Article Number: 77 Rating: 4.8/5 from 4 votes Last Updated: Mon, Feb 27, 2017 at 5:54 PM
|
|
|
- Evelyn Thornton
- 6 years ago
- Views:
Transcription
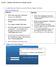
1 Nagios XI - SNMP Trap Tutorial Article Number: 77 Rating: 4.8/5 from 4 votes Last Updated: Mon, Feb 27, 2017 at 5:54 PM O ve r vie w This document describes how SNMP Traps work and integrate with Nagios XI. SNMP means Simple Network Management Protocol. Devices that have SNMP functionality can provide active and passive monitoring. Active = The Nagios XI server initiates the connection to the SNMP enabled device to retrieve information Passive = The SNMP enabled device sends Traps to the Nagios XI server This document is purely focused on SNMP Traps. Traps can be overwhelming to start with and the difficulty starts when you're trying to learn following other guides that aren't specific The goal of this tutorial is to provide step by step instructions to allow you to setup an test environment and see first hand how traps work. To make this as simple as possible we will SNMP Sender This server will SEND SNMP Traps to the receiving server. It is monitoring a single CentOS server which you will also be instructed to setup. This is achieved using the SNMP Trap Sender component built into Nagios XI SNMP Receiver This server will RECEIVE SNMP Traps from the sending server. Here you will receive status updates of the CentOS server being monitored on the sender server. After following this document and deploying the test environment you will have a solid understanding of how SNMP Traps work and will be able to easily configure SNMP Traps receive NO TE: The SNMP Sender server is purely used to provide the functionality of sending Traps to Nagios XI SNMP Receiving server, specifically for this tutorial. In your real world produc Tar ge t Audie nc e This document is intended for use by Nagios XI Administrators who wish to learn how SNMP Traps work. You will need to be able to deploy a test environment using virtual machines (VM's). Using VM's allows us to use pre-installed Nagios XI templates and makes it relatively easy to follo The G o a l The following diagram gives an overview of the test environment you will deploy. Here you can see the SNMP Sender server is monitoring a CentOS server using NRPE using active checks. Whenever a state changes occurs an any check on the SNMP Sender server Below are two screenshots showing what this tutorial will show you how to do. The top screenshot is the SNMP Sender monitoring the CentOS sever and the bottom screenshot is the
2 De plo y Envir o nme nt You need to create three VM's: 1. CentOS /8 A minimal install This will have the NRPE Agent installed on it 2. Nagios XI SNMP Sender /8 Use a Nagios XI VM downloaded from the Nagios Website (2014R2.6 +) 3. Nagios XI SNMP Receiver /8 Use a Nagios XI VM downloaded from the Nagios Website (2014R2.6 +) NO TE: These VM's will require Internet access to install certain components. When prompted below you will need to define a valid default gateway and correct DNS servers. For the C e nt OS 6.5 Ins t allat io n These steps were performed using CentOS-6.5-x86_64-bin-DVD1.iso Boot the CentOS installer ISO Select Ins ta ll o r up g ra d e a n e xis ting s ys te m You can skip the media test The GUI installer appears Click Ne xt Select your la ng ua g e and click Ne xt Select your ke yb o a rd and click Ne xt Storage - For the purposes of this guide I am: Selecting Ba s ic Stora ge e De vicee and click Ne xt Storage Device Warning Tic k the box Ap p ly my c ho ic e to a ll d e vic e s with und e te c te d p a rtitio ns o r file s ys te ms
3 Hostname Click Ye s, d is c a rd a ny d a ta Leave hostname as default Click C onfigure Ne twork Select S ys te m e th0 Click Ed it Tic k the box C o nne c t a uto ma tic a lly IPv4 SeS e ttings s tab Provide the static IP Address parameters ( /8) Click Ap p ly Click C lo s e Click Ne xt Select your Time z o ne Click Ne xt Provide a root password for this host Click Ne xt Which type of install would you like - For the purposes of this guide I am: Replace Existing Linux System(s) Click Ne xt Click Write cha nge s to dis k Select Minima l and click Ne xt Wait while the installation is performed When the installation is complete click Re boot Nagio s XI SNMP Se nde r and Re c e ive r Deploy the two Nagios XI VM's and power them on Once they have booted you will need to configure each one with it's static IP Address, follow these steps: Access the Console of your Nagios XI VM Username: ro o t Password: na gios s xi system-config-network Select De vice configura tion and press Ente r Select the network adapter e th0 and press Ente r Press the d o wn a rro w key twic e Press the s p a c e b a r to d is a b le DHC P Press the d o wn a rro w key o nc e Type the Static IP Address SNMP Sender = SNMP Receiver = Press the d o wn a rro w key o nc e Type the Netmask Press the d o wn a rro w key o nc e Type the De fa ult Ga te wa y Press the d o wn a rro w key o nc e Type the P rima ry DNS S e rve r Press the d o wn a rro w key twic e Press Ente r on the OK O K button Press the Ta b button o nc e Press Ente r on the SaS a ve button Press the Ta b button o nc e Press Ente r on the S a ve & Q uit button
4 ifdown eth0 Wait while the command completes ifup eth0 Wait while the command completes exit At this point you should open a web browser to the two Nagios XI servers to complete the Nagios XI installation. Now you have the three servers deployed ready to go. At this point it might be helpful to shut each one down and take a snapshot of it before continuing to allow you to go backwards Ins t all NRPE On The C e nt OS Se rve r Now you will install the NRPE agent on the CentOS server so we can monitor this server from our SNMP Sender Nagios XI server. Establish an SSH session to the CentOS server yum -y install wget openssl-devel cd /tmp wget Wait for the file to download tar xzf linux-nrpe-agent.tar.gz cd linux-nrpe-agent./fullinstall y Wait for the fullinstall command to complete When prompted, type the IP Address of the Nagios XI SNMP Sender: exit The NPRE Client / agent is now installed and listening on port Monit or The Ce nt OS Se rve r From The SNMP Se nde r Nagios XI Se rve r Now run a Configuration Wizard to monitor the CentOS server. Open a web page to C lic k the C onfigure o menu heading C lic k the link Run the Monitoring Wiz a rd C lic k the heading Linux S e rve r In the IP Ad d re s s fie ld type: S e le c t the Linux Distribution C e nto S Click Ne xt In the Ho s t Na me field type: CentOS Accept all the defaults EXCEPT for: Users: Warning Number: 1
5 Click Ne xt Click Finis h Warning Number: 1 Critical Number: 2 Wait while the wizard creates the services to monitor the CentOS server Click the link Vie w s ta tus d e ta ils fo r C e nto S In a couple of minutes all of these services will appear OK (some might have a warning state like Yum Updates) Now you are monitoring this CentOS server and you will be using it in testing to trigger SNMP traps. Ins t all SNMPTT o n Nagio s XI SNMP Re c e ive r Se rve r Now you'll install the required components on the Nagios XI SNMP Receiver server so it will accept SNMP Traps. Establish an SSH session to the Nagios XI SNMP Receiver server cd /tmp yum -y install wget openssl-devel Wait for the package to download / update Type wget sh./nagiosxi-snmptrap-setup.sh Wait while the components are downloaded and installed sed -i 's/.*mibs_environment.*/mibs_environment = ALL/g' /etc/snmp/snmptt.ini sed -i 's/.*translate_integers.*/translate_integers = 0/g' /etc/snmp/snmptt.ini service snmptt restart Now the Nagios XI SNMP Receiver Server is ready to receive SNMP Traps. Conf igure Nagios XI SNMP Se nde r Se rve r You have one last step to perform and your environment will be setup and sending SNMP Traps. Establish an SSH session to the Nagios XI SNMP Sender server cd /usr/local/nagiosxi/html/includes/components/snmptrapsender/ chmod +x install.sh./install.sh Wait while the components are downloaded and installed Once completed type: exit Open a web page to C lic k the Admin menu heading Under S ys te m Exte ns io ns click Ma na g e C o mp o ne nts Scroll c downo until you find S NMP Tra p S e nd e r C lic k the C o nfig ure icon Tic k the box Ena ble b Inte grag tion n Under trap hosts we need to provide the parameters of the SNMP Receiver Server Host Address: Port: 16 2
6 C lic k the Apply p SeS e ttings s button You will get the message settings updated While we are here you should save a copy of the MIBs available on this page as we will use them later on Rig ht click on NAGIOS- S - NOTIFY- MIB.txt and select Saa ve Link As Save the file to your desktop Repeat for NAGIO S - RO O T- MIB.txt Te s t Enviro nme nt De plo yme nt C o mple t e You have now completely setup the test environment and from here on the tutorial on SNMP Traps will being. At this point it might be helpful to shut each one down and take a snapsho Tut o r ia l Pr o c e s s The first part of the tutorial will show you: How traps are received Uploading MIBs Adding A SNMP Trap Service To Nagios XI At this point you will have a basic understanding of how SNMP Traps are received by Nagios XI. The second part of the tutorial will go into more detail: Reading MIBs and understanding OID's Creating SNMP Trap Events At the end of the second part of the tutorial you should have a thorough understanding of how SNMP Traps work and at this point you should be able to determine how to configure SN Tut o r ia l Pa r t 1 The focus in part one is to show you the working parts without going into too much detail (we'll save that for part two). Here you will follow these steps to send a test trap to your SNMP Receiving Server. Here's what you'll do: Open the XI Web interface on the SNMP Sending server Observe the current state of the Users service for CentOS Establish an SSH session to the CentOS server Go back to the XI SNMP Sending server Schedule an immediate check of the Users service for CentOS Watch it go into the Warning State Establish an SSH session to the XI SNMP Receiving Server See the SNMP Trap that was logged Upload a MIB file to the SNMP Receiving Server Send another SNMP Trap See the SNMP Trap that was logged Add the SNMP Trap Service To SNMP Receiving Server Send another SNMP Trap See the service status on the SNMP Receiving Server Obs e rve Us e rs Se rvic e Open a web page to CentOS C lic k the Us e rs service It should look like the following picture:
7 SSH To C e nt OS Se rve r Establish an SSH session to your CentOS server Minimize the SSH session as we only need it to establish a user login C he c k Us e rs Se rvic e To Fo rc e An SNMP Trap To Be Se nt Go b a c k to the Nagios XI page with the Us e rs service C lic k the ScheS c dule d a force e d imme diad te chec ck c k link Wait while it executes the check and the screen updates It will now go into a Warning state and like the following picture: C o nf irm SNMP Trap Is Re c e ive d On SNMP Re c e ive r Establish an SSH session to your SNMP Receiving server cat /var/log/snmptt/snmpttunknown.log You will get an output similar to the following picture: So what you have confirmed here is that the SNMP Receiving server successfully received a trap from the sending server. Right now it is not doing anything as it is going into the snmp The snmpttunknown.log file is where traps go that the SNMPTT service does not know what to do with. The next step will be to upload MIBs. Leave the SSH session to your S NMP Re c e iving server o p e n as we will return to it shortly. Before you continue, e xit the SSH session on your CentOS server as this will return the service check back to an OK state. Upload MIB File s Remember those two files you saved to your desktop earlier? They were NAGIOS-ROOT-MIB.txt and NAGIOS-NOTIFY-MIB.txt. Now you will upload them to your SNMP Receiving serve Open a web page to C lic k the Admin menu heading Under S ys te m Exte ns io ns click Ma na g e MIBs C lic k the Brows e button Navigate to your Desktop and double click the file NAGIOS-S - ROOT-O MIB.txt Leave the Process trap box un-ticked
