Context-Sensitive Pointer Analysis. Recall Context Sensitivity. Partial Transfer Functions [Wilson et. al. 95] Emami 1994
|
|
|
- Nigel Shepherd
- 6 years ago
- Views:
Transcription
1 Context-Sensitive Pointer Analysis Last time Flow-insensitive pointer analysis Today Context-sensitive pointer analysis Emami invocation graphs Partial Transfer Functions The big picture Recall Context Sensitivity Is x constant? a = id(4); a = id(4); 4 5 b = id(5); id(x) 4,5 4,5 b = id(5); id(x) Context-sensitive analysis Computes an answer for every callsite: x is 4 in the first call x is 5 in the second call CS553 Lecture Context-Sensitive Pointer Analysis 2 CS553 Lecture Context-Sensitive Pointer Analysis 3 Emami 1994 Uses invocation graph for context-sensitivity Can be exponential in program size Handles function pointers Characterization of Emami Flow-sensitive Context-sensitive May and must analysis Heap modeling: one heap variable Aggregate modeling of fields and arrays Partial Transfer Functions [Wilson et. al. 95] Key idea Exploit commonality among contexts Provide one procedure summary (PTF) for all contexts that share the same input/output aliasing relationships CS553 Lecture Context-Sensitive Pointer Analysis 4 CS553 Lecture Context-Sensitive Pointer Analysis 5 1
2 Partial Transfer Functions Example main() int *a,*b,c,d; a = &c; b = &d; swap(&a, &b); // S0 for (i = 0; i<2; i++) bar(&a,&a); // S1 bar(&b,&b); // S2 bar(&a,&b); // S3 bar(&b,&a); // S4 void bar(int **i, int **j) swap(i,j); void swap(int **x, int **y) int *temp = *x; *x = *y; *y = temp; How many contexts do we care about? Two: the formals either alias or they do not alias In practice Only need 1 or 2 PTF s per procedure Complex to implement CS553 Lecture Context-Sensitive Pointer Analysis 6 The Big Picture Where do we lose precision? Let s revisit our running example from last week CS553 Lecture Context-Sensitive Pointer Analysis 7 Revisiting Our Earlier Example Flow-insensitive context-sensitive (FICS) p 1 b p 2 d q 1 f q 2 g x 1 b, f x 2 d, g a b, d, f, g b c, e d c, e f c, e g c, e CS553 Lecture Context-Sensitive Pointer Analysis 8 Revisiting Our Earlier Example (cont) Flow-sensitive context-sensitive (FSCS) p 11 p 11 b q 11 f p 21 d q 21 g x 11 b x 12 f x 21 d x 22 g a 11 f a 12 g f 11 c g 11 e first callsite first def CS553 Lecture Context-Sensitive Pointer Analysis 9 2
3 Revisiting Our Earlier Example (cont) Flow-insensitive context-insensitive (FICI) p b, d q f, g x b, d, f, g a b, d, f, g b c, e d c, e f c, e g c, e CS553 Lecture Context-Sensitive Pointer Analysis 10 Revisiting Our Earlier Example (cont) Flow-sensitive context-insensitive (FSCI) p b, d q f, g x 1 b, d x 2 f, g a 1 f, g a 2 f, g f 1 c g 1 c f 2 c, e (weak update) g 2 c, e (weak update) CS553 Lecture Context-Sensitive Pointer Analysis 11 Strong vs. Weak Updates Strong update When we know precisely what an assignment through a pointer refers to, the assignment kills old information Such cases are analogous to assignments to scalars int a; a := 5; a := 6; a=5 a=6 int *a, b; a := &b; a->b b := 5; a->b, b=5 *a := 6; a->b, b=6 CS553 Lecture Context-Sensitive Pointer Analysis 12 Strong vs. Weak Updates Weak update When we do not know what an assignment through a pointer refers to, we cannot use that assignment to kill old facts So the imprecision spreads int *a, b, c; if (blah) a := &b; else a := &c; a->b,c b := 5; Does not kill b=5 a->b,c, b=5 because *a might *a := 6; update c and not b a->b,c, b=5 b=6 CS553 Lecture Context-Sensitive Pointer Analysis 13 3
4 Imprecision Weak updates Occur more often in flow-insensitive and context-insensitive analyses The callgraph When function pointers are used, pointer analysis is needed to build the callgraph Imprecision in pointer analysis leads to imprecision in the callgraph A conservative callgraph has more edges than a less conservative callgraph Imprecision in the callgraph leads to further imprecision in the pointer analysis The basic issue The need for approximation CS553 Lecture Context-Sensitive Pointer Analysis 14 Approximations Many ways to approximate Recall that the constraint graph has nodes representing variables and edges representing constraints The many dimensions of pointer analysis represent different ways of collapsing the constraint graph Flow-insensitive Andersen: Collapse all constraints (assignments) pertaining to a given variable into a single node Steensgaard: Collapse all nodes that have been assigned to one another into a single node Allows information to flow from rhs to lhs as well as from lhs to rhs CS553 Lecture Context-Sensitive Pointer Analysis 15 Andersen 94 Steensgaard 96 Uses subset constraints Cubic complexity in program size, O(n 3 ) Characterization of Andersen Flow-insensitive Context-insensitive May analysis Heap modeling? Aggregate modeling: fields Uses unification constraints Almost linear in terms of program size Uses fast union-find algorithm Imprecision from merging points-to sets Characterization of Steensgaard Flow-insensitive Context-insensitive May analysis Heap modeling: none Aggregate modeling: possibly source: Barbara Ryder s Reference Analysis slides CS553 Lecture Context-Sensitive Pointer Analysis 16 source: Barbara Ryder s Reference Analysis slides CS553 Lecture Context-Sensitive Pointer Analysis 17 4
5 More Approximations Context-insensitive analysis Collapse all constraints arising from different callsites of a procedure into a single node Partial Transfer Functions Collapse constraints for all callsites of a procedure that share the same aliasing relationships Field-insensitive Collapse all fields of a structure into a single node Yet More Approximations Address Taken Collapse all objects that have their address taken into a single node Assume that all pointers point to this node Heap naming One heap: Collapse all heap objects into a single node Static allocation site Collapse all instances of objects that are allocated at the same program location into a single node Field-based Collapse all instances of a struct type into one node per field Example: one node for all instances of student.name, and another node for all instances of student.gpa CS553 Lecture Context-Sensitive Pointer Analysis 18 CS553 Lecture Context-Sensitive Pointer Analysis 19 Concepts Partial Transfer Functions Exploit commonality among contexts Next Time Next lecture Profile-guided optimization Sources of imprecision CS553 Lecture Context-Sensitive Pointer Analysis 20 CS553 Lecture Context-Sensitive Pointer Analysis 21 5
Alias Analysis. Last time Interprocedural analysis. Today Intro to alias analysis (pointer analysis) CS553 Lecture Alias Analysis I 1
 Alias Analysis Last time Interprocedural analysis Today Intro to alias analysis (pointer analysis) CS553 Lecture Alias Analysis I 1 Aliasing What is aliasing? When two expressions denote the same mutable
Alias Analysis Last time Interprocedural analysis Today Intro to alias analysis (pointer analysis) CS553 Lecture Alias Analysis I 1 Aliasing What is aliasing? When two expressions denote the same mutable
Interprocedural Analysis. Motivation. Interprocedural Analysis. Function Calls and Pointers
 Interprocedural Analysis Motivation Last time Introduction to alias analysis Today Interprocedural analysis Procedural abstraction Cornerstone of programming Introduces barriers to analysis Example x =
Interprocedural Analysis Motivation Last time Introduction to alias analysis Today Interprocedural analysis Procedural abstraction Cornerstone of programming Introduces barriers to analysis Example x =
