Reverse Engineering For The Not So Backward
|
|
|
- Leo Gyles Webb
- 6 years ago
- Views:
Transcription
1 Reverse Engineering For The Not So Backward It is a Friday night and I am sitting home hyped up on caffeine and resting from a long work week. I like to relax on Friday nights and get stuff done, such as pay bills, do any side jobs that need to be done, and follow up on some of my independent research stuff. One of my interests (I have many) involves software reverse engineering. For years humans have been reverse engineering creations done by others to gain an insight on ones work or to build something of their own based around it, adding their own ideas and making it better, or worse. We reverse engineer things ranging from simple children s toys to the human species. Software is no different than anything else ever reverse engineered. Software made and distributed on a PC comes in executable form in a way that only machines can understand. Cryptic binary operations that have been converted from a high level language that a human used to make the program can only be understood by the machine. It is all a matter of procedure and a lot of it gets carried out within the extremely fast environment we call the CPU. Coders ranging from a solo programmer in his garage all the way to major corporations create software that will do what they specify it to do. Software that does not come with its original source, so called closed source, does not give the user the blueprints in how it was made and thought up. It is like looking at a car engine and not knowing how things work without some detailed engineering spec. Most closed source software is software that requires purchase and most likely contains many creative and intuitive functions to carry out what it does and how it is better than its competitors. Open source software is different in that the source code is given and the user is free to change anything they choose to, for the most part, make it better. It is closed source software that a reverse engineer is after and below I will attempt to explain the concepts use on a simple example. It is ok if you do not understand what is going on exactly, it is the concept that I am trying to get across. Reverse engineering, besides requiring a good programming background, requires a lot of time and patience to master. What is Reverse Engineering? In simplest terms, reverse engineering is the means by which closed source software in executable form can be examined at the machine code level for its overall functionality. This machine code, understood natively by the CPU, is very cryptic and has no defined method of abstraction. Different compilers and machines may produce and read machine code differently than the next, yet have the same functionality. Those reasons are why reverse engineering is so complex. Reverse engineering is used everywhere, from software companies trying to understand their competitors methods to hackers trying to find vulnerabilities. Reverse engineering can be for the good and the bad. Some things to know and gather before moving on First and foremost you do not need to be a computer scientist to read this. The point of this is all about the concept of the subject, which you should get by the end. You do not need to understand the code, but to just follow my methods on how things are done. If you are brave enough to do what I am doing on your own, feel free. Below are some of the requirements to get you started. For the rest of you, all you need is a working brain. -Microsoft C/C++ Linker and Compiler (CL.EXE): This tool is packaged with Visual Studio and can probably be found somewhere on Microsoft s website for free I am sure. It is responsible for turning the source code into the binary files that we will be reversing.
2 -Ollydbg This program is a Debugger and a Disassembler all in one. This program will be used to reverse engineer our binary file. Luckily this program is free for all and a simple Google search will guide you the way. -XVI32 Hex Editor This free Hex Editor we will use to make the final patches to our binary file and change it so that it does what we want it to do. Final Notes The program below is a proof of concept for this exercise and was created by me. It is a console win32 application, so there is no GUI, although it easily could have one. I find running things from the command prompt to be easier. If the correct password is entered then the windows Calculator should launch. If the wrong password is entered then an error is displayed and the program exits. If no password is entered an error is displayed and the program exits. Now these methods of password verification are very weak, yet to this day are still used by some large software programs. Most password verification programs contain more cryptic verifiers and pose a lot more challenge to a reverse engineer, but still can be done. That said, the below program is simple to reverse by today s standards, but a great place to start. Enjoy Let s get started already!!! This program takes in one argument as the password, in plain text. It compares the input, and if it equals the correct password, sets a flag. If the flag is set to signify a correct password the program proceeds. Our goal in this program is to modify the flag so ANY password will work. I give the source code below, but it is for show only. We will be working with the binary and pretending that the below source code was not at our disposal at time of reverse engineering. Source: #include <stdio.h> int main(int argc, char **argv) { int value = 0; if(argc < 2){ printf("no password entered..."); exit(0); } if (!(strcmp(argv[1], "password"))) { value = 1; } if(value == 1) { printf("congrats you got the password!!!"); system("start calc.exe"); } else{ printf("wrong password...you cannot proceed");} return 0; } Compiling the code: cl o main.c
3 Running binary with no password: Main.exe Output: No password entered Running binary with wrong password: Main.exe Output: Wrong password.you cannot proceed Running binary with correct password (password): Main.exe password Output: Congrats you got the password!!! Calculator runs Now let s pretend we didn t know the password and keep getting stuck with the error from method two above. Now it is time to have some fun!! Olly to the rescue!!! Here is the procedure: 1. Launch good ole Olly. 2. Go to file Open. Browse to where Main.exe is stored. Single click it. 3. Under Arguments put in the password of your choice. Anything you wish, and remember we do not know the real password so we are guessing. Soon it won t matter anyway :). 4. Olly shows a lot of stuff garbage to most.this is machine code. Sexy isn t it!! Scroll the big window in the center all the way to the top. Below is what you should see. It is so beautiful. Let me dump the whole program machine code out below for you, just in case you cannot see the above. It is important that we have this.
4 55 PUSH EBP 8BEC MOV EBP,ESP 51 PUSH ECX C745 FC >MOV DWORD PTR SS:[EBP-4],0 837D CMP DWORD PTR SS:[EBP+8],2 7D 17 JGE SHORT main E04000 PUSH main.0040e000 E CALL main c 6A 00 PUSH 0 E8 AB CALL main d E04000 PUSH main.0040e018 8B45 0C MOV EAX,DWORD PTR SS:[EBP+C] 8B48 04 MOV ECX,DWORD PTR DS:[EAX+4] 51 PUSH ECX E CALL main C4 08 ADD ESP,8 85C0 TEST EAX,EAX JNZ SHORT main C745 FC >MOV DWORD PTR SS:[EBP-4],1 837D FC 01 CMP DWORD PTR SS:[EBP-4],1 75 1C JNZ SHORT main E04000 PUSH main.0040e024 E CALL main c 68 48E04000 PUSH main.0040e048 E CALL main c EB 0D JMP SHORT main E04000 PUSH main.0040e058 E8 E CALL main c 33C0 XOR EAX,EAX 8BE5 MOV ESP,EBP 5D POP EBP C3 RETN The letters and numbers to the left side are called opcodes. Opcodes are the actual binary instructions, represented in HEX, that are extracted from the executable. If you viewed the executable in a HEX Viewer (as we will do later) you will see these opcodes. These are going to be important later. The opcodes are translated to assembly code, created from a compiler and more human readable than the binary, but not so much more. The stuff down the middle that kind of looks like English are the actual assembly instructions. We will be focusing on these instructions for now. Just so you know, the stuff I created above in source code is automatically generated to this when compiled (using cl). Now you see how hard reversing can be when there is no source code available. Before I go on I am going to remind you that I am not going to give a lesson on Assembly Language. You will have to bare with me and take my word for things if you do not fully understand. Read over again if you get lost. Do not let this stuff intimidate you too much. Let s look for some things that stand out. The nice thing about assembly is that some of the instructions actually look somewhat understandable. The CALL instruction calls internal and external functions. The JMP, JNZ,
5 JNE instructions jump over code on specific conditions that are determined before the instruction call, usually a couple bytes before hand. The CMP instruction does a comparison and sets a flag based on the comparison. A keen reverser will look for these kinds of instructions and proceed from there. Another thing a good reverser does is find variables used within the program. EBP is a register that seems to be storing variable data. As a matter of fact [EBP-4] (EBP offset -4) looks like it is storing something. By the looks of it the value 0 is being placed into [EBP-4], this signifies a common variable declaration situation. Most C languages do not like variables instantiated without being initialized, this one happens to be initialized to zero and I would guess it is an integer or a long of some kind. It is 4 bytes (hence the 4 offset value) so it is a word value, I would guess 32-bit unsigned integer. The next instruction you see a CMP on a value stored in [EBP+8]. I would guess this holds the argument input amount (ARGC), usually [EBP+8] holds that value. As you can see from analyzing the assembly, there is no place where the real password is stored. But in order for a comparison to be done it must be either in a register or on the stack, most likely the stack. Any PUSH instruction from memory could be this value as well as anything else, it is hard to tell. Could this be our password value? We are not going to search around and see, that takes the fun out of it. Plus if the value is encrypted or obfuscated it would be of no use anyway. Let us proceed. I am interested in that variable, the one at [EBP-4], it HAS to be used for something. But let us see what kind of CALL instructions we have first. I analyzed the last line to see what was being called. Simple analyses, or by just using Olly to find out for you, tells us that the function at is a strcmp function. Now this function, along with many others from the C/C++ standard library were imported during the linking stage of building the binary. The whole function is stored in our binary for faster and portable access. Their location is specified by a memory address within the binary, hence the CALL.main , this is merely saying call the function at that address. The strcmp function, by just googling (remember we do not have source) takes two arguments which happen to be strings that are compared. The first argument is already on the stack, and as I said above it is most likely the real password. The second argument comes from [EBP+C] and is moved into EAX. This value happens to be the password we send in (ARGV[]) and it is an array. [EAX+4] is the element of that array that contains our string, in C terms [EAX+4] is the same as ARGV[1], or 4 bytes from the start of the array. [EAX+4] is pushed onto the stack for strcpy to access. So to recap our EBP and EAX registers, here is what we know: [EBP-4] holds some weird integer variable, [EAX+4] holds our password we sent in, and [EBP+8] holds the total argument sent in the program, which in our case is always one when properly used. How things can unfold so quickly!!
