Legion Bootcamp: Debugging & Profiling Tools
|
|
|
- Charlotte Wade
- 5 years ago
- Views:
Transcription
1 Legion Bootcamp: Debugging & Profiling Tools Wonchan Lee
2 Debugging Tools: Runtime Checks & LegionSpy
3 Runtime Checks Provide warning or error messages when the application breaks runtime s assumptions 3
4 Runtime Checks Provide warning or error messages when the application breaks runtime s assumptions 1. Disjointness checks Verify the disjointness of the index partitioning claimed to be disjoint IndexPartition create_index_partition(context ctx, IndexSpace parent,! const Coloring &coloring,! bool disjoint,! int part_color = -1);! Enabled by passing the -hl:disjointness flag on the command line 2. Privilege Checks 3. Bounds checks $./partitioning -hl:disjointness! Running daxpy for 1024 elements...! Partitioning data into 3 sub-regions...! [0-1] {ERROR}{runtime}: ERROR: colors 0 and 1 of partition 1 are not disjoint when they are claimed to be!! Assertion failed: (false), function create_index_partition, file /Users/wclee/Workspace/ stanford/projects/legion//runtime/runtime.cc, line 5348.! 4
5 Runtime Checks Provide warning or error messages when the application breaks runtime s assumptions 1. Disjointness checks 2. Privilege Checks Dynamically verify if all memory accesses abide by the privileges stated in task s region requirements Compensate lack of static checking from the compiler (However, Legion language has a type system and a compiler. See the next talk!) 3. Bounds checks 4
6 Runtime Checks Provide warning or error messages when the application breaks runtime s assumptions 1. Disjointness checks 2. Privilege Checks Enabled by compiling runtime source with the flag -DPRIVILEGE_CHECKS E.g. 3. Bounds checks TaskLauncher init_launcher(init_field_task_id, TaskArgument(NULL, 0));! init_launcher.add_region_requirement(! RegionRequirement(input_lr, READ_ONLY, EXCLUSIVE, input_lr));! init_launcher.add_field(0, FID_X); runtime->execute_task(ctx, init_launcher);!! void init_field_task(const Task *task, const vector<physicalregion> ®ions,! Context ctx, HighLevelRuntime *runtime)! {!...! RegionAccessor<AccessorType::Generic, double> acc =! regions[0].get_field_accessor(fid_x).typeify<double>();!! for (GenericPointInRectIterator<1> pir(rect); pir; pir++)! acc.write(domainpoint::from_point<1>(pir.p), drand48());! 4
7 Runtime Checks Provide warning or error messages when the application breaks runtime s assumptions 1. Disjointness checks 2. Privilege Checks Enabled by compiling runtime source with the flag -DPRIVILEGE_CHECKS E.g. $./privileges! Running daxpy for 1024 elements...! Initializing field 0...! PRIVILEGE CHECK ERROR IN TASK init_field_task: Need WRITE-DISCARD privileges but only hold READ-ONLY privileges! Assertion failed: (false), function check_privileges, file /Users/wclee/Workspace/stanford/ projects/legion//runtime/accessor.h, line 160.! 3. Bounds checks 4
8 Runtime Checks Provide warning or error messages when the application breaks runtime s assumptions 1. Disjointness checks 2. Privilege checks 3. Bounds Checks Check if all memory accesses fall within the logical region s bounds Enabled by compiling runtime source with the flag -DBOUNDS_CHECKS E.g. $./bounds! Running daxpy for 1024 elements...! Initializing field 0...! Initializing field 1...! Running daxpy computation with alpha ! BOUNDS CHECK ERROR IN TASK 3: Accessing invalid 1D point (1024)! Assertion failed: (false), function check_bounds, file /Users/wclee/Workspace/stanford/ projects/legion//runtime/runtime.cc, line ! 4
9 LegionSpy Provides various visual aids for better program understanding Runtime inserts copies for data movement between tasks, which are not entirely transparent to users Helpful to detect the default mapper s sub-optimal decision (will come to this point later with a simple example) Also able to check logical and physical data flows (mostly useful for runtime developers) 5
10 Steps to Run LegionSpy Compile a Legion application with the -DLEGION_SPY flag added to the CC_FLAGS variable Run the application with the following flags passed on the command line: -cat legion_spy -level 2! The standard error output should be redirect to a file Pass the resulting log file to legion_spy.py! 6
11 Logical and Physical Analyses Logical Analysis (with the -l flag) Compares dependencies computed by the runtime (mdep) with all possible dependencies between operations (adep) Warnings when mdep adep 0 (possibly due to runtime optimizations) Errors when adep mdep 0 (possible runtime bugs, please report us!) Physical Analysis (with the -c flag) Checks if each logical dependence is substantiated by actual data flow between physical instances Reports missing data flows (also possible runtime bugs, please report us!) 7
12 Partitioning Graphs Generated by passing the -P flag to LegionSpy Show index spaces and their partitions Index partitions are in italics Label * on edges means the index partition is disjoint 8
13 Partitioning Graphs (cont d) Also show logical regions and their partitions Logical partitions are in italics Label * on edges means the logical partition is disjoint Each region/partition is specified by index space id, field space id, and tree id 9
14 Event Graphs Generated by the -p flag Visualize operations and their dependences Each box represents an operation instances of index space tasks instances of single tasks copy operations (runtime task) 10
15 Event Graphs Generated by the -p flag Visualize operations and their dependences Each box represents an operation user-triggered copy operations acquire operations release operations 10
16 Event Graphs Generated by the -p flag Visualize operations and their dependences Each box represents an operation Each edge corresponds to explicit dependence between two operations 10
17 Event Graphs (cont d) Passing the -v flag makes the graph also show A list of accessed physical instances with the access privilege and coherence mode Privileges RO: Read-Only WO: Write-Only RW: Read-Write Red: Reduction Coherence E: Exclusive S: Simultaneous A: Atomic R: Relaxed Connections between parent tasks and their child operations 11
18 Instance Graphs (experimental) Generated by the -i flag (add -v for a verbose graph) Provide an instance-centric view of operations Boxes are tasks and ovals are physical instances Solid edges connect tasks with the physical instances they access Dashed edges correspond to copy operations 12
19 More about Debugging Please visit /debugging 13
20 Profiling Tool: LegionProf
21 Steps to Run LegionProf Compile a Legion application with -DLEGION_PROF added to the CC_FLAGS variable Run the application with the following flags passed on the command line: -cat legion_prof -level 2! The standard error output should be redirected to a file You can also pass -hl:prof <int> to specify a node to get the profile result Pass the resulting log file to legion_prof.py! 15
22 Timeline Output Generated by passing the -p flag to LegionProf Shows which tasks ran on which processors at what time and for how long 16
