A few examples are below. Checking your results in decimal is the easiest way to verify you ve got it correct.
|
|
|
- Elizabeth Kathryn Howard
- 5 years ago
- Views:
Transcription
1 CS107 Handout 22S Spring 2007 May 4, 2007 Assignment 5 Solution Brought to you by Julie Zelenski and Jerry Cain. Problem 1: Binary numbers and bit operations A few examples are below. Checking your results in decimal is the easiest way to verify you ve got it correct. 58 = = = = = = = = = *3 = * = = 60 Adding one to the maximum signed short (32767) gives the most negative short Adding one to the maximum unsigned short (65535) returns zero. In both cases, it is doing the usual binary arithmetic and carrying the last bit into the sign bit or off the end, wrapping back into range. No error is reported in either case. Assigning from larger to smaller type just truncates to the lower byte(s). For example, assigning the short 1025 to a char produces 1. The other direction has no problem or truncation. The remainder of a number when divided by 4 can be found in the bits in the places below 4 (i.e. the bits in the 2 and 1 s place). Thus we want to get the value of just those bits from the number. A bitwise AND can pull out a specific subset of bits, by AND ing with something that has just those bits on. The integer 3 has only the 2 and 1 bits on, so if we take a number and bitwise AND it with 3, we can quickly compute its remainder when divided by 4: printf( Remainder of %d is %d\n, num, num & 3); If the upper byte of a short is all zero bits, then we can assign it to a char without data loss. Using a similar approach as above, we can extract just the high order bits from a number to see whether they are all zeros. The short with all the upper bits on is ( ). printf( High byte of %d clear? %d \n, num, (num & 32512) == 0));
2 There are easier and more portable ways to compute the number to AND against (using bitmask or bit shifting), but we won t get into it for now. To change a number s sign in two s complement, we need to invert all the bits and add one. Inverting all the bits can be done with a bitwise XOR with that number that has all bits on. This operation will turn all bits previously off on and all bits on off, exactly what we want. The value with all bits on is 1. printf( Start with %d, change sign %dn, num, (num ^ -1) + 1); Here s a simple encryption/decryption program that reads a file from standard input and writes the result to standard output. It encrypts every character with a constant key of Z. You could adapt it to encrypt by shorts or ints and using different keys if you felt like it. If you run this program twice on the same file, you will get the original contents back. #include <stdio.h> #define KEY Z int main(void) int ch; 2 while ((ch = getc(stdin))!= EOF) putc(ch ^ KEY, stdout); return 0; Probelm 2: ASCII and extended ASCII As expected, the mapping for characters in the bottom half of the range is wellestablished, but the upper half is full of variation. For example, the ASCII value 153 is mapped to the trademark symbol on the Mac, but to the u with a circumflex over it on UNIX. Setting up a web page or sending an with extended ASCII characters is therefore not a reliable activity. Unless the receiver is using a system with the same character mappings, there is no guarantee your intention is properly interpreted.
3 Problem 3: It's just bits and bytes This is from an epic, results can differ due to machine endianness or instruction encoding: The string "hi!" as an integer: , as an instruction: call 0xa1a59c00. The integer 3 as float: e-45, which is definitely not 3.0. struct binky b; printf("printing 4-byte struct as float %f\n", *(float *)&b); int i; char *s = "Hi there!"; i = *(int *)s; short s = 1; // s will have 1 in LSB, 0 in MSB char ch = *(char *)&s; // read out first byte of short printf("endian is %s.\n". (ch == 0? "big" : "little")); float f = ; printf( Value %d\n, f); // printf will use unconverted bits 3 Problem 4: Identical Outputs As we ve stressed in lecture, type information is used at compile-time to make decisions about how many bytes of data to load/store and calculating offsets and the like, but all that is left at runtime is a sequence of instructions and data laid out in memory for it to operate on. Looking at the generated code tells you little about what a given 4 bytes is: an int? a struct fraction *? a sequence of 4 characters? It is possible for many different C functions to compile to the same output the exact same sequence of CPU instructions is appropriate if the functions access the same memory locations in the same pattern. For example, look at this set of machine instructions: R2 = Mem[] R3 = R2 + 4 R4 = Mem[ + 4] Mem[R4] = R3 a) void PtrOnly(void) int **b, *a; *b = &a[1]; // or equivalently, *b = a + 1
4 4 b) void IntOnly(void) int arr[2]; *(int *)(arr[1]) = arr[0] + 4; Problem 5: Find the linked list The basic strategy is to scan the heap from bottom to top, at each location try to interpret the bytes as though they were the head node of such a list. We check what would be the data field and if it matches what we want, we access what would be the next field, verify that it points into a valid area of the heap and then dereference and see if what follows matches the rest of the list. const void *const kheapend = ((char *)kheapstart + kheapsize - sizeof(list)) bool islistonheap(void) const char *pos; for (pos = kheapstart; pos <= kheapend; pos++) const struct list *current = (struct list *)position; if ((current->data == 1) && isinheap(current->next)) current = current->next; if ((current->data == 2) && isinheap(current->next)) current = current->next; if (current->data == 3) && (current->next == NULL)) return true; return false; static bool isinheap(const void *ptr) return (ptr >= kheapstart && ptr <= kheapend); // Helper function
5 5 line 1 line 2 line 3 Problem 6: Homestar Runner: The System Is Down a) Consider the following record definition: typedef struct int coachz; short *thecheat[2]; homestarrunner **strongbad; homestarrunner; void pompom(homestarrunner strongmad, homestarrunner *marzipan) char bubs[4]; bubs[*bubs] = *(marzipan->thecheat[strongmad.coachz]); ((homestarrunner *)(strongmad.thecheat))->strongbad += *(int *)bubs; Generate code for the entire pompom function. // line 1 = 4; // line 2 R1 =.1 M[]; R1 = + R1; // make space for 4 characters on the stack // load *bubs // prepare bubs + *bubs R2 = M[ + 24]; // load marzipan R2 = R2 + 4; // advance R2 to address thecheat[0] instead of coachz R3 = M[ + 8]; // load strongmad.coachz R3 = R3 * 4; // scale offset by sizeof(short *) R2 = R2 + R3; // advance R2 to address thecheat[strongmad.coach] R2 = M[R2]; // pull thecheat[strongmad.coach] into R2 R2 =.2 M[R2]; // pull short M[R1] =.1 R2; // assign short to one byte at bubs + *bubs marzipan // line 3 R1 = M[]; // load bubs[0-3] as a single int R1 = R1 * 4; // scale by sizeof(homestarrunner *) R2 = + 24; // prepare address of pretend strongbad R3 = M[R2]; // load old strongbad value strongmad R3 = R3 + R1; // do pointer arithmetic M[R2] = R3; // flush new value to strongbad // clean up (not require, though here for completeness) = + 4; RETURN; strongbad thecheat[1] thecheat[0] coachz return PC bubs[0-3]
