Security 08. Black Hat Search Engine Optimisation. SIFT Pty Ltd Australia. Paul Theriault
|
|
|
- Lydia Pamela Todd
- 6 years ago
- Views:
Transcription
1 Security 08 Black Hat Search Engine Optimisation SIFT Pty Ltd Australia Paul Theriault
2 1. Search Engine Optimisation 2. Blackhat techniques explained 3. Security Recommendations
3 Search Engine Optimisation (SEO) Improving your website s ranking in search results Search Engines rank pages based upon Keywords Links Magic (of the Top Secret Propriety Variety) SEO involves creating keywords & links to improve the ranking of a website for a given search term
4 White Hat vs Black Hat White Hat: A white hat is the hero or good guy, especially in computing slang, where it refers to an ethical hacker that focuses on securing and protecting IT systems. Black Hat: black hat n. colloq. (orig. U.S.) (a) a villain or criminal, esp. one in a film or other work of fiction; a bad guy ; (b) Computing slang a person who engages in illegal or malicious hacking, creates or distributes computer viruses, etc.
5 Black Hat SEO Black Hat SEO: using tricks to fool the search engines to push your website higher in search results Usually fine line between legitimate and disallowed SEO practices usually comes down to whether the action is deceptive Not illegal in itself, but generally against search engines terms of service
6 Relevance to Security Brand Damage Brand associated with negative keywords Brand associated with undesirable websites Customer mistakes another site for you own Lost sales & revenue Phishing Website exploited by blackhats - Brand damage - Delisted from search engines
7 1. Search Engine Optimisation 2. Blackhat techniques explained 3. Security Recommendations
8 Search Engines Simplified Search Engines rank pages by examining: Keyword Search Occurrence, keyword density, page location Links relationships between pages & sites ranking of origin or destination This is done by Search Engine Bots scour pages for keywords, links and other characteristics Blackhat SEO often aims to trick the bots
9 Search Ranking Ranking of a page for a given search phrase
10 Black Hat SEO Manipulating Content Keyword stuffing Cloaking Content Theft Manipulating Links Link spamming Link farms Impacts
11 Keyword Stuffing & Cloaking Keyword Stuffing Increasing the number of occurrences of keywords Often hidden from users, but visible to search engine bots Hiding keywords behind images, in the background, off the screen etc Not really relevant to security just be aware of it Cloaking Similar to keyword stuffing Show one page to the search bot, another to the user
12 Cloaking Yahoo! caught cloaking (
13 Cloaking
14 Content Theft Copy content from existing website May allow a site to steal another site s ranking Search Engines attempt to weed out duplicates Which site is the original? Stolen content often used in link farms
15 Manipulating Links links from other sites are like a vote for your site in search rankings Depends on who the link is from though Higher ranking of the linking site, better the vote Blackhats perform many activities to generate links and networks
16 Link Farms Networks of fake websites (thousands) Site content is often copied, or non-sensical designed for search engine bots not people Create links on these pages to boost the ranking of another site
17 Link Spamming Comment Spam Relevant to you if your website allows feedback or hosts forums etc. Cross-site scripting vulnerabilities Users are allowed to insert malicious scripts into comments, forum posts Blackhats use your website ranking to increase their own sites rankings May reduce your sites ranking
18 Brand Damage Searching for negative keywords results in your website Searching for your brand results in competitors or undesirable sites
19 Google Bombing
20 Google Bombing
21 Page Hijacking?
22 Page Hijacking?
23 Page Hijacking?
24 Page Hijacking
25 Page Hijacking Impacts Brand Damage Customers choose competitor s website Brand Theft Used in Phishing Fake login page present to steal login credentials Serving Malware For example, installing key loggers on customers machines
26 1. Search Engine Optimisation 2. Blackhat techniques explained 3. Security Recommendations
27 Security Recommendations Monitor search results and register page with search engines Implement mechanisms to prevent comment spam & similar Ensure website and free from Cross-site Scripting and similar issues Perform search engine optimisation!
28 Monitor search results Use alerts to identify people ripping off your content Google provides a tool to aid it s web crawler Reduces the chance of penalties or delisting Contact other search engines
29 Prevent Comment Spam Prevent Comment Spam Authenticate user prior comment Use captcha check to prevent automated spam Only allow plaintext in comments No HTML or JavaScript
30 Ensure website is secure Adhere to secure development practices Open Web Application Standards Project (OWASP) Remove Cross-site scripting bugs (and similar) secure development standards perform application security testing
31 Whitehat Search Engine Optimisation Higher ranked sites have higher influence Best way to prevent illegitimate site beating you in rankings is to be the top! easier said than done using Black Hat SEO techniques may result in removal from search engine index Follow search engine guidelines
32 Questions?
33 Security 08 Black Hat Search Engine Optimisation SIFT Pty Ltd Australia Paul Theriault
WEBSITES PUBLISHING. Website is published by uploading files on the remote server which is provided by the hosting company.
 WEBSITES PUBLISHING http://www.tutorialspoint.com/internet_technologies/website_publishing.htm Website publishing is the process of uploading content on the internet. It includes: uploading files updating
WEBSITES PUBLISHING http://www.tutorialspoint.com/internet_technologies/website_publishing.htm Website publishing is the process of uploading content on the internet. It includes: uploading files updating
Below, we will walk through the three main elements of the algorithm, which include Domain Attributes, On-Page and Off-Page factors.
 Search engine optimization is the active practicing of improving your websites ability to rank in the natural search engine results. Each of the major search engines have a proprietary algorithm that makes
Search engine optimization is the active practicing of improving your websites ability to rank in the natural search engine results. Each of the major search engines have a proprietary algorithm that makes
Online Threats. This include human using them!