23 Timeline Output Generated by passing the -p flag to LegionProf Shows which tasks ran on which processors at what time and for how long Task id and timestamps appear when hovering a bar 16
24 Timeline Output Generated by passing the -p flag to LegionProf Shows which tasks ran on which processors at what time and for how long The last few lines are for utility processors where runtime tasks run 16
25 Runtime Statistics Additionally LegionProf prints out the statistics of How long each processor was active ****************************************************! PROCESSOR STATS! ****************************************************! CPU Processor 0x1! Total time: us! Active time: 2078 us (18.247%)! Application time: 1932 us (16.965%)! Meta time: 146 us (1.282%)! How many instances were created on each memory ****************************************************! MEMORY STATS! ****************************************************! Memory 0x1! Total Instances: 2! Memory 0x2! Total Instances: 5! How often a task was invoked and how long it was running ! Task Statistics! ! Task ID us (7.959%)! Executions (APP):! Total Invocations: 4! Cummulative Time: 1160 us (2.037%)! Non-Cummulative Time: 1160 us (2.037%)! Average Cum Time: us! Average Non-Cum Time: us! Meta Execution Time (META):! Cummulative Time: 5315 us (9.334%)! Non-Cummulative Time: 3372 us (5.922%)! 17
26 Performance Tuning Configuring runtime parameters Writing a custom mapper Point of mapping interface is to decouple the program correctness from the performance Changing the actual application code 18
27 More about Profiling and Tuning Please visit /profiling 19
28 Performance Tuning Example: Eliminating unnecessary copies
29 Profiling DAXPY Application DAXPY: Double precision A times X Plus Y init_field task: initializes X and Y daxpy task: calculates AXPY check_task: verifies the calculation result 21
30 Profiling DAXPY Application DAXPY: Double precision A times X Plus Y Large gap (454ms) between two tasks init_field task: initializes X and Y daxpy task: calculates AXPY check_task: verifies the calculation result 21
31 Detecting Unnecessary Copies from Event Graph Copy operation 7, 8, and 9 are unnecessarily making local copies to memory 0x2 22
32 Instance Graph of DAXPY instances that merge results from index space tasks local instances for the check_task 23
33 Example Mapper for Avoiding Unnecessary Copies Make the check_task use directly the instances on memory 0x1 (Memory::SYSTEM_MEM) bool DAXPYMapper::map_task(Task *task)! {! if (task->task_id == CHECK_TASK_ID) {! const set<memory> &vis_mems =! machine->get_visible_memories(task->target_proc);! for (unsigned idx = 0; idx < task->regions.size(); idx++) {! for(set<memory>::iterator it = vis_mems.begin();! it!= vis_mems.end(); ++it) {! if (machine->get_memory_kind(*it) == Memory::SYSTEM_MEM)! {! task->regions[idx].target_ranking.push_back(*it);! break;!...! 24
34 Changes in Event Graph Copy operation 7, 8, and 9 disappeared 25
35 Changes in Instance Graph We can verify that the check_task is using directly the instances on the memory 0x1 26
36 Changes in Timeline Gap reduced to 247ms 27
37 Questions?
The Legion Mapping Interface
 The Legion Mapping Interface Mike Bauer 1 Philosophy Decouple specification from mapping Performance portability Expose all mapping (perf) decisions to Legion user Guessing is bad! Don t want to fight
The Legion Mapping Interface Mike Bauer 1 Philosophy Decouple specification from mapping Performance portability Expose all mapping (perf) decisions to Legion user Guessing is bad! Don t want to fight
Demonstration of Legion Runtime Using the PENNANT Mini-App
 Demonstration of Legion Runtime Using the PENNANT Mini-App Charles Ferenbaugh Los Alamos National Laboratory LA-UR-14-29180 1 A brief overview of PENNANT Implements a small subset of basic physics from
Demonstration of Legion Runtime Using the PENNANT Mini-App Charles Ferenbaugh Los Alamos National Laboratory LA-UR-14-29180 1 A brief overview of PENNANT Implements a small subset of basic physics from
CS510 Advanced Topics in Concurrency. Jonathan Walpole
 CS510 Advanced Topics in Concurrency Jonathan Walpole Threads Cannot Be Implemented as a Library Reasoning About Programs What are the valid outcomes for this program? Is it valid for both r1 and r2 to
CS510 Advanced Topics in Concurrency Jonathan Walpole Threads Cannot Be Implemented as a Library Reasoning About Programs What are the valid outcomes for this program? Is it valid for both r1 and r2 to
Givy, a software DSM runtime using raw pointers
 Givy, a software DSM runtime using raw pointers François Gindraud UJF/Inria Compilation days (21/09/2015) F. Gindraud (UJF/Inria) Givy 21/09/2015 1 / 22 Outline 1 Distributed shared memory systems Examples
Givy, a software DSM runtime using raw pointers François Gindraud UJF/Inria Compilation days (21/09/2015) F. Gindraud (UJF/Inria) Givy 21/09/2015 1 / 22 Outline 1 Distributed shared memory systems Examples
Announcements. Office hours. Reading. W office hour will be not starting next week. Chapter 7 (this whole week) CMSC 412 S02 (lect 7)
 Office hours Announcements W office hour will be 10-11 not 11-12 starting next week Reading Chapter 7 (this whole week) 1 Problems with the Producer-Consumer Shared Memory Solution Consider the three address
Office hours Announcements W office hour will be 10-11 not 11-12 starting next week Reading Chapter 7 (this whole week) 1 Problems with the Producer-Consumer Shared Memory Solution Consider the three address
New Mapping Interface
 New Mapping Interface Mike Bauer NVIDIA Research 1 Why Have A Mapping Interface? Legion Program Legion Legion Mapper Scheduling is hard Lots of runtimes have heuristics What do you do when they are wrong?
New Mapping Interface Mike Bauer NVIDIA Research 1 Why Have A Mapping Interface? Legion Program Legion Legion Mapper Scheduling is hard Lots of runtimes have heuristics What do you do when they are wrong?
Clang Static Analyzer Documentation
 Clang Static Analyzer Documentation Release 6 Analyzer Team Aug 13, 2018 Contents 1 Debug Checks 3 1.1 General Analysis Dumpers........................................ 3 1.2 Path Tracking...............................................
Clang Static Analyzer Documentation Release 6 Analyzer Team Aug 13, 2018 Contents 1 Debug Checks 3 1.1 General Analysis Dumpers........................................ 3 1.2 Path Tracking...............................................
The Spin Model Checker : Part I/II
 The Spin Model Checker : Part I/II Moonzoo Kim CS Dept. KAIST Korea Advanced Institute of Science and Technology Motivation: Tragic Accidents Caused by SW Bugs 2 Cost of Software Errors June 2002 Software
The Spin Model Checker : Part I/II Moonzoo Kim CS Dept. KAIST Korea Advanced Institute of Science and Technology Motivation: Tragic Accidents Caused by SW Bugs 2 Cost of Software Errors June 2002 Software
Order Is A Lie. Are you sure you know how your code runs?
