McAfee Labs Threats Report
|
|
|
- Gwenda McKenzie
- 5 years ago
- Views:
Transcription
1 McAfee Labs Threats Report September 218 TOP STORIES OF THE QUARTER Want to Break Into a Locked Windows 1 Device? Ask Cortana (CVE ) Threat Report: Don t Join Blockchain Revolution Without Ensuring Security AsiaHitGroup Gang Again Sneaks Billing-Fraud Apps Onto Google Play 1 McAfee Labs Threats Report, September 218
2 McAfee Global Threat Intelligence analyzed, on average, 1,8, URLs, 8, files, and another 2, files in a sandbox each day in Q2. Introduction Welcome to the McAfee Labs Threats Report September 218. In this edition, we highlight the notable investigative research and trends in threats statistics gathered by the McAfee Advanced Threat Research and McAfee Labs teams in Q2 of 218. Cybercriminals continue to follow the money. Although this statement is familiar, our latest Threats Report clearly shows the migration from certain older attacks to new threat vectors as they become more profitable. Just as in Q1, we see the popularity of cryptocurrency mining continue to rise. In this report we detail recent findings from three McAfee Labs analyses that appeared in Q2. You can read summaries of each on pages 5-7. One area of investigation by our research teams is in digital assistants. In Q2 we analyzed a vulnerability in Microsoft s Cortana. This flaw allowed an attacker to log into a locked Windows device and execute code. ing our vulnerability disclosure policy, we communicated our findings to Microsoft; the analysis resulted in CVE We also examined the world of cryptocurrency attacks with an in-depth view of blockchain technology. Our report detailed many of the vulnerabilities being exploited by threat actors looking for a quick return on their investment. This report was researched and written by: Christiaan Beek Carlos Castillo Cedric Cochin Ashley Dolezal Steve Grobman Charles McFarland Niamh Minihane Chris Palm Eric Peterson Steve Povolny Raj Samani Craig Schmugar ReseAnne Sims Dan Sommer Bing Sun 2 McAfee Labs Threats Report, September 218
3 KEY TOPIC Turning to malware, our report details an area of cybercrime that is often poorly reported compared with the large-scale and noisy ransomware attacks of the past 18 months. Billing fraud has been the modus operandi of multiple threat actor groups for some time. We examine a campaign by the AsiaHitGroup that has attempted to charge 2, victims using apps from official stores such as Google Play. In Q2, McAfee Global Threat Intelligence received an average of 49 billion queries per day. Meanwhile, the amount of new malware has fallen for the second successive quarter; however, this may not be significant because we saw a spike in Q4 of 217, and new samples have been relatively flat for four of the past five quarters. New mobile malware samples increased 27% in Q2; this is the second successive quarter of growth. Coin miner malware remains very active; total samples grew by 86% in Q2, with more than 2.5 million new files added to the malware database. We are pleased to let you know that all of our research is now available on the McAfee epolicy Orchestrator (McAfee epo ) platform, starting with Version This is in addition to our usual social channels, detailed below, plus the home pages of McAfee Labs and McAfee Advanced Threat Research. Stay Safe. Stay Informed. Steve Grobman, Chief Technology Officer Raj Samani, Chief Scientist and McAfee Fellow, Advanced Threat 3 McAfee Labs Threats Report, September 218
4 Table of Contents 5 Want to Break Into a Locked Windows 1 Device? Ask Cortana (CVE ) Prev Hash Nonce Data 6 Threat Report: Don t Join Blockchain Revolution Without Ensuring Security 7 AsiaHitGroup Gang Again Sneaks Billing-Fraud Apps Onto Google Play 9 Threats Statistics 4 McAfee Labs Threats Report, September 218
5 KEY TOPIC Top stories of the quarter Want to Break Into a Locked Windows 1 Device? Ask Cortana (CVE ) McAfee Labs and the Advanced Threat Research team discovered a vulnerability in the Cortana voice assistant in Microsoft Windows 1. The flaw, for which Microsoft provided a fix in June, can lead to unauthorized code execution. We explain how this vulnerability can be used to execute code from the locked screen of a fully patched Windows 1 machine (RS3 and RS4 before the June patch). In this analysis, we address three vectors of research that have been combined by Microsoft and together represent CVE The first of these is an information leak; we finish with a demo showing full code execution to log in to a locked Windows device! We submitted the vulnerability to Microsoft in April as part of the Advanced Threat Research team s responsible disclosure policy. Attribution for this vulnerability submission goes to Cedric Cochin, Cyber Security Architect and Senior Principal Engineer. Microsoft Cortana Vulnerability Execute PS1 payload (AMSI bypass, remove Defender from the equation, then UAC bypass) Execute PS1 with HIGH integrity (no UAC) Credentials reset. Adversary now has full access to locked user s session Initial Execution 1st Stage Payload 2nd Stage Payload Actions on objective Figure 1. With four basic steps, an attacker can exploit Cortana and gain full control of a Windows 1 system. 5 McAfee Labs Threats Report, September 218
6 KEY TOPIC Threat Report: Don t Join Blockchain Revolution Without Ensuring Security Due to the increasing popularity of cryptocurrencies, the blockchain revolution is in full swing. Cybercriminals have also found new angles including illegal coin mining and theft leading to profits. The McAfee Advanced Threat Research team published in June a blockchain threat report to explain current threats against the users and implementers of blockchain technologies. Even if you have not heard of blockchain, you have likely heard of cryptocurrencies, especially Bitcoin, the most popular implementation. Cryptocurrencies are built on top of blockchain, which records transactions in a decentralized way and enables a trusted ledger between trustless participants. Each block in the ledger is linked to the next block, creating a chain. The chain enables anyone to validate all transactions without going to an outside source. From this, decentralized currencies such as Bitcoin are possible. In this report, we examine the primary attack vectors: phishing, malware, implementation vulnerabilities, and technology. Hash Function Hash Function Prev Nonce Prev Nonce Prev Nonce Hash Data Hash Data Hash Data Block Miners hash a block until a valid hash is found, incrementing the Nonce between attempts. The valid hash becomes part of the next block. The chain can be followed by using the previous hash of each block. Figure 2. A proof-of-work blockchain, building on each previous hash. Source: 6 McAfee Labs Threats Report, September 218
