Mapping Non-conventional Extensions of Genetic Programming
|
|
|
- Brooke Jefferson
- 6 years ago
- Views:
Transcription
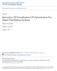
1 Unconventional Computation UC 06 York, 4-8 September 2006, Mapping Non-conventional Extensions of Genetic Programming W. B. Langdon Department of Computer Science, University of Essex, UK Abstract. Conventional genetic programming research excludes memory and iteration. We have begun an extensive analysis of the space through which GP or other unconventional AI approaches search and extend it to consider explicit program stop instructions (T8) and any time models (T). We report halting probability, run time and functionality (including entropy of binary functions) of both halting and anytime programs. Turing complete program fitness landscapes, even with halt, scale poorly. Introduction Recent work on strengthening the theoretical underpinnings of genetic programming (GP) has considered how GP searches its fitness landscape []. Results gained on the space of all possible programs are applicable to both GP and other search based automatic programming techniques. We have proved convergence results for the two most important forms of GP, i.e. trees (without side effects) and linear GP. Few researchers allow their GP s to include iteration or recursion. Indeed there are only about 60 papers (out of 4000) where loops or recursion have been included in GP [2, Appendix B]. Without some form of looping and memory there are algorithms which cannot be represented and so GP stands no chance of evolving them. We have recently shown [] in the limit of large T programs (cf. Figure ) that: The T halting probability falls sub-linearly with program length. Our models suggest the chance of not looping falls as O(length /2 ). Whilst including both non-looping and programs which escape loops we observe O(length /4 ). Memory (2 bytes=96bits) I/O Registers Overflow flag CPU Fig.. T and T8 have the same bit addressable memory and input output
2 Run time of terminating programs grows sub-linearly with program length. Again both mathematical and Markov models are confirmed by experiments and show run time of non-looping programs grows as O(length /2 ). Similarly, including both non-looping and programs which exit loops, for the T, we observe run time O(length /4 ). Despite the fraction of programs falling to zero, the shear number of programs, means the number of halting T programs grows exponentially with their size. Experimentally the types of loop and their length varies with the size of T program. Long programs are dominated by programs which fall into, and cannot escape from, one of two types of loop. In both cases the loops are very tight. So (in our experiments) even for the longest programs (we considered programs of up to 6 million instruction) on average no more than a few hundred different instructions are executed. It is important to stress that these, and our previous results, apply not only to genetic programming, but to any other unconventional computation embedded in the same representation. While the T computer is Turing complete, [2, Appendix A], these results are not universal. The T was chosen since it is a minimal Turing complete von Neumann architecture computer with strong similarities with both real computers and linear genetic programming [4]. At the 2006 Dagstuhl Theory of Evolutionary Algorithms [Seminar 0606] the question of the generality of the T was raised. In Section 4 we shall show that the impact of the addition of an explicit halt instruction is, as predicted, to dramatically change the scaling laws. With the T8 computer (T+halt) almost all programs stop before executing more than a few instructions. Sections 5 and 6 consider a third alterative halting technique: the any time algorithms [5]. In this regime, each program is given a fixed quantum of time and then aborted. The program s answer is read from the output register regardless of where its execution had reached. These last two experimental sections (5 and 6) consider program functionality, rather than just if they stop or not. 2 T and T8 Example Turing Complete Computers To test our theoretical results we need a simple Turing complete system. In [] we introduced the T seven instruction CPU, itself based on the Kowalczy F-4 minimal instruction set computer cf. appendix of [2]. The T8 adds a single halt instruction to the T instruction set. The T8 (see Figure and Table ) consists of: directly accessed bit addressable memory (there are no special registers), a single arithmetic operator (ADD), an unconditional JUMP, a conditional Branch if overflow flag is Set (BVS) jump, four copy instructions and the program halt. COPY PC allows a programmer to save the current program address for use as the return address in subroutine calls, whilst the direct and indirect addressing modes allow access to stacks and arrays. 2
3 Table. T8 Turing Complete Instruction Set Every ADD either sets or clears the overflow bit v. COPY PC and JUMP use just enough bits to address each program instruction. LDi and STi, treat one of their arguments as the address of the data. (LDi and STi data addresses are 4 or 8 bits.) JUMP addresses are moded with program length. Programs terminate either by executing their last instruction (which must not be a jump) or by executing a HALT. Instruction args operation ADD A + B C v set BVS #addr pc if v= COPY 2 A B LDi B STi 2 COPY PC pc A JUMP addr pc HALT 0 pc end In Section 4 eight bit byte data words are used, whilst Sections 5 and 6 both use four bit nibbles. The number of bits in address words is just big enough to be able to address every instruction in the program. E.g., if the program is 00 instructions, then BVS, JUMP and COPY PC instructions use 9 bits. These experiments use 2 bytes (96 bits) of memory (plus the overflow flag). Experimental Method There are too many programs to test all of them, instead we gather representative statistics about those of a particular length by randomly sampling. By sampling a range of lengths we create a picture of the whole search space. Note we do not bias the sampling in favour of short programs. One hundred thousand programs of each of various lengths ( instructions) are each run from a random starting point (NB not necessarily from the start) with random inputs, until either they execute a HALT, reach their last instruction and stop, an infinite loop is detected or an individual instruction has been executed more than 00 times. (In practise we can detect almost all infinite loops by keeping track of the machine s contents, i.e. memory and overflow bit. We can be sure the loop is infinite, if the contents is identical to what it was when the instruction was last executed.) The program s execution paths are then analysed. Statistics are gathered on the number of instructions executed, normal program terminations, type of loops, length of loops, start of first loop, etc. 4 Terminating T8 Programs Figure 2 shows, as expected, inclusion of the HALT instruction dramatically changes the nature of the search space. Almost all T8 programs stop, with only a small fraction looping. This is the opposite of the T (most programs loop). Figures and 4 show the run time of terminating T8 programs. In both programs stopped by reaching their end (Figure ) and by a HALT instruction (Figure 4), the fraction of programs falls exponentially fast with run time. In both cases, it falls most rapidly with short programs and appears to reach a limit of (/8) length for longer programs. A decay rate of /8 would be expected if
4 stopped by Halt infinite loop stopped by end of prog possibly infinite loop Number of programs e+06 e+0 Program length Fig. 2. Almost all short T8 programs are stopped by reaching their end (*). This proportion falls rapidly (about /length) towards zero. Longer programs are mostly stopped by a halt instruction. The fraction of programs trapped in loops (+ and ) appears to settle near a limit of in 50. programs ran until they reach a HALT instruction. I.e. to a first approximation, run time of long terminating T8 programs can be estimated by ignoring the possibility of loops. This gives a geometric distribution and so an expected run time of 8 instructions regardless of program size. For all but very short programs, Figure 5 confirms the mean is indeed about 8. For a geometric distribution the standard deviation is.48 (also consistent with measurements) so almost all T8 programs terminate after executing no more than instructions (mean+σ). Again this is in sharp contrast with the T, where long terminating T programs run many instruction, and so perhaps may do something more useful. 5 T8 Functions and Any Time Programs The introduction of Turing completeness into genetic programming raises the halting problem, in particular how to assign fitness to a program which may loop indefinitely [6]. Here we look at any time algorithms [5] implemented by T8 computers. I.e. we insist all program halt after a certain number of instructions. Then we extract an answer from the output register regardless of whether it terminated or was aborted. (The input and output registers are mapped to overlapping memory locations, which the CPU treats identically to the rest of the memory, cf. Figure.) We allow the T8 5 instructions. (5 was chosen since by then we expect all but 0.% of non-looping T8 programs to have stopped, cf. Figure 4.) 4
5 Normalised frequency (=) Prog Len= Prog Len= Prog Len=5 Prog Len= Prog Len=6 Prog Len=2 len 255 or more /8 geometric decrease Instructions executed Fig.. Distribution of frequency of normally stopping T8 programs by their run time. Noisy data suppressed. To ease comparison, all data has been vertically rescaled so that data at the left lie on top of each other. Distributions fit geometric decay. As program gets longer the decay constant tends to / Prog Len= Prog Len= Prog Len=5 Prog Len= Prog Len=6 Prog Len=2 len 255 or more /8 geometric decrease Count Instructions executed Fig. 4. Distribution of frequency of HALTed T8 programs by their run time. There is an geometric fall in frequency at all lengths, however for lengths < 2 the decay is faster than (-/8). For longer random T8 programs, the decay constant tends to /8. 5
