FAILURE MODE ANALYSIS USING MULTILEVEL FLOW MODELS
|
|
|
- Audrey Underwood
- 6 years ago
- Views:
Transcription
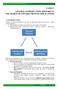
1 FAILURE MODE ANALYSIS USING MULTILEVEL FLOW MODELS Bengt Öhman* * Department of Information Technology, Lund Institute of Technology, Box 118, Lund, Sweden. Fax: , bengt@it.lth.se Abstract Failure mode analysis for complex systems is an important, and sometimes challenging, task. In this paper, a method for failure mode analysis based on Multilevel Flow Models (MFM) is presented. When an MFM model of the system exists, it is possible to perform an automated failure mode analysis, and even to give failure predictions in an online system in real time. The system is implemented in a version of the MFM Toolbox, a program for editing and testing MFM models on a Windows-based PC. I. INTRODUCTION When designing a complex industrial system, it is often important to study the effects of failures on other parts of the system. Traditionally, this has been done using manual methods, by filling out forms by hand, such as the Failure Mode and Effects Analysis method (FMEA). Some methods with automated computer support have evolved, such as the Fault Tree Analysis method (FTA), and the Goal Tree - Success Tree method (GTST). There are also tools available to automate parts of an FMEA analysis, see [10]. All these methods will collectively be called Failure Mode Analysis methods, or FMA methods for short, in this paper. An overview of some methods is available in [2]. GTST is described in [9], and FTA is described in [1]. A problem with many of these methods is that it is not possible to analyze several failures at the same time. Also, since the methods are mostly manual, it is possible to miss important scenarios during the analysis. Another important aspect is what will happen if the process is changed how will the new system behave? Are the previously obtained results still valid for the new process? These questions can be difficult to answer, and they may require that the whole analysis be done all over again. Model-based methods have an advantage in this scenario, especially with computer support. The part requiring most work the construction of the model is already done. What is needed is to change the part of the model that is affected by the restructuring of the process, after which all the original cases plus any new ones may be evaluated again. This will require less time and effort compared to a manual analysis, since the analysis itself is mostly automated. What is described in this paper is a new method for failure mode analysis based on Multilevel Flow Models (MFM) [8]. MFM is a graphical modeling language for systems of flows of mass, energy, or information, and is a good base for several diagnosis algorithms, such as alarm analysis and measurement validation, see [3]. Thus, if an MFM model of the system exists, it can be used for several other diagnosis algorithms, thereby increasing the value of the model. The FMA method developed for MFM has many nice properties, such as the possibility for on-line prediction of failures in real time, and it would make a nice complement to the traditional FMA methods. II. ABOUT FAILURE MODE ANALYSIS The purpose of performing a failure mode analysis is to investigate the effects of one or several failures in a system. This can be done using several methods, among the most well-known are FMEA and FTA (see part I). The general idea with these methods is to find all possible failures of a system, and to relate these to each other so that the effects or causes of a fault can be determined. This can be done using a graph, such as the one in Figure 1. Here, the faults numbered 1 to 4 are called basic faults, and the combination of one or several basic faults leads to larger faults. The analysis is then performed by starting with a large fault, and then investigating the tree to find the basic faults leading to this failure. Fault #6 Fault #1 Fault #2 Fault #3 Fault #5 Figure 1. An example of a fault tree. Fault #4 A shortcoming with the common methods for failure mode analysis is that the analysis is often done during the design phase for the system, and the results of the analysis are not easily retrievable by the operators during operation. It may also be the case that some of the failure modes are not analyzed, due to insufficient effort in the analysis. With these thoughts in mind, it is easy to see that an on-line, real Copyright 1999 by the European Union Control Association (EUCA). This paper was published in the proceedings of the 5 th European Control Conference, Karlsruhe, Germany, 1999, and is made available as an electronic reprint by the permission of EUCA.
2 time FMA system would be advantageous. Such a system would be able to provide the operators with predictions of future failures based on the current state of the system. The FMA algorithm for MFM is capable of both off-line and on-line analysis, and could be used in both the design phase for a system, and when the system is running. III. ABOUT MFM Multilevel Flow Models were invented by professor Morten Lind [8], and they are primarily used for modeling goals and functions and their relations of technical systems. However, the MFM models make an excellent base for diagnostic reasoning, and several algorithms have been developed. MFM models describe the goals and functions of a system. The goals describe the purposes of running the system (the answer to the question why? ), and the functions describe the capabilities of the system (the answer to the question how? ). The functions are connected in terms of flows of mass, energy, or information. The flow structures are connected into networks, to which the goals are attached. The functions are realized by components, which are the physical objects in a system. The connection between the networks and the goals are called achieve relations, because they indicate that goals are achieved when the flow functions in the connected networks are working. There are also condition relations, which tells that a certain goal has to be achieved for the conditioned function to be available. Goals The goals in an MFM model describe the intentional goals of running a system. Examples of goals are keep the water level within an acceptable range, produce electrical power, and cool the. Without knowing the true goals of running a system, it is practically impossible to build a good MFM model of the system, since the whole purpose of the system is to fulfill the goals. Components The components represent the physical structures of a system. This can be, for example, a piece of pipe, a water tank, or an accumulator. The components are usually not shown in an MFM model. Functions The functions in MFM represent the capabilities of a system, such as transport water, supply electricity, or prevent transport of radiation. The functions may or may not be associated with a physical component in the system. A component may also be associated with several functions. An electrical, for example, may have both the function of transporting water, and the function of acting as a sink for electrical energy. The MFM functions are these: A source is a function that is capable of providing an unlimited amount of mass or energy. A sink is a function that acts as a drain of mass or energy. A transport is a function that is capable of transporting mass, energy, or information. A barrier is a function that is capable of preventing the transport of mass, energy, or information. A storage is a function that is capable of storing mass or energy. A balance is a function that connects one or more inflows to one or more outflows. An observer is a function that translates sensor values to information. A decision is a function that represents control actions by humans or automatic controllers. An actor is a function that can transform information into physical actions. A manager is a function that is used to represent management of a system, for example PID-controllers, human operators, etc. These functions are shown in Figure 2. Source Sink Transport Barrier Storage Balance Observer Decision Actor Manager Goal Figure 2. The symbols that represent MFM functions. Relations A set of connected flow functions is called a network. To the networks, goals can be connected via achieve relations. When a certain condition is met (such as all the functions in the network are working properly ), the connected goals are said to be achieved. In order for a certain function to be available, some goals may have to be achieved. This is expressed by using condition relations. These relations connect a goal with a function. There may be several conditions emanating from a goal, and several conditions may be connected to a function. In order to express management functions, there is also a relation called an achieve-by-management relation. This is used to express the fact that the flow functions need some kind of management (automatic or by an operator) to function as designed. These relations are shown in Figure 3. Network Achieve relation Condition relation Achieve-bymanagement relation Figure 3. The relations between the MFM objects.
3 An Example of an MFM Model To illustrate how MFM is used, an example is presented here. The system, which is shown in Figure 4, consists of an engine, and a cooling system. The cooling fluid is ed by an electrical, and the needs lubrication in order to work. The engine runs o n gasoline and oxygen, and if the cooling system breaks down, the engine will overheat and stop functioning. The cooling fluid in this system is water. Oxygen Gasoline Pump Engine energy of the gasoline to be available, the gasoline transport from the tank to the engine must be working. The one to the right states that the heat energy sink can not work unless the cooling system is working. M1 E1 Supply gas M2 Keep engine running Cool engine Power Lubricant M3 Lubricate E2 Supply power to Figure 4. An engine which runs on gasoline and oxygen. The engine needs a cooling system, and the circulator in the cooling system needs electrical power and lubricant. This is not an example taken from a real system, but it is adequate for demonstration purposes. In order to create an MFM model of this system, the important questions to ask are what are the goals of the system, and what functions are available in the system. Several goals can be found for this system, but in this case let us concentrate on these five: Keep engine running. This is the main goal of the system. Supply gas. Gasoline is needed for the engine to work. Cool engine. The engine needs cooling in order to work. Lubricate. The needs lubrication. Supply power to. The needs electrical power. The functions that can be found in this model are for example gasoline supply, gasoline transport, water transport, and lubricant source. An MFM model of this system is shown in Figure 5. The network marked E1 is a model of the energy balance in the engine. To the left are two sources of energy. The top source is the oxygen supply (the air), and the bottom source is the gasoline supply. In the middle of the network, there is an energy balance where the chemical energy of the gasoline and oxygen is transformed into kinetic energy and heat energy. The kinetic energy is absorbed by the top sink, and the heat energy is absorbed by the bottom sink. If all of these functions work, the top goal ( keep engine running ) is achieved. There are two conditions going up to the top network. The one to the left states that in order for the chemical Figure 5. An MFM model of the example system. The network marked M1 is a model of the physical transport of gasoline from the tank to the engine. The network marked M3 is a model of the physical transport of lubricant to the. The network marked E2 is a model of the transport of electrical power to the. The network marked M2, finally, is a model of the circulation of water in the cooling system. The leftmost transport in the network is a model of the, and the storage in the middle is a model of the heat exchanger in the engine. Both the source function and the sink function are models of the other heat exchanger element. This could of course be expressed by modeling the source and the sink in this network as a single storage, and creating a circular flow in the network instead of a straight one, but in this model the straight flow was chosen. IV. ALGORITHMS FOR MFM Several algorithms and methods have been developed for use with MFM models. Three of these, measurement validation, fault diagnosis, and alarm analysis, by Larsson [3, 5], have been implemented in the MFM Toolbox, a program for Windows 95 and NT. The MFM Toolbox is a tool for creating, editing and testing MFM models, and is a good base for adding new algorithms. The measurement validation algorithm uses measured flow values together with the MFM model to check that the flow values are consistent with the model. The fault diagnosis algorithm is similar to a backward chaining expert system, but the inherent structure of an MFM model guarantee that the diagnosis will be completed in linear (or sub-linear) time. This is advantageous for real time systems, see [4]. The algorithms have successfully been used in several projects, see [6, 7].
