ms-help://ms.technet.2004apr.1033/win2ksrv/tnoffline/prodtechnol/win2ksrv/howto/efsguide.htm
|
|
|
- Bertina Lynette Jackson
- 6 years ago
- Views:
Transcription
1 Page 1 of 14 Windows 2000 Server Step-by-Step Guide to Encrypting File System (EFS) Abstract This document provides sample procedures that demonstrate the end-user and administrative capabilities of the Encrypting File System (EFS) included with the Microsoft Windows 2000 operating system. EFS is based on public-key encryption and takes advantage of the CryptoAPI architecture in Windows Introduction The Encrypting File System (EFS) included with the Microsoft Windows 2000 operating system is based on public-key encryption and takes advantage of the CryptoAPI architecture in Windows Each file is encrypted using a randomly generated file encryption key, which is independent of a user's public/private key pair; thereby stifling many forms of cryptoanalysis-based attack. File encryption can use any symmetric encryption algorithm. The release of EFS uses the Data Encryption Standard X, or DESX (128 bit in North America and 40 bit International) as the encryption algorithm. Future releases will allow alternate encryption schemes. EFS supports encryption and decryption of files stored on local drives as well as those stored on remote file servers. Note In the case of remote servers, you can encrypt files and folders on the server but your data is not protected if you access a file over the network. Windows 2000 provides network protocols such as Secure Sockets Layer/Private Communication Technology (SSL/PCT) to encrypt data access over the network. User Interaction The default configuration of EFS allows users to start encrypting files with no administrative effort. EFS automatically generates a public-key pair and file encryption certificate for file encryption for a user the first time a user encrypts a file. File encryption and decryption is supported per file or for an entire folder. Folder encryption is transparently enforced. All files (and folders) created in a folder marked for encryption are automatically encrypted. Each file has a unique file encryption key, making it safe to rename. If you rename a file from an encrypted folder to an unencrypted folder on the same volume, the file remains encrypted. However, if you copy an unencrypted file into an encrypted folder, the file remains in the state that it was in in this case the file remains unencrypted. Command-line tools and administrative interfaces are provided for advanced users and recovery agents. You don't have to decrypt a file to open it and use it. EFS automatically detects an encrypted file and locates a user's file encryption key from the system's key store. Since the key storage mechanism is based on CryptoAPI, in the future, users will have the flexibility of storing keys on secure devices, such as smart cards. The initial release of EFS does not support file sharing. However, the EFS architecture is designed to allow file sharing between any number of people by the simple use of their file encryption certificates. Users can then independently decrypt files using their own private keys. Users can be added easily (if they have a configured public key pair) or removed from a group of permitted sharers. Data Recovery EFS provides built-in data recovery support. The Windows 2000 security infrastructure enforces the configuration of data recovery keys. You can use file encryption only if the system is configured with one or more recovery keys. EFS allows recovery agents to configure public keys that are used to recover encrypted data if a user leaves the company. Only the file encryption key is available using the recovery key, not a user's private key. This ensures that no other private information is revealed to the recovery agent. Data recovery is intended for business environments where the organization expects to be able to recover data encrypted by an employee after an employee leaves or if file encryption keys are lost. The recovery policy can be defined at the domain controller of a Windows 2000 domain. This policy is enforced on all computers in that domain. The recovery policy is under the control of domain administrators who can delegate this to designated data security administrator accounts using Windows 2000 directory service delegation features. This provides strong control and allows flexibility regarding who is authorized to recover encrypted data. EFS supports multiple recovery agents by allowing multiple data recovery certificates configurations. These features provide organizations with redundancy and flexibility in implementing their recovery procedures. In the default Windows 2000 installation, when the first domain controller is set up, the domain administrator is the specified recovery agent for the domain. The way the domain administrator configures the recovery policy determines how EFS is implemented for users on their local computers. The domain administrator logs on to the first domain controller to change the recovery policy for the domain. Table 1 helps you see the effect on users of several recovery policy configurations. Table 1 Effect of Recovery Policy Configurations on Users Default recovery agent Domain administrator Administrator of local computer No recovery agent Effect on EFS locally EFS is available locally EFS is available locally EFS cannot be used Configuration Recovery policy in place configured with designated recovery agent(s) No recovery policy at the domain level Empty recovery policy Action by domain administrator None required Delete recovery policy on first domain controller Delete every recovery agent EFS can also be used in a home environment. EFS automatically generates recovery keys and self-signed certificates when the local administrator logs on, making the local administrator the default recovery agent. Home users can also use the command line tool to recover data using the administrator's account. This reduces the administrative overhead for a home user. The remainder of this paper provides sample procedures that demonstrate the end-user and administrative capabilities of Windows 2000 EFS. These are intended for use when evaluating EFS for your network. Please walk through these examples sequentially. Requirements and Prerequisites To complete this walkthrough, you need the following: A client computer running Windows 2000 Professional operating system. A server computer running Windows 2000 Server operating system. A Windows 2000 Server domain controller. A local area network to connect these three computers. All three computers should be members of the same domain. The common infrastructure assumed in this guide is covered in the Step-by-Step Guide to a Common Infrastructure Part I: Installing a Windows 2000 Server as a Domain Controller and Part II: Installing a
2 Page 2 of 14 Windows 2000 Professional Workstation and Connecting it to a Domain If you are not using the common infrastructure, you need to make the appropriate changes to this instruction set. The computer names you will see throughout this document are based upon the common infrastructure. The User scenarios described in this guide should be run on a client running Windows 2000 Professional. The Administrative scenarios should be run on a server (not a domain controller) running Windows 2000 Server. The section titled, "Securing the Default Recovery Key for the Domain," should be run on a domain controller running Windows 2000 Server. User Scenarios Encrypting a Folder or File When encrypting a folder or file, you can use Windows Explorer or you can use the command-line utility, Cipher.exe. Both procedures are described next. This guide assumes you are performing the User Scenario exercises on a computer running Windows 2000 Professional. To use Windows Explorer to encrypt a folder or file 1. Click Start, point to Programs, point to Accessories, and click Windows Explorer. 2. Right-click the folder or file name you wish to work with (in this example a folder we created under My Documents called Encrypted Files), and choose Properties. 3. On the General tab in the Encrypted Files Properties dialog box, click Advanced. Figure 1 Advanced attributes 4. On the Advanced Attributes dialog box, select Encrypt contents to secure data and click OK. This returns you to the Encrypted Files Properties dialog box. 5. Click OK in the Encrypted Files Properties dialog box. 6. You are asked to choose between encrypting the folder and all its contents or just the folder itself. If the folder is empty, choose to encrypt the folder only; otherwise, choose the folder and its contents, and click OK. 7. A dialog box shows you the status of encrypting the folder or file. Click OK again to make this change, and close the snap-in. Decrypting a Folder or File As with encryption, you can use Windows Explorer or a command-line utility to decrypt a folder or file. Both procedures are described next. Note that you do not need to decrypt a file to open the file and edit it. Decrypt a file that you want to make accessible to others. To use Windows Explore to decrypt a folder or file 1. Click Start, point to Programs, point to Accessories, and select Windows Explorer. 2. Right-click the folder or file name, and choose Properties. 3. On the General tab of the Properties dialog box, click Advanced. 4. On the Advanced Attributes dialog box, clear the Encrypt contents to secure data check box, and click OK. 5. Click OK in the Encrypted Files Properties dialog box. 6. You are asked to choose between decrypting the folder and all its contents or just the folder itself. The default is to decrypt the folder only, and then click OK. Note It is recommended that you encrypt folders and not individual files. This is because many existing applications are not aware of encryption and can therefore render the file in clear text. To use Cipher.exe to encrypt a folder or file 1. To encrypt the folder, D:\Encrypted Files (substitute this with the drive letter and folder that you are working with), click Start, click Run, type cmd and click OK. For example, at the command prompt, type: D:\>cipher /e /s:"d:\encrypted Files" 2. Press ENTER.
