Tracking Structures. Etienne Forest KEK Tsukuba, Japan Talk at Jefferson Laboratory 6/13/2003
|
|
|
- Alyson Sabina Bennett
- 5 years ago
- Views:
Transcription
1 Tracking Structures Etienne Forest KEK Tsukuba, Japan Talk at Jefferson Laboratory 6/13/2003
2 The Secret of Modern Propaganda Its task is the highest creative art of putting complicated events and facts in a way simple enough to be understood by the man on the street. If propaganda is to succeed, it must know what it wants. It must keep a clear and firm goal in mind, and seek the appropriate means and methods to reach that goal. Propaganda is a means to an end. Its purpose is to lead the people to an understanding that will allow them to willingly and without internal resistance devote themselves to the tasks and goals of a superior leadership. Good propaganda does not need to lie, indeed it may not lie. It has no reason to fear the truth. It is a mistake to believe that people cannot take the truth. They can. It is only a matter of presenting the truth to people in a way that they will be able to understand. A propaganda that lies proves that it has a bad cause. It cannot be successful in the long run. A good propaganda will always come along that serves a good cause. But propaganda is still necessary if a good cause is to succeed. A good idea does not win simply because it is good. It must be presented properly if it is to win.
3 What is the complex idea here? Write a tracking code primarily for single particle dynamics which will handle all possible topologies : common beamlines, pretzels, recirculators, dogbones and beyond in a way which mimics nature so that objects in real life have a parallel existence in the silicon world. This code should admit in theory arbitrarily complex magnets and still computes uncompromisingly all the various quantities which interests us: radiation integrals, lattice functions and their nonlinear equivalents. Within its model(s) for the various magnets, it must be capable of computing ANYTHING correctly. Question: Can this set of goals be reduced into a simple idea which can guide us or are we condemned to keep this huge set of requirements in our heads at all time? Answer: Thanks to existence of polymorphic types (Taylor-real*8), normal form theory and the existence of pointers in modern languages we know with absolute certainty that the above requirements can be reduced to a single simple idea from which everything else follows. The failure to uncover this idea or, as in the case of the CLASSIC/MAD9 gang, to appreciate its importance, leads inexorably to failure as I predicted in 1995 and was later confirmed. So what is that idea?
4 The Factory Magnet Object Attached to the physical objects are two single particle propagators: forward and backward. The magnet and its propagators cannot depend on the beam line in which they are ultimately placed. Our beam line structure (layout) must permit the full Euclidean group acting on the local propagators: translations and rotations. Conclusion: the alignment properties of the propagators immersed in the beam line structure (layout) will be inherited from the layout. And, conversely, in the single dynamics case, the layout will derive its propagators from the factory magnet object.
5 Simple Principles The two magnet propagators are attached to the magnet and depend on internal details irrelevant to our code. We access these details through physical knobs. The beam line structure must accommodate these magnets and permit misalignments which cannot depend on the internal details of the propagators. At no point in time can we compromise on the above two points. These are sine qua non conditions. We must be unchangeable in our principle, hard as steel in our organization but supple and adaptable in our tactics and methods to achieve these goals.
6 Remarkable results: If we insist during the development of the code to respect fanatically the two principles outline above, then thanks to the modern tools at our disposal since the early 1990s, this code will satisfy all the complex prerequisites listed before. In particular, the separation of the beam line structure from the factory magnet object will impose a novel idea on us: a beam line is NOT a collection of magnet propagators. The concept that a beam line is a sequential list of magnet propagators has been known to be wrong since the early 90s and yet the misguided CLASSIC gang misprogrammed MAD9/CLASSIC when they ought to have known better. It is mathematically and physically wrong.
7 The beam line is actually a collection of discrete s variables: on the computer it is represented as a link list which contains Euclidean patches/misalignments and a pointer to the actual factory magnet propagators. This will permit the correct simulation of recirculators, pretzel and other oddities. It will follow that, in a code equipped with the correct structures, insuring that magnets in common beam lines behave as one and the same magnet will be automatic rather than something imposed by hacker-style programming. In reality, in the silicon world, they will be the same object as in the real world.
8 Subsidiary remarkable results: Although our set of simple principles does not address the issue of algorithms (computation of lattice functions, etc ), in fact, this issue is automatically handled. Or to be more precise, its handling is not relevant to code design. How can that be? Three words: 1) Automatic Differentiation (Berz s DA for example) 2) Operator Overloading/Polymorphism (Bengtsson s original idea, reimplemented in F95 by myself ) 3) Normal Form theory on Taylor series maps and moments These things, in modern languages, such as C++ in 1990, and now in F95 as well, insure that WE NEED NOT to worry about algorithms for our favorite objects (β,α,γ, and the rest) And yet the MAD9/CLASSIC effort worried about these things constantly, putting an emphasis on field representations and algorithms for the computations of lattice functions. In the end, CLASSIC is incapable of doing any recirculators! A totally predictable failure that prompted Bengtsson and myself to quit the Titanic before it left port!