6 After strcmp returns, the stack is flushed and EAX is zeroed out. The JNZ instruction jumps if the return value of strcmp was anything but zero (JNZ = Jump if Not Zero). If the value of the return function was zero it means that the two strings sent in were equal and that the password was correct. So let s ignore the JNZ instruction and proceed to the next couple lines to see what happens if both strings were equal (which in our case wouldn t have been the case because we had the wrong password). Look at that, our mystery variable at [EBP-4] pops up again. This time the variable is assigned a value of 1 instead of zero. Very interesting I must say. Below the assignment is another CMP and it looks like it is comparing the value of [EBP-4] to 1. Now if the flow went as expected with our bad password the value at [EBP-4] would still be 0 due to the jump over the assignment. The next compare jumps if the compare returns false, or any value other than zero. So let s not jump, let s proceed to the next couple instructions as if we had the right password and [EBP-4] was really set to 1. I see a PUSH and a CALL instruction. That means a function is being called. By further analysis the CALL to C happens to be a printf() instruction that takes one parameter, a string that outputs to the screen. And after that another CALL is done to C, and by analyzing that I find that is a System() call that takes one parameter, a string that represents a command. I would bet the command that runs is PUSHED at 0040E048, and that happens to be a string for the CALC.EXE program. Whoa, that is what is supposed to happen when the password is right!! Wow. We are not done yet because we need to make it run with our password. Let s do a simple thing with Olly first to really make sure that this variable is the only thing that needs to be changed. We are going to change the CMP instruction to compare the variable at [EBP-4] to zero instead of one, so that the program runs normally as if we had the correct password. A simple change in Olly can do that. Double click the instruction and let s change it!
7 Let s make one simple change to this: Now click Assemble and then click Cancel. Are you ready to see what happens? Click the blue play arrow at the top of Olly. If all goes well you should see the Calculator pop up. I did. We did it, we cracked it!!!! But the change in Olly is only temporary and the main executable is unchanged. We now need to patch the executable so that the change is permanent. Remember the opcodes stuff? Well let s go back to them and make some simple changes in the binary with a hex editor, in this case XVI32. Pay attention to the opcode value 837D FC 01, this is going to be changed in the executable. Now apply the change to the CMP instruction as done before. Do not run though when done. Let s see what we get now. Sweet, we see a change. Now we get the opcode 837D FC 00, with the last digit being the only change. We will use this to change our main binary. Fire up XVI32 and do the following. Make sure Olly is closed now so that the binary can be read and written to. 1. Go to File->Open and browse to where the Main.exe file is located. Double Click it. 2. We are now in hex view. Make sure you are in edit mode, by going to Tools and making sure Overwrite is checked. Here is what we got. All the ugly opcode values and their ASCII equivalents. By the way, opcodes are HEX!!
8 Let s do this patch and get this over with already. Go to Search->Find. Make sure the Hex String bubble is checked. In the box type in, without the quotes, 837DFC01, hit Ok. You will go to an area where this opcode exists. Now the simple part - Move over 4 places with the right arrow so that the 01 block is highlighted, click once inside of the highlighted block so that the background of all the opcodes turns white. Type in 00. Now go to File->Save and close XVI32. Now let s go to the command prompt and see what happens. Running the binary with no password: Main.exe Output: No password entered Running the binary with wrong password: Main.exe p@ssw0rd Output: Congrats you got the password!!! Calculator runs Don t believe me, see for yourself with a few trial runs:
9 Sweet. I love this stuff. So there you have it. We successfully reversed a program. All it took was a few hours and one, ONE simple hex change and we cracked this program. If they were all that easy! As you can see this stuff takes patience and experience. The benefits are very good when it is mastered. I hope most of you got the concept through, enough to make me happy since I spent a few hours on this exercise, make me feel good some how. Haha. By all means try it out. I will give you the.exe file and you can go at it and screw around, it is really fun. Thanks for reading and stay tuned for more exciting articles by the one and only DJT3K Copyright 2006 T3K. Skill comes with those that work hard.
