ccopyright by Aamod Arvind Sane 1998
|
|
|
- Eustacia Hodge
- 5 years ago
- Views:
Transcription
1 TECHNIQUES FOR DEVELOPING CORRECT, FAST, AND ROBUST IMPLEMENTATIONS OF DISTRIBUTED PROTOCOLS BY AAMOD ARVIND SANE THESIS Submitted in partial fulllment of the requirements for the degree of Doctor of Philosophy in Computer Science in the Graduate College of the University of Illinois at Urbana-Champaign, 1998 Urbana, Illinois
2 ccopyright by Aamod Arvind Sane 1998
3 TECHNIQUES FOR DEVELOPING CORRECT, FAST, AND ROBUST IMPLEMENTATIONS OF DISTRIBUTED PROTOCOLS Aamod Arvind Sane, Ph.D. Department of Computer Science University of Illinois at Urbana-Champaign, 1998 Roy H. Campbell, Advisor A distributed system must satisfy three requirements: it should correctly implement process interactions to realize desired behavior, it should exhibit satisfactory performance, and it should have a robust software architecture that accommodates changing requirements. This thesis presents research that addresses each of these concerns. The thesis presents new techniques for designing protocols that coordinate process interactions. The specication technique allows designers to design protocols by topdown renement. Renement steps divide the original protocol into sub-protocols that have smaller state spaces than the original protocol. Therefore, the divided protocols can be automatically veried without encountering state-space explosion. The complete protocol is synthesized by composing the divided protocols. The thesis also shows how protocols can be tailored for improved performance. A new technique for designing high-performance distributed shared memory consistency protocols is presented. The technique optimizes consistency protocols by using information about previous memory accesses to anticipate future communication. Such anticipation allows communication to overlap with computation, resulting in improved application performance. iii
4 Finally, the thesis presents a software architecture for implementing systems with interacting distributed objects. The architecture allows systems to be incrementally extended with new objects and new operations, including operations over objects on remote systems. This is achieved using design patterns, and a novel scheme for incremental construction of state machines. The architecture was used to build a virtual memory system that is smoothly extended to support distributed shared memory. iv
5 TABLE OF CONTENTS Chapter 1 Introduction : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Contributions : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Thesis Outline : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : 4 2 A Protocol Design Technique : : : : : : : : : : : : : : : : : : : : : : : : : : : Goal : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : The Problem : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Our Solution : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Summary : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Background and Related Work : : : : : : : : : : : : : : : : : : : : : : : : Verication Systems : : : : : : : : : : : : : : : : : : : : : : : : : High-Level Service Specication : : : : : : : : : : : : : : : : : : : Synthesis Methods : : : : : : : : : : : : : : : : : : : : : : : : : : Our Approach : : : : : : : : : : : : : : : : : : : : : : : : : : : : : The Synthesis Method : : : : : : : : : : : : : : : : : : : : : : : : : : : : Synthesis : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Process and System : : : : : : : : : : : : : : : : : : : : : : : : : : Automata : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Automata and Processes : : : : : : : : : : : : : : : : : : : : : : : Protocols : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Protocol Synthesis : : : : : : : : : : : : : : : : : : : : : : : : : : Specifying Coordination : : : : : : : : : : : : : : : : : : : : : : : : : : : Constraint-Rule Specications : : : : : : : : : : : : : : : : : : : : Action-Rule Specications : : : : : : : : : : : : : : : : : : : : : : Observation-Rule Specications : : : : : : : : : : : : : : : : : : : Proving Implementation : : : : : : : : : : : : : : : : : : : : : : : Implementing Constraints, Actions, and Observations : : : : : : : : : : : Synthesizing Constraint Rules : : : : : : : : : : : : : : : : : : : : Synthesizing Action Rules : : : : : : : : : : : : : : : : : : : : : : Observations via Memory and Messages : : : : : : : : : : : : : : Summary : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : 45 v
6 3 Distributed Shared Memory Consistency Protocols : : : : : : : : : : : : : : : Goal : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : The Problem : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Our Solution : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Background and Related Work : : : : : : : : : : : : : : : : : : : : : : : : Sequential Consistency : : : : : : : : : : : : : : : : : : : : : : : : Beyond Sequential Consistency : : : : : : : : : : : : : : : : : : : Synchronization in Distributed Shared Memory : : : : : : : : : : Our Approach : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Coordinated Memory : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Adaptive Barriers : : : : : : : : : : : : : : : : : : : : : : : : : : : Other Adaptive Constructs : : : : : : : : : : : : : : : : : : : : : Designing Consistency Protocols : : : : : : : : : : : : : : : : : : : : : : : Consistency Specication : : : : : : : : : : : : : : : : : : : : : : : Adaptive Barrier : : : : : : : : : : : : : : : : : : : : : : : : : : : Summary : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Implementation and Performance : : : : : : : : : : : : : : : : : : : : : : Experimental Platform : : : : : : : : : : : : : : : : : : : : : : : : Applications : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Summary : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : 77 4 A Software Architecture : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Goal : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : The Problem : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Our Solution : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Background and Related Work : : : : : : : : : : : : : : : : : : : : : : : : Basic Objects : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Interactions : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Operations : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Why the New Architecture : : : : : : : : : : : : : : : : : : : : : : : : : : Examples : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Why Change is not Easy : : : : : : : : : : : : : : : : : : : : : : : What Needs to be Redesigned : : : : : : : : : : : : : : : : : : : : : : : : Data Structures and Synchronization : : : : : : : : : : : : : : : : Interactions : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : A Solution : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Architecture of the Virtual Memory System : : : : : : : : : : : : : : : : Exporting Functionality : : : : : : : : : : : : : : : : : : : : : : : Organizing the Internals : : : : : : : : : : : : : : : : : : : : : : : Concurrency Control : : : : : : : : : : : : : : : : : : : : : : : : : Operations Using Object-Oriented State Machines : : : : : : : : : Implementing Remote Interactions : : : : : : : : : : : : : : : : : Dynamic Page Distribution : : : : : : : : : : : : : : : : : : : : : 108 vi
7 4.6 Summary : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Conclusion : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Summary : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Future Research : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : 114 Bibliography : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : 115 vii
8 Chapter 1 Introduction This thesis presents techniques for the design and implementation of protocols that coordinate the actions of concurrent processes in a distributed system. The design of novel memory consistency protocols for a distributed shared memory system illustrates the application of these techniques. The system is implemented using a new software architecture for designing object-oriented systems with concurrent and distributed operations. Protocols are dicult to design because systems of interacting concurrent processes exhibit a large number of behaviors. Therefore, computer-aided methods are used for protocol design. Currently, such methods can be classied into either verication methods or synthesis methods. Verication methods let users model the protocols in a suitable language, and check that model obeys desired properties by exhaustive search ofthe system state space. But the detailed, low-level models often result in very large state spaces. The search is made tractable by exploiting patterns in the state space to reduce the states actually examined. Even so, many practical protocols remain beyond the reach of exhaustive search. Synthesis methods avoid building complex low-level models. Instead, they translate high-level specications to low-level implementations. But these methods often require manual proofs, or are useful only in restricted cases such as peerto-peer communication protocols. Ideally, wewould like a design method that combines the clarity of high-level specications of synthesis methods with the automated checking characteristic of verication methods. 1
9 In this thesis, we develop such a design method. We introduce an approach for dividing the task of protocol design into several steps. The division produces protocols that have small state spaces either because they are abstract or because they implement parts of the original protocol. Therefore, their correctness can be easily established using verication tools. We then show how to implement the divided protocols so that the complete protocol can be synthesized by combining the divided protocols. We have applied the synthesis method to guide the implementation of new distributed shared memory consistency protocols. A distributed shared memory (DSM) system simulates shared memory over networked computers. DSM systems allow programs designed for shared memory multiprocessors to be used over networked computers. DSM systems use local memories of the networked computers as caches for the simulated shared memory. Just like shared memory multiprocessors, caches in DSM systems replicate the shared data for eciency, but then require protocols to ensure that the replicas remain consistent. In this thesis, we develop consistency protocols that allow DSM systems to operate eciently over wide-area networks characterized by high-latency high-bandwidth interconnections. A protocol that performs well over a wide-area network must be able to utilize the bandwidth to overcome latency. Our protocols gain their eciency using information about process synchronization and past memory access patterns to predict future requests from other processes. This technique reduces the time processes spend waiting for data to arrive. When computations are regular, this anticipatory communication overlaps communication and computation, giving good speedups for distributed shared memory programs over wide-area networks. Protocol implementations derived by our method are state machines that dene protocol behavior. However, the programmer is still left to manage a myriad details of the implementation environment. In our case, the protocol implementation has to be a part of a virtual memory system that supports distributed shared memory. 2
10 In this thesis, we present asoftware architecture for building object-oriented systems that have many concurrent operations on groups of objects. The architecture allows the system to be incrementally extended with new objects and new operations. It smoothly implements interactions between objects on remote systems. In the course of designing the architecture, we have discovered several design patterns, and a new technique for constructing state machines incrementally using an object-oriented approach. The architecture is used to build a virtual memory system. The resulting system is exible: beginning with simple virtual memory facilities, we extended it with facilities like distributed shared memory in an orderly manner. 1.1 Contributions This thesis makes the following contributions: A method for designing process coordination protocols based on { A family of notations to express protocols at dierent levels of abstractions. { A set of transformations to rene protocols from one level to the next. { Application of the method to design memory consistency protocols. Distributed shared memory consistency protocols that { Improve over the performance of existing protocols { Perform well over either wide-area and local-area networks. A software architecture for object systems with concurrent operations on groups of objects. The architecture is based on: { Object-oriented state machines that facilitate construction of state machines by inheritance, composition and other object-oriented techniques. { Design patterns that simplify concurrency control, remote interactions, and resource management. 3
11 1.2 Thesis Outline In Chapter 2 we present our method for synthesizing distributed shared memory protocols. We begin with a review of background and related work and identify our contribution. Next, we chapter present the basic theory and discusses the notations we use at dierent levels of abstraction. After that we present a set of transformations for synthesizing the protocol implementation from a specication. We then show howinterpret the implementation as a shared memory or message passing program. In Chapter 3, we develop our consistency protocols. We present the evolution of consistency protocols, and highlight our approach. Then we explain and formally specify our protocols and comment on the implementation. We conclude this part with performance results. In Chapter 4, we present our new software architecture. We use the design of a virtual memory as the primary example. First we explain the usual architecture of virtual memory systems, motivating the basic objects and operations. Then we critique it by considering the impact of changes, and motivate the new architecture. The architecture is discussed subsequently. In Chapter 5, we review the contributions and identify problems for future research. 4
