Symantec Advanced Threat Protection App for Splunk
|
|
|
- Ronald Davis
- 5 years ago
- Views:
Transcription
1 Symantec Advanced Threat Protection App for Splunk Administrator Guide Date Published: 27 th Mar 2017 Document Version: 1.0.5
2 Table of Contents Installing and setting up the ATP app 3 About the Symantec ATP app 3 Symantec ATP Apps on Splunkbase 3 Setting up the Symantec ATP App and Add-on in Splunk Environment 4 Configuring event forwarding to Splunk 5 Setting up Symantec ATP Incident retrieval via OAuth 10 Install & Configuring apps and add-ons in a Distributed Splunk Environment 13 Configuring Symantec Security.cloud 15 Configuring Symantec ATP Manager 17 Configuring Symantec ATP App for Splunk 19 Configuring Symantec ATP app for Splunk logging 21 Using the Symantec ATP App and Add-on for Splunk 23 Dashboards 23 Tools 31 Help 36 Troubleshooting 38 Search 39 Viewing ATP incidents and related events in Splunk 40 Adaptive Response Framework 43 Using Adaptive Response 45 i
3 ARF in Splunk Enterprise Security Suite (ESS) 45 ARF in Symantec ATP Add-on for Splunk 52 Workflow for Symantec ATP app 55 Troubleshooting the Symantec ATP app 56 APPENDIX A: Installing an app or add-on in Splunk Enterprise 57 APPENDIX B: Various Possible Splunk Distributed Deployments 58 Indexer Clustering 58 Search Head Clustering 59 Multisite Clustering 60 APPENDIX C: Event data collection in Splunk 61 APPENDIX D: Eventgen configuration for sample event data 62 APPENDIX E: Best Practices for Scheduling Saved Searches 63 APPENDIX G: Important Configurations and Limitations 64 Important Configurations 64 Known Limitations 64 ii
4 Installing and setting up the ATP app This chapter includes the following topics: About the Symantec ATP app Symantec ATP App on Splunkbase Setting up the Symantec ATP App & Add-on in Splunk Environment Configuring event forwarding to Splunk Setting up Symantec ATP Incident retrieval via OAuth Install & Configuring apps and add-ons in a Distributed Splunk Environment Configuring Symantec Security.cloud Configuring Symantec ATP Manager Configuring Symantec ATP App for Splunk About the Symantec ATP app The Symantec Advanced Threat Protection (ATP) app lets you leverage the power of Splunk and provides an aggregated as well as individual visualizations for Network, Endpoint and by collecting data from Symantec ATP and Symantec Security.cloud. This allows the incident responder to monitor and investigate possible threats in the organization by aggregating ATP incident and related event data from your ATP appliances in the Splunk console. This App contains both the standard Splunk module and the Adaptive Response for Splunk Enterprise Security Suite (ES) app for executing endpoint isolate/re-join and delete file actions. The Adaptive Response leverages the AR Framework solution provided by Splunk through the Splunk Enterprise Security Suite. Symantec ATP Apps on Splunkbase There are two bundles available on Splunkbase for the Symantec Endpoint Protection App for Splunk. Table 1 - Bundle Names on Splunk Base Bundle Name Splunkbase URL Description Symantec ATP App for Splunk (symantec_atp_app) Symantec ATP Add-on for Splunk (TAsymantec_atp) Symantec ATP App for Splunk Symantec ATP Add-on for Splunk Symantec ATP App for Splunk Administrator Guide 3
5 Setting up the Symantec ATP App and Add-on in Splunk Environment Installing apps in Splunk The Symantec ATP app lets you aggregate Symantec Advanced Threat Protection (ATP) incident and related event data from all of your control points and view them in the Splunk console. Before you set up the app, ensure that you have all of the following requirements: Proper Splunk credentials You must have the proper credentials to download the free Symantec ATP app. See the Splunk documentation for more information. Symantec Advanced Threat Protection 2.2 or higher Splunk Enterprise 6.4.x and above Symantec Security.cloud credential with ViewStats permission Splunk Enterprise Security Suite (required only for Adaptive Response) Table 2 - How to set up the Symantec ATP app for Splunk Phase Task Description 1. Install the Symantec ATP app in Splunk. 2. Configure Symantec ATP app in Splunk. 3. Perform post setup configuration Download the free Symantec ATP app from the Splunk app store and install it. Generate an OAuth client from the ATP Manager Configure HTTP Event forwarding to Splunk 1. Go to the Splunk app store: 2. In the Search field, search for Symantec ATP. 3. In the search results, click on the Symantec ATP app for Splunk. 4. On the app description page, click on Download for the Symantec ATP app. 5. Specify your Splunk logon credentials and click Login. 6. Follow the online prompts to download the app. The app appears in the Splunk console as Symantec ATP for Splunk. Note: Both the Symantec ATP app and Add-On are required 1 to be installed. For multiple servers involving Search Head, Forwarder and Indexer, see Install & Configuring apps and add-ons in a Distributed Splunk Environment You must obtain an OAuth client to secure communications between the ATP appliance and Splunk to retrieve Incident details. Use a unique OAuth client for each instance of ATP that you register with Splunk. You must have ATP admin rights to create an OAuth client in the ATP Manager. See Setting up Symantec ATP Incident retrieval via OAuth Tip: It is recommended that you keep this page open in your browser so that you can copy/paste the client ID and client secret in the next phase. You must configure ATP to secure communications between the ATP appliance and Splunk to send events from ATP. Splunk requires a generated token and this token is use to exchange the logs. See Configuring event forwarding to Splunk Tip: It is recommended that you keep this page open in your browser so that you can copy/paste the client ID and client secret in the next phase. Depending on the control points in your environment the following steps allow you to configure credential for each control points in your environment and which control point to display for your environment. 1. Configure what control points you have in environment to be display, see Configuring Symantec ATP App for Splunk. 2. Configure credential for ATP: , see Configuring Symantec Security.cloud. 3. Configure Incident retrieval from ATP Manager, see Configuring Symantec ATP Manager. 1 Changes made in release to comply with certification requirement. Symantec ATP App for Splunk Administrator Guide 4
6 Configuring event forwarding to Splunk 1. In Splunk Forwarder, create a token for HEC Collector. Click on Settings -> Data -> Data inputs. Under the HTTP Event Collector section, click on Add new 2. Enter a name for HTTP Event Collector (HEC), and then click on Next button to proceed. Symantec ATP App for Splunk Administrator Guide 5
7 3. Click on Next button to proceed. 4. Click on Next button to proceed. Symantec ATP App for Splunk Administrator Guide 6
8 5. Copy the Token Value. We will refer to it as the Splunk HEC Token. 6. In Symantec ATP Manager, navigate to Settings -> Data Sharing Symantec ATP App for Splunk Administrator Guide 7
9 7. Under Splunk Event Forwarding, click on Configure Splunk. 8. Fill in the details of the hostname, port (i.e is the default), and the Splunk HEC token generated in step 5. Click on Save button to proceed. Symantec ATP App for Splunk Administrator Guide 8
10 9. Fill in the details of the hostname, port (i.e is the default), and the copied token generated in step 5. Click on Save button to proceed. Symantec ATP App for Splunk Administrator Guide 9
11 Setting up Symantec ATP Incident retrieval via OAuth 1. In Symantec ATP Manager, navigate to Settings -> Data Sharing. Under the OAuth clients section, click on Add Application. 2. Enter a name in the App Name field, and click on Generate. 3. Copy the string in the Client Secret section, click on the Done button to return to the main screen. Symantec ATP App for Splunk Administrator Guide 10
12 4. The newly created OAuth client would be visible on the Data Sharing section. 5. In Splunk, click on the App menu and select Manage Apps. Under the Symantec Add-on for Splunk, click on the Set up under Actions. Symantec ATP App for Splunk Administrator Guide 11
13 6. In the section under ATP Server URL, enter the FQDN or IP address of the ATP server. Paste the Client Secret which is copied in step If the above steps are completed successfully, the Splunk app will be able to retrieve Incident details. Symantec ATP App for Splunk Administrator Guide 12
14 Install & Configuring apps and add-ons in a Distributed Splunk Environment Following is the matrix of apps to be deployed in Splunk s distributed environment. Table 2 - Matrix for Splunk Distributed Setup App Name Search Head Indexer Instance Forwarder Instance Instance Symantec ATP App for Splunk (symantec_atp_app) Yes Symantec ATP Add-on for Splunk (TA-symantec_atp) Yes Yes Yes Information about which Symantec application should be setup on which Splunk instance is included in the configuration section. For information about distributed deployment for Splunk, please visit Splunk s documentation: Follow the steps below to configure Symantec ATP app and add-on for Splunk using the application Setup pages. Table 3 - Matrix for Splunk Distributed Setup configuration requirement App Name Setup Section Search Head Instance Indexer Instance Forwarder Instance Symantec ATP App for Splunk Endpoint Yes (App won t be installed on (App won t be installed on (symantec_atp_app) (If Symantec ATP Endpoint Indexers) Forwarders) Protection is available) Symantec ATP App for Splunk Network Yes (App won t be installed on (App won t be installed on (symantec_atp_app) (If Symantec ATP Network Indexers) Forwarders) Protection is available) Symantec ATP App for Splunk Yes (App won t be installed on (App won t be installed on (symantec_atp_app) (If Symantec Indexers) Forwarders) Security.cloud is available) Symantec ATP App for Splunk Adaptive Yes (App won t be installed on (App won t be installed on (symantec_atp_app) Response (If Adaptive Response Indexers) Forwarders) feature is to be used) Symantec ATP Add-on for Splunk (No setup page (No setup page Yes (TA-symantec_atp) Security.cloud Credentials configurations required) configurations required) (Credentials will be used in API calls to Datafeeds URL to collect data) Symantec ATP Add-on for Splunk (No setup page (No setup page Yes (TA-symantec_atp) Security.cloud Data Collection configurations required) configurations required) (To collect logs and forward to indexers) Symantec ATP App for Splunk Administrator Guide 13
15 App Name Setup Section Search Head Instance Indexer Instance Forwarder Instance Symantec ATP Add-on for Splunk ATP Manager Yes (No setup page Yes (TA-symantec_atp) Credentials (If Adaptive Response configurations required) (Credentials will be used in feature is to be used) API calls to ATP Manager URL to collect Incident logs and AR Actions) Symantec ATP Add-on for Splunk ATP Manager (No setup page (No setup page Yes (TA-symantec_atp) Data Collection configurations required) configurations required) (To collect ATP Incident logs and forward to indexers) Symantec ATP Add-on for Splunk Saved Searches Yes (No setup page (No setup page (TA-symantec_atp) (Not available in (To generate Adaptive configurations required) configurations required) Setup Page. Refer Response incidents from Configuration for indexed data) Adaptive Response section) Symantec ATP App for Splunk Administrator Guide 14
16 Configuring Symantec Security.cloud Configuration of Symantec Security.cloud credentials is required to collect logs. This configuration is done from the Setup page of Symantec ATP Add-on for Splunk (TA-symantec_atp). The configuration requires the following parameters to be entered on the Setup page: 1. Check mark the Symantec Security.cloud Configuration to show the relevant section. 2. Data Feeds Web Service URL of Symantec Security.cloud instance (auto populated) 3. Username 4. Password NOTE: Once the user saves these credentials, Splunk stores these credentials internally in an encrypted form and these credentials won t be displayed again on revisiting this Setup page. Symantec ATP App for Splunk Administrator Guide 15
17 Incorrect Credentials While saving the credentials, an API call is made to Symantec Security.cloud using the provided credentials and only the verified credentials will be stored in Splunk. If invalid credentials are provided an error will be displayed on the Setup page. If credentials were successfully saved in Splunk previously and if new credentials provided are incorrect, the existing credentials will remain as is and no changes will be saved. Note that, Symantec Security.cloud allows a maximum of 3 wrong attempts of API calls with incorrect password and then the account for that username will be blocked. So make sure only correct and working credentials are provided in Splunk. The data collection should be disabled before changing the password for the provided username in Symantec Security.cloud, otherwise the account might get locked while trying to collect data with incorrect existing credentials. Adding Multiple Credentials Adding multiple credentials for Security.cloud is not supported. If different credentials with different username are provided, existing credentials will be replaced by new credentials provided the new credentials are valid and authenticated. Updating Credentials To update the credentials, the user needs to specify the same Data Feeds Web Services URL and Username and a different password on the form and then save to update the password for that credential set. If different values for IP/Domain Name and Username are provided which are not already present in Splunk, a new set of credentials will be created. Symantec ATP App for Splunk Administrator Guide 16
