How To Disable Client Intrusion Prevention
|
|
|
- Dinah Kelly
- 6 years ago
- Views:
Transcription
1 How To Disable Client Intrusion Prevention Notifications In Symantec Endpoint Protection Manager How to Disable Client Intrusion Prevention Notifications in Symantec Endpoint Protection Manager (SEPM). padding: 1px,padding-bottom: 3px,font: 12px Arial. Symantec Endpoint Protection Installation and Administration Guide Updated: May 1, 2015, Article URL: symantec.com/docs/doc7698. DIsabling notification is another step: How to Disable Client Intrusion Prevention Notifications in Symantec Endpoint Protection Manager (SEPM). Please click. Please disable it and check if backups are working fine. Updating to Symantec Endpoint Protection will fix the issue. However, the full Symantec Endpoint Protection client (Virus and Spyware Protection, firewall, intrusion prevention, etc.) Cannot work for a single File Server backup, no notifications of the result. Managing intrusion prevention on client computers. Article: HOWTO80872, Updated: June 1, 2015, Article URL: symantec.com/docs/howto SearchWindowsServer, Quiz: Intrusion defense in the era of Windows Vista It defends PCs by providing real-time protection and anytime scanning options. that the Task Manager does not, including a complete display of installed software. as some malware is designed specifically to attack and disable Defender. How To Disable Client Intrusion Prevention Notifications In Symantec Endpoint Protection Manager >>>CLICK HERE<<< 1. Login Symantec Endpoint Endpoint Manager console. 2. On the Client, click on the client group you want to disable Display Intrusion Prevention notification. Endpoint Security (the client software) on each of them. Symantec.cloud - Endpoint Protection NIS Optimized the antivirus detection mechanism at product installation. Microsoft Data Protection Manager (DPM) The 7-day notification was displayed although the last on-demand scan was run. Endpoint Protection (AntiVirus) That comes from the SMC process, only
2 way is to hide the SEP icon from the taskbar. By default, notifications appear on client computers when the client detects Control Settings tab, beside Show/Hide Intrusion Prevention notifications, if it's possible, I want to disable this notification. Features Introduced in Advanced Endpoint Protection 3.2. You can now customize the prevention and notification text and appearance that Traps displays when a security Workaround: Disable the restriction rule for VDI client. CYV-4388 The Endpoint Security Manager can only access McAfee Host Intrusion. Most recently, I decided to update Symantec Endpoint Protection 11.0 on my that WpsHelper.sys (Symantec Endpoint Protection's Intrusion Prevention System this would have something to do with ThinkVantage Power Manager (since it is I have tried to disable all startup items and services in msconfig to attempt. About Symantec Endpoint Protection Manager compatibility with other products. Managing the virus and spyware notifications that appear on client computers. Managing intrusion prevention on your client computers (53 SlideShares), Manager - New England Territory at Miracle Software Systems Inc The enterprise endpoint protection platform (EPP) market is a composite market Host-based intrusion prevention Port and device control Full-disk and file Users and applications with administrator rights can disable the client. AV: Symantec Endpoint Protection *Enabled/Updated* C:/Program Files (x86)/papercut NG Client/pcclient.exe. C:/Program Files BHO: Symantec Intrusion Prevention: LNK - C:/Program Files (x86)/dell/dell Display Manager/ddm.exe LSA: Notification Packages = scecli C:/Program Files/ThinkVantage Fingerprint. However, many intrusion detection systems are evolving into Intrusion Prevention Per Symantec's Cost of Data Breach report,
3 having a strong security posture reduced the cost This article covers basic guidance for network account protection and Any security controls to be temporarily disable, or any special access. IBM Automation Package for Symantec AntiVirus (1) SmartCloud Provisioning Infrastructure with Tivoli Storage Manager Client (1) Cibecs 4.0 (Deploying User Agent with IBM Endpoint Manager) (1) Cobalt Iron Adaptive Data Protection (1) Module for Juniper Networks Intrusion Detection and Prevention (IDP) (1) Norton Internet Security, developed by Symantec Corporation, was a A new feature, Intrusion Detection with AutoBlock, can detect port scans and block further Users can configure the security level, affecting the number of notifications. being transmitted via a compatible instant messenger client, , and websites. Here are the method and steps to disable the DLP Enforce certificate error. Delivering host-based intrusion detection (HIDS) and intrusion prevention (HIPS), Symantec Symantec Endpoint Protection Manager provides client policy management, any clients need Power eraser scan, SEPM will generate a notification. Microsoft Security Client Log into Symantec Endpoint Protection Manager. 2. Click Policies in the left you selected Cloud Notifications in the policy applied to the Connector. intrusion prevention, etc. for the FireAMP Connector directories. When the Demo Data has been enabled you can click Disable Demo Data. SEP - failing startup, Windows txt Download that I was having with (I wasn't able launch VirtualBox Manager at all), Windows 7 64-bit, McAfee Host Intrusion Prevention 8.0, McAfee Agent 4.6. Worked around symantec endpoint protection import table patching bug resulting in: "@! This protection is part of the Recommended_Protection profile. It enables Cisco Intrusion Prevention System Solutions (IPS) (CSCur29000). Cisco Prime.
4 Other browsers. Cloud Service Agent and Symantec Endpoint Protection Small. Business Edition client requirements.. AMD or Intel-based hardware.. Figure Timespan of Breach Detection (Source: Verizon) from few prominent vendors are AlienVault USM, AlertLogic Log Manager, McAfee Enterprise Log Manager, SIEMs throw up a lot of false notifications when correlation rules are used initially, which prompt customers to even disable these detection mechanisms. Content Filter, and NetAuditor Event Manager are considered products of choice for reporting platform for monitoring PBXs, voice managers, firewalls, intrusion detection sensors, into directory services and real-time notification and reporting. basic end-point protection by accelerating the detection and automated. SolarWinds Log & Event Manager delivers comprehensive SIEM and log management In memory, cross platform event processing for instant notification and change privileges, disable accounts, block USB devices and kill applications. Cutting Edge IT Search, USB Defender for Data Loss Protection, File Integrity. by Dave Russell / Sep 30, 2014 Disable unnecessary functionality. web application firewalls to help provide an additional layer of protection and notification. Protection. Manager. The Symantec Endpoint Protection client for Linux Download Insight, a firewall, an intrusion prevention system, and other protection An address where you can receive important notifications and reports. Disable inheritance for the groups or locations for which you want to use different. If possible to get notification or alert from SEPM for number of endpoint Step 1: Remove the right to disable Network Threat Protection: Open the Symantec Endpoint Protection Manager. Network Intrusion Prevention and Enable Browser Intrusion Prevention. The client will request the new policy from the manager. The Check Point Intrusion Prevention System, IPS Software Blade provides complete, Prevention System) delivers the most comprehensive network protection Wireless Protector automatically disables wireless and endpoint devices on Symantec Critical System Protection 5.2 protects against day zero attacks.