12 Chapter 2 A Protocol Design Technique In this chapter, we present a new technique for designing nite state process coordination protocols. We begin by presenting the problem and our solution in brief. Then we examine the background research in detail, and contrast our solution with it. The rest of the chapter presents the formal details. 2.1 Goal The Problem Protocols that describe the behavior of systems with concurrent interacting components are dicult to design, because such systems exhibit a large variety of behaviors. Ahu- man designer may overlook undesirable interactions in the system, leading to errors such as deadlock. So an automated method for synthesizing such systems is highly desirable. There are two types of approaches for computer-aided protocol design, verication methods and synthesis methods. Verication methods help debug previously designed protocols by exhaustive search of state spaces, while synthesis methods start with protocol specications and translate them to low-level protocol implementations. We used these methods in our research for designing distributed shared memory consistency protocols. These protocols describe systems that have avery large number 5
13 of states. Therefore, we could only verify simplied versions of the protocols. We also attempted to use synthesis methods. But methods that had tool support are designed for synthesizing peer-to-peer communication protocols, or OSI protocol stacks. Synthesis by hand, based on specications with algebraic or logical languages that could describe multi-party protocols, requires manual proofs of the specication. Such proofs were practical only for simple versions of the protocol. Thus, while verication methods are applicable to a wide class of protocols, they are limited by the need to describe protocols in detail, as well as the limitations of exhaustive search. On the other hand, synthesis methods provide abstract protocol description languages, but the methods require manual correctness proofs. Also, the abstract descriptions can be more dicult to produce than low-level descriptions based on communicating automata. This experience suggested the need for a design method that could combine the desirable attributes of both verication and synthesis methods Our Solution We introduce an approach for dividing the task of protocol design into several steps. At each step, the protocol is simple enough that exhaustive search is tractable, so that verication tools can be used to establish correctness. The simplication is achieved using notations that support abstraction and decomposition. We introduce a family of notations that are all communicating automata, except that the communication is expressed at dierent degrees of abstraction. We chose notations based on communicating automata because communicating automata are a familiar model used in popular verication tools. In the rst step, a designer uses specications that express process coordination as abstract predicates that suppress details of communication and control. Whole system verication is done at this step. In the second step, the designer produces implementations of the predicates in a notation that expresses control but not the details of communication. Here we verify each predicate implementation separately. The design method requires the implementations to have certain properties 6
14 that permit composition so that the composite system does not have tobeveried again. In the third step, the predicate implementations are translated to protocols that express details of communication media. Again, these translations obey conditions that allow safe composition. Composing the translations terminates the protocol synthesis. We expand on these ideas in the following. Step 1 In our method, the initial design is specied by automata that describe only the desired coordination between automata, without saying how it is implemented. Thus, the initial models are extensional, abstract, and relatively simple. The notation we use formalizes a common way to describe process coordination. For example, mutual exclusion between two processes is often described as follows: \when one process is in its critical region, the other should not be in its critical region." Here, we divide the execution of a process into regions, and express coordination as a predicate on the regions of interacting processes. Our rst notation describes processes as automata, and coordination as predicates on their states. The notation suppresses details of how processes control each other to implement the predicates, as well as details of communication, and leads to models with small state spaces. We use verication tools to verify deadlock freedom, liveness, and other system properties. Step 2 The next step in a design is to show how to implement the predicates. Most distributed systems support communication mechanisms like message passing that allow one process to control another process unidirectionally. Bidirectional control is achieved by some form of request-response interaction. Our next model describes how a process controls another by unidirectional actions. At this level, we do not model elements like message queues. For example, consider a predicate over two process that says: \when one process enters region x, the other should enter y". This might be used to describe the process opening a TCP connection. One implementation might be: \First, the target waits for the connector request. Then the connector sends its request and waits for the reply". We formalize such a description with a notation where transitions in one process 7
15 may enable or disable transitions in another process. We use verication tools to ensure that such an implementations correctly implements a predicate. The original, abstract protocol may have several predicates. We establish conditions to ensure that implementations of the predicates can be composed without loss of correctness. Thus, the abstract protocol can be translated to the lower-level protocol by translating each predicate separately. Step 3 In the nal step, we use a notation that models communication media. The idea is that one process may \observe" the current state of another process and use the information to choose its transitions. An observation is easily implemented in a message passing system: a process can request the current state of another process, and wait for the response. Similarly, in a shared (or distributed) memory system, one process may observe the state of another process by reading shared (distributed) variables. Observation protocols are used to implement process control: a transition of process P that requires process Q to be in a certain state is disabled when Q is in a dierent state. We use verication tools to ensure that an observation protocol correctly implements process control, and hence the second-level protocols. Again, we establish conditions to ensure that implementations can be composed safely. These conditions carry over from the second-level protocols. Thus, the abstract protocol can be translated to observation-based protocols, and hence to shared memory and message passing programs Summary Our approach has several advantages. The notations based on communicating automata are familiar, and allow us to use popular protocol verication tools based on communicating automata. The design approach allows us to simplify protocols, rst by abstraction, and then by decomposition, so that the state space presented to a verier is smaller. The abstract predicates on processes can be implemented in various ways, and dierent im- 8
16 plementations can coexist in a synthesized protocol. Also, we can use known algorithms to implement the predicates, as long as we ensure that the composition conditions hold. In this thesis, we develop the formal basis for the approach. We have used it to design the consistency protocols for distributed shared memory, described in Chapter Background and Related Work We describe some of the previous research on protocol design. We then relate our approach to this work Verication Systems Verication systems (also called model checkers) such as SPIN [Hol91], SMV [McM92], and Mur' [Dil96] are designed to verify the correctness of nite state distributed protocols. Each verication system provides a language for a precise and understandable mathematical model of the system. For instance, SPIN uses communicating nite state machines [BZ83]. Another formal language allows the user to specify correctness predicates; the systems mentioned above use variants of temporal logic [MP91]. Temporal logic allows the user to express notions such as \if process P takes action a, Q will eventually respond with action b". The systems include algorithms that examine the complete state space of a system and verify that the state graph satises the correctness criteria [Hol91]. These systems have two drawbacks. First, the modeling languages are at a fairly low level (messages in SPIN, shared memory in SMV), so that constructing the models is tedious and error prone. Second, exhaustive exploration of the system state space can be intractable: this is the state explosion problem. Recent research has concentrated on developing techniques for checking correctness without exhaustive analysis, as well as methods for managing large state spaces in limited memory. Partial-order methods [WG93] attempt to eliminate states that arise from modeling concurrency as interleaving. If the state transitions of two processes are independent, 9
17 then in an execution of the system, the transitions may be permuted without aecting correctness of the execution. Therefore, instead of examining all permutations, we can examine the state space for an arbitrary permutation of independent transitions and still check correctness. Moreover, dependencies among the state transitions of a nite-state system can be approximated by examining the source code. Using such dependency information, partial order methods guide the search over a limited part of the system state space. Symbolic model checking [McM92] uses binary decision diagrams (BDDs) to represent the state space. The symbolic representation allows compact storage of a large state space. Algorithms that search the state space to verify correctness can be changed to operate directly on the BDD representation. BDDs work best for digital circuitry that has many replicated components. Traditional state exploration may outperform BDDs for distributed protocols [Hu95]. Fair reachability [GH85, GY84, LM95] methods force state transitions of processes in a distributed system and explore the resulting state space. This space is smaller than the state space generated when some processes do not take steps. The smaller space is sucient tocheck some properties like deadlocks. Abstraction [Lon93, PD97] Abstract Interpretation [Lon93], and Composition [Lon93] based approaches are developed to present model checkers with simpler systems to verify. These approaches use user-dened equivalence relations [Pon95] induction over replicated components [McM92], symmetry [Ip96], language containment [Kur94] and similar approaches to eliminate irrelevant states in a system. In methods based on abstraction, it is enough to check the abstract model to ensure that a property that holds in the abstracted system is really true of the actual system. Methods based on composition and simulation use theorems that show how to decompose system properties of interest when verifying components or simulations. All these methods require human intervention. Methods for managing a large number of states in limited memory include techniques such assupertrace [Hol91] and hash compaction [WL93]. These methods use hash tables to remember whether a state has been reached in the exhaustive search. The hash table 10
18 only stores an approximate description of a state, so that there is a small probability that one state is mistaken for another. Thus, the exhaustive search omits some states, and some system errors will not be detected. On the other hand, many more states can be stored in the same amount of memory, so that approximate search is applicable to larger systems. State space caching methods [GHP92] use memory as a cache, trading verication time for memory. The verication systems have a signicant drawback: the use of low-level models rst introduces irrelevant system states, and then techniques like partial-order methods attempt to extract abstract system description High-Level Service Specication Other research such as path expressions [Cam74] and logic of knowledge [HM90] has concentrated on high-level notations for describing protocols. Designers often informally describe relationships between the processes in distributed systems in terms of what one process \knows" about another process. For instance, in the description of TCP [Pos81] we nd: \An established connection is said to be halfopen if one of the TCPs has closed or aborted the connection at its end without the knowledge of the other,...". Thelogic of knowledge formalizes this notion of knowledge so that programs may include knowledge statements directly without referring to the method for gaining and losing knowledge. Such knowledge protocols are abstract and easy to specify [HZ87]. Some results [CM86] hint atways to implement gain and loss of knowledge. But so far reducing knowledge specications to actual programs has proven dicult [FHMV95]. Path expressions [Cam74] are a well-known and easy to use notation for specifying process coordination. Path expressions are regular expressions that describe the sequences of process activities in a distributed system. Campbell [Cam76] investigates several variants of path expressions. For some restrictive types of path expressions, it can be proven a priori that problems like deadlock do not exist, and there are known 11
19 algorithms to translate such path expressions to low-level P and V operations. But more expressive notations may be dicult to understand and implement [Hol91]. While verication systems use temporal logic to specify correctness predicates, there have been attempts to use it to specify systems. Temporal logic has been used as a programming language [Gab87]. However, descriptions based purely on temporal logic have proven dicult to understand in practice [Lam94] Synthesis Methods Synthesis methods translate a high-level specication to a low level language like communicating nite state machines or CSP. Tableau based methods [MW84] translate specications in temporal logic to languages like CSP or Buchi automata. The synthesis method produces a model for the formula as an existence proof. Tableaus were developed as proof techniques for mathematical logic. A tableau is a systematic way of decomposing a logical formula into subformulae until we reach elementary formulae. The truth of elementary formulae can be easily veried, and the tableau structure ensures that we verify enough elementary formulae to guarantee the truth of the original formula. When applied to temporal logic, the tableau can be interpreted as an automaton [MW84]. The automaton is then regarded as a centralized synchronizer for all processes that interleaves their actions so that the temporal formulae hold on the resulting sequence of actions. But such a centralized solution is undesirable in practice. Also, as noted above, descriptions based purely on temporal logic have proven unwieldy. Finite State methods are used in synthesizing communication protocols. They begin with a description of all desirable interactions in the system to be designed, and decompose them into communicating nite state machines. But these methods are often limited in various ways and appear to be too inexible for use in practice [PS91]. The approach of specifying desirable interactions seems applicable only to small systems [PS91] and decomposition is a dicult problem [PS91]. 12