7 KEY TOPIC AsiaHitGroup Gang Again Sneaks Billing-Fraud Apps Onto Google Play The McAfee Mobile Research team found a new billingfraud campaign of at least 15 apps published in 218 on Google Play. Toll fraud (which includes billing fraud) is a leading category of potentially harmful apps on Google Play, according to the report Android Security 217 Year in Review. This new campaign demonstrates that cybercriminals keep finding new ways to steal money from victims using apps on official stores such as Google Play. The actors behind this campaign, the AsiaHitGroup Gang, has been active since at least late 216 with the distribution of the fake-installer applications Sonvpay.A, which attempted to charge at least 2, victims from primarily Thailand and Malaysia for the download of copies of popular applications. One year later, in November 217, a new campaign was discovered on Google Play, Sonvpay.B, which used IP address geolocation to confirm the country of the victim and added Russian victims to the billing fraud to increase its potential to steal money from unsuspected users. Our investigation explains how the malware in these campaigns works. Figure 3. Malicious apps from the AsiaHitGroup Gang formerly found on Google Play. 7 McAfee Labs Threats Report, September 218
8 KEY TOPIC STATISTICS McAfee Global Threat Intelligence Every quarter, the McAfee Global Threat Intelligence (McAfee GTI) cloud dashboard allows us to see and analyze real-world attack patterns that lead to better customer protection. This information provides insights into attack volumes that our customers experience. Each day, on average, McAfee GTI received 49 billion queries and 13 billion lines of telemetry, while analyzing 1,8, URLs and 8, files, plus another 2, files in a sandbox. McAfee GTI protections against malicious files reported 86, (.1%) of them risky in Q2, out of 86 million tested files. McAfee GTI protections against malicious URLs reported 365, (.5%) of them risky in Q2, out of 73 million tested URLs. McAfee GTI protections against malicious IP addresses reported 268, (.4%) of them risky in Q2, out of 67 million tested IP addresses. 8 McAfee Labs Threats Report, September 218
9 Threats Statistics 1 Malware 17 Incidents 19 Web and Network Threats 9 McAfee Labs Threats Report, September 218
10 Malware 7,, 6,, 5,, 4,, New malware 9,, 8,, 7,, 6,, 5,, Total malware Malware data comes from the McAfee Sample Database, which includes malicious files gathered by McAfee spam traps, crawlers, and customer submissions, as well as from other industry sources. 3,, 4,, 2,, 1,, 3,, 2,, 1,, Source: McAfee Labs, 218. Source: McAfee Labs, 218. New Mac OS malware Total Mac OS malware 9, 5, 8, 45, 7, 6, 5, 4, 3, 2, 1, 4, 35, 3, 25, 2, 15, 1, 5, Source: McAfee Labs, 218. Source: McAfee Labs, McAfee Labs Threats Report, September 218
11 New mobile malware Total mobile malware 3,, 3,, 2,5, 25,, 2,, 2,, 1,5, 15,, 1,, 1,, 5, 5,, Source: McAfee Labs, 218. Source: McAfee Labs, 218. Regional mobile malware infection rates (Percentage of mobile customers reporting infections) Global mobile malware infection rates (Percentage of mobile customers reporting infections) 14% 12% 18% 16% 14% 12% 1% 8% 6% 4% 2% % Africa Asia Australia Europe North America South America Q3 217 Q4 217 Q1 218 Q % 8% 6% 4% 2% % Source: McAfee Labs, 218. Source: McAfee Labs, McAfee Labs Threats Report, September 218
12 New ransomware 2,, Total ransomware 2,5, 18,, 16,, 2,, 14,, 12,, 1,5, 1,, 1,, 8,, 6,, 5, 4,, 2,, Source: McAfee Labs, 218. Source: McAfee Labs, ,, 8, 6, 4, 2, New Android lockscreen malware 2,, 1,6, 1,2, 8, 4, Total Android lockscreen malware Source: McAfee Labs, 218. Source: McAfee Labs, McAfee Labs Threats Report, September 218
13 1,6, 1,4, 1,2, 1,, 8, 6, 4, 2, New malicious signed binaries ,, 25,, 2,, 15,, 1,, 5,, Total malicious signed binaries Certificate authorities provide digital certificates that deliver information once a binary (application) is signed and validated by the content provider. When cybercriminals obtain digital certificates for malicious signed binaries, attacks are much simpler to execute. Source: McAfee Labs, 218. Source: McAfee Labs, ,8, 1,6, 1,4, 1,2, 1,, 8, 6, 4, New exploit malware 2,, 18,, 16,, 14,, 12,, 1,, 8,, 6,, 4,, Total exploit malware Exploits take advantage of bugs and vulnerabilities in software and hardware. Zeroday attacks are examples of successful exploits. For an example, see the McAfee Labs post Analyzing Microsoft Office Zero-Day Exploit CVE : Memory Corruption Vulnerability. 2, 2,, Source: McAfee Labs, 218. Source: McAfee Labs, McAfee Labs Threats Report, September 218
14 25, 2, 15, 1, 5, New macro malware 1,8, 1,6, 1,4, 1,2, 1,, 8, 6, 4, 2, Total macro malware Macro malware usually arrives as a Word or Excel document in a spam or zipped attachment. Bogus but tempting filenames encourage victims to open the documents, leading to infection if macros are enabled. Q2 Q3 Q4 Q1 Q2 Q3 Q4 Q Source: McAfee Labs, 218. Source: McAfee Labs, ,, 4,5, 4,, 3,5, 3,, New Faceliker malware 25,, 2,, Total Faceliker malware The Faceliker Trojan manipulates Facebook clicks to artificially like certain content. To learn more, read this post from McAfee Labs. 2,5, 2,, 15,, 1,5, 1,, 1,, 5, ,, Source: McAfee Labs, 218. Source: McAfee Labs, McAfee Labs Threats Report, September 218
15 8,, 7,, 6,, 5,, New JavaScript malware 7,, 6,, 5,, Total JavaScript malware For more on JavaScript and PowerShell threats, read The rise of script-based malware, from an earlier McAfee Labs Threats Report. 4,, 4,, 3,, 3,, 2,, 2,, 1,, 1,, Source: McAfee Labs, 218. Source: McAfee Labs, 218. New PowerShell malware Total PowerShell malware 18, 7, 16, 14, 12, 1, 6, 5, 4, 8, 6, 4, 2, 3, 2, 1, Source: McAfee Labs, 218. Source: McAfee Labs, McAfee Labs Threats Report, September 218
16 45, 4, 35, 3, New LNK malware 1,4, 1,2, 1,, Total LNK malware Cybercriminals are increasingly using.lnk shortcuts to surreptitiously deliver malicious PowerShell scripts and other malware. 25, 8, 2, 6, 15, 1, 5, 4, 2, Source: McAfee Labs, 218. Source: McAfee Labs, ,, 2,5, 2,, 1,5, New coin miner malware 6,, 5,, 4,, 3,, Total coin miner malware Coin miner malware hijacks systems to create ( mine ) cryptocurrency without victims consent or awareness. New coin miner threats have jumped massively in ,, 2,, 5, 1,, Source: McAfee Labs, 218. Source: McAfee Labs, McAfee Labs Threats Report, September 218
17 Incidents Publicly disclosed security incidents by region (Number of publicly disclosed incidents) Top 1 attack vectors in (Number of reported breaches) Security incidents data is compiled from several sources, including hackmageddon.com, privacyrights.org/databreaches, haveibeenpwned. com, and databreaches.net Africa Asia-Pacific Multiple Regions Americas Europe Unknown Malware Account Hacking Leak Unauthorized Access Theft Vulnerability W-2 Scam Denial of Service Defacement The majority of attack vectors are either not known or not publicly reported. Source: McAfee Labs, 218. Source: McAfee Labs, McAfee Labs Threats Report, September 218