18 Disabling Data Collection Data collection can be stopped, by unchecking the option Enable data collection check box and saving the configurations. Please note that to enable or disable the data collection, credentials are required. Configuring Data Collection Interval The Data collection interval is Every 15 minutes by default. This collection interval can be changed by modifying the value of interval in seconds for script://$splunk_home/etc/apps/tasymantec_atp/bin/ _security_cloud_collect.py stanza of inputs.conf file TA-symantec_atp/default. Configuring Symantec ATP Manager Configuration of Symantec ATP Manager credentials is required to collect ATP incident logs. This configuration is done from the Setup page of Symantec ATP Add-on for Splunk (TA-symantec_atp). The configuration requires the following parameters to be entered on Setup page: 1. Check Symantec ATP Manager Configuration to show the relevant section. 2. ATP Server URL of Symantec ATP Manager 3. Password (Provide in client_id:client_secret format available from ATP Manager) a. Example if your client_id available from ATP manager is O2ID.xyz.pqr.123 and client_secret available from ATP manager is xyz , the concatenated string of both these values with a colon ( : ) in between should be provided in password field as O2ID.xyz.pqr.123:xyz NOTE: Once the user saves these credentials, Splunk stores these credentials internally in an encrypted form and these credentials won t be displayed again on revisiting this Setup page. Symantec ATP App for Splunk Administrator Guide 17
19 Incorrect Credentials While saving the credentials, an API call is made to Symantec ATP Manager using the provided credentials and only the verified credentials will be stored in Splunk. If invalid credentials are provided an error will be displayed on Setup page. If credentials were successfully saved in Splunk previously and if new credentials provided were incorrect, existing credentials will remain as is and no changes will be saved. Adding Multiple Credentials Multiple credentials can be provided for different ATP Server URLs. In this scenario, Incident data will be collected from all the ATP Managers for which the credentials are provided and successfully stored. A user can add multiple credentials for multiple ATP Managers. For example user can configure below set of credentials: Credential #1 ATP Server URL: atp1.symanteccloud.com Password: O2ID.xyz.pqr.123:xyz Credential #2 ATP Server URL: atp2.symanteccloud.com Password: O2ID.abc.lmn.456:pqr Symantec ATP App for Splunk Administrator Guide 18
20 Updating Credentials To update the credentials, user need to specify the same ATP Server URL different password on the form and then save to update the password for that credential set. If different values of ATP Server URL are provided which are not already present in the Splunk, a new set of credentials will be created. Disabling Incident Data Collection Incident Data collection can be stopped, by unchecking the option Enable Incident data collection check box and saving the configurations. Please note that to enable or disable the data collection, credentials are required. Configuring Incident Data Collection Interval The Data collection interval is Every 10 minutes by default. This collection interval can be changed by modifying the value of interval in seconds for script://$splunk_home/etc/apps/tasymantec_atp/bin/atp_incidents_collect.py and script://$splunk_home/etc/apps/tasymantec_atp/bin/atp_incident_events_collect.py stanzas of inputs.conf file TA-symantec_atp/default. Configuring Symantec ATP App for Splunk Configuration of Symantec ATP App for Splunk is required to configure the dashboard layouts based on the Symantec control points data availability. For example, if you have purchase Symantec Advanced Threat Protection for Endpoint, you can configure the Splunk app to show only the Endpoint dashboard. This configuration is done from the Setup page of Symantec ATP App for Splunk (symantec_atp_app). Symantec ATP App for Splunk Administrator Guide 19
21 The configuration requires the following parameters to be entered Setup page: Endpoint 3. Network 4. Adaptive Response The user needs to specify which of the above control points are relevant in Splunk. This configuration will enable or disable the dashboards or dashboard panels related to these components accordingly. If the user enables Adaptive Response, a separate dashboard for monitoring Splunk Adaptive Response framework related Action calls will be enabled. For example, if the user selects all the components, all the dashboards and dashboard panels will be visible in the Symantec ATP App for Splunk as shown below: If the user selects only component, the dashboards and dashboard panels related to only Symantec Security.cloud event data will be visible in the Symantec ATP App for Splunk as shown below: Configuring for Adaptive Response To leverage Splunk Adaptive Response Framework with Splunk Enterprise Security (ESS) App, no additional configurations are required as default configurations in the app and add-on will work. As the Adaptive Response feature is provided in Symantec ATP Add-on for Splunk, it should be disabled on all Splunk instances except Splunk Search Head. To disable the Adaptive Response related functionalities, follow these steps: Symantec ATP App for Splunk Administrator Guide 20
22 Table 4 - Disabling Adaptive Response Phase Task Description 1. Disable ATP App for Splunk 2. Disable ATP App Add-On for Splunk Disabling and removing Adaptive Response menu and functionality Disabling and removing Adaptive Response saved searches in Add-On 1. In the Splunk console, go to Manage Apps 2. In Symantec ATP App for Splunk (symantec_atp_app), click on Setup page 3. Uncheck the Adaptive Response checkbox and save the configurations. This will hide the Adaptive Response dashboard from the app navigation menu 1. In the Splunk console, go to Manage Apps 2. In Symantec ATP Add-on for Splunk (TA-symantec_atp), click on View Objects 3. Disable Following Saved Searches: a. es_symantec_atp_high_priority_incident b. es_symantec_atp_medium_priority_incident c. es_symantec_atp_low_priority_incident Since AR is specific feature of Splunk ESS App, If these saved searches are not disabled it would index incident related data which would not be utilised by Splunk User. To leverage Splunk Adaptive Response Framework with Non-ES environment that is in absence of Splunk Enterprise Security (ESS) App, you need additional configurations in the app and add-on as below: Table 5 - Enabling Adaptive Response for non-enterprise security app customer Phase Task Description 1. Enable ATP App for Splunk Enabling Adaptive Response functionality 1. In the Splunk console, go to Manage Apps 2. In Symantec ATP App for Splunk (symantec_atp_app), click on Setup page 3. Checked the Adaptive Response checkbox and save the configurations. This will show the Adaptive Response dashboard from the app navigation menu. 2. Enable ATP App Add-On for Splunk Enabling Adaptive Response savedsearch in Add-On 1. In the Splunk console, go to Manage Apps 2. In Symantec ATP Add-on for Splunk (TA-symantec_atp), click on View Objects 3. Enable following saved searches by setting the disable parameter value as False : a. es_symantec_atp_high_priority_incident b. es_symantec_atp_medium_priority_incident c. es_symantec_atp_low_priority_incident If these saved searches are not enabled, the search queries won t be executed and corresponding actions won t be executed on the searched incidents. 4. For each enabled savedsearch, disable the parameter action.notable by setting its value as 0. This will prevent the App from trying to create incidents for Enterprise Security Suite as notable action is available only when Enterprise Security Suite is installed. 5. For each enabled savedsearch, you need to add a new parameter for each ATP action that you want to take automatically on execution of that savedsearch in action.<action_name> = 1 format. For example, if you want to take delete file action we need to add the parameter as action. symantec_atp_delete_file_action = 1. The value of <action_name> should be same as actions specified in alert_actions.conf file in this same add-on. 6. Enable the python script which will take automatic command and check ATP action automatically on regular intervals for all automatic actions taken. To enable this script, we need to set the value of disable parameter as False for stanza [script://$splunk_home/etc/apps/tasymantec_atp/bin/symantec_atp_async_command_status.py] in inputs.conf file of this add-on. All Adaptive Response related events and logs will be indexed in index=main by default. To change the index for these logs (for example new index is summary ), you need to uncomment #param.index = main and replace the index name main by summary for all stanzas in alert_actions.conf file of this add-on. Configuring Symantec ATP app for Splunk logging The default logs generated by Symantec ATP app and add-on are set to ERROR level. To change the log level for more detailed logs, follow the steps below: Symantec ATP App for Splunk Administrator Guide 21
23 Table 6 Changing the default log level App Symantec ATP App for Splunk Steps to change the log level Change the default parameter of setup_logging method from loglevel=logging.error to loglevel=logging.debug in $SPLUNK_HOME/etc/apps/symantec_atp/bin/logger_manager.py The default log location for these logs is $SPLUNK_HOME/etc/apps/symantec_atp/local/logs/. The default index where these logs will be indexed is index=main. To change the index for these logs for example change from index=main to index=_internal, we need to uncomment #index = main and replace the index name main by _internal for stanza [monitor://$splunk_home/etc/apps/symantec_atp_app/local/logs] in inputs.conf file of this add-on Symantec ATP Add-on for Splunk Change the default parameter of setup_logging method from loglevel=logging.error to loglevel=logging.debug in $SPLUNK_HOME/etc/apps/TA-symantec_atp/bin/logger_manager.py The default log location for these logs is $SPLUNK_HOME/etc/apps/TA-symantec_atp/local/logs/. The default index where these logs will be indexed is index=main. To change the index for these logs for example change from index=main to index=_internal, we need to uncomment #index = main and replace the index name main by _internal for stanza [monitor://$splunk_home/etc/apps/symantec_atp_app/local/logs] in inputs.conf file of this add-on. Please do not change the log level in setup_logger in TA-symantec_atp/bin/lib/cim_actions.py as this may affect the behavior of Adaptive Response feature. The Adaptive Response feature depends on event logs generated by this method. The default log location for these logs is $SPLUNK_HOME/var/log/splunk Symantec ATP App for Splunk Administrator Guide 22
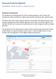
