Kareem Naaz (KN) Encryption and Decryption using Sorting
|
|
|
- Dana Barnett
- 5 years ago
- Views:
Transcription
1 Kareem Naaz (KN) Encryption and Decryption using Sorting Shaik Kareem Basha Asst. Professor CSE Abstract: In Computer networks, Messages are transmitted from sender to receiver with high security. Encryption Algorithm is used by sender to convert plain text into cipher text before sending text to receiver. At the receiver, Decryption Algorithm is used to convert cipher text into plain text. Sorting is a process of arranging data in a specific order according to requirements of Application. In the proposed paper I am using sorting algorithm to encrypt plain text into cipher text at the sender and at the receiver also sorting algorithm is used to convert cipher text into plain text. At the sender plain text is sorted in alphabetical order and the indices of characters of plain text are also sorted in that order and placed into index array. To the receiver cipher text and index array are sent. At the receiver index array, which contains indices of sorted plain text, is sorted in increasing order and characters of cipher text are also sorted in the same order to form plain text. I followed the various stages of Software Development Life Cycle to demonstrate the proposed sorting algorithm. Section I will give introduction about proposed sorting algorithm. In section II, proposed Algorithm is Analyzed and Designed. In section III, proposed algorithm is Implemented using C programming Language. In section IV, I tested the implementation of proposed algorithm using different test cases. In section V, I concluded the proposed Algorithm. I. INTRODUCTION In Computer networks, Messages are transmitted from sender to receiver with high security. Encryption is the process of converting plain text of n characters into cipher text of n characters. Plain text is the readable text where as cipher text is unreadable text, which is difficult to understand. Decryption is the process of converting cipher text of n characters into plain text of n characters. Encryption Algorithm is used by sender to convert plain text into cipher text before sending text to receiver. At the receiver, Decryption Algorithm is used to convert cipher text into plain text. Sorting is a process of arranging data in a specific order according to requirements of Application. In the proposed paper I am using sorting algorithm to encrypt plain text into cipher text at the sender and at the receiver also sorting algorithm is used to convert cipher text into plain text. At the sender side I am using plain text and index array, which stores the indices of characters of plain text. In KNEnrypt() algorithm, plain text is sorted in alphabetical order and the indices of characters of plain text with in index array are also sorted in that order to form cipher text. To the receiver cipher text and index array are sent. At the receiver KNDecrypt() algorithm uses index array, which contains indices of sorted plain text characters, is sorted in increasing order and characters of cipher text are also sorted in the same order to form plain text. In the proposed paper, I am using sorting technique at the sender to encrypt plain text into cipher text and at the receiver, sorting technique is used to decrypt cipher text into plain text. II. ANALYSIS AND DESIGN OF PROPOSED ALGORITHM The proposed KareemNaaz (KN) Encryption and Decryption using Sorting Algorithms converts plain text of n characters into cipher text of n characters after Encryption and converts cipher text of n characters into plain text of n characters after Decryption. The proposed Encryption Algorithm sorts all the characters in Alphabetical Order and indices of input plain text in that order to make it as cipher text. The proposed Decryption Algorithm sorts all the indices in Increasing Order and characters of cipher text in that order to make it as plain text. The proposed Encryption Algorithm sort s characters of Page 30
2 input plain text in Alphabetical Order, and the indices of characters are also sorted to form cipher text. The proposed Decryption Algorithm sorts indices of cipher text in Increasing Order and characters of cipher text are also sorted to form plain text. Fig 2.1 shows the tasks of Encryption and Decryption Algorithms using Sorting. Fig 2.1 Encryption and Decryption using Sorting Fig 2.2 shows the characters and indices of input Plain Text, which consists of 26 characters starting from index 0 to index 25. Fig 2.2 Plain Text with 26 characters Fig 2.3 shows the encrypted cipher text, which consists of 26 characters of plain text sorted in Alphabetical order and indices of plain text characters also sorted in that order to form cipher text. Fig 2.3 Cipher Text with 26 Sorted Characters and Indices (Encryption) Fig 2.4 shows the decrypted plain text, which consists of indices of characters of cipher text from 0 to 25, which are sorted in increasing order and characters of cipher text are also sorted in that order to form plain text. Fig 2.4 Plain Text with 26 Sorted Indices and Characters (Decryption) Algorithm 2.1 swaps the two given elements a and b. This algorithm is repeatedly called by KNEncrypt() and KNDecrypt() Algorithms to swap characters of plain text, characters of cipher text, indices of plain text and indices of cipher text. Algorithm Swap(a,b) { // a and b are elements which are to be swapped temp=a; a=b; b=temp; I N D I A I S M Y C O U N T R Y A L L I N D I A N S A A A C D D I I I I I L L M N N N N O R S S T U Y Y I N D I A I S M Y C O U N T R Y A L L I N D I A N S Algorithm 2.1 swaps two indices or characters of text: The time taken by swap algorithm is 3 units, since it consists of 3 assignment statements. Page 31
3 Algorithm 2.2 is used to convert plain text of n characters into cipher text of n characters. This algorithm takes plain text of n characters, index array which contains indices of plain text characters as input. It uses the concept of Insertion sort to sort all the plain text characters and indices of characters of plain text. Outer for loop repeats from first character to last character of plain text, inner for loop repeats from current character of text to first character of text in reverse order. If the current character is smaller than the previous character then current character is swapped with previous character and index of current character is also swapped with the index of previous character. This process continues until all the characters of plain text are alphabetically sorted and indices of plain text characters are also sorted in that order to form cipher text. The proposed KNEncrypt Algorithm is as follows: Algorithm KNEncrypt(plain, n,index) { // plain is the input text with n characters // index is an integer array which contains indices of characters of input text for i=0 to n-1 step 1 do { // loop repeats from first character of text to last character of text for j=i to 1 step -1 do { // loop repeats from current character of text to first character of text if (plain[j] < plain[j-1]) then { // if current character of text is smaller than previous character swap(plain[j],plain[j-1]); // swap current and previous characters of input text swap(index[j],index[j-1]); // swap indices of current and previous characters of input text else break; // if current character of text is greater or equal to previous character cipher=plain; // make the modified input plain text as cipher text return cipher; // return cipher text Algorithm 2.2 Encryption of plain text using Sorting: In Algorithm 2.2, Outer for loop repeats n times and for I iteration of outer for loop, inner for loop repeats 1 time, for II iteration of outer for loop, inner for loop repeats 2 times. In the same way for n th iteration of outer for loop, inner for loop repeats n times. So the overall time taken by KNEncrypt() algorithm is as follows: T(n)= n T(n)= n(n+1)/2 = (n 2 + n)/2 = n 2 T(n)=O(n 2 ) The time taken by KNEncrypt() Algorithm can also be reduced by using efficient sorting algorithm to sort characters of plain text in Alphabetical order, indices of characters in that order. The proposed algorithm uses Insertion Sort technique to sort characters and indices of plain text. Algorithm 2.3 is used to convert cipher text of n characters into plain text of n characters. This algorithm takes cipher text of n characters, index array which contains indices of cipher text characters as input. It uses the concept of Insertion sort to sort all the cipher text characters and indices of characters of cipher text. Outer for loop repeats from first character to last character of cipher text, inner for loop repeats from current character of text to first character of text in reverse order. If the index of current character is smaller than the index of previous character then index of current character is swapped with index of previous character and current character is also swapped with previous character. This process continues until all the indices of cipher text are sorted in increasing order and cipher text characters are also sorted in that order to form plain text. Page 32