6 2 0 Stopped by end of program HALTed Instructions in possibly infinite loop Instructions in infinite loop Program instructions executed e+06 e+0 T8 Program length Fig. 5. Mean number of T8 instructions obeyed by terminating programs ( and ) and length of loops ( and +) v. program size. Noisy data suppressed. Data are consistent with long random T8 programs having a geometric distribution, with mean of 8 and thus standard deviation is 8 2 /8 =.48. Final loops in non-terminating programs are even tighter than in T [, Fig. 9]. In this section and Section 6 we look at functions of two inputs, by defining two input registers (occupying adjacent 4 bit nibbles) and looking at the data left in memory after the program stops (or is stopped). In these sections, the data word size is 4 bits. Each random program is started from a chosen random starting point 256 times just as before, except the two input registers are given in turn each of their possible values. To avoid excessive run time and since we are now running each program 256 times (rather than once) the number of programs tested per length is reduced from to 000. In addition to studying the random functions generated by the T8 we also study the variation between individual programs runs with each of the 256 different inputs and how this varies as the program runs. We use Shannon s [] information theoretic entropy measure S = k p klog 2 (p k ), to quantify the difference between the state of the T8 (programme counter, overflow bit and memory) on different runs, with different inputs, at the same time. 5. Any Time T8 Entropy We have two confounding effects. We measure the change in the variation between T8 processors as they run the same program (from different inputs), so a major influence is whether a particular processor is still running or has obeyed a HALT instruction or reached the end of its program. For simplicity when cal- 6
7 8 All LOOP (229, noise added) others (42) max_entropy(x) 6 Entropy (bits) Test cases still running after 5 instructions Fig. 6. Entropy of T8 programs of instructions still running at least one test case after 5 time steps. Noise is added to + data to spread them. culating the entropy of a mixture of stopped and still executing programs, the stopped programs are treated as if they were all in the same stopped state. This means in the graphs that follow, the number of runs of a program that reach the t th instruction has an impact of the entropy as well as (for example) the difference between the contents of memory. (Remember apart from the input register, each of the 256 runs, start in the same, random, state.) To illustrate this, Figure 6 shows the 229 (+) of 000 T8 programs of instructions which always get stuck in a loop tend to have a high entropy. In contrast the entropy of the remaining 42 programs circ strongly depends upon how many runs (test cases) are still executing. (Figure 6 takes a snap shot after 5 instructions have been obeyed). It is clear the number of active test cases has a strong influence on the variation in memory contents etc. between test cases. I.e. entropy, in most short T8 programs, is as large as possible, given the number of test cases still running. This is consistent with the fact that most short programs implement the identity function, see Figure 9, which has maximum entropy. Figure shows the average number of test cases still running up to instruction 5. The shortest programs tend to stop or loop immediately. Only those still looping show on Figure. Short programs which loop on one test case tend to loop on all of them, giving the almost constant plots for short programs seen in Figure. Longer random programs, tend to run for longer and have more variation between the number of instructions they execute on the different test cases. Figure 8 shows there is a corresponding behaviour in terms of variation between the same program given different inputs. I.e., loops are needed to keep small programs running and compact loops mean small programs tend to keep
8 Program test cases still running length lengths 89 to Instructions obeyed Fig.. Mean number of test cases where T8 program has not HALTed or stopped. 000 random T8 programs of different lengths. their variability. This gives the almost constant high entropy plots for short programs seen in Figure 8. However longer random programs tend to run for longer and use more instructions. More random instructions actually means that the memory etc. tends to behave the same on every input and this convergence increases as the programs run for more time. Indeed there is also less variation in average behaviour with longer random T8 programs. Leading to the general decrease in entropy with run time seen in Figure 8. In the next section we will restrict ourselves to just looking at the I/O registers rather than the whole of memory, that is the notion of programs as implementing functions which map from inputs to output. However we shall see the two views: entropy and functionality, are consistent. 5.2 Any Time T8 Convergence of Functions There are = possible functions of two 4 bit inputs and an 8 bit output. However, as shown by Figure 9, uniformly chosen random programs of a given length sample these functions very unequally. (This is also true of the T, cf. Figures 2 and ). In particular the identity function and the 256 functions which return constants are much more likely than others. Figure 9 also plots two variations on the identity (where the least significant or most significant nibble implement a 4 bit identity function) and two cases of 4 bit constants. In these four cases the other 4 bits are free to vary. Note that while they represent a huge number of functions they are less frequent than either of their 8 bit namesakes. 8
9 Mean entropy (bits) length lengths 89 to Instructions obeyed Fig. 8. Evolution of variation between test cases in 000 random T8 programs of different lengths. Same programs as in Figure Count (of 000) 0 Identity Constant Constant lsn Constant msn Identity lsn Identity msn e+06 e+0 T8 program length Fig. 9. Frequency of common functions implemented by random T8 programs of different lengths by 5 instruction cycles. Data are noisy due to sample size, but the trend to falling proportion of functions, except the constants, with program size can be seen. 9
10 The rise in the frequency of the constant functions and fall in the identity function with increasing program size (Figure 9) are consistent with the corresponding fall in entropy seen in Figure 8. (The same will be seen in the next section for the T, cf. Figures 2 and 4.) 6 T Functions and Any Time Programs Having shown the success of the any time approach, we return to the T. The measurements in this section are based on running the T on 256 test cases as in Section 5. However since without a HALT instruction, the T programs tend to run for much longer, we increase the any time limit from 5 to 000 instructions. Figure 0 confirms removing HALT does indeed mean most programs run up to the any time limit. Figure 0 relates to all 256 runs of each random program. Whilst the error bars (top solid line) show on average there is some variation between identical programs starting with different inputs for middle sized programs both very large and very small programs have the same (any time) run time. This suggests most big T programs loop regardless of their input. Whilst short programs halt whatever their input. Only at intermediate lengths can the input switch random programs looping/halting behaviour. The diagonal line shows that, for program shorter than , the fraction of runs which stop falls approximately as / length, as expected. (For even longer T programs, the 000 instruction limit aborts a few programs even though they are not stuck in loops.) Figure shows that the fraction of programs which never loop, falls as O(/ length), as we found previously []. Figure plots combined behaviour over 256 test cases rather than a single run and the data word size is half that reported in []. However, initially we have similar results: the fraction of T programs which do not loop falls with program length. Notice that for longer programs the fraction does not continue towards zero. This is because we now use the any time approach to abort non-terminated programs and so a few programs (9 4 out of 000) are stopped early, when they might have continued to find themselves in loops. As expected, when we allow the T to run for longer the variation between test cases reduces and there is an increased tendency for programs to become independent of their inputs. If a program s output does not depend on its input, i.e. all 256 test cases yield the same answer, then it effectively returns a constant. In Figure 2 the constant functions ( ) are those where the program s output (after up to 000 instructions) does not depend upon its inputs. Notice the rise in the proportion of constants with program length, even though, in most cases, each program runs exactly instructions. In [] we found that longer T programs tend to obey more random instructions (about length) before they get stuck in tight loops. We suggest that the rise in constants with program length in Figure 2, is due to the greater loss of information in longer random sequence of non-looping instructions before a tight loop is entered. Also, the loss of knowledge about the input registers in the 0
11 000 50% Mean instructions run 00 0 Instructions run (min, mean, max) Fraction test cases not running to % length -/ % e+06 e+0 T program length 20% 0% 5% 2% % 0.5% 0.2% 0.% 0.05% Fig. 0. Run time on 256 test cases of 000 random T programs of each of a variety of lengths. Some short programs run to their end and stop but almost all longer programs run up to the limit of 000 instructions on all test cases. 000 no loop all loop mixed 800 Count (out of 000) e+06 e+0 T (anytime 000) Program length Fig.. Looping characteristics of Random T programs on 256 test cases. All programs still running are aborted after 000 instructions. Error bars show standard error.