18 Top sectors targeted in North and South America (Number of reported breaches) 45 Top 1 targeted sectors in (Number of reported breaches) Online Services Technology Media Retail Entertainment Finance Education Mutiple Public Health Care Cryptocurrency Retail Technology Entertainment Media Multiple Education Finance Public Health Care Q3 217 Q4 217 Q1 218 Q2 218 Source: McAfee Labs, 218. Source: McAfee Labs, McAfee Labs Threats Report, September 218
19 Web and Network Threats 2,, 18,, 16,, 14,, 12,, 1,, 8,, 6,, 4,, 2,, 4,5, 4,, 3,5, 3,, 2,5, 2,, 1,5, 1,, New suspect URLs New malicious downloads URLs Source: McAfee Labs, ,, 1,, 8,, 6,, 4,, 2,, 8, 7, 6, 5, 4, 3, 2, New malicious URLs New phishing URLs Source: McAfee Labs, 218. The McAfee TrustedSource Web Database contains URLs (web pages) organized into categories, based on web reputation, to use with filtering policies to manage web access. Suspect URLs are the total number of sites that earn High Risk or Medium Risk scores. Malicious URLs deploy code, including drive-by executables and Trojans, designed to hijack a computer s settings or activity. Malicious downloads come from sites that allow users, sometimes without their knowledge, to inadvertently download code that is harmful or annoying. Phishing URLs are web pages that typically arrive in hoax s to steal user account information. 5, 1, Source: McAfee Labs, 218. Source: McAfee Labs, McAfee Labs Threats Report, September 218
20 Top malware connecting to control servers in Q2 1% 1% 1% 1% 2% 3% 4% GoScanSSH Wapomi 5% China Chopper Maazben 52% Ramnit 35% Salty Muieblackcat Mirai Others Spam botnet prevalence by volume in Q2 3% 2%1% 1% 7% Gamut Cutwail Stealrat Kelihos Necurs 86% Others The Gamut spam botnet outpaced all others during Q2. Most notably, it pushed Canada Revenue Agency phishing scams in high volume. Recent campaigns were related to bogus job offers that are commonly used as a money mule recruitment tactic. Source: McAfee Labs, 218. Source: McAfee Labs, 218. Top countries hosting botnet control servers in Q2 Top network attacks in Q2 2% 2% 2% 2% 4% 24% 4% 5% 5% 14% 36% United States Germany Russia Netherlands France China Japan Brazil United Kingdom Hong Kong Others 9% 13% 4% 3% 3% 3% Denial of service 13% 52% Server message block Browser Brute force Web DNS Scan SSL Source: McAfee Labs, 218. Source: McAfee Labs, McAfee Labs Threats Report, September 218
21 About McAfee McAfee is the device-to-cloud cybersecurity company. Inspired by the power of working together, McAfee creates business and consumer solutions that make our world a safer place. By building solutions that work with other companies products, McAfee helps businesses orchestrate cyber environments that are truly integrated, where protection, detection, and correction of threats happen simultaneously and collaboratively. By protecting consumers across all their devices, McAfee secures their digital lifestyle at home and away. By working with other security players, McAfee is leading the effort to unite against cybercriminals for the benefit of all. About McAfee Labs and Advanced Threat Research McAfee Labs, led by McAfee Advanced Threat Research, is one of the world s leading sources for threat research, threat intelligence, and cybersecurity thought leadership. With data from millions of sensors across key threats vectors file, web, message, and network McAfee Labs and McAfee Advanced Threat Research deliver real-time threat intelligence, critical analysis, and expert thinking to improve protection and reduce risks Mission College Blvd. Santa Clara, CA McAfee and the McAfee logo are trademarks or registered trademarks of McAfee, LLC or its subsidiaries in the US and other countries. Other marks and brands may be claimed as the property of others. Copyright 218 McAfee LLC. 4116_918 SEPTEMBER McAfee Labs Threats Report, September 218
McAfee Labs Threat Report
 McAfee Labs Threat Report December 217 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threat Report, December 217 The McAfee Labs count of new malware in Q3 reached an all-time
McAfee Labs Threat Report December 217 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threat Report, December 217 The McAfee Labs count of new malware in Q3 reached an all-time
McAfee Labs Threats Report
 McAfee Labs Threats Report March 218 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threats Report, March 218 The McAfee Labs count of new malware in Q4 reached an all-time
McAfee Labs Threats Report March 218 THREATS STATISTICS Malware Incidents Web and Network Threats 1 McAfee Labs Threats Report, March 218 The McAfee Labs count of new malware in Q4 reached an all-time
Building Resilience in a Digital Enterprise
 Building Resilience in a Digital Enterprise Top five steps to help reduce the risk of advanced targeted attacks To be successful in business today, an enterprise must operate securely in the cyberdomain.
Building Resilience in a Digital Enterprise Top five steps to help reduce the risk of advanced targeted attacks To be successful in business today, an enterprise must operate securely in the cyberdomain.
Protecting Your Enterprise Databases from Ransomware
 Protecting Your Enterprise Databases from Ransomware 1 Protecting Your Enterprise Databases from Ransomware Protecting Your Enterprise Databases from Ransomware Ransomware is no longer the new kid on the
Protecting Your Enterprise Databases from Ransomware 1 Protecting Your Enterprise Databases from Ransomware Protecting Your Enterprise Databases from Ransomware Ransomware is no longer the new kid on the
with Advanced Protection
 with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco
 What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
Security & Phishing
 Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
Defend Against the Unknown
 Defend Against the Unknown Stay ahead of new threats with McAfee Endpoint Threat Defense solutions Targeted exploits. Ransomware. Explosive growth in zero-day malware. Organizations are locked in an ongoing
Defend Against the Unknown Stay ahead of new threats with McAfee Endpoint Threat Defense solutions Targeted exploits. Ransomware. Explosive growth in zero-day malware. Organizations are locked in an ongoing
Phishing Activity Trends Report August, 2005
 Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Phishing Activity Trends Report January, 2005
 Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Activity Trends Report January, 2005 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent web sites which attempt to trick them into divulging
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Top 10 Global Threat Rank by Source
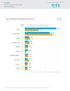 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
McAfee Database Security Insights
 McAfee Database Security Insights Managing the multitude of alerts, reports, and events and sometimes finding the proverbial needle in a haystack is challenging. Monitoring the activity on busy enterprise
McAfee Database Security Insights Managing the multitude of alerts, reports, and events and sometimes finding the proverbial needle in a haystack is challenging. Monitoring the activity on busy enterprise