Practical Malware Analysis
 Practical Malware Analysis Ch 4: A Crash Course in x86 Disassembly Revised 1-16-7 Basic Techniques Basic static analysis Looks at malware from the outside Basic dynamic analysis Only shows you how the
Practical Malware Analysis Ch 4: A Crash Course in x86 Disassembly Revised 1-16-7 Basic Techniques Basic static analysis Looks at malware from the outside Basic dynamic analysis Only shows you how the
Rev101. spritzers - CTF team. spritz.math.unipd.it/spritzers.html
 Rev101 spritzers - CTF team spritz.math.unipd.it/spritzers.html Disclaimer All information presented here has the only purpose of teaching how reverse engineering works. Use your mad skillz only in CTFs
Rev101 spritzers - CTF team spritz.math.unipd.it/spritzers.html Disclaimer All information presented here has the only purpose of teaching how reverse engineering works. Use your mad skillz only in CTFs
INSIDE THE ULTIMA ONLINE CLIENT - INSERTING A SLEEP
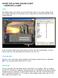 INSIDE THE ULTIMA ONLINE CLIENT - INSERTING A SLEEP GOAL The Ultima Online client utilizes too much CPU power when it s not doing anything useful. For example, when we are at the logon screen or when we
INSIDE THE ULTIMA ONLINE CLIENT - INSERTING A SLEEP GOAL The Ultima Online client utilizes too much CPU power when it s not doing anything useful. For example, when we are at the logon screen or when we
Subprograms: Arguments
 Subprograms: Arguments ICS312 Machine-Level and Systems Programming Henri Casanova (henric@hawaii.edu) Activation Records The stack is useful to store and rieve urn addresses, transparently managed via
Subprograms: Arguments ICS312 Machine-Level and Systems Programming Henri Casanova (henric@hawaii.edu) Activation Records The stack is useful to store and rieve urn addresses, transparently managed via
Program Exploitation Intro
 Program Exploitation Intro x86 Assembly 04//2018 Security 1 Univeristà Ca Foscari, Venezia What is Program Exploitation "Making a program do something unexpected and not planned" The right bugs can be
Program Exploitation Intro x86 Assembly 04//2018 Security 1 Univeristà Ca Foscari, Venezia What is Program Exploitation "Making a program do something unexpected and not planned" The right bugs can be
LdPinch Report. Feng Zhu Jinpeng Wei
 LdPinch Report Feng Zhu (fzhu001@fiu.edu), Jinpeng Wei (weijp@cs.fiu.edu) 1 Malware General Information Malware Name: LdPinch (named by ThreatExpert) File size: 641,536 bytes File type: PE32 executable
LdPinch Report Feng Zhu (fzhu001@fiu.edu), Jinpeng Wei (weijp@cs.fiu.edu) 1 Malware General Information Malware Name: LdPinch (named by ThreatExpert) File size: 641,536 bytes File type: PE32 executable
CVE EXPLOIT USING 108 BYTES AND DOWNLOADING A FILE WITH YOUR UNLIMITED CODE BY VALTHEK
 CVE-2017-11882 EXPLOIT USING 108 BYTES AND DOWNLOADING A FILE WITH YOUR UNLIMITED CODE BY VALTHEK First words of thank to Embedy Company to discover the initial exploit and POC of 44 bytes máximum, Ridter
CVE-2017-11882 EXPLOIT USING 108 BYTES AND DOWNLOADING A FILE WITH YOUR UNLIMITED CODE BY VALTHEK First words of thank to Embedy Company to discover the initial exploit and POC of 44 bytes máximum, Ridter
Reverse Engineering Low Level Software. CS5375 Software Reverse Engineering Dr. Jaime C. Acosta
 1 Reverse Engineering Low Level Software CS5375 Software Reverse Engineering Dr. Jaime C. Acosta Machine code 2 3 Machine code Assembly compile Machine Code disassemble 4 Machine code Assembly compile
1 Reverse Engineering Low Level Software CS5375 Software Reverse Engineering Dr. Jaime C. Acosta Machine code 2 3 Machine code Assembly compile Machine Code disassemble 4 Machine code Assembly compile
Recitation: Bomb Lab. September 17 th 2018
 15-213 Recitation: Bomb Lab September 17 th 2018 Agenda Logistics - Bomb Lab Overview - Introduction to GDB - GDB and Assembly Tips What is Bomb Lab? An exercise in reading x86-64 assembly code. A chance
15-213 Recitation: Bomb Lab September 17 th 2018 Agenda Logistics - Bomb Lab Overview - Introduction to GDB - GDB and Assembly Tips What is Bomb Lab? An exercise in reading x86-64 assembly code. A chance
Mitchell Adair January, 2014
 Mitchell Adair January, 2014 Know Owen from our time at Sandia National Labs Currently work for Raytheon Founded UTDallas s Computer Security Group (CSG) in Spring 2010 Reversing, binary auditing, fuzzing,
Mitchell Adair January, 2014 Know Owen from our time at Sandia National Labs Currently work for Raytheon Founded UTDallas s Computer Security Group (CSG) in Spring 2010 Reversing, binary auditing, fuzzing,
Advanced Buffer Overflow
 Pattern Recognition and Applications Lab Advanced Buffer Overflow Ing. Davide Maiorca, Ph.D. davide.maiorca@diee.unica.it Computer Security A.Y. 2016/2017 Department of Electrical and Electronic Engineering
Pattern Recognition and Applications Lab Advanced Buffer Overflow Ing. Davide Maiorca, Ph.D. davide.maiorca@diee.unica.it Computer Security A.Y. 2016/2017 Department of Electrical and Electronic Engineering
Overview of Compiler. A. Introduction
 CMPSC 470 Lecture 01 Topics: Overview of compiler Compiling process Structure of compiler Programming language basics Overview of Compiler A. Introduction What is compiler? What is interpreter? A very
CMPSC 470 Lecture 01 Topics: Overview of compiler Compiling process Structure of compiler Programming language basics Overview of Compiler A. Introduction What is compiler? What is interpreter? A very
WIBU protection knuth20 implementation analysis
 WIBU protection knuth20 implementation analysis by anonymous 15.09.2006. Intro Couple of weeks ago, I faced WIBU dongle protection. Before that, I had no expirience with it. The first thing I've checked
WIBU protection knuth20 implementation analysis by anonymous 15.09.2006. Intro Couple of weeks ago, I faced WIBU dongle protection. Before that, I had no expirience with it. The first thing I've checked
CSC 2400: Computer Systems. Towards the Hardware: Machine-Level Representation of Programs
 CSC 2400: Computer Systems Towards the Hardware: Machine-Level Representation of Programs Towards the Hardware High-level language (Java) High-level language (C) assembly language machine language (IA-32)
CSC 2400: Computer Systems Towards the Hardware: Machine-Level Representation of Programs Towards the Hardware High-level language (Java) High-level language (C) assembly language machine language (IA-32)
Intro to x86 Binaries. From ASM to exploit
 Intro to x86 Binaries From ASM to exploit Intro to x86 Binaries I lied lets do a quick ctf team thing Organization Ideas? Do we need to a real structure right now? Mailing list is OTW How do we get more
Intro to x86 Binaries From ASM to exploit Intro to x86 Binaries I lied lets do a quick ctf team thing Organization Ideas? Do we need to a real structure right now? Mailing list is OTW How do we get more
SIMPLE PROGRAMMING. The 10 Minute Guide to Bitwise Operators
 Simple Programming SIMPLE PROGRAMMING The 10 Minute Guide to Bitwise Operators (Cause you've got 10 minutes until your interview starts and you know you should probably know this, right?) Twitter: Web:
Simple Programming SIMPLE PROGRAMMING The 10 Minute Guide to Bitwise Operators (Cause you've got 10 minutes until your interview starts and you know you should probably know this, right?) Twitter: Web:
An Introduction to IDA and crackmes - Cruehead[MiB] crackme 2 writeup Mitchell Adair 08/14/2011 utdcsg.org
![An Introduction to IDA and crackmes - Cruehead[MiB] crackme 2 writeup Mitchell Adair 08/14/2011 utdcsg.org An Introduction to IDA and crackmes - Cruehead[MiB] crackme 2 writeup Mitchell Adair 08/14/2011 utdcsg.org](/thumbs/72/66601522.jpg) An Introduction to IDA and crackmes - Cruehead[MiB] crackme 2 writeup Mitchell Adair 08/14/2011 utdcsg.org This is a writeup over Cruehead's crackme 2, hopefully providing an intro to IDA and some general
An Introduction to IDA and crackmes - Cruehead[MiB] crackme 2 writeup Mitchell Adair 08/14/2011 utdcsg.org This is a writeup over Cruehead's crackme 2, hopefully providing an intro to IDA and some general
buffer overflow exploitation
 buffer overflow exploitation Samuele Andreoli, Nicolò Fornari, Giuseppe Vitto May 11, 2016 University of Trento Introduction 1 introduction A Buffer Overflow is an anomaly where a program, while writing
buffer overflow exploitation Samuele Andreoli, Nicolò Fornari, Giuseppe Vitto May 11, 2016 University of Trento Introduction 1 introduction A Buffer Overflow is an anomaly where a program, while writing
