Efficient Elliptic Curve Processor Architectures for Field Programmable Logic
|
|
|
- Shanon Patterson
- 5 years ago
- Views:
Transcription
1 Efficient Elliptic Curve Processor Architectures for Field Programmable Logic by Gerardo Orlando A Dissertation Submitted to the Faculty of the WORCESTER POLYTECHNIC INSTITUTE in partial fulfillment of the requirements for the Degree of Doctor of Philosophy in Electrical Engineering by March 4, 2002 APPROVED: Dr. Christof Paar Dissertation Advisor ECE Department Dr. Berk Sunar Dissertation Committee ECE Department Dr. Fred J. Looft Dissertation Committee ECE Department Dr. Wayne P. Burleson Dissertation Committee ECE Department University of Massacusetts Dr. John Orr Head of ECE Department
2 Abstract Elliptic curve cryptosystems offer security comparable to that of traditional asymmetric cryptosystems, such as those based on the RSA encryption and digital signature algorithms, with smaller keys and computationally more efficient algorithms. The ability to use smaller keys and computationally more efficient algorithms than traditional asymmetric cryptographic algorithms are two of the main reasons why elliptic curve cryptography has become popular. As the popularity of elliptic curve cryptography increases, the need for efficient hardware solutions that accelerate the computation of elliptic curve point multiplications also increases. This dissertation introduces elliptic curve processor architectures suitable for the computation of point multiplications for curves defined over fields GF (2 m ) and curves defined over fields GF (p). Each of the processor architectures presented here allows designers to tailor the performance and hardware requirements according to their performance and cost goals. Moreover, these architectures are well suited for implementation in modern field programmable gate arrays (FPGAs). This point was proved with prototyped implementations. The fastest prototyped GF (2 m ) processor can compute an arbitrary point multiplication for curves defined over fields GF (2 167 ) in 0.21 milliseconds and the prototyped processor for the field GF ( ) is capable of computing a point multiplication in about 3.6 milliseconds. The most critical component of an elliptic curve processor is its arithmetic unit. A typical arithmetic unit includes an adder/subtractor, a multiplier, and possibly a squarer. Some of the architectures presented in this work are based on multiplier and squarer architectures developed as part of the work presented in this dissertation. The GF (2 m ) least significant bit super-serial multiplier architecture, the
3 GF (2 m ) most significant bit super-serial multiplier architecture, and a new GF (p) Montgomery multiplier architecture were developed as part of this work together with a new squaring architecture for GF (2 m ).
4 Acknowledgements The work presented in this dissertation is the results of over four years of research. I want to thank Christof Paar for advising me throughout this research work. I also want to thank the members of the dissertation committee, Berk Sunar, Fred J. Looft, and Wayne P. Burleson, for reviewing this work. The majority of the research work presented here was done on a part-time basis while I worked as an engineer. I want to thank Julian Bubrowski, Walter Schneider, and Jim Sheedy for allowing me to balance my professional work with my research work. This work would have not been possible without their help. Finally, this work will not have been possible without the love and moral support of my sisters Clara and Marian, my mother Maria, and my father Juan. Lastly but not least, I want to acknowledge that the love and understanding of my wife Diane, my son Leonardo, and my daughter Jane carried me over the finish line. i
5 Contents 1 Introduction Motivation Summary of Research Contributions Dissertation Outline Background Finite Field Arithmetic GF(p) Arithmetic Background Montgomery Reduction GF(2 m ) Arithmetic Background Elliptic Curve Arithmetic Elliptic Curve Discrete Logarithm Problem (ECDLP) Coordinate Representation Special Coordinates and Algorithms Montgomery Point Multiplication Algorithm for GF(2 m ) Jacobi Form Point Multiplication Algorithms Generic Point Multiplication Algorithms ii
6 2.8.2 Fixed-Point Point Multiplication Algorithms Summary of Point Multiplication Algorithms Elliptic Curve Processor Architecture Architecture Main Controller (MC) Arithmetic Unit Controller (AUC) Arithmetic Unit (AU) GF(2 m ) Arithmetic Unit Introduction GF(2 m ) Multiplier Architectures GF(2 m ) Squarer Architectures Adder Most Significant Bit First Multiplier (MSB) Architecture Complexity, Critical Path Delay, and Performance Least Significant Bit First Multiplier (LSB) Architecture Complexity, Critical Path Delay, and Performance Most Significant Digit First Multiplier (MSD) Architecture Complexity, Critical Path Delay, and Performance Least Significant Digit First Multiplier (LSD) Architecture Complexity, Critical Path Delay, and Performance Most Significant Bit First Super-Serial Multiplier (MSB-SSM) iii
7 4.7.1 Architecture Complexity, Critical Path Delay, and Performance Least Significant Bit First Super-Serial Multiplier (LSB-SSM) Architecture Complexity, Critical Path Delay, and Performance New Squaring Architecture Architecture Complexity, Critical Path Delay, and Performance Parallel Squarers with Fixed Irreducible Polynomial Support Zero Test Register File GF(2 m ) Arithmetic Unit Complexity and Performance Complexity Performance GF(p) Arithmetic Unit Introduction High-Radix Montgomery Multiplication with Quotient Pipelining High-Radix, Precomputation-Based Montgomery Multiplication with Quotient Pipelining Validity of Algorithm Accuracy of Algorithm Range of S i Processing Time iv
8 5.3.5 Multiplications of Interest in the Computation of Point Multiplications Two s Complement and Binary Stored-Carry Number Representation Area and Storage Adder Complexity, Critical Path Delay, and Performance New Montgomery Multiplier BSC Shift Register BSC to NR Converter Booth Recoders 1 and ÃB i Scalar Multiplier Qαi d Scalar Multiplier Carry-Save Adder Tree S i /2 k Circuit Registers Complexity Critical Path Delay Performance Register File Multiplexer GF(p) Arithmetic Unit Complexity and Performance Complexity Performance Comparison of GF(2 m ) and GF(p) Arithmetic Units Introduction v
9 6.1.1 Complexity Performance Prototype Implementations Description of the Prototype Implementations of the GF(2 m ) Processors Complexity and Performance of the Prototyped GF(2 m ) Processors Description of the Prototype Implementation of the GF(p) Processor Complexity and Performance of the Prototyped GF(p) Processor Comparison of Prototyped GF(p) and GF(2 m ) Processors Conclusions Summary and Conclusions Recommendations for Further Research A Hardware Implementation Models 272 A.1 Introduction A.1.1 Two-Input Gate Implementations A.1.2 FPGA Implementations A.2 Logic Complexity and Critical Path Delay for Implementations that Use Two-Input Gates as Logic Elements A.3 Logic Complexity and Critical Path Delay for FPGA Implementations 287 B Acronyms and Symbols 296 B.1 Acronyms vi
10 B.2 Symbols vii
11 List of Figures 2.1 Point addition Point double Elliptic curve analogue of the Diffie-Hellman key agreement algorithm Arrangement of multiplier k for the fixed-point comb point multiplication algorithm G[s, I s,r ] precomputation table for the fixed-point comb point multiplication algorithm Point multiplication hierarchy Elliptic curve processor architecture MC instruction format Main controller AUC instruction format Arithmetic unit controller Functional block diagram of the arithmetic unit MSB multiplier LSB multiplier MSD multiplier LSD multiplier viii
12 4.5 Super-serial multiplier emulation of a bit-serial multiplier Processing units of the MSB and the MSB-SSM multipliers MSB-SSM multiplier Processing units of the LSB-SSM and the LSB multipliers LSB-SSM multiplier New squaring architecture using LSB or LSD multipliers New squaring architecture using LSB-SSM multipliers Zero test circuits GF (2 m ) arithmetic units GF (p) arithmetic unit Carry-save addition of two s complement numbers GF (p) adder GF (p) multiplier BSC to NR converter Example of the Modified Booth Recoding Algorithm Window recoder Generation and formatting of positive multiples Generation and formatting of negative multiples Processing unit for nonredundant number representation ÃB i scalar multiplier example for nonredundant number representation ÃB i scalar multiplier example for binary stored-carry number representation Qα i d scalar multiplier example for Multiplication and Lookup 1 reduction methods that uses nonredundant number representation Qα i d scalar multiplier example for Lookup 2 based reduction that uses nonredundant number representation ix
13 5.15 S i /2 k circuit Multiplexer options GF (2 m ) arithmetic unit architecture A.1 Two s complement with zero circuit A.2 Shift register circuit A.3 Binary tree and ripple adder architectures A.4 Ripple-carry adder A.5 Increment adder A.6 3:2 carry-save adder A.7 4:2 carry-save adder A.8 GF (2) adder implementation with a LUT A.9 2:1 multiplexer implementation with a LUT A.10 Half adder implementation with LUTs A.11 Full adder implementation with LUTs A.12 Two s complement with zero cell circuit implementation with a LUT 292 A.13 Shift register cell implementation with a LUT A.14 Binary tree implementation with LUTs A.15 GF (2) mult/add tree implementation with LUTs x
14 List of Tables 2.1 Complexity of GF (p) arithmetic operations Approximate bit-complexity of GF (2 m ) arithmetic operations Complexity of GF (2 m ) arithmetic operations Point addition and point double formulas for elliptic curves defined over fields GF (p) (p > 3) and points represented using affine coordinates Point addition and point double formulas for elliptic curves defined over fields GF (2 m ) and points represented using affine coordinates Point addition and point double formulas for elliptic curves defined over fields GF (p) (p > 3) and points represented using Jacobian coordinates Point addition and point double formulas for elliptic curves defined over fields GF (2 m ) and points represented using Jacobian coordinates Computational complexity of point addition and point double for curves defined over fields GF (p) (p > 3) Computational complexity of point addition and point double for curves defined over fields GF (2 m ) Montgomery point multiplication using projective coordinates Computational complexity of the Montgomery point multiplication algorithm xi
15 2.12 Complexity of point multiplication algorithms Complexity of point multiplication algorithms for k = 160 m log 2 p MC instruction set execution control instructions MC instruction set data manipulation and arithmetic instructions MC instruction set symbols MC components AUC instruction set AUC instruction set symbols AUC components Time-area characteristics of GF (2 m ) multipliers Time-area characteristics of GF (2 m ) squarers Complexity and critical path delay of GF (2 m ) adders Complexity and critical path delay of MSB multiplier Performance of MSB multiplier Complexity and critical path delay of LSB multiplier Performance of LSB multiplier Complexity and critical path delay of MSD multiplier Complexity and critical path delay of MSD multiplier for m >> D >> r Performance of MSD multiplier Complexity and critical path delay of LSD multiplier Complexity and critical path delay of LSD multiplier for m >> D >> r Performance of LSD multiplier xii