24 Using the Symantec ATP App and Add-on for Splunk This chapter includes the following topics: Dashboards in ATP app Viewing ATP incidents and related events in Splunk Dashboards The Symantec ATP app uses the term, control point for each of the area of protection provided by Symantec Advanced Threat Protection solution. The Symantec ATP app for Splunk provides various visualization and provides incident responders with information about their environment. Protection at a glance This dashboard enables users to have a collective view of endpoint, network, roaming on the protection status maintained by Symantec ATP Manager. It consists of various panels and charts as described below. Table 7 - List of Protection at a glance panels/charts Panel/Chart Suspicious Files Description ATP uses a file classifier to analyze files with unknown dispositions. The file classifier breakdowns files by their attributes to determine if the file is good or malicious, based on decision trees that are trained with millions of files. This technology uses machine-learning instead of signatures or sandbox detonation. ATP Endpoint do not block Suspicious file and highlight the possibility of a new and unknown threat. This panel shows a weekly trend of the number of Suspicious files detected in ATP Endpoint. Sandboxing Convictions (Cynic) Open Incidents Targeted Attacks File Reputation (Insight) Network Threats Blocked Network Threats Monitored New and Unknown Threats Cynic analysis and virtual execution detonates files in a cloud-based sandbox environment, analyzes, and reports each step of the observed behavior. Cynic uses machine-learning technology to compare the results to known bad attributes. It then correlates your data with real-world data provided by the Symantec Global Intelligence Network to determine if the files are malicious. This panel shows a weekly trend of the aggregated detection across all control points. This panel shows a weekly trend of current incidents that are opened and retrieved via ATP Public API This panel shows a weekly trend of the number of incidents created based on Dynamic Adversary Intelligence, which detects known targeted attacks based on attributes. Insight technology used to identify new threats in both ATP Endpoint and Network. This panel shows a weekly total of the aggregated blocked events across Endpoint and Network control points. Intruder prevention events that are blocked in both ATP Endpoint and Network. This panel shows the weekly trend of the aggregated blocked events across Endpoint and Network control points. Intruder prevention events that are not blocked in both ATP Endpoint and Network. This panel shows a weekly trend of the aggregated events that are not blocked at the Endpoint and Network control points. The New and Unknown Threats widget lists the number of files that were detected as threats within your environment by the following Symantec technologies: Cynic, Insight, and Mobile Insight technologies across control points. This panel shows the weekly trend of the aggregated detected events across Endpoint and Network control points. Symantec ATP App for Splunk Administrator Guide 23
25 Panel/Chart Event contributions by affected IP Conviction URLs Top 25 SHA256 Malicious File Names Description Top 10 IP addresses that generate events based on the selected filter (default 15 days). This can be used as a base line to query further on why a certain IP is generating these many events. A list of URLs convicted by Endpoint IPS, Network IPS, and control points based on the selected filter (default 15 days). This information can be used to supplement IPS/FW or network security devices in the environment to prevent accessing of these malicious domains. A list of malicious files detected and blocked by various control points based on the selected filter (15 days). This information can be used to supplement endpoint or network security devices to block access for these malicious files using the hash. A list of malicious files detected by various control points based on the selected filter (15 days). Figure 1 Protection at a glance Endpoint Protection at a glance This dashboard provides information on the endpoint related events from both Symantec ATP and Endpoint Protection. It consists of various panels and charts as described below: Symantec ATP App for Splunk Administrator Guide 24
26 Table 8 Endpoint Protection at a glance panels/charts Panel/Chart IPS(Vantage) File Reputation (Insight) AntiVirus Engine Suspicious Files Description Signature based detection engine that finds threats in the network steam. Network traffic is blocked at the endpoint, and the source of events can be used to block at the network security devices. This panel shows a weekly total of the aggregated blocked or monitored events across Endpoint. Insight technology used to identify new threats in both ATP Endpoint and Network. This panel shows a weekly total of the aggregated blocked or monitored events across Endpoint. Signature based detection engine that detect file based malware. Files detected are blocked at the endpoint. This panel shows a weekly total of the aggregated blocked events across Endpoint. ATP uses a file classifier to analyze files with unknown dispositions. The file classifier breaks down files by their attributes to determine if the file is good or malicious, based on decision trees that are trained with millions of files. This technology uses machine-learning instead of signatures or sandbox detonation. ATP Endpoint does not block suspicious files and highlights the possibility of a new and unknown threat. This panel shows a weekly trend of the number of suspicious files detected in ATP Endpoint. Users at Risk All Files inspected Blocked Traffic Local Host by conviction Remote Host by conviction Top 25 Files List the name of Windows logon users who contributes to AV and IPS events. This panel shows a weekly total of the aggregated events across Endpoint. Total number of files inspected by SEP whether good, bad or unknown. shows a weekly total of the aggregated events across Endpoint. The trending will show if new Process executables files are seen in the environment and if such trends are expected. (for example, Firefox update. This graph shows the trending of blocked IPS traffic based on the selected filter (default 15 days) for Endpoint and is used to baseline the network. An increase of blocked traffic on a non-working day could potentially show unauthorized traffic or infected hosts. This graph shows the trending of conviction for both AV and IPS based on the selected filter (default 15 days) for Endpoint. The endpoints are investigated for their detection volume. This graph shows the trending of conviction for both AV and IPS based on the selected filter (default 15 days) for Endpoint. The remote computers are investigated for attempting to infect the local endpoint and should be blocked at the network security devices. A list of the top 25 files process executable files seen by endpoints based on the selected filter (default 15 days). This list contains good, bad, and unknown reputation of in the environment and shows the popularity of files, for example users who recently updated to new version of Chrome. It provides information on the SHA256, MD5 and Digital signature of the file. Symantec ATP App for Splunk Administrator Guide 25
27 Figure 2 Endpoint at a glance Symantec ATP App for Splunk Administrator Guide 26
28 Network & Roaming Protection at a glance This dashboard gives users an overview of the overall network being monitored using Symantec ATP Manager. It consists of various panels and charts as described below: Table 9 Network and Roaming Protection at a glance panels/charts Panel/Chart Blacklist(IP/URL/Domain) Blacklist(File) IPS(Vantage) File Reputation (Insight) Mobile File Reputation (Mobile Insight) Sandboxing Conviction(Cynic) AntiVirus Engine Infected System Network Traffic Web Traffic Event Contributions by affected IP Conviction URLs Description The blacklist uses both Deepsight and user defined blacklist ATP policy to match network packet inspected by ATP. This panel shows a weekly trend for network and roaming control point. The blacklist matches user defined blacklist ATP policy to match file inspected by ATP. This panel shows a weekly trend for network and roaming control point. Signature based detection engine that finds threats in the network steam. Network traffic is detected (blocked or monitored) at the ATP Network appliance. This panel shows a weekly trend for network roaming control points. Insight technology used to identify new threats in both ATP Network and Roaming. This panel shows a weekly aggregated Insight detection events for network and roaming control points. Mobile Insight technology used to identify new mobile APK threats in both ATP Network and Roaming. This panel shows weekly aggregated Mobile Insight detection events for network and roaming control point. Cynic analysis and virtual execution detonates files in a cloud-based sandbox environment, analyzes, and reports each step of the observed behavior. Cynic uses machine-learning technology to compare the results to known bad attributes. It then correlates your data with real-world data provided by the Symantec Global Intelligence Network to determine if the files are malicious. This panel shows a weekly trend of files downloaded from the network that has been convicted by Cynic. Signature based detection engine that detects file based malware when downloading from the Internet. Files detected are blocked by ATP Network and Roaming. This panel shows a weekly trend of files blocked events across network and roaming control points This panel shows a weekly trend of detection based on IPS technology of type category System Infection. This could mean that an endpoint is infected and part of a botnet. This panel shows both blocked and allowed traffic, for blocked traffic check if there are suspicious process running on endpoint. For allowed traffic, check if ATP Network or Roaming has blocking enabled. This graph shows the trending of allowed and blocked events on the selected filter (default 15 days) for ATP Network control point. If the Allowed traffic is higher than expected, consider putting ATP into inline blocking mode, or check if the network or endpoint has been misconfigured and is allowing malicious traffic. This graph shows the trending of both allowed and blocked events on the selected filter (default 15 days) for ATP Roaming control point. If the Allowed traffic is higher than expected, consider configuring ATP Roaming in blocking mode. Top 10 IP addresses that generate events based on the selected filter (default 15 days). This can be used as a base line to inquiry further about why a certain IP is generating the volume of events. A list of URLs convicted by Network and Roaming IPS control points based on the selected filter (default 15 days). This information can be used to supplement IPS/FW or network security devices in the environment to prevent accessing of these malicious domains. Symantec ATP App for Splunk Administrator Guide 27
29 Figure 3 Network & Roaming Protection at a glance Symantec ATP App for Splunk Administrator Guide 28
30 Protection at a glance This dashboard gives users an overview of the overall cloud monitoring parameters. It consists of various panels and charts as described below. Table 10 Protection at a glance panels/charts Panel/Chart Total Malware Malware Targets Phishing Targets Malicious Sources Malicious URLs Description Weekly trending information about the total number of malware items blocked by Symantec .cloud and ATP: service. Weekly trending information about the total number of unique recipients targeted by attackers and blocked by the .cloud service. Weekly trending information about the total number of unique phishing recipients targeted by attackers and blocked by the .cloud service. Weekly trending information about the number of unique MTA IPs delivering malicious payloads to the recipients. Weekly trending information about the number of s blocked that contain malicious URLs. Sandboxing Convictions (Cynic) Attacks Timeline Geographical View of Sources Malware Types Malwares Top 10 Recipients Top 10 Sources Top 10 Senders Malware Sources Malicious URLs Cynic Convictions Link Following URLs Cynic analysis and virtual execution detonates files in a cloud-based sandbox environment, and then analyzes and reports each step of the observed behavior. Cynic uses machine learning technology to compare the results to known bad attributes. It then correlates your data with real-world data provided by the Symantec Global Intelligence Network to determine if the files are malicious. This panel shows a weekly trend of s with attachments convicted by Cynic. This panel provides an overview of the attack timeline indicating the volume of malware attacks blocked by Symantec .cloud for the selected timeframe. This panel provides a geographical view of the attack landscape and provides visibility into origination of the attack, i.e. the countries from which malicious s are being sent. This panel displays the breakdown of malware categorized by Symantec .cloud service. For additional information about malware types, click here. This panel displays the breakdown of malware blocked by the Symantec .cloud service. Ex: JS/Downloader, Trojan.Gen, etc This panel displays the top 10 recipients (targets) of malicious s for your organization. This panel displays the top 10 sources (IP addresses of the MTA) of the malicious s that attackers attempted to deliver to your organization. This panel displays the top 10 senders (envelope from) of the malicious s that attackers attempted to deliver to your organization. This panel displays the IP address of the sending MTA, source country and number of malware threats that attackers attempted to deliver to your organization. This panel displays the URLs in the s that are blocked by Symantec .cloud service. These URLs can be in the body or attachments. This panel displays the number of Cynic (sandbox) convictions detected by the ATP: service. Symantec .cloud service link-following technology actively opens each link in the and checks the destination website for malware or other types of potentially harmful content at the time the link is clicked.this panel displays information about URLs that are convicted by link-following technology and includes both source (URL that is in body or attachment) and destination URLs (URL from which the actual payload is downloaded). Symantec ATP App for Splunk Administrator Guide 29