 Online Threats There are many dangers from using the web (and computer in general). One should watch out for malware, automated programs designed to cause harm to you, your data, and your system. You are
Online Threats There are many dangers from using the web (and computer in general). One should watch out for malware, automated programs designed to cause harm to you, your data, and your system. You are
Basics of SEO Published on: 20 September 2017
 Published on: 20 September 2017 DISCLAIMER The data in the tutorials is supposed to be one for reference. We have made sure that maximum errors have been rectified. Inspite of that, we (ECTI and the authors)
Published on: 20 September 2017 DISCLAIMER The data in the tutorials is supposed to be one for reference. We have made sure that maximum errors have been rectified. Inspite of that, we (ECTI and the authors)
deseo: Combating Search-Result Poisoning Yu USF
 deseo: Combating Search-Result Poisoning Yu Jin @MSCS USF Your Google is not SAFE! SEO Poisoning - A new way to spread malware! Why choose SE? 22.4% of Google searches in the top 100 results > 50% for
deseo: Combating Search-Result Poisoning Yu Jin @MSCS USF Your Google is not SAFE! SEO Poisoning - A new way to spread malware! Why choose SE? 22.4% of Google searches in the top 100 results > 50% for
Web Application Security. Philippe Bogaerts
 Web Application Security Philippe Bogaerts OWASP TOP 10 3 Aim of the OWASP Top 10 educate developers, designers, architects and organizations about the consequences of the most common web application security
Web Application Security Philippe Bogaerts OWASP TOP 10 3 Aim of the OWASP Top 10 educate developers, designers, architects and organizations about the consequences of the most common web application security
CIS 4360 Secure Computer Systems XSS
 CIS 4360 Secure Computer Systems XSS Professor Qiang Zeng Spring 2017 Some slides are adapted from the web pages by Kallin and Valbuena Previous Class Two important criteria to evaluate an Intrusion Detection
CIS 4360 Secure Computer Systems XSS Professor Qiang Zeng Spring 2017 Some slides are adapted from the web pages by Kallin and Valbuena Previous Class Two important criteria to evaluate an Intrusion Detection
AffiliateBeginnersGuide.com
 1 of 5 AffiliateBeginnersGuide.com Web site catalog - links to guides RSS Feed: http://www.affiliatebeginnersguide.com/affbgfeed.rss Main page http://www.affiliatebeginnersguide.com/ Main page Affiliate
1 of 5 AffiliateBeginnersGuide.com Web site catalog - links to guides RSS Feed: http://www.affiliatebeginnersguide.com/affbgfeed.rss Main page http://www.affiliatebeginnersguide.com/ Main page Affiliate
Search Engine Optimization (SEO)
 Search Engine Optimization (SEO) Saurabh Chavan, Apoorva Chitre, Husain Bhala Abstract Search engine optimization is often about making small modifications to parts of your website. When viewed individually,
Search Engine Optimization (SEO) Saurabh Chavan, Apoorva Chitre, Husain Bhala Abstract Search engine optimization is often about making small modifications to parts of your website. When viewed individually,
The PKI Lie. The OWASP Foundation Attacking Certificate Based Authentication. OWASP & WASC AppSec 2007 Conference
 The PKI Lie Attacking Certificate Based Authentication Ofer Maor CTO, Hacktics OWASP & WASC AppSec 2007 Conference San Jose Nov 2007 Copyright 2007 - The OWASP Foundation Permission is granted to copy,
The PKI Lie Attacking Certificate Based Authentication Ofer Maor CTO, Hacktics OWASP & WASC AppSec 2007 Conference San Jose Nov 2007 Copyright 2007 - The OWASP Foundation Permission is granted to copy,
ANALYSIS ON OFF-PAGE SEO
 http:// ANALYSIS ON OFF-PAGE SEO 1 Kamlesh Kumar Manji Bhai Patel Research Scholar, Monad University, Hapur (India) ABSTRACT In this paper, natural search engine ranking factors and their effectiveness
http:// ANALYSIS ON OFF-PAGE SEO 1 Kamlesh Kumar Manji Bhai Patel Research Scholar, Monad University, Hapur (India) ABSTRACT In this paper, natural search engine ranking factors and their effectiveness
Hacking Intranet Websites from the Outside
 1 Hacking Intranet Websites from the Outside "JavaScript malware just got a lot more dangerous" Black Hat (Japan) 10.05.2006 Jeremiah Grossman (Founder and CTO) WhiteHat Security 2 WhiteHat Sentinel -
1 Hacking Intranet Websites from the Outside "JavaScript malware just got a lot more dangerous" Black Hat (Japan) 10.05.2006 Jeremiah Grossman (Founder and CTO) WhiteHat Security 2 WhiteHat Sentinel -
Promoting Website CS 4640 Programming Languages for Web Applications
 Promoting Website CS 4640 Programming Languages for Web Applications [Jakob Nielsen and Hoa Loranger, Prioritizing Web Usability, Chapter 5] [Sean McManus, Web Design, Chapter 15] 1 Search Engine Optimization
Promoting Website CS 4640 Programming Languages for Web Applications [Jakob Nielsen and Hoa Loranger, Prioritizing Web Usability, Chapter 5] [Sean McManus, Web Design, Chapter 15] 1 Search Engine Optimization
Web Security II. Slides from M. Hicks, University of Maryland
 Web Security II Slides from M. Hicks, University of Maryland Recall: Putting State to HTTP Web application maintains ephemeral state Server processing often produces intermediate results; not long-lived
Web Security II Slides from M. Hicks, University of Maryland Recall: Putting State to HTTP Web application maintains ephemeral state Server processing often produces intermediate results; not long-lived
Web Application Threats and Remediation. Terry Labach, IST Security Team
 Web Application Threats and Remediation Terry Labach, IST Security Team IST Security Team The problem While we use frewalls and other means to prevent attackers from access to our networks, we encourage
Web Application Threats and Remediation Terry Labach, IST Security Team IST Security Team The problem While we use frewalls and other means to prevent attackers from access to our networks, we encourage
Imperva Incapsula Website Security
 Imperva Incapsula Website Security DA T A SH E E T Application Security from the Cloud Imperva Incapsula cloud-based website security solution features the industry s leading WAF technology, as well as
Imperva Incapsula Website Security DA T A SH E E T Application Security from the Cloud Imperva Incapsula cloud-based website security solution features the industry s leading WAF technology, as well as
Digital Marketing on the platform of Search Engine Optimization A review. Sonika Kanojia Program Coordinator Chandigarh University India.
 Digital Marketing on the platform of Search Engine Optimization A review Sonika Kanojia Program Coordinator Chandigarh University India Abstract Every owner or manager of a company is seeking ways to promote
Digital Marketing on the platform of Search Engine Optimization A review Sonika Kanojia Program Coordinator Chandigarh University India Abstract Every owner or manager of a company is seeking ways to promote
A Review Paper on Network Security Attacks and Defences
 EUROPEAN ACADEMIC RESEARCH Vol. IV, Issue 12/ March 2017 ISSN 2286-4822 www.euacademic.org Impact Factor: 3.4546 (UIF) DRJI Value: 5.9 (B+) A Review Paper on Network Security Attacks and ALLYSA ASHLEY
EUROPEAN ACADEMIC RESEARCH Vol. IV, Issue 12/ March 2017 ISSN 2286-4822 www.euacademic.org Impact Factor: 3.4546 (UIF) DRJI Value: 5.9 (B+) A Review Paper on Network Security Attacks and ALLYSA ASHLEY
Webomania Solutions Pvt. Ltd. 2017
 The other name for link manipulation is Phishing or you can say link manipulation is type of phishing attack done generally to mislead the user to a replica website or a looka-like of some well-known site.
