapted from: http://courses.knox.edu/cs205/205tutorials/viprimer.html vi Primer This document is designed to introduce you to the standard UNIX screen editor, vi (short for "visual"). Vi can be used to
Shell Start-up and Configuration Files
 ULI101 Week 10 Lesson Overview Shell Start-up and Configuration Files Shell History Alias Statement Shell Variables Introduction to Shell Scripting Positional Parameters echo and read Commands if and test
ULI101 Week 10 Lesson Overview Shell Start-up and Configuration Files Shell History Alias Statement Shell Variables Introduction to Shell Scripting Positional Parameters echo and read Commands if and test
Essentials for Scientific Computing: Bash Shell Scripting Day 3
 Essentials for Scientific Computing: Bash Shell Scripting Day 3 Ershaad Ahamed TUE-CMS, JNCASR May 2012 1 Introduction In the previous sessions, you have been using basic commands in the shell. The bash
Essentials for Scientific Computing: Bash Shell Scripting Day 3 Ershaad Ahamed TUE-CMS, JNCASR May 2012 1 Introduction In the previous sessions, you have been using basic commands in the shell. The bash
Unix Guide. Meher Krishna Patel. Created on : Octorber, 2017 Last updated : December, More documents are freely available at PythonDSP
 Unix Guide Meher Krishna Patel Created on : Octorber, 2017 Last updated : December, 2017 More documents are freely available at PythonDSP Table of contents Table of contents i 1 Unix commands 1 1.1 Unix
Unix Guide Meher Krishna Patel Created on : Octorber, 2017 Last updated : December, 2017 More documents are freely available at PythonDSP Table of contents Table of contents i 1 Unix commands 1 1.1 Unix
Shells and Shell Programming
 Shells and Shell Programming 1 Shells A shell is a command line interpreter that is the interface between the user and the OS. The shell: analyzes each command determines what actions are to be performed
Shells and Shell Programming 1 Shells A shell is a command line interpreter that is the interface between the user and the OS. The shell: analyzes each command determines what actions are to be performed
My Favorite bash Tips and Tricks
 1 of 6 6/18/2006 7:44 PM My Favorite bash Tips and Tricks Prentice Bisbal Abstract Save a lot of typing with these handy bash features you won't find in an old-fashioned UNIX shell. bash, or the Bourne
1 of 6 6/18/2006 7:44 PM My Favorite bash Tips and Tricks Prentice Bisbal Abstract Save a lot of typing with these handy bash features you won't find in an old-fashioned UNIX shell. bash, or the Bourne
Lecture 5. Essential skills for bioinformatics: Unix/Linux
 Lecture 5 Essential skills for bioinformatics: Unix/Linux UNIX DATA TOOLS Text processing with awk We have illustrated two ways awk can come in handy: Filtering data using rules that can combine regular
Lecture 5 Essential skills for bioinformatics: Unix/Linux UNIX DATA TOOLS Text processing with awk We have illustrated two ways awk can come in handy: Filtering data using rules that can combine regular
Introduction to Linux
 Introduction to Linux The command-line interface A command-line interface (CLI) is a type of interface, that is, a way to interact with a computer. Window systems, punched cards or a bunch of dials, buttons
Introduction to Linux The command-line interface A command-line interface (CLI) is a type of interface, that is, a way to interact with a computer. Window systems, punched cards or a bunch of dials, buttons
Shells & Shell Programming (Part B)
 Shells & Shell Programming (Part B) Software Tools EECS2031 Winter 2018 Manos Papagelis Thanks to Karen Reid and Alan J Rosenthal for material in these slides CONTROL STATEMENTS 2 Control Statements Conditional
Shells & Shell Programming (Part B) Software Tools EECS2031 Winter 2018 Manos Papagelis Thanks to Karen Reid and Alan J Rosenthal for material in these slides CONTROL STATEMENTS 2 Control Statements Conditional
Unix as a Platform Exercises + Solutions. Course Code: OS 01 UNXPLAT
 Unix as a Platform Exercises + Solutions Course Code: OS 01 UNXPLAT Working with Unix Most if not all of these will require some investigation in the man pages. That's the idea, to get them used to looking
Unix as a Platform Exercises + Solutions Course Code: OS 01 UNXPLAT Working with Unix Most if not all of these will require some investigation in the man pages. That's the idea, to get them used to looking
Introduction p. 1 Who Should Read This Book? p. 1 What You Need to Know Before Reading This Book p. 2 How This Book Is Organized p.