Calvin Lin The University of Texas at Austin
 Interprocedural Analysis Last time Introduction to alias analysis Today Interprocedural analysis March 4, 2015 Interprocedural Analysis 1 Motivation Procedural abstraction Cornerstone of programming Introduces
Interprocedural Analysis Last time Introduction to alias analysis Today Interprocedural analysis March 4, 2015 Interprocedural Analysis 1 Motivation Procedural abstraction Cornerstone of programming Introduces
CS711 Advanced Programming Languages Pointer Analysis Overview and Flow-Sensitive Analysis
 CS711 Advanced Programming Languages Pointer Analysis Overview and Flow-Sensitive Analysis Radu Rugina 8 Sep 2005 Pointer Analysis Informally: determine where pointers (or references) in the program may
CS711 Advanced Programming Languages Pointer Analysis Overview and Flow-Sensitive Analysis Radu Rugina 8 Sep 2005 Pointer Analysis Informally: determine where pointers (or references) in the program may
Alias Analysis & Points-to Analysis. Hwansoo Han
 Alias Analysis & Points-to Analysis Hwansoo Han May vs. Must Information May information The information is true on some path through a CFG Must information The information is true on all paths through
Alias Analysis & Points-to Analysis Hwansoo Han May vs. Must Information May information The information is true on some path through a CFG Must information The information is true on all paths through
Static Program Analysis Part 9 pointer analysis. Anders Møller & Michael I. Schwartzbach Computer Science, Aarhus University
 Static Program Analysis Part 9 pointer analysis Anders Møller & Michael I. Schwartzbach Computer Science, Aarhus University Agenda Introduction to points-to analysis Andersen s analysis Steensgaards s
Static Program Analysis Part 9 pointer analysis Anders Møller & Michael I. Schwartzbach Computer Science, Aarhus University Agenda Introduction to points-to analysis Andersen s analysis Steensgaards s
Points-to Analysis. Xiaokang Qiu Purdue University. November 16, ECE 468 Adapted from Kulkarni 2012
 Points-to Analysis Xiaokang Qiu Purdue University ECE 468 Adapted from Kulkarni 2012 November 16, 2016 Simple example x := 5 ptr := @x *ptr := 9 y := x program S1 S2 S3 S4 dependences What are the dependences
Points-to Analysis Xiaokang Qiu Purdue University ECE 468 Adapted from Kulkarni 2012 November 16, 2016 Simple example x := 5 ptr := @x *ptr := 9 y := x program S1 S2 S3 S4 dependences What are the dependences
Lecture 20 Pointer Analysis
 Lecture 20 Pointer Analysis Basics Design Options Pointer Analysis Algorithms Pointer Analysis Using BDDs Probabilistic Pointer Analysis (Slide content courtesy of Greg Steffan, U. of Toronto) 15-745:
Lecture 20 Pointer Analysis Basics Design Options Pointer Analysis Algorithms Pointer Analysis Using BDDs Probabilistic Pointer Analysis (Slide content courtesy of Greg Steffan, U. of Toronto) 15-745:
CSE 501 Midterm Exam: Sketch of Some Plausible Solutions Winter 1997
 1) [10 pts] On homework 1, I asked about dead assignment elimination and gave the following sample solution: 8. Give an algorithm for dead assignment elimination that exploits def/use chains to work faster
1) [10 pts] On homework 1, I asked about dead assignment elimination and gave the following sample solution: 8. Give an algorithm for dead assignment elimination that exploits def/use chains to work faster
Lecture 14 Pointer Analysis
 Lecture 14 Pointer Analysis Basics Design Options Pointer Analysis Algorithms Pointer Analysis Using BDDs Probabilistic Pointer Analysis [ALSU 12.4, 12.6-12.7] Phillip B. Gibbons 15-745: Pointer Analysis
Lecture 14 Pointer Analysis Basics Design Options Pointer Analysis Algorithms Pointer Analysis Using BDDs Probabilistic Pointer Analysis [ALSU 12.4, 12.6-12.7] Phillip B. Gibbons 15-745: Pointer Analysis
Lecture 27. Pros and Cons of Pointers. Basics Design Options Pointer Analysis Algorithms Pointer Analysis Using BDDs Probabilistic Pointer Analysis
 Pros and Cons of Pointers Lecture 27 Pointer Analysis Basics Design Options Pointer Analysis Algorithms Pointer Analysis Using BDDs Probabilistic Pointer Analysis Many procedural languages have pointers
Pros and Cons of Pointers Lecture 27 Pointer Analysis Basics Design Options Pointer Analysis Algorithms Pointer Analysis Using BDDs Probabilistic Pointer Analysis Many procedural languages have pointers
Flow-sensitive Alias Analysis
 Flow-sensitive Alias Analysis Last time Client-Driven pointer analysis Today Demand DFA paper Scalable flow-sensitive alias analysis March 30, 2015 Flow-Sensitive Alias Analysis 1 Recall Previous Flow-Sensitive
Flow-sensitive Alias Analysis Last time Client-Driven pointer analysis Today Demand DFA paper Scalable flow-sensitive alias analysis March 30, 2015 Flow-Sensitive Alias Analysis 1 Recall Previous Flow-Sensitive
Lecture 16 Pointer Analysis
 Pros and Cons of Pointers Lecture 16 Pointer Analysis Basics Design Options Pointer Analysis Algorithms Pointer Analysis Using BDDs Probabilistic Pointer Analysis Many procedural languages have pointers
Pros and Cons of Pointers Lecture 16 Pointer Analysis Basics Design Options Pointer Analysis Algorithms Pointer Analysis Using BDDs Probabilistic Pointer Analysis Many procedural languages have pointers
Interprocedural Analysis. Dealing with Procedures. Course so far: Terminology
 Interprocedural Analysis Course so far: Control Flow Representation Dataflow Representation SSA form Classic DefUse and UseDef Chains Optimizations Scheduling Register Allocation Just-In-Time Compilation
Interprocedural Analysis Course so far: Control Flow Representation Dataflow Representation SSA form Classic DefUse and UseDef Chains Optimizations Scheduling Register Allocation Just-In-Time Compilation
Simple example. Analysis of programs with pointers. Program model. Points-to relation
 Simple eample Analsis of programs with pointers := 5 ptr := & *ptr := 9 := program S1 S2 S3 S4 What are the defs and uses of in this program? Problem: just looking at variable names will not give ou the
Simple eample Analsis of programs with pointers := 5 ptr := & *ptr := 9 := program S1 S2 S3 S4 What are the defs and uses of in this program? Problem: just looking at variable names will not give ou the
Lecture Notes: Pointer Analysis
 Lecture Notes: Pointer Analysis 15-819O: Program Analysis Jonathan Aldrich jonathan.aldrich@cs.cmu.edu Lecture 9 1 Motivation for Pointer Analysis In programs with pointers, program analysis can become
Lecture Notes: Pointer Analysis 15-819O: Program Analysis Jonathan Aldrich jonathan.aldrich@cs.cmu.edu Lecture 9 1 Motivation for Pointer Analysis In programs with pointers, program analysis can become
Alias Analysis. Advanced Topics. What is pointer analysis? Last Time
 Advanced Topics Last Time Experimental Methodology Today What s a managed language? Alias Analysis - dealing with pointers Focus on statically typed managed languages Method invocation resolution Alias
Advanced Topics Last Time Experimental Methodology Today What s a managed language? Alias Analysis - dealing with pointers Focus on statically typed managed languages Method invocation resolution Alias
Lecture Notes: Pointer Analysis
 Lecture Notes: Pointer Analysis 17-355/17-665/17-819: Program Analysis (Spring 2019) Jonathan Aldrich aldrich@cs.cmu.edu 1 Motivation for Pointer Analysis In the spirit of extending our understanding of
Lecture Notes: Pointer Analysis 17-355/17-665/17-819: Program Analysis (Spring 2019) Jonathan Aldrich aldrich@cs.cmu.edu 1 Motivation for Pointer Analysis In the spirit of extending our understanding of