3 Page 3 of 14 Figure 2 Cipher command The folder's attributes report that this folder is encrypted. To use Cipher.exe to decrypt a folder or file 1. To decrypt the folder, D:\Encrypted Files, type C:\>cipher /d /s:"c:\encrypted Files" 2. Press Enter. Using an Encrypted File or Folder If you are the user who encrypted a file, you can use that file as before. You can open, edit, copy, and rename the file. If you are not the user who encrypted the file, you cannot do any of those things and you receive an Access Denied error message if you attempt to access the file. Only the user who encrypted the file can decrypt it making it available again to others in its unencrypted (plain text) form. With an encrypted folder, if you had access to that folder before it was encrypted, you can still open it. Folders are only marked as encrypted so that all files in them are encrypted as they are created, and sub-folders are marked encrypted at creation. Note An encrypted folder can be decrypted only by the user who encrypted it. Copying an Encrypted Folder or File The following explains the procedures and limitations for copying encrypted folders or files on the same volume and from one volume to another. To copy a file or folder on the same computer from one NTFS partition in a Windows 2000 location to another NTFS partition in a Windows 2000 location. Copy the file or folder as you would an unencrypted file. Use Windows Explorer or the command prompt. The copy is encrypted. To copy a file or folder on the same computer from an NTFS partition in a Windows 2000 volume to a FAT partition. Copy the file or folder as you would an unencrypted file. Use Windows Explorer or the command prompt. Because the destination file system does not support encryption, the copy is in clear text. To copy a file or folder to a different computer where both use the NTFS partitions in Windows Copy the file or folder as you would an unencrypted file. Use Windows Explorer or the command prompt. If the remote computer allows you to encrypt files, the copy is encrypted; otherwise it is in clear text. Note that the remote computer must be trusted for delegation; in a domain environment, remote encryption is not enabled by default. To copy a file or folder to a different computer from an NTFS partition in a Windows 2000 location to a FAT or NTFS in a Windows NT 4.0 location. Copy the file or folder as you would an unencrypted file. Use Windows Explorer or the command prompt. Because the destination file system does not support encryption, the copy is in clear text. Note If your original file was encrypted, Microsoft recommends that you use the File Properties, Advanced option to confirm the status of the destination file. Moving or Renaming an Encrypted Folder or File The following explains the procedures and limitations for moving encrypted folders or files on the same volume and from one volume to another. To move or rename a file or folder within the same volume. Move the file as you would an unencrypted file. Use Windows Explorer, the context menu, or the command prompt. The destination file or folder remains encrypted. To move a file or folder between volumes. This is essentially a copy operation. Review the previous section, Copying an Encrypted Folder or File. Deleting an Encrypted Folder or File If you have access to delete the file or folder, you can delete it as you could an unencrypted file. Note Deleting an encrypted folder or file is not restricted to the user who originally encrypted the file. Backing Up an Encrypted Folder or File The following explains the procedures and limitations for backing up encrypted folders or files. Backing up by copying. Backup created using the Copy command or menu selection can end up in clear text, as explained previously in the section, Copying an Encrypted Folder or File. Backing up using Backup in Windows 2000 or any backup utility that supports Windows 2000 features. This is the recommended way to back up encrypted files. The backup operation maintains the file encryption, and the backup operator does not need access to private keys to do the backup; they only need access to the file or folder to complete the task. To use Backup to back up a file, folder, or drive
4 Page 4 of Click Start, point to Programs, point to Accessories, point to System Tools, and then click Backup. The Backup wizard appears. 2. Click the Backup tab. 3. Select the drive, files, or folders that you want to back up. (in this case My Documents\Encrypted Files). Figure 3 Backup file selection 4. Select the destination in the Backup media or file name list. Click Browse to locate a pre-existing backup file. 5. Click Start Backup. 6. In the Backup Job Information dialog box, make selections, and then click Start Backup. When the backup process is complete, click Close in the Backup Progress dialog box. Backup backs up the entire encrypted file, folder, or drive to the backup file you selected. This file can be copied to FAT media, such as floppy disks, and is secure because its contents remain encrypted. Restoring an Encrypted File or Folder Restore operations parallel those used for backing up encrypted files. The following explains the procedures and limitations for restoring backed up encrypted files to the computer where the backup was performed and to a computer other than the one where the files were backed up. Restoring by Copying. Restored files created using the Copy command or menu selection can end up in clear text, as explained previously in the section, Copying an Encrypted Folder or File. Restoring using Backup in Windows 2000 or any backup utility that supports Windows 2000 features. This is the recommended way to restore encrypted files. The restore operation maintains the file encryption, and the restoring agent doesn't need access to private keys to restore the files. After the restoration is complete, the user with the private key can use the file normally. To use Backup to restore a file on the same computer 1. Click Start, point to Programs, point to Accessories, point to System Tools, and then click Backup. 2. Click the Restore tab. 3. Right-click File, and then click Catalog file. 4. Enter the path to the backup file (for example, C:\Encryptedbackup.bkf). 5. Check the encrypted folder that needs to be restored. All its contents are restored automatically. In the Restore files to list, select Alternate location.
5 Page 5 of 14 Figure 4 Restore window 6. In the Alternate location box, provide the name of the folder where you want the encrypted material to be restored. 7. Click Start Restore. 8. Click OK to confirm the restore process. 9. Click OK to confirm the backup file. When the restore process is complete, click Close. The Restore Progress dialog shows you the progress of the operation. You can use the Properties of the folder to check that indeed it was restored encrypted. 10. Close the Backup window. Restoring Files to a Different Computer If you want to be able to use encrypted files on a computer other than the one the files were encrypted on, you need to ensure that your encryption certificate and associated private key are available on the other system. You can do this either by using a Roaming Profile or by manually moving your keys. Using a Roaming Profile. Request that your administrator set up a roaming profile for you if you don't already have one. Once you have a roaming profile, the encryption keys you use are the same on all computers that you sign on to with that user account. Note that even if you use roaming profiles, you may want to back up your encryption certificate and private key. However, if you do lose the keys that enable you to decrypt a file, you can request the designated recovery agent (by default the local or domain administrator) to recover your encrypted files. Manually moving keys. Before you contemplate moving your keys manually, you should back up your encryption certificate and private key. You can then restore your certificate and key on a different system. To back up your encryption certificate and private key 1. To start the Microsoft Management Console (MMC), click Start, click Run, type mmc in the Open box, and click OK. 2. On the Console menu, click Add/Remove snap-ins, and click Add. 3. Locate the Certificates snap-in, and click Add. Select My user account and then click Finish. Click Close. Click OK. 4. Locate the Encrypting File System certificates in your Personal certificate store. Click the + next to Certificates Current User. Expand the Personal folder. Click Certificates. 5. Right-click your certificate, click All Tasks, and click Export. This starts the Certificate Manager Export wizard. Click Next. 6. Click Yes, export the private key. Click Next. 7. The export format available is Personal Information Exchange-PKCS#12, or.pfx personal exchange format. Click Next. 8. Provide the password to protect the.pfx data. Click Next. 9. Provide the path and file name where the.pfx data is to be stored. In this case, type c:\mykey. Click Next. 10. A list of certificates and keys to be exported is displayed. Click Finish to confirm. 11. Click OK to close the wizard, and close the snap-in. This exports the encryption certificate and private key to a.pfx file that must be backed up securely. To restore your encryption certificate and private key on a different system 1. Copy the.pfx file to a floppy disk, and take it to the computer where you want to import the encryption certificate and private key. 2. Start the Certificates snap-in by clicking Start, clicking Run, and then typing mmc. 3. On the Console menu, click Add/Remove snap-ins, and click Add.
6 Page 6 of Click Certificates, and click Add. Select My user account and then click Finish. Click Close. Click OK. 5. Right-click Personal store, click All Tasks, and click Import to import the.pfx file. 6. This starts the Certificate Manager Import wizard. Follow the wizard steps to successfully import the certificate and private key. 7. Provide the path to the.pfx file. In our example, it is c:\mykey.pfx. 8. Type the password to unwrap the.pfx data. 9. Click Place all certificates in the following store, and accept the Personal certificate store. Click Next. 10. Click Finish, and then click OK to start the import operation. When the import is complete, click OK to close the wizard. Once you have the same keys available, you can transparently use encrypted files that may have been backed up on different computer. Folders and Files On a Remote Server You can transparently encrypt and decrypt files and use encrypted files stored on a remote server. This works whether you access those files remotely or log on to the other computer locally. However, you must remember that when you move encrypted files using backup and restore mechanisms, you must ensure that the appropriate encryption certificate and private keys are also moved to allow you to use the encrypted files in their new destinations. Without correct private keys, you cannot open or decrypt the files. Note If you open the encrypted file over the network, the data that is transmitted over the network by this process is not encrypted. Other protocols, such as Secure Sockets Layer/Personal Communication Technology (SSL/PCT) or Internet Protocol Security (IPSec) must be used to encrypt data over the wire. Administrative Scenarios Securing the Default Recovery Key on a Stand-alone Computer For this set, logon as Administrator to the local computer (in our example, this is the machine named HQ-RES-SRV-01), a member server. Be sure you logon to the computer locally (as opposed to logging onto the domain). As part of the local administrator's initial logon, a default recovery policy is set up on each stand-alone computer. This policy makes the local administrator the default recovery agent for the computer. To change this policy 1. Click Start, click Run, and type MMC in the Open box. Click OK. 2. Click Console, click Add/Remove Snap-In. Click Add. 3. Click Group Policy and click Add. 4. Accept the default of Local Computer and click Finish. Click Close and click OK. 5. Click the + next to Local Computer Policy to expand it. In the same way, expand Computer Configuration, Windows Settings, Security Settings, Public Key Policies, and then click Encrypted Data Recovery Agents. Your screen should look something like the one below. Figure 5 Encrypted data recovery agents 6. You see a self-signed Administrator certificate in the policy. This makes the local administrator account the default recovery agent. If you delete this certificate, you have an empty recovery policy, which turns EFS off. EFS doesn't allow encryption of data if there are no recovery agents set up. 7. To protect the recovery key associated with this certificate, click Console, and click Add/Remove snap-ins. Click Add. 8. Click Certificates, and click Add. Click Current User. Click Finish. Click Close. Click OK. 9. Click the + next to Certificates Current User. In the same way, expand the Personal folder. Click Certificates in the left pane. 10. Click Administrator in the right pane and scroll to Intended Purposes. This should be set to File Recovery. Use the procedure in the section, Restoring Files to a Different Computer, to export the certificate and private key in a.pfx file. 11. After you have created the.pfx file, delete the certificate and the private key associated with it from the Personal store. This ensures that the only copy of the key is in the.pfx file. To do so, click Administrator in the right pane and then click the red X on the toolbar. You will receive a warning message saying that you will not be able to decrypt data encrypted using this certificate. Click Yes to continue.