31 Panel/Chart Description Figure 4 Protection at a glance Symantec ATP App for Splunk Administrator Guide 30
32 Tools This menu item enables users to search for specific list of items from the overall data collected by Symantec ATP manager to get a drill down view on any of the specific events that user is tracking. It is divided into four sub-sections as described below. Investigation This dashboard lets users search a specific list of s and associated attachments for malware. It consists of the following panels: Malicious Traffic Malicious Files Attachment Overview Symantec ATP App for Splunk Administrator Guide 31
33 Figure 5 Investigation Symantec ATP App for Splunk Administrator Guide 32
34 Endpoint Investigation This dashboard lets users drill down to specific events related to Endpoint investigation. It consists of various panels as described below: Endpoint Information Malicious Files Malicious Connections Related Threats Related Events Figure 6 Endpoint Investigation Symantec ATP App for Splunk Administrator Guide 33
35 File Investigation This dashboard lets users drill down to specific file investigations related to end-points, s or networks. It consists of various panels as described below: File Information File Overview Seen on Endpoints Related Connections Figure 7 File Investigation Symantec ATP App for Splunk Administrator Guide 34
36 Domain Investigation This dashboard lets users drill down to domain/url related investigation that have been tracked across network, endpoint or sources. It consists of various panels as described below: Domain Information Related Connections Files Downloaded Related Endpoints Related s Symantec ATP App for Splunk Administrator Guide 35
37 Figure 8 Domain Investigation Help This menu item lets users troubleshoot issues with the Symantec Splunk apps and add-ons using information from logs as well as Splunk license usage information. Splunk License Usage This dashboard lets users track overall Splunk license usage. Symantec ATP App for Splunk Administrator Guide 36
38 Figure 9 Splunk License Usage Symantec ATP App for Splunk Administrator Guide 37
39 Troubleshooting This dashboard gives users a starting point for any investigation related to the events that are being indexed in Splunk for Symantec ATP. It also allows users to search log files that are indexed to enable better tracking. Figure 10 Troubleshooting Dashboard Symantec ATP App for Splunk Administrator Guide 38
40 Search This menu can be used similarly to the search and reporting app to perform free-form searches on data indexed in Splunk. Figure 11 Splunk Search Symantec ATP App for Splunk Administrator Guide 39
41 Viewing ATP incidents and related events in Splunk The Symantec ATP app lets you view Symantec Advanced Threat Protection (ATP) incidents and related events in the Splunk console. You must first configure OAuth for your ATP appliance and enable it for the Symantec ATP app to replicate ATP incidents and related events in Splunk. See Setting up Symantec ATP Incident retrieval via OAuth. By default, the ATP Import Jobs service runs every 10 minutes to replicate ATP incident and related event data. To change the data collection interval, refer Configuring Incident Data Collection Interval section in this document. The Symantec ATP app only replicates incidents that occur when the connection between the ATP appliance and Splunk is enabled and healthy. Whenever incident information is updated in ATP manager, corresponding new events will be created in Splunk with updated information. This dashboard will always show the latest information on a particular incident. The Symantec ATP app leverages the Splunk platform to let you sort columns, perform searches, and apply filters on Incident and Event Summary pages. See the Splunk documentation for more information. Symantec ATP App for Splunk Administrator Guide 40
42 Figure 12 Incident Report Symantec ATP App for Splunk Administrator Guide 41
43 To view ATP incidents and related events in Splunk Table 11 Viewing incidents and related events Task To view basic information about a specific incident To view detailed information about a specific incident To view the events that are related to an incident To view details about event types To view all fields on the incident and related events page without tabs Optional Steps Hover over the reference icon for that incident. Click the reference icon for that incident. The Incident page appears. 1 Click the reference icon for the incident. 2 On the Incident page, click the Event Summary tab. 1 On the Event Summary tab, scroll down to the list of related events. 2 Click on an event type in the Event Type column to view additional tabs that provide information such as threat details, file information, etc. Perform the following steps if you prefer to see all fields in a single view as opposed to tabbed view. 1 Click on the gear icon on the top right corner of the screen to open the Settings panel. 2 Navigate to Forms and disable the Tabbed form setting. Symantec ATP App for Splunk Administrator Guide 42
44 Adaptive Response Framework This chapter includes the following topics: Adaptive Response Splunk ATP App Symantec ATP App for Splunk Administrator Guide 43
45 Workflow for Symantec ATP app Using Adaptive Response ARF in Splunk Enterprise Security Suite (ESS) Adaptive Response Splunk ATP App Symantec ATP App for Splunk Administrator Guide 44
46 Workflow for Symantec ATP app Using Adaptive Response Previously Symantec ATP Admins had to monitor the security logs collected by Symantec ATP and sent to Splunk, then find the security incidents from those logs in Splunk, remember the endpoints where the incidents occurred, and then go to Symantec ATP to take action on those endpoints. Adaptive Response Framework closes the gap between Symantec ATP and Splunk. Using Splunk s Adaptive Response Framework, Symantec ATP admins can now execute various Symantec ATP actions like Delete File, Isolate Endpoint, and Rejoin Endpoint directly from Splunk Apps whenever the incidents are detected in Splunk (based on data sent from Symantec ATP logs/events to Splunk. There are two ways to take Symantec ATP actions on the endpoints: Table 12 - Different type of actions available for Adaptive Response Manual Actions (with Enterprise Security Suite) Splunk provides a Splunk Enterprise Security Suite (ESS), which leverages the Splunk s Adaptive Response Framework and allows Admins to monitor and manage threats and incidents directly from the Splunk Apps. It has rich dashboards that help monitor the Incidents, take Manual Actions on the Incidents, and also Monitor these Actions. Splunk Enterprise Security Suite is extendable by adding a compatible Module App (Adaptive Response Add-ons) for a particular domain/technology. The Suite detects configurations in these Adaptive Response Add-ons and helps monitor and take actions on the Incidents reported by these Add-ons. Automatic actions (without Enterprise Security Suite) In scenarios where Splunk Enterprise Security Suite (ESS) is not purchased and is not installed in your Splunk infrastructure, Symantec ATP App still offers an elegant way to monitor and take action on the incidents reported by analytics on Symantec ATP events/logs. To achieve this, Symantec ATP Add-on for Splunk leverages Adaptive Response Framework independent of Splunk Enterprise Security Suite (ESS) and can execute Symantec ATP actions. But the actions will be executed automatically when the incidents are reported and there will be no user Interaction on these actions. Symantec ATP Add-on for Splunk (TA-symantec_atp) is one such module for Splunk Enterprise Security Suite. It leverages Splunk Adaptive Response Framework and empowers System Admins to monitor and take actions on Incidents reported by analytics on Symantec ATP events/logs from the Splunk Enterprise Security Suite dashboards. ARF in Splunk Enterprise Security Suite (ESS) Splunk provides the Adaptive Response Framework in the Enterprise Security Suite by leveraging the modular action functionality provided in Splunk_SA_CIM.notabl Symantec ATP App for Splunk Administrator Guide 45
47 The Splunk core already provides standard alert actions like sending s, notable events, calling a Webhook URL, etc. But Modular Actions on top of these are nothing but custom alert actions. These custom alert actions let you invoke Python scripts that use APIs external to Splunk. The Enterprise Security Suite app provides support for Correlation/Saved Searches with notable actions. When a Splunk Enterprise Security Correlation/Saved Search (with Notable Event mapped) is executed and gets at least one event in the results, notable events will be created through standard notable action. These Notable events are visible in the Incident Review dashboard of Splunk Enterprise Security App and no other alert action (other than notable action) is executed automatically because none are mapped. The Incident Review dashboard is shown below: Figure 13 Enterprise Security Suit Splunk, as a part of the Adaptive Response Framework, has enhanced this Incident Review dashboard in the latest Enterprise Security Suite app, which provides the option to take actions on these notable events. Users can view the notable event details by expanding the left arrow for that notable event and execute alert actions manually for each of the notable events by clicking on Run Adaptive Response Actions for the notable event and selecting the specific Alert Action. Symantec ATP App for Splunk Administrator Guide 46
48 Figure 14 Incident details When a notable event's "Run Adaptive Response Actions" menu item is clicked, it will populate all of the standard and custom actions by reading the alert_actions.conf files of all the installed apps on that Splunk instance. Users can select multiple actions on this popup and run them for that notable event. Symantec ATP App for Splunk Administrator Guide 47
49 Figure 15 Available actions Symantec ATP App for Splunk Administrator Guide 48
50 Figure 16 Selected action to execute Figure 17 Executed action When these actions are run, for each such selected action corresponding actions are invoked from alert_actions.conf. For each of these actions, Splunk invokes the sendalert command by passing the Notable Event content in a result.csv file path with the action name in the parameters. This sendalert command then calls the Python script with same name as the action name and provides the.csv file path to that script. These Python scripts, one for each Alert Action, extend the SymantecATPBaseAction (symantec_atp_base_actions.py) to leverage Adaptive Response Framework. Each Alert Action Python script passes Symantec ATP App for Splunk Administrator Guide 49
51 specific action name, disposition and action_group parameters to SymantecATPBaseAction, which makes REST API calls to Symantec ATP. symantec_atp_base_actions.py: Class name: SymantecATPBaseAction Description: This Python script performs the following actions: Makes API calls to Symantec ATP Manager. Handles API call response given by Symantec ATP in proper format and indexes it in specific index, source and sourcetype to be used further in the Action dashboard. The SymantecATPBaseAction (symantec_atp_base_actions.py) Python script extends the ModularAction class from cim_actions.py file to comply with the ModularAction and leaves the implementation of custom logic for that action to the Python scripts extending this one. The cim_actions.py is the core of Adaptive Response Framework and is copied from Splunk_SA_CIM app into our Adaptive Response Add-on, i.e. Symantec ATP Add-on for Splunk TAsymantec_atp/bin/lib folder. This way any Splunk saved search can execute any Modular Action. Each action Python script with custom logic should also have a corresponding action HTML file with the exact same action name. If the HTML file is blank, the Show Actions popup will not populate any form and will be executed directly. If the HTML files have a form, the user can input values when selecting the action and these input values will be available in the action Python script. The developer can then use this data in business logic or as parameters to external REST APIs. When these Alert Actions are executed successfully, the user can check the Alert Action status in Adaptive Responses : Figure 18 Status of executed actions Users can click on this Alert Action name to view the events and response related to this action. Users can also click on View Adaptive Response Invocations menu items in the Actions menu to view more details on notable events and corresponding alert action responses. Symantec ATP App for Splunk Administrator Guide 50
52 Figure 19 viewing action details Symantec ATP App for Splunk Administrator Guide 51