 Introduction p. 1 Who Should Read This Book? p. 1 What You Need to Know Before Reading This Book p. 2 How This Book Is Organized p. 2 Conventions Used in This Book p. 2 Introduction to UNIX p. 5 An Overview
Introduction p. 1 Who Should Read This Book? p. 1 What You Need to Know Before Reading This Book p. 2 How This Book Is Organized p. 2 Conventions Used in This Book p. 2 Introduction to UNIX p. 5 An Overview
CSCI 211 UNIX Lab. Shell Programming. Dr. Jiang Li. Jiang Li, Ph.D. Department of Computer Science
 CSCI 211 UNIX Lab Shell Programming Dr. Jiang Li Why Shell Scripting Saves a lot of typing A shell script can run many commands at once A shell script can repeatedly run commands Help avoid mistakes Once
CSCI 211 UNIX Lab Shell Programming Dr. Jiang Li Why Shell Scripting Saves a lot of typing A shell script can run many commands at once A shell script can repeatedly run commands Help avoid mistakes Once
A Brief Introduction to the Linux Shell for Data Science
 A Brief Introduction to the Linux Shell for Data Science Aris Anagnostopoulos 1 Introduction Here we will see a brief introduction of the Linux command line or shell as it is called. Linux is a Unix-like
A Brief Introduction to the Linux Shell for Data Science Aris Anagnostopoulos 1 Introduction Here we will see a brief introduction of the Linux command line or shell as it is called. Linux is a Unix-like
CS Unix Tools & Scripting
 Cornell University, Spring 2014 1 February 24, 2014 1 Slides evolved from previous versions by Hussam Abu-Libdeh and David Slater A note on awk for (item in array) The order in which items are returned
Cornell University, Spring 2014 1 February 24, 2014 1 Slides evolved from previous versions by Hussam Abu-Libdeh and David Slater A note on awk for (item in array) The order in which items are returned
Shell Programming (bash)
 Shell Programming Shell Programming (bash) Commands run from a file in a subshell A great way to automate a repeated sequence of commands. File starts with #!/bin/bash absolute path to the shell program
Shell Programming Shell Programming (bash) Commands run from a file in a subshell A great way to automate a repeated sequence of commands. File starts with #!/bin/bash absolute path to the shell program
Unix File System. Learning command-line navigation of the file system is essential for efficient system usage
 ULI101 Week 02 Week Overview Unix file system File types and file naming Basic file system commands: pwd,cd,ls,mkdir,rmdir,mv,cp,rm man pages Text editing Common file utilities: cat,more,less,touch,file,find
ULI101 Week 02 Week Overview Unix file system File types and file naming Basic file system commands: pwd,cd,ls,mkdir,rmdir,mv,cp,rm man pages Text editing Common file utilities: cat,more,less,touch,file,find
Operating Systems, Unix Files and Commands SEEM
 Operating Systems, Unix Files and Commands SEEM 3460 1 Major Components of Operating Systems (OS) Process management Resource management CPU Memory Device File system Bootstrapping SEEM 3460 2 Programs
Operating Systems, Unix Files and Commands SEEM 3460 1 Major Components of Operating Systems (OS) Process management Resource management CPU Memory Device File system Bootstrapping SEEM 3460 2 Programs
Chapter 4. Unix Tutorial. Unix Shell
 Chapter 4 Unix Tutorial Users and applications interact with hardware through an operating system (OS). Unix is a very basic operating system in that it has just the essentials. Many operating systems,
Chapter 4 Unix Tutorial Users and applications interact with hardware through an operating system (OS). Unix is a very basic operating system in that it has just the essentials. Many operating systems,
Shells and Shell Programming
 Shells and Shell Programming Shells A shell is a command line interpreter that is the interface between the user and the OS. The shell: analyzes each command determines what actions are to be performed
Shells and Shell Programming Shells A shell is a command line interpreter that is the interface between the user and the OS. The shell: analyzes each command determines what actions are to be performed
Unix Introduction to UNIX
 Unix Introduction to UNIX Get Started Introduction The UNIX operating system Set of programs that act as a link between the computer and the user. Developed in 1969 by a group of AT&T employees Various
Unix Introduction to UNIX Get Started Introduction The UNIX operating system Set of programs that act as a link between the computer and the user. Developed in 1969 by a group of AT&T employees Various
COMP 4/6262: Programming UNIX
 COMP 4/6262: Programming UNIX Lecture 12 shells, shell programming: passing arguments, if, debug March 13, 2006 Outline shells shell programming passing arguments (KW Ch.7) exit status if (KW Ch.8) test
COMP 4/6262: Programming UNIX Lecture 12 shells, shell programming: passing arguments, if, debug March 13, 2006 Outline shells shell programming passing arguments (KW Ch.7) exit status if (KW Ch.8) test
CHE3935. Lecture 1. Introduction to Linux
 CHE3935 Lecture 1 Introduction to Linux 1 Logging In PuTTY is a free telnet/ssh client that can be run without installing it within Windows. It will only give you a terminal interface, but used with a
CHE3935 Lecture 1 Introduction to Linux 1 Logging In PuTTY is a free telnet/ssh client that can be run without installing it within Windows. It will only give you a terminal interface, but used with a
Linux Systems Administration Getting Started with Linux
 Linux Systems Administration Getting Started with Linux Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International
Linux Systems Administration Getting Started with Linux Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International
Linux Essentials Objectives Topics:
 Linux Essentials Linux Essentials is a professional development certificate program that covers basic knowledge for those working and studying Open Source and various distributions of Linux. Exam Objectives
Linux Essentials Linux Essentials is a professional development certificate program that covers basic knowledge for those working and studying Open Source and various distributions of Linux. Exam Objectives
Introduction to Linux. Woo-Yeong Jeong Computer Systems Laboratory Sungkyunkwan University
 Introduction to Linux Woo-Yeong Jeong (wooyeong@csl.skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu What is Linux? A Unix-like operating system of a computer What is an
Introduction to Linux Woo-Yeong Jeong (wooyeong@csl.skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu What is Linux? A Unix-like operating system of a computer What is an
Conditional Control Structures. Dr.T.Logeswari
 Conditional Control Structures Dr.T.Logeswari TEST COMMAND test expression Or [ expression ] Syntax Ex: a=5; b=10 test $a eq $b ; echo $? [ $a eq $b] ; echo $? 2 Unix Shell Programming - Forouzan 2 TEST
Conditional Control Structures Dr.T.Logeswari TEST COMMAND test expression Or [ expression ] Syntax Ex: a=5; b=10 test $a eq $b ; echo $? [ $a eq $b] ; echo $? 2 Unix Shell Programming - Forouzan 2 TEST
Open up a terminal, make sure you are in your home directory, and run the command.