7 Page 7 of Secure the.pfx file in a safe or locked cabinet. This file should be used only when a file needs to be recovered. Securing the Default Recovery Key for the Domain As with the stand-alone computer, a default recovery policy is configured for the domain when the first domain controller is set up. The default recovery policy uses a self-signed certificate to make the domain Administrator account the recovery agent. Note To change the default, log on as Administrator on the first domain controller of the domain, and follow the steps above to secure the recovery key for the domain. Requesting a File Recovery Certificate If you decide to use the default recovery policies, you never need to request a file recovery certificate. However, in circumstances where multiple recovery agents are needed for the domain or where the recovery agent needs to be different from the domain administrator due to legal or corporate policy, you may need to identify certain users as recovery agents, and these users must be issued file recovery certificates. To accomplish this, the following procedures must be completed: An Enterprise Certificate Authority (CA) must be set up, if one isn't available. (See also Step-by-Step Guide to Setting up a Certificate Authority). The policy on the Enterprise CA must allow the designated user/agents to request and obtain a file recovery certificate. Each user must request a file recovery certificate. To set up an Enterprise CA 1. Log on to the first domain controller in the domain as the domain administrator. In our example, this entails logging onto the computer HQ-RES-DC-01 in the RESKIT.COM domain. 2. Click Start, point to Settings, and select Control Panel. 3. Double-click Add/Remove Programs 4. Click Add/Remove Windows Components. 5. Click Certificate Services. You will receive a warning that once Certificate Services are installed, the computer cannot be renamed and the computer cannot join or be removed from a domain. Click Yes to continue. Click Next. 6. Make sure the Enterprise root CA radio button is selected and click Next. 7. Fill in the properties as shown below. Figure 6 CA identifying information 8. Click Next. Click Next to accept the default data storage location. 9. If IIS is running, you are prompted whether to temporarily shut that service down. Click OK. 10. You may be prompted to insert the Windows 2000 Server CD-ROM; unless you are installing from a network source insert the CD- ROM or provide the path to the network source. Click OK to proceed. 11. After the component has installed, click Finish. Close the Add/Remove Programs and Control Panel. To create a policy for users designated as recovery agents 1. Click Start, point to Programs, point to Administrative Tools, and click Active Directory Computers and Users. 2. Right click Groups, click New, click Group, type Domain Recovery Agents and click OK. 3. To add users to that group, right-click Domain Recovery Agents in the right pane, click Properties, click the Members tab. 4. Click Add, click Administrator, and click Add. Click OK twice. Close the Active Directory Computers and Users snap-in. Add the Domain Recovery Agents group to the EFS Recovery Template. This procedure allows users in that group to request recovery certificates. 1. Click Start, point to Programs, point to Administrative Tools, and click Active Directory Sites and Services.
8 Page 8 of On the View menu, click Show Services. 3. Click the + next to Services in the left pane. Use this method to expand the Public Key Services folder. 4. Click Certificate Templates (in the left pane). Figure 7 Certificate templates 5. Double-click EFSRecovery in the right pane. 6. Click the Security tab. 7. Click Add. Scroll to the group Domain Recovery Agents. Click Domain Recovery Agents and click the Add button. Click OK. 8. With Domain Recovery Agents selected in the top pane, select the Enroll check box in the bottom pane. 9. Click OK, and close the Active Directory Sites and Services snap-in. Note For more information on administering Certificate Services, refer to the document, Step-by-Step Guide to Administering Certificate Services. To request a file recovery certificate 1. Start the Certificates snap-in by clicking Start, clicking Run, and then typing mmc. 2. On the Console menu, select Add/Remove snap-ins, and click Add. 3. Click Certificates, and click Add. Select My user account and then click Finish. Click Close. Click OK. 4. Click the + next to Certificates Current User. 5. Right-click Personal in the left pane, click All Tasks, and click Request New Certificate. This starts the Certificate Request wizard. 6. The first page of the wizard is informational. Click Next to continue. 7. A list of certificate templates is displayed. Click EFS Recovery Agent, and click Next. 8. Type in a friendly name that you can use to distinguish this certificate from others. Add a description if you desire. Click Next. 9. The next page shows you the summary of your choices. Click Finish to obtain the certificate. 10. Click Install Certificate and then click OK. You have now obtained a file recovery certificate. At this point, you need to do two things: Copy the certificate without the private key to a.cer file. You need to do this only if the certificate is not automatically published in the directory, in order to enable the domain administrator to add it to the recovery policy. Export this certificate with the private key to a secure.pfx file. To copy the certificate to a.cer file 1. Click the + next to Certificates under Personal in the left pane (unless it is already expanded.) 2. In the right pane, right-click the certificate you just created. 3. Click All Tasks and click Export. This starts the Certificate Export wizard as described previously in this document. Click Next to begin the export process. 4. Click No, do not export the private key and click Next. 5. Choose the default.cer file format, and click Next. 6. Provide the file path, and click Next. 7. Click Finish to perform the export, and then click OK. To export the certificate to a secure.pfx file 1. Follow the steps outlined in the section Restoring Files to a Different Computer. 2. Remember to delete the certificate and the private key from your store after you have exported it to a.pfx file. This key is highly sensitive, as it can decrypt any encrypted file where the recovery policy is in effect.
9 Page 9 of Close the Certificate snap-in. Setting Up a Recovery Policy for the Entire Domain Once recovery agents have been identified and issued certificates, the domain administrator can add these certificates to the recovery policy, as described next. To add certificates to recovery policy 1. Click the Start button, point to Programs, point to Administrative Tools, and then select Domain Security Policy. 2. Click the + next to Security Settings. 3. Click the + next to Public Key Policies. 4. Click Encrypted Data Recovery Agents. Now right-click it and click Add. The Add Recovery Agent wizard starts. Click Next. 5. Click Browse Folders. 6. Click the certificate that was created in the previous steps, exportnewcertificate.cer, and click Open. Figure 8 Select certificate from folder 7. Click Next, and then click Finish. The new certificate now appears in the right pane of the Domain Security Policy snap-in. Figure 9 New certificate Setting a Recovery Policy for a Specific Organizational Unit You may be required to establish a unique recovery policy for a subset of computers in your domain. You can accomplish this by using the Group Policy infrastructure. To do this, repeat the steps described above for an organizational unit (OU) rather than a domain node. In the case of an OU, you do not have a default Group Policy Object that you can simply edit. Therefore, you need to click Add in the Group Policy dialog box to add a new GPO. Once you have added the new GPO, use Edit to start the Group Policy snap-in and then follow the same steps as above to define a different recovery policy for that OU. Recovering a File or Folder
10 Page 10 of 14 Recovery agents may need to recover files or folders if a user loses his or her key or leaves the company, or if there is a legal requirement to do so. The process of recovery is similar to decryption once the recovery key is available on the system. To recover a file or folder 1. Back up the files or folder to a.bkf file from the system where they currently exist. For complete procedures, see the section, Backing Up an Encrypted Folder or File. 2. Copy the.bkf file to the secured recovery agent's computer. To do this, you can use removable media such as floppy disk, or you can the.bkf file to the recovery agent. 3. The recovery agent should restored the files or folder in the.bkf file locally on a secured system. For complete procedures, see the section, Restoring an Encrypted Folder or File. 4. Use the Certificates snap-in to import the recovery key and certificate from the.pfx file to the secured system. See Restoring an Encrypted Folder or File for the import procedure. 5. Once the recovery key is imported into the context, you can simply open each file, or you can use the Windows Explorer Properties dialog box to decrypt individual files or entire folders. 6. Once the decryption is complete, the recovery agent can recreate the.bkf file, this time containing decrypted files and folders, and mail it back to requestor. Disabling EFS for a Specific Set of Computers In some cases, you may need to ensure that a stand-alone computer or some computer in an OU (in Active Directory) has EFS disabled. The best way to disable EFS is to set an empty recovery policy. You can do this locally on the computer using the local Group Policy snap-in or by defining a GPO at the OU level with an empty recovery policy. Note There is a difference between an empty policy and no policy. In Active Directory where the effective policy is an accumulation of Group Policy Objects defined at various levels in the directory tree, the absence of a recovery policy at higher-level nodes (for example, at the domain node) allows policies at a lower level to take effect. An empty recovery policy at higher-level nodes disables EFS by providing no effective recovery certificates. On a given computer (stand-alone or joined to the domain), an effective policy must have at least one valid recovery certificate to enable EFS on that computer. Therefore, on a given computer, the absence of a recovery policy or an empty recovery policy has the same effect EFS is disabled. More Information For the latest information on Microsoft Windows 2000 network operating system, visit our World Wide Web site at the Windows NT Server Forum on the Microsoft Network (GO WORD: MSNTS) the Windows 2000/NT Forum at Windows 2000 Web Site Resources Exploring Security Services Windows 2000 Planning and Deployment Guide Send feedback to Microsoft 2004 Microsoft Corporation. All rights reserved.
