Game Industry Characteristics
|
|
|
- Abraham Simmons
- 5 years ago
- Views:
Transcription
1 Game Industry Characteristics CODE DEVELOPMENT LANGUAGES PACKAGES DATA TEAM USERS C/C++ Rendering 3D Models Game Concept Designers Anyone Java Python Physics AI Surface Bitmaps AI Scripts Software Engineers Artists & Modellers Proprietary Database Player Statistics Controller Input Sound Animation Sequences Sound Effects
2 Typical Collaboration for Client Architecture MAIN SCRIPTS STATE STANDARD C/C++ CODE PACKAGES COMMUNICATION PACKAGE PROCESS BOUNDARY
3 Alternative Collaboration Using CORBA Architecture MAIN Java or Scripts w/ Standard Language Mapping Interoperable CORBA Servants Standard C/C++ Code Packages STATE PROCESS BOUNDARY
4 Developer Prototyping Process 1. Start by running multiplayer sample code. 2. Examine UML and extend samples. 3. Generate code for customized samples. 4. Examine critical metrics with diagnostic tools. 5. Round-trip engineering iterations refine code.
5 The Ninja Networking Developer Acceleration Kit streamlines the process of designing CORBA servants. Automated tools support roundtrip engineering, taking even non-corba developers from modelling the interfaces to generating the servant code.
6 Automatically Generated Implementation of the Object Interface HEADER #ifndef EXAMPLEINTERFACE_IMPL_H_HEADER_INCLUDED_C2FAFEB7 #define EXAMPLEINTERFACE_IMPL_H_HEADER_INCLUDED_C2FAFEB7 #include "ExampleS.h" #include "tao/corbafwd.h" #include "tao/portableserver/servant_base.h" //##ModelId=3D class ExampleInterface_Impl : virtual public TAO_RefCountServantBase, virtual public POA_Example::ExampleInterface public: //##ModelId=3D CORBA::Float ExampleAttr(); //##ModelId=3D void ExampleAttr(CORBA::Float ExampleAttr); SOURCE #include "ExampleInterface_Impl.h" //##ModelId=3D CORBA::Float ExampleInterface_Impl::ExampleAttr() } //##ModelId=3D void ExampleInterface_Impl::ExampleAttr(CORBA::Float ExampleAttr) } //##ModelId=3D C3 void ExampleInterface_Impl::ExampleOp(const char *arg) } //##ModelId=3D C3 void ExampleOp(const char *arg); }; #endif /* EXAMPLEINTERFACE_IMPL_H_HEADER_INCLUDED_C2FAFEB7 */
7 CORBA Object Factories Simplify Development
8 Developer Servant and Client Main Blocks SERVANT #include "ace\ace.h" #include "Default_Servant_Factory.h" #include "Ninja_Core_Singleton.h" #include "tao\corbafwd.h" #include "ExampleInterface_Impl.h" #include "ExampleS.h" INSTANTIATE_DEFAULT_SERVANT_FACTORY(ExampleInterface, ExampleInterface_Impl); Default_Servant_Factory<ExampleInterface, ExampleInterface_Impl> example_factory; int main (int argc, char* argv[]) ACE::init(); //Should be the first statement executed in this process. Ninja_Core_Singleton::instance()->start_orb( argc, argv); ExampleInterface_var example_servant = example_factory.create_servant(); //Leave the servant active until no longer needed some_event.wait(); } //ExampleInterface_var example_servant goes out of scope. Ninja_Core_Singleton::instance()->shutdown_orb(TRUE); CLIENT #include "ace\ace.h" #include "Reference_Factory.h" #include "Ninja_Core_Singleton.h" #include "tao\corbafwd.h" #include "ExampleC.h" INSTANTIATE_REFERENCE_FACTORY(ExampleInterface, ExampleInterface_var); int main (int argc, char* argv[]) ACE::init(); //Should be the first statement executed in this process. Ninja_Core_Singleton::instance()->start_orb( argc, argv); Reference_Factory<ExampleInterface, ExampleInterface_var> example_factory( argc, argv, Ninja_Core_Singleton::instance()->orb_name()); ExampleInterface_var example = example_factory.get_reference(); //Leave the servant active until no longer needed some_event.wait(); }//ExampleInterface_var example_servant goes out of scope. } ACE::fini(); return 0; Ninja_Core_Singleton::instance()->shutdown_orb(TRUE); ACE::fini(); return 0; }
9 Peer-to-Peer End-User System End User System (Peer) NAT Firewall 2 INTERNET 1 IP AUTO-DISCOVERY SERVER ORB is installed with game software. Application loader configures ORB at run-time. IP address is auto-discovered: 3 2 NAT Firewall 1 User login 2 Server sends enclave-external endpoint 3 Peers start their session via UDP. End User System (Peer)
10 Client-Server End-User System End User System (Client) NAT Firewall INTERNET SERVER NAT Firewall Client-Server games may also use TCP/IP. End User System (Client)
AQUILA. Project Defense. Sandeep Misra. (IST ) Development of C++ Client for a Java QoS API based on CORBA
 AQUILA (IST-1999-10077) Adaptive Resource Control for QoS Using an IP-based Layered Architecture Project Defense Development of C++ Client for a Java QoS API based on CORBA http://www-st st.inf..inf.tu-dresden.de/aquila/
AQUILA (IST-1999-10077) Adaptive Resource Control for QoS Using an IP-based Layered Architecture Project Defense Development of C++ Client for a Java QoS API based on CORBA http://www-st st.inf..inf.tu-dresden.de/aquila/
CS 326 Operating Systems C Programming. Greg Benson Department of Computer Science University of San Francisco
 CS 326 Operating Systems C Programming Greg Benson Department of Computer Science University of San Francisco Why C? Fast (good optimizing compilers) Not too high-level (Java, Python, Lisp) Not too low-level
CS 326 Operating Systems C Programming Greg Benson Department of Computer Science University of San Francisco Why C? Fast (good optimizing compilers) Not too high-level (Java, Python, Lisp) Not too low-level
P.G.TRB - COMPUTER SCIENCE. c) data processing language d) none of the above
 P.G.TRB - COMPUTER SCIENCE Total Marks : 50 Time : 30 Minutes 1. C was primarily developed as a a)systems programming language b) general purpose language c) data processing language d) none of the above
P.G.TRB - COMPUTER SCIENCE Total Marks : 50 Time : 30 Minutes 1. C was primarily developed as a a)systems programming language b) general purpose language c) data processing language d) none of the above
CE221 Programming in C++ Part 1 Introduction
 CE221 Programming in C++ Part 1 Introduction 06/10/2017 CE221 Part 1 1 Module Schedule There are two lectures (Monday 13.00-13.50 and Tuesday 11.00-11.50) each week in the autumn term, and a 2-hour lab
CE221 Programming in C++ Part 1 Introduction 06/10/2017 CE221 Part 1 1 Module Schedule There are two lectures (Monday 13.00-13.50 and Tuesday 11.00-11.50) each week in the autumn term, and a 2-hour lab
Programs. Function main. C Refresher. CSCI 4061 Introduction to Operating Systems
 Programs CSCI 4061 Introduction to Operating Systems C Program Structure Libraries and header files Compiling and building programs Executing and debugging Instructor: Abhishek Chandra Assume familiarity
Programs CSCI 4061 Introduction to Operating Systems C Program Structure Libraries and header files Compiling and building programs Executing and debugging Instructor: Abhishek Chandra Assume familiarity
Final CSE 131B Winter 2003
 Login name Signature Name Student ID Final CSE 131B Winter 2003 Page 1 Page 2 Page 3 Page 4 Page 5 Page 6 Page 7 Page 8 _ (20 points) _ (25 points) _ (21 points) _ (40 points) _ (30 points) _ (25 points)
Login name Signature Name Student ID Final CSE 131B Winter 2003 Page 1 Page 2 Page 3 Page 4 Page 5 Page 6 Page 7 Page 8 _ (20 points) _ (25 points) _ (21 points) _ (40 points) _ (30 points) _ (25 points)
3) Click the Screen Sharing option and click connect to establish the session
 Preliminary steps before starting the experiment: 1) Click the Launch button to start the experiment. 2) Click OK to create a new session 3) Click the Screen Sharing option and click connect to establish
Preliminary steps before starting the experiment: 1) Click the Launch button to start the experiment. 2) Click OK to create a new session 3) Click the Screen Sharing option and click connect to establish
Internet Networking recitation #
 recitation # UDP NAT Traversal Winter Semester 2013, Dept. of Computer Science, Technion 1 UDP NAT Traversal problems 2 A sender from the internet can't pass a packet through a NAT to a destination host.
