McAfee Labs Threat Report
|
|
|
- Garey Shepherd
- 6 years ago
- Views:
Transcription
1 McAfee Labs Threat Report December 217 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threat Report, December 217
2 The McAfee Labs count of new malware in Q3 reached an all-time high of 57.6 million new samples, an increase of 1% from Q2. Introduction Welcome to the McAfee Labs Threats Report. In this edition, we highlight the statistics gathered by McAfee Labs in Q3 of 217. The biggest number of the quarter is our count of new malware, which reached an all-time high of 57.6 million new samples, an increase of 1% from Q2. The total count in the McAfee Labs sample database is now more than 78 million. New ransomware rose by 36% this quarter, largely from widespread Android screen-locking malware. The easy availability of exploit kits and dark web sources fuel the rapid creation of new malware. Some of the biggest malware stories that McAfee covered in Q3 include the data breach at the Equifax credit reporting company; another data breach, through a misconfigured AWS server, at a Verizon customer support supplier; and a remote code execution vulnerability in Apache Struts, a popular component of many websites across the world. Every quarter, the McAfee Global Threat Intelligence cloud dashboard allows us to see and analyze real-world attack patterns that lead to better customer protection. This information provides insight into attack volumes that our customers experience. See Page 9 for Q3 results. Raj Samani, Chief Scientist and McAfee Fellow, Advanced Threat Research Team Stay Informed Our Q3 report demonstrates an escalation in threats, not only in these stories and other reports but also in our statistics, which show increases across multiple categories. Staying informed of emerging threats and the tactics employed by malicious actors is essential. McAfee Labs is committed to helping our customers keep up to date. For more information on threats, follow This report was researched and written by: Niamh Minihane Francisca Moreno Eric Peterson Raj Samani Craig Schmugar Dan Sommer Bing Sun 2 McAfee Labs Threat Report, December 217
3 Threats Statistics 4 Malware 9 Incidents 11 Web and Network Threats 3 McAfee Labs Threat Report, December 217
4 Malware 6,, 5,, New malware 9,, 75,, Total malware New malware increased by 1% in Q3, to a record high of 57.6 million samples. 4,, 6,, 3,, 45,, 2,, 3,, 1,, 15,, ,, 2,5, 2,, New mobile malware 25,, 2,, 15,, Total mobile malware New mobile malware jumped by 6% in Q3, fueled by a big increase in Android screenlocking ransomware. 1,5, 1,, 1,, 5,, 5, McAfee Labs Threat Report, December 217
5 Regional mobile malware infection rates (Percentage of mobile customers reporting infections) Global mobile malware infection rates (Percentage of mobile customers reporting infections) 25% 14% 2% 12% 15% 1% 1% 8% 5% 6% % Africa Asia Australia Europe North America South America Q4 216 Q1 217 Q2 217 Q % 2% % New Mac malware Total Mac malware 35, 7, 3, 6, 25, 5, 2, 4, 15, 3, 1, 2, 5, 1, McAfee Labs Threat Report, December 217
6 1,8, 1,5, 1,2, New ransomware 14,, 12,, 1,, Total ransomware New ransomware rose by 36% in Q3, boosted by a big increase in Android screenlocking threats. 9, 8,, 6, 6,, 3, 4,, ,, ,6, 1,4, 1,2, 1,, 8, 6, New malicious signed binaries 24,, 2,, 16,, 12,, 8,, 4,, Total malicious signed binaries 4, 2, McAfee Labs Threat Report, December 217
7 New macro malware Total macro malware 25, 1,5, 2, 1,2, 15, 9, 1, 6, 5, 3, ,, 4,5, 4,, New Faceliker malware 16,, 14,, 12,, Total Faceliker malware The Faceliker Trojan manipulates Facebook clicks to artificially like certain content. To learn more, read this post from McAfee Labs. 3,5, 1,, 3,, 8,, 2,5, 6,, 2,, 4,, 1,5, 2,, 1,, 5, McAfee Labs Threat Report, December 217
8 7,, 6,, 5,, 4,, 3,, New JavaScript malware 5,, 4,, 3,, 2,, 1,, Total JavaScript malware JavaScript malware fell by 26% in Q3 from an all-time high in Q2. For more on JavaScript threats, see The rise of scriptbased malware, in the McAfee Labs Threats Report, September ,, 1,, , 14, 12, 1, 8, New PowerShell malware 3, 25, 2, 15, 1, Total PowerShell malware PowerShell malware more than doubled in Q3 compared with Q2. For more on PowerShell threats, see The rise of script-based malware, in the McAfee Labs Threats Report, September , 5, 4, 2, McAfee Labs Threat Report, December 217
9 Incidents McAFEE GLOBAL THREAT INTELLIGENCE Publicly disclosed security incidents by region (Number of publicly disclosed incidents) Q1 Q2 Q3 Q4 Q1 Q2 Q Africa Asia Multiple Americas Europe Oceana Top 1 attack vectors in (Number of publicly disclosed incidents) Unknown Account hijacking Leak Malware DDoS Targeted SQL injection Defacement W-2 scam Vulnerability Every quarter, the McAfee Global Threat Intelligence cloud dashboard allows us to see and analyze realworld attack patterns that lead to better customer protection. This information provides insight into attack volumes that our customers experience. In Q3, our customers saw the following attack volumes: McAfee GTI received on average 45 billion queries per day in Q3. McAfee GTI protections against malicious files increased to 4 million per day in Q3 from 36 million in Q2. Continued on page 1. 9 McAfee Labs Threat Report, December 217