6 b) Now generate code for the puppetthing function. You needn t draw the stack frame out, but it can only help. homestarrunner **puppetthing(homestarrunner *marshie, homestarrunner& mrshmallow) return (**puppetthing(&mrshmallow, *marshie)).strongbad; 6 R1 = M[ + 8]; // &mrshallow is address of referenced objects R2 = M[ + 4]; // passing *marshie by ref requires marshie be passed = 8; // make space for two params of recursive call M[] = R1; // put &mrshmallow at the bottom M[ + 4] = R2; // place marshie above that CALL <puppetthing> // call, expecting RV to be populated with a double ptr = + 8; // clean up params R1 = M[RV]; // dereference RV to get homestarrunner * RV = M[R1 + 12]; // replace RV with contents of strongbad field relative // to R1 address RET; // answer is in RV let s get out of here mrshmallow marshie return PC mrshmallow marshie
7 7 Problem 7: The Hitchhiker s Guide To The Galaxy Consider the following type and function definition: line 1 line 2 line 3 typedef struct short **arthur; char ford[12]; int trillian; short zaphod[6]; galaxy; static galaxy *hitchhikersguide(galaxy *mice, short **dolphins); static short *thanksforallthefish(galaxy marvin, int *deepthought) marvin.zaphod[100] = deepthought[*marvin.ford]; ((galaxy *)((galaxy *)(marvin.zaphod))->ford)->trillian = **marvin.arthur; return hitchhikersguide(&marvin + 1, marvin.arthur)->arthur[10]; Generate code for the entire thanksforallthefish function. Be clear about what assembly code corresponds to what line. // line 1 R1 = M[ + 36]; R2 =.1 M[ + 8]; R3 = R2 * 4; R4 = R1 + R3; R5 = M[R4]; M[ + 224] =.2 R5; // line 2 R1 = M[ + 4]; R2 = M[R1]; R3 =.2 M[R2]; M[ + 44] = R3; // load deepthought marvin.zaphod[4 5] // load *marvin.ford // scale by sizeof(int) marvin.zaphod[2 3] // compute &deepthought[*marvin.ford] // load int of rhs marvin.zaphod[0 1] // flush to marvin.zaphod[100] // load marvin.arthur // load *marvin.arthur // load **marvin.arthur // flush to trillian field deepthought marvin.trillian marvin.ford[8 11] marvin.ford[4 7] // line 3 R1 = + 36; // load &marvin + 1 marvin.ford[0 3] CALL <hitchhikersguide> R2 = M[ + 4]; M[] = R1; // load marvin.arthur // load &marvin + 1 = 8; M[ + 4] = R2; // make space for params // load marvin.arthur marvin.arthur saved pc = + 8; // clean up params R1 = M[RV]; // load arthur field of galaxy addressed by return value RV = M[R1 + 40]; // load 10 th pointer to short in array of short pointers RET;
8 8 Problem 8: C++ s Dark Side class jedimaster public: int luke(jedimaster *macewindu, jedimaster obiwan); int& anakin(short *padme, jedimaster& leia); ; private: short council[4]; short *yoda; obiwan.council[0..1] int jedimaster::luke(jedimaster *macewindu, jedimaster obiwan) macewindu line 1 obiwan.yoda += macewindu->council[40]; this line 2 return obiwan.anakin((short *) &obiwan, *this); portion built just before anakin method is called obiwan.council[2..3] obiwan.yoda leia padme this saved PC This was straightforward code generation, save for the fact that you needed to understand that k-argument methods operate just like k+1-argument functions, where the address of the relevant object is spliced in as argument 0 and everything else is shifted over to make room. // obiwan.yoda += macewindu->council[40]; R1 = M[ + 20]; // load obiwan.yoda R2 = M[ + 8]; // load macewindu R3 =.2 M[R2 + 80]; // load macewindu->council[40]; R4 = R3 * 2; // scale offset by sizeof(short) R5 = R1 + R4; // advance old value of obiwan.yoda by scaled offset M[ + 20] = R5; // flush back new value to obiwan.yoda // return obiwan.anakin((short *) &obiwan, *this); R1 = + 12; // load &obiwan (and look! it's a short *!, too) R2 = M[ + 4]; // load this = 12; // make space for three params (including this!) M[] = R1; // initialize this M[ + 4] = R1; // initialize padme M[ + 8] = R2; // initialize leia CALL <jedimaster::anakin> = + 12; // clean up parameters RV = M[RV]; // convert reference into a copy RET;
CS107 Handout 13 Spring 2008 April 18, 2008 Computer Architecture: Take II
 CS107 Handout 13 Spring 2008 April 18, 2008 Computer Architecture: Take II Example: Simple variables Handout written by Julie Zelenski and Nick Parlante A variable is a location in memory. When a variable
CS107 Handout 13 Spring 2008 April 18, 2008 Computer Architecture: Take II Example: Simple variables Handout written by Julie Zelenski and Nick Parlante A variable is a location in memory. When a variable
11 'e' 'x' 'e' 'm' 'p' 'l' 'i' 'f' 'i' 'e' 'd' bool equal(const unsigned char pstr[], const char *cstr) {
![11 'e' 'x' 'e' 'm' 'p' 'l' 'i' 'f' 'i' 'e' 'd' bool equal(const unsigned char pstr[], const char *cstr) { 11 'e' 'x' 'e' 'm' 'p' 'l' 'i' 'f' 'i' 'e' 'd' bool equal(const unsigned char pstr[], const char *cstr) {](/thumbs/91/107167676.jpg) This document contains the questions and solutions to the CS107 midterm given in Spring 2016 by instructors Julie Zelenski and Michael Chang. This was an 80-minute exam. Midterm questions Problem 1: C-strings
This document contains the questions and solutions to the CS107 midterm given in Spring 2016 by instructors Julie Zelenski and Michael Chang. This was an 80-minute exam. Midterm questions Problem 1: C-strings
Page 1. Where Have We Been? Chapter 2 Representing and Manipulating Information. Why Don t Computers Use Base 10?
 Where Have We Been? Class Introduction Great Realities of Computing Int s are not Integers, Float s are not Reals You must know assembly Memory Matters Performance! Asymptotic Complexity It s more than
Where Have We Been? Class Introduction Great Realities of Computing Int s are not Integers, Float s are not Reals You must know assembly Memory Matters Performance! Asymptotic Complexity It s more than
Work relative to other classes
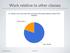 Work relative to other classes 1 Hours/week on projects 2 C BOOTCAMP DAY 1 CS3600, Northeastern University Slides adapted from Anandha Gopalan s CS132 course at Univ. of Pittsburgh Overview C: A language
Work relative to other classes 1 Hours/week on projects 2 C BOOTCAMP DAY 1 CS3600, Northeastern University Slides adapted from Anandha Gopalan s CS132 course at Univ. of Pittsburgh Overview C: A language
Programming in C - Part 2
 Programming in C - Part 2 CPSC 457 Mohammad Reza Zakerinasab May 11, 2016 These slides are forked from slides created by Mike Clark Where to find these slides and related source code? http://goo.gl/k1qixb