4 The alarm analysis algorithm will be described in detail, because the FMA algorithm relies on certain aspects of this algorithm. Alarm Analysis Using MFM Most industrial processes are equipped with a large number of sensors. The sensors are all connected to some form of alarm, so that the operators can know when something goes wrong. However, in case of a major fault, many of the alarms may trigger at the same time. This may overload the operators with alarms, and the real cause of the fault may be drowned among all the secondary faults. This is a potentially dangerous situation, and the alarm analysis algorithm for MFM is designed to separate the primary faults from the secondary faults in order to reduce the number of alarms presented to the operator. The algorithm works by associating discrete alarm states, such as low flow and high volume, with each flow function in the MFM model. Due to the semantic interpretations of the MFM flow functions, it is possible to conclude that certain faults may cause consequential faults in connected flow functions. The method uses a set of causation rules to check each pair of flow functions, to separate the faults that must be primary from the faults that may be consequences of the primary faults. However, the method does not guarantee that the faults marked as secondary are not in fact primary faults. There can be hidden primary faults that look as if they were caused by another primary fault, and which are therefore classified as secondary. Therefore, the algorithm only sorts the faults into the classes primary and secondary or hidden primary. An example of how the algorithm works is given below. Figure 6 describes a closed tank connected to a. Figure 6. A closed tank, with an inflow and an outflow. The outflow of the tank is connected to a. In this simple system, it is reasonable to assume that a too low volume in the tank may cause a too low flow through the. In addition, a too low flow through the may cause a too high volume in the tank. There is also the possibility that a too high volume in the tank may cause a too high flow through the, and that a too high flow through the may cause a too low volume in the tank. These four causation rules describe how one fault may cause another. Now, assume that the tank becomes empty, and therefore a level alarm is activated. Because of the low level in the tank, the flow will become too low, and activate another alarm. By using the first rule above, it is possible to conclude that the low volume in the tank is the cause for both alarms, the primary fault, whereas the low flow through the is a consequential, or secondary fault. The alarm analysis algorithm uses a set of rules like these for every legal MFM connection to find out which alarms are primary and which are secondary. In the MFM representation, the situation described here would be modeled like in Figure 7. Tank Pump Figure 7. A model of the tank- system. The MFM functions have, as described above, associated alarm states. The storage function can be in one of three alarm states, namely normal, high volume (hivol), or low volume (lovol). The transport function can be in the states normal, high flow (hiflow), or low flow (loflow). The states are set by rules of the following form: if the flow through the transport is less than a threshold value f lo, set the alarm state of the transport to loflow. The threshold value can be statically set in advance, or updated dynamically for example when the state of the process changes. The causation rules for the tank- system can now be written using only MFM functions and their associated alarm states: 1. A storage lovol may cause a downstream transport to have a loflow. 2. A transport loflow may cause an upstream storage to have a hivol. 3. A storage hivol may cause a downstream transport to have a hiflow. 4. A transport hiflow may cause an upstream storage to have a lovol. Similar rules have been derived for all legal MFM connections, and they are described in detail in [3, 5]. Since there are only a limited number of legal MFM connections and a discrete number of states, it is possible to store the causation rules in a table. The alarm analysis algorithm looks at each pair of MFM functions, and if both functions are in an alarmed state, the table is used to conclude which function has a primary alarm, and which has a secondary (consequential) alarm. If only one of the two functions is alarmed, the alarmed function is primary. A special case occurs when a function does not have a connected sensor (the function is said to be unmeasured). Since it is then impossible to know the real state of the function, the alarm analysis algorithm uses the state of the connected functions to guess the state of the unmeasured function. This is done using the same table as described above, and the method is called consequence propagation. For example, in the situation described above, if the flow through the is not measured and the volume in the tank is low, the consequence propagation rules will guess that the flow through the is low. It should be noted that because of the inherent structure of the MFM models, it is always sufficient to only look at
5 two connected functions at a time. This is important, since it allows the complexity of the algorithm to be kept linear, or even sub-linear, with regard to the size of the model. V. FAILURE MODE ANALYSIS USING MFM The failure mode analysis I have developed for MFM is based on the consequence propagation used in the alarm analysis algorithm by Larsson [3], expanded with timing information associated with condition relations and storages. An important fact here is that the consequence propagation in the alarm analysis algorithm will stop as soon as a function with a sensor reading which is in the normal range is found. In the FMA algorithm, the consequence propagation will not stop until the whole model has been searched, because of the assumption that the functions that seem to be working now may stop working in the future. The motives for associating the timing information with only storages and condition relations were: Failures will take time to propagate between MFM networks. Storages often have an intrinsic capability to delay the propagation of failures within a network. Adding time delay information to all functions and relations would be unfeasible in terms of modeling effort. The points above may be debatable, since there are most often propagation delays in other functions as well. However, these objects were carefully chosen because the method will give good results without any serious drawbacks with this setup. The timing information needed for an analysis must be either derived from simulated cases, derived from stored real process data, or estimated by hand. Often, the last option is the only one available, but the method may result in useful data even if the exact timings are slightly wrong. The same problems arise for all FMA methods that are based on timings, so this is not in any way unique for the MFM version. The method described here has been implemented in a version of the MFM Toolbox, see section IV. Assignment of Timing Information When the MFM model is built in the MFM Toolbox, it is possible to assign timing information to each storage and to each condition relation. In the current version of the algorithm, all conditions emanating from the same goal will have the same delay. This is currently under evaluation, and may be changed in the future so that each condition has its own timing delay. The timings are printed next to the function, as shown in Figure 8. Here, the following is assumed: If the gasoline support fails, the engine will stop directly. If the engine cooling fails, the engine will run for twenty minutes. If the lubrication of the stops, the will fail after ten minutes. If the power to the fails, the will fail immediately. If the fails, the stored water in the engines heat exchanger will last for five minutes. These timings are not taken from any real situation, but they are adequate for this example. M1 E1 0 Keep engine running 0 20 Supply gas Cool engine M3 M Lubricate 5 E2 Supply power to Figure 8. An MFM model of the engine with timing information visible. An FMA Run After the timing information is entered into the model, it is possible to run test cases. This is done in the following way: first, the user inputs the start state (the state of the system at time zero), by asserting failures in one or more functions. Then, the analysis is started by a user command, and the result is presented on the screen. An example of this is shown in Figure 9. Here, the initial failure is that the lubricant has run out. The result of this is that the will fail due to lack of lubricant, and after a while the engine will fail due to lack of cooling. After the complete FMA run has been performed, the program will collect these failures and generate a list of all functions with alarmed sensors, sorted in order of time -to-failure. This is exemplified in Figure 10. The Algorithm in Pseudocode The algorithm works by assigning new state informa tion to each function in the MFM model. The new information consists of a time stamp, called failure time, which holds information on when the function will fail. There is also a variable called current failure time, which is used during the traversal of the model. It is used to keep track of the current time in the system. In pseudocode, the algorithm for failure mode analysis looks like this:
6 For each function with an alarmed sensor: Set the failure time of the function to 0. Propagate the alarms as far as possible according to the rules in the alarm analysis algorithm. Set the failure time of the currently examined function to the current failure time, if the function has not been reached before or if the failure time stored for the function is larger than the current failure time. Update the current failure time when passing conditions and storages. Stop the propagation if the failure time of the currently examined function is less than the current failure time. M1 Keep engine running E1 Supply gas M2 0 Lubricate M Cool engine E2 Supply power to Figure 9. Example of an FMA run. This is a situation where the lubricant runs out, and the impacts of this on the system. Results of Failure Mode Analysis ================================ T = 0 F8: "Lubricant source" F9: "Lubricant transport" T = 10 F1: "Water " F2: "Engine heat exchanger" T = F11: "Gasoline supply" F17: "Kinetic energy sink" F19: "Heat energy sink" Figure 10. The textual output from the FMA run. The measured MFM functions that failed are sorted in time order. The list of functions at time T = 0 are the initially failed functions. Here, the algorithm has predicted that, for example, the water will fail within ten minutes. for the affected parts of the system. The method has certain advantages compared to traditional methods, for example the possibility to build a system for on-line real time failure prediction with this method. The algorithm has been implemented and tested in the MFM Toolbox, a program for editing and testing MFM models. VII. ACKNOWLEDGMENTS The author wishes to thank Jan Eric Larsson and Fredrik Dahlstrand at the Department of Information Technology for helpful advice during the development of this algorithm. Thanks also go to Gordon Broderick, Noranda Corporation, for the inspiration that led to the algorithm. VIII. REFERENCES [1] D. J. Allen, M. S. M. Rao, New Algorithms for the Synthesis and Analysis of Fault Trees, Industrial and Engineering Chemistry: Fundamentals, vol. 19, no. 1, pp , [2] A. Jalashgar, Identification of Hidden Failures in Process Control Systems through Function-Oriented System Analysis, Doctor s thesis, Risø R 936(EN), Risø National Laboratory, Roskilde, Denmark, [3] J. E. Larsson, Knowledge-Based Methods for Control Systems, Doctor s thesis, TFRT 1040, Department of Automatic Control, Lund Instit ute of Technology, Lund, [4] J. E. Larsson, Hyperfast Algorithms for Model-Based Diagnosis, Proceedings of the IEEE/IFAC Joint Symposium on Computer-Aided Control Systems Design, Tucson, Arizona, [5] J. E. Larsson, Diagnosis Based on Explicit Means-End Models, Artificial Intelligence, vol. 80, no. 1, pp , [6] J. E. Larsson, B. Hayes-Roth, D. M. Gaba, Goals and Functions of the Human Body: An MFM Model for Fault Diagnosis, IEEE Transactions on Systems, Man, and Cybernetics, vol. 27, no. 6, pp , [7] J. E. Larsson, B. Hayes-Roth, D. M. Gaba, B. E. Smith, Evaluation of a medical diagnosis system using simulator test scenarios, Artificial Intelligence in Medicine, vol. 11, pp , [8] M. Lind, Representing Goals and Functions of Complex Systems An Introduction to Multilevel Flow Modeling, Technical report, 90 D 38, Institute of Automatic Control Systems, Technical University of Denmark, Lyngby, [9] M. Modarres, Functional Modeling of Complex Systems Using a GTST-MPLD Framework, Proceedings of the International Workshop on Functional Modeling of Complex Technical Systems, Ispra, Italy, [10] C. J. Price, D. R. Pugh, N. Snooke, J. E. Hunt, M. S. Wilson, Combining Functional and Structural Reasoning for Safety Analysis of Electrical Designs, Knowledge Engineering Review, vol. 12, no. 3, pp , VI. CONCLUSIONS A new method for failure mode analysis based on MFM has been developed. The method takes a given situation as input, and outputs a list of predicted time -to-failure values
Diagnostic Reasoning Strategies for Means-End Models
 Diagnostic Reasoning Strategies for Means-End Models Jan Eric Larsson Department of Automatic Control Lund University Box 118, 22100 Lund, Sweden E-mail: janeric@it.lth.se This is a preprint of an article
Diagnostic Reasoning Strategies for Means-End Models Jan Eric Larsson Department of Automatic Control Lund University Box 118, 22100 Lund, Sweden E-mail: janeric@it.lth.se This is a preprint of an article
CONTROL SYSTEMS, ROBOTICS AND AUTOMATION Vol. XVI - Control Reconfiguration - Jan Lunze
 CONTROL RECONFIGURATION Jan Lunze The Institute of Automation and Computer Control, Ruhr University Bochum, Germany Keywords: Model-matching, Reconfigurability, Reconfiguration, Recoverability. Contents
CONTROL RECONFIGURATION Jan Lunze The Institute of Automation and Computer Control, Ruhr University Bochum, Germany Keywords: Model-matching, Reconfigurability, Reconfiguration, Recoverability. Contents
Virtual Plant control based on ABB 800xa Conceptualization to Simulator
 Virtual Plant control based on ABB 800xa Conceptualization to Simulator Yousef Iskandarani, Karina Nohammer and Hamid Reza Karimi Department of Engineering University of Agder Jon Lilletuns vei 9, 4879
Virtual Plant control based on ABB 800xa Conceptualization to Simulator Yousef Iskandarani, Karina Nohammer and Hamid Reza Karimi Department of Engineering University of Agder Jon Lilletuns vei 9, 4879
Chapter 2 Overview of the Design Methodology
 Chapter 2 Overview of the Design Methodology This chapter presents an overview of the design methodology which is developed in this thesis, by identifying global abstraction levels at which a distributed
Chapter 2 Overview of the Design Methodology This chapter presents an overview of the design methodology which is developed in this thesis, by identifying global abstraction levels at which a distributed
Annual Training plan 2018
 Annual Training plan 2018 Leadership,, HR, Creativity, Secretary Courses Sr. No. Course Name Date Venue Fees U.S $ January 1. Time & Stress 7-11/1/2018 Abu Dhabi 2600 2. Legal Writing Skills 7-11/1/2018
Annual Training plan 2018 Leadership,, HR, Creativity, Secretary Courses Sr. No. Course Name Date Venue Fees U.S $ January 1. Time & Stress 7-11/1/2018 Abu Dhabi 2600 2. Legal Writing Skills 7-11/1/2018
6.001 Notes: Section 8.1
 6.001 Notes: Section 8.1 Slide 8.1.1 In this lecture we are going to introduce a new data type, specifically to deal with symbols. This may sound a bit odd, but if you step back, you may realize that everything
6.001 Notes: Section 8.1 Slide 8.1.1 In this lecture we are going to introduce a new data type, specifically to deal with symbols. This may sound a bit odd, but if you step back, you may realize that everything
1 Lab + Hwk 5: Particle Swarm Optimization
 1 Lab + Hwk 5: Particle Swarm Optimization This laboratory requires the following equipment: C programming tools (gcc, make), already installed in GR B001 Webots simulation software Webots User Guide Webots
1 Lab + Hwk 5: Particle Swarm Optimization This laboratory requires the following equipment: C programming tools (gcc, make), already installed in GR B001 Webots simulation software Webots User Guide Webots
1 Lab 5: Particle Swarm Optimization
 1 Lab 5: Particle Swarm Optimization This laboratory requires the following: (The development tools are installed in GR B0 01 already): C development tools (gcc, make, etc.) Webots simulation software
1 Lab 5: Particle Swarm Optimization This laboratory requires the following: (The development tools are installed in GR B0 01 already): C development tools (gcc, make, etc.) Webots simulation software
LOGICAL OPERATOR USAGE IN STRUCTURAL MODELLING
 LOGICAL OPERATOR USAGE IN STRUCTURAL MODELLING Ieva Zeltmate (a) (a) Riga Technical University, Faculty of Computer Science and Information Technology Department of System Theory and Design ieva.zeltmate@gmail.com
LOGICAL OPERATOR USAGE IN STRUCTURAL MODELLING Ieva Zeltmate (a) (a) Riga Technical University, Faculty of Computer Science and Information Technology Department of System Theory and Design ieva.zeltmate@gmail.com
Regulatory Aspects of Digital Healthcare Solutions
 Regulatory Aspects of Digital Healthcare Solutions TÜV SÜD Product Service GmbH Dr. Markus Siebert Rev. 02 / 2017 02.05.2017 TÜV SÜD Product Service GmbH Slide 1 Contents Digital solutions as Medical Device
Regulatory Aspects of Digital Healthcare Solutions TÜV SÜD Product Service GmbH Dr. Markus Siebert Rev. 02 / 2017 02.05.2017 TÜV SÜD Product Service GmbH Slide 1 Contents Digital solutions as Medical Device
Diagnosis of a Continuous Dynamic System from Distributed Measurements
 Presented at the IEEE International Measurement Technology Conference, Baltimore, Maryland, May 1 4, 2000 Diagnosis of a Continuous Dynamic System from Distributed Measurements Eric-J. Manders 1 and Lee
Presented at the IEEE International Measurement Technology Conference, Baltimore, Maryland, May 1 4, 2000 Diagnosis of a Continuous Dynamic System from Distributed Measurements Eric-J. Manders 1 and Lee
1 Lab + Hwk 5: Particle Swarm Optimization
 1 Lab + Hwk 5: Particle Swarm Optimization This laboratory requires the following equipment: C programming tools (gcc, make). Webots simulation software. Webots User Guide Webots Reference Manual. The
1 Lab + Hwk 5: Particle Swarm Optimization This laboratory requires the following equipment: C programming tools (gcc, make). Webots simulation software. Webots User Guide Webots Reference Manual. The
Black-box Testing Techniques
 T-76.5613 Software Testing and Quality Assurance Lecture 4, 20.9.2006 Black-box Testing Techniques SoberIT Black-box test case design techniques Basic techniques Equivalence partitioning Boundary value
T-76.5613 Software Testing and Quality Assurance Lecture 4, 20.9.2006 Black-box Testing Techniques SoberIT Black-box test case design techniques Basic techniques Equivalence partitioning Boundary value
ON-LINE QUALITATIVE MODEL-BASED DIAGNOSIS OF TECHNOLOGICAL SYSTEMS USING COLORED PETRI NETS
 ON-LINE QUALITATIVE MODEL-BASED DIAGNOSIS OF TECHNOLOGICAL SYSTEMS USING COLORED PETRI NETS Adrien Leitold 1 Miklós Gerzson 2 Anna I. Pózna 2 and Katalin M. Hangos 2,3 1 Department of Mathematics 3 Process
ON-LINE QUALITATIVE MODEL-BASED DIAGNOSIS OF TECHNOLOGICAL SYSTEMS USING COLORED PETRI NETS Adrien Leitold 1 Miklós Gerzson 2 Anna I. Pózna 2 and Katalin M. Hangos 2,3 1 Department of Mathematics 3 Process
Micropolis Interdependency Modeling using Open Hybrid Automata
 Micropolis Interdependency Modeling using Open Hybrid Automata Constantinos Heracleous KIOS Research Center for Intelligent Systems and Networks, Department of Electrical and Computer Engineering, University
Micropolis Interdependency Modeling using Open Hybrid Automata Constantinos Heracleous KIOS Research Center for Intelligent Systems and Networks, Department of Electrical and Computer Engineering, University
IN a mobile ad hoc network, nodes move arbitrarily.
