Available online at ScienceDirect. Procedia Computer Science 60 (2015 )
|
|
|
- Elwin Tucker
- 6 years ago
- Views:
Transcription
1 Available online at ScienceDirect Procedia Computer Science 60 (2015 ) th International Conference in Knowledge Based and Intelligent Information and Engineering Systems Personal ID System by Means of Random Input Passwords Mieko Tanaka-Yamawaki a *, Yuki Tanaka b, Katsutoshi Yoshii a a Department of Information.& Knowledge Eng., Graduate School of Engineering, Tottori University, 101-4, Koyamacho-Minami, Tottori, Japan b Being Co.,Ltd., Support Division, 312-1, Sakurabashi, Tsu, Mie, , Japan Abstract A new password system is proposed that utilizes unconscious habits in typing the keyboard. Such password, named the Random Input Password (RIP, in short), is a random sequence of a fixed length generated by individual each time. In other words, this systems uses the human-generated random number as a password. This ID system does not require any specific codes to memorize, thus has a potential to flee us from the flood of increasing number of passwords. Although the RIP is different every time, it reflects peculiarities of individuals and distinguish each person to a certain degree. The identifier is constructed by using 6 parameters extracted from the pre-registered data for each individual. The average accuracy evaluated by using 9 individuals was that the Type-I error rate that disapproves the right person is 23% and Type-II error rate that approves wrong persons is 19% on the average. A possible refinement is discussed by reconsidering the effectiveness of the parameters The Authors. Published by Elsevier B.V. This is an open access article under the CC BY-NC-ND license ( The Authors. Published by Elsevier B.V. Peer-review under responsibility of KES of KES International. Keywords: Random Input Password (RIP), Human Random Generator (HuRG), Self Refusal Error(Type-I), Others Allowable Error(Type-II), Self Organizing Map (SOM) 1. Introduction Nowadays we are surrounded by rapidly changing financial and social systems, and under such environment we have many occasions to use passwords and very often forget the right one. In fact, there are too many passwords to remember for most of us. Moreover, the number of passwords increases almost every day, when we make reservations for conferences, airlines, hotels, and restaurants. This situation must be simplified. As a possible way to escape from the flood of passwords, we propose a new kind of password, the Random Input Password (RIP). The RIP is a random string generated by human. The use of human random generator (HuRG) 1,2,3 was originally practiced in the community of neurological doctors as a simple way of detecting the level of schizophrenia, based on the fact that the patients in the advanced stage of schizophrenia have difficulty to generated random numbers. The human random generation also caught the interests of computer scientists for the Turing Test to distinguish human * Corresponding author. Tel.: ; fax: address: mieko@eecs.tottori-u.ac.jp The Authors. Published by Elsevier B.V. This is an open access article under the CC BY-NC-ND license ( Peer-review under responsibility of KES International doi: /j.procs
2 1818 Mieko Tanaka-Yamawaki et al. / Procedia Computer Science 60 ( 2015 ) and a computer who impersonates man. It was also used in the study of developmental psychology in the context that the random generating ability reflects the stage of child developments. Our study of HuRG is not the same as any one of them. We have accumulated much data from normal young adults (namely, students in our Laboratory) to show that the random generation by human exhibits peculiarities of the person who generated the random strings. So far, we have investigated the relationship between the level of randomness of data strings and the character, age group, the level of dementia of the person who generate the data. In this paper, we propose to apply the HuRG for a new type of ID system that is free from memorizing any specific strings for passwords. 2 Random Input Password (RIP) In order to apply HuRG for the ID system, we set up a specific type of HuRG, that we call the "Random Input Password (RIP)", where the subject simply hits the selected keys on the PC keyboard L times by using one finger, within 2 seconds after hitting the previous key, as random as possible. We choose the four contact keys "T, Y, G, H" which are coded by "0, 1, 2, 3", respectively, as shown in Fig.1. The conditions of RIP is summarized in Table 1. The input length L is chosen to be 50, 40, 30 and 20. Fig.1 Hitting one of the 4 keys TYGH coded by Table 1. The conditions used to data taking of RIP keys input length L conditions 4 contact keys on the keyboard as random as possible, and quick next input within 2 seconds only one finger used There are four important elements to distinguish individuals from the random generations: [a] sequential patterns of the input keys [b] time intervals between key strokes [c] directions of the finger motions [d] intervals before returning to the same key [a]sequential patterns of the input keys Sequential patterns of the key appearance carries information characteristic to individuals. In order to quantify the sequential pattern, we count the frequency of appearance of 4 keys, represented by 4 symbols, "0, 1, 2, 3" corresponding to "T, Y, G, H", the frequency of appearance of arrays of length 2, such as "00, 01, 02, 03, 10, 11, 12, 13,.., 33", and of length 3, such as "000,.., 333". For example, the data sequence "32021" gives us the frequency of appearance of 1-digit to be "one" for the symbols "0", "1" and "3", and "two" for the symbol "2", and for 2-digit, "one" for the symbols "32", "20", "02", "21".
3 Mieko Tanaka-Yamawaki et al. / Procedia Computer Science 60 ( 2015 ) In particular, the 2-digit patterns are important to distinguish individuals. The patterns longer than 3 are not suitable, since the probability of appearance in the data sequence L=30-50 becomes too small. Thus we have 3 indices: P 1 : frequency of appearances of 1-digit patterns 0, 1, 2, 3 P 2 : frequency of appearances of 2-digit patterns 00,..,33 P 3 :frequency of appearances of 3-digit patterns 000,..,333 [b]time intervals between key strokes There are 3 types of intervals in key hitting as shown in Fig. 2. The accuracy of measurement is 0.1 second. The input data pass the identifier if two or more parameters out of three pass the test. Those three parameters are: T 1 : time between the two consecutive press-downs T 2 : time from the press-down to the release-up of a key T 3 : time from the release-up of the previous key to the press-down of the next key (T 3 =T 1 T 2 ) T 2 T 3 T 2 T 3 T 1 T 1 [c]directions of the finger motions (D) Fig. 2 Three time intervals, T 1, T 2, T 3 are illustrated The frequency of appearance of the five directions, {still( ), horizontal( ), vertical( ), left slant( ), right slant ( )}, that the input finger moves between two consecutive inputs reflects characteristics of the individuals. The frequencies of appearance of the 5 directions are registered as the reference vector for each subject. If the test vector coincides with the reference vector, the inner product between the test vector and the reference vector becomes one, and the test data proves to have been generated by the same subject. However, the reference vector involves variances over N=20 trials. Thus we set the evaluation criteria for each subject based on the average and the standard deviation of N=20 trials, in such a way that the 9 subjects separately recognized in this experiment. [d]intervals to return to the same key(r) The intervals before returning to the same key also carries information of individuals. Usually, the distance larger than 10, or zero is hardly observed. 3 Learning the Pattern of Individuals The pattern of individual subjects is constructed by using the 6 parameters of the 4 elements, P 2, P 3, T 1, T 2, D, and R. The average values of the 6 parameters with errors are used as identifiers. 3.1 Experimental Setup A subject of the experiment is asked to input the ID and RIP, consecutively by N times. If all the 4 elements, P, T, D, R, are correct, then it passes the authentication. After collecting N RIPs from all the subjects, a set of identifiers are constructed. The process of authentication is one-to-one, as illustrated in Fig.3. When User B enters his/her ID and a RIP, the identifier of B is called from the system and used to check the similarity with the input.
