A RISC class (extended abstract)
|
|
|
- Monica Lesley Malone
- 5 years ago
- Views:
Transcription
1 A RISC class (extended abstract) Andrew Koenig AT&T Bell Laboratories Murray Hill, New Jersey The state of the art Over the past several years, C+ + class authors have spent a lot of effort on container classes: classes whose objects contain objects of some other class. During that time, a canonical style has evolved: a container actually holds objects while an object of an auxiliary class called an iterator marks a place in the container. This strategy is similar to how arrays work in traditional languages: an array holds values and an auxiliary value, usually an integer or a pointer, marks a place in the array. Thus when we write a C program fragment like: int a[n]; int i; for (i = 0; i < N; i++) a[i] = i; we are using a as a container and i as an iterator. Because the iterator idea fits well with data structures in traditional programming languages, C+ + programmers find it easy to adopt. However, iterators are not quite as simple in practice as in theory. For example, the possibility that containers might be const implies that two kinds of iterators are actually necessary for each kind of container: one that can only read the container and one that can read and write it. This is analogous to the two kinds of pointers that might point to an object of type T, namely T* and const T*. In addition to requiring three classes for each kind of container, the traditional approach puts lots of features into the container and iterators. Aside from the usual social pressure, this is sometimes necessary to ensure proper interaction with iterators. For example, the list class from the USL Standard Components library supports the following operations: Create a list from 0 4 elements. Copy and assign a list. Determine the length of a list. Concatenate two lists. Determine if two lists are equal. Add, access, or delete an element at either end. Access the nth element. Sort a list. Print an entire list, recursively using the output operation defined on the list elements In addition, list iterators support the following operations: Create, copy, assign, and compare iterators. Find the list associated with a given iterator. Determine if the iterator is at the end of its list.
2 - 2 - Search for an element with a given value. Advance the iterator to refer to the next element in the list (in either direction). Access the element before or after the iterator (iterators point between elements). The operations add up: the USL list class has 70 members and one friend function, divided as follows: List: 27 members, one friend. Const_listiter: 28 members. Listiter: 15 members. The implementation is more than 900 lines of source code. A radical old idea All this functionality is very nice, but it sometimes leaves one wishing for less. If we can have lightweight processes and RISC (Reduced Instruction Set Computer) chips, why not a RISC (Reduced Instruction Set Container) class? For inspiration, I went back more than a third of a century and looked at Lisp. Lisp has grown greatly over the years, but its original notion of a list was defined in terms of just five operations: nil: a list with no elements. cons(a,b): a list whose first component is a and whose subsequent components are those of the list b. car(s): the first component of s; s must be a list with at least one component. cdr(s): all the components of s except the first; s must be a list with at least one component. null(s): true if s has no components, false otherwise; s must be a list. There is a very large body of theory and practice that shows that these operations are useful. Moreover, it s easy enough to implement in C+ + if we add the restriction that all the elements of a list must be the same type. Using templates, we can then define a class Seq<T> that represents a list of objects of type T. It s called Seq rather than List to avoid confusing it with any of the other List classes out there. Suppose we start by implementing just the five primitive Lisp operations. How might those look in C+ +? Assume that t has type T and s has type Seq<T>. Then the following C+ + operations suggest themselves: Seq<T>(): a sequence with no elements. cons(t,s): a sequence with first element t and subsequent elements those of s. s.hd(): the first element of s; s must have at least one element. s.tl(): a sequence containing all but the first element of s; s must have at least one element. (const void*)s: nonzero if s has no elements, otherwise zero. The names hd and tl are there because they are easier to explain to non-lispers than car and cdr. The conversion to const void* is intended to be used in if and while statements. Well, maybe a few extras... This class is pretty easy to implement. Moreover, it is useful as it stands. However, it is hard to resist the temptation to add a few additional operations to make it easier to use. Some of this ease of use comes from differences in typical style between Lisp and C+ + programs.
3 - 3 - For example, suppose we want to compute the number of elements in a sequence s. A Lisp programmer might write it this way: int length(const Seq<T>& s) if (s) return (1+ (length (s.tl()))); return 0; but a C+ + programmer would be prone to do it this way: int length(seq<t> s) int n = 0; while (s) s = s.tl(); n++; return n; This combination of testing for null and extracting an element happens so often that it is useful to introduce an operation called next to do that. Using it, the inner loop looks like this: while (s.next()) n++; It also turns out to be useful to overload next to put the element it extracted into a variable passed by reference, so that int n, sum = 0; while (intseq.next(n)) sum += n; adds the elements of a Seq<int> named intseq and puts the result in sum. Another common operation is to put a new value at the head of a list. Using the primitives, that looks like this: s = cons(s, x); and is again sufficiently common to warrant a built-in operation: s.insert(x); There are efficiency reasons for these extra built-ins, too; we will discuss those later. Of course, it is a hard judgment call where to stop adding things. Example of use The best way to give a feel for how this class works is with a complete example. We will begin with a function to merge two sequences, assumed to be in ascending order:
4 - 4 - Seq<T> merge(const Seq<T>& x, const Seq<T>& y) if (!x) return y; if (!y) return x; T xh = x.hd(); T yh = y.hd(); if (xh < yh) return cons(xh, merge(x.tl(), y)); return cons(yh, merge(x, y.tl())); Programmers who aren t used to recursion might prefer doing it this way: Seq<T> merge(seq<t> x, Seq<T> y) Seq<T> r; while (x && y) if (x.hd() < y.hd()) r.insert(x.hd()); else r.insert(y.hd()); y.next(); while (x) r.insert(x.hd()); while (y) r.insert(y.hd()); y.next(); r.flip(); return r; Aside from the primitives and insert and next, this second implementation uses one other built-in: s.flip() reverses the elements of s in place. Which of these two versions is easier to understand probably depends on where you were brought up. Next we ll look at a function that splits a sequence into two piles, much the way one would deal a deck of cards. We will assume either that the piles are empty to start, or that our caller doesn t mind our piling the elements on top of the ones already there. The elements are reversed in the process, just as they are when dealing cards:
5 - 5 - void split(seq<t> x, Seq<T>& y, Seq<T>& z) while (x) y.insert(x.hd()); if (x) z.insert(x.hd()); The only thing the least bit tricky here is that if (x) //... cannot be collapsed into if (x.next()) //... because we want to see if x is non-empty only after removing the first element. Finally, we can use these two functions to make a simple sort function: Seq<T> sort(const Seq<T>& x) if (!x!x.tl()) return x; Seq<T> p, q; split(x, p, q); return merge(sort(p), sort(q)); Simple as it is, this merge sort has O( log n) performance, even in the worst case. Perhaps a measure of the utility of the Seq class is how rare it is to find a sort that can be explained to novices and also has good asymptotic performance. Experience I implemented this class using a straightforward use-counted memory allocation technique. That means that copying a Seq<T> object does not copy its components, so it is not particularly expensive to pass Seq<T> objects directly to functions instead of references. This implementation partly motivates some of the extra operations, because some optimizations are possible if the right use counts happen to be 1. For example, if the use counts of all the elements of a sequence are 1, it is possible to concatenate another sequence onto the end of it in place. This can be substantially faster than the obvious implementation:
6 - 6 - Seq<T> operator+(const Seq<T>& r, const Seq<T>& s) if (!s) return r; if (!r) return s; return cons(r.hd(), r.tl()+s); A similar optimization is possible for the flip operation. Even with the extra operations and optimizations, the class has only fourteen members and four friends. The complete implementation is less than 200 lines of source code; the manual page fits on one (double sided) sheet of paper. For the operations it supports, it runs about as fast as the USL list class. Future directions Right now, this class is used by the author and a few of his colleagues. That experience shows that it is indeed useful, but a few more operations would make it even more useful. One is a length function. Of course it is possible to find the length of a sequence, but it is sometimes important to be able to do so without looking through the whole thing. For instance, one may wish to copy a sequence into an array, in which case it is important to know how much memory to allocate before beginning the copy. The price of this ability is storing the length in every sequence. However, once that is done, updating it is inexpensive. Another useful operation is the ability to compare entire sequences, especially in a lexical sense. That makes it easy, for example, to sort a container full of sequences. More generally, it would be interesting to apply the RISC approach to other data structures. It works well for sequences because it is possible to get away without modifying the elements of a sequence after it has been created. This restriction is harder for more general data structures, but the functional programming community has shown that it is possible. The interesting question is whether that style can be transplanted into C+ + and, if so, whether people will find it worthwhile to use. This is an open question that deserves an answer.