recitation # UDP NAT Traversal Winter Semester 2013, Dept. of Computer Science, Technion 1 UDP NAT Traversal problems 2 A sender from the internet can't pass a packet through a NAT to a destination host.
Session Abstract 11/25/2013
 1 Session Abstract While WebRTC is powerful and has huge open opportunities on the Internet, most enterprises are just now deploying SIP as a way to normalize and reduce costs in their communications infrastructure.
1 Session Abstract While WebRTC is powerful and has huge open opportunities on the Internet, most enterprises are just now deploying SIP as a way to normalize and reduce costs in their communications infrastructure.
index_ qxd 7/18/02 11:48 AM Page 259 Index
 index_259-265.qxd 7/18/02 11:48 AM Page 259 Index acceptance testing, 222 activity definition, 249 key concept in RUP, 40 Actor artifact analysis and iterative development, 98 described, 97 136 in the
index_259-265.qxd 7/18/02 11:48 AM Page 259 Index acceptance testing, 222 activity definition, 249 key concept in RUP, 40 Actor artifact analysis and iterative development, 98 described, 97 136 in the
CSCI-243 Exam 1 Review February 22, 2015 Presented by the RIT Computer Science Community
 CSCI-243 Exam 1 Review February 22, 2015 Presented by the RIT Computer Science Community http://csc.cs.rit.edu History and Evolution of Programming Languages 1. Explain the relationship between machine
CSCI-243 Exam 1 Review February 22, 2015 Presented by the RIT Computer Science Community http://csc.cs.rit.edu History and Evolution of Programming Languages 1. Explain the relationship between machine
CS103 Lecture 1 Slides. Introduction Mark Redekopp
 1 CS103 Lecture 1 Slides Introduction Mark Redekopp 2 What is Computer Science All science is computer science It is very interdisciplinary: Math, Engineering, Medicine, Natural sciences, Art, Linguistics,
1 CS103 Lecture 1 Slides Introduction Mark Redekopp 2 What is Computer Science All science is computer science It is very interdisciplinary: Math, Engineering, Medicine, Natural sciences, Art, Linguistics,
In addition to name. Each variable in C program is characterized by its Type Scope Storage Class. Type Have already discussed
 Variables, Storage Class, Scope, Multiple File Multiple Module Projects Overview Will examine how variables characterized Will introduce and study variable s storage class Will examine a variable s visibility
Variables, Storage Class, Scope, Multiple File Multiple Module Projects Overview Will examine how variables characterized Will introduce and study variable s storage class Will examine a variable s visibility
CSci 4061 Introduction to Operating Systems. Programs in C/Unix
 CSci 4061 Introduction to Operating Systems Programs in C/Unix Today Basic C programming Follow on to recitation Structure of a C program A C program consists of a collection of C functions, structs, arrays,
CSci 4061 Introduction to Operating Systems Programs in C/Unix Today Basic C programming Follow on to recitation Structure of a C program A C program consists of a collection of C functions, structs, arrays,
Acquiring the CORBA Environment
 Bionic Buffalo Tech Note #40: Initializing CORBA Applications last revised Sunday 1 November 1998 1998 Bionic Buffalo Corporation. All rights reserved. Tatanka and TOAD are trademarks of Bionic Buffalo
Bionic Buffalo Tech Note #40: Initializing CORBA Applications last revised Sunday 1 November 1998 1998 Bionic Buffalo Corporation. All rights reserved. Tatanka and TOAD are trademarks of Bionic Buffalo
Interactive Graphical Systems HT2006
 HT2006 Networked Virtual Environments Informationsteknologi 2006-09-26 #1 This Lecture Background and history on Networked VEs Fundamentals (TCP/IP, etc) Background and history on Learning NVEs Demo of
HT2006 Networked Virtual Environments Informationsteknologi 2006-09-26 #1 This Lecture Background and history on Networked VEs Fundamentals (TCP/IP, etc) Background and history on Learning NVEs Demo of
Lab 1: First Steps in C++ - Eclipse
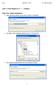 Lab 1: First Steps in C++ - Eclipse Step Zero: Select workspace 1. Upon launching eclipse, we are ask to chose a workspace: 2. We select a new workspace directory (e.g., C:\Courses ): 3. We accept the
Lab 1: First Steps in C++ - Eclipse Step Zero: Select workspace 1. Upon launching eclipse, we are ask to chose a workspace: 2. We select a new workspace directory (e.g., C:\Courses ): 3. We accept the
Chapter 11 Introduction to Programming in C
 C: A High-Level Language Chapter 11 Introduction to Programming in C Original slides from Gregory Byrd, North Carolina State University Modified slides by Chris Wilcox, Colorado State University! Gives
C: A High-Level Language Chapter 11 Introduction to Programming in C Original slides from Gregory Byrd, North Carolina State University Modified slides by Chris Wilcox, Colorado State University! Gives
QoS Control of Video Streams Using Quality Objects and the CORBA Audio/Video Service
 QoS Control of Streams Using Quality Objects and the CORBA Audio/ Service BBN Technologies OOMWorks Cambridge, MA St. Louis, MO http://www.dist-systems.bbn.com/tech/quo http://www.oomworks.com Craig Rodrigues
QoS Control of Streams Using Quality Objects and the CORBA Audio/ Service BBN Technologies OOMWorks Cambridge, MA St. Louis, MO http://www.dist-systems.bbn.com/tech/quo http://www.oomworks.com Craig Rodrigues
CSE 303, Winter 2006, Final Examination 16 March Please do not turn the page until everyone is ready.