4 1820 Mieko Tanaka-Yamawaki et al. / Procedia Computer Science 60 ( 2015 ) Nine students in the age of 20's served as the subjects of this experiment. The job flow is shown in Fig.4. The number of input, N, is chosen to be 20 and 30. The display of the registration is shown in Fig. 5, and the display of the identification is shown in Fig. 6. We first perform a closed test, using the same N=30 data set to test the performance of the system. Then, by using new data taken a few days to a few weeks after the days when the first set of data are taken, we perform open tests. Fig. 3 One-to-one authentication method Fig. 4 System flowchart Fig. 5 Registration window is shown at the 2nd RIP of N=30
5 Mieko Tanaka-Yamawaki et al. / Procedia Computer Science 60 ( 2015 ) Fig. 6 Execution window is shown at the moment of login 3.2 Evaluation by the identifiers The identifiers are constructed for each subject who offered data set of N strings of equal length L. Essentially they are eight dimensional real-valued vectors of the parameters, V = (P, T, D, R) (1) Each element of this vector is obtained by averaging over the elements by N samples, with errors proportional to the standard deviations per element. The test data is also converted to a vector of the same dimension. V test = (P', T', D', R') (2) If the inner product between the test vector and the corresponding vector of the identifier is sufficiently large, the test string is admitted to be the RIP of the right person. (V, V test ) > threshold (3) However, the threshold values of this evaluation criteria are currently chosen by experience. 4 Experimental Results The results are evaluated by two parameters, SR and OA. SR, the self refusal rate, is the Type-I error rate in which the right person is rejected by the ID system, and OA, the others allowable rate, is the Type-II error rate in which wrong persons are admitted by the ID systems 4. Those two errors are reciprocal each other. It is impossible to eliminate both of them simultaneously. If the Type-I error rate is large, the right person has difficulty in entering the system, which is quite awkward but common to many biometrical IDs such as finger prints. On the other hand, if the Type-II error rate is large, the system is not secure. Those two errors depend on the choice of the threshold values. We have tested L = 30, 40, 50 and N = 20, 30. The result is summarized in Fig.7 for the closed test, and in Fig.8 for the open test. The closed test is a test in which the test data are chosen from the set of the same data set used for learning, while the open test uses new data set independent of the data set used for learning. The best result, with the smallest errors, is obtained in the case of L=40, N=20 for both cases 5. The result for individual subjects (A, B,, H,I), together with the average value is summarized in Fig.8. The average values of the errors would be much smaller if we exclude the two subjects (E, G).
6 1822 Mieko Tanaka-Yamawaki et al. / Procedia Computer Science 60 ( 2015 ) L,N 50,30 40,30 30,30 50,20 40,20 30,20 SR(%) OA(%) Fig. 7 Average error rates for six sets of L,N (close test) L,N 50,30 40,30 30,30 50,20 40,20 30,20 SR(%) OA(%) Fig. 8 Average error rates for six sets of L,N (open test) A B C D E F G H I AVE SR(%) OA(%) Fig. 9 Average error rates for individual subjects(close test)
7 Mieko Tanaka-Yamawaki et al. / Procedia Computer Science 60 ( 2015 ) A B C D E F G H I AVE SR(%) OA(%) Fig. 10 Average error rates for individual subjects (open test) 5 Selection of Parameters Encouraged by the partial success of the preliminary result, some attempts have been practiced in order to reduce the errors, by selecting the parameters as well as the subjects. By interviewing the nine subjects who offered the data, it is found that the subject G intentionally generated different types of data every time. On the other hand, I,B,D,F,H show quite encouraging results, as shown in Fig. 8 and Fig. 9. We therefore assume that the RIP is suitable to use among friends of a small circle who attempt to behave cooperatively. By this reason, we exclude G, E, A, C and concentrate to find good parameters to authenticate 5 subjects (I,B,D,F,H) who offer positive attitude in the experiment. The first attempt is to compare the relative contribution of P 1, P 2,..., P 6. Fig shows the degree of matching between the identifier and the test data for those parameters. The better performance is obtained as the pattern length grows up to P 4, then get saturated and falls after P 5. Fig. 11 Performance of P 1, P 2,..., P 6 Next, the relative performance of 8 parameters in Eq. (1), such as P 1, P 2, P 3, T 1, T 2, T 3, D, R, have been examined by mans of self-organizing maps (SOM) 7. In the practice, the spherical SOM 8 is used in order to eliminate the boundary
8 1824 Mieko Tanaka-Yamawaki et al. / Procedia Computer Science 60 ( 2015 ) effect. SOM is a leaning machine based on teacher-less neural network, and used to represent multi-dimensional data in lower dimensional spaces, such as one, two, or three. The SOM is a useful to classify multidimensional data into groups. By using this tool,, various combinations of parameters are examined. In order to examine the effectiveness of parameter P 2, the frequency of appearance of TT, TH, YT, YY, YG, YH, GT, GY, GG, GH, HT, HY, HG, HH for the selected 5 subjects are classified. If P 2 is a good parameter to distinguish the 5 subjects, the 30 data files of each subject aggregate separately. The selected 5 subjects are coded as {A,B,C,D,E} for convenience. The 30 independent data files per subject (150 data files in total) classified into 5 distinct areas, as shown in Fig.12. For example, the 30 files of subject A are named as A-1, A-2,..., A-30, and 100% of them are gathered into the region A in the picture (a), which is viewed from the side of A. Also 100% of the 30 files of subject D, named as D-1, D-2,.., D-30, are gathered into the region D in the picture D. However, the rate of aggregation of the region B is 26/30 the region C is 29/30 the region E is 25/30, as shown in the picture (b), (c), (e), respectively. Fig.12 Result of SOM classification by using SOM based on P 2. The regions A,B,C,D,E are shown in the pictures (a), (b), (c), (d), (e), respectively. C Fig.13 Result of SOM classification by using SOM based on T 1, T 2, T 3. The regions A,B,C,D,E are shown in the pictures (a), (b), (c), (d), (e), respectively.
9 Mieko Tanaka-Yamawaki et al. / Procedia Computer Science 60 ( 2015 ) (a) (b) (c) (d) (e) Fig.12 Result of SOM classification by using SOM based on T 1, T 2, T 3, and P 2. The regions A,B,C,D,E are shown in the pictures (a), (b), (c), (d), (e), respectively. Table 2 Occupation rates of 30 files in each region A-E Index Subjects A B C D E P 2 30/30 26/30 29/30 30/30 25/30 T 1, T 2, T 3 30/30 30/30 30/30 30/30 30/30 P 2+T 1, T 2,T 3 30/30 30/30 30/30 29/30 30/30 6. Conclusion We have constructed a personal authentication system based on the Random Input Password (RIP) and tested the system by using 9 subjects, for the parameters L=30, 40, 50, and N=20, 30. The relative frequencies of appearance of the 4 keys, the time intervals of consecutive inputs, and the patterns of RIPs are used to identify individuals. We have tested this system on 9 individuals as subjects, by closed tests as well as open tests. Using the parameters L=40 and N=20 which are supposed to be the best in our experiments, the result shows 23 percent of Type-I error, and 19 percent of Type-II error. While the level of Type-I error may be tolerable, Type-II should be significantly reduced for the sake of security. We expect to achieve improvement by reconsidering the indicators in more detail. Still, this kind of random password may not be safe by itself, if used alone. However, we can imagine various situations under which the RIP may add the level of security, if used together with other means. References 1. W.A.Wagenaar, Generation of Random Sequences by Human Subjects: A Critical Survey of Literature, Psychological Bulletin, Vol.77, pp.65-72, J.N.Towse, D.Nell(1998), Analyzing Human Random Generation Behavior: A Review of Methods Used and a Computer Program for Describing Performance, Instruments & Computers, Vol.30, pp M.Tanaka-Yamawaki and M.Mishima, Effective indices to characterize short sequences of human random generations, Artificial Life and Robotics,vol.12, pp , ITSCJ biometrics, 5. M.Tanaka-Yamawaki, Y. Tanaka, Proposing a System for Individual Authentication Using the Random Input Password, talk at COST Action TD 0120 held at The University of Seville, September 16-17, Seville Spain, Y. Mitani, Effectiveness of input patterns in RIP, Bachelors Thesis submitted to Tottori University (2015) 7. T. Kohonen, The Self-Organizing Map, Proceedings of the IEEE, Vol.78, Issue 9, pp , The authors are grateful to SOM-Japan led by Prof. H. Tokutaka for providing us to use their product.