 IEEE TRANSACTIONS ON MOBILE COMPUTING, VOL. 5, NO. 6, JUNE 2006 609 Distributed Cache Updating for the Dynamic Source Routing Protocol Xin Yu Abstract On-demand routing protocols use route caches to make
IEEE TRANSACTIONS ON MOBILE COMPUTING, VOL. 5, NO. 6, JUNE 2006 609 Distributed Cache Updating for the Dynamic Source Routing Protocol Xin Yu Abstract On-demand routing protocols use route caches to make
Automatic Merging of Specification Documents in a Parallel Development Environment
 Automatic Merging of Specification Documents in a Parallel Development Environment Rickard Böttcher Linus Karnland Department of Computer Science Lund University, Faculty of Engineering December 16, 2008
Automatic Merging of Specification Documents in a Parallel Development Environment Rickard Böttcher Linus Karnland Department of Computer Science Lund University, Faculty of Engineering December 16, 2008
USING STRUCTURAL AND FUNCTIONAL INFORMATION IN DIAGNOSTIC DESIGN
 From: AAAI-83 Proceedings. Copyright 1983, AAAI (www.aaai.org). All rights reserved. USING STRUCTURAL AND FUNCTIONAL INFORMATION IN DIAGNOSTIC DESIGN Walter Hamscher The Artificial Intelligence Laboratory
From: AAAI-83 Proceedings. Copyright 1983, AAAI (www.aaai.org). All rights reserved. USING STRUCTURAL AND FUNCTIONAL INFORMATION IN DIAGNOSTIC DESIGN Walter Hamscher The Artificial Intelligence Laboratory
LATTICE-BOLTZMANN METHOD FOR THE SIMULATION OF LAMINAR MIXERS
 14 th European Conference on Mixing Warszawa, 10-13 September 2012 LATTICE-BOLTZMANN METHOD FOR THE SIMULATION OF LAMINAR MIXERS Felix Muggli a, Laurent Chatagny a, Jonas Lätt b a Sulzer Markets & Technology
14 th European Conference on Mixing Warszawa, 10-13 September 2012 LATTICE-BOLTZMANN METHOD FOR THE SIMULATION OF LAMINAR MIXERS Felix Muggli a, Laurent Chatagny a, Jonas Lätt b a Sulzer Markets & Technology
International Journal of Advance Engineering and Research Development. Flow Control Loop Analysis for System Modeling & Identification
 Scientific Journal of Impact Factor(SJIF): 3.134 e-issn(o): 2348-4470 p-issn(p): 2348-6406 International Journal of Advance Engineering and Research Development Volume 2,Issue 5, May -2015 Flow Control
Scientific Journal of Impact Factor(SJIF): 3.134 e-issn(o): 2348-4470 p-issn(p): 2348-6406 International Journal of Advance Engineering and Research Development Volume 2,Issue 5, May -2015 Flow Control
Eliminating Annotations by Automatic Flow Analysis of Real-Time Programs
 Eliminating Annotations by Automatic Flow Analysis of Real-Time Programs Jan Gustafsson Department of Computer Engineering, Mälardalen University Box 883, S-721 23 Västerås, Sweden jangustafsson@mdhse
Eliminating Annotations by Automatic Flow Analysis of Real-Time Programs Jan Gustafsson Department of Computer Engineering, Mälardalen University Box 883, S-721 23 Västerås, Sweden jangustafsson@mdhse
Tech Byte 20: The Benefits of Power Switching in Dual Bus UPS Designs
 Introduction Dual bus uninterruptible power supply architectures have long been recognized as the preferred redundancy design for supporting mission critical applications. However, a dual bus design represents
Introduction Dual bus uninterruptible power supply architectures have long been recognized as the preferred redundancy design for supporting mission critical applications. However, a dual bus design represents
KRAL Electronics BEM 300 and BEM 500.
 KRAL Electronics BEM 300 and BEM 500. KRAL Electronics BEM 300 and BEM 500 Electronic units that are coordinated to KRAL flowmeters and their diverse applications. Coordinated to the flowmeters and their
KRAL Electronics BEM 300 and BEM 500. KRAL Electronics BEM 300 and BEM 500 Electronic units that are coordinated to KRAL flowmeters and their diverse applications. Coordinated to the flowmeters and their
Exception Handling in S88 using Grafchart *
 Presented at the World Batch Forum North American Conference Woodcliff Lake, NJ April 7-10, 2002 107 S. Southgate Drive Chandler, Arizona 85226-3222 480-893-8803 Fax 480-893-7775 E-mail: info@wbf.org www.wbf.org
Presented at the World Batch Forum North American Conference Woodcliff Lake, NJ April 7-10, 2002 107 S. Southgate Drive Chandler, Arizona 85226-3222 480-893-8803 Fax 480-893-7775 E-mail: info@wbf.org www.wbf.org
(Timings: 2.00 pm pm)
 NOTICE / SCHOOL OF TECHNOLOGY MANAGEMENT & ENGINEERING MASTER OF BUSINESS ADMINISTRATION IN TECHNOLOGY MANAGEMENT (2017-22) YEAR: I, SEMESTER: I, SHIRPUR, INDORE & NAVI MUMBAI (Timings: 2.00 pm - 5.00
NOTICE / SCHOOL OF TECHNOLOGY MANAGEMENT & ENGINEERING MASTER OF BUSINESS ADMINISTRATION IN TECHNOLOGY MANAGEMENT (2017-22) YEAR: I, SEMESTER: I, SHIRPUR, INDORE & NAVI MUMBAI (Timings: 2.00 pm - 5.00
Experimental Study for Detection of Leaks in. Horizontal Pipelines
 Contemporary Engineering Sciences, Vol. 11, 2018, no. 101, 5017-5025 HIKARI Ltd, www.m-hikari.com https://doi.org/10.12988/ces.2018.810551 Experimental Study for Detection of Leaks in Horizontal Pipelines
Contemporary Engineering Sciences, Vol. 11, 2018, no. 101, 5017-5025 HIKARI Ltd, www.m-hikari.com https://doi.org/10.12988/ces.2018.810551 Experimental Study for Detection of Leaks in Horizontal Pipelines
Lecture 1 GENERAL INTRODUCTION: HISTORICAL BACKGROUND AND SPECTRUM OF APPLICATIONS
 Lecture 1 GENERAL INTRODUCTION: HISTORICAL BACKGROUND AND SPECTRUM OF APPLICATIONS 1.1 INTRODUCTION Analysis of physical problems in any area of engineering and science involves a multipronged approach:
Lecture 1 GENERAL INTRODUCTION: HISTORICAL BACKGROUND AND SPECTRUM OF APPLICATIONS 1.1 INTRODUCTION Analysis of physical problems in any area of engineering and science involves a multipronged approach:
Anomaly Detection Solutions for Improved Equipment Availability
 Detection Solutions for Improved Equipment Availability Big Data is the enabler for Hitachi s Detection Technology Advances in ICT have made it easy to collect and store massive amounts of operational
Detection Solutions for Improved Equipment Availability Big Data is the enabler for Hitachi s Detection Technology Advances in ICT have made it easy to collect and store massive amounts of operational
USBCAN-OBD. USB to CAN adapter. User Manual. Document version 3.01 (2015/04/22)
 USB to CAN adapter User Manual Document version 3.01 (2015/04/22) Contents 1. Introduction... 3 1.1 Functional Overview... 3 1.2 Properties at a Glance...3 1.3 Typical application... 3 2. Installation...
USB to CAN adapter User Manual Document version 3.01 (2015/04/22) Contents 1. Introduction... 3 1.1 Functional Overview... 3 1.2 Properties at a Glance...3 1.3 Typical application... 3 2. Installation...