The other name for link manipulation is Phishing or you can say link manipulation is type of phishing attack done generally to mislead the user to a replica website or a looka-like of some well-known site.
Lecture Overview. IN5290 Ethical Hacking
 Lecture Overview IN5290 Ethical Hacking Lecture 6: Web hacking 2, Cross Site Scripting (XSS), Cross Site Request Forgery (CSRF), Session related attacks Universitetet i Oslo Laszlo Erdödi How to use Burp
Lecture Overview IN5290 Ethical Hacking Lecture 6: Web hacking 2, Cross Site Scripting (XSS), Cross Site Request Forgery (CSRF), Session related attacks Universitetet i Oslo Laszlo Erdödi How to use Burp
Lecture 6: Web hacking 2, Cross Site Scripting (XSS), Cross Site Request Forgery (CSRF), Session related attacks
 IN5290 Ethical Hacking Lecture 6: Web hacking 2, Cross Site Scripting (XSS), Cross Site Request Forgery (CSRF), Session related attacks Universitetet i Oslo Laszlo Erdödi Lecture Overview How to use Burp
IN5290 Ethical Hacking Lecture 6: Web hacking 2, Cross Site Scripting (XSS), Cross Site Request Forgery (CSRF), Session related attacks Universitetet i Oslo Laszlo Erdödi Lecture Overview How to use Burp
Advertising Network Affiliate Marketing Algorithm Analytics Auto responder autoresponder Backlinks Blog
 Advertising Network A group of websites where one advertiser controls all or a portion of the ads for all sites. A common example is the Google Search Network, which includes AOL, Amazon,Ask.com (formerly
Advertising Network A group of websites where one advertiser controls all or a portion of the ads for all sites. A common example is the Google Search Network, which includes AOL, Amazon,Ask.com (formerly
Website Audit : Is your website being held back by hidden issues?
 Website Audit : Is your website being held back by hidden issues? What is a Website Audit? A website audit helps determine your site health and what your site may need in order to improve search engine
Website Audit : Is your website being held back by hidden issues? What is a Website Audit? A website audit helps determine your site health and what your site may need in order to improve search engine
SEO Search Engine Optimisation An Intro to SEO. Prepared By: Paul Dobinson Tel
 SEO Search Engine Optimisation An Intro to SEO Prepared By: Paul Dobinson Tel 441-278-1004 paul@bermudayp.com Points - What is SEO - differences SEO vs SEM - Search Engines - Crawlers /Accessibility -
SEO Search Engine Optimisation An Intro to SEO Prepared By: Paul Dobinson Tel 441-278-1004 paul@bermudayp.com Points - What is SEO - differences SEO vs SEM - Search Engines - Crawlers /Accessibility -
Principles of ICT Systems and Data Security
 Principles of ICT Systems and Data Security Ethical Hacking Ethical Hacking What is ethical hacking? Ethical Hacking It is a process where a computer security expert, who specialises in penetration testing
Principles of ICT Systems and Data Security Ethical Hacking Ethical Hacking What is ethical hacking? Ethical Hacking It is a process where a computer security expert, who specialises in penetration testing
SEO News. 15 SEO Fixes for Better Rankings. For SEO, marketing books and guides, visit
 SEO News SEO News and Updates as We Published So Far! For latest news, visit http://www.nigcworld.com/wp/seonews this week latest seo updates google bing yahooothers/ 15 SEO Fixes for Better Rankings 1.
SEO News SEO News and Updates as We Published So Far! For latest news, visit http://www.nigcworld.com/wp/seonews this week latest seo updates google bing yahooothers/ 15 SEO Fixes for Better Rankings 1.
AN OVERVIEW OF SEARCHING AND DISCOVERING WEB BASED INFORMATION RESOURCES
 Journal of Defense Resources Management No. 1 (1) / 2010 AN OVERVIEW OF SEARCHING AND DISCOVERING Cezar VASILESCU Regional Department of Defense Resources Management Studies Abstract: The Internet becomes
Journal of Defense Resources Management No. 1 (1) / 2010 AN OVERVIEW OF SEARCHING AND DISCOVERING Cezar VASILESCU Regional Department of Defense Resources Management Studies Abstract: The Internet becomes
11/6/17. Why Isn t Our Site on the First Page of Google? WHAT WE RE GOING TO COVER SETTING EXPECTATIONS
 Why Isn t Our Site on the First Page of Google? WHAT WE RE GOING TO COVER Setting expectations Understanding search engine optimization High level overview of ranking factors Why Isn t My Site on the First
Why Isn t Our Site on the First Page of Google? WHAT WE RE GOING TO COVER Setting expectations Understanding search engine optimization High level overview of ranking factors Why Isn t My Site on the First
CSCE 813 Internet Security Case Study II: XSS
 CSCE 813 Internet Security Case Study II: XSS Professor Lisa Luo Fall 2017 Outline Cross-site Scripting (XSS) Attacks Prevention 2 What is XSS? Cross-site scripting (XSS) is a code injection attack that
CSCE 813 Internet Security Case Study II: XSS Professor Lisa Luo Fall 2017 Outline Cross-site Scripting (XSS) Attacks Prevention 2 What is XSS? Cross-site scripting (XSS) is a code injection attack that
Search Engine Marketing: Search Engine Marketing Fundamentals
 1 Search Engine Marketing: Search Engine Marketing Fundamentals Title: Search Engine Marketing: Search Engine Marketing Fundamentals Course material - knowledge required - for certification Copyright 2018
1 Search Engine Marketing: Search Engine Marketing Fundamentals Title: Search Engine Marketing: Search Engine Marketing Fundamentals Course material - knowledge required - for certification Copyright 2018
SEARCH ENGINES AND THEIR ABUSE
 UNIT 15 SEARCH ENGINES AND THEIR ABUSE Structure 15.1 Introduction 15.2 Objectives 15.3 What are Search Engines? 15.4 The Process: How a Search Engine Works 15.4.1 Web Crawling 15.4.2 Indexing 15.4.3 Searching
UNIT 15 SEARCH ENGINES AND THEIR ABUSE Structure 15.1 Introduction 15.2 Objectives 15.3 What are Search Engines? 15.4 The Process: How a Search Engine Works 15.4.1 Web Crawling 15.4.2 Indexing 15.4.3 Searching
PROTECTING YOUR BUSINESS ASSETS
 PROTECTING YOUR BUSINESS ASSETS How to Spot Danger Before Your Computer Gets Infected, Your Site Hosts Malware, and Your Credit Card Number Gets Stolen A MyNAMS Presentation by Regina Smola @2012 Regina
PROTECTING YOUR BUSINESS ASSETS How to Spot Danger Before Your Computer Gets Infected, Your Site Hosts Malware, and Your Credit Card Number Gets Stolen A MyNAMS Presentation by Regina Smola @2012 Regina
CHAPTER 8 SECURING INFORMATION SYSTEMS
 CHAPTER 8 SECURING INFORMATION SYSTEMS BY: S. SABRAZ NAWAZ SENIOR LECTURER IN MANAGEMENT & IT SEUSL Learning Objectives Why are information systems vulnerable to destruction, error, and abuse? What is
CHAPTER 8 SECURING INFORMATION SYSTEMS BY: S. SABRAZ NAWAZ SENIOR LECTURER IN MANAGEMENT & IT SEUSL Learning Objectives Why are information systems vulnerable to destruction, error, and abuse? What is
Digital Marketing Overview of Digital Marketing Website Creation Search Engine Optimization What is Google Page Rank?