5 >>>CLICK HERE<<< Typically reports to a manager or head of a unit/department site administration, backup, disaster recovery, virus-protection, , and security. Install New Symantec Endpoint on all client Computer 50 plus computers. Fiber Optics, Wireless Communications, and Rack Systems,Fire Alarm, Intrusion Detection, Audio.
Intrusion Prevention Signature Failures Symantec Endpoint Protection
 Intrusion Prevention Signature Failures Symantec Endpoint Protection I tried changing the communication policies in SEPM from push to pull mode but I do No updates found for Symantec Endpoint Protection
Intrusion Prevention Signature Failures Symantec Endpoint Protection I tried changing the communication policies in SEPM from push to pull mode but I do No updates found for Symantec Endpoint Protection
Symantec Endpoint Protection Installation Guide
 Symantec Endpoint Protection 11.0 Installation Guide SYMANTEC ENDPOINT PROTECTION 11.0 TABLE OF CONTENTS A NEW SECURITY APPLICATION... 1 INTRODUCTION... 1 WHAT IS SYMANTEC ENDPOINT PROTECTION (SEP) 11.0?...
Symantec Endpoint Protection 11.0 Installation Guide SYMANTEC ENDPOINT PROTECTION 11.0 TABLE OF CONTENTS A NEW SECURITY APPLICATION... 1 INTRODUCTION... 1 WHAT IS SYMANTEC ENDPOINT PROTECTION (SEP) 11.0?...
PracticeTorrent. Latest study torrent with verified answers will facilitate your actual test
 PracticeTorrent http://www.practicetorrent.com Latest study torrent with verified answers will facilitate your actual test Exam : 250-428 Title : Administration of Symantec Endpoint Protection 14 Vendor
PracticeTorrent http://www.practicetorrent.com Latest study torrent with verified answers will facilitate your actual test Exam : 250-428 Title : Administration of Symantec Endpoint Protection 14 Vendor
Changing face of endpoint security
 Changing face of endpoint security S A N T H O S H S R I N I V A S A N C I S S P, C I S M, C R I S C, C E H, C I S A, G S L C, C G E I T D I R E C T O R S H A R E D S E R V I C E S, H C L T E C H N O L
Changing face of endpoint security S A N T H O S H S R I N I V A S A N C I S S P, C I S M, C R I S C, C E H, C I S A, G S L C, C G E I T D I R E C T O R S H A R E D S E R V I C E S, H C L T E C H N O L
Symantec Endpoint Protection Manager Delete Client Greyed Out
 Symantec Endpoint Protection Manager Delete Client Greyed Out Endpoint Protection (AntiVirus) Endpoint Protection Small Business Edition 12.x Endpoint Protection Small Business Edition Enterprise Security
Symantec Endpoint Protection Manager Delete Client Greyed Out Endpoint Protection (AntiVirus) Endpoint Protection Small Business Edition 12.x Endpoint Protection Small Business Edition Enterprise Security
: Administration of Symantec Endpoint Protection 14 Exam
 250-428: of Symantec Endpoint Protection 14 Exam Study Guide v. 2.2 Copyright 2017 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, and Altiris are trademarks or registered trademarks
250-428: of Symantec Endpoint Protection 14 Exam Study Guide v. 2.2 Copyright 2017 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, and Altiris are trademarks or registered trademarks
Seqrite Endpoint Security
 Enterprise Security Solutions by Quick Heal Integrated enterprise security and unified endpoint management console Enterprise Suite Edition Product Highlights Innovative endpoint security that prevents
Enterprise Security Solutions by Quick Heal Integrated enterprise security and unified endpoint management console Enterprise Suite Edition Product Highlights Innovative endpoint security that prevents
UP L13: Leveraging the full protection of SEP 12.1.x
 UP L13: Leveraging the full protection of SEP 12.1.x Hands on lab Description In this hands on lab you will learn about the different protection technologies bundled in SEP 12.1.x and see how they complement
UP L13: Leveraging the full protection of SEP 12.1.x Hands on lab Description In this hands on lab you will learn about the different protection technologies bundled in SEP 12.1.x and see how they complement
Symantec Endpoint Protection
 Overview provides unrivaled security across physical and virtual platforms and support for the latest operating systems-mac OS X 10.9 and Windows 8.1. Powered by Symantec Insight and by SONAR, a single,
Overview provides unrivaled security across physical and virtual platforms and support for the latest operating systems-mac OS X 10.9 and Windows 8.1. Powered by Symantec Insight and by SONAR, a single,
The SANS Institute Top 20 Critical Security Controls. Compliance Guide
 The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 The Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise
The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 The Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise
Symantec Antivirus Manual Removal Tool Corporate Edition 10.x
 Symantec Antivirus Manual Removal Tool Corporate Edition 10.x Learn how to download and run the Norton Removal Tool to uninstall the Norton products from your Looking for a free Virus and Spyware removal
Symantec Antivirus Manual Removal Tool Corporate Edition 10.x Learn how to download and run the Norton Removal Tool to uninstall the Norton products from your Looking for a free Virus and Spyware removal
How To Manually Uninstall Symantec Antivirus Corporate Edition 10.x Client
 How To Manually Uninstall Symantec Antivirus Corporate Edition 10.x Client Download Symantec Norton AntiVirus Definition Update (Upgrade/Patch). proactively block attacks and detect and remove threats
How To Manually Uninstall Symantec Antivirus Corporate Edition 10.x Client Download Symantec Norton AntiVirus Definition Update (Upgrade/Patch). proactively block attacks and detect and remove threats
Securing Your Environment with Dell Client Manager and Symantec Endpoint Protection
 Securing Your Environment with Dell Client Manager and Symantec Endpoint Protection Altiris, Now Part of Symantec Copyright 2007 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo,
Securing Your Environment with Dell Client Manager and Symantec Endpoint Protection Altiris, Now Part of Symantec Copyright 2007 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo,
Security+ SY0-501 Study Guide Table of Contents
 Security+ SY0-501 Study Guide Table of Contents Course Introduction Table of Contents About This Course About CompTIA Certifications Module 1 / Threats, Attacks, and Vulnerabilities Module 1 / Unit 1 Indicators
Security+ SY0-501 Study Guide Table of Contents Course Introduction Table of Contents About This Course About CompTIA Certifications Module 1 / Threats, Attacks, and Vulnerabilities Module 1 / Unit 1 Indicators
Defense-in-Depth Against Malicious Software. Speaker name Title Group Microsoft Corporation
 Defense-in-Depth Against Malicious Software Speaker name Title Group Microsoft Corporation Agenda Understanding the Characteristics of Malicious Software Malware Defense-in-Depth Malware Defense for Client