9 Examples of Structures Two Rings or One double Ring
10 Switching beam lines
11 Layout Structure and Fibre St art _Ground FIBRE: Element in a Lattice POINTER:: DIR POINT ER:: P0C,BET A0 ELEMENT: General Abstract Element on the "bench" Start ELEMENT MAGNET_CHART MAGNET_1 4 CHART 3 MAGNET_I Last Lastpos=3 2 End_Ground PATCH MAGNET_N 1 Inheritance End MAGNET_I: Single particle Propagator for Magnet I MAGNET_CHART Legend i Special nodes of type fibre Actual nodes of type fibre representing "magnet" number i FORWARD PROPAGATOR Pointer to next node Pointer to previous node Null Pointer at the start and the end of the list BACKWARDS PROPAGATOR 1 Linked cut in tracking a ring (S or one-sphere topology) Linked replacing 1 in the case of S
12 Patch Magnet 1 A d α B Magnet 2 C h Magnet 3
13 Frames Misaligned Element D_IN ENT(3,3) MID(3,3) D_OUT ENT(1,3) A(3) L MID(1,3) Ο(3) ALPHA B(3) EXI(1,3) EXI(3,3)
14 Full Polymorphic Package PTC STRUCTURE FPP Polymorphic Tracking Code Sa_ROTATION_MIS Sb_EXTEND_POLY Sc_1_POL_TEMPLATE Sc_2_POL_TEMPLATE FPP Sd_EUCLIDEAN Se_FRAME Sf_STATUS Fitted B-Field Element Sg_0_fitted.f90 Sg_1_TEMPLATE_KIND.f90 Sg_2_TEMPLATE_KIND.f90 Sh_DEF_KIND.f90 Si_DEF_ELEMENT Lattice function Sj_ELEMENTS Sk_LINK_LIST Fitting Sl_FAMILY Sn_MAD_LIKE Sm_TRACKING User Routines So_FITTING MAIN PROGRAM Window routines
15 Fully Polymorphic Package Complex_polymorph.f90 Polymorphic types: Can change at run time Allows complex TPSA Finally, at the top, this package overloads various useful parameterizations of a map: Dragt-Finn, inverse Dragt-Finn, vector fields, vector fields in resonance basis, and, of course, normal forms. Basic Operations of the TPSA packages involving Taylor series are overloaded here, for example +,-,/, etc... as well as other things such as derivatives. Here we really overload dab.f and newda.f90 real_polymorph.f90 complex_taylor.90 tpsalie_analysis.f90 tpsalie.90 Tpsa.f90 definition.f90 Complex type is overloaded. The complex type is made of 2taylors: TYPE complextaylor type (taylor) r type (taylor) i END TYPE complextaylor Code that overloads the Taylor packages (including that of Berz) as well as the analysis routines of Lielib Here operations on maps are overloaded. A new type damap is introduced (as well as other useful types). Map operations are overloaded, for example, concatenation and inverse. Both TPSA Taylor series are merged here. A new type called taylor combines taylorlow and the integer pointer of Berz's TPSA. The complex taylor type and the polymorphic types are also defined there. Lielib.f90 Analysis Routines newlielib.f90 Berz's TPSA Package: polynomials are represented by integer pointers. dabnew.f90 newda.f90 New TPSA Package define_newda.f90 Defines a new type called taylorlow b_da_arrays_all.f90 OR b_da_arrays_fix.f90 New Dynamical allocation of Berz's Package a_scratch_size.f90 File_handler Scratch_size
16 Algorithms???? A ī 1 M ii+1 =A i+1 R( φ ii+1 ) A ī 1 M ii+1 R( φ ii+1 ) A -1 = 3/4 1/4-1 3 φ A i+1
17 y=x+norm%a_t i=1 p=>psr%start write(16,*) i,p%mag%name, (y(1).sub.'10')**2+(y(1).sub.'01')**2 write(6,*) i,p%mag%name, (y(1).sub.'10')**2+(y(1).sub.'01')**2 do i=1,psr%n call TRACK(PSR,y,i,i+1,DEFAULT) p=>psr%start write(16,*) i+1,p%mag%name,(y(1).sub.'10')**2+(y(1).sub.'01')**2 enddo Algorithms are nowhere to be found in PTC!
P T C. Library User Guide. Dan T. Abell
 P T C Library User Guide Dan T. Abell It doesn t matter how beautiful your theory is, it doesn t matter how smart you are. If it doesn t agree with experiment, it s wrong. Richard P. Feynman The purpose
P T C Library User Guide Dan T. Abell It doesn t matter how beautiful your theory is, it doesn t matter how smart you are. If it doesn t agree with experiment, it s wrong. Richard P. Feynman The purpose
Zlib: a Numerical Library for Optimal Design of Truncated Power Series Algebra and Map Parameterization Routines
 SLAC-PUB-7363 November 1996 Zlib: a Numerical Library for Optimal Design of Truncated Power Series Algebra and Map Parameterization Routines Yiton T. Yan Stanford Linear Accelerator Center, Stanford University,
SLAC-PUB-7363 November 1996 Zlib: a Numerical Library for Optimal Design of Truncated Power Series Algebra and Map Parameterization Routines Yiton T. Yan Stanford Linear Accelerator Center, Stanford University,
PTC Integration into MAD-X
 PTC Integration into MAD-X What is PTC? (Etienne s words) Some Facts about PTC What are the advantages for MAD-X? Magnet Treatment in PTC How will we use PTC in MAD-X? New MAD-X Module with Attributes
PTC Integration into MAD-X What is PTC? (Etienne s words) Some Facts about PTC What are the advantages for MAD-X? Magnet Treatment in PTC How will we use PTC in MAD-X? New MAD-X Module with Attributes
Mathematics Mathematics Applied mathematics Mathematics
 Mathematics Mathematics is the mother of science. It applies the principles of physics and natural sciences for analysis, design, manufacturing and maintenance of systems. Mathematicians seek out patterns
Mathematics Mathematics is the mother of science. It applies the principles of physics and natural sciences for analysis, design, manufacturing and maintenance of systems. Mathematicians seek out patterns
A novel design for maximum use of public IP Space by ISPs one IP per customer
 A novel design for maximum use of public IP Space by ISPs one IP per customer 6/20/2018 Jim McNally, James Lopeman Plusten Mark Steckel Citywisper Abstract This paper outlines a new design for ISP networks
A novel design for maximum use of public IP Space by ISPs one IP per customer 6/20/2018 Jim McNally, James Lopeman Plusten Mark Steckel Citywisper Abstract This paper outlines a new design for ISP networks
Precision Spin Tracking for Electric Dipole Moment Searches
 Precision Spin Tracking for Electric Dipole Moment Searches Outline: Spin Evolution in Storage Rings Technique for EDM Measurement and Systematic Errors Integration Methods, Current Status of Our Program
Precision Spin Tracking for Electric Dipole Moment Searches Outline: Spin Evolution in Storage Rings Technique for EDM Measurement and Systematic Errors Integration Methods, Current Status of Our Program
Programming in C++ Prof. Partha Pratim Das Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur
 Programming in C++ Prof. Partha Pratim Das Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture - 43 Dynamic Binding (Polymorphism): Part III Welcome to Module
Programming in C++ Prof. Partha Pratim Das Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture - 43 Dynamic Binding (Polymorphism): Part III Welcome to Module
14.1 Encoding for different models of computation
 Lecture 14 Decidable languages In the previous lecture we discussed some examples of encoding schemes, through which various objects can be represented by strings over a given alphabet. We will begin this
Lecture 14 Decidable languages In the previous lecture we discussed some examples of encoding schemes, through which various objects can be represented by strings over a given alphabet. We will begin this
Interpretations and Models. Chapter Axiomatic Systems and Incidence Geometry
 Interpretations and Models Chapter 2.1-2.4 - Axiomatic Systems and Incidence Geometry Axiomatic Systems in Mathematics The gold standard for rigor in an area of mathematics Not fully achieved in most areas
Interpretations and Models Chapter 2.1-2.4 - Axiomatic Systems and Incidence Geometry Axiomatic Systems in Mathematics The gold standard for rigor in an area of mathematics Not fully achieved in most areas
PARALLEL TRAINING OF NEURAL NETWORKS FOR SPEECH RECOGNITION
 PARALLEL TRAINING OF NEURAL NETWORKS FOR SPEECH RECOGNITION Stanislav Kontár Speech@FIT, Dept. of Computer Graphics and Multimedia, FIT, BUT, Brno, Czech Republic E-mail: xkonta00@stud.fit.vutbr.cz In
PARALLEL TRAINING OF NEURAL NETWORKS FOR SPEECH RECOGNITION Stanislav Kontár Speech@FIT, Dept. of Computer Graphics and Multimedia, FIT, BUT, Brno, Czech Republic E-mail: xkonta00@stud.fit.vutbr.cz In
Module 1 Lecture Notes 2. Optimization Problem and Model Formulation
 Optimization Methods: Introduction and Basic concepts 1 Module 1 Lecture Notes 2 Optimization Problem and Model Formulation Introduction In the previous lecture we studied the evolution of optimization
Optimization Methods: Introduction and Basic concepts 1 Module 1 Lecture Notes 2 Optimization Problem and Model Formulation Introduction In the previous lecture we studied the evolution of optimization
Key questions to ask before commissioning any web designer to build your website.