 Order Is A Lie Are you sure you know how your code runs? Order in code is not respected by Compilers Processors (out-of-order execution) SMP Cache Management Understanding execution order in a multithreaded
Order Is A Lie Are you sure you know how your code runs? Order in code is not respected by Compilers Processors (out-of-order execution) SMP Cache Management Understanding execution order in a multithreaded
OpenSSD Platform Simulator to Reduce SSD Firmware Test Time. Taedong Jung, Yongmyoung Lee, Ilhoon Shin
 OpenSSD Platform Simulator to Reduce SSD Firmware Test Time Taedong Jung, Yongmyoung Lee, Ilhoon Shin Department of Electronic Engineering, Seoul National University of Science and Technology, South Korea
OpenSSD Platform Simulator to Reduce SSD Firmware Test Time Taedong Jung, Yongmyoung Lee, Ilhoon Shin Department of Electronic Engineering, Seoul National University of Science and Technology, South Korea
CS-211 Fall 2017 Test 1 Version A Oct. 2, Name:
 CS-211 Fall 2017 Test 1 Version A Oct. 2, 2017 True/False Questions... Name: 1. (10 points) For the following, Check T if the statement is true, the F if the statement is false. (a) T F : If I code a C
CS-211 Fall 2017 Test 1 Version A Oct. 2, 2017 True/False Questions... Name: 1. (10 points) For the following, Check T if the statement is true, the F if the statement is false. (a) T F : If I code a C
Tolerating Hardware Device Failures in Software. Asim Kadav, Matthew J. Renzelmann, Michael M. Swift University of Wisconsin Madison
 Tolerating Hardware Device Failures in Software Asim Kadav, Matthew J. Renzelmann, Michael M. Swift University of Wisconsin Madison Current state of OS hardware interaction Many device drivers assume device
Tolerating Hardware Device Failures in Software Asim Kadav, Matthew J. Renzelmann, Michael M. Swift University of Wisconsin Madison Current state of OS hardware interaction Many device drivers assume device
Page 1. Cache Coherence
 Page 1 Cache Coherence 1 Page 2 Memory Consistency in SMPs CPU-1 CPU-2 A 100 cache-1 A 100 cache-2 CPU-Memory bus A 100 memory Suppose CPU-1 updates A to 200. write-back: memory and cache-2 have stale
Page 1 Cache Coherence 1 Page 2 Memory Consistency in SMPs CPU-1 CPU-2 A 100 cache-1 A 100 cache-2 CPU-Memory bus A 100 memory Suppose CPU-1 updates A to 200. write-back: memory and cache-2 have stale
CS315A Midterm Solutions
 K. Olukotun Spring 05/06 Handout #14 CS315a CS315A Midterm Solutions Open Book, Open Notes, Calculator okay NO computer. (Total time = 120 minutes) Name (please print): Solutions I agree to abide by the
K. Olukotun Spring 05/06 Handout #14 CS315a CS315A Midterm Solutions Open Book, Open Notes, Calculator okay NO computer. (Total time = 120 minutes) Name (please print): Solutions I agree to abide by the
The Design of a Distributed Model Checking Algorithm for Spin
 The Design of a Distributed Model Checking Algorithm for Spin Gerard J. Holzmann http://eis.jpl.nasa.gov/lars http://spinroot.com/gerard/ Presented at FMCAD 2006, San Jose, California November 14, 2006
The Design of a Distributed Model Checking Algorithm for Spin Gerard J. Holzmann http://eis.jpl.nasa.gov/lars http://spinroot.com/gerard/ Presented at FMCAD 2006, San Jose, California November 14, 2006
Directory Implementation. A High-end MP
 ectory Implementation Distributed memory each processor (or cluster of processors) has its own memory processor-memory pairs are connected via a multi-path interconnection network snooping with broadcasting
ectory Implementation Distributed memory each processor (or cluster of processors) has its own memory processor-memory pairs are connected via a multi-path interconnection network snooping with broadcasting
Scalable Locking. Adam Belay
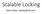 Scalable Locking Adam Belay Problem: Locks can ruin performance 12 finds/sec 9 6 Locking overhead dominates 3 0 0 6 12 18 24 30 36 42 48 Cores Problem: Locks can ruin performance the locks
Scalable Locking Adam Belay Problem: Locks can ruin performance 12 finds/sec 9 6 Locking overhead dominates 3 0 0 6 12 18 24 30 36 42 48 Cores Problem: Locks can ruin performance the locks
Legion Bootcamp: Data Model. Sean Treichler
 Legion Bootcamp: Data Model Sean Treichler 1 Tasks Operate on Data A task has a stack and heap used for private (intra- task) data Nearly all data shared between tasks lives in logical regions Logical
Legion Bootcamp: Data Model Sean Treichler 1 Tasks Operate on Data A task has a stack and heap used for private (intra- task) data Nearly all data shared between tasks lives in logical regions Logical
Designing Memory Consistency Models for. Shared-Memory Multiprocessors. Sarita V. Adve
 Designing Memory Consistency Models for Shared-Memory Multiprocessors Sarita V. Adve Computer Sciences Department University of Wisconsin-Madison The Big Picture Assumptions Parallel processing important
Designing Memory Consistency Models for Shared-Memory Multiprocessors Sarita V. Adve Computer Sciences Department University of Wisconsin-Madison The Big Picture Assumptions Parallel processing important
Just-In-Time Compilation
 Just-In-Time Compilation Thiemo Bucciarelli Institute for Software Engineering and Programming Languages 18. Januar 2016 T. Bucciarelli 18. Januar 2016 1/25 Agenda Definitions Just-In-Time Compilation
Just-In-Time Compilation Thiemo Bucciarelli Institute for Software Engineering and Programming Languages 18. Januar 2016 T. Bucciarelli 18. Januar 2016 1/25 Agenda Definitions Just-In-Time Compilation
Question 1. Notes on the Exam. Today. Comp 104: Operating Systems Concepts 11/05/2015. Revision Lectures
 Comp 104: Operating Systems Concepts Revision Lectures Today Here are a sample of questions that could appear in the exam Please LET ME KNOW if there are particular subjects you want to know about??? 1
Comp 104: Operating Systems Concepts Revision Lectures Today Here are a sample of questions that could appear in the exam Please LET ME KNOW if there are particular subjects you want to know about??? 1
Progress on OpenMP Specifications
 Progress on OpenMP Specifications Wednesday, November 13, 2012 Bronis R. de Supinski Chair, OpenMP Language Committee This work has been authored by Lawrence Livermore National Security, LLC under contract
Progress on OpenMP Specifications Wednesday, November 13, 2012 Bronis R. de Supinski Chair, OpenMP Language Committee This work has been authored by Lawrence Livermore National Security, LLC under contract
CS377P Programming for Performance Multicore Performance Cache Coherence
 CS377P Programming for Performance Multicore Performance Cache Coherence Sreepathi Pai UTCS October 26, 2015 Outline 1 Cache Coherence 2 Cache Coherence Awareness 3 Scalable Lock Design 4 Transactional
CS377P Programming for Performance Multicore Performance Cache Coherence Sreepathi Pai UTCS October 26, 2015 Outline 1 Cache Coherence 2 Cache Coherence Awareness 3 Scalable Lock Design 4 Transactional
AMCAT Automata Coding Sample Questions And Answers
 1) Find the syntax error in the below code without modifying the logic. #include int main() float x = 1.1; switch (x) case 1: printf( Choice is 1 ); default: printf( Invalid choice ); return
1) Find the syntax error in the below code without modifying the logic. #include int main() float x = 1.1; switch (x) case 1: printf( Choice is 1 ); default: printf( Invalid choice ); return
A new, modular dependency solver for cabal-install
 A new, modular dependency solver for cabal-install Andres Löh Well-Typed LLP Duncan Coutts Well-Typed LLP HIW 2011 23 September 2011 Why? Error messages are suboptimal. We want the solver to be more configurable.