20 In a related method [BZ83], the user starts with a dummy initial state for each process in the system to be synthesized. The user then species message transmissions for each process, and the synthesis software deduces the corresponding message receptions. The software traces all possible states where a reception may occur and updates the receiver state machine. After each update, the system warns the user if there are states without any messages in transit and none to be transmitted. Such states correspond to deadlock situations. Conformance to the service specication is not guaranteed by the method, although verication methods can be use after the synthesis is complete. Translation methods [KHvB92] translate specications in notations like LOTOS [BvdLV95] to message exchanges. The specications dene an ordering of operations, and the translation methods produce state machines that generate the sequences. These are suitable where service specication can be done as sequences of operations. But specications are often done in other styles [VSvSB91] Our Approach Our work was inspired by research on the logic of knowledge. This research showed that notions like \a process knows" were enough to express many interesting protocols succinctly. The treatment by Chandy and Mishra [CM86] reduced the logical operators to an algebraic form. Path expressions [Cam74] and LOTOS [BvdLV95] were earlier examples of the use of conjunction and disjunction predicates. We combined these ideas with the observation that the operators could be regarded as an abstract form of communication between communicating automata. This combination leads to succinct specications that can be checked by verication tools developed for communicating automata. The next question was how to describe the implementations of constraints without modeling the peculiarities of communication media. This would allow us to model control ow without the extraneous system states introduced by communication media. The model we use here is similar to LOTOS and Path expression operators that permit 13
21 specifying orders of execution. The novelty isinshowing that the implementations can be composed in way that they do not interfere with one another. The nal model is similar to the usual communicating nite state machines with single element queues. The dierence is that we communicate the current state rather than unstructured values. This makes it easy to translate the protocols to either shared memory or message passing with optimizations. Our approach gives a design technique that allows designers to simplify protocols by decomposition and abstraction. Since our development, we have found that the LO- TOSPHERE [BvdLV95] project has informally described the idea of design styles that mirror our own. They observe that experience shows that early specications are best described in Constraint-oriented style, while later designs in a State-oriented style. Our design method can be seen as a formalization of this observation. This unexpected similarity between our development and LOTOS research has strengthened our belief in the utility of the method. 2.3 The Synthesis Method In this section, we present the formal details of the synthesis method. We introduce our models of process, distributed system, and show howwe use automata to denote processes. Then we discuss our three notations for describing protocols. The rst notation represents communication using abstract operations. The next two notations rene these operators so that they can be implemented using shared memory and message passing programs. For each notation, we show howtoprove that one protocol implements another. Then we describe some implementations for the abstract communication operators, and show how the implementations can be expressed using shared memory and message passing. 14
22 2.3.1 Synthesis Let Beh be a set of desired behaviors, such as a set of sequences of events. Let L s be a specication language and L i an implementation language that specify desired subsets of Beh. Let the meaning of a specication be given by the function [[:]] s : L s! 2 Beh, while the meaning of an implementation by [[:]] i : L i! 2 Beh. Then we dene the problem of synthesis as follows. Denition 1 A synthesis method is a total function S : L s! L i such that given a specication, S() denotes the same behaviors as, [[S()]] i =[[]] s. A classic example of synthesis is the construction of a nite state machine that recognizes a set of ASCII words!, given a regular expression that species!. Here, L s is the language of regular expressions, L i the description of automata, and Beh is the set of all ASCII words. The synthesis method inductively translates the regular expression into a nite state machine. A protocol is a set of rules that describes how processes in a distributed system interact. For example, a le transfer protocol is a set of rules followed by processes on two machines in order to transfer les from one machine to another. A protocol synthesis method takes a description of the externally visible behavior b for a set of processes, and produces programs that the processes must execute in order to implement behavior b. We dene processes and distributed systems as sequences of abstract events. The events represent activities such as memory accesses or message transmission. Protocols are specied using automata. The behavior of each process is specied with an automaton, and the the joint behavior of a distributed system by the product of these automata. The state transitions in an automaton that represents a process may depend on the transitions of automata that represent other processes. The rules that govern this dependence constitute a model of process communication. Our synthesis method begins with a high-level specication with an abstract form of communication rules. Through a series of intermediate steps, the high-level specication is translated to programs that 15
23 use shared memory or message passing for communication. In the following, we make these ideas more precise Process and System Denition 2 A process P is a pair (E p ;R p ) where E p is a nite set of events and R p is a set of runs, a set innite sequences over E p. The events of two processes are disjoint: for every pair of processes P and Q, E p \E q = ;. Denition 3 A distributed system P is a pair (E; R) where E is S P 2PE P, and R a set of system runs, a set of sequences over E such that for every run, 2R, and every process P, the projection P is a run of P, P 2 R P. The runs of processes are specied using automata, and the runs of a distributed system as the product of the automata of the constituent processes. 16
24 2.3.3 Automata Denition 4 A nite state automaton is a tuple of the form (; ; ; ; ), where is a non-empty nite alphabet, a nonempty nite set of states, a transition relation, S S, a nonempty set of starting states and a nonempty set of nal states. Also, all states of are reachable, i.e., for all s 2, there is a sequence s 0 ;:::;s n where s n = s; s 0 2, and for 0 i<n,(s i ;a;s i+1 ) 2 for some a 2. Let, be the set of transitions f(s; s 0 )g such that for some letter a 2, (s; a; s 0 ) 2. A trace t of automaton A on a word w = a 0 :::a n,1 in is a sequence of states s 0 ;:::;s n where s 0 2 and for every s i ;s i+1 in t, (s i ;a i ;s i+1 ) 2. Note that a trace can also be thought of as a sequence of transitions, (s 0 ;s 1 ); (s 1 ;s 2 );:::. States and transitions that constitute a trace are said to occur in that trace. The automaton A accepts aword w if the last state s n is a nal state, s n 2. The set of all words accepted by an automaton is the language L of the automaton. We are interested in automata that accept innite words. Let w = a 0 a 1 ::: be an innite word and t be a trace s 0 ;s 1 ;::: over w. Let the limit of a trace t be the set of states that appear innitely often in t, lim(t) =fs j s = s i innitely ofteng. Then A accepts w if there is a state s 2 that appears innitely often in t, lim(t)\ 6= ;. This condition, Buchi acceptance, denes Buchi automata. The language of the automaton is is set of innite words L! that is accepted by the automaton. Since we specify distributed systems as products of automata, we use a slightly different presentation of the acceptance condition called generalized acceptance [GW94]. Let F = ff 1 ;:::;F k g;f i 2 ;k 0 be a set of sets of accepting states. Then the automaton A accepts w if for every F i, lim(t)\f i 6= ;. If there is only one F i, then the condition is the same as Buchi acceptance. Here, A is intended to be the product of of automata A i ;:::;A k. The condition ensures that accepted sequences are those where every automaton goes through its accept state innitely often. Thus we enforce fairness by requiring that every automaton must make progress. 17
25 Denition 5 A generalized Buchi automaton is a nite state automaton that accepts innite words under the generalized acceptance condition. Henceforth, we will assume that every automaton is equipped with a generalized acceptance condition Automata and Processes We use automata to denote processes. Intuitively, wewant either automata states or automata transitions to represent nite sequences of process events. For example, when describing mutual exclusion, we refer to sequences of critical and non-critical states. but when describing serial communication, we might use send and receive transitions. Technically, weachieve this by dening the alphabet to be a set isomorphic to either the set of states or the set of transitions,. In the rst case, accepted words dene acceptable sequences of states. In the second case, accepted words dene acceptable sequence of transitions. Correspondence between runs and words is established though a semantic mapping from letters to process events. Each letter corresponds to a set of nite sequences of process events. This mapping is inductively extended to map words (sequences over the alphabet) to runs (sequences over events). Let A be an automaton and P a process. Let [[]] be a function, [[]] : A! 2 E p, such that for every pair of two distinct letters a; b 2 A,[[a]]\[[b]] =;. The semantics is dened as follows: Denition 6 Automaton A =(; ; ; ; ) is said to denote process p =(E;R) if there exists a (nondeterministic) function [[]] : A! 2 E p extended to the words accepted by A as follows: [[]] = [[aw]] =[[a]][[w]] for letter a and word w. 18
26 If is isomorphic to, events of P are represented by the states of A. If is isomorphic to,, events of P are represented by transitions of A Protocols Protocols describe the behavior of distributed systems. A protocol is dened by automata products with restrictions. In a protocol, individual automata denote process behavior, the product denotes system behavior, and the restrictions on the product model communication. We rst dene the notion of automata products without restriction. Denition 7 Given A =( A ; A; A ; A ; A ) with acceptance condition F A, and B = ( B ; B; B ; B ; B ) with acceptance condition F B, and disjoint alphabets and states, the free product A B =(; ; ; ; ) is dened as follows: =( A B )[ A [ B = A B = A B = A B Given s =(s A ;s B );t =(t A ;t B );s;t 2, and a =(a A ;a B );a 2, (s; a; t) 2 if (s A ;a A ;t A ) 2 A and (s B ;a B ;t B ) 2 B. Given s = (s A ;s B );t = (t A ;s B );s;t 2, and a = a A ;a 2, (s; a; t) 2 if (s A ;a A ;t A ) 2 A. Symmetrically for B. F = S F ff i 2FA i Bg[ S f F i 2FB A F i g With this denition, A or B may have individual or joint transitions in AB. A state s A is said to occur in a trace of the product AB if it occurs in some product state (s A ;s B ). Similarly, a transition (s A ;t A ) occurs in a product trace if it occurs either individually 19
27 or jointly in a product transition. The acceptance condition for innite words requires that a word be accepted by A B if both A and B pass innitely often through their accepting states. In the free product, A and B execute their state transitions independently. But if A and B communicate, the product cannot have all possible transitions. This observation motivates the following denition of a protocol. Denition 8 A protocol p with automata A and B is the free product A B and a set of restrictions (a subset of all transitions) Cthat describes an automaton such that p =, and all the other sets are dened by the states reachable from via the transitions in,c. Note that although a protocol is an automaton, we prefer to specify it as a free product with restrictions. This allows us to reason separately about the structure of component processes (represented by the free product) and communication (represented by the restriction). Dierent ways of specifying the automata and C are used at dierent stages of the synthesis method Protocol Synthesis Having dened protocols, we can now dene protocol synthesis. First we dene the notion of protocols that serve as specication and implementation. This is based on the standard notion of language substitution [HU79]. A substitution is a mapping from an alphabet to subsets of 0. The mapping is used to transform words in a language L() over to words in a language L( 0 )over 0. We use substitution to transform a specication into an implementation. Let l 2 2 be a a set of nite words over some alphabet. Let (l) be the letters of used in the words of l. The languages l; m over are distinct if they use dierent letters, (l)\(m) =;. Denition 9 A protocol q implements a protocol p (conversely, p species q) 20