16 4.14 MSB-SSM multiplication example for AB mod (α i=0 f iα i ) with D = Complexity and critical path delay of MSB-SSM multiplier Performance of MSB-SSM multiplier LSB-SSM multiplication example for AB mod x i=0 f iα i +C with D = Complexity and critical path delay of LSB-SSM multiplier Performance of LSB-SSM multiplier Number of clock cycles required to compute a square operation when using different types of multipliers Complexity and critical path delay of the squaring adapter to be used with LSB and LSD multipliers Complexity and critical path delay of the squaring adapter to be used with LSB-SSM multipliers with digit sizes with even values Distribution of squaring to multiplication processing time ratios for the GF (2 m ) fields polynomials specified in [ANS98, ANS99] with prime m in the range Distribution of squaring to multiplication processing time ratios for the GF (2 m ) fields polynomials specified in [IEE98] with prime m in the range when using LSB or LSB-SSM multipliers Complexity and critical path delay statistics for parallel squarers that support the fixed trinomials specified in [IEE98, ANS98, ANS99] of prime degree in the range Complexity and critical path delay statistics for parallel squarers that support the fixed pentanomials specified in [IEE98] of prime degree in the range xiii
17 4.27 Complexity and critical path delay statistics for parallel squarers that support the fixed pentanomials specified in [ANS98, ANS99] of prime degree in the range Complexity and critical path delay of zero test circuits Complexity and critical path delay of register file Complexity of architecture 4 for arithmetic units based on MSB-SSM multipliers Complexity of architecture 1 for arithmetic units based on LSB-SSM multipliers Complexity of architecture 2 for arithmetic units based on LSB-SSM multipliers Complexity of architecture 4 for arithmetic units based on MSB multipliers Complexity of architecture 5 for arithmetic units based on MSB multipliers Complexity of architecture 1 for arithmetic units based on LSB multipliers Complexity of architecture 2 for arithmetic units based on LSB multipliers Complexity of architecture 3 for arithmetic units based on LSB multipliers Complexity of architecture 4 for arithmetic units based on MSD multipliers that support programmable and fixed irreducible polynomials (m >> D >> r) xiv
18 4.39 Complexity of architecture 5 for arithmetic units based on MSD multipliers that support programmable and fixed irreducible polynomials (m >> D >> r) Complexity of architecture 1 for arithmetic units based on LSD multipliers that support programmable and fixed irreducible polynomials (m >> D >> r) Complexity of architecture 2 for arithmetic units based on LSD multipliers that support programmable and fixed irreducible polynomials (m >> D >> r) Complexity of architecture 3 for arithmetic units based on LSD multipliers that support programmable and fixed irreducible polynomials (m >> D >> r) Summary of arithmetic unit gate complexity according to multiplier family for architectures that include squaring circuitry, that provide programmable polynomial support, and that exhibit m >> D >> r Summary of arithmetic unit FPGA logic complexity according to multiplier family for architectures that include squaring circuitry, that provide programmable polynomial support, and that exhibit m >> D >> r Summary of critical path delays of GF (2 m ) multipliers that support programmable irreducible polynomials for which m >> D >> r Summary of critical path delays, according to multiplier families, of GF (2 m ) arithmetic units that support programmable irreducible polynomials for which m >> D >> r Throughput of GF (2 m ) arithmetic units for multiplication operations (in clock cycles) xv
19 4.48 Throughput of GF (2 m ) arithmetic units for square operations (in clock cycles) Throughput of GF (2 m ) arithmetic units for addition operations (in clock cycles) Throughput for the different field operations of GF (2 m ) arithmetic units that incorporate squaring circuitry (estimates are provided in clock cycles according to the multiplier families) Accuracy of different reduction methods Approximate maximum value of Qα j+1 2 k(d+1) Q j Approximate maximum value of 2 k i d 1 j=0 ( Qα j+1 2 k(d+1) Q j+1 ) 2 kj Multiplications of interest Bus widths Approximate bus widths (Multiplication reduction method) Complexity of GF (p) adder Critical path delay of GF (p) adder Performance of GF (p) adder Components of the GF (p) multiplier Complexity and critical path delay of BSC shift register Complexity and critical path delay of BSC to NR converter Complexity and critical path delay of Booth recoder Complexity and critical path delay of ÃB i scalar multiplier Complexity and critical path delay of Qα i d scalar multiplier Carry-save adder tree configurations Complexity and critical path delay of carry-save adder tree Complexity and critical path delay of S i /2 k circuit Complexity and critical path delay of registers xvi
20 5.20 Complexity of GF (p) multiplier Critical path delay of GF (p) multiplier Average latency of GF (p) multiplier Average throughput of GF (p) multiplier Complexity and critical path delay of register file Complexity and critical path delay of multiplexer Complexity of the GF (p) arithmetic unit Complexity of the GF (p) arithmetic unit (cont.) Complexity of GF (2 m ) and GF (p) arithmetic units (m >> k,d,r,s,u,v,d) Complexity ratio between GF (2 m ) and GF (p) (min. complexity) arithmetic units (m >> k, D, r, s, u, v, d) Complexity ratio between GF (2 m ) and GF (p) (max. complexity) arithmetic units (m >> k, D, r, s, u, v, d) Critical path delay of GF (2 m ) and GF (p) arithmetic units Processing time for GF (p) and GF (2 m ) arithmetic units (in # clock cycles) Logic complexity of GF (2 m ) processors (m = 167) Estimated LUT complexity of an arithmetic unit versus measured LUT complexity of GF (2 m ) processor (m = 167) Point multiplication performance of GF (2 m ) processors Performance of leading hardware accelerators that compute point multiplications for curves defined over fields GF (2 m ) Logic complexity of GF (p) processor Estimated LUT complexity of arithmetic unit versus measured LUT complexity of GF (p) processor (w 0 = 237) Estimated point multiplication performance of GF (p) processor xvii
21 6.13 Performance of leading hardware accelerators that compute point multiplications for curves defined over fields GF (p) Complexity of GF (2 m ) and GF (p) processors normalized with respect to m Approximate processing time for the computation of different field operations in the GF (2 m ) and GF (p) processors Ratio of time-area characteristics of prototypes A.1 Frequently used terms in complexity and timing estimates A.2 Frequently used terms in complexity and timing estimates (cont.) A.3 Complexity of basic building blocks for implementations that use twoinput gates as logic elements A.4 Critical path delay of basic building blocks for implementations that use two-input gates as logic elements A.5 Complexity of composite building blocks for implementations that use two-input gates as logic elements A.6 Critical path delay of composite building blocks for implementations using two-input gates as logic elements A.7 Complexity of basic building blocks for implementations using FPGA logic A.8 Critical path delay of basic building blocks for implementations using FPGA logic A.9 Complexity of composite building blocks for implementations using FPGA logic A.10 Critical path delay of composite building blocks for implementations using FPGA logic xviii
22 B.1 Acronyms B.2 Symbols xix
23 Chapter 1 Introduction 1.1 Motivation This work introduces elliptic curve processor architectures designed to take advantage of the features offered by reprogrammable hardware, in particular field programmable gate array (FPGA) hardware. The first elliptic curve cryptosystems were independently proposed in 1985 by Neil Koblitz [Kob87] and Victor Miller [Mil86]. Since its inception, elliptic curve cryptography has been the subject of extensive cryptanalysis. Today, elliptic curve cryptosystems are deemed secure for commercial [ANS98, ANS99, IEE98] as well as government use [FIP00]. Based on today s cryptanalytical knowledge, elliptic curve cryptosystems offer security comparable to that of traditional public-key cryptosystems, such as those based on the RSA [RSA78] and the ElGamal [ElG85] encryption and digital signature algorithms, and those based on the Diffie-Hellman key agreement algorithm [DH76], with smaller keys and computationally more efficient algorithms. The ability to use smaller keys and computationally more efficient algorithms 1
24 than traditional cryptographic algorithms are two of the main reasons why elliptic curve cryptography is becoming popular for use in constrained environments such as cellular phones and personal digital assistant devices, which contain limited amounts of memory and are battery-powered. The same reasons also make elliptic curve cryptography attractive for high performance systems, such as secure networking devices, whose ability to protect and route traffic are a function of their capacity to establish secure connections. The establishments of these secure connections often involve public-key operations. Efficient software implementations of elliptic curve algorithms have been and continue to be a topic of extensive research. Some important works in this area are documented in [SOOS95, HLM00, WBV + 96, WMPW98, LD99a]. Software architectures have the great advantage that they are portable to multiple hardware platforms. Their main disadvantages are their lower performance when compared to specialized hardware architectures and their inability to protect private keys from disclosure with the same degree of security that is achievable in hardware. These disadvantages are some of the reasons motivating the study of efficient hardware architectures. Efficient hardware implementations of elliptic curve algorithms are just beginning to be documented. Among the most significant hardware architectures for elliptic curves defined over fields GF (2 m ) are [AMV93, Ros98b, GSS99, SES98, LMWL00, OP00a]. As of this writing, the elliptic curve processor architecture documented in [OP01] is the only elliptic curve processor architecture for GF (p) documented in the open literature. The emphasis of this work is on elliptic curve processor architectures based on the architectures introduced by the author in [OP00a] and [OP01] as part of the research work documented here. These architectures are well suited for implementation using 2
25 FPGAs, which is the hardware platform emphasized in this work. Unlike traditional very large scale integration (VLSI) hardware, FPGAs do not possess fixed functionality after fabrication. FPGAs are reconfigurable hardware devices; that is, devices whose functionality is programmable. The configuration of an FPGA device can be changed over time thus allowing the same FPGA to implement different functions. The reconfigurability of FPGAs and the use of architecturally scalable elliptic curve processor architectures afford implementations the benefits listed below. Architecture Efficiency: The complexity of finite field arithmetic architectures depends greatly on whether arithmetic for one specific field representation is being implemented or whether it is implemented for arbitrary finite field representations. The most dramatic example is perhaps squaring in GF (2 m ) using standard basis. For a specific field, squaring can be performed in one clock cycle, whereas a general architecture usually requires m/2 clock cycles (where m 160 for elliptic curves cryptosystems) [BG89]. One of the algorithmic options explored in this work is the use of parallel squarers optimized for the different GF (2 m ) fields. The reconfigurability of FPGA logic allows the instantiation of different squarer architectures in the same hardware. Scalable Security: Depending on the application, different levels of security may be required. The main factor that determines the security of an elliptic curve cryptosystem is the size of the underlying finite field. For instance, the National Institute of Standards and Technology (NIST) announced a list of curves that can support keys of 163 to 571 bits [FIP00]. Realizing such a wide operand range efficiently in traditional hardware is a major challenge whereas the use of architecturally scalable elliptic curve processor architectures together with 3