A new, modular dependency solver for cabal-install Andres Löh Well-Typed LLP Duncan Coutts Well-Typed LLP HIW 2011 23 September 2011 Why? Error messages are suboptimal. We want the solver to be more configurable.
Notes on the Exam. Question 1. Today. Comp 104:Operating Systems Concepts 11/05/2015. Revision Lectures (separate questions and answers)
 Comp 104:Operating Systems Concepts Revision Lectures (separate questions and answers) Today Here are a sample of questions that could appear in the exam Please LET ME KNOW if there are particular subjects
Comp 104:Operating Systems Concepts Revision Lectures (separate questions and answers) Today Here are a sample of questions that could appear in the exam Please LET ME KNOW if there are particular subjects
Quiz I Solutions MASSACHUSETTS INSTITUTE OF TECHNOLOGY Fall Department of Electrical Engineering and Computer Science
 Department of Electrical Engineering and Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.828 Fall 2012 Quiz I Solutions Mean 65 Median 66 Std. dev 17.5214 14 12 10 8 6 4 2 0 0 10 20 30 40 50 60
Department of Electrical Engineering and Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.828 Fall 2012 Quiz I Solutions Mean 65 Median 66 Std. dev 17.5214 14 12 10 8 6 4 2 0 0 10 20 30 40 50 60
The SPIN Model Checker
 The SPIN Model Checker Metodi di Verifica del Software Andrea Corradini Lezione 1 2013 Slides liberamente adattate da Logic Model Checking, per gentile concessione di Gerard J. Holzmann http://spinroot.com/spin/doc/course/
The SPIN Model Checker Metodi di Verifica del Software Andrea Corradini Lezione 1 2013 Slides liberamente adattate da Logic Model Checking, per gentile concessione di Gerard J. Holzmann http://spinroot.com/spin/doc/course/
Checking System Rules Using System-Specific, Programmer- Written Compiler Extensions
 Motivation for using Checking System Rules Using System-Specific, Programmer- Written Compiler Extensions Dawson Engler Benjamin Chelf Andy Chou Seth Hallem 1 Computer Systems Laboratory Stanford University
Motivation for using Checking System Rules Using System-Specific, Programmer- Written Compiler Extensions Dawson Engler Benjamin Chelf Andy Chou Seth Hallem 1 Computer Systems Laboratory Stanford University
Memory Consistency Models
 Memory Consistency Models Contents of Lecture 3 The need for memory consistency models The uniprocessor model Sequential consistency Relaxed memory models Weak ordering Release consistency Jonas Skeppstedt
Memory Consistency Models Contents of Lecture 3 The need for memory consistency models The uniprocessor model Sequential consistency Relaxed memory models Weak ordering Release consistency Jonas Skeppstedt
Comp 204: Computer Systems and Their Implementation. Lecture 25a: Revision Lectures (separate questions and answers)
 Comp 204: Computer Systems and Their Implementation Lecture 25a: Revision Lectures (separate questions and answers) 1 Today Here are a sample of questions that could appear in the exam Please LET ME KNOW
Comp 204: Computer Systems and Their Implementation Lecture 25a: Revision Lectures (separate questions and answers) 1 Today Here are a sample of questions that could appear in the exam Please LET ME KNOW
RM0327 Reference manual
 Reference manual Multi-Target Trace API version 1.0 Overview Multi-Target Trace (MTT) is an application instrumentation library that provides a consistent way to embed instrumentation into a software application,
Reference manual Multi-Target Trace API version 1.0 Overview Multi-Target Trace (MTT) is an application instrumentation library that provides a consistent way to embed instrumentation into a software application,
Fall 2015 COMP Operating Systems. Lab #3
 Fall 2015 COMP 3511 Operating Systems Lab #3 Outline n Operating System Debugging, Generation and System Boot n Review Questions n Process Control n UNIX fork() and Examples on fork() n exec family: execute
Fall 2015 COMP 3511 Operating Systems Lab #3 Outline n Operating System Debugging, Generation and System Boot n Review Questions n Process Control n UNIX fork() and Examples on fork() n exec family: execute
Section 1: True / False (1 point each, 15 pts total)
 Section : True / False ( point each, pts total) Circle the word TRUE or the word FALSE. If neither is circled, both are circled, or it impossible to tell which is circled, your answer will be considered
Section : True / False ( point each, pts total) Circle the word TRUE or the word FALSE. If neither is circled, both are circled, or it impossible to tell which is circled, your answer will be considered
CS370 Operating Systems
 CS370 Operating Systems Colorado State University Yashwant K Malaiya Spring 1018 L14 Deadlocks Slides based on Text by Silberschatz, Galvin, Gagne Various sources 1 1 FAQ Mutex vs Semaphore 2 2 FAQ Does
CS370 Operating Systems Colorado State University Yashwant K Malaiya Spring 1018 L14 Deadlocks Slides based on Text by Silberschatz, Galvin, Gagne Various sources 1 1 FAQ Mutex vs Semaphore 2 2 FAQ Does
SPIN, PETERSON AND BAKERY LOCKS
 Concurrent Programs reasoning about their execution proving correctness start by considering execution sequences CS4021/4521 2018 jones@scss.tcd.ie School of Computer Science and Statistics, Trinity College
Concurrent Programs reasoning about their execution proving correctness start by considering execution sequences CS4021/4521 2018 jones@scss.tcd.ie School of Computer Science and Statistics, Trinity College
SDD Advanced-User Manual Version 1.1
 SDD Advanced-User Manual Version 1.1 Arthur Choi and Adnan Darwiche Automated Reasoning Group Computer Science Department University of California, Los Angeles Email: sdd@cs.ucla.edu Download: http://reasoning.cs.ucla.edu/sdd
SDD Advanced-User Manual Version 1.1 Arthur Choi and Adnan Darwiche Automated Reasoning Group Computer Science Department University of California, Los Angeles Email: sdd@cs.ucla.edu Download: http://reasoning.cs.ucla.edu/sdd
AP COMPUTER SCIENCE JAVA CONCEPTS IV: RESERVED WORDS
 AP COMPUTER SCIENCE JAVA CONCEPTS IV: RESERVED WORDS PAUL L. BAILEY Abstract. This documents amalgamates various descriptions found on the internet, mostly from Oracle or Wikipedia. Very little of this
AP COMPUTER SCIENCE JAVA CONCEPTS IV: RESERVED WORDS PAUL L. BAILEY Abstract. This documents amalgamates various descriptions found on the internet, mostly from Oracle or Wikipedia. Very little of this
SMP/BIOS Overview. Nov 18, 2014
 SMP/BIOS Overview Nov 18, 2014!!! SMP/BIOS is currently supported only on Cortex-M3/M4 (Ducati/Benelli) subsystems and Cortex-A15 (Vayu/K2/Omap5) subsystems!!! Agenda SMP/BIOS Overview What is SMP/BIOS?
SMP/BIOS Overview Nov 18, 2014!!! SMP/BIOS is currently supported only on Cortex-M3/M4 (Ducati/Benelli) subsystems and Cortex-A15 (Vayu/K2/Omap5) subsystems!!! Agenda SMP/BIOS Overview What is SMP/BIOS?