53 Splunk Enterprise Security Suite app also provides an Adaptive Response Action Center Dashboard to monitor the executions of these Modular Actions invoked through the Incident Review dashboard. Figure 20 Viewing list of actions taken on Adaptive Response Active Center Dashboard ARF in Symantec ATP Add-on for Splunk The Symantec ATP Add-on for Splunk (TA-symantec_atp) leverages the Adaptive Response by including/copying the modular actions functionality provided in Splunk_SA_CIM. Symantec ATP App for Splunk Administrator Guide 52
54 The Splunk core already provides standard alert actions like sending s, notable events?, calling a Webhook URL, etc. Modular Actions on top of these are nothing but custom alert actions. These custom alert actions allow the invocation of custom Python scripts that can include APIs external to Splunk. Splunk has developed this Custom Modular Actions functionality by creating a Splunk command called "sendalert" which is configured in the action stanza of alert_actions.conf with is_custom=1. Parameters of this command are the saved search result file path, action name, etc. So when a Saved Search/Alert (with Alert Actions mapped) is executed and gets at least one event in the results, the corresponding actions are invoked from alert_actons.conf automatically. For each action, Splunk invokes the sendalert command by passing the saved search result.csv file path and action name in the parameters. This sendalert command then calls the Python script with same name as the action name and provides the.csv file path to that script. These Python scripts, each for one Alert Action, extend the SymantecATPBaseAction (symantec_atp_base_actions.py) to leverage the Adaptive Response Framework. Each Alert Action Python script passes specific action name, disposition and action_group parameters SymantecATPBaseAction, which makes REST API calls to Symantec ATP. symantec_atp_base_actions.py: Class name: SymantecATPBaseAction Description: This Python script does performs the following actions: Makes API calls to Symantec ATP Manager Handles API call response given by Symantec ATP in proper format and indexes it in specific index, source and sourcetype to be used further in the Action dashboard The SymantecATPBaseAction (symantec_atp_base_actions.py) Python script extends the ModularAction class from the cim_actions.py file to comply with the ModularAction and leaves the implementation of custom logic for that action to the Python scripts extending this one. The cim_actions.py is the core of the Adaptive Response Framework and is copied from the Splunk_SA_CIM app into our Adaptive Response Add-on Symantec ATP Add-on for Splunk TAsymantec_atp/bin/lib folder. This way any Splunk saved search can execute any Modular Action. Each action Python script with custom logic should also have a corresponding action HTML file with the exact action name. If the HTML file is blank, the Show Actions popup will not populate any form and will be executed directly. If the HTML files have form, users can input values when selecting the action and these input values will be available in the action Python script. Ddevelopers can use these values in business logic or as parameters to external REST APIs. Unlike Splunk Enterprise Security Suite, these actions are invoked automatically rather than manually by a user, which means that there is no user to fill in the form.hence for automatic actions it is suggested to keep such HTML files blank. Symantec ATP App for Splunk (symantec_atp_app) also provides an Adaptive Response Dashboard to monitor the execution of these Modular Actions invoked automatically through Saved Search Alert Actions. Symantec ATP App for Splunk Administrator Guide 53
55 Adaptive Response Splunk ATP App This dashboard enables users to keep track of the saved searches with which Symantec ATP actions are associated and are scheduled to take automated actions. Figure 21 Adaptive Response Dashboard Symantec ATP App for Splunk Administrator Guide 54
56 Workflow for Symantec ATP app Table 13 Workflow in ESS and non ES environment Workflow in ESS environment 1. After setup of the TA-symantec_atp, it will communicate with Symantec ATP by using the ATP Manager credentials. 2. The alert actions are executed automatically when the corresponding savedsearches return any events in result. 3. The savedsearches are scheduled to execute every 10 minutes and include searches for events of last 10 minutes. 4. To configure the search schedules, edit cron schedules mentioned in TA-symantec_atp/default/savedsearches.conf. 5. The ESS app recognizes the Correlation Searches configured in TAsymantec_atp. 6. To enable or disable the notable event actions, in ESS app, go to Configure -> Content management. 7. Filter the list of Correlation Searches with TA-symantec_atp. 8. Edit the Correlation search and add Notable Action in the action list if not added already or disabled. 9. When the savedsearches are executed every 10 minutes the corresponding Correlation searches will create a notable event for each savedsearch result event. 10. User can track the notable events from the dashboard in app ESS - > Incident Review. 11. To execute a manual Symantec ATP Action on notable event, click on the Actions menu item in the last column of notable event and click "Run Adaptive Response Actions. 12. In the popup, add the action to be executed and click on "Run" and close the popup. 13. The details of the executed actions on a notable event can be viewed in the details drop of notable event. 14. The actions and responses can be tracked from the dashboard in app ESS -> Audit -> Adaptive Response Action Center. Workflow in non ESS environment 15. After setup of the TA-symantec_atp, it will communicate with Symantec ATP by using the ATP Manager credentials. 16. The alert actions are executed automatically when the corresponding savedsearches return any events in result. 17. The savedsearches are scheduled to execute every 10 minutes and include searches for events of last 10 minutes. 18. To configure the search schedules, edit cron schedules mentioned in TA-symantec_atp/default/savedsearches.conf. 19. The actions and responses can be tracked from the dashboard in app symantec_app -> Adaptive Response dashboard. Symantec ATP App for Splunk Administrator Guide 55
57 Troubleshooting the Symantec ATP app When an issue arises with the Symantec ATP app, the first place you should look is the Symantec ATP App Logs for more information. You may want to increase the logging level to debug to view all of the app activity that has occurred (info is the default logging level). See Configuring Symantec ATP app for Splunk logging. Table 14 - Troubleshoot the ATP app, describes some possible reasons why the Symantec ATP app may not be replicating ATP incidents and related events and offers some suggestions on how to troubleshoot. Table 14 - Troubleshoot the ATP app Issue The ATP appliance is down. The OAuth token is invalid or expired or Incident and related events are not populated. Recommendation Log onto the ATP Manager and review the system health. See the Symantec Advanced Threat Protection Administration Guide for more information. The Symantec ATP app cannot replicate incidents and related events unless you have a valid authentication client registered with the ATP instance. Confirm the OAuth client ID and client secret in ATP Manager or obtain a new one. See Setting up Symantec ATP Incident retrieval via OAuth Events are not populated. Log onto the ATP Manage and check the Splunk Event Forward health status. See Configuring event forwarding to Splunk The dashboard did not populate value. Ensure OAuth, Splunk Event Forwarding and ESS Credential is properly configured and enabled Ensure Splunk Event Forwarding from ATP Manager to Splunk server uses default port 8088 on TCP, ensure firewall between connections allows this. The control point dashboard did not populate. Ensure correct ESS Credentials are entered and have ViewStats permission. In the browser, access and check if is able to download a sample log file. See Setting up Symantec ATP Incident retrieval via OAuth under the section of Configuring Symantec Security.cloud. Permission error when configuring ATP: or proxy connection is required. Ensure that the Splunk server has internet connectivity directly as the app requires it. If proxy need to be defined in Splunk, edit /opt/splunk/etc/splunk-launch.conf and add the following: HTTP_PROXY=<proxy_ip> HTTPS_PROXY=<proxy_ip> Restart Splunk server by /opt/splunk/bin/splunk restart. In the Splunk server console, enter the following in the command line and replace the username and password. curl If the command is successful, a list of events would be shown. Incident Summary event count does not match the Related Events count. The ATP appliance incident creation engine might log related events to the database after the incident is logged. Allow some time for the events be logged and imported by the ATP Import Job. Symantec ATP App for Splunk Administrator Guide 56
58 APPENDIX A: Installing an app or add-on in Splunk Enterprise Steps to install and configure a Splunk Application from the Splunk UI. 1. Within Splunk user interface, an Apps menu appears in the upper left corner. 2. Clicking this pops up a button reading Manage Apps. On the next page (listing the installed applications), the button Install app from file allows an administrator to upload spl/zip file directly to Splunk from the local system. Restart Splunk server by executing $SPLUNK_HOME/bin/splunk restart where $SPLUNK_HOME is replaced by the folder path where Splunk is installed. 3. After successful upload and restart of Splunk, the user will be asked to set up/configure the app. Click Set up Now to go to the app configuration page. If the user is not asked for any such popup, go to the Splunk home page and click on the App icon and the setup page will appear. Symantec ATP App for Splunk Administrator Guide 57
59 APPENDIX B: Various Possible Splunk Distributed Deployments Indexer Clustering Symantec ATP App for Splunk Administrator Guide 58
60 Search Head Clustering Symantec ATP App for Splunk Administrator Guide 59
61 Multisite Clustering Symantec ATP App for Splunk Administrator Guide 60
Symantec Ransomware Protection
 Symantec Ransomware Protection Protection Against Ransomware Defense in depth across all control points is required to stop ransomware @ Email Symantec Email Security.cloud, Symantec Messaging Gateway
Symantec Ransomware Protection Protection Against Ransomware Defense in depth across all control points is required to stop ransomware @ Email Symantec Email Security.cloud, Symantec Messaging Gateway
USM Anywhere AlienApps Guide
 USM Anywhere AlienApps Guide Updated April 23, 2018 Copyright 2018 AlienVault. All rights reserved. AlienVault, AlienApp, AlienApps, AlienVault OSSIM, Open Threat Exchange, OTX, Unified Security Management,
USM Anywhere AlienApps Guide Updated April 23, 2018 Copyright 2018 AlienVault. All rights reserved. AlienVault, AlienApp, AlienApps, AlienVault OSSIM, Open Threat Exchange, OTX, Unified Security Management,
Comodo Dome Shield - Admin Guide
 rat Comodo Dome Shield Software Version 1.12 Administrator Guide Guide Version 1.12.111717 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Dome
rat Comodo Dome Shield Software Version 1.12 Administrator Guide Guide Version 1.12.111717 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Dome
ForeScout Extended Module for VMware AirWatch MDM
 ForeScout Extended Module for VMware AirWatch MDM Version 1.7.2 Table of Contents About the AirWatch MDM Integration... 4 Additional AirWatch Documentation... 4 About this Module... 4 How it Works... 5
ForeScout Extended Module for VMware AirWatch MDM Version 1.7.2 Table of Contents About the AirWatch MDM Integration... 4 Additional AirWatch Documentation... 4 About this Module... 4 How it Works... 5
ForeScout Extended Module for MobileIron
 Version 1.8 Table of Contents About MobileIron Integration... 4 Additional MobileIron Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
Version 1.8 Table of Contents About MobileIron Integration... 4 Additional MobileIron Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
rat Comodo EDR Software Version 1.7 Administrator Guide Guide Version Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013
 rat Comodo EDR Software Version 1.7 Administrator Guide Guide Version 1.1.120318 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo EDR...3 1.1 Purchase
rat Comodo EDR Software Version 1.7 Administrator Guide Guide Version 1.1.120318 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo EDR...3 1.1 Purchase
ForeScout Extended Module for Splunk
 Version 2.8 Table of Contents About Splunk Integration... 5 Support for Splunk Enterprise and Splunk Enterprise Security... 6 What's New... 6 Support for Splunk Cloud... 6 Support for Batch Messaging...
Version 2.8 Table of Contents About Splunk Integration... 5 Support for Splunk Enterprise and Splunk Enterprise Security... 6 What's New... 6 Support for Splunk Cloud... 6 Support for Batch Messaging...