 CSE 303, Winter 2006, Final Examination 16 March 2006 Please do not turn the page until everyone is ready. Rules: The exam is closed-book, closed-note, except for one side of one 8.5x11in piece of paper.
CSE 303, Winter 2006, Final Examination 16 March 2006 Please do not turn the page until everyone is ready. Rules: The exam is closed-book, closed-note, except for one side of one 8.5x11in piece of paper.
Programming Proverbs
 Programming Proverbs slide 1 9. Get the syntax correct now, not later. Henry F. Ledgard, Programming Proverbs: Principles of Good Programming with Numerous Examples to Improve Programming Style and Proficiency,
Programming Proverbs slide 1 9. Get the syntax correct now, not later. Henry F. Ledgard, Programming Proverbs: Principles of Good Programming with Numerous Examples to Improve Programming Style and Proficiency,
lecture'7:' quality'assurance'
 so1ware'quality'assurance' lecture'7:' quality'assurance' csc444h fall 2014 humans are fallible infeasible)to)completely)fix)the)humans) need)to)double)and)triple)check)their)work)to)find) the)problems)
so1ware'quality'assurance' lecture'7:' quality'assurance' csc444h fall 2014 humans are fallible infeasible)to)completely)fix)the)humans) need)to)double)and)triple)check)their)work)to)find) the)problems)
Kurt Schmidt. October 30, 2018
 to Structs Dept. of Computer Science, Drexel University October 30, 2018 Array Objectives to Structs Intended audience: Student who has working knowledge of Python To gain some experience with a statically-typed
to Structs Dept. of Computer Science, Drexel University October 30, 2018 Array Objectives to Structs Intended audience: Student who has working knowledge of Python To gain some experience with a statically-typed
Final CSE 131B Spring 2004
 Login name Signature Name Student ID Final CSE 131B Spring 2004 Page 1 Page 2 Page 3 Page 4 Page 5 Page 6 Page 7 Page 8 (25 points) (24 points) (32 points) (24 points) (28 points) (26 points) (22 points)
Login name Signature Name Student ID Final CSE 131B Spring 2004 Page 1 Page 2 Page 3 Page 4 Page 5 Page 6 Page 7 Page 8 (25 points) (24 points) (32 points) (24 points) (28 points) (26 points) (22 points)
RECOMMENDATION. Don't Write Entire Programs Unless You Want To Spend 3-10 Times As Long Doing Labs! Write 1 Function - Test That Function!
 1 2 RECOMMENDATION Don't Write Entire Programs Unless You Want To Spend 3-10 Times As Long Doing Labs! Write 1 Function - Test That Function! 2 Function Overloading C++ provides the capability of Using
1 2 RECOMMENDATION Don't Write Entire Programs Unless You Want To Spend 3-10 Times As Long Doing Labs! Write 1 Function - Test That Function! 2 Function Overloading C++ provides the capability of Using
Blender as a tool for Video Game Prototyping
 Blender as a tool for Video Game Prototyping By INTRODUCTION What is a prototype? INTRO > What > How > BLENDER in a commercial context > End INTRODUCTION What is a prototype? For a commercial dev studio
Blender as a tool for Video Game Prototyping By INTRODUCTION What is a prototype? INTRO > What > How > BLENDER in a commercial context > End INTRODUCTION What is a prototype? For a commercial dev studio
JXTA TM Technology for XML Messaging
 JXTA TM Technology for XML Messaging OASIS Symposium New Orleans, LA 27-April-2004 Richard Manning Senior Software Architect Advanced Technology & Edge Computing Center Sun Microsystems Inc. www.jxta.org
JXTA TM Technology for XML Messaging OASIS Symposium New Orleans, LA 27-April-2004 Richard Manning Senior Software Architect Advanced Technology & Edge Computing Center Sun Microsystems Inc. www.jxta.org
Pro WCF 4. Practical Microsoft SOA Implementation SECOND EDITION. Apress* Nishith Pathak
 Pro WCF 4 Practical Microsoft SOA Implementation SECOND EDITION Nishith Pathak Apress* Contents at a Glance iv About the Author About the Technical Reviewer Acknowledgments xiv xv xvi Introduction xvil
Pro WCF 4 Practical Microsoft SOA Implementation SECOND EDITION Nishith Pathak Apress* Contents at a Glance iv About the Author About the Technical Reviewer Acknowledgments xiv xv xvi Introduction xvil
ELEC 875 Design Recovery and Automated Evolution. Week 1 Class 2 Modeling. ELEC 875 Design Recovery and Automated Evolution
 ELEC 875 Design Recovery and Automated Evolution Week 1 Class 2 Modeling Papers for next week Singer, J., Lethbridge, T., Vinson, N. and Anquetil, N., "An Examination of Software Engineering Work Practices",
ELEC 875 Design Recovery and Automated Evolution Week 1 Class 2 Modeling Papers for next week Singer, J., Lethbridge, T., Vinson, N. and Anquetil, N., "An Examination of Software Engineering Work Practices",
Software Paradigms (Lesson 10) Selected Topics in Software Architecture
 Software Paradigms (Lesson 10) Selected Topics in Software Architecture Table of Contents 1 World-Wide-Web... 2 1.1 Basic Architectural Solution... 2 1.2 Designing WWW Applications... 7 2 CORBA... 11 2.1
Software Paradigms (Lesson 10) Selected Topics in Software Architecture Table of Contents 1 World-Wide-Web... 2 1.1 Basic Architectural Solution... 2 1.2 Designing WWW Applications... 7 2 CORBA... 11 2.1
Desarrollo de Aplicaciones en Red. El modelo de comunicación. General concepts. Models of communication. Message Passing
 Desarrollo de Aplicaciones en Red El modelo de comunicación José Rafael Rojano Cáceres http://www.uv.mx/rrojano 1 2 General concepts As we saw in a Distributed System the logical and physical component
Desarrollo de Aplicaciones en Red El modelo de comunicación José Rafael Rojano Cáceres http://www.uv.mx/rrojano 1 2 General concepts As we saw in a Distributed System the logical and physical component
Implementing an ADT with a Class
 Implementing an ADT with a Class the header file contains the class definition the source code file normally contains the class s method definitions when using Visual C++ 2012, the source code and the
Implementing an ADT with a Class the header file contains the class definition the source code file normally contains the class s method definitions when using Visual C++ 2012, the source code and the
Modifiers. int foo(int x) { static int y=0; /* value of y is saved */ y = x + y + 7; /* across invocations of foo */ return y; }
 Modifiers unsigned. For example unsigned int would have a range of [0..2 32 1] on a 32-bit int machine. const Constant or read-only. Same as final in Java. static Similar to static in Java but not the
Modifiers unsigned. For example unsigned int would have a range of [0..2 32 1] on a 32-bit int machine. const Constant or read-only. Same as final in Java. static Similar to static in Java but not the
Avaya Port Matrix: Avaya Aura Performance Center 7.1