12 000 Count (of 000) 00 0 Identity Constant Constant lsn Constant msn Identity lsn Identity msn e+06 e+0 T program length Fig. 2. Variation of some common functions implemented by T with program length. Note, except for the 256 constant functions, after 000 instructions most of the functions considered in Figure 9 become rare Frequency 0. Identity Constant Constant lsn Constant msn Identity lsn Identity msn e+06 e+0 T program length Fig.. Variation of some common functions implemented by T with program length. As Figure 2 except we include only programs which do not loop at all. 2
13 final loop is usually either small or repeating the same instructions many times does not loose any more information. This explanation is reinforced if we look at only the programs which did not loop. Figure shows the rise in the proportion of constants with program length is even more pronounced. Whilst Figure 5 shows, if loops are excluded, in most cases variation between different input values falls rapidly to zero. Figures 4 and 5 also show test cases become more similar as the programs run. However programs which become locked into loops have less of a tendency to converge than those which are not looping. I.e. loops actually lock in variation and without them random programs are dissipative and so implement only the 2 n constant functions. Discussion Of course the undecidability of the Halting problem has long been known, however it appears to have become an excuse for not looking at unconventional approaches to evolve more powerful than O() functions. More recently work by Chaitin [8] started to consider a probabilistic information theoretic approach. However this is based on self-delimiting Turing machines (particularly the Chaitin machines ) and has lead to a non-zero value for Ω [9] and postmodern metamathematics. The special self-delimiting approach means halting programs cannot be extended and so each blocks out an exponentially large part of the search space. This can give very different statistics for the whole space. Our approach is firmly based on the von Neumann architecture, which for practical purposes is Turing complete. Indeed the T is similar to the linear genetic programming area of existing Turing complete genetic programming research. Real computer systems lose information. We had expected this to lead to further convergence properties in programming languages with iteration and memory. However these results hint at strong differences between looping and non-looping programs. It appears that many tight loops are non-dissipative, in the sense that they cycle the computer through the same sequence of states indefinitely. In contrast, non-looping programs continue to explore the computer s state space but in doing so they become disconnected from where they started, in that they arrive at the same state regardless of where they started. This means they are useless, since they implement a constant. Requiring input and output to be via fixed width registers is limiting. Variable sized I/O (cf. Turing tapes) is needed in general. Real CPUs achieve this by multiplexing their use of I/O registers. May be this too can be modelled. It may be possible to obtain further results for the space of von Neumann architecture computer programs by separating the initial execution from looping. These initial experiments suggest the program path (i.e. conditional branches, jumps, etc.) of the program is initially not so important and that our earlier models on linear programs might be relevant. If, in other machines, most loops are also drawn from only a small number of types (in the case of T only two) it may be possible to build small predictive models of loop formation and execution.
14 Entropy (bits) length 2 lengths 255 to Instructions obeyed Fig. 4. Average reduction in variation between test cases for 000 random T programs of each of a variety of lengths run on 256 test cases, up to 000 steps. The smooth averages conceal strong peaks in the data at 0 (constants),, 2,, 4, 5 and 8 bits (e.g. identity). 8 lengths, T Program lengths 89 to Entropy (bits) 5 4 length L= Instructions obeyed Fig. 5. As Figure 4 except we include only runs which did not loop on any test case. 4
15 Only a tiny fraction of the whole program is used. The rest has absolutely no effect. In future it may be possible to derive bounds on the effectiveness of testing (w.r.t. ISO 900 requirements) based on code coverage. 8 Conclusions The introduction of an explicit HALT instruction leads to almost all programs stopping. The geometric distribution gives an expected run time of the inverse of the frequency with which the HALT is used. This gives, in these experiments, very short run times and few interesting programs. We also explored the any time approach, looking particularly at common functions and information theoretic measures of running programs. Entropy clearly illustrates a difference between non-dissipative looping programs and dissipative non-looping programs. There is some evidence that large random non-looping programs converge on the constant functions, however, possibly due to the size of the available memory, this is not as clear as we expected. This needs further investigation. We anticipate that detailed mathematical and Markov models could be applied to both the T and T8 any time approaches. While genetic programming is perhaps the most advanced automatic programming technique, we have been analysing the fundamentals questions concerning the nature of programming search spaces. Therefore these results apply to any form of unconventional computing technique using this or similar representations which seeks to use search to create programs. Acknowledgements I would like to thank Dagstuhl Seminar Funded by EPSRC GR/T24/0. References. W. B. Langdon and R. Poli. Foundations of Genetic Programming. Springer W. B. Langdon and R. Poli. On Turing complete T and MISC F-4 program fitness landscapes. Technical Report CSM-445, Computer Science, Uni. Essex, UK, The halting probability in von Neumann architectures. W. B. Langdon and R. Poli. In Collet et al. editors, EuroGP-2006 LNCS 905, pages Springer. 4. Wolfgang Banzhaf, Peter Nordin, Robert E. Keller, and Frank D. Francone. Genetic Programming An Introduction. Morgan Kaufmann, Astro Teller. Genetic programming, indexed memory, the halting problem, and other curiosities. In FLAIRS, pages 20 24, Pensacola, Florida, 994. IEEE Press. 6. S. R. Maxwell III. Experiments with a coroutine model for genetic programming. In 994 IEEE World Congress on Computational Intelligence, pp4 4a.. Claude E. Shannon and Warren Weaver. The Mathematical Theory of Communication. The University of Illinois Press, Urbana, G. J. Chaitin. An algebraic equation for the halting probability. In R. Herken, ed., The Universal Turing Machine A Half-Century Survey, pp OUP, C. S. Calude, M. J. Dinneen and C-K Shu. Computing a glimpse of randomness. Experimental Mathematics, ():6 0,
Mapping Non-conventional Extensions of Genetic Programming
 Revision :.3 To be submitted to Special Issue of Natural Computation Mapping Non-conventional Extensions of Genetic Programming W. B. Langdon and R. Poli Department of Computer Science, University of Essex,
Revision :.3 To be submitted to Special Issue of Natural Computation Mapping Non-conventional Extensions of Genetic Programming W. B. Langdon and R. Poli Department of Computer Science, University of Essex,
Mapping Non-conventional Extensions of Genetic Programming
 Preprint Natural Computing (28) ():2-4, DOI./s4--944-x Mapping Non-conventional Extensions of Genetic Programming W. B. Langdon and R. Poli Department of Computer Science, University of Essex, UK Abstract.
Preprint Natural Computing (28) ():2-4, DOI./s4--944-x Mapping Non-conventional Extensions of Genetic Programming W. B. Langdon and R. Poli Department of Computer Science, University of Essex, UK Abstract.
Leave-One-Out Support Vector Machines
 Leave-One-Out Support Vector Machines Jason Weston Department of Computer Science Royal Holloway, University of London, Egham Hill, Egham, Surrey, TW20 OEX, UK. Abstract We present a new learning algorithm
Leave-One-Out Support Vector Machines Jason Weston Department of Computer Science Royal Holloway, University of London, Egham Hill, Egham, Surrey, TW20 OEX, UK. Abstract We present a new learning algorithm
1 More configuration model
 1 More configuration model In the last lecture, we explored the definition of the configuration model, a simple method for drawing networks from the ensemble, and derived some of its mathematical properties.
1 More configuration model In the last lecture, we explored the definition of the configuration model, a simple method for drawing networks from the ensemble, and derived some of its mathematical properties.
Big Mathematical Ideas and Understandings
 Big Mathematical Ideas and Understandings A Big Idea is a statement of an idea that is central to the learning of mathematics, one that links numerous mathematical understandings into a coherent whole.
Big Mathematical Ideas and Understandings A Big Idea is a statement of an idea that is central to the learning of mathematics, one that links numerous mathematical understandings into a coherent whole.