1.7 Limit of a Function
 1.7 Limit of a Function We will discuss the following in this section: 1. Limit Notation 2. Finding a it numerically 3. Right and Left Hand Limits 4. Infinite Limits Consider the following graph Notation:
1.7 Limit of a Function We will discuss the following in this section: 1. Limit Notation 2. Finding a it numerically 3. Right and Left Hand Limits 4. Infinite Limits Consider the following graph Notation:
CNIT 127: Exploit Development. Ch 1: Before you begin. Updated
 CNIT 127: Exploit Development Ch 1: Before you begin Updated 1-14-16 Basic Concepts Vulnerability A flaw in a system that allows an attacker to do something the designer did not intend, such as Denial
CNIT 127: Exploit Development Ch 1: Before you begin Updated 1-14-16 Basic Concepts Vulnerability A flaw in a system that allows an attacker to do something the designer did not intend, such as Denial
MITOCW watch?v=0jljzrnhwoi
 MITOCW watch?v=0jljzrnhwoi The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=0jljzrnhwoi The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
4. Jump to *RA 4. StackGuard 5. Execute code 5. Instruction Set Randomization 6. Make system call 6. System call Randomization
 04/04/06 Lecture Notes Untrusted Beili Wang Stages of Static Overflow Solution 1. Find bug in 1. Static Analysis 2. Send overflowing input 2. CCured 3. Overwrite return address 3. Address Space Randomization
04/04/06 Lecture Notes Untrusted Beili Wang Stages of Static Overflow Solution 1. Find bug in 1. Static Analysis 2. Send overflowing input 2. CCured 3. Overwrite return address 3. Address Space Randomization
Buffer-Overflow Attacks on the Stack
 Computer Systems Buffer-Overflow Attacks on the Stack Introduction A buffer overflow occurs when a program, while writing data to a buffer, overruns the buffer's boundary and overwrites memory in adjacent
Computer Systems Buffer-Overflow Attacks on the Stack Introduction A buffer overflow occurs when a program, while writing data to a buffer, overruns the buffer's boundary and overwrites memory in adjacent
Writing Code and Programming Microcontrollers
 Writing Code and Programming Microcontrollers This document shows how to develop and program software into microcontrollers. It uses the example of an Atmel ATmega32U2 device and free software. The ATmega32U2
Writing Code and Programming Microcontrollers This document shows how to develop and program software into microcontrollers. It uses the example of an Atmel ATmega32U2 device and free software. The ATmega32U2
A practicalintroduction to embedded programming. Brian Plancher 10/17/2018
 A practicalintroduction to embedded programming Brian Plancher Brian_Plancher@g.harvard.edu 10/17/2018 This week s task is simple: 1. Since the boards you made 2 weeks ago are perfect and are still in
A practicalintroduction to embedded programming Brian Plancher Brian_Plancher@g.harvard.edu 10/17/2018 This week s task is simple: 1. Since the boards you made 2 weeks ago are perfect and are still in
How to approach a computational problem
 How to approach a computational problem A lot of people find computer programming difficult, especially when they first get started with it. Sometimes the problems are problems specifically related to
How to approach a computational problem A lot of people find computer programming difficult, especially when they first get started with it. Sometimes the problems are problems specifically related to
CSC 8400: Computer Systems. Machine-Level Representation of Programs
 CSC 8400: Computer Systems Machine-Level Representation of Programs Towards the Hardware High-level language (Java) High-level language (C) assembly language machine language (IA-32) 1 Compilation Stages
CSC 8400: Computer Systems Machine-Level Representation of Programs Towards the Hardware High-level language (Java) High-level language (C) assembly language machine language (IA-32) 1 Compilation Stages
Lab 3. The Art of Assembly Language (II)
 Lab. The Art of Assembly Language (II) Dan Bruce, David Clark and Héctor D. Menéndez Department of Computer Science University College London October 2, 2017 License Creative Commons Share Alike Modified
Lab. The Art of Assembly Language (II) Dan Bruce, David Clark and Héctor D. Menéndez Department of Computer Science University College London October 2, 2017 License Creative Commons Share Alike Modified
What the CPU Sees Basic Flow Control Conditional Flow Control Structured Flow Control Functions and Scope. C Flow Control.
 C Flow Control David Chisnall February 1, 2011 Outline What the CPU Sees Basic Flow Control Conditional Flow Control Structured Flow Control Functions and Scope Disclaimer! These slides contain a lot of
C Flow Control David Chisnall February 1, 2011 Outline What the CPU Sees Basic Flow Control Conditional Flow Control Structured Flow Control Functions and Scope Disclaimer! These slides contain a lot of
2SKILL. Variables Lesson 6. Remembering numbers (and other stuff)...
 Remembering numbers (and other stuff)... Let s talk about one of the most important things in any programming language. It s called a variable. Don t let the name scare you. What it does is really simple.
Remembering numbers (and other stuff)... Let s talk about one of the most important things in any programming language. It s called a variable. Don t let the name scare you. What it does is really simple.
Reversing Basics A Practical Approach
 Reversing Basics A Practical Approach Author: Amit Malik (DouBle_Zer0) E-Mail: m.amit30@gmail.com Note: Keep Out of Reach of Children/Danger-Software Poison. Download EXE/Crackme: https://sites.google.com/site/hacking1now/crackmes
Reversing Basics A Practical Approach Author: Amit Malik (DouBle_Zer0) E-Mail: m.amit30@gmail.com Note: Keep Out of Reach of Children/Danger-Software Poison. Download EXE/Crackme: https://sites.google.com/site/hacking1now/crackmes
COPYRIGHTED MATERIAL. Starting Strong with Visual C# 2005 Express Edition
 1 Starting Strong with Visual C# 2005 Express Edition Okay, so the title of this chapter may be a little over the top. But to be honest, the Visual C# 2005 Express Edition, from now on referred to as C#
1 Starting Strong with Visual C# 2005 Express Edition Okay, so the title of this chapter may be a little over the top. But to be honest, the Visual C# 2005 Express Edition, from now on referred to as C#
Towards the Hardware"
 CSC 2400: Computer Systems Towards the Hardware Chapter 2 Towards the Hardware High-level language (Java) High-level language (C) assembly language machine language (IA-32) 1 High-Level Language Make programming
CSC 2400: Computer Systems Towards the Hardware Chapter 2 Towards the Hardware High-level language (Java) High-level language (C) assembly language machine language (IA-32) 1 High-Level Language Make programming
The name of our class will be Yo. Type that in where it says Class Name. Don t hit the OK button yet.
 Mr G s Java Jive #2: Yo! Our First Program With this handout you ll write your first program, which we ll call Yo. Programs, Classes, and Objects, Oh My! People regularly refer to Java as a language that
Mr G s Java Jive #2: Yo! Our First Program With this handout you ll write your first program, which we ll call Yo. Programs, Classes, and Objects, Oh My! People regularly refer to Java as a language that
Low-Level Essentials for Understanding Security Problems Aurélien Francillon
 Low-Level Essentials for Understanding Security Problems Aurélien Francillon francill@eurecom.fr Computer Architecture The modern computer architecture is based on Von Neumann Two main parts: CPU (Central
Low-Level Essentials for Understanding Security Problems Aurélien Francillon francill@eurecom.fr Computer Architecture The modern computer architecture is based on Von Neumann Two main parts: CPU (Central
EECE.3170: Microprocessor Systems Design I Summer 2017 Homework 4 Solution
 1. (40 points) Write the following subroutine in x86 assembly: Recall that: int f(int v1, int v2, int v3) { int x = v1 + v2; urn (x + v3) * (x v3); Subroutine arguments are passed on the stack, and can
1. (40 points) Write the following subroutine in x86 assembly: Recall that: int f(int v1, int v2, int v3) { int x = v1 + v2; urn (x + v3) * (x v3); Subroutine arguments are passed on the stack, and can
These are notes for the third lecture; if statements and loops.