4 The proposed KNDecrypt Algorithm is as follows: Algorithm KNDecrypt(cipher, n,index) { // cipher is the cipher text with n characters obtained //after Encryption. // index is an integer array, which contains indices of characters of cipher text. for i=0 to n-1 step 1 do { // loop repeats from first character to last character of cipher text. for j=i to 1 step -1 do { // loop repeats from current character to first character of cipher text. if (index[j] < index[j-1]) then {if index of current character is smaller than index of previous //character of cipher text swap(cipher[j],cipher[j-1]); // swap current and previous characters of cipher text swap(index[j],index[j-1]);// swap indices of current and previous characters of cipher text else break; // if index of current character is greater or equal to index of previous character of //cipher text. plain=cipher; // make modified cipher text as plain text return plain; // return plain text Algorithm 2.3 Decryption of cipher text using Sorting: In Algorithm 2.3, Outer for loop repeats n times and for I iteration of outer for loop, inner for loop repeats 1 time, for II iteration of outer for loop, inner for loop repeats 2 times. In the same way for n th iteration of outer for loop, inner for loop repeats n times. So the overall time taken by KNDecrypt() algorithm is as follows: T(n)= n T(n)= n(n+1)/2 = (n 2 + n)/2 = n 2 T(n)=O(n 2 ) The time taken by KNDecrypt() Algorithm can also be reduced by using efficient sorting algorithm to sort indices of cipher text in increasing order, cipher characters in that order. The proposed algorithm uses Insertion Sort technique to sort indices and characters of cipher text. III. IMPLEMENTATION OF PROPOSED ALGORITHM USING C The Proposed Algorithm is implemented by using C Programming Language, which is a robust, structure oriented programming language, which provides different concepts like functions, pointers, structures, arrays and so on to solve complex problems. /* Program to implement Encryption and Decryption of text using Sorting*/ # include <stdio.h> # include <conio.h> char input[50]; // input array to store plain text with n characters int index[50]; // index array to store indices of characters of plain text int n; // number of characters of plain text void CharSwap(char *a,char *b) char temp=*a; { // function to swap two characters of text Page 33
5 *a=*b; *b=temp; void IntSwap(int *a,int *b) { // function to swap two indices of characters of text int temp=*a; *a=*b; *b=temp; void KNEncrypt() { // Encryption of plain text by sorting characters and indices of plain text int i,j; for(i=0;i<n;i++) // outer loop repeats from first character to last character of plain text for(j=i;j>0;j--) // inner loop repeats from current character to first character of plain text if(input[j]<input[j-1]) { // if current character is smaller than previous character of plain text CharSwap(&input[j],&input[j-1]); // swap current and previous characters of plain text IntSwap(&index[j],&index[j-1]); // swap indices of current and previous characters of text else // if current character is greater or equal to previous character of text break; // stop comparing characters of plain text void KNDecrypt(){ //Decryption of cipher text by sorting indices and characters of cipher text int i,j; for(i=0;i<n;i++)// loop repeats from first character to last character of cipher text for(j=i;j>0;j--) // loop repeats from current character to previous character of cipher text if(index[j]<index[j-1]) { // if index of current character is smaller than index of previous //character of cipher text IntSwap(&index[j],&index[j-1]); // swap indices of current and previous characters of cipher CharSwap(&input[j],&input[j-1]);//swap current and previous characters of cipher text else // if index of current character is greater or equal to index of previous character of cipher break; // stop comparing characters of cipher text void main() { int i; clrscr(); printf("\nimplementation of KareemNaaz Encrytion Decryption Algorithm"); printf("\nenter plain text:\n"); Page 34
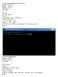
6 scanf("%s",input); // read plain text from key board n=strlen(input); // n is the length of plain text for(i=0;i<n;i++) // placing indices of plain text into index array index[i]=i; KNEncrypt(); // Encrypt plain text of n characters to cipher text printf("\nafter Encryption Cipher Text:\n %s",input); KNDecrypt(); //Decrypt cipher text of n characters to plain text printf("\nafter Decryption Plain Text:\n %s",input); getch(); Program 3.1 To Encrypt and Decrypt text by using Sorting: IV. TESTING OF PROPOSED ALGORITHM Different Test Cases are considered to test the result of Program 3.1. The following screen shot, shows the result of proposed algorithm. Consider the following Test Case in which plain text consists of 26 characters indiaismycountryallindians starting from index 0 to index 25. After Encryption, cipher text is aaacddiiiiillmnnnnorsstuyy. After Decryption, plain text is indiaismycountryallindians. Fig 4.1 shows the encrypted cipher text and decrypted plain text. Fig 4.1 output screen shot of program 3.1 Page 35
7 V. CONCLUSION I conclude that In the proposed KareemNaaz (KN) Encryption and Decryption using Sorting paper, KNEncrypt() algorithm takes plain text of n characters as input, sort all the characters of plain text in alphabetical order and also sorts the indices of plain text characters in that order to form cipher text of n characters. Proposed KNDecrypt() algorithm will take cipher text of n characters as input, sort all the indices of cipher text in increasing order and also sorts characters of cipher text in that order to form plain text of n characters. In both KNEncrypt() and KNDecrypt() algorithm, I am using Insertion Sort technique to sort characters of plain text in alphabetical order, indices of cipher text in increasing order, characters of cipher text and indices of plain text. To reduce complexity some other sorting algorithms can also be preferred. REFERENCES [1] Aho, Alfred V. and Jeffrey D. Ullman [1983]. Data Structures and Algorithms. AddisonWesley,Reading, Massachusetts. [2] Cormen, Thomas H., Charles E. Leiserson and Ronald L. Rivest [1990]. Introduction to Algorithms. McGraw-Hill, New York. [3] Knuth, Donald. E. [1998]. The Art of Computer Programming, Volume 3, Sorting and Searching. Addison- Wesley, Reading, Massachusetts. Page 36
KareemNaaz Matrix Divide and Sorting Algorithm
 KareemNaaz Matrix Divide and Sorting Algorithm Shaik Kareem Basha* Department of Computer Science and Engineering, HITAM, India Review Article Received date: 18/11/2016 Accepted date: 13/12/2016 Published
KareemNaaz Matrix Divide and Sorting Algorithm Shaik Kareem Basha* Department of Computer Science and Engineering, HITAM, India Review Article Received date: 18/11/2016 Accepted date: 13/12/2016 Published
Keywords queue, left sub list, right sub list, output array list, output linked list, input array list, divide list, sort, combine
 Volume 4, Issue 12, December 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Divide and
Volume 4, Issue 12, December 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Divide and
IP Packet Filtering using Hash Table for Dedicated Real Time IP Filter
 I.J. Wireless and Microwave Technologies, 2017, 1, 24-29 Published Online January 2017 in MECS(http://www.mecs-press.net) DOI: 10.5815/ijwmt.2017.01.03 Available online at http://www.mecs-press.net/ijwmt
I.J. Wireless and Microwave Technologies, 2017, 1, 24-29 Published Online January 2017 in MECS(http://www.mecs-press.net) DOI: 10.5815/ijwmt.2017.01.03 Available online at http://www.mecs-press.net/ijwmt
CS 157: Assignment 5
 Problem : Printing Neatly CS 157: Assignment 5 Douglas R. Lanman 4 April 006 In a word processor or in L A TEX, one routinely encounters the pretty printing problem. That is, how does one transform text
Problem : Printing Neatly CS 157: Assignment 5 Douglas R. Lanman 4 April 006 In a word processor or in L A TEX, one routinely encounters the pretty printing problem. That is, how does one transform text
Downloaded from
 Unit I Chapter -1 PROGRAMMING IN C++ Review: C++ covered in C++ Q1. What are the limitations of Procedural Programming? Ans. Limitation of Procedural Programming Paradigm 1. Emphasis on algorithm rather
Unit I Chapter -1 PROGRAMMING IN C++ Review: C++ covered in C++ Q1. What are the limitations of Procedural Programming? Ans. Limitation of Procedural Programming Paradigm 1. Emphasis on algorithm rather
Data Structures and Algorithms
 Data Structures and Algorithms Luciano Bononi Computer Science Engineering University of Bologna bononi@cs.unibo.it http://www.cs.unibo.it/~bononi/ Slide credits: these slides have been translated from
Data Structures and Algorithms Luciano Bononi Computer Science Engineering University of Bologna bononi@cs.unibo.it http://www.cs.unibo.it/~bononi/ Slide credits: these slides have been translated from
Outline. Computer Science 331. Desirable Properties of Hash Functions. What is a Hash Function? Hash Functions. Mike Jacobson.