EXPERIENCES FROM MODEL BASED DEVELOPMENT OF DRIVE-BY-WIRE CONTROL SYSTEMS
 EXPERIENCES FROM MODEL BASED DEVELOPMENT OF DRIVE-BY-WIRE CONTROL SYSTEMS Per Johannessen 1, Fredrik Törner 1 and Jan Torin 2 1 Volvo Car Corporation, Department 94221, ELIN, SE-405 31 Göteborg, SWEDEN;
EXPERIENCES FROM MODEL BASED DEVELOPMENT OF DRIVE-BY-WIRE CONTROL SYSTEMS Per Johannessen 1, Fredrik Törner 1 and Jan Torin 2 1 Volvo Car Corporation, Department 94221, ELIN, SE-405 31 Göteborg, SWEDEN;
SOFTWARE TOOL FOR AUTOMATED FAILURE MODES AND EFFECTS ANALYSIS (FMEA) OF HYDRAULIC SYSTEMS
 SOFTWARE TOOL FOR AUTOMATED FAILURE MODES AND EFFECTS ANALYSIS (FMEA) OF HYDRAULIC SYSTEMS Jacek S. Stecki*, Finn Conrad** and Beng Oh*** *Depratjnent of Mechanical Engineering, Monash University Wellington
SOFTWARE TOOL FOR AUTOMATED FAILURE MODES AND EFFECTS ANALYSIS (FMEA) OF HYDRAULIC SYSTEMS Jacek S. Stecki*, Finn Conrad** and Beng Oh*** *Depratjnent of Mechanical Engineering, Monash University Wellington
03 October Day Date Subjects. Wednesday 14 November 2018 Mathematics-I. Friday 16 November 2018 Programming for Problem Solving
 NOTICE / SCHOOL OF TECHNOLOGY MANAGEMENT & ENGINEERING MASTER OF BUSINESS ADMINISTRATION IN TECHNOLOGY MANAGEMENT (2018-23) YEAR: I, SEMESTER: I, SHIRPUR, INDORE & NAVI MUMBAI (Timings: 10.00 am - 1.00
NOTICE / SCHOOL OF TECHNOLOGY MANAGEMENT & ENGINEERING MASTER OF BUSINESS ADMINISTRATION IN TECHNOLOGY MANAGEMENT (2018-23) YEAR: I, SEMESTER: I, SHIRPUR, INDORE & NAVI MUMBAI (Timings: 10.00 am - 1.00
Analyzing and Segmenting Finger Gestures in Meaningful Phases
 2014 11th International Conference on Computer Graphics, Imaging and Visualization Analyzing and Segmenting Finger Gestures in Meaningful Phases Christos Mousas Paul Newbury Dept. of Informatics University
2014 11th International Conference on Computer Graphics, Imaging and Visualization Analyzing and Segmenting Finger Gestures in Meaningful Phases Christos Mousas Paul Newbury Dept. of Informatics University
A Limitation of BAN Logic Analysis on a Man-in-the-middle Attack
 ISS 1746-7659, England, U Journal of Information and Computing Science Vol. 1, o. 3, 2006, pp. 131-138 Limitation of Logic nalysis on a Man-in-the-middle ttack + Shiping Yang, Xiang Li Computer Software
ISS 1746-7659, England, U Journal of Information and Computing Science Vol. 1, o. 3, 2006, pp. 131-138 Limitation of Logic nalysis on a Man-in-the-middle ttack + Shiping Yang, Xiang Li Computer Software
Playback Testing Using Log files
 Playback Testing Using Log files Author Vijay Upadya, vijayu@microsoft.com Abstract Most testers are familiar with record/playback testing. A variation of this approach is log playback testing. Instead
Playback Testing Using Log files Author Vijay Upadya, vijayu@microsoft.com Abstract Most testers are familiar with record/playback testing. A variation of this approach is log playback testing. Instead
SOME TYPES AND USES OF DATA MODELS
 3 SOME TYPES AND USES OF DATA MODELS CHAPTER OUTLINE 3.1 Different Types of Data Models 23 3.1.1 Physical Data Model 24 3.1.2 Logical Data Model 24 3.1.3 Conceptual Data Model 25 3.1.4 Canonical Data Model
3 SOME TYPES AND USES OF DATA MODELS CHAPTER OUTLINE 3.1 Different Types of Data Models 23 3.1.1 Physical Data Model 24 3.1.2 Logical Data Model 24 3.1.3 Conceptual Data Model 25 3.1.4 Canonical Data Model
Self-Cultivation System
 Development of a Microorganism Incubator using CFD Simulations Self-Cultivation System A comfortable mixing incubator to grow microorganism for agricultural, animal husbandry and ocean agriculture industries
Development of a Microorganism Incubator using CFD Simulations Self-Cultivation System A comfortable mixing incubator to grow microorganism for agricultural, animal husbandry and ocean agriculture industries
CFD MODELING FOR PNEUMATIC CONVEYING
 CFD MODELING FOR PNEUMATIC CONVEYING Arvind Kumar 1, D.R. Kaushal 2, Navneet Kumar 3 1 Associate Professor YMCAUST, Faridabad 2 Associate Professor, IIT, Delhi 3 Research Scholar IIT, Delhi e-mail: arvindeem@yahoo.co.in
CFD MODELING FOR PNEUMATIC CONVEYING Arvind Kumar 1, D.R. Kaushal 2, Navneet Kumar 3 1 Associate Professor YMCAUST, Faridabad 2 Associate Professor, IIT, Delhi 3 Research Scholar IIT, Delhi e-mail: arvindeem@yahoo.co.in
-----other notes This picture was taken from here:
 This is an introduction to programmable logic controllers - PLCs for short. Here is a picture of a simple one. A programmable logic controller is unit of hardware used to control and automate an industrial
This is an introduction to programmable logic controllers - PLCs for short. Here is a picture of a simple one. A programmable logic controller is unit of hardware used to control and automate an industrial
Cause & Effect Charts
 Cause & Effect Charts for protection systems compliant with IEC 61508 SIL-3 Dr. Wolfgang Brendel 1 History of Cause & Effect Matrix Cause &Effect Established specification method Recommended NORSOK standard
Cause & Effect Charts for protection systems compliant with IEC 61508 SIL-3 Dr. Wolfgang Brendel 1 History of Cause & Effect Matrix Cause &Effect Established specification method Recommended NORSOK standard
Concept as a Generalization of Class and Principles of the Concept-Oriented Programming
 Computer Science Journal of Moldova, vol.13, no.3(39), 2005 Concept as a Generalization of Class and Principles of the Concept-Oriented Programming Alexandr Savinov Abstract In the paper we describe a
Computer Science Journal of Moldova, vol.13, no.3(39), 2005 Concept as a Generalization of Class and Principles of the Concept-Oriented Programming Alexandr Savinov Abstract In the paper we describe a
Monitoring Interfaces for Faults
 Monitoring Interfaces for Faults Aleksandr Zaks RV 05 - Fifth Workshop on Runtime Verification Joint work with: Amir Pnueli, Lenore Zuck Motivation Motivation Consider two components interacting with each
Monitoring Interfaces for Faults Aleksandr Zaks RV 05 - Fifth Workshop on Runtime Verification Joint work with: Amir Pnueli, Lenore Zuck Motivation Motivation Consider two components interacting with each
ZR12-AL USER GUIDE ZR12-AL VERSION 1.5
 USER GUIDE VERSION 1.5 ZR12-AL MANUFACTURED BY BELVOIR WAY, FAIRFIELD INDUSTRIAL ESTATE, LOUTH, LINCOLNSHIRE, LN11 0LQ UK TEL:+44(0)1507 604399 FAX:+44(0)1507 601956 ZR12-AL Fluids Suitable For This Machine:
USER GUIDE VERSION 1.5 ZR12-AL MANUFACTURED BY BELVOIR WAY, FAIRFIELD INDUSTRIAL ESTATE, LOUTH, LINCOLNSHIRE, LN11 0LQ UK TEL:+44(0)1507 604399 FAX:+44(0)1507 601956 ZR12-AL Fluids Suitable For This Machine:
Personal Trusted Device in Personal Communications
 Personal Trusted Device in Personal Communications Jari Porras, Pekka Jäppinen, Petri Hiirsalmi, Arto Hämäläinen, Sami Saalasti, Raine Koponen and Satu Keski-Jaskari Laboratory of Communications Engineering
Personal Trusted Device in Personal Communications Jari Porras, Pekka Jäppinen, Petri Hiirsalmi, Arto Hämäläinen, Sami Saalasti, Raine Koponen and Satu Keski-Jaskari Laboratory of Communications Engineering
Operating Instructions EB 8388 EN. Series 373x Positioners. EXPERT + Valve Diagnostics
 Series 373x Positioners EXPERT + Valve Diagnostics Fig. 1 Valve diagnostics with SAMSON TROVIS-VIEW Operator Interface, e.g. for Type 3730-3 Positioner Operating Instructions EB 8388 EN Firmware version
Series 373x Positioners EXPERT + Valve Diagnostics Fig. 1 Valve diagnostics with SAMSON TROVIS-VIEW Operator Interface, e.g. for Type 3730-3 Positioner Operating Instructions EB 8388 EN Firmware version
CHHATTISGARH SWAMI VIVEKANAND TECHNICAL UNIVERSITY
 CHHATTISGARH SWAMI VIVEKANAND TECHNICAL UNIVERSITY Courses of Study and Scheme of Examination of B.E. First Year (2012-13) Common to all branches of Engineering except Bio-Tech. & Bio-Medical. FIRST SEMESTER
CHHATTISGARH SWAMI VIVEKANAND TECHNICAL UNIVERSITY Courses of Study and Scheme of Examination of B.E. First Year (2012-13) Common to all branches of Engineering except Bio-Tech. & Bio-Medical. FIRST SEMESTER
CeweCetrics Start up manual
 CeweCetrics Start up manual Contents Introduction...3 What is Cetrics?... 3 An outline... 3 Definitions... 4 Typical fields of application... 6 Documentation... 7 Product support... 7 Installation...8
CeweCetrics Start up manual Contents Introduction...3 What is Cetrics?... 3 An outline... 3 Definitions... 4 Typical fields of application... 6 Documentation... 7 Product support... 7 Installation...8
Practical Tips for using Backpropagation
 Practical Tips for using Backpropagation Keith L. Downing August 31, 2017 1 Introduction In practice, backpropagation is as much an art as a science. The user typically needs to try many combinations of
Practical Tips for using Backpropagation Keith L. Downing August 31, 2017 1 Introduction In practice, backpropagation is as much an art as a science. The user typically needs to try many combinations of
CASE BASED REASONING A SHORT OVERVIEW
 CASE BASED REASONING A SHORT OVERVIEW Z. Budimac, V. Kurbalija Institute of Mathematics and Computer Science, Fac. of Science, Univ. of Novi Sad Trg D. Obradovića 4, 21000 Novi Sad, Yugoslavia zjb@im.ns.ac.yu,
CASE BASED REASONING A SHORT OVERVIEW Z. Budimac, V. Kurbalija Institute of Mathematics and Computer Science, Fac. of Science, Univ. of Novi Sad Trg D. Obradovića 4, 21000 Novi Sad, Yugoslavia zjb@im.ns.ac.yu,
Honours Project Proposal. Luke Ross Supervisor: Dr. Karen Bradshaw Department of Computer Science, Rhodes University
 Honours Project Proposal Luke Ross Supervisor: Dr. Karen Bradshaw Department of Computer Science, Rhodes University 2 March 2012 1. Principal Investigator Investigator - Luke Allan Ross Supervisor - Dr.