Available online at ScienceDirect. Procedia Computer Science 59 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 59 (2015 ) 550 558 International Conference on Computer Science and Computational Intelligence (ICCSCI 2015) The Implementation
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 59 (2015 ) 550 558 International Conference on Computer Science and Computational Intelligence (ICCSCI 2015) The Implementation
Available online at ScienceDirect. Procedia Computer Science 60 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 60 (2015 ) 891 899 19th International Conference on Knowledge Based and Intelligent Information and Engineering Systems
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 60 (2015 ) 891 899 19th International Conference on Knowledge Based and Intelligent Information and Engineering Systems
Available online at ScienceDirect. Procedia Computer Science 60 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 60 (2015 ) 1014 1020 19th International Conference on Knowledge Based and Intelligent Information and Engineering Systems
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 60 (2015 ) 1014 1020 19th International Conference on Knowledge Based and Intelligent Information and Engineering Systems
Three-Dimensional Reconstruction from Projections Based On Incidence Matrices of Patterns
 Available online at www.sciencedirect.com ScienceDirect AASRI Procedia 9 (2014 ) 72 77 2014 AASRI Conference on Circuit and Signal Processing (CSP 2014) Three-Dimensional Reconstruction from Projections
Available online at www.sciencedirect.com ScienceDirect AASRI Procedia 9 (2014 ) 72 77 2014 AASRI Conference on Circuit and Signal Processing (CSP 2014) Three-Dimensional Reconstruction from Projections
ScienceDirect. Analogy between immune system and sensor replacement using mobile robots on wireless sensor networks
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 35 (2014 ) 1352 1359 18 th International Conference in Knowledge Based and Intelligent Information & Engineering Systems
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 35 (2014 ) 1352 1359 18 th International Conference in Knowledge Based and Intelligent Information & Engineering Systems
A User Authentication Based on Personal History - A User Authentication System Using History -
 A User Authentication Based on Personal History - A User Authentication System Using E-mail History - Masakatsu NISHIGAKI Graduate School of Science and Technology, Shizuoka University, 3-5-1 Johoku, Hamamatsu,
A User Authentication Based on Personal History - A User Authentication System Using E-mail History - Masakatsu NISHIGAKI Graduate School of Science and Technology, Shizuoka University, 3-5-1 Johoku, Hamamatsu,
Available online at ScienceDirect. Procedia Engineering 161 (2016 ) Bohdan Stawiski a, *, Tomasz Kania a
 Available online at www.sciencedirect.com ScienceDirect Procedia Engineering 161 (16 ) 937 943 World Multidisciplinary Civil Engineering-Architecture-Urban Planning Symposium 16, WMCAUS 16 Testing Quality
Available online at www.sciencedirect.com ScienceDirect Procedia Engineering 161 (16 ) 937 943 World Multidisciplinary Civil Engineering-Architecture-Urban Planning Symposium 16, WMCAUS 16 Testing Quality
Available online at ScienceDirect. Procedia Computer Science 56 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 56 (2015 ) 150 155 The 12th International Conference on Mobile Systems and Pervasive Computing (MobiSPC 2015) A Shadow
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 56 (2015 ) 150 155 The 12th International Conference on Mobile Systems and Pervasive Computing (MobiSPC 2015) A Shadow
Available online at ScienceDirect. Procedia Computer Science 58 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 58 (2015 ) 552 557 Second International Symposium on Computer Vision and the Internet (VisionNet 15) Fingerprint Recognition
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 58 (2015 ) 552 557 Second International Symposium on Computer Vision and the Internet (VisionNet 15) Fingerprint Recognition
ScienceDirect. Extending Lifetime of Wireless Sensor Networks by Management of Spare Nodes
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 34 (2014 ) 493 498 The 2nd International Workshop on Communications and Sensor Networks (ComSense-2014) Extending Lifetime
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 34 (2014 ) 493 498 The 2nd International Workshop on Communications and Sensor Networks (ComSense-2014) Extending Lifetime
Available online at ScienceDirect. Procedia Computer Science 45 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 45 (2015 ) 205 214 International Conference on Advanced Computing Technologies and Applications (ICACTA- 2015) Automatic
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 45 (2015 ) 205 214 International Conference on Advanced Computing Technologies and Applications (ICACTA- 2015) Automatic
Available online at ScienceDirect. Procedia Engineering 111 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Engineering 111 (2015 ) 902 906 XXIV R-S-P seminar, Theoretical Foundation of Civil Engineering (24RSP) (TFoCE 2015) About development and
Available online at www.sciencedirect.com ScienceDirect Procedia Engineering 111 (2015 ) 902 906 XXIV R-S-P seminar, Theoretical Foundation of Civil Engineering (24RSP) (TFoCE 2015) About development and
Available online at ScienceDirect. Energy Procedia 69 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Energy Procedia 69 (2015 ) 1885 1894 International Conference on Concentrating Solar Power and Chemical Energy Systems, SolarPACES 2014 Heliostat
Available online at www.sciencedirect.com ScienceDirect Energy Procedia 69 (2015 ) 1885 1894 International Conference on Concentrating Solar Power and Chemical Energy Systems, SolarPACES 2014 Heliostat
ScienceDirect. A privacy preserving technique to prevent sensitive behavior exposure in semantic location-based service
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 35 (2014 ) 318 327 18 th International Conference on Knowledge-Based and Intelligent Information & Engineering Systems
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 35 (2014 ) 318 327 18 th International Conference on Knowledge-Based and Intelligent Information & Engineering Systems
Available online at ScienceDirect. Procedia Computer Science 89 (2016 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 89 (2016 ) 341 348 Twelfth International Multi-Conference on Information Processing-2016 (IMCIP-2016) Parallel Approach
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 89 (2016 ) 341 348 Twelfth International Multi-Conference on Information Processing-2016 (IMCIP-2016) Parallel Approach
OPTIMIZING A VIDEO PREPROCESSOR FOR OCR. MR IBM Systems Dev Rochester, elopment Division Minnesota
 OPTIMIZING A VIDEO PREPROCESSOR FOR OCR MR IBM Systems Dev Rochester, elopment Division Minnesota Summary This paper describes how optimal video preprocessor performance can be achieved using a software
OPTIMIZING A VIDEO PREPROCESSOR FOR OCR MR IBM Systems Dev Rochester, elopment Division Minnesota Summary This paper describes how optimal video preprocessor performance can be achieved using a software
Behavior-based Authentication Systems. Multimedia Security