Assertions, pre/postconditions
 Programming as a contract Assertions, pre/postconditions Assertions: Section 4.2 in Savitch (p. 239) Specifying what each method does q Specify it in a comment before method's header Precondition q What
Programming as a contract Assertions, pre/postconditions Assertions: Section 4.2 in Savitch (p. 239) Specifying what each method does q Specify it in a comment before method's header Precondition q What
reclaim disk space by shrinking files
 Sandeep Sahore reclaim disk space by shrinking files Sandeep Sahore holds a Master s degree in computer science from the University of Toledo and has nearly 15 years of experience in the computing industry.
Sandeep Sahore reclaim disk space by shrinking files Sandeep Sahore holds a Master s degree in computer science from the University of Toledo and has nearly 15 years of experience in the computing industry.
Using a debugger. Segmentation fault? GDB to the rescue!
 Using a debugger Segmentation fault? GDB to the rescue! But first... Let's talk about the quiz Let's talk about the previous homework assignment Let's talk about the current homework assignment K findkey(v
Using a debugger Segmentation fault? GDB to the rescue! But first... Let's talk about the quiz Let's talk about the previous homework assignment Let's talk about the current homework assignment K findkey(v
TSO-CC: Consistency-directed Coherence for TSO. Vijay Nagarajan
 TSO-CC: Consistency-directed Coherence for TSO Vijay Nagarajan 1 People Marco Elver (Edinburgh) Bharghava Rajaram (Edinburgh) Changhui Lin (Samsung) Rajiv Gupta (UCR) Susmit Sarkar (St Andrews) 2 Multicores
TSO-CC: Consistency-directed Coherence for TSO Vijay Nagarajan 1 People Marco Elver (Edinburgh) Bharghava Rajaram (Edinburgh) Changhui Lin (Samsung) Rajiv Gupta (UCR) Susmit Sarkar (St Andrews) 2 Multicores
Processes and Threads
 COS 318: Operating Systems Processes and Threads Kai Li and Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall13/cos318 Today s Topics u Concurrency
COS 318: Operating Systems Processes and Threads Kai Li and Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall13/cos318 Today s Topics u Concurrency
Process Synchronisation (contd.) Deadlock. Operating Systems. Spring CS5212
 Operating Systems Spring 2009-2010 Outline Process Synchronisation (contd.) 1 Process Synchronisation (contd.) 2 Announcements Presentations: will be held on last teaching week during lectures make a 20-minute
Operating Systems Spring 2009-2010 Outline Process Synchronisation (contd.) 1 Process Synchronisation (contd.) 2 Announcements Presentations: will be held on last teaching week during lectures make a 20-minute
THREADS: (abstract CPUs)
 CS 61 Scribe Notes (November 29, 2012) Mu, Nagler, Strominger TODAY: Threads, Synchronization - Pset 5! AT LONG LAST! Adversarial network pong handling dropped packets, server delays, overloads with connection
CS 61 Scribe Notes (November 29, 2012) Mu, Nagler, Strominger TODAY: Threads, Synchronization - Pset 5! AT LONG LAST! Adversarial network pong handling dropped packets, server delays, overloads with connection
Midterm Exam Answers
 Department of Electrical Engineering and Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.824 Fall 2002 Midterm Exam Answers The average score was 55 (out of 80). Here s the distribution: 10 8
Department of Electrical Engineering and Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.824 Fall 2002 Midterm Exam Answers The average score was 55 (out of 80). Here s the distribution: 10 8
Stream Computing using Brook+
 Stream Computing using Brook+ School of Electrical Engineering and Computer Science University of Central Florida Slides courtesy of P. Bhaniramka Outline Overview of Brook+ Brook+ Software Architecture
Stream Computing using Brook+ School of Electrical Engineering and Computer Science University of Central Florida Slides courtesy of P. Bhaniramka Outline Overview of Brook+ Brook+ Software Architecture
Meta-Programming and JIT Compilation
 Meta-Programming and JIT Compilation Sean Treichler 1 Portability vs. Performance Many scientific codes sp ~100% of their cycles in a tiny fraction of the code base We want these kernels to be as fast
Meta-Programming and JIT Compilation Sean Treichler 1 Portability vs. Performance Many scientific codes sp ~100% of their cycles in a tiny fraction of the code base We want these kernels to be as fast
Applications of. Virtual Memory in. OS Design
 Applications of Virtual Memory in OS Design Nima Honarmand Introduction Virtual memory is a powerful level of indirection Indirection: IMO, the most powerful concept in Computer Science Fundamental Theorem
Applications of Virtual Memory in OS Design Nima Honarmand Introduction Virtual memory is a powerful level of indirection Indirection: IMO, the most powerful concept in Computer Science Fundamental Theorem
PROFESSOR: DR.JALILI BY: MAHDI ESHAGHI
 PROFESSOR: DR.JALILI BY: MAHDI ESHAGHI 1 2 Overview Distributed OZ Java RMI CORBA IDL IDL VS C++ CORBA VS RMI 3 Distributed OZ Oz Language Multi paradigm language, strong support for compositionality and
PROFESSOR: DR.JALILI BY: MAHDI ESHAGHI 1 2 Overview Distributed OZ Java RMI CORBA IDL IDL VS C++ CORBA VS RMI 3 Distributed OZ Oz Language Multi paradigm language, strong support for compositionality and
CS 261 Fall C Introduction. Variables, Memory Model, Pointers, and Debugging. Mike Lam, Professor
 CS 261 Fall 2017 Mike Lam, Professor C Introduction Variables, Memory Model, Pointers, and Debugging The C Language Systems language originally developed for Unix Imperative, compiled language with static
CS 261 Fall 2017 Mike Lam, Professor C Introduction Variables, Memory Model, Pointers, and Debugging The C Language Systems language originally developed for Unix Imperative, compiled language with static
New PM: taming a custom pipeline of Falcon JIT
 New PM: taming a custom pipeline of Falcon JIT Fedor Sergeev Azul Systems Compiler team AGENDA Intro to Falcon JIT Legacy Pass Manager Falcon-specific problems New Pass Manager Design & current status
New PM: taming a custom pipeline of Falcon JIT Fedor Sergeev Azul Systems Compiler team AGENDA Intro to Falcon JIT Legacy Pass Manager Falcon-specific problems New Pass Manager Design & current status
There are three basic elements in object oriented programming: encapsulation, inheritance and polymorphism.