 Avaya Port Matrix: Avaya Aura Performance Center 7.1 Issue 1.0 November 2014 1 ALL INFORMATION IS BELIEVED TO BE CORRECT AT THE TIME OF PUBLICATION AND IS PROVIDED "AS IS". AVAYA INC. DISCLAIMS ALL WARRANTIES,
Avaya Port Matrix: Avaya Aura Performance Center 7.1 Issue 1.0 November 2014 1 ALL INFORMATION IS BELIEVED TO BE CORRECT AT THE TIME OF PUBLICATION AND IS PROVIDED "AS IS". AVAYA INC. DISCLAIMS ALL WARRANTIES,
Chapter 11 Introduction to Programming in C
 Chapter 11 Introduction to Programming in C Original slides from Gregory Byrd, North Carolina State University Modified slides by Chris Wilcox, Colorado State University C: A High-Level Language! Gives
Chapter 11 Introduction to Programming in C Original slides from Gregory Byrd, North Carolina State University Modified slides by Chris Wilcox, Colorado State University C: A High-Level Language! Gives
UNIT III (PART-II) & UNIT IV(PART-I)
 UNIT III (PART-II) & UNIT IV(PART-I) Function: it is defined as self contained block of code to perform a task. Functions can be categorized to system-defined functions and user-defined functions. System
UNIT III (PART-II) & UNIT IV(PART-I) Function: it is defined as self contained block of code to perform a task. Functions can be categorized to system-defined functions and user-defined functions. System
CS 216 Fall 2007 Midterm 1 Page 1 of 10 Name: ID:
 Page 1 of 10 Name: Email ID: You MUST write your name and e-mail ID on EACH page and bubble in your userid at the bottom of EACH page including this page and page 10. If you do not do this, you will receive
Page 1 of 10 Name: Email ID: You MUST write your name and e-mail ID on EACH page and bubble in your userid at the bottom of EACH page including this page and page 10. If you do not do this, you will receive
MDSE USE CASES. Chapter #3
 Chapter #3 MDSE USE CASES Teaching material for the book Model-Driven Software Engineering in Practice by Morgan & Claypool, USA, 2012. www.mdse-book.com MDSE GOES FAR BEYOND CODE-GENERATION www.mdse-book.com
Chapter #3 MDSE USE CASES Teaching material for the book Model-Driven Software Engineering in Practice by Morgan & Claypool, USA, 2012. www.mdse-book.com MDSE GOES FAR BEYOND CODE-GENERATION www.mdse-book.com
Introduction to Programming (Java) 4/12
 Introduction to Programming (Java) 4/12 Michal Krátký Department of Computer Science Technical University of Ostrava Introduction to Programming (Java) 2008/2009 c 2006 2008 Michal Krátký Introduction
Introduction to Programming (Java) 4/12 Michal Krátký Department of Computer Science Technical University of Ostrava Introduction to Programming (Java) 2008/2009 c 2006 2008 Michal Krátký Introduction
CS2141 Software Development using C/C++ C++ Basics
 CS2141 Software Development using C/C++ C++ Basics Integers Basic Types Can be short, long, or just plain int C++ does not define the size of them other than short
CS2141 Software Development using C/C++ C++ Basics Integers Basic Types Can be short, long, or just plain int C++ does not define the size of them other than short
Presented By: Niharjyoti Sarangi
 Presented By: Niharjyoti Sarangi 1. 2. 3. 4. 5. 6. 7. 8. INTRODUCTION WHAT & WHY KEY FEATURES JXTA ARCHITECTURE JXTA LAYERS JXTA JARGONS JXTA PROTOCOLS JXTA SHELLS JXTA ADVANTAGES 2 AN OPEN P2P PROTOCOL
Presented By: Niharjyoti Sarangi 1. 2. 3. 4. 5. 6. 7. 8. INTRODUCTION WHAT & WHY KEY FEATURES JXTA ARCHITECTURE JXTA LAYERS JXTA JARGONS JXTA PROTOCOLS JXTA SHELLS JXTA ADVANTAGES 2 AN OPEN P2P PROTOCOL
TENA R A N G E L V C
 TENA RANGE LVC TENA Test and Training Enabling Architecture (TENA) See https://www.tena-sda.org/display/intro/home Targeted at LVC applications in a range environment; has substantial spillover to the
TENA RANGE LVC TENA Test and Training Enabling Architecture (TENA) See https://www.tena-sda.org/display/intro/home Targeted at LVC applications in a range environment; has substantial spillover to the
Exam Duration: 2hrs and 30min Software Design
 Exam Duration: 2hrs and 30min. 433-254 Software Design Section A Multiple Choice (This sample paper has less questions than the exam paper The exam paper will have 25 Multiple Choice questions.) 1. Which
Exam Duration: 2hrs and 30min. 433-254 Software Design Section A Multiple Choice (This sample paper has less questions than the exam paper The exam paper will have 25 Multiple Choice questions.) 1. Which
Array Initialization
 Array Initialization Array declarations can specify initializations for the elements of the array: int primes[10] = { 2, 3, 5, 7, 11, 13, 17, 19, 23, 29 ; initializes primes[0] to 2, primes[1] to 3, primes[2]
Array Initialization Array declarations can specify initializations for the elements of the array: int primes[10] = { 2, 3, 5, 7, 11, 13, 17, 19, 23, 29 ; initializes primes[0] to 2, primes[1] to 3, primes[2]
MPI 1. CSCI 4850/5850 High-Performance Computing Spring 2018
 MPI 1 CSCI 4850/5850 High-Performance Computing Spring 2018 Tae-Hyuk (Ted) Ahn Department of Computer Science Program of Bioinformatics and Computational Biology Saint Louis University Learning Objectives
MPI 1 CSCI 4850/5850 High-Performance Computing Spring 2018 Tae-Hyuk (Ted) Ahn Department of Computer Science Program of Bioinformatics and Computational Biology Saint Louis University Learning Objectives
Topic 8: Lazy Evaluation
 Topic 8: Lazy Evaluation 1 Recommended Exercises and Readings From Haskell: The craft of functional programming (3 rd Ed.) Exercises: 17.1, 17.2, 17.4, 17.8, 17.23, 17.25, 17.28, 17.29 Readings: Chapter
Topic 8: Lazy Evaluation 1 Recommended Exercises and Readings From Haskell: The craft of functional programming (3 rd Ed.) Exercises: 17.1, 17.2, 17.4, 17.8, 17.23, 17.25, 17.28, 17.29 Readings: Chapter
Memory Allocation in C
 Memory Allocation in C When a C program is loaded into memory, it is organized into three areas of memory, called segments: the text segment, stack segment and heap segment. The text segment (also called
Memory Allocation in C When a C program is loaded into memory, it is organized into three areas of memory, called segments: the text segment, stack segment and heap segment. The text segment (also called
Agent and Object Technology Lab Dipartimento di Ingegneria dell Informazione Università degli Studi di Parma. Distributed and Agent Systems
 Agent and Object Technology Lab Dipartimento di Ingegneria dell Informazione Università degli Studi di Parma Distributed and Agent Systems Prof. Agostino Poggi What is CORBA? CORBA (Common Object Request
Agent and Object Technology Lab Dipartimento di Ingegneria dell Informazione Università degli Studi di Parma Distributed and Agent Systems Prof. Agostino Poggi What is CORBA? CORBA (Common Object Request
Program Translation. text. text. binary. binary. C program (p1.c) Compiler (gcc -S) Asm code (p1.s) Assembler (gcc or as) Object code (p1.