 Key questions to ask before commissioning any web designer to build your website. KEY QUESTIONS TO ASK Before commissioning a web designer to build your website. As both an entrepreneur and business owner,
Key questions to ask before commissioning any web designer to build your website. KEY QUESTIONS TO ASK Before commissioning a web designer to build your website. As both an entrepreneur and business owner,
CHAPTER 2 LITERATURE REVIEW
 22 CHAPTER 2 LITERATURE REVIEW 2.1 GENERAL The basic transportation problem was originally developed by Hitchcock (1941). Efficient methods of solution are derived from the simplex algorithm and were developed
22 CHAPTER 2 LITERATURE REVIEW 2.1 GENERAL The basic transportation problem was originally developed by Hitchcock (1941). Efficient methods of solution are derived from the simplex algorithm and were developed
(Refer Slide Time: 00:02:02)
 Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 20 Clipping: Lines and Polygons Hello and welcome everybody to the lecture
Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 20 Clipping: Lines and Polygons Hello and welcome everybody to the lecture
Don t just read it; fight it! Ask your own questions, look for your own examples, discover your own proofs. Is the hypothesis necessary?
 Don t just read it; fight it! Ask your own questions, look for your own examples, discover your own proofs. Is the hypothesis necessary? Is the converse true? What happens in the classical special case?
Don t just read it; fight it! Ask your own questions, look for your own examples, discover your own proofs. Is the hypothesis necessary? Is the converse true? What happens in the classical special case?
CS103 Spring 2018 Mathematical Vocabulary
 CS103 Spring 2018 Mathematical Vocabulary You keep using that word. I do not think it means what you think it means. - Inigo Montoya, from The Princess Bride Consider the humble while loop in most programming
CS103 Spring 2018 Mathematical Vocabulary You keep using that word. I do not think it means what you think it means. - Inigo Montoya, from The Princess Bride Consider the humble while loop in most programming
1) What is the role of information technology in modern organizations? 2) Discuss the memory and storage devices.
 (DMCA 101) ASSIGNMENT - 1, MAY-2014. PAPER- I : INFORMATION TECHNOLOGY 1) What is the role of information technology in modern organizations? 2) Discuss the memory and storage devices. 3) What is software?
(DMCA 101) ASSIGNMENT - 1, MAY-2014. PAPER- I : INFORMATION TECHNOLOGY 1) What is the role of information technology in modern organizations? 2) Discuss the memory and storage devices. 3) What is software?
NEW CERN PROTON SYNCHROTRON BEAM OPTIMIZATION TOOL
 16th Int. Conf. on Accelerator and Large Experimental Control Systems ICALEPCS2017, Barcelona, Spain JACoW Publishing NEW CERN PROTON SYNCHROTRON BEAM OPTIMIZATION TOOL E. Piselli, A. Akroh CERN, Geneva,
16th Int. Conf. on Accelerator and Large Experimental Control Systems ICALEPCS2017, Barcelona, Spain JACoW Publishing NEW CERN PROTON SYNCHROTRON BEAM OPTIMIZATION TOOL E. Piselli, A. Akroh CERN, Geneva,
CS61C Machine Structures. Lecture 4 C Pointers and Arrays. 1/25/2006 John Wawrzynek. www-inst.eecs.berkeley.edu/~cs61c/
 CS61C Machine Structures Lecture 4 C Pointers and Arrays 1/25/2006 John Wawrzynek (www.cs.berkeley.edu/~johnw) www-inst.eecs.berkeley.edu/~cs61c/ CS 61C L04 C Pointers (1) Common C Error There is a difference
CS61C Machine Structures Lecture 4 C Pointers and Arrays 1/25/2006 John Wawrzynek (www.cs.berkeley.edu/~johnw) www-inst.eecs.berkeley.edu/~cs61c/ CS 61C L04 C Pointers (1) Common C Error There is a difference
M.C.A. DEGREE EXAMINATION, MAY First Year Paper - I : INFORMATION TECHNOLOGY. Time : 03 Hours Maximum Marks : 75
 M.C.A. DEGREE EXAMINATION, MAY - 2013 First Year Paper - I : INFORMATION TECHNOLOGY (DMCA 101) Time : 03 Hours Maximum Marks : 75 Section - A (3 15 = 45) Answer any Three of the following 1) What is the
M.C.A. DEGREE EXAMINATION, MAY - 2013 First Year Paper - I : INFORMATION TECHNOLOGY (DMCA 101) Time : 03 Hours Maximum Marks : 75 Section - A (3 15 = 45) Answer any Three of the following 1) What is the
4.2 Variations on a Scheme -- Lazy Evaluation
 [Go to first, previous, next page; contents; index] 4.2 Variations on a Scheme -- Lazy Evaluation Now that we have an evaluator expressed as a Lisp program, we can experiment with alternative choices in
[Go to first, previous, next page; contents; index] 4.2 Variations on a Scheme -- Lazy Evaluation Now that we have an evaluator expressed as a Lisp program, we can experiment with alternative choices in
Topics in Software Testing
 Dependable Software Systems Topics in Software Testing Material drawn from [Beizer, Sommerville] Software Testing Software testing is a critical element of software quality assurance and represents the
Dependable Software Systems Topics in Software Testing Material drawn from [Beizer, Sommerville] Software Testing Software testing is a critical element of software quality assurance and represents the
Parallel Transport on the Torus
 MLI Home Mathematics The Torus Parallel Transport Parallel Transport on the Torus Because it really is all about the torus, baby After reading about the torus s curvature, shape operator, and geodesics,
MLI Home Mathematics The Torus Parallel Transport Parallel Transport on the Torus Because it really is all about the torus, baby After reading about the torus s curvature, shape operator, and geodesics,
Marketer s Guide to Website Redesign
 Marketer s Guide to Website Redesign Why Most Website Redesigns Fail Avoid costly mistakes and discover the strategy that guarantees ROI (Results On Internet ) A failed website redesign can cost your company
Marketer s Guide to Website Redesign Why Most Website Redesigns Fail Avoid costly mistakes and discover the strategy that guarantees ROI (Results On Internet ) A failed website redesign can cost your company
JMR ELECTRONICS INC. WHITE PAPER
 THE NEED FOR SPEED: USING PCI EXPRESS ATTACHED STORAGE FOREWORD The highest performance, expandable, directly attached storage can be achieved at low cost by moving the server or work station s PCI bus
THE NEED FOR SPEED: USING PCI EXPRESS ATTACHED STORAGE FOREWORD The highest performance, expandable, directly attached storage can be achieved at low cost by moving the server or work station s PCI bus
Grade 6 Math Circles November 6 & Relations, Functions, and Morphisms
 Faculty of Mathematics Waterloo, Ontario N2L 3G1 Centre for Education in Mathematics and Computing Relations Let s talk about relations! Grade 6 Math Circles November 6 & 7 2018 Relations, Functions, and
Faculty of Mathematics Waterloo, Ontario N2L 3G1 Centre for Education in Mathematics and Computing Relations Let s talk about relations! Grade 6 Math Circles November 6 & 7 2018 Relations, Functions, and
critically examined in the Federal Archives.