 Behavior-based Authentication Systems Multimedia Security Part 1: User Authentication Through Typing Biometrics Features Part 2: User Re-Authentication via Mouse Movements 2 User Authentication Through
Behavior-based Authentication Systems Multimedia Security Part 1: User Authentication Through Typing Biometrics Features Part 2: User Re-Authentication via Mouse Movements 2 User Authentication Through
ScienceDirect. A Secure and Light Weight Authentication Service in Hadoop using One Time Pad
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 50 (2015 ) 81 86 2nd International Symposium on Big Data and Cloud Computing (ISBCC 15) A Secure and Light Weight Authentication
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 50 (2015 ) 81 86 2nd International Symposium on Big Data and Cloud Computing (ISBCC 15) A Secure and Light Weight Authentication
Available online at ScienceDirect. Procedia Computer Science 35 (2014 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 35 (2014 ) 388 396 18 th International Conference on Knowledge-Based and Intelligent Information & Engineering Systems
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 35 (2014 ) 388 396 18 th International Conference on Knowledge-Based and Intelligent Information & Engineering Systems
Surface Roughness Control Based on Digital Copy Milling Concept to Achieve Autonomous Milling Operation
 Available online at www.sciencedirect.com Procedia CIRP 4 (2012 ) 35 40 3rd CIRP Conference on Process Machine Interactions (3rd PMI) Surface Roughness Control Based on Digital Copy Milling Concept to
Available online at www.sciencedirect.com Procedia CIRP 4 (2012 ) 35 40 3rd CIRP Conference on Process Machine Interactions (3rd PMI) Surface Roughness Control Based on Digital Copy Milling Concept to
A Novel Smoke Detection Method Using Support Vector Machine
 A Novel Smoke Detection Method Using Support Vector Machine Hidenori Maruta Information Media Center Nagasaki University, Japan 1-14 Bunkyo-machi, Nagasaki-shi Nagasaki, Japan Email: hmaruta@nagasaki-u.ac.jp
A Novel Smoke Detection Method Using Support Vector Machine Hidenori Maruta Information Media Center Nagasaki University, Japan 1-14 Bunkyo-machi, Nagasaki-shi Nagasaki, Japan Email: hmaruta@nagasaki-u.ac.jp
Procedia - Social and Behavioral Sciences 143 ( 2014 ) CY-ICER D visualization in teaching anatomy
 Available online at www.sciencedirect.com ScienceDirect Procedia - Social and Behavioral Sciences 143 ( 2014 ) 367 371 CY-ICER 2014 3D visualization in teaching anatomy David Brazina a, Rostislav Fojtik
Available online at www.sciencedirect.com ScienceDirect Procedia - Social and Behavioral Sciences 143 ( 2014 ) 367 371 CY-ICER 2014 3D visualization in teaching anatomy David Brazina a, Rostislav Fojtik
Available online at ScienceDirect. Procedia Computer Science 96 (2016 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 96 (2016 ) 946 950 20th International Conference on Knowledge Based and Intelligent Information and Engineering Systems
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 96 (2016 ) 946 950 20th International Conference on Knowledge Based and Intelligent Information and Engineering Systems
Available online at ScienceDirect. Procedia Computer Science 96 (2016 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 96 (2016 ) 560 567 20th International Conference on Knowledge Based and Intelligent Information and Engineering Systems,
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 96 (2016 ) 560 567 20th International Conference on Knowledge Based and Intelligent Information and Engineering Systems,
Available online at ScienceDirect. Procedia Computer Science 56 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 56 (2015 ) 612 617 International Workshop on the Use of Formal Methods in Future Communication Networks (UFMFCN 2015) A
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 56 (2015 ) 612 617 International Workshop on the Use of Formal Methods in Future Communication Networks (UFMFCN 2015) A
Cluster Analysis using Spherical SOM
 Cluster Analysis using Spherical SOM H. Tokutaka 1, P.K. Kihato 2, K. Fujimura 2 and M. Ohkita 2 1) SOM Japan Co-LTD, 2) Electrical and Electronic Department, Tottori University Email: {tokutaka@somj.com,
Cluster Analysis using Spherical SOM H. Tokutaka 1, P.K. Kihato 2, K. Fujimura 2 and M. Ohkita 2 1) SOM Japan Co-LTD, 2) Electrical and Electronic Department, Tottori University Email: {tokutaka@somj.com,
Text clustering based on a divide and merge strategy
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 55 (2015 ) 825 832 Information Technology and Quantitative Management (ITQM 2015) Text clustering based on a divide and
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 55 (2015 ) 825 832 Information Technology and Quantitative Management (ITQM 2015) Text clustering based on a divide and
Defenses against Large Scale Online Password Guessing by Using Persuasive Cued Click Points
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 2, Issue. 4, April 2013,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 2, Issue. 4, April 2013,
Available online at ScienceDirect. Procedia Computer Science 56 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 56 (2015 ) 266 270 The 10th International Conference on Future Networks and Communications (FNC 2015) A Context-based Future
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 56 (2015 ) 266 270 The 10th International Conference on Future Networks and Communications (FNC 2015) A Context-based Future
A Hand Gesture Recognition Method Based on Multi-Feature Fusion and Template Matching
 Available online at www.sciencedirect.com Procedia Engineering 9 (01) 1678 1684 01 International Workshop on Information and Electronics Engineering (IWIEE) A Hand Gesture Recognition Method Based on Multi-Feature
Available online at www.sciencedirect.com Procedia Engineering 9 (01) 1678 1684 01 International Workshop on Information and Electronics Engineering (IWIEE) A Hand Gesture Recognition Method Based on Multi-Feature
Available online at ScienceDirect. Procedia Computer Science 98 (2016 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 98 (2016 ) 515 521 The 3rd International Symposium on Emerging Information, Communication and Networks (EICN 2016) A Speculative
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 98 (2016 ) 515 521 The 3rd International Symposium on Emerging Information, Communication and Networks (EICN 2016) A Speculative
Domain Specific Search Engine for Students
 Domain Specific Search Engine for Students Domain Specific Search Engine for Students Wai Yuen Tang The Department of Computer Science City University of Hong Kong, Hong Kong wytang@cs.cityu.edu.hk Lam
Domain Specific Search Engine for Students Domain Specific Search Engine for Students Wai Yuen Tang The Department of Computer Science City University of Hong Kong, Hong Kong wytang@cs.cityu.edu.hk Lam
Available online at ScienceDirect. IERI Procedia 4 (2013 ) 2 7
 Available online at www.sciencedirect.com ScienceDirect IERI Procedia 4 (2013 ) 2 7 2013 International Conference on Electronic Engineering and Computer Science The Web Security Password Authentication
Available online at www.sciencedirect.com ScienceDirect IERI Procedia 4 (2013 ) 2 7 2013 International Conference on Electronic Engineering and Computer Science The Web Security Password Authentication