11 Page 11 of 14
12 Page 12 of 14
13 Page 13 of 14
14 Page 14 of 14
ms-help://ms.technet.2004apr.1033/ad/tnoffline/prodtechnol/ad/windows2000/howto/mapcerts.htm
 Page 1 of 8 Active Directory Step-by-Step Guide to Mapping Certificates to User Accounts Introduction The Windows 2000 operating system provides a rich administrative model for managing user accounts.
Page 1 of 8 Active Directory Step-by-Step Guide to Mapping Certificates to User Accounts Introduction The Windows 2000 operating system provides a rich administrative model for managing user accounts.
Windows 2000 Disk Management
 LAB PROCEDURE 25 Windows 2000 Disk Management OBJECTIVES 1. Use Disk Cleanup. 2. Backup a file. 3. Restore a backup. 4. Compress a file. 5. Encrypt a file. Troubleshooting RESOURCES 1. Marcraft 8000 Trainer
LAB PROCEDURE 25 Windows 2000 Disk Management OBJECTIVES 1. Use Disk Cleanup. 2. Backup a file. 3. Restore a backup. 4. Compress a file. 5. Encrypt a file. Troubleshooting RESOURCES 1. Marcraft 8000 Trainer
This guide describes how to use the Dfs Share Creation wizard.
 Step-by-Step Guide to Distributed File System (Dfs) Because shared files are widely distributed across networks, administrators face growing problems as they try to keep users connected to the data they
Step-by-Step Guide to Distributed File System (Dfs) Because shared files are widely distributed across networks, administrators face growing problems as they try to keep users connected to the data they
Step-by-step installation guide for monitoring untrusted servers using Operations Manager
 Step-by-step installation guide for monitoring untrusted servers using Operations Manager Most of the time through Operations Manager, you may require to monitor servers and clients that are located outside
Step-by-step installation guide for monitoring untrusted servers using Operations Manager Most of the time through Operations Manager, you may require to monitor servers and clients that are located outside
Microsoft Windows Encrypting File System (EFS) Certificate Migration from XP to VISTA (also works with Windows 7) Instruction Guide
 Microsoft Windows Encrypting File System (EFS) Certificate Migration from XP to VISTA (also works with Windows 7) Instruction Guide Army Information Assurance CAC/PKI Division 2530 Crystal Drive Arlington,
Microsoft Windows Encrypting File System (EFS) Certificate Migration from XP to VISTA (also works with Windows 7) Instruction Guide Army Information Assurance CAC/PKI Division 2530 Crystal Drive Arlington,
x CH03 2/26/04 1:24 PM Page
 03 078973107x CH03 2/26/04 1:24 PM Page 45 3............................................. Setting Up, Managing, and Troubleshooting Security Accounts and Policies 1. You re a help desk technician for your
03 078973107x CH03 2/26/04 1:24 PM Page 45 3............................................. Setting Up, Managing, and Troubleshooting Security Accounts and Policies 1. You re a help desk technician for your
ms-help://ms.technet.2004apr.1033/win2ksrv/tnoffline/prodtechnol/win2ksrv/howto/grpolwt.htm
 Page 1 of 17 Windows 2000 Server Step-by-Step Guide to Understanding the Group Policy Feature Set Operating System Abstract Group Policy is the central component of the Change and Configuration Management
Page 1 of 17 Windows 2000 Server Step-by-Step Guide to Understanding the Group Policy Feature Set Operating System Abstract Group Policy is the central component of the Change and Configuration Management
Configuring File Server Resource Manager (FSRM)
 Configuring File Server Resource Manager (FSRM) LESSON 5 70-411 EXAM OBJECTIVE Objective 2.2 Configure File Server Resource Manager (FSRM). This objective may include but is not limited to: install the
Configuring File Server Resource Manager (FSRM) LESSON 5 70-411 EXAM OBJECTIVE Objective 2.2 Configure File Server Resource Manager (FSRM). This objective may include but is not limited to: install the
8 MANAGING SHARED FOLDERS & DATA
 MANAGING SHARED FOLDERS & DATA STORAGE.1 Introduction to Windows XP File Structure.1.1 File.1.2 Folder.1.3 Drives.2 Windows XP files and folders Sharing.2.1 Simple File Sharing.2.2 Levels of access to
MANAGING SHARED FOLDERS & DATA STORAGE.1 Introduction to Windows XP File Structure.1.1 File.1.2 Folder.1.3 Drives.2 Windows XP files and folders Sharing.2.1 Simple File Sharing.2.2 Levels of access to
Implementing Messaging Security for Exchange Server Clients
 Implementing Messaging Security for Exchange Server Clients Objectives Scenario At the end of this lab, you will be able to: Protect e-mail messages using S/MIME signing and encryption Manage e-mail attachment
Implementing Messaging Security for Exchange Server Clients Objectives Scenario At the end of this lab, you will be able to: Protect e-mail messages using S/MIME signing and encryption Manage e-mail attachment
Configuration of Microsoft Live Communications Server for Partitioned Intradomain Federation
 Configuration of Microsoft Live Communications Server for Partitioned Intradomain Federation Domain Verification for LCS Servers, page 1 Enable Port 5060 on LCS Server, page 1 Configure a LCS Static Route
Configuration of Microsoft Live Communications Server for Partitioned Intradomain Federation Domain Verification for LCS Servers, page 1 Enable Port 5060 on LCS Server, page 1 Configure a LCS Static Route
Step-by-Step Guide to Installing Cluster Service
 Page 1 of 23 TechNet Home > Products & Technologies > Windows 2000 Server > Deploy > Configure Specific Features Step-by-Step Guide to Installing Cluster Service Topics on this Page Introduction Checklists
Page 1 of 23 TechNet Home > Products & Technologies > Windows 2000 Server > Deploy > Configure Specific Features Step-by-Step Guide to Installing Cluster Service Topics on this Page Introduction Checklists
S/MIME on Good for Enterprise MS Online Certificate Status Protocol. Installation and Configuration Notes. Updated: November 10, 2011
 S/MIME on Good for Enterprise MS Online Certificate Status Protocol Installation and Configuration Notes Updated: November 10, 2011 Installing the Online Responder service... 1 Preparing the environment...
S/MIME on Good for Enterprise MS Online Certificate Status Protocol Installation and Configuration Notes Updated: November 10, 2011 Installing the Online Responder service... 1 Preparing the environment...
8 Administering Groups
 8 Administering Groups Exam Objectives in this Chapter: Plan a security group hierarchy based on delegation requirements. Plan a security group strategy. Why This Chapter Matters As an administrator, you
8 Administering Groups Exam Objectives in this Chapter: Plan a security group hierarchy based on delegation requirements. Plan a security group strategy. Why This Chapter Matters As an administrator, you
Windows Server 2003 Network Administration Goals
 Objectives Differentiate between the different editions of Windows Server 2003 Explain Windows Server 2003 network models and server roles Identify concepts relating to Windows Server 2003 network management
Objectives Differentiate between the different editions of Windows Server 2003 Explain Windows Server 2003 network models and server roles Identify concepts relating to Windows Server 2003 network management
Workshop on Windows Server 2012
 Workshop on Windows Server 2012 Topics covered on Workshop DHCP Scope Splitting. A Dynamic Host Configuration Protocol (DHCP) split-scope configuration using multiple DHCP servers allows for increased
Workshop on Windows Server 2012 Topics covered on Workshop DHCP Scope Splitting. A Dynamic Host Configuration Protocol (DHCP) split-scope configuration using multiple DHCP servers allows for increased
Identity with Windows Server 2016
 Identity with Windows Server 2016 Course 20742B - 5 Days - Instructor-led, Hands on Introduction This five-day instructor-led course teaches IT Pros how to deploy and configure Active Directory Domain
Identity with Windows Server 2016 Course 20742B - 5 Days - Instructor-led, Hands on Introduction This five-day instructor-led course teaches IT Pros how to deploy and configure Active Directory Domain
Managing Group Policy application and infrastructure
 CHAPTER 5 Managing Group Policy application and infrastructure There is far more to managing Group Policy than knowing the location of specific policy items. After your environment has more than a couple
CHAPTER 5 Managing Group Policy application and infrastructure There is far more to managing Group Policy than knowing the location of specific policy items. After your environment has more than a couple
METHODOLOGY This program will be conducted with interactive lectures, PowerPoint presentations, discussions and practical exercises.