Programming in C - Part 2 CPSC 457 Mohammad Reza Zakerinasab May 11, 2016 These slides are forked from slides created by Mike Clark Where to find these slides and related source code? http://goo.gl/k1qixb
Variables Data types Variable I/O. C introduction. Variables. Variables 1 / 14
 C introduction Variables Variables 1 / 14 Contents Variables Data types Variable I/O Variables 2 / 14 Usage Declaration: t y p e i d e n t i f i e r ; Assignment: i d e n t i f i e r = v a l u e ; Definition
C introduction Variables Variables 1 / 14 Contents Variables Data types Variable I/O Variables 2 / 14 Usage Declaration: t y p e i d e n t i f i e r ; Assignment: i d e n t i f i e r = v a l u e ; Definition
ECE 250 / CS 250 Computer Architecture. C to Binary: Memory & Data Representations. Benjamin Lee
 ECE 250 / CS 250 Computer Architecture C to Binary: Memory & Data Representations Benjamin Lee Slides based on those from Alvin Lebeck, Daniel Sorin, Andrew Hilton, Amir Roth, Gershon Kedem Administrivia
ECE 250 / CS 250 Computer Architecture C to Binary: Memory & Data Representations Benjamin Lee Slides based on those from Alvin Lebeck, Daniel Sorin, Andrew Hilton, Amir Roth, Gershon Kedem Administrivia
Bits and Bytes. Why bits? Representing information as bits Binary/Hexadecimal Byte representations» numbers» characters and strings» Instructions
 Bits and Bytes Topics Why bits? Representing information as bits Binary/Hexadecimal Byte representations» numbers» characters and strings» Instructions Bit-level manipulations Boolean algebra Expressing
Bits and Bytes Topics Why bits? Representing information as bits Binary/Hexadecimal Byte representations» numbers» characters and strings» Instructions Bit-level manipulations Boolean algebra Expressing
Spring 2008 May 14 th, 2008 CS107 Midterm Solution
 CS107 Handout 25S Spring 2008 May 14 th, 2008 CS107 Midterm Solution Problem 1: Your Friendly Green Grocer (15 points: 5, 4, and 6) Consider the following struct definitions: line 1 line 2 line 3 typedef
CS107 Handout 25S Spring 2008 May 14 th, 2008 CS107 Midterm Solution Problem 1: Your Friendly Green Grocer (15 points: 5, 4, and 6) Consider the following struct definitions: line 1 line 2 line 3 typedef
Under the Hood: Data Representations, Memory and Bit Operations. Computer Science 104 Lecture 3
 Under the Hood: Data Representations, Memory and Bit Operations Computer Science 104 Lecture 3 Homework #1 Due Feb 6 Reading TAs Finish Chapter 1 Start Chapter 2 Admin +1 UTA: Michael Zhou Lindsay is Head
Under the Hood: Data Representations, Memory and Bit Operations Computer Science 104 Lecture 3 Homework #1 Due Feb 6 Reading TAs Finish Chapter 1 Start Chapter 2 Admin +1 UTA: Michael Zhou Lindsay is Head
CS 61C: Great Ideas in Computer Architecture Introduction to C
 CS 61C: Great Ideas in Computer Architecture Introduction to C Instructors: Vladimir Stojanovic & Nicholas Weaver http://inst.eecs.berkeley.edu/~cs61c/ 1 Agenda C vs. Java vs. Python Quick Start Introduction
CS 61C: Great Ideas in Computer Architecture Introduction to C Instructors: Vladimir Stojanovic & Nicholas Weaver http://inst.eecs.berkeley.edu/~cs61c/ 1 Agenda C vs. Java vs. Python Quick Start Introduction
Section Notes - Week 1 (9/17)
 Section Notes - Week 1 (9/17) Why do we need to learn bits and bitwise arithmetic? Since this class is about learning about how computers work. For most of the rest of the semester, you do not have to
Section Notes - Week 1 (9/17) Why do we need to learn bits and bitwise arithmetic? Since this class is about learning about how computers work. For most of the rest of the semester, you do not have to
CS107, Lecture 3 Bits and Bytes; Bitwise Operators
 CS107, Lecture 3 Bits and Bytes; Bitwise Operators reading: Bryant & O Hallaron, Ch. 2.1 This document is copyright (C) Stanford Computer Science and Nick Troccoli, licensed under Creative Commons Attribution
CS107, Lecture 3 Bits and Bytes; Bitwise Operators reading: Bryant & O Hallaron, Ch. 2.1 This document is copyright (C) Stanford Computer Science and Nick Troccoli, licensed under Creative Commons Attribution
Why Don t Computers Use Base 10? Lecture 2 Bits and Bytes. Binary Representations. Byte-Oriented Memory Organization. Base 10 Number Representation
 Lecture 2 Bits and Bytes Topics! Why bits?! Representing information as bits " Binary/Hexadecimal " Byte representations» numbers» characters and strings» Instructions! Bit-level manipulations " Boolean
Lecture 2 Bits and Bytes Topics! Why bits?! Representing information as bits " Binary/Hexadecimal " Byte representations» numbers» characters and strings» Instructions! Bit-level manipulations " Boolean
C Programming. Course Outline. C Programming. Code: MBD101. Duration: 10 Hours. Prerequisites:
 C Programming Code: MBD101 Duration: 10 Hours Prerequisites: You are a computer science Professional/ graduate student You can execute Linux/UNIX commands You know how to use a text-editing tool You should
C Programming Code: MBD101 Duration: 10 Hours Prerequisites: You are a computer science Professional/ graduate student You can execute Linux/UNIX commands You know how to use a text-editing tool You should
Goals for this Week. CSC 2400: Computer Systems. Bits, Bytes and Data Types. Binary number system. Finite representations of binary integers
 CSC 2400: Computer Systems Bits, Bytes and Data Types 1 Goals for this Week Binary number system Why binary? Converting between decimal and binary and octal and hexadecimal number systems Finite representations
CSC 2400: Computer Systems Bits, Bytes and Data Types 1 Goals for this Week Binary number system Why binary? Converting between decimal and binary and octal and hexadecimal number systems Finite representations
a) Write the signed (two s complement) binary number in decimal: b) Write the unsigned binary number in hexadecimal:
 CS107 Autumn 2018 CS107 Midterm Practice Problems Cynthia Lee Problem 1: Integer Representation There is a small amount of scratch space between problems for you to write your work, but it is not necessary
CS107 Autumn 2018 CS107 Midterm Practice Problems Cynthia Lee Problem 1: Integer Representation There is a small amount of scratch space between problems for you to write your work, but it is not necessary
Computer Organization & Systems Exam I Example Questions
 Computer Organization & Systems Exam I Example Questions 1. Pointer Question. Write a function char *circle(char *str) that receives a character pointer (which points to an array that is in standard C
Computer Organization & Systems Exam I Example Questions 1. Pointer Question. Write a function char *circle(char *str) that receives a character pointer (which points to an array that is in standard C
Declaration. Fundamental Data Types. Modifying the Basic Types. Basic Data Types. All variables must be declared before being used.