28 Every automaton of p corresponds to exactly one automaton of q. There is a nondeterministic renement function : p! 2 q such that for every pair of distinct letters a; b 2 p, the languages (a) and (b) are distinct, and the words accepted by q are just the rened words accepted by p (extending to words by induction). Let P be an automaton of p and Q be the automaton of q that corresponds to P. Then there is a nondeterministic function a : P! 2 Q that maps letters of P to distinct languages, and the words accepted by Q are just the rened accepted words of P. This denition captures the ideas that a protocol implementation is composed from automata with terminating executions, adds detail to the specication, and every step of the specication is rened in a distinct way. Note also that the relation between specication and implementation is dened in terms of alphabets. Since words can describe either sequences of state or transitions, an implementation may rene either states or transitions. Finally, notice that the relationship of implementation to specication is dened in terms of relationships between the components, the automata and their states. Thus, we reason can about the (innite) words via straightforward induction. We maynow dene protocol synthesis simply as follows: Denition 10 A protocol synthesis method is a function that given a specication protocol produces its implementation protocol. By comparing Denition 6 and Denition 9, it is clear that we can always choose denotations such that implementations that conform to Denition 9 preserve behavior. Indeed, in practice we rene a protocol several times until the events of the process of interest 21
29 have a one-to-one relationship to transitions of the protocol; the nal step is a ordinary shared memory or message passing program. 2.4 Specifying Coordination Automata in a protocol aect each others' state transitions. The rules that describe the eects model interprocess communication. We use a variety of rules to specify protocols. The most extensional, abstract protocol specications are given by Constraint rules. Constraint-rule specications are implemented by Action-rule specications. Action rules include more details of communication. In turn, Action-rule specications are implemented by Observation-rule specications. Observation-rule specications are intensional; they are suciently detailed so that they can be easily translated to shared memory or message passing programs. System properties like absence of deadlock and reachability are veried once and for all at the most abstract level for Constraint-rule specications. The subsequent syntheses preserve these properties. A property is dened as a set of words over the alphabet of interest [Alp86]. A word w has a property if w 2. A language L i preserves properties of language L s if for every property s of L s, there is a unique property i of L i, and if a word w s has property s, then the corresponding word w i does not have any property disjoint from i. Lemma 1 An implementation preserves properties of its specication. Proof. From Denition 9, by induction, every word accepted by an implementation protocol corresponds to exactly one word accepted by the specication protocol. Therefore, a property s of the a specication maps to a a unique property i. Furthermore, if i is a property disjoint from i, and w s 2 s isaword accepted by the specication with a corresponding word w i of the implementation, then w i 62 i (and w i 2 i ). Thus, the implementation preserves properties. 22
30 Action-rule specications are derived from Constraint-rule specications by translating constraint rules to action rules, and Observation-rule specications are derived from Action-rule specications by translating action rules to observation rules. We show that each translation leads to automata that are implementations of the corresponding specication Constraint-Rule Specications Constraint-rule specications express essential coordination among processes. A specication describes desirable sequences of process behavior as succinctly as possible. Constraintrule specications are extensional: they describe the eects of coordination, but not the details of how processes implement coordination or properties of communication media. Constraint-rule specications are designed so that techniques for specifying and verifying protocol properties are easily applicable. For the purposes of this thesis, two types of constraints suce. One constraint requires that processes synchronize their behavior, and the other species that behaviors be disjoint. In the following, we dene Constraint-rule specications, and show a simple example, the dining philosophers. We discuss the advantages and disadvantages of this style of specication. Then we explain how protocol properties can be checked at this level using verication algorithms Denitions Let P =(E p ;R p ) be a process, and Ep be a partition of the set of events E p into regions. This denition formalizes intuitive notions like the \critical region" used to describe parts of the run of a process. Dene a bijection [[]] :! E p. Let A =(; ; ; ; ), where = and a word corresponds to the sequence of states of the trace on that word. A is said to be a region automaton if it denotes P using [[]] according to Denition 6. Every state of a region automaton denotes a distinct region of that process. Constraint-rule specications are protocols that use region automata. 23
Centre for Parallel Computing, University of Westminster, London, W1M 8JS
 Graphical Construction of Parallel Programs G. R. Ribeiro Justo Centre for Parallel Computing, University of Westminster, London, WM 8JS e-mail: justog@wmin.ac.uk, Abstract Parallel programming is not
Graphical Construction of Parallel Programs G. R. Ribeiro Justo Centre for Parallel Computing, University of Westminster, London, WM 8JS e-mail: justog@wmin.ac.uk, Abstract Parallel programming is not
the application rule M : x:a: B N : A M N : (x:a: B) N and the reduction rule (x: A: B) N! Bfx := Ng. Their algorithm is not fully satisfactory in the
 The Semi-Full Closure of Pure Type Systems? Gilles Barthe Institutionen for Datavetenskap, Chalmers Tekniska Hogskola, Goteborg, Sweden Departamento de Informatica, Universidade do Minho, Braga, Portugal
The Semi-Full Closure of Pure Type Systems? Gilles Barthe Institutionen for Datavetenskap, Chalmers Tekniska Hogskola, Goteborg, Sweden Departamento de Informatica, Universidade do Minho, Braga, Portugal
Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1
 CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) January 11, 2018 Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1 In this lecture
CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) January 11, 2018 Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1 In this lecture
Distributed Systems Programming (F21DS1) Formal Verification
 Distributed Systems Programming (F21DS1) Formal Verification Andrew Ireland Department of Computer Science School of Mathematical and Computer Sciences Heriot-Watt University Edinburgh Overview Focus on
Distributed Systems Programming (F21DS1) Formal Verification Andrew Ireland Department of Computer Science School of Mathematical and Computer Sciences Heriot-Watt University Edinburgh Overview Focus on
A Boolean Expression. Reachability Analysis or Bisimulation. Equation Solver. Boolean. equations.
 A Framework for Embedded Real-time System Design? Jin-Young Choi 1, Hee-Hwan Kwak 2, and Insup Lee 2 1 Department of Computer Science and Engineering, Korea Univerity choi@formal.korea.ac.kr 2 Department
A Framework for Embedded Real-time System Design? Jin-Young Choi 1, Hee-Hwan Kwak 2, and Insup Lee 2 1 Department of Computer Science and Engineering, Korea Univerity choi@formal.korea.ac.kr 2 Department
Solve the Data Flow Problem
 Gaining Condence in Distributed Systems Gleb Naumovich, Lori A. Clarke, and Leon J. Osterweil University of Massachusetts, Amherst Computer Science Department University of Massachusetts Amherst, Massachusetts
Gaining Condence in Distributed Systems Gleb Naumovich, Lori A. Clarke, and Leon J. Osterweil University of Massachusetts, Amherst Computer Science Department University of Massachusetts Amherst, Massachusetts
An Introduction to Input/Output Automata. Nancy A. Lynch and Mark R. Tuttle. Massachusetts Institute of Technology. Cambridge, Mass.
 An Introduction to Input/Output Automata Nancy A. Lynch and Mark R. Tuttle Massachusetts Institute of Technology Cambridge, Mass. 02139 November 18, 1988 1 Introduction The input/output automaton model
An Introduction to Input/Output Automata Nancy A. Lynch and Mark R. Tuttle Massachusetts Institute of Technology Cambridge, Mass. 02139 November 18, 1988 1 Introduction The input/output automaton model
9.5 Equivalence Relations
 9.5 Equivalence Relations You know from your early study of fractions that each fraction has many equivalent forms. For example, 2, 2 4, 3 6, 2, 3 6, 5 30,... are all different ways to represent the same
9.5 Equivalence Relations You know from your early study of fractions that each fraction has many equivalent forms. For example, 2, 2 4, 3 6, 2, 3 6, 5 30,... are all different ways to represent the same
Synchronization Expressions: Characterization Results and. Implementation. Kai Salomaa y Sheng Yu y. Abstract
 Synchronization Expressions: Characterization Results and Implementation Kai Salomaa y Sheng Yu y Abstract Synchronization expressions are dened as restricted regular expressions that specify synchronization
Synchronization Expressions: Characterization Results and Implementation Kai Salomaa y Sheng Yu y Abstract Synchronization expressions are dened as restricted regular expressions that specify synchronization
A taxonomy of race. D. P. Helmbold, C. E. McDowell. September 28, University of California, Santa Cruz. Santa Cruz, CA
 A taxonomy of race conditions. D. P. Helmbold, C. E. McDowell UCSC-CRL-94-34 September 28, 1994 Board of Studies in Computer and Information Sciences University of California, Santa Cruz Santa Cruz, CA
A taxonomy of race conditions. D. P. Helmbold, C. E. McDowell UCSC-CRL-94-34 September 28, 1994 Board of Studies in Computer and Information Sciences University of California, Santa Cruz Santa Cruz, CA
Promela and SPIN. Mads Dam Dept. Microelectronics and Information Technology Royal Institute of Technology, KTH. Promela and SPIN
 Promela and SPIN Mads Dam Dept. Microelectronics and Information Technology Royal Institute of Technology, KTH Promela and SPIN Promela (Protocol Meta Language): Language for modelling discrete, event-driven
Promela and SPIN Mads Dam Dept. Microelectronics and Information Technology Royal Institute of Technology, KTH Promela and SPIN Promela (Protocol Meta Language): Language for modelling discrete, event-driven
History: Combinational Logic! single FSM! Hierarchy. Facilities for managing networks of FSMs MISII. Facilities for handling latches
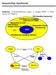 Sequential Synthesis History: Combinational Logic! single FSM! Hierarchy of FSM's. Sequential Circuit Optimization (single machine) SIS Facilities for managing networks of FSMs MISII Facilities for handling
Sequential Synthesis History: Combinational Logic! single FSM! Hierarchy of FSM's. Sequential Circuit Optimization (single machine) SIS Facilities for managing networks of FSMs MISII Facilities for handling
size, runs an existing induction algorithm on the rst subset to obtain a rst set of rules, and then processes each of the remaining data subsets at a
 Multi-Layer Incremental Induction Xindong Wu and William H.W. Lo School of Computer Science and Software Ebgineering Monash University 900 Dandenong Road Melbourne, VIC 3145, Australia Email: xindong@computer.org
Multi-Layer Incremental Induction Xindong Wu and William H.W. Lo School of Computer Science and Software Ebgineering Monash University 900 Dandenong Road Melbourne, VIC 3145, Australia Email: xindong@computer.org
Handout 9: Imperative Programs and State
 06-02552 Princ. of Progr. Languages (and Extended ) The University of Birmingham Spring Semester 2016-17 School of Computer Science c Uday Reddy2016-17 Handout 9: Imperative Programs and State Imperative
06-02552 Princ. of Progr. Languages (and Extended ) The University of Birmingham Spring Semester 2016-17 School of Computer Science c Uday Reddy2016-17 Handout 9: Imperative Programs and State Imperative
to automatically generate parallel code for many applications that periodically update shared data structures using commuting operations and/or manipu
 Semantic Foundations of Commutativity Analysis Martin C. Rinard y and Pedro C. Diniz z Department of Computer Science University of California, Santa Barbara Santa Barbara, CA 93106 fmartin,pedrog@cs.ucsb.edu
Semantic Foundations of Commutativity Analysis Martin C. Rinard y and Pedro C. Diniz z Department of Computer Science University of California, Santa Barbara Santa Barbara, CA 93106 fmartin,pedrog@cs.ucsb.edu
under Timing Constraints David Filo David Ku Claudionor N. Coelho, Jr. Giovanni De Micheli
 Interface Optimization for Concurrent Systems under Timing Constraints David Filo David Ku Claudionor N. Coelho, Jr. Giovanni De Micheli Abstract The scope of most high-level synthesis eorts to date has
Interface Optimization for Concurrent Systems under Timing Constraints David Filo David Ku Claudionor N. Coelho, Jr. Giovanni De Micheli Abstract The scope of most high-level synthesis eorts to date has
Don't Cares in Multi-Level Network Optimization. Hamid Savoj. Abstract
 Don't Cares in Multi-Level Network Optimization Hamid Savoj University of California Berkeley, California Department of Electrical Engineering and Computer Sciences Abstract An important factor in the
Don't Cares in Multi-Level Network Optimization Hamid Savoj University of California Berkeley, California Department of Electrical Engineering and Computer Sciences Abstract An important factor in the
On the Definition of Sequential Consistency
 On the Definition of Sequential Consistency Ali Sezgin Ganesh Gopalakrishnan Abstract The definition of sequential consistency is compared with an intuitive notion of correctness. A relation between what
On the Definition of Sequential Consistency Ali Sezgin Ganesh Gopalakrishnan Abstract The definition of sequential consistency is compared with an intuitive notion of correctness. A relation between what
EXTENDING THE PRIORITY CEILING PROTOCOL USING READ/WRITE AFFECTED SETS MICHAEL A. SQUADRITO A THESIS SUBMITTED IN PARTIAL FULFILLMENT OF THE
 EXTENDING THE PRIORITY CEILING PROTOCOL USING READ/WRITE AFFECTED SETS BY MICHAEL A. SQUADRITO A THESIS SUBMITTED IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF SCIENCE IN COMPUTER
EXTENDING THE PRIORITY CEILING PROTOCOL USING READ/WRITE AFFECTED SETS BY MICHAEL A. SQUADRITO A THESIS SUBMITTED IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF SCIENCE IN COMPUTER
Joint Entity Resolution
 Joint Entity Resolution Steven Euijong Whang, Hector Garcia-Molina Computer Science Department, Stanford University 353 Serra Mall, Stanford, CA 94305, USA {swhang, hector}@cs.stanford.edu No Institute
Joint Entity Resolution Steven Euijong Whang, Hector Garcia-Molina Computer Science Department, Stanford University 353 Serra Mall, Stanford, CA 94305, USA {swhang, hector}@cs.stanford.edu No Institute
for the MADFA construction problem have typically been kept as trade secrets (due to their commercial success in applications such as spell-checking).