 More on Object Oriented Programming Concepts Functional, structured programming often results in programs that describe a hierarchy of tasks to be performed. Object oriented design, however, results in
More on Object Oriented Programming Concepts Functional, structured programming often results in programs that describe a hierarchy of tasks to be performed. Object oriented design, however, results in
Chapter 7: Deadlocks CS370 Operating Systems
 Chapter 7: Deadlocks CS370 Operating Systems Objectives: Description of deadlocks, which prevent sets of concurrent processes from completing their tasks Different methods for preventing or avoiding deadlocks
Chapter 7: Deadlocks CS370 Operating Systems Objectives: Description of deadlocks, which prevent sets of concurrent processes from completing their tasks Different methods for preventing or avoiding deadlocks
Parallelism Marco Serafini
 Parallelism Marco Serafini COMPSCI 590S Lecture 3 Announcements Reviews First paper posted on website Review due by this Wednesday 11 PM (hard deadline) Data Science Career Mixer (save the date!) November
Parallelism Marco Serafini COMPSCI 590S Lecture 3 Announcements Reviews First paper posted on website Review due by this Wednesday 11 PM (hard deadline) Data Science Career Mixer (save the date!) November
High Level Programming for GPGPU. Jason Yang Justin Hensley
 Jason Yang Justin Hensley Outline Brook+ Brook+ demonstration on R670 AMD IL 2 Brook+ Introduction 3 What is Brook+? Brook is an extension to the C-language for stream programming originally developed
Jason Yang Justin Hensley Outline Brook+ Brook+ demonstration on R670 AMD IL 2 Brook+ Introduction 3 What is Brook+? Brook is an extension to the C-language for stream programming originally developed
Objectives. Introduce static keyword examine syntax describe common uses
 Static Objectives Introduce static keyword examine syntax describe common uses 2 Static Static represents something which is part of a type rather than part of an object Two uses of static field method
Static Objectives Introduce static keyword examine syntax describe common uses 2 Static Static represents something which is part of a type rather than part of an object Two uses of static field method
Priority Queues (Heaps)
 Priority Queues (Heaps) October 11, 2016 CMPE 250 Priority Queues October 11, 2016 1 / 29 Priority Queues Many applications require that we process records with keys in order, but not necessarily in full
Priority Queues (Heaps) October 11, 2016 CMPE 250 Priority Queues October 11, 2016 1 / 29 Priority Queues Many applications require that we process records with keys in order, but not necessarily in full
Sendmail crackaddr - Static Analysis strikes back
 Sendmail crackaddr - Static Analysis strikes back Bogdan Mihaila Technical University of Munich, Germany December 6, 2014 Name Lastname < name@mail.org > ()()()()()()()()()... ()()() 1 / 25 Abstract Interpretation
Sendmail crackaddr - Static Analysis strikes back Bogdan Mihaila Technical University of Munich, Germany December 6, 2014 Name Lastname < name@mail.org > ()()()()()()()()()... ()()() 1 / 25 Abstract Interpretation
Assertions & Design-by-Contract using JML Erik Poll University of Nijmegen
 Assertions & Design-by-Contract using JML Erik Poll University of Nijmegen Erik Poll - JML p.1/39 Overview Assertions Design-by-Contract for Java using JML Contracts and Inheritance Tools for JML Demo
Assertions & Design-by-Contract using JML Erik Poll University of Nijmegen Erik Poll - JML p.1/39 Overview Assertions Design-by-Contract for Java using JML Contracts and Inheritance Tools for JML Demo
CS307 Operating Systems Deadlocks
 CS307 Deadlocks Fan Wu Department of Computer Science and Engineering Shanghai Jiao Tong University Spring 2016 Bridge Crossing Example Traffic only in one direction Each section of a bridge can be viewed
CS307 Deadlocks Fan Wu Department of Computer Science and Engineering Shanghai Jiao Tong University Spring 2016 Bridge Crossing Example Traffic only in one direction Each section of a bridge can be viewed
Deadlocks. Bridge Crossing Example. The Problem of Deadlock. Deadlock Characterization. Resource-Allocation Graph. System Model
 CS07 Bridge Crossing Example Deadlocks Fan Wu Department of Computer Science and Engineering Shanghai Jiao Tong University Spring 2016 Traffic only in one direction Each section of a bridge can be viewed
CS07 Bridge Crossing Example Deadlocks Fan Wu Department of Computer Science and Engineering Shanghai Jiao Tong University Spring 2016 Traffic only in one direction Each section of a bridge can be viewed
A framework for verification of Program Control Unit of VLIW processors
 A framework for verification of Program Control Unit of VLIW processors Santhosh Billava, Saankhya Labs, Bangalore, India (santoshb@saankhyalabs.com) Sharangdhar M Honwadkar, Saankhya Labs, Bangalore,
A framework for verification of Program Control Unit of VLIW processors Santhosh Billava, Saankhya Labs, Bangalore, India (santoshb@saankhyalabs.com) Sharangdhar M Honwadkar, Saankhya Labs, Bangalore,
Legion: Expressing Locality and Independence with Logical Regions
 Legion: Expressing Locality and Independence with Logical Regions Michael Bauer Stanford University mebauer@cs.stanford.edu Sean Treichler Stanford University sjt@cs.stanford.edu Elliott Slaughter Stanford
Legion: Expressing Locality and Independence with Logical Regions Michael Bauer Stanford University mebauer@cs.stanford.edu Sean Treichler Stanford University sjt@cs.stanford.edu Elliott Slaughter Stanford
CS370 Operating Systems
 CS370 Operating Systems Colorado State University Yashwant K Malaiya Spring 2018 L16 Deadlocks, Main Memory Slides based on Text by Silberschatz, Galvin, Gagne Various sources 1 1 Where we are: Deadlocks
CS370 Operating Systems Colorado State University Yashwant K Malaiya Spring 2018 L16 Deadlocks, Main Memory Slides based on Text by Silberschatz, Galvin, Gagne Various sources 1 1 Where we are: Deadlocks
REACT. REACT: Event-driven Asynchronous Concurrent Turing-complete
 REACT REACT: Event-driven Asynchronous Concurrent Turing-complete Students: Will Noble, Aleksandar Milicevic Supervisor: Stelios Sidiroglou PI: Prof. Martin Rinard Robotics Programming Abstraction gap
REACT REACT: Event-driven Asynchronous Concurrent Turing-complete Students: Will Noble, Aleksandar Milicevic Supervisor: Stelios Sidiroglou PI: Prof. Martin Rinard Robotics Programming Abstraction gap
my $full_path = can_run('wget') or warn 'wget is not installed!';
 NAME IPC::Cmd - finding and running system commands made easy SYNOPSIS use IPC::Cmd qw[can_run run run_forked]; my $full_path = can_run('wget') or warn 'wget is not installed!'; ### commands can be arrayrefs
NAME IPC::Cmd - finding and running system commands made easy SYNOPSIS use IPC::Cmd qw[can_run run run_forked]; my $full_path = can_run('wget') or warn 'wget is not installed!'; ### commands can be arrayrefs
Distributed Shared Memory
 Distributed Shared Memory History, fundamentals and a few examples Coming up The Purpose of DSM Research Distributed Shared Memory Models Distributed Shared Memory Timeline Three example DSM Systems The
Distributed Shared Memory History, fundamentals and a few examples Coming up The Purpose of DSM Research Distributed Shared Memory Models Distributed Shared Memory Timeline Three example DSM Systems The
DPHPC: Introduction to OpenMP Recitation session
 SALVATORE DI GIROLAMO DPHPC: Introduction to OpenMP Recitation session Based on http://openmp.org/mp-documents/intro_to_openmp_mattson.pdf OpenMP An Introduction What is it? A set
SALVATORE DI GIROLAMO DPHPC: Introduction to OpenMP Recitation session Based on http://openmp.org/mp-documents/intro_to_openmp_mattson.pdf OpenMP An Introduction What is it? A set
Operating Systems Comprehensive Exam. Spring Student ID # 3/16/2006
 Operating Systems Comprehensive Exam Spring 2006 Student ID # 3/16/2006 You must complete all of part I (60%) You must complete two of the three sections in part II (20% each) In Part I, circle or select
Operating Systems Comprehensive Exam Spring 2006 Student ID # 3/16/2006 You must complete all of part I (60%) You must complete two of the three sections in part II (20% each) In Part I, circle or select
Stateflow Best Practices By Michael Burke
 Stateflow Best Practices By Michael Burke 2012 The MathWorks, Inc. 1 Topics Background Overview of terms Readability Stateflow hierarchy Modeling tips Basic rules: MAAB style guide 2 Background Objective
Stateflow Best Practices By Michael Burke 2012 The MathWorks, Inc. 1 Topics Background Overview of terms Readability Stateflow hierarchy Modeling tips Basic rules: MAAB style guide 2 Background Objective
A Practical Approach to Programming With Assertions
 A Practical Approach to Programming With Assertions Ken Bell Christian-Albrechts Universität Kiel Department of Computer Science and Applied Mathematics Real-Time Systems and Embedded Systems Group July
A Practical Approach to Programming With Assertions Ken Bell Christian-Albrechts Universität Kiel Department of Computer Science and Applied Mathematics Real-Time Systems and Embedded Systems Group July
Fall 2015 COMP Operating Systems. Lab 06
 Fall 2015 COMP 3511 Operating Systems Lab 06 Outline Monitor Deadlocks Logical vs. Physical Address Space Segmentation Example of segmentation scheme Paging Example of paging scheme Paging-Segmentation
Fall 2015 COMP 3511 Operating Systems Lab 06 Outline Monitor Deadlocks Logical vs. Physical Address Space Segmentation Example of segmentation scheme Paging Example of paging scheme Paging-Segmentation
Regent. Elliott Slaughter. December 8, 2015
 Regent Elliott Slaughter 1 Regent A language for the Legion programming model Implicit parallelism, sequential semantics Tasks + automatic discovery of depences Automatic data movement A A(r) for i = 0,
Regent Elliott Slaughter 1 Regent A language for the Legion programming model Implicit parallelism, sequential semantics Tasks + automatic discovery of depences Automatic data movement A A(r) for i = 0,
CPSC/ECE 3220 Fall 2017 Exam Give the definition (note: not the roles) for an operating system as stated in the textbook. (2 pts.