 Bettina Martin-Weber BASYS - The Federal Archives database-driven archival management system for description, administration and presentation of metadata and digital archives Back in 2004 I already took
Bettina Martin-Weber BASYS - The Federal Archives database-driven archival management system for description, administration and presentation of metadata and digital archives Back in 2004 I already took
Programming in C++ Prof. Partha Pratim Das Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur
 Programming in C++ Prof. Partha Pratim Das Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 04 Programs with IO and Loop We will now discuss the module 2,
Programming in C++ Prof. Partha Pratim Das Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 04 Programs with IO and Loop We will now discuss the module 2,
Section 2.4: Arguments with Quantified Statements
 Section 2.4: Arguments with Quantified Statements In this section, we shall generalize the ideas we developed in Section 1.3 to arguments which involve quantified statements. Most of the concepts we shall
Section 2.4: Arguments with Quantified Statements In this section, we shall generalize the ideas we developed in Section 1.3 to arguments which involve quantified statements. Most of the concepts we shall
Chapter Fourteen Bonus Lessons: Algorithms and Efficiency
 : Algorithms and Efficiency The following lessons take a deeper look at Chapter 14 topics regarding algorithms, efficiency, and Big O measurements. They can be completed by AP students after Chapter 14.
: Algorithms and Efficiency The following lessons take a deeper look at Chapter 14 topics regarding algorithms, efficiency, and Big O measurements. They can be completed by AP students after Chapter 14.
Lecture Notes on Alias Analysis
 Lecture Notes on Alias Analysis 15-411: Compiler Design André Platzer Lecture 26 1 Introduction So far we have seen how to implement and compile programs with pointers, but we have not seen how to optimize
Lecture Notes on Alias Analysis 15-411: Compiler Design André Platzer Lecture 26 1 Introduction So far we have seen how to implement and compile programs with pointers, but we have not seen how to optimize
Recursively Enumerable Languages, Turing Machines, and Decidability
 Recursively Enumerable Languages, Turing Machines, and Decidability 1 Problem Reduction: Basic Concepts and Analogies The concept of problem reduction is simple at a high level. You simply take an algorithm
Recursively Enumerable Languages, Turing Machines, and Decidability 1 Problem Reduction: Basic Concepts and Analogies The concept of problem reduction is simple at a high level. You simply take an algorithm
Inheritance and Overloading in Agda
 Inheritance and Overloading in Agda Paolo Capriotti 3 June 2013 Abstract One of the challenges of the formalization of mathematics in a proof assistant is defining things in such a way that the syntax
Inheritance and Overloading in Agda Paolo Capriotti 3 June 2013 Abstract One of the challenges of the formalization of mathematics in a proof assistant is defining things in such a way that the syntax
An Evolution of Mathematical Tools
 An Evolution of Mathematical Tools From Conceptualization to Formalization Here's what we do when we build a formal model (or do a computation): 0. Identify a collection of objects/events in the real world.
An Evolution of Mathematical Tools From Conceptualization to Formalization Here's what we do when we build a formal model (or do a computation): 0. Identify a collection of objects/events in the real world.
Formal Methods of Software Design, Eric Hehner, segment 1 page 1 out of 5
 Formal Methods of Software Design, Eric Hehner, segment 1 page 1 out of 5 [talking head] Formal Methods of Software Engineering means the use of mathematics as an aid to writing programs. Before we can
Formal Methods of Software Design, Eric Hehner, segment 1 page 1 out of 5 [talking head] Formal Methods of Software Engineering means the use of mathematics as an aid to writing programs. Before we can
For Review Purposes Only. Two Types of Definitions Closed Form and Recursive Developing Habits of Mind. Table H Output.
 79_CH_p-9.pdf Page 7. Two Types of Definitions Closed Form and Recursive The table below is from Exercise of Lesson.. Table H Developing You can describe a function that agrees with this table in more
79_CH_p-9.pdf Page 7. Two Types of Definitions Closed Form and Recursive The table below is from Exercise of Lesson.. Table H Developing You can describe a function that agrees with this table in more
Data & Procedure Reasoning about correctness
 Data & Procedure Reasoning about correctness Although this book focuses primarily on the data side of computation, its study cannot truly be separated from the study of procedure. The next two chapters
Data & Procedure Reasoning about correctness Although this book focuses primarily on the data side of computation, its study cannot truly be separated from the study of procedure. The next two chapters
Database Management System Prof. Partha Pratim Das Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur
 Database Management System Prof. Partha Pratim Das Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur Lecture - 01 Course Overview (Refer Slide Time: 00:45) Welcome
Database Management System Prof. Partha Pratim Das Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur Lecture - 01 Course Overview (Refer Slide Time: 00:45) Welcome
Digital Systems Design with PLDs and FPGAs Kuruvilla Varghese Department of Electronic Systems Engineering Indian Institute of Science Bangalore
 Digital Systems Design with PLDs and FPGAs Kuruvilla Varghese Department of Electronic Systems Engineering Indian Institute of Science Bangalore Lecture-31 Evolution of PLDs So welcome to this lecture
Digital Systems Design with PLDs and FPGAs Kuruvilla Varghese Department of Electronic Systems Engineering Indian Institute of Science Bangalore Lecture-31 Evolution of PLDs So welcome to this lecture
Biometrics problem or solution?