10 Health Top sectors targeted in North and South America (Number of publicly disclosed incidents) Public Sector Education Finance Retail Technology Entertainment Hospitality Online Services Manufacturing Top 1 targeted sectors in (Number of publicly disclosed incidents) Public Health People Education Finance Online services Multiple Retail Entertainment Software development McAfee GTI protections against potentially unwanted programs (PUPs) shows a decrease back to typical levels at 45 million per day in Q3 from an abnormal high of 77 million in Q2. McAfee GTI protections against medium-risk URLs shows an increase to 43 million per day in Q3 from 42 million in Q2. McAfee GTI protections against high-risk URLs shows an increase to 56 million per day in Q3 from 41 million in Q2. Q4 216 Q1 217 Q2 217 Q3 217 McAfee GTI protections against risky IP addresses shows a decrease to 48 million per day in Q3 from 58 million per day in Q2. 1 McAfee Labs Threat Report, December 217
11 Web and Network Threats 18,, 15,, 12,, 9,, 6,, 3,, New suspect URLs Spam botnet prevalence by volume in Q3 2%1% 1% Gamut Necurs Cutwail 49% Darkmailer Lethic 39% Others Gamut remains the most prevalent spamming botnet during Q3, with Necurs a close second. Necurs proliferated several Ykcol (Locky) ransomware campaigns with themes such as Status Invoice, Your Payment, and ing: [Random Numbers].JPG during the quarter. New spam URLs New phishing URLs 1,, 1,4, 8, 1,2, 6, 1,, 4, 8, 2, 6, , 2, McAfee Labs Threat Report, December 217
12 Top malware connecting to control servers in Q3 Top countries hosting botnet control servers in Q3 2% 2% 9% Wapomi United States 3% 4% 5% 49% Maazben China Chopper RedLeaves Onion Duke 28% 39% Germany China Netherlands France Muieblackcat 3% Russia 26% Ramnit Others 3% 4% 4% 5% 14% Canada Others Top network attacks in Q3 7% 4% 5% SMB Browser 12% 13% 44% Denial of service Brute force Malware DNS Others 16% 12 McAfee Labs Threat Report, December 217
13 About McAfee McAfee is one of the world s leading independent cybersecurity companies. Inspired by the power of working together, McAfee creates business and consumer solutions that make the world a safer place. By building solutions that work with other companies products, McAfee helps businesses orchestrate cyber environments that are truly integrated, where protection, detection, and correction of threats happen simultaneously and collaboratively. By protecting consumers across all their devices, McAfee secures their digital lifestyle at home and away. By working with other security players, McAfee is leading the effort to unite against cybercriminals for the benefit of all. About McAfee Labs McAfee Labs is one of the world s leading sources for threat research, threat intelligence, and cybersecurity thought leadership. With data from millions of sensors across key threats vectors file, web, message, and network McAfee Labs delivers real-time threat intelligence, critical analysis, and expert thinking to improve protection and reduce risks Mission College Blvd. Santa Clara, CA The information in this document is provided only for educational purposes and for the convenience of McAfee customers. The information contained herein is subject to change without notice, and is provided as is, without guarantee or warranty as to the accuracy or applicability of the information to any specific situation or circumstance. McAfee and the McAfee logo are trademarks or registered trademarks of McAfee, LLC or its subsidiaries in the United States and other countries. Other marks and brands may be claimed as the property of others. Copyright 217 McAfee, LLC 378_1117_rp-threats-dec-217 December McAfee Labs Threat Report, December 217
McAfee Labs Threats Report
 McAfee Labs Threats Report March 218 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threats Report, March 218 The McAfee Labs count of new malware in Q4 reached an all-time
McAfee Labs Threats Report March 218 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threats Report, March 218 The McAfee Labs count of new malware in Q4 reached an all-time
McAfee Labs Threats Report
 McAfee Labs Threats Report September 218 TOP STORIES OF THE QUARTER Want to Break Into a Locked Windows 1 Device? Ask Cortana (CVE-218-814) Threat Report: Don t Join Blockchain Revolution Without Ensuring
McAfee Labs Threats Report September 218 TOP STORIES OF THE QUARTER Want to Break Into a Locked Windows 1 Device? Ask Cortana (CVE-218-814) Threat Report: Don t Join Blockchain Revolution Without Ensuring
Protecting Your Enterprise Databases from Ransomware
 Protecting Your Enterprise Databases from Ransomware 1 Protecting Your Enterprise Databases from Ransomware Protecting Your Enterprise Databases from Ransomware Ransomware is no longer the new kid on the
Protecting Your Enterprise Databases from Ransomware 1 Protecting Your Enterprise Databases from Ransomware Protecting Your Enterprise Databases from Ransomware Ransomware is no longer the new kid on the
Building Resilience in a Digital Enterprise
 Building Resilience in a Digital Enterprise Top five steps to help reduce the risk of advanced targeted attacks To be successful in business today, an enterprise must operate securely in the cyberdomain.
Building Resilience in a Digital Enterprise Top five steps to help reduce the risk of advanced targeted attacks To be successful in business today, an enterprise must operate securely in the cyberdomain.