 CPSC/ECE 3220 Fall 2017 Exam 1 Name: 1. Give the definition (note: not the roles) for an operating system as stated in the textbook. (2 pts.) Referee / Illusionist / Glue. Circle only one of R, I, or G.
CPSC/ECE 3220 Fall 2017 Exam 1 Name: 1. Give the definition (note: not the roles) for an operating system as stated in the textbook. (2 pts.) Referee / Illusionist / Glue. Circle only one of R, I, or G.
What is the Race Condition? And what is its solution? What is a critical section? And what is the critical section problem?
 What is the Race Condition? And what is its solution? Race Condition: Where several processes access and manipulate the same data concurrently and the outcome of the execution depends on the particular
What is the Race Condition? And what is its solution? Race Condition: Where several processes access and manipulate the same data concurrently and the outcome of the execution depends on the particular
EMBEDDED SYSTEMS PROGRAMMING More About Languages
 EMBEDDED SYSTEMS PROGRAMMING 2015-16 More About Languages JAVA: ANNOTATIONS (1/2) Structured comments to source code (=metadata). They provide data about the code, but they are not part of the code itself
EMBEDDED SYSTEMS PROGRAMMING 2015-16 More About Languages JAVA: ANNOTATIONS (1/2) Structured comments to source code (=metadata). They provide data about the code, but they are not part of the code itself
Distributed Systems (ICE 601) Transactions & Concurrency Control - Part1
 Distributed Systems (ICE 601) Transactions & Concurrency Control - Part1 Dongman Lee ICU Class Overview Transactions Why Concurrency Control Concurrency Control Protocols pessimistic optimistic time-based
Distributed Systems (ICE 601) Transactions & Concurrency Control - Part1 Dongman Lee ICU Class Overview Transactions Why Concurrency Control Concurrency Control Protocols pessimistic optimistic time-based
5) Attacker causes damage Different to gaining control. For example, the attacker might quit after gaining control.
 Feb 23, 2009 CSE, 409/509 Mitigation of Bugs, Life of an exploit 1) Bug inserted into code 2) Bug passes testing 3) Attacker triggers bug 4) The Attacker gains control of the program 5) Attacker causes
Feb 23, 2009 CSE, 409/509 Mitigation of Bugs, Life of an exploit 1) Bug inserted into code 2) Bug passes testing 3) Attacker triggers bug 4) The Attacker gains control of the program 5) Attacker causes
System Administration and Network Security
 System Administration and Network Security Master SSCI, M2P subject Duration: up to 3 hours. All answers should be justified. Clear and concise answers will be rewarded. 1 Network Administration To keep
System Administration and Network Security Master SSCI, M2P subject Duration: up to 3 hours. All answers should be justified. Clear and concise answers will be rewarded. 1 Network Administration To keep
Portland State University ECE 588/688. Memory Consistency Models
 Portland State University ECE 588/688 Memory Consistency Models Copyright by Alaa Alameldeen 2018 Memory Consistency Models Formal specification of how the memory system will appear to the programmer Places
Portland State University ECE 588/688 Memory Consistency Models Copyright by Alaa Alameldeen 2018 Memory Consistency Models Formal specification of how the memory system will appear to the programmer Places
Efficient concurrent waiting for C++20
 Doc number: P0514R3 Revises: P0514R2, P0126R2, N4195 Date: 2018-02-10 Project: Programming Language C++, Concurrency Working Group Reply-to: Olivier Giroux Efficient concurrent waiting
Doc number: P0514R3 Revises: P0514R2, P0126R2, N4195 Date: 2018-02-10 Project: Programming Language C++, Concurrency Working Group Reply-to: Olivier Giroux Efficient concurrent waiting
PERFORMANCE ANALYSIS AND DEBUGGING FOR VOLTA. Felix Schmitt 11 th Parallel Tools Workshop September 11-12, 2017
 PERFORMANCE ANALYSIS AND DEBUGGING FOR VOLTA Felix Schmitt 11 th Parallel Tools Workshop September 11-12, 2017 INTRODUCING TESLA V100 Volta Architecture Improved NVLink & HBM2 Volta MPS Improved SIMT Model
PERFORMANCE ANALYSIS AND DEBUGGING FOR VOLTA Felix Schmitt 11 th Parallel Tools Workshop September 11-12, 2017 INTRODUCING TESLA V100 Volta Architecture Improved NVLink & HBM2 Volta MPS Improved SIMT Model
CIS Operating Systems Memory Management Address Translation for Paging. Professor Qiang Zeng Spring 2018
 CIS 3207 - Operating Systems Memory Management Address Translation for Paging Professor Qiang Zeng Spring 2018 Previous class What is logical address? Who use it? Describes a location in the logical memory
CIS 3207 - Operating Systems Memory Management Address Translation for Paging Professor Qiang Zeng Spring 2018 Previous class What is logical address? Who use it? Describes a location in the logical memory
Data Handling in OpenMP
 Data Handling in OpenMP Manipulate data by threads By private: a thread initializes and uses a variable alone Keep local copies, such as loop indices By firstprivate: a thread repeatedly reads a variable
Data Handling in OpenMP Manipulate data by threads By private: a thread initializes and uses a variable alone Keep local copies, such as loop indices By firstprivate: a thread repeatedly reads a variable
Formal Methods for Software Development
 Formal Methods for Software Development Verification with Spin Wolfgang Ahrendt 07 September 2018 FMSD: Spin /GU 180907 1 / 34 Spin: Previous Lecture vs. This Lecture Previous lecture Spin appeared as
Formal Methods for Software Development Verification with Spin Wolfgang Ahrendt 07 September 2018 FMSD: Spin /GU 180907 1 / 34 Spin: Previous Lecture vs. This Lecture Previous lecture Spin appeared as
CS 471 Operating Systems. Yue Cheng. George Mason University Fall 2017
 CS 471 Operating Systems Yue Cheng George Mason University Fall 2017 1 Review: Sync Terminology Worksheet 2 Review: Semaphores 3 Semaphores o Motivation: Avoid busy waiting by blocking a process execution