Honours Project Proposal Luke Ross Supervisor: Dr. Karen Bradshaw Department of Computer Science, Rhodes University 2 March 2012 1. Principal Investigator Investigator - Luke Allan Ross Supervisor - Dr.
Telecom Italia response. to the BEREC public consultation on
 Telecom Italia response to the BEREC public consultation on Guidelines on Net Neutrality and Transparency: Best practise and recommended approaches - BOR (11) 44 (2 November 2011) Telecom Italia response
Telecom Italia response to the BEREC public consultation on Guidelines on Net Neutrality and Transparency: Best practise and recommended approaches - BOR (11) 44 (2 November 2011) Telecom Italia response
Online Dial-A-Ride Problem with Time Windows: an exact algorithm using status vectors
 Online Dial-A-Ride Problem with Time Windows: an exact algorithm using status vectors A. Fabri 1 and P. Recht 2 1 Universität Dortmund a.fabri@wiso.uni-dortmund.de 2 Universität Dortmund p.recht@wiso.uni-dortmund.de
Online Dial-A-Ride Problem with Time Windows: an exact algorithm using status vectors A. Fabri 1 and P. Recht 2 1 Universität Dortmund a.fabri@wiso.uni-dortmund.de 2 Universität Dortmund p.recht@wiso.uni-dortmund.de
SIMATIC. Process Control PCS 7 V7.0 PCS 7 OS Process Control. Preface, Contents. Additional Documentation 1 Functions of the PCS 7 OS in Process Mode
 s SIMATIC Process Control PCS 7 V7.0 PCS 7 OS Process Control Operating Instructions Preface, Contents Additional Documentation 1 Functions of the PCS 7 OS in Process Mode 2 PCS 7 OS Process Mode - User
s SIMATIC Process Control PCS 7 V7.0 PCS 7 OS Process Control Operating Instructions Preface, Contents Additional Documentation 1 Functions of the PCS 7 OS in Process Mode 2 PCS 7 OS Process Mode - User
Date: May 19, Dear Dr. Domingo,
 Date: May 19, 2015 Reference: EMA15003 VIA E-MAIL Dr. Silvia Domingo European Medicines Agency 30 Churchill Place, Canary Wharf London E14 5EU UNITED KINGDOM Silvia.Domingo@ema.europa.eu Dear Dr. Domingo,
Date: May 19, 2015 Reference: EMA15003 VIA E-MAIL Dr. Silvia Domingo European Medicines Agency 30 Churchill Place, Canary Wharf London E14 5EU UNITED KINGDOM Silvia.Domingo@ema.europa.eu Dear Dr. Domingo,
Engineering SCADA (Introduction) Dr. Sasidharan Sreedharan
 Engineering SCADA (Introduction) Dr. Sasidharan Sreedharan www.sasidharan.webs.com Contents What is a SCADA System Simple SCADA System lay out and working Components of a SCADA System Levels of SCADA -
Engineering SCADA (Introduction) Dr. Sasidharan Sreedharan www.sasidharan.webs.com Contents What is a SCADA System Simple SCADA System lay out and working Components of a SCADA System Levels of SCADA -
Making the Impossible Possible
 Making the Impossible Possible Find and Eliminate Data Errors with Automated Discovery and Data Lineage Introduction Organizations have long struggled to identify and take advantage of opportunities for
Making the Impossible Possible Find and Eliminate Data Errors with Automated Discovery and Data Lineage Introduction Organizations have long struggled to identify and take advantage of opportunities for
EVALUATION ASSIGNMENT 2
 EVALUATION ASSIGNMENT 2 CS5760 Graduate Human-Computer Interaction Abstract An investigation of the user interface domain, heuristic principles, and critical usability concerns for the current design and
EVALUATION ASSIGNMENT 2 CS5760 Graduate Human-Computer Interaction Abstract An investigation of the user interface domain, heuristic principles, and critical usability concerns for the current design and
DESIGN AND OPTIMISATION OF DEPENDABLE MEASUREMENT SYSTEMS
 12th IMEKO TC1 & TC7 Joint Symposium on Man Science & Measurement September, 3 5, 2008, Annecy, France DESIGN AND OPTIMISATION OF DEPENDABLE MEASUREMENT SYSTEMS Blaise CONRARD, Mireille BAYART Laboratoire
12th IMEKO TC1 & TC7 Joint Symposium on Man Science & Measurement September, 3 5, 2008, Annecy, France DESIGN AND OPTIMISATION OF DEPENDABLE MEASUREMENT SYSTEMS Blaise CONRARD, Mireille BAYART Laboratoire
The role of functional decomposition
 The role of functional decomposition Jon Bell Doc. ref. SD/TR/FR/10: July 27, 2004 Abstract Hierarchical decomposition of function is already a feature of the language used for interpretation of simulation
The role of functional decomposition Jon Bell Doc. ref. SD/TR/FR/10: July 27, 2004 Abstract Hierarchical decomposition of function is already a feature of the language used for interpretation of simulation
Motivation Thermal Modeling
 Motivation Thermal Modeling First approach (Physical Buildings) Second Approach (Simulation Models) Model-Based Optimal Control Design Robust MPC Comparing Different Control Strategies Co-design of Control
Motivation Thermal Modeling First approach (Physical Buildings) Second Approach (Simulation Models) Model-Based Optimal Control Design Robust MPC Comparing Different Control Strategies Co-design of Control
Lecture 3: Linear Classification
 Lecture 3: Linear Classification Roger Grosse 1 Introduction Last week, we saw an example of a learning task called regression. There, the goal was to predict a scalar-valued target from a set of features.
Lecture 3: Linear Classification Roger Grosse 1 Introduction Last week, we saw an example of a learning task called regression. There, the goal was to predict a scalar-valued target from a set of features.