Genetic Algorithms and Genetic Programming. Lecture 9: (23/10/09)
 Genetic Algorithms and Genetic Programming Lecture 9: (23/10/09) Genetic programming II Michael Herrmann michael.herrmann@ed.ac.uk, phone: 0131 6 517177, Informatics Forum 1.42 Overview 1. Introduction:
Genetic Algorithms and Genetic Programming Lecture 9: (23/10/09) Genetic programming II Michael Herrmann michael.herrmann@ed.ac.uk, phone: 0131 6 517177, Informatics Forum 1.42 Overview 1. Introduction:
Chapter 2 Basic Structure of High-Dimensional Spaces
 Chapter 2 Basic Structure of High-Dimensional Spaces Data is naturally represented geometrically by associating each record with a point in the space spanned by the attributes. This idea, although simple,
Chapter 2 Basic Structure of High-Dimensional Spaces Data is naturally represented geometrically by associating each record with a point in the space spanned by the attributes. This idea, although simple,
Genetic Programming Part 1
 Genetic Programming Part 1 Evolutionary Computation Lecture 11 Thorsten Schnier 06/11/2009 Previous Lecture Multi-objective Optimization Pareto optimality Hyper-volume based indicators Recent lectures
Genetic Programming Part 1 Evolutionary Computation Lecture 11 Thorsten Schnier 06/11/2009 Previous Lecture Multi-objective Optimization Pareto optimality Hyper-volume based indicators Recent lectures
Previous Lecture Genetic Programming
 Genetic Programming Previous Lecture Constraint Handling Penalty Approach Penalize fitness for infeasible solutions, depending on distance from feasible region Balanace between under- and over-penalization
Genetic Programming Previous Lecture Constraint Handling Penalty Approach Penalize fitness for infeasible solutions, depending on distance from feasible region Balanace between under- and over-penalization
Course notes for Data Compression - 2 Kolmogorov complexity Fall 2005
 Course notes for Data Compression - 2 Kolmogorov complexity Fall 2005 Peter Bro Miltersen September 29, 2005 Version 2.0 1 Kolmogorov Complexity In this section, we present the concept of Kolmogorov Complexity
Course notes for Data Compression - 2 Kolmogorov complexity Fall 2005 Peter Bro Miltersen September 29, 2005 Version 2.0 1 Kolmogorov Complexity In this section, we present the concept of Kolmogorov Complexity
Fast Automated Estimation of Variance in Discrete Quantitative Stochastic Simulation
 Fast Automated Estimation of Variance in Discrete Quantitative Stochastic Simulation November 2010 Nelson Shaw njd50@uclive.ac.nz Department of Computer Science and Software Engineering University of Canterbury,
Fast Automated Estimation of Variance in Discrete Quantitative Stochastic Simulation November 2010 Nelson Shaw njd50@uclive.ac.nz Department of Computer Science and Software Engineering University of Canterbury,
(Refer Slide Time: 1:40)
 Computer Architecture Prof. Anshul Kumar Department of Computer Science and Engineering, Indian Institute of Technology, Delhi Lecture - 3 Instruction Set Architecture - 1 Today I will start discussion
Computer Architecture Prof. Anshul Kumar Department of Computer Science and Engineering, Indian Institute of Technology, Delhi Lecture - 3 Instruction Set Architecture - 1 Today I will start discussion
DESIGN AND ANALYSIS OF ALGORITHMS. Unit 1 Chapter 4 ITERATIVE ALGORITHM DESIGN ISSUES
 DESIGN AND ANALYSIS OF ALGORITHMS Unit 1 Chapter 4 ITERATIVE ALGORITHM DESIGN ISSUES http://milanvachhani.blogspot.in USE OF LOOPS As we break down algorithm into sub-algorithms, sooner or later we shall
DESIGN AND ANALYSIS OF ALGORITHMS Unit 1 Chapter 4 ITERATIVE ALGORITHM DESIGN ISSUES http://milanvachhani.blogspot.in USE OF LOOPS As we break down algorithm into sub-algorithms, sooner or later we shall
6.856 Randomized Algorithms
 6.856 Randomized Algorithms David Karger Handout #4, September 21, 2002 Homework 1 Solutions Problem 1 MR 1.8. (a) The min-cut algorithm given in class works because at each step it is very unlikely (probability
6.856 Randomized Algorithms David Karger Handout #4, September 21, 2002 Homework 1 Solutions Problem 1 MR 1.8. (a) The min-cut algorithm given in class works because at each step it is very unlikely (probability
ITERATIVE COLLISION RESOLUTION IN WIRELESS NETWORKS
 ITERATIVE COLLISION RESOLUTION IN WIRELESS NETWORKS An Undergraduate Research Scholars Thesis by KATHERINE CHRISTINE STUCKMAN Submitted to Honors and Undergraduate Research Texas A&M University in partial
ITERATIVE COLLISION RESOLUTION IN WIRELESS NETWORKS An Undergraduate Research Scholars Thesis by KATHERINE CHRISTINE STUCKMAN Submitted to Honors and Undergraduate Research Texas A&M University in partial
Automatic Programming with Ant Colony Optimization
 Automatic Programming with Ant Colony Optimization Jennifer Green University of Kent jg9@kent.ac.uk Jacqueline L. Whalley University of Kent J.L.Whalley@kent.ac.uk Colin G. Johnson University of Kent C.G.Johnson@kent.ac.uk
Automatic Programming with Ant Colony Optimization Jennifer Green University of Kent jg9@kent.ac.uk Jacqueline L. Whalley University of Kent J.L.Whalley@kent.ac.uk Colin G. Johnson University of Kent C.G.Johnson@kent.ac.uk
(Refer Slide Time: 1:27)
 Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture 1 Introduction to Data Structures and Algorithms Welcome to data
Data Structures and Algorithms Dr. Naveen Garg Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture 1 Introduction to Data Structures and Algorithms Welcome to data
Real Numbers finite subset real numbers floating point numbers Scientific Notation fixed point numbers
 Real Numbers We have been studying integer arithmetic up to this point. We have discovered that a standard computer can represent a finite subset of the infinite set of integers. The range is determined
Real Numbers We have been studying integer arithmetic up to this point. We have discovered that a standard computer can represent a finite subset of the infinite set of integers. The range is determined
Bits, Words, and Integers
 Computer Science 52 Bits, Words, and Integers Spring Semester, 2017 In this document, we look at how bits are organized into meaningful data. In particular, we will see the details of how integers are
Computer Science 52 Bits, Words, and Integers Spring Semester, 2017 In this document, we look at how bits are organized into meaningful data. In particular, we will see the details of how integers are
ARTISTIC PATTERNS: FROM RANDOMNESS TO SYMMETRY
 Symmetry: Culture and Science Vol. 26, No. x, page_first-page_last, 2015 ARTISTIC PATTERNS: FROM RANDOMNESS TO SYMMETRY Douglas Dunham1,*, John Shier2 Mathematician, (b. Pasadena, Calif., U.S.A., 1938).
Symmetry: Culture and Science Vol. 26, No. x, page_first-page_last, 2015 ARTISTIC PATTERNS: FROM RANDOMNESS TO SYMMETRY Douglas Dunham1,*, John Shier2 Mathematician, (b. Pasadena, Calif., U.S.A., 1938).
Administrivia. Next Monday is Thanksgiving holiday. Tuesday and Wednesday the lab will be open for make-up labs. Lecture as usual on Thursday.
 Administrivia Next Monday is Thanksgiving holiday. Tuesday and Wednesday the lab will be open for make-up labs. Lecture as usual on Thursday. Lab notebooks will be due the week after Thanksgiving, when
Administrivia Next Monday is Thanksgiving holiday. Tuesday and Wednesday the lab will be open for make-up labs. Lecture as usual on Thursday. Lab notebooks will be due the week after Thanksgiving, when
Concurrent/Parallel Processing
 Concurrent/Parallel Processing David May: April 9, 2014 Introduction The idea of using a collection of interconnected processing devices is not new. Before the emergence of the modern stored program computer,
Concurrent/Parallel Processing David May: April 9, 2014 Introduction The idea of using a collection of interconnected processing devices is not new. Before the emergence of the modern stored program computer,
Challenge Problem 5 - The Solution Dynamic Characteristics of a Truss Structure
 Challenge Problem 5 - The Solution Dynamic Characteristics of a Truss Structure In the final year of his engineering degree course a student was introduced to finite element analysis and conducted an assessment
Challenge Problem 5 - The Solution Dynamic Characteristics of a Truss Structure In the final year of his engineering degree course a student was introduced to finite element analysis and conducted an assessment
Math 7 Glossary Terms
 Math 7 Glossary Terms Absolute Value Absolute value is the distance, or number of units, a number is from zero. Distance is always a positive value; therefore, absolute value is always a positive value.
Math 7 Glossary Terms Absolute Value Absolute value is the distance, or number of units, a number is from zero. Distance is always a positive value; therefore, absolute value is always a positive value.