RANSOMWARE PROTECTION. A Best Practices Approach to Securing Your Enterprise
 RANSOMWARE PROTECTION A Best Practices Approach to Securing Your Enterprise TABLE OF CONTENTS Introduction...3 What is Ransomware?...4 Employee Education...5 Vulnerability Patch Management...6 System Backups...7
RANSOMWARE PROTECTION A Best Practices Approach to Securing Your Enterprise TABLE OF CONTENTS Introduction...3 What is Ransomware?...4 Employee Education...5 Vulnerability Patch Management...6 System Backups...7
Phishing Activity Trends Report August, 2006
 Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
CLOUD REPORT LITTLE CHANGE IN GDPR-READINESS LEVELS WITH MAY 2018 DEADLINE LOOMING. 24.6% of cloud services rated high on GDPR-readiness
 SEPTEMBER 2017 CLOUD REPORT LITTLE CHANGE IN GDPR-READINESS LEVELS WITH MAY 2018 DEADLINE LOOMING 24.6% of cloud services rated high on GDPR-readiness REPORT HIGHLIGHTS 24.6 percent of cloud services are
SEPTEMBER 2017 CLOUD REPORT LITTLE CHANGE IN GDPR-READINESS LEVELS WITH MAY 2018 DEADLINE LOOMING 24.6% of cloud services rated high on GDPR-readiness REPORT HIGHLIGHTS 24.6 percent of cloud services are
Getting over Ransomware - Plan your Strategy for more Advanced Threats
 Getting over Ransomware - Plan your Strategy for more Advanced Threats Kaspersky Lab Hong Kong Eric Kwok General Manager Lapcom Ltd. BEYOND ANTI-VIRUS: TRUE CYBERSECURITY FROM KASPERSKY LAB 20 years ago
Getting over Ransomware - Plan your Strategy for more Advanced Threats Kaspersky Lab Hong Kong Eric Kwok General Manager Lapcom Ltd. BEYOND ANTI-VIRUS: TRUE CYBERSECURITY FROM KASPERSKY LAB 20 years ago
2018 Cyber Security Predictions
 2018 Cyber Security Predictions Rampa Manoonsin Country Manager, Thailand Symantec At a Glance 175M endpoints under protection $5B+ FY18E revenue 2100+ patents Leader in 4 Gartner MQs SWG, EPP, DLP and
2018 Cyber Security Predictions Rampa Manoonsin Country Manager, Thailand Symantec At a Glance 175M endpoints under protection $5B+ FY18E revenue 2100+ patents Leader in 4 Gartner MQs SWG, EPP, DLP and
McAfee Web Gateway Administration
 McAfee Web Gateway Administration Education Services Administration Course Training The McAfee Web Gateway Administration course from Education Services provides an in-depth introduction to the tasks crucial
McAfee Web Gateway Administration Education Services Administration Course Training The McAfee Web Gateway Administration course from Education Services provides an in-depth introduction to the tasks crucial
Phishing Activity Trends Report October, 2004
 Phishing Activity Trends Report October, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
Phishing Activity Trends Report October, 2004 Phishing is a form of online identity theft that uses spoofed emails designed to lure recipients to fraudulent websites which attempt to trick them into divulging
McAfee Embedded Control
 McAfee Embedded Control System integrity, change control, and policy compliance in one solution McAfee Embedded Control maintains the integrity of your system by only allowing authorized code to run and
McAfee Embedded Control System integrity, change control, and policy compliance in one solution McAfee Embedded Control maintains the integrity of your system by only allowing authorized code to run and
McAfee Labs Threats Report
 McAfee Labs Threats Report December 218 TOP STORIES OF THE QUARTER Underground Forums Boost the Effectiveness of Cybercriminals Cryptomining Boom Times Continue Exploit Kits Add Support for Vulnerabilities,
McAfee Labs Threats Report December 218 TOP STORIES OF THE QUARTER Underground Forums Boost the Effectiveness of Cybercriminals Cryptomining Boom Times Continue Exploit Kits Add Support for Vulnerabilities,
9 Steps to Protect Against Ransomware
 9 Steps to Protect Against Ransomware IT Support Analyst Task Overview Security Manager Security Dashboard Self Service log Secur Devices With Vulnerabilities Critical Important/High Moderate/Medium 40
9 Steps to Protect Against Ransomware IT Support Analyst Task Overview Security Manager Security Dashboard Self Service log Secur Devices With Vulnerabilities Critical Important/High Moderate/Medium 40
How Enterprise Tackles Phishing. Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong
 How Enterprise Tackles Phishing Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong Hackers turning to easy marks - Social engineering Phishing was the #1 threat vector (> 50%) for Office
How Enterprise Tackles Phishing Nelson Yuen Technology Manager, Cybersecurity Microsoft Hong Kong Hackers turning to easy marks - Social engineering Phishing was the #1 threat vector (> 50%) for Office
Mapping traditional AV detection failures. October 2017
 Mapping traditional AV detection failures October 2017 TABLE OF CONTENTS Introduction 01 Methodology 02 Findings 03 AV failures common malware 03 Multiple AV failures 04 Four leading AVs failures 05 Conclusion
Mapping traditional AV detection failures October 2017 TABLE OF CONTENTS Introduction 01 Methodology 02 Findings 03 AV failures common malware 03 Multiple AV failures 04 Four leading AVs failures 05 Conclusion
The Scenes of Cyber Crime
 Organizer: BRIDGING BARRIERS: LEGAL AND TECHNICAL OF CYBERCRIME CASES The Scenes of Cyber Crime 5 July 2011 Toralv Dirro EMEA Security Strategist, McAfee Labs Low Risk + High Profit -> Crime 500,000 Cyber
Organizer: BRIDGING BARRIERS: LEGAL AND TECHNICAL OF CYBERCRIME CASES The Scenes of Cyber Crime 5 July 2011 Toralv Dirro EMEA Security Strategist, McAfee Labs Low Risk + High Profit -> Crime 500,000 Cyber
Targeted Ransomware No Longer a Future Threat
 REPORT Targeted Ransomware No Longer a Future Threat Analysis of a t argeted and manual ransomware campaign February 2016 Table of Contents Authors This report was researched and written by: Christiaan
REPORT Targeted Ransomware No Longer a Future Threat Analysis of a t argeted and manual ransomware campaign February 2016 Table of Contents Authors This report was researched and written by: Christiaan
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of July, 2007 Summarization of July Report Findings For the first time recorded by the APWG, China has surpassed the United States as the country hosting the
Phishing Activity Trends Report for the Month of July, 2007 Summarization of July Report Findings For the first time recorded by the APWG, China has surpassed the United States as the country hosting the
This Online Gaming Company Didn t Want to Roll the Dice on Security That s Why it Worked with BlackBerry
 This Online Gaming Company Didn t Want to Roll the Dice on Security That s Why it Worked with BlackBerry At a Glance With offices across the country, this gaming company has been in operation for decades.
This Online Gaming Company Didn t Want to Roll the Dice on Security That s Why it Worked with BlackBerry At a Glance With offices across the country, this gaming company has been in operation for decades.
THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION BREACH & ATTACK SIMULATION
 BREACH & ATTACK SIMULATION THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION Cymulate s cyber simulation platform allows you to test your security assumptions, identify possible security gaps and receive
BREACH & ATTACK SIMULATION THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION Cymulate s cyber simulation platform allows you to test your security assumptions, identify possible security gaps and receive
JAPAN CYBER-SAVVINESS REPORT 2016 CYBERSECURITY: USER KNOWLEDGE, BEHAVIOUR AND ATTITUDES IN JAPAN
 JAPAN CYBER-SAVVINESS REPORT 2016 CYBERSECURITY: USER KNOWLEDGE, BEHAVIOUR AND ATTITUDES IN JAPAN 1. Why did ESET undertake this survey? 2. Survey methodology 3. Key highlights 4. User confidence in protecting
JAPAN CYBER-SAVVINESS REPORT 2016 CYBERSECURITY: USER KNOWLEDGE, BEHAVIOUR AND ATTITUDES IN JAPAN 1. Why did ESET undertake this survey? 2. Survey methodology 3. Key highlights 4. User confidence in protecting
Défense In-Depth Security. Samson Oduor - Internet Solutions Kenya Watson Kamanga - Seacom
 Défense In-Depth Security Samson Oduor - Internet Solutions Kenya Watson Kamanga - Seacom Siku Njema! Good Day! 2 Defense In-depth Security Approach SECTION 1 Introductions SECTION 4 Case - Study SECTION
Défense In-Depth Security Samson Oduor - Internet Solutions Kenya Watson Kamanga - Seacom Siku Njema! Good Day! 2 Defense In-depth Security Approach SECTION 1 Introductions SECTION 4 Case - Study SECTION
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of June, 2007 Summarization of June Report Findings In the June 2007 report the APWG introduces a brand-domain pairs measurement (page 4) which combines the
Phishing Activity Trends Report for the Month of June, 2007 Summarization of June Report Findings In the June 2007 report the APWG introduces a brand-domain pairs measurement (page 4) which combines the
10 Quick Tips to Mobile Security
 10 Quick Tips to Mobile Security 10 Quick Tips to Mobile Security contents 03 Introduction 05 Mobile Threats and Consequences 06 Important Mobile Statistics 07 Top 10 Mobile Safety Tips 19 Resources 22
10 Quick Tips to Mobile Security 10 Quick Tips to Mobile Security contents 03 Introduction 05 Mobile Threats and Consequences 06 Important Mobile Statistics 07 Top 10 Mobile Safety Tips 19 Resources 22
IC B01: Internet Security Threat Report: How to Stay Protected
 IC B01: Internet Security Threat Report: How to Stay Protected Piero DePaoli Director, Product Marketing IC B01: Internet Security Threat Report: How to Stay Protected 1 Topics 1 Targeted Attacks 2 Spam
IC B01: Internet Security Threat Report: How to Stay Protected Piero DePaoli Director, Product Marketing IC B01: Internet Security Threat Report: How to Stay Protected 1 Topics 1 Targeted Attacks 2 Spam
Panda Security 2010 Page 1
 Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
CloudSOC and Security.cloud for Microsoft Office 365
 Solution Brief CloudSOC and Email Security.cloud for Microsoft Office 365 DID YOU KNOW? Email is the #1 delivery mechanism for malware. 1 Over 40% of compliance related data in Office 365 is overexposed
Solution Brief CloudSOC and Email Security.cloud for Microsoft Office 365 DID YOU KNOW? Email is the #1 delivery mechanism for malware. 1 Over 40% of compliance related data in Office 365 is overexposed
Securing Your Microsoft Azure Virtual Networks
 Securing Your Microsoft Azure Virtual Networks IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up
Securing Your Microsoft Azure Virtual Networks IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up
Petroleum Refiner Overhauls Security Infrastructure
 Petroleum Refiner Overhauls Security Infrastructure Small team strengthens security posture and responds faster to threats HollyFrontier Customer Profile Fortune 500 independent petroleum refiner and distributor
Petroleum Refiner Overhauls Security Infrastructure Small team strengthens security posture and responds faster to threats HollyFrontier Customer Profile Fortune 500 independent petroleum refiner and distributor
Understanding the McAfee Endpoint Security 10 Threat Prevention Module
 Understanding the McAfee Endpoint Security 10 Threat Prevention Module Key enhancements and new capabilities 1 Understanding the McAfee Endpoint Security 10 Threat Prevention Module Table of Contents 3
Understanding the McAfee Endpoint Security 10 Threat Prevention Module Key enhancements and new capabilities 1 Understanding the McAfee Endpoint Security 10 Threat Prevention Module Table of Contents 3
Services solutions for Managed Service Providers (MSPs)
 McAfee Advanced Threat Defense Services solutions for Managed Service Providers (MSPs) Differentiate your services and protect customers against zero-day attacks with the industry s most comprehensive
McAfee Advanced Threat Defense Services solutions for Managed Service Providers (MSPs) Differentiate your services and protect customers against zero-day attacks with the industry s most comprehensive
McAfee Advanced Threat Defense
 Advanced Threat Defense Detect advanced malware Advanced Threat Defense enables organizations to detect advanced, evasive malware and convert threat information into immediate action and protection. Unlike
Advanced Threat Defense Detect advanced malware Advanced Threat Defense enables organizations to detect advanced, evasive malware and convert threat information into immediate action and protection. Unlike
McAfee Embedded Control for Retail
 McAfee Embedded Control for Retail System integrity, change control, and policy compliance for retail point of sale systems McAfee Embedded Control for retail maintains the integrity of your point-of-sale
McAfee Embedded Control for Retail System integrity, change control, and policy compliance for retail point of sale systems McAfee Embedded Control for retail maintains the integrity of your point-of-sale
Prolexic Attack Report Q4 2011
 Prolexic Attack Report Q4 2011 Prolexic believes the nature of DDoS attacks are changing: they are becoming more concentrated and damaging. Packet-per-second volume is increasing dramatically, while attack
Prolexic Attack Report Q4 2011 Prolexic believes the nature of DDoS attacks are changing: they are becoming more concentrated and damaging. Packet-per-second volume is increasing dramatically, while attack
How NSFOCUS Protected the G20 Summit. Guy Rosefelt on the Strategy, Staff and Tools Needed to Ensure Cybersecurity
 How NSFOCUS Protected the G20 Summit Guy Rosefelt on the Strategy, Staff and Tools Needed to Ensure Cybersecurity SPONSORED BY Rosefelt is responsible for developing NSFOCUS threat intelligence and web
How NSFOCUS Protected the G20 Summit Guy Rosefelt on the Strategy, Staff and Tools Needed to Ensure Cybersecurity SPONSORED BY Rosefelt is responsible for developing NSFOCUS threat intelligence and web
Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any
 OWASP Top 10 Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any tester can (and should) do security testing
OWASP Top 10 Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any tester can (and should) do security testing
Security by Default: Enabling Transformation Through Cyber Resilience
 Security by Default: Enabling Transformation Through Cyber Resilience FIVE Steps TO Better Security Hygiene Solution Guide Introduction Government is undergoing a transformation. The global economic condition,
Security by Default: Enabling Transformation Through Cyber Resilience FIVE Steps TO Better Security Hygiene Solution Guide Introduction Government is undergoing a transformation. The global economic condition,
Electronic payments in the Netherlands
 Electronic payments in the Netherlands The Dutch approach on Cybersecurity Gijs Boudewijn Deputy General Manager Vienna May 19 th 2015 Agenda Facts and figures Fraud developments in the Netherlands - Situation
Electronic payments in the Netherlands The Dutch approach on Cybersecurity Gijs Boudewijn Deputy General Manager Vienna May 19 th 2015 Agenda Facts and figures Fraud developments in the Netherlands - Situation
QUARTERLY TRENDS AND ANALYSIS REPORT
 September 1, 2007 Volume 2, Issue 3 QUARTERLY TRENDS AND ANALYSIS REPORT www.us-cert.gov Introduction This report summarizes and provides analysis of incident reports submitted to US-CERT during the U.S.
September 1, 2007 Volume 2, Issue 3 QUARTERLY TRENDS AND ANALYSIS REPORT www.us-cert.gov Introduction This report summarizes and provides analysis of incident reports submitted to US-CERT during the U.S.
