GCE Computing. COMP3 Problem Solving, Programming, Operating Systems, Databases and Networking Summer Version: 1.0
|
|
|
- Spencer Brown
- 5 years ago
- Views:
Transcription
1 GCE Computing COMP3 Problem Solving, Programming, Operating Systems, Databases and Networking 2510 Summer 2016 Version: 1.0
2 It was pleasing to see the quality of responses to some questions and in particular the improvement to responses to question parts on topics that have been asked about previously. Two general weaknesses in candidate responses were noted in more than one question part. The first of these was that candidates often ignored the context of a question and gave responses that were either too general or that, whilst true in the general case, did not apply in the specific context of a question. The second was a tendency to attribute human qualities to computers and talk about computers finding tasks easy, or being able to understand something better. Candidates should recognise that computers do not find things easy or understand things, but instead computers and programmers are concerned with aspect of correctness and efficiency such as how quickly an algorithm runs or how straightforward it is for the programmer to code the algorithm. Specific feedback on each question part can be found below. Question 1 Question 1 was about various aspects of computer security. Part (a) was very well answered with the vast majority of candidates correctly identifying that a web server log was a method of accounting and a digital signature was a form of authentication. In part (b), most candidates were able to demonstrate a good understanding of computer viruses, explaining that they were malicious, self-replicating programs that attached themselves to other programs. Understanding of worms was less good, with many candidates failing to recognise that the key feature of a worm is that it distributes itself over a network by exploiting security weaknesses. Many candidates confused worms with Trojans or believed that the distinction between a worm and virus related to the actions that they might take on an infected computer rather than their method of spread. The use of digital signatures, covered in part (c) has been asked about before, and was fairly well understood. Many full mark responses were seen. Even candidates who did not achieve many marks mentioned key terms, suggesting that they had some degree of understanding. Some candidates went on to explain parts of the process that were not asked about on this paper, such as how the entire message might be encrypted or how the digital signature would be authenticated by the recipient. It is important that candidates read the question being asked so that they do not waste time writing material that cannot achieve marks. Question 2 Question 2 was about Reverse Polish Notation (RPN). The vast majority of candidates were able to convert both of the expressions from RPN to infix notation for part (a). Part (b) asked candidates to explain an advantage of RPN. The majority of candidates were able to do this, although some responses were rather superficial. It is true that RPN does not require the use of brackets in expressions, but few candidates went on to explain that this was the case because the order of evaluation was determined entirely by the order in which the operators appeared. Some candidates revealed a lack of understanding of why the lack of the use of brackets was significant, suggesting that it would save memory. Candidates need to be careful to 2 of 8
3 avoid using human-oriented terms such as understand and easier in the context of answers relating to computer programs. Responses such as A computer can understand it more easily were not markworthy. Question 3 Question 3 was about floating point representation of numbers. Parts (a) to (c) which required mathematical working were mostly well answered, but parts (d) and (e) were less well so. The majority of candidates were correctly able to identify the most negative value for part (a). For part (b), candidates had to convert from floating point to decimal. Candidates seemed to find this question part harder than similar question parts in previous years as a result of the magnitude of the mantissa (11). Candidates who worked out the answer using the calculation answer = mantissa * 2exponent appeared to make fewer calculation errors than those who attempted to work out the answer by shifting the binary point by 11 places. Part (c) was very well answered with the vast majority of candidates achieving all three marks. Those who failed to achieve full marks had most commonly arrived at an incorrect representation of 12¾ in fixed point binary at the start of their working or gave the exponent as -4 instead of +4. The advantages of normalising floating point numbers were not well known for part (d) (i). Important advantages include achieving the maximum precision within a given number of bits and facilitating simple/efficient comparison of two numbers because each number has a unique representation. It was not sufficient to state that normalisation offered improved or maximum precision; a candidate had to make clear that this was within a given number of bits. A small number of candidates gave advantages of floating point over fixed point or advantages of normalising a database. For part (d) (ii) candidates were presented with some stimulus material about how floating point representation was used and had to analyse this and then use their understanding