 More Linux Commands 0.1 wc The Linux command for acquiring size statistics on a file is wc. This command can provide information from line count, to bytes in a file. Open up a terminal, make sure you are
More Linux Commands 0.1 wc The Linux command for acquiring size statistics on a file is wc. This command can provide information from line count, to bytes in a file. Open up a terminal, make sure you are
Lab 3a Using the vi editor
 Lab 3a Using the vi editor Objectives: Become familiar with the vi Editor Review the three vi Modes Review keystrokes to move between vi modes Create a new file with vi Editor Invoke vi with show mode
Lab 3a Using the vi editor Objectives: Become familiar with the vi Editor Review the three vi Modes Review keystrokes to move between vi modes Create a new file with vi Editor Invoke vi with show mode
Linux shell programming for Raspberry Pi Users - 2
 Linux shell programming for Raspberry Pi Users - 2 Sarwan Singh Assistant Director(S) NIELIT Chandigarh 1 SarwanSingh.com Education is the kindling of a flame, not the filling of a vessel. - Socrates SHELL
Linux shell programming for Raspberry Pi Users - 2 Sarwan Singh Assistant Director(S) NIELIT Chandigarh 1 SarwanSingh.com Education is the kindling of a flame, not the filling of a vessel. - Socrates SHELL
SHELL SCRIPT BASIC. UNIX Programming 2014 Fall by Euiseong Seo
 SHELL SCRIPT BASIC UNIX Programming 2014 Fall by Euiseong Seo Shell Script Interactive shell sequentially executes a series of commands Some tasks are repetitive and automatable They are what programs
SHELL SCRIPT BASIC UNIX Programming 2014 Fall by Euiseong Seo Shell Script Interactive shell sequentially executes a series of commands Some tasks are repetitive and automatable They are what programs
Contents. Note: pay attention to where you are. Note: Plaintext version. Note: pay attention to where you are... 1 Note: Plaintext version...
 Contents Note: pay attention to where you are........................................... 1 Note: Plaintext version................................................... 1 Hello World of the Bash shell 2 Accessing
Contents Note: pay attention to where you are........................................... 1 Note: Plaintext version................................................... 1 Hello World of the Bash shell 2 Accessing
Essential Unix (and Linux) for the Oracle DBA. Revision no.: PPT/2K403/02
 Essential Unix (and Linux) for the Oracle DBA Revision no.: PPT/2K403/02 Architecture of UNIX Systems 2 UNIX System Structure 3 Operating system interacts directly with Hardware Provides common services
Essential Unix (and Linux) for the Oracle DBA Revision no.: PPT/2K403/02 Architecture of UNIX Systems 2 UNIX System Structure 3 Operating system interacts directly with Hardware Provides common services
Overview LEARN. History of Linux Linux Architecture Linux File System Linux Access Linux Commands File Permission Editors Conclusion and Questions
 Lanka Education and Research Network Linux Architecture, Linux File System, Linux Basic Commands 28 th November 2016 Dilum Samarasinhe () Overview History of Linux Linux Architecture Linux File System
Lanka Education and Research Network Linux Architecture, Linux File System, Linux Basic Commands 28 th November 2016 Dilum Samarasinhe () Overview History of Linux Linux Architecture Linux File System
Linux Shell Scripting. Linux System Administration COMP2018 Summer 2017
 Linux Shell Scripting Linux System Administration COMP2018 Summer 2017 What is Scripting? Commands can be given to a computer by entering them into a command interpreter program, commonly called a shell
Linux Shell Scripting Linux System Administration COMP2018 Summer 2017 What is Scripting? Commands can be given to a computer by entering them into a command interpreter program, commonly called a shell
Exploring UNIX: Session 3
 Exploring UNIX: Session 3 UNIX file system permissions UNIX is a multi user operating system. This means several users can be logged in simultaneously. For obvious reasons UNIX makes sure users cannot
Exploring UNIX: Session 3 UNIX file system permissions UNIX is a multi user operating system. This means several users can be logged in simultaneously. For obvious reasons UNIX makes sure users cannot