8 C lic k the Uploa a d MIB button You will get a message New MIB was installed successfully C lic k the Brows e button Navigate to your Desktop and double click the file NAGIOS-S - NOTIFY- MIB.txt Tic k the box P ro c e s s tra p C lic k the Uploa a d MIB button You will get a message saying MIB file successfully processed Re turn to your S S H s e s s io n on your SNMP S Re cec e iving server service snmptt restart You will get a message saying the snmptt service stopped and started Now that you have uploaded the Nagios SNMP MIBs, the Receiving server will now know what to do with the SNMP Traps it will receive. Forc e An SNMP Trap To Be Se nt Now you will re-send that same trap again and observe what the SNMP Receiving server did this time. Establish an SSH session to your C e nto S server Minimize the SSH session as we only need it to establish a user login Open a web page to CentOS C lic k the Us e rs service C lic k the ScheS c dule d a force e d imme diad te chec ck c k link Wait while it executes the check and the screen updates, it will go into a warning state Re turn to your S S H s e s s io n on your SNMP S Re cec e iving server cat /var/log/snmptt/snmptt.log You will get an output similar to the picture below: So what you have confirmed here is that the SNMP Receiving server successfully received a trap from the sending server AND it is recording it into the snmptt.log file. The snmptt.log fi Add SNMP Traps Se rvic e t o SNMP Re c e iving Se rve r Now you will log into Nagios XI on the SNMP Receiving server and create the SNMP Trap service. Open a web page to http :// /na gios xi C lic k the Admin menu heading Under Monitoring C onfig click Unconfigure d Obje cts You should see something similar to the picture below: In the Actions column click the Play button (CC onfigure ) This opens the Passive Object Monitoring wizard at Step 3 as per the picture below:
9 Click Ne xt Click Finis h Wait while the wizard creates the SNMP Traps service Click the link Vie w s ta tus d e ta ils fo r s nmp s e nd e r You will see a picture similar to below: NO TE: this will display No check results for service yet as you need to send another trap before it gets updated. Fo rc e An SNMP Trap To Be Se nt And Se e St at us On SNMP Re c e iving Se rve r Now you will re-send that same trap again and observe what the SNMP Receiving server did this time. Re turn to your S S H s e s s io n to your C e nto S server Type exit Open a web page to CentOS C lic k the Us e rs service C lic k the ScheS c dule d a force e d imme diad te chec ck c k link Wait while it executes the check and the screen updates, it will go into an OK state Open a web page to SNMP Traps C lic k the SNMP S Tra ps p s service You will see a picture similar to below: Now you can see the SNMP Traps service on the SNMP Receiving server has updated
10 Now you can see the SNMP Traps service on the SNMP Receiving server has updated There is quite a bit of information there, you will learn in Part 2 of this tutorial on how to optimize this The key information here is "CentOS Users 0 OK 0 users currently logged in" Now SSHS H back into the C e nto S server and force an immediate check on the Us e rs service on the SNMP S SeS e nding server This will enter a WARNING state again and will send another trap. It will look like the picture below: On the SNMP Receiving server you will see that the SNMP Traps service looks like this: The key information here is "CentOS Users 1 WARNING 1 users currently logged in" However as you can see from the screenshot the actual service STATUS of the SNMP Traps service is "Ok" whereas on the SNMP Sending server it is WARNING. The reason for this is Tut orial Part 1 - Summary The steps you have followed so far have given you a basic example of how SNMP traps are received and processed by Nagios XI. However as you have seen, it looks like there is mo In Part 2 of the tutorial we'll delve into much detail about how this works and by the end you'll be on your way to mastering SNMP Traps. Tut o r ia l Pa r t 2 This section of the tutorial will have a lot more detail. The basic topics you'll cover are: Showing how the current SNMP Trap Receiving configuration is basic and the limitations that come with this Explaining how to read a MIB and understanding OIDs Explaining how SNMPTT sends traps to Nagios XI Edit the SNMPTT configuration file to create custom EVENTS What is SNMPTT? SNMP Trap Translator is the program that runs on the SNMP Receiving server. It takes the events from the SNMP Trap Daemon (SNMPTRAPD) service and figures o SNMP Trap Re c e iving Conf igurat ion At the end of part one you saw that when a SNMP Trap was received it came with a lot of information AND it did not correctly reflect the state of the service on the sending server. He Return to your S S H s e s s io n to your C e nto S server service crond stop Open a web page to CentOS C lic k the C ro n S c he d uling Da e mo n service C lic k the ScheS c dule d a force e d imme diad te chec ck c k link Wait while it executes the check and the screen updates, it will go into an CRITICAL state as per the picture below:
11 Open a web page to SNMP Traps C lic k the SNMP S Tra ps p s service On the SNMP Receiving server you will see that the SNMP Traps service looks like the picture below: Here you can see it has updated the status to reflect the sending server HOWEVER we no longer have any information about the "Users service" which was the previous status What was just demonstrated is that our current SNMP Trap configuration will only show the status of the last SNMP Trap received. In particular this SNMP Trap service is for ALL SNMP All of this can be configured to make it more meaningful and useful. So far we have identified the following: A lot more information is being display than what is necessary The service status is not correctly reflected (always showing Ok) All traps are received on just one services The next step is to learn about SNMP OIDs and MIBs. OIDs and MIBs What do these acronyms mean? OID = Object Identifier This string is a series of number numbers separated with periods (.) MIB = Management Information Base This is a text file containing all the information about specific OIDs and how they relate to each other Here's a picture of that first SNMP Trap you received: On the first line we have This is the OID Think of each number as a branch in a tree. Every time you have a period followed by another number you are creating another branch in the tree Eventually the last number will reference a value that is being sent (you could say it was a leaf) Think of it along the lines of computer. motherboard. disk drive. file system. folder. file (this is just a theoretical example) For every company out there that has an SNMP enabled device, they would have applied to IANA (Internet Assigned Numbers Authority) to obtain their own Private Enterprise Number So this means that in all of our OIDs, the first series of numbers will always be the same = Enterprises # = Nagios If for example you had a Dell device, their PEN is 674, so they would have: = Enterprises # 674 = Dell Inc.
12 Now every number that follows will relate to a specific Nagios item. How do you know what each of the numbers mean? This is where a MIB comes into play. We have two MIB Here's a diagram of the two MIB files. Below is an explanation of how this all works: NAGIO S - RO O T- MIB.txt is the "top level" MIB file which the NOTIFY file relies on, here is an extract from the start of the file: NAGIOS-ROOT-MIB DEFINITIONS ::= BEGIN IMPORTS MODULE-IDENTITY, enterprises FROM SNMPv2-SMI TEXTUAL-CONVENTION FROM SNMPv2-TC; nagios MODULE-IDENTITY LAST-UPDATED " Z" -- March 9, 2005 ORGANIZATION "Nagios" CONTACT-INFO " Blah Blah Blah " DESCRIPTION "Objects for Nagios(tm) NMS" REVISION " Z" -- March 9, 2005
13 DESCRIPTION "Spell check" REVISION " Z" --January 20, 2005 DESCRIPTION "Initial Version" ::= {enterprises 20006} What is important here is the MODULE- IDENTITY which is called na gios s. This contains all the information about this MIB and it ends with ::= {e nte rp ris e s }.} What this mea Now the remaining information you'll need to continue to decipher the OID will be defined in the NAGIOS- NOTIFY- MIB.txt file. Here is an extract from the start of the NAGIOS- S - NOTIFY- MIB.txt file: NAGIOS-NOTIFY-MIB DEFINITIONS ::= BEGIN IMPORTS MODULE-IDENTITY, OBJECT-TYPE, NOTIFICATION-TYPE, Integer32 FROM SNMPv2-SMI nagios,notifytype,hoststateid,hoststatetype,servicestateid FROM NAGIOS-ROOT-MIB; nagiosnotify MODULE-IDENTITY LAST-UPDATED " Z" -- March 9, 2005 ORGANIZATION "Nagios" CONTACT-INFO " Blah Blah Blah " DESCRIPTION " DESCRIBE DESCRIBE DESCRIBE " REVISION " Z" -- March 9, 2005 DESCRIPTION "Spell check" REVISION " Z" --January 20, 2005 DESCRIPTION "Initial Version" ::= { nagios 1 } First, the IMPORTS section shows that it is importing na gios s (PEN 20006) from the MIB file NAGIO S - RO O T- MIB. Next is the MODULE- IDENTITY which is called na gios s Notify. This contains all the information about this MIB and it ends with ::= {na g io s 1}. What this means is that this module fo Going back to our original OID number it is: To find this in the NAGIOS-S - NOTIFY- MIB.txt file, all you need to do is search for: ::= { nagiosnotify 7 } Which results in the following: nsvcevent NOTIFICATION-TYPE OBJECTS { nhostname, nhoststateid, nsvcdesc, nsvcstateid, nsvcattempt, nsvcdurationsec, nsvcgroupname, nsvclastcheck, nsvclastchange, nsvcoutput } STATUS current DESCRIPTION "The SNMP trap that is generated as a result of an event with the service in Nagios." ::= { nagiosnotify 7 } What this means is that the OID is an SNMP Trap that was generated as a result of a service event in Nagios. This makes sense because: You had a service on the sending server that you forced an immediate check to be scheduled The check triggered a threshold which made it enter a warning state The sending server sent a trap to the receiving server The trap received contained the data One last thing to point out is that this trap contains O BJ EC TS. So instead of the trap just being a value like "87" or "NIC DOWN" it contains multiple values such as nho s tna me, nho s Going back to the original trap, you can see all the different values are OBJECTS in this trap:
14 How do you know what object relates to what value? The Va lue 0-10 fields are all the information about the sending server, the device that actually sends the trap. The Ent Va lue 0 Looking at Ent Va lue 0 : Refer to the picture below to understand what this OID means: nsvchostname OID = Description = Ho s tna me a s s p e c ifie d in the Na g io s c o nfig ura tio n file. Value = C e nto S So this is correct the, the trap was related to the CentOS server which had the hostname of C e nto S The other three values are: nsvcdesc OID = Description = This va lue is ta ke n from the de s cription dire ctive of the s e rvice de finition. Value = Us e rs nsvcstateid OID = Description = A numb e r tha t c o rre s p o nd s to the c urre nt s ta te o f the s e rvic e : 0 =O K, 1=WARNING, 2 =C RITIC AL, 3=UNKNO WN Value = 1 nsvcoutput OID = Description = The te xt o utp ut fro m the la s t s e rvic e c he c k (i.e. P ing O K) Value = USERS WARNING - 1 us e rs currec ntly logge g g e d in What you have learned here is that from just one OID ( ) information from any service monitored by the sending Nagios XI server can be sent through to the receiving server. That completes the section on OIDs and MIBs. Se nding Traps To Nagios XI Remember how you uploaded the two MIB files into Nagios XI earlier? When uploading the NAGIOS-S - NOTIFY- MIB.txt file you selected the box to Process trap. What this did was:
15 Read through the MIB file and find any SNMP Traps Add these traps to the snmptt configuration file /etc/snmp/snmptt.conf These traps are added as EVENTS to the new file EVENTS tell the SNMPTT service what to do with the SNMPT Trap Have a look at the EVENTS that were created in the SNMPTT configuration. Primarily there were four EVENTs added to /e tc /s nmp /s nmptt.conf o nf however you are going to focus on se EVENT nsvcevent "Status Events" Normal FORMAT The SNMP trap that is generated as a result of an event with the service $* EXEC /usr/local/bin/snmptraphandling.py "$r" "SNMP Traps" "$s" "$@" "$-*" "The SNMP trap that is generated as a result of an event with the SDESC The SNMP trap that is generated as a result of an event with the service in Nagios. Variables: 1: nhostname 2: nhoststateid 3: nsvcdesc 4: nsvcstateid 5: nsvcattempt 6: nsvcdurationsec 7: nsvcgroupname 8: nsvclastcheck 9: nsvclastchange 10: nsvcoutput EDESC The first thing to explain is that everything between SDESC and EDESCC is purely there as comments. It has no affect whatsoever on the notification to Nagios. With that being the case, this leaves three lines remaining which are configurable: EVENT FORMAT EXEC This line contains the OID which is matched against. This line is what is logged in any log mechanisms that SNMPTT uses. This line is what sends the trap to Nagios. In this case it executes a python script and it is the python script that actually does the talking to Nagios. One of the powerful features of SNMPTT is the ability to use variables, this way you can reference different objects in the trap itself. This allows you to make flexible configurations. The EVENT line is broken up into four arguments separated by spaces: EVENT nsvcevent "Status Events" Normal Argument #1 = Unique text label (alias) containing NO spaces nsvcevent Argument #2 = The OID you want to match against Argument #3 = Used when logging output, for your purposes "Status Events" is all that is required "Status Events" Argument #4 = Severity. This is used in the output and the logging and is also referenced as a variable ($s). Normal The FORMAT line is one long string and can contains variables. FORMAT The SNMP trap that is generated as a result of an event with the service $* In this example you can see that $ * has been used, this is a variable $ * means it will expand all the variables (OO BJ EC TS ) that were sent with the trap For example you can see in the picture below that it has logged the ns vc Ho s tna me, ns vc De s c n, n nsvcsta S te ID, and nsvcoutput. This give you the string: The SNMP trap that is generated as a result of an event with the service CentOS Users 1 USERS WARNING - 1 users currently logged in The EXEC line is the command that will be executed. SNMPTT is using the script /us r/loca l/bin/s nmptra pha ndling.py which sends PASSIVE check results to the Nagios command pipe. It requires the following arguments: <HOST> <SERVICE> <SEVERITY> <TIME> <PERFDATA> <DATA>
16 <HOST> <SERVICE> <SEVERITY> <TIME> <PERFDATA> <DATA> <HOST> = The host object in Nagios that this event is for <SERVICE> = The service object in Nagios this event is for <SEVERITY> = The state of the object, which can be INFORMATIONAL, NORMAL, SEVERE, MAJOR, CRITICAL, WARNING, MINOR (the script turns these into Nagios status codes 0/ <TIME> = The time which should be recored for the passive check <PERFDATA> = Any performance data (can be left empty) <DATA> = The useful status information NOTE: It's important that each argument is enclosed in "double quotes". The EXEC line added by default is: /usr/local/bin/snmptraphandling.py "$r" "SNMP Traps" "$s" "$@" "$-*" "The SNMP trap that is generated as a result of an event with the The arguments being sent also include variables which are explained below: <HOST> = "$r" "$r" = The hostname of the device that sent the trap to this server <SERVICE> = "SNMP Traps" The name of the service we are sending a Passive check for is "SNMP Traps" <SEVERITY> = "$s" "$s" = the SEVERITY defined in the EVENT line (in this case it is Normal) <TIME> = "$@" "$@" = the EPOCH value of when the trap was received <PERFDATA> = "$-*" $ - * means it will expand all the variables (OO BJ EC TS ) that were sent with the trap in the format of "variable name (variable type):value" nsvchostname (OCTETSTR):CentOS nsvcdesc (OCTETSTR):Users nsvcstateid (INTEGER):0 nsvcoutput (OCTETSTR):USERS OK - 0 users currently log <DATA> = "The SNMP trap that is generated as a result of an event with the service $*" $ * means it will expand all the variables (OO BJ EC TS ) that were sent with the trap (exactly the same as the FORMAT line) When you put it all together what is actually being executed by the EXEC line is: /usr/local/bin/snmptraphandling.py "snmpsender" "SNMP Traps" "Normal" " " "nsvchostname (OCTETSTR):CentOS nsvcdesc (OCTETSTR): When this EXEC statement is executed, Nagios XI will receive it and do one of two things: IF there is already an SNMP Traps service for the host being targeted: It will update that service and it will NOT log anything in nagios.log (this can be enabled) IF there is NOT an SNMP Traps service for the host being targeted: The following entries will be logged in nagios.log [ ] Warning: Passive check result was received for service 'SNMP Traps' on host 'snmpsender', but the service could not be found! [ ] Error: External command failed -> PROCESS_SERVICE_CHECK_RESULT;snmpsender;SNMP Traps;0;The SNMP trap that is generated as a result of an event w [ ] External command error: Command failed The "SNMP Traps" service will appear as an Unconfigured object under Admin > Monitoring C onfig > Unconfigure d Obje cts Below is a picture showing an SNMP Trap, the EVENT configuration in SNMPTT and the final result in Nagios XI:
17 At this point you have been shown how SNMP Traps integrated into Nagios XI. You have also learned what an OID is and how to read a MIB file. C re at e C us t o m Eve nt s In SNMPTT The next step involves modifying the SNMPTT EVENTs to produce more meaningful data to be sent to Nagios XI. The goal here is to do the following: Multiple SNMP Trap services in Nagios XI to reflect each monitored service of the CentOS server Only send important information to Nagios XI (don't cloud the issue with too much information) Service status to be correctly reflected (OK / WARNING / CRITICAL / UNKNOWN) The following steps will require you to edit the.conf files at the command line on the SNMP Receiving server. You will be instructed to use the command line editor called nano. Before Es ta b lis h an S S H s e s s io n to yum -y install nano Wait while nano is installed/updated Leave the ssh session open as we'll be using it next Now you will edit the /e tc /s nmp /s nmptt.conf o nf file: nano /etc/snmp/snmptt.conf Use the down d o a rrow w key until you reach the section EVENT nsvceve nt "Sta tus Eve nts " Norma l Change the FORMAT line so it is as follows: FORMAT An SNMP trap received from a Nagios XI SERVICE with the details: $* All that you have done here is to make the message that gets logged to snmptt.log a little more meaningful Change the EXEC line so it is as follows: EXEC /usr/local/bin/snmptraphandling.py "$1" "SNMP Trap - $2" "$s" "$@" "" "$4" Press C TRL + X Y To save the changes Press Ente r to save the changes to the existing file service snmptt restart What does the EXEC line do now? It is using the values of the O BJ EC TS that exist in the trap. Here are the O BJ EC TS that exist in the trap: In the SNMPTT config file, these values can be referenced as: Ent Value 0 = $1 Ent Value 1 = $2 Ent Value 2 = $3 Ent Value 3 = $4 With this in mind, here's the new EXEC line broken down: EXEC /usr/local/bin/snmptraphandling.py "$1" "SNMP Trap - $2" "$s" "$@" "" "$4"
18 EXEC /usr/local/bin/snmptraphandling.py "$1" "SNMP Trap - $2" "$s" "$@" "" "$4" <HOST> = "$1" "$1" = CentOS <SERVICE> = "SNMP Traps - $2" The name of the service we are sending a Passive check for is "SNMP Traps - Users" <SEVERITY> = "$s" "$s" = the SEVERITY defined in the EVENT line (in this case it is Normal) <TIME> = "$@" "$@" = the EPOCH value of when the trap was received <PERFDATA> = "" NO performance data is being sent so we are providing empty quotes <DATA> = "$4" The status data we are sending is "USERS WARNING - 1 users currently logged in" What you are doing down is sending a Passive check result for the service S NMP Tra p s - Us e rs for the host C e nto S. These will come through as an Unconfigured Object initially b Now send a trap and see how the service appears as in Nagios XI. Establish an S S H s e s s io n to your C e nto S server Minimize the SSH session as we only need it to establish a user login Open a web page to CentOS C lic k the Us e rs service C lic k the ScheS c dule d a force e d imme diad te chec ck c k link Wait while it executes the check and the screen updates, it will go into a warning state Open a web page to C lic k the Admin menu heading Under Monitoring C onfig click Unconfigure d Obje cts You should see something similar to the picture below: To create the SNMP S Tra p - Us e rs service: In the Actions column click the Pla y button (Configure) This opens the Passive Object Monitoring wizard at Step 3 Click Ne xt Click Finis h Wait while the wizard creates the SNMP Traps service C lic k the link Vie w s ta tus d e ta ils fo r C e nto S You will see a picture similar to below: Now you need to send another trap for the service to update, we'll come back to this screen shortly
19 Now you need to send another trap for the service to update, we'll come back to this screen shortly Re turn to your S S H s e s s io n to your C e nto S server exit Return to the SENDING SNMP server and Schec dule a force e d imme dia te che ckk for the Us e rs service Wait while it executes the check and the screen updates, it will go into an OK state Return to the REC EIVING SNMP server and the SNMP S Tra p - Us e rs service will now be updated like the picture below: This reflects exactly what appears on the sending server (except we've pre-pended the service name with SNMP Tra p - ) Now test the service going into a WARNING state Establish an S S H s e s s io n to your C e nto S server Minimize the SSH session as we only need it to establish a user login Return to the SENDING SNMP server and Schec dule a force e d imme dia te che ckk for the Us e rs service Wait while it executes the check and the screen updates, it will go into a Warning state Return to the REC EIVING SNMP server and the SNMP S Tra p - Us e rs service will now be updated like the picture below: HOLD ON! O!! Even though the Status Information says USERS WARNING the Status column is still Okk Correct. You need to make some more changes to the /e tc /s nmp /s nmptt.conf file before the service state will be reflected. This will be covered next. This was intentional as part of the tutorial. You are being shown the configuration step by step so you understand each change you are making. The way the service state is being reflected in Nagios is when we send the S EVERITY value using the "$s s " variable. You define the SEVERITY as part of the EVENT line, in this case What you can do is create MULTIPLE EVENTS in the /e tc /s nmp /s nmptt.conf file for the SAME OID. Each EVENT will have a different SEVERITY value. So when the EXEC line sends However HOW does SNMPTT know which EVENT to use when there are multiple events defined for the SAME OID? We can add an additional line to the EVENT config called a MATC In English, you are going to create three separate expressions: If the service state in the trap is 0 then it will be Norma l If the service state in the trap is 1 then it will be Wa rning If the service state in the trap is 2 or 3 then it will be C ritic a l First look at the trap data: As explained earlier, Ent Value 2 (nsvcstateid) = $ 3 and in the picture above the current state is 1 (Warning). So the three separate MATCH expressions will be: Ok MATCH $3: 0 Warning MATCH $3: 1 Critical or Unknown MATCH $3: 2 MATCH $3: 3 An EVENT can have multiple MATC H statements. Because there isn't an Unknown SEVERITY we will use C ritic a l for the Unknown service status's from Nagios. In the next steps you will edit the /e tc /s nmp /s nmp tt.c o nf file and a d d the extra EVENT statements. NOTE: Each EVENT is id e ntic a l for the other e xc e p t for the EVENT line and the MATC H line.