 Outline Computer Science 331 Mike Jacobson Department of Computer Science University of Calgary Lecture #20 1 Definition Desirable Property: Easily Computed 2 3 Universal Hashing 4 References Mike Jacobson
Outline Computer Science 331 Mike Jacobson Department of Computer Science University of Calgary Lecture #20 1 Definition Desirable Property: Easily Computed 2 3 Universal Hashing 4 References Mike Jacobson
Smart Sort and its Analysis
 Smart Sort and its Analysis Varun Jain and Suneeta Agarwal Department of Computer Science and Engineering, Motilal Nehru National Institute of Technology, Allahabad-211004, Uttar Pradesh, India. varun_jain22@yahoo.com,
Smart Sort and its Analysis Varun Jain and Suneeta Agarwal Department of Computer Science and Engineering, Motilal Nehru National Institute of Technology, Allahabad-211004, Uttar Pradesh, India. varun_jain22@yahoo.com,
CSE101-lec#19. Array searching and sorting techniques. Created By: Amanpreet Kaur & Sanjeev Kumar SME (CSE) LPU. LPU CSE101 C Programming
 CSE101-lec#19 Array searching and sorting techniques Created By: Amanpreet Kaur & Sanjeev Kumar SME (CSE) LPU Outline Introduction Linear search Binary search Bubble sort Introduction The process of finding
CSE101-lec#19 Array searching and sorting techniques Created By: Amanpreet Kaur & Sanjeev Kumar SME (CSE) LPU Outline Introduction Linear search Binary search Bubble sort Introduction The process of finding
Elementary Sorting Algorithms
 Elementary Sorting Algorithms COMP1927 16x1 Sedgewick Chapter 6 WARM UP EXERCISE: HANDSHAKE PROBLEM In a room of n people, how many different handshakes are possible? 0 + 1 + 2 + + (n-1) Using Maths formula:
Elementary Sorting Algorithms COMP1927 16x1 Sedgewick Chapter 6 WARM UP EXERCISE: HANDSHAKE PROBLEM In a room of n people, how many different handshakes are possible? 0 + 1 + 2 + + (n-1) Using Maths formula:
D.Abhyankar 1, M.Ingle 2. -id: 2 M.Ingle, School of Computer Science, D.A. University, Indore M.P.
 A Novel Mergesort D.Abhyankar 1, M.Ingle 2 1 D. Abhyankar, School of Computer Science, D.A. University, Indore M.P. India Email-id: deepak.scsit@gmail.com 2 M.Ingle, School of Computer Science, D.A. University,
A Novel Mergesort D.Abhyankar 1, M.Ingle 2 1 D. Abhyankar, School of Computer Science, D.A. University, Indore M.P. India Email-id: deepak.scsit@gmail.com 2 M.Ingle, School of Computer Science, D.A. University,
Q 1. Attempt any TEN of the following:
 Subject Code: 17212 Model Answer Page No: 1 / 26 Important Instructions to examiners: 1) The answers should be examined by key words and not as word-to-word as given in the model answer scheme. 2) The
Subject Code: 17212 Model Answer Page No: 1 / 26 Important Instructions to examiners: 1) The answers should be examined by key words and not as word-to-word as given in the model answer scheme. 2) The
CS3110 Spring 2017 Lecture 18: Binary Search Trees
 CS3110 Spring 2017 Lecture 18: Binary Search Trees Robert Constable Date for Due Date PS5 Out on April 10 April 24 PS6 Out on April 24 May 8 (day of last lecture) 1 Summarizing Computational Geometry In
CS3110 Spring 2017 Lecture 18: Binary Search Trees Robert Constable Date for Due Date PS5 Out on April 10 April 24 PS6 Out on April 24 May 8 (day of last lecture) 1 Summarizing Computational Geometry In
Position Sort. Anuj Kumar Developer PINGA Solution Pvt. Ltd. Noida, India ABSTRACT. Keywords 1. INTRODUCTION 2. METHODS AND MATERIALS
 Position Sort International Journal of Computer Applications (0975 8887) Anuj Kumar Developer PINGA Solution Pvt. Ltd. Noida, India Mamta Former IT Faculty Ghaziabad, India ABSTRACT Computer science has
Position Sort International Journal of Computer Applications (0975 8887) Anuj Kumar Developer PINGA Solution Pvt. Ltd. Noida, India Mamta Former IT Faculty Ghaziabad, India ABSTRACT Computer science has
Keywords Comparisons, Insertion Sort, Selection Sort, Bubble Sort, Quick Sort, Merge Sort, Time Complexity.
 Volume 4, Issue 2, February 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com A Comparative
Volume 4, Issue 2, February 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com A Comparative
Using Templates to Introduce Time Efficiency Analysis in an Algorithms Course
 Using Templates to Introduce Time Efficiency Analysis in an Algorithms Course Irena Pevac Department of Computer Science Central Connecticut State University, New Britain, CT, USA Abstract: We propose
Using Templates to Introduce Time Efficiency Analysis in an Algorithms Course Irena Pevac Department of Computer Science Central Connecticut State University, New Britain, CT, USA Abstract: We propose
A Block Cipher Basing Upon a Revisit to the Feistel Approach and the Modular Arithmetic Inverse of a Key Matrix
 IAENG International Journal of Computer Science, 32:4, IJCS_32_4_ A Block Cipher Basing Upon a Revisit to the Feistel Approach and the Modular Arithmetic Inverse of a Key Matrix S. Udaya Kumar V. U. K.
IAENG International Journal of Computer Science, 32:4, IJCS_32_4_ A Block Cipher Basing Upon a Revisit to the Feistel Approach and the Modular Arithmetic Inverse of a Key Matrix S. Udaya Kumar V. U. K.