Assignment 4: CS Machine Learning
 Assignment 4: CS7641 - Machine Learning Saad Khan November 29, 2015 1 Introduction The purpose of this assignment is to apply some of the techniques learned from reinforcement learning to make decisions
Assignment 4: CS7641 - Machine Learning Saad Khan November 29, 2015 1 Introduction The purpose of this assignment is to apply some of the techniques learned from reinforcement learning to make decisions
Unit 1 Chapter 4 ITERATIVE ALGORITHM DESIGN ISSUES
 DESIGN AND ANALYSIS OF ALGORITHMS Unit 1 Chapter 4 ITERATIVE ALGORITHM DESIGN ISSUES http://milanvachhani.blogspot.in USE OF LOOPS As we break down algorithm into sub-algorithms, sooner or later we shall
DESIGN AND ANALYSIS OF ALGORITHMS Unit 1 Chapter 4 ITERATIVE ALGORITHM DESIGN ISSUES http://milanvachhani.blogspot.in USE OF LOOPS As we break down algorithm into sub-algorithms, sooner or later we shall
A Singular Example for the Averaged Mean Curvature Flow
 To appear in Experimental Mathematics Preprint Vol. No. () pp. 3 7 February 9, A Singular Example for the Averaged Mean Curvature Flow Uwe F. Mayer Abstract An embedded curve is presented which under numerical
To appear in Experimental Mathematics Preprint Vol. No. () pp. 3 7 February 9, A Singular Example for the Averaged Mean Curvature Flow Uwe F. Mayer Abstract An embedded curve is presented which under numerical
Evolutionary Lossless Compression with GP-ZIP
 Evolutionary Lossless Compression with GP-ZIP Ahmad Kattan and Riccardo Poli Abstract In this paper we propose a new approach for applying Genetic Programming to lossless data compression based on combining
Evolutionary Lossless Compression with GP-ZIP Ahmad Kattan and Riccardo Poli Abstract In this paper we propose a new approach for applying Genetic Programming to lossless data compression based on combining
6.001 Notes: Section 31.1
 6.001 Notes: Section 31.1 Slide 31.1.1 In previous lectures we have seen a number of important themes, which relate to designing code for complex systems. One was the idea of proof by induction, meaning
6.001 Notes: Section 31.1 Slide 31.1.1 In previous lectures we have seen a number of important themes, which relate to designing code for complex systems. One was the idea of proof by induction, meaning
DOWNLOAD PDF BIG IDEAS MATH VERTICAL SHRINK OF A PARABOLA
 Chapter 1 : BioMath: Transformation of Graphs Use the results in part (a) to identify the vertex of the parabola. c. Find a vertical line on your graph paper so that when you fold the paper, the left portion
Chapter 1 : BioMath: Transformation of Graphs Use the results in part (a) to identify the vertex of the parabola. c. Find a vertical line on your graph paper so that when you fold the paper, the left portion
Some Applications of Graph Bandwidth to Constraint Satisfaction Problems
 Some Applications of Graph Bandwidth to Constraint Satisfaction Problems Ramin Zabih Computer Science Department Stanford University Stanford, California 94305 Abstract Bandwidth is a fundamental concept
Some Applications of Graph Bandwidth to Constraint Satisfaction Problems Ramin Zabih Computer Science Department Stanford University Stanford, California 94305 Abstract Bandwidth is a fundamental concept
CS 24: INTRODUCTION TO. Spring 2018 Lecture 3 COMPUTING SYSTEMS
 CS 24: INTRODUCTION TO Spring 2018 Lecture 3 COMPUTING SYSTEMS LAST TIME Basic components of processors: Buses, multiplexers, demultiplexers Arithmetic/Logic Unit (ALU) Addressable memory Assembled components
CS 24: INTRODUCTION TO Spring 2018 Lecture 3 COMPUTING SYSTEMS LAST TIME Basic components of processors: Buses, multiplexers, demultiplexers Arithmetic/Logic Unit (ALU) Addressable memory Assembled components
You ve already read basics of simulation now I will be taking up method of simulation, that is Random Number Generation
 Unit 5 SIMULATION THEORY Lesson 39 Learning objective: To learn random number generation. Methods of simulation. Monte Carlo method of simulation You ve already read basics of simulation now I will be
Unit 5 SIMULATION THEORY Lesson 39 Learning objective: To learn random number generation. Methods of simulation. Monte Carlo method of simulation You ve already read basics of simulation now I will be
A CLASS OF INDIRECT UTILITY FUNCTIONS PREDICTING GIFFEN BEHAVIOUR. P.G. MOFFATT, School of Economics, University of East Anglia, UK.
 A CLASS OF INDIRECT UTILITY FUNCTIONS PREDICTING GIFFEN BEHAVIOUR P.G. MOFFATT, School of Economics, University of East Anglia, UK September 2010 Abstract The problem of recognising Giffen behaviour is
A CLASS OF INDIRECT UTILITY FUNCTIONS PREDICTING GIFFEN BEHAVIOUR P.G. MOFFATT, School of Economics, University of East Anglia, UK September 2010 Abstract The problem of recognising Giffen behaviour is
This chapter explains two techniques which are frequently used throughout
 Chapter 2 Basic Techniques This chapter explains two techniques which are frequently used throughout this thesis. First, we will introduce the concept of particle filters. A particle filter is a recursive
Chapter 2 Basic Techniques This chapter explains two techniques which are frequently used throughout this thesis. First, we will introduce the concept of particle filters. A particle filter is a recursive
Filling Space with Random Line Segments
 Filling Space with Random Line Segments John Shier Abstract. The use of a nonintersecting random search algorithm with objects having zero width ("measure zero") is explored. The line length in the units
Filling Space with Random Line Segments John Shier Abstract. The use of a nonintersecting random search algorithm with objects having zero width ("measure zero") is explored. The line length in the units
The Traveling Salesman Problem: Adapting 2-Opt And 3-Opt Local Optimization to Branch & Bound Techniques
 The Traveling Salesman Problem: Adapting 2-Opt And 3-Opt Local Optimization to Branch & Bound Techniques Hitokazu Matsushita hitokazu@byu.edu Ogden Mills ogdenlaynemills@gmail.com Nathan Lambson nlambson@gmail.com
The Traveling Salesman Problem: Adapting 2-Opt And 3-Opt Local Optimization to Branch & Bound Techniques Hitokazu Matsushita hitokazu@byu.edu Ogden Mills ogdenlaynemills@gmail.com Nathan Lambson nlambson@gmail.com
Adaptive Crossover in Genetic Algorithms Using Statistics Mechanism
 in Artificial Life VIII, Standish, Abbass, Bedau (eds)(mit Press) 2002. pp 182 185 1 Adaptive Crossover in Genetic Algorithms Using Statistics Mechanism Shengxiang Yang Department of Mathematics and Computer
in Artificial Life VIII, Standish, Abbass, Bedau (eds)(mit Press) 2002. pp 182 185 1 Adaptive Crossover in Genetic Algorithms Using Statistics Mechanism Shengxiang Yang Department of Mathematics and Computer
Unit 1. Word Definition Picture. The number s distance from 0 on the number line. The symbol that means a number is greater than the second number.
 Unit 1 Word Definition Picture Absolute Value The number s distance from 0 on the number line. -3 =3 Greater Than The symbol that means a number is greater than the second number. > Greatest to Least To
Unit 1 Word Definition Picture Absolute Value The number s distance from 0 on the number line. -3 =3 Greater Than The symbol that means a number is greater than the second number. > Greatest to Least To
One-Point Geometric Crossover
 One-Point Geometric Crossover Alberto Moraglio School of Computing and Center for Reasoning, University of Kent, Canterbury, UK A.Moraglio@kent.ac.uk Abstract. Uniform crossover for binary strings has
One-Point Geometric Crossover Alberto Moraglio School of Computing and Center for Reasoning, University of Kent, Canterbury, UK A.Moraglio@kent.ac.uk Abstract. Uniform crossover for binary strings has
An Information-Theoretic Approach to the Prepruning of Classification Rules
 An Information-Theoretic Approach to the Prepruning of Classification Rules Max Bramer University of Portsmouth, Portsmouth, UK Abstract: Keywords: The automatic induction of classification rules from
An Information-Theoretic Approach to the Prepruning of Classification Rules Max Bramer University of Portsmouth, Portsmouth, UK Abstract: Keywords: The automatic induction of classification rules from
Top-Level View of Computer Organization
 Top-Level View of Computer Organization Bởi: Hoang Lan Nguyen Computer Component Contemporary computer designs are based on concepts developed by John von Neumann at the Institute for Advanced Studies
Top-Level View of Computer Organization Bởi: Hoang Lan Nguyen Computer Component Contemporary computer designs are based on concepts developed by John von Neumann at the Institute for Advanced Studies
Lecture 5: The Halting Problem. Michael Beeson
 Lecture 5: The Halting Problem Michael Beeson Historical situation in 1930 The diagonal method appears to offer a way to extend just about any definition of computable. It appeared in the 1920s that it
Lecture 5: The Halting Problem Michael Beeson Historical situation in 1930 The diagonal method appears to offer a way to extend just about any definition of computable. It appeared in the 1920s that it
Intermediate Mathematics League of Eastern Massachusetts
 Meet # January 010 Intermediate Mathematics League of Eastern Massachusetts Meet # January 010 Category 1 - Mystery Meet #, January 010 1. Of all the number pairs whose sum equals their product, what is
Meet # January 010 Intermediate Mathematics League of Eastern Massachusetts Meet # January 010 Category 1 - Mystery Meet #, January 010 1. Of all the number pairs whose sum equals their product, what is
Pareto Front Genetic Programming Parameter Selection Based on Design of Experiments and Industrial Data
 Pareto Front Genetic Programming Parameter Selection Based on Design of Experiments and Industrial Data Flor Castillo The Dow Chemical Company 230 N Brazosport Blvd, B27 Freeport, TX 7754 facastillo@dow.com
Pareto Front Genetic Programming Parameter Selection Based on Design of Experiments and Industrial Data Flor Castillo The Dow Chemical Company 230 N Brazosport Blvd, B27 Freeport, TX 7754 facastillo@dow.com
Binary Representations of Integers and the Performance of Selectorecombinative Genetic Algorithms
 Binary Representations of Integers and the Performance of Selectorecombinative Genetic Algorithms Franz Rothlauf Department of Information Systems University of Bayreuth, Germany franz.rothlauf@uni-bayreuth.de
Binary Representations of Integers and the Performance of Selectorecombinative Genetic Algorithms Franz Rothlauf Department of Information Systems University of Bayreuth, Germany franz.rothlauf@uni-bayreuth.de
Centrality Book. cohesion.