20 Return to the S S H s e s s io n you have open on the REC EIVING SNMP server nano /etc/snmp/snmptt.conf Use the down d o a rrow w key until you reach the section EVENT nsvceve nt "Sta tus Eve nts " Norma l This EVENT line d o e s n't c ha ng e as it is already Norma l After the EXEC line press Ente r to start a new line MATCH $3: 0 NOTE: This EVENT will only be executed if the service state of 0 exists in the trap in $ 3 Use the d o wn a rro w key until you go past the EDES C line Afte r the EDESC C line press Ente r twicee Add the following four lines: EVENT nsvcevent "Status Events" Warning FORMAT An SNMP trap received from a Nagios XI SERVICE with the details: $* EXEC /usr/local/bin/snmptraphandling.py "$1" "SNMP Trap - $2" "$s" "$@" "" "$4" MATCH $3: 1 Note: This EVENT will only be executed if the service state of 1 exists in the trap in $ 3 Afte r the MATC H line press Ente r twic e Add the following five lines: EVENT nsvcevent "Status Events" Critical FORMAT An SNMP trap received from a Nagios XI SERVICE with the details: $* EXEC /usr/local/bin/snmptraphandling.py "$1" "SNMP Trap - $2" "$s" "$@" "" "$4" MATCH $3: 2 MATCH $3: 3 This EVENT will only be executed if the service state of 2 or 3 exists in the trap in $ 3 Press C TRL + X Y To save the changes Press Ente r to save the changes to the existing file service snmptt restart Now you can do some tests to make sure it is working as expected. Re turn to your S S H s e s s io n to your C e nto S server exit Re turn to the SENDING S SNMP server and Schec dule a force e d imme dia te che ckk for the Us e rs service Wait while it executes the check and the screen updates, it will go into an OK state Re turn to the REC EIVING SNMP server and the SNMP S Tra p - Us e rs service will now be updated like the picture below: This reflects exactly what appears on the sending server, nothing new here. Now test the service going into a WARNING state Es ta b lis h an S S H s e s s io n to your C e nto S server Minimize the SSH session as we only need it to establish a user login Re turn to the SENDING S SNMP server and Schec dule a force e d imme dia te che ckk for the Us e rs service Wait while it executes the check and the screen updates, it will go into a Warning state Re turn to the REC EIVING SNMP server and the SNMP S Tra p - Us e rs service will now be updated like the picture below:
21 Now it is correctly reflecting the Warning status. Now let's test Critical. Es ta b lis h an ADDITIO NAL S S H session to your C e nto S server Minimize the SSH session as we only need it to establish a second user login Re turn to the SENDING S SNMP server and Schec dule a force e d imme dia te che ckk for the Us e rs service Wait while it executes the check and the screen updates, it will go into a critical state Re turn to the REC EIVING SNMP server and the SNMP S Tra p - Us e rs service will now be updated like the picture below: Now it is correctly reflecting the Critical status At this point we have achieved the following: Only send important information to Nagios XI (don't cloud the issue with too much information) Service status to be correctly reflected (OK / WARNING / CRITICAL / UNKNOWN) HOWEVER we still haven't done this: Multiple SNMP Trap services in Nagios XI to reflect each monitored service of the CentOS server Throughout this tutorial you have seen that when a trap is received on a Nagios XI server AND it doesn't already exist as a service in Nagios XI, it will appear under the Unconfigured However they will only appear under Unconfigured Objects when the service changes state. So it might be a while before some are received. If you wanted to create these services now you could actually go into Core Configuration Manager and make multiple copies of the SNMP Trap - Users service and rename each on Another way to do this is to disconnect the CentOS server from the network and by doing this all of the services will change their state. In addition to this you will see the host state of Open a c o ns o le session to your C e nto S VM Login to the console as ro o t ifdown eth0 Open a web page to CentOS C lic k the host object C e nto S (the word CentOS) Under Quick Actions click Sche dule a force d imme dia te che ck C lic k the Ad va nc e d tab Under C o mma nd s click Scc he d ule imme d ia te c he c k fo r a ll s e rvic e s o n this ho s t Click C ommit Click Do ne CentOS Here you will see something similar to the picture below:
22 Now a trap for each of these services has been sent through to the REC EIVING SNMP server Open a web page to C lic k the Admin menu heading Under Monitoring C onfig click Unconfigure d Obje cts You should see something similar to the picture below: To create all these SNMP Tra p - xxx services: Tic k the b o x next to C e nto S At the b o tto m next to With S e le c te d click the PlaP y button (Configure) This opens the Passive Object Monitoring wizard at Step 3 Click Ne xt Click Finis h Wait while the wizard creates the SNMP Traps service Click the link Vie w s ta tus d e ta ils fo r C e nto S Now you will have all the SNMP S Tra p - xxx services created Now you can bring the C e nto S server online and all of these services will be updated Re turn to the c o ns o le session to your C e nto S VM ifup eth0 Open a web page to CentOS C lic k the host object C e nto S (the word CentOS) Under Quick Actions click Sche dule a force d imme dia te che ck C lic k the Ad va nc e d tab Under C o mma nd s click S c he d ule imme d ia te c he c k fo r a ll s e rvic e s o n this ho s t Click C ommit Click Do ne Open a web page to CentOS Here you will see something similar to the picture below:
23 Now you have all the SNMP Trap services receiving data for the CentOS host HO LD O N!!! What about the CentOS ho s t object? It is still g re y in the pep e nding state. If you click on the host object C e nto S (the word CentOS) you'll see it says Ho s t c he c k is p e nd ing... This is because the SNMP Traps that arrive for the HO S T object come in on a different O ID! HOST S T traps use the OID The last part of this tutorial will be to add the EVENT statements to the /e tc /s nmp /s nmptt.conf file. This will ensure that the HOST object also gets it's status updated. Re turn to the S S H s e s s io n you have open on the REC EIVING SNMP server cat /var/log/snmptt/snmptt.log grep The last line will be similar to the picture below: This is showing you the trap received for the HOST object. nano /etc/snmp/snmptt.conf Use the d o wn a rro w key until you reach the section EVENT nhos s teve nt "Sta tus Eve nts " Norma l This EVENT line doesn't change as it is already Norma l Change the FORMAT line so it is as follows: FORMAT An SNMP trap received from a Nagios XI HOST with the details: $* All that you have done here is to make the message that gets logged to snmptt.log a little more meaningful Change the EXEC line so it is as follows: EXEC /usr/local/bin/snmptraphandling.py "$1" "PROCESS_HOST_CHECK_RESULT" "$s" "$@" "" "$3" After the EXEC line press Ente r to start a new line MATCH $2: 0 This EVENT will only be executed if the ho s t s ta te of 0 exists in the trap in $ 2 Use the d o wn a rro w key until you go past the EDES C line After the EDESCC line press Ente r twice Add the following six lines: EVENT nhostevent "Status Events" Critical FORMAT An SNMP trap received from a Nagios XI HOST with the details: $* EXEC /usr/local/bin/snmptraphandling.py "$1" "PROCESS_HOST_CHECK_RESULT" "$s" "$@" "" "$3" MATCH $2: 1 MATCH $2: 2 MATCH $2: 3 This EVENT will only be executed if the ho s t s ta te of 1 or 2 or 3 exists in the trap in $ 2
24 Press C TRL + X Y to save the changes Press Ente r to save the changes to the existing file service snmptt restart Now you can do some tests to make sure it is working as expected. Re turn to the c o ns o le session to your C e nto S VM ifdown eth0 Open a web page to CentOS C lic k the ho s t object C e nto S (the word CentOS) Under Quick Actions click Sche dule a force d imme dia te che ck Wait while it executes the check and the screen updates, it will go into a critical state Open a web page to CentOS Here you will see that the HO S T object C e nto S is now in a C ritc a l state and the color is red Re turn to the c o ns o le session to your C e nto S VM ifup eth0 Within a minute or so the everything should return back to an OK state on the REC EIVING SNMP server. The ho s t o b je c t now has a g re e n b a c kg ro und, similar to the picture below
25 Congratulations, you've now completed the SNMP Trap Tutorial. S NMP Tr a p Tut o r ia l - S umma r y While the S in SNMP stands for Simple, you've seen how it can be hard to learn SNMP. Hopefully this tutorial has helped break down some of these barriers. At this point you should have a good understanding of how SNMP Traps are received and handled by Nagios XI. Armed this this knowledge you will now be able to setup Nagios XI to receive SNMP Traps from various SNMP enabled devices on your network. Fina l Tho ught s For any support related questions please visit the Nagios Support Forums at: Posted by: tle a - Mon, Mar 9, 2015 at 10:19 PM. This article has been viewed times. Online URL:
Article Number: 549 Rating: Unrated Last Updated: Tue, May 30, 2017 at 11:02 AM
 Configuring Your Server With A Static IP Address Article Number: 549 Rating: Unrated Last Updated: Tue, May 30, 2017 at 11:02 AM O ve r vie w This KB article shows you how to configure your Nagios server
Configuring Your Server With A Static IP Address Article Number: 549 Rating: Unrated Last Updated: Tue, May 30, 2017 at 11:02 AM O ve r vie w This KB article shows you how to configure your Nagios server
It is important to remember that an external worker needs all of the plugins installed on it so it can execute the checks that are handed to it.
 Nagios XI - Mod-Gearman Queues and Workers Article Number: 484 Rating: 5/5 from 3 votes Last Updated: Thu, Jul 6, 2017 at 5:30 PM O ve r vie w The purpose of this article is to explain how queues work
Nagios XI - Mod-Gearman Queues and Workers Article Number: 484 Rating: 5/5 from 3 votes Last Updated: Thu, Jul 6, 2017 at 5:30 PM O ve r vie w The purpose of this article is to explain how queues work
This is sometimes necessary to free up disk space on a volume that cannot have extra disk space easily added.