An anecdote about ML type inference
 An anecdote about ML type inference Andrew Koenig (ark@research.att.com) AT&T Bell Laboratories Murray Hill, New Jersey 07974 Introduction ML strongly supports functional programming; its programmers t
An anecdote about ML type inference Andrew Koenig (ark@research.att.com) AT&T Bell Laboratories Murray Hill, New Jersey 07974 Introduction ML strongly supports functional programming; its programmers t
Intro. Scheme Basics. scm> 5 5. scm>
 Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
CSCI-1200 Data Structures Spring 2018 Lecture 7 Order Notation & Basic Recursion
 CSCI-1200 Data Structures Spring 2018 Lecture 7 Order Notation & Basic Recursion Review from Lectures 5 & 6 Arrays and pointers, Pointer arithmetic and dereferencing, Types of memory ( automatic, static,
CSCI-1200 Data Structures Spring 2018 Lecture 7 Order Notation & Basic Recursion Review from Lectures 5 & 6 Arrays and pointers, Pointer arithmetic and dereferencing, Types of memory ( automatic, static,
DOWNLOAD PDF LINKED LIST PROGRAMS IN DATA STRUCTURE
 Chapter 1 : What is an application of linear linked list data structures? - Quora A linked list is a linear data structure, in which the elements are not stored at contiguous memory locations. The elements
Chapter 1 : What is an application of linear linked list data structures? - Quora A linked list is a linear data structure, in which the elements are not stored at contiguous memory locations. The elements
SCHEME 7. 1 Introduction. 2 Primitives COMPUTER SCIENCE 61A. October 29, 2015
 SCHEME 7 COMPUTER SCIENCE 61A October 29, 2015 1 Introduction In the next part of the course, we will be working with the Scheme programming language. In addition to learning how to write Scheme programs,
SCHEME 7 COMPUTER SCIENCE 61A October 29, 2015 1 Introduction In the next part of the course, we will be working with the Scheme programming language. In addition to learning how to write Scheme programs,
CMSC 341 Hashing (Continued) Based on slides from previous iterations of this course
 CMSC 341 Hashing (Continued) Based on slides from previous iterations of this course Today s Topics Review Uses and motivations of hash tables Major concerns with hash tables Properties Hash function Hash
CMSC 341 Hashing (Continued) Based on slides from previous iterations of this course Today s Topics Review Uses and motivations of hash tables Major concerns with hash tables Properties Hash function Hash
/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Priority Queues / Heaps Date: 9/27/17
 01.433/33 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Priority Queues / Heaps Date: 9/2/1.1 Introduction In this lecture we ll talk about a useful abstraction, priority queues, which are
01.433/33 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Priority Queues / Heaps Date: 9/2/1.1 Introduction In this lecture we ll talk about a useful abstraction, priority queues, which are
PROBLEM SOLVING 11. July 24, 2012
 PROBLEM SOLVING 11 COMPUTER SCIENCE 61A July 24, 2012 Today s section will be a kind of Meta-Section, we are going to walk through some medium to hard-ish problems in Scheme, and we will discuss some methods
PROBLEM SOLVING 11 COMPUTER SCIENCE 61A July 24, 2012 Today s section will be a kind of Meta-Section, we are going to walk through some medium to hard-ish problems in Scheme, and we will discuss some methods
Lecture Notes for Chapter 2: Getting Started
 Instant download and all chapters Instructor's Manual Introduction To Algorithms 2nd Edition Thomas H. Cormen, Clara Lee, Erica Lin https://testbankdata.com/download/instructors-manual-introduction-algorithms-2ndedition-thomas-h-cormen-clara-lee-erica-lin/
Instant download and all chapters Instructor's Manual Introduction To Algorithms 2nd Edition Thomas H. Cormen, Clara Lee, Erica Lin https://testbankdata.com/download/instructors-manual-introduction-algorithms-2ndedition-thomas-h-cormen-clara-lee-erica-lin/
CMSC 341 Lecture 16/17 Hashing, Parts 1 & 2
 CMSC 341 Lecture 16/17 Hashing, Parts 1 & 2 Prof. John Park Based on slides from previous iterations of this course Today s Topics Overview Uses and motivations of hash tables Major concerns with hash
CMSC 341 Lecture 16/17 Hashing, Parts 1 & 2 Prof. John Park Based on slides from previous iterations of this course Today s Topics Overview Uses and motivations of hash tables Major concerns with hash
Lab 4X - Intro to MOOS Programming HINTS
 Lab 4X - Intro to MOOS Programming HINTS 2.680 Unmanned Marine Vehicle Autonomy, Sensing and Communications Spring, 2018 Michael Benjamin, mikerb@mit.edu Henrik Schmidt, henrik@mit.edu Department of Mechanical
Lab 4X - Intro to MOOS Programming HINTS 2.680 Unmanned Marine Vehicle Autonomy, Sensing and Communications Spring, 2018 Michael Benjamin, mikerb@mit.edu Henrik Schmidt, henrik@mit.edu Department of Mechanical
CSE 143. Complexity Analysis. Program Efficiency. Constant Time Statements. Big Oh notation. Analyzing Loops. Constant Time Statements (2) CSE 143 1
 CSE 1 Complexity Analysis Program Efficiency [Sections 12.1-12., 12., 12.9] Count number of instructions executed by program on inputs of a given size Express run time as a function of the input size Assume
CSE 1 Complexity Analysis Program Efficiency [Sections 12.1-12., 12., 12.9] Count number of instructions executed by program on inputs of a given size Express run time as a function of the input size Assume
Functional Programming. Pure Functional Programming
 Functional Programming Pure Functional Programming Computation is largely performed by applying functions to values. The value of an expression depends only on the values of its sub-expressions (if any).