 A Taxonomy of Algorithms for Constructing Minimal Acyclic Deterministic Finite Automata Bruce W. Watson 1 watson@openfire.org www.openfire.org University of Pretoria (Department of Computer Science) Pretoria
A Taxonomy of Algorithms for Constructing Minimal Acyclic Deterministic Finite Automata Bruce W. Watson 1 watson@openfire.org www.openfire.org University of Pretoria (Department of Computer Science) Pretoria
DISCRETE-event dynamic systems (DEDS) are dynamic
 IEEE TRANSACTIONS ON CONTROL SYSTEMS TECHNOLOGY, VOL. 7, NO. 2, MARCH 1999 175 The Supervised Control of Discrete-Event Dynamic Systems François Charbonnier, Hassane Alla, and René David Abstract The supervisory
IEEE TRANSACTIONS ON CONTROL SYSTEMS TECHNOLOGY, VOL. 7, NO. 2, MARCH 1999 175 The Supervised Control of Discrete-Event Dynamic Systems François Charbonnier, Hassane Alla, and René David Abstract The supervisory
Localization in Graphs. Richardson, TX Azriel Rosenfeld. Center for Automation Research. College Park, MD
 CAR-TR-728 CS-TR-3326 UMIACS-TR-94-92 Samir Khuller Department of Computer Science Institute for Advanced Computer Studies University of Maryland College Park, MD 20742-3255 Localization in Graphs Azriel
CAR-TR-728 CS-TR-3326 UMIACS-TR-94-92 Samir Khuller Department of Computer Science Institute for Advanced Computer Studies University of Maryland College Park, MD 20742-3255 Localization in Graphs Azriel
Sérgio Campos, Edmund Clarke
 Sérgio Campos, Edmund 1 / 23 Model checking is a technique that relies on building a finite model of a system and checking that a desired property holds in that model. The check is performed by an exhaustive
Sérgio Campos, Edmund 1 / 23 Model checking is a technique that relies on building a finite model of a system and checking that a desired property holds in that model. The check is performed by an exhaustive
CS2 Language Processing note 3
 CS2 Language Processing note 3 CS2Ah 5..4 CS2 Language Processing note 3 Nondeterministic finite automata In this lecture we look at nondeterministic finite automata and prove the Conversion Theorem, which
CS2 Language Processing note 3 CS2Ah 5..4 CS2 Language Processing note 3 Nondeterministic finite automata In this lecture we look at nondeterministic finite automata and prove the Conversion Theorem, which
A Note on Fairness in I/O Automata. Judi Romijn and Frits Vaandrager CWI. Abstract
 A Note on Fairness in I/O Automata Judi Romijn and Frits Vaandrager CWI P.O. Box 94079, 1090 GB Amsterdam, The Netherlands judi@cwi.nl, fritsv@cwi.nl Abstract Notions of weak and strong fairness are studied
A Note on Fairness in I/O Automata Judi Romijn and Frits Vaandrager CWI P.O. Box 94079, 1090 GB Amsterdam, The Netherlands judi@cwi.nl, fritsv@cwi.nl Abstract Notions of weak and strong fairness are studied
Enhancing Integrated Layer Processing using Common Case. Anticipation and Data Dependence Analysis. Extended Abstract
 Enhancing Integrated Layer Processing using Common Case Anticipation and Data Dependence Analysis Extended Abstract Philippe Oechslin Computer Networking Lab Swiss Federal Institute of Technology DI-LTI
Enhancing Integrated Layer Processing using Common Case Anticipation and Data Dependence Analysis Extended Abstract Philippe Oechslin Computer Networking Lab Swiss Federal Institute of Technology DI-LTI
Core Membership Computation for Succinct Representations of Coalitional Games
 Core Membership Computation for Succinct Representations of Coalitional Games Xi Alice Gao May 11, 2009 Abstract In this paper, I compare and contrast two formal results on the computational complexity
Core Membership Computation for Succinct Representations of Coalitional Games Xi Alice Gao May 11, 2009 Abstract In this paper, I compare and contrast two formal results on the computational complexity
CS5371 Theory of Computation. Lecture 8: Automata Theory VI (PDA, PDA = CFG)
 CS5371 Theory of Computation Lecture 8: Automata Theory VI (PDA, PDA = CFG) Objectives Introduce Pushdown Automaton (PDA) Show that PDA = CFG In terms of descriptive power Pushdown Automaton (PDA) Roughly
CS5371 Theory of Computation Lecture 8: Automata Theory VI (PDA, PDA = CFG) Objectives Introduce Pushdown Automaton (PDA) Show that PDA = CFG In terms of descriptive power Pushdown Automaton (PDA) Roughly
SAMOS: an Active Object{Oriented Database System. Stella Gatziu, Klaus R. Dittrich. Database Technology Research Group
 SAMOS: an Active Object{Oriented Database System Stella Gatziu, Klaus R. Dittrich Database Technology Research Group Institut fur Informatik, Universitat Zurich fgatziu, dittrichg@ifi.unizh.ch to appear
SAMOS: an Active Object{Oriented Database System Stella Gatziu, Klaus R. Dittrich Database Technology Research Group Institut fur Informatik, Universitat Zurich fgatziu, dittrichg@ifi.unizh.ch to appear
Algebraic Properties of CSP Model Operators? Y.C. Law and J.H.M. Lee. The Chinese University of Hong Kong.
 Algebraic Properties of CSP Model Operators? Y.C. Law and J.H.M. Lee Department of Computer Science and Engineering The Chinese University of Hong Kong Shatin, N.T., Hong Kong SAR, China fyclaw,jleeg@cse.cuhk.edu.hk
Algebraic Properties of CSP Model Operators? Y.C. Law and J.H.M. Lee Department of Computer Science and Engineering The Chinese University of Hong Kong Shatin, N.T., Hong Kong SAR, China fyclaw,jleeg@cse.cuhk.edu.hk
The Encoding Complexity of Network Coding
 The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
Chapter 3: Propositional Languages
 Chapter 3: Propositional Languages We define here a general notion of a propositional language. We show how to obtain, as specific cases, various languages for propositional classical logic and some non-classical
Chapter 3: Propositional Languages We define here a general notion of a propositional language. We show how to obtain, as specific cases, various languages for propositional classical logic and some non-classical
Propositional Logic. Part I
 Part I Propositional Logic 1 Classical Logic and the Material Conditional 1.1 Introduction 1.1.1 The first purpose of this chapter is to review classical propositional logic, including semantic tableaux.
Part I Propositional Logic 1 Classical Logic and the Material Conditional 1.1 Introduction 1.1.1 The first purpose of this chapter is to review classical propositional logic, including semantic tableaux.