I/O and Shell Scripting
 I/O and Shell Scripting File Descriptors Redirecting Standard Error Shell Scripts Making a Shell Script Executable Specifying Which Shell Will Run a Script Comments in Shell Scripts File Descriptors Resources
I/O and Shell Scripting File Descriptors Redirecting Standard Error Shell Scripts Making a Shell Script Executable Specifying Which Shell Will Run a Script Comments in Shell Scripts File Descriptors Resources
Introduction to UNIX. Logging in. Basic System Architecture 10/7/10. most systems have graphical login on Linux machines
 Introduction to UNIX Logging in Basic system architecture Getting help Intro to shell (tcsh) Basic UNIX File Maintenance Intro to emacs I/O Redirection Shell scripts Logging in most systems have graphical
Introduction to UNIX Logging in Basic system architecture Getting help Intro to shell (tcsh) Basic UNIX File Maintenance Intro to emacs I/O Redirection Shell scripts Logging in most systems have graphical
COMS 6100 Class Notes 3
 COMS 6100 Class Notes 3 Daniel Solus September 1, 2016 1 General Remarks The class was split into two main sections. We finished our introduction to Linux commands by reviewing Linux commands I and II
COMS 6100 Class Notes 3 Daniel Solus September 1, 2016 1 General Remarks The class was split into two main sections. We finished our introduction to Linux commands by reviewing Linux commands I and II
EECS 470 Lab 5. Linux Shell Scripting. Friday, 1 st February, 2018
 EECS 470 Lab 5 Linux Shell Scripting Department of Electrical Engineering and Computer Science College of Engineering University of Michigan Friday, 1 st February, 2018 (University of Michigan) Lab 5:
EECS 470 Lab 5 Linux Shell Scripting Department of Electrical Engineering and Computer Science College of Engineering University of Michigan Friday, 1 st February, 2018 (University of Michigan) Lab 5:
SHELL SCRIPT BASIC. UNIX Programming 2015 Fall by Euiseong Seo
 SHELL SCRIPT BASIC UNIX Programming 2015 Fall by Euiseong Seo Shell Script! Interactive shell sequentially executes a series of commands! Some tasks are repetitive and automatable! They are what programs
SHELL SCRIPT BASIC UNIX Programming 2015 Fall by Euiseong Seo Shell Script! Interactive shell sequentially executes a series of commands! Some tasks are repetitive and automatable! They are what programs
Editors in Unix come in two general flavours:
 Review notes #2 1. Unix account 2.Login: with a terminal or using telnet or ssh 3. Change password 4. Must logout! 5. Emails: (a) mutt (b) pine (c).forward file 6.Basic commands: who, ls, cat, more, man
Review notes #2 1. Unix account 2.Login: with a terminal or using telnet or ssh 3. Change password 4. Must logout! 5. Emails: (a) mutt (b) pine (c).forward file 6.Basic commands: who, ls, cat, more, man
1 Installation (briefly)
 Jumpstart Linux Bo Waggoner Updated: 2014-09-15 Abstract A basic, rapid tutorial on Linux and its command line for the absolute beginner. Prerequisites: a computer on which to install, a DVD and/or USB
Jumpstart Linux Bo Waggoner Updated: 2014-09-15 Abstract A basic, rapid tutorial on Linux and its command line for the absolute beginner. Prerequisites: a computer on which to install, a DVD and/or USB
More Raspian. An editor Configuration files Shell scripts Shell variables System admin
 More Raspian An editor Configuration files Shell scripts Shell variables System admin Nano, a simple editor Nano does not require the mouse. You must use your keyboard to move around the file and make
More Raspian An editor Configuration files Shell scripts Shell variables System admin Nano, a simple editor Nano does not require the mouse. You must use your keyboard to move around the file and make
Basic Linux (Bash) Commands
 Basic Linux (Bash) Commands Hint: Run commands in the emacs shell (emacs -nw, then M-x shell) instead of the terminal. It eases searching for and revising commands and navigating and copying-and-pasting
Basic Linux (Bash) Commands Hint: Run commands in the emacs shell (emacs -nw, then M-x shell) instead of the terminal. It eases searching for and revising commands and navigating and copying-and-pasting
Introduction. File System. Note. Achtung!