Functional Programming Pure Functional Programming Computation is largely performed by applying functions to values. The value of an expression depends only on the values of its sub-expressions (if any).
A Tour of the Cool Support Code
 A Tour of the Cool Support Code 1 Introduction The Cool compiler project provides a number of basic data types to make the task of writing a Cool compiler tractable in the timespan of the course. This
A Tour of the Cool Support Code 1 Introduction The Cool compiler project provides a number of basic data types to make the task of writing a Cool compiler tractable in the timespan of the course. This
Problem Set 4: Streams and Lazy Evaluation
 Due Friday, March 24 Computer Science (1)21b (Spring Term, 2017) Structure and Interpretation of Computer Programs Problem Set 4: Streams and Lazy Evaluation Reading Assignment: Chapter 3, Section 3.5.
Due Friday, March 24 Computer Science (1)21b (Spring Term, 2017) Structure and Interpretation of Computer Programs Problem Set 4: Streams and Lazy Evaluation Reading Assignment: Chapter 3, Section 3.5.
SCHEME The Scheme Interpreter. 2 Primitives COMPUTER SCIENCE 61A. October 29th, 2012
 SCHEME COMPUTER SCIENCE 6A October 29th, 202 In the next part of the course, we will be working with the Scheme programming language. In addition to learning how to write Scheme programs, we will eventually
SCHEME COMPUTER SCIENCE 6A October 29th, 202 In the next part of the course, we will be working with the Scheme programming language. In addition to learning how to write Scheme programs, we will eventually
Unit 8: Analysis of Algorithms 1: Searching
 P Computer Science Unit 8: nalysis of lgorithms 1: Searching Topics: I. Sigma and Big-O notation II. Linear Search III. Binary Search Materials: I. Rawlins 1.6 II. Rawlins 2.1 III. Rawlins 2.3 IV. Sigma
P Computer Science Unit 8: nalysis of lgorithms 1: Searching Topics: I. Sigma and Big-O notation II. Linear Search III. Binary Search Materials: I. Rawlins 1.6 II. Rawlins 2.1 III. Rawlins 2.3 IV. Sigma
CS 137 Part 8. Merge Sort, Quick Sort, Binary Search. November 20th, 2017
 CS 137 Part 8 Merge Sort, Quick Sort, Binary Search November 20th, 2017 This Week We re going to see two more complicated sorting algorithms that will be our first introduction to O(n log n) sorting algorithms.
CS 137 Part 8 Merge Sort, Quick Sort, Binary Search November 20th, 2017 This Week We re going to see two more complicated sorting algorithms that will be our first introduction to O(n log n) sorting algorithms.
Lesson 13 - Vectors Dynamic Data Storage
 Lesson 13 - Vectors Dynamic Data Storage Summary In this lesson we introduce the Standard Template Library by demonstrating the use of Vectors to provide dynamic storage of data elements. New Concepts
Lesson 13 - Vectors Dynamic Data Storage Summary In this lesson we introduce the Standard Template Library by demonstrating the use of Vectors to provide dynamic storage of data elements. New Concepts
Dynamic Data Types - Recursive Records
 Dynamic Data Types - Recursive Records Example: class List { int hd; List tl ;} J.Carette (McMaster) CS 2S03 1 / 19 Dynamic Data Types - Recursive Records Example: class List { int hd; List tl ;} Note:
Dynamic Data Types - Recursive Records Example: class List { int hd; List tl ;} J.Carette (McMaster) CS 2S03 1 / 19 Dynamic Data Types - Recursive Records Example: class List { int hd; List tl ;} Note:
Assignment 1: grid. Due November 20, 11:59 PM Introduction
 CS106L Fall 2008 Handout #19 November 5, 2008 Assignment 1: grid Due November 20, 11:59 PM Introduction The STL container classes encompass a wide selection of associative and sequence containers. However,
CS106L Fall 2008 Handout #19 November 5, 2008 Assignment 1: grid Due November 20, 11:59 PM Introduction The STL container classes encompass a wide selection of associative and sequence containers. However,
Fibonacci in Lisp. Computer Programming: Skills & Concepts (CP1) Programming Languages. Varieties of Programing Language
 Fibonacci in Lisp Computer Programming: Skills & Concepts (CP1) Programming Languages (defun fibonacci (n) (if (or (= n 0) (= n 1)) 1 (+ (fibonacci (- n 1)) (fibonacci (- n 2))))) 22nd November 2010 defun-
Fibonacci in Lisp Computer Programming: Skills & Concepts (CP1) Programming Languages (defun fibonacci (n) (if (or (= n 0) (= n 1)) 1 (+ (fibonacci (- n 1)) (fibonacci (- n 2))))) 22nd November 2010 defun-
G Programming Languages - Fall 2012
 G22.2110-003 Programming Languages - Fall 2012 Lecture 2 Thomas Wies New York University Review Last week Programming Languages Overview Syntax and Semantics Grammars and Regular Expressions High-level
G22.2110-003 Programming Languages - Fall 2012 Lecture 2 Thomas Wies New York University Review Last week Programming Languages Overview Syntax and Semantics Grammars and Regular Expressions High-level
Data Structures Lecture 3 Order Notation and Recursion
 Data Structures Lecture 3 Order Notation and Recursion 1 Overview The median grade.cpp program from Lecture 2 and background on constructing and using vectors. Algorithm analysis; order notation Recursion
Data Structures Lecture 3 Order Notation and Recursion 1 Overview The median grade.cpp program from Lecture 2 and background on constructing and using vectors. Algorithm analysis; order notation Recursion
Hash Tables. CS 311 Data Structures and Algorithms Lecture Slides. Wednesday, April 22, Glenn G. Chappell
 Hash Tables CS 311 Data Structures and Algorithms Lecture Slides Wednesday, April 22, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks CHAPPELLG@member.ams.org 2005
Hash Tables CS 311 Data Structures and Algorithms Lecture Slides Wednesday, April 22, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks CHAPPELLG@member.ams.org 2005
Sorting: Given a list A with n elements possessing a total order, return a list with the same elements in non-decreasing order.