arxiv: v3 [cs.ds] 18 Apr 2011
![arxiv: v3 [cs.ds] 18 Apr 2011 arxiv: v3 [cs.ds] 18 Apr 2011](/thumbs/84/89362283.jpg) A tight bound on the worst-case number of comparisons for Floyd s heap construction algorithm Ioannis K. Paparrizos School of Computer and Communication Sciences Ècole Polytechnique Fèdèrale de Lausanne
A tight bound on the worst-case number of comparisons for Floyd s heap construction algorithm Ioannis K. Paparrizos School of Computer and Communication Sciences Ècole Polytechnique Fèdèrale de Lausanne
Loops / Repetition Statements. There are three loop constructs in C. Example 2: Grade of several students. Example 1: Fixing Bad Keyboard Input
 Loops / Repetition Statements Repetition s allow us to execute a multiple times Often they are referred to as loops C has three kinds of repetition s: the while loop the for loop the do loop The programmer
Loops / Repetition Statements Repetition s allow us to execute a multiple times Often they are referred to as loops C has three kinds of repetition s: the while loop the for loop the do loop The programmer
VISUAL BASIC COLLECTIONS
 VISUAL BASIC COLLECTIONS AND HASH TABLES Tom Niemann Preface Hash tables offer a method for quickly storing and accessing data based on a key value. When you access a Visual Basic collection using a key,
VISUAL BASIC COLLECTIONS AND HASH TABLES Tom Niemann Preface Hash tables offer a method for quickly storing and accessing data based on a key value. When you access a Visual Basic collection using a key,
Lecture C8: Trees part II 3 C 2 A 4 D. Response to 'Muddiest Part of the Lecture Cards' (16 respondents)
 Lecture C8: Trees part II Response to 'Muddiest Part of the Lecture Cards' (16 respondents) 1) Is the tree in the Depth first example actually a tree? (It has 6 vertices and 8 edges a tree has N verticed
Lecture C8: Trees part II Response to 'Muddiest Part of the Lecture Cards' (16 respondents) 1) Is the tree in the Depth first example actually a tree? (It has 6 vertices and 8 edges a tree has N verticed
CS 345. Functions. Vitaly Shmatikov. slide 1
 CS 345 Functions Vitaly Shmatikov slide 1 Reading Assignment Mitchell, Chapter 7 C Reference Manual, Chapters 4 and 9 slide 2 Procedural Abstraction Can be overloaded (e.g., binary +) Procedure is a named
CS 345 Functions Vitaly Shmatikov slide 1 Reading Assignment Mitchell, Chapter 7 C Reference Manual, Chapters 4 and 9 slide 2 Procedural Abstraction Can be overloaded (e.g., binary +) Procedure is a named
Loops / Repetition Statements
 Loops / Repetition Statements Repetition statements allow us to execute a statement multiple times Often they are referred to as loops C has three kinds of repetition statements: the while loop the for
Loops / Repetition Statements Repetition statements allow us to execute a statement multiple times Often they are referred to as loops C has three kinds of repetition statements: the while loop the for
Problem Solving and 'C' Programming
 Problem Solving and 'C' Programming Targeted at: Entry Level Trainees Session 05: Selection and Control Structures 2007, Cognizant Technology Solutions. All Rights Reserved. The information contained herein
Problem Solving and 'C' Programming Targeted at: Entry Level Trainees Session 05: Selection and Control Structures 2007, Cognizant Technology Solutions. All Rights Reserved. The information contained herein
Quicksort Using Median of Medians as Pivot
 International Journal of Science and Engineering Investigations vol. 5, issue 56, September 216 ISSN: 2251-8843 Quicksort Using Median of Medians as Pivot Aviral Khattar HCL Technologies (aviral92@gmail.com)
International Journal of Science and Engineering Investigations vol. 5, issue 56, September 216 ISSN: 2251-8843 Quicksort Using Median of Medians as Pivot Aviral Khattar HCL Technologies (aviral92@gmail.com)
Decision Sort and its Parallel Formulation
 Decision Sort and its Parallel Formulation Udayan Khurana Computer Science and Engineering Thapar Institute of Engineering and Technology Patiala, Punjab, India- 147004 udayankhurana@gmail.com Abstract
Decision Sort and its Parallel Formulation Udayan Khurana Computer Science and Engineering Thapar Institute of Engineering and Technology Patiala, Punjab, India- 147004 udayankhurana@gmail.com Abstract
Agenda. The main body and cout. Fundamental data types. Declarations and definitions. Control structures
 The main body and cout Agenda 1 Fundamental data types Declarations and definitions Control structures References, pass-by-value vs pass-by-references The main body and cout 2 C++ IS AN OO EXTENSION OF
The main body and cout Agenda 1 Fundamental data types Declarations and definitions Control structures References, pass-by-value vs pass-by-references The main body and cout 2 C++ IS AN OO EXTENSION OF
A Class of Non Invertible Matrices in GF (2) for Practical One Way Hash Algorithm
 A Class of Non Invertible Matrices in GF (2) for Practical One Way Hash Algorithm Artan Berisha Faculty of Mathematical and Natural Scienes University of Prishtina, Kosovo Behar Baxhaku Faculty of Mathematical
A Class of Non Invertible Matrices in GF (2) for Practical One Way Hash Algorithm Artan Berisha Faculty of Mathematical and Natural Scienes University of Prishtina, Kosovo Behar Baxhaku Faculty of Mathematical
LECTURE 03 LINKED LIST
 DATA STRUCTURES AND ALGORITHMS LECTURE 03 LINKED LIST IMRAN IHSAN ASSISTANT PROFESSOR AIR UNIVERSITY, ISLAMABAD LINKED LISTS DEFINITION A linked list is a data structure where each object is stored in
DATA STRUCTURES AND ALGORITHMS LECTURE 03 LINKED LIST IMRAN IHSAN ASSISTANT PROFESSOR AIR UNIVERSITY, ISLAMABAD LINKED LISTS DEFINITION A linked list is a data structure where each object is stored in
Software Analysis. Asymptotic Performance Analysis
 Software Analysis Performance Analysis Presenter: Jonathan Aldrich Performance Analysis Software Analysis 1 Asymptotic Performance Analysis How do we compare algorithm performance? Abstract away low-level
Software Analysis Performance Analysis Presenter: Jonathan Aldrich Performance Analysis Software Analysis 1 Asymptotic Performance Analysis How do we compare algorithm performance? Abstract away low-level
CSCI2100B Data Structures Introduction
 https://www.cse.cuhk.edu.hk/irwin.king/teaching/csci2100b/2013 CSCI2100B Data Structures Introduction Irwin King king@cse.cuhk.edu.hk http://www.cse.cuhk.edu.hk/~king Department of Computer Science & Engineering
https://www.cse.cuhk.edu.hk/irwin.king/teaching/csci2100b/2013 CSCI2100B Data Structures Introduction Irwin King king@cse.cuhk.edu.hk http://www.cse.cuhk.edu.hk/~king Department of Computer Science & Engineering
Subject: Fundamental of Computer Programming 2068
 Subject: Fundamental of Computer Programming 2068 1 Write an algorithm and flowchart to determine whether a given integer is odd or even and explain it. Algorithm Step 1: Start Step 2: Read a Step 3: Find
Subject: Fundamental of Computer Programming 2068 1 Write an algorithm and flowchart to determine whether a given integer is odd or even and explain it. Algorithm Step 1: Start Step 2: Read a Step 3: Find
DC104 DATA STRUCTURE JUNE Q.2 a. If you are using C language to implement the heterogeneous linked list, what pointer type will you use?
 Q.2 a. If you are using C language to implement the heterogeneous linked list, what pointer type will you use? The heterogeneous linked list contains different data types in its nodes and we need a link
Q.2 a. If you are using C language to implement the heterogeneous linked list, what pointer type will you use? The heterogeneous linked list contains different data types in its nodes and we need a link
Aman Kumar. Department of Computer Science & Engineering, IIT Kanpur 3 November, 2014
 A Comparison Based Analysis of Four Different Types of Sorting Algorithms in Data Structures with Their Performances Nidhi Imran Simarjeet International Journal of Advanced Research in Computer Science
A Comparison Based Analysis of Four Different Types of Sorting Algorithms in Data Structures with Their Performances Nidhi Imran Simarjeet International Journal of Advanced Research in Computer Science
PROGRAMMING IN C LAB MANUAL FOR DIPLOMA IN ECE/EEE
 PROGRAMMING IN C LAB MANUAL FOR DIPLOMA IN ECE/EEE 1. Write a C program to perform addition, subtraction, multiplication and division of two numbers. # include # include int a, b,sum,
PROGRAMMING IN C LAB MANUAL FOR DIPLOMA IN ECE/EEE 1. Write a C program to perform addition, subtraction, multiplication and division of two numbers. # include # include int a, b,sum,
6/12/2013. Introduction to Algorithms (2 nd edition) Overview. The Sorting Problem. Chapter 2: Getting Started. by Cormen, Leiserson, Rivest & Stein
 Introduction to Algorithms (2 nd edition) by Cormen, Leiserson, Rivest & Stein Chapter 2: Getting Started (slides enhanced by N. Adlai A. DePano) Overview Aims to familiarize us with framework used throughout
Introduction to Algorithms (2 nd edition) by Cormen, Leiserson, Rivest & Stein Chapter 2: Getting Started (slides enhanced by N. Adlai A. DePano) Overview Aims to familiarize us with framework used throughout
UNIT 3: ANALYSIS OF SIMPLE ALGORITHMS
 UNIT 3: ANALYSIS OF SIMPLE ALGORITHMS Analysis of simple Algorithms Structure Page Nos. 3.0 Introduction 85 3.1 Objective 85 3.2 Euclid Algorithm for GCD 86 3.3 Horner s Rule for Polynomial Evaluation
UNIT 3: ANALYSIS OF SIMPLE ALGORITHMS Analysis of simple Algorithms Structure Page Nos. 3.0 Introduction 85 3.1 Objective 85 3.2 Euclid Algorithm for GCD 86 3.3 Horner s Rule for Polynomial Evaluation
Index Sort. Abstract. Keywords: Index Sort, Binary Search, Position.