 These are notes for the third lecture; if statements and loops. 1 Yeah, this is going to be the second slide in a lot of lectures. 2 - Dominant language for desktop application development - Most modern
These are notes for the third lecture; if statements and loops. 1 Yeah, this is going to be the second slide in a lot of lectures. 2 - Dominant language for desktop application development - Most modern
CS61 Section Solutions 3
 CS61 Section Solutions 3 (Week of 10/1-10/5) 1. Assembly Operand Specifiers 2. Condition Codes 3. Jumps 4. Control Flow Loops 5. Procedure Calls 1. Assembly Operand Specifiers Q1 Operand Value %eax 0x104
CS61 Section Solutions 3 (Week of 10/1-10/5) 1. Assembly Operand Specifiers 2. Condition Codes 3. Jumps 4. Control Flow Loops 5. Procedure Calls 1. Assembly Operand Specifiers Q1 Operand Value %eax 0x104
T Hands-on 2. User-mode debuggers OllyDbg
 T-110.6220 Hands-on 2 User-mode debuggers OllyDbg Disassemblers vs debuggers Static analysis / Disassemblers Theoretic approach Give us a static view of the binary Example: IDA Dynamic analysis / Debuggers
T-110.6220 Hands-on 2 User-mode debuggers OllyDbg Disassemblers vs debuggers Static analysis / Disassemblers Theoretic approach Give us a static view of the binary Example: IDA Dynamic analysis / Debuggers
Buffer Overflows Defending against arbitrary code insertion and execution
 www.harmonysecurity.com info@harmonysecurity.com Buffer Overflows Defending against arbitrary code insertion and execution By Stephen Fewer Contents 1 Introduction 2 1.1 Where does the problem lie? 2 1.1.1
www.harmonysecurity.com info@harmonysecurity.com Buffer Overflows Defending against arbitrary code insertion and execution By Stephen Fewer Contents 1 Introduction 2 1.1 Where does the problem lie? 2 1.1.1
C Pointers 2013 Author Riko H i
 http:/cdorm.net/understanding C Pointers 2013 Author Riko H i Copyright 2013 CDorm.net All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form
http:/cdorm.net/understanding C Pointers 2013 Author Riko H i Copyright 2013 CDorm.net All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form
Chapter 7: User Defined Functions and Stack Mechanics
 Chapter 7: User Defined Functions and Stack Mechanics Objectives: (a) Demonstrate the ability to analyze simple programs that use library and user defined functions. (b) Describe the organization and contents
Chapter 7: User Defined Functions and Stack Mechanics Objectives: (a) Demonstrate the ability to analyze simple programs that use library and user defined functions. (b) Describe the organization and contents
Hello World! Computer Programming for Kids and Other Beginners. Chapter 1. by Warren Sande and Carter Sande. Copyright 2009 Manning Publications
 Hello World! Computer Programming for Kids and Other Beginners by Warren Sande and Carter Sande Chapter 1 Copyright 2009 Manning Publications brief contents Preface xiii Acknowledgments xix About this
Hello World! Computer Programming for Kids and Other Beginners by Warren Sande and Carter Sande Chapter 1 Copyright 2009 Manning Publications brief contents Preface xiii Acknowledgments xix About this
Advanced Buffer Overflow
 Pattern Recognition and Applications Lab Advanced Buffer Overflow Ing. Davide Maiorca, Ph.D. davide.maiorca@diee.unica.it Computer Security A.Y. 2017/2018 Department of Electrical and Electronic Engineering
Pattern Recognition and Applications Lab Advanced Buffer Overflow Ing. Davide Maiorca, Ph.D. davide.maiorca@diee.unica.it Computer Security A.Y. 2017/2018 Department of Electrical and Electronic Engineering
Getting Started. Excerpted from Hello World! Computer Programming for Kids and Other Beginners
 Getting Started Excerpted from Hello World! Computer Programming for Kids and Other Beginners EARLY ACCESS EDITION Warren D. Sande and Carter Sande MEAP Release: May 2008 Softbound print: November 2008
Getting Started Excerpted from Hello World! Computer Programming for Kids and Other Beginners EARLY ACCESS EDITION Warren D. Sande and Carter Sande MEAP Release: May 2008 Softbound print: November 2008
Intro to Cracking and Unpacking. Nathan Rittenhouse
 Intro to Cracking and Unpacking Nathan Rittenhouse nathan_@mit.edu Keygenning Take this crackme: http://crackmes.de/users/moofy/crackme_2 Write a key generator Process Watch where user data is inputted
Intro to Cracking and Unpacking Nathan Rittenhouse nathan_@mit.edu Keygenning Take this crackme: http://crackmes.de/users/moofy/crackme_2 Write a key generator Process Watch where user data is inputted
XP: Backup Your Important Files for Safety
 XP: Backup Your Important Files for Safety X 380 / 1 Protect Your Personal Files Against Accidental Loss with XP s Backup Wizard Your computer contains a great many important files, but when it comes to
XP: Backup Your Important Files for Safety X 380 / 1 Protect Your Personal Files Against Accidental Loss with XP s Backup Wizard Your computer contains a great many important files, but when it comes to
Lecture 03 Bits, Bytes and Data Types
 Lecture 03 Bits, Bytes and Data Types Computer Languages A computer language is a language that is used to communicate with a machine. Like all languages, computer languages have syntax (form) and semantics
Lecture 03 Bits, Bytes and Data Types Computer Languages A computer language is a language that is used to communicate with a machine. Like all languages, computer languages have syntax (form) and semantics
CPS104 Recitation: Assembly Programming
 CPS104 Recitation: Assembly Programming Alexandru Duțu 1 Facts OS kernel and embedded software engineers use assembly for some parts of their code some OSes had their entire GUIs written in assembly in
CPS104 Recitation: Assembly Programming Alexandru Duțu 1 Facts OS kernel and embedded software engineers use assembly for some parts of their code some OSes had their entire GUIs written in assembly in
Autodesk AutoCAD DWG-AC1021 Heap Corruption
 security research Autodesk AutoCAD DWG-AC1021 Heap Corruption Mar 2013 AutoCAD is a software for computer-aided design (CAD) and technical drawing in 2D/3D, being one of the worlds leading CAD design tools.
security research Autodesk AutoCAD DWG-AC1021 Heap Corruption Mar 2013 AutoCAD is a software for computer-aided design (CAD) and technical drawing in 2D/3D, being one of the worlds leading CAD design tools.