 Sorting The sorting problem is defined as follows: Sorting: Given a list A with n elements possessing a total order, return a list with the same elements in non-decreasing order. Remember that total order
Sorting The sorting problem is defined as follows: Sorting: Given a list A with n elements possessing a total order, return a list with the same elements in non-decreasing order. Remember that total order
CIS4/681 { Articial Intelligence 2 > (insert-sort '( )) ( ) 2 More Complicated Recursion So far everything we have dened requires
 1 A couple of Functions 1 Let's take another example of a simple lisp function { one that does insertion sort. Let us assume that this sort function takes as input a list of numbers and sorts them in ascending
1 A couple of Functions 1 Let's take another example of a simple lisp function { one that does insertion sort. Let us assume that this sort function takes as input a list of numbers and sorts them in ascending
CS32 Discussion Sec.on 1B Week 2. TA: Zhou Ren
 CS32 Discussion Sec.on 1B Week 2 TA: Zhou Ren Agenda Copy Constructor Assignment Operator Overloading Linked Lists Copy Constructors - Motivation class School { public: }; School(const string &name); string
CS32 Discussion Sec.on 1B Week 2 TA: Zhou Ren Agenda Copy Constructor Assignment Operator Overloading Linked Lists Copy Constructors - Motivation class School { public: }; School(const string &name); string
Functional programming with Common Lisp
 Functional programming with Common Lisp Dr. C. Constantinides Department of Computer Science and Software Engineering Concordia University Montreal, Canada August 11, 2016 1 / 81 Expressions and functions
Functional programming with Common Lisp Dr. C. Constantinides Department of Computer Science and Software Engineering Concordia University Montreal, Canada August 11, 2016 1 / 81 Expressions and functions
Solution printed. Do not start the test until instructed to do so! CS 2604 Data Structures Midterm Spring Instructions:
 VIRG INIA POLYTECHNIC INSTITUTE AND STATE U T PROSI M UNI VERSI TY Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted
VIRG INIA POLYTECHNIC INSTITUTE AND STATE U T PROSI M UNI VERSI TY Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted
Summer 2017 Discussion 10: July 25, Introduction. 2 Primitives and Define
 CS 6A Scheme Summer 207 Discussion 0: July 25, 207 Introduction In the next part of the course, we will be working with the Scheme programming language. In addition to learning how to write Scheme programs,
CS 6A Scheme Summer 207 Discussion 0: July 25, 207 Introduction In the next part of the course, we will be working with the Scheme programming language. In addition to learning how to write Scheme programs,
1 ICS 161: Design and Analysis of Algorithms Lecture notes for January 23, Bucket Sorting
 1 ICS 161: Design and Analysis of Algorithms Lecture notes for January 23, 1996 2 Bucket Sorting We ve seen various algorithms for sorting in O(n log n) time and a lower bound showing that O(n log n) is
1 ICS 161: Design and Analysis of Algorithms Lecture notes for January 23, 1996 2 Bucket Sorting We ve seen various algorithms for sorting in O(n log n) time and a lower bound showing that O(n log n) is
Introduction to C++ Introduction to C++ 1
 1 What Is C++? (Mostly) an extension of C to include: Classes Templates Inheritance and Multiple Inheritance Function and Operator Overloading New (and better) Standard Library References and Reference
1 What Is C++? (Mostly) an extension of C to include: Classes Templates Inheritance and Multiple Inheritance Function and Operator Overloading New (and better) Standard Library References and Reference
Lecture 11 Unbounded Arrays
 Lecture 11 Unbounded Arrays 15-122: Principles of Imperative Computation (Spring 2018) Rob Simmons, Frank Pfenning Arrays have efficient O(1) access to elements given an index, but their size is set at
Lecture 11 Unbounded Arrays 15-122: Principles of Imperative Computation (Spring 2018) Rob Simmons, Frank Pfenning Arrays have efficient O(1) access to elements given an index, but their size is set at
SCHEME 8. 1 Introduction. 2 Primitives COMPUTER SCIENCE 61A. March 23, 2017
 SCHEME 8 COMPUTER SCIENCE 61A March 2, 2017 1 Introduction In the next part of the course, we will be working with the Scheme programming language. In addition to learning how to write Scheme programs,
SCHEME 8 COMPUTER SCIENCE 61A March 2, 2017 1 Introduction In the next part of the course, we will be working with the Scheme programming language. In addition to learning how to write Scheme programs,
Table ADT and Sorting. Algorithm topics continuing (or reviewing?) CS 24 curriculum
 Table ADT and Sorting Algorithm topics continuing (or reviewing?) CS 24 curriculum A table ADT (a.k.a. Dictionary, Map) Table public interface: // Put information in the table, and a unique key to identify
Table ADT and Sorting Algorithm topics continuing (or reviewing?) CS 24 curriculum A table ADT (a.k.a. Dictionary, Map) Table public interface: // Put information in the table, and a unique key to identify
Lecture 2: Getting Started
 Lecture 2: Getting Started Insertion Sort Our first algorithm is Insertion Sort Solves the sorting problem Input: A sequence of n numbers a 1, a 2,..., a n. Output: A permutation (reordering) a 1, a 2,...,
Lecture 2: Getting Started Insertion Sort Our first algorithm is Insertion Sort Solves the sorting problem Input: A sequence of n numbers a 1, a 2,..., a n. Output: A permutation (reordering) a 1, a 2,...,
2. List Implementations (a) Class Templates (b) Contiguous (c) Simply Linked (d) Simply Linked with Position Pointer (e) Doubly Linked
 Chapter 6 LISTS AND STRINGS 1. List Specifications 2. List Implementations (a) Class Templates (b) Contiguous (c) Simply Linked (d) Simply Linked with Position Pointer (e) Doubly Linked 3. Strings 4. Application:
Chapter 6 LISTS AND STRINGS 1. List Specifications 2. List Implementations (a) Class Templates (b) Contiguous (c) Simply Linked (d) Simply Linked with Position Pointer (e) Doubly Linked 3. Strings 4. Application:
Documentation for LISP in BASIC
 Documentation for LISP in BASIC The software and the documentation are both Copyright 2008 Arthur Nunes-Harwitt LISP in BASIC is a LISP interpreter for a Scheme-like dialect of LISP, which happens to have
Documentation for LISP in BASIC The software and the documentation are both Copyright 2008 Arthur Nunes-Harwitt LISP in BASIC is a LISP interpreter for a Scheme-like dialect of LISP, which happens to have
Computer Science 62. Bruce/Mawhorter Fall 16. Midterm Examination. October 5, Question Points Score TOTAL 52 SOLUTIONS. Your name (Please print)
 Computer Science 62 Bruce/Mawhorter Fall 16 Midterm Examination October 5, 2016 Question Points Score 1 15 2 10 3 10 4 8 5 9 TOTAL 52 SOLUTIONS Your name (Please print) 1. Suppose you are given a singly-linked
Computer Science 62 Bruce/Mawhorter Fall 16 Midterm Examination October 5, 2016 Question Points Score 1 15 2 10 3 10 4 8 5 9 TOTAL 52 SOLUTIONS Your name (Please print) 1. Suppose you are given a singly-linked
Sorting is a problem for which we can prove a non-trivial lower bound.