 Index Sort Hari Krishna Gurram M.Tech (CS), Ucek, JNTU Kakinada. Gera Jaideep M.Tech(CS), Ucek, JNTU Kakinada. harikrishna553@gmail.com jaideep.gera@gmail.com Abstract One of the fundamental issues in
Index Sort Hari Krishna Gurram M.Tech (CS), Ucek, JNTU Kakinada. Gera Jaideep M.Tech(CS), Ucek, JNTU Kakinada. harikrishna553@gmail.com jaideep.gera@gmail.com Abstract One of the fundamental issues in
arxiv: v1 [cs.ds] 3 Oct 2017
![arxiv: v1 [cs.ds] 3 Oct 2017 arxiv: v1 [cs.ds] 3 Oct 2017](/thumbs/87/95842935.jpg) ORDERED DAGS: HYPERCUBESORT MIKHAIL GUDIM arxiv:70.00v [cs.ds] Oct 07 Abstract. We generalize the insertion into a binary heap to any directed acyclic graph (DAG) with one source vertex. This lets us formulate
ORDERED DAGS: HYPERCUBESORT MIKHAIL GUDIM arxiv:70.00v [cs.ds] Oct 07 Abstract. We generalize the insertion into a binary heap to any directed acyclic graph (DAG) with one source vertex. This lets us formulate
Parallel Algorithms: The Minimum Spanning Tree And Minimum Steiner Tree Problems
 Parallel Algorithms: The Minimum Spanning Tree And Minimum Steiner Tree Problems Katie Zrncic COMP 512 Spring 2005 Introduction Parallel computing is one of the most exciting technologies to achieve prominence
Parallel Algorithms: The Minimum Spanning Tree And Minimum Steiner Tree Problems Katie Zrncic COMP 512 Spring 2005 Introduction Parallel computing is one of the most exciting technologies to achieve prominence
'C' Programming Language
 F.Y. Diploma : Sem. II [DE/EJ/ET/EN/EX] 'C' Programming Language Time: 3 Hrs.] Prelim Question Paper Solution [Marks : 70 Q.1 Attempt any FIVE of the following : [10] Q.1(a) Define pointer. Write syntax
F.Y. Diploma : Sem. II [DE/EJ/ET/EN/EX] 'C' Programming Language Time: 3 Hrs.] Prelim Question Paper Solution [Marks : 70 Q.1 Attempt any FIVE of the following : [10] Q.1(a) Define pointer. Write syntax
Computer Science Foundation Exam
 Computer Science Foundation Exam December 18, 015 Section I B COMPUTER SCIENCE NO books, notes, or calculators may be used, and you must work entirely on your own. SOLUTION Question # Max Pts Category
Computer Science Foundation Exam December 18, 015 Section I B COMPUTER SCIENCE NO books, notes, or calculators may be used, and you must work entirely on your own. SOLUTION Question # Max Pts Category
Pointers. Mr. Ovass Shafi (Assistant Professor) Department of Computer Applications
 Pointers Introduction: A variable is a named memory location that holds some value. Each variable has some address associated with it. Till now we only worked on the values stored in the variables and
Pointers Introduction: A variable is a named memory location that holds some value. Each variable has some address associated with it. Till now we only worked on the values stored in the variables and
Programming Problems 21st Annual Computer Science Programming Contest
 Programming Problems 21st Annual Computer Science Programming Contest Department of Mathematics and Computer Science Western Carolina University 23 March 2010 Problem One: Palindrome Finder A palindrome
Programming Problems 21st Annual Computer Science Programming Contest Department of Mathematics and Computer Science Western Carolina University 23 March 2010 Problem One: Palindrome Finder A palindrome
Unit 3 Decision making, Looping and Arrays
 Unit 3 Decision making, Looping and Arrays Decision Making During programming, we have a number of situations where we may have to change the order of execution of statements based on certain conditions.
Unit 3 Decision making, Looping and Arrays Decision Making During programming, we have a number of situations where we may have to change the order of execution of statements based on certain conditions.
Computer Science Foundation Exam
 Computer Science Foundation Exam May 19, 2018 Section I A DATA STRUCTURES SOLUTION NO books, notes, or calculators may be used, and you must work entirely on your own. Name: UCFID: NID: Question # Max
Computer Science Foundation Exam May 19, 2018 Section I A DATA STRUCTURES SOLUTION NO books, notes, or calculators may be used, and you must work entirely on your own. Name: UCFID: NID: Question # Max
International Journal of Scientific & Engineering Research, Volume 4, Issue 7, July ISSN
 International Journal of Scientific & Engineering Research, Volume 4, Issue 7, July-201 971 Comparative Performance Analysis Of Sorting Algorithms Abhinav Yadav, Dr. Sanjeev Bansal Abstract Sorting Algorithms
International Journal of Scientific & Engineering Research, Volume 4, Issue 7, July-201 971 Comparative Performance Analysis Of Sorting Algorithms Abhinav Yadav, Dr. Sanjeev Bansal Abstract Sorting Algorithms
UNIVERSITY OF SWAZILAND
 UNIVERSITY OF SWAZILAND FACULTY OF SCIENCE DEPARTMENT OF ELECTRICAL &ELECTRONIC ENGINEERING PROGRAMMING TECHNIQUES I COURSE CODE - EE271 MAIN EXAMINATION DECEMBER 2011 DURATION OF THE EXAMINATION - 3 HOURS
UNIVERSITY OF SWAZILAND FACULTY OF SCIENCE DEPARTMENT OF ELECTRICAL &ELECTRONIC ENGINEERING PROGRAMMING TECHNIQUES I COURSE CODE - EE271 MAIN EXAMINATION DECEMBER 2011 DURATION OF THE EXAMINATION - 3 HOURS
arxiv: v3 [cs.ds] 3 Apr 2018
![arxiv: v3 [cs.ds] 3 Apr 2018 arxiv: v3 [cs.ds] 3 Apr 2018](/thumbs/87/96355553.jpg) arxiv:1711.07746v3 [cs.ds] 3 Apr 2018 The Hidden Binary Search Tree: A Balanced Rotation-Free Search Tree in the AVL RAM Model Saulo Queiroz Email: sauloqueiroz@utfpr.edu.br Academic Department of Informatics
arxiv:1711.07746v3 [cs.ds] 3 Apr 2018 The Hidden Binary Search Tree: A Balanced Rotation-Free Search Tree in the AVL RAM Model Saulo Queiroz Email: sauloqueiroz@utfpr.edu.br Academic Department of Informatics
3/12/2018. Structures. Programming in C++ Sequential Branching Repeating. Loops (Repetition)
 Structures Programming in C++ Sequential Branching Repeating Loops (Repetition) 2 1 Loops Repetition is referred to the ability of repeating a statement or a set of statements as many times this is necessary.
Structures Programming in C++ Sequential Branching Repeating Loops (Repetition) 2 1 Loops Repetition is referred to the ability of repeating a statement or a set of statements as many times this is necessary.
ARC Sort: Enhanced and Time Efficient Sorting Algorithm
 International Journal of Applied Information Systems (IJAIS) ISSN : 9-088 Volume 7., April 01 www.ijais.org ARC : Enhanced and Time Efficient ing Algorithm Ankit R. Chadha Electronics & Telecommunication
International Journal of Applied Information Systems (IJAIS) ISSN : 9-088 Volume 7., April 01 www.ijais.org ARC : Enhanced and Time Efficient ing Algorithm Ankit R. Chadha Electronics & Telecommunication
F.Y. Diploma : Sem. II [CO/CD/CM/CW/IF] Programming in C
![F.Y. Diploma : Sem. II [CO/CD/CM/CW/IF] Programming in C F.Y. Diploma : Sem. II [CO/CD/CM/CW/IF] Programming in C](/thumbs/78/77846471.jpg) F.Y. Diploma : Sem. II [CO/CD/CM/CW/IF] Programming in C Time : 3 Hrs.] Prelim Question Paper Solution [Marks : 70 Q.1 Attempt any FIVE of the following : [10] Q.1 (a) List any four relational operators.