 Digital Marketing Overview of Digital Marketing What is marketing and digital marketing? Understanding Marketing and Digital Marketing Process? Website Creation Understanding about Internet, websites,
Digital Marketing Overview of Digital Marketing What is marketing and digital marketing? Understanding Marketing and Digital Marketing Process? Website Creation Understanding about Internet, websites,
CLOAK OF VISIBILITY : DETECTING WHEN MACHINES BROWSE A DIFFERENT WEB
 CLOAK OF VISIBILITY : DETECTING WHEN MACHINES BROWSE A DIFFERENT WEB CIS 601: Graduate Seminar Prof. S. S. Chung Presented By:- Amol Chaudhari CSU ID 2682329 AGENDA About Introduction Contributions Background
CLOAK OF VISIBILITY : DETECTING WHEN MACHINES BROWSE A DIFFERENT WEB CIS 601: Graduate Seminar Prof. S. S. Chung Presented By:- Amol Chaudhari CSU ID 2682329 AGENDA About Introduction Contributions Background
Vidder PrecisionAccess
 Vidder PrecisionAccess Transparent Multi-Factor Authentication June 2015 910 E HAMILTON AVENUE. SUITE 430. CAMPBELL, CA 95008 P: 408.418.0440 F: 408.706.5590 WWW.VIDDER.COM Table of Contents I. Overview...
Vidder PrecisionAccess Transparent Multi-Factor Authentication June 2015 910 E HAMILTON AVENUE. SUITE 430. CAMPBELL, CA 95008 P: 408.418.0440 F: 408.706.5590 WWW.VIDDER.COM Table of Contents I. Overview...
TOP RANKING FACTORS A QUICK OVERVIEW OF THE TRENDING TOP RANKING FACTORS
 TOP RANKING FACTORS A QUICK OVERVIEW OF THE TRENDING TOP RANKING FACTORS SEO is NOT Dead Plenty of New Algorithm Updates Panda, Penguin, Hummingbird, RankBrain (AI and Deep Learning) New Ranking Factors
TOP RANKING FACTORS A QUICK OVERVIEW OF THE TRENDING TOP RANKING FACTORS SEO is NOT Dead Plenty of New Algorithm Updates Panda, Penguin, Hummingbird, RankBrain (AI and Deep Learning) New Ranking Factors
Please be aware that not every step is necessary for your website, or it may be outside the scope of our agreed-upon deliverables.
 Every client has unique needs for their SEO project. Each SEO project is slightly different. If you have ever been curious as to what we do when we review a client s website, then this checklist provides
Every client has unique needs for their SEO project. Each SEO project is slightly different. If you have ever been curious as to what we do when we review a client s website, then this checklist provides
INF3700 Informasjonsteknologi og samfunn. Application Security. Audun Jøsang University of Oslo Spring 2015
 INF3700 Informasjonsteknologi og samfunn Application Security Audun Jøsang University of Oslo Spring 2015 Outline Application Security Malicious Software Attacks on applications 2 Malicious Software 3
INF3700 Informasjonsteknologi og samfunn Application Security Audun Jøsang University of Oslo Spring 2015 Outline Application Security Malicious Software Attacks on applications 2 Malicious Software 3
Attacks Against Websites. Tom Chothia Computer Security, Lecture 11
 Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
SEOHUNK INTERNATIONAL D-62, Basundhara Apt., Naharkanta, Hanspal, Bhubaneswar, India
 SEOHUNK INTERNATIONAL D-62, Basundhara Apt., Naharkanta, Hanspal, Bhubaneswar, India 752101. p: 305-403-9683 w: www.seohunkinternational.com e: info@seohunkinternational.com DOMAIN INFORMATION: S No. Details
SEOHUNK INTERNATIONAL D-62, Basundhara Apt., Naharkanta, Hanspal, Bhubaneswar, India 752101. p: 305-403-9683 w: www.seohunkinternational.com e: info@seohunkinternational.com DOMAIN INFORMATION: S No. Details
Ethical Hacking. Content Outline: Session 1
 Ethical Hacking Content Outline: Session 1 Ethics & Hacking Hacking history : How it all begin - Why is security needed? - What is ethical hacking? - Ethical Hacker Vs Malicious hacker - Types of Hackers
Ethical Hacking Content Outline: Session 1 Ethics & Hacking Hacking history : How it all begin - Why is security needed? - What is ethical hacking? - Ethical Hacker Vs Malicious hacker - Types of Hackers
Blackhat Search Engine Optimization Techniques (SEO) and Counter Measures
 2018 IJSRST Volume 4 Issue 11 Print ISSN: 2395-6011 Online ISSN: 2395-602X Themed Section: Science and Technology DOI : https://doi.org/10.32628/ijsrst1840117 Blackhat Search Engine Optimization Techniques
2018 IJSRST Volume 4 Issue 11 Print ISSN: 2395-6011 Online ISSN: 2395-602X Themed Section: Science and Technology DOI : https://doi.org/10.32628/ijsrst1840117 Blackhat Search Engine Optimization Techniques
Business Continuity Management
 University of Oslo INF3510 Information Security Autumn 2018 Workshop Questions and s Lecture 8: Risk Management and Business Continuity Management Question 1: Risk factors A possible definition of information
University of Oslo INF3510 Information Security Autumn 2018 Workshop Questions and s Lecture 8: Risk Management and Business Continuity Management Question 1: Risk factors A possible definition of information
Search Engine Optimization (Make your presence online with Addkoncepts)
 Search Engine Optimization Features Included in SEO Brief Products/Services Analysis Level 1 (Regular-SEO) Rs. 7,000/- per Months Level 2 (Advance-SEO) Rs. 12,000/- per Month Primary Keyword Secondary
Search Engine Optimization Features Included in SEO Brief Products/Services Analysis Level 1 (Regular-SEO) Rs. 7,000/- per Months Level 2 (Advance-SEO) Rs. 12,000/- per Month Primary Keyword Secondary
ELEVATESEO. INTERNET TRAFFIC SALES TEAM PRODUCT INFOSHEETS. JUNE V1.0 WEBSITE RANKING STATS. Internet Traffic
 SALES TEAM PRODUCT INFOSHEETS. JUNE 2017. V1.0 1 INTERNET TRAFFIC Internet Traffic Most of your internet traffic will be provided from the major search engines. Social Media services and other referring
SALES TEAM PRODUCT INFOSHEETS. JUNE 2017. V1.0 1 INTERNET TRAFFIC Internet Traffic Most of your internet traffic will be provided from the major search engines. Social Media services and other referring
Manually Create Phishing Page For Facebook 2014
 Manually Create Phishing Page For Facebook 2014 While you are creating phishing page manually you have to do a lot of work Web Templates -- For importing premade template for Gmail, Facebook from SET.