 3 Unix Shell 1: Introduction Lab Objective: Explore the basics of the Unix Shell. Understand how to navigate and manipulate file directories. Introduce the Vim text editor for easy writing and editing
3 Unix Shell 1: Introduction Lab Objective: Explore the basics of the Unix Shell. Understand how to navigate and manipulate file directories. Introduce the Vim text editor for easy writing and editing
Table of contents. Our goal. Notes. Notes. Notes. Summer June 29, Our goal is to see how we can use Unix as a tool for developing programs
 Summer 2010 Department of Computer Science and Engineering York University Toronto June 29, 2010 1 / 36 Table of contents 1 2 3 4 2 / 36 Our goal Our goal is to see how we can use Unix as a tool for developing
Summer 2010 Department of Computer Science and Engineering York University Toronto June 29, 2010 1 / 36 Table of contents 1 2 3 4 2 / 36 Our goal Our goal is to see how we can use Unix as a tool for developing
B a s h s c r i p t i n g
 8 Bash Scripting Any self-respecting hacker must be able to write scripts. For that matter, any selfrespecting Linux administrator must be able to script. Hackers often need to automate commands, sometimes
8 Bash Scripting Any self-respecting hacker must be able to write scripts. For that matter, any selfrespecting Linux administrator must be able to script. Hackers often need to automate commands, sometimes
Vi & Shell Scripting
 Vi & Shell Scripting Comp-206 : Introduction to Week 3 Joseph Vybihal Computer Science McGill University Announcements Sina Meraji's office hours Trottier 3rd floor open area Tuesday 1:30 2:30 PM Thursday
Vi & Shell Scripting Comp-206 : Introduction to Week 3 Joseph Vybihal Computer Science McGill University Announcements Sina Meraji's office hours Trottier 3rd floor open area Tuesday 1:30 2:30 PM Thursday
Assignment clarifications
 Assignment clarifications How many errors to print? at most 1 per token. Interpretation of white space in { } treat as a valid extension, involving white space characters. Assignment FAQs have been updated.
Assignment clarifications How many errors to print? at most 1 per token. Interpretation of white space in { } treat as a valid extension, involving white space characters. Assignment FAQs have been updated.
Scripting Languages Course 1. Diana Trandabăț
 Scripting Languages Course 1 Diana Trandabăț Master in Computational Linguistics - 1 st year 2017-2018 Today s lecture Introduction to scripting languages What is a script? What is a scripting language
Scripting Languages Course 1 Diana Trandabăț Master in Computational Linguistics - 1 st year 2017-2018 Today s lecture Introduction to scripting languages What is a script? What is a scripting language
Introduction to Linux
 Introduction to Linux Prof. Jin-Soo Kim( jinsookim@skku.edu) TA - Kisik Jeong (kisik@csl.skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu What is Linux? A Unix-like operating
Introduction to Linux Prof. Jin-Soo Kim( jinsookim@skku.edu) TA - Kisik Jeong (kisik@csl.skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu What is Linux? A Unix-like operating
Shell. SSE2034: System Software Experiment 3, Fall 2018, Jinkyu Jeong
 Shell Prof. Jinkyu Jeong (Jinkyu@skku.edu) TA -- Minwoo Ahn (minwoo.ahn@csl.skku.edu) TA -- Donghyun Kim (donghyun.kim@csl.skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu
Shell Prof. Jinkyu Jeong (Jinkyu@skku.edu) TA -- Minwoo Ahn (minwoo.ahn@csl.skku.edu) TA -- Donghyun Kim (donghyun.kim@csl.skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu
Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades Q2
 Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades 2017-2018 Q2 Facultat d Informàtica de Barcelona This first lab session is focused on getting experience in working
Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades 2017-2018 Q2 Facultat d Informàtica de Barcelona This first lab session is focused on getting experience in working
 http://xkcd.com/208/ 1. Review of pipes 2. Regular expressions 3. sed 4. awk 5. Editing Files 6. Shell loops 7. Shell scripts cat seqs.fa >0! TGCAGGTATATCTATTAGCAGGTTTAATTTTGCCTGCACTTGGTTGGGTACATTATTTTAAGTGTATTTGACAAG!
http://xkcd.com/208/ 1. Review of pipes 2. Regular expressions 3. sed 4. awk 5. Editing Files 6. Shell loops 7. Shell scripts cat seqs.fa >0! TGCAGGTATATCTATTAGCAGGTTTAATTTTGCCTGCACTTGGTTGGGTACATTATTTTAAGTGTATTTGACAAG!