Protecting Against Online Fraud. F5 EMEA Webinar August 2014
 Protecting Against Online Fraud F5 EMEA Webinar August 2014 Agenda Fraud threat trends and business challenges Web fraud protection Mobile fraud protection Security operations center Example architecture
Protecting Against Online Fraud F5 EMEA Webinar August 2014 Agenda Fraud threat trends and business challenges Web fraud protection Mobile fraud protection Security operations center Example architecture
Be certain. MessageLabs Intelligence: May 2006
 Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
Protecting the Home Front
 Protecting the Home Front Defending the variety of devices in increasingly connected homes 1 Protecting the Home Front Protecting the Home Front Defending the variety of devices in increasingly connected
Protecting the Home Front Defending the variety of devices in increasingly connected homes 1 Protecting the Home Front Protecting the Home Front Defending the variety of devices in increasingly connected
SYMANTEC ENTERPRISE SECURITY. Symantec Internet Security Threat Report September 2005 Power and Energy Industry Data Sheet
 SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
SYMANTEC ENTERPRISE SECURITY Symantec Internet Security Threat Report September 00 Power and Energy Industry Data Sheet An important note about these statistics The statistics discussed in this document
Load Balancing with McAfee Network Security Platform
 Load Balancing with McAfee Network Security Platform Optimizing intrusion prevention system performance 1 Load Balancing with McAfee Network Security Platform Load Balancing with McAfee Network Security
Load Balancing with McAfee Network Security Platform Optimizing intrusion prevention system performance 1 Load Balancing with McAfee Network Security Platform Load Balancing with McAfee Network Security
VIETNAM CYBER-SAVVINESS REPORT 2015 CYBERSECURITY: USER KNOWLEDGE, BEHAVIOUR AND ATTITUDES IN VIETNAM
 VIETNAM CYBER-SAVVINESS REPORT 2015 CYBERSECURITY: USER KNOWLEDGE, BEHAVIOUR AND ATTITUDES IN VIETNAM 1. Why did ESET Undertake this Report? 2. Report Methodology 3. Key Highlights 4. How Many users in
VIETNAM CYBER-SAVVINESS REPORT 2015 CYBERSECURITY: USER KNOWLEDGE, BEHAVIOUR AND ATTITUDES IN VIETNAM 1. Why did ESET Undertake this Report? 2. Report Methodology 3. Key Highlights 4. How Many users in
Botnets: major players in the shadows. Author Sébastien GOUTAL Chief Science Officer
 Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
Evolution of Spear Phishing. White Paper
 Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
HOSTED SECURITY SERVICES
 HOSTED SECURITY SERVICES A PROVEN STRATEGY FOR PROTECTING CRITICAL IT INFRASTRUCTURE AND DEVICES Being always-on, always-connected might be good for business, but it creates an ideal climate for cybercriminal
HOSTED SECURITY SERVICES A PROVEN STRATEGY FOR PROTECTING CRITICAL IT INFRASTRUCTURE AND DEVICES Being always-on, always-connected might be good for business, but it creates an ideal climate for cybercriminal
McAfee Endpoint Security
 McAfee Endpoint Security Frequently Asked Questions Overview You re facing new challenges in light of the increase of advanced malware. Limited integration between threat detection, network, and endpoint
McAfee Endpoint Security Frequently Asked Questions Overview You re facing new challenges in light of the increase of advanced malware. Limited integration between threat detection, network, and endpoint
COST OF CYBER CRIME STUDY INSIGHTS ON THE SECURITY INVESTMENTS THAT MAKE A DIFFERENCE
 2017 COST OF CYBER CRIME STUDY INSIGHTS ON THE SECURITY INVESTMENTS THAT MAKE A DIFFERENCE NUMBER OF SECURITY BREACHES IS RISING AND SO IS SPEND Average number of security breaches each year 130 Average
2017 COST OF CYBER CRIME STUDY INSIGHTS ON THE SECURITY INVESTMENTS THAT MAKE A DIFFERENCE NUMBER OF SECURITY BREACHES IS RISING AND SO IS SPEND Average number of security breaches each year 130 Average
Course Outline (version 2)
 Course Outline (version 2) Page. 1 CERTIFIED SECURE COMPUTER USER This course is aimed at end users in order to educate them about the main threats to their data s security. It also equips the students
Course Outline (version 2) Page. 1 CERTIFIED SECURE COMPUTER USER This course is aimed at end users in order to educate them about the main threats to their data s security. It also equips the students
Automated Context and Incident Response
 Technical Brief Automated Context and Incident Response www.proofpoint.com Incident response requires situational awareness of the target, his or her environment, and the attacker. However, security alerts
Technical Brief Automated Context and Incident Response www.proofpoint.com Incident response requires situational awareness of the target, his or her environment, and the attacker. However, security alerts
CE Advanced Network Security Phishing I
 CE 817 - Advanced Network Security Phishing I Lecture 15 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
CE 817 - Advanced Network Security Phishing I Lecture 15 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
McAfee Web Gateway Administration Intel Security Education Services Administration Course Training
 McAfee Web Gateway Administration Intel Security Education Services Administration Course Training The McAfee Web Gateway Administration course from Education Services provides an in-depth introduction
McAfee Web Gateway Administration Intel Security Education Services Administration Course Training The McAfee Web Gateway Administration course from Education Services provides an in-depth introduction
WHITEPAPER. Protecting Against Account Takeover Based Attacks
 WHITEPAPER Protecting Against Account Takeover Based Email Attacks Executive Summary The onslaught of targeted email attacks such as business email compromise, spear phishing, and ransomware continues
WHITEPAPER Protecting Against Account Takeover Based Email Attacks Executive Summary The onslaught of targeted email attacks such as business email compromise, spear phishing, and ransomware continues
KASPERSKY FRAUD PREVENTION FOR ENDPOINTS
 KASPERSKY FRAUD PREVENTION FOR ENDPOINTS www.kaspersky.com KASPERSKY FRAUD PREVENTION 1. Ways of Attacking Online Banking The prime motive behind cybercrime is making money and today s sophisticated criminal
KASPERSKY FRAUD PREVENTION FOR ENDPOINTS www.kaspersky.com KASPERSKY FRAUD PREVENTION 1. Ways of Attacking Online Banking The prime motive behind cybercrime is making money and today s sophisticated criminal
 Cross-site request forgery Cross-site scripting Man-in-the-browser Session hijacking Malware Man-in-the-middle DNS cache poisoning DNS spoofing DNS hijacking Dictionary attacks DDoS DDoS Eavesdropping
Cross-site request forgery Cross-site scripting Man-in-the-browser Session hijacking Malware Man-in-the-middle DNS cache poisoning DNS spoofing DNS hijacking Dictionary attacks DDoS DDoS Eavesdropping
EY Consulting. Is your strategy planning for the future or creating it? #TransformativeAge
 2018 Ernst & Young Advisory. All rights reserved. Graphics studio France 1802SG1267. ED 04082018 EY Consulting Is your strategy planning for the future or creating it? #TransformativeAge The better the
2018 Ernst & Young Advisory. All rights reserved. Graphics studio France 1802SG1267. ED 04082018 EY Consulting Is your strategy planning for the future or creating it? #TransformativeAge The better the
IBM Security Network Protection Solutions