F.Y. Diploma : Sem. II [CO/CD/CM/CW/IF] Programming in C Time : 3 Hrs.] Prelim Question Paper Solution [Marks : 70 Q.1 Attempt any FIVE of the following : [10] Q.1 (a) List any four relational operators.
4. SEARCHING AND SORTING LINEAR SEARCH
 4. SEARCHING AND SORTING SEARCHING Searching and sorting are fundamental operations in computer science. Searching refers to the operation of finding the location of a given item in a collection of items.
4. SEARCHING AND SORTING SEARCHING Searching and sorting are fundamental operations in computer science. Searching refers to the operation of finding the location of a given item in a collection of items.
Chapter Contents. An Introduction to Sorting. Selection Sort. Selection Sort. Selection Sort. Iterative Selection Sort. Chapter 9
 An Introduction to Sorting Chapter 9 Chapter Contents Iterative Recursive The Efficiency of Iterative Recursive The Efficiency of of a Chain of Linked Nodes The Java Code The Efficiency of Comparing the
An Introduction to Sorting Chapter 9 Chapter Contents Iterative Recursive The Efficiency of Iterative Recursive The Efficiency of of a Chain of Linked Nodes The Java Code The Efficiency of Comparing the
DELHI PUBLIC SCHOOL TAPI
 Loops Chapter-1 There may be a situation, when you need to execute a block of code several number of times. In general, statements are executed sequentially: The first statement in a function is executed
Loops Chapter-1 There may be a situation, when you need to execute a block of code several number of times. In general, statements are executed sequentially: The first statement in a function is executed
Computers Programming Course 7. Iulian Năstac
 Computers Programming Course 7 Iulian Năstac Recap from previous course Operators in C Programming languages typically support a set of operators, which differ in the calling of syntax and/or the argument
Computers Programming Course 7 Iulian Năstac Recap from previous course Operators in C Programming languages typically support a set of operators, which differ in the calling of syntax and/or the argument
Cryptanalysis of Homophonic Substitution- Transposition Cipher
 San Jose State University SJSU ScholarWorks Master's Projects Master's Theses and Graduate Research Spring 2014 Cryptanalysis of Homophonic Substitution- Transposition Cipher Jeffrey Yi Follow this and
San Jose State University SJSU ScholarWorks Master's Projects Master's Theses and Graduate Research Spring 2014 Cryptanalysis of Homophonic Substitution- Transposition Cipher Jeffrey Yi Follow this and
COMP6700/2140 Recursive Operations
 COMP6700/2140 Recursive Operations Alexei B Khorev and Josh Milthorpe Research School of Computer Science, ANU May 2017 Alexei B Khorev and Josh Milthorpe (RSCS, ANU) COMP6700/2140 Recursive Operations
COMP6700/2140 Recursive Operations Alexei B Khorev and Josh Milthorpe Research School of Computer Science, ANU May 2017 Alexei B Khorev and Josh Milthorpe (RSCS, ANU) COMP6700/2140 Recursive Operations
/* Area and circumference of a circle */ /*celsius to fahrenheit*/
 /* Area and circumference of a circle */ #include #include #define pi 3.14 int radius; float area, circum; printf("\nenter radius of the circle : "); scanf("%d",&radius); area = pi
/* Area and circumference of a circle */ #include #include #define pi 3.14 int radius; float area, circum; printf("\nenter radius of the circle : "); scanf("%d",&radius); area = pi
// CSE/CE/IT 124 JULY 2015, 2.a. algorithm to inverse the digits of a given integer. Step 1: Start Step 2: Read: NUMBER Step 3: r=0,rev=0
 // CSE/CE/IT 124 JULY 2015, 2a algorithm to inverse the digits of a given integer Step 1: Start Step 2: Read: NUMBER Step 3: r=0,rev=0 Step 4: repeat until NUMBER > 0 r=number%10; rev=rev*10+r; NUMBER=NUMBER/10;
// CSE/CE/IT 124 JULY 2015, 2a algorithm to inverse the digits of a given integer Step 1: Start Step 2: Read: NUMBER Step 3: r=0,rev=0 Step 4: repeat until NUMBER > 0 r=number%10; rev=rev*10+r; NUMBER=NUMBER/10;
Partha Sarathi Mandal
 MA 253: Data Structures Lab with OOP Tutorial 1 http://www.iitg.ernet.in/psm/indexing_ma253/y13/index.html Partha Sarathi Mandal psm@iitg.ernet.in Dept. of Mathematics, IIT Guwahati Reference Books Cormen,
MA 253: Data Structures Lab with OOP Tutorial 1 http://www.iitg.ernet.in/psm/indexing_ma253/y13/index.html Partha Sarathi Mandal psm@iitg.ernet.in Dept. of Mathematics, IIT Guwahati Reference Books Cormen,
Sorting. Bubble Sort. Selection Sort
 Sorting In this class we will consider three sorting algorithms, that is, algorithms that will take as input an array of items, and then rearrange (sort) those items in increasing order within the array.
Sorting In this class we will consider three sorting algorithms, that is, algorithms that will take as input an array of items, and then rearrange (sort) those items in increasing order within the array.
PESIT Bangalore South Campus Hosur road, 1km before Electronic City, Bengaluru -100 Department of Basic Science and Humanities
 PESIT Bangalore South Campus Hosur road, 1km before Electronic City, Bengaluru -100 Department of Basic Science and Humanities Continuous Internal Evaluation Test 2 Date: 0-10- 2017 Marks: 0 Subject &
PESIT Bangalore South Campus Hosur road, 1km before Electronic City, Bengaluru -100 Department of Basic Science and Humanities Continuous Internal Evaluation Test 2 Date: 0-10- 2017 Marks: 0 Subject &
Analysis of Algorithms Part I: Analyzing a pseudo-code
 Analysis of Algorithms Part I: Analyzing a pseudo-code Introduction Pseudo-code representation of an algorithm Analyzing algorithms Measuring the running time and memory size of an algorithm Calculating
Analysis of Algorithms Part I: Analyzing a pseudo-code Introduction Pseudo-code representation of an algorithm Analyzing algorithms Measuring the running time and memory size of an algorithm Calculating
Fundamentals of Computer Programming Using C
 CHARUTAR VIDYA MANDAL S SEMCOM Vallabh Vidyanagar Faculty Name: Ami D. Trivedi Class: FYBCA Subject: US01CBCA01 (Fundamentals of Computer Programming Using C) *UNIT 3 (Structured Programming, Library Functions
CHARUTAR VIDYA MANDAL S SEMCOM Vallabh Vidyanagar Faculty Name: Ami D. Trivedi Class: FYBCA Subject: US01CBCA01 (Fundamentals of Computer Programming Using C) *UNIT 3 (Structured Programming, Library Functions
An Application of Graph Theory in Cryptography
 Volume 119 No. 13 2018, 375-383 ISSN: 1314-3395 (on-line version) url: http://www.ijpam.eu ijpam.eu An Application of Graph Theory in Cryptography P. Amudha 1 A.C. Charles Sagayaraj 2 A.C.Shantha Sheela
Volume 119 No. 13 2018, 375-383 ISSN: 1314-3395 (on-line version) url: http://www.ijpam.eu ijpam.eu An Application of Graph Theory in Cryptography P. Amudha 1 A.C. Charles Sagayaraj 2 A.C.Shantha Sheela
Lecture Notes 14 More sorting CSS Data Structures and Object-Oriented Programming Professor Clark F. Olson
 Lecture Notes 14 More sorting CSS 501 - Data Structures and Object-Oriented Programming Professor Clark F. Olson Reading for this lecture: Carrano, Chapter 11 Merge sort Next, we will examine two recursive
Lecture Notes 14 More sorting CSS 501 - Data Structures and Object-Oriented Programming Professor Clark F. Olson Reading for this lecture: Carrano, Chapter 11 Merge sort Next, we will examine two recursive
Write a program that creates in the main function two linked lists of characters and fills them with the following values:
 Write a program that creates in the main function two linked lists of characters and fills them with the following values: The first list will have 3 nodes with the following characters: A,B, and C. The
Write a program that creates in the main function two linked lists of characters and fills them with the following values: The first list will have 3 nodes with the following characters: A,B, and C. The
Functions. Arash Rafiey. September 26, 2017
 September 26, 2017 are the basic building blocks of a C program. are the basic building blocks of a C program. A function can be defined as a set of instructions to perform a specific task. are the basic
September 26, 2017 are the basic building blocks of a C program. are the basic building blocks of a C program. A function can be defined as a set of instructions to perform a specific task. are the basic
STRUCTURE EXITS, NOT LOOPS
 STRUCTURE EXITS, NOT LOOPS Mordechai Ben-Ari Department of Science Teaching Weizmann Institute of Science Rehovot 76100 Israel ntbenari@wis.weizmann.ac.il Copyright c 1996 by the Association for Computing
STRUCTURE EXITS, NOT LOOPS Mordechai Ben-Ari Department of Science Teaching Weizmann Institute of Science Rehovot 76100 Israel ntbenari@wis.weizmann.ac.il Copyright c 1996 by the Association for Computing
Arrays in C. Prof. Indranil Sen Gupta Dept. of Computer Science & Engg. Indian Institute of Technology Kharagpur. Basic Concept
 Arrays in C Prof. Indranil Sen Gupta Dept. of Computer Science & Engg. Indian Institute of Technology Kharagpur 1 Basic Concept Many applications require multiple data items that have common characteristics.