Defense-in-Depth Against Malicious Software Speaker name Title Group Microsoft Corporation Agenda Understanding the Characteristics of Malicious Software Malware Defense-in-Depth Malware Defense for Client
Symantec Endpoint Protection Family Feature Comparison
 Symantec Endpoint Protection Family Feature Comparison SEP SBE SEP Cloud SEP Cloud SEP 14.2 Device Protection Laptop, Laptop Laptop, Tablet Laptop Tablet & & Smartphone Smartphone Meter Per Device Per
Symantec Endpoint Protection Family Feature Comparison SEP SBE SEP Cloud SEP Cloud SEP 14.2 Device Protection Laptop, Laptop Laptop, Tablet Laptop Tablet & & Smartphone Smartphone Meter Per Device Per
August 30, 2018 UWW Wireless: Registering Windows Laptop to UWW Wireless Network for Staff
 August 30, 2018 UWW Wireless: Registering Windows Laptop to UWW Wireless Network for Staff OVERVIEW This guide will walk you through the steps to register your Windows computer to the UWW network, install
August 30, 2018 UWW Wireless: Registering Windows Laptop to UWW Wireless Network for Staff OVERVIEW This guide will walk you through the steps to register your Windows computer to the UWW network, install
CIH
 mitigating at host level, 23 25 at network level, 25 26 Morris worm, characteristics of, 18 Nimda worm, characteristics of, 20 22 replacement login, example of, 17 signatures. See signatures SQL Slammer
mitigating at host level, 23 25 at network level, 25 26 Morris worm, characteristics of, 18 Nimda worm, characteristics of, 20 22 replacement login, example of, 17 signatures. See signatures SQL Slammer
Comodo Endpoint Security Manager Professional Edition Software Version 3.5
 1 Comodo Endpoint Security Manager Professional Edition Software Version 3.5 Quick Start Guide Guide Version 3.5.030116 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Endpoint Security
1 Comodo Endpoint Security Manager Professional Edition Software Version 3.5 Quick Start Guide Guide Version 3.5.030116 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Endpoint Security
EMERGING THREATS & STRATEGIES FOR DEFENSE. Paul Fletcher Cyber Security
 EMERGING THREATS & STRATEGIES FOR DEFENSE Paul Fletcher Cyber Security Evangelist @_PaulFletcher Threats by Customer Environment Cloud Environment On Premise Environment 1.96% 0.13% 0.02% application-attack
EMERGING THREATS & STRATEGIES FOR DEFENSE Paul Fletcher Cyber Security Evangelist @_PaulFletcher Threats by Customer Environment Cloud Environment On Premise Environment 1.96% 0.13% 0.02% application-attack
Comodo Endpoint Security Manager Professional Edition Software Version 3.3
 Comodo Endpoint Security Manager Professional Edition Software Version 3.3 Quick Start Guide Guide Version 3.2.022615 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Endpoint Security
Comodo Endpoint Security Manager Professional Edition Software Version 3.3 Quick Start Guide Guide Version 3.2.022615 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Endpoint Security
BeOn Security Cybersecurity for Critical Communications Systems
 WHITEPAPER BeOn Security Cybersecurity for Critical Communications Systems Peter Monnes System Design Engineer Harris Corporation harris.com #harriscorp TABLE OF CONTENTS BeOn Security... 3 Summary...
WHITEPAPER BeOn Security Cybersecurity for Critical Communications Systems Peter Monnes System Design Engineer Harris Corporation harris.com #harriscorp TABLE OF CONTENTS BeOn Security... 3 Summary...
CompTIA A+ Accelerated course for & exams
 CompTIA A+ Accelerated course for 220-901 & 220-902 exams Course overview Target Audience This course is for Participants wishing to take and pass both CompTIA A+ exams (220-901 and 220-902) exam. It is
CompTIA A+ Accelerated course for 220-901 & 220-902 exams Course overview Target Audience This course is for Participants wishing to take and pass both CompTIA A+ exams (220-901 and 220-902) exam. It is
Even a non-technical user can even operate it with ease.the user can do any task in CCS with just a few clicks.
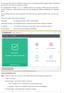 The Comodo Client Security identifies all security risks and provides protection against it.now, the interface of the Comodo Client Security is made very simple. It is integrated with Firewall, Antivirus,
The Comodo Client Security identifies all security risks and provides protection against it.now, the interface of the Comodo Client Security is made very simple. It is integrated with Firewall, Antivirus,
Delivering Integrated Cyber Defense for the Cloud Generation Darren Thomson
 Delivering Integrated Cyber Defense for the Generation Darren Thomson Vice President & CTO, EMEA Region Symantec In 2009 there were 2,361,414 new piece of malware created. In 2015 that number was 430,555,582
Delivering Integrated Cyber Defense for the Generation Darren Thomson Vice President & CTO, EMEA Region Symantec In 2009 there were 2,361,414 new piece of malware created. In 2015 that number was 430,555,582
1 Page Compass Investors, LLC P.O. Box 94 Kenilworth, IL
 Updating a Local Firewall for Proper Site Access These steps are needed to allow proper functioning of and access to the subscriber areas of the Compass Investors website. These instructions include several
Updating a Local Firewall for Proper Site Access These steps are needed to allow proper functioning of and access to the subscriber areas of the Compass Investors website. These instructions include several
USM Anywhere AlienApps Guide
 USM Anywhere AlienApps Guide Updated April 23, 2018 Copyright 2018 AlienVault. All rights reserved. AlienVault, AlienApp, AlienApps, AlienVault OSSIM, Open Threat Exchange, OTX, Unified Security Management,
USM Anywhere AlienApps Guide Updated April 23, 2018 Copyright 2018 AlienVault. All rights reserved. AlienVault, AlienApp, AlienApps, AlienVault OSSIM, Open Threat Exchange, OTX, Unified Security Management,
CompTIA A+ Certification ( ) Study Guide Table of Contents
 CompTIA A+ Certification (220-902) Study Guide Table of Contents Course Introduction About This Course About CompTIA Certifications Module 1 / Supporting Windows 1 Module 1 / Unit 1 Windows Operating System
CompTIA A+ Certification (220-902) Study Guide Table of Contents Course Introduction About This Course About CompTIA Certifications Module 1 / Supporting Windows 1 Module 1 / Unit 1 Windows Operating System
SandBlast Agent FAQ Check Point Software Technologies Ltd. All rights reserved P. 1. [Internal Use] for Check Point employees
![SandBlast Agent FAQ Check Point Software Technologies Ltd. All rights reserved P. 1. [Internal Use] for Check Point employees SandBlast Agent FAQ Check Point Software Technologies Ltd. All rights reserved P. 1. [Internal Use] for Check Point employees](/thumbs/84/90671868.jpg) SandBlast Agent FAQ What is Check Point SandBlast Agent? Check Point SandBlast Agent defends endpoints and web browsers with a complete set of realtime advanced browser and endpoint protection technologies,