 Program Translation Compilation & Linking 1 text C program (p1.c) Compiler (gcc -S) text Asm code (p1.s) binary binary Assembler (gcc or as) Object code (p1.o) Linker (gcc or ld) Executable program (p1)
Program Translation Compilation & Linking 1 text C program (p1.c) Compiler (gcc -S) text Asm code (p1.s) binary binary Assembler (gcc or as) Object code (p1.o) Linker (gcc or ld) Executable program (p1)
SharePoint Development Web Development Generate from Usage. Cloud Development Windows Development Office Development
 Silverlight Tools SharePoint Development Web Development Generate from Usage New WPF Editor Multi-core Development Cloud Development Windows Development Office Development Customizable IDE UI Test Automation
Silverlight Tools SharePoint Development Web Development Generate from Usage New WPF Editor Multi-core Development Cloud Development Windows Development Office Development Customizable IDE UI Test Automation
Lesson 5: Functions and Libraries. EE3490E: Programming S1 2018/2019 Dr. Đào Trung Kiên Hanoi Univ. of Science and Technology
 Lesson 5: Functions and Libraries 1 Functions 2 Overview Function is a block of statements which performs a specific task, and can be called by others Each function has a name (not identical to any other),
Lesson 5: Functions and Libraries 1 Functions 2 Overview Function is a block of statements which performs a specific task, and can be called by others Each function has a name (not identical to any other),
Classes and Objects 3/28/2017. How can multiple methods within a Java class read and write the same variable?
 Peer Instruction 8 Classes and Objects How can multiple methods within a Java class read and write the same variable? A. Allow one method to reference a local variable of the other B. Declare a variable
Peer Instruction 8 Classes and Objects How can multiple methods within a Java class read and write the same variable? A. Allow one method to reference a local variable of the other B. Declare a variable
CS 161 Computer Security
 Raluca Popa Spring 2018 CS 161 Computer Security Homework 1 Due: Monday, January 29th, at 11:59pm Instructions. This homework is due Monday, January 29th, at 11:59pm. No late homeworks will be accepted
Raluca Popa Spring 2018 CS 161 Computer Security Homework 1 Due: Monday, January 29th, at 11:59pm Instructions. This homework is due Monday, January 29th, at 11:59pm. No late homeworks will be accepted
Net Centric Computing - Graphics
 Net Centric Computing - Graphics Sandro Spina Computer Graphics and Simulation Group Computer Science Department University of Malta 1 Graphics + Web = Web3D2009 Web3D 2009 Symposium, 14th International
Net Centric Computing - Graphics Sandro Spina Computer Graphics and Simulation Group Computer Science Department University of Malta 1 Graphics + Web = Web3D2009 Web3D 2009 Symposium, 14th International
Testing, code coverage and static analysis. COSC345 Software Engineering
 Testing, code coverage and static analysis COSC345 Software Engineering Outline Various testing processes ad hoc / formal / automatic Unit tests and test driven development Code coverage metrics Integration
Testing, code coverage and static analysis COSC345 Software Engineering Outline Various testing processes ad hoc / formal / automatic Unit tests and test driven development Code coverage metrics Integration
KS3 Programme of Study Subject: Computing Year group: Y7
 KS3 Programme of Study Subject: Computing Year group: Y7 Cybercrime 14/11/16 2/12/16 due AF1 Introduction - savings, set up folders, Health and Safety, Classroom Rules How to log on and secure passwords
KS3 Programme of Study Subject: Computing Year group: Y7 Cybercrime 14/11/16 2/12/16 due AF1 Introduction - savings, set up folders, Health and Safety, Classroom Rules How to log on and secure passwords
CSI33 Data Structures
 Outline Department of Mathematics and Computer Science Bronx Community College October 25, 2017 Outline Outline 1 Chapter 8: A C++ Introduction For Python Programmers Function Details Assert Statements
Outline Department of Mathematics and Computer Science Bronx Community College October 25, 2017 Outline Outline 1 Chapter 8: A C++ Introduction For Python Programmers Function Details Assert Statements
MARKING KEY The University of British Columbia MARKING KEY Computer Science 260 Midterm #1 Examination 12:30 noon, Tuesday, February 14, 2012
 MARKING KEY The University of British Columbia MARKING KEY Computer Science 260 Midterm #1 Examination 12:30 noon, Tuesday, February 14, 2012 Instructor: K. S. Booth Time: 70 minutes (one hour ten minutes)
MARKING KEY The University of British Columbia MARKING KEY Computer Science 260 Midterm #1 Examination 12:30 noon, Tuesday, February 14, 2012 Instructor: K. S. Booth Time: 70 minutes (one hour ten minutes)
FINAL TERM EXAMINATION SPRING 2010 CS304- OBJECT ORIENTED PROGRAMMING
 FINAL TERM EXAMINATION SPRING 2010 CS304- OBJECT ORIENTED PROGRAMMING Question No: 1 ( Marks: 1 ) - Please choose one Classes like TwoDimensionalShape and ThreeDimensionalShape would normally be concrete,
FINAL TERM EXAMINATION SPRING 2010 CS304- OBJECT ORIENTED PROGRAMMING Question No: 1 ( Marks: 1 ) - Please choose one Classes like TwoDimensionalShape and ThreeDimensionalShape would normally be concrete,
CSE 12 Spring 2016 Week One, Lecture Two
 CSE 12 Spring 2016 Week One, Lecture Two Homework One and Two: hw2: Discuss in section today - Introduction to C - Review of basic programming principles - Building from fgetc and fputc - Input and output
CSE 12 Spring 2016 Week One, Lecture Two Homework One and Two: hw2: Discuss in section today - Introduction to C - Review of basic programming principles - Building from fgetc and fputc - Input and output
Chapter 11 Introduction to Programming in C
 Chapter 11 Introduction to Programming in C Original slides from Gregory Byrd, North Carolina State University Modified by Chris Wilcox, Yashwant Malaiya Colorado State University C: A High-Level Language
Chapter 11 Introduction to Programming in C Original slides from Gregory Byrd, North Carolina State University Modified by Chris Wilcox, Yashwant Malaiya Colorado State University C: A High-Level Language
LABORATORY 1 REVISION
 UTCN Computer Science Department Software Design 2012/2013 LABORATORY 1 REVISION ================================================================== I. UML Revision This section focuses on reviewing the
UTCN Computer Science Department Software Design 2012/2013 LABORATORY 1 REVISION ================================================================== I. UML Revision This section focuses on reviewing the
Unified Modeling Language (UML)
 1.17 Software Engineering Case Study: Introduction to Object Technology and the UML (Required) Object orientation A natural way of thinking about the world and computer programs Unified Modeling Language