 Systems IBM Security IBM Security Network Protection Solutions Pre-emptive protection to keep you Ahead of the Threat Tanmay Shah Product Lead Network Protection Appliances IBM Security Systems 1 IBM Security
Systems IBM Security IBM Security Network Protection Solutions Pre-emptive protection to keep you Ahead of the Threat Tanmay Shah Product Lead Network Protection Appliances IBM Security Systems 1 IBM Security
What s on the Horizon for 2016
 Mobile Threat Report What s on the Horizon for 2016 This Threat Report was written by: Bruce Snell Cybersecurity and Privacy Director Intel Security Table of Contents Introduction...3 Stagefright: Setting
Mobile Threat Report What s on the Horizon for 2016 This Threat Report was written by: Bruce Snell Cybersecurity and Privacy Director Intel Security Table of Contents Introduction...3 Stagefright: Setting
IBM Security Systems. IBM X-Force 2012 & CISO Survey. Cyber Security Threat Landscape IBM Corporation IBM Corporation
 IBM X-Force 2012 & CISO Survey Cyber Security Threat Landscape 1 2012 IBM Corporation IBM X-Force 2011 Trend and Risk Report Highlights The mission of the IBM X-Force research and development team is to:
IBM X-Force 2012 & CISO Survey Cyber Security Threat Landscape 1 2012 IBM Corporation IBM X-Force 2011 Trend and Risk Report Highlights The mission of the IBM X-Force research and development team is to:
Abstract. The Challenges. ESG Lab Review Proofpoint Advanced Threat Protection. Figure 1. Top Ten IT Skills Shortages for 2016
 ESG Lab Review Proofpoint Advanced Threat Protection Enterprise Strategy Group Getting to the bigger truth. Date: January 2017 Author: Tony Palmer, Senior Lab Analyst; and Jack Poller, Senior Lab Analyst
ESG Lab Review Proofpoint Advanced Threat Protection Enterprise Strategy Group Getting to the bigger truth. Date: January 2017 Author: Tony Palmer, Senior Lab Analyst; and Jack Poller, Senior Lab Analyst
Mobile Field Worker Security Advocate Series: Customer Conversation Guide. Research by IDC, 2015
 Mobile Field Worker Security Advocate Series: Customer Conversation Guide Research by IDC, 2015 Agenda 1. Security Requirements for Mobile Field Workers 2. Key Mobile Security Challenges Companies Face
Mobile Field Worker Security Advocate Series: Customer Conversation Guide Research by IDC, 2015 Agenda 1. Security Requirements for Mobile Field Workers 2. Key Mobile Security Challenges Companies Face
Cyber Insurance: What is your bank doing to manage risk? presented by
 Cyber Insurance: What is your bank doing to manage risk? David Kitchen presented by Lisa Micciche Today s Agenda Claims Statistics Common Types of Cyber Attacks Typical Costs Incurred to Respond to an
Cyber Insurance: What is your bank doing to manage risk? David Kitchen presented by Lisa Micciche Today s Agenda Claims Statistics Common Types of Cyber Attacks Typical Costs Incurred to Respond to an
Cyber Defense Operations Center
 Cyber Defense Operations Center Providing world-class security protection, detection, and response Marek Jedrzejewicz Principal Security Engineering Manager Microsoft Corporation 1 Cybersecurity. In the
Cyber Defense Operations Center Providing world-class security protection, detection, and response Marek Jedrzejewicz Principal Security Engineering Manager Microsoft Corporation 1 Cybersecurity. In the
McAfee Embedded Control
 McAfee Embedded Control System integrity, change control, and policy compliance in one solution for integrated control systems McAfee Embedded Control for integrated control systems (ICSs) maintains the
McAfee Embedded Control System integrity, change control, and policy compliance in one solution for integrated control systems McAfee Embedded Control for integrated control systems (ICSs) maintains the
Proofpoint, Inc.
 1 2018 Proofpoint, Inc. Juan Carlos Cabrera Country Manager Caribbean & Central America AMENAZAS EN EL 2018 SABES QUIEN ESTA UTILIZANDO TU DOMINIO? 2 2017 Proofpoint, Inc. Juan Carlos Cabrera Country Manager
1 2018 Proofpoint, Inc. Juan Carlos Cabrera Country Manager Caribbean & Central America AMENAZAS EN EL 2018 SABES QUIEN ESTA UTILIZANDO TU DOMINIO? 2 2017 Proofpoint, Inc. Juan Carlos Cabrera Country Manager
EBOOK. Stopping Fraud. How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats.
 EBOOK Stopping Email Fraud How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats www.proofpoint.com EBOOK Stopping Email Fraud 2 Today s email attacks have
EBOOK Stopping Email Fraud How Proofpoint Helps Protect Your Organization from Impostors, Phishers and Other Non-Malware Threats www.proofpoint.com EBOOK Stopping Email Fraud 2 Today s email attacks have
Post-Intrusion Report June White paper
 Post-Intrusion Report June 2015 White paper TABLE OF CONTENTS About the data in this report.... 3 Classification of data.... 3 High-level trends.... 4 Detected threats by category.... 4 A spike in indicators
Post-Intrusion Report June 2015 White paper TABLE OF CONTENTS About the data in this report.... 3 Classification of data.... 3 High-level trends.... 4 Detected threats by category.... 4 A spike in indicators
Securing Your Amazon Web Services Virtual Networks
 Securing Your Amazon Web Services s IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up a workload,
Securing Your Amazon Web Services s IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up a workload,
Radware: Anatomy of an IoT Botnet and Economics of Defense
 BRKPAR-4000 Radware: Anatomy of an IoT Botnet and Economics of Defense Eric Grubel Anatomy of an IoT Botnet and Economics of Defense Eric Grubel VP, Business Development January 2018 Theme of Discussion
BRKPAR-4000 Radware: Anatomy of an IoT Botnet and Economics of Defense Eric Grubel Anatomy of an IoT Botnet and Economics of Defense Eric Grubel VP, Business Development January 2018 Theme of Discussion
IBM Security Systems IBM X-Force 2012 Annual Trend and Risk Report
 IBM Security Systems IBM X-Force 2012 Annual Trend and Risk Report Leslie Horacek X-Force Threat Response Manager horacek@be.ibm.com April 2013 1 X-Force is the foundation for advanced security and threat
IBM Security Systems IBM X-Force 2012 Annual Trend and Risk Report Leslie Horacek X-Force Threat Response Manager horacek@be.ibm.com April 2013 1 X-Force is the foundation for advanced security and threat
Discover threats quickly, remediate immediately, and mitigate the impact of malware and breaches
 Discover threats quickly, remediate immediately, and mitigate the impact of malware and breaches Introduction No matter how hard you work to educate your employees about the constant and evolving threats
Discover threats quickly, remediate immediately, and mitigate the impact of malware and breaches Introduction No matter how hard you work to educate your employees about the constant and evolving threats
Reducing Operational Costs and Combating Ransomware with McAfee SIEM and Integrated Security
 Reducing Operational Costs and Combating Ransomware with McAfee SIEM and Integrated Security Healthcare provider manages threats with ease Atrius Health Customer Profile Large regional healthcare provider
Reducing Operational Costs and Combating Ransomware with McAfee SIEM and Integrated Security Healthcare provider manages threats with ease Atrius Health Customer Profile Large regional healthcare provider
>MESSAGELABS END USER IT SECURITY GUIDE >WHAT STEPS CAN YOU TAKE TO KEEP YOURSELF, YOUR COLLEAGUES AND YOUR COMPANY SAFE ONLINE?