 Movin g /var/log/ Article Number: 473 Rating: Unrated Last Updated: Tue, Mar 29, 2016 at 5:56 PM O ve r vie w This KB article will walk you through the steps of moving the /var/log directory to a new disk/volume
Movin g /var/log/ Article Number: 473 Rating: Unrated Last Updated: Tue, Mar 29, 2016 at 5:56 PM O ve r vie w This KB article will walk you through the steps of moving the /var/log directory to a new disk/volume
Article Number: 38 Rating: Unrated Last Updated: Thu, Apr 28, 2016 at 9:49 PM
 Nagios Log Server - Logs Not Searchable or Not Coming In Article Number: 38 Rating: Unrated Last Updated: Thu, Apr 28, 2016 at 9:49 PM O ve r vie w When running a query in a dashboard, logs are not showing
Nagios Log Server - Logs Not Searchable or Not Coming In Article Number: 38 Rating: Unrated Last Updated: Thu, Apr 28, 2016 at 9:49 PM O ve r vie w When running a query in a dashboard, logs are not showing
Article Number: 722 Rating: Unrated Last Updated: Thu, Jul 20, 2017 at 12:31 AM
 Nagios XI - Using Scripts / Plugins With NCPA Article Number: 7 Rating: Unrated Last Updated: Thu, Jul 0, 017 at 1:31 AM O ve r vie w This KB article explains how to use external scripts / plugins with
Nagios XI - Using Scripts / Plugins With NCPA Article Number: 7 Rating: Unrated Last Updated: Thu, Jul 0, 017 at 1:31 AM O ve r vie w This KB article explains how to use external scripts / plugins with
Article Number: 513 Rating: 5/5 from 1 votes Last Updated: Tue, Jul 19, 2016 at 10:09 PM
 Nagios XI - MySQL/MariaDB - Max Connections Article Number: 513 Rating: 5/5 from 1 votes Last Updated: Tue, Jul 19, 2016 at 10:09 PM O ve r vie w This KB article is about the MySQL / MariaDB database and
Nagios XI - MySQL/MariaDB - Max Connections Article Number: 513 Rating: 5/5 from 1 votes Last Updated: Tue, Jul 19, 2016 at 10:09 PM O ve r vie w This KB article is about the MySQL / MariaDB database and
Article Number: 602 Rating: Unrated Last Updated: Tue, Jan 2, 2018 at 5:13 PM
 NRDP - Installing NRDP From Source Article Number: 602 Rating: Unrated Last Updated: Tue, Jan 2, 2018 at 5:13 PM I ns t a lling NRDP Fr o m S o ur c e This document describes how to install Nagios Remote
NRDP - Installing NRDP From Source Article Number: 602 Rating: Unrated Last Updated: Tue, Jan 2, 2018 at 5:13 PM I ns t a lling NRDP Fr o m S o ur c e This document describes how to install Nagios Remote
This document is intended for use by Nagios Administrators that want to monitor SNMP devices using an SNMP Walk to discover it's available objects.
 Purpose This document describes how to use the SNMP Walk Wizard, it briefly explains SNMP and how to reference a MIB file or OID. SNMP is the acronym for Simple Network Management Protocol. An SNMP Walk
Purpose This document describes how to use the SNMP Walk Wizard, it briefly explains SNMP and how to reference a MIB file or OID. SNMP is the acronym for Simple Network Management Protocol. An SNMP Walk
This guide is broken up into several sections and covers different Linux distributions and non- Linux operating systems.
 NRPE - How To Uninstall NRPE Article Number: 741 Rating: Unrated Last Updated: Fri, Aug 11, 2017 at 1:02 AM Unins t a lling NRPE This document describes how to unins ta ll NRPE that is installed from source.
NRPE - How To Uninstall NRPE Article Number: 741 Rating: Unrated Last Updated: Fri, Aug 11, 2017 at 1:02 AM Unins t a lling NRPE This document describes how to unins ta ll NRPE that is installed from source.
OK: {C: 68% free / 99.51GB total} 'C: free'= g; ; ;0; 'C: free %'=68%;20;10;0;100
 Disk Space Checks Article Number: 770 Rating: Unrated Last Updated: Mon, Nov 13, 2017 at 6:27 PM Dis k S pa c e C he c ks Disk space checks vary depending on the following factors: Disk Free Space - Percentage
Disk Space Checks Article Number: 770 Rating: Unrated Last Updated: Mon, Nov 13, 2017 at 6:27 PM Dis k S pa c e C he c ks Disk space checks vary depending on the following factors: Disk Free Space - Percentage
Next. Welcome! This guide will get you started down the path to bulk text messaging excellence. Let s start by going over the basics of the system
 A-PDF Merger DEMO : Purchase from www.a-pdf.com to remove the watermark User Guide Next Welcome! This guide will get you started down the path to bulk text messaging excellence. Let s start by going over
A-PDF Merger DEMO : Purchase from www.a-pdf.com to remove the watermark User Guide Next Welcome! This guide will get you started down the path to bulk text messaging excellence. Let s start by going over
Table of Contents 1 V3 & V4 Appliance Quick Start V4 Appliance Reference...3
 Table of Contents 1 V & V4 Appliance Quick Start...1 1.1 Quick Start...1 1.2 Accessing Appliance Menus...1 1. Updating Appliance...1 1.4 Webmin...1 1.5 Setting Hostname IP Address...2 1.6 Starting and
Table of Contents 1 V & V4 Appliance Quick Start...1 1.1 Quick Start...1 1.2 Accessing Appliance Menus...1 1. Updating Appliance...1 1.4 Webmin...1 1.5 Setting Hostname IP Address...2 1.6 Starting and
ESET SHARED LOCAL CACHE
 ESET SHARED LOCAL CACHE User Guide Linux distribution: CentOS 6.x 64-bit Click here to download the most recent version of this document ESET SHARED LOCAL CACHE Copyright 2016 by ESET, spol. s r. o. ESET
ESET SHARED LOCAL CACHE User Guide Linux distribution: CentOS 6.x 64-bit Click here to download the most recent version of this document ESET SHARED LOCAL CACHE Copyright 2016 by ESET, spol. s r. o. ESET
The Balabit s Privileged Session Management 5 F5 Azure Reference Guide
 The Balabit s Privileged Session Management 5 F5 Azure Reference Guide March 12, 2018 Abstract Administrator Guide for Balabit s Privileged Session Management (PSM) Copyright 1996-2018 Balabit, a One Identity
The Balabit s Privileged Session Management 5 F5 Azure Reference Guide March 12, 2018 Abstract Administrator Guide for Balabit s Privileged Session Management (PSM) Copyright 1996-2018 Balabit, a One Identity
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3
 Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
ESET SHARED LOCAL CACHE
 ESET SHARED LOCAL CACHE User Guide Linux distribution: CentOS 6.6 64-bit Click here to download the most recent version of this document ESET SHARED LOCAL CACHE Copyright 2014 by ESET, spol. s r. o. ESET
ESET SHARED LOCAL CACHE User Guide Linux distribution: CentOS 6.6 64-bit Click here to download the most recent version of this document ESET SHARED LOCAL CACHE Copyright 2014 by ESET, spol. s r. o. ESET
CIS 231 Windows 10 Install Lab # 3
 CIS 231 Windows 10 Install Lab # 3 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems later in
CIS 231 Windows 10 Install Lab # 3 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems later in
CIS 231 Windows 7 Install Lab #2
 CIS 231 Windows 7 Install Lab #2 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems later in the
CIS 231 Windows 7 Install Lab #2 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems later in the
Monitoring Apache Tomcat Servers With Nagios XI
 Purpose This document describes how to add custom Apache Tomcat plugins and checks, namely check_tomcatsessions, to your server. Implementing Apache Tomcat plugins within will allow you the to monitor
Purpose This document describes how to add custom Apache Tomcat plugins and checks, namely check_tomcatsessions, to your server. Implementing Apache Tomcat plugins within will allow you the to monitor
Article Number: 552 Rating: Unrated Last Updated: Sun, Nov 20, 2016 at 6:09 PM. This guide will show you how to integrate Nagios XI with ServiceNow.
 Nagios XI - Integrating ServiceNow Article Number: 552 Rating: Unrated Last Updated: Sun, Nov 20, 2016 at 6:09 PM O ve r vie w This guide will show you how to integrate Nagios XI with ServiceNow. ServiceNow
Nagios XI - Integrating ServiceNow Article Number: 552 Rating: Unrated Last Updated: Sun, Nov 20, 2016 at 6:09 PM O ve r vie w This guide will show you how to integrate Nagios XI with ServiceNow. ServiceNow
How To Monitor Apache Cassandra Distributed Databases
 Purpose This document describes how to configure to monitor Apache Cassandra distributed database implementations in order to ensure that data, as well as the hardware housing it, is operating properly.
Purpose This document describes how to configure to monitor Apache Cassandra distributed database implementations in order to ensure that data, as well as the hardware housing it, is operating properly.
IT Essentials v6.0 Windows 10 Software Labs
 IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
Training manual: An introduction to North Time Pro 2019 ESS at the terminal
 Training manual: An introduction to North Time Pro 2019 ESS at the terminal Document t2-0800 Revision 15.1 Copyright North Time Pro www.ntdltd.com +44 (0) 2892 604000 For more information about North
Training manual: An introduction to North Time Pro 2019 ESS at the terminal Document t2-0800 Revision 15.1 Copyright North Time Pro www.ntdltd.com +44 (0) 2892 604000 For more information about North
This document is intended for use by Nagios Administrators that want to use Slack for notifications.
 Purpose This document describes how integrate the Slack messaging platform with. This integration will allow to send notifications to Slack channels, enabling teams to see the health of their devices monitored
Purpose This document describes how integrate the Slack messaging platform with. This integration will allow to send notifications to Slack channels, enabling teams to see the health of their devices monitored
CIS 231 Windows 2012 R2 Server Install Lab #1
 CIS 231 Windows 2012 R2 Server Install Lab #1 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems
CIS 231 Windows 2012 R2 Server Install Lab #1 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems
Redhat OpenStack 5.0 and PLUMgrid OpenStack Networking Suite 2.0 Installation Hands-on lab guide
 Redhat OpenStack 5.0 and PLUMgrid OpenStack Networking Suite 2.0 Installation Hands-on lab guide Oded Nahum Principal Systems Engineer PLUMgrid EMEA November 2014 Page 1 Page 2 Table of Contents Table
Redhat OpenStack 5.0 and PLUMgrid OpenStack Networking Suite 2.0 Installation Hands-on lab guide Oded Nahum Principal Systems Engineer PLUMgrid EMEA November 2014 Page 1 Page 2 Table of Contents Table
This documentation can used to generate a request that can be submitted to any of these CA types.
 Nagios Core - Configuring SSL/TLS Article Number: 595 Rating: 5/5 from 1 votes Last Updated: Thu, Jul 20, 2017 at 8:09 PM C o nf igur ing S S L/TLS Fo r Na gio s C o r e This KB article describes how to
Nagios Core - Configuring SSL/TLS Article Number: 595 Rating: 5/5 from 1 votes Last Updated: Thu, Jul 20, 2017 at 8:09 PM C o nf igur ing S S L/TLS Fo r Na gio s C o r e This KB article describes how to
Virtual Data Center (vdc) Manual
 Virtual Data Center (vdc) Manual English Version 1.0 Page 1 of 43 Content 1 HOW TO USE CLOUD PORTAL (VMWARE VIRTUAL DATA CENTER)... 3 2 VMWARE SYSTEM DETAILS... 5 3 HOW TO MANAGE VIRTUAL MACHINE... 6 Edit
Virtual Data Center (vdc) Manual English Version 1.0 Page 1 of 43 Content 1 HOW TO USE CLOUD PORTAL (VMWARE VIRTUAL DATA CENTER)... 3 2 VMWARE SYSTEM DETAILS... 5 3 HOW TO MANAGE VIRTUAL MACHINE... 6 Edit
Create a pfsense router for your private lab network template
 Create a pfsense router for your private lab network template Some labs will require a private network where you can deploy services like DHCP. Here are instructions for setting up an uplink router for
Create a pfsense router for your private lab network template Some labs will require a private network where you can deploy services like DHCP. Here are instructions for setting up an uplink router for
LAN Setup Reflection. Ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external?