Load Balancing with McAfee Network Security Platform
 Load Balancing with McAfee Network Security Platform Optimizing intrusion prevention system performance 1 Load Balancing with McAfee Network Security Platform Load Balancing with McAfee Network Security
Load Balancing with McAfee Network Security Platform Optimizing intrusion prevention system performance 1 Load Balancing with McAfee Network Security Platform Load Balancing with McAfee Network Security
Securing Your Microsoft Azure Virtual Networks
 Securing Your Microsoft Azure Virtual Networks IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up
Securing Your Microsoft Azure Virtual Networks IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up
with Advanced Protection
 with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
McAfee Database Security Insights
 McAfee Database Security Insights Managing the multitude of alerts, reports, and events and sometimes finding the proverbial needle in a haystack is challenging. Monitoring the activity on busy enterprise
McAfee Database Security Insights Managing the multitude of alerts, reports, and events and sometimes finding the proverbial needle in a haystack is challenging. Monitoring the activity on busy enterprise
Reducing Operational Costs and Combating Ransomware with McAfee SIEM and Integrated Security
 Reducing Operational Costs and Combating Ransomware with McAfee SIEM and Integrated Security Healthcare provider manages threats with ease Atrius Health Customer Profile Large regional healthcare provider
Reducing Operational Costs and Combating Ransomware with McAfee SIEM and Integrated Security Healthcare provider manages threats with ease Atrius Health Customer Profile Large regional healthcare provider
IBM Security Systems IBM X-Force 2012 Annual Trend and Risk Report
 IBM Security Systems IBM X-Force 2012 Annual Trend and Risk Report Leslie Horacek X-Force Threat Response Manager horacek@be.ibm.com April 2013 1 X-Force is the foundation for advanced security and threat
IBM Security Systems IBM X-Force 2012 Annual Trend and Risk Report Leslie Horacek X-Force Threat Response Manager horacek@be.ibm.com April 2013 1 X-Force is the foundation for advanced security and threat
Securing Your Amazon Web Services Virtual Networks
 Securing Your Amazon Web Services s IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up a workload,
Securing Your Amazon Web Services s IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up a workload,
Security & Phishing
 Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
McAfee Embedded Control
 McAfee Embedded Control System integrity, change control, and policy compliance in one solution McAfee Embedded Control maintains the integrity of your system by only allowing authorized code to run and
McAfee Embedded Control System integrity, change control, and policy compliance in one solution McAfee Embedded Control maintains the integrity of your system by only allowing authorized code to run and
Targeted Ransomware No Longer a Future Threat
 REPORT Targeted Ransomware No Longer a Future Threat Analysis of a t argeted and manual ransomware campaign February 2016 Table of Contents Authors This report was researched and written by: Christiaan
REPORT Targeted Ransomware No Longer a Future Threat Analysis of a t argeted and manual ransomware campaign February 2016 Table of Contents Authors This report was researched and written by: Christiaan
Ten Ways to Prepare for Incident Response
 Ten Ways to Prepare for Incident Response 1 Ten Ways to Prepare for Incident Response Introduction As a senior consultant on the Foundstone Services incident response and forensic team, I regularly respond
Ten Ways to Prepare for Incident Response 1 Ten Ways to Prepare for Incident Response Introduction As a senior consultant on the Foundstone Services incident response and forensic team, I regularly respond
Protecting the Home Front
 Protecting the Home Front Defending the variety of devices in increasingly connected homes 1 Protecting the Home Front Protecting the Home Front Defending the variety of devices in increasingly connected
Protecting the Home Front Defending the variety of devices in increasingly connected homes 1 Protecting the Home Front Protecting the Home Front Defending the variety of devices in increasingly connected
Top 10 Global Threat Rank by Source
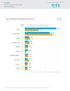 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
McAfee Endpoint Threat Defense and Response Family
 Defense and Family Detect zero-day malware, secure patient-zero, and combat advanced attacks The escalating sophistication of cyberthreats requires a new generation of protection for endpoints. Advancing
Defense and Family Detect zero-day malware, secure patient-zero, and combat advanced attacks The escalating sophistication of cyberthreats requires a new generation of protection for endpoints. Advancing
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco
 What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
Mapping traditional AV detection failures. October 2017
 Mapping traditional AV detection failures October 2017 TABLE OF CONTENTS Introduction 01 Methodology 02 Findings 03 AV failures common malware 03 Multiple AV failures 04 Four leading AVs failures 05 Conclusion
Mapping traditional AV detection failures October 2017 TABLE OF CONTENTS Introduction 01 Methodology 02 Findings 03 AV failures common malware 03 Multiple AV failures 04 Four leading AVs failures 05 Conclusion
McAfee Complete Endpoint Threat Protection Advanced threat protection for sophisticated attacks
 McAfee Complete Endpoint Threat Protection Advanced threat protection for sophisticated attacks Key Advantages Stay ahead of zero-day threats, ransomware, and greyware with machine learning and dynamic
McAfee Complete Endpoint Threat Protection Advanced threat protection for sophisticated attacks Key Advantages Stay ahead of zero-day threats, ransomware, and greyware with machine learning and dynamic
Sustainable Security Operations
 Sustainable Security Operations Optimize processes and tools to make the most of your team s time and talent The number and types of security incidents organizations face daily are steadily increasing,
Sustainable Security Operations Optimize processes and tools to make the most of your team s time and talent The number and types of security incidents organizations face daily are steadily increasing,
Understanding the McAfee Endpoint Security 10 Threat Prevention Module
 Understanding the McAfee Endpoint Security 10 Threat Prevention Module Key enhancements and new capabilities 1 Understanding the McAfee Endpoint Security 10 Threat Prevention Module Table of Contents 3
Understanding the McAfee Endpoint Security 10 Threat Prevention Module Key enhancements and new capabilities 1 Understanding the McAfee Endpoint Security 10 Threat Prevention Module Table of Contents 3