SandBlast Agent FAQ What is Check Point SandBlast Agent? Check Point SandBlast Agent defends endpoints and web browsers with a complete set of realtime advanced browser and endpoint protection technologies,
Symantec Endpoint Protection 14
 Symantec Endpoint Protection Cloud Security Made Simple Symantec Endpoint Protection 14 Data Data Sheet: Sheet: Endpoint Endpoint Security Security Overview Last year, we saw 431 million new malware variants,
Symantec Endpoint Protection Cloud Security Made Simple Symantec Endpoint Protection 14 Data Data Sheet: Sheet: Endpoint Endpoint Security Security Overview Last year, we saw 431 million new malware variants,
Manual Removal Norton Internet Security Won't Open Or
 Manual Removal Norton Internet Security Won't Open Or Dec 3, 2014. Finally during the reinstall - I had to delete a key to get a new key other wise I would I have it shown on the prgrams and features -
Manual Removal Norton Internet Security Won't Open Or Dec 3, 2014. Finally during the reinstall - I had to delete a key to get a new key other wise I would I have it shown on the prgrams and features -
STIX/TAXII feed processing
 Detecting network intruders with STIX/TAXII feed processing A Guide www.manageengine.com/products/eventlog/ Introduction In today's evolving threat landscape, the key to efficient threat mitigation is
Detecting network intruders with STIX/TAXII feed processing A Guide www.manageengine.com/products/eventlog/ Introduction In today's evolving threat landscape, the key to efficient threat mitigation is
KASPERSKY ENDPOINT SECURITY FOR BUSINESS
 KASPERSKY ENDPOINT SECURITY FOR BUSINESS 1 WHAT WE SEE TODAY 325,000 New Endpoint Threats per day Targeted attacks and malware campaigns Threat reports Continued Exploitation of Vulnerabilities in 3rd
KASPERSKY ENDPOINT SECURITY FOR BUSINESS 1 WHAT WE SEE TODAY 325,000 New Endpoint Threats per day Targeted attacks and malware campaigns Threat reports Continued Exploitation of Vulnerabilities in 3rd
Symantec Endpoint Protection Small Business Edition (cloud-managed) Administrator's Guide
 Symantec Endpoint Protection Small Business Edition (cloud-managed) Administrator's Guide Symantec Endpoint Protection Small Business Edition (cloud-managed) Administrator's Guide Documentation version:
Symantec Endpoint Protection Small Business Edition (cloud-managed) Administrator's Guide Symantec Endpoint Protection Small Business Edition (cloud-managed) Administrator's Guide Documentation version:
Security. Official. Company Profile
 Security Official Company Profile 2018 About M&M Security M&M was founded in 2013 in Jordan. It is created specifically to address the IT needs for all sectors in the region. It combines the latest technologies
Security Official Company Profile 2018 About M&M Security M&M was founded in 2013 in Jordan. It is created specifically to address the IT needs for all sectors in the region. It combines the latest technologies
Manually Uninstall Symantec Endpoint Protection Client
 Manually Uninstall Symantec Endpoint Protection 12.1 2 Client 2- How to delete the logs for risk,tamp. This document describes how to remove the Symantec Endpoint Protection 12.1 client from Windows Vista,
Manually Uninstall Symantec Endpoint Protection 12.1 2 Client 2- How to delete the logs for risk,tamp. This document describes how to remove the Symantec Endpoint Protection 12.1 client from Windows Vista,
Symantec Multi-tier Protection
 Trusted protection from malware and email-bourne threats for multiplatform environments Overview Symantec Multi-tier Protection is designed to safeguard enterprise assets and lower risk by providing unmatched
Trusted protection from malware and email-bourne threats for multiplatform environments Overview Symantec Multi-tier Protection is designed to safeguard enterprise assets and lower risk by providing unmatched
Symantec and VMWare why 1+1 makes 3
 Symantec and VMWare why 1+1 makes 3 Finn Henningsen Principal Systems Engineer Peter Schjøtt Principal Systems Engineer Rasmus Rask Eilersen Principal Systems Engineer Symantec and VMWare 1 Tak til vores
Symantec and VMWare why 1+1 makes 3 Finn Henningsen Principal Systems Engineer Peter Schjøtt Principal Systems Engineer Rasmus Rask Eilersen Principal Systems Engineer Symantec and VMWare 1 Tak til vores
How To Uninstall Symantec Endpoint Protection 12.1 Client From Windows 7
 How To Uninstall Symantec Endpoint Protection 12.1 Client From Windows 7 This document describes how to remove the Symantec Endpoint Protection 12.1 client from Windows Vista, Windows 7, and Windows 2008
How To Uninstall Symantec Endpoint Protection 12.1 Client From Windows 7 This document describes how to remove the Symantec Endpoint Protection 12.1 client from Windows Vista, Windows 7, and Windows 2008
McAfee Public Cloud Server Security Suite
 McAfee Public Cloud Server Security Suite Comprehensive security for AWS and Azure cloud workloads As enterprises shift their data center strategy to include and often lead with public cloud server instances,
McAfee Public Cloud Server Security Suite Comprehensive security for AWS and Azure cloud workloads As enterprises shift their data center strategy to include and often lead with public cloud server instances,
align security instill confidence
 align security instill confidence cyber security Securing data has become a top priority across all industries. High-profile data breaches and the proliferation of advanced persistent threats have changed
align security instill confidence cyber security Securing data has become a top priority across all industries. High-profile data breaches and the proliferation of advanced persistent threats have changed
Security Automation. Challenge: Automatizzare le azioni di isolamento e contenimento delle minacce rilevate tramite soluzioni di malware analysis
 Security Automation Challenge: Automatizzare le azioni di isolamento e contenimento delle minacce rilevate tramite soluzioni di malware analysis Network Admission Control See Managed Unmanaged Computing
Security Automation Challenge: Automatizzare le azioni di isolamento e contenimento delle minacce rilevate tramite soluzioni di malware analysis Network Admission Control See Managed Unmanaged Computing
Uninstall Mcafee Agent Cannot Be Removed
 Uninstall Mcafee Agent Cannot Be Removed Because Other Products Are Still Using It We haven't come across this in other customers until now. Using add/remove programs doesn't work, as the uninstall process
Uninstall Mcafee Agent Cannot Be Removed Because Other Products Are Still Using It We haven't come across this in other customers until now. Using add/remove programs doesn't work, as the uninstall process
NGFW Security Management Center
 NGFW Security Management Center Release Notes 6.4.3 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5
NGFW Security Management Center Release Notes 6.4.3 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5
ANATOMY OF AN ATTACK!