Title: Increasing the stability and robustness of simulation-based network assignment models for largescale
 Title: Increasing the stability and robustness of simulation-based network assignment models for largescale applications Author: Michael Mahut, INRO Consultants Inc. Larger-scale dynamic network models
Title: Increasing the stability and robustness of simulation-based network assignment models for largescale applications Author: Michael Mahut, INRO Consultants Inc. Larger-scale dynamic network models
Modeling of a DaimlerChrysler Truck Engine using an Eulerian Spray Model
 Modeling of a DaimlerChrysler Truck Engine using an Eulerian Spray Model C. Hasse, S. Vogel, N. Peters Institut für Technische Mechanik RWTH Aachen Templergraben 64 52056 Aachen Germany c.hasse@itm.rwth-aachen.de
Modeling of a DaimlerChrysler Truck Engine using an Eulerian Spray Model C. Hasse, S. Vogel, N. Peters Institut für Technische Mechanik RWTH Aachen Templergraben 64 52056 Aachen Germany c.hasse@itm.rwth-aachen.de
Exploration of Fault Diagnosis Technology for Air Compressor Based on Internet of Things
 Exploration of Fault Diagnosis Technology for Air Compressor Based on Internet of Things Zheng Yue-zhai and Chen Xiao-ying Abstract With the development of network and communication technology, this article
Exploration of Fault Diagnosis Technology for Air Compressor Based on Internet of Things Zheng Yue-zhai and Chen Xiao-ying Abstract With the development of network and communication technology, this article
Enhanced function of standard controller by control variable sensor discredibility detection
 Proceedings of the 5th WSEAS Int. Conf. on System Science and Simulation in Engineering, Tenerife, Canary Islands, Spain, December 16-18, 2006 119 Enhanced function of standard controller by control variable
Proceedings of the 5th WSEAS Int. Conf. on System Science and Simulation in Engineering, Tenerife, Canary Islands, Spain, December 16-18, 2006 119 Enhanced function of standard controller by control variable
Error Analysis, Statistics and Graphing
 Error Analysis, Statistics and Graphing This semester, most of labs we require us to calculate a numerical answer based on the data we obtain. A hard question to answer in most cases is how good is your
Error Analysis, Statistics and Graphing This semester, most of labs we require us to calculate a numerical answer based on the data we obtain. A hard question to answer in most cases is how good is your
A Transformation-Based Model of Evolutionary Architecting for Embedded System Product Lines
 A Transformation-Based Model of Evolutionary Architecting for Embedded System Product Lines Jakob Axelsson School of Innovation, Design and Engineering, Mälardalen University, SE-721 23 Västerås, Sweden
A Transformation-Based Model of Evolutionary Architecting for Embedded System Product Lines Jakob Axelsson School of Innovation, Design and Engineering, Mälardalen University, SE-721 23 Västerås, Sweden
Déjà Vu: A Hierarchical Case-Based Reasoning System for Software Design
 Déjà Vu: A Hierarchical Case-Based Reasoning System for Software Design Barry Smyth Hitachi Dublin Laboratory Trinity College Dublin 2 Ireland. Tel. 01-6798911 Fax. 01-6798926 E-mail: bsmyth@vax1.tcd.ie
Déjà Vu: A Hierarchical Case-Based Reasoning System for Software Design Barry Smyth Hitachi Dublin Laboratory Trinity College Dublin 2 Ireland. Tel. 01-6798911 Fax. 01-6798926 E-mail: bsmyth@vax1.tcd.ie
Software Engineering - I
 Software Engineering - I An Introduction to Software Construction Techniques for Industrial Strength Software Chapter 3 Requirement Engineering Copy Rights Virtual University of Pakistan 1 Requirement
Software Engineering - I An Introduction to Software Construction Techniques for Industrial Strength Software Chapter 3 Requirement Engineering Copy Rights Virtual University of Pakistan 1 Requirement
Fair City Plaza. Task: Diagnose problems, recommend improvements for small municipal district cooling system
 Fair City Plaza Task: Diagnose problems, recommend improvements for small municipal district cooling system The Fair City Plaza district cooling system provides chilled water to five buildings in a downtown
Fair City Plaza Task: Diagnose problems, recommend improvements for small municipal district cooling system The Fair City Plaza district cooling system provides chilled water to five buildings in a downtown
Accord Builder. User Guide
 User Guide Document: V 3.6 User Guide R01 V3.6 User Guide R01 Page 1 of 110 Table of Contents 1 Introduction... 7 2 General Summary and Definitions... 8 2.1 Accord Platform and Plant... 8 2.2 PLC Control
User Guide Document: V 3.6 User Guide R01 V3.6 User Guide R01 Page 1 of 110 Table of Contents 1 Introduction... 7 2 General Summary and Definitions... 8 2.1 Accord Platform and Plant... 8 2.2 PLC Control
Dependability tree 1
 Dependability tree 1 Means for achieving dependability A combined use of methods can be applied as means for achieving dependability. These means can be classified into: 1. Fault Prevention techniques
Dependability tree 1 Means for achieving dependability A combined use of methods can be applied as means for achieving dependability. These means can be classified into: 1. Fault Prevention techniques
Fundamentals of Operations Research. Prof. G. Srinivasan. Department of Management Studies. Indian Institute of Technology, Madras. Lecture No.
 Fundamentals of Operations Research Prof. G. Srinivasan Department of Management Studies Indian Institute of Technology, Madras Lecture No. # 13 Transportation Problem, Methods for Initial Basic Feasible
Fundamentals of Operations Research Prof. G. Srinivasan Department of Management Studies Indian Institute of Technology, Madras Lecture No. # 13 Transportation Problem, Methods for Initial Basic Feasible
Hierarchical Disk Driven Scheduling for Mixed Workloads
 Hierarchical Disk Driven Scheduling for Mixed Workloads Gwendolyn Einfeld gwen@soe.ucsc.edu Computer Science Department University of California, Santa Cruz Santa Cruz, CA 9564 Abstract Disk schedulers
Hierarchical Disk Driven Scheduling for Mixed Workloads Gwendolyn Einfeld gwen@soe.ucsc.edu Computer Science Department University of California, Santa Cruz Santa Cruz, CA 9564 Abstract Disk schedulers
6.001 Notes: Section 15.1
 6.001 Notes: Section 15.1 Slide 15.1.1 Our goal over the next few lectures is to build an interpreter, which in a very basic sense is the ultimate in programming, since doing so will allow us to define
6.001 Notes: Section 15.1 Slide 15.1.1 Our goal over the next few lectures is to build an interpreter, which in a very basic sense is the ultimate in programming, since doing so will allow us to define
Handling Cyclic Execution Paths in Timing Analysis of Component-based Software
 Handling Cyclic Execution Paths in Timing Analysis of Component-based Software Luka Lednicki, Jan Carlson Mälardalen Real-time Research Centre Mälardalen University Västerås, Sweden Email: {luka.lednicki,
Handling Cyclic Execution Paths in Timing Analysis of Component-based Software Luka Lednicki, Jan Carlson Mälardalen Real-time Research Centre Mälardalen University Västerås, Sweden Email: {luka.lednicki,
Process Control and Instrumentation Technology Model: PCT-200
 Process Control and Instrumentation Technology Model: PCT-200 Introduction The PCT-200 Process Control and Instrumentation rig provides a self-contained process control system which is representative of
Process Control and Instrumentation Technology Model: PCT-200 Introduction The PCT-200 Process Control and Instrumentation rig provides a self-contained process control system which is representative of
How flowmeters perform self-verification
 How flowmeters perform self-verification Here s how modern flowmeters verify their own measurement performance By Nathan Hedrick, Endress+Hauser, USA Process manufacturing and other industrial facilities
How flowmeters perform self-verification Here s how modern flowmeters verify their own measurement performance By Nathan Hedrick, Endress+Hauser, USA Process manufacturing and other industrial facilities
Data Mining for Fault Diagnosis and Machine Learning. for Rotating Machinery
 Key Engineering Materials Vols. 293-294 (2005) pp 175-182 online at http://www.scientific.net (2005) Trans Tech Publications, Switzerland Online available since 2005/Sep/15 Data Mining for Fault Diagnosis
Key Engineering Materials Vols. 293-294 (2005) pp 175-182 online at http://www.scientific.net (2005) Trans Tech Publications, Switzerland Online available since 2005/Sep/15 Data Mining for Fault Diagnosis
3 September
 3 September 2012 Reference: EMA 12007 By e-mail: Silvia.Domingo@ema.europa.eu Dr. Silvia DOMINGO European Medicines Agency 7 Westferry Circus Canary Wharf London E14 4HB, United Kingdom Subject: epmf Database
3 September 2012 Reference: EMA 12007 By e-mail: Silvia.Domingo@ema.europa.eu Dr. Silvia DOMINGO European Medicines Agency 7 Westferry Circus Canary Wharf London E14 4HB, United Kingdom Subject: epmf Database
28th Seismic Research Review: Ground-Based Nuclear Explosion Monitoring Technologies
 APPLICATION OF ARTIFICIAL NEURAL NETWORK MODELING TO THE ANALYSIS OF THE AUTOMATED RADIOXENON SAMPLER-ANALYZER STATE OF HEALTH SENSORS James C. Hayes, Pamela G. Doctor, Tom R. Heimbigner, Charles W. Hubbard,