 Declaration Fundamental Data Types All variables must be declared before being used. Tells compiler to set aside an appropriate amount of space in memory to hold a value. Enables the compiler to perform
Declaration Fundamental Data Types All variables must be declared before being used. Tells compiler to set aside an appropriate amount of space in memory to hold a value. Enables the compiler to perform
AGENDA Binary Operations CS 3330 Samira Khan
 AGENDA Binary Operations CS 3330 Logistics Review from last Lecture Samira Khan University of Virginia Jan 31, 2017 Binary Operations Logical Operations Bitwise Operations Examples 2 Feedbacks Quizzes
AGENDA Binary Operations CS 3330 Logistics Review from last Lecture Samira Khan University of Virginia Jan 31, 2017 Binary Operations Logical Operations Bitwise Operations Examples 2 Feedbacks Quizzes
Fundamental of Programming (C)
 Borrowed from lecturer notes by Omid Jafarinezhad Fundamental of Programming (C) Lecturer: Vahid Khodabakhshi Lecture 3 Constants, Variables, Data Types, And Operations Department of Computer Engineering
Borrowed from lecturer notes by Omid Jafarinezhad Fundamental of Programming (C) Lecturer: Vahid Khodabakhshi Lecture 3 Constants, Variables, Data Types, And Operations Department of Computer Engineering
CS61C Machine Structures. Lecture 4 C Structs & Memory Management. 9/5/2007 John Wawrzynek. www-inst.eecs.berkeley.edu/~cs61c/
 CS61C Machine Structures Lecture 4 C Structs & Memory Management 9/5/2007 John Wawrzynek (www.cs.berkeley.edu/~johnw) www-inst.eecs.berkeley.edu/~cs61c/ CS 61C L04 C Structs (1) C String Standard Functions
CS61C Machine Structures Lecture 4 C Structs & Memory Management 9/5/2007 John Wawrzynek (www.cs.berkeley.edu/~johnw) www-inst.eecs.berkeley.edu/~cs61c/ CS 61C L04 C Structs (1) C String Standard Functions
Why Don t Computers Use Base 10? Lecture 2 Bits and Bytes. Binary Representations. Byte-Oriented Memory Organization. Base 10 Number Representation
 Lecture 2 Bits and Bytes Topics Why bits? Representing information as bits Binary/Hexadecimal Byte representations» numbers» characters and strings» Instructions Bit-level manipulations Boolean algebra
Lecture 2 Bits and Bytes Topics Why bits? Representing information as bits Binary/Hexadecimal Byte representations» numbers» characters and strings» Instructions Bit-level manipulations Boolean algebra
CS 61C: Great Ideas in Computer Architecture. (Brief) Review Lecture
 CS 61C: Great Ideas in Computer Architecture (Brief) Review Lecture Instructor: Justin Hsia 7/16/2013 Summer 2013 Lecture #13 1 Topic List So Far (1/2) Number Representation Signed/unsigned, Floating Point
CS 61C: Great Ideas in Computer Architecture (Brief) Review Lecture Instructor: Justin Hsia 7/16/2013 Summer 2013 Lecture #13 1 Topic List So Far (1/2) Number Representation Signed/unsigned, Floating Point
CS Programming In C
 CS 24000 - Programming In C Week Two: Basic C Program Organization and Data Types Zhiyuan Li Department of Computer Science Purdue University, USA 2 int main() { } return 0; The Simplest C Program C programs
CS 24000 - Programming In C Week Two: Basic C Program Organization and Data Types Zhiyuan Li Department of Computer Science Purdue University, USA 2 int main() { } return 0; The Simplest C Program C programs
CSCI-243 Exam 1 Review February 22, 2015 Presented by the RIT Computer Science Community
 CSCI-243 Exam 1 Review February 22, 2015 Presented by the RIT Computer Science Community http://csc.cs.rit.edu History and Evolution of Programming Languages 1. Explain the relationship between machine
CSCI-243 Exam 1 Review February 22, 2015 Presented by the RIT Computer Science Community http://csc.cs.rit.edu History and Evolution of Programming Languages 1. Explain the relationship between machine
Kurt Schmidt. October 30, 2018
 to Structs Dept. of Computer Science, Drexel University October 30, 2018 Array Objectives to Structs Intended audience: Student who has working knowledge of Python To gain some experience with a statically-typed
to Structs Dept. of Computer Science, Drexel University October 30, 2018 Array Objectives to Structs Intended audience: Student who has working knowledge of Python To gain some experience with a statically-typed
Bit Manipulation in C
 Bit Manipulation in C Bit Manipulation in C C provides six bitwise operators for bit manipulation. These operators act on integral operands (char, short, int and long) represented as a string of binary
Bit Manipulation in C Bit Manipulation in C C provides six bitwise operators for bit manipulation. These operators act on integral operands (char, short, int and long) represented as a string of binary
Jagannath Institute of Management Sciences Lajpat Nagar. BCA II Sem. C Programming
 Jagannath Institute of Management Sciences Lajpat Nagar BCA II Sem C Programming UNIT I Pointers: Introduction to Pointers, Pointer Notation,Decalaration and Initialization, Accessing variable through
Jagannath Institute of Management Sciences Lajpat Nagar BCA II Sem C Programming UNIT I Pointers: Introduction to Pointers, Pointer Notation,Decalaration and Initialization, Accessing variable through
Agenda. Peer Instruction Question 1. Peer Instruction Answer 1. Peer Instruction Question 2 6/22/2011
 CS 61C: Great Ideas in Computer Architecture (Machine Structures) Introduction to C (Part II) Instructors: Randy H. Katz David A. Patterson http://inst.eecs.berkeley.edu/~cs61c/sp11 Spring 2011 -- Lecture
CS 61C: Great Ideas in Computer Architecture (Machine Structures) Introduction to C (Part II) Instructors: Randy H. Katz David A. Patterson http://inst.eecs.berkeley.edu/~cs61c/sp11 Spring 2011 -- Lecture
CS61C Machine Structures. Lecture 5 C Structs & Memory Mangement. 1/27/2006 John Wawrzynek. www-inst.eecs.berkeley.edu/~cs61c/
 CS61C Machine Structures Lecture 5 C Structs & Memory Mangement 1/27/2006 John Wawrzynek (www.cs.berkeley.edu/~johnw) www-inst.eecs.berkeley.edu/~cs61c/ CS 61C L05 C Structs (1) C String Standard Functions
CS61C Machine Structures Lecture 5 C Structs & Memory Mangement 1/27/2006 John Wawrzynek (www.cs.berkeley.edu/~johnw) www-inst.eecs.berkeley.edu/~cs61c/ CS 61C L05 C Structs (1) C String Standard Functions
CS 61C: Great Ideas in Computer Architecture. Lecture 2: Numbers & C Language. Krste Asanović & Randy Katz
 CS 61C: Great Ideas in Computer Architecture Lecture 2: Numbers & C Language Krste Asanović & Randy Katz http://inst.eecs.berkeley.edu/~cs61c Numbers wrap-up This is not on the exam! Break C Primer Administrivia,
CS 61C: Great Ideas in Computer Architecture Lecture 2: Numbers & C Language Krste Asanović & Randy Katz http://inst.eecs.berkeley.edu/~cs61c Numbers wrap-up This is not on the exam! Break C Primer Administrivia,
Agenda. CS 61C: Great Ideas in Computer Architecture. Lecture 2: Numbers & C Language 8/29/17. Recap: Binary Number Conversion
 CS 61C: Great Ideas in Computer Architecture Lecture 2: Numbers & C Language Krste Asanović & Randy Katz http://inst.eecs.berkeley.edu/~cs61c Numbers wrap-up This is not on the exam! Break C Primer Administrivia,
CS 61C: Great Ideas in Computer Architecture Lecture 2: Numbers & C Language Krste Asanović & Randy Katz http://inst.eecs.berkeley.edu/~cs61c Numbers wrap-up This is not on the exam! Break C Primer Administrivia,
Fundamental Data Types. CSE 130: Introduction to Programming in C Stony Brook University
 Fundamental Data Types CSE 130: Introduction to Programming in C Stony Brook University Program Organization in C The C System C consists of several parts: The C language The preprocessor The compiler
Fundamental Data Types CSE 130: Introduction to Programming in C Stony Brook University Program Organization in C The C System C consists of several parts: The C language The preprocessor The compiler
CS31 Discussion 1E Spring 17 : week 08
 CS31 Discussion 1E Spring 17 : week 08 TA: Bo-Jhang Ho bojhang@cs.ucla.edu Credit to former TA Chelsea Ju Project 5 - Map cipher to crib Approach 1: For each pair of positions, check two letters in cipher