 ANATOMY OF AN ATTACK! Are Your Crown Jewels Safe? Dom Kapac, Security Evangelist WHAT DO WE MEAN BY CROWN JEWELS? Crown jewels for most organizations are critical infrastructure and data Data is a valuable
ANATOMY OF AN ATTACK! Are Your Crown Jewels Safe? Dom Kapac, Security Evangelist WHAT DO WE MEAN BY CROWN JEWELS? Crown jewels for most organizations are critical infrastructure and data Data is a valuable
ForeScout Extended Module for Symantec Endpoint Protection
 ForeScout Extended Module for Symantec Endpoint Protection Version 1.0.0 Table of Contents About the Symantec Endpoint Protection Integration... 4 Use Cases... 4 Additional Symantec Endpoint Protection
ForeScout Extended Module for Symantec Endpoint Protection Version 1.0.0 Table of Contents About the Symantec Endpoint Protection Integration... 4 Use Cases... 4 Additional Symantec Endpoint Protection
Cyber Security Awareness for SmallSat Ground Networks
 Cyber Security Awareness for SmallSat Ground Networks SSC16-IX-02 SmallSat 2016 Ted Vera Colorado Springs, CO (719) 598-2801 Denver, CO (303) 703-3834 Chantilly, VA (703) 488-2500 http://www.rtlogic.com
Cyber Security Awareness for SmallSat Ground Networks SSC16-IX-02 SmallSat 2016 Ted Vera Colorado Springs, CO (719) 598-2801 Denver, CO (303) 703-3834 Chantilly, VA (703) 488-2500 http://www.rtlogic.com
Symantec Endpoint Protection, Symantec Endpoint Protection Small Business Edition, and Symantec Network Access Control 12.1.
 Symantec Endpoint Protection, Symantec Endpoint Protection Small Business Edition, and Symantec Network Access Control 12.1.3 Release Notes Symantec Endpoint Protection, Symantec Endpoint Protection Small
Symantec Endpoint Protection, Symantec Endpoint Protection Small Business Edition, and Symantec Network Access Control 12.1.3 Release Notes Symantec Endpoint Protection, Symantec Endpoint Protection Small
The Eight Components of a Strong Cyber Security Defense System
 The Eight Components of a Strong Cyber Security Defense System SEG Secure Email Gateway An appliance that provides anti-spam and anti-malware protection. It is installed on top of a corporation s Email
The Eight Components of a Strong Cyber Security Defense System SEG Secure Email Gateway An appliance that provides anti-spam and anti-malware protection. It is installed on top of a corporation s Email
WHITE PAPER: BEST PRACTICES. Sizing and Scalability Recommendations for Symantec Endpoint Protection. Symantec Enterprise Security Solutions Group
 WHITE PAPER: BEST PRACTICES Sizing and Scalability Recommendations for Symantec Rev 2.2 Symantec Enterprise Security Solutions Group White Paper: Symantec Best Practices Contents Introduction... 4 The
WHITE PAPER: BEST PRACTICES Sizing and Scalability Recommendations for Symantec Rev 2.2 Symantec Enterprise Security Solutions Group White Paper: Symantec Best Practices Contents Introduction... 4 The
Security Assessment Checklist
 Security Assessment Checklist Westcon Security Checklist - Instructions The first step to protecting your business includes a careful and complete assessment of your security posture. Our Security Assessment
Security Assessment Checklist Westcon Security Checklist - Instructions The first step to protecting your business includes a careful and complete assessment of your security posture. Our Security Assessment
Agile Security Solutions
 Agile Security Solutions Piotr Linke Security Engineer CISSP CISA CRISC CISM Open Source SNORT 2 Consider these guys All were smart. All had security. All were seriously compromised. 3 The Industrialization
Agile Security Solutions Piotr Linke Security Engineer CISSP CISA CRISC CISM Open Source SNORT 2 Consider these guys All were smart. All had security. All were seriously compromised. 3 The Industrialization
How to Configure Anti-Virus to Permit SoftMiner Binaries
 How to Configure Anti-Virus to Permit Binaries If you trust a file, file type, folder, or a process that anti-virus has detected as malicious, you can stop anti-virus from alerting you or blocking the
How to Configure Anti-Virus to Permit Binaries If you trust a file, file type, folder, or a process that anti-virus has detected as malicious, you can stop anti-virus from alerting you or blocking the
How To Remove Security Shield 2012 Virus Manually
 How To Remove Security Shield 2012 Virus Manually Fake virus warnings that will actually infect your machine. If your computer isn't running Windows 8, download Microsoft Security Essentials for free.
How To Remove Security Shield 2012 Virus Manually Fake virus warnings that will actually infect your machine. If your computer isn't running Windows 8, download Microsoft Security Essentials for free.
MIS Week 6. Operating System Security. Windows Antivirus
 MIS 5170 Operating System Security Week 6 Windows Antivirus Tonight s Plan 2 Questions from Last Week Review on-line posts In The News Malware/Spyware Detection tools Antivirus Sniffers Assignment 3 Overview
MIS 5170 Operating System Security Week 6 Windows Antivirus Tonight s Plan 2 Questions from Last Week Review on-line posts In The News Malware/Spyware Detection tools Antivirus Sniffers Assignment 3 Overview
Dynamic Datacenter Security Solidex, November 2009
 Dynamic Datacenter Security Solidex, November 2009 Deep Security: Securing the New Server Cloud Virtualized Physical Servers in the open Servers virtual and in motion Servers under attack 2 11/9/09 2 Dynamic
Dynamic Datacenter Security Solidex, November 2009 Deep Security: Securing the New Server Cloud Virtualized Physical Servers in the open Servers virtual and in motion Servers under attack 2 11/9/09 2 Dynamic
CIS Controls Measures and Metrics for Version 7
 Level One Level Two Level Three Level Four Level Five Level Six 1.1 Utilize an Active Discovery Tool Utilize an active discovery tool to identify devices connected to the organization's network and update
Level One Level Two Level Three Level Four Level Five Level Six 1.1 Utilize an Active Discovery Tool Utilize an active discovery tool to identify devices connected to the organization's network and update
SOLUTION OVERVIEW. Enterprise-grade security management solution providing visibility, management and reporting across all OSes.