 CENTER OF KNOWLEDGE, PATH TO SUCCESS Website: IDENTITY WITH WINDOWS SERVER 2016 Course 20742: 5 days; Instructor-Led INTRODUCTION This five-day instructor-led course teaches IT Pros how to deploy and configure
CENTER OF KNOWLEDGE, PATH TO SUCCESS Website: IDENTITY WITH WINDOWS SERVER 2016 Course 20742: 5 days; Instructor-Led INTRODUCTION This five-day instructor-led course teaches IT Pros how to deploy and configure
IT Essentials v6.0 Windows 10 Software Labs
 IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
Automating the Windows 2000 Installation
 Chapter 2 Automating the Windows 2000 Installation MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER Perform an unattended installation of Windows 2000 Professional. Install Windows 2000 Professional by
Chapter 2 Automating the Windows 2000 Installation MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER Perform an unattended installation of Windows 2000 Professional. Install Windows 2000 Professional by
Chapter. Accessing Files and Folders MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER
 Chapter 10 Accessing Files and Folders MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER Monitor, manage, and troubleshoot access to files and folders. Configure, manage, and troubleshoot file compression
Chapter 10 Accessing Files and Folders MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER Monitor, manage, and troubleshoot access to files and folders. Configure, manage, and troubleshoot file compression
VMware AirWatch Certificate Authentication for EAS with NDES-MSCEP
 VMware AirWatch Certificate Authentication for EAS with NDES-MSCEP For VMware AirWatch Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
VMware AirWatch Certificate Authentication for EAS with NDES-MSCEP For VMware AirWatch Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
Course Outline 20742B
 Course Outline 20742B Module 1: Installing and configuring domain controllers This module describes the features of AD DS and how to install domain controllers (DCs). It also covers the considerations
Course Outline 20742B Module 1: Installing and configuring domain controllers This module describes the features of AD DS and how to install domain controllers (DCs). It also covers the considerations
M20742-Identity with Windows Server 2016
 M20742-Identity with Windows Server 2016 Course Number: M20742 Category: Technical Microsoft Duration: 5 days Certification: 70-742 Overview This five-day instructor-led course teaches IT Pros how to deploy
M20742-Identity with Windows Server 2016 Course Number: M20742 Category: Technical Microsoft Duration: 5 days Certification: 70-742 Overview This five-day instructor-led course teaches IT Pros how to deploy
Managing and Maintaining a Microsoft Windows Server 2003 Environment
 COURSE OVERVIEW This course combines five days of instructor-led training with additional e-learning content to provide students with the knowledge and skills that are required to manage accounts and resources,
COURSE OVERVIEW This course combines five days of instructor-led training with additional e-learning content to provide students with the knowledge and skills that are required to manage accounts and resources,
Advanced Security Measures for Clients and Servers
 Advanced Security Measures for Clients and Servers Wayne Harris MCSE Senior Consultant Certified Security Solutions Importance of Active Directory Security Active Directory creates a more secure network
Advanced Security Measures for Clients and Servers Wayne Harris MCSE Senior Consultant Certified Security Solutions Importance of Active Directory Security Active Directory creates a more secure network
Install and Issuing your first Full Feature Operator Card
 Install and Issuing your first Full Feature Operator Card Install S-Series versasec.com 1(28) Table of Contents Install and Issuing your first Full Feature Operator Card... 3 Section 1: Install and Initial
Install and Issuing your first Full Feature Operator Card Install S-Series versasec.com 1(28) Table of Contents Install and Issuing your first Full Feature Operator Card... 3 Section 1: Install and Initial
VMware AirWatch Certificate Authentication for EAS with ADCS
 VMware AirWatch Certificate Authentication for EAS with ADCS For VMware AirWatch Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
VMware AirWatch Certificate Authentication for EAS with ADCS For VMware AirWatch Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
Microsoft Dynamics GP Web Client Installation and Administration Guide For Service Pack 1
 Microsoft Dynamics GP 2013 Web Client Installation and Administration Guide For Service Pack 1 Copyright Copyright 2013 Microsoft. All rights reserved. Limitation of liability This document is provided
Microsoft Dynamics GP 2013 Web Client Installation and Administration Guide For Service Pack 1 Copyright Copyright 2013 Microsoft. All rights reserved. Limitation of liability This document is provided
Lab - Create a Partition in Windows 8
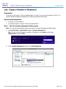 Lab - Create a Partition in Windows 8 Introduction In this lab, you will create a FAT32 formatted partition on a disk. You will convert the partition to NTFS. You will then identify the differences between
Lab - Create a Partition in Windows 8 Introduction In this lab, you will create a FAT32 formatted partition on a disk. You will convert the partition to NTFS. You will then identify the differences between
At Course Completion: Course Outline: Course 20742: Identity with Windows Server Learning Method: Instructor-led Classroom Learning
 Course Outline: Course 20742: Identity with Windows Server 2016 Learning Method: Instructor-led Classroom Learning Duration: 5.00 Day(s)/ 40 hrs Overview: This five-day instructor-led course teaches IT
Course Outline: Course 20742: Identity with Windows Server 2016 Learning Method: Instructor-led Classroom Learning Duration: 5.00 Day(s)/ 40 hrs Overview: This five-day instructor-led course teaches IT
F-Secure Client Security. Quick Installation Guide
 F-Secure Client Security Quick Installation Guide F-Secure Client Security TOC 3 Contents Chapter 1: Introduction...5 Chapter 2: Installing Client Security...7 System requirements...8 Stand-alone installation...9
F-Secure Client Security Quick Installation Guide F-Secure Client Security TOC 3 Contents Chapter 1: Introduction...5 Chapter 2: Installing Client Security...7 System requirements...8 Stand-alone installation...9
Active Directory Services with Windows Server
 Active Directory Services with Windows Server 10969B; 5 days, Instructor-led Course Description Get hands on instruction and practice administering Active Directory technologies in Windows Server 2012
Active Directory Services with Windows Server 10969B; 5 days, Instructor-led Course Description Get hands on instruction and practice administering Active Directory technologies in Windows Server 2012
Managing Applications, Services, Folders, and Libraries
 4 LESSON Managing Applications, Services, Folders, and Libraries EXAM OBJECTIVE MATRIX SKILLS/CONCEPTS EXAM OBJECTIVE DESCRIPTION EXAM OBJECTIVE NUMBER Installing and Managing Applications Understand application
4 LESSON Managing Applications, Services, Folders, and Libraries EXAM OBJECTIVE MATRIX SKILLS/CONCEPTS EXAM OBJECTIVE DESCRIPTION EXAM OBJECTIVE NUMBER Installing and Managing Applications Understand application
Copyright
 This video will look at creating a relying party trust in Active Directory Federation Services. A relying party trust is required in order to create claims that will be used by the resource partner. In
This video will look at creating a relying party trust in Active Directory Federation Services. A relying party trust is required in order to create claims that will be used by the resource partner. In
COURSE OUTLINE. COURSE OBJECTIVES After completing this course, students will be able to: 1 - INSTALLING & CONFIGURING DCS
 20742 Identity with Windows Server 2016 This course teaches IT Pros how to deploy and configure Active Directory Domain Services in a distributed environment, how to implement Group Policy, how to perform
20742 Identity with Windows Server 2016 This course teaches IT Pros how to deploy and configure Active Directory Domain Services in a distributed environment, how to implement Group Policy, how to perform
SCCM Plug-in User Guide. Version 3.0
 SCCM Plug-in User Guide Version 3.0 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 301 4th Ave
SCCM Plug-in User Guide Version 3.0 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 301 4th Ave
Windows 2000 System Administration Handbook, 1/e
 Windows 2000 System Administration Handbook, 1/e Will Willis, Lewisville, Texas David Watts, Sugarland, Texas Tillman Strahan, Lewisville, Texas Copyright 2000, 721 pp. Paper format ISBN 0-13-027010-5
Windows 2000 System Administration Handbook, 1/e Will Willis, Lewisville, Texas David Watts, Sugarland, Texas Tillman Strahan, Lewisville, Texas Copyright 2000, 721 pp. Paper format ISBN 0-13-027010-5
Managing Group Policy application and infrastructure
 CHAPTER 5 Managing Group Policy application and infrastructure There is far more to managing Group Policy than knowing the location of specific policy items. After your environment has more than a couple
CHAPTER 5 Managing Group Policy application and infrastructure There is far more to managing Group Policy than knowing the location of specific policy items. After your environment has more than a couple
70-742: Identity in Windows Server Course Overview
 70-742: Identity in Windows Server 2016 Course Overview This course provides students with the knowledge and skills to install and configure domain controllers, manage Active Directory objects, secure
70-742: Identity in Windows Server 2016 Course Overview This course provides students with the knowledge and skills to install and configure domain controllers, manage Active Directory objects, secure
Q&A. DEMO Version
 Managing and Maintaining Windows 8 Q&A DEMO Version Copyright (c) 2013 Chinatag LLC. All rights reserved. Important Note Please Read Carefully For demonstration purpose only, this free version Chinatag
Managing and Maintaining Windows 8 Q&A DEMO Version Copyright (c) 2013 Chinatag LLC. All rights reserved. Important Note Please Read Carefully For demonstration purpose only, this free version Chinatag
Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server
 Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server Configure a Presence Gateway for Microsoft Exchange Integration, page 1 SAN and Wildcard Certificate Support, page
Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server Configure a Presence Gateway for Microsoft Exchange Integration, page 1 SAN and Wildcard Certificate Support, page
Identity with Windows Server 2016
 Identity with Windows Server 2016 20742B; 5 days, Instructor-led Course Description This five-day instructor-led course teaches IT Pros how to deploy and configure Active Directory Domain Services (AD
Identity with Windows Server 2016 20742B; 5 days, Instructor-led Course Description This five-day instructor-led course teaches IT Pros how to deploy and configure Active Directory Domain Services (AD
Table of Contents. Section 1: DocSTAR WebView v1.0 Requirements & Installation CD... 1 Section 2: DocSTAR WebView v1.