APPLICATION OF ARTIFICIAL NEURAL NETWORK MODELING TO THE ANALYSIS OF THE AUTOMATED RADIOXENON SAMPLER-ANALYZER STATE OF HEALTH SENSORS James C. Hayes, Pamela G. Doctor, Tom R. Heimbigner, Charles W. Hubbard,
The Great Mystery of Theoretical Application to Fluid Flow in Rotating Flow Passage of Axial Flow Pump, Part I: Theoretical Analysis
 Proceedings of the 2nd WSEAS Int. Conference on Applied and Theoretical Mechanics, Venice, Italy, November 20-22, 2006 228 The Great Mystery of Theoretical Application to Fluid Flow in Rotating Flow Passage
Proceedings of the 2nd WSEAS Int. Conference on Applied and Theoretical Mechanics, Venice, Italy, November 20-22, 2006 228 The Great Mystery of Theoretical Application to Fluid Flow in Rotating Flow Passage
Distributed Deadlock Detection for. Distributed Process Networks
 0 Distributed Deadlock Detection for Distributed Process Networks Alex Olson Embedded Software Systems Abstract The distributed process network (DPN) model allows for greater scalability and performance
0 Distributed Deadlock Detection for Distributed Process Networks Alex Olson Embedded Software Systems Abstract The distributed process network (DPN) model allows for greater scalability and performance
TMS1122: Chemistry of Materials
 Course Structure Level I Semester I Engineering Science and Design Credits Mathematics, Basic Science & Credits Complementary Studies Credits ENT1111: Workshop Technology I TMS1113: Foundation of Mathematics
Course Structure Level I Semester I Engineering Science and Design Credits Mathematics, Basic Science & Credits Complementary Studies Credits ENT1111: Workshop Technology I TMS1113: Foundation of Mathematics
Modeling and Simulation (An Introduction)
 Modeling and Simulation (An Introduction) 1 The Nature of Simulation Conceptions Application areas Impediments 2 Conceptions Simulation course is about techniques for using computers to imitate or simulate
Modeling and Simulation (An Introduction) 1 The Nature of Simulation Conceptions Application areas Impediments 2 Conceptions Simulation course is about techniques for using computers to imitate or simulate
LCD LCDS LCDRI CONTROLLER OPERATING MANUAL
 This manual contains important safety information about installation and use of this equipment. Ignoring this information could result in injuries or damages. It is strictly forbidden to use this equipment
This manual contains important safety information about installation and use of this equipment. Ignoring this information could result in injuries or damages. It is strictly forbidden to use this equipment
Converter SINAMICS G150. Type 6SL37102G
 Tests carried out on drives This documentation pertains to LV Umrichter E11 F72 F76 F79 L45 L50 L57 L68 M54 U11 Reference Manual Converter SINAMICS G150 Type 6SL37102G Edition 02/2019 www.siemens.com/drives
Tests carried out on drives This documentation pertains to LV Umrichter E11 F72 F76 F79 L45 L50 L57 L68 M54 U11 Reference Manual Converter SINAMICS G150 Type 6SL37102G Edition 02/2019 www.siemens.com/drives
PARALLEL ENGINEERING SIMULATIONS BASED ON FORMING SIMULATION OF A HEAT EXCHANGER PLATE
 PARALLEL ENGINEERING SIMULATIONS BASED ON FORMING SIMULATION OF A HEAT EXCHANGER PLATE Gabrielson P.*, Thuvesen D.** * Alfa Laval Lund AB Box 74, S-221 00 LUND, Sweden & Div. of Production and Materials
PARALLEL ENGINEERING SIMULATIONS BASED ON FORMING SIMULATION OF A HEAT EXCHANGER PLATE Gabrielson P.*, Thuvesen D.** * Alfa Laval Lund AB Box 74, S-221 00 LUND, Sweden & Div. of Production and Materials
An Anomaly in Unsynchronized Pointer Jumping in Distributed Memory Parallel Machine Model
 An Anomaly in Unsynchronized Pointer Jumping in Distributed Memory Parallel Machine Model Sun B. Chung Department of Quantitative Methods and Computer Science University of St. Thomas sbchung@stthomas.edu
An Anomaly in Unsynchronized Pointer Jumping in Distributed Memory Parallel Machine Model Sun B. Chung Department of Quantitative Methods and Computer Science University of St. Thomas sbchung@stthomas.edu
An Interactive Technique for Robot Control by Using Image Processing Method
 An Interactive Technique for Robot Control by Using Image Processing Method Mr. Raskar D. S 1., Prof. Mrs. Belagali P. P 2 1, E&TC Dept. Dr. JJMCOE., Jaysingpur. Maharashtra., India. 2 Associate Prof.
An Interactive Technique for Robot Control by Using Image Processing Method Mr. Raskar D. S 1., Prof. Mrs. Belagali P. P 2 1, E&TC Dept. Dr. JJMCOE., Jaysingpur. Maharashtra., India. 2 Associate Prof.
Automated Analysis of Digital Relay Data Based on Expert System
 Automated Analysis of Digital Relay Data Based on Expert System X. Luo, Student Member, IEEE, and M. Kezunovic, Fellow, IEEE Abstract Modern digital protective relays generate various files and reports
Automated Analysis of Digital Relay Data Based on Expert System X. Luo, Student Member, IEEE, and M. Kezunovic, Fellow, IEEE Abstract Modern digital protective relays generate various files and reports
A simple problem that has a solution that is far deeper than expected!
 The Water, Gas, Electricity Problem A simple problem that has a solution that is far deeper than expected! Consider the diagram below of three houses and three utilities: water, gas, and electricity. Each
The Water, Gas, Electricity Problem A simple problem that has a solution that is far deeper than expected! Consider the diagram below of three houses and three utilities: water, gas, and electricity. Each
CHAPTER III TMN MANAGEMENT
 CHAPTER III TMN MANAGEMENT TMN Management TMN Management The term TMN is introduced by the ITU-T (the former CCITT) as an abbreviation for 'Telecommunications Management Network'. The concept of a TMN
CHAPTER III TMN MANAGEMENT TMN Management TMN Management The term TMN is introduced by the ITU-T (the former CCITT) as an abbreviation for 'Telecommunications Management Network'. The concept of a TMN
Application Note AN18.01.en
 Application Note AN18.01.en by Diplom-Wirt.-Ing. (FH) Thomas Walker - (engineering/business management degree) Redundant power supplies and parallel operation of power supply units How to achieve the best
Application Note AN18.01.en by Diplom-Wirt.-Ing. (FH) Thomas Walker - (engineering/business management degree) Redundant power supplies and parallel operation of power supply units How to achieve the best
6 th European Energy Forum
 1 UNLOCKING SMART CAPABILITIES FOR LOCAL AUTHORITIES Jan Kowalczyk, CEO, Banner Group, Warsaw, Poland 6 th European Energy Forum Unlocking smart capabilities for local authorities Paris, 22-23 May 2017
1 UNLOCKING SMART CAPABILITIES FOR LOCAL AUTHORITIES Jan Kowalczyk, CEO, Banner Group, Warsaw, Poland 6 th European Energy Forum Unlocking smart capabilities for local authorities Paris, 22-23 May 2017
Use of Artificial Neural Networks to Investigate the Surface Roughness in CNC Milling Machine
 Use of Artificial Neural Networks to Investigate the Surface Roughness in CNC Milling Machine M. Vijay Kumar Reddy 1 1 Department of Mechanical Engineering, Annamacharya Institute of Technology and Sciences,
Use of Artificial Neural Networks to Investigate the Surface Roughness in CNC Milling Machine M. Vijay Kumar Reddy 1 1 Department of Mechanical Engineering, Annamacharya Institute of Technology and Sciences,
(Formerly University of Pune) INSTRUCTIONS FOR CANDIDATES
 SAVITRIBAI PHULE PUNE UNIVERSITY (Formerly University of Pune) 254 /- 2016 Examination Circular No. 254 of 2016 Programme of B.E. (All Branches) In Sem Examinations, AUGUST, 2016 INSTRUCTIONS FOR CANDIDATES
SAVITRIBAI PHULE PUNE UNIVERSITY (Formerly University of Pune) 254 /- 2016 Examination Circular No. 254 of 2016 Programme of B.E. (All Branches) In Sem Examinations, AUGUST, 2016 INSTRUCTIONS FOR CANDIDATES
A Neural Network Model Of Insurance Customer Ratings
 A Neural Network Model Of Insurance Customer Ratings Jan Jantzen 1 Abstract Given a set of data on customers the engineering problem in this study is to model the data and classify customers
A Neural Network Model Of Insurance Customer Ratings Jan Jantzen 1 Abstract Given a set of data on customers the engineering problem in this study is to model the data and classify customers
System fault diagnostics using fault tree analysis
 Loughborough University Institutional Repository System fault diagnostics using fault tree analysis This item was submitted to Loughborough University's Institutional Repository by the/an author. Citation:
Loughborough University Institutional Repository System fault diagnostics using fault tree analysis This item was submitted to Loughborough University's Institutional Repository by the/an author. Citation:
Med-Info. Council Directive 93/42/EEC on medical devices. TÜV SÜD Product Service GmbH
 Med-Info International expert information for the medical device industry Council Directive 93/42/E on medical devices Practice-oriented summary of the most important aspects and requirements contained
Med-Info International expert information for the medical device industry Council Directive 93/42/E on medical devices Practice-oriented summary of the most important aspects and requirements contained