Available online at ScienceDirect. Procedia Computer Science 96 (2016 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 96 (2016 ) 1409 1417 20th International Conference on Knowledge Based and Intelligent Information and Engineering Systems,
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 96 (2016 ) 1409 1417 20th International Conference on Knowledge Based and Intelligent Information and Engineering Systems,
Relation Organization of SOM Initial Map by Improved Node Exchange
 JOURNAL OF COMPUTERS, VOL. 3, NO. 9, SEPTEMBER 2008 77 Relation Organization of SOM Initial Map by Improved Node Echange MIYOSHI Tsutomu Department of Information and Electronics, Tottori University, Tottori,
JOURNAL OF COMPUTERS, VOL. 3, NO. 9, SEPTEMBER 2008 77 Relation Organization of SOM Initial Map by Improved Node Echange MIYOSHI Tsutomu Department of Information and Electronics, Tottori University, Tottori,
Available online at ScienceDirect. Procedia Computer Science 87 (2016 ) 12 17
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 87 (2016 ) 12 17 4th International Conference on Recent Trends in Computer Science & Engineering Segment Based Indexing
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 87 (2016 ) 12 17 4th International Conference on Recent Trends in Computer Science & Engineering Segment Based Indexing
Reducing Points In a Handwritten Curve (Improvement in a Note-taking Tool)
 Reducing Points In a Handwritten Curve (Improvement in a Note-taking Tool) Kaoru Oka oka@oz.ces.kyutech.ac.jp Faculty of Computer Science and Systems Engineering Kyushu Institute of Technology Japan Ryoji
Reducing Points In a Handwritten Curve (Improvement in a Note-taking Tool) Kaoru Oka oka@oz.ces.kyutech.ac.jp Faculty of Computer Science and Systems Engineering Kyushu Institute of Technology Japan Ryoji
ScienceDirect. The use of Optical Methods for Leak Testing Dampers
 Available online at www.sciencedirect.com ScienceDirect Procedia Engineering 69 ( 2014 ) 788 794 24th DAAAM International Symposium on Intelligent Manufacturing and Automation, 2013 The use of Optical
Available online at www.sciencedirect.com ScienceDirect Procedia Engineering 69 ( 2014 ) 788 794 24th DAAAM International Symposium on Intelligent Manufacturing and Automation, 2013 The use of Optical
Performance Analysis of Adaptive Beamforming Algorithms for Smart Antennas
 Available online at www.sciencedirect.com ScienceDirect IERI Procedia 1 (214 ) 131 137 214 International Conference on Future Information Engineering Performance Analysis of Adaptive Beamforming Algorithms
Available online at www.sciencedirect.com ScienceDirect IERI Procedia 1 (214 ) 131 137 214 International Conference on Future Information Engineering Performance Analysis of Adaptive Beamforming Algorithms
Available online at ScienceDirect. Procedia Computer Science 46 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 46 (2015 ) 1754 1761 International Conference on Information and Communication Technologies (ICICT 2014) Age Estimation
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 46 (2015 ) 1754 1761 International Conference on Information and Communication Technologies (ICICT 2014) Age Estimation
Available online at ScienceDirect. Procedia Computer Science 60 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 60 (2015 ) 1720 1727 19th International Conference on Knowledge Based and Intelligent Information and Engineering Systems
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 60 (2015 ) 1720 1727 19th International Conference on Knowledge Based and Intelligent Information and Engineering Systems
ScienceDirect. Exporting files into cloud using gestures in hand held devices-an intelligent attempt.
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 50 (2015 ) 258 263 2nd International Symposium on Big Data and Cloud Computing (ISBCC 15) Exporting files into cloud using
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 50 (2015 ) 258 263 2nd International Symposium on Big Data and Cloud Computing (ISBCC 15) Exporting files into cloud using
Procedia - Social and Behavioral Sciences 174 ( 2015 ) INTE Jintavee Khlaisang*
 Available online at www.sciencedirect.com ScienceDirect Procedia - Social and Behavioral Sciences 174 ( 2015 ) 751 758 INTE 2014 Research-based guidelines for evaluating educational service website: case
Available online at www.sciencedirect.com ScienceDirect Procedia - Social and Behavioral Sciences 174 ( 2015 ) 751 758 INTE 2014 Research-based guidelines for evaluating educational service website: case
CAN WE ESCAPE PASSWORDS?
 INFOSECURITY WITH PLYMOUTH UNIVERSITY CAN WE ESCAPE PASSWORDS? Prof. Steven Furnell Centre for Security, Communications & Network Research Plymouth University United Kingdom Introduction Represents an
INFOSECURITY WITH PLYMOUTH UNIVERSITY CAN WE ESCAPE PASSWORDS? Prof. Steven Furnell Centre for Security, Communications & Network Research Plymouth University United Kingdom Introduction Represents an
Available online at ScienceDirect. Procedia Computer Science 20 (2013 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 20 (2013 ) 522 527 Complex Adaptive Systems, Publication 3 Cihan H. Dagli, Editor in Chief Conference Organized by Missouri
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 20 (2013 ) 522 527 Complex Adaptive Systems, Publication 3 Cihan H. Dagli, Editor in Chief Conference Organized by Missouri
IJESRT. Scientific Journal Impact Factor: (ISRA), Impact Factor: 1.852
 IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY INTELLEGENT APPROACH FOR OFFLINE SIGNATURE VERIFICATION USING CHAINCODE AND ENERGY FEATURE EXTRACTION ON MULTICORE PROCESSOR Raju
IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY INTELLEGENT APPROACH FOR OFFLINE SIGNATURE VERIFICATION USING CHAINCODE AND ENERGY FEATURE EXTRACTION ON MULTICORE PROCESSOR Raju
Available online at ScienceDirect. Procedia Engineering 154 (2016 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Engineering 154 (2016 ) 223 228 12th International Conference on Hydroinformatics, HIC 2016 An Improved Method of Avoiding RF Congestion
Available online at www.sciencedirect.com ScienceDirect Procedia Engineering 154 (2016 ) 223 228 12th International Conference on Hydroinformatics, HIC 2016 An Improved Method of Avoiding RF Congestion
Development of a tool for the easy determination of control factor interaction in the Design of Experiments and the Taguchi Methods
 Development of a tool for the easy determination of control factor interaction in the Design of Experiments and the Taguchi Methods IKUO TANABE Department of Mechanical Engineering, Nagaoka University
Development of a tool for the easy determination of control factor interaction in the Design of Experiments and the Taguchi Methods IKUO TANABE Department of Mechanical Engineering, Nagaoka University
SharePoint User Manual For Undergraduate Business Students
 SharePoint User Manual For Undergraduate Business Students Prepared by the Undergraduate Office (UGO), CUHK Business School Page 1 of 22 Table of Contents 1. Login SharePoint... 3 2. UGO SharePoint Homepage...
SharePoint User Manual For Undergraduate Business Students Prepared by the Undergraduate Office (UGO), CUHK Business School Page 1 of 22 Table of Contents 1. Login SharePoint... 3 2. UGO SharePoint Homepage...