 LAN Setup Reflection Ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other VMs in the classroom?
LAN Setup Reflection Ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other VMs in the classroom?
CELLTRAQ Battery Monitoring Software
 CELLTRAQ Battery Monitoring Software Instructions April 2009 167-000128A INNOVATION TECHNOLOGY QUALITY WORLDWIDE Page 2 CELLTRAQ Overview CELLTRAQ CELLTRAQ is a web application that is used to monitor
CELLTRAQ Battery Monitoring Software Instructions April 2009 167-000128A INNOVATION TECHNOLOGY QUALITY WORLDWIDE Page 2 CELLTRAQ Overview CELLTRAQ CELLTRAQ is a web application that is used to monitor
Installing and Upgrading Cisco Network Registrar Virtual Appliance
 CHAPTER 3 Installing and Upgrading Cisco Network Registrar Virtual Appliance The Cisco Network Registrar virtual appliance includes all the functionality available in a version of Cisco Network Registrar
CHAPTER 3 Installing and Upgrading Cisco Network Registrar Virtual Appliance The Cisco Network Registrar virtual appliance includes all the functionality available in a version of Cisco Network Registrar
Purpose. Target Audience. Solution Overview NCPA. Using NCPA For Passive Checks
 Using For Passive Checks Purpose This document describes how to configure the Nagios Cross Platform Agent () to send passive check results to Nagios XI or Nagios Core using Nagios Remote Data Processor
Using For Passive Checks Purpose This document describes how to configure the Nagios Cross Platform Agent () to send passive check results to Nagios XI or Nagios Core using Nagios Remote Data Processor
Setting Up read&write for ipad
 Setting Up read&write for ipad 1. Open up Settings 2. Tap on General. 3. Move down until you find the keyboard button. Tap on it. 1. 2. 3. Settings Keyboards 3. 4. 3. Tap on Keyboards. Then Add New Keyboard
Setting Up read&write for ipad 1. Open up Settings 2. Tap on General. 3. Move down until you find the keyboard button. Tap on it. 1. 2. 3. Settings Keyboards 3. 4. 3. Tap on Keyboards. Then Add New Keyboard
Argument 1 = A number (0, 1, 2, 3) that will be used as the exit code the script will exit with (this is how Nagios determines the status)
 Nagios XI - Using Scripts / Plugins With NSClient++ Article Number: 58 Rating: Unrated Last Updated: Wed, Jul 19, 017 at 11:59 PM O ve r vie w This KB article explains how to use external scripts / plugins
Nagios XI - Using Scripts / Plugins With NSClient++ Article Number: 58 Rating: Unrated Last Updated: Wed, Jul 19, 017 at 11:59 PM O ve r vie w This KB article explains how to use external scripts / plugins
PeerLink Help Manual
 Manual Updated Monday, August 13, 2012 I Table of Contents 1... 1 Getting Started Solutions Overview... 1 Term inology... 2 Requirem ents... 4 Architecture Overview... 6 How File Collaboration... Works
Manual Updated Monday, August 13, 2012 I Table of Contents 1... 1 Getting Started Solutions Overview... 1 Term inology... 2 Requirem ents... 4 Architecture Overview... 6 How File Collaboration... Works
Lab 1: Accessing the Linux Operating System Spring 2009
 CIS 90 Linux Lab Exercise Lab 1: Accessing the Linux Operating System Spring 2009 Lab 1: Accessing the Linux Operating System This lab takes a look at UNIX through an online experience on an Ubuntu Linux
CIS 90 Linux Lab Exercise Lab 1: Accessing the Linux Operating System Spring 2009 Lab 1: Accessing the Linux Operating System This lab takes a look at UNIX through an online experience on an Ubuntu Linux
SUSE Cloud Admin Appliance Walk Through. You may download the SUSE Cloud Admin Appliance the following ways.
 SUSE Cloud Admin Appliance Walk Through First before you proceed with deploying the Admin Appliance you must go through and answer the questionnaire to ensure you have an idea of the scope of the project
SUSE Cloud Admin Appliance Walk Through First before you proceed with deploying the Admin Appliance you must go through and answer the questionnaire to ensure you have an idea of the scope of the project
Purpose. Target Audience. Prerequisites. What Is An Event Handler? Nagios XI. Introduction to Event Handlers
 Purpose This document describes how to use event handlers in to take predefined actions when the hosts or services you are monitoring change state. Event handlers are used to automate processes taken when
Purpose This document describes how to use event handlers in to take predefined actions when the hosts or services you are monitoring change state. Event handlers are used to automate processes taken when
1) Use either Chrome of Firefox to access the VMware vsphere web Client. https://vweb.bristolcc.edu. FireFox
 CIS 231 Windows 7 Install Lab #2 1) Use either Chrome of Firefox to access the VMware vsphere web Client. https://vweb.bristolcc.edu CHROME At the your connection is not private message, click Advanced
CIS 231 Windows 7 Install Lab #2 1) Use either Chrome of Firefox to access the VMware vsphere web Client. https://vweb.bristolcc.edu CHROME At the your connection is not private message, click Advanced
Contents. Note: pay attention to where you are. Note: Plaintext version. Note: pay attention to where you are... 1 Note: Plaintext version...
 Contents Note: pay attention to where you are........................................... 1 Note: Plaintext version................................................... 1 Hello World of the Bash shell 2 Accessing
Contents Note: pay attention to where you are........................................... 1 Note: Plaintext version................................................... 1 Hello World of the Bash shell 2 Accessing
Nagios XI Using The Core Config Manager For Host Management
 The Industry Standard in IT Infrastructure Monitoring Purpose This document describes how to manage hosts, host groups and host templates using the Nagios XI Core Config Manager. While monitoring wizards
The Industry Standard in IT Infrastructure Monitoring Purpose This document describes how to manage hosts, host groups and host templates using the Nagios XI Core Config Manager. While monitoring wizards
How to use IBM/Softlayer Object Storage for Offsite Backup
 IBM/Softlayer Object Storage for Offsite Backup How to use IBM/Softlayer Object Storage for Offsite Backup How to use IBM/Softlayer Object Storage for Offsite Backup IBM/Softlayer Object Storage is a redundant
IBM/Softlayer Object Storage for Offsite Backup How to use IBM/Softlayer Object Storage for Offsite Backup How to use IBM/Softlayer Object Storage for Offsite Backup IBM/Softlayer Object Storage is a redundant
FireFox. CIS 231 Windows 10 Install Lab # 3. 1) Use either Chrome of Firefox to access the VMware vsphere web Client.
 CIS 231 Windows 10 Install Lab # 3 1) Use either Chrome of Firefox to access the VMware vsphere web Client. https://vweb.bristolcc.edu CHROME At the your connection is not private message, click Advanced
CIS 231 Windows 10 Install Lab # 3 1) Use either Chrome of Firefox to access the VMware vsphere web Client. https://vweb.bristolcc.edu CHROME At the your connection is not private message, click Advanced
Purpose. Target Audience. Install SNMP On The Remote Linux Machine. Nagios XI. Monitoring Linux Using SNMP
 Purpose This document describes how to monitor Linux machines with using SNMP. SNMP is an agentless method of monitoring network devices and servers, and is often preferable to installing dedicated agents
Purpose This document describes how to monitor Linux machines with using SNMP. SNMP is an agentless method of monitoring network devices and servers, and is often preferable to installing dedicated agents
Online Help StruxureWare Data Center Expert
 Online Help StruxureWare Data Center Expert Version 7.2.7 What's New in StruxureWare Data Center Expert 7.2.x Learn more about the new features available in the StruxureWare Data Center Expert 7.2.x release.
Online Help StruxureWare Data Center Expert Version 7.2.7 What's New in StruxureWare Data Center Expert 7.2.x Learn more about the new features available in the StruxureWare Data Center Expert 7.2.x release.
LAN Setup Reflection
 LAN Setup Reflection After the LAN setup, ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other
LAN Setup Reflection After the LAN setup, ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other
Nagios Snmp External Command Error With No Output (return Code 3)
 Nagios Snmp External Command Error With No Output (return Code 3) Added value of custom variables to Object JSON output for hosts, services Fixed bug #583: Status Check Output of (No output on stdout)
Nagios Snmp External Command Error With No Output (return Code 3) Added value of custom variables to Object JSON output for hosts, services Fixed bug #583: Status Check Output of (No output on stdout)
There are separate firewall daemons for for IPv4 and IPv6 and hence there are separate commands which are provided below.
 SNMP Trap - Firewall Rules Article Number: 87 Rating: 1/5 from 1 votes Last Updated: Tue, Dec 18, 2018 at 5:25 PM Fir e wa ll Rule s These steps explain how to check if the Operating System (OS) of the
SNMP Trap - Firewall Rules Article Number: 87 Rating: 1/5 from 1 votes Last Updated: Tue, Dec 18, 2018 at 5:25 PM Fir e wa ll Rule s These steps explain how to check if the Operating System (OS) of the
FireFox. CIS 231 Windows 2012 R2 Server Install Lab #1
 CIS 231 Windows 2012 R2 Server Install Lab #1 1) Use either Chrome or Firefox to access the VMware vsphere web Client. https://vweb.bristolcc.edu CHROME At the your connection is not private message, click
CIS 231 Windows 2012 R2 Server Install Lab #1 1) Use either Chrome or Firefox to access the VMware vsphere web Client. https://vweb.bristolcc.edu CHROME At the your connection is not private message, click
Configuring the SMA 500v Virtual Appliance
 Using the SMA 500v Virtual Appliance Configuring the SMA 500v Virtual Appliance Registering Your Appliance Using the 30-day Trial Version Upgrading Your Appliance Configuring the SMA 500v Virtual Appliance
Using the SMA 500v Virtual Appliance Configuring the SMA 500v Virtual Appliance Registering Your Appliance Using the 30-day Trial Version Upgrading Your Appliance Configuring the SMA 500v Virtual Appliance
Overview of the Cisco NCS Command-Line Interface
 CHAPTER 1 Overview of the Cisco NCS -Line Interface This chapter provides an overview of how to access the Cisco Prime Network Control System (NCS) command-line interface (CLI), the different command modes,
CHAPTER 1 Overview of the Cisco NCS -Line Interface This chapter provides an overview of how to access the Cisco Prime Network Control System (NCS) command-line interface (CLI), the different command modes,
HP LeftHand SAN Solutions
 HP LeftHand SAN Solutions Support Document Installation Manuals VSA 8.0 Quick Start - Demo Version Legal Notices Warranty The only warranties for HP products and services are set forth in the express warranty
HP LeftHand SAN Solutions Support Document Installation Manuals VSA 8.0 Quick Start - Demo Version Legal Notices Warranty The only warranties for HP products and services are set forth in the express warranty
Installation. Power on and initial setup. Before You Begin. Procedure
 Power on and initial setup, page 1 Customize ESXi host for remote access, page 4 Access and configure ESXi host, page 6 Deploy virtual machines, page 13 Install applications on virtual machines, page 14
Power on and initial setup, page 1 Customize ESXi host for remote access, page 4 Access and configure ESXi host, page 6 Deploy virtual machines, page 13 Install applications on virtual machines, page 14
Citrix CloudPlatform (powered by Apache CloudStack) Version Patch D Release Notes. Revised July 02, :15 pm Pacific
 Citrix CloudPlatform (powered by Apache CloudStack) Version 3.0.5 Patch D Release Notes Revised July 02, 2014 10:15 pm Pacific Citrix CloudPlatform (powered by Apache CloudStack) Version 3.0.5 Patch D
Citrix CloudPlatform (powered by Apache CloudStack) Version 3.0.5 Patch D Release Notes Revised July 02, 2014 10:15 pm Pacific Citrix CloudPlatform (powered by Apache CloudStack) Version 3.0.5 Patch D
Orchid Core VMS Installation Guide
 Orchid Core VMS Installation Guide Version 2.2.2 Orchid Core VMS Installation Guide v2.2.2 1 C O N T E N T S About the Orchid Core VMS Installation Guide 2 Installation 3 Working in Windows 3 Working in
Orchid Core VMS Installation Guide Version 2.2.2 Orchid Core VMS Installation Guide v2.2.2 1 C O N T E N T S About the Orchid Core VMS Installation Guide 2 Installation 3 Working in Windows 3 Working in
UCS Director 5.4 Windows/Linux CSV Workflow Deployment
 UCS Director 5.4 Windows/Linux CSV Workflow Deployment The purpose of this document is to illustrate the steps to implement the CSV Workflow that can be used for Windows or Linux VM deployments. The CSV
UCS Director 5.4 Windows/Linux CSV Workflow Deployment The purpose of this document is to illustrate the steps to implement the CSV Workflow that can be used for Windows or Linux VM deployments. The CSV
This document is intended for use by Nagios XI Administrators who wish to monitor JMX applications.