Manually Create Phishing Page For Facebook 2014 While you are creating phishing page manually you have to do a lot of work Web Templates -- For importing premade template for Gmail, Facebook from SET.
Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any
 OWASP Top 10 Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any tester can (and should) do security testing
OWASP Top 10 Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any tester can (and should) do security testing
SEO According to Google
 SEO According to Google An On-Page Optimization Presentation By Rachel Halfhill Lead Copywriter at CDI Agenda Overview Keywords Page Titles URLs Descriptions Heading Tags Anchor Text Alt Text Resources
SEO According to Google An On-Page Optimization Presentation By Rachel Halfhill Lead Copywriter at CDI Agenda Overview Keywords Page Titles URLs Descriptions Heading Tags Anchor Text Alt Text Resources
Finding the Linchpins of the Dark Web: A Study on Topologically Dedicated Hosts on Malicious Web Infrastructures
 Finding the Linchpins of the Dark Web: A Study on Topologically Dedicated Hosts on Malicious Web Infrastructures Zhou Li, Indiana University Bloomington Sumayah Alrwais, Indiana University Bloomington
Finding the Linchpins of the Dark Web: A Study on Topologically Dedicated Hosts on Malicious Web Infrastructures Zhou Li, Indiana University Bloomington Sumayah Alrwais, Indiana University Bloomington
SEO Dubai. SEO Dubai is currently the top ranking SEO agency in Dubai, UAE. First lets get to know what is SEO?
 SEO Dubai Address Contact Person Mobile Number Email JLT DMCC Dubai, United Arab Emirates Jumeirah Lakes Towers 123220 Dubai, United Arab Emirates Manager support@s1seo.com SEO Dubai is currently the top
SEO Dubai Address Contact Person Mobile Number Email JLT DMCC Dubai, United Arab Emirates Jumeirah Lakes Towers 123220 Dubai, United Arab Emirates Manager support@s1seo.com SEO Dubai is currently the top
How Cyber-Criminals Steal and Profit from your Data
 How Cyber-Criminals Steal and Profit from your Data Presented by: Nick Podhradsky, SVP Operations SBS CyberSecurity www.sbscyber.com Consulting Network Security IT Audit Education 1 Agenda Why cybersecurity
How Cyber-Criminals Steal and Profit from your Data Presented by: Nick Podhradsky, SVP Operations SBS CyberSecurity www.sbscyber.com Consulting Network Security IT Audit Education 1 Agenda Why cybersecurity
Web Spam Taxonomy. Zoltán Gyöngyi Hector Garcia-Molina
 Web Spam Taxonomy Zoltán Gyöngyi Hector Garcia-Molina Roadmap Subject Observed behavior Boosting Term-based Link-based Hiding Statistics Challenges AIRWeb'05 Tokyo, May 10, 2005 2 Roadmap Subject Observed
Web Spam Taxonomy Zoltán Gyöngyi Hector Garcia-Molina Roadmap Subject Observed behavior Boosting Term-based Link-based Hiding Statistics Challenges AIRWeb'05 Tokyo, May 10, 2005 2 Roadmap Subject Observed
Cyber Security Guide. For Politicians and Political Parties
 Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
AUDIT REPORT BELMONT TV.COM. Sep 14, Report Content Last Updated. On-Page Optimization. Off-Page Optimization. Keywords Report.