AppDefense Cb Defense Configuration Guide. AppDefense Appendix Cb Defense Integration Configuration Guide
 AppDefense Appendix Cb Defense Integration Configuration Guide Table of Contents Overview 3 Requirements 3 Provision API Key for Cb Defense Integration 3 Figure 1 Integration Type 4 Figure 2 API Key Provisioning
AppDefense Appendix Cb Defense Integration Configuration Guide Table of Contents Overview 3 Requirements 3 Provision API Key for Cb Defense Integration 3 Figure 1 Integration Type 4 Figure 2 API Key Provisioning
Cisco Threat Intelligence Director (TID)
 The topics in this chapter describe how to configure and use TID in the Firepower System. Overview, page 1 Requirements for Threat Intelligence Director, page 4 How To Set Up, page 6 Analyze TID Incident
The topics in this chapter describe how to configure and use TID in the Firepower System. Overview, page 1 Requirements for Threat Intelligence Director, page 4 How To Set Up, page 6 Analyze TID Incident
ForeScout App for Splunk
 How-to Guide Version 2.0.0 Table of Contents About Splunk Integration... 3 Use Cases... 3 Data Mining and Trend Analysis of CounterACT Data... 4 Continuous Posture Tracking Based on a Broad Range of CounterACT
How-to Guide Version 2.0.0 Table of Contents About Splunk Integration... 3 Use Cases... 3 Data Mining and Trend Analysis of CounterACT Data... 4 Continuous Posture Tracking Based on a Broad Range of CounterACT
ForeScout Extended Module for Symantec Endpoint Protection
 ForeScout Extended Module for Symantec Endpoint Protection Version 1.0.0 Table of Contents About the Symantec Endpoint Protection Integration... 4 Use Cases... 4 Additional Symantec Endpoint Protection
ForeScout Extended Module for Symantec Endpoint Protection Version 1.0.0 Table of Contents About the Symantec Endpoint Protection Integration... 4 Use Cases... 4 Additional Symantec Endpoint Protection
ForeScout Extended Module for Carbon Black
 ForeScout Extended Module for Carbon Black Version 1.0 Table of Contents About the Carbon Black Integration... 4 Advanced Threat Detection with the IOC Scanner Plugin... 4 Use Cases... 5 Carbon Black Agent
ForeScout Extended Module for Carbon Black Version 1.0 Table of Contents About the Carbon Black Integration... 4 Advanced Threat Detection with the IOC Scanner Plugin... 4 Use Cases... 5 Carbon Black Agent
Compare Security Analytics Solutions
 Compare Security Analytics Solutions Learn how Cisco Stealthwatch compares with other security analytics products. This solution scales easily, giving you visibility across the entire network. Stealthwatch
Compare Security Analytics Solutions Learn how Cisco Stealthwatch compares with other security analytics products. This solution scales easily, giving you visibility across the entire network. Stealthwatch
Flowmon Application for QRadar User Guide
 Flowmon Application for QRadar User Guide Version 01.00.00 Flowmon Application for QRadar is an extension connecting IBM QRadar with events from Flowmon ADS Solution. Flowmon Application was build with
Flowmon Application for QRadar User Guide Version 01.00.00 Flowmon Application for QRadar is an extension connecting IBM QRadar with events from Flowmon ADS Solution. Flowmon Application was build with
ForeScout App & Add-ons for Splunk
 How-to Guide Version 2.7 Table of Contents About Splunk Integration... 4 Support for Splunk Adaptive Response... 5 What's New... 5 Support for Batch Messaging... 5 Support for Customized Indexes... 7 Use
How-to Guide Version 2.7 Table of Contents About Splunk Integration... 4 Support for Splunk Adaptive Response... 5 What's New... 5 Support for Batch Messaging... 5 Support for Customized Indexes... 7 Use
Need for Speed: Unleashing the Power of SecOps with Adaptive Response. Malhar Shah CEO, Crest Data Systems Meera Shankar Alliance Manager, Splunk
 Need for Speed: Unleashing the Power of SecOps with Adaptive Response Malhar Shah CEO, Crest Data Systems Meera Shankar Alliance Manager, Splunk September 27, 2017 Washington, DC Forward-Looking Statements
Need for Speed: Unleashing the Power of SecOps with Adaptive Response Malhar Shah CEO, Crest Data Systems Meera Shankar Alliance Manager, Splunk September 27, 2017 Washington, DC Forward-Looking Statements
Forescout. eyeextend for MobileIron. Configuration Guide. Version 1.9
 Forescout Version 1.9 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 1.9 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Symantec & Blue Coat Technical Update Webinar 29. Juni 2017
 Avantec Blue Coat/Symantec Webinar Jean Marc Edder Senior Systems Engineer The Global Leader in Cyber Network + + Cloud Global market leader in Endpoint, Email, Data Loss Prevention and Website, User Authentication
Avantec Blue Coat/Symantec Webinar Jean Marc Edder Senior Systems Engineer The Global Leader in Cyber Network + + Cloud Global market leader in Endpoint, Email, Data Loss Prevention and Website, User Authentication
DomainTools for Splunk
 DomainTools for Splunk Installation Guide version 2.0 January 2018 Solution Overview The DomainTools Technology Add-On (TA) for Splunk populates a whois index with DomainTools Whois and Risk Score data
DomainTools for Splunk Installation Guide version 2.0 January 2018 Solution Overview The DomainTools Technology Add-On (TA) for Splunk populates a whois index with DomainTools Whois and Risk Score data
Cisco Cloud Security. How to Protect Business to Support Digital Transformation
 Cisco Cloud Security How to Protect Business to Support Digital Transformation Dragan Novakovic Cybersecurity Consulting Systems Engineer January 2018. Security Enables Digitization Digital Disruption,
Cisco Cloud Security How to Protect Business to Support Digital Transformation Dragan Novakovic Cybersecurity Consulting Systems Engineer January 2018. Security Enables Digitization Digital Disruption,
Connection Logging. Introduction to Connection Logging
 The following topics describe how to configure the Firepower System to log connections made by hosts on your monitored network: Introduction to, page 1 Strategies, page 2 Logging Decryptable Connections
The following topics describe how to configure the Firepower System to log connections made by hosts on your monitored network: Introduction to, page 1 Strategies, page 2 Logging Decryptable Connections
The Vectra App for Splunk. Table of Contents. Overview... 2 Getting started Setup... 4 Using the Vectra App for Splunk... 4
 Table of Contents Overview... 2 Getting started... 3 Installation... 3 Setup... 4 Using the Vectra App for Splunk... 4 The Vectra Dashboard... 5 Hosts... 7 Detections... 8 Correlations... 9 Technical support...
Table of Contents Overview... 2 Getting started... 3 Installation... 3 Setup... 4 Using the Vectra App for Splunk... 4 The Vectra Dashboard... 5 Hosts... 7 Detections... 8 Correlations... 9 Technical support...
Bomgar PA Integration with ServiceNow
 Bomgar PA Integration with ServiceNow 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of
Bomgar PA Integration with ServiceNow 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of
ForeScout Extended Module for Splunk
 ForeScout Extended Module for Splunk Version 2.7.0 Table of Contents About Splunk Integration... 5 Support for Splunk Enterprise and Splunk Enterprise Security... 7 What's New... 7 Support for Splunk Cloud...
ForeScout Extended Module for Splunk Version 2.7.0 Table of Contents About Splunk Integration... 5 Support for Splunk Enterprise and Splunk Enterprise Security... 7 What's New... 7 Support for Splunk Cloud...
McAfee Network Security Platform 8.3
 8.3.7.44-8.3.7.14 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions Known
8.3.7.44-8.3.7.14 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions Known
Avanan for G Suite. Technical Overview. Copyright 2017 Avanan. All rights reserved.
 Avanan for G Suite Technical Overview Contents Intro 1 How Avanan Works 2 Email Security for Gmail 3 Data Security for Google Drive 4 Policy Automation 5 Workflows and Notifications 6 Authentication 7
Avanan for G Suite Technical Overview Contents Intro 1 How Avanan Works 2 Email Security for Gmail 3 Data Security for Google Drive 4 Policy Automation 5 Workflows and Notifications 6 Authentication 7
ForeScout Extended Module for ServiceNow
 ForeScout Extended Module for ServiceNow Version 1.2 Table of Contents About ServiceNow Integration... 4 Use Cases... 4 Asset Identification... 4 Asset Inventory True-up... 5 Additional ServiceNow Documentation...
ForeScout Extended Module for ServiceNow Version 1.2 Table of Contents About ServiceNow Integration... 4 Use Cases... 4 Asset Identification... 4 Asset Inventory True-up... 5 Additional ServiceNow Documentation...
McAfee Network Security Platform 8.3
 8.3.7.28-8.3.3.9 Manager-Mxx30-series Release Notes McAfee Network Security Platform 8.3 Revision C Contents About this release New features Enhancements Resolved issues Installation instructions Known
8.3.7.28-8.3.3.9 Manager-Mxx30-series Release Notes McAfee Network Security Platform 8.3 Revision C Contents About this release New features Enhancements Resolved issues Installation instructions Known
2. D3 Cyber Incident Response Integration for Splunk
 Table of Contents 1. Description D3 Add-on and App... 2 1.1 D3 Cyber Add-on... 2 1.2 D3 Cyber App... 2 2. D3 Cyber Incident Response Integration for Splunk... 2 3. D3 Cyber App for Splunk... 2 4. Installation
Table of Contents 1. Description D3 Add-on and App... 2 1.1 D3 Cyber Add-on... 2 1.2 D3 Cyber App... 2 2. D3 Cyber Incident Response Integration for Splunk... 2 3. D3 Cyber App for Splunk... 2 4. Installation
VARONIS DATALERT APP FOR IBM QRADAR
 VARONIS DATALERT APP FOR IBM QRADAR Integration Guide Publishing Information Software version 0 Document version 1 Publication date October 9, 2018 Copyright 2005-2018 Varonis Systems Inc. All rights reserved.
VARONIS DATALERT APP FOR IBM QRADAR Integration Guide Publishing Information Software version 0 Document version 1 Publication date October 9, 2018 Copyright 2005-2018 Varonis Systems Inc. All rights reserved.
At a Glance: Symantec Security.cloud vs Microsoft O365 E3
 At a Glance: Symantec Email Security.cloud vs Microsoft O365 E3 Microsoft O365 E3 Security as a Feature Symantec Email Security.cloud Why This Is Important Spam Protection Third-party blacklists subscribed
At a Glance: Symantec Email Security.cloud vs Microsoft O365 E3 Microsoft O365 E3 Security as a Feature Symantec Email Security.cloud Why This Is Important Spam Protection Third-party blacklists subscribed
Enhanced Threat Detection, Investigation, and Response
 Enhanced Threat Detection, Investigation, and Response What s new in Cisco Stealthwatch Enterprise Release 6.10.2 Cisco Stealthwatch Enterprise is a comprehensive visibility and security analytics solution
Enhanced Threat Detection, Investigation, and Response What s new in Cisco Stealthwatch Enterprise Release 6.10.2 Cisco Stealthwatch Enterprise is a comprehensive visibility and security analytics solution
Comodo Dome Shield - Admin Guide
 rat Comodo Dome Shield Software Version 1.16 Administrator Guide Guide Version 1.16.062718 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Dome
rat Comodo Dome Shield Software Version 1.16 Administrator Guide Guide Version 1.16.062718 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Dome
Integrate Palo Alto Traps. EventTracker v8.x and above
 EventTracker v8.x and above Publication Date: August 16, 2018 Abstract This guide provides instructions to configure Palo Alto Traps to send its syslog to EventTracker Enterprise. Scope The configurations
EventTracker v8.x and above Publication Date: August 16, 2018 Abstract This guide provides instructions to configure Palo Alto Traps to send its syslog to EventTracker Enterprise. Scope The configurations
USER MANUAL. SalesPort Salesforce Customer Portal for WordPress (Lightning Mode) TABLE OF CONTENTS. Version: 3.1.0
 USER MANUAL TABLE OF CONTENTS Introduction...1 Benefits of Customer Portal...1 Prerequisites...1 Installation...2 Salesforce App Installation... 2 Salesforce Lightning... 2 WordPress Manual Plug-in installation...
USER MANUAL TABLE OF CONTENTS Introduction...1 Benefits of Customer Portal...1 Prerequisites...1 Installation...2 Salesforce App Installation... 2 Salesforce Lightning... 2 WordPress Manual Plug-in installation...