 Sorting The sorting problem is defined as follows: Sorting: Given a list a with n elements possessing a total order, return a list with the same elements in non-decreasing order. Remember that total order
Sorting The sorting problem is defined as follows: Sorting: Given a list a with n elements possessing a total order, return a list with the same elements in non-decreasing order. Remember that total order
/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Sorting lower bound and Linear-time sorting Date: 9/19/17
 601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Sorting lower bound and Linear-time sorting Date: 9/19/17 5.1 Introduction You should all know a few ways of sorting in O(n log n)
601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Sorting lower bound and Linear-time sorting Date: 9/19/17 5.1 Introduction You should all know a few ways of sorting in O(n log n)
Scheme as implemented by Racket
 Scheme as implemented by Racket (Simple view:) Racket is a version of Scheme. (Full view:) Racket is a platform for implementing and using many languages, and Scheme is one of those that come out of the
Scheme as implemented by Racket (Simple view:) Racket is a version of Scheme. (Full view:) Racket is a platform for implementing and using many languages, and Scheme is one of those that come out of the
How many leaves on the decision tree? There are n! leaves, because every permutation appears at least once.
 Chapter 8. Sorting in Linear Time Types of Sort Algorithms The only operation that may be used to gain order information about a sequence is comparison of pairs of elements. Quick Sort -- comparison-based
Chapter 8. Sorting in Linear Time Types of Sort Algorithms The only operation that may be used to gain order information about a sequence is comparison of pairs of elements. Quick Sort -- comparison-based
C++ 11 and the Standard Library: Containers, Iterators, Algorithms
 and the Standard Library:,, Comp Sci 1575 Outline 1 2 3 4 Outline 1 2 3 4 #i n clude i n t main ( ) { i n t v a l u e 0 = 5 ; // C++ 98 i n t v a l u e 1 ( 5 ) ; // C++ 98 i n t v a
and the Standard Library:,, Comp Sci 1575 Outline 1 2 3 4 Outline 1 2 3 4 #i n clude i n t main ( ) { i n t v a l u e 0 = 5 ; // C++ 98 i n t v a l u e 1 ( 5 ) ; // C++ 98 i n t v a
An Introduction to Subtyping
 An Introduction to Subtyping Type systems are to me the most interesting aspect of modern programming languages. Subtyping is an important notion that is helpful for describing and reasoning about type
An Introduction to Subtyping Type systems are to me the most interesting aspect of modern programming languages. Subtyping is an important notion that is helpful for describing and reasoning about type
Repetition Through Recursion
 Fundamentals of Computer Science I (CS151.02 2007S) Repetition Through Recursion Summary: In many algorithms, you want to do things again and again and again. For example, you might want to do something
Fundamentals of Computer Science I (CS151.02 2007S) Repetition Through Recursion Summary: In many algorithms, you want to do things again and again and again. For example, you might want to do something
Chapter 18: Parallel Databases
 Chapter 18: Parallel Databases Introduction Parallel machines are becoming quite common and affordable Prices of microprocessors, memory and disks have dropped sharply Recent desktop computers feature
Chapter 18: Parallel Databases Introduction Parallel machines are becoming quite common and affordable Prices of microprocessors, memory and disks have dropped sharply Recent desktop computers feature
We cover recursion in 150. Why do it again in 151?
 Recursion We cover recursion in 150. Why do it again in 151? First, good solutions to problems are often recursive. Here is a quick way to sort a list of objects: split the list in half, recursively sort
Recursion We cover recursion in 150. Why do it again in 151? First, good solutions to problems are often recursive. Here is a quick way to sort a list of objects: split the list in half, recursively sort
Sorting. Sorting in Arrays. SelectionSort. SelectionSort. Binary search works great, but how do we create a sorted array in the first place?
 Sorting Binary search works great, but how do we create a sorted array in the first place? Sorting in Arrays Sorting algorithms: Selection sort: O(n 2 ) time Merge sort: O(nlog 2 (n)) time Quicksort: O(n
Sorting Binary search works great, but how do we create a sorted array in the first place? Sorting in Arrays Sorting algorithms: Selection sort: O(n 2 ) time Merge sort: O(nlog 2 (n)) time Quicksort: O(n
CSCE 2014 Final Exam Spring Version A
 CSCE 2014 Final Exam Spring 2017 Version A Student Name: Student UAID: Instructions: This is a two-hour exam. Students are allowed one 8.5 by 11 page of study notes. Calculators, cell phones and computers
CSCE 2014 Final Exam Spring 2017 Version A Student Name: Student UAID: Instructions: This is a two-hour exam. Students are allowed one 8.5 by 11 page of study notes. Calculators, cell phones and computers
Functions, Pointers, and the Basics of C++ Classes
 Functions, Pointers, and the Basics of C++ Classes William E. Skeith III Functions in C++ Vocabulary You should be familiar with all of the following terms already, but if not, you will be after today.
Functions, Pointers, and the Basics of C++ Classes William E. Skeith III Functions in C++ Vocabulary You should be familiar with all of the following terms already, but if not, you will be after today.