Available online at ScienceDirect. Procedia Computer Science 89 (2016 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 89 (2016 ) 562 567 Twelfth International Multi-Conference on Information Processing-2016 (IMCIP-2016) Image Recommendation
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 89 (2016 ) 562 567 Twelfth International Multi-Conference on Information Processing-2016 (IMCIP-2016) Image Recommendation
Particular experience in design and implementation of a Current Research Information System in Russia: national specificity
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 00 (2014) 000 000 www.elsevier.com/locate/procedia CRIS 2014 Particular experience in design and implementation of a Current
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 00 (2014) 000 000 www.elsevier.com/locate/procedia CRIS 2014 Particular experience in design and implementation of a Current
Procedia - Social and Behavioral Sciences 195 ( 2015 ) World Conference on Technology, Innovation and Entrepreneurship
 Available online at www.sciencedirect.com ScienceDirect Procedia - Social and Behavioral Sciences 195 ( 2015 ) 1959 1965 World Conference on Technology, Innovation and Entrepreneurship Investigation of
Available online at www.sciencedirect.com ScienceDirect Procedia - Social and Behavioral Sciences 195 ( 2015 ) 1959 1965 World Conference on Technology, Innovation and Entrepreneurship Investigation of
SCADA Systems Management based on WEB Services
 Available online at www.sciencedirect.com ScienceDirect Procedia Economics and Finance 32 ( 2015 ) 464 470 Emerging Markets Queries in Finance and Business SCADA Systems Management based on WEB Services
Available online at www.sciencedirect.com ScienceDirect Procedia Economics and Finance 32 ( 2015 ) 464 470 Emerging Markets Queries in Finance and Business SCADA Systems Management based on WEB Services
An Improved KNN Classification Algorithm based on Sampling
 International Conference on Advances in Materials, Machinery, Electrical Engineering (AMMEE 017) An Improved KNN Classification Algorithm based on Sampling Zhiwei Cheng1, a, Caisen Chen1, b, Xuehuan Qiu1,
International Conference on Advances in Materials, Machinery, Electrical Engineering (AMMEE 017) An Improved KNN Classification Algorithm based on Sampling Zhiwei Cheng1, a, Caisen Chen1, b, Xuehuan Qiu1,
Available online at ScienceDirect. Procedia Computer Science 22 (2013 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 22 (2013 ) 945 953 17 th International Conference in Knowledge Based and Intelligent Information and Engineering Systems
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 22 (2013 ) 945 953 17 th International Conference in Knowledge Based and Intelligent Information and Engineering Systems
Interactive Video Retrieval System Integrating Visual Search with Textual Search
 From: AAAI Technical Report SS-03-08. Compilation copyright 2003, AAAI (www.aaai.org). All rights reserved. Interactive Video Retrieval System Integrating Visual Search with Textual Search Shuichi Shiitani,
From: AAAI Technical Report SS-03-08. Compilation copyright 2003, AAAI (www.aaai.org). All rights reserved. Interactive Video Retrieval System Integrating Visual Search with Textual Search Shuichi Shiitani,
Indian Multi-Script Full Pin-code String Recognition for Postal Automation
 2009 10th International Conference on Document Analysis and Recognition Indian Multi-Script Full Pin-code String Recognition for Postal Automation U. Pal 1, R. K. Roy 1, K. Roy 2 and F. Kimura 3 1 Computer
2009 10th International Conference on Document Analysis and Recognition Indian Multi-Script Full Pin-code String Recognition for Postal Automation U. Pal 1, R. K. Roy 1, K. Roy 2 and F. Kimura 3 1 Computer
Available online at ScienceDirect. Procedia Computer Science 52 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 52 (2015 ) 614 621 The 6th International Conference on Ambient Systems, Networks and Technologies (ANT 2015) Investigating
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 52 (2015 ) 614 621 The 6th International Conference on Ambient Systems, Networks and Technologies (ANT 2015) Investigating
Completing & Submitted the IRB Approval of Human Subjects Form
 Completing & Submitted the IRB Approval of Human Subjects Form All areas of the form should be completed. Once completed it must be submitted to the IRB by sending it to the EU IRB Chairperson. The following
Completing & Submitted the IRB Approval of Human Subjects Form All areas of the form should be completed. Once completed it must be submitted to the IRB by sending it to the EU IRB Chairperson. The following
Available online at ScienceDirect. Procedia Computer Science 59 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 59 (2015 ) 419 426 International Conference on Computer Science and Computational Intelligence (ICCSCI 2015) Degree Centrality
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 59 (2015 ) 419 426 International Conference on Computer Science and Computational Intelligence (ICCSCI 2015) Degree Centrality
Optimizing industry robot for maximum speed with high accuracy
 Available online at www.sciencedirect.com Procedia Engineering 48 (2012 ) 533 542 MMaMS 2012 Optimizing industry robot for maximum speed with high accuracy Peter Papcun a *, Ján Jadlovský a a Department
Available online at www.sciencedirect.com Procedia Engineering 48 (2012 ) 533 542 MMaMS 2012 Optimizing industry robot for maximum speed with high accuracy Peter Papcun a *, Ján Jadlovský a a Department
Segmentation of Arabic handwritten text to lines
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 73 (2015 ) 115 121 The International Conference on Advanced Wireless, Information, and Communication Technologies (AWICT
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 73 (2015 ) 115 121 The International Conference on Advanced Wireless, Information, and Communication Technologies (AWICT
Authentication by Mouse Movements. CS 297 Report. Shivani Hashia Advisor: Dr.Chris Pollett. May 2004
 Authentication by Mouse Movements CS 297 Report by Shivani Hashia (shivani_hash@hotmail.com) Advisor: Dr.Chris Pollett May 2004 Authentication by Mouse Movements By Shivani Hashia Abstract Security systems
Authentication by Mouse Movements CS 297 Report by Shivani Hashia (shivani_hash@hotmail.com) Advisor: Dr.Chris Pollett May 2004 Authentication by Mouse Movements By Shivani Hashia Abstract Security systems
ScienceDirect. Reducing Semantic Gap in Video Retrieval with Fusion: A survey
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 50 (2015 ) 496 502 Reducing Semantic Gap in Video Retrieval with Fusion: A survey D.Sudha a, J.Priyadarshini b * a School
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 50 (2015 ) 496 502 Reducing Semantic Gap in Video Retrieval with Fusion: A survey D.Sudha a, J.Priyadarshini b * a School
Total cost of ownership for application replatform by open-source SW
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 91 (2016 ) 677 682 Information Technology and Quantitative Management (ITQM 2016) Total cost of ownership for application
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 91 (2016 ) 677 682 Information Technology and Quantitative Management (ITQM 2016) Total cost of ownership for application
Available online at ScienceDirect. Procedia Computer Science 46 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 46 (2015 ) 949 956 International Conference on Information and Communication Technologies (ICICT 2014) Software Test Automation:
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 46 (2015 ) 949 956 International Conference on Information and Communication Technologies (ICICT 2014) Software Test Automation:
A METHOD OF MAP MATCHING FOR PERSONAL POSITIONING SYSTEMS
 The 21 st Asian Conference on Remote Sensing December 4-8, 2000 Taipei, TAIWA A METHOD OF MAP MATCHIG FOR PERSOAL POSITIOIG SSTEMS Kay KITAZAWA, usuke KOISHI, Ryosuke SHIBASAKI Ms., Center for Spatial