Phishing Activity Trends Report January, 2005
 Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
GUIDE. Navigating the General Data Protection Regulation Mini Guide
 GUIDE Navigating the General Data Protection Regulation Mini Guide Introduction The General Data Protection Regulation (GDPR) will deliver a long overdue modernization and harmonization of privacy and
GUIDE Navigating the General Data Protection Regulation Mini Guide Introduction The General Data Protection Regulation (GDPR) will deliver a long overdue modernization and harmonization of privacy and
SIEM Solutions from McAfee
 SIEM Solutions from McAfee Monitor. Prioritize. Investigate. Respond. Today s security information and event management (SIEM) solutions need to be able to identify and defend against attacks within an
SIEM Solutions from McAfee Monitor. Prioritize. Investigate. Respond. Today s security information and event management (SIEM) solutions need to be able to identify and defend against attacks within an
Seven Steps to Ease the Pain of Managing a SOC
 Seven Steps to Ease the Pain of Managing a SOC 1 Seven Steps to Ease the Pain of Managing a SOC Seven Steps to Ease the Pain of Managing a SOC If the complex, stressful, and time-consuming nature of running
Seven Steps to Ease the Pain of Managing a SOC 1 Seven Steps to Ease the Pain of Managing a SOC Seven Steps to Ease the Pain of Managing a SOC If the complex, stressful, and time-consuming nature of running
IBM Security Systems. IBM X-Force 2012 & CISO Survey. Cyber Security Threat Landscape IBM Corporation IBM Corporation
 IBM X-Force 2012 & CISO Survey Cyber Security Threat Landscape 1 2012 IBM Corporation IBM X-Force 2011 Trend and Risk Report Highlights The mission of the IBM X-Force research and development team is to:
IBM X-Force 2012 & CISO Survey Cyber Security Threat Landscape 1 2012 IBM Corporation IBM X-Force 2011 Trend and Risk Report Highlights The mission of the IBM X-Force research and development team is to:
Phishing Activity Trends Report August, 2005
 Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
UK Gender Pay Gap Report 2018
 UK Gender Pay Gap Report 2018 As part of McAfee s commitment to build a better, more balanced workplace and community, we wholly embrace the UK Gender Pay Gap report. This year s calculations cover our
UK Gender Pay Gap Report 2018 As part of McAfee s commitment to build a better, more balanced workplace and community, we wholly embrace the UK Gender Pay Gap report. This year s calculations cover our
Internet Security Threat Report Volume XIII. Patrick Martin Senior Product Manager Symantec Security Response October, 2008
 Internet Security Threat Report Volume XIII Patrick Martin Senior Product Manager Symantec Security Response October, 2008 Agenda 1 ISTR XIII Important Facts 2 ISTR XIII Key Messages 3 ISTR XIII Key Facts
Internet Security Threat Report Volume XIII Patrick Martin Senior Product Manager Symantec Security Response October, 2008 Agenda 1 ISTR XIII Important Facts 2 ISTR XIII Key Messages 3 ISTR XIII Key Facts
White Paper. New Gateway Anti-Malware Technology Sets the Bar for Web Threat Protection
 White Paper New Gateway Anti-Malware Technology Sets the Bar for Web Threat Protection The latest version of the flagship McAfee Gateway Anti-Malware technology adapts to new threats and plans for future
White Paper New Gateway Anti-Malware Technology Sets the Bar for Web Threat Protection The latest version of the flagship McAfee Gateway Anti-Malware technology adapts to new threats and plans for future
Be certain. MessageLabs Intelligence: May 2006
 Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
United Automotive Electronic Systems Co., Ltd Relies on McAfee for Comprehensive Security
 United Automotive Electronic Systems Co., Ltd Relies on McAfee for Comprehensive Security Global Venture chooses McAfee for Complex Security Landscape UAES Customer Profile Joint venture of the United
United Automotive Electronic Systems Co., Ltd Relies on McAfee for Comprehensive Security Global Venture chooses McAfee for Complex Security Landscape UAES Customer Profile Joint venture of the United
McAfee Network Security Platform Administration Course
 McAfee Network Security Platform Administration Course Education Services administration course The McAfee Network Security Platform Administration course from McAfee Education Services is an essential
McAfee Network Security Platform Administration Course Education Services administration course The McAfee Network Security Platform Administration course from McAfee Education Services is an essential
IBM Security Network Protection Solutions
 Systems IBM Security IBM Security Network Protection Solutions Pre-emptive protection to keep you Ahead of the Threat Tanmay Shah Product Lead Network Protection Appliances IBM Security Systems 1 IBM Security
Systems IBM Security IBM Security Network Protection Solutions Pre-emptive protection to keep you Ahead of the Threat Tanmay Shah Product Lead Network Protection Appliances IBM Security Systems 1 IBM Security
McAfee Labs Threats Report
 McAfee Labs Threats Report December 218 TOP STORIES OF THE QUARTER Underground Forums Boost the Effectiveness of Cybercriminals Cryptomining Boom Times Continue Exploit Kits Add Support for Vulnerabilities,
McAfee Labs Threats Report December 218 TOP STORIES OF THE QUARTER Underground Forums Boost the Effectiveness of Cybercriminals Cryptomining Boom Times Continue Exploit Kits Add Support for Vulnerabilities,
Defend Against the Unknown
 Defend Against the Unknown Stay ahead of new threats with McAfee Endpoint Threat Defense solutions Targeted exploits. Ransomware. Explosive growth in zero-day malware. Organizations are locked in an ongoing
Defend Against the Unknown Stay ahead of new threats with McAfee Endpoint Threat Defense solutions Targeted exploits. Ransomware. Explosive growth in zero-day malware. Organizations are locked in an ongoing
McAfee Embedded Control
 McAfee Embedded Control System integrity, change control, and policy compliance in one solution for integrated control systems McAfee Embedded Control for integrated control systems (ICSs) maintains the
McAfee Embedded Control System integrity, change control, and policy compliance in one solution for integrated control systems McAfee Embedded Control for integrated control systems (ICSs) maintains the
McAfee Application Control/ McAfee Change Control Administration
 McAfee Application Control/ McAfee Change Control Administration Education Services Administration Course The McAfee University McAfee Application Application Control/McAfee Change Control Administration
McAfee Application Control/ McAfee Change Control Administration Education Services Administration Course The McAfee University McAfee Application Application Control/McAfee Change Control Administration
Predators are lurking in the Dark Web - is your network vulnerable?