CO444H. Ben Livshits. Datalog Pointer analysis
 CO444H Ben Livshits Datalog Pointer analysis 1 Call Graphs Class analysis: Given a reference variable x, what are the classes of the objects that x refers to at runtime? We saw CHA and RTA Deal with polymorphic/virtual
CO444H Ben Livshits Datalog Pointer analysis 1 Call Graphs Class analysis: Given a reference variable x, what are the classes of the objects that x refers to at runtime? We saw CHA and RTA Deal with polymorphic/virtual
More Dataflow Analysis
 More Dataflow Analysis Steps to building analysis Step 1: Choose lattice Step 2: Choose direction of dataflow (forward or backward) Step 3: Create transfer function Step 4: Choose confluence operator (i.e.,
More Dataflow Analysis Steps to building analysis Step 1: Choose lattice Step 2: Choose direction of dataflow (forward or backward) Step 3: Create transfer function Step 4: Choose confluence operator (i.e.,
A Context-Sensitive Memory Model for Verification of C/C++ Programs
 A Context-Sensitive Memory Model for Verification of C/C++ Programs Arie Gurfinkel and Jorge A. Navas University of Waterloo and SRI International SAS 17, August 30th, 2017 Gurfinkel and Navas (UWaterloo/SRI)
A Context-Sensitive Memory Model for Verification of C/C++ Programs Arie Gurfinkel and Jorge A. Navas University of Waterloo and SRI International SAS 17, August 30th, 2017 Gurfinkel and Navas (UWaterloo/SRI)
Partitioned Memory Models for Program Analysis
 Partitioned Memory Models for Program Analysis Wei Wang 1 Clark Barrett 2 Thomas Wies 3 1 Google 2 Stanford University 3 New York University January 13, 2017 Wei Wang Partitioned Memory Models January
Partitioned Memory Models for Program Analysis Wei Wang 1 Clark Barrett 2 Thomas Wies 3 1 Google 2 Stanford University 3 New York University January 13, 2017 Wei Wang Partitioned Memory Models January
A Simple SQL Injection Pattern
 Lecture 12 Pointer Analysis 1. Motivation: security analysis 2. Datalog 3. Context-insensitive, flow-insensitive pointer analysis 4. Context sensitivity Readings: Chapter 12 A Simple SQL Injection Pattern
Lecture 12 Pointer Analysis 1. Motivation: security analysis 2. Datalog 3. Context-insensitive, flow-insensitive pointer analysis 4. Context sensitivity Readings: Chapter 12 A Simple SQL Injection Pattern
OOPLs - call graph construction. Example executed calls
 OOPLs - call graph construction Compile-time analysis of reference variables and fields Problem: how to resolve virtual function calls? Need to determine to which objects (or types of objects) a reference
OOPLs - call graph construction Compile-time analysis of reference variables and fields Problem: how to resolve virtual function calls? Need to determine to which objects (or types of objects) a reference
Reference Analyses. VTA - Variable Type Analysis
 Reference Analyses Variable Type Analysis for Java Related points-to analyses for C Steengaard Andersen Field-sensitive points-to for Java Object-sensitive points-to for Java Other analysis approaches
Reference Analyses Variable Type Analysis for Java Related points-to analyses for C Steengaard Andersen Field-sensitive points-to for Java Object-sensitive points-to for Java Other analysis approaches
No model may be available. Software Abstractions. Recap on Model Checking. Model Checking for SW Verif. More on the big picture. Abst -> MC -> Refine
 No model may be available Programmer Software Abstractions Tests Coverage Code Abhik Roychoudhury CS 5219 National University of Singapore Testing Debug Today s lecture Abstract model (Boolean pgm.) Desirable
No model may be available Programmer Software Abstractions Tests Coverage Code Abhik Roychoudhury CS 5219 National University of Singapore Testing Debug Today s lecture Abstract model (Boolean pgm.) Desirable
Computer Programming
 Computer Programming Dr. Deepak B Phatak Dr. Supratik Chakraborty Department of Computer Science and Engineering Session: Parameter Passing in Function Calls Dr. Deepak B. Phatak & Dr. Supratik Chakraborty,
Computer Programming Dr. Deepak B Phatak Dr. Supratik Chakraborty Department of Computer Science and Engineering Session: Parameter Passing in Function Calls Dr. Deepak B. Phatak & Dr. Supratik Chakraborty,
Cloning-Based Context-Sensitive Pointer Alias Analysis using BDDs
 More Pointer Analysis Last time Flow-Insensitive Pointer Analysis Inclusion-based analysis (Andersen) Today Class projects Context-Sensitive analysis March 3, 2014 Flow-Insensitive Pointer Analysis 1 John
More Pointer Analysis Last time Flow-Insensitive Pointer Analysis Inclusion-based analysis (Andersen) Today Class projects Context-Sensitive analysis March 3, 2014 Flow-Insensitive Pointer Analysis 1 John
Extra notes on Field- sensitive points- to analysis with inclusion constraints Sept 9, 2015
 Extra notes on Field- sensitive points- to analysis with inclusion constraints Sept 9, 2015 Week 3 CS6304 The Rountev et al. paper at OOPSLA 2000 extended Andersen s points- to analysis for C programs
Extra notes on Field- sensitive points- to analysis with inclusion constraints Sept 9, 2015 Week 3 CS6304 The Rountev et al. paper at OOPSLA 2000 extended Andersen s points- to analysis for C programs
Parameterized Object Sensitivity for Points-to Analysis for Java. Authors: Ana Milanova, Atanas Rountev, Barbara G. Ryder Presenter: Zheng Song
 Parameterized Object Sensitivity for Points-to Analysis for Java Authors: Ana Milanova, Atanas Rountev, Barbara G. Ryder Presenter: Zheng Song Outlines Introduction Existing Method and its limitation Object
Parameterized Object Sensitivity for Points-to Analysis for Java Authors: Ana Milanova, Atanas Rountev, Barbara G. Ryder Presenter: Zheng Song Outlines Introduction Existing Method and its limitation Object
Compiler Structure. Data Flow Analysis. Control-Flow Graph. Available Expressions. Data Flow Facts
 Compiler Structure Source Code Abstract Syntax Tree Control Flow Graph Object Code CMSC 631 Program Analysis and Understanding Fall 2003 Data Flow Analysis Source code parsed to produce AST AST transformed
Compiler Structure Source Code Abstract Syntax Tree Control Flow Graph Object Code CMSC 631 Program Analysis and Understanding Fall 2003 Data Flow Analysis Source code parsed to produce AST AST transformed
Loop-Oriented Array- and Field-Sensitive Pointer Analysis for Automatic SIMD Vectorization
 Loop-Oriented Array- and Field-Sensitive Pointer Analysis for Automatic SIMD Vectorization Yulei Sui, Xiaokang Fan, Hao Zhou and Jingling Xue School of Computer Science and Engineering The University of
Loop-Oriented Array- and Field-Sensitive Pointer Analysis for Automatic SIMD Vectorization Yulei Sui, Xiaokang Fan, Hao Zhou and Jingling Xue School of Computer Science and Engineering The University of
CS553 Lecture Generalizing Data-flow Analysis 3
 Generalizing Data-flow Analysis Announcements Project 2 writeup is available Read Stephenson paper Last Time Control-flow analysis Today C-Breeze Introduction Other types of data-flow analysis Reaching
Generalizing Data-flow Analysis Announcements Project 2 writeup is available Read Stephenson paper Last Time Control-flow analysis Today C-Breeze Introduction Other types of data-flow analysis Reaching
CS558 Programming Languages
 CS558 Programming Languages Fall 2016 Lecture 4a Andrew Tolmach Portland State University 1994-2016 Pragmatics of Large Values Real machines are very efficient at handling word-size chunks of data (e.g.