 WebView v1.0 Installation Guide Revision 3 7/29/2003 WebView v1.0 Installation GuG ide Revision 3 7/29/2003 u Introduction Table of Contents Section 1: DocSTAR WebView v1.0 Requirements & Installation
WebView v1.0 Installation Guide Revision 3 7/29/2003 WebView v1.0 Installation GuG ide Revision 3 7/29/2003 u Introduction Table of Contents Section 1: DocSTAR WebView v1.0 Requirements & Installation
20742: Identity with Windows Server 2016
 Course Content Course Description: This five-day instructor-led course teaches IT Pros how to deploy and configure Active Directory Domain Services (AD DS) in a distributed environment, how to implement
Course Content Course Description: This five-day instructor-led course teaches IT Pros how to deploy and configure Active Directory Domain Services (AD DS) in a distributed environment, how to implement
VMware AirWatch Certificate Authentication for EAS with NDES-MSCEP. For VMware AirWatch
 VMware AirWatch Certificate Authentication for EAS with NDES-MSCEP For VMware AirWatch H a v e d o c u m e n t a t io n f e e d b a c k? S u b m it a D o c u m e n t a t io n F e e d b a c k s u p p o
VMware AirWatch Certificate Authentication for EAS with NDES-MSCEP For VMware AirWatch H a v e d o c u m e n t a t io n f e e d b a c k? S u b m it a D o c u m e n t a t io n F e e d b a c k s u p p o
IBM Client Security Solutions. Client Security Software Version 1.0 Administrator's Guide
 IBM Client Security Solutions Client Security Software Version 1.0 Administrator's Guide December 1999 1 Before using this information and the product it supports, be sure to read Appendix A - U.S. export
IBM Client Security Solutions Client Security Software Version 1.0 Administrator's Guide December 1999 1 Before using this information and the product it supports, be sure to read Appendix A - U.S. export
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE. 31 January 2017
 BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
Installation Guide. . All right reserved. For more information about Specops Deploy and other Specops products, visit
 . All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
. All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
Cisco Secure ACS for Windows v3.2 With PEAP MS CHAPv2 Machine Authentication
 Cisco Secure ACS for Windows v3.2 With PEAP MS CHAPv2 Machine Authentication Document ID: 43486 Contents Introduction Prerequisites Requirements Components Used Background Theory Conventions Network Diagram
Cisco Secure ACS for Windows v3.2 With PEAP MS CHAPv2 Machine Authentication Document ID: 43486 Contents Introduction Prerequisites Requirements Components Used Background Theory Conventions Network Diagram
DigitalPersona Pro Enterprise
 DigitalPersona Pro Enterprise Quick Start Guide Version 5 DATA PROTECTION REMOTE ACCESS SECURE COMMUNICATION STRONG AUTHENTICATION ACCESS RECOVERY SINGLE SIGN-ON DigitalPersona Pro Enterprise DigitalPersona
DigitalPersona Pro Enterprise Quick Start Guide Version 5 DATA PROTECTION REMOTE ACCESS SECURE COMMUNICATION STRONG AUTHENTICATION ACCESS RECOVERY SINGLE SIGN-ON DigitalPersona Pro Enterprise DigitalPersona
Installation and Configuration Guide
 Installation and Configuration Guide 1 Document Versions: Date Version Description June, 14, 2014 1.0 Initial Release March, 14, 2016 1.1 Minor Changes 2 Installing SCUP 2011: Install WSUS (If needed).
Installation and Configuration Guide 1 Document Versions: Date Version Description June, 14, 2014 1.0 Initial Release March, 14, 2016 1.1 Minor Changes 2 Installing SCUP 2011: Install WSUS (If needed).
Active Directory Services with Windows Server
 Course Code: M10969 Vendor: Microsoft Course Overview Duration: 5 RRP: POA Active Directory Services with Windows Server Overview Get Hands on instruction and practice administering Active Directory technologies
Course Code: M10969 Vendor: Microsoft Course Overview Duration: 5 RRP: POA Active Directory Services with Windows Server Overview Get Hands on instruction and practice administering Active Directory technologies
"Charting the Course... MOC B Active Directory Services with Windows Server Course Summary
 Description Course Summary Get Hands on instruction and practice administering Active Directory technologies in Windows Server 2012 and Windows Server 2012 R2 in this 5-day Microsoft Official Course. You
Description Course Summary Get Hands on instruction and practice administering Active Directory technologies in Windows Server 2012 and Windows Server 2012 R2 in this 5-day Microsoft Official Course. You
Microsoft. TS Windows 7,Configuring.
 70-680 Microsoft TS Windows 7,Configuring http://www.pass4sureofficial.com Dumpspdf.com is a reputable IT certification examination guide, study guides and audio exam provider, we not only ensure that
70-680 Microsoft TS Windows 7,Configuring http://www.pass4sureofficial.com Dumpspdf.com is a reputable IT certification examination guide, study guides and audio exam provider, we not only ensure that
Enabling Smart Card Logon for Linux Using Centrify Suite
 DoD Public Key Enablement (PKE) Reference Guide Enabling Smart Card Logon for Linux Using Centrify Suite 2012.4 Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke/ URL: http://iase.disa.smil.mil/pki-pke/
DoD Public Key Enablement (PKE) Reference Guide Enabling Smart Card Logon for Linux Using Centrify Suite 2012.4 Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke/ URL: http://iase.disa.smil.mil/pki-pke/
Active Directory Services with Windows Server
 Active Directory Services with Windows Server Duration: 5 Days Course Code: 10969B About this course Get Hands on instruction and practice administering Active Directory technologies in Windows Server
Active Directory Services with Windows Server Duration: 5 Days Course Code: 10969B About this course Get Hands on instruction and practice administering Active Directory technologies in Windows Server
20411D D Enayat Meer
 Lab A Module 8: Implementing Direct Access by Using the Getting Started Wizard Scenario: Recommended lab time is 240 Minutes {a complete class session is dedicated for this lab} Many users at A. Datum
Lab A Module 8: Implementing Direct Access by Using the Getting Started Wizard Scenario: Recommended lab time is 240 Minutes {a complete class session is dedicated for this lab} Many users at A. Datum
ACTIVE DIRECTORY SERVICES WITH WINDOWS SERVER
 CENTER OF KNOWLEDGE, PATH TO SUCCESS Website: ACTIVE DIRECTORY SERVICES WITH WINDOWS SERVER Course: 10969A; Duration: 5 Days; Instructor-led WHAT YOU WILL LEARN Get hands-on instruction and practice administering
CENTER OF KNOWLEDGE, PATH TO SUCCESS Website: ACTIVE DIRECTORY SERVICES WITH WINDOWS SERVER Course: 10969A; Duration: 5 Days; Instructor-led WHAT YOU WILL LEARN Get hands-on instruction and practice administering
Practical 23 Manage Desktop Configuration using group policy and remote installation services.