 Monitoring JMX With Purpose This document will cover how to monitor Java application servers using the check_jmx plugin within, in order for users to be notified when java applications are not functioning
Monitoring JMX With Purpose This document will cover how to monitor Java application servers using the check_jmx plugin within, in order for users to be notified when java applications are not functioning
17 In big Data Centers it may be practical to collect event and error messages to a central syslog server.
 Slide 0 Welcome to this Web-Based-Training session providing you an introduction to the Initial Setup of the ETERNUS DX80 S2, DX90 S2, DX410 S2 and DX440 S2. 1 In this first chapter we will look at the
Slide 0 Welcome to this Web-Based-Training session providing you an introduction to the Initial Setup of the ETERNUS DX80 S2, DX90 S2, DX410 S2 and DX440 S2. 1 In this first chapter we will look at the
Troubleshooting with the rx2800i4 Management Processor
 Effective: 12/14/18 Revision: A Troubleshooting with the rx2800i4 Management Processor Overview Identify a VMS workstation running VMS 8.4-2 or newer. In a VMS workstation, setup to log your session to
Effective: 12/14/18 Revision: A Troubleshooting with the rx2800i4 Management Processor Overview Identify a VMS workstation running VMS 8.4-2 or newer. In a VMS workstation, setup to log your session to
QUICK START GUIDE. Your Power Solutions Partner
 Alpha Technologies S.A. Avenue Alexander Flemming 1 B-1348 Ottignies-Louvain-La-Neuve Belgium COMP@S QUICK START GUIDE Your Power Solutions Partner Aug 19, 2015 Table of Contents CHAPTER 1 : CONNECTING
Alpha Technologies S.A. Avenue Alexander Flemming 1 B-1348 Ottignies-Louvain-La-Neuve Belgium COMP@S QUICK START GUIDE Your Power Solutions Partner Aug 19, 2015 Table of Contents CHAPTER 1 : CONNECTING
Configure the Cisco DNA Center Appliance
 Review Cisco DNA Center Configuration Wizard Parameters, page 1 Configure Cisco DNA Center Using the Wizard, page 5 Review Cisco DNA Center Configuration Wizard Parameters When Cisco DNA Center configuration
Review Cisco DNA Center Configuration Wizard Parameters, page 1 Configure Cisco DNA Center Using the Wizard, page 5 Review Cisco DNA Center Configuration Wizard Parameters When Cisco DNA Center configuration
Creating a Yubikey MFA Service in AWS
 Amazon AWS is a cloud based development environment with a goal to provide many options to companies wishing to leverage the power and convenience of cloud computing within their organisation. In 2013
Amazon AWS is a cloud based development environment with a goal to provide many options to companies wishing to leverage the power and convenience of cloud computing within their organisation. In 2013
Integration with Network Management Systems. Network Management System (NMS) Integration
 Integration with Network Management Systems Network Management System (NMS) Integration The securityprobe is embedded with full SNMP and can integrate with any SNMP based network management systems, such
Integration with Network Management Systems Network Management System (NMS) Integration The securityprobe is embedded with full SNMP and can integrate with any SNMP based network management systems, such
Network Management Utility
 4343-7705-02 Network Management Utility Foreword Welcome Network Management Utility is utility software that provides central control over printers, copiers, and other devices on a network. With Network
4343-7705-02 Network Management Utility Foreword Welcome Network Management Utility is utility software that provides central control over printers, copiers, and other devices on a network. With Network
RH-202. RedHat. Redhat Certified Technician on Redhat Enterprise Linux 4 (Labs)
 RedHat RH-202 Redhat Certified Technician on Redhat Enterprise Linux 4 (Labs) Download Full Version : https://killexams.com/pass4sure/exam-detail/rh-202 QUESTION: 159 Install the dialog-* Questions asking
RedHat RH-202 Redhat Certified Technician on Redhat Enterprise Linux 4 (Labs) Download Full Version : https://killexams.com/pass4sure/exam-detail/rh-202 QUESTION: 159 Install the dialog-* Questions asking
Assignment 1: Build Environment
 Read the entire assignment before beginning! Submit deliverables to CourSys: https://courses.cs.sfu.ca/ Late penalty is 10% per calendar day (each 0 to 24 hour period past due, max 2 days). This assignment
Read the entire assignment before beginning! Submit deliverables to CourSys: https://courses.cs.sfu.ca/ Late penalty is 10% per calendar day (each 0 to 24 hour period past due, max 2 days). This assignment
Master Node Setup Guide
 Introduction Welcome to this step by step guide that will take you through the process of creating your own Masternode. This guide is aimed at the casual Windows 10 PC user who has purchased Satoshi Coin
Introduction Welcome to this step by step guide that will take you through the process of creating your own Masternode. This guide is aimed at the casual Windows 10 PC user who has purchased Satoshi Coin
Using SSL/TLS with Active Directory / LDAP
 Purpose This document describes how to install the required certificate on the for use with LDAP or Active Directory (AD) Integration in. This process is required if your LDAP / AD server has a self signed
Purpose This document describes how to install the required certificate on the for use with LDAP or Active Directory (AD) Integration in. This process is required if your LDAP / AD server has a self signed
Send the Ctrl-Alt-Delete key sequence to the Guest OS one of two ways: Key sequence: Ctlr-Alt-Ins Menu Sequence: VM / Guest / Send Ctrl-Alt-Delete
 CIS 231 Windows 2008 Server Install Lab #1 (Virtual Machines) Keys to Remember when using the vsphere client. Send the Ctrl-Alt-Delete key sequence to the Guest OS one of two ways: Key sequence: Ctlr-Alt-Ins
CIS 231 Windows 2008 Server Install Lab #1 (Virtual Machines) Keys to Remember when using the vsphere client. Send the Ctrl-Alt-Delete key sequence to the Guest OS one of two ways: Key sequence: Ctlr-Alt-Ins
Scvmm 2012 Install Virtual Guest Services. Manually >>>CLICK HERE<<<
 Scvmm 2012 Install Virtual Guest Services Manually SCVMM 2012 R2 - Installing Virtual Switch Fails with Error 2916 Ensure that the Windows Remote Management (WinRM) service and the VMM agent are installed
Scvmm 2012 Install Virtual Guest Services Manually SCVMM 2012 R2 - Installing Virtual Switch Fails with Error 2916 Ensure that the Windows Remote Management (WinRM) service and the VMM agent are installed
SharePoint Designer Advanced
 SharePoint Designer Advanced SharePoint Designer Advanced (1:00) Thank you for having me here today. As mentioned, my name is Susan Hernandez, and I work at Applied Knowledge Group (http://www.akgroup.com).
SharePoint Designer Advanced SharePoint Designer Advanced (1:00) Thank you for having me here today. As mentioned, my name is Susan Hernandez, and I work at Applied Knowledge Group (http://www.akgroup.com).