CS558 Programming Languages Fall 2016 Lecture 4a Andrew Tolmach Portland State University 1994-2016 Pragmatics of Large Values Real machines are very efficient at handling word-size chunks of data (e.g.
Advanced Compiler Construction
 CS 526 Advanced Compiler Construction http://misailo.cs.illinois.edu/courses/cs526 INTERPROCEDURAL ANALYSIS The slides adapted from Vikram Adve So Far Control Flow Analysis Data Flow Analysis Dependence
CS 526 Advanced Compiler Construction http://misailo.cs.illinois.edu/courses/cs526 INTERPROCEDURAL ANALYSIS The slides adapted from Vikram Adve So Far Control Flow Analysis Data Flow Analysis Dependence
Flow- Context- Sensitive Pointer Analysis
 Flow- Context- Sensitive Pointer Analysis Yulei Sui Supervisor: Prof. Jingling CORG UNSW December 24, 2010 1 / 38 Pointer Analysis Why Pointer Analysis? Why Pointer Analysis is difficult? Outline Flow-
Flow- Context- Sensitive Pointer Analysis Yulei Sui Supervisor: Prof. Jingling CORG UNSW December 24, 2010 1 / 38 Pointer Analysis Why Pointer Analysis? Why Pointer Analysis is difficult? Outline Flow-
CSE 3302 Programming Languages Lecture 5: Control
 CSE 3302 Programming Languages Lecture 5: Control (based on the slides by Chengkai Li) Leonidas Fegaras University of Texas at Arlington CSE 3302 L5 Fall 2009 1 Control Control: what gets executed, when,
CSE 3302 Programming Languages Lecture 5: Control (based on the slides by Chengkai Li) Leonidas Fegaras University of Texas at Arlington CSE 3302 L5 Fall 2009 1 Control Control: what gets executed, when,
CSE 307: Principles of Programming Languages
 CSE 307: Principles of Programming Languages Variables and Constants R. Sekar 1 / 22 Topics 2 / 22 Variables and Constants Variables are stored in memory, whereas constants need not be. Value of variables
CSE 307: Principles of Programming Languages Variables and Constants R. Sekar 1 / 22 Topics 2 / 22 Variables and Constants Variables are stored in memory, whereas constants need not be. Value of variables
Goal of lecture. Object-oriented Programming. Context of discussion. Message of lecture
 Goal of lecture Object-oriented Programming Understand inadequacies of class languages like Ur- Java Extend Ur-Java so it becomes an object-oriented language Implementation in SaM heap allocation of objects
Goal of lecture Object-oriented Programming Understand inadequacies of class languages like Ur- Java Extend Ur-Java so it becomes an object-oriented language Implementation in SaM heap allocation of objects
Linked Data Representations. Data Structures and Programming Techniques
 Linked Data Representations 1 Linked Data Representations Linked data representations such as lists, stacks, queues, sets and trees are very useful in Computer Science and applications. E.g., in Databases,
Linked Data Representations 1 Linked Data Representations Linked data representations such as lists, stacks, queues, sets and trees are very useful in Computer Science and applications. E.g., in Databases,
GCC Internals Alias analysis
 GCC Internals Alias analysis Diego Novillo dnovillo@google.com November 2007 Overview GIMPLE represents alias information explicitly Alias analysis is just another pass Artificial symbols represent memory
GCC Internals Alias analysis Diego Novillo dnovillo@google.com November 2007 Overview GIMPLE represents alias information explicitly Alias analysis is just another pass Artificial symbols represent memory
Allocation & Efficiency Generic Containers Notes on Assignment 5
 Allocation & Efficiency Generic Containers Notes on Assignment 5 CS 311 Data Structures and Algorithms Lecture Slides Friday, October 30, 2009 Glenn G. Chappell Department of Computer Science University
Allocation & Efficiency Generic Containers Notes on Assignment 5 CS 311 Data Structures and Algorithms Lecture Slides Friday, October 30, 2009 Glenn G. Chappell Department of Computer Science University
CMSC 341 Lecture 15 Leftist Heaps
 Based on slides from previous iterations of this course CMSC 341 Lecture 15 Leftist Heaps Prof. John Park Review of Heaps Min Binary Heap A min binary heap is a Complete binary tree Neither child is smaller
Based on slides from previous iterations of this course CMSC 341 Lecture 15 Leftist Heaps Prof. John Park Review of Heaps Min Binary Heap A min binary heap is a Complete binary tree Neither child is smaller
Lecture 4 Memory Management
 Lecture 4 Memory Management Dr. Wilson Rivera ICOM 4036: Programming Languages Electrical and Computer Engineering Department University of Puerto Rico Some slides adapted from Sebesta s textbook Lecture
Lecture 4 Memory Management Dr. Wilson Rivera ICOM 4036: Programming Languages Electrical and Computer Engineering Department University of Puerto Rico Some slides adapted from Sebesta s textbook Lecture
BBM 201 DATA STRUCTURES
 BBM 201 DATA STRUCTURES Lecture 8: Dynamically Allocated Linked Lists 2017-2018 Fall int x; x = 8; int A[4]; An array is stored as one contiguous block of memory. How can we add a fifth element to the
BBM 201 DATA STRUCTURES Lecture 8: Dynamically Allocated Linked Lists 2017-2018 Fall int x; x = 8; int A[4]; An array is stored as one contiguous block of memory. How can we add a fifth element to the
CMSC 341 Lecture 15 Leftist Heaps
 Based on slides from previous iterations of this course CMSC 341 Lecture 15 Leftist Heaps Prof. John Park Review of Heaps Min Binary Heap A min binary heap is a Complete binary tree Neither child is smaller
Based on slides from previous iterations of this course CMSC 341 Lecture 15 Leftist Heaps Prof. John Park Review of Heaps Min Binary Heap A min binary heap is a Complete binary tree Neither child is smaller
CS558 Programming Languages Winter 2018 Lecture 4a. Andrew Tolmach Portland State University
 CS558 Programming Languages Winter 2018 Lecture 4a Andrew Tolmach Portland State University 1994-2018 Pragmatics of Large Values Real machines are very efficient at handling word-size chunks of data (e.g.