of the mantissa and exponent to explain how a more precise representation could be achieved. It was pleasing to see how many candidates correctly identified that one of the two bits was redundant and could be inferred and then went on to explain that the bit that was freed up could be used in the mantissa to store an extra bit of precision. To achieve the second mark, candidates had to make clear that the extra bit would be used in the mantissa, not the exponent, which some failed to do. Some candidates answered a question from a previous paper that had asked about moving a bit between the mantissa and exponent. Such responses were not markworthy on this occasion. Question 4 This question was about data transmission and Mealy machines. For part (a) the vast majority of candidates were able to work out the correct parity bit and give suitable start and stop bits. For part (b), most candidates were able to explain that asynchronous data transmission meant that that the clocks at the sender and receiver were not synchronised, or that there was no common clock. However, the purpose of the start and stop bit were poorly understood. The start bit is used to temporarily synchronise the clock of the receiver to that of the transmitter. The least well understood part of the question was the purpose of the stop bit. The stop bit serves two purposes. The first is to allow the receiver to process the received data, for example, to transfer it out of a 3 of 8
4 receive buffer, before the next transmission is received. The second is to allow the identification of the next start bit, which is why the stop and start bit always have different binary values. Parts (c) and (d) were well answered, with most candidates being able to use the Mealy machine and then recognise the significance of its output. For part (e), the advantages of serial communication were not well understood, with many candidates failing to achieve any marks and only a few achieving both. When answering this type of question, candidates need to be aware of the context given in the question. Good responses recognised that a small amount of data was being sent, so data transmission speed was not a significant factor in this system, and went on to discuss problems associated with parallel communication that would not occur if serial communication was used, notably data skew and crosstalk. Marks were awarded for points relating to costs if these were justified, but really the fact that fewer wires were required so this would be cheaper was a very weak point given that the question stated that the two communicating devices were next to each other. Candidates need to ensure that they consider their response in relation to the context of a question. Question 5 This question was about data structures, with much of the emphasis placed on binary trees. Parts (a) and (b), which related to searching a binary search tree, were both well answered with two thirds of candidates correctly identifying the items that would be examined during the search and over half correctly identifying the time complexity of the search operation for part (b). For part (c) candidates had to represent a binary tree using an array of records. This was well tackled with candidates correctly using pointers to indicate the relationships between the data items. It was not enough to represent leaf node branches with a blank space or a dash for the left and right pointers. An appropriate value such as an unused index number eg 0 or a NULL value was required. Most candidates achieved a reasonable number of marks for question part (d). The key difference between a static and dynamic data structure, that the former had a fixed size that was defined at compile time and that the latter had a variable size which could change at run time was well understood. However, not many candidates went on to explain any other differences, such as the fact that memory space might be wasted if a static structure was relatively empty or that a static structure would generally be allocated consecutive memory locations. The purpose of the heap was well understood, as being a pool of available unused memory that could be allocated to a dynamic structure at runtime. The most common misunderstanding was that the heap was where a dynamic structure stored its data. Some candidates made did not get the mark for explaining the purpose of the heap as whilst they made clear that the heap was used for dynamically allocating memory, their responses did not make clear that the heap was the unused memory rather than the memory that new data was stored in. Part (e) (i) was well answered with the majority of candidates correctly identifying the order that the items would be output. Virtually everyone who correctly identified the order explained the significance of this for part (e) (ii). 4 of 8