int n = 10; int sum = 10; while (n > 1) { sum = sum + n; n--; } cout << "The sum of the integers 1 to 10 is " << sum << endl;
 Debugging Some have said that any monkey can write a program the hard part is debugging it. While this is somewhat oversimplifying the difficult process of writing a program, it is sometimes more time
Debugging Some have said that any monkey can write a program the hard part is debugging it. While this is somewhat oversimplifying the difficult process of writing a program, it is sometimes more time
CSE 351. GDB Introduction
 CSE 351 GDB Introduction Lab 2 Out either tonight or tomorrow Due April 27 th (you have ~12 days) Reading and understanding x86_64 assembly Debugging and disassembling programs Today: General debugging
CSE 351 GDB Introduction Lab 2 Out either tonight or tomorrow Due April 27 th (you have ~12 days) Reading and understanding x86_64 assembly Debugging and disassembling programs Today: General debugging
CSE P 501 Compilers. x86 Lite for Compiler Writers Hal Perkins Autumn /25/ Hal Perkins & UW CSE J-1
 CSE P 501 Compilers x86 Lite for Compiler Writers Hal Perkins Autumn 2011 10/25/2011 2002-11 Hal Perkins & UW CSE J-1 Agenda Learn/review x86 architecture Core 32-bit part only for now Ignore crufty, backward-compatible
CSE P 501 Compilers x86 Lite for Compiler Writers Hal Perkins Autumn 2011 10/25/2011 2002-11 Hal Perkins & UW CSE J-1 Agenda Learn/review x86 architecture Core 32-bit part only for now Ignore crufty, backward-compatible
Stack -- Memory which holds register contents. Will keep the EIP of the next address after the call
 Call without Parameter Value Transfer What are involved? ESP Stack Pointer Register Grows by 4 for EIP (return address) storage Stack -- Memory which holds register contents Will keep the EIP of the next
Call without Parameter Value Transfer What are involved? ESP Stack Pointer Register Grows by 4 for EIP (return address) storage Stack -- Memory which holds register contents Will keep the EIP of the next
Lecture Notes for 04/04/06: UNTRUSTED CODE Fatima Zarinni.
 Lecture Notes for 04/04/06 UNTRUSTED CODE Fatima Zarinni. Last class we started to talk about the different System Solutions for Stack Overflow. We are going to continue the subject. Stages of Stack Overflow
Lecture Notes for 04/04/06 UNTRUSTED CODE Fatima Zarinni. Last class we started to talk about the different System Solutions for Stack Overflow. We are going to continue the subject. Stages of Stack Overflow
Welcome to Lab! Feel free to get started until we start talking! The lab document is located on the course website:
 Welcome to Lab! Feel free to get started until we start talking! The lab document is located on the course website: https://users.wpi.edu/~sjarvis/ece2049_smj/ece2049_labs.html You do not need to keep
Welcome to Lab! Feel free to get started until we start talking! The lab document is located on the course website: https://users.wpi.edu/~sjarvis/ece2049_smj/ece2049_labs.html You do not need to keep
CSCI 2021: Introduction
 CSCI 2021: Introduction Chris Kauffman Last Updated: Fri Jan 25 12:57:44 CST 2019 1 CSCI 2021 - Logistics Reading Bryant/O Hallaron: Ch 1 C references: basic syntax, types, compilation Goals Basic Model
CSCI 2021: Introduction Chris Kauffman Last Updated: Fri Jan 25 12:57:44 CST 2019 1 CSCI 2021 - Logistics Reading Bryant/O Hallaron: Ch 1 C references: basic syntax, types, compilation Goals Basic Model
CSE 361S Intro to Systems Software Lab Assignment #4
 Due: Thursday, October 23, 2008. CSE 361S Intro to Systems Software Lab Assignment #4 In this lab, you will mount a buffer overflow attack on your own program. As stated in class, we do not condone using
Due: Thursday, October 23, 2008. CSE 361S Intro to Systems Software Lab Assignment #4 In this lab, you will mount a buffer overflow attack on your own program. As stated in class, we do not condone using
Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur
 Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur Lecture 18 Switch Statement (Contd.) And Introduction to
Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur Lecture 18 Switch Statement (Contd.) And Introduction to
X86 Addressing Modes Chapter 3" Review: Instructions to Recognize"
 X86 Addressing Modes Chapter 3" Review: Instructions to Recognize" 1 Arithmetic Instructions (1)! Two Operand Instructions" ADD Dest, Src Dest = Dest + Src SUB Dest, Src Dest = Dest - Src MUL Dest, Src
X86 Addressing Modes Chapter 3" Review: Instructions to Recognize" 1 Arithmetic Instructions (1)! Two Operand Instructions" ADD Dest, Src Dest = Dest + Src SUB Dest, Src Dest = Dest - Src MUL Dest, Src
CS 103 Lab - Party Like A Char Star
 1 Introduction In this lab you will implement a "hangman" game where the user is shown blanks representing letter of a word and then tries to guess and fill in the letters with a limited number of guesses.
1 Introduction In this lab you will implement a "hangman" game where the user is shown blanks representing letter of a word and then tries to guess and fill in the letters with a limited number of guesses.
Chapter 1 Introduction
 Chapter 1 Introduction Why I Am Writing This: Why I am I writing a set of tutorials on compilers and how to build them? Well, the idea goes back several years ago when Rapid-Q, one of the best free BASIC
Chapter 1 Introduction Why I Am Writing This: Why I am I writing a set of tutorials on compilers and how to build them? Well, the idea goes back several years ago when Rapid-Q, one of the best free BASIC
War Industries Presents: An Introduction to Programming for Hackers Part III - Advanced Variables & Flow Control.
 War Industries Presents: An Introduction to Programming for Hackers Part III - Advanced Variables & Flow Control By Lovepump, 2004 Visit: www.warindustries.com Part II Programs 101 Goals: At the end of
War Industries Presents: An Introduction to Programming for Hackers Part III - Advanced Variables & Flow Control By Lovepump, 2004 Visit: www.warindustries.com Part II Programs 101 Goals: At the end of
administrivia today start assembly probably won t finish all these slides Assignment 4 due tomorrow any questions?
 administrivia today start assembly probably won t finish all these slides Assignment 4 due tomorrow any questions? exam on Wednesday today s material not on the exam 1 Assembly Assembly is programming
administrivia today start assembly probably won t finish all these slides Assignment 4 due tomorrow any questions? exam on Wednesday today s material not on the exam 1 Assembly Assembly is programming
CSCI 334: Principles of Programming Languages. Computer Architecture (a really really fast introduction) Lecture 11: Control Structures II
 1 byte{ 1 byte{ CSCI 334: Principles of Programming Languages Lecture 11: Control Structures II Computer Architecture (a really really fast introduction) Instructor: Dan Barowy Memory Instructions main
1 byte{ 1 byte{ CSCI 334: Principles of Programming Languages Lecture 11: Control Structures II Computer Architecture (a really really fast introduction) Instructor: Dan Barowy Memory Instructions main
CS354 gdb Tutorial Written by Chris Feilbach
 CS354 gdb Tutorial Written by Chris Feilbach Purpose This tutorial aims to show you the basics of using gdb to debug C programs. gdb is the GNU debugger, and is provided on systems that
CS354 gdb Tutorial Written by Chris Feilbach Purpose This tutorial aims to show you the basics of using gdb to debug C programs. gdb is the GNU debugger, and is provided on systems that
Computer Architecture and Assembly Language. Practical Session 3
 Computer Architecture and Assembly Language Practical Session 3 Advanced Instructions division DIV r/m - unsigned integer division IDIV r/m - signed integer division Dividend Divisor Quotient Remainder
Computer Architecture and Assembly Language Practical Session 3 Advanced Instructions division DIV r/m - unsigned integer division IDIV r/m - signed integer division Dividend Divisor Quotient Remainder
T Jarkko Turkulainen, F-Secure Corporation
 T-110.6220 2010 Emulators and disassemblers Jarkko Turkulainen, F-Secure Corporation Agenda Disassemblers What is disassembly? What makes up an instruction? How disassemblers work Use of disassembly In
T-110.6220 2010 Emulators and disassemblers Jarkko Turkulainen, F-Secure Corporation Agenda Disassemblers What is disassembly? What makes up an instruction? How disassemblers work Use of disassembly In
Without further ado, let s go over and have a look at what I ve come up with.