CS558 Programming Languages Winter 2018 Lecture 4a Andrew Tolmach Portland State University 1994-2018 Pragmatics of Large Values Real machines are very efficient at handling word-size chunks of data (e.g.
Analysis of Object-oriented Programming Languages
 Analysis of Object-oriented Programming Languages Dr. Barbara G. Ryder Rutgers University http://www.cs.rutgers.edu/~ryder http://prolangs.rutgers.edu/ OOAnalysis, Dagstuhl 2/03, BG Ryder 1 Outline Why
Analysis of Object-oriented Programming Languages Dr. Barbara G. Ryder Rutgers University http://www.cs.rutgers.edu/~ryder http://prolangs.rutgers.edu/ OOAnalysis, Dagstuhl 2/03, BG Ryder 1 Outline Why
Alias Analysis in LLVM
 Alias Analysis in LLVM by Sheng-Hsiu Lin Presented to the Graduate and Research Committee of Lehigh University in Candidacy for the Degree of Master of Science in Computer Science Lehigh University May
Alias Analysis in LLVM by Sheng-Hsiu Lin Presented to the Graduate and Research Committee of Lehigh University in Candidacy for the Degree of Master of Science in Computer Science Lehigh University May
Data Flow Testing. CSCE Lecture 10-02/09/2017
 Data Flow Testing CSCE 747 - Lecture 10-02/09/2017 Control Flow Capture dependencies in terms of how control passes between parts of a program. We care about the effect of a statement when it affects the
Data Flow Testing CSCE 747 - Lecture 10-02/09/2017 Control Flow Capture dependencies in terms of how control passes between parts of a program. We care about the effect of a statement when it affects the
Introduction to Shape and Pointer Analysis
 Introduction to Shape and Pointer Analsis CS 502 Lecture 11 10/30/08 Some slides adapted from Nielson, Nielson, Hankin Principles of Program Analsis Analsis of the Heap Thus far, we have focussed on control
Introduction to Shape and Pointer Analsis CS 502 Lecture 11 10/30/08 Some slides adapted from Nielson, Nielson, Hankin Principles of Program Analsis Analsis of the Heap Thus far, we have focussed on control
Tracking Pointers with Path and Context Sensitivity for Bug Detection in C Programs. {livshits,
 Tracking Pointers with Path and Context Sensitivity for Bug Detection in C Programs {livshits, lam}@cs.stanford.edu 2 Background Software systems are getting bigger Harder to develop Harder to modify Harder
Tracking Pointers with Path and Context Sensitivity for Bug Detection in C Programs {livshits, lam}@cs.stanford.edu 2 Background Software systems are getting bigger Harder to develop Harder to modify Harder
Program Static Analysis. Overview
 Program Static Analysis Overview Program static analysis Abstract interpretation Data flow analysis Intra-procedural Inter-procedural 2 1 What is static analysis? The analysis to understand computer software
Program Static Analysis Overview Program static analysis Abstract interpretation Data flow analysis Intra-procedural Inter-procedural 2 1 What is static analysis? The analysis to understand computer software
Global Optimization. Lecture Outline. Global flow analysis. Global constant propagation. Liveness analysis. Local Optimization. Global Optimization
 Lecture Outline Global Optimization Global flow analysis Global constant propagation Liveness analysis Compiler Design I (2011) 2 Local Optimization Recall the simple basic-block optimizations Constant
Lecture Outline Global Optimization Global flow analysis Global constant propagation Liveness analysis Compiler Design I (2011) 2 Local Optimization Recall the simple basic-block optimizations Constant
Recap: Pointers. int* int& *p &i &*&* ** * * * * IFMP 18, M. Schwerhoff
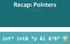 Recap: Pointers IFMP 18, M. Schwerhoff int* int& *p &i &*&* ** * * * * A 0 A 1 A 2 A 3 A 4 A 5 A 0 A 1 A 2 A 3 A 4 A 5 5 i int* p; A 0 A 1 A 2 A 3 A 4 A 5 5 i p int* p; p = &i; A 0 A 1 A 2 A 3 A 4 A 5
Recap: Pointers IFMP 18, M. Schwerhoff int* int& *p &i &*&* ** * * * * A 0 A 1 A 2 A 3 A 4 A 5 A 0 A 1 A 2 A 3 A 4 A 5 5 i int* p; A 0 A 1 A 2 A 3 A 4 A 5 5 i p int* p; p = &i; A 0 A 1 A 2 A 3 A 4 A 5
Overview. Why Pointers?
 Overview CS345H: Programming Languages Lecture 16: Imperative Languages II Thomas Dillig Last time, we have seen how we can give meaning to a simple imperative Specifically, we wrote operational semantics
Overview CS345H: Programming Languages Lecture 16: Imperative Languages II Thomas Dillig Last time, we have seen how we can give meaning to a simple imperative Specifically, we wrote operational semantics
CS 31 Discussion 1A, Week 4. Zengwen Yuan (zyuan [at] cs.ucla.edu) Humanities A65, Friday 10:00 11:50 a.m.