CS31 Discussion 1E Spring 17 : week 08 TA: Bo-Jhang Ho bojhang@cs.ucla.edu Credit to former TA Chelsea Ju Project 5 - Map cipher to crib Approach 1: For each pair of positions, check two letters in cipher
CS61C : Machine Structures
 inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture 5 C Memory Management Lecturer PSOE Dan Garcia www.cs.berkeley.edu/~ddgarcia CS61C L05 C Structures, Memory Management (1) 2005-01-28 The
inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture 5 C Memory Management Lecturer PSOE Dan Garcia www.cs.berkeley.edu/~ddgarcia CS61C L05 C Structures, Memory Management (1) 2005-01-28 The
Review: C Strings. A string in C is just an array of characters. Lecture #4 C Strings, Arrays, & Malloc
 CS61C L4 C Pointers (1) inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture #4 C Strings, Arrays, & Malloc Albert Chae Instructor 2008-06-26 Review: C Strings A string in C is just an array
CS61C L4 C Pointers (1) inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture #4 C Strings, Arrays, & Malloc Albert Chae Instructor 2008-06-26 Review: C Strings A string in C is just an array
Lecture 03 Bits, Bytes and Data Types
 Lecture 03 Bits, Bytes and Data Types Computer Languages A computer language is a language that is used to communicate with a machine. Like all languages, computer languages have syntax (form) and semantics
Lecture 03 Bits, Bytes and Data Types Computer Languages A computer language is a language that is used to communicate with a machine. Like all languages, computer languages have syntax (form) and semantics
Number Systems for Computers. Outline of Introduction. Binary, Octal and Hexadecimal numbers. Issues for Binary Representation of Numbers
 Outline of Introduction Administrivia What is computer architecture? What do computers do? Representing high level things in binary Data objects: integers, decimals, characters, etc. Memory locations (We
Outline of Introduction Administrivia What is computer architecture? What do computers do? Representing high level things in binary Data objects: integers, decimals, characters, etc. Memory locations (We
Embedded Systems - FS 2018
 Institut für Technische Informatik und Kommunikationsnetze Prof. L. Thiele Embedded Systems - FS 2018 Lab 0 Date : 28.2.2018 Prelab Filling the gaps Goals of this Lab You are expected to be already familiar
Institut für Technische Informatik und Kommunikationsnetze Prof. L. Thiele Embedded Systems - FS 2018 Lab 0 Date : 28.2.2018 Prelab Filling the gaps Goals of this Lab You are expected to be already familiar
This is CS50. Harvard University Fall Quiz 0 Answer Key
 Quiz 0 Answer Key Answers other than the below may be possible. Binary Bulbs. 0. Bit- Sized Questions. 1. Because 0 is non- negative, we need to set aside one pattern of bits (000) for it, which leaves
Quiz 0 Answer Key Answers other than the below may be possible. Binary Bulbs. 0. Bit- Sized Questions. 1. Because 0 is non- negative, we need to set aside one pattern of bits (000) for it, which leaves
More about BOOLEAN issues
 More about BOOLEAN issues Every boolean test is an implicit comparison against zero (0). However, zero is not a simple concept. It represents: the integer zero for all integral types the floating point
More about BOOLEAN issues Every boolean test is an implicit comparison against zero (0). However, zero is not a simple concept. It represents: the integer zero for all integral types the floating point
Jin-Soo Kim Systems Software & Architecture Lab. Seoul National University. Integers. Spring 2019
 Jin-Soo Kim (jinsoo.kim@snu.ac.kr) Systems Software & Architecture Lab. Seoul National University Integers Spring 2019 4190.308: Computer Architecture Spring 2019 Jin-Soo Kim (jinsoo.kim@snu.ac.kr) 2 A
Jin-Soo Kim (jinsoo.kim@snu.ac.kr) Systems Software & Architecture Lab. Seoul National University Integers Spring 2019 4190.308: Computer Architecture Spring 2019 Jin-Soo Kim (jinsoo.kim@snu.ac.kr) 2 A
Fundamentals of Programming
 Fundamentals of Programming Lecture 3 - Constants, Variables, Data Types, And Operations Lecturer : Ebrahim Jahandar Borrowed from lecturer notes by Omid Jafarinezhad Outline C Program Data types Variables
Fundamentals of Programming Lecture 3 - Constants, Variables, Data Types, And Operations Lecturer : Ebrahim Jahandar Borrowed from lecturer notes by Omid Jafarinezhad Outline C Program Data types Variables
A Fast Review of C Essentials Part I
 A Fast Review of C Essentials Part I Structural Programming by Z. Cihan TAYSI Outline Program development C Essentials Functions Variables & constants Names Formatting Comments Preprocessor Data types
A Fast Review of C Essentials Part I Structural Programming by Z. Cihan TAYSI Outline Program development C Essentials Functions Variables & constants Names Formatting Comments Preprocessor Data types
EL2310 Scientific Programming
 Lecture 11: Structures and Memory (yaseminb@kth.se) Overview Overview Lecture 11: Structures and Memory Structures Continued Memory Allocation Lecture 11: Structures and Memory Structures Continued Memory
Lecture 11: Structures and Memory (yaseminb@kth.se) Overview Overview Lecture 11: Structures and Memory Structures Continued Memory Allocation Lecture 11: Structures and Memory Structures Continued Memory
C: How to Program. Week /Mar/05
 1 C: How to Program Week 2 2007/Mar/05 Chapter 2 - Introduction to C Programming 2 Outline 2.1 Introduction 2.2 A Simple C Program: Printing a Line of Text 2.3 Another Simple C Program: Adding Two Integers
1 C: How to Program Week 2 2007/Mar/05 Chapter 2 - Introduction to C Programming 2 Outline 2.1 Introduction 2.2 A Simple C Program: Printing a Line of Text 2.3 Another Simple C Program: Adding Two Integers
Hardware: Logical View
 Hardware: Logical View CPU Memory Bus Disks Net USB Etc. 1 Hardware: Physical View USB I/O controller Storage connections CPU Memory 2 Hardware: 351 View (version 0) instructions? Memory CPU data CPU executes
Hardware: Logical View CPU Memory Bus Disks Net USB Etc. 1 Hardware: Physical View USB I/O controller Storage connections CPU Memory 2 Hardware: 351 View (version 0) instructions? Memory CPU data CPU executes
ICS Instructor: Aleksandar Kuzmanovic TA: Ionut Trestian Recitation 2
 ICS 2008 Instructor: Aleksandar Kuzmanovic TA: Ionut Trestian Recitation 2 Data Representations Sizes of C Objects (in Bytes) C Data Type Compaq Alpha Typical 32-bit Intel IA32 int 4 4 4 long int 8 4 4
ICS 2008 Instructor: Aleksandar Kuzmanovic TA: Ionut Trestian Recitation 2 Data Representations Sizes of C Objects (in Bytes) C Data Type Compaq Alpha Typical 32-bit Intel IA32 int 4 4 4 long int 8 4 4
Bits, Bytes, and Integers
 Bits, Bytes, and Integers with contributions from Dr. Bin Ren, College of William & Mary 1 Bits, Bytes, and Integers Representing information as bits Bit-level manipulations Integers Representation: unsigned
Bits, Bytes, and Integers with contributions from Dr. Bin Ren, College of William & Mary 1 Bits, Bytes, and Integers Representing information as bits Bit-level manipulations Integers Representation: unsigned
211: Computer Architecture Summer 2016
 211: Computer Architecture Summer 2016 Liu Liu Topic: C Programming Data Representation I/O: - (example) cprintf.c Memory: - memory address - stack / heap / constant space - basic data layout Pointer:
211: Computer Architecture Summer 2016 Liu Liu Topic: C Programming Data Representation I/O: - (example) cprintf.c Memory: - memory address - stack / heap / constant space - basic data layout Pointer:
Recap. ANSI C Reserved Words C++ Multimedia Programming Lecture 2. Erwin M. Bakker Joachim Rijsdam
 Multimedia Programming 2004 Lecture 2 Erwin M. Bakker Joachim Rijsdam Recap Learning C++ by example No groups: everybody should experience developing and programming in C++! Assignments will determine
Multimedia Programming 2004 Lecture 2 Erwin M. Bakker Joachim Rijsdam Recap Learning C++ by example No groups: everybody should experience developing and programming in C++! Assignments will determine