 >MESSAGELABS END USER IT SECURITY GUIDE >WHAT STEPS CAN YOU TAKE TO KEEP YOURSELF, YOUR COLLEAGUES AND YOUR COMPANY SAFE ONLINE? >CONTENTS >WHAT IS MESSAGING AND WEB SECURITY? >P1 >EMAIL THREATS >P1 >VIRUSES
>MESSAGELABS END USER IT SECURITY GUIDE >WHAT STEPS CAN YOU TAKE TO KEEP YOURSELF, YOUR COLLEAGUES AND YOUR COMPANY SAFE ONLINE? >CONTENTS >WHAT IS MESSAGING AND WEB SECURITY? >P1 >EMAIL THREATS >P1 >VIRUSES
GUIDE. Navigating the General Data Protection Regulation Mini Guide
 GUIDE Navigating the General Data Protection Regulation Mini Guide Introduction The General Data Protection Regulation (GDPR) will deliver a long overdue modernization and harmonization of privacy and
GUIDE Navigating the General Data Protection Regulation Mini Guide Introduction The General Data Protection Regulation (GDPR) will deliver a long overdue modernization and harmonization of privacy and
Automating Security Response based on Internet Reputation
 Add Your Logo here Do not use master Automating Security Response based on Internet Reputation IP and DNS Reputation for the IPS Platform Anthony Supinski Senior Systems Engineer www.h3cnetworks.com www.3com.com
Add Your Logo here Do not use master Automating Security Response based on Internet Reputation IP and DNS Reputation for the IPS Platform Anthony Supinski Senior Systems Engineer www.h3cnetworks.com www.3com.com
The State of Mobile Advertising Q2 2012
 Q2 2012 Executive summary In our first edition of the State of Mobile Advertising report, we take an in-depth look at the monetization of mobile advertising from four perspectives within the ad delivery
Q2 2012 Executive summary In our first edition of the State of Mobile Advertising report, we take an in-depth look at the monetization of mobile advertising from four perspectives within the ad delivery
Personal Cybersecurity
 Personal Cybersecurity The Basic Principles Jeremiah School, CEO How big is the issue? 9 8 7 6 5 4 3 2 1 Estimated global damages in 2018 0 2016 2018 2020 2022 2024 2026 2028 2030 Internet Users Billions
Personal Cybersecurity The Basic Principles Jeremiah School, CEO How big is the issue? 9 8 7 6 5 4 3 2 1 Estimated global damages in 2018 0 2016 2018 2020 2022 2024 2026 2028 2030 Internet Users Billions
CHECK POINT SANDBLAST MOBILE BEHAVIORAL RISK ANALYSIS
 CHECK POINT SANDBLAST MOBILE BEHAVIORAL RISK ANALYSIS AN ADVANCED APPROACH TO COMPREHENSIVE MOBILE SECURITY Accurate threat detection and efficient response are critical components of preventing advanced
CHECK POINT SANDBLAST MOBILE BEHAVIORAL RISK ANALYSIS AN ADVANCED APPROACH TO COMPREHENSIVE MOBILE SECURITY Accurate threat detection and efficient response are critical components of preventing advanced
Phishing Activity Trends Report. 4 th Quarter Unifying the. Global Response To Cybercrime. October December 2012
 4 th Quarter 2012 Unifying the Global Response To Cybercrime October December 2012 Published April 24, 2013 Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member companies,
4 th Quarter 2012 Unifying the Global Response To Cybercrime October December 2012 Published April 24, 2013 Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member companies,
McAfee Complete Endpoint Threat Protection Advanced threat protection for sophisticated attacks
 McAfee Complete Endpoint Threat Protection Advanced threat protection for sophisticated attacks Key Advantages Stay ahead of zero-day threats, ransomware, and greyware with machine learning and dynamic
McAfee Complete Endpoint Threat Protection Advanced threat protection for sophisticated attacks Key Advantages Stay ahead of zero-day threats, ransomware, and greyware with machine learning and dynamic
THE ACCENTURE CYBER DEFENSE SOLUTION
 THE ACCENTURE CYBER DEFENSE SOLUTION A MANAGED SERVICE FOR CYBER DEFENSE FROM ACCENTURE AND SPLUNK. YOUR CURRENT APPROACHES TO CYBER DEFENSE COULD BE PUTTING YOU AT RISK Cyber-attacks are increasingly
THE ACCENTURE CYBER DEFENSE SOLUTION A MANAGED SERVICE FOR CYBER DEFENSE FROM ACCENTURE AND SPLUNK. YOUR CURRENT APPROACHES TO CYBER DEFENSE COULD BE PUTTING YOU AT RISK Cyber-attacks are increasingly
THE REAL TRUTH BEHIND RANSOMWARE EDDY WILLEMS SECURITY EVANGELIST
 THE REAL TRUTH BEHIND RANSOMWARE EDDY WILLEMS SECURITY EVANGELIST TWITTER: @EDDYWILLEMS 1 OFFERING SECURITY SOLUTIONS WORLDWIDE Founded in Bochum, Germany in 1985 First AV solution in 1987 Global head
THE REAL TRUTH BEHIND RANSOMWARE EDDY WILLEMS SECURITY EVANGELIST TWITTER: @EDDYWILLEMS 1 OFFERING SECURITY SOLUTIONS WORLDWIDE Founded in Bochum, Germany in 1985 First AV solution in 1987 Global head
Product overview. McAfee Web Protection Hybrid Integration Guide. Overview
 McAfee Web Protection Hybrid Integration Guide Product overview Overview The McAfee Web Protection hybrid solution is the integration of McAfee Web Gateway and McAfee Web Gateway Cloud Service (McAfee
McAfee Web Protection Hybrid Integration Guide Product overview Overview The McAfee Web Protection hybrid solution is the integration of McAfee Web Gateway and McAfee Web Gateway Cloud Service (McAfee
Understanding the Changing Cybersecurity Problem
 Understanding the Changing Cybersecurity Problem Keith Price BBus, MSc, CGEIT, CISM, CISSP Founder & Principal Consultant 1 About About me - Specialise in information security strategy, architecture, and
Understanding the Changing Cybersecurity Problem Keith Price BBus, MSc, CGEIT, CISM, CISSP Founder & Principal Consultant 1 About About me - Specialise in information security strategy, architecture, and
Protect Your Endpoint, Keep Your Business Safe. White Paper. Exosphere, Inc. getexosphere.com
 Protect Your Endpoint, Keep Your Business Safe. White Paper Exosphere, Inc. getexosphere.com White Paper Today s Threat Landscape Cyber attacks today are increasingly sophisticated and widespread, rendering
Protect Your Endpoint, Keep Your Business Safe. White Paper Exosphere, Inc. getexosphere.com White Paper Today s Threat Landscape Cyber attacks today are increasingly sophisticated and widespread, rendering
JPCERT/CC Incident Handling Report [January 1, March 31, 2018]
![JPCERT/CC Incident Handling Report [January 1, March 31, 2018] JPCERT/CC Incident Handling Report [January 1, March 31, 2018]](/thumbs/89/100577955.jpg) JPCERT-IR-2018-01 Issued: 2018-04-12 JPCERT/CC Incident Handling Report [January 1, 2018 - March 31, 2018] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
JPCERT-IR-2018-01 Issued: 2018-04-12 JPCERT/CC Incident Handling Report [January 1, 2018 - March 31, 2018] 1. About the Incident Handling Report JPCERT Coordination Center (herein, JPCERT/CC) receives
Post Intrusion Report
 Post Intrusion Report JUNE 2015 VERSION 2.0 Report Table of Contents About the data in this report 3 Classification of data 3 High-level trends 4 Detected threats by category 4 A spike in indicators of
Post Intrusion Report JUNE 2015 VERSION 2.0 Report Table of Contents About the data in this report 3 Classification of data 3 High-level trends 4 Detected threats by category 4 A spike in indicators of