Bring Back the Obvious Definition of count()
 Bring Back the Obvious Definition of count() Bjarne Stroustrup AT&T Bell Laboratories Murray Hill, New Jersey 07974 Alex Stepanov, Matt Austern Silicon Graphics Inc. ABSTRACT #X3J16/96-0029 WG21/N0847
Bring Back the Obvious Definition of count() Bjarne Stroustrup AT&T Bell Laboratories Murray Hill, New Jersey 07974 Alex Stepanov, Matt Austern Silicon Graphics Inc. ABSTRACT #X3J16/96-0029 WG21/N0847
PAIRS AND LISTS 6. GEORGE WANG Department of Electrical Engineering and Computer Sciences University of California, Berkeley
 PAIRS AND LISTS 6 GEORGE WANG gswang.cs61a@gmail.com Department of Electrical Engineering and Computer Sciences University of California, Berkeley June 29, 2010 1 Pairs 1.1 Overview To represent data types
PAIRS AND LISTS 6 GEORGE WANG gswang.cs61a@gmail.com Department of Electrical Engineering and Computer Sciences University of California, Berkeley June 29, 2010 1 Pairs 1.1 Overview To represent data types
Machine-Independent Optimizations
 Chapter 9 Machine-Independent Optimizations High-level language constructs can introduce substantial run-time overhead if we naively translate each construct independently into machine code. This chapter
Chapter 9 Machine-Independent Optimizations High-level language constructs can introduce substantial run-time overhead if we naively translate each construct independently into machine code. This chapter
6.001 Notes: Section 17.5
 6.001 Notes: Section 17.5 Slide 17.5.1 Now, let's look at one example in which changing the evaluation model allows us to explore a very different kind of computational problem. Our goal is to show how
6.001 Notes: Section 17.5 Slide 17.5.1 Now, let's look at one example in which changing the evaluation model allows us to explore a very different kind of computational problem. Our goal is to show how
Scan and Quicksort. 1 Scan. 1.1 Contraction CSE341T 09/20/2017. Lecture 7
 CSE341T 09/20/2017 Lecture 7 Scan and Quicksort 1 Scan Scan is a very useful primitive for parallel programming. We will use it all the time in this class. First, lets start by thinking about what other
CSE341T 09/20/2017 Lecture 7 Scan and Quicksort 1 Scan Scan is a very useful primitive for parallel programming. We will use it all the time in this class. First, lets start by thinking about what other
CS1622. Semantic Analysis. The Compiler So Far. Lecture 15 Semantic Analysis. How to build symbol tables How to use them to find
 CS1622 Lecture 15 Semantic Analysis CS 1622 Lecture 15 1 Semantic Analysis How to build symbol tables How to use them to find multiply-declared and undeclared variables. How to perform type checking CS
CS1622 Lecture 15 Semantic Analysis CS 1622 Lecture 15 1 Semantic Analysis How to build symbol tables How to use them to find multiply-declared and undeclared variables. How to perform type checking CS
CS 137 Part 7. Big-Oh Notation, Linear Searching and Basic Sorting Algorithms. November 10th, 2017
 CS 137 Part 7 Big-Oh Notation, Linear Searching and Basic Sorting Algorithms November 10th, 2017 Big-Oh Notation Up to this point, we ve been writing code without any consideration for optimization. There
CS 137 Part 7 Big-Oh Notation, Linear Searching and Basic Sorting Algorithms November 10th, 2017 Big-Oh Notation Up to this point, we ve been writing code without any consideration for optimization. There
Tutorial Letter 102/1/2012 Programming: Data Structures
 /1/2012 Tutorial Letter 102/1/2012 Programming: Data Structures COS2611 Semester 1 School of Computing This tutorial letter contains important information regarding the Exam. Bar code List of all tutorial
/1/2012 Tutorial Letter 102/1/2012 Programming: Data Structures COS2611 Semester 1 School of Computing This tutorial letter contains important information regarding the Exam. Bar code List of all tutorial
Algebraic Specifications
 Object-Oriented Design Lecture 2 CSU 370 Fall 2007 (Pucella) Tuesday, Sep 11, 2007 Algebraic Specifications Last time I said a word about the abstraction barrier, separating the clients from the implementors.
Object-Oriented Design Lecture 2 CSU 370 Fall 2007 (Pucella) Tuesday, Sep 11, 2007 Algebraic Specifications Last time I said a word about the abstraction barrier, separating the clients from the implementors.
An introduction to Digital Signal Processors (DSP) Using the C55xx family
 An introduction to Digital Signal Processors (DSP) Using the C55xx family Group status (~2 minutes each) 5 groups stand up What processor(s) you are using Wireless? If so, what technologies/chips are you
An introduction to Digital Signal Processors (DSP) Using the C55xx family Group status (~2 minutes each) 5 groups stand up What processor(s) you are using Wireless? If so, what technologies/chips are you
CS 270 Algorithms. Oliver Kullmann. Binary search. Lists. Background: Pointers. Trees. Implementing rooted trees. Tutorial
 Week 7 General remarks Arrays, lists, pointers and 1 2 3 We conclude elementary data structures by discussing and implementing arrays, lists, and trees. Background information on pointers is provided (for
Week 7 General remarks Arrays, lists, pointers and 1 2 3 We conclude elementary data structures by discussing and implementing arrays, lists, and trees. Background information on pointers is provided (for
Abstraction Functions Lecture 9 Fall 2005
 Abstraction Functions 6.170 Lecture 9 Fall 2005 8.1 Introduction In this lecture, we turn to our second tool for understanding abstract data types: the abstraction function. The rep invariant describes
Abstraction Functions 6.170 Lecture 9 Fall 2005 8.1 Introduction In this lecture, we turn to our second tool for understanding abstract data types: the abstraction function. The rep invariant describes
Chapter 9 Subroutines and Control Abstraction. June 22, 2016
 Chapter 9 Subroutines and Control Abstraction June 22, 2016 Stack layout Common to have subroutine activation record allocated on a stack Typical fare for a frame: arguments, return value, saved registers,
Chapter 9 Subroutines and Control Abstraction June 22, 2016 Stack layout Common to have subroutine activation record allocated on a stack Typical fare for a frame: arguments, return value, saved registers,
Properties of an identifier (and the object it represents) may be set at
 Properties of an identifier (and the object it represents) may be set at Compile-time These are static properties as they do not change during execution. Examples include the type of a variable, the value
Properties of an identifier (and the object it represents) may be set at Compile-time These are static properties as they do not change during execution. Examples include the type of a variable, the value
Chapter 10 Recursion
 Chapter 10 Recursion Written by Dr. Mark Snyder [minor edits for this semester by Dr. Kinga Dobolyi] Recursion implies that something is defined in terms of itself. We will see in detail how code can be
Chapter 10 Recursion Written by Dr. Mark Snyder [minor edits for this semester by Dr. Kinga Dobolyi] Recursion implies that something is defined in terms of itself. We will see in detail how code can be
Spare Matrix Formats, and The Standard Template Library
 Annotated slides CS319: Scientific Computing (with C++) Spare Matrix Formats, and The Standard Template Library Week 10: 9am and 4pm, 20 March 2019 1 Sparse Matrices 2 3 Compressed Column Storage 4 (Not)
Annotated slides CS319: Scientific Computing (with C++) Spare Matrix Formats, and The Standard Template Library Week 10: 9am and 4pm, 20 March 2019 1 Sparse Matrices 2 3 Compressed Column Storage 4 (Not)
Section 05: Solutions
 Section 05: Solutions 1. Asymptotic Analysis (a) Applying definitions For each of the following, choose a c and n 0 which show f(n) O(g(n)). Explain why your values of c and n 0 work. (i) f(n) = 5000n
Section 05: Solutions 1. Asymptotic Analysis (a) Applying definitions For each of the following, choose a c and n 0 which show f(n) O(g(n)). Explain why your values of c and n 0 work. (i) f(n) = 5000n
Trees can be used to store entire records from a database, serving as an in-memory representation of the collection of records in a file.