Bitnami Coppermine for Huawei Enterprise Cloud
 Bitnami Coppermine for Huawei Enterprise Cloud Description Coppermine is a multi-purpose, full-featured web picture gallery. It includes user management, private galleries, automatic thumbnail creation,
Bitnami Coppermine for Huawei Enterprise Cloud Description Coppermine is a multi-purpose, full-featured web picture gallery. It includes user management, private galleries, automatic thumbnail creation,
DEPLOYING A 3SCALE API GATEWAY ON RED HAT OPENSHIFT
 TUTORIAL: DEPLOYING A 3SCALE API GATEWAY ON RED HAT OPENSHIFT This tutorial describes how to deploy a dockerized version of the 3scale API Gateway 1.0 (APIcast) that is packaged for easy installation and
TUTORIAL: DEPLOYING A 3SCALE API GATEWAY ON RED HAT OPENSHIFT This tutorial describes how to deploy a dockerized version of the 3scale API Gateway 1.0 (APIcast) that is packaged for easy installation and
Build your own NAS with OpenMediaVault
 Build your own NAS with OpenMediaVault Installation Minimum Requirements i486 or amd64 platform 1 GiB RAM 2 GiB HDD/DOM/CF/USB Thumb Drive used as OpenMediaVault system drive. Flash Drives without static
Build your own NAS with OpenMediaVault Installation Minimum Requirements i486 or amd64 platform 1 GiB RAM 2 GiB HDD/DOM/CF/USB Thumb Drive used as OpenMediaVault system drive. Flash Drives without static
Design News Gadget Freak. AutoNag reminder system. Background: Server OS Installation:
 Design News Gadget Freak AutoNag reminder system Background: This is an automated paging system for playing back pre-recorded announcements at specified times. It has the side benefit of being a full voice
Design News Gadget Freak AutoNag reminder system Background: This is an automated paging system for playing back pre-recorded announcements at specified times. It has the side benefit of being a full voice
VB. Microsoft. TS- Visual Studio Tools for 2007 MS Office System (VTSO)
 Microsoft 70-543-VB TS- Visual Studio Tools for 2007 MS Office System (VTSO) Download Full Version : https://killexams.com/pass4sure/exam-detail/70-543-vb LONDON. You need to grant permission for the add-in
Microsoft 70-543-VB TS- Visual Studio Tools for 2007 MS Office System (VTSO) Download Full Version : https://killexams.com/pass4sure/exam-detail/70-543-vb LONDON. You need to grant permission for the add-in
Control Panel software usage guide (v beta)
 Control Panel software usage guide (v 1.012 beta) (note: the pictures throughout the guide may not directly correspond with your server installation, however all features are covered) 1. Connecting to
Control Panel software usage guide (v 1.012 beta) (note: the pictures throughout the guide may not directly correspond with your server installation, however all features are covered) 1. Connecting to
Configure the Cisco DNA Center Appliance
 Review Cisco DNA Center Configuration Wizard Parameters, page 1 Configure Cisco DNA Center Using the Wizard, page 5 Review Cisco DNA Center Configuration Wizard Parameters When Cisco DNA Center configuration
Review Cisco DNA Center Configuration Wizard Parameters, page 1 Configure Cisco DNA Center Using the Wizard, page 5 Review Cisco DNA Center Configuration Wizard Parameters When Cisco DNA Center configuration
Quick-start guide for installing the client software and starting your first review
 User s Guide Getting Started with the Collaborator Client Quick-start guide for installing the client software and starting your first review Contents Introduction...2 Download Client Software...2 Installation
User s Guide Getting Started with the Collaborator Client Quick-start guide for installing the client software and starting your first review Contents Introduction...2 Download Client Software...2 Installation
The Pr o f e s s i o n a l La n d l o r d Ho w To
 The Pr o f e s s i o n a l La n d l o r d Ho w To Providing Property Management Solutions for Over 25 Years PROMAS Central - Manager Setup - V12 What is PROMAS Central? PROMAS Central consists of the Internet
The Pr o f e s s i o n a l La n d l o r d Ho w To Providing Property Management Solutions for Over 25 Years PROMAS Central - Manager Setup - V12 What is PROMAS Central? PROMAS Central consists of the Internet
CCT-1301 MK2 USER MANUAL
 denver-elect ronics. com CCT-1301 MK2 USER MANUAL www.facebook.com/denverelectronics ENG-1 1.Shutter 1 7 8 2 3 2.Speaker 3.ON/OFF 4.USB port 5.Micro SD card slot 6.Lens 4 7.Charging indicator light 8.Busy
denver-elect ronics. com CCT-1301 MK2 USER MANUAL www.facebook.com/denverelectronics ENG-1 1.Shutter 1 7 8 2 3 2.Speaker 3.ON/OFF 4.USB port 5.Micro SD card slot 6.Lens 4 7.Charging indicator light 8.Busy
Amazon Web Services Hands on EC2 December, 2012
 Amazon Web Services Hands on EC2 December, 2012 Copyright 2011-2012, Amazon Web Services, All Rights Reserved Page 1-42 Table of Contents Launch a Linux Instance... 4 Connect to the Linux Instance Using
Amazon Web Services Hands on EC2 December, 2012 Copyright 2011-2012, Amazon Web Services, All Rights Reserved Page 1-42 Table of Contents Launch a Linux Instance... 4 Connect to the Linux Instance Using
rx2800i4 Management Processor Setup
 Effective: 12/17/18 RX2660 MP SETUP Revision: A rx2800i4 Management Processor Setup Log into the Management Processor (MP) serial port on the rx2800i4. (Make a connection to the MP LAN DB9 serial port,
Effective: 12/17/18 RX2660 MP SETUP Revision: A rx2800i4 Management Processor Setup Log into the Management Processor (MP) serial port on the rx2800i4. (Make a connection to the MP LAN DB9 serial port,
Networking for Wide Format Printers
 Networking for Wide Format Printers Table of Contents Configure PC before RIP Installa on... 1 Verifying Your Network Se ngs for Mac Communica on... 3 Changing Your Network Adapter for Mac Communica on...
Networking for Wide Format Printers Table of Contents Configure PC before RIP Installa on... 1 Verifying Your Network Se ngs for Mac Communica on... 3 Changing Your Network Adapter for Mac Communica on...
InControl 2 Software Appliance Setup Guide
 InControl 2 Software Appliance Setup Guide (Last updated: 2017-11) Contents 1. Introduction Minimum Hardware Requirements 2. For VMware ESXi 6.0 and ESXi 5.5 (SCSI) Networking Creating InControl and DB
InControl 2 Software Appliance Setup Guide (Last updated: 2017-11) Contents 1. Introduction Minimum Hardware Requirements 2. For VMware ESXi 6.0 and ESXi 5.5 (SCSI) Networking Creating InControl and DB
Adafruit WebIDE. Created by Tyler Cooper. Last updated on :29:47 PM UTC
 Adafruit WebIDE Created by Tyler Cooper Last updated on 2018-03-12 08:29:47 PM UTC Guide Contents Guide Contents Overview Installation Easy installation: Manual Installation: Uninstallation: Getting Started
Adafruit WebIDE Created by Tyler Cooper Last updated on 2018-03-12 08:29:47 PM UTC Guide Contents Guide Contents Overview Installation Easy installation: Manual Installation: Uninstallation: Getting Started
WA2031 WebSphere Application Server 8.0 Administration on Windows. Student Labs. Web Age Solutions Inc. Copyright 2012 Web Age Solutions Inc.
 WA2031 WebSphere Application Server 8.0 Administration on Windows Student Labs Web Age Solutions Inc. Copyright 2012 Web Age Solutions Inc. 1 Table of Contents Directory Paths Used in Labs...3 Lab Notes...4
WA2031 WebSphere Application Server 8.0 Administration on Windows Student Labs Web Age Solutions Inc. Copyright 2012 Web Age Solutions Inc. 1 Table of Contents Directory Paths Used in Labs...3 Lab Notes...4
Introduction. 1 of 42
 Introduction Looking for information on how to host Rock internally? Well look no further. In this step-by-step guide we'll walk through the process of getting Rock up and running. Before we jump in, let's
Introduction Looking for information on how to host Rock internally? Well look no further. In this step-by-step guide we'll walk through the process of getting Rock up and running. Before we jump in, let's
Physics REU Unix Tutorial
 Physics REU Unix Tutorial What is unix? Unix is an operating system. In simple terms, its the set of programs that makes a computer work. It can be broken down into three parts. (1) kernel: The component
Physics REU Unix Tutorial What is unix? Unix is an operating system. In simple terms, its the set of programs that makes a computer work. It can be broken down into three parts. (1) kernel: The component
More Raspian. An editor Configuration files Shell scripts Shell variables System admin
 More Raspian An editor Configuration files Shell scripts Shell variables System admin Nano, a simple editor Nano does not require the mouse. You must use your keyboard to move around the file and make
More Raspian An editor Configuration files Shell scripts Shell variables System admin Nano, a simple editor Nano does not require the mouse. You must use your keyboard to move around the file and make
MIB Browser Version 10 User Guide
 MIB Browser Version 10 User Guide The ireasoning MIB browser is a powerful and easy-to-use tool powered by ireasoning SNMP API. MIB browser is an indispensable tool for engineers to manage SNMP enabled
MIB Browser Version 10 User Guide The ireasoning MIB browser is a powerful and easy-to-use tool powered by ireasoning SNMP API. MIB browser is an indispensable tool for engineers to manage SNMP enabled
Network Drawing. Computer Specs, I ve used. Installing a Network-Based Intrusion Detection
 HS1 HS2 OK1 OK2 PS 1 2 3 4 5 6 7 8 9 101112 COL- ACT- STA.- CONSOLE SD Installing a Network-Based Intrusion Detection created by: Rainer Bemsel Version 1.0 Dated: Apr/10/2003 The purpose of this document
HS1 HS2 OK1 OK2 PS 1 2 3 4 5 6 7 8 9 101112 COL- ACT- STA.- CONSOLE SD Installing a Network-Based Intrusion Detection created by: Rainer Bemsel Version 1.0 Dated: Apr/10/2003 The purpose of this document
Installing the WHI Virtual Private Network (VPN) for WHIX Users Updated 12/16/2016
 Installing the WHI Virtual Private Network (VPN) for WHIX Users Updated 12/16/2016 Note: Please read the FAQ section at the end of this document. I. Overview The way in which you connect to the WHI network
Installing the WHI Virtual Private Network (VPN) for WHIX Users Updated 12/16/2016 Note: Please read the FAQ section at the end of this document. I. Overview The way in which you connect to the WHI network
How to Deploy an Oracle E-Business Suite System in Minutes Using Oracle VM Templates
 HOL 10472 How to Deploy an Oracle E-Business Suite System in Minutes Using Oracle VM Templates Simon Coter Product Manager, Oracle VM & VirtualBox simon.coter@oracle.com Christophe Pauliat Systems sales
HOL 10472 How to Deploy an Oracle E-Business Suite System in Minutes Using Oracle VM Templates Simon Coter Product Manager, Oracle VM & VirtualBox simon.coter@oracle.com Christophe Pauliat Systems sales
Alarm Counter. A Ceilometer OpenStack Application
 Alarm Counter A Ceilometer OpenStack Application Tejas Tovinkere Pattabhi UTD VOLUNTEER AT AWARD SOLUTIONS Summer 2015 Contents Alarm Counter 1 Introduction...2 2 Pre-Requisites...2 2.1 Server Creation...
Alarm Counter A Ceilometer OpenStack Application Tejas Tovinkere Pattabhi UTD VOLUNTEER AT AWARD SOLUTIONS Summer 2015 Contents Alarm Counter 1 Introduction...2 2 Pre-Requisites...2 2.1 Server Creation...
Installation guide for Choic Multi User Edition
 Installation guide for ChoiceMail Multi User Edition March, 2004 Version 2.1 Copyright DigiPortal Software Inc., 2002 2004 All rights reserved ChoiceMail Multi User Installation Guide 1. Go to the URL
Installation guide for ChoiceMail Multi User Edition March, 2004 Version 2.1 Copyright DigiPortal Software Inc., 2002 2004 All rights reserved ChoiceMail Multi User Installation Guide 1. Go to the URL
Using the Cisco NCS Command-Line Interface
 CHAPTER 2 This chapter provides helpful tips for understanding and configuring the Cisco Prime Network Control System (NCS) from the command-line interface (CLI). The Cisco NCS can be deployed for small,
CHAPTER 2 This chapter provides helpful tips for understanding and configuring the Cisco Prime Network Control System (NCS) from the command-line interface (CLI). The Cisco NCS can be deployed for small,
How To Set User Account Password In Windows 7 From Guest
 How To Set User Account Password In Windows 7 From Guest To change the password of a specific user in windows 7 or 8.1, without knowing How to change or set Windows 7 default font settings to bold, italic?
How To Set User Account Password In Windows 7 From Guest To change the password of a specific user in windows 7 or 8.1, without knowing How to change or set Windows 7 default font settings to bold, italic?
CSharp. Microsoft. UPGRADE-MCAD Skills to MCPD Dvlpr by Using the MS.NET Frmwk
 Microsoft 70-551-CSharp UPGRADE-MCAD Skills to MCPD Dvlpr by Using the MS.NET Frmwk Download Full Version : http://killexams.com/pass4sure/exam-detail/70-551-csharp Answer: A,C QUESTION: 78 You create
Microsoft 70-551-CSharp UPGRADE-MCAD Skills to MCPD Dvlpr by Using the MS.NET Frmwk Download Full Version : http://killexams.com/pass4sure/exam-detail/70-551-csharp Answer: A,C QUESTION: 78 You create