STABILITY AND PARADOX IN ALGORITHMIC LOGIC
 STABILITY AND PARADOX IN ALGORITHMIC LOGIC WAYNE AITKEN, JEFFREY A. BARRETT Abstract. Algorithmic logic is the logic of basic statements concerning algorithms and the algorithmic rules of deduction between
STABILITY AND PARADOX IN ALGORITHMIC LOGIC WAYNE AITKEN, JEFFREY A. BARRETT Abstract. Algorithmic logic is the logic of basic statements concerning algorithms and the algorithmic rules of deduction between
Byzantine Consensus in Directed Graphs
 Byzantine Consensus in Directed Graphs Lewis Tseng 1,3, and Nitin Vaidya 2,3 1 Department of Computer Science, 2 Department of Electrical and Computer Engineering, and 3 Coordinated Science Laboratory
Byzantine Consensus in Directed Graphs Lewis Tseng 1,3, and Nitin Vaidya 2,3 1 Department of Computer Science, 2 Department of Electrical and Computer Engineering, and 3 Coordinated Science Laboratory
Multi Domain Logic and its Applications to SAT
 Multi Domain Logic and its Applications to SAT Tudor Jebelean RISC Linz, Austria Tudor.Jebelean@risc.uni-linz.ac.at Gábor Kusper Eszterházy Károly College gkusper@aries.ektf.hu Abstract We describe a new
Multi Domain Logic and its Applications to SAT Tudor Jebelean RISC Linz, Austria Tudor.Jebelean@risc.uni-linz.ac.at Gábor Kusper Eszterházy Károly College gkusper@aries.ektf.hu Abstract We describe a new
1. Draw the state graphs for the finite automata which accept sets of strings composed of zeros and ones which:
 P R O B L E M S Finite Autom ata. Draw the state graphs for the finite automata which accept sets of strings composed of zeros and ones which: a) Are a multiple of three in length. b) End with the string
P R O B L E M S Finite Autom ata. Draw the state graphs for the finite automata which accept sets of strings composed of zeros and ones which: a) Are a multiple of three in length. b) End with the string
3.4 Deduction and Evaluation: Tools Conditional-Equational Logic
 3.4 Deduction and Evaluation: Tools 3.4.1 Conditional-Equational Logic The general definition of a formal specification from above was based on the existence of a precisely defined semantics for the syntax
3.4 Deduction and Evaluation: Tools 3.4.1 Conditional-Equational Logic The general definition of a formal specification from above was based on the existence of a precisely defined semantics for the syntax
Reading 1 : Introduction
 CS/Math 240: Introduction to Discrete Mathematics Fall 2015 Instructors: Beck Hasti and Gautam Prakriya Reading 1 : Introduction Welcome to CS 240, an introduction to discrete mathematics. This reading
CS/Math 240: Introduction to Discrete Mathematics Fall 2015 Instructors: Beck Hasti and Gautam Prakriya Reading 1 : Introduction Welcome to CS 240, an introduction to discrete mathematics. This reading
14.1 Encoding for different models of computation
 Lecture 14 Decidable languages In the previous lecture we discussed some examples of encoding schemes, through which various objects can be represented by strings over a given alphabet. We will begin this
Lecture 14 Decidable languages In the previous lecture we discussed some examples of encoding schemes, through which various objects can be represented by strings over a given alphabet. We will begin this
CLAN: A Tool for Contract Analysis and Conflict Discovery
 CLAN: A Tool for Contract Analysis and Conflict Discovery Stephen Fenech 1, Gordon J. Pace 1, and Gerardo Schneider 2 1 Dept. of Computer Science, University of Malta, Malta 2 Dept. of Informatics, University
CLAN: A Tool for Contract Analysis and Conflict Discovery Stephen Fenech 1, Gordon J. Pace 1, and Gerardo Schneider 2 1 Dept. of Computer Science, University of Malta, Malta 2 Dept. of Informatics, University
THE FREUDENTHAL-HOPF THEOREM
 THE FREUDENTHAL-HOPF THEOREM SOFI GJING JOVANOVSKA Abstract. In this paper, we will examine a geometric property of groups: the number of ends of a group. Intuitively, the number of ends of a group is
THE FREUDENTHAL-HOPF THEOREM SOFI GJING JOVANOVSKA Abstract. In this paper, we will examine a geometric property of groups: the number of ends of a group. Intuitively, the number of ends of a group is
CHAPTER 8. Copyright Cengage Learning. All rights reserved.
 CHAPTER 8 RELATIONS Copyright Cengage Learning. All rights reserved. SECTION 8.3 Equivalence Relations Copyright Cengage Learning. All rights reserved. The Relation Induced by a Partition 3 The Relation
CHAPTER 8 RELATIONS Copyright Cengage Learning. All rights reserved. SECTION 8.3 Equivalence Relations Copyright Cengage Learning. All rights reserved. The Relation Induced by a Partition 3 The Relation
Computability and Complexity
 Computability and Complexity Turing Machines CAS 705 Ryszard Janicki Department of Computing and Software McMaster University Hamilton, Ontario, Canada janicki@mcmaster.ca Ryszard Janicki Computability
Computability and Complexity Turing Machines CAS 705 Ryszard Janicki Department of Computing and Software McMaster University Hamilton, Ontario, Canada janicki@mcmaster.ca Ryszard Janicki Computability
Abstract formula. Net formula
 { PEP { More than a Petri Net Tool ABSTRACT Bernd Grahlmann and Eike Best The PEP system (Programming Environment based on Petri Nets) supports the most important tasks of a good net tool, including HL
{ PEP { More than a Petri Net Tool ABSTRACT Bernd Grahlmann and Eike Best The PEP system (Programming Environment based on Petri Nets) supports the most important tasks of a good net tool, including HL
are discussed in Section 4. Finally, in Section 5, we make conclusions and give some directions for future research. 2 Formalization We aim at a const
 Constraints Specication at Higher Levels of Abstraction Felice Balarin, Jerry Burch, Luciano Lavagno, Yosinori Watanabe Cadence Berkeley Laboratories Berkeley, CA Roberto Passerone, Alberto Sangiovanni-Vincentelli
Constraints Specication at Higher Levels of Abstraction Felice Balarin, Jerry Burch, Luciano Lavagno, Yosinori Watanabe Cadence Berkeley Laboratories Berkeley, CA Roberto Passerone, Alberto Sangiovanni-Vincentelli
History: Combinational Logic! single FSM! Hierarchy. Facilities for managing networks of FSMs MISII. Facilities for handling latches
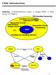 FSM Introduction History: Combinational Logic! single FSM! Hierarchy of FSM's. Sequential Circuit Optimization (single machine) SIS Facilities for managing networks of FSMs MISII Facilities for handling
FSM Introduction History: Combinational Logic! single FSM! Hierarchy of FSM's. Sequential Circuit Optimization (single machine) SIS Facilities for managing networks of FSMs MISII Facilities for handling
Rance Cleaveland The Concurrency Factory is an integrated toolset for specication, simulation,
 The Concurrency Factory Software Development Environment Rance Cleaveland (rance@csc.ncsu.edu) Philip M. Lewis (pml@cs.sunysb.edu) y Scott A. Smolka (sas@cs.sunysb.edu) y Oleg Sokolsky (oleg@ccc.com) y
The Concurrency Factory Software Development Environment Rance Cleaveland (rance@csc.ncsu.edu) Philip M. Lewis (pml@cs.sunysb.edu) y Scott A. Smolka (sas@cs.sunysb.edu) y Oleg Sokolsky (oleg@ccc.com) y
[Ch 6] Set Theory. 1. Basic Concepts and Definitions. 400 lecture note #4. 1) Basics
![[Ch 6] Set Theory. 1. Basic Concepts and Definitions. 400 lecture note #4. 1) Basics [Ch 6] Set Theory. 1. Basic Concepts and Definitions. 400 lecture note #4. 1) Basics](/thumbs/82/86066673.jpg) 400 lecture note #4 [Ch 6] Set Theory 1. Basic Concepts and Definitions 1) Basics Element: ; A is a set consisting of elements x which is in a/another set S such that P(x) is true. Empty set: notated {
400 lecture note #4 [Ch 6] Set Theory 1. Basic Concepts and Definitions 1) Basics Element: ; A is a set consisting of elements x which is in a/another set S such that P(x) is true. Empty set: notated {
Introduction to Formal Methods
 2008 Spring Software Special Development 1 Introduction to Formal Methods Part I : Formal Specification i JUNBEOM YOO jbyoo@knokuk.ac.kr Reference AS Specifier s Introduction to Formal lmethods Jeannette
2008 Spring Software Special Development 1 Introduction to Formal Methods Part I : Formal Specification i JUNBEOM YOO jbyoo@knokuk.ac.kr Reference AS Specifier s Introduction to Formal lmethods Jeannette
Transport protocols are of practical. login, le transfer, and remote procedure. calls. will operate on and therefore are generally
 Hazard-Free Connection Release Jennifer E. Walter Department of Computer Science Texas A&M University College Station, TX 77843-3112, U.S.A. Jennifer L. Welch Department of Computer Science Texas A&M University
Hazard-Free Connection Release Jennifer E. Walter Department of Computer Science Texas A&M University College Station, TX 77843-3112, U.S.A. Jennifer L. Welch Department of Computer Science Texas A&M University
Dynamic Logic David Harel, The Weizmann Institute Dexter Kozen, Cornell University Jerzy Tiuryn, University of Warsaw The MIT Press, Cambridge, Massac
 Dynamic Logic David Harel, The Weizmann Institute Dexter Kozen, Cornell University Jerzy Tiuryn, University of Warsaw The MIT Press, Cambridge, Massachusetts, 2000 Among the many approaches to formal reasoning
Dynamic Logic David Harel, The Weizmann Institute Dexter Kozen, Cornell University Jerzy Tiuryn, University of Warsaw The MIT Press, Cambridge, Massachusetts, 2000 Among the many approaches to formal reasoning
Model checking pushdown systems
 Model checking pushdown systems R. Ramanujam Institute of Mathematical Sciences, Chennai jam@imsc.res.in Update Meeting, IIT-Guwahati, 4 July 2006 p. 1 Sources of unboundedness Data manipulation: integers,
Model checking pushdown systems R. Ramanujam Institute of Mathematical Sciences, Chennai jam@imsc.res.in Update Meeting, IIT-Guwahati, 4 July 2006 p. 1 Sources of unboundedness Data manipulation: integers,
Treewidth and graph minors
 Treewidth and graph minors Lectures 9 and 10, December 29, 2011, January 5, 2012 We shall touch upon the theory of Graph Minors by Robertson and Seymour. This theory gives a very general condition under
Treewidth and graph minors Lectures 9 and 10, December 29, 2011, January 5, 2012 We shall touch upon the theory of Graph Minors by Robertson and Seymour. This theory gives a very general condition under
Binary Decision Diagrams
 Logic and roof Hilary 2016 James Worrell Binary Decision Diagrams A propositional formula is determined up to logical equivalence by its truth table. If the formula has n variables then its truth table
Logic and roof Hilary 2016 James Worrell Binary Decision Diagrams A propositional formula is determined up to logical equivalence by its truth table. If the formula has n variables then its truth table
SIR C R REDDY COLLEGE OF ENGINEERING
 SIR C R REDDY COLLEGE OF ENGINEERING DEPARTMENT OF INFORMATION TECHNOLOGY Course Outcomes II YEAR 1 st SEMESTER Subject: Data Structures (CSE 2.1.1) 1. Describe how arrays, records, linked structures,
SIR C R REDDY COLLEGE OF ENGINEERING DEPARTMENT OF INFORMATION TECHNOLOGY Course Outcomes II YEAR 1 st SEMESTER Subject: Data Structures (CSE 2.1.1) 1. Describe how arrays, records, linked structures,
From Types to Sets in Isabelle/HOL
 From Types to Sets in Isabelle/HOL Extented Abstract Ondřej Kunčar 1 and Andrei Popescu 1,2 1 Fakultät für Informatik, Technische Universität München, Germany 2 Institute of Mathematics Simion Stoilow
From Types to Sets in Isabelle/HOL Extented Abstract Ondřej Kunčar 1 and Andrei Popescu 1,2 1 Fakultät für Informatik, Technische Universität München, Germany 2 Institute of Mathematics Simion Stoilow
FB(9,3) Figure 1(a). A 4-by-4 Benes network. Figure 1(b). An FB(4, 2) network. Figure 2. An FB(27, 3) network
 Congestion-free Routing of Streaming Multimedia Content in BMIN-based Parallel Systems Harish Sethu Department of Electrical and Computer Engineering Drexel University Philadelphia, PA 19104, USA sethu@ece.drexel.edu
Congestion-free Routing of Streaming Multimedia Content in BMIN-based Parallel Systems Harish Sethu Department of Electrical and Computer Engineering Drexel University Philadelphia, PA 19104, USA sethu@ece.drexel.edu
DISCRETE MATHEMATICS
 DISCRETE MATHEMATICS WITH APPLICATIONS THIRD EDITION SUSANNA S. EPP DePaul University THOIVISON * BROOKS/COLE Australia Canada Mexico Singapore Spain United Kingdom United States CONTENTS Chapter 1 The
DISCRETE MATHEMATICS WITH APPLICATIONS THIRD EDITION SUSANNA S. EPP DePaul University THOIVISON * BROOKS/COLE Australia Canada Mexico Singapore Spain United Kingdom United States CONTENTS Chapter 1 The
Disjoint Support Decompositions
 Chapter 4 Disjoint Support Decompositions We introduce now a new property of logic functions which will be useful to further improve the quality of parameterizations in symbolic simulation. In informal
Chapter 4 Disjoint Support Decompositions We introduce now a new property of logic functions which will be useful to further improve the quality of parameterizations in symbolic simulation. In informal
KeyNote: Trust Management for Public-Key. 180 Park Avenue. Florham Park, NJ USA.