1.17 Software Engineering Case Study: Introduction to Object Technology and the UML (Required) Object orientation A natural way of thinking about the world and computer programs Unified Modeling Language
Exercise Session 2 Simon Gerber
 Exercise Session 2 Simon Gerber CASP 2014 Exercise 2: Binary search tree Implement and test a binary search tree in C: Implement key insert() and lookup() functions Implement as C module: bst.c, bst.h
Exercise Session 2 Simon Gerber CASP 2014 Exercise 2: Binary search tree Implement and test a binary search tree in C: Implement key insert() and lookup() functions Implement as C module: bst.c, bst.h
TN FIREWALL CONSIDERATIONS FOR CAMELOT IP CAMERAS
 TN0020 - FIREWALL CONSIDERATIONS FOR CAMELOT IP CAMERAS 1 CAMELOT IP CAMERAS IN THE LAN Discovering a Camelot IP camera in the LAN and maintaining a session with it makes use of two UDP ports in the PC
TN0020 - FIREWALL CONSIDERATIONS FOR CAMELOT IP CAMERAS 1 CAMELOT IP CAMERAS IN THE LAN Discovering a Camelot IP camera in the LAN and maintaining a session with it makes use of two UDP ports in the PC
UNIVERSITY OF SWAZILAND
 UNIVERSITY OF SWAZILAND DEPARTMENT OF COMPUTER SCIENCE CSC242 - OBJECT ORIENTED PROGRAMMING FINAL EXAMINATION MAY 2017 Instructions 1. The time allowed is THREE (3) H0URS. 2. Read all the questions in
UNIVERSITY OF SWAZILAND DEPARTMENT OF COMPUTER SCIENCE CSC242 - OBJECT ORIENTED PROGRAMMING FINAL EXAMINATION MAY 2017 Instructions 1. The time allowed is THREE (3) H0URS. 2. Read all the questions in
Spectrum Enterprise SIP Trunking Service Ipitomy IP1200 IP PBX Configuration Guide
 Spectrum Enterprise SIP Trunking Service Ipitomy IP1200 IP PBX Configuration Guide About Spectrum Enterprise: Spectrum Enterprise is a division of Charter Communications following a merger with Time Warner
Spectrum Enterprise SIP Trunking Service Ipitomy IP1200 IP PBX Configuration Guide About Spectrum Enterprise: Spectrum Enterprise is a division of Charter Communications following a merger with Time Warner
Array Basics: Outline. Creating and Accessing Arrays. Creating and Accessing Arrays. Arrays (Savitch, Chapter 7)
 Array Basics: Outline Arrays (Savitch, Chapter 7) TOPICS Array Basics Arrays in Classes and Methods Programming with Arrays Searching and Sorting Arrays Multi-Dimensional Arrays Static Variables and Constants
Array Basics: Outline Arrays (Savitch, Chapter 7) TOPICS Array Basics Arrays in Classes and Methods Programming with Arrays Searching and Sorting Arrays Multi-Dimensional Arrays Static Variables and Constants
Process Concept: views of a process Process Scheduling CSCI 6730/ 4730 Operating Systems
 Chapter 3: Processes: Outline Process Concept: views of a process Process Scheduling CSCI 6730/ 4730 Operating Systems Operations on Processes Cooperating Processes Inter Process Communication (IPC) RPC:
Chapter 3: Processes: Outline Process Concept: views of a process Process Scheduling CSCI 6730/ 4730 Operating Systems Operations on Processes Cooperating Processes Inter Process Communication (IPC) RPC:
416 Distributed Systems. Networks review; Day 2 of 2 Fate sharing, e2e principle And start of RPC Jan 10, 2018
 416 Distributed Systems Networks review; Day 2 of 2 Fate sharing, e2e principle And start of RPC Jan 10, 2018 1 Last Time Modularity, Layering, and Decomposition Example: UDP layered on top of IP to provide
416 Distributed Systems Networks review; Day 2 of 2 Fate sharing, e2e principle And start of RPC Jan 10, 2018 1 Last Time Modularity, Layering, and Decomposition Example: UDP layered on top of IP to provide
Call The Project Dynamic-Memory
 1 2 2 Call The Project Dynamic-Memory 4 4 Copy-Paste Main # include "Utilities.hpp" int main(int argc, char * argv[]) { short int *PtrNo; (*PtrNo) = 5; printf ("(*PtrNo) = %d\n", (*PtrNo)); } getchar();
1 2 2 Call The Project Dynamic-Memory 4 4 Copy-Paste Main # include "Utilities.hpp" int main(int argc, char * argv[]) { short int *PtrNo; (*PtrNo) = 5; printf ("(*PtrNo) = %d\n", (*PtrNo)); } getchar();
PROGRAMMAZIONE I A.A. 2017/2018
 PROGRAMMAZIONE I A.A. 2017/2018 FUNCTIONS INTRODUCTION AND MAIN All the instructions of a C program are contained in functions. üc is a procedural language üeach function performs a certain task A special
PROGRAMMAZIONE I A.A. 2017/2018 FUNCTIONS INTRODUCTION AND MAIN All the instructions of a C program are contained in functions. üc is a procedural language üeach function performs a certain task A special
S. Monaghan CSEE, University of Essex. September 21, Client Program and Server Program 3
 CSEE University of Essex CE806 - Distributed Computing (2010-11) Laboratory 6 Java IDL (Script/code checked and working in Computer Laboratory 1 on 21/9/2010) S. Monaghan CSEE, University of Essex September
CSEE University of Essex CE806 - Distributed Computing (2010-11) Laboratory 6 Java IDL (Script/code checked and working in Computer Laboratory 1 on 21/9/2010) S. Monaghan CSEE, University of Essex September
Port Mirroring in CounterACT. CounterACT Technical Note
 Table of Contents About Port Mirroring and the Packet Engine... 3 Information Based on Specific Protocols... 4 ARP... 4 DHCP... 5 HTTP... 6 NetBIOS... 7 TCP/UDP... 7 Endpoint Lifecycle... 8 Active Endpoint
Table of Contents About Port Mirroring and the Packet Engine... 3 Information Based on Specific Protocols... 4 ARP... 4 DHCP... 5 HTTP... 6 NetBIOS... 7 TCP/UDP... 7 Endpoint Lifecycle... 8 Active Endpoint
Functions & Memory Maps Review C Programming Language
 Functions & Memory Maps Review C Programming Language Data Abstractions CSCI-2320 Dr. Tom Hicks Computer Science Department Constants c 2 What Is A Constant? Constant a Value that cannot be altered by
Functions & Memory Maps Review C Programming Language Data Abstractions CSCI-2320 Dr. Tom Hicks Computer Science Department Constants c 2 What Is A Constant? Constant a Value that cannot be altered by
mith College Computer Science CSC231 Bash Labs Week #10, 11, 12 Spring 2017 Introduction to C Dominique Thiébaut
 mith College CSC231 Bash Labs Week #10, 11, 12 Spring 2017 Introduction to C Dominique Thiébaut dthiebaut@smith.edu Learning C in 4 Hours! D. Thiebaut Dennis Ritchie 1969 to 1973 AT&T Bell Labs Close to
mith College CSC231 Bash Labs Week #10, 11, 12 Spring 2017 Introduction to C Dominique Thiébaut dthiebaut@smith.edu Learning C in 4 Hours! D. Thiebaut Dennis Ritchie 1969 to 1973 AT&T Bell Labs Close to
CS 580 FINAL EXAM. Fall April 29, 2014
 CS 580 FINAL EXAM Fall 201 April 29, 2014 You are to build a range tree for your final exam. A range tree is a tree where each node contains a minimum and a maximum value as well as a linked list to store
CS 580 FINAL EXAM Fall 201 April 29, 2014 You are to build a range tree for your final exam. A range tree is a tree where each node contains a minimum and a maximum value as well as a linked list to store
That means circular linked list is similar to the single linked list except that the last node points to the first node in the list.