26 the reconfigurability of FPGA logic allows implementations to realize different security levels in the same hardware. For example, an FPGA can be configured with an elliptic curve processor function that supports 163-bit arithmetic. Later, the same FPGA can be reconfigured with an elliptic curve processor function that supports 571-bit arithmetic. Scalable Performance-Cost Trade-Off: Different applications may favor very different trade-offs between processing speed and logic resources. For the elliptic curve processor architectures presented here, the finite field multiplier is the most critical component. This work describes different multiplier architectures whose performance and complexity are scalable. These multiplier architectures allow implementers to explore different area-time trade-offs. Moreover, the fine degree of scalability of some of these multipliers allows implementers to best use the resources available in the targeted FPGA platforms. The rest of this document is devoted to the description of elliptic curve processor architectures that exploit the features of FPGA logic described above. 4
27 1.2 Summary of Research Contributions This work introduces new elliptic curve processor architectures suitable for the computation of point multiplications for elliptic curves defined over fields GF (2 m ). These architectures are based on the architecture presented by the author at the Cryptographic Hardware and Embedded Systems CHES 2000 conference. This architecture was published as part of the proceedings of that conference in [OP00a]. This work extends the work documented in [OP00a] to elliptic curve processors based on different types of GF (2 m ) multipliers and squaring architectures. Two of the GF (2 m ) multipliers used in the elliptic curve processor architectures discussed in this document were developed as part of the dissertation research documented here. These multipliers belong to the family of multipliers originally named super-serial multipliers. These are multipliers of low complexity especially designed to exploit the availability of memory in modern FPGA logic. The first multiplier was presented in the Seventh Annual IEEE Symposium on Field-Programmable Custom Computing Machines (FCCM 99) and it was published as part of the proceedings of that conference in [OP99]. A new super-serial multiplier is also introduced in this dissertation. This multiplier is discussed in Section 4.8. One of the squaring architectures for GF (2 m ) discussed in this document was developed as part of the dissertation research. This squaring architecture is based on the observation that a squaring operation in GF (2 m ) can be transformed into a multiplication by a constant and a sum, when the field elements are represented using standard basis. The computation of the multiplication and the sum can be performed with a simple circuit and a least-significant bit/digit first multiplier. This work was published in the IEE Electronic Letters Journal in [OP00b]. This work introduces a new elliptic curve processor architecture suitable for the 5
28 computation of point multiplications for elliptic curves defined over fields GF (p). This processor is an extension of the processor architecture for GF (2 m ) introduced in [OP00a]. The centerpiece of this processor is a new Montgomery multiplier optimized for field programmable logic, which was developed as part of the work documented here. This processor architecture was presented at the Cryptographic Hardware and Embedded Systems CHES 2001 conference and it was published as part of the proceedings of that conference in [OP01]. 6
29 1.3 Dissertation Outline Chapter 2 introduces the arithmetic and algorithmic concepts needed for the understanding of this dissertation. This chapter starts with an introduction to GF (2 m ) and GF (p) finite fields. The chapter then proceeds with an introduction to elliptic curve arithmetic and the elliptic curve discrete logarithm problem. The chapter ends with an introduction to elliptic curve coordinate representations and with descriptions of point multiplication algorithms, which are the core functions of elliptic curve processors. Chapter 3 introduces the general architecture of the elliptic curve processors introduced in this work. This section also describes the architecture of the two programmable processors used in the elliptic curve processor architectures. This chapter ends with a general description of the architecture of the arithmetic units used by the elliptic curve processors. Chapter 4 introduces GF (2 m ) arithmetic unit architectures. These architectures are based on six types of GF (2 m ) multipliers and two squaring architectures. Two of the multiplier architectures and one of the squaring architectures were developed by the author as part of the dissertation research presented here. This chapter also provides complexity and performance estimates for the different architectures. Chapter 5 introduces a GF (p) arithmetic unit architecture. This architecture is based on a new Montgomery multiplier introduced by the author as part of the dissertation research documented here. This chapter describes the new Montgomery multiplier in detail and provides complexity and performance estimates for different configurations of the arithmetic unit. Chapter 6 compares the complexity and performance of arithmetic units for GF (2 m ) finite fields based on digit-serial multipliers and the arithmetic unit archi- 7
30 tecture for GF (p) finite fields based on the new Montgomery multiplier. This section also compares the complexity and performance of prototype implementations of an elliptic curve processor for point multiplication for curves defined over a GF (2 m ) finite field and an elliptic curve processor for point multiplication for curves defined over a GF (p) finite field. Chapter 7 summarizes the conclusions of this work and provides recommendations for further research. Appendix A describes the models used to quantify the complexity and the performance of the circuits that form part of the elliptic curve processors introduced here. Appendix B lists the acronyms and symbols used in this work. 8
31 Chapter 2 Background 2.1 Finite Field Arithmetic This section provides a brief introduction to finite field arithmetic. Finite field arithmetic is used in many public-key cryptosystems in use today, including elliptic curve cryptosystems. Additional information on this topic can be found in [McE87, LN94, Big85]. A finite field is a finite set of elements with interesting properties. Before describing its properties, it is convenient to introduce few terms. A group is a set of elements G with one binary operation,, that exhibit the following properties: 1. A group is closed under the operation: a b = c for a, b, c G. 2. The operation is associative: (a b) c = a (b c). 3. The group contains an identity element e G such that a e = e a = a for a G. 4. Every element a G has an inverse a 1 G such that a a 1 = a 1 a = e. 9
32 Abelian groups are groups with the additional property that the group operation is commutative; that is, a b = b a for a, b G. Cyclic groups are characterized by the existence of generators. A generator g is a group element that can represent each group element a as a = ig for i = 0... G 1, where ig = g g... g. The number of elements in the group is }{{} i times known as the order of the group and it is represented here with the symbol G, where G represents the group under consideration. A field is a set of elements F with two binary operations, represented here as addition (+) and multiplication ( ), that exhibit the following properties: 1. The elements of F form an abelian group under the + operation. 2. The elements of the set F, which is a set that contains all the elements in the set F except the additive identity, form an abelian group under the operation. 3. The distribute laws apply to the two binary operations; for example, a (b+c) = (a b) + (a c) for a, b, c F. Finite fields are also referred to as Galois fields and are represented here by the symbol GF (q). Finite fields exist only for q = p m, where p is a prime number and m is a positive integer. The number of elements of a finite field is q. Each field element represents an equivalence class, or a collection of elements with common properties. For finite fields GF (p), all the integers that are congruent to each other modulo p represent an equivalence class. Two elements a and b are congruent if they generate the same remainder r [0, p) when divided by p. The congruence relation is represented here as a b mod p, where a b mod p if a = s p + r, b = t p + r, and s and t are two arbitrary integers. The elements of a 10
33 field are often represented by their least positive residue, which are integers in the range [0, p). For finite fields GF (p m ), where p is prime and m is greater than one, this work uses standard (or polynomial) basis representation. In this representation all polynomials G(α) = i=0 a iα i with a i GF (p), which are congruent to each other modulo F (α), represent an equivalence class. F (x) = x m + m 1 i=0 f ix i with f i GF (p) is an irreducible polynomial over the field GF (p); that is, a polynomial that is only divisible by itself or an element of the field GF (p) over the field GF (p). α is a root of the irreducible polynomial in GF (p m ) that does not belong to the field GF (p). Two elements A = n a i=0 a iα i and B = n b i=0 b iα i of GF (p m ) are congruent if when divided by the polynomial F (α) they generate the same remainder R = m 1 i=0 r iα i of degree lower than the degree of F (x) (a i, b i, r i GF (p)). The congruence relation for GF (p m ) is represented here as A B mod F (α), where A = S F (α) + R, B = T F (α) + R, and where S = n s i=0 s iα i and T = nt i=0 t iα i are two arbitrary polynomials with coefficients in GF (p). The elements of a field GF (p) are represented here by the polynomials of least degree in their equivalence class. Using this representation, the elements of a field are represented with polynomials of degree lower than that of F (x). Arithmetic in fields GF (p m ) using standard basis representation is analogous to polynomial arithmetic with the added restriction that the operations involving coefficients are handled as finite fields operation in the field GF (p). Of importance in this work are finite fields GF (p) with primes p greater than three and the fields GF (2 m ). The fields GF (p) are often referred to as prime fields and the fields GF (2 m ) are often referred to as binary fields. 11