ForeScout Extended Module for MaaS360
 Version 1.8 Table of Contents About MaaS360 Integration... 4 Additional ForeScout MDM Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
Version 1.8 Table of Contents About MaaS360 Integration... 4 Additional ForeScout MDM Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
Logging into the Firepower System
 The following topics describe how to log into the Firepower System: Firepower System User Accounts, on page 1 User Interfaces in Firepower Management Center Deployments, on page 3 Logging Into the Firepower
The following topics describe how to log into the Firepower System: Firepower System User Accounts, on page 1 User Interfaces in Firepower Management Center Deployments, on page 3 Logging Into the Firepower
Integrate Microsoft Office 365. EventTracker v8.x and above
 EventTracker v8.x and above Publication Date: March 5, 2017 Abstract This guide provides instructions to configure Office 365 to generate logs for critical events. Once EventTracker is configured to collect
EventTracker v8.x and above Publication Date: March 5, 2017 Abstract This guide provides instructions to configure Office 365 to generate logs for critical events. Once EventTracker is configured to collect
Forescout. eyeextend for Splunk. Configuration Guide. Version 2.9
 Forescout Version 2.9 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 2.9 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
MODERN DESKTOP SECURITY
 MODERN DESKTOP SECURITY I M GOING TO BE HONEST. WE RE IN THE FIGHT OF OUR DIGITAL LIVES, AND WE ARE NOT WINNING! M I C H A E L M C C A U L, C H A I R M A N, U S H O M E L A N D S E C U R I T Y C O M M
MODERN DESKTOP SECURITY I M GOING TO BE HONEST. WE RE IN THE FIGHT OF OUR DIGITAL LIVES, AND WE ARE NOT WINNING! M I C H A E L M C C A U L, C H A I R M A N, U S H O M E L A N D S E C U R I T Y C O M M
F5 Analytics and Visibility Solutions
 Agility 2017 Hands-on Lab Guide F5 Analytics and Visibility Solutions F5 Networks, Inc. 2 Contents: 1 Class 1: Introduction to F5 Analytics 5 1.1 Lab Environment Setup.......................................
Agility 2017 Hands-on Lab Guide F5 Analytics and Visibility Solutions F5 Networks, Inc. 2 Contents: 1 Class 1: Introduction to F5 Analytics 5 1.1 Lab Environment Setup.......................................
Connection Logging. About Connection Logging
 The following topics describe how to configure the Firepower System to log connections made by hosts on your monitored network: About, page 1 Strategies, page 2 Logging Decryptable Connections with SSL
The following topics describe how to configure the Firepower System to log connections made by hosts on your monitored network: About, page 1 Strategies, page 2 Logging Decryptable Connections with SSL
Configuring Antivirus Devices
 CHAPTER 9 Revised: November 11, 2007 Antivirus (AV) devices provide detection and prevention against known viruses and anomalies. This chapter describes how to configure and add the following devices and
CHAPTER 9 Revised: November 11, 2007 Antivirus (AV) devices provide detection and prevention against known viruses and anomalies. This chapter describes how to configure and add the following devices and
How-to Guide: Tenable Applications for Splunk. Last Revised: August 21, 2018
 How-to Guide: Tenable Applications for Splunk Last Revised: August 21, 2018 Table of Contents Overview 3 Components 4 Tenable Add-on (TA-tenable) 5 Source and Source Types 6 CIM Mapping 7 Tenable App for
How-to Guide: Tenable Applications for Splunk Last Revised: August 21, 2018 Table of Contents Overview 3 Components 4 Tenable Add-on (TA-tenable) 5 Source and Source Types 6 CIM Mapping 7 Tenable App for
SIEM Tool Plugin Installation and Administration
 SIEM Tool Plugin Installation and Administration 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are
SIEM Tool Plugin Installation and Administration 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
McAfee Security Connected Integrating epo and MFECC
 McAfee Security Connected Integrating epo and MFECC Table of Contents Overview 3 User Accounts & Privileges 3 Prerequisites 3 Configuration Steps 3 Value Add 12 FOR INTERNAL AND CHANNEL USE ONLY Rev 1
McAfee Security Connected Integrating epo and MFECC Table of Contents Overview 3 User Accounts & Privileges 3 Prerequisites 3 Configuration Steps 3 Value Add 12 FOR INTERNAL AND CHANNEL USE ONLY Rev 1
Comodo cwatch Network Software Version 2.23
 rat Comodo cwatch Network Software Version 2.23 Administrator Guide Guide Version 2.23.060618 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo cwatch
rat Comodo cwatch Network Software Version 2.23 Administrator Guide Guide Version 2.23.060618 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo cwatch
vrealize Automation Management Pack 2.0 Guide
 vrealize Automation Management Pack 2.0 Guide This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for
vrealize Automation Management Pack 2.0 Guide This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for
SonicWall Capture Client 1.0. Operations
 SonicWall Capture Client 1.0 Operations Contents Part 1. Introduction About Capture Client................................................................5 Description...........................................................................
SonicWall Capture Client 1.0 Operations Contents Part 1. Introduction About Capture Client................................................................5 Description...........................................................................
ForeScout Extended Module for ServiceNow
 ForeScout Extended Module for ServiceNow Version 1.1.0 Table of Contents About this Integration... 4 Use Cases... 4 Asset Identification... 4 Asset Inventory True-up... 5 Additional ServiceNow Documentation...
ForeScout Extended Module for ServiceNow Version 1.1.0 Table of Contents About this Integration... 4 Use Cases... 4 Asset Identification... 4 Asset Inventory True-up... 5 Additional ServiceNow Documentation...
Log Data: A Source of Value. Nagios Enterprises LLC Nagios Enterprises 2017 Logs: A Source of Value // 1
 Log Data: A Source of Value Nagios Enterprises LLC 2017 Nagios Enterprises 2017 Logs: A Source of Value // 1 Log Data: A Source of Value Nagios Enterprises LLC 2017 Introduction Part 1 : What s in a Log?
Log Data: A Source of Value Nagios Enterprises LLC 2017 Nagios Enterprises 2017 Logs: A Source of Value // 1 Log Data: A Source of Value Nagios Enterprises LLC 2017 Introduction Part 1 : What s in a Log?
Protecting Against Modern Attacks. Protection Against Modern Attack Vectors
 Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
Comodo Unknown File Hunter Software Version 2.1
 rat Comodo Unknown File Hunter Software Version 2.1 Administrator Guide Guide Version 2.1.061118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
rat Comodo Unknown File Hunter Software Version 2.1 Administrator Guide Guide Version 2.1.061118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
Forescout. eyeextend for ServiceNow. Configuration Guide. Version 2.0
 Forescout Version 2.0 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 2.0 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Agari App for Splunk Quick-Start Guide
 Agari App for Splunk Quick-Start Guide Initial Release (v1.1.0) This document describes how to get started with the Agari App for Splunk. This release is available to Agari customers via SplunkBase (https://splunkbase.splunk.com/app/3568/).
Agari App for Splunk Quick-Start Guide Initial Release (v1.1.0) This document describes how to get started with the Agari App for Splunk. This release is available to Agari customers via SplunkBase (https://splunkbase.splunk.com/app/3568/).
 Trend Micro Incorporated reserves the right to make changes to this document and to the service described herein without notice. Before installing and using the service, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the service described herein without notice. Before installing and using the service, review the readme files, release
File Reputation Filtering and File Analysis
 This chapter contains the following sections: Overview of, page 1 Configuring File Reputation and Analysis Features, page 5 File Reputation and File Analysis Reporting and Tracking, page 14 Taking Action
This chapter contains the following sections: Overview of, page 1 Configuring File Reputation and Analysis Features, page 5 File Reputation and File Analysis Reporting and Tracking, page 14 Taking Action
vrealize Operations Management Pack for NSX for vsphere 2.0
 vrealize Operations Management Pack for NSX for vsphere 2.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
vrealize Operations Management Pack for NSX for vsphere 2.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
How-To Configure Mailbox Auto Remediation for Office 365 on Cisco Security
 How-To Configure Mailbox Auto Remediation for Office 365 on Cisco Email Security Beginning with AsyncOS 10.0 1 2017 2017 Cisco Cisco and/or and/or its affiliates. its affiliates. All rights All rights
How-To Configure Mailbox Auto Remediation for Office 365 on Cisco Email Security Beginning with AsyncOS 10.0 1 2017 2017 Cisco Cisco and/or and/or its affiliates. its affiliates. All rights All rights
Comodo Dome Shield. Administrator Guide Guide Version Software Version 2.4. Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013
 rat Comodo Dome Shield Software Version 2.4 Administrator Guide Guide Version 2.4.032019 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Dome Shield...3
rat Comodo Dome Shield Software Version 2.4 Administrator Guide Guide Version 2.4.032019 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Dome Shield...3
Symantec Endpoint Protection Family Feature Comparison
 Symantec Endpoint Protection Family Feature Comparison SEP SBE SEP Cloud SEP Cloud SEP 14.2 Device Protection Laptop, Laptop Laptop, Tablet Laptop Tablet & & Smartphone Smartphone Meter Per Device Per
Symantec Endpoint Protection Family Feature Comparison SEP SBE SEP Cloud SEP Cloud SEP 14.2 Device Protection Laptop, Laptop Laptop, Tablet Laptop Tablet & & Smartphone Smartphone Meter Per Device Per
Forescout. eyeextend for Carbon Black. Configuration Guide. Version 1.1
 Forescout Version 1.1 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 1.1 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
IBM QRadar User Behavior Analytics (UBA) app Version 2 Release 5. User Guide IBM
 IBM QRadar User Behavior Analytics (UBA) app Version 2 Release 5 User Guide IBM Note Before you use this information and the product that it supports, read the information in Notices on page 111. Product
IBM QRadar User Behavior Analytics (UBA) app Version 2 Release 5 User Guide IBM Note Before you use this information and the product that it supports, read the information in Notices on page 111. Product
Partner Management Console Administrator's Guide
 Partner Management Console Administrator's Guide Partner Management Console Administrator's Guide Documentation version: November 17, 2017 Legal Notice Copyright 2017 Symantec Corporation. All rights reserved.
Partner Management Console Administrator's Guide Partner Management Console Administrator's Guide Documentation version: November 17, 2017 Legal Notice Copyright 2017 Symantec Corporation. All rights reserved.
Licensing the Firepower System
 The following topics explain how to license the Firepower System. About Firepower Feature Licenses, page 1 Service Subscriptions for Firepower Features, page 1 Classic Licensing for the Firepower System,
The following topics explain how to license the Firepower System. About Firepower Feature Licenses, page 1 Service Subscriptions for Firepower Features, page 1 Classic Licensing for the Firepower System,
Access Control. Access Control Overview. Access Control Rules and the Default Action
 The following topics explain access control rules. These rules control which traffic is allowed to pass through the device, and apply advanced services to the traffic, such as intrusion inspection. Overview,
The following topics explain access control rules. These rules control which traffic is allowed to pass through the device, and apply advanced services to the traffic, such as intrusion inspection. Overview,
Cisco Threat Intelligence Director (TID)
 The topics in this chapter describe how to configure and use TID in the Firepower System. Overview, page 1 Using TID Sources to Ingest Feed Data, page 6 Using Access Control to Publish TID Data and Generate
The topics in this chapter describe how to configure and use TID in the Firepower System. Overview, page 1 Using TID Sources to Ingest Feed Data, page 6 Using Access Control to Publish TID Data and Generate
Imperva Incapsula Website Security
 Imperva Incapsula Website Security DA T A SH E E T Application Security from the Cloud Imperva Incapsula cloud-based website security solution features the industry s leading WAF technology, as well as
Imperva Incapsula Website Security DA T A SH E E T Application Security from the Cloud Imperva Incapsula cloud-based website security solution features the industry s leading WAF technology, as well as
Bomgar SIEM Tool Plugin Installation and Administration
 Bomgar SIEM Tool Plugin Installation and Administration 2018 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are
Bomgar SIEM Tool Plugin Installation and Administration 2018 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are
Netwrix Auditor for SQL Server
 Netwrix Auditor for SQL Server Quick-Start Guide Version: 9.5 10/25/2017 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Netwrix Auditor for SQL Server Quick-Start Guide Version: 9.5 10/25/2017 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Enterprise Ransomware Mitigations
 打造數碼安全校園 Enterprise Ransomware Mitigations Windows 10, Edge Browser, Office ATP Enterprise Mobility Suite (EMS) ATP OneDrive for Business Azure Backup 3rd party Cloud Backup THE WINDOWS CLIENT DEFENSE
打造數碼安全校園 Enterprise Ransomware Mitigations Windows 10, Edge Browser, Office ATP Enterprise Mobility Suite (EMS) ATP OneDrive for Business Azure Backup 3rd party Cloud Backup THE WINDOWS CLIENT DEFENSE
Securing Office 365 with Symantec
 February, 2016 Solution Overview: Enterprise Security Adoption of Microsoft Office 365, Google Apps, and other cloud-based productivity solutions is growing. Microsoft in its Ignite 2015 session claimed
February, 2016 Solution Overview: Enterprise Security Adoption of Microsoft Office 365, Google Apps, and other cloud-based productivity solutions is growing. Microsoft in its Ignite 2015 session claimed
McAfee Network Security Platform 8.3
 8.3.7.86-8.3.7.56 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision C Contents About this release New features Enhancements Resolved issues Installation instructions Known
8.3.7.86-8.3.7.56 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision C Contents About this release New features Enhancements Resolved issues Installation instructions Known
Sophos XG Firewall v Release Notes. Sophos XG Firewall Reports Guide v17
 Sophos XG Firewall v 15.01.0 Release Notes Sophos XG Firewall Reports Guide v17 For Sophos Customers Document Date: October 2017 Contents ii Contents Reports... 4 Basics...4 Reports Navigation... 6 Dashboards...