 Leaning Objective: In this Module you will be learning the following: Circular Linked Lists and it operations Introduction: Circular linked list is a sequence of elements in which every element has link
Leaning Objective: In this Module you will be learning the following: Circular Linked Lists and it operations Introduction: Circular linked list is a sequence of elements in which every element has link
Chapter 3: Processes: Outline. Operating Systems. Remote Procedure Calls (RPC) Client-Server Remote Machine Communication Mechanisms
 Chapter 3: Processes: Outline Operating Systems RPC: Processes Process Concept: views of a process Process Scheduling Operations on Processes Cooperating Processes Inter Process Communication (IPC) Local
Chapter 3: Processes: Outline Operating Systems RPC: Processes Process Concept: views of a process Process Scheduling Operations on Processes Cooperating Processes Inter Process Communication (IPC) Local
Ministry of Higher Education Colleges of Applied Sciences Final Exam Academic Year 2009/2010. Student s Name
 Ministry of Higher Education Colleges of Applied Sciences Final Exam Academic Year 2009/2010 Course Number/Name: SFDV4001 Object-Oriented Programming & U.I. Date: Time: College: Sohar[ ] Ibri[ ] Rustaq[
Ministry of Higher Education Colleges of Applied Sciences Final Exam Academic Year 2009/2010 Course Number/Name: SFDV4001 Object-Oriented Programming & U.I. Date: Time: College: Sohar[ ] Ibri[ ] Rustaq[
G52CPP C++ Programming Lecture 6. Dr Jason Atkin
 G52CPP C++ Programming Lecture 6 Dr Jason Atkin 1 Last lecture The Stack Lifetime of local variables Global variables Static local variables const (briefly) 2 Visibility is different from lifetime Just
G52CPP C++ Programming Lecture 6 Dr Jason Atkin 1 Last lecture The Stack Lifetime of local variables Global variables Static local variables const (briefly) 2 Visibility is different from lifetime Just
The ITAPS Mesh Interface
 The ITAPS Mesh Interface Carl Ollivier-Gooch Advanced Numerical Simulation Laboratory, University of British Columbia Needs and Challenges for Unstructured Mesh Usage Application PDE Discretization Mesh
The ITAPS Mesh Interface Carl Ollivier-Gooch Advanced Numerical Simulation Laboratory, University of British Columbia Needs and Challenges for Unstructured Mesh Usage Application PDE Discretization Mesh
Spectrum Enterprise SIP Trunking Service IPitomy IP1100, IP1200, IP2000, IP5000 v5.0.5 to IP PBX Configuration Guide
 Spectrum Enterprise SIP Trunking Service IPitomy IP1100, IP1200, IP2000, IP5000 v5.0.5 to 5.1.3 About Spectrum Enterprise: IP PBX Configuration Guide Spectrum Enterprise is a division of Charter Communications
Spectrum Enterprise SIP Trunking Service IPitomy IP1100, IP1200, IP2000, IP5000 v5.0.5 to 5.1.3 About Spectrum Enterprise: IP PBX Configuration Guide Spectrum Enterprise is a division of Charter Communications
Announcements. CSCI 334: Principles of Programming Languages. Lecture 18: C/C++ Announcements. Announcements. Instructor: Dan Barowy
 CSCI 334: Principles of Programming Languages Lecture 18: C/C++ Homework help session will be tomorrow from 7-9pm in Schow 030A instead of on Thursday. Instructor: Dan Barowy HW6 and HW7 solutions We only
CSCI 334: Principles of Programming Languages Lecture 18: C/C++ Homework help session will be tomorrow from 7-9pm in Schow 030A instead of on Thursday. Instructor: Dan Barowy HW6 and HW7 solutions We only
Introduction to UML p. 1 Introduction to the Object-Oriented Paradigm p. 1 What Is Visual Modeling? p. 6 Systems of Graphical Notation p.
 Introduction p. xxi Introduction to UML p. 1 Introduction to the Object-Oriented Paradigm p. 1 What Is Visual Modeling? p. 6 Systems of Graphical Notation p. 7 Understanding UML Diagrams p. 10 Visual Modeling
Introduction p. xxi Introduction to UML p. 1 Introduction to the Object-Oriented Paradigm p. 1 What Is Visual Modeling? p. 6 Systems of Graphical Notation p. 7 Understanding UML Diagrams p. 10 Visual Modeling
Modularity. Object Request Broker. Object Request Broker. These slides are based on Wikipedia and other Web sources (URLs given)
 These slides are based on Wikipedia and other Web sources (URLs given) Web Service Distributed Architectures Object Request Broker Software Engineering function Andreas Zeller Saarland University function
These slides are based on Wikipedia and other Web sources (URLs given) Web Service Distributed Architectures Object Request Broker Software Engineering function Andreas Zeller Saarland University function
Avaya Proprietary Use pursuant to the terms of your signed agreement or Avaya policy.