34 2.2 GF(p) Arithmetic Background This section provides a brief introduction to GF (p) field arithmetic. For additional information on this subject the reader is referred to [McE87, LN94]. For the computation of elliptic curves point multiplications, an elliptic curve processor must be capable of computing modular additions, subtractions, multiplications, and inverses. Addition is the simplest modular operation that an elliptic curve processor needs to implement. The addition of two field elements a and b, where a, b [0, p), can be computed in two steps. The first step adds the two operands. The second step reduces the result by subtracting p from a + b, if this result is greater than or equal to p. The operation just described can be extended to modular subtractions. Multiplication, including squaring, is the most critical operation in the computation of elliptic curve point multiplications. The multiplication of two element a, b [0, p) yields a result ab [0, (p 1) 2 ]. The reduction of this result can be performed with a division: ab mod p (qp + r) mod p r mod p, where q = ab/p and r = ab qp [0, p) (q represents the quotient and r the remainder of the division). Division is more complex than multiplication. Division requires quotient estimation, multiplications, and additions. Modern reduction algorithms, such as Montgomery reduction, yield approximated results. These methods trade accuracy for speed. The approximated results are of the form r + ɛp, where ɛ 0 defines the approximation accuracy. These results are congruent modulo p to the desired result r. For the elliptic curve processor for GF (p) introduced here, this work recommends the use of Montgomery multiplication. Montgomery multiplication interleaves mul- 12
35 tiplication and reduction steps. The computational cost of Montgomery multiplication is approximately equal to the computational cost of two multiplications when assuming that these multiplications are done using the schoolbook multiplication method. The following section provides a brief introduction to Montgomery reduction. The version of the Montgomery multiplication algorithm of interest here is presented in Sections 5.2. Inversion is the most complex operation that an elliptic processor must implement. This work focuses on the computation of inverses using Fermat s Little Theorem (this is the same approach used here for GF (2 m )). Equation (2.1) shows the expression used here to compute inverses (GF (p) represents the multiplicative group of GF (p)). a 1 mod p a p 2 mod p for a GF (p) (2.1) The bit-complexities of the arithmetic operations that must be implemented by an elliptic curve processor are summarized in Table 2.1. This table assumes that the field elements are represented by m-bit numbers (m = log 2 p ), that multiplications are computed using the Montgomery multiplication algorithm, and that inversions are computed according to Equation (2.1) using the Montgomery multiplication algorithm Montgomery Reduction This section provides a brief introduction to Montgomery reduction. For additional information on this topic, readers are referred to the following references: [Mon85, MvOV97, BSS99, KAK96]. 13
36 Table 2.1: Complexity of GF (p) arithmetic operations GF (p) operation Bit-complexity Addition O(m) Multiplication O(m 2 ) (Montgomery mult.) Inverse O(m 3 ) (Fermat s Little Theorem & Montgomery mult.) The GF (p) multiplier introduced here uses what is known as Montgomery reduction. This reduction method was introduced in [Mon85]. The Montgomery reduction of a number x < RM using the algorithm introduced in [Mon85] yields a weighted residue of the form xr 1 mod M [0, 2M). R is a constant such that R > M and gcd(r, M) = 1, which is arbitrarily chosen so that it simplifies the reduction process: a power of two for hardware implementations. M represents the modulus of operation (M = p for GF (p)). The following sections use M to represent the modulus when discussing aspects related to Montgomery multiplication. The effectiveness of Montgomery reduction lies on performing arithmetic using weighted residues of the form xr mod M rather than x mod M itself. These residues are referred to here as Montgomery residues. The basic idea is to perform a transformation at the beginning of an algorithm, such as exponentiation, then perform arithmetic using Montgomery residues, and, at the end of the algorithm, transform the results back to residues that are not weighted. For example, the computation of the exponentiation x e mod M involves the following steps: 1. Computation of the residue xr mod M. 2. Computation of the exponentiation (xr mod M) e mod M using multiplications and Montgomery reductions. (Note that the Montgomery reduction of a product (xr mod M)(yR mod M) yields the Montgomery residue xyr mod 14
37 M.) 3. Conversion of the result (x e )R mod M to x e mod M. 4. If necessary, reduction of x e mod M to obtain result in least residue representation (i.e., a result in the range [0, M)). The previous example demonstrates a common use of Montgomery residues. Note that the arithmetic operations involving Montgomery residues are not limited to multiplication; addition, subtraction, negation, equality/inequality testing, and greatest common divisor computations involving M, can all be done using Montgomery residues [Mon85]. Note that the transformation of x mod M into xr mod M can be performed by multiplying x mod M by R 2 mod M and then reducing the result using Montgomery reduction [Mon85]. (Note that the constant R 2 mod M needs to be computed only once for a given modulus and that standards that specify the use of elliptic curve cryptography change these infrequently; for example, [FIP00] specifies a set of moduli for the foreseeable future). The conversion of a result xr mod M into x mod M can be performed by multiplying xr mod M by one and then reducing the result using Montgomery reduction (((xr mod M) 1)R 1 mod M x mod M) [Mon85]. The reduction in Step 4 may be needed when the result of the Montgomery reduction exceeds the value of M. 15
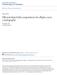
38 2.3 GF(2 m ) Arithmetic Background This section provides a brief introduction to GF (2 m ) field arithmetic. For additional information on this subject the reader is referred to [McE87, LN94]. This work considers arithmetic in fields of characteristic two, GF (2 m ), using a standard basis representation. A field GF (2 m ) is isomorphic to GF (2)[x]/(F (x)), where F (x) = x m + t i=0 f ix i is a monic irreducible polynomial of degree m with coefficients f i {0, 1}. Here each residue class is represented by the polynomial of least degree in its class. A standard basis representation uses the basis defined by the set of elements {1, α, α 2,..., α m 1 }, where α is a root of the irreducible polynomial F (x). In this basis, field elements are represented as polynomials in α of degree less than m with coefficients 0 or 1; for example, an element A is represented as A = m 1 i=0 a iα i with coefficients a i {0, 1}. The addition of two elements A = m 1 i=0 a iα i and B = m 1 i=0 b iα i, as shown by Equation (2.2), requires the modulo 2 addition of the coefficients of the two field elements. m 1 A + B mod F (α) = (a i + b i mod 2)α i (2.2) i=0 The multiplication of two field elements A = m 1 i=0 a iα i and B = m 1 i=0 b iα i is defined by Equation (2.3). This equation expresses the multiplication operation in a way that resembles the operation of the multipliers studied here. These multipliers accumulate products of digits of the multiplier B and the multiplicand A. The reductions modulo F (α) are computed using Equation (2.4). 16
U k-2. U k-1 V 1. V k-1. W k-1 W 1 P 1. P k-1
 A Super-Serial Galois Fields Multiplier for FPGAs and its Application to Public-Key Algorithms Gerardo Orlando Christof Paar GTE Government Systems ECE Department 77 A. St. Worcester Polytechnic Institute
A Super-Serial Galois Fields Multiplier for FPGAs and its Application to Public-Key Algorithms Gerardo Orlando Christof Paar GTE Government Systems ECE Department 77 A. St. Worcester Polytechnic Institute
Dual-Field Arithmetic Unit for GF (p) and GF (2 m )
 Dual-Field Arithmetic Unit for GF (p) and GF (2 m ) Johannes Wolkerstorfer Institute for Applied Information Processing and Communications, Graz University of Technology, Inffeldgasse 16a, 8010 Graz, Austria
Dual-Field Arithmetic Unit for GF (p) and GF (2 m ) Johannes Wolkerstorfer Institute for Applied Information Processing and Communications, Graz University of Technology, Inffeldgasse 16a, 8010 Graz, Austria
Cryptography and Network Security
 Cryptography and Network Security CRYPTOGRAPHY AND NETWORK SECURITY PRAKASH C. GUPTA Former Head Department of Information Technology Maharashtra Institute of Technology Pune Delhi-110092 2015 CRYPTOGRAPHY
Cryptography and Network Security CRYPTOGRAPHY AND NETWORK SECURITY PRAKASH C. GUPTA Former Head Department of Information Technology Maharashtra Institute of Technology Pune Delhi-110092 2015 CRYPTOGRAPHY
HIGH PERFORMANCE ELLIPTIC CURVE CRYPTO-PROCESSOR FOR FPGA PLATFORMS
 HIGH PERFORMANCE ELLIPTIC CURVE CRYPTO-PROCESSOR FOR FPGA PLATFORMS Debdeep Mukhopadhyay Dept. of Computer Science and Engg. IIT Kharagpur 3/6/2010 NTT Labs, Japan 1 Outline Elliptic Curve Cryptography
HIGH PERFORMANCE ELLIPTIC CURVE CRYPTO-PROCESSOR FOR FPGA PLATFORMS Debdeep Mukhopadhyay Dept. of Computer Science and Engg. IIT Kharagpur 3/6/2010 NTT Labs, Japan 1 Outline Elliptic Curve Cryptography
Scalable Montgomery Multiplication Algorithm
 1 Scalable Montgomery Multiplication Algorithm Brock J. Prince Department of Electrical & Computer Engineering, Oregon State University, Corvallis, Oregon 97331 E-mail: princebr@engr.orst.edu May 29, 2002
1 Scalable Montgomery Multiplication Algorithm Brock J. Prince Department of Electrical & Computer Engineering, Oregon State University, Corvallis, Oregon 97331 E-mail: princebr@engr.orst.edu May 29, 2002
TABLE OF CONTENTS CHAPTER NO. TITLE PAGE NO.
 vii TABLE OF CONTENTS CHAPTER NO. TITLE PAGE NO. ABSTRACT LIST OF TABLES LIST OF FIGURES LIST OF SYMBOLS AND ABBREVIATION iii xii xiv xvii 1 INTRODUCTION 1 1.1 GENERAL 1 1.2 TYPES OF WIRELESS COMMUNICATION
vii TABLE OF CONTENTS CHAPTER NO. TITLE PAGE NO. ABSTRACT LIST OF TABLES LIST OF FIGURES LIST OF SYMBOLS AND ABBREVIATION iii xii xiv xvii 1 INTRODUCTION 1 1.1 GENERAL 1 1.2 TYPES OF WIRELESS COMMUNICATION
Elliptic Curves over Prime and Binary Fields in Cryptography
 Elliptic Curves over Prime and Binary Fields in Cryptography Authors Dana Neustadter (danan@ellipticsemi.com) Tom St Denis (tstdenis@ellipticsemi.com) Copyright 2008 Elliptic Semiconductor Inc. Elliptic
Elliptic Curves over Prime and Binary Fields in Cryptography Authors Dana Neustadter (danan@ellipticsemi.com) Tom St Denis (tstdenis@ellipticsemi.com) Copyright 2008 Elliptic Semiconductor Inc. Elliptic
ECC Elliptic Curve Cryptography. Foundations of Cryptography - ECC pp. 1 / 31
 ECC Elliptic Curve Cryptography Foundations of Cryptography - ECC pp. 1 / 31 Elliptic Curve an elliptic curve E is a smooth, projective, algebraic curve defined by the following equation: y 2 3 2 a xy
ECC Elliptic Curve Cryptography Foundations of Cryptography - ECC pp. 1 / 31 Elliptic Curve an elliptic curve E is a smooth, projective, algebraic curve defined by the following equation: y 2 3 2 a xy
Bipartite Modular Multiplication
 Bipartite Modular Multiplication Marcelo E. Kaihara and Naofumi Takagi Department of Information Engineering, Nagoya University, Nagoya, 464-8603, Japan {mkaihara, ntakagi}@takagi.nuie.nagoya-u.ac.jp Abstract.
Bipartite Modular Multiplication Marcelo E. Kaihara and Naofumi Takagi Department of Information Engineering, Nagoya University, Nagoya, 464-8603, Japan {mkaihara, ntakagi}@takagi.nuie.nagoya-u.ac.jp Abstract.