Arrays in C Prof. Indranil Sen Gupta Dept. of Computer Science & Engg. Indian Institute of Technology Kharagpur 1 Basic Concept Many applications require multiple data items that have common characteristics.
COMP6700/2140 Correctness and Efficiency
 COMP6700/2140 Correctness and Efficiency Alexei B Khorev and Josh Milthorpe Research School of Computer Science, ANU May 2017 Alexei B Khorev and Josh Milthorpe (RSCS, ANU) COMP6700/2140 Correctness and
COMP6700/2140 Correctness and Efficiency Alexei B Khorev and Josh Milthorpe Research School of Computer Science, ANU May 2017 Alexei B Khorev and Josh Milthorpe (RSCS, ANU) COMP6700/2140 Correctness and
Unit 1 - Arrays. 1 What is an array? Explain with Example. What are the advantages of using an array?
 1 What is an array? Explain with Example. What are the advantages of using an array? An array is a fixed-size sequenced collection of elements of the same data type. An array is derived data type. The
1 What is an array? Explain with Example. What are the advantages of using an array? An array is a fixed-size sequenced collection of elements of the same data type. An array is derived data type. The
Chapter4: Data Structures. Data: It is a collection of raw facts that has implicit meaning.
 Chapter4: s Data: It is a collection of raw facts that has implicit meaning. Data may be single valued like ID, or multi valued like address. Information: It is the processed data having explicit meaning.
Chapter4: s Data: It is a collection of raw facts that has implicit meaning. Data may be single valued like ID, or multi valued like address. Information: It is the processed data having explicit meaning.
 CS6202 - PROGRAMMING & DATA STRUCTURES UNIT I Part - A 1. W hat are Keywords? Keywords are certain reserved words that have standard and pre-defined meaning in C. These keywords can be used only for their
CS6202 - PROGRAMMING & DATA STRUCTURES UNIT I Part - A 1. W hat are Keywords? Keywords are certain reserved words that have standard and pre-defined meaning in C. These keywords can be used only for their
Homework Assignment #3 Graph
 CISC 4080 Computer Algorithms Spring, 2019 Homework Assignment #3 Graph Some of the problems are adapted from problems in the book Introduction to Algorithms by Cormen, Leiserson and Rivest, and some are
CISC 4080 Computer Algorithms Spring, 2019 Homework Assignment #3 Graph Some of the problems are adapted from problems in the book Introduction to Algorithms by Cormen, Leiserson and Rivest, and some are
Journal of Global Research in Computer Science. Engineering of a Quicksort Partitioning Algorithm
 Volume 2, No. 2, February 2011 Journal of Global Research in Computer Science RESEARCH PAPER Available Online at www.jgrcs.info Engineering of a Quicksort Partitioning Algorithm D.Abhyankar* 1 and M.Ingle
Volume 2, No. 2, February 2011 Journal of Global Research in Computer Science RESEARCH PAPER Available Online at www.jgrcs.info Engineering of a Quicksort Partitioning Algorithm D.Abhyankar* 1 and M.Ingle
SRI VENKATESWARA COLLEGE OF ENGINEERING. COURSE DELIVERY PLAN - THEORY Page 1 of 6
 COURSE DELIVERY PLAN - THEORY Page 1 of 6 Department of Computer Science and Engineering B.E/B.Tech/M.E/M.Tech : B.E(CSE) & B.Tech (IT) Regulation:2016 PG Specialisation : -- : I LP: CS16301 Rev. No: 00
COURSE DELIVERY PLAN - THEORY Page 1 of 6 Department of Computer Science and Engineering B.E/B.Tech/M.E/M.Tech : B.E(CSE) & B.Tech (IT) Regulation:2016 PG Specialisation : -- : I LP: CS16301 Rev. No: 00
What is recursion. WAP to find sum of n natural numbers using recursion (5)
 DEC 2014 Q1 a What is recursion. WAP to find sum of n natural numbers using recursion (5) Recursion is a phenomenon in which a function calls itself. A function which calls itself is called recursive function.
DEC 2014 Q1 a What is recursion. WAP to find sum of n natural numbers using recursion (5) Recursion is a phenomenon in which a function calls itself. A function which calls itself is called recursive function.
CAMBRIDGE SCHOOL, NOIDA ASSIGNMENT 1, TOPIC: C++ PROGRAMMING CLASS VIII, COMPUTER SCIENCE
 CAMBRIDGE SCHOOL, NOIDA ASSIGNMENT 1, TOPIC: C++ PROGRAMMING CLASS VIII, COMPUTER SCIENCE a) Mention any 4 characteristic of the object car. Ans name, colour, model number, engine state, power b) What
CAMBRIDGE SCHOOL, NOIDA ASSIGNMENT 1, TOPIC: C++ PROGRAMMING CLASS VIII, COMPUTER SCIENCE a) Mention any 4 characteristic of the object car. Ans name, colour, model number, engine state, power b) What
Flow Control. CSC215 Lecture
 Flow Control CSC215 Lecture Outline Blocks and compound statements Conditional statements if - statement if-else - statement switch - statement? : opertator Nested conditional statements Repetitive statements
Flow Control CSC215 Lecture Outline Blocks and compound statements Conditional statements if - statement if-else - statement switch - statement? : opertator Nested conditional statements Repetitive statements
Sorting Pearson Education, Inc. All rights reserved.
 1 19 Sorting 2 19.1 Introduction (Cont.) Sorting data Place data in order Typically ascending or descending Based on one or more sort keys Algorithms Insertion sort Selection sort Merge sort More efficient,
1 19 Sorting 2 19.1 Introduction (Cont.) Sorting data Place data in order Typically ascending or descending Based on one or more sort keys Algorithms Insertion sort Selection sort Merge sort More efficient,
CS2 Algorithms and Data Structures Note 1
 CS2 Algorithms and Data Structures Note 1 Analysing Algorithms This thread of the course is concerned with the design and analysis of good algorithms and data structures. Intuitively speaking, an algorithm
CS2 Algorithms and Data Structures Note 1 Analysing Algorithms This thread of the course is concerned with the design and analysis of good algorithms and data structures. Intuitively speaking, an algorithm
Dept. of CSE, IIT KGP
 Control Flow: Looping CS10001: Programming & Data Structures Pallab Dasgupta Professor, Dept. of Computer Sc. & Engg., Indian Institute of Technology Kharagpur Types of Repeated Execution Loop: Group of
Control Flow: Looping CS10001: Programming & Data Structures Pallab Dasgupta Professor, Dept. of Computer Sc. & Engg., Indian Institute of Technology Kharagpur Types of Repeated Execution Loop: Group of
IECD Institute for Entrepreneurship and Career Development Bharathidasan University, Tiruchirappalli 23.