 Predators are lurking in the Dark Web - is your network vulnerable? Venkatesh Sadayappan (Venky) Security Portfolio Marketing Leader IBM Security - Central & Eastern Europe Venky.iss@cz.ibm.com @IBMSecurityCEE
Predators are lurking in the Dark Web - is your network vulnerable? Venkatesh Sadayappan (Venky) Security Portfolio Marketing Leader IBM Security - Central & Eastern Europe Venky.iss@cz.ibm.com @IBMSecurityCEE
Petroleum Refiner Overhauls Security Infrastructure
 Petroleum Refiner Overhauls Security Infrastructure Small team strengthens security posture and responds faster to threats HollyFrontier Customer Profile Fortune 500 independent petroleum refiner and distributor
Petroleum Refiner Overhauls Security Infrastructure Small team strengthens security posture and responds faster to threats HollyFrontier Customer Profile Fortune 500 independent petroleum refiner and distributor
10 Quick Tips to Mobile Security
 10 Quick Tips to Mobile Security 10 Quick Tips to Mobile Security contents 03 Introduction 05 Mobile Threats and Consequences 06 Important Mobile Statistics 07 Top 10 Mobile Safety Tips 19 Resources 22
10 Quick Tips to Mobile Security 10 Quick Tips to Mobile Security contents 03 Introduction 05 Mobile Threats and Consequences 06 Important Mobile Statistics 07 Top 10 Mobile Safety Tips 19 Resources 22
McAfee Virtual Network Security Platform
 McAfee Virtual Network Security Platform Complete threat detection for cloud networks McAfee Virtual Network Security Platform is a complete network threat and intrusion prevention system (IPS) solution
McAfee Virtual Network Security Platform Complete threat detection for cloud networks McAfee Virtual Network Security Platform is a complete network threat and intrusion prevention system (IPS) solution
Global Manufacturer MAUSER Realizes Dream of Interconnected, Adaptive Security a Reality
 Global Manufacturer MAUSER Realizes Dream of Interconnected, Adaptive Security a Reality McAfee provides a trusted partnership for this agencies security infrastructure MAUSER Group Customer Profile Global
Global Manufacturer MAUSER Realizes Dream of Interconnected, Adaptive Security a Reality McAfee provides a trusted partnership for this agencies security infrastructure MAUSER Group Customer Profile Global
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
Data Loss Prevention - Global Market Outlook ( )
 Report Information More information from: https://www.wiseguyreports.com/reports/826969-data-loss-prevention-global-market-outlook-2016-2022 Data Loss Prevention - Global Market Outlook (2016-2022) Report
Report Information More information from: https://www.wiseguyreports.com/reports/826969-data-loss-prevention-global-market-outlook-2016-2022 Data Loss Prevention - Global Market Outlook (2016-2022) Report
McAfee Web Gateway Administration
 McAfee Web Gateway Administration Education Services Administration Course Training The McAfee Web Gateway Administration course from Education Services provides an in-depth introduction to the tasks crucial
McAfee Web Gateway Administration Education Services Administration Course Training The McAfee Web Gateway Administration course from Education Services provides an in-depth introduction to the tasks crucial
Phishing Activity Trends Report October, 2004
 Phishing Activity Trends Report October, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report October, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
ISO in the world today
 ISO 27001 in the world today 1 Agenda ISO 27001 worldwide Why ISO 27001 Framework to implement ISO 27001 2 ISO 27001 worldwide Source: ISO Annual Survey 3 ISO 27001 worldwide Number of Certificates Year
ISO 27001 in the world today 1 Agenda ISO 27001 worldwide Why ISO 27001 Framework to implement ISO 27001 2 ISO 27001 worldwide Source: ISO Annual Survey 3 ISO 27001 worldwide Number of Certificates Year
Security by Default: Enabling Transformation Through Cyber Resilience
 Security by Default: Enabling Transformation Through Cyber Resilience FIVE Steps TO Better Security Hygiene Solution Guide Introduction Government is undergoing a transformation. The global economic condition,
Security by Default: Enabling Transformation Through Cyber Resilience FIVE Steps TO Better Security Hygiene Solution Guide Introduction Government is undergoing a transformation. The global economic condition,
9 Steps to Protect Against Ransomware
 9 Steps to Protect Against Ransomware IT Support Analyst Task Overview Security Manager Security Dashboard Self Service log Secur Devices With Vulnerabilities Critical Important/High Moderate/Medium 40
9 Steps to Protect Against Ransomware IT Support Analyst Task Overview Security Manager Security Dashboard Self Service log Secur Devices With Vulnerabilities Critical Important/High Moderate/Medium 40
McAfee Embedded Control for Healthcare
 McAfee Embedded Control for Healthcare A single solution for system integrity, change control, and policy compliance McAfee Embedded Control for healthcare part of the McAfee product offering maintains
McAfee Embedded Control for Healthcare A single solution for system integrity, change control, and policy compliance McAfee Embedded Control for healthcare part of the McAfee product offering maintains
akamai s [state of the internet] / security
![akamai s [state of the internet] / security akamai s [state of the internet] / security](/thumbs/89/100126392.jpg) [Volume 2 / Number 2] akamai s [state of the internet] / security Q2 215 executive summary The Security Report has five research sections: Quarter-over-quarter and year-ago quarterly attack statistics
[Volume 2 / Number 2] akamai s [state of the internet] / security Q2 215 executive summary The Security Report has five research sections: Quarter-over-quarter and year-ago quarterly attack statistics
Cyber Attack: Is Your Business at Risk?