 Biometrics problem or solution? Summary Biometrics are a security approach that offers great promise, but also presents users and implementers with a number of practical problems. Whilst some of these
Biometrics problem or solution? Summary Biometrics are a security approach that offers great promise, but also presents users and implementers with a number of practical problems. Whilst some of these
An Alternate Paradigm for High-Level Application Development
 Abstract An Alternate Paradigm for High-Level Application Development D. Douglas We discuss an alternative to traditional paradigms under which high-level accelerator applications are developed. In this
Abstract An Alternate Paradigm for High-Level Application Development D. Douglas We discuss an alternative to traditional paradigms under which high-level accelerator applications are developed. In this
Lecture 34 SDLC Phases and UML Diagrams
 That Object-Oriented Analysis and Design Prof. Partha Pratim Das Department of Computer Science and Engineering Indian Institute of Technology-Kharagpur Lecture 34 SDLC Phases and UML Diagrams Welcome
That Object-Oriented Analysis and Design Prof. Partha Pratim Das Department of Computer Science and Engineering Indian Institute of Technology-Kharagpur Lecture 34 SDLC Phases and UML Diagrams Welcome
https://www.eskimo.com/~scs/cclass/notes/sx8.html
 1 de 6 20-10-2015 10:41 Chapter 8: Strings Strings in C are represented by arrays of characters. The end of the string is marked with a special character, the null character, which is simply the character
1 de 6 20-10-2015 10:41 Chapter 8: Strings Strings in C are represented by arrays of characters. The end of the string is marked with a special character, the null character, which is simply the character
Introduction to PSpice
 Introduction to PSpice Simulation Software 1 The Origins of SPICE In the 1960 s, simulation software begins CANCER Computer Analysis of Nonlinear Circuits, Excluding Radiation Developed at the University
Introduction to PSpice Simulation Software 1 The Origins of SPICE In the 1960 s, simulation software begins CANCER Computer Analysis of Nonlinear Circuits, Excluding Radiation Developed at the University
(Refer Slide Time: 02:59)
 Numerical Methods and Programming P. B. Sunil Kumar Department of Physics Indian Institute of Technology, Madras Lecture - 7 Error propagation and stability Last class we discussed about the representation
Numerical Methods and Programming P. B. Sunil Kumar Department of Physics Indian Institute of Technology, Madras Lecture - 7 Error propagation and stability Last class we discussed about the representation
Getting Students Excited About Learning Mathematics
 Getting Students Excited About Learning Mathematics Introduction Jen Mei Chang Department of Mathematics and Statistics California State University, Long Beach jchang9@csulb.edu It wasn t so long ago when
Getting Students Excited About Learning Mathematics Introduction Jen Mei Chang Department of Mathematics and Statistics California State University, Long Beach jchang9@csulb.edu It wasn t so long ago when
In particular, we have seen this already when we looked at how images are just bits We started with a very simple device that can be in one of two
 1 So far in this course, we have focused on how mathematics and computer science enable us to understand complex phenomena in the world around us. We did this by following a simple process: We start by
1 So far in this course, we have focused on how mathematics and computer science enable us to understand complex phenomena in the world around us. We did this by following a simple process: We start by
THE UNIVERSAL ACCELERATOR PARSER
 THE UNIVERSAL ACCELERATOR PARSER D. A. Bates, LBNL, Berkeley, CA 94720, USA D. Sagan, Cornell University, Ithaca, NY, 14850, USA A. Wolski, University of Liverpool, UK, and the Cockcroft Institute, Daresbury,
THE UNIVERSAL ACCELERATOR PARSER D. A. Bates, LBNL, Berkeley, CA 94720, USA D. Sagan, Cornell University, Ithaca, NY, 14850, USA A. Wolski, University of Liverpool, UK, and the Cockcroft Institute, Daresbury,
(Refer Slide Time: 01:25)
 Computer Architecture Prof. Anshul Kumar Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture - 32 Memory Hierarchy: Virtual Memory (contd.) We have discussed virtual
Computer Architecture Prof. Anshul Kumar Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture - 32 Memory Hierarchy: Virtual Memory (contd.) We have discussed virtual
CS-XXX: Graduate Programming Languages. Lecture 9 Simply Typed Lambda Calculus. Dan Grossman 2012
 CS-XXX: Graduate Programming Languages Lecture 9 Simply Typed Lambda Calculus Dan Grossman 2012 Types Major new topic worthy of several lectures: Type systems Continue to use (CBV) Lambda Caluclus as our
CS-XXX: Graduate Programming Languages Lecture 9 Simply Typed Lambda Calculus Dan Grossman 2012 Types Major new topic worthy of several lectures: Type systems Continue to use (CBV) Lambda Caluclus as our
THE POINCARÉ CONJECTURE The Mathematics of Smooth Behavior
 THE POINCARÉ CONJECTURE The Mathematics of Smooth Behavior Freshman Seminar University of California, Irvine Bernard Russo University of California, Irvine Spring 2015 Bernard Russo (UCI) THE POINCARÉ
THE POINCARÉ CONJECTURE The Mathematics of Smooth Behavior Freshman Seminar University of California, Irvine Bernard Russo University of California, Irvine Spring 2015 Bernard Russo (UCI) THE POINCARÉ
MIPS and Basic Assembly Language CS 64: Computer Organization and Design Logic Lecture #4
 MIPS and Basic Assembly Language CS 64: Computer Organization and Design Logic Lecture #4 Ziad Matni Dept. of Computer Science, UCSB This Week on Didja Know Dat?! 4/12/18 Matni, CS64, Sp18 2 Why do CPU
MIPS and Basic Assembly Language CS 64: Computer Organization and Design Logic Lecture #4 Ziad Matni Dept. of Computer Science, UCSB This Week on Didja Know Dat?! 4/12/18 Matni, CS64, Sp18 2 Why do CPU
Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 14
 Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 14 Scan Converting Lines, Circles and Ellipses Hello everybody, welcome again
Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 14 Scan Converting Lines, Circles and Ellipses Hello everybody, welcome again
VISUAL GUIDE to. RX Scripting. for Roulette Xtreme - System Designer 2.0. L J Howell UX Software Ver. 1.0
 VISUAL GUIDE to RX Scripting for Roulette Xtreme - System Designer 2.0 L J Howell UX Software 2009 Ver. 1.0 TABLE OF CONTENTS INTRODUCTION...ii What is this book about?... iii How to use this book... iii
VISUAL GUIDE to RX Scripting for Roulette Xtreme - System Designer 2.0 L J Howell UX Software 2009 Ver. 1.0 TABLE OF CONTENTS INTRODUCTION...ii What is this book about?... iii How to use this book... iii
Post-Quantum Cryptography A Collective Challenge
 Post-Quantum Cryptography A Collective Challenge Christophe Petit University of Oxford Mathematical Institute Christophe Petit -Oxford Crypto Day 1 Cryptography is very useful Cryptography is the science
Post-Quantum Cryptography A Collective Challenge Christophe Petit University of Oxford Mathematical Institute Christophe Petit -Oxford Crypto Day 1 Cryptography is very useful Cryptography is the science
Accelerator Modeling. David Sagan Cornell University. Jlab ERL Workshop, March 19-23, 2005 David Sagan -1-
 Accelerator Modeling David Sagan Cornell University Jlab ERL Workshop, March 19-23, 2005 David Sagan -1- Cornell s s CESR Storage Ring E+ / E- Collider. In operation since 1979. Used for both HEP and as
Accelerator Modeling David Sagan Cornell University Jlab ERL Workshop, March 19-23, 2005 David Sagan -1- Cornell s s CESR Storage Ring E+ / E- Collider. In operation since 1979. Used for both HEP and as
The name of our class will be Yo. Type that in where it says Class Name. Don t hit the OK button yet.