CS107 Handout 08 Spring 2007 April 9, 2007 The Ins and Outs of C Arrays
 CS107 Handout 08 Spring 2007 April 9, 2007 The Ins and Outs of C Arrays C Arrays This handout was written by Nick Parlante and Julie Zelenski. As you recall, a C array is formed by laying out all the elements
CS107 Handout 08 Spring 2007 April 9, 2007 The Ins and Outs of C Arrays C Arrays This handout was written by Nick Parlante and Julie Zelenski. As you recall, a C array is formed by laying out all the elements
Programming Fundamentals (CS 302 ) Dr. Ihsan Ullah. Lecturer Department of Computer Science & IT University of Balochistan
 Programming Fundamentals (CS 302 ) Dr. Ihsan Ullah Lecturer Department of Computer Science & IT University of Balochistan 1 Outline p Introduction p Program development p C language and beginning with
Programming Fundamentals (CS 302 ) Dr. Ihsan Ullah Lecturer Department of Computer Science & IT University of Balochistan 1 Outline p Introduction p Program development p C language and beginning with
COMP2611: Computer Organization. Data Representation
 COMP2611: Computer Organization Comp2611 Fall 2015 2 1. Binary numbers and 2 s Complement Numbers 3 Bits: are the basis for binary number representation in digital computers What you will learn here: How
COMP2611: Computer Organization Comp2611 Fall 2015 2 1. Binary numbers and 2 s Complement Numbers 3 Bits: are the basis for binary number representation in digital computers What you will learn here: How
2.1. Unit 2. Integer Operations (Arithmetic, Overflow, Bitwise Logic, Shifting)
 2.1 Unit 2 Integer Operations (Arithmetic, Overflow, Bitwise Logic, Shifting) 2.2 Skills & Outcomes You should know and be able to apply the following skills with confidence Perform addition & subtraction
2.1 Unit 2 Integer Operations (Arithmetic, Overflow, Bitwise Logic, Shifting) 2.2 Skills & Outcomes You should know and be able to apply the following skills with confidence Perform addition & subtraction
Bits and Bytes January 13, 2005
 15-213 The Class That Gives CMU Its Zip! Topics Bits and Bytes January 13, 25 Why bits? Representing information as bits Binary / Hexadecimal Byte representations» Numbers» Characters and strings» Instructions
15-213 The Class That Gives CMU Its Zip! Topics Bits and Bytes January 13, 25 Why bits? Representing information as bits Binary / Hexadecimal Byte representations» Numbers» Characters and strings» Instructions
Number Systems. Binary Numbers. Appendix. Decimal notation represents numbers as powers of 10, for example
 Appendix F Number Systems Binary Numbers Decimal notation represents numbers as powers of 10, for example 1729 1 103 7 102 2 101 9 100 decimal = + + + There is no particular reason for the choice of 10,
Appendix F Number Systems Binary Numbers Decimal notation represents numbers as powers of 10, for example 1729 1 103 7 102 2 101 9 100 decimal = + + + There is no particular reason for the choice of 10,
ECET 264 C Programming Language with Applications
 ECET 264 C Programming Language with Applications Lecture 6 Control Structures and More Operators Paul I. Lin Professor of Electrical & Computer Engineering Technology http://www.etcs.ipfw.edu/~lin Lecture
ECET 264 C Programming Language with Applications Lecture 6 Control Structures and More Operators Paul I. Lin Professor of Electrical & Computer Engineering Technology http://www.etcs.ipfw.edu/~lin Lecture
CS61C : Machine Structures
 inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture 5 C Memory Management Lecturer PSOE Dan Garcia www.cs.berkeley.edu/~ddgarcia CS 61C L04 C Structures, Memory Management (1) 2004-09-10 Barry
inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture 5 C Memory Management Lecturer PSOE Dan Garcia www.cs.berkeley.edu/~ddgarcia CS 61C L04 C Structures, Memory Management (1) 2004-09-10 Barry
CS24: INTRODUCTION TO COMPUTING SYSTEMS. Spring 2018 Lecture 6
 CS24: INTRODUCTION TO COMPUTING SYSTEMS Spring 2018 Lecture 6 LAST TIME: SYSTEM V AMD64 ABI How to implement basic C abstractions in x86-64? C subroutines with arguments, and local/global variables Began
CS24: INTRODUCTION TO COMPUTING SYSTEMS Spring 2018 Lecture 6 LAST TIME: SYSTEM V AMD64 ABI How to implement basic C abstractions in x86-64? C subroutines with arguments, and local/global variables Began
Understanding Pointers
 Division of Mathematics and Computer Science Maryville College Pointers and Addresses Memory is organized into a big array. Every data item occupies one or more cells. A pointer stores an address. A pointer
Division of Mathematics and Computer Science Maryville College Pointers and Addresses Memory is organized into a big array. Every data item occupies one or more cells. A pointer stores an address. A pointer
Intermediate Programming, Spring 2017*
 600.120 Intermediate Programming, Spring 2017* Misha Kazhdan *Much of the code in these examples is not commented because it would otherwise not fit on the slides. This is bad coding practice in general
600.120 Intermediate Programming, Spring 2017* Misha Kazhdan *Much of the code in these examples is not commented because it would otherwise not fit on the slides. This is bad coding practice in general
EL2310 Scientific Programming
 Lecture 12: Memory, Files and Bitoperations (pronobis@kth.se) Overview Overview Lecture 12: Memory, Files and Bit operations Wrap Up Main function; reading and writing Bitwise Operations Wrap Up Lecture
Lecture 12: Memory, Files and Bitoperations (pronobis@kth.se) Overview Overview Lecture 12: Memory, Files and Bit operations Wrap Up Main function; reading and writing Bitwise Operations Wrap Up Lecture
Exercise Session 2 Simon Gerber
 Exercise Session 2 Simon Gerber CASP 2014 Exercise 2: Binary search tree Implement and test a binary search tree in C: Implement key insert() and lookup() functions Implement as C module: bst.c, bst.h
Exercise Session 2 Simon Gerber CASP 2014 Exercise 2: Binary search tree Implement and test a binary search tree in C: Implement key insert() and lookup() functions Implement as C module: bst.c, bst.h
First of all, it is a variable, just like other variables you studied
 Pointers: Basics What is a pointer? First of all, it is a variable, just like other variables you studied So it has type, storage etc. Difference: it can only store the address (rather than the value)
Pointers: Basics What is a pointer? First of all, it is a variable, just like other variables you studied So it has type, storage etc. Difference: it can only store the address (rather than the value)
Computer Science 324 Computer Architecture Mount Holyoke College Fall Topic Notes: Bits and Bytes and Numbers
 Computer Science 324 Computer Architecture Mount Holyoke College Fall 2007 Topic Notes: Bits and Bytes and Numbers Number Systems Much of this is review, given the 221 prerequisite Question: how high can
Computer Science 324 Computer Architecture Mount Holyoke College Fall 2007 Topic Notes: Bits and Bytes and Numbers Number Systems Much of this is review, given the 221 prerequisite Question: how high can
Spring 2007 May 16, 2007 CS107 Midterm Solution
 CS107 Handout 26S Spring 2007 May 16, 2007 CS107 Midterm Solution Problem 1: Color Theory (15 points: ) Consider the following struct definitions: typedef struct palette short *lavender; char indigo[4];
CS107 Handout 26S Spring 2007 May 16, 2007 CS107 Midterm Solution Problem 1: Color Theory (15 points: ) Consider the following struct definitions: typedef struct palette short *lavender; char indigo[4];
COP Study Union - Fall 2017
 COP 3502 - Study Union - Fall 2017 Chris Marsh Contents 1 Tries 3 1.1 Insertion...................................... 4 1.1.1 Worst Case Runtime........................... 4 1.1.2 Best Case Runtime............................
COP 3502 - Study Union - Fall 2017 Chris Marsh Contents 1 Tries 3 1.1 Insertion...................................... 4 1.1.1 Worst Case Runtime........................... 4 1.1.2 Best Case Runtime............................