 15 July 2017 Cyber Attack: Is Your Business at Risk? Stanley Wong Regional Head of Financial Lines, Asia Pacific Agenda Some common misconceptions by SMEs around cyber protection Cyber Claims and Industry
15 July 2017 Cyber Attack: Is Your Business at Risk? Stanley Wong Regional Head of Financial Lines, Asia Pacific Agenda Some common misconceptions by SMEs around cyber protection Cyber Claims and Industry
U.S. State of Cybercrime
 EXCLUSIVE RESEARCH FROM EXECUTIVE SUMMARY 2017 U.S. State of Cybercrime IDG Communications, Inc. 2017 U.S. State of Cybercrime TODAY S CYBERCRIMES ARE BECOMING MORE TARGETED AND BUILT FOR MAXIMUM IMPACT,
EXCLUSIVE RESEARCH FROM EXECUTIVE SUMMARY 2017 U.S. State of Cybercrime IDG Communications, Inc. 2017 U.S. State of Cybercrime TODAY S CYBERCRIMES ARE BECOMING MORE TARGETED AND BUILT FOR MAXIMUM IMPACT,
Vulnerability Management & Vulnerability Assessment. Nessus Attack Scripting Language (NASL). CVE databases, NVD database
 Case Study 2018 Solution/Service Title Vulnerability Management & Vulnerability Assessment Client Industry Cybersecurity, Vulnerability Assessment and Management, Network Security Client Overview Client
Case Study 2018 Solution/Service Title Vulnerability Management & Vulnerability Assessment Client Industry Cybersecurity, Vulnerability Assessment and Management, Network Security Client Overview Client
(Botnets and Malware) The Zbot attack. Group 7: Andrew Mishoe David Colvin Hubert Liu George Chen John Marshall Buck Scharfnorth
 (Botnets and Malware) The Zbot attack Group 7: Andrew Mishoe David Colvin Hubert Liu George Chen John Marshall Buck Scharfnorth What Happened? Type of Attack Botnet - refers to group of compromised computers
(Botnets and Malware) The Zbot attack Group 7: Andrew Mishoe David Colvin Hubert Liu George Chen John Marshall Buck Scharfnorth What Happened? Type of Attack Botnet - refers to group of compromised computers
Prolexic Attack Report Q4 2011
 Prolexic Attack Report Q4 2011 Prolexic believes the nature of DDoS attacks are changing: they are becoming more concentrated and damaging. Packet-per-second volume is increasing dramatically, while attack
Prolexic Attack Report Q4 2011 Prolexic believes the nature of DDoS attacks are changing: they are becoming more concentrated and damaging. Packet-per-second volume is increasing dramatically, while attack
PRODUCT OVERVIEW. Extend your security intelligence from local network to global cyberspace
 PRODUCT OVERVIEW Extend your security intelligence from local network to global cyberspace What is a Threat Intelligence solution? ESET s Threat Intelligence service provides global knowledge on targeted
PRODUCT OVERVIEW Extend your security intelligence from local network to global cyberspace What is a Threat Intelligence solution? ESET s Threat Intelligence service provides global knowledge on targeted
WEB APPLICATION VULNERABILITIES
 WEB APPLICATION VULNERABILITIES CONTENTS Introduction... 3 1. Materials and methods... 3 2. Executive summary... 4 3. Client snapshot... 4 4. Trends... 5 5. Manual web application security assessment...
WEB APPLICATION VULNERABILITIES CONTENTS Introduction... 3 1. Materials and methods... 3 2. Executive summary... 4 3. Client snapshot... 4 4. Trends... 5 5. Manual web application security assessment...
McAfee Embedded Control for Retail
 McAfee Embedded Control for Retail System integrity, change control, and policy compliance for retail point of sale systems McAfee Embedded Control for retail maintains the integrity of your point-of-sale
McAfee Embedded Control for Retail System integrity, change control, and policy compliance for retail point of sale systems McAfee Embedded Control for retail maintains the integrity of your point-of-sale
Kaspersky Security. The Power to Protect Your Organization
 Kaspersky Security SOLUTIONS The Power to Protect Your Organization We believe that every organization from the smallest business to the largest corporation or government body should feel empowered to
Kaspersky Security SOLUTIONS The Power to Protect Your Organization We believe that every organization from the smallest business to the largest corporation or government body should feel empowered to
SYMANTEC ENTERPRISE SECURITY. Symantec Internet Security Threat Report September 2005 Power and Energy Industry Data Sheet
 SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
Panda Security 2010 Page 1
 Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
SIEM: Five Requirements that Solve the Bigger Business Issues
 SIEM: Five Requirements that Solve the Bigger Business Issues After more than a decade functioning in production environments, security information and event management (SIEM) solutions are now considered
SIEM: Five Requirements that Solve the Bigger Business Issues After more than a decade functioning in production environments, security information and event management (SIEM) solutions are now considered
Security Gap Analysis: Aggregrated Results
 Email Security Gap Analysis: Aggregrated Results Average rates at which enterprise email security systems miss spam, phishing and malware attachments November 2017 www.cyren.com 1 Email Security Gap Analysis:
Email Security Gap Analysis: Aggregrated Results Average rates at which enterprise email security systems miss spam, phishing and malware attachments November 2017 www.cyren.com 1 Email Security Gap Analysis:
Protecting your next investment: The importance of cybersecurity due diligence
 Protecting your next investment: The importance of cybersecurity due diligence Oct. 11, 2018 Baker Tilly Virchow Krause, LLP. All rights reserved. Baker Tilly refers to Baker Tilly Virchow Krause, LLP,
Protecting your next investment: The importance of cybersecurity due diligence Oct. 11, 2018 Baker Tilly Virchow Krause, LLP. All rights reserved. Baker Tilly refers to Baker Tilly Virchow Krause, LLP,
Caribbean Cyber Security: Not Only Government s Responsibility
 Caribbean Cyber Security: Not Only Government s Responsibility AWARENESS AND VIGILANCE IS EVERYBODY S RESPONSIBILITY Preseted at: ICT Symposium Antigua and Barbuda March 2017 Caribbean Cyber Security Events
Caribbean Cyber Security: Not Only Government s Responsibility AWARENESS AND VIGILANCE IS EVERYBODY S RESPONSIBILITY Preseted at: ICT Symposium Antigua and Barbuda March 2017 Caribbean Cyber Security Events
RANSOMWARE PROTECTION. A Best Practices Approach to Securing Your Enterprise
 RANSOMWARE PROTECTION A Best Practices Approach to Securing Your Enterprise TABLE OF CONTENTS Introduction...3 What is Ransomware?...4 Employee Education...5 Vulnerability Patch Management...6 System Backups...7
RANSOMWARE PROTECTION A Best Practices Approach to Securing Your Enterprise TABLE OF CONTENTS Introduction...3 What is Ransomware?...4 Employee Education...5 Vulnerability Patch Management...6 System Backups...7
THE REAL TRUTH BEHIND RANSOMWARE EDDY WILLEMS SECURITY EVANGELIST
 THE REAL TRUTH BEHIND RANSOMWARE EDDY WILLEMS SECURITY EVANGELIST TWITTER: @EDDYWILLEMS 1 OFFERING SECURITY SOLUTIONS WORLDWIDE Founded in Bochum, Germany in 1985 First AV solution in 1987 Global head
THE REAL TRUTH BEHIND RANSOMWARE EDDY WILLEMS SECURITY EVANGELIST TWITTER: @EDDYWILLEMS 1 OFFERING SECURITY SOLUTIONS WORLDWIDE Founded in Bochum, Germany in 1985 First AV solution in 1987 Global head
McAfee Endpoint Security
 McAfee Endpoint Security Frequently Asked Questions Overview You re facing new challenges in light of the increase of advanced malware. Limited integration between threat detection, network, and endpoint
McAfee Endpoint Security Frequently Asked Questions Overview You re facing new challenges in light of the increase of advanced malware. Limited integration between threat detection, network, and endpoint
McAfee VirusScan and McAfee epolicy Orchestrator Administration Course
 McAfee VirusScan and McAfee epolicy Orchestrator Administration Course Education Services administration course training The McAfee VirusScan Enterprise and McAfee epolicy Orchestrator (McAfee epo ) Administration
McAfee VirusScan and McAfee epolicy Orchestrator Administration Course Education Services administration course training The McAfee VirusScan Enterprise and McAfee epolicy Orchestrator (McAfee epo ) Administration
JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015]
![JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015]](/thumbs/83/87837079.jpg) JPCERT-IR-2015-05 Issued: 2016-01-14 JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
JPCERT-IR-2015-05 Issued: 2016-01-14 JPCERT/CC Incident Handling Report [October 1, 2015 December 31, 2015] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
Technical Brochure F-SECURE THREAT SHIELD
 Technical Brochure F-SECURE THREAT SHIELD F-SECURE THREATSHIELD F-Secure ThreatShield is a gateway-level security solution for protecting email and web traffic, with built-in network sandboxing technology.