 Cohesion The graph-theoretic terms discussed in the previous chapter have very specific and concrete meanings which are highly shared across the field of graph theory and other fields like social network
Cohesion The graph-theoretic terms discussed in the previous chapter have very specific and concrete meanings which are highly shared across the field of graph theory and other fields like social network
UNIT 1 ANALYSIS OF ALGORITHMS
 UNIT 1 ANALYSIS OF ALGORITHMS Analysis of Algorithms Structure Page Nos. 1.0 Introduction 7 1.1 Objectives 7 1.2 Mathematical Background 8 1.3 Process of Analysis 12 1.4 Calculation of Storage Complexity
UNIT 1 ANALYSIS OF ALGORITHMS Analysis of Algorithms Structure Page Nos. 1.0 Introduction 7 1.1 Objectives 7 1.2 Mathematical Background 8 1.3 Process of Analysis 12 1.4 Calculation of Storage Complexity
Sencer Yeralan and Helen Emery Gainesville, Florida January 2000
 Preface This book is an outgrowth of the notes and experiments developed for the graduate classes at the University of Florida. It is intended for students, hobbyists, engineers, and scientists who would
Preface This book is an outgrowth of the notes and experiments developed for the graduate classes at the University of Florida. It is intended for students, hobbyists, engineers, and scientists who would
Automation of Electro-Hydraulic Routing Design using Hybrid Artificially-Intelligent Techniques
 Automation of Electro-Hydraulic Routing Design using Hybrid Artificially-Intelligent Techniques OLIVER Q. FAN, JOHN P. SHACKLETON, TATIANA KALGONOVA School of engineering and design Brunel University Uxbridge
Automation of Electro-Hydraulic Routing Design using Hybrid Artificially-Intelligent Techniques OLIVER Q. FAN, JOHN P. SHACKLETON, TATIANA KALGONOVA School of engineering and design Brunel University Uxbridge
An Evolutionary Algorithm for Minimizing Multimodal Functions
 An Evolutionary Algorithm for Minimizing Multimodal Functions D.G. Sotiropoulos, V.P. Plagianakos and M.N. Vrahatis University of Patras, Department of Mamatics, Division of Computational Mamatics & Informatics,
An Evolutionary Algorithm for Minimizing Multimodal Functions D.G. Sotiropoulos, V.P. Plagianakos and M.N. Vrahatis University of Patras, Department of Mamatics, Division of Computational Mamatics & Informatics,
Algorithm Efficiency & Sorting. Algorithm efficiency Big-O notation Searching algorithms Sorting algorithms
 Algorithm Efficiency & Sorting Algorithm efficiency Big-O notation Searching algorithms Sorting algorithms Overview Writing programs to solve problem consists of a large number of decisions how to represent
Algorithm Efficiency & Sorting Algorithm efficiency Big-O notation Searching algorithms Sorting algorithms Overview Writing programs to solve problem consists of a large number of decisions how to represent
Chapter 4: Implicit Error Detection
 4. Chpter 5 Chapter 4: Implicit Error Detection Contents 4.1 Introduction... 4-2 4.2 Network error correction... 4-2 4.3 Implicit error detection... 4-3 4.4 Mathematical model... 4-6 4.5 Simulation setup
4. Chpter 5 Chapter 4: Implicit Error Detection Contents 4.1 Introduction... 4-2 4.2 Network error correction... 4-2 4.3 Implicit error detection... 4-3 4.4 Mathematical model... 4-6 4.5 Simulation setup
Contents. Slide Set 1. About these slides. Outline of Slide Set 1. Typographical conventions: Italics. Typographical conventions. About these slides
 Slide Set 1 for ENCM 369 Winter 2014 Lecture Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary Winter Term, 2014 ENCM 369 W14 Section
Slide Set 1 for ENCM 369 Winter 2014 Lecture Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary Winter Term, 2014 ENCM 369 W14 Section
A New Measure of the Cluster Hypothesis
 A New Measure of the Cluster Hypothesis Mark D. Smucker 1 and James Allan 2 1 Department of Management Sciences University of Waterloo 2 Center for Intelligent Information Retrieval Department of Computer
A New Measure of the Cluster Hypothesis Mark D. Smucker 1 and James Allan 2 1 Department of Management Sciences University of Waterloo 2 Center for Intelligent Information Retrieval Department of Computer
CSCI 270: Introduction to Algorithms and Theory of Computing Fall 2017 Prof: Leonard Adleman Scribe: Joseph Bebel
 CSCI 270: Introduction to Algorithms and Theory of Computing Fall 2017 Prof: Leonard Adleman Scribe: Joseph Bebel We will now discuss computer programs, a concrete manifestation of what we ve been calling
CSCI 270: Introduction to Algorithms and Theory of Computing Fall 2017 Prof: Leonard Adleman Scribe: Joseph Bebel We will now discuss computer programs, a concrete manifestation of what we ve been calling
SECTION 1.3: BASIC GRAPHS and SYMMETRY
 (Section.3: Basic Graphs and Symmetry).3. SECTION.3: BASIC GRAPHS and SYMMETRY LEARNING OBJECTIVES Know how to graph basic functions. Organize categories of basic graphs and recognize common properties,
(Section.3: Basic Graphs and Symmetry).3. SECTION.3: BASIC GRAPHS and SYMMETRY LEARNING OBJECTIVES Know how to graph basic functions. Organize categories of basic graphs and recognize common properties,
Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay
 Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay Lecture - 11 Coding Strategies and Introduction to Huffman Coding The Fundamental
Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay Lecture - 11 Coding Strategies and Introduction to Huffman Coding The Fundamental
Chapter 9. Software Testing
 Chapter 9. Software Testing Table of Contents Objectives... 1 Introduction to software testing... 1 The testers... 2 The developers... 2 An independent testing team... 2 The customer... 2 Principles of
Chapter 9. Software Testing Table of Contents Objectives... 1 Introduction to software testing... 1 The testers... 2 The developers... 2 An independent testing team... 2 The customer... 2 Principles of
KNOWING the modes of failure and safe operating limits
 IEEE TRANSACTIONS ON EVOLUTIONARY COMPUTATION 1 Evolving Problems to Learn About Particle Swarm Optimizers and Other Search Algorithms W. B. Langdon and Riccardo Poli Abstract We use evolutionary computation
IEEE TRANSACTIONS ON EVOLUTIONARY COMPUTATION 1 Evolving Problems to Learn About Particle Swarm Optimizers and Other Search Algorithms W. B. Langdon and Riccardo Poli Abstract We use evolutionary computation
Machine Learning and Pervasive Computing
 Stephan Sigg Georg-August-University Goettingen, Computer Networks 17.12.2014 Overview and Structure 22.10.2014 Organisation 22.10.3014 Introduction (Def.: Machine learning, Supervised/Unsupervised, Examples)
Stephan Sigg Georg-August-University Goettingen, Computer Networks 17.12.2014 Overview and Structure 22.10.2014 Organisation 22.10.3014 Introduction (Def.: Machine learning, Supervised/Unsupervised, Examples)
Epidemic spreading on networks
 Epidemic spreading on networks Due date: Sunday October 25th, 2015, at 23:59. Always show all the steps which you made to arrive at your solution. Make sure you answer all parts of each question. Always
Epidemic spreading on networks Due date: Sunday October 25th, 2015, at 23:59. Always show all the steps which you made to arrive at your solution. Make sure you answer all parts of each question. Always
Multi-Way Number Partitioning
 Proceedings of the Twenty-First International Joint Conference on Artificial Intelligence (IJCAI-09) Multi-Way Number Partitioning Richard E. Korf Computer Science Department University of California,
Proceedings of the Twenty-First International Joint Conference on Artificial Intelligence (IJCAI-09) Multi-Way Number Partitioning Richard E. Korf Computer Science Department University of California,
Interactive 3D Visualization Of Optimization For Water Distribution Systems
 City University of New York (CUNY) CUNY Academic Works International Conference on Hydroinformatics 8-1-2014 Interactive 3D Visualization Of Optimization For Water Distribution Systems Matthew Barrie Johns
City University of New York (CUNY) CUNY Academic Works International Conference on Hydroinformatics 8-1-2014 Interactive 3D Visualization Of Optimization For Water Distribution Systems Matthew Barrie Johns
A nodal based evolutionary structural optimisation algorithm