The 21 st Asian Conference on Remote Sensing December 4-8, 2000 Taipei, TAIWA A METHOD OF MAP MATCHIG FOR PERSOAL POSITIOIG SSTEMS Kay KITAZAWA, usuke KOISHI, Ryosuke SHIBASAKI Ms., Center for Spatial
: BIOMETRIC AUTHENTICATION TOOL FOR USER IDENTIFICATION
 2006-287: BIOMETRIC AUTHENTICATION TOOL FOR USER IDENTIFICATION Mario Garcia, Texas A&M University-Corpus Christi American Society for Engineering Education, 2006 Page 11.277.1 Biometric Authentication
2006-287: BIOMETRIC AUTHENTICATION TOOL FOR USER IDENTIFICATION Mario Garcia, Texas A&M University-Corpus Christi American Society for Engineering Education, 2006 Page 11.277.1 Biometric Authentication
Procedia Computer Science
 Procedia Computer Science 3 (2011) 859 865 Procedia Computer Science 00 (2010) 000 000 Procedia Computer Science www.elsevier.com/locate/procedia www.elsevier.com/locate/procedia WCIT-2010 A new median
Procedia Computer Science 3 (2011) 859 865 Procedia Computer Science 00 (2010) 000 000 Procedia Computer Science www.elsevier.com/locate/procedia www.elsevier.com/locate/procedia WCIT-2010 A new median
Procedia Computer Science
 Procedia Computer Science 3 (2011) 584 588 Procedia Computer Science 00 (2010) 000 000 Procedia Computer Science www.elsevier.com/locate/procedia www.elsevier.com/locate/procedia WCIT 2010 Diagnosing internal
Procedia Computer Science 3 (2011) 584 588 Procedia Computer Science 00 (2010) 000 000 Procedia Computer Science www.elsevier.com/locate/procedia www.elsevier.com/locate/procedia WCIT 2010 Diagnosing internal
ScienceDirect. Exporting data from an openehr repository to standard formats
 Available online at www.sciencedirect.com ScienceDirect Procedia Technology 16 (2014 ) 1391 1396 CENTERIS 2014 - Conference on ENTERprise Information Systems / ProjMAN 2014 - International Conference on
Available online at www.sciencedirect.com ScienceDirect Procedia Technology 16 (2014 ) 1391 1396 CENTERIS 2014 - Conference on ENTERprise Information Systems / ProjMAN 2014 - International Conference on
Enhanced Iris Recognition System an Integrated Approach to Person Identification
 Enhanced Iris Recognition an Integrated Approach to Person Identification Gaganpreet Kaur Research Scholar, GNDEC, Ludhiana. Akshay Girdhar Associate Professor, GNDEC. Ludhiana. Manvjeet Kaur Lecturer,
Enhanced Iris Recognition an Integrated Approach to Person Identification Gaganpreet Kaur Research Scholar, GNDEC, Ludhiana. Akshay Girdhar Associate Professor, GNDEC. Ludhiana. Manvjeet Kaur Lecturer,
Available online at ScienceDirect. Procedia Computer Science 34 (2014 ) Generic Connector for Mobile Devices
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 34 (2014 ) 613 618 International Symposium on Emerging Inter-networks, Communication and Mobility (EICM-2014) Generic Email
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 34 (2014 ) 613 618 International Symposium on Emerging Inter-networks, Communication and Mobility (EICM-2014) Generic Email
Preliminary Research on Distributed Cluster Monitoring of G/S Model
 Available online at www.sciencedirect.com Physics Procedia 25 (2012 ) 860 867 2012 International Conference on Solid State Devices and Materials Science Preliminary Research on Distributed Cluster Monitoring
Available online at www.sciencedirect.com Physics Procedia 25 (2012 ) 860 867 2012 International Conference on Solid State Devices and Materials Science Preliminary Research on Distributed Cluster Monitoring
A recommendation engine by using association rules
 Available online at www.sciencedirect.com Procedia - Social and Behavioral Sciences 62 ( 2012 ) 452 456 WCBEM 2012 A recommendation engine by using association rules Ozgur Cakir a 1, Murat Efe Aras b a
Available online at www.sciencedirect.com Procedia - Social and Behavioral Sciences 62 ( 2012 ) 452 456 WCBEM 2012 A recommendation engine by using association rules Ozgur Cakir a 1, Murat Efe Aras b a
POWERSCHOOL PARENT PORTAL. The Basics
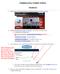 The Basics 1. Click on the A+ Parent Portal link on the right side of the Mt. Mourne website 2. Click on PowerSchool Login for Parents - use Chrome or Firefox not IE 3. If you already have an account,
The Basics 1. Click on the A+ Parent Portal link on the right side of the Mt. Mourne website 2. Click on PowerSchool Login for Parents - use Chrome or Firefox not IE 3. If you already have an account,
The Growing Gap between Landline and Dual Frame Election Polls
 MONDAY, NOVEMBER 22, 2010 Republican Share Bigger in -Only Surveys The Growing Gap between and Dual Frame Election Polls FOR FURTHER INFORMATION CONTACT: Scott Keeter Director of Survey Research Michael
MONDAY, NOVEMBER 22, 2010 Republican Share Bigger in -Only Surveys The Growing Gap between and Dual Frame Election Polls FOR FURTHER INFORMATION CONTACT: Scott Keeter Director of Survey Research Michael
Available online at ScienceDirect. Procedia Computer Science 87 (2016 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 87 (2016 ) 270 274 4th International Conference on Recent Trends in Computer Science & Engineering Analysis of Routing
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 87 (2016 ) 270 274 4th International Conference on Recent Trends in Computer Science & Engineering Analysis of Routing
SOST 201 September 20, Stem-and-leaf display 2. Miscellaneous issues class limits, rounding, and interval width.
 1 Social Studies 201 September 20, 2006 Presenting data and stem-and-leaf display See text, chapter 4, pp. 87-160. Introduction Statistical analysis primarily deals with issues where it is possible to
1 Social Studies 201 September 20, 2006 Presenting data and stem-and-leaf display See text, chapter 4, pp. 87-160. Introduction Statistical analysis primarily deals with issues where it is possible to
Robustness of Selective Desensitization Perceptron Against Irrelevant and Partially Relevant Features in Pattern Classification
 Robustness of Selective Desensitization Perceptron Against Irrelevant and Partially Relevant Features in Pattern Classification Tomohiro Tanno, Kazumasa Horie, Jun Izawa, and Masahiko Morita University
Robustness of Selective Desensitization Perceptron Against Irrelevant and Partially Relevant Features in Pattern Classification Tomohiro Tanno, Kazumasa Horie, Jun Izawa, and Masahiko Morita University
ScienceDirect. Vulnerability Assessment & Penetration Testing as a Cyber Defence Technology
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 57 (2015 ) 710 715 3rd International Conference on Recent Trends in Computing 2015 (ICRTC-2015) Vulnerability Assessment
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 57 (2015 ) 710 715 3rd International Conference on Recent Trends in Computing 2015 (ICRTC-2015) Vulnerability Assessment
Improvement of a tool for the easy determination of control factor interaction in the Design of Experiments and the Taguchi Methods
 Improvement of a tool for the easy determination of control factor in the Design of Experiments and the Taguchi Methods I. TANABE, and T. KUMAI Abstract In recent years, the Design of Experiments (hereafter,
Improvement of a tool for the easy determination of control factor in the Design of Experiments and the Taguchi Methods I. TANABE, and T. KUMAI Abstract In recent years, the Design of Experiments (hereafter,
RETRACTED ARTICLE. Web-Based Data Mining in System Design and Implementation. Open Access. Jianhu Gong 1* and Jianzhi Gong 2
 Send Orders for Reprints to reprints@benthamscience.ae The Open Automation and Control Systems Journal, 2014, 6, 1907-1911 1907 Web-Based Data Mining in System Design and Implementation Open Access Jianhu
Send Orders for Reprints to reprints@benthamscience.ae The Open Automation and Control Systems Journal, 2014, 6, 1907-1911 1907 Web-Based Data Mining in System Design and Implementation Open Access Jianhu