Technical Brochure F-SECURE THREAT SHIELD F-SECURE THREATSHIELD F-Secure ThreatShield is a gateway-level security solution for protecting email and web traffic, with built-in network sandboxing technology.
Reduce Your Network's Attack Surface
 WHITE PAPER Reduce Your Network's Attack Surface Ixia's ThreatARMOR Frees Up Security Resources and Personnel The Threat Landscape When you re dealing with network security, one of the primary measurements
WHITE PAPER Reduce Your Network's Attack Surface Ixia's ThreatARMOR Frees Up Security Resources and Personnel The Threat Landscape When you re dealing with network security, one of the primary measurements
Protecting Against Application DDoS A acks with BIG-IP ASM: A Three- Step Solution
 Protecting Against Application DDoS A acks with BIG-IP ASM: A Three- Step Solution Today's security threats increasingly involve application-layer DDoS attacks mounted by organized groups of attackers
Protecting Against Application DDoS A acks with BIG-IP ASM: A Three- Step Solution Today's security threats increasingly involve application-layer DDoS attacks mounted by organized groups of attackers
Phishing Activity Trends Report August, 2006
 Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
McAfee MVISION Cloud. Data Security for the Cloud Era
 McAfee MVISION Cloud Data Security for the Cloud Era McAfee MVISION Cloud protects data where it lives today, with a solution that was built natively in the cloud, for the cloud. It s cloud-native data
McAfee MVISION Cloud Data Security for the Cloud Era McAfee MVISION Cloud protects data where it lives today, with a solution that was built natively in the cloud, for the cloud. It s cloud-native data
Standard Categories for Incident Response (definitions) V2.1. Standard Categories for Incident Response Teams. Definitions V2.1.
 Standard Categories for Incident Response Teams Definitions V2.1 February 2018 Standard Categories for Incident Response (definitions) V2.1 1 Introduction This document outlines categories that Incident
Standard Categories for Incident Response Teams Definitions V2.1 February 2018 Standard Categories for Incident Response (definitions) V2.1 1 Introduction This document outlines categories that Incident
McAfee Public Cloud Server Security Suite
 McAfee Public Cloud Server Security Suite Comprehensive security for AWS and Azure cloud workloads As enterprises shift their data center strategy to include and often lead with public cloud server instances,
McAfee Public Cloud Server Security Suite Comprehensive security for AWS and Azure cloud workloads As enterprises shift their data center strategy to include and often lead with public cloud server instances,
Défense In-Depth Security. Samson Oduor - Internet Solutions Kenya Watson Kamanga - Seacom
 Défense In-Depth Security Samson Oduor - Internet Solutions Kenya Watson Kamanga - Seacom Siku Njema! Good Day! 2 Defense In-depth Security Approach SECTION 1 Introductions SECTION 4 Case - Study SECTION
Défense In-Depth Security Samson Oduor - Internet Solutions Kenya Watson Kamanga - Seacom Siku Njema! Good Day! 2 Defense In-depth Security Approach SECTION 1 Introductions SECTION 4 Case - Study SECTION
Cyber-Threats and Countermeasures in Financial Sector
 Michael Mavroforakis, PhD Group CISO & CDO SEV: Workshop on Digital Enablers (Cloud & Cybersecurity) 27th March 2018 Agenda: CYBERSECURITY Potential Targets Attack Examples Insider vs Outsider Threats
Michael Mavroforakis, PhD Group CISO & CDO SEV: Workshop on Digital Enablers (Cloud & Cybersecurity) 27th March 2018 Agenda: CYBERSECURITY Potential Targets Attack Examples Insider vs Outsider Threats
Automated Context and Incident Response
 Technical Brief Automated Context and Incident Response www.proofpoint.com Incident response requires situational awareness of the target, his or her environment, and the attacker. However, security alerts
Technical Brief Automated Context and Incident Response www.proofpoint.com Incident response requires situational awareness of the target, his or her environment, and the attacker. However, security alerts
MOBILE THREAT LANDSCAPE. February 2018
 MOBILE THREAT LANDSCAPE February 2018 WHERE DO MOBILE THREATS COME FROM? In 2017, mobile applications have been a target of choice for hackers to access and steal data, with 86% of mobile threats coming
MOBILE THREAT LANDSCAPE February 2018 WHERE DO MOBILE THREATS COME FROM? In 2017, mobile applications have been a target of choice for hackers to access and steal data, with 86% of mobile threats coming
Understanding the Changing Cybersecurity Problem
 Understanding the Changing Cybersecurity Problem Keith Price BBus, MSc, CGEIT, CISM, CISSP Founder & Principal Consultant 1 About About me - Specialise in information security strategy, architecture, and
Understanding the Changing Cybersecurity Problem Keith Price BBus, MSc, CGEIT, CISM, CISSP Founder & Principal Consultant 1 About About me - Specialise in information security strategy, architecture, and
Imperva Incapsula Website Security
 Imperva Incapsula Website Security DA T A SH E E T Application Security from the Cloud Imperva Incapsula cloud-based website security solution features the industry s leading WAF technology, as well as
Imperva Incapsula Website Security DA T A SH E E T Application Security from the Cloud Imperva Incapsula cloud-based website security solution features the industry s leading WAF technology, as well as
IBM Cloud Internet Services: Optimizing security to protect your web applications