 Large Trees 1 Trees can be used to store entire records from a database, serving as an in-memory representation of the collection of records in a file. Trees can also be used to store indices of the collection
Large Trees 1 Trees can be used to store entire records from a database, serving as an in-memory representation of the collection of records in a file. Trees can also be used to store indices of the collection
Lecture 6: Sequential Sorting
 15-150 Lecture 6: Sequential Sorting Lecture by Dan Licata February 2, 2012 Today s lecture is about sorting. Along the way, we ll learn about divide and conquer algorithms, the tree method, and complete
15-150 Lecture 6: Sequential Sorting Lecture by Dan Licata February 2, 2012 Today s lecture is about sorting. Along the way, we ll learn about divide and conquer algorithms, the tree method, and complete
Virtualization. Q&A with an industry leader. Virtualization is rapidly becoming a fact of life for agency executives,
 Virtualization Q&A with an industry leader Virtualization is rapidly becoming a fact of life for agency executives, as the basis for data center consolidation and cloud computing and, increasingly, as
Virtualization Q&A with an industry leader Virtualization is rapidly becoming a fact of life for agency executives, as the basis for data center consolidation and cloud computing and, increasingly, as
How to approach a computational problem
 How to approach a computational problem A lot of people find computer programming difficult, especially when they first get started with it. Sometimes the problems are problems specifically related to
How to approach a computational problem A lot of people find computer programming difficult, especially when they first get started with it. Sometimes the problems are problems specifically related to
Let the dynamic table support the operations TABLE-INSERT and TABLE-DELETE It is convenient to use the load factor ( )
 17.4 Dynamic tables Let us now study the problem of dynamically expanding and contracting a table We show that the amortized cost of insertion/ deletion is only (1) Though the actual cost of an operation
17.4 Dynamic tables Let us now study the problem of dynamically expanding and contracting a table We show that the amortized cost of insertion/ deletion is only (1) Though the actual cost of an operation
Chapter 18: Parallel Databases Chapter 19: Distributed Databases ETC.
 Chapter 18: Parallel Databases Chapter 19: Distributed Databases ETC. Introduction Parallel machines are becoming quite common and affordable Prices of microprocessors, memory and disks have dropped sharply
Chapter 18: Parallel Databases Chapter 19: Distributed Databases ETC. Introduction Parallel machines are becoming quite common and affordable Prices of microprocessors, memory and disks have dropped sharply
Algorithm for siftdown(int currentposition) while true (infinite loop) do if the currentposition has NO children then return
 0. How would we write the BinaryHeap siftdown function recursively? [0] 6 [1] [] 15 10 Name: template class BinaryHeap { private: int maxsize; int numitems; T * heap;... [3] [4] [5] [6] 114 0
0. How would we write the BinaryHeap siftdown function recursively? [0] 6 [1] [] 15 10 Name: template class BinaryHeap { private: int maxsize; int numitems; T * heap;... [3] [4] [5] [6] 114 0
Recap: Pointers. int* int& *p &i &*&* ** * * * * IFMP 18, M. Schwerhoff
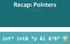 Recap: Pointers IFMP 18, M. Schwerhoff int* int& *p &i &*&* ** * * * * A 0 A 1 A 2 A 3 A 4 A 5 A 0 A 1 A 2 A 3 A 4 A 5 5 i int* p; A 0 A 1 A 2 A 3 A 4 A 5 5 i p int* p; p = &i; A 0 A 1 A 2 A 3 A 4 A 5
Recap: Pointers IFMP 18, M. Schwerhoff int* int& *p &i &*&* ** * * * * A 0 A 1 A 2 A 3 A 4 A 5 A 0 A 1 A 2 A 3 A 4 A 5 5 i int* p; A 0 A 1 A 2 A 3 A 4 A 5 5 i p int* p; p = &i; A 0 A 1 A 2 A 3 A 4 A 5
Computer Science II Lecture 2 Strings, Vectors and Recursion
 1 Overview of Lecture 2 Computer Science II Lecture 2 Strings, Vectors and Recursion The following topics will be covered quickly strings vectors as smart arrays Basic recursion Mostly, these are assumed
1 Overview of Lecture 2 Computer Science II Lecture 2 Strings, Vectors and Recursion The following topics will be covered quickly strings vectors as smart arrays Basic recursion Mostly, these are assumed
I m sure you have been annoyed at least once by having to type out types like this:
 Type Inference The first thing I m going to talk about is type inference. C++11 provides mechanisms which make the compiler deduce the types of expressions. These features allow you to make your code more
Type Inference The first thing I m going to talk about is type inference. C++11 provides mechanisms which make the compiler deduce the types of expressions. These features allow you to make your code more
Heap Management. Heap Allocation
 Heap Management Heap Allocation A very flexible storage allocation mechanism is heap allocation. Any number of data objects can be allocated and freed in a memory pool, called a heap. Heap allocation is
Heap Management Heap Allocation A very flexible storage allocation mechanism is heap allocation. Any number of data objects can be allocated and freed in a memory pool, called a heap. Heap allocation is
The divide-and-conquer paradigm involves three steps at each level of the recursion: Divide the problem into a number of subproblems.
 2.3 Designing algorithms There are many ways to design algorithms. Insertion sort uses an incremental approach: having sorted the subarray A[1 j - 1], we insert the single element A[j] into its proper
2.3 Designing algorithms There are many ways to design algorithms. Insertion sort uses an incremental approach: having sorted the subarray A[1 j - 1], we insert the single element A[j] into its proper
;; definition of function, fun, that adds 7 to the input (define fun (lambda (x) (+ x 7)))
 Homework 1 Due 13 September Handout 2 CSC 131: Fall, 2006 6 September Reading 1. Read Mitchell, Chapter 3. 2. The Scheme Tutorial and the Scheme Quick Reference from the Links web page, as needed for the
Homework 1 Due 13 September Handout 2 CSC 131: Fall, 2006 6 September Reading 1. Read Mitchell, Chapter 3. 2. The Scheme Tutorial and the Scheme Quick Reference from the Links web page, as needed for the
Scan and its Uses. 1 Scan. 1.1 Contraction CSE341T/CSE549T 09/17/2014. Lecture 8
 CSE341T/CSE549T 09/17/2014 Lecture 8 Scan and its Uses 1 Scan Today, we start by learning a very useful primitive. First, lets start by thinking about what other primitives we have learned so far? The
CSE341T/CSE549T 09/17/2014 Lecture 8 Scan and its Uses 1 Scan Today, we start by learning a very useful primitive. First, lets start by thinking about what other primitives we have learned so far? The
Order Analysis of Algorithms. Sorting problem
 Order Analysis of Algorithms Debdeep Mukhopadhyay IIT Kharagpur Sorting problem Input: A sequence of n numbers, a1,a2,,an Output: A permutation (reordering) (a1,a2,,an ) of the input sequence such that
Order Analysis of Algorithms Debdeep Mukhopadhyay IIT Kharagpur Sorting problem Input: A sequence of n numbers, a1,a2,,an Output: A permutation (reordering) (a1,a2,,an ) of the input sequence such that
Sorting. Task Description. Selection Sort. Should we worry about speed?