 Computer Aided Optimum Design in Engineering IX 55 A dal based evolutionary structural optimisation algorithm Y.-M. Chen 1, A. J. Keane 2 & C. Hsiao 1 1 ational Space Program Office (SPO), Taiwan 2 Computational
Computer Aided Optimum Design in Engineering IX 55 A dal based evolutionary structural optimisation algorithm Y.-M. Chen 1, A. J. Keane 2 & C. Hsiao 1 1 ational Space Program Office (SPO), Taiwan 2 Computational
A New Crossover Technique for Cartesian Genetic Programming
 A New Crossover Technique for Cartesian Genetic Programming Genetic Programming Track Janet Clegg Intelligent Systems Group, Department of Electronics University of York, Heslington York, YO DD, UK jc@ohm.york.ac.uk
A New Crossover Technique for Cartesian Genetic Programming Genetic Programming Track Janet Clegg Intelligent Systems Group, Department of Electronics University of York, Heslington York, YO DD, UK jc@ohm.york.ac.uk
Overview. EE 4504 Computer Organization. Much of the computer s architecture / organization is hidden from a HLL programmer
 Overview EE 4504 Computer Organization Section 7 The Instruction Set Much of the computer s architecture / organization is hidden from a HLL programmer In the abstract sense, the programmer should not
Overview EE 4504 Computer Organization Section 7 The Instruction Set Much of the computer s architecture / organization is hidden from a HLL programmer In the abstract sense, the programmer should not
Non Stationary Variograms Based on Continuously Varying Weights
 Non Stationary Variograms Based on Continuously Varying Weights David F. Machuca-Mory and Clayton V. Deutsch Centre for Computational Geostatistics Department of Civil & Environmental Engineering University
Non Stationary Variograms Based on Continuously Varying Weights David F. Machuca-Mory and Clayton V. Deutsch Centre for Computational Geostatistics Department of Civil & Environmental Engineering University
CS 450 Numerical Analysis. Chapter 7: Interpolation
 Lecture slides based on the textbook Scientific Computing: An Introductory Survey by Michael T. Heath, copyright c 2018 by the Society for Industrial and Applied Mathematics. http://www.siam.org/books/cl80
Lecture slides based on the textbook Scientific Computing: An Introductory Survey by Michael T. Heath, copyright c 2018 by the Society for Industrial and Applied Mathematics. http://www.siam.org/books/cl80
Linear Cryptanalysis of Reduced Round Serpent
 Linear Cryptanalysis of Reduced Round Serpent Eli Biham 1, Orr Dunkelman 1, and Nathan Keller 2 1 Computer Science Department, Technion Israel Institute of Technology, Haifa 32000, Israel, {biham,orrd}@cs.technion.ac.il,
Linear Cryptanalysis of Reduced Round Serpent Eli Biham 1, Orr Dunkelman 1, and Nathan Keller 2 1 Computer Science Department, Technion Israel Institute of Technology, Haifa 32000, Israel, {biham,orrd}@cs.technion.ac.il,
Curriculum Catalog
 2017-2018 Curriculum Catalog 2017 Glynlyon, Inc. Table of Contents MATHEMATICS 800 FUNDAMENTALS COURSE OVERVIEW... 1 UNIT 1: THE REAL NUMBER SYSTEM... 1 UNIT 2: MODELING PROBLEMS IN INTEGERS... 2 UNIT
2017-2018 Curriculum Catalog 2017 Glynlyon, Inc. Table of Contents MATHEMATICS 800 FUNDAMENTALS COURSE OVERVIEW... 1 UNIT 1: THE REAL NUMBER SYSTEM... 1 UNIT 2: MODELING PROBLEMS IN INTEGERS... 2 UNIT
Treewidth and graph minors
 Treewidth and graph minors Lectures 9 and 10, December 29, 2011, January 5, 2012 We shall touch upon the theory of Graph Minors by Robertson and Seymour. This theory gives a very general condition under
Treewidth and graph minors Lectures 9 and 10, December 29, 2011, January 5, 2012 We shall touch upon the theory of Graph Minors by Robertson and Seymour. This theory gives a very general condition under
Data Analysis and Solver Plugins for KSpread USER S MANUAL. Tomasz Maliszewski
 Data Analysis and Solver Plugins for KSpread USER S MANUAL Tomasz Maliszewski tmaliszewski@wp.pl Table of Content CHAPTER 1: INTRODUCTION... 3 1.1. ABOUT DATA ANALYSIS PLUGIN... 3 1.3. ABOUT SOLVER PLUGIN...
Data Analysis and Solver Plugins for KSpread USER S MANUAL Tomasz Maliszewski tmaliszewski@wp.pl Table of Content CHAPTER 1: INTRODUCTION... 3 1.1. ABOUT DATA ANALYSIS PLUGIN... 3 1.3. ABOUT SOLVER PLUGIN...
1.3 Data processing; data storage; data movement; and control.
 CHAPTER 1 OVERVIEW ANSWERS TO QUESTIONS 1.1 Computer architecture refers to those attributes of a system visible to a programmer or, put another way, those attributes that have a direct impact on the logical
CHAPTER 1 OVERVIEW ANSWERS TO QUESTIONS 1.1 Computer architecture refers to those attributes of a system visible to a programmer or, put another way, those attributes that have a direct impact on the logical
Speeding up Evolutionary Algorithms Through Restricted Mutation Operators
 Speeding up Evolutionary Algorithms Through Restricted Mutation Operators Benjamin Doerr 1, Nils Hebbinghaus 1 and Frank Neumann 2 1 Max-Planck-Institut für Informatik, 66123 Saarbrücken, Germany. 2 Institut
Speeding up Evolutionary Algorithms Through Restricted Mutation Operators Benjamin Doerr 1, Nils Hebbinghaus 1 and Frank Neumann 2 1 Max-Planck-Institut für Informatik, 66123 Saarbrücken, Germany. 2 Institut
Interval Algorithms for Coin Flipping
 IJCSNS International Journal of Computer Science and Network Security, VOL.10 No.2, February 2010 55 Interval Algorithms for Coin Flipping Sung-il Pae, Hongik University, Seoul, Korea Summary We discuss
IJCSNS International Journal of Computer Science and Network Security, VOL.10 No.2, February 2010 55 Interval Algorithms for Coin Flipping Sung-il Pae, Hongik University, Seoul, Korea Summary We discuss
Lecture 6 Binary Search
 Lecture 6 Binary Search 15-122: Principles of Imperative Computation (Spring 2018) Frank Pfenning One of the fundamental and recurring problems in computer science is to find elements in collections, such
Lecture 6 Binary Search 15-122: Principles of Imperative Computation (Spring 2018) Frank Pfenning One of the fundamental and recurring problems in computer science is to find elements in collections, such
Performance Level Descriptors. Mathematics
 Performance Level Descriptors Grade 3 Well Students rarely, Understand that our number system is based on combinations of 1s, 10s, and 100s (place value, compare, order, decompose, and combine using addition)
Performance Level Descriptors Grade 3 Well Students rarely, Understand that our number system is based on combinations of 1s, 10s, and 100s (place value, compare, order, decompose, and combine using addition)
Introduction to numerical algorithms
 Introduction to numerical algorithms Given an algebraic equation or formula, we may want to approximate the value, and while in calculus, we deal with equations or formulas that are well defined at each
Introduction to numerical algorithms Given an algebraic equation or formula, we may want to approximate the value, and while in calculus, we deal with equations or formulas that are well defined at each
Learning internal representations
 CHAPTER 4 Learning internal representations Introduction In the previous chapter, you trained a single-layered perceptron on the problems AND and OR using the delta rule. This architecture was incapable
CHAPTER 4 Learning internal representations Introduction In the previous chapter, you trained a single-layered perceptron on the problems AND and OR using the delta rule. This architecture was incapable
The Encoding Complexity of Network Coding
 The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
A Model-Independent, Multi-Image Approach to MR Inhomogeneity Correction
 Tina Memo No. 2007-003 Published in Proc. MIUA 2007 A Model-Independent, Multi-Image Approach to MR Inhomogeneity Correction P. A. Bromiley and N.A. Thacker Last updated 13 / 4 / 2007 Imaging Science and
Tina Memo No. 2007-003 Published in Proc. MIUA 2007 A Model-Independent, Multi-Image Approach to MR Inhomogeneity Correction P. A. Bromiley and N.A. Thacker Last updated 13 / 4 / 2007 Imaging Science and
File Size Distribution on UNIX Systems Then and Now
 File Size Distribution on UNIX Systems Then and Now Andrew S. Tanenbaum, Jorrit N. Herder*, Herbert Bos Dept. of Computer Science Vrije Universiteit Amsterdam, The Netherlands {ast@cs.vu.nl, jnherder@cs.vu.nl,
File Size Distribution on UNIX Systems Then and Now Andrew S. Tanenbaum, Jorrit N. Herder*, Herbert Bos Dept. of Computer Science Vrije Universiteit Amsterdam, The Netherlands {ast@cs.vu.nl, jnherder@cs.vu.nl,