 WEBSITE AUDIT REPORT Report Content Last Updated Sep 14, 217 On-Page Optimization Off-Page Optimization Social Media Keywords Report BELMONT TV.COM Steve.Smith@belmonttv.com 4723 King Street Arlington,
WEBSITE AUDIT REPORT Report Content Last Updated Sep 14, 217 On-Page Optimization Off-Page Optimization Social Media Keywords Report BELMONT TV.COM Steve.Smith@belmonttv.com 4723 King Street Arlington,
Search Engine Visibility Analysis
 2018 Search Engine Visibility Analysis We do the market research, so you don t have to! Report For www.yourclientsite.com Contents Introduction... 2 Website Analysis and Recommendations... 3 Current Status
2018 Search Engine Visibility Analysis We do the market research, so you don t have to! Report For www.yourclientsite.com Contents Introduction... 2 Website Analysis and Recommendations... 3 Current Status
D I G I T A L SIM SCHOOL OF INTERNET MARKETING
 D I G I T A L M A R K E T I N G SCHOOL OF INTERNET MARKETING DIGITAL MARKETING TRAINING SYLLABUS What is Digital Marketing? Why organizations do digital marketing? 4 P's and 4 C's of Marketing What is
D I G I T A L M A R K E T I N G SCHOOL OF INTERNET MARKETING DIGITAL MARKETING TRAINING SYLLABUS What is Digital Marketing? Why organizations do digital marketing? 4 P's and 4 C's of Marketing What is
Mobile Friendly Website. Checks whether your website is responsive. Out of 10. Out of Social
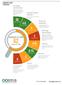 Website Score Overview On-Page Optimization Checks your website for different issues impacting performance and Search Engine Optimization problems. 3 3 WEBSITE SCORE 62 1 1 Competitor Analysis 4.6 5 Analysis
Website Score Overview On-Page Optimization Checks your website for different issues impacting performance and Search Engine Optimization problems. 3 3 WEBSITE SCORE 62 1 1 Competitor Analysis 4.6 5 Analysis
Cyber Vigilantes. Rob Rachwald Director of Security Strategy. Porto Alegre, October 5, 2011
 Cyber Vigilantes Rob Rachwald Director of Security Strategy Porto Alegre, October 5, 2011 Hacking: Industry Analysis Hacking has become industrialized. Attack techniques and vectors keep changing with
Cyber Vigilantes Rob Rachwald Director of Security Strategy Porto Alegre, October 5, 2011 Hacking: Industry Analysis Hacking has become industrialized. Attack techniques and vectors keep changing with
How to do an On-Page SEO Analysis Table of Contents
 How to do an On-Page SEO Analysis Table of Contents Step 1: Keyword Research/Identification Step 2: Quality of Content Step 3: Title Tags Step 4: H1 Headings Step 5: Meta Descriptions Step 6: Site Performance
How to do an On-Page SEO Analysis Table of Contents Step 1: Keyword Research/Identification Step 2: Quality of Content Step 3: Title Tags Step 4: H1 Headings Step 5: Meta Descriptions Step 6: Site Performance
Detecting Spam Web Pages
 Detecting Spam Web Pages Marc Najork Microsoft Research Silicon Valley About me 1989-1993: UIUC (home of NCSA Mosaic) 1993-2001: Digital Equipment/Compaq Started working on web search in 1997 Mercator
Detecting Spam Web Pages Marc Najork Microsoft Research Silicon Valley About me 1989-1993: UIUC (home of NCSA Mosaic) 1993-2001: Digital Equipment/Compaq Started working on web search in 1997 Mercator
Cyber Security & Ethical Hacking Training. Introduction to Cyber Security Introduction to Cyber Security. Linux Operating System and Networking: LINUX
 Cyber Security & Ethical Hacking Training. Introduction to Cyber Security Introduction to Cyber Security HTML PHP Database Linux Operating System and Networking: LINUX NETWORKING Information Gathering:
Cyber Security & Ethical Hacking Training. Introduction to Cyber Security Introduction to Cyber Security HTML PHP Database Linux Operating System and Networking: LINUX NETWORKING Information Gathering:
2.1 WEBSITE SCORE. Website Score Overview. Out of 100. On-Page Optimization. Mobile Friendly Website. Keyword Rankings. Off-Page Optimization.
 WEBSITE AUDIT REPORT Report Content Last Updated Jun 5, 218 On-Page Optimization Off-Page Optimization Social Media Keywords Report FABTECH MOTORSPORTS info@fabtechmotorsports.com 4331 Eucalyptus Avenue
WEBSITE AUDIT REPORT Report Content Last Updated Jun 5, 218 On-Page Optimization Off-Page Optimization Social Media Keywords Report FABTECH MOTORSPORTS info@fabtechmotorsports.com 4331 Eucalyptus Avenue
Phishing Read Behind The Lines
 Phishing Read Behind The Lines Veljko Pejović veljko@cs.ucsb.edu What is Phishing? "Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and
Phishing Read Behind The Lines Veljko Pejović veljko@cs.ucsb.edu What is Phishing? "Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and
OWASP Top 10 Risks. Many thanks to Dave Wichers & OWASP
 OWASP Top 10 Risks Dean.Bushmiller@ExpandingSecurity.com Many thanks to Dave Wichers & OWASP My Mom I got on the email and did a google on my boy My boy works in this Internet thing He makes cyber cafes
OWASP Top 10 Risks Dean.Bushmiller@ExpandingSecurity.com Many thanks to Dave Wichers & OWASP My Mom I got on the email and did a google on my boy My boy works in this Internet thing He makes cyber cafes
5 Choosing keywords Initially choosing keywords Frequent and rare keywords Evaluating the competition rates of search
 Seo tutorial Seo tutorial Introduction to seo... 4 1. General seo information... 5 1.1 History of search engines... 5 1.2 Common search engine principles... 6 2. Internal ranking factors... 8 2.1 Web page
Seo tutorial Seo tutorial Introduction to seo... 4 1. General seo information... 5 1.1 History of search engines... 5 1.2 Common search engine principles... 6 2. Internal ranking factors... 8 2.1 Web page
A web directory lists web sites by category and subcategory. Web directory entries are usually found and categorized by humans.
 1 After WWW protocol was introduced in Internet in the early 1990s and the number of web servers started to grow, the first technology that appeared to be able to locate them were Internet listings, also
1 After WWW protocol was introduced in Internet in the early 1990s and the number of web servers started to grow, the first technology that appeared to be able to locate them were Internet listings, also
Ethical Hacking and. Version 6. Spamming
 Ethical Hacking and Countermeasures Version 6 Module XL Spamming News Source: http://www.nzherald.co.nz/ Module Objective This module will familiarize you with: Spamming Techniques used by Spammers How
Ethical Hacking and Countermeasures Version 6 Module XL Spamming News Source: http://www.nzherald.co.nz/ Module Objective This module will familiarize you with: Spamming Techniques used by Spammers How
SEO Factors Influencing National Search Results
 SEO Factors Influencing National Search Results 1. Domain Age Domain Factors 2. Keyword Appears in Top Level Domain: Doesn t give the boost that it used to, but having your keyword in the domain still
SEO Factors Influencing National Search Results 1. Domain Age Domain Factors 2. Keyword Appears in Top Level Domain: Doesn t give the boost that it used to, but having your keyword in the domain still
Use and Abuse of Anti-Spam White/Black Lists
 Page 1 of 5 Use and Abuse of Anti-Spam White/Black Lists September 26, 2006 White and Black lists are standard spam filters. Their typically simple interface, provide a way to quickly identify emails as
Page 1 of 5 Use and Abuse of Anti-Spam White/Black Lists September 26, 2006 White and Black lists are standard spam filters. Their typically simple interface, provide a way to quickly identify emails as
Deep Sea Phishing: Examples & Countermeasures
 Deep Sea Phishing: Examples & Countermeasures Phishing is impersonation of a person or brand. Our focus is email-based phishing. Phishing is not malware, spam, or xss, although these often coincide. Current
Deep Sea Phishing: Examples & Countermeasures Phishing is impersonation of a person or brand. Our focus is email-based phishing. Phishing is not malware, spam, or xss, although these often coincide. Current
Computer Network Vulnerabilities
 Computer Network Vulnerabilities Objectives Explain how routers are used to protect networks Describe firewall technology Describe intrusion detection systems Describe honeypots Routers Routers are like
Computer Network Vulnerabilities Objectives Explain how routers are used to protect networks Describe firewall technology Describe intrusion detection systems Describe honeypots Routers Routers are like
Advanced Digital Markeitng Training Syllabus
 Advanced Digital Markeitng Training Syllabus Digital Marketing Overview What is marketing? What is Digital Marketing? Understanding Marketing Process Why Digital Marketing Wins Over Traditional Marketing?