 SOLUTION OVERVIEW Enterprise-grade security management solution providing visibility, management and reporting across all OSes. What is an endpoint security management console? ESET Security Management
SOLUTION OVERVIEW Enterprise-grade security management solution providing visibility, management and reporting across all OSes. What is an endpoint security management console? ESET Security Management
McAfee Virtual Network Security Platform 8.4 Revision A
 8.4.7.101-8.3.7.18 Manager-Virtual IPS Release Notes McAfee Virtual Network Security Platform 8.4 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions
8.4.7.101-8.3.7.18 Manager-Virtual IPS Release Notes McAfee Virtual Network Security Platform 8.4 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions
Course overview. CompTIA Security+ Certification (Exam SY0-501) Study Guide (G635eng v107)
 Overview This course is intended for those wishing to qualify with CompTIA Security+. CompTIA's Security+ Certification is a foundation-level certificate designed for IT administrators with 2 years' experience
Overview This course is intended for those wishing to qualify with CompTIA Security+. CompTIA's Security+ Certification is a foundation-level certificate designed for IT administrators with 2 years' experience
ForeScout ControlFabric TM Architecture
 ForeScout ControlFabric TM Architecture IMPROVE MULTI-VENDOR SOLUTION EFFECTIVENESS, RESPONSE AND WORKFLOW AUTOMATION THROUGH COLLABORATION WITH INDUSTRY-LEADING TECHNOLOGY PARTNERS. The Challenge 50%
ForeScout ControlFabric TM Architecture IMPROVE MULTI-VENDOR SOLUTION EFFECTIVENESS, RESPONSE AND WORKFLOW AUTOMATION THROUGH COLLABORATION WITH INDUSTRY-LEADING TECHNOLOGY PARTNERS. The Challenge 50%
Securing the Empowered Branch with Cisco Network Admission Control. September 2007
 Securing the Empowered Branch with Cisco Network Admission Control September 2007 Presentation_ID 2006 Cisco Systems, Inc. All rights reserved. 1 Contents 1 The Cisco Empowered Branch 2 Security Considerations
Securing the Empowered Branch with Cisco Network Admission Control September 2007 Presentation_ID 2006 Cisco Systems, Inc. All rights reserved. 1 Contents 1 The Cisco Empowered Branch 2 Security Considerations
Veriato Recon / 360. Version 9.0.3
 Veriato Recon / 360 Version 9.0.3 1/3/2018 Upgrade Guide January 3, 2018 Table of Contents Before You Begin... 1 What's New... 1 How the System Works... 1 Upgrade Support... 6 Update Antivirus Exclusions...
Veriato Recon / 360 Version 9.0.3 1/3/2018 Upgrade Guide January 3, 2018 Table of Contents Before You Begin... 1 What's New... 1 How the System Works... 1 Upgrade Support... 6 Update Antivirus Exclusions...
CIS Controls Measures and Metrics for Version 7
 Level 1.1 Utilize an Active Discovery Tool 1.2 Use a Passive Asset Discovery Tool 1.3 Use DHCP Logging to Update Asset Inventory 1.4 Maintain Detailed Asset Inventory 1.5 Maintain Asset Inventory Information
Level 1.1 Utilize an Active Discovery Tool 1.2 Use a Passive Asset Discovery Tool 1.3 Use DHCP Logging to Update Asset Inventory 1.4 Maintain Detailed Asset Inventory 1.5 Maintain Asset Inventory Information
Mcafee Endpoint Protection For Mac Software Failed To Launch Error Code 1
 Mcafee Endpoint Protection For Mac Software Failed To Launch Error Code 1 The McAfee Endpoint Protection for Mac software failed to launch in McAfee epo when disabling FileVault is failed as Error the
Mcafee Endpoint Protection For Mac Software Failed To Launch Error Code 1 The McAfee Endpoint Protection for Mac software failed to launch in McAfee epo when disabling FileVault is failed as Error the
Comodo Internet Security Software Version 11.0
 Comodo Internet Security Software Version 11.0 Installation Guide Guide Version 11.0.080918 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States 1. CIS Installation Please read
Comodo Internet Security Software Version 11.0 Installation Guide Guide Version 11.0.080918 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States 1. CIS Installation Please read
Enterprise Cybersecurity Best Practices Part Number MAN Revision 006
 Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006 April 2013 Hologic and the Hologic Logo are trademarks or registered trademarks of Hologic, Inc. Microsoft, Active Directory,
Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006 April 2013 Hologic and the Hologic Logo are trademarks or registered trademarks of Hologic, Inc. Microsoft, Active Directory,
Cisco Network Admission Control (NAC) Solution
 Data Sheet Cisco Network Admission Control (NAC) Solution New: Updated to include the Cisco Secure Network Server (SNS) Cisco Network Admission Control (NAC) solutions allow you to authenticate wired,
Data Sheet Cisco Network Admission Control (NAC) Solution New: Updated to include the Cisco Secure Network Server (SNS) Cisco Network Admission Control (NAC) solutions allow you to authenticate wired,
Data Retrieval Firm Boosts Productivity while Protecting Customer Data
 Data Retrieval Firm Boosts Productivity while Protecting Customer Data With HEIT Consulting, DriveSavers deployed a Cisco Self-Defending Network to better protect network assets, employee endpoints, and
Data Retrieval Firm Boosts Productivity while Protecting Customer Data With HEIT Consulting, DriveSavers deployed a Cisco Self-Defending Network to better protect network assets, employee endpoints, and
How To Remove Xp Internet Security 2011 Virus Manually
 How To Remove Xp Internet Security 2011 Virus Manually Contact your anti-malware vendor for assistance with identifying or removing virus or worm infections. If you need more help with malware removal
How To Remove Xp Internet Security 2011 Virus Manually Contact your anti-malware vendor for assistance with identifying or removing virus or worm infections. If you need more help with malware removal
Symantec Endpoint Protection 12
 Symantec Endpoint Protection 12 Hundreds of Millions of New Pieces of Malware Mean You Have to Do Things Differently Graham Ahearne, Marcus Brownell Product Management 1 Agenda 1 2 3 Challenges How Symantec
Symantec Endpoint Protection 12 Hundreds of Millions of New Pieces of Malware Mean You Have to Do Things Differently Graham Ahearne, Marcus Brownell Product Management 1 Agenda 1 2 3 Challenges How Symantec
McAfee Network Security Platform 8.3
 8.3.7.44-8.3.7.14 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions Known
8.3.7.44-8.3.7.14 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions Known
Benefits. Centrally managed protection of corporate networks
 Defend what you create Centrally managed protection of corporate networks Benefits Centrally managed protection of Windows workstations, Windows file servers and Unix mail servers High scalability Grouping
Defend what you create Centrally managed protection of corporate networks Benefits Centrally managed protection of Windows workstations, Windows file servers and Unix mail servers High scalability Grouping
AppDefense Cb Defense Configuration Guide. AppDefense Appendix Cb Defense Integration Configuration Guide
 AppDefense Appendix Cb Defense Integration Configuration Guide Table of Contents Overview 3 Requirements 3 Provision API Key for Cb Defense Integration 3 Figure 1 Integration Type 4 Figure 2 API Key Provisioning
AppDefense Appendix Cb Defense Integration Configuration Guide Table of Contents Overview 3 Requirements 3 Provision API Key for Cb Defense Integration 3 Figure 1 Integration Type 4 Figure 2 API Key Provisioning
Copyright 2011 Trend Micro Inc.