 Sorting Should we worry about speed? Task Description We have an array of n values in any order We need to have the array sorted in ascending or descending order of values 2 Selection Sort Select the smallest
Sorting Should we worry about speed? Task Description We have an array of n values in any order We need to have the array sorted in ascending or descending order of values 2 Selection Sort Select the smallest
COMP 105 Homework: Type Systems
 Due Tuesday, March 29, at 11:59 PM (updated) The purpose of this assignment is to help you learn about type systems. Setup Make a clone of the book code: git clone linux.cs.tufts.edu:/comp/105/build-prove-compare
Due Tuesday, March 29, at 11:59 PM (updated) The purpose of this assignment is to help you learn about type systems. Setup Make a clone of the book code: git clone linux.cs.tufts.edu:/comp/105/build-prove-compare
Binary Trees. For example: Jargon: General Binary Trees. root node. level: internal node. edge. leaf node. Data Structures & File Management
 Binary Trees 1 A binary tree is either empty, or it consists of a node called the root together with two binary trees called the left subtree and the right subtree of the root, which are disjoint from
Binary Trees 1 A binary tree is either empty, or it consists of a node called the root together with two binary trees called the left subtree and the right subtree of the root, which are disjoint from
COSE212: Programming Languages. Lecture 4 Recursive and Higher-Order Programming
 COSE212: Programming Languages Lecture 4 Recursive and Higher-Order Programming Hakjoo Oh 2016 Fall Hakjoo Oh COSE212 2016 Fall, Lecture 4 September 27, 2016 1 / 21 Recursive and Higher-Order Programming
COSE212: Programming Languages Lecture 4 Recursive and Higher-Order Programming Hakjoo Oh 2016 Fall Hakjoo Oh COSE212 2016 Fall, Lecture 4 September 27, 2016 1 / 21 Recursive and Higher-Order Programming
Streams and Lazy Evaluation in Lisp
 Streams and Lazy Evaluation in Lisp Overview Different models of expression evaluation Lazy vs. eager evaluation Normal vs. applicative order evaluation Computing with streams in Lisp Motivation Unix Pipes
Streams and Lazy Evaluation in Lisp Overview Different models of expression evaluation Lazy vs. eager evaluation Normal vs. applicative order evaluation Computing with streams in Lisp Motivation Unix Pipes
Binary Tree Node Relationships. Binary Trees. Quick Application: Expression Trees. Traversals
 Binary Trees 1 Binary Tree Node Relationships 2 A binary tree is either empty, or it consists of a node called the root together with two binary trees called the left subtree and the right subtree of the
Binary Trees 1 Binary Tree Node Relationships 2 A binary tree is either empty, or it consists of a node called the root together with two binary trees called the left subtree and the right subtree of the
CSCI-1200 Data Structures Fall 2011 Lecture 24 Garbage Collection & Smart Pointers
 CSCI-1200 Data Structures Fall 2011 Lecture 24 Garbage Collection & Smart Pointers Review from Lecture 23 Basic exception mechanisms: try/throw/catch Functions & exceptions, constructors & exceptions Today
CSCI-1200 Data Structures Fall 2011 Lecture 24 Garbage Collection & Smart Pointers Review from Lecture 23 Basic exception mechanisms: try/throw/catch Functions & exceptions, constructors & exceptions Today
Arrays. myints = new int[15];
![Arrays. myints = new int[15]; Arrays. myints = new int[15];](/thumbs/72/66387724.jpg) Arrays As you know from COMP 202 (or equivalent), an array is a data structure that holds a set of elements that are of the same type. Each element in the array can be accessed or indexed by a unique number
Arrays As you know from COMP 202 (or equivalent), an array is a data structure that holds a set of elements that are of the same type. Each element in the array can be accessed or indexed by a unique number
Fun facts about recursion
 Outline examples of recursion principles of recursion review: recursive linked list methods binary search more examples of recursion problem solving using recursion 1 Fun facts about recursion every loop
Outline examples of recursion principles of recursion review: recursive linked list methods binary search more examples of recursion problem solving using recursion 1 Fun facts about recursion every loop
Lecture Notes 4 More C++ and recursion CSS 501 Data Structures and Object-Oriented Programming Professor Clark F. Olson
 Lecture Notes 4 More C++ and recursion CSS 501 Data Structures and Object-Oriented Programming Professor Clark F. Olson Reading for this lecture: Carrano, Chapter 2 Copy constructor, destructor, operator=
Lecture Notes 4 More C++ and recursion CSS 501 Data Structures and Object-Oriented Programming Professor Clark F. Olson Reading for this lecture: Carrano, Chapter 2 Copy constructor, destructor, operator=
CS106A, Stanford Handout #30. Coding Style
 CS106A, Stanford Handout #30 Fall, 2004-05 Nick Parlante Coding Style When writing paper, you can have well-crafted, correctly spelled sentences and create "A" work. Or you can hack out the text in a hurry.
CS106A, Stanford Handout #30 Fall, 2004-05 Nick Parlante Coding Style When writing paper, you can have well-crafted, correctly spelled sentences and create "A" work. Or you can hack out the text in a hurry.
Below are example solutions for each of the questions. These are not the only possible answers, but they are the most common ones.
 6.001, Fall Semester, 2002 Quiz II Sample solutions 1 MASSACHVSETTS INSTITVTE OF TECHNOLOGY Department of Electrical Engineering and Computer Science 6.001 Structure and Interpretation of Computer Programs
6.001, Fall Semester, 2002 Quiz II Sample solutions 1 MASSACHVSETTS INSTITVTE OF TECHNOLOGY Department of Electrical Engineering and Computer Science 6.001 Structure and Interpretation of Computer Programs
6.001 Notes: Section 4.1
 6.001 Notes: Section 4.1 Slide 4.1.1 In this lecture, we are going to take a careful look at the kinds of procedures we can build. We will first go back to look very carefully at the substitution model,
6.001 Notes: Section 4.1 Slide 4.1.1 In this lecture, we are going to take a careful look at the kinds of procedures we can build. We will first go back to look very carefully at the substitution model,
09/02/2013 TYPE CHECKING AND CASTING. Lecture 5 CS2110 Spring 2013
 1 TYPE CHECKING AND CASTING Lecture 5 CS2110 Spring 2013 1 Type Checking 2 Java compiler checks to see if your code is legal Today: Explore how this works What is Java doing? Why What will Java do if it
1 TYPE CHECKING AND CASTING Lecture 5 CS2110 Spring 2013 1 Type Checking 2 Java compiler checks to see if your code is legal Today: Explore how this works What is Java doing? Why What will Java do if it
15. Pointers, Algorithms, Iterators and Containers II
 498 Recall: Pointers running over the Array 499 Beispiel 15. Pointers, Algorithms, Iterators and Containers II int a[5] = 3, 4, 6, 1, 2; for (int p = a; p < a+5; ++p) std::cout
498 Recall: Pointers running over the Array 499 Beispiel 15. Pointers, Algorithms, Iterators and Containers II int a[5] = 3, 4, 6, 1, 2; for (int p = a; p < a+5; ++p) std::cout
Constructors, Destructors, and Assignment Operators. Literature: Effective C++, Third Edition Chapter 2
 Constructors, Destructors, and Assignment Operators Literature: Effective C++, Third Edition Chapter 2 Overview Autogenerated Functions in Classes Prevent Autogeneration Explicitly Declare Destructors
Constructors, Destructors, and Assignment Operators Literature: Effective C++, Third Edition Chapter 2 Overview Autogenerated Functions in Classes Prevent Autogeneration Explicitly Declare Destructors