 Mr G s Java Jive #2: Yo! Our First Program With this handout you ll write your first program, which we ll call Yo. Programs, Classes, and Objects, Oh My! People regularly refer to Java as a language that
Mr G s Java Jive #2: Yo! Our First Program With this handout you ll write your first program, which we ll call Yo. Programs, Classes, and Objects, Oh My! People regularly refer to Java as a language that
An introduction to plotting data
 An introduction to plotting data Eric D. Black California Institute of Technology February 25, 2014 1 Introduction Plotting data is one of the essential skills every scientist must have. We use it on a
An introduction to plotting data Eric D. Black California Institute of Technology February 25, 2014 1 Introduction Plotting data is one of the essential skills every scientist must have. We use it on a
Text. Text metrics. There are some important metrics that we must consider when working with text. Figure 4-1 shows the basics.
 Text Drawing text has some special properties and thus is treated in a separate chapter. We first need to talk about the sizing of text. Then we discuss fonts and how text is actually drawn. There is then
Text Drawing text has some special properties and thus is treated in a separate chapter. We first need to talk about the sizing of text. Then we discuss fonts and how text is actually drawn. There is then
How a Global Insurance Provider in Japan uses BlackBerry UEM to Secure, Protect and Connect its Mobile Workforce
 How a Global Insurance Provider in Japan uses BlackBerry UEM to Secure, Protect and Connect its Mobile Workforce At a Glance Aegon Sony Life Insurance Company (ASLIC), a joint venture between Sony Life
How a Global Insurance Provider in Japan uses BlackBerry UEM to Secure, Protect and Connect its Mobile Workforce At a Glance Aegon Sony Life Insurance Company (ASLIC), a joint venture between Sony Life
Hardware Modeling using Verilog Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur
 Hardware Modeling using Verilog Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 01 Introduction Welcome to the course on Hardware
Hardware Modeling using Verilog Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 01 Introduction Welcome to the course on Hardware
The Topology of Bendless Orthogonal Three-Dimensional Graph Drawing. David Eppstein Computer Science Dept. Univ. of California, Irvine
 The Topology of Bendless Orthogonal Three-Dimensional Graph Drawing David Eppstein Computer Science Dept. Univ. of California, Irvine Graph drawing: visual display of symbolic information Vertices and
The Topology of Bendless Orthogonal Three-Dimensional Graph Drawing David Eppstein Computer Science Dept. Univ. of California, Irvine Graph drawing: visual display of symbolic information Vertices and
Software Design. Introduction. Software Design (Introduction) SERG
 Software Design Introduction Software Design How to implement the what. Requirements Document (RD) is starting point. Software design is a highly-creative activity. Good designers are worth their weight
Software Design Introduction Software Design How to implement the what. Requirements Document (RD) is starting point. Software design is a highly-creative activity. Good designers are worth their weight
Computer Architecture Prof. Smruthi Ranjan Sarangi Department of Computer Science and Engineering Indian Institute of Technology, Delhi
 Computer Architecture Prof. Smruthi Ranjan Sarangi Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture 32 The Memory Systems Part III Welcome back. (Refer Slide
Computer Architecture Prof. Smruthi Ranjan Sarangi Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture 32 The Memory Systems Part III Welcome back. (Refer Slide
Computing Fundamentals Advanced functions & Recursion
 Computing Fundamentals Advanced functions & Recursion Salvatore Filippone salvatore.filippone@uniroma2.it 2014 2015 (salvatore.filippone@uniroma2.it) Recursion 2014 2015 1 / 14 Anonymous functions Useful
Computing Fundamentals Advanced functions & Recursion Salvatore Filippone salvatore.filippone@uniroma2.it 2014 2015 (salvatore.filippone@uniroma2.it) Recursion 2014 2015 1 / 14 Anonymous functions Useful
(Refer Slide Time: 00:03:51)
 Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 17 Scan Converting Lines, Circles and Ellipses Hello and welcome everybody
Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 17 Scan Converting Lines, Circles and Ellipses Hello and welcome everybody
Alverton Community Primary School
 Year 1 I can tell an adult if I see anything worrying online. I can give instructions to my friend and follow their instructions to move around. I can describe what happens when I press buttons on a robot.
Year 1 I can tell an adult if I see anything worrying online. I can give instructions to my friend and follow their instructions to move around. I can describe what happens when I press buttons on a robot.