 Subject code - CCP01 Chapt Chapter 1 INTRODUCTION TO C 1. A group of software developed for certain purpose are referred as ---- a. Program b. Variable c. Software d. Data 2. Software is classified into
Subject code - CCP01 Chapt Chapter 1 INTRODUCTION TO C 1. A group of software developed for certain purpose are referred as ---- a. Program b. Variable c. Software d. Data 2. Software is classified into
Unit 5. Decision Making and Looping. School of Science and Technology INTRODUCTION
 INTRODUCTION Decision Making and Looping Unit 5 In the previous lessons we have learned about the programming structure, decision making procedure, how to write statements, as well as different types of
INTRODUCTION Decision Making and Looping Unit 5 In the previous lessons we have learned about the programming structure, decision making procedure, how to write statements, as well as different types of
Aryan College. Fundamental of C Programming. Unit I: Q1. What will be the value of the following expression? (2017) A + 9
 Fundamental of C Programming Unit I: Q1. What will be the value of the following expression? (2017) A + 9 Q2. Write down the C statement to calculate percentage where three subjects English, hindi, maths
Fundamental of C Programming Unit I: Q1. What will be the value of the following expression? (2017) A + 9 Q2. Write down the C statement to calculate percentage where three subjects English, hindi, maths
An Unique Data mining Task for Sorting: Data Preprocessing for efficient External Sorting
 An Unique Data mining Task for Sorting: Data Preprocessing for efficient External Sorting S.Hrushikesava Raju Associate Professor, Dept. of CSE, SIETK, Puttur. Dr.T. Swarna Latha Professor, Dept. of CSE,
An Unique Data mining Task for Sorting: Data Preprocessing for efficient External Sorting S.Hrushikesava Raju Associate Professor, Dept. of CSE, SIETK, Puttur. Dr.T. Swarna Latha Professor, Dept. of CSE,
C, C++, Fortran: Basics
 C, C++, Fortran: Basics Bruno Abreu Calfa Last Update: September 27, 2011 Table of Contents Outline Contents 1 Introduction and Requirements 1 2 Basic Programming Elements 2 3 Application: Numerical Linear
C, C++, Fortran: Basics Bruno Abreu Calfa Last Update: September 27, 2011 Table of Contents Outline Contents 1 Introduction and Requirements 1 2 Basic Programming Elements 2 3 Application: Numerical Linear
MAHARASHTRASTATE BOARD OF TECHNICAL EDUCATION (Autonomous) (ISO/IEC Certified)
 Subject Code: 17330 Model Answer Page 1/ 22 Important Instructions to examiners: 1) The answers should be examined by key words and not as word-to-word as given in the model answer scheme. 2) The model
Subject Code: 17330 Model Answer Page 1/ 22 Important Instructions to examiners: 1) The answers should be examined by key words and not as word-to-word as given in the model answer scheme. 2) The model
Downloaded from
 Unit-II Data Structure Arrays, Stacks, Queues And Linked List Chapter: 06 In Computer Science, a data structure is a particular way of storing and organizing data in a computer so that it can be used efficiently.
Unit-II Data Structure Arrays, Stacks, Queues And Linked List Chapter: 06 In Computer Science, a data structure is a particular way of storing and organizing data in a computer so that it can be used efficiently.
Sound Programming with PC Speaker
 23 Let your gentleness be evident to all. Sound Programming with PC Speaker Sound programming can be classified as with PC speaker and with sound blaster card. In this chapter, let s see sound programming
23 Let your gentleness be evident to all. Sound Programming with PC Speaker Sound programming can be classified as with PC speaker and with sound blaster card. In this chapter, let s see sound programming
CSc 372. Comparative Programming Languages. 15 : Haskell List Comprehension. Department of Computer Science University of Arizona
 1/20 CSc 372 Comparative Programming Languages 15 : Haskell List Comprehension Department of Computer Science University of Arizona collberg@gmail.com Copyright c 2013 Christian Collberg 2/20 List Comprehensions
1/20 CSc 372 Comparative Programming Languages 15 : Haskell List Comprehension Department of Computer Science University of Arizona collberg@gmail.com Copyright c 2013 Christian Collberg 2/20 List Comprehensions
Heap Order Property: Key stored at the parent is smaller or equal to the key stored at either child.
 A Binary Heap is a data structure that is an array object that can be viewed as a nearly complete binary tree. The tree is completely filled on all levels except the lowest, which may only be partially
A Binary Heap is a data structure that is an array object that can be viewed as a nearly complete binary tree. The tree is completely filled on all levels except the lowest, which may only be partially
Algorithm Analysis. Algorithm Analysis 1
 Algorithm Analysis 1 Algorithm Analysis Example: Sequential Search. Given an array of n elements, determine if a given number val is in the array. If so, set loc to be the index of the first occurrence
Algorithm Analysis 1 Algorithm Analysis Example: Sequential Search. Given an array of n elements, determine if a given number val is in the array. If so, set loc to be the index of the first occurrence
ME 4447/ME Microprocessor Control of Manufacturing Systems/ Introduction to Mechatronics. Instructor: Professor Charles Ume
 ME 4447/ME 6405 Microprocessor Control of Manufacturing Systems/ Introduction to Mechatronics Instructor: Professor Charles Ume Lecture on Codewarrior Integrated Development Environment Contents Overview
ME 4447/ME 6405 Microprocessor Control of Manufacturing Systems/ Introduction to Mechatronics Instructor: Professor Charles Ume Lecture on Codewarrior Integrated Development Environment Contents Overview
Beyond Counting. Owen Kaser. September 17, 2014
 Beyond Counting Owen Kaser September 17, 2014 1 Introduction Combinatorial objects such as permutations and combinations are frequently studied from a counting perspective. For instance, How many distinct
Beyond Counting Owen Kaser September 17, 2014 1 Introduction Combinatorial objects such as permutations and combinations are frequently studied from a counting perspective. For instance, How many distinct
LECTURE 17. Array Searching and Sorting
 LECTURE 17 Array Searching and Sorting ARRAY SEARCHING AND SORTING Today we ll be covering some of the more common ways for searching through an array to find an item, as well as some common ways to sort
LECTURE 17 Array Searching and Sorting ARRAY SEARCHING AND SORTING Today we ll be covering some of the more common ways for searching through an array to find an item, as well as some common ways to sort
Case Control Structure. Rab Nawaz Jadoon DCS. Assistant Professor. Department of Computer Science. COMSATS IIT, Abbottabad Pakistan
 Case Control Structure DCS COMSATS Institute of Information Technology Rab Nawaz Jadoon Assistant Professor COMSATS IIT, Abbottabad Pakistan Introduction to Computer Programming (ICP) Decision control
Case Control Structure DCS COMSATS Institute of Information Technology Rab Nawaz Jadoon Assistant Professor COMSATS IIT, Abbottabad Pakistan Introduction to Computer Programming (ICP) Decision control
Questions Bank. 14) State any four advantages of using flow-chart
 Questions Bank Sub:PIC(22228) Course Code:-EJ-2I ----------------------------------------------------------------------------------------------- Chapter:-1 (Overview of C Programming)(10 Marks) 1) State
Questions Bank Sub:PIC(22228) Course Code:-EJ-2I ----------------------------------------------------------------------------------------------- Chapter:-1 (Overview of C Programming)(10 Marks) 1) State