Low Power Elliptic Curve Cryptography
 Low Power Elliptic Curve Cryptography by Erdinç Öztürk A Thesis Submitted to the Faculty of the Worcester Polytechnic Institute in partial fulfillment of the requirements for the Degree of Master of Science
Low Power Elliptic Curve Cryptography by Erdinç Öztürk A Thesis Submitted to the Faculty of the Worcester Polytechnic Institute in partial fulfillment of the requirements for the Degree of Master of Science
SEC 1: Elliptic Curve Cryptography
 Standards for Efficient Cryptography SEC 1: Elliptic Curve Cryptography Contact: Certicom Research Daniel R. L. Brown (dbrown@certicom.com) May 21, 2009 Version 2.0 c 2009 Certicom Corp. License to copy
Standards for Efficient Cryptography SEC 1: Elliptic Curve Cryptography Contact: Certicom Research Daniel R. L. Brown (dbrown@certicom.com) May 21, 2009 Version 2.0 c 2009 Certicom Corp. License to copy
Novel Approach Design of Elliptic curve Cryptography Implementation in VLSI
 Novel Approach Design of Elliptic curve Cryptography Implementation in VLSI V. CHANDRASEKARAN Department of Electronics and Communication Engineering Central Polytechnic College Chennai 113, INDIA N.NAGARAJAN
Novel Approach Design of Elliptic curve Cryptography Implementation in VLSI V. CHANDRASEKARAN Department of Electronics and Communication Engineering Central Polytechnic College Chennai 113, INDIA N.NAGARAJAN
Understanding Cryptography by Christof Paar and Jan Pelzl. Chapter 9 Elliptic Curve Cryptography
 Understanding Cryptography by Christof Paar and Jan Pelzl www.crypto-textbook.com Chapter 9 Elliptic Curve Cryptography ver. February 2nd, 2015 These slides were prepared by Tim Güneysu, Christof Paar
Understanding Cryptography by Christof Paar and Jan Pelzl www.crypto-textbook.com Chapter 9 Elliptic Curve Cryptography ver. February 2nd, 2015 These slides were prepared by Tim Güneysu, Christof Paar
A High-Speed FPGA Implementation of an RSD- Based ECC Processor
 A High-Speed FPGA Implementation of an RSD- Based ECC Processor Abstract: In this paper, an exportable application-specific instruction-set elliptic curve cryptography processor based on redundant signed
A High-Speed FPGA Implementation of an RSD- Based ECC Processor Abstract: In this paper, an exportable application-specific instruction-set elliptic curve cryptography processor based on redundant signed
An Optimized Montgomery Modular Multiplication Algorithm for Cryptography
 118 IJCSNS International Journal of Computer Science and Network Security, VOL.13 No.1, January 2013 An Optimized Montgomery Modular Multiplication Algorithm for Cryptography G.Narmadha 1 Asst.Prof /ECE,
118 IJCSNS International Journal of Computer Science and Network Security, VOL.13 No.1, January 2013 An Optimized Montgomery Modular Multiplication Algorithm for Cryptography G.Narmadha 1 Asst.Prof /ECE,
Realizing Arbitrary-Precision Modular Multiplication with a Fixed-Precision Multiplier Datapath
 Realizing Arbitrary-Precision Modular Multiplication with a Fixed-Precision Multiplier Datapath Johann Großschädl University of Luxembourg johann.groszschaedl@uni.lu Erkay Savaş Sabanci University, Turkey
Realizing Arbitrary-Precision Modular Multiplication with a Fixed-Precision Multiplier Datapath Johann Großschädl University of Luxembourg johann.groszschaedl@uni.lu Erkay Savaş Sabanci University, Turkey
This chapter continues our overview of public-key cryptography systems (PKCSs), and begins with a description of one of the earliest and simplest
 1 2 3 This chapter continues our overview of public-key cryptography systems (PKCSs), and begins with a description of one of the earliest and simplest PKCS, Diffie- Hellman key exchange. This first published
1 2 3 This chapter continues our overview of public-key cryptography systems (PKCSs), and begins with a description of one of the earliest and simplest PKCS, Diffie- Hellman key exchange. This first published
A High-Speed FPGA Implementation of an RSD-Based ECC Processor
 RESEARCH ARTICLE International Journal of Engineering and Techniques - Volume 4 Issue 1, Jan Feb 2018 A High-Speed FPGA Implementation of an RSD-Based ECC Processor 1 K Durga Prasad, 2 M.Suresh kumar 1
RESEARCH ARTICLE International Journal of Engineering and Techniques - Volume 4 Issue 1, Jan Feb 2018 A High-Speed FPGA Implementation of an RSD-Based ECC Processor 1 K Durga Prasad, 2 M.Suresh kumar 1
High-Performance Modular Multiplication on the Cell Broadband Engine
 High-Performance Modular Multiplication on the Cell Broadband Engine Joppe W. Bos Laboratory for Cryptologic Algorithms EPFL, Lausanne, Switzerland joppe.bos@epfl.ch 1 / 21 Outline Motivation and previous
High-Performance Modular Multiplication on the Cell Broadband Engine Joppe W. Bos Laboratory for Cryptologic Algorithms EPFL, Lausanne, Switzerland joppe.bos@epfl.ch 1 / 21 Outline Motivation and previous
About the Author. Dependency Chart. Chapter 1: Logic and Sets 1. Chapter 2: Relations and Functions, Boolean Algebra, and Circuit Design
 Preface About the Author Dependency Chart xiii xix xxi Chapter 1: Logic and Sets 1 1.1: Logical Operators: Statements and Truth Values, Negations, Conjunctions, and Disjunctions, Truth Tables, Conditional
Preface About the Author Dependency Chart xiii xix xxi Chapter 1: Logic and Sets 1 1.1: Logical Operators: Statements and Truth Values, Negations, Conjunctions, and Disjunctions, Truth Tables, Conditional
Low-Power Elliptic Curve Cryptography Using Scaled Modular Arithmetic
 Low-Power Elliptic Curve Cryptography Using Scaled Modular Arithmetic E. Öztürk1, B. Sunar 1, and E. Savaş 2 1 Department of Electrical & Computer Engineering, Worcester Polytechnic Institute, Worcester
Low-Power Elliptic Curve Cryptography Using Scaled Modular Arithmetic E. Öztürk1, B. Sunar 1, and E. Savaş 2 1 Department of Electrical & Computer Engineering, Worcester Polytechnic Institute, Worcester
Multifunction Residue Architectures for Cryptography 1
 Multifunction Residue Architectures for Cryptography 1 LAXMI TRIVENI.D, M.TECH., EMBEDDED SYSTEMS & VLSI 2 P.V.VARAPRASAD,RAO ASSOCIATE PROFESSOR., SLC S INSTITUTE OF ENGINEERING AND TECHNOLOGY Abstract
Multifunction Residue Architectures for Cryptography 1 LAXMI TRIVENI.D, M.TECH., EMBEDDED SYSTEMS & VLSI 2 P.V.VARAPRASAD,RAO ASSOCIATE PROFESSOR., SLC S INSTITUTE OF ENGINEERING AND TECHNOLOGY Abstract
Versatile Montgomery Multiplier Architectures
 Versatile Montgomery Multiplier Architectures by Gunnar Gaubatz A Thesis Submitted to the Faculty of the Worcester Polytechnic Institute in partial fulfillment of the requirements for the Degree of Master
Versatile Montgomery Multiplier Architectures by Gunnar Gaubatz A Thesis Submitted to the Faculty of the Worcester Polytechnic Institute in partial fulfillment of the requirements for the Degree of Master
Applications of The Montgomery Exponent
 Applications of The Montgomery Exponent Shay Gueron 1,3 1 Dept. of Mathematics, University of Haifa, Israel (shay@math.haifa.ac.il) Or Zuk 2,3 2 Dept. of Physics of Complex Systems, Weizmann Institute
Applications of The Montgomery Exponent Shay Gueron 1,3 1 Dept. of Mathematics, University of Haifa, Israel (shay@math.haifa.ac.il) Or Zuk 2,3 2 Dept. of Physics of Complex Systems, Weizmann Institute
Key Management and Distribution
 CPE 542: CRYPTOGRAPHY & NETWORK SECURITY Chapter 10 Key Management; Other Public Key Cryptosystems Dr. Lo ai Tawalbeh Computer Engineering Department Jordan University of Science and Technology Jordan
CPE 542: CRYPTOGRAPHY & NETWORK SECURITY Chapter 10 Key Management; Other Public Key Cryptosystems Dr. Lo ai Tawalbeh Computer Engineering Department Jordan University of Science and Technology Jordan
Faster Interleaved Modular Multiplier Based on Sign Detection
 Faster Interleaved Modular Multiplier Based on Sign Detection Mohamed A. Nassar, and Layla A. A. El-Sayed Department of Computer and Systems Engineering, Alexandria University, Alexandria, Egypt eng.mohamedatif@gmail.com,
Faster Interleaved Modular Multiplier Based on Sign Detection Mohamed A. Nassar, and Layla A. A. El-Sayed Department of Computer and Systems Engineering, Alexandria University, Alexandria, Egypt eng.mohamedatif@gmail.com,
- 0 - CryptoLib: Cryptography in Software John B. Lacy 1 Donald P. Mitchell 2 William M. Schell 3 AT&T Bell Laboratories ABSTRACT
 - 0 - CryptoLib: Cryptography in Software John B. Lacy 1 Donald P. Mitchell 2 William M. Schell 3 AT&T Bell Laboratories ABSTRACT With the capacity of communications channels increasing at the current
- 0 - CryptoLib: Cryptography in Software John B. Lacy 1 Donald P. Mitchell 2 William M. Schell 3 AT&T Bell Laboratories ABSTRACT With the capacity of communications channels increasing at the current
c 2006 by CRC Press, LLC.
 This is the of the Handbook of Elliptic and Hyperelliptic Curve Cryptography, Henri Cohen, Christophe Doche, and Gerhard Frey, Editors, CRC Press 2006. CRC Press has granted the following specific permissions
This is the of the Handbook of Elliptic and Hyperelliptic Curve Cryptography, Henri Cohen, Christophe Doche, and Gerhard Frey, Editors, CRC Press 2006. CRC Press has granted the following specific permissions
Parallelized Radix-4 Scalable Montgomery Multipliers
 Parallelized Radix-4 Scalable Montgomery Multipliers Nathaniel Pinckney and David Money Harris 1 1 Harvey Mudd College, 301 Platt. Blvd., Claremont, CA, USA e-mail: npinckney@hmc.edu ABSTRACT This paper
Parallelized Radix-4 Scalable Montgomery Multipliers Nathaniel Pinckney and David Money Harris 1 1 Harvey Mudd College, 301 Platt. Blvd., Claremont, CA, USA e-mail: npinckney@hmc.edu ABSTRACT This paper
Elliptic Curve Cryptography. Implementation and Performance Testing of Curve Representations
 Elliptic Curve Cryptography Implementation and Performance Testing of Curve Representations Olav Wegner Eide Master s Thesis Spring 2017 Elliptic Curve Cryptography Implementation and Performance Testing
Elliptic Curve Cryptography Implementation and Performance Testing of Curve Representations Olav Wegner Eide Master s Thesis Spring 2017 Elliptic Curve Cryptography Implementation and Performance Testing
Dr. Jinyuan (Stella) Sun Dept. of Electrical Engineering and Computer Science University of Tennessee Fall 2010
 CS 494/594 Computer and Network Security Dr. Jinyuan (Stella) Sun Dept. of Electrical Engineering and Computer Science University of Tennessee Fall 2010 1 Public Key Cryptography Modular Arithmetic RSA
CS 494/594 Computer and Network Security Dr. Jinyuan (Stella) Sun Dept. of Electrical Engineering and Computer Science University of Tennessee Fall 2010 1 Public Key Cryptography Modular Arithmetic RSA
An Algorithm and Hardware Architecture for Integrated Modular Division and Multiplication in GF (p) and GF (2 n )
 An Algorithm and Hardware Architecture for Integrated Modular Division and Multiplication in GF (p) and GF (2 n ) Lo ai A. Tawalbeh and Alexandre F. Tenca School of Electrical Engineering and Computer
An Algorithm and Hardware Architecture for Integrated Modular Division and Multiplication in GF (p) and GF (2 n ) Lo ai A. Tawalbeh and Alexandre F. Tenca School of Electrical Engineering and Computer
Channel Coding and Cryptography Part II: Introduction to Cryptography
 Channel Coding and Cryptography Part II: Introduction to Cryptography Prof. Dr.-Ing. habil. Andreas Ahrens Communications Signal Processing Group, University of Technology, Business and Design Email: andreas.ahrens@hs-wismar.de
Channel Coding and Cryptography Part II: Introduction to Cryptography Prof. Dr.-Ing. habil. Andreas Ahrens Communications Signal Processing Group, University of Technology, Business and Design Email: andreas.ahrens@hs-wismar.de