 Practical 23 Manage Desktop Configuration using group policy and remote installation services. Group Policy Collection:- Group Policy is an infrastructure that allows you to implement specific configurations
Practical 23 Manage Desktop Configuration using group policy and remote installation services. Group Policy Collection:- Group Policy is an infrastructure that allows you to implement specific configurations
Part I. Windows XP Overview, Installation, and Startup COPYRIGHTED MATERIAL
 Part I Windows XP Overview, Installation, and Startup COPYRIGHTED MATERIAL Chapter 1 What s New in Windows XP? Windows XP suffers somewhat from a dual personality. In some ways it is a significant release,
Part I Windows XP Overview, Installation, and Startup COPYRIGHTED MATERIAL Chapter 1 What s New in Windows XP? Windows XP suffers somewhat from a dual personality. In some ways it is a significant release,
Enable the Always Offline Mode to Provide Faster Access to Files
 Enable the Always Offline Mode to Provide Faster Access to Files 13 out of 16 rated this helpful - Rate this topic Published: April 18, 2012 Updated: July 3, 2013 Applies To: Windows 8, Windows 8.1, Windows
Enable the Always Offline Mode to Provide Faster Access to Files 13 out of 16 rated this helpful - Rate this topic Published: April 18, 2012 Updated: July 3, 2013 Applies To: Windows 8, Windows 8.1, Windows
Installation Instructions for SAS Activity-Based Management 6.2
 Installation Instructions for SAS Activity-Based Management 6.2 Copyright Notice The correct bibliographic citation for this manual is as follows: SAS Institute Inc., Installation Instructions for SAS
Installation Instructions for SAS Activity-Based Management 6.2 Copyright Notice The correct bibliographic citation for this manual is as follows: SAS Institute Inc., Installation Instructions for SAS
Parallels Virtuozzo Containers 4.6 for Windows
 Parallels Parallels Virtuozzo Containers 4.6 for Windows Deploying Microsoft Clusters Copyright 1999-2010 Parallels Holdings, Ltd. and its affiliates. All rights reserved. Parallels Holdings, Ltd. c/o
Parallels Parallels Virtuozzo Containers 4.6 for Windows Deploying Microsoft Clusters Copyright 1999-2010 Parallels Holdings, Ltd. and its affiliates. All rights reserved. Parallels Holdings, Ltd. c/o
5.5.3 Lab: Managing Administrative Settings and Snap-ins in Windows XP
 5.5.3 Lab: Managing Administrative Settings and Snap-ins in Windows XP Introduction Print and complete this lab. In this lab, you will use administrative tools to monitor system resources. You will also
5.5.3 Lab: Managing Administrative Settings and Snap-ins in Windows XP Introduction Print and complete this lab. In this lab, you will use administrative tools to monitor system resources. You will also
Install Certificate on the Cisco Secure ACS Appliance for PEAP Clients
 Install Certificate on the Cisco Secure ACS Appliance for PEAP Clients Document ID: 64067 Contents Introduction Prerequisites Requirements Components Used Conventions Microsoft Certificate Service Installation
Install Certificate on the Cisco Secure ACS Appliance for PEAP Clients Document ID: 64067 Contents Introduction Prerequisites Requirements Components Used Conventions Microsoft Certificate Service Installation
LAB 5 ANSWER KEY WORKING WITH FIREWALLS, ENCRYPTED FILE SYSTEMS (EFS) AND USER ACCOUNT CONTROL (UAC)
 LAB 5 ANSWER KEY WORKING WITH FIREWALLS, ENCRYPTED FILE SYSTEMS (EFS) AND USER ACCOUNT CONTROL (UAC) This lab contains the following exercises: Exercise 5.1 Exercise 5.2 Exercise 5.3 Exercise 5.4 Exercise
LAB 5 ANSWER KEY WORKING WITH FIREWALLS, ENCRYPTED FILE SYSTEMS (EFS) AND USER ACCOUNT CONTROL (UAC) This lab contains the following exercises: Exercise 5.1 Exercise 5.2 Exercise 5.3 Exercise 5.4 Exercise
Identity with Microsoft Windows Server 2016 (MS-20742)
 Identity with Microsoft Windows Server 2016 (MS-20742) Modality: Virtual Classroom Duration: 5 Days SATV Value: 5 Days SUBSCRIPTION: Master, Premium About this course Windows Server vnext, which we now
Identity with Microsoft Windows Server 2016 (MS-20742) Modality: Virtual Classroom Duration: 5 Days SATV Value: 5 Days SUBSCRIPTION: Master, Premium About this course Windows Server vnext, which we now
SafeGuard LAN Crypt Client help
 SafeGuard LAN Crypt Client help Product version: 3.95 Document date: September 2016 Contents 1 What is SafeGuard LAN Crypt?...3 1.1 Data protection using SafeGuard LAN Crypt...3 1.2 SafeGuard LAN Crypt
SafeGuard LAN Crypt Client help Product version: 3.95 Document date: September 2016 Contents 1 What is SafeGuard LAN Crypt?...3 1.1 Data protection using SafeGuard LAN Crypt...3 1.2 SafeGuard LAN Crypt
BitLocker: How to enable Network Unlock
 BitLocker: How to enable Network Unlock 7 out of 9 rated this helpful - Rate this topic Published: August 15, 2012 Updated: August 15, 2012 Applies To: Windows Server 2012 Windows 8 and Windows Server
BitLocker: How to enable Network Unlock 7 out of 9 rated this helpful - Rate this topic Published: August 15, 2012 Updated: August 15, 2012 Applies To: Windows Server 2012 Windows 8 and Windows Server
COPYRIGHTED MATERIAL. Contents. Assessment Test
 Contents Introduction Assessment Test xxvii xxxvii Chapter 1 Installing Windows 7 1 Introducing Windows 7 2 Windows 7 Architecture 5 Preparing to Install Windows 7 6 Windows 7 Starter 7 Windows 7 Home
Contents Introduction Assessment Test xxvii xxxvii Chapter 1 Installing Windows 7 1 Introducing Windows 7 2 Windows 7 Architecture 5 Preparing to Install Windows 7 6 Windows 7 Starter 7 Windows 7 Home
Chapter 1: Windows Platform and Architecture. You will learn:
 Chapter 1: Windows Platform and Architecture Windows 2000 product family. New features/facilities of. Windows architecture. Changes to the kernel and kernel architecture. New features/facilities. Kernel
Chapter 1: Windows Platform and Architecture Windows 2000 product family. New features/facilities of. Windows architecture. Changes to the kernel and kernel architecture. New features/facilities. Kernel
Exam: Title : Windows 2000 Pro. Ver :
 Exam: 070-210 Title : Windows 2000 Pro Ver : 01.26.04 QUESTION 1 You purchase a USB board, ISDN terminal adapter for your Windows 2000 Professional portable computer. You plug the device into the USB port.
Exam: 070-210 Title : Windows 2000 Pro Ver : 01.26.04 QUESTION 1 You purchase a USB board, ISDN terminal adapter for your Windows 2000 Professional portable computer. You plug the device into the USB port.
Lesson 3: Identifying Key Characteristics of Workgroups and Domains
 1-16 Chapter 1 Introduction to Windows XP Professional Lesson 3: Identifying Key Characteristics of Workgroups and Domains Windows XP Professional supports two types of network environments in which users
1-16 Chapter 1 Introduction to Windows XP Professional Lesson 3: Identifying Key Characteristics of Workgroups and Domains Windows XP Professional supports two types of network environments in which users
Setting Access Controls on Files, Folders, Shares, and Other System Objects in Windows 2000
 Setting Access Controls on Files, Folders, Shares, and Other System Objects in Windows 2000 Define and set DAC policy (define group membership, set default DAC attributes, set DAC on files systems) Modify
Setting Access Controls on Files, Folders, Shares, and Other System Objects in Windows 2000 Define and set DAC policy (define group membership, set default DAC attributes, set DAC on files systems) Modify
Dohatec CA. Export/Import Procedure etoken Pro 72K FOR USERS OF ETOKENS [VERSION 1.0]
![Dohatec CA. Export/Import Procedure etoken Pro 72K FOR USERS OF ETOKENS [VERSION 1.0] Dohatec CA. Export/Import Procedure etoken Pro 72K FOR USERS OF ETOKENS [VERSION 1.0]](/thumbs/83/87091309.jpg) Dohatec CA Export/Import Procedure etoken Pro 72K FOR USERS OF ETOKENS [VERSION 1.0] 1 1 Digital Certificate Certificates issued by Dohatec CA are in X.509 v3 format. In Microsoft windows machines, these
Dohatec CA Export/Import Procedure etoken Pro 72K FOR USERS OF ETOKENS [VERSION 1.0] 1 1 Digital Certificate Certificates issued by Dohatec CA are in X.509 v3 format. In Microsoft windows machines, these
Getting Started with the Ed-Fi ODS and Ed-Fi ODS API
 Getting Started with the Ed-Fi ODS and Ed-Fi ODS API Ed-Fi ODS and Ed-Fi ODS API Version 2.0 - Technical Preview January 2015 2014-2015 Ed-Fi Alliance, LLC. All rights reserved. Ed-Fi is a registered trademark
Getting Started with the Ed-Fi ODS and Ed-Fi ODS API Ed-Fi ODS and Ed-Fi ODS API Version 2.0 - Technical Preview January 2015 2014-2015 Ed-Fi Alliance, LLC. All rights reserved. Ed-Fi is a registered trademark
Symantec Endpoint Protection Installation Guide
 Symantec Endpoint Protection 11.0 Installation Guide SYMANTEC ENDPOINT PROTECTION 11.0 TABLE OF CONTENTS A NEW SECURITY APPLICATION... 1 INTRODUCTION... 1 WHAT IS SYMANTEC ENDPOINT PROTECTION (SEP) 11.0?...
Symantec Endpoint Protection 11.0 Installation Guide SYMANTEC ENDPOINT PROTECTION 11.0 TABLE OF CONTENTS A NEW SECURITY APPLICATION... 1 INTRODUCTION... 1 WHAT IS SYMANTEC ENDPOINT PROTECTION (SEP) 11.0?...