![CS 31 Discussion 1A, Week 4. Zengwen Yuan (zyuan [at] cs.ucla.edu) Humanities A65, Friday 10:00 11:50 a.m. CS 31 Discussion 1A, Week 4. Zengwen Yuan (zyuan [at] cs.ucla.edu) Humanities A65, Friday 10:00 11:50 a.m.](/thumbs/93/112326429.jpg) CS 31 Discussion 1A, Week 4 Zengwen Yuan (zyuan [at] cs.ucla.edu) Humanities A65, Friday 10:00 11:50 a.m. Today s focus Notes from the project 2 grading Function call predefined function define a function
CS 31 Discussion 1A, Week 4 Zengwen Yuan (zyuan [at] cs.ucla.edu) Humanities A65, Friday 10:00 11:50 a.m. Today s focus Notes from the project 2 grading Function call predefined function define a function
 POINTERS - Pointer is a variable that holds a memory address of another variable of same type. - It supports dynamic allocation routines. - It can improve the efficiency of certain routines. C++ Memory
POINTERS - Pointer is a variable that holds a memory address of another variable of same type. - It supports dynamic allocation routines. - It can improve the efficiency of certain routines. C++ Memory
Lecture 26: Pointer Analysis
 [Based on slides from R. Bodik] Lecture 26: Pointer Analysis Administrivia HKN survey next Thursday. Worth 5 points (but you must show up!). Today Points-to analysis: an instance of static analysis for
[Based on slides from R. Bodik] Lecture 26: Pointer Analysis Administrivia HKN survey next Thursday. Worth 5 points (but you must show up!). Today Points-to analysis: an instance of static analysis for
Lecture 26: Pointer Analysis. General Goals of Static Analysis. Client 1: Example. Client 1: Optimizing virtual calls in Java
 [Based on slides from R. Bodik] Administrivia Lecture 26: Pointer Analysis HKN survey next Thursday. Worth 5 points (but you must show up!). Today Points-to analysis: an instance of static analysis for
[Based on slides from R. Bodik] Administrivia Lecture 26: Pointer Analysis HKN survey next Thursday. Worth 5 points (but you must show up!). Today Points-to analysis: an instance of static analysis for
Code Generation II. Code generation for OO languages. Object layout Dynamic dispatch. Parameter-passing mechanisms Allocating temporaries in the AR
 Code Generation II Code generation for OO languages Object layout Dynamic dispatch Parameter-passing mechanisms Allocating temporaries in the AR Object Layout OO implementation = Stuff from last lecture
Code Generation II Code generation for OO languages Object layout Dynamic dispatch Parameter-passing mechanisms Allocating temporaries in the AR Object Layout OO implementation = Stuff from last lecture
Recitation 02/02/07 Defining Classes and Methods. Chapter 4
 Recitation 02/02/07 Defining Classes and Methods 1 Miscellany Project 2 due last night Exam 1 (Ch 1-4) Thursday, Feb. 8, 8:30-9:30pm PHYS 112 Sample Exam posted Project 3 due Feb. 15 10:00pm check newsgroup!
Recitation 02/02/07 Defining Classes and Methods 1 Miscellany Project 2 due last night Exam 1 (Ch 1-4) Thursday, Feb. 8, 8:30-9:30pm PHYS 112 Sample Exam posted Project 3 due Feb. 15 10:00pm check newsgroup!
Module 27 Switch-case statements and Run-time storage management
 Module 27 Switch-case statements and Run-time storage management In this module we will discuss the pending constructs in generating three-address code namely switch-case statements. We will also discuss
Module 27 Switch-case statements and Run-time storage management In this module we will discuss the pending constructs in generating three-address code namely switch-case statements. We will also discuss
Parameter passing. Programming in C. Important. Parameter passing... C implements call-by-value parameter passing. UVic SEng 265
 Parameter passing Programming in C UVic SEng 265 Daniel M. German Department of Computer Science University of Victoria 1 SEng 265 dmgerman@uvic.ca C implements call-by-value parameter passing int a =
Parameter passing Programming in C UVic SEng 265 Daniel M. German Department of Computer Science University of Victoria 1 SEng 265 dmgerman@uvic.ca C implements call-by-value parameter passing int a =
Data Space Randomization
 Data Space Randomization Sandeep Bhatkar 1 and R. Sekar 2 1 Symantec Research Laboratories, Culver City, CA 90230, USA 2 Stony Brook University, Stony Brook, NY 11794, USA Abstract. Over the past several
Data Space Randomization Sandeep Bhatkar 1 and R. Sekar 2 1 Symantec Research Laboratories, Culver City, CA 90230, USA 2 Stony Brook University, Stony Brook, NY 11794, USA Abstract. Over the past several
CSE 333. Lecture 10 - references, const, classes. Hal Perkins Paul G. Allen School of Computer Science & Engineering University of Washington
 CSE 333 Lecture 10 - references, const, classes Hal Perkins Paul G. Allen School of Computer Science & Engineering University of Washington Administrivia New C++ exercise out today, due Friday morning
CSE 333 Lecture 10 - references, const, classes Hal Perkins Paul G. Allen School of Computer Science & Engineering University of Washington Administrivia New C++ exercise out today, due Friday morning
Data Structure Analysis: A Fast and Scalable Context-Sensitive Heap Analysis
 Data Structure Analysis: A Fast and Scalable Context-Sensitive Heap Analysis Chris Lattner Vikram Adve University of Illinois at Urbana-Champaign {lattner,vadve}@cs.uiuc.edu ABSTRACT Our recent work has
Data Structure Analysis: A Fast and Scalable Context-Sensitive Heap Analysis Chris Lattner Vikram Adve University of Illinois at Urbana-Champaign {lattner,vadve}@cs.uiuc.edu ABSTRACT Our recent work has
CSCI 2132 Software Development. Lecture 17: Functions and Recursion
 CSCI 2132 Software Development Lecture 17: Functions and Recursion Instructor: Vlado Keselj Faculty of Computer Science Dalhousie University 15-Oct-2018 (17) CSCI 2132 1 Previous Lecture Example: binary
CSCI 2132 Software Development Lecture 17: Functions and Recursion Instructor: Vlado Keselj Faculty of Computer Science Dalhousie University 15-Oct-2018 (17) CSCI 2132 1 Previous Lecture Example: binary
CS61C Midterm Review on C & Memory Management
 CS61C Midterm Review on C & Memory Management Fall 2006 Aaron Staley Some material taken from slides by: Michael Le Navtej Sadhal Overview C Array and Pointer Goodness! Memory Management The Three Three
CS61C Midterm Review on C & Memory Management Fall 2006 Aaron Staley Some material taken from slides by: Michael Le Navtej Sadhal Overview C Array and Pointer Goodness! Memory Management The Three Three
CS 4120 Lecture 31 Interprocedural analysis, fixed-point algorithms 9 November 2011 Lecturer: Andrew Myers
 CS 4120 Lecture 31 Interprocedural analysis, fixed-point algorithms 9 November 2011 Lecturer: Andrew Myers These notes are not yet complete. 1 Interprocedural analysis Some analyses are not sufficiently
CS 4120 Lecture 31 Interprocedural analysis, fixed-point algorithms 9 November 2011 Lecturer: Andrew Myers These notes are not yet complete. 1 Interprocedural analysis Some analyses are not sufficiently
Announcements. Working on requirements this week Work on design, implementation. Types. Lecture 17 CS 169. Outline. Java Types
 Announcements Types Working on requirements this week Work on design, implementation Lecture 17 CS 169 Prof. Brewer CS 169 Lecture 16 1 Prof. Brewer CS 169 Lecture 16 2 Outline Type concepts Where do types
Announcements Types Working on requirements this week Work on design, implementation Lecture 17 CS 169 Prof. Brewer CS 169 Lecture 16 1 Prof. Brewer CS 169 Lecture 16 2 Outline Type concepts Where do types
References and pointers
 References and pointers Pointers are variables whose value is a reference, i.e. an address of a store location. Early languages (Fortran, COBOL, Algol 60) had no pointers; added to Fortran 90. In Pascal,
References and pointers Pointers are variables whose value is a reference, i.e. an address of a store location. Early languages (Fortran, COBOL, Algol 60) had no pointers; added to Fortran 90. In Pascal,
CS 32. Lecture 5: Templates
 CS 32 Lecture 5: Templates Vectors Sort of like what you remember from Physics but sort of not Can have many components Usually called entries Like Python lists Array vs. Vector What s the difference?