Investigating the Application of Genetic Programming to Function Approximation
 Investigating the Application of Genetic Programming to Function Approximation Jeremy E. Emch Computer Science Dept. Penn State University University Park, PA 16802 Abstract When analyzing a data set it
Investigating the Application of Genetic Programming to Function Approximation Jeremy E. Emch Computer Science Dept. Penn State University University Park, PA 16802 Abstract When analyzing a data set it
Understanding Competitive Co-evolutionary Dynamics via Fitness Landscapes
 Understanding Competitive Co-evolutionary Dynamics via Fitness Landscapes Elena Popovici and Kenneth De Jong George Mason University, Fairfax, VA 3 epopovic@gmu.edu, kdejong@gmu.edu Abstract. Co-evolutionary
Understanding Competitive Co-evolutionary Dynamics via Fitness Landscapes Elena Popovici and Kenneth De Jong George Mason University, Fairfax, VA 3 epopovic@gmu.edu, kdejong@gmu.edu Abstract. Co-evolutionary
Sparse Matrices Reordering using Evolutionary Algorithms: A Seeded Approach
 1 Sparse Matrices Reordering using Evolutionary Algorithms: A Seeded Approach David Greiner, Gustavo Montero, Gabriel Winter Institute of Intelligent Systems and Numerical Applications in Engineering (IUSIANI)
1 Sparse Matrices Reordering using Evolutionary Algorithms: A Seeded Approach David Greiner, Gustavo Montero, Gabriel Winter Institute of Intelligent Systems and Numerical Applications in Engineering (IUSIANI)
Evolving Better Software Parameters SSBSE 2018 Hot off the Press Track, LNCS11036, pp , Montpellier. doi: / _22
 Evolving Better Software Parameters SSBSE 2018 Hot off the Press Track, LNCS11036, pp363-369, Montpellier. doi:10.1007/978-3-319-99241-9_22 W. B. Langdon Department of Computer Science 3.9.2018 Evolving
Evolving Better Software Parameters SSBSE 2018 Hot off the Press Track, LNCS11036, pp363-369, Montpellier. doi:10.1007/978-3-319-99241-9_22 W. B. Langdon Department of Computer Science 3.9.2018 Evolving
The Diagonal Method and Hypercomputation
 The Diagonal Method and Hypercomputation Toby Ord and Tien D. Kieu The diagonal method is often used to show that Turing machines cannot solve their own halting problem. There have been several recent
The Diagonal Method and Hypercomputation Toby Ord and Tien D. Kieu The diagonal method is often used to show that Turing machines cannot solve their own halting problem. There have been several recent
Competing Tahoe Senders Adam Stambler Brian Do Group 7 12/7/2010. Computer and Communication Networks : 14:332:423
 Competing Tahoe Senders Adam Stambler Brian Do Group 7 12/7/2010 Computer and Communication Networks : 14:332:423 1 Break Down of Contributions Adam Stambler Brian Do Algorithm Design 50 50 Coding 70 30
Competing Tahoe Senders Adam Stambler Brian Do Group 7 12/7/2010 Computer and Communication Networks : 14:332:423 1 Break Down of Contributions Adam Stambler Brian Do Algorithm Design 50 50 Coding 70 30
4. Write sets of directions for how to check for direct variation. How to check for direct variation by analyzing the graph :
 Name Direct Variations There are many relationships that two variables can have. One of these relationships is called a direct variation. Use the description and example of direct variation to help you
Name Direct Variations There are many relationships that two variables can have. One of these relationships is called a direct variation. Use the description and example of direct variation to help you
An Experimental Investigation into the Rank Function of the Heterogeneous Earliest Finish Time Scheduling Algorithm
 An Experimental Investigation into the Rank Function of the Heterogeneous Earliest Finish Time Scheduling Algorithm Henan Zhao and Rizos Sakellariou Department of Computer Science, University of Manchester,
An Experimental Investigation into the Rank Function of the Heterogeneous Earliest Finish Time Scheduling Algorithm Henan Zhao and Rizos Sakellariou Department of Computer Science, University of Manchester,
Welfare Navigation Using Genetic Algorithm
 Welfare Navigation Using Genetic Algorithm David Erukhimovich and Yoel Zeldes Hebrew University of Jerusalem AI course final project Abstract Using standard navigation algorithms and applications (such
Welfare Navigation Using Genetic Algorithm David Erukhimovich and Yoel Zeldes Hebrew University of Jerusalem AI course final project Abstract Using standard navigation algorithms and applications (such
A Dynamical Systems Analysis of Collaboration Methods in Cooperative Co-evolution.
 A Dynamical Systems Analysis of Collaboration Methods in Cooperative Co-evolution. Elena Popovici and Kenneth De Jong George Mason University Fairfax, VA epopovic@gmu.edu kdejong@gmu.edu Abstract Cooperative
A Dynamical Systems Analysis of Collaboration Methods in Cooperative Co-evolution. Elena Popovici and Kenneth De Jong George Mason University Fairfax, VA epopovic@gmu.edu kdejong@gmu.edu Abstract Cooperative
5 Classifications of Accuracy and Standards
 5 Classifications of Accuracy and Standards 5.1 Classifications of Accuracy All surveys performed by Caltrans or others on all Caltrans-involved transportation improvement projects shall be classified
5 Classifications of Accuracy and Standards 5.1 Classifications of Accuracy All surveys performed by Caltrans or others on all Caltrans-involved transportation improvement projects shall be classified
Genetic Programming: A study on Computer Language
 Genetic Programming: A study on Computer Language Nilam Choudhary Prof.(Dr.) Baldev Singh Er. Gaurav Bagaria Abstract- this paper describes genetic programming in more depth, assuming that the reader is
Genetic Programming: A study on Computer Language Nilam Choudhary Prof.(Dr.) Baldev Singh Er. Gaurav Bagaria Abstract- this paper describes genetic programming in more depth, assuming that the reader is
A Comparison of Cartesian Genetic Programming and Linear Genetic Programming
 A Comparison of Cartesian Genetic Programming and Linear Genetic Programming Garnett Wilson 1,2 and Wolfgang Banzhaf 1 1 Memorial Univeristy of Newfoundland, St. John s, NL, Canada 2 Verafin, Inc., St.
A Comparison of Cartesian Genetic Programming and Linear Genetic Programming Garnett Wilson 1,2 and Wolfgang Banzhaf 1 1 Memorial Univeristy of Newfoundland, St. John s, NL, Canada 2 Verafin, Inc., St.
COSC 311: ALGORITHMS HW1: SORTING
 COSC 311: ALGORITHMS HW1: SORTIG Solutions 1) Theoretical predictions. Solution: On randomly ordered data, we expect the following ordering: Heapsort = Mergesort = Quicksort (deterministic or randomized)
COSC 311: ALGORITHMS HW1: SORTIG Solutions 1) Theoretical predictions. Solution: On randomly ordered data, we expect the following ordering: Heapsort = Mergesort = Quicksort (deterministic or randomized)
Logic, Words, and Integers
 Computer Science 52 Logic, Words, and Integers 1 Words and Data The basic unit of information in a computer is the bit; it is simply a quantity that takes one of two values, 0 or 1. A sequence of k bits
Computer Science 52 Logic, Words, and Integers 1 Words and Data The basic unit of information in a computer is the bit; it is simply a quantity that takes one of two values, 0 or 1. A sequence of k bits
Revised Sheet Metal Simulation, J.E. Akin, Rice University
 Revised Sheet Metal Simulation, J.E. Akin, Rice University A SolidWorks simulation tutorial is just intended to illustrate where to find various icons that you would need in a real engineering analysis.
Revised Sheet Metal Simulation, J.E. Akin, Rice University A SolidWorks simulation tutorial is just intended to illustrate where to find various icons that you would need in a real engineering analysis.
DLD VIDYA SAGAR P. potharajuvidyasagar.wordpress.com. Vignana Bharathi Institute of Technology UNIT 1 DLD P VIDYA SAGAR
 UNIT I Digital Systems: Binary Numbers, Octal, Hexa Decimal and other base numbers, Number base conversions, complements, signed binary numbers, Floating point number representation, binary codes, error
UNIT I Digital Systems: Binary Numbers, Octal, Hexa Decimal and other base numbers, Number base conversions, complements, signed binary numbers, Floating point number representation, binary codes, error