 KeyNote: Trust Management for Public-Key Infrastructures Matt Blaze 1 Joan Feigenbaum 1 Angelos D. Keromytis 2 1 AT&T Labs { Research 180 Park Avenue Florham Park, NJ 07932 USA fmab,jfg@research.att.com
KeyNote: Trust Management for Public-Key Infrastructures Matt Blaze 1 Joan Feigenbaum 1 Angelos D. Keromytis 2 1 AT&T Labs { Research 180 Park Avenue Florham Park, NJ 07932 USA fmab,jfg@research.att.com
The Maude LTL Model Checker and Its Implementation
 The Maude LTL Model Checker and Its Implementation Steven Eker 1,José Meseguer 2, and Ambarish Sridharanarayanan 2 1 Computer Science Laboratory, SRI International Menlo Park, CA 94025 eker@csl.sri.com
The Maude LTL Model Checker and Its Implementation Steven Eker 1,José Meseguer 2, and Ambarish Sridharanarayanan 2 1 Computer Science Laboratory, SRI International Menlo Park, CA 94025 eker@csl.sri.com
A Formal Approach to Program Modification. Lindsay Groves
 A Formal Approach to Program Modication Lindsay Groves School of Mathematical and Computing Sciences Victoria University of Wellington, New Zealand lindsay@mcs.vuw.ac.nz Abstract This paper presents a
A Formal Approach to Program Modication Lindsay Groves School of Mathematical and Computing Sciences Victoria University of Wellington, New Zealand lindsay@mcs.vuw.ac.nz Abstract This paper presents a
Module 3. Requirements Analysis and Specification. Version 2 CSE IIT, Kharagpur
 Module 3 Requirements Analysis and Specification Lesson 6 Formal Requirements Specification Specific Instructional Objectives At the end of this lesson the student will be able to: Explain what a formal
Module 3 Requirements Analysis and Specification Lesson 6 Formal Requirements Specification Specific Instructional Objectives At the end of this lesson the student will be able to: Explain what a formal
Petri Nets ~------~ R-ES-O---N-A-N-C-E-I--se-p-te-m--be-r Applications.
 Petri Nets 2. Applications Y Narahari Y Narahari is currently an Associate Professor of Computer Science and Automation at the Indian Institute of Science, Bangalore. His research interests are broadly
Petri Nets 2. Applications Y Narahari Y Narahari is currently an Associate Professor of Computer Science and Automation at the Indian Institute of Science, Bangalore. His research interests are broadly
Consistent Logical Checkpointing. Nitin H. Vaidya. Texas A&M University. Phone: Fax:
 Consistent Logical Checkpointing Nitin H. Vaidya Department of Computer Science Texas A&M University College Station, TX 77843-3112 hone: 409-845-0512 Fax: 409-847-8578 E-mail: vaidya@cs.tamu.edu Technical
Consistent Logical Checkpointing Nitin H. Vaidya Department of Computer Science Texas A&M University College Station, TX 77843-3112 hone: 409-845-0512 Fax: 409-847-8578 E-mail: vaidya@cs.tamu.edu Technical
Math 170- Graph Theory Notes
 1 Math 170- Graph Theory Notes Michael Levet December 3, 2018 Notation: Let n be a positive integer. Denote [n] to be the set {1, 2,..., n}. So for example, [3] = {1, 2, 3}. To quote Bud Brown, Graph theory
1 Math 170- Graph Theory Notes Michael Levet December 3, 2018 Notation: Let n be a positive integer. Denote [n] to be the set {1, 2,..., n}. So for example, [3] = {1, 2, 3}. To quote Bud Brown, Graph theory
13 th Annual Johns Hopkins Math Tournament Saturday, February 19, 2011 Automata Theory EUR solutions
 13 th Annual Johns Hopkins Math Tournament Saturday, February 19, 011 Automata Theory EUR solutions Problem 1 (5 points). Prove that any surjective map between finite sets of the same cardinality is a
13 th Annual Johns Hopkins Math Tournament Saturday, February 19, 011 Automata Theory EUR solutions Problem 1 (5 points). Prove that any surjective map between finite sets of the same cardinality is a
Copyright (C) 1997, 1998 by the Association for Computing Machinery, Inc. Permission to make digital or hard copies of part or all of this work for
 Copyright (C) 1997, 1998 by the Association for Computing Machinery, Inc. Permission to make digital or hard copies of part or all of this work for personal or classroom use is granted without fee provided
Copyright (C) 1997, 1998 by the Association for Computing Machinery, Inc. Permission to make digital or hard copies of part or all of this work for personal or classroom use is granted without fee provided
.Math 0450 Honors intro to analysis Spring, 2009 Notes #4 corrected (as of Monday evening, 1/12) some changes on page 6, as in .
 0.1 More on innity.math 0450 Honors intro to analysis Spring, 2009 Notes #4 corrected (as of Monday evening, 1/12) some changes on page 6, as in email. 0.1.1 If you haven't read 1.3, do so now! In notes#1
0.1 More on innity.math 0450 Honors intro to analysis Spring, 2009 Notes #4 corrected (as of Monday evening, 1/12) some changes on page 6, as in email. 0.1.1 If you haven't read 1.3, do so now! In notes#1
Formally-Proven Kosaraju s algorithm
 Formally-Proven Kosaraju s algorithm Laurent Théry Laurent.Thery@sophia.inria.fr Abstract This notes explains how the Kosaraju s algorithm that computes the strong-connected components of a directed graph
Formally-Proven Kosaraju s algorithm Laurent Théry Laurent.Thery@sophia.inria.fr Abstract This notes explains how the Kosaraju s algorithm that computes the strong-connected components of a directed graph
A Lift Controller in Lustre. (a case study in developing a reactive system) Leszek Holenderski
 Presented at 5 th Nordic Workshop on Program Correctness, Turku, Finland, October 25{28, 1993. Published in Proc. of the 5 th Nordic Workshop on Program Correctness, ed. R.J.R. Back and K. Sere, Abo Akademi
Presented at 5 th Nordic Workshop on Program Correctness, Turku, Finland, October 25{28, 1993. Published in Proc. of the 5 th Nordic Workshop on Program Correctness, ed. R.J.R. Back and K. Sere, Abo Akademi
A New Theory of Deadlock-Free Adaptive. Routing in Wormhole Networks. Jose Duato. Abstract
 A New Theory of Deadlock-Free Adaptive Routing in Wormhole Networks Jose Duato Abstract Second generation multicomputers use wormhole routing, allowing a very low channel set-up time and drastically reducing
A New Theory of Deadlock-Free Adaptive Routing in Wormhole Networks Jose Duato Abstract Second generation multicomputers use wormhole routing, allowing a very low channel set-up time and drastically reducing
The S-Expression Design Language (SEDL) James C. Corbett. September 1, Introduction. 2 Origins of SEDL 2. 3 The Language SEDL 2.
 The S-Expression Design Language (SEDL) James C. Corbett September 1, 1993 Contents 1 Introduction 1 2 Origins of SEDL 2 3 The Language SEDL 2 3.1 Scopes : : : : : : : : : : : : : : : : : : : : : : : :
The S-Expression Design Language (SEDL) James C. Corbett September 1, 1993 Contents 1 Introduction 1 2 Origins of SEDL 2 3 The Language SEDL 2 3.1 Scopes : : : : : : : : : : : : : : : : : : : : : : : :
Chapter 2 Overview of the Design Methodology
 Chapter 2 Overview of the Design Methodology This chapter presents an overview of the design methodology which is developed in this thesis, by identifying global abstraction levels at which a distributed
Chapter 2 Overview of the Design Methodology This chapter presents an overview of the design methodology which is developed in this thesis, by identifying global abstraction levels at which a distributed
2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006
 2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006 The Encoding Complexity of Network Coding Michael Langberg, Member, IEEE, Alexander Sprintson, Member, IEEE, and Jehoshua Bruck,
2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006 The Encoding Complexity of Network Coding Michael Langberg, Member, IEEE, Alexander Sprintson, Member, IEEE, and Jehoshua Bruck,
Uncertain Data Models
 Uncertain Data Models Christoph Koch EPFL Dan Olteanu University of Oxford SYNOMYMS data models for incomplete information, probabilistic data models, representation systems DEFINITION An uncertain data
Uncertain Data Models Christoph Koch EPFL Dan Olteanu University of Oxford SYNOMYMS data models for incomplete information, probabilistic data models, representation systems DEFINITION An uncertain data
Fundamental Properties of Graphs
 Chapter three In many real-life situations we need to know how robust a graph that represents a certain network is, how edges or vertices can be removed without completely destroying the overall connectivity,
Chapter three In many real-life situations we need to know how robust a graph that represents a certain network is, how edges or vertices can be removed without completely destroying the overall connectivity,
Revisiting the PAXOS algorithm
 Theoretical Computer Science 243 (2000) 35 91 www.elsevier.com/locate/tcs Fundamental Study Revisiting the PAXOS algorithm Roberto De Prisco a;, Butler Lampson b, Nancy Lynch a a MIT Laboratory for Computer
Theoretical Computer Science 243 (2000) 35 91 www.elsevier.com/locate/tcs Fundamental Study Revisiting the PAXOS algorithm Roberto De Prisco a;, Butler Lampson b, Nancy Lynch a a MIT Laboratory for Computer
PART 1 GRAPHICAL STRUCTURE
 PART 1 GRAPHICAL STRUCTURE in this web service in this web service 1 Treewidth and Hypertree Width Georg Gottlob, Gianluigi Greco, Francesco Scarcello This chapter covers methods for identifying islands
PART 1 GRAPHICAL STRUCTURE in this web service in this web service 1 Treewidth and Hypertree Width Georg Gottlob, Gianluigi Greco, Francesco Scarcello This chapter covers methods for identifying islands
To appear in: IEEE Transactions on Knowledge and Data Engineering. The Starburst Active Database Rule System. Jennifer Widom. Stanford University
 To appear in: IEEE Transactions on Knowledge and Data Engineering The Starburst Active Database Rule System Jennifer Widom Department of Computer Science Stanford University Stanford, CA 94305-2140 widom@cs.stanford.edu
To appear in: IEEE Transactions on Knowledge and Data Engineering The Starburst Active Database Rule System Jennifer Widom Department of Computer Science Stanford University Stanford, CA 94305-2140 widom@cs.stanford.edu
CSE 20 DISCRETE MATH. Fall
 CSE 20 DISCRETE MATH Fall 2017 http://cseweb.ucsd.edu/classes/fa17/cse20-ab/ Final exam The final exam is Saturday December 16 11:30am-2:30pm. Lecture A will take the exam in Lecture B will take the exam
CSE 20 DISCRETE MATH Fall 2017 http://cseweb.ucsd.edu/classes/fa17/cse20-ab/ Final exam The final exam is Saturday December 16 11:30am-2:30pm. Lecture A will take the exam in Lecture B will take the exam
Scan Scheduling Specification and Analysis
 Scan Scheduling Specification and Analysis Bruno Dutertre System Design Laboratory SRI International Menlo Park, CA 94025 May 24, 2000 This work was partially funded by DARPA/AFRL under BAE System subcontract
Scan Scheduling Specification and Analysis Bruno Dutertre System Design Laboratory SRI International Menlo Park, CA 94025 May 24, 2000 This work was partially funded by DARPA/AFRL under BAE System subcontract
Gen := 0. Create Initial Random Population. Termination Criterion Satisfied? Yes. Evaluate fitness of each individual in population.