CS 32 Lecture 5: Templates Vectors Sort of like what you remember from Physics but sort of not Can have many components Usually called entries Like Python lists Array vs. Vector What s the difference?
CS32 - Week 2. Umut Oztok. July 1, Umut Oztok CS32 - Week 2
 CS32 - Week 2 Umut Oztok July 1, 2016 Arrays A basic data structure (commonly used). Organize data in a sequential way. Arrays A basic data structure (commonly used). Organize data in a sequential way.
CS32 - Week 2 Umut Oztok July 1, 2016 Arrays A basic data structure (commonly used). Organize data in a sequential way. Arrays A basic data structure (commonly used). Organize data in a sequential way.
ECE 2400 Computer Systems Programming Fall 2018 Topic 7: Concrete Data Types
 ECE 2400 Computer Systems Programming Fall 2018 Topic 7: Concrete Data Types School of Electrical and Computer Engineering Cornell University revision: 2018-10-11-00-22 1 List CDTs 4 1.1. List CDT Interface.............................
ECE 2400 Computer Systems Programming Fall 2018 Topic 7: Concrete Data Types School of Electrical and Computer Engineering Cornell University revision: 2018-10-11-00-22 1 List CDTs 4 1.1. List CDT Interface.............................
Data Structure Analysis: A Fast and Scalable Context-Sensitive Heap Analysis
 Data Structure Analysis: A Fast and Scalable Context-Sensitive Heap Analysis Chris Lattner Vikram Adve University of Illinois at Urbana-Champaign {lattner,vadve}@cs.uiuc.edu ABSTRACT In our recent work,
Data Structure Analysis: A Fast and Scalable Context-Sensitive Heap Analysis Chris Lattner Vikram Adve University of Illinois at Urbana-Champaign {lattner,vadve}@cs.uiuc.edu ABSTRACT In our recent work,
Agenda. The main body and cout. Fundamental data types. Declarations and definitions. Control structures
 The main body and cout Agenda 1 Fundamental data types Declarations and definitions Control structures References, pass-by-value vs pass-by-references The main body and cout 2 C++ IS AN OO EXTENSION OF
The main body and cout Agenda 1 Fundamental data types Declarations and definitions Control structures References, pass-by-value vs pass-by-references The main body and cout 2 C++ IS AN OO EXTENSION OF
Pointer Analysis. What is Points-to Analysis? Outline. What is Points-to Analysis? What is Points-to Analysis? What is Pointer Analysis? Rupesh Nasre.
 Pointer Analysis What is? Ruesh Nasre. CS6843 Analysis IIT Madras Jan 2016 = a; if ( == *) { } else { } a oints to x 4 Outline What is? Introduction Pointer analysis as a DFA rolem Design decisions analysis,
Pointer Analysis What is? Ruesh Nasre. CS6843 Analysis IIT Madras Jan 2016 = a; if ( == *) { } else { } a oints to x 4 Outline What is? Introduction Pointer analysis as a DFA rolem Design decisions analysis,
Pointer Analysis. Lecture 40 (adapted from notes by R. Bodik) 5/2/2008 Prof. P. N. Hilfinger CS164 Lecture 40 1
 Pointer Analysis Lecture 40 (adapted from notes by R. Bodik) 5/2/2008 Prof. P. N. Hilfinger CS164 Lecture 40 1 2 Today Points-to analysis an instance of static analysis for understanding pointers Andersen
Pointer Analysis Lecture 40 (adapted from notes by R. Bodik) 5/2/2008 Prof. P. N. Hilfinger CS164 Lecture 40 1 2 Today Points-to analysis an instance of static analysis for understanding pointers Andersen
Calvin Lin The University of Texas at Austin
 Loop Invariant Code Motion Last Time Loop invariant code motion Value numbering Today Finish value numbering More reuse optimization Common subession elimination Partial redundancy elimination Next Time
Loop Invariant Code Motion Last Time Loop invariant code motion Value numbering Today Finish value numbering More reuse optimization Common subession elimination Partial redundancy elimination Next Time
CS 112 Introduction to Computing II. Wayne Snyder Computer Science Department Boston University
 9/5/6 CS Introduction to Computing II Wayne Snyder Department Boston University Today: Arrays (D and D) Methods Program structure Fields vs local variables Next time: Program structure continued: Classes
9/5/6 CS Introduction to Computing II Wayne Snyder Department Boston University Today: Arrays (D and D) Methods Program structure Fields vs local variables Next time: Program structure continued: Classes
IMPLEMENTATION OF SIGNAL HANDLING. CS124 Operating Systems Fall , Lecture 15
 IMPLEMENTATION OF SIGNAL HANDLING CS124 Operating Systems Fall 2017-2018, Lecture 15 2 Signal Handling UNIX operating systems allow es to register for and handle signals Provides exceptional control flow
IMPLEMENTATION OF SIGNAL HANDLING CS124 Operating Systems Fall 2017-2018, Lecture 15 2 Signal Handling UNIX operating systems allow es to register for and handle signals Provides exceptional control flow
CS61C : Machine Structures
 inst.eecs.berkeley.edu/~cs61c/su06 CS61C : Machine Structures Lecture #6: Memory Management CS 61C L06 Memory Management (1) 2006-07-05 Andy Carle Memory Management (1/2) Variable declaration allocates
inst.eecs.berkeley.edu/~cs61c/su06 CS61C : Machine Structures Lecture #6: Memory Management CS 61C L06 Memory Management (1) 2006-07-05 Andy Carle Memory Management (1/2) Variable declaration allocates
Pointers, Dynamic Data, and Reference Types
 Pointers, Dynamic Data, and Reference Types Review on Pointers Reference Variables Dynamic Memory Allocation The new operator The delete operator Dynamic Memory Allocation for Arrays 1 C++ Data Types simple
Pointers, Dynamic Data, and Reference Types Review on Pointers Reference Variables Dynamic Memory Allocation The new operator The delete operator Dynamic Memory Allocation for Arrays 1 C++ Data Types simple
Making Context-sensitive Points-to Analysis with Heap Cloning Practical For The Real World
 Making Context-sensitive Points-to Analysis with Heap Cloning Practical For The Real World Chris Lattner Apple Andrew Lenharth UIUC Vikram Adve UIUC What is Heap Cloning? Distinguish objects by acyclic
Making Context-sensitive Points-to Analysis with Heap Cloning Practical For The Real World Chris Lattner Apple Andrew Lenharth UIUC Vikram Adve UIUC What is Heap Cloning? Distinguish objects by acyclic
Semantic Analysis. How to Ensure Type-Safety. What Are Types? Static vs. Dynamic Typing. Type Checking. Last time: CS412/CS413
 CS412/CS413 Introduction to Compilers Tim Teitelbaum Lecture 13: Types and Type-Checking 19 Feb 07 Semantic Analysis Last time: Semantic errors related to scopes Symbol tables Name resolution This lecture:
CS412/CS413 Introduction to Compilers Tim Teitelbaum Lecture 13: Types and Type-Checking 19 Feb 07 Semantic Analysis Last time: Semantic errors related to scopes Symbol tables Name resolution This lecture:
Safety Checks and Semantic Understanding via Program Analysis Techniques