 WHITE PAPER IBM Cloud Internet Services: Optimizing security to protect your web applications Secure Internet applications and APIs against denialof-service attacks, customer data compromise, and abusive
WHITE PAPER IBM Cloud Internet Services: Optimizing security to protect your web applications Secure Internet applications and APIs against denialof-service attacks, customer data compromise, and abusive
McAfee Network Security Platform
 McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
Panda Security. Corporate Presentation. Gianluca Busco Arré Country Manager
 Panda Security Corporate Presentation Gianluca Busco Arré Country Manager Great minds and Global Presence From 1990, Panda Security has become the leading European multinational developing advanced cybersecurity
Panda Security Corporate Presentation Gianluca Busco Arré Country Manager Great minds and Global Presence From 1990, Panda Security has become the leading European multinational developing advanced cybersecurity
Abstract. The Challenges. ESG Lab Review Proofpoint Advanced Threat Protection. Figure 1. Top Ten IT Skills Shortages for 2016
 ESG Lab Review Proofpoint Advanced Threat Protection Enterprise Strategy Group Getting to the bigger truth. Date: January 2017 Author: Tony Palmer, Senior Lab Analyst; and Jack Poller, Senior Lab Analyst
ESG Lab Review Proofpoint Advanced Threat Protection Enterprise Strategy Group Getting to the bigger truth. Date: January 2017 Author: Tony Palmer, Senior Lab Analyst; and Jack Poller, Senior Lab Analyst
ISACA West Florida Chapter - Cybersecurity Event
 ISACA West Florida Chapter - Cybersecurity Event Presented by Sri Sridharan Managing Director & Chief Operating Officer Florida Center for Cybersecurity CURRENT TRENDS Top Cybersecurity Trends of 2015
ISACA West Florida Chapter - Cybersecurity Event Presented by Sri Sridharan Managing Director & Chief Operating Officer Florida Center for Cybersecurity CURRENT TRENDS Top Cybersecurity Trends of 2015
McAfee epolicy Orchestrator
 McAfee epolicy Orchestrator Centrally get, visualize, share, and act on security insights Security management requires cumbersome juggling between tools and data. This puts the adversary at an advantage
McAfee epolicy Orchestrator Centrally get, visualize, share, and act on security insights Security management requires cumbersome juggling between tools and data. This puts the adversary at an advantage
Machine-Powered Learning for People-Centered Security
 White paper Machine-Powered Learning for People-Centered Security Protecting Email with the Proofpoint Stateful Composite Scoring Service www.proofpoint.com INTRODUCTION: OUTGUNNED AND OVERWHELMED Today
White paper Machine-Powered Learning for People-Centered Security Protecting Email with the Proofpoint Stateful Composite Scoring Service www.proofpoint.com INTRODUCTION: OUTGUNNED AND OVERWHELMED Today
McAfee Advanced Threat Defense
 Advanced Threat Defense Detect advanced malware Advanced Threat Defense enables organizations to detect advanced, evasive malware and convert threat information into immediate action and protection. Unlike
Advanced Threat Defense Detect advanced malware Advanced Threat Defense enables organizations to detect advanced, evasive malware and convert threat information into immediate action and protection. Unlike
How NSFOCUS Protected the G20 Summit. Guy Rosefelt on the Strategy, Staff and Tools Needed to Ensure Cybersecurity
 How NSFOCUS Protected the G20 Summit Guy Rosefelt on the Strategy, Staff and Tools Needed to Ensure Cybersecurity SPONSORED BY Rosefelt is responsible for developing NSFOCUS threat intelligence and web
How NSFOCUS Protected the G20 Summit Guy Rosefelt on the Strategy, Staff and Tools Needed to Ensure Cybersecurity SPONSORED BY Rosefelt is responsible for developing NSFOCUS threat intelligence and web
Perimeter Defenses T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN
 T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN Perimeter Defenses Enterprises need to take their security strategy beyond stacking up layers of perimeter defenses to building up predictive
T R U E N E T W O R K S E C U R I T Y DEPENDS ON MORE THAN Perimeter Defenses Enterprises need to take their security strategy beyond stacking up layers of perimeter defenses to building up predictive
How Enterprise Tackles Phishing. Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong
 How Enterprise Tackles Phishing Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong Hackers turning to easy marks - Social engineering Phishing was the #1 threat vector (> 50%) for Office
How Enterprise Tackles Phishing Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong Hackers turning to easy marks - Social engineering Phishing was the #1 threat vector (> 50%) for Office
Web Application Threat Trend Report
 Web Application Threat Trend Report Trends for 2017 Penta Security Systems Inc. Contents I. Overview II. Executive Summary III. 2017 Web Application Threat Trends 1. Overall Trends 2. Trends in Primary
Web Application Threat Trend Report Trends for 2017 Penta Security Systems Inc. Contents I. Overview II. Executive Summary III. 2017 Web Application Threat Trends 1. Overall Trends 2. Trends in Primary
Kaspersky Security Network
 The Kaspersky Security Network (KSN) is a complex distributed infrastructure dedicated to intelligently processing cybersecurity-related data streams from millions of voluntary participants around the
The Kaspersky Security Network (KSN) is a complex distributed infrastructure dedicated to intelligently processing cybersecurity-related data streams from millions of voluntary participants around the