Advanced Digital Markeitng Training Syllabus Digital Marketing Overview What is marketing? What is Digital Marketing? Understanding Marketing Process Why Digital Marketing Wins Over Traditional Marketing?
Europcar International Franchisee Websites Search Engine Optimisation
 Introduction Everybody would like their site to be found easily on search engines. There is no magic that can guarantee this, but there are some principles that by following will help in your search engine
Introduction Everybody would like their site to be found easily on search engines. There is no magic that can guarantee this, but there are some principles that by following will help in your search engine
Security and Privacy. Xin Liu Computer Science University of California, Davis. Introduction 1-1
 Security and Privacy Xin Liu Computer Science University of California, Davis Introduction 1-1 What is network security? Confidentiality: only sender, intended receiver should understand message contents
Security and Privacy Xin Liu Computer Science University of California, Davis Introduction 1-1 What is network security? Confidentiality: only sender, intended receiver should understand message contents
CS47300 Web Information Search and Management
 CS47300 Web Information Search and Management Search Engine Optimization Prof. Chris Clifton 31 October 2018 What is Search Engine Optimization? 90% of search engine clickthroughs are on the first page
CS47300 Web Information Search and Management Search Engine Optimization Prof. Chris Clifton 31 October 2018 What is Search Engine Optimization? 90% of search engine clickthroughs are on the first page
DRIVE YOUR CONTENT WITH SEO
 DRIVE YOUR CONTENT WITH SEO TODAY. 1) Google s beliefs 2) Updates 3) Technical Considerations 1) Focus on the user and all else will follow. 2) It s best to do one thing really, really well. 3) Fast is
DRIVE YOUR CONTENT WITH SEO TODAY. 1) Google s beliefs 2) Updates 3) Technical Considerations 1) Focus on the user and all else will follow. 2) It s best to do one thing really, really well. 3) Fast is
SEO 1 8 O C T O B E R 1 7
 SEO 1 8 O C T O B E R 1 7 Search Engine Optimisation (SEO) Search engines Search Engine Market Global Search Engine Market Share June 2017 90.00% 80.00% 79.29% 70.00% 60.00% 50.00% 40.00% 30.00% 20.00%
SEO 1 8 O C T O B E R 1 7 Search Engine Optimisation (SEO) Search engines Search Engine Market Global Search Engine Market Share June 2017 90.00% 80.00% 79.29% 70.00% 60.00% 50.00% 40.00% 30.00% 20.00%
CompTIA Security+ Malware. Threats and Vulnerabilities Vulnerability Management
 CompTIA Security+ Lecture Six Threats and Vulnerabilities Vulnerability Management Copyright 2011 - VTC Malware Malicious code refers to software threats to network and systems, including viruses, Trojan
CompTIA Security+ Lecture Six Threats and Vulnerabilities Vulnerability Management Copyright 2011 - VTC Malware Malicious code refers to software threats to network and systems, including viruses, Trojan
Wayward Wi-Fi. How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk
 Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
e-commerce Study Guide Test 2. Security Chapter 10
 e-commerce Study Guide Test 2. Security Chapter 10 True/False Indicate whether the sentence or statement is true or false. 1. Necessity refers to preventing data delays or denials (removal) within the
e-commerce Study Guide Test 2. Security Chapter 10 True/False Indicate whether the sentence or statement is true or false. 1. Necessity refers to preventing data delays or denials (removal) within the
2 Minute SEO A Basic Introduction to Search Engines
 Page 1 of 6 Extract from XSP Cheat Sheet 2 Minute SEO A Basic Introduction to Search Engines By James Schramko www.xspcheatsheet.com This report is FREE and you may distribute it using ethical marketing
Page 1 of 6 Extract from XSP Cheat Sheet 2 Minute SEO A Basic Introduction to Search Engines By James Schramko www.xspcheatsheet.com This report is FREE and you may distribute it using ethical marketing
BCA (6 th Semester) Teaching Schedule
 BCA (6 th Semester) Teaching Schedule 030010609: DSE8 Introduction to Optimization Objective: To imbibe the concepts of SEO in context of website development, and apply its techniques to improve search
BCA (6 th Semester) Teaching Schedule 030010609: DSE8 Introduction to Optimization Objective: To imbibe the concepts of SEO in context of website development, and apply its techniques to improve search
Finding Vulnerabilities in Web Applications
 Finding Vulnerabilities in Web Applications Christopher Kruegel, Technical University Vienna Evolving Networks, Evolving Threats The past few years have witnessed a significant increase in the number of
Finding Vulnerabilities in Web Applications Christopher Kruegel, Technical University Vienna Evolving Networks, Evolving Threats The past few years have witnessed a significant increase in the number of
I G H T T H E A G A I N S T S P A M. ww w.atmail.com. Copyright 2015 atmail pty ltd. All rights reserved. 1
 T H E F I G H T A G A I N S T S P A M ww w.atmail.com Copyright 2015 atmail pty ltd. All rights reserved. 1 EXECUTIVE SUMMARY IMPLEMENTATION OF OPENSOURCE ANTI-SPAM ENGINES IMPLEMENTATION OF OPENSOURCE
T H E F I G H T A G A I N S T S P A M ww w.atmail.com Copyright 2015 atmail pty ltd. All rights reserved. 1 EXECUTIVE SUMMARY IMPLEMENTATION OF OPENSOURCE ANTI-SPAM ENGINES IMPLEMENTATION OF OPENSOURCE
Evolution of Spear Phishing. White Paper
 Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
A PRACTICE BUILDERS white paper. 8 Ways to Improve SEO Ranking of Your Healthcare Website
 A PRACTICE BUILDERS white paper 8 Ways to Improve SEO Ranking of Your Healthcare Website More than 70 percent of patients find their healthcare providers through a search engine. This means appearing high
A PRACTICE BUILDERS white paper 8 Ways to Improve SEO Ranking of Your Healthcare Website More than 70 percent of patients find their healthcare providers through a search engine. This means appearing high
FAQ. Usually appear to be sent from official address
 FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
Site Audit SpaceX
 Site Audit 217 SpaceX Site Audit: Issues Total Score Crawled Pages 48 % -13 3868 Healthy (649) Broken (39) Have issues (276) Redirected (474) Blocked () Errors Warnings Notices 4164 +3311 1918 +7312 5k
Site Audit 217 SpaceX Site Audit: Issues Total Score Crawled Pages 48 % -13 3868 Healthy (649) Broken (39) Have issues (276) Redirected (474) Blocked () Errors Warnings Notices 4164 +3311 1918 +7312 5k
Unique Phishing Attacks (2008 vs in thousands)
 The process of attempting to acquire sensitive information, such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. In the 2 nd half
The process of attempting to acquire sensitive information, such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. In the 2 nd half
Security Architect Northeast US Enterprise CISSP, GCIA, GCFA Cisco Systems. BRKSEC-2052_c Cisco Systems, Inc. All rights reserved.