 Safety Checks and Semantic Understanding via Program Analysis Techniques Nurit Dor Joint Work: EranYahav, Inbal Ronen, Sara Porat Goal Find properties of a program Anti-patterns that indicate potential
Safety Checks and Semantic Understanding via Program Analysis Techniques Nurit Dor Joint Work: EranYahav, Inbal Ronen, Sara Porat Goal Find properties of a program Anti-patterns that indicate potential
Intermediate Programming, Spring 2017*
 600.120 Intermediate Programming, Spring 2017* Misha Kazhdan *Much of the code in these examples is not commented because it would otherwise not fit on the slides. This is bad coding practice in general
600.120 Intermediate Programming, Spring 2017* Misha Kazhdan *Much of the code in these examples is not commented because it would otherwise not fit on the slides. This is bad coding practice in general
Conditioned Slicing. David Jong-hoon An. May 23, Abstract
 Conditioned Slicing David Jong-hoon An May 23, 2007 Abstract Program debugging is often a tedious and difficult process that requires programmers to inspect complicated code to understand and analyze the
Conditioned Slicing David Jong-hoon An May 23, 2007 Abstract Program debugging is often a tedious and difficult process that requires programmers to inspect complicated code to understand and analyze the
CONTENTS: Array Usage Multi-Dimensional Arrays Reference Types. COMP-202 Unit 6: Arrays
 CONTENTS: Array Usage Multi-Dimensional Arrays Reference Types COMP-202 Unit 6: Arrays Introduction (1) Suppose you want to write a program that asks the user to enter the numeric final grades of 350 COMP-202
CONTENTS: Array Usage Multi-Dimensional Arrays Reference Types COMP-202 Unit 6: Arrays Introduction (1) Suppose you want to write a program that asks the user to enter the numeric final grades of 350 COMP-202
Reuse Optimization. LLVM Compiler Infrastructure. Local Value Numbering. Local Value Numbering (cont)
 LLVM Compiler Infrastructure Source: LLVM: A Compilation Framework for Lifelong Program Analysis & Transformation by Lattner and Adve Reuse Optimization Eliminate redundant operations in the dynamic execution
LLVM Compiler Infrastructure Source: LLVM: A Compilation Framework for Lifelong Program Analysis & Transformation by Lattner and Adve Reuse Optimization Eliminate redundant operations in the dynamic execution
MCS 360 Exam 2 11 November In order to get full credit, you need to show your work.
 MCS 360 Exam 2 11 November 2015 Name: Do not start until instructed to do so. In order to get full credit, you need to show your work. You have 50 minutes to complete the exam. Good Luck! Problem 1.a /15
MCS 360 Exam 2 11 November 2015 Name: Do not start until instructed to do so. In order to get full credit, you need to show your work. You have 50 minutes to complete the exam. Good Luck! Problem 1.a /15
Lecture Notes on Memory Layout
 Lecture Notes on Memory Layout 15-122: Principles of Imperative Computation Frank Pfenning André Platzer Lecture 11 1 Introduction In order to understand how programs work, we can consider the functions,
Lecture Notes on Memory Layout 15-122: Principles of Imperative Computation Frank Pfenning André Platzer Lecture 11 1 Introduction In order to understand how programs work, we can consider the functions,
Scalable Flow-Sensitive Pointer Analysis for Java with Strong Updates
 Scalable Flow-Sensitive Pointer Analysis for Java with Strong Updates Arnab De and Deepak D Souza Department of Computer Science and Automation, Indian Institute of Science, Bangalore, India {arnabde,deepakd}@csa.iisc.ernet.in
Scalable Flow-Sensitive Pointer Analysis for Java with Strong Updates Arnab De and Deepak D Souza Department of Computer Science and Automation, Indian Institute of Science, Bangalore, India {arnabde,deepakd}@csa.iisc.ernet.in
Class Information ANNOUCEMENTS
 Class Information ANNOUCEMENTS Third homework due TODAY at 11:59pm. Extension? First project has been posted, due Monday October 23, 11:59pm. Midterm exam: Friday, October 27, in class. Don t forget to
Class Information ANNOUCEMENTS Third homework due TODAY at 11:59pm. Extension? First project has been posted, due Monday October 23, 11:59pm. Midterm exam: Friday, October 27, in class. Don t forget to
Abstract Data Types. Lecture 05 Summary. Abstract Data Types Structures in C 1/26/2009. Slides by Mark Hancock (adapted from notes by Craig Schock)
 Abstract Data Types 1 Lecture 05 Summary Abstract Data Types Structures in C 2 1 By the end of this lecture, you will be able to describe the main components of an abstract data type. You will also be
Abstract Data Types 1 Lecture 05 Summary Abstract Data Types Structures in C 2 1 By the end of this lecture, you will be able to describe the main components of an abstract data type. You will also be
CS 261: Data Structures. Dynamic Arrays. Introduction
 CS 261: Data Structures Dynamic Arrays Introduction Arrays Core data structure Example: double arraybag[100]; struct Students{ int count; }; char initials[2]; 2 Positives: Arrays -- Pros and Cons Simple
CS 261: Data Structures Dynamic Arrays Introduction Arrays Core data structure Example: double arraybag[100]; struct Students{ int count; }; char initials[2]; 2 Positives: Arrays -- Pros and Cons Simple
Dependence and Data Flow Models. (c) 2007 Mauro Pezzè & Michal Young Ch 6, slide 1
 Dependence and Data Flow Models (c) 2007 Mauro Pezzè & Michal Young Ch 6, slide 1 Why Data Flow Models? Models from Chapter 5 emphasized control Control flow graph, call graph, finite state machines We
Dependence and Data Flow Models (c) 2007 Mauro Pezzè & Michal Young Ch 6, slide 1 Why Data Flow Models? Models from Chapter 5 emphasized control Control flow graph, call graph, finite state machines We
ECE 2400 Computer Systems Programming Fall 2018 Topic 8: Complexity Analysis
 ECE 2400 Computer Systems Programming Fall 2018 Topic 8: Complexity Analysis School of Electrical and Computer Engineering Cornell University revision: 2018-10-11-00-23 1 Analyzing Algorithms 2 1.1. Linear
ECE 2400 Computer Systems Programming Fall 2018 Topic 8: Complexity Analysis School of Electrical and Computer Engineering Cornell University revision: 2018-10-11-00-23 1 Analyzing Algorithms 2 1.1. Linear
Practical Virtual Method Call Resolution for Java
 Practical Virtual Method Call Resolution for Java Sable TR 1999-2 10/4/99 1 Introduction Objective To determine at compile time a call graph with as few nodes and edges as possible Background.Soot Framework
Practical Virtual Method Call Resolution for Java Sable TR 1999-2 10/4/99 1 Introduction Objective To determine at compile time a call graph with as few nodes and edges as possible Background.Soot Framework