CELLULAR AUTOMATA IN MATHEMATICAL MODELING JOSH KANTOR. 1. History
 CELLULAR AUTOMATA IN MATHEMATICAL MODELING JOSH KANTOR 1. History Cellular automata were initially conceived of in 1948 by John von Neumann who was searching for ways of modeling evolution. He was trying
CELLULAR AUTOMATA IN MATHEMATICAL MODELING JOSH KANTOR 1. History Cellular automata were initially conceived of in 1948 by John von Neumann who was searching for ways of modeling evolution. He was trying
shortcut Tap into learning NOW! Visit for a complete list of Short Cuts. Your Short Cut to Knowledge
 shortcut Your Short Cut to Knowledge The following is an excerpt from a Short Cut published by one of the Pearson Education imprints. Short Cuts are short, concise, PDF documents designed specifically
shortcut Your Short Cut to Knowledge The following is an excerpt from a Short Cut published by one of the Pearson Education imprints. Short Cuts are short, concise, PDF documents designed specifically
Chapter 6 Control Flow. June 9, 2015
 Chapter 6 Control Flow June 9, 2015 Expression evaluation It s common in programming languages to use the idea of an expression, which might be a simple object function invocation over some number of arguments
Chapter 6 Control Flow June 9, 2015 Expression evaluation It s common in programming languages to use the idea of an expression, which might be a simple object function invocation over some number of arguments
Visual Design. Simplicity, Gestalt Principles, Organization/Structure
 Visual Design Simplicity, Gestalt Principles, Organization/Structure Many examples are from Universal Principles of Design, Lidwell, Holden, and Butler Why discuss visual design? You need to present the
Visual Design Simplicity, Gestalt Principles, Organization/Structure Many examples are from Universal Principles of Design, Lidwell, Holden, and Butler Why discuss visual design? You need to present the
LibRCPS Manual. Robert Lemmen
 LibRCPS Manual Robert Lemmen License librcps version 0.2, February 2008 Copyright c 2004 2008 Robert Lemmen This program is free software; you can redistribute
LibRCPS Manual Robert Lemmen License librcps version 0.2, February 2008 Copyright c 2004 2008 Robert Lemmen This program is free software; you can redistribute
4.1 Review - the DPLL procedure
 Applied Logic Lecture 4: Efficient SAT solving CS 4860 Spring 2009 Thursday, January 29, 2009 The main purpose of these notes is to help me organize the material that I used to teach today s lecture. They
Applied Logic Lecture 4: Efficient SAT solving CS 4860 Spring 2009 Thursday, January 29, 2009 The main purpose of these notes is to help me organize the material that I used to teach today s lecture. They
Integrity Instruments Application Notes. Release 1
 Integrity Instruments Application Notes Release 1 What is EIA/TIA/RS-485 What is EIA/TIA/RS-422 Half Duplex and Full Duplex Communication Asynchronous Communicatin Grounding EIA/TIA/RS-485/422 Shielding
Integrity Instruments Application Notes Release 1 What is EIA/TIA/RS-485 What is EIA/TIA/RS-422 Half Duplex and Full Duplex Communication Asynchronous Communicatin Grounding EIA/TIA/RS-485/422 Shielding
this is processed giving us: perceived color that we actually experience and base judgments upon.
 color we have been using r, g, b.. why what is a color? can we get all colors this way? how does wavelength fit in here, what part is physics, what part is physiology can i use r, g, b for simulation of
color we have been using r, g, b.. why what is a color? can we get all colors this way? how does wavelength fit in here, what part is physics, what part is physiology can i use r, g, b for simulation of
Light. Form of Electromagnetic Energy Only part of Electromagnetic Spectrum that we can really see
 Light Form of Electromagnetic Energy Only part of Electromagnetic Spectrum that we can really see Facts About Light The speed of light, c, is constant in a vacuum. Light can be: REFLECTED ABSORBED REFRACTED
Light Form of Electromagnetic Energy Only part of Electromagnetic Spectrum that we can really see Facts About Light The speed of light, c, is constant in a vacuum. Light can be: REFLECTED ABSORBED REFRACTED
Recap: Pointers. int* int& *p &i &*&* ** * * * * IFMP 18, M. Schwerhoff
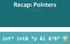 Recap: Pointers IFMP 18, M. Schwerhoff int* int& *p &i &*&* ** * * * * A 0 A 1 A 2 A 3 A 4 A 5 A 0 A 1 A 2 A 3 A 4 A 5 5 i int* p; A 0 A 1 A 2 A 3 A 4 A 5 5 i p int* p; p = &i; A 0 A 1 A 2 A 3 A 4 A 5
Recap: Pointers IFMP 18, M. Schwerhoff int* int& *p &i &*&* ** * * * * A 0 A 1 A 2 A 3 A 4 A 5 A 0 A 1 A 2 A 3 A 4 A 5 5 i int* p; A 0 A 1 A 2 A 3 A 4 A 5 5 i p int* p; p = &i; A 0 A 1 A 2 A 3 A 4 A 5
In further discussion, the books make other kinds of distinction between high level languages:
 Max and Programming This essay looks at Max from the point of view of someone with a bit of experience in traditional computer programming. There are several questions that come up from time to time on
Max and Programming This essay looks at Max from the point of view of someone with a bit of experience in traditional computer programming. There are several questions that come up from time to time on
II. Linear Programming
 II. Linear Programming A Quick Example Suppose we own and manage a small manufacturing facility that produced television sets. - What would be our organization s immediate goal? - On what would our relative
II. Linear Programming A Quick Example Suppose we own and manage a small manufacturing facility that produced television sets. - What would be our organization s immediate goal? - On what would our relative
Kernel Korner AEM: A Scalable and Native Event Mechanism for Linux
 Kernel Korner AEM: A Scalable and Native Event Mechanism for Linux Give your application the ability to register callbacks with the kernel. by Frédéric Rossi In a previous article [ An Event Mechanism
Kernel Korner AEM: A Scalable and Native Event Mechanism for Linux Give your application the ability to register callbacks with the kernel. by Frédéric Rossi In a previous article [ An Event Mechanism
RIS shading Series #2 Meet The Plugins
 RIS shading Series #2 Meet The Plugins In this tutorial I will be going over what each type of plugin is, what their uses are, and the basic layout of each. By the end you should understand the three basic
RIS shading Series #2 Meet The Plugins In this tutorial I will be going over what each type of plugin is, what their uses are, and the basic layout of each. By the end you should understand the three basic
1: Introduction to Object (1)
 1: Introduction to Object (1) 김동원 2003.01.20 Overview (1) The progress of abstraction Smalltalk Class & Object Interface The hidden implementation Reusing the implementation Inheritance: Reusing the interface
1: Introduction to Object (1) 김동원 2003.01.20 Overview (1) The progress of abstraction Smalltalk Class & Object Interface The hidden implementation Reusing the implementation Inheritance: Reusing the interface
DISCRETE COMPUTER SIMULATION WITH JAVA
 DISCRETE COMPUTER SIMULATION WITH JAVA Ricardo Augusto Cassel Department of Management Science - The Management School - Lancaster University Lancaster, LA1 4YX, United Kingdom Michael Pidd Department
DISCRETE COMPUTER SIMULATION WITH JAVA Ricardo Augusto Cassel Department of Management Science - The Management School - Lancaster University Lancaster, LA1 4YX, United Kingdom Michael Pidd Department
Computational Complexity and Implications for Security DRAFT Notes on Infeasible Computation for MA/CS 109 Leo Reyzin with the help of Nick Benes
 Computational Complexity and Implications for Security DRAFT Notes on Infeasible Computation for MA/CS 109 Leo Reyzin with the help of Nick Benes The Study of Computational Complexity Let s summarize what
Computational Complexity and Implications for Security DRAFT Notes on Infeasible Computation for MA/CS 109 Leo Reyzin with the help of Nick Benes The Study of Computational Complexity Let s summarize what
Intro. Scheme Basics. scm> 5 5. scm>
 Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
THE FINITE LAB-TRANSFORM (FLT) Peter Lablans
 THE FINITE LAB-TRANSFORM (FLT) Peter Lablans Warning: The subject matter of this article is, at least partially, protected by Copyright Registration and by issued patents and pending patent applications.