ECET 264 C Programming Language with Applications
 ECET 264 C Programming Language with Applications Lecture 9 & 10 Control Structures and More Operators Paul I. Lin Professor of Electrical & Computer Engineering Technology http://www.ecet.ipfw.edu/~lin
ECET 264 C Programming Language with Applications Lecture 9 & 10 Control Structures and More Operators Paul I. Lin Professor of Electrical & Computer Engineering Technology http://www.ecet.ipfw.edu/~lin
Time: 8:30-10:00 pm (Arrive at 8:15 pm) Location What to bring:
 ECE 120 Midterm 1 HKN Review Session Time: 8:30-10:00 pm (Arrive at 8:15 pm) Location: Your Room on Compass What to bring: icard, pens/pencils, Cheat sheet (Handwritten) Overview of Review Binary IEEE
ECE 120 Midterm 1 HKN Review Session Time: 8:30-10:00 pm (Arrive at 8:15 pm) Location: Your Room on Compass What to bring: icard, pens/pencils, Cheat sheet (Handwritten) Overview of Review Binary IEEE
Chapter 2 - Introduction to C Programming
 Chapter 2 - Introduction to C Programming 2 Outline 2.1 Introduction 2.2 A Simple C Program: Printing a Line of Text 2.3 Another Simple C Program: Adding Two Integers 2.4 Memory Concepts 2.5 Arithmetic
Chapter 2 - Introduction to C Programming 2 Outline 2.1 Introduction 2.2 A Simple C Program: Printing a Line of Text 2.3 Another Simple C Program: Adding Two Integers 2.4 Memory Concepts 2.5 Arithmetic
l l l l l l l Base 2; each digit is 0 or 1 l Each bit in place i has value 2 i l Binary representation is used in computers
 198:211 Computer Architecture Topics: Lecture 8 (W5) Fall 2012 Data representation 2.1 and 2.2 of the book Floating point 2.4 of the book Computer Architecture What do computers do? Manipulate stored information
198:211 Computer Architecture Topics: Lecture 8 (W5) Fall 2012 Data representation 2.1 and 2.2 of the book Floating point 2.4 of the book Computer Architecture What do computers do? Manipulate stored information
CS 110 Computer Architecture. Lecture 2: Introduction to C, Part I. Instructor: Sören Schwertfeger.
 CS 110 Computer Architecture Lecture 2: Introduction to C, Part I Instructor: Sören Schwertfeger http://shtech.org/courses/ca/ School of Information Science and Technology SIST ShanghaiTech University
CS 110 Computer Architecture Lecture 2: Introduction to C, Part I Instructor: Sören Schwertfeger http://shtech.org/courses/ca/ School of Information Science and Technology SIST ShanghaiTech University
Bits, Bytes, and Integers Part 2
 Bits, Bytes, and Integers Part 2 15-213: Introduction to Computer Systems 3 rd Lecture, Jan. 23, 2018 Instructors: Franz Franchetti, Seth Copen Goldstein, Brian Railing 1 First Assignment: Data Lab Due:
Bits, Bytes, and Integers Part 2 15-213: Introduction to Computer Systems 3 rd Lecture, Jan. 23, 2018 Instructors: Franz Franchetti, Seth Copen Goldstein, Brian Railing 1 First Assignment: Data Lab Due:
Quiz 0 Answer Key. Answers other than the below may be possible. Multiple Choice. 0. a 1. a 2. b 3. c 4. b 5. d. True or False.
 Quiz 0 Answer Key Answers other than the below may be possible. Multiple Choice. 0. a 1. a 2. b 3. c 4. b 5. d True or False. 6. T or F 7. T 8. F 9. T 10. T or F Itching for Week 0? 11. 00011001 + 00011001
Quiz 0 Answer Key Answers other than the below may be possible. Multiple Choice. 0. a 1. a 2. b 3. c 4. b 5. d True or False. 6. T or F 7. T 8. F 9. T 10. T or F Itching for Week 0? 11. 00011001 + 00011001
CS61, Fall 2012 Midterm Review Section
 CS61, Fall 2012 Midterm Review Section (10/16/2012) Q1: Hexadecimal and Binary Notation - Solve the following equations and put your answers in hex, decimal and binary. Hexadecimal Decimal Binary 15 +
CS61, Fall 2012 Midterm Review Section (10/16/2012) Q1: Hexadecimal and Binary Notation - Solve the following equations and put your answers in hex, decimal and binary. Hexadecimal Decimal Binary 15 +
Administrivia. Introduction to Computer Systems. Pointers, cont. Pointer example, again POINTERS. Project 2 posted, due October 6
 CMSC 313 Introduction to Computer Systems Lecture 8 Pointers, cont. Alan Sussman als@cs.umd.edu Administrivia Project 2 posted, due October 6 public tests s posted Quiz on Wed. in discussion up to pointers
CMSC 313 Introduction to Computer Systems Lecture 8 Pointers, cont. Alan Sussman als@cs.umd.edu Administrivia Project 2 posted, due October 6 public tests s posted Quiz on Wed. in discussion up to pointers
Week 3 Lecture 2. Types Constants and Variables
 Lecture 2 Types Constants and Variables Types Computers store bits: strings of 0s and 1s Types define how bits are interpreted They can be integers (whole numbers): 1, 2, 3 They can be characters 'a',
Lecture 2 Types Constants and Variables Types Computers store bits: strings of 0s and 1s Types define how bits are interpreted They can be integers (whole numbers): 1, 2, 3 They can be characters 'a',
CS107, Lecture 9 C Generics Function Pointers
 CS107, Lecture 9 C Generics Function Pointers Reading: K&R 5.11 This document is copyright (C) Stanford Computer Science and Nick Troccoli, licensed under Creative Commons Attribution 2.5 License. All
CS107, Lecture 9 C Generics Function Pointers Reading: K&R 5.11 This document is copyright (C) Stanford Computer Science and Nick Troccoli, licensed under Creative Commons Attribution 2.5 License. All
CSI 402 Lecture 2 Working with Files (Text and Binary)
 CSI 402 Lecture 2 Working with Files (Text and Binary) 1 / 30 AQuickReviewofStandardI/O Recall that #include allows use of printf and scanf functions Example: int i; scanf("%d", &i); printf("value
CSI 402 Lecture 2 Working with Files (Text and Binary) 1 / 30 AQuickReviewofStandardI/O Recall that #include allows use of printf and scanf functions Example: int i; scanf("%d", &i); printf("value
CS 61c: Great Ideas in Computer Architecture
 Arrays, Strings, and Some More Pointers June 24, 2014 Review of Last Lecture C Basics Variables, functioss, control flow, types, structs Only 0 and NULL evaluate to false Pointers hold addresses Address
Arrays, Strings, and Some More Pointers June 24, 2014 Review of Last Lecture C Basics Variables, functioss, control flow, types, structs Only 0 and NULL evaluate to false Pointers hold addresses Address
Embedded Systems - FS 2018
 Institut für Technische Informatik und Kommunikationsnetze Prof. L. Thiele Embedded Systems - FS 2018 Sample solution to Lab 0 Date : 28.2.2018 Prelab Filling the gaps Goals of this Lab You are expected
Institut für Technische Informatik und Kommunikationsnetze Prof. L. Thiele Embedded Systems - FS 2018 Sample solution to Lab 0 Date : 28.2.2018 Prelab Filling the gaps Goals of this Lab You are expected
Lab 3. Pointers Programming Lab (Using C) XU Silei
 Lab 3. Pointers Programming Lab (Using C) XU Silei slxu@cse.cuhk.edu.hk Outline What is Pointer Memory Address & Pointers How to use Pointers Pointers Assignments Call-by-Value & Call-by-Address Functions
Lab 3. Pointers Programming Lab (Using C) XU Silei slxu@cse.cuhk.edu.hk Outline What is Pointer Memory Address & Pointers How to use Pointers Pointers Assignments Call-by-Value & Call-by-Address Functions
Data III & Integers I
 Data III & Integers I CSE 351 Spring 2017 Instructor: Ruth Anderson Teaching Assistants: Dylan Johnson Kevin Bi Linxing Preston Jiang Cody Ohlsen Yufang Sun Joshua Curtis Administrivia Everyone has VM
Data III & Integers I CSE 351 Spring 2017 Instructor: Ruth Anderson Teaching Assistants: Dylan Johnson Kevin Bi Linxing Preston Jiang Cody Ohlsen Yufang Sun Joshua Curtis Administrivia Everyone has VM
Programming refresher and intro to C programming
 Applied mechatronics Programming refresher and intro to C programming Sven Gestegård Robertz sven.robertz@cs.lth.se Department of Computer Science, Lund University 2018 Outline 1 C programming intro 2
Applied mechatronics Programming refresher and intro to C programming Sven Gestegård Robertz sven.robertz@cs.lth.se Department of Computer Science, Lund University 2018 Outline 1 C programming intro 2
Chapter 3. Fundamental Data Types
 Chapter 3. Fundamental Data Types Byoung-Tak Zhang TA: Hanock Kwak Biointelligence Laboratory School of Computer Science and Engineering Seoul National Univertisy http://bi.snu.ac.kr Variable Declaration
Chapter 3. Fundamental Data Types Byoung-Tak Zhang TA: Hanock Kwak Biointelligence Laboratory School of Computer Science and Engineering Seoul National Univertisy http://bi.snu.ac.kr Variable Declaration
CS 101: Computer Programming and Utilization
 CS 101: Computer Programming and Utilization Jul-Nov 2017 Umesh Bellur (cs101@cse.iitb.ac.in) Lecture 3: Number Representa.ons Representing Numbers Digital Circuits can store and manipulate 0 s and 1 s.