A Binary Redundant Scalar Point Multiplication in Secure Elliptic Curve Cryptosystems
 International Journal of Network Security, Vol3, No2, PP132 137, Sept 2006 (http://ijnsnchuedutw/) 132 A Binary Redundant Scalar Multiplication in Secure Elliptic Curve Cryptosystems Sangook Moon School
International Journal of Network Security, Vol3, No2, PP132 137, Sept 2006 (http://ijnsnchuedutw/) 132 A Binary Redundant Scalar Multiplication in Secure Elliptic Curve Cryptosystems Sangook Moon School
Comparison of Algorithms for Elliptic Curve Cryptography over Finite Fields of GF(2 m )
 Comparison of Algorithms for Elliptic Curve Cryptography over Finite Fields of GF( m ) The IASTED International Conference on Communication, Network, and Information Security CNIS 003, December -1, 003
Comparison of Algorithms for Elliptic Curve Cryptography over Finite Fields of GF( m ) The IASTED International Conference on Communication, Network, and Information Security CNIS 003, December -1, 003
Low-Power FIR Digital Filters Using Residue Arithmetic
 Low-Power FIR Digital Filters Using Residue Arithmetic William L. Freking and Keshab K. Parhi Department of Electrical and Computer Engineering University of Minnesota 200 Union St. S.E. Minneapolis, MN
Low-Power FIR Digital Filters Using Residue Arithmetic William L. Freking and Keshab K. Parhi Department of Electrical and Computer Engineering University of Minnesota 200 Union St. S.E. Minneapolis, MN
ECC1 Core. Elliptic Curve Point Multiply and Verify Core. General Description. Key Features. Applications. Symbol
 General Description Key Features Elliptic Curve Cryptography (ECC) is a public-key cryptographic technology that uses the mathematics of so called elliptic curves and it is a part of the Suite B of cryptographic
General Description Key Features Elliptic Curve Cryptography (ECC) is a public-key cryptographic technology that uses the mathematics of so called elliptic curves and it is a part of the Suite B of cryptographic
Studies on Modular Arithmetic Hardware Algorithms for Public-key Cryptography
 Studies on Modular Arithmetic Hardware Algorithms for Public-key Cryptography Marcelo Emilio Kaihara Graduate School of Information Science Nagoya University January 2006 iii Dedicated to my father. Abstract
Studies on Modular Arithmetic Hardware Algorithms for Public-key Cryptography Marcelo Emilio Kaihara Graduate School of Information Science Nagoya University January 2006 iii Dedicated to my father. Abstract
ARITHMETIC operations based on residue number systems
 IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS II: EXPRESS BRIEFS, VOL. 53, NO. 2, FEBRUARY 2006 133 Improved Memoryless RNS Forward Converter Based on the Periodicity of Residues A. B. Premkumar, Senior Member,
IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS II: EXPRESS BRIEFS, VOL. 53, NO. 2, FEBRUARY 2006 133 Improved Memoryless RNS Forward Converter Based on the Periodicity of Residues A. B. Premkumar, Senior Member,
Software Implementations of Elliptic Curve Cryptography
 Software Implementations of Elliptic Curve Cryptography Aneel Murari ECE679 Oregon State university June 9, 2003 Abstract Elliptic Curve Cyrptography has gained a lot of significance in recent times. This
Software Implementations of Elliptic Curve Cryptography Aneel Murari ECE679 Oregon State university June 9, 2003 Abstract Elliptic Curve Cyrptography has gained a lot of significance in recent times. This
An Efficient Pipelined Multiplicative Inverse Architecture for the AES Cryptosystem
 An Efficient Pipelined Multiplicative Inverse Architecture for the AES Cryptosystem Mostafa Abd-El-Barr and Amro Khattab Abstract In this paper, we introduce an architecture for performing a recursive
An Efficient Pipelined Multiplicative Inverse Architecture for the AES Cryptosystem Mostafa Abd-El-Barr and Amro Khattab Abstract In this paper, we introduce an architecture for performing a recursive
EECS150 - Digital Design Lecture 13 - Combinational Logic & Arithmetic Circuits Part 3
 EECS15 - Digital Design Lecture 13 - Combinational Logic & Arithmetic Circuits Part 3 October 8, 22 John Wawrzynek Fall 22 EECS15 - Lec13-cla3 Page 1 Multiplication a 3 a 2 a 1 a Multiplicand b 3 b 2 b
EECS15 - Digital Design Lecture 13 - Combinational Logic & Arithmetic Circuits Part 3 October 8, 22 John Wawrzynek Fall 22 EECS15 - Lec13-cla3 Page 1 Multiplication a 3 a 2 a 1 a Multiplicand b 3 b 2 b
Elliptic Curve Cryptography (ECC) Elliptic Curve Cryptography. Elliptic Curves. Elliptic Curve Cryptography (ECC) Elliptic curve
 Elliptic Curve Cryptography Gerardo Pelosi Dipartimento di Elettronica, Informazione e Bioingegneria (DEIB) Politecnico di Milano gerardo.pelosi - at - polimi.it ECC was introduced by Victor Miller and
Elliptic Curve Cryptography Gerardo Pelosi Dipartimento di Elettronica, Informazione e Bioingegneria (DEIB) Politecnico di Milano gerardo.pelosi - at - polimi.it ECC was introduced by Victor Miller and
Prime Field over Elliptic Curve Cryptography for Secured Message Transaction
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology ISSN 2320 088X IMPACT FACTOR: 5.258 IJCSMC,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology ISSN 2320 088X IMPACT FACTOR: 5.258 IJCSMC,
A Scalable Architecture for Montgomery Multiplication
 A Scalable Architecture for Montgomery Multiplication Alexandre F. Tenca and Çetin K. Koç Electrical & Computer Engineering Oregon State University, Corvallis, Oregon 97331 {tenca,koc}@ece.orst.edu Abstract.
A Scalable Architecture for Montgomery Multiplication Alexandre F. Tenca and Çetin K. Koç Electrical & Computer Engineering Oregon State University, Corvallis, Oregon 97331 {tenca,koc}@ece.orst.edu Abstract.
Studying Software Implementations of Elliptic Curve Cryptography
 Studying Software Implementations of Elliptic Curve Cryptography Hai Yan and Zhijie Jerry Shi Department of Computer Science and Engineering, University of Connecticut Abstract Elliptic Curve Cryptography
Studying Software Implementations of Elliptic Curve Cryptography Hai Yan and Zhijie Jerry Shi Department of Computer Science and Engineering, University of Connecticut Abstract Elliptic Curve Cryptography
Novel Multiplier Architectures for GF (p) andgf (2 n )
 Novel Multiplier Architectures for GF (p) andgf (2 n ) E. Savaş 1,A.F.Tenca 2,M.E.Çiftçibasi 3,andÇ. K. Koç 2 1 Faculty of Engineering and Natural Sciences Sabanci University Istanbul, Turkey TR-34956
Novel Multiplier Architectures for GF (p) andgf (2 n ) E. Savaş 1,A.F.Tenca 2,M.E.Çiftçibasi 3,andÇ. K. Koç 2 1 Faculty of Engineering and Natural Sciences Sabanci University Istanbul, Turkey TR-34956
Flexible FPGA-Based Architectures for Curve Point Multiplication over GF(p)
 016 Euromicro Conference on Digital System Design Flexible FPGA-Based Architectures for Curve Point Multiplication over GF(p) Dorian Amiet IMES Institut für Miroeletroni und Embedded Systems HSR Hochschule
016 Euromicro Conference on Digital System Design Flexible FPGA-Based Architectures for Curve Point Multiplication over GF(p) Dorian Amiet IMES Institut für Miroeletroni und Embedded Systems HSR Hochschule
Fast Multiplication on Elliptic Curves over GF (2 m ) without Precomputation
 Fast Multiplication on Elliptic Curves over GF (2 m ) without Precomputation Julio López 1 and Ricardo Dahab 2 1 Department of Combinatorics & Optimization University of Waterloo, Waterloo, Ontario N2L
Fast Multiplication on Elliptic Curves over GF (2 m ) without Precomputation Julio López 1 and Ricardo Dahab 2 1 Department of Combinatorics & Optimization University of Waterloo, Waterloo, Ontario N2L
CS669 Network Security
 UNIT II PUBLIC KEY ENCRYPTION Uniqueness Number Theory concepts Primality Modular Arithmetic Fermet & Euler Theorem Euclid Algorithm RSA Elliptic Curve Cryptography Diffie Hellman Key Exchange Uniqueness
UNIT II PUBLIC KEY ENCRYPTION Uniqueness Number Theory concepts Primality Modular Arithmetic Fermet & Euler Theorem Euclid Algorithm RSA Elliptic Curve Cryptography Diffie Hellman Key Exchange Uniqueness
A Scalable and High Performance Elliptic Curve Processor with Resistance to Timing Attacks
 A Scalable and High Performance Elliptic Curve Processor with Resistance to Timing Attacks Alireza Hodjat, David D. Hwang, Ingrid Verbauwhede, University of California, Los Angeles Katholieke Universiteit
A Scalable and High Performance Elliptic Curve Processor with Resistance to Timing Attacks Alireza Hodjat, David D. Hwang, Ingrid Verbauwhede, University of California, Los Angeles Katholieke Universiteit
Efficient finite field computations for elliptic curve cryptography
 University of Windsor Scholarship at UWindsor Electronic Theses and Dissertations Winter 2014 Efficient finite field computations for elliptic curve cryptography Wangchen Dai University of Windsor Follow
University of Windsor Scholarship at UWindsor Electronic Theses and Dissertations Winter 2014 Efficient finite field computations for elliptic curve cryptography Wangchen Dai University of Windsor Follow
SCHOOL OF ENGINEERING & BUILT ENVIRONMENT. Mathematics. Numbers & Number Systems
 SCHOOL OF ENGINEERING & BUILT ENVIRONMENT Mathematics Numbers & Number Systems Introduction Numbers and Their Properties Multiples and Factors The Division Algorithm Prime and Composite Numbers Prime Factors
SCHOOL OF ENGINEERING & BUILT ENVIRONMENT Mathematics Numbers & Number Systems Introduction Numbers and Their Properties Multiples and Factors The Division Algorithm Prime and Composite Numbers Prime Factors
NEW MODIFIED LEFT-TO-RIGHT RADIX-R REPRESENTATION FOR INTEGERS. Arash Eghdamian 1*, Azman Samsudin 1
 International Journal of Technology (2017) 3: 519-527 ISSN 2086-9614 IJTech 2017 NEW MODIFIED LEFT-TO-RIGHT RADIX-R REPRESENTATION FOR INTEGERS Arash Eghdamian 1*, Azman Samsudin 1 1 School of Computer
International Journal of Technology (2017) 3: 519-527 ISSN 2086-9614 IJTech 2017 NEW MODIFIED LEFT-TO-RIGHT RADIX-R REPRESENTATION FOR INTEGERS Arash Eghdamian 1*, Azman Samsudin 1 1 School of Computer
Binary Adders. Ripple-Carry Adder
 Ripple-Carry Adder Binary Adders x n y n x y x y c n FA c n - c 2 FA c FA c s n MSB position Longest delay (Critical-path delay): d c(n) = n d carry = 2n gate delays d s(n-) = (n-) d carry +d sum = 2n
Ripple-Carry Adder Binary Adders x n y n x y x y c n FA c n - c 2 FA c FA c s n MSB position Longest delay (Critical-path delay): d c(n) = n d carry = 2n gate delays d s(n-) = (n-) d carry +d sum = 2n
ECE 646 Fall 2009 Final Exam December 15, Multiple-choice test
 ECE 646 Fall 2009 Final Exam December 15, 2009 Multiple-choice test 1. (1 pt) Parallel processing can be used to speed up the following cryptographic transformations (please note that multiple answers
ECE 646 Fall 2009 Final Exam December 15, 2009 Multiple-choice test 1. (1 pt) Parallel processing can be used to speed up the following cryptographic transformations (please note that multiple answers
CHAPTER 1 INTRODUCTION
 1 CHAPTER 1 INTRODUCTION 1.1 Advance Encryption Standard (AES) Rijndael algorithm is symmetric block cipher that can process data blocks of 128 bits, using cipher keys with lengths of 128, 192, and 256
1 CHAPTER 1 INTRODUCTION 1.1 Advance Encryption Standard (AES) Rijndael algorithm is symmetric block cipher that can process data blocks of 128 bits, using cipher keys with lengths of 128, 192, and 256
Arithmetic Processing
 CS/EE 5830/6830 VLSI ARCHITECTURE Chapter 1 Basic Number Representations and Arithmetic Algorithms Arithmetic Processing AP = (operands, operation, results, conditions, singularities) Operands are: Set