 Matrix Equinox 3.0 Issue 1.0 December 15, 2016 Proprietary Use pursuant to the terms of your signed agreement or policy. December 2016 Matrix: Equinox 3.0 1 ALL INFORMATION IS BELIEVED TO BE CORRECT AT
Matrix Equinox 3.0 Issue 1.0 December 15, 2016 Proprietary Use pursuant to the terms of your signed agreement or policy. December 2016 Matrix: Equinox 3.0 1 ALL INFORMATION IS BELIEVED TO BE CORRECT AT
COMP 2355 Introduction to Systems Programming
 COMP 2355 Introduction to Systems Programming Christian Grothoff christian@grothoff.org http://grothoff.org/christian/ 1 Today Class syntax, Constructors, Destructors Static methods Inheritance, Abstract
COMP 2355 Introduction to Systems Programming Christian Grothoff christian@grothoff.org http://grothoff.org/christian/ 1 Today Class syntax, Constructors, Destructors Static methods Inheritance, Abstract
Chapter 5.6 Network and Multiplayer
 Chapter 5.6 Network and Multiplayer Multiplayer Modes: Event Timing Turn-Based Easy to implement Any connection type Real-Time Difficult to implement Latency sensitive 2 Multiplayer Modes: Shared I/O Input
Chapter 5.6 Network and Multiplayer Multiplayer Modes: Event Timing Turn-Based Easy to implement Any connection type Real-Time Difficult to implement Latency sensitive 2 Multiplayer Modes: Shared I/O Input
Compartmentalizing Formally Secure Compilation
 Compartmentalizing Formally Secure Compilation Cătălin Hrițcu Inria Paris https://secure-compilation.github.io 1 0. Compiler correctness Course outline as Trace Property Preservation 1. Secure interoperability
Compartmentalizing Formally Secure Compilation Cătălin Hrițcu Inria Paris https://secure-compilation.github.io 1 0. Compiler correctness Course outline as Trace Property Preservation 1. Secure interoperability
Oracle Tuxedo. Getting Started with Oracle Tuxedo CORBA Applications 12c Release 1 (12.1.1) June 2012
 Oracle Tuxedo Getting Started with Oracle Tuxedo CORBA Applications 12c Release 1 (12.1.1) June 2012 Oracle Tuxedo Getting Started with Oracle Tuxedo CORBA Applications, 12c Release 1 (12.1.1) Copyright
Oracle Tuxedo Getting Started with Oracle Tuxedo CORBA Applications 12c Release 1 (12.1.1) June 2012 Oracle Tuxedo Getting Started with Oracle Tuxedo CORBA Applications, 12c Release 1 (12.1.1) Copyright
LECTURE 5. Announcements
 LECTURE 5 Announcements Falling Behind? Talk to us You still pass the class if you hand in all projects at the end of the semester Hand in even if you think you won t satisfy the playtesting requirements
LECTURE 5 Announcements Falling Behind? Talk to us You still pass the class if you hand in all projects at the end of the semester Hand in even if you think you won t satisfy the playtesting requirements
CS 223: Data Structures and Programming Techniques. Exam 2. April 19th, 2012
 CS 223: Data Structures and Programming Techniques. Exam 2 April 19th, 2012 Instructor: Jim Aspnes Work alone. Do not use any notes or books. You have approximately 75 minutes to complete this exam. Please
CS 223: Data Structures and Programming Techniques. Exam 2 April 19th, 2012 Instructor: Jim Aspnes Work alone. Do not use any notes or books. You have approximately 75 minutes to complete this exam. Please
Generate Java source from UML class diagram in NetBeans Written Date : February 22, 2010
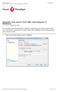 Generate Java source from UML class diagram in NetBeans Written Date : February 22, 2010 You can perform round-trip engineering in NetBeans, to keep Java source code and class model in sync. In this tutorial,
Generate Java source from UML class diagram in NetBeans Written Date : February 22, 2010 You can perform round-trip engineering in NetBeans, to keep Java source code and class model in sync. In this tutorial,
Team 4: Unicommerce. Team Members
 Team 4: Unicommerce 17-654: Analysis of Software Artifacts 18-841: Dependability Analysis of Middleware Wei Zhang Dawei Gu Maneesh Sharma Morgan Linton Team Members Wei Zhang wzhang@cs.cmu.edu Maneesh
Team 4: Unicommerce 17-654: Analysis of Software Artifacts 18-841: Dependability Analysis of Middleware Wei Zhang Dawei Gu Maneesh Sharma Morgan Linton Team Members Wei Zhang wzhang@cs.cmu.edu Maneesh
Lecture 7 Overview. IPv6 Source: Chapter 12 of Stevens book Chapter 31 of Comer s book
 Last Lecture Lecture 7 Overview Name and address conversions This Lecture IPv6 Source: Chapter 12 of Stevens book Chapter 31 of Comer s book Next Lecture Broadcast and multicast sockets Source: Chapters
Last Lecture Lecture 7 Overview Name and address conversions This Lecture IPv6 Source: Chapter 12 of Stevens book Chapter 31 of Comer s book Next Lecture Broadcast and multicast sockets Source: Chapters
COS 126 Midterm 1 Written Exam Fall 2011
 NAME: login id: Precept: COS 126 Midterm 1 Written Exam Fall 2011 This test has 8 questions, weighted as indicated. The exam is closed book, except that you are allowed to use a one page cheatsheet. No
NAME: login id: Precept: COS 126 Midterm 1 Written Exam Fall 2011 This test has 8 questions, weighted as indicated. The exam is closed book, except that you are allowed to use a one page cheatsheet. No
Multi-Channel Clustered Web Application Servers
 Multi-Channel Clustered Web Application Servers Masters Thesis Proposal Progress American University in Cairo Proposed by Karim Sobh (kmsobh@aucegypt.edu) Supervised by Dr. Ahmed Sameh (sameh@aucegypt.edu)
Multi-Channel Clustered Web Application Servers Masters Thesis Proposal Progress American University in Cairo Proposed by Karim Sobh (kmsobh@aucegypt.edu) Supervised by Dr. Ahmed Sameh (sameh@aucegypt.edu)
Principles of Computer Game Design and Implementation. Lecture 3
 Principles of Computer Game Design and Implementation Lecture 3 We already knew Introduction to this module History of video High-level information for a game (such as Game platform, player motivation,
Principles of Computer Game Design and Implementation Lecture 3 We already knew Introduction to this module History of video High-level information for a game (such as Game platform, player motivation,
ECE 462 Exam 1. 6:30-7:30PM, September 22, 2010
 ECE 462 Exam 1 6:30-7:30PM, September 22, 2010 I will not receive nor provide aid to any other student for this exam. Signature: You must sign here. Otherwise, the exam is not graded. This exam is printed
ECE 462 Exam 1 6:30-7:30PM, September 22, 2010 I will not receive nor provide aid to any other student for this exam. Signature: You must sign here. Otherwise, the exam is not graded. This exam is printed