CS 101: Computer Programming and Utilization Jul-Nov 2017 Umesh Bellur (cs101@cse.iitb.ac.in) Lecture 3: Number Representa.ons Representing Numbers Digital Circuits can store and manipulate 0 s and 1 s.
Math 230 Assembly Programming (AKA Computer Organization) Spring 2008
 Math 230 Assembly Programming (AKA Computer Organization) Spring 2008 MIPS Intro II Lect 10 Feb 15, 2008 Adapted from slides developed for: Mary J. Irwin PSU CSE331 Dave Patterson s UCB CS152 M230 L10.1
Math 230 Assembly Programming (AKA Computer Organization) Spring 2008 MIPS Intro II Lect 10 Feb 15, 2008 Adapted from slides developed for: Mary J. Irwin PSU CSE331 Dave Patterson s UCB CS152 M230 L10.1
CS 31: Intro to Systems Binary Arithmetic. Martin Gagné Swarthmore College January 24, 2016
 CS 31: Intro to Systems Binary Arithmetic Martin Gagné Swarthmore College January 24, 2016 Unsigned Integers Suppose we had one byte Can represent 2 8 (256) values If unsigned (strictly non-negative):
CS 31: Intro to Systems Binary Arithmetic Martin Gagné Swarthmore College January 24, 2016 Unsigned Integers Suppose we had one byte Can represent 2 8 (256) values If unsigned (strictly non-negative):
CS107, Lecture 3 Bits and Bytes; Bitwise Operators
 CS107, Lecture 3 Bits and Bytes; Bitwise Operators reading: Bryant & O Hallaron, Ch. 2.1 This document is copyright (C) Stanford Computer Science and Nick Troccoli, licensed under Creative Commons Attribution
CS107, Lecture 3 Bits and Bytes; Bitwise Operators reading: Bryant & O Hallaron, Ch. 2.1 This document is copyright (C) Stanford Computer Science and Nick Troccoli, licensed under Creative Commons Attribution
More about Binary 9/6/2016
 More about Binary 9/6/2016 Unsigned vs. Two s Complement 8-bit example: 1 1 0 0 0 0 1 1 2 7 +2 6 + 2 1 +2 0 = 128+64+2+1 = 195-2 7 +2 6 + 2 1 +2 0 = -128+64+2+1 = -61 Why does two s complement work this
More about Binary 9/6/2016 Unsigned vs. Two s Complement 8-bit example: 1 1 0 0 0 0 1 1 2 7 +2 6 + 2 1 +2 0 = 128+64+2+1 = 195-2 7 +2 6 + 2 1 +2 0 = -128+64+2+1 = -61 Why does two s complement work this
Arithmetic Operators. Portability: Printing Numbers
 Arithmetic Operators Normal binary arithmetic operators: + - * / Modulus or remainder operator: % x%y is the remainder when x is divided by y well defined only when x > 0 and y > 0 Unary operators: - +
Arithmetic Operators Normal binary arithmetic operators: + - * / Modulus or remainder operator: % x%y is the remainder when x is divided by y well defined only when x > 0 and y > 0 Unary operators: - +
CIS 2107 Computer Systems and Low-Level Programming Fall 2011 Midterm Solutions
 Fall 2011 Name: Page Points Score 1 7 2 10 3 8 4 13 6 17 7 4 8 16 9 15 10 10 Total: 100 Instructions The exam is closed book, closed notes. You may not use a calculator, cell phone, etc. For each of the
Fall 2011 Name: Page Points Score 1 7 2 10 3 8 4 13 6 17 7 4 8 16 9 15 10 10 Total: 100 Instructions The exam is closed book, closed notes. You may not use a calculator, cell phone, etc. For each of the
CprE 288 Introduction to Embedded Systems Exam 1 Review. 1
 CprE 288 Introduction to Embedded Systems Exam 1 Review http://class.ece.iastate.edu/cpre288 1 Overview of Today s Lecture Announcements Exam 1 Review http://class.ece.iastate.edu/cpre288 2 Announcements
CprE 288 Introduction to Embedded Systems Exam 1 Review http://class.ece.iastate.edu/cpre288 1 Overview of Today s Lecture Announcements Exam 1 Review http://class.ece.iastate.edu/cpre288 2 Announcements
17. Instruction Sets: Characteristics and Functions
 17. Instruction Sets: Characteristics and Functions Chapter 12 Spring 2016 CS430 - Computer Architecture 1 Introduction Section 12.1, 12.2, and 12.3 pp. 406-418 Computer Designer: Machine instruction set
17. Instruction Sets: Characteristics and Functions Chapter 12 Spring 2016 CS430 - Computer Architecture 1 Introduction Section 12.1, 12.2, and 12.3 pp. 406-418 Computer Designer: Machine instruction set
CS 31: Intro to Systems C Programming. Kevin Webb Swarthmore College September 13, 2018
 CS 31: Intro to Systems C Programming Kevin Webb Swarthmore College September 13, 2018 Reading Quiz Agenda Basics of C programming Comments, variables, print statements, loops, conditionals, etc. NOT the
CS 31: Intro to Systems C Programming Kevin Webb Swarthmore College September 13, 2018 Reading Quiz Agenda Basics of C programming Comments, variables, print statements, loops, conditionals, etc. NOT the
Integer Representation
 Integer Representation Announcements assign0 due tonight assign1 out tomorrow Labs start this week SCPD Note on ofce hours on Piazza Will get an email tonight about labs Goals for Today Introduction to
Integer Representation Announcements assign0 due tonight assign1 out tomorrow Labs start this week SCPD Note on ofce hours on Piazza Will get an email tonight about labs Goals for Today Introduction to
Computer Systems Principles. C Pointers
 Computer Systems Principles C Pointers 1 Learning Objectives Learn about floating point number Learn about typedef, enum, and union Learn and understand pointers 2 FLOATING POINT NUMBER 3 IEEE Floating
Computer Systems Principles C Pointers 1 Learning Objectives Learn about floating point number Learn about typedef, enum, and union Learn and understand pointers 2 FLOATING POINT NUMBER 3 IEEE Floating
C OVERVIEW. C Overview. Goals speed portability allow access to features of the architecture speed
 C Overview C OVERVIEW Goals speed portability allow access to features of the architecture speed C fast executables allows high-level structure without losing access to machine features many popular languages
C Overview C OVERVIEW Goals speed portability allow access to features of the architecture speed C fast executables allows high-level structure without losing access to machine features many popular languages