THE FINITE LAB-TRANSFORM (FLT) Peter Lablans Warning: The subject matter of this article is, at least partially, protected by Copyright Registration and by issued patents and pending patent applications.
Programming in C++ Prof. Partha Pratim Das Department of Computer Science and Engineering Programming in C++ Indian Institute of Technology, Kharagpur
 Programming in C++ Prof. Partha Pratim Das Department of Computer Science and Engineering Programming in C++ Indian Institute of Technology, Kharagpur Lecture 14 Default Parameters and Function Overloading
Programming in C++ Prof. Partha Pratim Das Department of Computer Science and Engineering Programming in C++ Indian Institute of Technology, Kharagpur Lecture 14 Default Parameters and Function Overloading
Excerpt from "Art of Problem Solving Volume 1: the Basics" 2014 AoPS Inc.
 Chapter 5 Using the Integers In spite of their being a rather restricted class of numbers, the integers have a lot of interesting properties and uses. Math which involves the properties of integers is
Chapter 5 Using the Integers In spite of their being a rather restricted class of numbers, the integers have a lot of interesting properties and uses. Math which involves the properties of integers is
Appendix E: Software
 Appendix E: Software Video Analysis of Motion Analyzing pictures (movies or videos) is a powerful tool for understanding how objects move. Like most forms of data, video is most easily analyzed using a
Appendix E: Software Video Analysis of Motion Analyzing pictures (movies or videos) is a powerful tool for understanding how objects move. Like most forms of data, video is most easily analyzed using a
Introduction to Modern Fortran
 Introduction to Modern Fortran p. 1/?? Introduction to Modern Fortran Advanced I/O and Files Nick Maclaren Computing Service nmm1@cam.ac.uk, ext. 34761 November 2007 Introduction to Modern Fortran p. 2/??
Introduction to Modern Fortran p. 1/?? Introduction to Modern Fortran Advanced I/O and Files Nick Maclaren Computing Service nmm1@cam.ac.uk, ext. 34761 November 2007 Introduction to Modern Fortran p. 2/??
This is a talk given by me to the Northwest C++ Users Group on May 19, 2010.
 This is a talk given by me to the Northwest C++ Users Group on May 19, 2010. 1 I like this picture because it clearly shows what is private and what is shared. In the message-passing system, threads operate
This is a talk given by me to the Northwest C++ Users Group on May 19, 2010. 1 I like this picture because it clearly shows what is private and what is shared. In the message-passing system, threads operate
1 More on the Bellman-Ford Algorithm
 CS161 Lecture 12 Shortest Path and Dynamic Programming Algorithms Scribe by: Eric Huang (2015), Anthony Kim (2016), M. Wootters (2017) Date: May 15, 2017 1 More on the Bellman-Ford Algorithm We didn t
CS161 Lecture 12 Shortest Path and Dynamic Programming Algorithms Scribe by: Eric Huang (2015), Anthony Kim (2016), M. Wootters (2017) Date: May 15, 2017 1 More on the Bellman-Ford Algorithm We didn t
Notes for Lecture 24
 U.C. Berkeley CS276: Cryptography Handout N24 Luca Trevisan April 21, 2009 Notes for Lecture 24 Scribed by Milosh Drezgich, posted May 11, 2009 Summary Today we introduce the notion of zero knowledge proof
U.C. Berkeley CS276: Cryptography Handout N24 Luca Trevisan April 21, 2009 Notes for Lecture 24 Scribed by Milosh Drezgich, posted May 11, 2009 Summary Today we introduce the notion of zero knowledge proof
Topic 1: What is HoTT and why?
 Topic 1: What is HoTT and why? May 5, 2014 Introduction Homotopy type theory (HoTT) is a newly emerging field of mathematics which is currently being developed as a foundation of mathematics which is in
Topic 1: What is HoTT and why? May 5, 2014 Introduction Homotopy type theory (HoTT) is a newly emerging field of mathematics which is currently being developed as a foundation of mathematics which is in
(DMCA101) M.C.A. DEGREE EXAMINATION, MAY First Year INFORMATION TECHNOLOGY
 (DMCA101) M.C.A. DEGREE EXAMINATION, MAY - 2017 First Year INFORMATION TECHNOLOGY Time : 3 Hours Maximum Marks : 70 SECTION - A (3 15 = 45) Answer any three of the following Q1) Discuss business pressures
(DMCA101) M.C.A. DEGREE EXAMINATION, MAY - 2017 First Year INFORMATION TECHNOLOGY Time : 3 Hours Maximum Marks : 70 SECTION - A (3 15 = 45) Answer any three of the following Q1) Discuss business pressures
General Simulation Principles
 1 / 24 General Simulation Principles Christos Alexopoulos and Dave Goldsman Georgia Institute of Technology, Atlanta, GA, USA 10/16/17 2 / 24 Outline 1 Steps in a Simulation Study 2 Some Definitions 3
1 / 24 General Simulation Principles Christos Alexopoulos and Dave Goldsman Georgia Institute of Technology, Atlanta, GA, USA 10/16/17 2 / 24 Outline 1 Steps in a Simulation Study 2 Some Definitions 3
Chapter 1 Getting Started
 Chapter 1 Getting Started The C# class Just like all object oriented programming languages, C# supports the concept of a class. A class is a little like a data structure in that it aggregates different
Chapter 1 Getting Started The C# class Just like all object oriented programming languages, C# supports the concept of a class. A class is a little like a data structure in that it aggregates different
Virtual Memory. Chapter 8
 Chapter 8 Virtual Memory What are common with paging and segmentation are that all memory addresses within a process are logical ones that can be dynamically translated into physical addresses at run time.
Chapter 8 Virtual Memory What are common with paging and segmentation are that all memory addresses within a process are logical ones that can be dynamically translated into physical addresses at run time.
Extension as the background of substance a formal approach
 Extension as the background of substance a formal approach Bart lomiej Skowron Wroc law University The Pontifical University of John Paul II, Kraków bartlomiej.skowron@gmail.com February 11, 2013 Presentation
Extension as the background of substance a formal approach Bart lomiej Skowron Wroc law University The Pontifical University of John Paul II, Kraków bartlomiej.skowron@gmail.com February 11, 2013 Presentation
PATH FINDING AND GRAPH TRAVERSAL
 PATH FINDING AND GRAPH TRAVERSAL PATH FINDING AND GRAPH TRAVERSAL Path finding refers to determining the shortest path between two vertices in a graph. We discussed the Floyd Warshall algorithm previously,
PATH FINDING AND GRAPH TRAVERSAL PATH FINDING AND GRAPH TRAVERSAL Path finding refers to determining the shortest path between two vertices in a graph. We discussed the Floyd Warshall algorithm previously,