CS/EE 5830/6830 VLSI ARCHITECTURE Chapter 1 Basic Number Representations and Arithmetic Algorithms Arithmetic Processing AP = (operands, operation, results, conditions, singularities) Operands are: Set
High Speed Cryptoprocessor for η T Pairing on 128-bit Secure Supersingular Elliptic Curves over Characteristic Two Fields
 High Speed Cryptoprocessor for η T Pairing on 128-bit Secure Supersingular Elliptic Curves over Characteristic Two Fields Santosh Ghosh, Dipanwita Roy Chowdhury, and Abhijit Das Computer Science and Engineering
High Speed Cryptoprocessor for η T Pairing on 128-bit Secure Supersingular Elliptic Curves over Characteristic Two Fields Santosh Ghosh, Dipanwita Roy Chowdhury, and Abhijit Das Computer Science and Engineering
A SIGNATURE ALGORITHM BASED ON DLP AND COMPUTING SQUARE ROOTS
 A SIGNATURE ALGORITHM BASED ON DLP AND COMPUTING SQUARE ROOTS Ounasser Abid 1 and Omar Khadir 2 1, 2 Laboratory of Mathematics, Cryptography and Mechanics, FSTM University Hassan II of Casablanca, Morocco
A SIGNATURE ALGORITHM BASED ON DLP AND COMPUTING SQUARE ROOTS Ounasser Abid 1 and Omar Khadir 2 1, 2 Laboratory of Mathematics, Cryptography and Mechanics, FSTM University Hassan II of Casablanca, Morocco
My 2 hours today: 1. Efficient arithmetic in finite fields minute break 3. Elliptic curves. My 2 hours tomorrow:
 My 2 hours today: 1. Efficient arithmetic in finite fields 2. 10-minute break 3. Elliptic curves My 2 hours tomorrow: 4. Efficient arithmetic on elliptic curves 5. 10-minute break 6. Choosing curves Efficient
My 2 hours today: 1. Efficient arithmetic in finite fields 2. 10-minute break 3. Elliptic curves My 2 hours tomorrow: 4. Efficient arithmetic on elliptic curves 5. 10-minute break 6. Choosing curves Efficient
Design and Implementation of Low-Complexity Redundant Multiplier Architecture for Finite Field
 Design and Implementation of Low-Complexity Redundant Multiplier Architecture for Finite Field Veerraju kaki Electronics and Communication Engineering, India Abstract- In the present work, a low-complexity
Design and Implementation of Low-Complexity Redundant Multiplier Architecture for Finite Field Veerraju kaki Electronics and Communication Engineering, India Abstract- In the present work, a low-complexity
Serial-Out Bit-level Mastrovito Multipliers for High Speed Hybrid-Double Multiplication Architectures
 Serial-Out Bit-level Mastrovito Multipliers for High Speed Hybrid-Double Multiplication Architectures Mrs Ramya K 1, Anupama H M 2, Anusha M K 3, Manjunath K N 4, Kishore Kumar 5 1 2,3,4,5 -----------------------------------------------------------------------------***---------------------------------------------------------------------------------
Serial-Out Bit-level Mastrovito Multipliers for High Speed Hybrid-Double Multiplication Architectures Mrs Ramya K 1, Anupama H M 2, Anusha M K 3, Manjunath K N 4, Kishore Kumar 5 1 2,3,4,5 -----------------------------------------------------------------------------***---------------------------------------------------------------------------------
Elliptic Curve Cryptography (ECC) Elliptic Curve Cryptography. Elliptic Curves. Elliptic Curve Cryptography (ECC) Elliptic curve
 Elliptic Curve Cryptography Gerardo Pelosi Dipartimento di Elettronica, Informazione e Bioingegneria (DEIB) Politecnico di Milano gerardo.pelosi - at - polimi.it ECC was introduced by Victor Miller and
Elliptic Curve Cryptography Gerardo Pelosi Dipartimento di Elettronica, Informazione e Bioingegneria (DEIB) Politecnico di Milano gerardo.pelosi - at - polimi.it ECC was introduced by Victor Miller and
! Addition! Multiplication! Bigger Example - RSA cryptography
 ! Addition! Multiplication! Bigger Example - RSA cryptography Modular Arithmetic Modular Exponentiation Primality Testing (Fermat s little theorem) Probabilistic algorithm Euclid s Algorithm for gcd (greatest
! Addition! Multiplication! Bigger Example - RSA cryptography Modular Arithmetic Modular Exponentiation Primality Testing (Fermat s little theorem) Probabilistic algorithm Euclid s Algorithm for gcd (greatest
(1) Modular arithmetic
 (1) Modular arithmetic In mathematics, modular arithmetic (sometimes called clock arithmetic) is a system of arithmetic for integers, where numbers "wrap يلتف حولaround " after they reach a certain value
(1) Modular arithmetic In mathematics, modular arithmetic (sometimes called clock arithmetic) is a system of arithmetic for integers, where numbers "wrap يلتف حولaround " after they reach a certain value
Algorithms and arithmetic for the implementation of cryptographic pairings
 Cairn seminar November 29th, 2013 Algorithms and arithmetic for the implementation of cryptographic pairings Nicolas Estibals CAIRN project-team, IRISA Nicolas.Estibals@irisa.fr What is an elliptic curve?
Cairn seminar November 29th, 2013 Algorithms and arithmetic for the implementation of cryptographic pairings Nicolas Estibals CAIRN project-team, IRISA Nicolas.Estibals@irisa.fr What is an elliptic curve?
Understanding Cryptography A Textbook for Students and Practitioners by Christof Paar and Jan Pelzl. Chapter 6 Introduction to Public-Key Cryptography
 Understanding Cryptography A Textbook for Students and Practitioners by Christof Paar and Jan Pelzl www.crypto-textbook.com Chapter 6 Introduction to Public-Key Cryptography ver. November 18, 2010 These
Understanding Cryptography A Textbook for Students and Practitioners by Christof Paar and Jan Pelzl www.crypto-textbook.com Chapter 6 Introduction to Public-Key Cryptography ver. November 18, 2010 These
EE878 Special Topics in VLSI. Computer Arithmetic for Digital Signal Processing
 EE878 Special Topics in VLSI Computer Arithmetic for Digital Signal Processing Part 6c High-Speed Multiplication - III Spring 2017 Koren Part.6c.1 Array Multipliers The two basic operations - generation
EE878 Special Topics in VLSI Computer Arithmetic for Digital Signal Processing Part 6c High-Speed Multiplication - III Spring 2017 Koren Part.6c.1 Array Multipliers The two basic operations - generation
IEEE-754 compliant Algorithms for Fast Multiplication of Double Precision Floating Point Numbers
 International Journal of Research in Computer Science ISSN 2249-8257 Volume 1 Issue 1 (2011) pp. 1-7 White Globe Publications www.ijorcs.org IEEE-754 compliant Algorithms for Fast Multiplication of Double
International Journal of Research in Computer Science ISSN 2249-8257 Volume 1 Issue 1 (2011) pp. 1-7 White Globe Publications www.ijorcs.org IEEE-754 compliant Algorithms for Fast Multiplication of Double
Published by: PIONEER RESEARCH & DEVELOPMENT GROUP (www.prdg.org) 158
 Enhancing The Security Of Koblitz s Method Using Transposition Techniques For Elliptic Curve Cryptography Santoshi Pote Electronics and Communication Engineering, Asso.Professor, SNDT Women s University,
Enhancing The Security Of Koblitz s Method Using Transposition Techniques For Elliptic Curve Cryptography Santoshi Pote Electronics and Communication Engineering, Asso.Professor, SNDT Women s University,
The Application of Elliptic Curves Cryptography in Embedded Systems
 The Application of Elliptic Curves Cryptography in Embedded Systems Wang Qingxian School of Computer Science and Engineering University of Electronic Science and Technology China Introduction to Cryptography
The Application of Elliptic Curves Cryptography in Embedded Systems Wang Qingxian School of Computer Science and Engineering University of Electronic Science and Technology China Introduction to Cryptography
Lecture 2 Algorithms with numbers
 Advanced Algorithms Floriano Zini Free University of Bozen-Bolzano Faculty of Computer Science Academic Year 2013-2014 Lecture 2 Algorithms with numbers 1 RSA Algorithm Why does RSA work? RSA is based
Advanced Algorithms Floriano Zini Free University of Bozen-Bolzano Faculty of Computer Science Academic Year 2013-2014 Lecture 2 Algorithms with numbers 1 RSA Algorithm Why does RSA work? RSA is based
International Journal of Advance Engineering and Research Development
 Scientific Journal of Impact Factor (SJIF): 4.72 International Journal of Advance Engineering and Research Development Volume 4, Issue 8, August -2017 A FAST FPGA DEVELOPMENT OF RSD BASED ECC PROCESSOR
Scientific Journal of Impact Factor (SJIF): 4.72 International Journal of Advance Engineering and Research Development Volume 4, Issue 8, August -2017 A FAST FPGA DEVELOPMENT OF RSD BASED ECC PROCESSOR
Content of this part
 UNIVERSITY OF MASSACHUSETTS Dept. of Electrical & Computer Engineering Introduction to Cryptography ECE 597XX/697XX Part 4 The Advanced Encryption Standard (AES) Israel Koren ECE597/697 Koren Part.4.1
UNIVERSITY OF MASSACHUSETTS Dept. of Electrical & Computer Engineering Introduction to Cryptography ECE 597XX/697XX Part 4 The Advanced Encryption Standard (AES) Israel Koren ECE597/697 Koren Part.4.1
Collision Search for Elliptic Curve Discrete Logarithm over GF(2 m ) with FPGA
 Collision Search for Elliptic Curve Discrete Logarithm over GF(2 m ) with FPGA Workshop on Cryptographic Hardware and Embedded Systems (CHES 2007) September 2007 Guerric Meurice de Dormale*, Philippe Bulens,
Collision Search for Elliptic Curve Discrete Logarithm over GF(2 m ) with FPGA Workshop on Cryptographic Hardware and Embedded Systems (CHES 2007) September 2007 Guerric Meurice de Dormale*, Philippe Bulens,
Hardware Implementation of a Montgomery Modular Multiplier in a Systolic Array
 Hardware Implementation of a Montgomery Modular Multiplier in a Systolic Array Sıddıka Berna Örs 1 Lejla Batina 1,2 Bart Preneel 1 Joos Vandewalle 1 1 Katholieke Universiteit Leuven, ESAT/SCD-COSIC Kasteelpark
Hardware Implementation of a Montgomery Modular Multiplier in a Systolic Array Sıddıka Berna Örs 1 Lejla Batina 1,2 Bart Preneel 1 Joos Vandewalle 1 1 Katholieke Universiteit Leuven, ESAT/SCD-COSIC Kasteelpark
EFFICIENT HARDWARE IMPLEMENTATIONS FOR THE ADVANCED ENCRYPTION STANDARD (AES) ALGORITHM
 EFFICIENT HARDWARE IMPLEMENTATIONS FOR THE ADVANCED ENCRYPTION STANDARD (AES) ALGORITHM by Issam Mahdi Hammad Submitted in partial fulfilment of the requirements for the degree of Master of Applied Science
EFFICIENT HARDWARE IMPLEMENTATIONS FOR THE ADVANCED ENCRYPTION STANDARD (AES) ALGORITHM by Issam Mahdi Hammad Submitted in partial fulfilment of the requirements for the degree of Master of Applied Science
Design and Evaluation of FPGA Based Hardware Accelerator for Elliptic Curve Cryptography Scalar Multiplication
 Design and Evaluation of FPGA Based Hardware Accelerator for Elliptic Curve Cryptography Scalar Multiplication Department of Electrical and Computer Engineering Tennessee Technological University Cookeville,
Design and Evaluation of FPGA Based Hardware Accelerator for Elliptic Curve Cryptography Scalar Multiplication Department of Electrical and Computer Engineering Tennessee Technological University Cookeville,
EE 486 Winter The role of arithmetic. EE 486 : lecture 1, the integers. SIA Roadmap - 2. SIA Roadmap - 1
 EE 486 Winter 2-3 The role of arithmetic EE 486 : lecture, the integers M. J. Flynn With increasing circuit density available with sub micron feature sizes, there s a corresponding broader spectrum of
EE 486 Winter 2-3 The role of arithmetic EE 486 : lecture, the integers M. J. Flynn With increasing circuit density available with sub micron feature sizes, there s a corresponding broader spectrum of
By, Ajinkya Karande Adarsh Yoga
 By, Ajinkya Karande Adarsh Yoga Introduction Early computer designers believed saving computer time and memory were more important than programmer time. Bug in the divide algorithm used in Intel chips.