 JIRA Integration Transcript VLL Hi, my name is Jonathan Wilson and I m the service management practitioner with NHS Digital based in the United Kingdom. NHS Digital is the provider of services to the National
JIRA Integration Transcript VLL Hi, my name is Jonathan Wilson and I m the service management practitioner with NHS Digital based in the United Kingdom. NHS Digital is the provider of services to the National
United States Naval Academy Electrical and Computer Engineering Department EC310-6 Week Midterm Spring 2015
 United States Naval Academy Electrical and Computer Engineering Department EC310-6 Week Midterm Spring 2015 1. Do a page check: you should have 8 pages including this cover sheet. 2. You have 50 minutes
United States Naval Academy Electrical and Computer Engineering Department EC310-6 Week Midterm Spring 2015 1. Do a page check: you should have 8 pages including this cover sheet. 2. You have 50 minutes
Objectives. ICT106 Fundamentals of Computer Systems Topic 8. Procedures, Calling and Exit conventions, Run-time Stack Ref: Irvine, Ch 5 & 8
 Objectives ICT106 Fundamentals of Computer Systems Topic 8 Procedures, Calling and Exit conventions, Run-time Stack Ref: Irvine, Ch 5 & 8 To understand how HLL procedures/functions are actually implemented
Objectives ICT106 Fundamentals of Computer Systems Topic 8 Procedures, Calling and Exit conventions, Run-time Stack Ref: Irvine, Ch 5 & 8 To understand how HLL procedures/functions are actually implemented
Week 5, continued. This is CS50. Harvard University. Fall Cheng Gong
 This is CS50. Harvard University. Fall 2014. Cheng Gong Table of Contents News... 1 Buffer Overflow... 1 Malloc... 6 Linked Lists... 7 Searching... 13 Inserting... 16 Removing... 19 News Good news everyone!
This is CS50. Harvard University. Fall 2014. Cheng Gong Table of Contents News... 1 Buffer Overflow... 1 Malloc... 6 Linked Lists... 7 Searching... 13 Inserting... 16 Removing... 19 News Good news everyone!
Lesson 1. Introduction to Programming OBJECTIVES
 Introduction to Programming If you re new to programming, you might be intimidated by code and flowcharts. You might even wonder how you ll ever understand them. This lesson offers some basic ideas and
Introduction to Programming If you re new to programming, you might be intimidated by code and flowcharts. You might even wonder how you ll ever understand them. This lesson offers some basic ideas and
Clickbank Domination Presents. A case study by Devin Zander. A look into how absolutely easy internet marketing is. Money Mindset Page 1
 Presents A case study by Devin Zander A look into how absolutely easy internet marketing is. Money Mindset Page 1 Hey guys! Quick into I m Devin Zander and today I ve got something everybody loves! Me
Presents A case study by Devin Zander A look into how absolutely easy internet marketing is. Money Mindset Page 1 Hey guys! Quick into I m Devin Zander and today I ve got something everybody loves! Me
Computer Systems Lecture 9
 Computer Systems Lecture 9 CPU Registers in x86 CPU status flags EFLAG: The Flag register holds the CPU status flags The status flags are separate bits in EFLAG where information on important conditions
Computer Systems Lecture 9 CPU Registers in x86 CPU status flags EFLAG: The Flag register holds the CPU status flags The status flags are separate bits in EFLAG where information on important conditions
Yup, left blank on purpose. You can use it to draw whatever you want :-)
 Yup, left blank on purpose. You can use it to draw whatever you want :-) Chapter 1 The task I have assigned myself is not an easy one; teach C.O.F.F.E.E. Not the beverage of course, but the scripting language
Yup, left blank on purpose. You can use it to draw whatever you want :-) Chapter 1 The task I have assigned myself is not an easy one; teach C.O.F.F.E.E. Not the beverage of course, but the scripting language
Data Exfiltration Techniques
 Data Exfiltration Techniques Introduction In this article we will see how malware encode or encrypt data that s exfiltrated to the Command and Control Server from infected machines. This is often done
Data Exfiltration Techniques Introduction In this article we will see how malware encode or encrypt data that s exfiltrated to the Command and Control Server from infected machines. This is often done
Memory Addressing, Binary, and Hexadecimal Review
 C++ By A EXAMPLE Memory Addressing, Binary, and Hexadecimal Review You do not have to understand the concepts in this appendix to become well-versed in C++. You can master C++, however, only if you spend
C++ By A EXAMPLE Memory Addressing, Binary, and Hexadecimal Review You do not have to understand the concepts in this appendix to become well-versed in C++. You can master C++, however, only if you spend
Printable View of: Week 13: Miscelaneous cool features. Returns from standard functions. returns from standard functions: scanf(), fopen()
 1 of 6 9/11/2009 12:57 PM Printable View of: Week 13: Miscelaneous cool features Print Save to File File: returns from standard functions: scanf(), fopen() returns from standard functions: scanf(), fopen()
1 of 6 9/11/2009 12:57 PM Printable View of: Week 13: Miscelaneous cool features Print Save to File File: returns from standard functions: scanf(), fopen() returns from standard functions: scanf(), fopen()
Dr. Ramesh K. Karne Department of Computer and Information Sciences, Towson University, Towson, MD /12/2014 Slide 1
 Dr. Ramesh K. Karne Department of Computer and Information Sciences, Towson University, Towson, MD 21252 rkarne@towson.edu 11/12/2014 Slide 1 Intel x86 Aseembly Language Assembly Language Assembly Language
Dr. Ramesh K. Karne Department of Computer and Information Sciences, Towson University, Towson, MD 21252 rkarne@towson.edu 11/12/2014 Slide 1 Intel x86 Aseembly Language Assembly Language Assembly Language
Lecture Notes on Memory Layout
 Lecture Notes on Memory Layout 15-122: Principles of Imperative Computation Frank Pfenning André Platzer Lecture 11 1 Introduction In order to understand how programs work, we can consider the functions,
Lecture Notes on Memory Layout 15-122: Principles of Imperative Computation Frank Pfenning André Platzer Lecture 11 1 Introduction In order to understand how programs work, we can consider the functions,
By: Dalbir Singh, Computer Science Dep't
 Assembly language is essentially the native language of your computer. Technically the processor of your machine understands machine code (consisting of ones and zeroes). But in order to write such a machine
Assembly language is essentially the native language of your computer. Technically the processor of your machine understands machine code (consisting of ones and zeroes). But in order to write such a machine
Post Experiment Interview Questions
 Post Experiment Interview Questions Questions about the Maximum Problem 1. What is this problem statement asking? 2. What is meant by positive integers? 3. What does it mean by the user entering valid
Post Experiment Interview Questions Questions about the Maximum Problem 1. What is this problem statement asking? 2. What is meant by positive integers? 3. What does it mean by the user entering valid
GS and ASLR in Windows Vista. Ollie Whitehouse
 GS and ASLR in Windows Vista Ollie Whitehouse Agenda 1 Introduction to GS / Detecting GS 2 GS Analysis Findings 3 Introduction to ASLR 4 ASLR Analysis Findings 5 Conclusions GS and ASLR in Windows Vista
GS and ASLR in Windows Vista Ollie Whitehouse Agenda 1 Introduction to GS / Detecting GS 2 GS Analysis Findings 3 Introduction to ASLR 4 ASLR Analysis Findings 5 Conclusions GS and ASLR in Windows Vista
Secure Programming Lecture 3: Memory Corruption I (Stack Overflows)
 Secure Programming Lecture 3: Memory Corruption I (Stack Overflows) David Aspinall, Informatics @ Edinburgh 24th January 2017 Outline Roadmap Memory corruption vulnerabilities Instant Languages and Runtimes
Secure Programming Lecture 3: Memory Corruption I (Stack Overflows) David Aspinall, Informatics @ Edinburgh 24th January 2017 Outline Roadmap Memory corruption vulnerabilities Instant Languages and Runtimes
C++ for Java Programmers
 Basics all Finished! Everything we have covered so far: Lecture 5 Operators Variables Arrays Null Terminated Strings Structs Functions 1 2 45 mins of pure fun Introduction Today: Pointers Pointers Even
Basics all Finished! Everything we have covered so far: Lecture 5 Operators Variables Arrays Null Terminated Strings Structs Functions 1 2 45 mins of pure fun Introduction Today: Pointers Pointers Even
printf( Please enter another number: ); scanf( %d, &num2);
 CIT 593 Intro to Computer Systems Lecture #13 (11/1/12) Now that we've looked at how an assembly language program runs on a computer, we're ready to move up a level and start working with more powerful
CIT 593 Intro to Computer Systems Lecture #13 (11/1/12) Now that we've looked at how an assembly language program runs on a computer, we're ready to move up a level and start working with more powerful
lcc-win32 Reference Manual
 lcc-win32 Reference Manual Version 2.2 January 2014 Written by Mark Holthouse Westwood High School mholthouse@westwood.k12.ma.us Contents Preface... 3 Using lcc-win32 for the First Time... 3 Starting a
lcc-win32 Reference Manual Version 2.2 January 2014 Written by Mark Holthouse Westwood High School mholthouse@westwood.k12.ma.us Contents Preface... 3 Using lcc-win32 for the First Time... 3 Starting a