Advanced Unix Programming Module 03 Raju Alluri spurthi.com
 Advanced Unix Programming Module 03 Raju Alluri askraju @ spurthi.com Advanced Unix Programming: Module 3 Shells & Shell Programming Environment Variables Writing Simple Shell Programs (shell scripts)
Advanced Unix Programming Module 03 Raju Alluri askraju @ spurthi.com Advanced Unix Programming: Module 3 Shells & Shell Programming Environment Variables Writing Simple Shell Programs (shell scripts)
Unix as a Platform Exercises. Course Code: OS-01-UNXPLAT
 Unix as a Platform Exercises Course Code: OS-01-UNXPLAT Working with Unix 1. Use the on-line manual page to determine the option for cat, which causes nonprintable characters to be displayed. Run the command
Unix as a Platform Exercises Course Code: OS-01-UNXPLAT Working with Unix 1. Use the on-line manual page to determine the option for cat, which causes nonprintable characters to be displayed. Run the command
Introduction to UNIX. SURF Research Boot Camp April Jeroen Engelberts Consultant Supercomputing
 Introduction to UNIX SURF Research Boot Camp April 2018 Jeroen Engelberts jeroen.engelberts@surfsara.nl Consultant Supercomputing Outline Introduction to UNIX What is UNIX? (Short) history of UNIX Cartesius
Introduction to UNIX SURF Research Boot Camp April 2018 Jeroen Engelberts jeroen.engelberts@surfsara.nl Consultant Supercomputing Outline Introduction to UNIX What is UNIX? (Short) history of UNIX Cartesius
The Unix Shell & Shell Scripts
 The Unix Shell & Shell Scripts You should do steps 1 to 7 before going to the lab. Use the Linux system you installed in the previous lab. In the lab do step 8, the TA may give you additional exercises
The Unix Shell & Shell Scripts You should do steps 1 to 7 before going to the lab. Use the Linux system you installed in the previous lab. In the lab do step 8, the TA may give you additional exercises
Introduction to Linux (Part II) BUPT/QMUL 2018/03/21
 Introduction to Linux (Part II) BUPT/QMUL 2018/03/21 Contents 10. vi 11. Other commands 12. Developing tools 2 10. Editor - vi Text editor Insert mode Override mode Use sub-commands Tradition tools and
Introduction to Linux (Part II) BUPT/QMUL 2018/03/21 Contents 10. vi 11. Other commands 12. Developing tools 2 10. Editor - vi Text editor Insert mode Override mode Use sub-commands Tradition tools and
Essential Skills for Bioinformatics: Unix/Linux
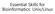 Essential Skills for Bioinformatics: Unix/Linux SHELL SCRIPTING Overview Bash, the shell we have used interactively in this course, is a full-fledged scripting language. Unlike Python, Bash is not a general-purpose
Essential Skills for Bioinformatics: Unix/Linux SHELL SCRIPTING Overview Bash, the shell we have used interactively in this course, is a full-fledged scripting language. Unlike Python, Bash is not a general-purpose
Additional Installation Information
 SNS Appliance Reference, on page 1 VMware Virtual Machine, on page 3 Linux KVM, on page 16 Microsoft Hyper-V, on page 19 SNS Appliance Reference Create a Bootable USB Device to Install Cisco ISE Use the
SNS Appliance Reference, on page 1 VMware Virtual Machine, on page 3 Linux KVM, on page 16 Microsoft Hyper-V, on page 19 SNS Appliance Reference Create a Bootable USB Device to Install Cisco ISE Use the
Cisco IOS Shell. Finding Feature Information. Prerequisites for Cisco IOS.sh. Last Updated: December 14, 2012
 Cisco IOS Shell Last Updated: December 14, 2012 The Cisco IOS Shell (IOS.sh) feature provides shell scripting capability to the Cisco IOS command-lineinterface (CLI) environment. Cisco IOS.sh enhances
Cisco IOS Shell Last Updated: December 14, 2012 The Cisco IOS Shell (IOS.sh) feature provides shell scripting capability to the Cisco IOS command-lineinterface (CLI) environment. Cisco IOS.sh enhances
THE HONG KONG POLYTECHNIC UNIVERSITY Department of Electronic and Information Engineering
 THE HONG KONG POLYTECHNIC UNIVERSITY Department of Electronic and Information Engineering ENG224 Information Technology Part I: Computers and the Internet Laboratory 2 Linux Shell Commands and vi Editor
THE HONG KONG POLYTECHNIC UNIVERSITY Department of Electronic and Information Engineering ENG224 Information Technology Part I: Computers and the Internet Laboratory 2 Linux Shell Commands and vi Editor
UNIX shell scripting
 UNIX shell scripting EECS 2031 Summer 2014 Przemyslaw Pawluk June 17, 2014 What we will discuss today Introduction Control Structures User Input Homework Table of Contents Introduction Control Structures
UNIX shell scripting EECS 2031 Summer 2014 Przemyslaw Pawluk June 17, 2014 What we will discuss today Introduction Control Structures User Input Homework Table of Contents Introduction Control Structures
Introduction to Linux
 Introduction to Linux Prof. Jin-Soo Kim( jinsookim@skku.edu) TA - Dong-Yun Lee (dylee@csl.skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu What is Linux? A Unix-like operating
Introduction to Linux Prof. Jin-Soo Kim( jinsookim@skku.edu) TA - Dong-Yun Lee (dylee@csl.skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu What is Linux? A Unix-like operating
There are some string operators that can be used in the test statement to perform string comparison.