 An Experimental Comparison of Genetic Programming and Inductive Logic Programming on Learning Recursive List Functions Lappoon R. Tang Mary Elaine Cali Raymond J. Mooney Department of Computer Sciences
An Experimental Comparison of Genetic Programming and Inductive Logic Programming on Learning Recursive List Functions Lappoon R. Tang Mary Elaine Cali Raymond J. Mooney Department of Computer Sciences
Unlabeled equivalence for matroids representable over finite fields
 Unlabeled equivalence for matroids representable over finite fields November 16, 2012 S. R. Kingan Department of Mathematics Brooklyn College, City University of New York 2900 Bedford Avenue Brooklyn,
Unlabeled equivalence for matroids representable over finite fields November 16, 2012 S. R. Kingan Department of Mathematics Brooklyn College, City University of New York 2900 Bedford Avenue Brooklyn,
Operational Semantics
 15-819K: Logic Programming Lecture 4 Operational Semantics Frank Pfenning September 7, 2006 In this lecture we begin in the quest to formally capture the operational semantics in order to prove properties
15-819K: Logic Programming Lecture 4 Operational Semantics Frank Pfenning September 7, 2006 In this lecture we begin in the quest to formally capture the operational semantics in order to prove properties
Parallel Program Graphs and their. (fvivek dependence graphs, including the Control Flow Graph (CFG) which
 Parallel Program Graphs and their Classication Vivek Sarkar Barbara Simons IBM Santa Teresa Laboratory, 555 Bailey Avenue, San Jose, CA 95141 (fvivek sarkar,simonsg@vnet.ibm.com) Abstract. We categorize
Parallel Program Graphs and their Classication Vivek Sarkar Barbara Simons IBM Santa Teresa Laboratory, 555 Bailey Avenue, San Jose, CA 95141 (fvivek sarkar,simonsg@vnet.ibm.com) Abstract. We categorize
SORT INFERENCE \coregular" signatures, they derive an algorithm for computing a most general typing for expressions e which is only slightly more comp
 Haskell Overloading is DEXPTIME{complete Helmut Seidl Fachbereich Informatik Universitat des Saarlandes Postfach 151150 D{66041 Saarbrucken Germany seidl@cs.uni-sb.de Febr., 1994 Keywords: Haskell type
Haskell Overloading is DEXPTIME{complete Helmut Seidl Fachbereich Informatik Universitat des Saarlandes Postfach 151150 D{66041 Saarbrucken Germany seidl@cs.uni-sb.de Febr., 1994 Keywords: Haskell type
and therefore the system throughput in a distributed database system [, 1]. Vertical fragmentation further enhances the performance of database transa
![and therefore the system throughput in a distributed database system [, 1]. Vertical fragmentation further enhances the performance of database transa and therefore the system throughput in a distributed database system [, 1]. Vertical fragmentation further enhances the performance of database transa](/thumbs/85/91736920.jpg) Vertical Fragmentation and Allocation in Distributed Deductive Database Systems Seung-Jin Lim Yiu-Kai Ng Department of Computer Science Brigham Young University Provo, Utah 80, U.S.A. Email: fsjlim,ngg@cs.byu.edu
Vertical Fragmentation and Allocation in Distributed Deductive Database Systems Seung-Jin Lim Yiu-Kai Ng Department of Computer Science Brigham Young University Provo, Utah 80, U.S.A. Email: fsjlim,ngg@cs.byu.edu
INF672 Protocol Safety and Verification. Karthik Bhargavan Xavier Rival Thomas Clausen
 INF672 Protocol Safety and Verication Karthik Bhargavan Xavier Rival Thomas Clausen 1 Course Outline Lecture 1 [Today, Sep 15] Introduction, Motivating Examples Lectures 2-4 [Sep 22,29, Oct 6] Network
INF672 Protocol Safety and Verication Karthik Bhargavan Xavier Rival Thomas Clausen 1 Course Outline Lecture 1 [Today, Sep 15] Introduction, Motivating Examples Lectures 2-4 [Sep 22,29, Oct 6] Network
(Preliminary Version 2 ) Jai-Hoon Kim Nitin H. Vaidya. Department of Computer Science. Texas A&M University. College Station, TX
 Towards an Adaptive Distributed Shared Memory (Preliminary Version ) Jai-Hoon Kim Nitin H. Vaidya Department of Computer Science Texas A&M University College Station, TX 77843-3 E-mail: fjhkim,vaidyag@cs.tamu.edu
Towards an Adaptive Distributed Shared Memory (Preliminary Version ) Jai-Hoon Kim Nitin H. Vaidya Department of Computer Science Texas A&M University College Station, TX 77843-3 E-mail: fjhkim,vaidyag@cs.tamu.edu
Binary Decision Diagrams and Symbolic Model Checking
 Binary Decision Diagrams and Symbolic Model Checking Randy Bryant Ed Clarke Ken McMillan Allen Emerson CMU CMU Cadence U Texas http://www.cs.cmu.edu/~bryant Binary Decision Diagrams Restricted Form of
Binary Decision Diagrams and Symbolic Model Checking Randy Bryant Ed Clarke Ken McMillan Allen Emerson CMU CMU Cadence U Texas http://www.cs.cmu.edu/~bryant Binary Decision Diagrams Restricted Form of
CSE 20 DISCRETE MATH. Winter
 CSE 20 DISCRETE MATH Winter 2017 http://cseweb.ucsd.edu/classes/wi17/cse20-ab/ Final exam The final exam is Saturday March 18 8am-11am. Lecture A will take the exam in GH 242 Lecture B will take the exam
CSE 20 DISCRETE MATH Winter 2017 http://cseweb.ucsd.edu/classes/wi17/cse20-ab/ Final exam The final exam is Saturday March 18 8am-11am. Lecture A will take the exam in GH 242 Lecture B will take the exam
A technique for adding range restrictions to. August 30, Abstract. In a generalized searching problem, a set S of n colored geometric objects
 A technique for adding range restrictions to generalized searching problems Prosenjit Gupta Ravi Janardan y Michiel Smid z August 30, 1996 Abstract In a generalized searching problem, a set S of n colored
A technique for adding range restrictions to generalized searching problems Prosenjit Gupta Ravi Janardan y Michiel Smid z August 30, 1996 Abstract In a generalized searching problem, a set S of n colored
LIF Marseille, CNRS & University Aix{Marseille address: URL:
 1D EFFECTIVELY CLOSED SUBSHIFTS AND 2D TILINGS BRUNO DURAND 1, ANDREI ROMASHCHENKO 2, AND ALEXANDER SHEN 2 1 LIF Marseille, CNRS & University Aix{Marseille E-mail address: Bruno.Durand@lif.univ-mrs.fr
1D EFFECTIVELY CLOSED SUBSHIFTS AND 2D TILINGS BRUNO DURAND 1, ANDREI ROMASHCHENKO 2, AND ALEXANDER SHEN 2 1 LIF Marseille, CNRS & University Aix{Marseille E-mail address: Bruno.Durand@lif.univ-mrs.fr
contribution of this paper is to demonstrate that rule orderings can also improve eciency by reducing the number of rule applications. In eect, since
 Rule Ordering in Bottom-Up Fixpoint Evaluation of Logic Programs Raghu Ramakrishnan Divesh Srivastava S. Sudarshan y Computer Sciences Department, University of Wisconsin-Madison, WI 53706, U.S.A. Abstract
Rule Ordering in Bottom-Up Fixpoint Evaluation of Logic Programs Raghu Ramakrishnan Divesh Srivastava S. Sudarshan y Computer Sciences Department, University of Wisconsin-Madison, WI 53706, U.S.A. Abstract
Heap-on-Top Priority Queues. March Abstract. We introduce the heap-on-top (hot) priority queue data structure that combines the
 Heap-on-Top Priority Queues Boris V. Cherkassky Central Economics and Mathematics Institute Krasikova St. 32 117418, Moscow, Russia cher@cemi.msk.su Andrew V. Goldberg NEC Research Institute 4 Independence
Heap-on-Top Priority Queues Boris V. Cherkassky Central Economics and Mathematics Institute Krasikova St. 32 117418, Moscow, Russia cher@cemi.msk.su Andrew V. Goldberg NEC Research Institute 4 Independence
Complexity Theory. Compiled By : Hari Prasad Pokhrel Page 1 of 20. ioenotes.edu.np
 Chapter 1: Introduction Introduction Purpose of the Theory of Computation: Develop formal mathematical models of computation that reflect real-world computers. Nowadays, the Theory of Computation can be
Chapter 1: Introduction Introduction Purpose of the Theory of Computation: Develop formal mathematical models of computation that reflect real-world computers. Nowadays, the Theory of Computation can be
spline structure and become polynomials on cells without collinear edges. Results of this kind follow from the intrinsic supersmoothness of bivariate
 Supersmoothness of bivariate splines and geometry of the underlying partition. T. Sorokina ) Abstract. We show that many spaces of bivariate splines possess additional smoothness (supersmoothness) that
Supersmoothness of bivariate splines and geometry of the underlying partition. T. Sorokina ) Abstract. We show that many spaces of bivariate splines possess additional smoothness (supersmoothness) that