CS 471 Operating Systems Yue Cheng George Mason University Fall 2017 1 Review: Sync Terminology Worksheet 2 Review: Semaphores 3 Semaphores o Motivation: Avoid busy waiting by blocking a process execution
Seminar in Software Engineering Presented by Dima Pavlov, November 2010
 Seminar in Software Engineering-236800 Presented by Dima Pavlov, November 2010 1. Introduction 2. Overview CBMC and SAT 3. CBMC Loop Unwinding 4. Running CBMC 5. Lets Compare 6. How does it work? 7. Conclusions
Seminar in Software Engineering-236800 Presented by Dima Pavlov, November 2010 1. Introduction 2. Overview CBMC and SAT 3. CBMC Loop Unwinding 4. Running CBMC 5. Lets Compare 6. How does it work? 7. Conclusions
Effective Data-Race Detection for the Kernel
 Effective Data-Race Detection for the Kernel John Erickson, Madanlal Musuvathi, Sebastian Burckhardt, Kirk Olynyk Microsoft Research Presented by Thaddeus Czauski 06 Aug 2011 CS 5204 2 How do we prevent
Effective Data-Race Detection for the Kernel John Erickson, Madanlal Musuvathi, Sebastian Burckhardt, Kirk Olynyk Microsoft Research Presented by Thaddeus Czauski 06 Aug 2011 CS 5204 2 How do we prevent
Pieter van den Hombergh. Fontys Hogeschool voor Techniek en Logistiek. September 9, 2016
 Pieter van den Hombergh Fontys Hogeschool voor Techniek en Logistiek September 9, 2016 Contents /FHTenL September 9, 2016 2/35 UML State Uses and application In behaviour is modeled with state charts (diagrams)
Pieter van den Hombergh Fontys Hogeschool voor Techniek en Logistiek September 9, 2016 Contents /FHTenL September 9, 2016 2/35 UML State Uses and application In behaviour is modeled with state charts (diagrams)
Oracle Database 11g: Program with PL/SQL Release 2
 Oracle University Contact Us: +41- (0) 56 483 31 31 Oracle Database 11g: Program with PL/SQL Release 2 Duration: 5 Days What you will learn This course introduces students to PL/SQL and helps them understand
Oracle University Contact Us: +41- (0) 56 483 31 31 Oracle Database 11g: Program with PL/SQL Release 2 Duration: 5 Days What you will learn This course introduces students to PL/SQL and helps them understand
SMP/BIOS Overview. March 19, 2015
 SMP/BIOS Overview March 19, 2015!!! SMP/BIOS is currently supported only on Cortex-M3/M4 (Ducati/Benelli) subsystems and Cortex-A15 (DRA7xx/K2/Omap5) subsystems!!! Agenda SMP/BIOS Overview What is SMP/BIOS?
SMP/BIOS Overview March 19, 2015!!! SMP/BIOS is currently supported only on Cortex-M3/M4 (Ducati/Benelli) subsystems and Cortex-A15 (DRA7xx/K2/Omap5) subsystems!!! Agenda SMP/BIOS Overview What is SMP/BIOS?
Laboratorio di Tecnologie dell'informazione
 Laboratorio di Tecnologie dell'informazione Ing. Marco Bertini marco.bertini@unifi.it http://www.micc.unifi.it/bertini/ Code testing: techniques and tools Testing can show the presence of errors, but not
Laboratorio di Tecnologie dell'informazione Ing. Marco Bertini marco.bertini@unifi.it http://www.micc.unifi.it/bertini/ Code testing: techniques and tools Testing can show the presence of errors, but not
Parallelizing SPECjbb2000 with Transactional Memory
 Parallelizing SPECjbb2000 with Transactional Memory JaeWoong Chung, Chi Cao Minh,, Brian D. Carlstrom, Christos Kozyrakis Picture comes here Computer Systems Lab Stanford University http://tcc.stanford.edu
Parallelizing SPECjbb2000 with Transactional Memory JaeWoong Chung, Chi Cao Minh,, Brian D. Carlstrom, Christos Kozyrakis Picture comes here Computer Systems Lab Stanford University http://tcc.stanford.edu
Chapter 5: Process Synchronization. Operating System Concepts 9 th Edition
 Chapter 5: Process Synchronization Silberschatz, Galvin and Gagne 2013 Chapter 5: Process Synchronization Background The Critical-Section Problem Peterson s Solution Synchronization Hardware Mutex Locks
Chapter 5: Process Synchronization Silberschatz, Galvin and Gagne 2013 Chapter 5: Process Synchronization Background The Critical-Section Problem Peterson s Solution Synchronization Hardware Mutex Locks
CSE 230 Intermediate Programming in C and C++ Functions
 CSE 230 Intermediate Programming in C and C++ Functions Fall 2017 Stony Brook University Instructor: Shebuti Rayana shebuti.rayana@stonybrook.edu http://www3.cs.stonybrook.edu/~cse230/ Concept of Functions
CSE 230 Intermediate Programming in C and C++ Functions Fall 2017 Stony Brook University Instructor: Shebuti Rayana shebuti.rayana@stonybrook.edu http://www3.cs.stonybrook.edu/~cse230/ Concept of Functions
Android Kernel Security
 Jeff Vander Stoep and Sami Tolvanen Android Kernel Security Linux Security Summit Aug 2018 Acknowledgements People who have reported security vulnerabilities to Android security: https://source.android.com/security/overview/acknowledgements
Jeff Vander Stoep and Sami Tolvanen Android Kernel Security Linux Security Summit Aug 2018 Acknowledgements People who have reported security vulnerabilities to Android security: https://source.android.com/security/overview/acknowledgements
Chapter 7: Deadlocks
 Chapter 7: Deadlocks System Model Deadlock Characterization Methods for Handling Deadlocks Deadlock Prevention Deadlock Avoidance Deadlock Detection Recovery from Deadlock Combined Approach to Deadlock
Chapter 7: Deadlocks System Model Deadlock Characterization Methods for Handling Deadlocks Deadlock Prevention Deadlock Avoidance Deadlock Detection Recovery from Deadlock Combined Approach to Deadlock
Relational Operators and if. Class 10
 Relational Operators and if Class 10 Data Type a data type consists of two things: Data Type a data type consists of two things: a set of values Data Type a data type consists of two things: a set of values
Relational Operators and if Class 10 Data Type a data type consists of two things: Data Type a data type consists of two things: a set of values Data Type a data type consists of two things: a set of values