5 R1 The one green in the same place so either of these could be green.
 Page: 1 of 20 1 R1 Now. Maybe what we should do is write out the cases that work. We wrote out one of them really very clearly here. [R1 takes out some papers.] Right? You did the one here um where you
Page: 1 of 20 1 R1 Now. Maybe what we should do is write out the cases that work. We wrote out one of them really very clearly here. [R1 takes out some papers.] Right? You did the one here um where you
INFORMATION SECURITY - PRACTICAL ASSESSMENT - BASICS IN BUFFER EXPLOITATION
 INFORMATION SECURITY - PRACTICAL ASSESSMENT - BASICS IN BUFFER EXPLOITATION GRENOBLE INP ENSIMAG http://www.ensimag.fr COMPUTER SCIENCE 3RD YEAR IF-MMIS - 1ST SEMESTER, 2011 Lecturers: Fabien Duchene -
INFORMATION SECURITY - PRACTICAL ASSESSMENT - BASICS IN BUFFER EXPLOITATION GRENOBLE INP ENSIMAG http://www.ensimag.fr COMPUTER SCIENCE 3RD YEAR IF-MMIS - 1ST SEMESTER, 2011 Lecturers: Fabien Duchene -
Black Box Debugging of Embedded Systems
 Black Box Debugging of Embedded Systems Introduction: Alexandru Ariciu Background in hacking Worked as a hacker for my whole life Worked in corporate security before (Pentester) Currently an ICS Penetration
Black Box Debugging of Embedded Systems Introduction: Alexandru Ariciu Background in hacking Worked as a hacker for my whole life Worked in corporate security before (Pentester) Currently an ICS Penetration
Buffer-Overflow Attacks on the Stack
 Computer Systems Buffer-Overflow Attacks on the Stack Introduction A buffer overflow occurs when a program, while writing data to a buffer, overruns the buffer's boundary and overwrites memory in adjacent
Computer Systems Buffer-Overflow Attacks on the Stack Introduction A buffer overflow occurs when a program, while writing data to a buffer, overruns the buffer's boundary and overwrites memory in adjacent
Hello, World! in C. Johann Myrkraverk Oskarsson October 23, The Quintessential Example Program 1. I Printing Text 2. II The Main Function 3
 Hello, World! in C Johann Myrkraverk Oskarsson October 23, 2018 Contents 1 The Quintessential Example Program 1 I Printing Text 2 II The Main Function 3 III The Header Files 4 IV Compiling and Running
Hello, World! in C Johann Myrkraverk Oskarsson October 23, 2018 Contents 1 The Quintessential Example Program 1 I Printing Text 2 II The Main Function 3 III The Header Files 4 IV Compiling and Running
Sandwiches for everyone
 Inf2C :: Computer Systems Today s menu ( And finally, monsieur, a wafer-thin mint ) Notes on security Or, why safety is an illusion, why ignorance is bliss, and why knowledge is power Stack overflows Or,
Inf2C :: Computer Systems Today s menu ( And finally, monsieur, a wafer-thin mint ) Notes on security Or, why safety is an illusion, why ignorance is bliss, and why knowledge is power Stack overflows Or,
Procedures, Parameters, Values and Variables. Steven R. Bagley
 Procedures, Parameters, Values and Variables Steven R. Bagley Recap A Program is a sequence of statements (instructions) Statements executed one-by-one in order Unless it is changed by the programmer e.g.
Procedures, Parameters, Values and Variables Steven R. Bagley Recap A Program is a sequence of statements (instructions) Statements executed one-by-one in order Unless it is changed by the programmer e.g.
Usability Test Report: Requesting Library Material 1
 Usability Test Report: Requesting Library Material 1 Summary Emily Daly and Kate Collins conducted usability testing on the processes of requesting library material. The test was conducted at the temporary
Usability Test Report: Requesting Library Material 1 Summary Emily Daly and Kate Collins conducted usability testing on the processes of requesting library material. The test was conducted at the temporary
Islamic University Gaza Engineering Faculty Department of Computer Engineering ECOM 2125: Assembly Language LAB. Lab # 10. Advanced Procedures
 Islamic University Gaza Engineering Faculty Department of Computer Engineering ECOM 2125: Assembly Language LAB Lab # 10 Advanced Procedures May, 2014 1 Assembly Language LAB Stack Parameters There are
Islamic University Gaza Engineering Faculty Department of Computer Engineering ECOM 2125: Assembly Language LAB Lab # 10 Advanced Procedures May, 2014 1 Assembly Language LAB Stack Parameters There are
Installing and Configuring the Voice UPB Bridge updated 22-Jan-2018
 Installing and Configuring the Voice UPB Bridge updated 22-Jan-2018 Before starting these instructions, you should already have your Voice assistant installed and working. These instructions can be used
Installing and Configuring the Voice UPB Bridge updated 22-Jan-2018 Before starting these instructions, you should already have your Voice assistant installed and working. These instructions can be used
CONTENTS: What Is Programming? How a Computer Works Programming Languages Java Basics. COMP-202 Unit 1: Introduction
 CONTENTS: What Is Programming? How a Computer Works Programming Languages Java Basics COMP-202 Unit 1: Introduction Announcements Did you miss the first lecture? Come talk to me after class. If you want
CONTENTS: What Is Programming? How a Computer Works Programming Languages Java Basics COMP-202 Unit 1: Introduction Announcements Did you miss the first lecture? Come talk to me after class. If you want
Exploiting the MSRPC Heap Overflow Part I
 Exploiting the MSRPC Heap Overflow Part I Dave Aitel Sep 11, 2003 Illustration 1Polyphemus Moth This little documentary chronicles the last moments of another beautiful moth, stuck somewhere between the
Exploiting the MSRPC Heap Overflow Part I Dave Aitel Sep 11, 2003 Illustration 1Polyphemus Moth This little documentary chronicles the last moments of another beautiful moth, stuck somewhere between the