 ACS-294- Unix (Winter Term, 26-7) Part II: Shell Programming Page 3 The test also returns a nonzero exit value if there is no argument: test String Operators There are some string operators that can be
ACS-294- Unix (Winter Term, 26-7) Part II: Shell Programming Page 3 The test also returns a nonzero exit value if there is no argument: test String Operators There are some string operators that can be
Exercise sheet 1 To be corrected in tutorials in the week from 23/10/2017 to 27/10/2017
 Einführung in die Programmierung für Physiker WS 207/208 Marc Wagner Francesca Cuteri: cuteri@th.physik.uni-frankfurt.de Alessandro Sciarra: sciarra@th.physik.uni-frankfurt.de Exercise sheet To be corrected
Einführung in die Programmierung für Physiker WS 207/208 Marc Wagner Francesca Cuteri: cuteri@th.physik.uni-frankfurt.de Alessandro Sciarra: sciarra@th.physik.uni-frankfurt.de Exercise sheet To be corrected
EECS2301. Example. Testing 3/22/2017. Linux/Unix Part 3. for SCRIPT in /path/to/scripts/dir/* do if [ -f $SCRIPT -a -x $SCRIPT ] then $SCRIPT fi done
![EECS2301. Example. Testing 3/22/2017. Linux/Unix Part 3. for SCRIPT in /path/to/scripts/dir/* do if [ -f $SCRIPT -a -x $SCRIPT ] then $SCRIPT fi done EECS2301. Example. Testing 3/22/2017. Linux/Unix Part 3. for SCRIPT in /path/to/scripts/dir/* do if [ -f $SCRIPT -a -x $SCRIPT ] then $SCRIPT fi done](/thumbs/80/82144305.jpg) Warning: These notes are not complete, it is a Skelton that will be modified/add-to in the class. If you want to us them for studying, either attend the class or get the completed notes from someone who
Warning: These notes are not complete, it is a Skelton that will be modified/add-to in the class. If you want to us them for studying, either attend the class or get the completed notes from someone who
More Scripting Techniques Scripting Process Example Script
 More Scripting Techniques Scripting Process Example Script 1 arguments to scripts positional parameters input using read exit status test program, also known as [ if statements error messages 2 case statement
More Scripting Techniques Scripting Process Example Script 1 arguments to scripts positional parameters input using read exit status test program, also known as [ if statements error messages 2 case statement
Basics. I think that the later is better.
 Basics Before we take up shell scripting, let s review some of the basic features and syntax of the shell, specifically the major shells in the sh lineage. Command Editing If you like vi, put your shell
Basics Before we take up shell scripting, let s review some of the basic features and syntax of the shell, specifically the major shells in the sh lineage. Command Editing If you like vi, put your shell
Command Line Interface The basics
 Command Line Interface The basics Marco Berghoff, SCC, KIT Steinbuch Centre for Computing (SCC) Funding: www.bwhpc-c5.de Motivation In the Beginning was the Command Line by Neal Stephenson In contrast
Command Line Interface The basics Marco Berghoff, SCC, KIT Steinbuch Centre for Computing (SCC) Funding: www.bwhpc-c5.de Motivation In the Beginning was the Command Line by Neal Stephenson In contrast
 http://xkcd.com/208/ 1. Review of pipes 2. Regular expressions 3. sed 4. Editing Files 5. Shell loops 6. Shell scripts cat seqs.fa >0! TGCAGGTATATCTATTAGCAGGTTTAATTTTGCCTGCACTTGGTTGGGTACATTATTTTAAGTGTATTTGACAAG!
http://xkcd.com/208/ 1. Review of pipes 2. Regular expressions 3. sed 4. Editing Files 5. Shell loops 6. Shell scripts cat seqs.fa >0! TGCAGGTATATCTATTAGCAGGTTTAATTTTGCCTGCACTTGGTTGGGTACATTATTTTAAGTGTATTTGACAAG!
Introduction in Unix. Linus Torvalds Ken Thompson & Dennis Ritchie
 Introduction in Unix Linus Torvalds Ken Thompson & Dennis Ritchie My name: John Donners John.Donners@surfsara.nl Consultant at SURFsara And Cedric Nugteren Cedric.Nugteren@surfsara.nl Consultant at SURFsara
Introduction in Unix Linus Torvalds Ken Thompson & Dennis Ritchie My name: John Donners John.Donners@surfsara.nl Consultant at SURFsara And Cedric Nugteren Cedric.Nugteren@surfsara.nl Consultant at SURFsara
ITST Searching, Extracting & Archiving Data
 ITST 1136 - Searching, Extracting & Archiving Data Name: Step 1 Sign into a Pi UN = pi PW = raspberry Step 2 - Grep - One of the most useful and versatile commands in a Linux terminal environment is the
ITST 1136 - Searching, Extracting & Archiving Data Name: Step 1 Sign into a Pi UN = pi PW = raspberry Step 2 - Grep - One of the most useful and versatile commands in a Linux terminal environment is the
UNIX System Programming Lecture 3: BASH Programming
 UNIX System Programming Outline Filesystems Redirection Shell Programming Reference BLP: Chapter 2 BFAQ: Bash FAQ BMAN: Bash man page BPRI: Bash Programming Introduction BABS: Advanced Bash Scripting Guide
UNIX System Programming Outline Filesystems Redirection Shell Programming Reference BLP: Chapter 2 BFAQ: Bash FAQ BMAN: Bash man page BPRI: Bash Programming Introduction BABS: Advanced Bash Scripting Guide
Std: XI CHAPTER-3 LINUX
 Commands: General format: Command Option Argument Command: ls - Lists the contents of a file. Option: Begins with minus sign (-) ls a Lists including the hidden files. Argument refers to the name of a