By, Ajinkya Karande Adarsh Yoga Introduction Early computer designers believed saving computer time and memory were more important than programmer time. Bug in the divide algorithm used in Intel chips.
Pipelined Quadratic Equation based Novel Multiplication Method for Cryptographic Applications
 , Vol 7(4S), 34 39, April 204 ISSN (Print): 0974-6846 ISSN (Online) : 0974-5645 Pipelined Quadratic Equation based Novel Multiplication Method for Cryptographic Applications B. Vignesh *, K. P. Sridhar
, Vol 7(4S), 34 39, April 204 ISSN (Print): 0974-6846 ISSN (Online) : 0974-5645 Pipelined Quadratic Equation based Novel Multiplication Method for Cryptographic Applications B. Vignesh *, K. P. Sridhar
CPE300: Digital System Architecture and Design
 CPE300: Digital System Architecture and Design Fall 2011 MW 17:30-18:45 CBC C316 Arithmetic Unit 10122011 http://www.egr.unlv.edu/~b1morris/cpe300/ 2 Outline Recap Fixed Point Arithmetic Addition/Subtraction
CPE300: Digital System Architecture and Design Fall 2011 MW 17:30-18:45 CBC C316 Arithmetic Unit 10122011 http://www.egr.unlv.edu/~b1morris/cpe300/ 2 Outline Recap Fixed Point Arithmetic Addition/Subtraction
Scalar Blinding on Elliptic Curves with Special Structure
 Scalar Blinding on Elliptic Curves with Special Structure Scott Fluhrer Cisco Systems August 11, 2015 1 Abstract This paper shows how scalar blinding can provide protection against side channel attacks
Scalar Blinding on Elliptic Curves with Special Structure Scott Fluhrer Cisco Systems August 11, 2015 1 Abstract This paper shows how scalar blinding can provide protection against side channel attacks
Cryptography and Network Security Chapter 10. Fourth Edition by William Stallings
 Cryptography and Network Security Chapter 10 Fourth Edition by William Stallings Chapter 10 Key Management; Other Public Key Cryptosystems No Singhalese, whether man or woman, would venture out of the
Cryptography and Network Security Chapter 10 Fourth Edition by William Stallings Chapter 10 Key Management; Other Public Key Cryptosystems No Singhalese, whether man or woman, would venture out of the
Issues in Information Systems Volume 18, Issue 2, pp , 2017
 IMPLEMENTING ELLIPTIC CURVE CRYPTOGRAPHY USING MICROSOFT EXCEL Abhijit Sen, Kwantlen Polytechnic University, abhijit.sen@kpu.ca ABSTRACT Microsoft Excel offers a number of data manipulation tools that
IMPLEMENTING ELLIPTIC CURVE CRYPTOGRAPHY USING MICROSOFT EXCEL Abhijit Sen, Kwantlen Polytechnic University, abhijit.sen@kpu.ca ABSTRACT Microsoft Excel offers a number of data manipulation tools that
High-Performance Integer Factoring with Reconfigurable Devices
 FPL 2010, Milan, August 31st September 2nd, 2010 High-Performance Integer Factoring with Reconfigurable Devices Ralf Zimmermann, Tim Güneysu, Christof Paar Horst Görtz Institute for IT-Security Ruhr-University
FPL 2010, Milan, August 31st September 2nd, 2010 High-Performance Integer Factoring with Reconfigurable Devices Ralf Zimmermann, Tim Güneysu, Christof Paar Horst Görtz Institute for IT-Security Ruhr-University
Scalable VLSI Design for Fast GF(p) Montgomery Inverse Computation
 Scalable VLSI Design for Fast GF(p) Montgomery Inverse Computation Adnan Abdul-Aziz Gutub 1, Erkay Savas 2, and Tatiana Kalganova 3 1 Department of Computer Engineering, King Fahd University of Petroleum
Scalable VLSI Design for Fast GF(p) Montgomery Inverse Computation Adnan Abdul-Aziz Gutub 1, Erkay Savas 2, and Tatiana Kalganova 3 1 Department of Computer Engineering, King Fahd University of Petroleum
ISSN Vol.08,Issue.12, September-2016, Pages:
 ISSN 2348 2370 Vol.08,Issue.12, September-2016, Pages:2273-2277 www.ijatir.org G. DIVYA JYOTHI REDDY 1, V. ROOPA REDDY 2 1 PG Scholar, Dept of ECE, TKR Engineering College, Hyderabad, TS, India, E-mail:
ISSN 2348 2370 Vol.08,Issue.12, September-2016, Pages:2273-2277 www.ijatir.org G. DIVYA JYOTHI REDDY 1, V. ROOPA REDDY 2 1 PG Scholar, Dept of ECE, TKR Engineering College, Hyderabad, TS, India, E-mail:
DIGITAL ARITHMETIC: OPERATIONS AND CIRCUITS
 C H A P T E R 6 DIGITAL ARITHMETIC: OPERATIONS AND CIRCUITS OUTLINE 6- Binary Addition 6-2 Representing Signed Numbers 6-3 Addition in the 2 s- Complement System 6-4 Subtraction in the 2 s- Complement
C H A P T E R 6 DIGITAL ARITHMETIC: OPERATIONS AND CIRCUITS OUTLINE 6- Binary Addition 6-2 Representing Signed Numbers 6-3 Addition in the 2 s- Complement System 6-4 Subtraction in the 2 s- Complement
A Comparison of Two Algorithms Involving Montgomery Modular Multiplication
 ISSN (Online) : 2319-8753 ISSN (Print) : 2347-6710 International Journal of Innovative Research in Science, Engineering and Technology An ISO 3297: 2007 Certified Organization Volume 6, Special Issue 5,
ISSN (Online) : 2319-8753 ISSN (Print) : 2347-6710 International Journal of Innovative Research in Science, Engineering and Technology An ISO 3297: 2007 Certified Organization Volume 6, Special Issue 5,
UNIVERSITY OF MASSACHUSETTS Dept. of Electrical & Computer Engineering. Digital Computer Arithmetic ECE 666
 UNIVERSITY OF MASSACHUSETTS Dept. of Electrical & Computer Engineering Digital Computer Arithmetic ECE 666 Part 6c High-Speed Multiplication - III Israel Koren Fall 2010 ECE666/Koren Part.6c.1 Array Multipliers
UNIVERSITY OF MASSACHUSETTS Dept. of Electrical & Computer Engineering Digital Computer Arithmetic ECE 666 Part 6c High-Speed Multiplication - III Israel Koren Fall 2010 ECE666/Koren Part.6c.1 Array Multipliers
This is a repository copy of High Speed and Low Latency ECC Implementation over GF(2m) on FPGA.
 This is a repository copy of High Speed and Low Latency ECC Implementation over GF(2m) on FPGA. White Rose Research Online URL for this paper: http://eprints.whiterose.ac.uk/99476/ Version: Accepted Version
This is a repository copy of High Speed and Low Latency ECC Implementation over GF(2m) on FPGA. White Rose Research Online URL for this paper: http://eprints.whiterose.ac.uk/99476/ Version: Accepted Version
Daniel V. Bailey 1 and Christof Paar 2. 1 Computer Science Department, Worcester Polytechnic Institute, Worcester, MA.
 Optimal Extension Fields for Fast Arithmetic in Public-Key Algorithms Daniel V. Bailey 1 and Christof Paar 2 1 Computer Science Department, Worcester Polytechnic Institute, Worcester, MA 01609 USA. Email:
Optimal Extension Fields for Fast Arithmetic in Public-Key Algorithms Daniel V. Bailey 1 and Christof Paar 2 1 Computer Science Department, Worcester Polytechnic Institute, Worcester, MA 01609 USA. Email:
Overview. Public Key Algorithms I
 Public Key Algorithms I Dr. Arjan Durresi Louisiana State University Baton Rouge, LA 70810 Durresi@csc.lsu.Edu These slides are available at: http://www.csc.lsu.edu/~durresi/csc4601-04/ Louisiana State
Public Key Algorithms I Dr. Arjan Durresi Louisiana State University Baton Rouge, LA 70810 Durresi@csc.lsu.Edu These slides are available at: http://www.csc.lsu.edu/~durresi/csc4601-04/ Louisiana State
Elliptic Curve Public Key Cryptography
 Why? Elliptic Curve Public Key Cryptography ECC offers greater security for a given key size. Why? Elliptic Curve Public Key Cryptography ECC offers greater security for a given key size. The smaller key
Why? Elliptic Curve Public Key Cryptography ECC offers greater security for a given key size. Why? Elliptic Curve Public Key Cryptography ECC offers greater security for a given key size. The smaller key
Implementation of Galois Field Arithmetic Unit on FPGA
 Implementation of Galois Field Arithmetic Unit on FPGA 1 LakhendraKumar, 2 Dr. K. L. Sudha 1 B.E project scholar, VIII SEM, Dept. of E&C, DSCE, Bangalore, India 2 Professor, Dept. of E&C, DSCE, Bangalore,
Implementation of Galois Field Arithmetic Unit on FPGA 1 LakhendraKumar, 2 Dr. K. L. Sudha 1 B.E project scholar, VIII SEM, Dept. of E&C, DSCE, Bangalore, India 2 Professor, Dept. of E&C, DSCE, Bangalore,
Volume 5, Issue 5 OCT 2016
 DESIGN AND IMPLEMENTATION OF REDUNDANT BASIS HIGH SPEED FINITE FIELD MULTIPLIERS Vakkalakula Bharathsreenivasulu 1 G.Divya Praneetha 2 1 PG Scholar, Dept of VLSI & ES, G.Pullareddy Eng College,kurnool
DESIGN AND IMPLEMENTATION OF REDUNDANT BASIS HIGH SPEED FINITE FIELD MULTIPLIERS Vakkalakula Bharathsreenivasulu 1 G.Divya Praneetha 2 1 PG Scholar, Dept of VLSI & ES, G.Pullareddy Eng College,kurnool
The most important development from the work on public-key cryptography is the digital signature. Message authentication protects two parties who
 1 The most important development from the work on public-key cryptography is the digital signature. Message authentication protects two parties who exchange messages from any third party. However, it does
1 The most important development from the work on public-key cryptography is the digital signature. Message authentication protects two parties who exchange messages from any third party. However, it does
Injntu.com Injntu.com Injntu.com R16
 1. a) What are the three methods of obtaining the 2 s complement of a given binary (3M) number? b) What do you mean by K-map? Name it advantages and disadvantages. (3M) c) Distinguish between a half-adder
1. a) What are the three methods of obtaining the 2 s complement of a given binary (3M) number? b) What do you mean by K-map? Name it advantages and disadvantages. (3M) c) Distinguish between a half-adder