 Web 2.0 Security Recommendations Ken Kaminski Security Architect Northeast US Enterprise CISSP, GCIA, GCFA Cisco Systems 1 Agenda Reputation Services Web application security Secure Coding and Web Application
Web 2.0 Security Recommendations Ken Kaminski Security Architect Northeast US Enterprise CISSP, GCIA, GCFA Cisco Systems 1 Agenda Reputation Services Web application security Secure Coding and Web Application
Spam Protection Guide
 Spam Email Protection Guide Version 1.0 Last Modified 5/29/2014 by Mike Copening Contents Overview of Spam at RTS... 1 Types of Spam... 1 Spam Tricks... 2 Imitation of 3 rd Party Email Template... 2 Spoofed
Spam Email Protection Guide Version 1.0 Last Modified 5/29/2014 by Mike Copening Contents Overview of Spam at RTS... 1 Types of Spam... 1 Spam Tricks... 2 Imitation of 3 rd Party Email Template... 2 Spoofed
Managing IT Risk: What Now and What to Look For. Presented By Tina Bode IT Assurance Services
 Managing IT Risk: What Now and What to Look For Presented By Tina Bode IT Assurance Services Agenda 1 2 WHAT TOP TEN IT SECURITY RISKS YOU CAN DO 3 QUESTIONS 2 IT S ALL CONNECTED Introduction All of our
Managing IT Risk: What Now and What to Look For Presented By Tina Bode IT Assurance Services Agenda 1 2 WHAT TOP TEN IT SECURITY RISKS YOU CAN DO 3 QUESTIONS 2 IT S ALL CONNECTED Introduction All of our
power up your business SEO (SEARCH ENGINE OPTIMISATION)
 SEO (SEARCH ENGINE OPTIMISATION) SEO (SEARCH ENGINE OPTIMISATION) The visibility of your business when a customer is looking for services that you offer is important. The first port of call for most people
SEO (SEARCH ENGINE OPTIMISATION) SEO (SEARCH ENGINE OPTIMISATION) The visibility of your business when a customer is looking for services that you offer is important. The first port of call for most people
WHITE PAPER. Best Practices for Web Application Firewall Management
 WHITE PAPER Best Practices for Web Application Firewall Management WHITE PAPER Best Practices for Web Application Firewall Management.. INTRODUCTION 1 DEPLOYMENT BEST PRACTICES 2 Document your security
WHITE PAPER Best Practices for Web Application Firewall Management WHITE PAPER Best Practices for Web Application Firewall Management.. INTRODUCTION 1 DEPLOYMENT BEST PRACTICES 2 Document your security
Attackers Process. Compromise the Root of the Domain Network: Active Directory
 Attackers Process Compromise the Root of the Domain Network: Active Directory BACKDOORS STEAL CREDENTIALS MOVE LATERALLY MAINTAIN PRESENCE PREVENTION SOLUTIONS INITIAL RECON INITIAL COMPROMISE ESTABLISH
Attackers Process Compromise the Root of the Domain Network: Active Directory BACKDOORS STEAL CREDENTIALS MOVE LATERALLY MAINTAIN PRESENCE PREVENTION SOLUTIONS INITIAL RECON INITIAL COMPROMISE ESTABLISH
1. Conduct an extensive Keyword Research
 5 Actionable task for you to Increase your website Presence Everyone knows the importance of a website. I want it to look this way, I want it to look that way, I want this to fly in here, I want this to
5 Actionable task for you to Increase your website Presence Everyone knows the importance of a website. I want it to look this way, I want it to look that way, I want this to fly in here, I want this to
W e b A p p l i c a t i o n S e c u r i t y : T h e D e v i l i s i n t h e D e t a i l s
 W e b A p p l i c a t i o n S e c u r i t y : T h e D e v i l i s i n t h e D e t a i l s Session I of III JD Nir, Security Analyst Why is this important? ISE Proprietary Agenda About ISE Web Applications
W e b A p p l i c a t i o n S e c u r i t y : T h e D e v i l i s i n t h e D e t a i l s Session I of III JD Nir, Security Analyst Why is this important? ISE Proprietary Agenda About ISE Web Applications
Digital Marketing Search Engine Optimization
 Digital Marketing Search Engine Optimization EduPristine www.edupristine.com What is SEO? Search Engine Optimization (SEO) is the act of optimizing your site s content so that it can be quickly found on
Digital Marketing Search Engine Optimization EduPristine www.edupristine.com What is SEO? Search Engine Optimization (SEO) is the act of optimizing your site s content so that it can be quickly found on
Computer Security. Assoc. Prof. Pannipa Phaiboonnimit. Adapted for English Section by Kittipitch Kuptavanich and Prakarn Unachak
 Computer Security Assoc. Prof. Pannipa Phaiboonnimit 1 Adapted for English Section by Kittipitch Kuptavanich and Prakarn Unachak Classification of Threats Computer Attack Intend to damage files, computers
Computer Security Assoc. Prof. Pannipa Phaiboonnimit 1 Adapted for English Section by Kittipitch Kuptavanich and Prakarn Unachak Classification of Threats Computer Attack Intend to damage files, computers