Enabling Smart Card Logon for Mac OS X Using Centrify Suite
 DoD Public Key Enablement (PKE) Reference Guide Enabling Smart Card Logon for Mac OS X Using Centrify Suite 2012.4 Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke/ URL: http://iase.disa.smil.mil/pki-pke/
DoD Public Key Enablement (PKE) Reference Guide Enabling Smart Card Logon for Mac OS X Using Centrify Suite 2012.4 Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke/ URL: http://iase.disa.smil.mil/pki-pke/
This PDF Document was generated for free by the Aloaha PDF Suite If you want to learn how to make your own PDF Documents visit:
 INSTALLING AND CONFIGURING A WINDOWS SERVER 2003 ENTERPRISE CERTIFICATION AUTHORITY Certification Authorities can issue certificates to users and computers for a variety of purposes. In the context of
INSTALLING AND CONFIGURING A WINDOWS SERVER 2003 ENTERPRISE CERTIFICATION AUTHORITY Certification Authorities can issue certificates to users and computers for a variety of purposes. In the context of
File System NTFS. Section Seven. NTFS, EFS, Partitioning, and Navigating Folders
 13 August 2002 File System Section Seven NTFS, EFS, Partitioning, and Navigating Folders NTFS DEFINITION New Technologies File System or NTFS was first applied in Windows NT 3.0 back in 1992. This technology
13 August 2002 File System Section Seven NTFS, EFS, Partitioning, and Navigating Folders NTFS DEFINITION New Technologies File System or NTFS was first applied in Windows NT 3.0 back in 1992. This technology
Administration Guide - NetApp File Archiver
 Page 1 of 100 Administration Guide - NetApp File Archiver TABLE OF CONTENTS OVERVIEW Introduction Key Features Terminology SYSTEM REQUIREMENTS DEPLOYMENT Installation Method 1: Interactive Install Method
Page 1 of 100 Administration Guide - NetApp File Archiver TABLE OF CONTENTS OVERVIEW Introduction Key Features Terminology SYSTEM REQUIREMENTS DEPLOYMENT Installation Method 1: Interactive Install Method
Module 9. Configuring IPsec. Contents:
 Configuring IPsec 9-1 Module 9 Configuring IPsec Contents: Lesson 1: Overview of IPsec 9-3 Lesson 2: Configuring Connection Security Rules 9-11 Lesson 3: Configuring IPsec NAP Enforcement 9-21 Lab: Configuring
Configuring IPsec 9-1 Module 9 Configuring IPsec Contents: Lesson 1: Overview of IPsec 9-3 Lesson 2: Configuring Connection Security Rules 9-11 Lesson 3: Configuring IPsec NAP Enforcement 9-21 Lab: Configuring
MU2b Authentication, Authorization and Accounting Questions Set 2
 MU2b Authentication, Authorization and Accounting Questions Set 2 1. You enable the audit of successful and failed policy changes. Where can you view entries related to policy change attempts? Lesson 2
MU2b Authentication, Authorization and Accounting Questions Set 2 1. You enable the audit of successful and failed policy changes. Where can you view entries related to policy change attempts? Lesson 2
USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003)
 YATANARPON TELEPORT COMPANY LTD., YATANARPON CERTIFICATION AUTHORITY USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003) Yatanarpon Teleport Company Ltd., Hlaing Universities Campus, Hlaing Township,
YATANARPON TELEPORT COMPANY LTD., YATANARPON CERTIFICATION AUTHORITY USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003) Yatanarpon Teleport Company Ltd., Hlaing Universities Campus, Hlaing Township,
Forensics Challenges. Windows Encrypted Content John Howie CISA CISM CISSP Director, Security Community, Microsoft Corporation
 Forensics Challenges Windows Encrypted Content John Howie CISA CISM CISSP Director, Security Community, Microsoft Corporation Introduction Encrypted content is a challenge for investigators Makes it difficult
Forensics Challenges Windows Encrypted Content John Howie CISA CISM CISSP Director, Security Community, Microsoft Corporation Introduction Encrypted content is a challenge for investigators Makes it difficult
PERFORMING A CUSTOM INSTALLATION
 PERFORMING A CUSTOM INSTALLATION OF OBSERVEIT ObserveIT Performing a Custom Installation of ObserveIT 1 of 46 TABLE OF CONTENTS TABLE OF CONTENTS... 2 OVERVIEW... 4 DOCUMENT VERSIONS... 4 PRODUCT VERSION...
PERFORMING A CUSTOM INSTALLATION OF OBSERVEIT ObserveIT Performing a Custom Installation of ObserveIT 1 of 46 TABLE OF CONTENTS TABLE OF CONTENTS... 2 OVERVIEW... 4 DOCUMENT VERSIONS... 4 PRODUCT VERSION...
Deployment guide for Duet Enterprise for Microsoft SharePoint and SAP Server 2.0
 Deployment guide for Duet Enterprise for Microsoft SharePoint and SAP Server 2.0 Microsoft Corporation Published: October 2012 Author: Microsoft Office System and Servers Team (itspdocs@microsoft.com)
Deployment guide for Duet Enterprise for Microsoft SharePoint and SAP Server 2.0 Microsoft Corporation Published: October 2012 Author: Microsoft Office System and Servers Team (itspdocs@microsoft.com)
Course Content of MCSA ( Microsoft Certified Solutions Associate )
 Course Content of MCSA 2012 - ( Microsoft Certified Solutions Associate ) Total Duration of MCSA : 45 Days Exam 70-410 - Installing and Configuring Windows Server 2012 (Course 20410A Duration : 40 hrs
Course Content of MCSA 2012 - ( Microsoft Certified Solutions Associate ) Total Duration of MCSA : 45 Days Exam 70-410 - Installing and Configuring Windows Server 2012 (Course 20410A Duration : 40 hrs
VMware Horizon FLEX Client User Guide
 Horizon FLEX 1.10 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
Horizon FLEX 1.10 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
Identity with Windows Server 2016 (20742)
 Identity with Windows Server 2016 (20742) Formato do curso: Presencial Preço: 1630 Duração: 35 horas This five-day instructor-led course teaches IT Pros how to deploy and configure Active Directory Domain
Identity with Windows Server 2016 (20742) Formato do curso: Presencial Preço: 1630 Duração: 35 horas This five-day instructor-led course teaches IT Pros how to deploy and configure Active Directory Domain
Quick Start - NetApp File Archiver
 Page 1 of 19 Quick Start - NetApp File Archiver TABLE OF CONTENTS OVERVIEW Introduction Key Features Terminology SYSTEM REQUIREMENTS DEPLOYMENT Installation Method 1: Interactive Install Method 2: Install
Page 1 of 19 Quick Start - NetApp File Archiver TABLE OF CONTENTS OVERVIEW Introduction Key Features Terminology SYSTEM REQUIREMENTS DEPLOYMENT Installation Method 1: Interactive Install Method 2: Install
YubiKey Smart Card Deployment Guide
 YubiKey Smart Card Deployment Guide Best Practices and Basic Setup YubiKey 4, YubiKey 4 Nano, YubiKey 4C, YubiKey 4C Nano, YubiKey NEO, YubiKey NEO-n Copyright 2017 Yubico Inc. All rights reserved. Trademarks
YubiKey Smart Card Deployment Guide Best Practices and Basic Setup YubiKey 4, YubiKey 4 Nano, YubiKey 4C, YubiKey 4C Nano, YubiKey NEO, YubiKey NEO-n Copyright 2017 Yubico Inc. All rights reserved. Trademarks
Secure ACS for Windows v3.2 With EAP TLS Machine Authentication
 Secure ACS for Windows v3.2 With EAP TLS Machine Authentication Document ID: 43722 Contents Introduction Prerequisites Requirements Components Used Background Theory Conventions Network Diagram Configuring
Secure ACS for Windows v3.2 With EAP TLS Machine Authentication Document ID: 43722 Contents Introduction Prerequisites Requirements Components Used Background Theory Conventions Network Diagram Configuring
Designing and Managing a Windows Public Key Infrastructure
 Designing and Managing a Windows Public Key Infrastructure Key Data Course #: 2821A Number of Days: 4 Format: Instructor-Led Certification Track: Exam 70-214: Implementing and Managing Security in a Windows
Designing and Managing a Windows Public Key Infrastructure Key Data Course #: 2821A Number of Days: 4 Format: Instructor-Led Certification Track: Exam 70-214: Implementing and Managing Security in a Windows
IceWarp SSL Certificate Process
 IceWarp Unified Communications IceWarp SSL Certificate Process Version 12 Printed on 20 April, 2017 Contents IceWarp SSL Certificate Process 1 Choosing the Proper Certificate Type... 2 Creating your CSR
IceWarp Unified Communications IceWarp SSL Certificate Process Version 12 Printed on 20 April, 2017 Contents IceWarp SSL Certificate Process 1 Choosing the Proper Certificate Type... 2 Creating your CSR
Acronis Backup & Recovery 11 Beta Advanced Editions
 Acronis Backup & Recovery 11 Beta Advanced Editions Quick Start Guide Table of contents 1 Main components... 3 2 Supported operating systems... 3 3 Where do I install the components?... 3 4 What you need
Acronis Backup & Recovery 11 Beta Advanced Editions Quick Start Guide Table of contents 1 Main components... 3 2 Supported operating systems... 3 3 Where do I install the components?... 3 4 What you need
KASPERSKY LAB. Kaspersky Administration Kit version 6.0. Reference Book
 KASPERSKY LAB Kaspersky Administration Kit version 6.0 Reference Book KASPERSKY ADMINISTRATION KIT VERSION 6.0 Reference Book Kaspersky Lab Ltd. Visit our website: http://www.kaspersky.com/ Revision date:
KASPERSKY LAB Kaspersky Administration Kit version 6.0 Reference Book KASPERSKY ADMINISTRATION KIT VERSION 6.0 Reference Book Kaspersky Lab Ltd. Visit our website: http://www.kaspersky.com/ Revision date:
Installation and Configuration Guide
 Installation and Configuration Guide 1 Document Versions: Date Version Description June 14, 2014 1.0 Initial Release March 14, 2016 1.1 Minor Changes June 21, 2017 1.2 Added Trusted Publishers 2 Installing
Installation and Configuration Guide 1 Document Versions: Date Version Description June 14, 2014 1.0 Initial Release March 14, 2016 1.1 Minor Changes June 21, 2017 1.2 Added Trusted Publishers 2 Installing