Chapter 2: Descriptive Statistics
 Chapter 2: Descriptive Statistics Student Learning Outcomes By the end of this chapter, you should be able to: Display data graphically and interpret graphs: stemplots, histograms and boxplots. Recognize,
Chapter 2: Descriptive Statistics Student Learning Outcomes By the end of this chapter, you should be able to: Display data graphically and interpret graphs: stemplots, histograms and boxplots. Recognize,
Available online at ScienceDirect. Procedia Engineering 99 (2015 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Engineering 99 (2015 ) 575 580 APISAT2014, 2014 Asia-Pacific International Symposium on Aerospace Technology, APISAT2014 A 3D Anisotropic
Available online at www.sciencedirect.com ScienceDirect Procedia Engineering 99 (2015 ) 575 580 APISAT2014, 2014 Asia-Pacific International Symposium on Aerospace Technology, APISAT2014 A 3D Anisotropic
Available online at ScienceDirect. Procedia Computer Science 89 (2016 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 89 (2016 ) 778 784 Twelfth International Multi-Conference on Information Processing-2016 (IMCIP-2016) Color Image Compression
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 89 (2016 ) 778 784 Twelfth International Multi-Conference on Information Processing-2016 (IMCIP-2016) Color Image Compression
Video Inter-frame Forgery Identification Based on Optical Flow Consistency
 Sensors & Transducers 24 by IFSA Publishing, S. L. http://www.sensorsportal.com Video Inter-frame Forgery Identification Based on Optical Flow Consistency Qi Wang, Zhaohong Li, Zhenzhen Zhang, Qinglong
Sensors & Transducers 24 by IFSA Publishing, S. L. http://www.sensorsportal.com Video Inter-frame Forgery Identification Based on Optical Flow Consistency Qi Wang, Zhaohong Li, Zhenzhen Zhang, Qinglong
A Data Classification Algorithm of Internet of Things Based on Neural Network
 A Data Classification Algorithm of Internet of Things Based on Neural Network https://doi.org/10.3991/ijoe.v13i09.7587 Zhenjun Li Hunan Radio and TV University, Hunan, China 278060389@qq.com Abstract To
A Data Classification Algorithm of Internet of Things Based on Neural Network https://doi.org/10.3991/ijoe.v13i09.7587 Zhenjun Li Hunan Radio and TV University, Hunan, China 278060389@qq.com Abstract To
Achieve Significant Throughput Gains in Wireless Networks with Large Delay-Bandwidth Product
 Available online at www.sciencedirect.com ScienceDirect IERI Procedia 10 (2014 ) 153 159 2014 International Conference on Future Information Engineering Achieve Significant Throughput Gains in Wireless
Available online at www.sciencedirect.com ScienceDirect IERI Procedia 10 (2014 ) 153 159 2014 International Conference on Future Information Engineering Achieve Significant Throughput Gains in Wireless
Properly even harmonious labelings of disconnected graphs
 Available online at www.sciencedirect.com ScienceDirect AKCE International Journal of Graphs and Combinatorics 12 (2015) 193 203 www.elsevier.com/locate/akcej Properly even harmonious labelings of disconnected
Available online at www.sciencedirect.com ScienceDirect AKCE International Journal of Graphs and Combinatorics 12 (2015) 193 203 www.elsevier.com/locate/akcej Properly even harmonious labelings of disconnected
Multiple Choice Style Informatics
 Multiple Choice Style Informatics Jordan Tabov, Emil Kelevedzhiev & Borislav Lazarov I. Introduction. Jordan Tabov was an IMO participant and has been a team leader of the Bulgarian IMO team. He graduated
Multiple Choice Style Informatics Jordan Tabov, Emil Kelevedzhiev & Borislav Lazarov I. Introduction. Jordan Tabov was an IMO participant and has been a team leader of the Bulgarian IMO team. He graduated
EVALUATING DIFFERENT TOUCH-BASED INTERACTION TECHNIQUES IN A PUBLIC INFORMATION KIOSK
 EVALUATING DIFFERENT TOUCH-BASED INTERACTION TECHNIQUES IN A PUBLIC INFORMATION KIOSK Roope Raisamo Department of Computer Science University of Tampere P.O. Box 607 (Pinninkatu 53B) FIN-33101 Tampere,
EVALUATING DIFFERENT TOUCH-BASED INTERACTION TECHNIQUES IN A PUBLIC INFORMATION KIOSK Roope Raisamo Department of Computer Science University of Tampere P.O. Box 607 (Pinninkatu 53B) FIN-33101 Tampere,
A New Soft-Thresholding Image Denoising Method
 Available online at www.sciencedirect.com Procedia Technology 6 (2012 ) 10 15 2nd International Conference on Communication, Computing & Security [ICCCS-2012] A New Soft-Thresholding Image Denoising Method
Available online at www.sciencedirect.com Procedia Technology 6 (2012 ) 10 15 2nd International Conference on Communication, Computing & Security [ICCCS-2012] A New Soft-Thresholding Image Denoising Method
A Biometric Authentication System That Automatically Generates Feature Points
 A Biometric Authentication System That Automatically Generates Feature Points Hiroshi Dozono 1, Youki Inaba 1, Masanori Nakakuni 2 1 Faculty of Science and Engineering, Saga University, 1-Honjyo Saga,
A Biometric Authentication System That Automatically Generates Feature Points Hiroshi Dozono 1, Youki Inaba 1, Masanori Nakakuni 2 1 Faculty of Science and Engineering, Saga University, 1-Honjyo Saga,
Frequency, proportional, and percentage distributions.
 1 Social Studies 201 September 13-15, 2004 Presenting data and stem-and-leaf display See text, chapter 4, pp. 87-160. Introduction Statistical analysis primarily deals with issues where it is possible
1 Social Studies 201 September 13-15, 2004 Presenting data and stem-and-leaf display See text, chapter 4, pp. 87-160. Introduction Statistical analysis primarily deals with issues where it is possible
Visualization and Statistical Analysis of Multi Dimensional Data of Wireless Sensor Networks Using Self Organising Maps
 Visualization and Statistical Analysis of Multi Dimensional Data of Wireless Sensor Networks Using Self Organising Maps Thendral Puyalnithi #1, V Madhu Viswanatham *2 School of Computer Science and Engineering,
Visualization and Statistical Analysis of Multi Dimensional Data of Wireless Sensor Networks Using Self Organising Maps Thendral Puyalnithi #1, V Madhu Viswanatham *2 School of Computer Science and Engineering,
Ovid Technologies, Inc. Databases
 Physical Therapy Workshop. August 10, 2001, 10:00 a.m. 12:30 p.m. Guide No. 1. Search terms: Diabetes Mellitus and Skin. Ovid Technologies, Inc. Databases ACCESS TO THE OVID DATABASES You must first go
Physical Therapy Workshop. August 10, 2001, 10:00 a.m. 12:30 p.m. Guide No. 1. Search terms: Diabetes Mellitus and Skin. Ovid Technologies, Inc. Databases ACCESS TO THE OVID DATABASES You must first go
Available online at ScienceDirect. Procedia Computer Science 96 (2016 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 96 (2016 ) 179 186 20th International Conference on Knowledge Based and Intelligent Information and Engineering Systems,
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 96 (2016 ) 179 186 20th International Conference on Knowledge Based and Intelligent Information and Engineering Systems,
Hypergraph Grammars in hp-adaptive Finite Element Method
 Available online at www.sciencedirect.com Procedia Computer Science 18 (2013 ) 1545 1554 2013 International Conference on Computational Science Hypergraph Grammars in hp-adaptive Finite Element Method
Available online at www.sciencedirect.com Procedia Computer Science 18 (2013 ) 1545 1554 2013 International Conference on Computational Science Hypergraph Grammars in hp-adaptive Finite Element Method
2D Electrophoresis Gel Image and Diagnosis of a Disease
 2D Electrophoresis Gel Image and Diagnosis of a Disease Gene Kim and MyungHo Kim Bioinformatics Frontier Inc. 93 B Taylor Ave East Brunswick, NJ mkim@biofront.biz Abstract * : The process of diagnosing
2D Electrophoresis Gel Image and Diagnosis of a Disease Gene Kim and MyungHo Kim Bioinformatics Frontier Inc. 93 B Taylor Ave East Brunswick, NJ mkim@biofront.biz Abstract * : The process of diagnosing