Commands: General format: Command Option Argument Command: ls - Lists the contents of a file. Option: Begins with minus sign (-) ls a Lists including the hidden files. Argument refers to the name of a
Additional Installation Information
 SNS Appliance Reference, on page 1 VMware Virtual Machine, on page 3 Linux KVM, on page 18 Microsoft Hyper-V, on page 21 SNS Appliance Reference Create a Bootable USB Device to Install Cisco ISE Use the
SNS Appliance Reference, on page 1 VMware Virtual Machine, on page 3 Linux KVM, on page 18 Microsoft Hyper-V, on page 21 SNS Appliance Reference Create a Bootable USB Device to Install Cisco ISE Use the
Additional Installation Information
 SNS Appliance Reference, on page 1 VMware Virtual Machine, on page 3 Linux KVM, on page 18 Microsoft Hyper-V, on page 21 SNS Appliance Reference Create a Bootable USB Device to Install Cisco ISE Use the
SNS Appliance Reference, on page 1 VMware Virtual Machine, on page 3 Linux KVM, on page 18 Microsoft Hyper-V, on page 21 SNS Appliance Reference Create a Bootable USB Device to Install Cisco ISE Use the
bash Tests and Looping Administrative Shell Scripting COMP2101 Fall 2017
 bash Tests and Looping Administrative Shell Scripting COMP2101 Fall 2017 Command Lists A command is a sequence of commands separated by the operators ; & && and ; is used to simply execute commands in
bash Tests and Looping Administrative Shell Scripting COMP2101 Fall 2017 Command Lists A command is a sequence of commands separated by the operators ; & && and ; is used to simply execute commands in
Introduction to Linux Basics Part II. Georgia Advanced Computing Resource Center University of Georgia Suchitra Pakala
 Introduction to Linux Basics Part II 1 Georgia Advanced Computing Resource Center University of Georgia Suchitra Pakala pakala@uga.edu 2 Variables in Shell HOW DOES LINUX WORK? Shell Arithmetic I/O and
Introduction to Linux Basics Part II 1 Georgia Advanced Computing Resource Center University of Georgia Suchitra Pakala pakala@uga.edu 2 Variables in Shell HOW DOES LINUX WORK? Shell Arithmetic I/O and
Introduction to UNIX Part II
 T H E U N I V E R S I T Y of T E X A S H E A L T H S C I E N C E C E N T E R A T H O U S T O N S C H O O L of H E A L T H I N F O R M A T I O N S C I E N C E S Introduction to UNIX Part II For students
T H E U N I V E R S I T Y of T E X A S H E A L T H S C I E N C E C E N T E R A T H O U S T O N S C H O O L of H E A L T H I N F O R M A T I O N S C I E N C E S Introduction to UNIX Part II For students
Basic UNIX Commands BASIC UNIX COMMANDS. 1. cat command. This command is used to create a file in unix. Syntax: $ cat filename
 Basic UNIX Commands BASIC UNIX COMMANDS 1. cat This is used to create a file in unix. $ cat >filename This is also used for displaying contents in a file. $ cat filename 2. ls It displays the list of files
Basic UNIX Commands BASIC UNIX COMMANDS 1. cat This is used to create a file in unix. $ cat >filename This is also used for displaying contents in a file. $ cat filename 2. ls It displays the list of files
Shell Programming Overview
 Overview Shell programming is a way of taking several command line instructions that you would use in a Unix command prompt and incorporating them into one program. There are many versions of Unix. Some
Overview Shell programming is a way of taking several command line instructions that you would use in a Unix command prompt and incorporating them into one program. There are many versions of Unix. Some
OPERATING SYSTEMS LAB LAB # 6. I/O Redirection and Shell Programming. Shell Programming( I/O Redirection and if-else Statement)
 P a g e 1 OPERATING SYSTEMS LAB LAB 6 I/O Redirection and Shell Programming Lab 6 Shell Programming( I/O Redirection and if-else Statement) P a g e 2 Redirection of Standard output/input i.e. Input - Output
P a g e 1 OPERATING SYSTEMS LAB LAB 6 I/O Redirection and Shell Programming Lab 6 Shell Programming( I/O Redirection and if-else Statement) P a g e 2 Redirection of Standard output/input i.e. Input - Output
This lab exercise is to be submitted at the end of the lab session! passwd [That is the command to change your current password to a new one]
![This lab exercise is to be submitted at the end of the lab session! passwd [That is the command to change your current password to a new one] This lab exercise is to be submitted at the end of the lab session! passwd [That is the command to change your current password to a new one]](/thumbs/93/111834574.jpg) Data and Computer Security (CMPD414) Lab II Topics: secure login, moving into HOME-directory, navigation on Unix, basic commands for vi, Message Digest This lab exercise is to be submitted at the end of
Data and Computer Security (CMPD414) Lab II Topics: secure login, moving into HOME-directory, navigation on Unix, basic commands for vi, Message Digest This lab exercise is to be submitted at the end of
Unix Scripts and Job Scheduling. Overview. Running a Shell Script
 Unix Scripts and Job Scheduling Michael B. Spring Department of Information Science and Telecommunications University of Pittsburgh spring@imap.pitt.edu http://www.sis.pitt.edu/~spring Overview Shell Scripts
Unix Scripts and Job Scheduling Michael B. Spring Department of Information Science and Telecommunications University of Pittsburgh spring@imap.pitt.edu http://www.sis.pitt.edu/~spring Overview Shell Scripts