Sophos XG Firewall v 15.01.0 Release Notes Sophos XG Firewall Reports Guide v17 For Sophos Customers Document Date: October 2017 Contents ii Contents Reports... 4 Basics...4 Reports Navigation... 6 Dashboards...
Update on new Microsoft Cloud Technology
 Update on new Microsoft Cloud Technology Advanced Threat Protection Thomas Collier Technical Pre-Sales OFFICE 365 PHISH PROTECTION STACK Protect during Mail Flow Protect Post Delivery Detect & Respond
Update on new Microsoft Cloud Technology Advanced Threat Protection Thomas Collier Technical Pre-Sales OFFICE 365 PHISH PROTECTION STACK Protect during Mail Flow Protect Post Delivery Detect & Respond
Pure Storage FlashArray Management Pack for VMware vrealize Operations Manager User Guide. (Version with Purity 4.9.
 Pure Storage FlashArray Management Pack for VMware vrealize Operations Manager User Guide (Version 1.0.139 with Purity 4.9.x or higher) Sunday, November 27, 2016 16:13 Pure Storage FlashArray Management
Pure Storage FlashArray Management Pack for VMware vrealize Operations Manager User Guide (Version 1.0.139 with Purity 4.9.x or higher) Sunday, November 27, 2016 16:13 Pure Storage FlashArray Management
Cisco ISE pxgrid App 1.0 for IBM QRadar SIEM. Author: John Eppich
 Cisco ISE pxgrid App 1.0 for IBM QRadar SIEM Author: John Eppich Table of Contents About This Document... 4 Solution Overview... 5 Technical Details... 6 Cisco ISE pxgrid Installation... 7 Generating the
Cisco ISE pxgrid App 1.0 for IBM QRadar SIEM Author: John Eppich Table of Contents About This Document... 4 Solution Overview... 5 Technical Details... 6 Cisco ISE pxgrid Installation... 7 Generating the
AppSpider Enterprise. Getting Started Guide
 AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
 Trend Micro Incorporated reserves the right to make changes to this document and to the service described herein without notice. Before installing and using the service, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the service described herein without notice. Before installing and using the service, review the readme files, release
Comodo IT and Security Manager Software Version 5.4
 Comodo IT and Security Manager Software Version 5.4 End User Guide Guide Version 5.4.090716 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
Comodo IT and Security Manager Software Version 5.4 End User Guide Guide Version 5.4.090716 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
Forescout. eyeextend for VMware AirWatch. Configuration Guide. Version 1.9
 Forescout Version 1.9 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 1.9 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
<Partner Name> RSA ARCHER GRC Platform Implementation Guide. RiskLens <Partner Product>
 RSA ARCHER GRC Platform Implementation Guide 2.4.1 Wesley Loeffler, RSA Engineering Last Modified: April 25 th, 2018 2.4 Solution Summary The & Archer integration connects
RSA ARCHER GRC Platform Implementation Guide 2.4.1 Wesley Loeffler, RSA Engineering Last Modified: April 25 th, 2018 2.4 Solution Summary The & Archer integration connects
Un SOC avanzato per una efficace risposta al cybercrime
 Un SOC avanzato per una efficace risposta al cybercrime Identificazione e conferma di un incidente @RSAEMEA #RSAEMEASummit @masiste75 Mauro Costantini - Presales Consultant Agenda A look into the threat
Un SOC avanzato per una efficace risposta al cybercrime Identificazione e conferma di un incidente @RSAEMEA #RSAEMEASummit @masiste75 Mauro Costantini - Presales Consultant Agenda A look into the threat
Product overview. McAfee Web Protection Hybrid Integration Guide. Overview
 McAfee Web Protection Hybrid Integration Guide Product overview Overview The McAfee Web Protection hybrid solution is the integration of McAfee Web Gateway and McAfee Web Gateway Cloud Service (McAfee
McAfee Web Protection Hybrid Integration Guide Product overview Overview The McAfee Web Protection hybrid solution is the integration of McAfee Web Gateway and McAfee Web Gateway Cloud Service (McAfee
McAfee Network Security Platform 8.3
 8.3.7.28-8.3.7.6 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision B Contents About this release New features Enhancements Resolved issues Installation instructions Known
8.3.7.28-8.3.7.6 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision B Contents About this release New features Enhancements Resolved issues Installation instructions Known
Delivering Integrated Cyber Defense for the Cloud Generation Darren Thomson
 Delivering Integrated Cyber Defense for the Generation Darren Thomson Vice President & CTO, EMEA Region Symantec In 2009 there were 2,361,414 new piece of malware created. In 2015 that number was 430,555,582
Delivering Integrated Cyber Defense for the Generation Darren Thomson Vice President & CTO, EMEA Region Symantec In 2009 there were 2,361,414 new piece of malware created. In 2015 that number was 430,555,582
VARONIS APP FOR SPLUNK. User Guide
 VARONIS APP FOR SPLUNK User Guide Publishing Information Software version Version 1.14 Document version 2 Publication date September, 2017 Copyright 2005-2017 Varonis Systems Inc. All rights reserved.
VARONIS APP FOR SPLUNK User Guide Publishing Information Software version Version 1.14 Document version 2 Publication date September, 2017 Copyright 2005-2017 Varonis Systems Inc. All rights reserved.
Vodafone Secure Device Manager Administration User Guide
 Vodafone Secure Device Manager Administration User Guide Vodafone New Zealand Limited. Correct as of June 2017. Vodafone Ready Business Contents Introduction 3 Help 4 How to find help in the Vodafone Secure
Vodafone Secure Device Manager Administration User Guide Vodafone New Zealand Limited. Correct as of June 2017. Vodafone Ready Business Contents Introduction 3 Help 4 How to find help in the Vodafone Secure
ForeScout Extended Module for Qualys VM
 ForeScout Extended Module for Qualys VM Version 1.2.1 Table of Contents About the Qualys VM Integration... 3 Additional Qualys VM Documentation... 3 About This Module... 3 Components... 4 Considerations...
ForeScout Extended Module for Qualys VM Version 1.2.1 Table of Contents About the Qualys VM Integration... 3 Additional Qualys VM Documentation... 3 About This Module... 3 Components... 4 Considerations...
Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting
 Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting Microsoft Cloud Evangelist at Patriot Consulting Principal Systems Architect with 17 Years of experience Technical certifications: MCSE, MCITP Office
Joe Stocker, CISSP, MCITP, VTSP Patriot Consulting Microsoft Cloud Evangelist at Patriot Consulting Principal Systems Architect with 17 Years of experience Technical certifications: MCSE, MCITP Office
The Invisible Threat of Modern Malware Lee Gitzes, CISSP Comm Solutions Company
 The Invisible Threat of Modern Malware Lee Gitzes, CISSP Comm Solutions Company November 12, 2014 Malware s Evolution Why the change? Hacking is profitable! Breaches and Malware are Projected to Cost $491
The Invisible Threat of Modern Malware Lee Gitzes, CISSP Comm Solutions Company November 12, 2014 Malware s Evolution Why the change? Hacking is profitable! Breaches and Malware are Projected to Cost $491
Comodo Device Manager Software Version 4.0
 Comodo Device Manager Software Version 4.0 End User Guide Guide Version 4.0.112316 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Device Manager...
Comodo Device Manager Software Version 4.0 End User Guide Guide Version 4.0.112316 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Device Manager...
Cisco Firepower NGFW. Anticipate, block, and respond to threats
 Cisco Firepower NGFW Anticipate, block, and respond to threats You have a mandate to build and secure a network that supports ongoing innovation Mobile access Social collaboration Public / private hybrid
Cisco Firepower NGFW Anticipate, block, and respond to threats You have a mandate to build and secure a network that supports ongoing innovation Mobile access Social collaboration Public / private hybrid
Juniper Sky Advanced Threat Prevention
 Juniper Sky Advanced Threat Prevention Product Overview Juniper Sky Advanced Threat Prevention is a cloud-based service that provides complete advanced malware protection. Integrated with SRX Series Services
Juniper Sky Advanced Threat Prevention Product Overview Juniper Sky Advanced Threat Prevention is a cloud-based service that provides complete advanced malware protection. Integrated with SRX Series Services
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
McAfee Network Security Platform 9.2
 Revision B McAfee Network Security Platform 9.2 (9.2.7.9-9.2.7.10 Manager-Virtual IPS Release Notes) Contents About this release New features Enhancements Resolved issues Installation instructions Known
Revision B McAfee Network Security Platform 9.2 (9.2.7.9-9.2.7.10 Manager-Virtual IPS Release Notes) Contents About this release New features Enhancements Resolved issues Installation instructions Known
McAfee Network Security Platform 8.3
 Revision A McAfee Network Security Platform 8.3 (8.3.7.86-8.3.5.53 Manager-NS-series Release Notes) Contents About this release New features Enhancements Resolved issues Installation instructions Known
Revision A McAfee Network Security Platform 8.3 (8.3.7.86-8.3.5.53 Manager-NS-series Release Notes) Contents About this release New features Enhancements Resolved issues Installation instructions Known
vrealize Hyperic Monitoring and Management Guide vrealize Hyperic 5.8.4
 vrealize Hyperic Monitoring and Management Guide vrealize Hyperic 5.8.4 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
vrealize Hyperic Monitoring and Management Guide vrealize Hyperic 5.8.4 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
McAfee Firewall Enterprise epolicy Orchestrator Extension
 Integration Guide Revision A McAfee Firewall Enterprise epolicy Orchestrator Extension COPYRIGHT Copyright 2012 McAfee, Inc. Do not copy without permission. TRADEMARK ATTRIBUTIONS McAfee, the McAfee logo,
Integration Guide Revision A McAfee Firewall Enterprise epolicy Orchestrator Extension COPYRIGHT Copyright 2012 McAfee, Inc. Do not copy without permission. TRADEMARK ATTRIBUTIONS McAfee, the McAfee logo,