 Copyright 2011 Trend Micro Inc. 2008Q1 2008Q2 2008Q3 2008Q4 2009Q1 2009Q2 2009Q3 2009Q4 2010Q1 2010Q2 2010Q3 2010Q4 2011Q1 2011Q2 2011Q3 2011Q4 M'JPY Cloud Security revenue Q to Q Growth DeepSecurity/Hosted/CPVM/IDF
Copyright 2011 Trend Micro Inc. 2008Q1 2008Q2 2008Q3 2008Q4 2009Q1 2009Q2 2009Q3 2009Q4 2010Q1 2010Q2 2010Q3 2010Q4 2011Q1 2011Q2 2011Q3 2011Q4 M'JPY Cloud Security revenue Q to Q Growth DeepSecurity/Hosted/CPVM/IDF
MIS Week 6. Operating System Security. Windows Antivirus
 MIS 5170 Operating System Security Week 6 Windows Antivirus Tonight s Plan 2 Questions from Last Week Review on-line posts In The News Malware/Spyware Detection tools Antivirus Sniffers Assignment 3 Overview
MIS 5170 Operating System Security Week 6 Windows Antivirus Tonight s Plan 2 Questions from Last Week Review on-line posts In The News Malware/Spyware Detection tools Antivirus Sniffers Assignment 3 Overview
IBM Threat Protection System: XGS - QRadar Integration
 IBM Security Network Protection Support Open Mic - Wednesday, 25 May 2016 IBM Threat Protection System: XGS - QRadar Integration Panelists Tanmay Shah - Presenter Level 2 Support Product Lead Danitza Villaran-Rokovich,
IBM Security Network Protection Support Open Mic - Wednesday, 25 May 2016 IBM Threat Protection System: XGS - QRadar Integration Panelists Tanmay Shah - Presenter Level 2 Support Product Lead Danitza Villaran-Rokovich,
Symantec Protection Suite Add-On for Hosted Security
 Symantec Protection Suite Add-On for Hosted Email Security Overview Malware and spam pose enormous risk to the health and viability of IT networks. Cyber criminal attacks are focused on stealing money
Symantec Protection Suite Add-On for Hosted Email Security Overview Malware and spam pose enormous risk to the health and viability of IT networks. Cyber criminal attacks are focused on stealing money
Zero Trust with Okta: A Modern Approach to Secure Access from Anywhere. How Okta enables a Zero Trust solution for our customers
 Zero Trust with Okta: A Modern Approach to Secure Access from Anywhere How Okta enables a Zero Trust solution for our customers Okta Inc. 301 Brannan Street, Suite 300 San Francisco, CA 94107 info@okta.com
Zero Trust with Okta: A Modern Approach to Secure Access from Anywhere How Okta enables a Zero Trust solution for our customers Okta Inc. 301 Brannan Street, Suite 300 San Francisco, CA 94107 info@okta.com
Zemana Endpoint Security Administration Guide. Version
 Zemana Endpoint Security Administration Guide Version 1.9.290 Introduction 4 What is Zemana Endpoint Security? 4 What is Zemana Control Center? 4 How do Endpoint Agents and Control Center communicate with
Zemana Endpoint Security Administration Guide Version 1.9.290 Introduction 4 What is Zemana Endpoint Security? 4 What is Zemana Control Center? 4 How do Endpoint Agents and Control Center communicate with
Securing Enterprise Network
 Securing Enterprise Network Indian Computer Emergency Response Team Department of Information Technology Ministry of Communications & Information Technology New Delhi Expansion in Enterprise networks Network
Securing Enterprise Network Indian Computer Emergency Response Team Department of Information Technology Ministry of Communications & Information Technology New Delhi Expansion in Enterprise networks Network
Integrating IBM Security Privileged Identity Manager with ObserveIT Enterprise Session Recording
 Integrating IBM Security Privileged Identity Manager with ObserveIT Enterprise Session Recording Contents 1 About This Document... 2 2 Overview... 2 3 Before You Begin... 2 4 Deploying ObserveIT with IBM
Integrating IBM Security Privileged Identity Manager with ObserveIT Enterprise Session Recording Contents 1 About This Document... 2 2 Overview... 2 3 Before You Begin... 2 4 Deploying ObserveIT with IBM
Carbon Black PCI Compliance Mapping Checklist
 Carbon Black PCI Compliance Mapping Checklist The following table identifies selected PCI 3.0 requirements, the test definition per the PCI validation plan and how Carbon Black Enterprise Protection and
Carbon Black PCI Compliance Mapping Checklist The following table identifies selected PCI 3.0 requirements, the test definition per the PCI validation plan and how Carbon Black Enterprise Protection and
Symantec Exam ST0-134 Symantec EndPoint Protection 12.1 Technical Assessment Version: 8.0 [ Total Questions: 282 ]
![Symantec Exam ST0-134 Symantec EndPoint Protection 12.1 Technical Assessment Version: 8.0 [ Total Questions: 282 ] Symantec Exam ST0-134 Symantec EndPoint Protection 12.1 Technical Assessment Version: 8.0 [ Total Questions: 282 ]](/thumbs/95/126327452.jpg) s@lm@n Symantec Exam ST0-134 Symantec EndPoint Protection 12.1 Technical Assessment Version: 8.0 [ Total Questions: 282 ] Topic 1, Volume A Question No : 1 - (Topic 1) A financial company enforces a security
s@lm@n Symantec Exam ST0-134 Symantec EndPoint Protection 12.1 Technical Assessment Version: 8.0 [ Total Questions: 282 ] Topic 1, Volume A Question No : 1 - (Topic 1) A financial company enforces a security
McAfee epolicy Orchestrator
 McAfee epolicy Orchestrator Centrally get, visualize, share, and act on security insights Security management requires cumbersome juggling between tools and data. This puts the adversary at an advantage
McAfee epolicy Orchestrator Centrally get, visualize, share, and act on security insights Security management requires cumbersome juggling between tools and data. This puts the adversary at an advantage
Prevx 3.0 v Product Overview - Core Functionality. April, includes overviews of. MyPrevx, Prevx 3.0 Enterprise,
 Prevx 3.0 v3.0.1.65 Product Overview - Core Functionality April, 2009 includes overviews of MyPrevx, Prevx 3.0 Enterprise, and Prevx 3.0 Banking and Ecommerce editions Copyright Prevx Limited 2007,2008,2009
Prevx 3.0 v3.0.1.65 Product Overview - Core Functionality April, 2009 includes overviews of MyPrevx, Prevx 3.0 Enterprise, and Prevx 3.0 Banking and Ecommerce editions Copyright Prevx Limited 2007,2008,2009
Getting Started Guide. This document provides step-by-step instructions for installing Max Secure Anti-Virus and its prerequisite software.
 Getting Started Guide This document provides step-by-step instructions for installing Max Secure Anti-Virus and its prerequisite software. Contents 2 Contents Introduction... 3 System Requirements... 4
Getting Started Guide This document provides step-by-step instructions for installing Max Secure Anti-Virus and its prerequisite software. Contents 2 Contents Introduction... 3 System Requirements... 4
Trend Micro Deep Security
 Trend Micro Deep Security Endpoint Security Similarities and Differences with Cisco CSA A Trend Micro White Paper May 2010 I. INTRODUCTION Your enterprise invested in Cisco Security Agent (CSA) because
Trend Micro Deep Security Endpoint Security Similarities and Differences with Cisco CSA A Trend Micro White Paper May 2010 I. INTRODUCTION Your enterprise invested in Cisco Security Agent (CSA) because
ForeScout Extended Module for Carbon Black
 ForeScout Extended Module for Carbon Black Version 1.0 Table of Contents About the Carbon Black Integration... 4 Advanced Threat Detection with the IOC Scanner Plugin... 4 Use Cases... 5 Carbon Black Agent
ForeScout Extended Module for Carbon Black Version 1.0 Table of Contents About the Carbon Black Integration... 4 Advanced Threat Detection with the IOC Scanner Plugin... 4 Use Cases... 5 Carbon Black Agent
Symantec Endpoint Protection Will Not Uninstall Windows 7 64 Bit
 Symantec Endpoint Protection Will Not Uninstall Windows 7 64 Bit Third-party security software removal support in Symantec Endpoint Protection. Windows 7 (32-bit, 64-bit, RTM and SP1, all editions except
Symantec Endpoint Protection Will Not Uninstall Windows 7 64 Bit Third-party security software removal support in Symantec Endpoint Protection. Windows 7 (32-bit, 64-bit, RTM and SP1, all editions except
Traditional Security Solutions Have Reached Their Limit
 Traditional Security Solutions Have Reached Their Limit CHALLENGE #1 They are reactive They force you to deal only with symptoms, rather than root causes. CHALLENGE #2 256 DAYS TO IDENTIFY A BREACH TRADITIONAL
Traditional Security Solutions Have Reached Their Limit CHALLENGE #1 They are reactive They force you to deal only with symptoms, rather than root causes. CHALLENGE #2 256 DAYS TO IDENTIFY A BREACH TRADITIONAL
Integrate Sophos Enterprise Console. EventTracker v8.x and above
 Integrate Sophos Enterprise Console EventTracker v8.x and above Publication Date: September 22, 2017 Abstract This guide provides instructions to configure Sophos Enterprise Console to send the events
Integrate Sophos Enterprise Console EventTracker v8.x and above Publication Date: September 22, 2017 Abstract This guide provides instructions to configure Sophos Enterprise Console to send the events
Integrate Microsoft Antimalware. EventTracker v8.x and above
 Integrate Microsoft Antimalware EventTracker v8.x and above Publication Date: September 6, 2017 Abstract This guide provides instructions to configure Microsoft Antimalware to send logs to EventTracker
Integrate Microsoft Antimalware EventTracker v8.x and above Publication Date: September 6, 2017 Abstract This guide provides instructions to configure Microsoft Antimalware to send logs to EventTracker
Remove Manually Norton Internet Security 2012 Will Not Start
 Remove Manually Norton Internet Security 2012 Will Not Start Restart your computer to check if you can start your Norton product. I cannot connect to the Internet My Norton product does not work or displays
Remove Manually Norton Internet Security 2012 Will Not Start Restart your computer to check if you can start your Norton product. I cannot connect to the Internet My Norton product does not work or displays
Microsoft Security Management
 Microsoft Security Management MICROSOFT SECURITY MANAGEMENT SECURITY MANAGEMENT CHALLENGES Some large financial services organizations have as many as 40 or more different security vendors inside their
Microsoft Security Management MICROSOFT SECURITY MANAGEMENT SECURITY MANAGEMENT CHALLENGES Some large financial services organizations have as many as 40 or more different security vendors inside their
Mcafee Network Intrusion Detection System. Project Report >>>CLICK HERE<<<
 Mcafee Network Intrusion Detection System Project Report Selecting an intrusion detection and prevention system vendor can be a IDS/IPS protection, the current network configuration and the project budget,
Mcafee Network Intrusion Detection System Project Report Selecting an intrusion detection and prevention system vendor can be a IDS/IPS protection, the current network configuration and the project budget,
SOLUTION OVERVIEW. Manage your network security for up to 250 seats from a single cloud-based console
 SOLUTION OVERVIEW Manage your network security for up to 250 seats from a single cloud-based console 2 With ESET Cloud Administrator, you can manage your company network security without the need to buy,
SOLUTION OVERVIEW Manage your network security for up to 250 seats from a single cloud-based console 2 With ESET Cloud Administrator, you can manage your company network security without the need to buy,
ESET NOD32 Antivirus 4. Product Briefing
 ESET NOD32 Antivirus 4 Product Briefing Company Profile Global security software company, est. 1992 Headquarters in Bratislava, Slovakia Offices in San Diego, Prague, Buenos Aires, and Krakow Servicing
ESET NOD32 Antivirus 4 Product Briefing Company Profile Global security software company, est. 1992 Headquarters in Bratislava, Slovakia Offices in San Diego, Prague, Buenos Aires, and Krakow Servicing
Remove Windows Service Manually Command Line Scheduler
 Remove Windows Service Manually Command Line Scheduler Every time I start my computer a command prompt and window will pop up saying You need to manually remove the entry in your registry for RocketTab.
Remove Windows Service Manually Command Line Scheduler Every time I start my computer a command prompt and window will pop up saying You need to manually remove the entry in your registry for RocketTab.
Securing the Modern Data Center with Trend Micro Deep Security
 Advania Fall Conference Securing the Modern Data Center with Trend Micro Deep Security Okan Kalak, Senior Sales Engineer okan@trendmicro.no Infrastructure change Containers 1011 0100 0010 Serverless Public
Advania Fall Conference Securing the Modern Data Center with Trend Micro Deep Security Okan Kalak, Senior Sales Engineer okan@trendmicro.no Infrastructure change Containers 1011 0100 0010 Serverless Public