5 For part (f) candidates had to explain why graph traversal was a more complex problem than tree traversal. Many responses recognised that features such as cycles and weighting were the key factors that might contribute to this. Some candidates went beyond what was required and provided excellent explanations of, for example, how a cycle in a graph might cause a problem for a traversal algorithm. Question 6 This question was about methods of using software, including rich (thick) and thin client systems and the use of Software as a Service. Most candidates achieved some marks and were able to describe the fundamental difference between the two, ie that rich client systems did processing locally whilst thin client systems relied on processing data on a server. Descriptions of the different hardware requirements of the two were less good. As was the case when a similar question was asked previously, many candidates just referred to better hardware, more powerful machines or even more hardware, none of which were markworthy. To achieve marks candidates needed to make specific points such as a rich client needing to have sufficient secondary storage for all the software. Many responses also only concentrated on the hardware requirements of the workstations, ignoring the server and network which would have been required for a thin client system. With regard to Software as a Service, most candidates knew what this was, ie software that was accessed and run on a remote server, and many candidates wrote a little about it, but few went on to describe many other features of it, such as the fact that it might be provided on a subscription basis rather than as a one-off purchase or that the server would be operated by a separate company who would take care of tasks such as updating the software. A small number of candidates got rich and thin client systems the wrong way around or compared peer-to-peer with server based systems instead of answering the question asked. Another occasionally seen mistake was to believe that thin clients connected to rich clients so the rich clients could do the processing. Question 7 This question was about Turing machines. After being introduced to the specification as a new topic in 2009 this topic is now fairly well understood. For part (a) candidates had to consider which aspects of a modern computer system most closely mapped to the purpose of the transition function and tape in the Turing machine, and for part (b) candidates had to explain the relationship between a Turing machine and an algorithm. About a quarter of candidates achieved both marks for (a). For (b), candidates were expected to recognise that if an algorithm existed for a problem then a Turing machine could be created to solve the problem, and vice-versa. It was not enough to just state that a Turing machine could carry out an algorithm; to be markworthy a response had to make clear that a Turing machine could carry out any algorithm. The trace for part (c) was very well completed with the overwhelming majority of candidates achieving full marks. For part (d) candidates had to explain the purpose of the Turing machine. From just examining the relationship between the input and output, a number of explanations were 5 of 8
6 plausible, but having carried through the process of a trace and having examined the transition function, candidates needed to identify that the Turing machine would reverse the order of the string on the tape. Responses that referred to flipping needed to make clear that it was the order that changed rather than that bits were flipped from 0s to 1s. Question 8 This question was about relational databases. For part (a) candidates had to draw relationships onto an Entity-Relationship diagram. Most candidates achieved at least one mark, but only about a third achieved both. A surprising number drew only two relationships when the question had stated that three were required. For part (b) candidates had to complete an update query. This was well answered. The most common errors were to include quotation marks where they were not required or to be confused about the syntax of the first line, for example by including the fieldname instead of just the table name after the keyword UPDATE. Part (c) required candidates to write a query to retrieve data from the database. The vast majority of candidates understood the basic structure of a query and were able to achieve some marks. Common mistakes were to include the Customer table in the FROM clause, which was not necessary, to miss out the part of the link between the Parcel and PriceBand tables that related to the parcel weight and to put the list into descending instead of ascending order. Some responses were seen that included (ASC) in brackets in the ORDER BY clause. The inclusion of brackets would prevent this from working; the brackets are included in mark schemes to indicate to examiners that the ASC is optional, they are not part of the language syntax. Candidates needed to redesign part of the database to eliminate some redundancy that was identified for part (d). The majority of candidates recognised that a new relation was required to represent the postcodes, but the number who correctly designed the new relation and redesigned the Parcel relation was relatively small. The most common error was to include the house number in the new PostcodeLookup relation instead of leaving it in the Parcel relation. Question 9 This question was about operating systems. Two thirds of candidates were able to identify three appropriate types of management that would be carried out by an operating system for part (a). For part (b), candidates had to explain what an interactive operating system was. To achieve the mark for this question part a candidate had to explain that the OS would be in direct two-way communication with the user. It was not enough to just state that the OS would respond to user inputs, as this would be the case with most types of operating system. Question 10 This question was about abstraction, object-oriented programming and linked lists. For part (a) candidates had to explain how the LinkedList class was a form of abstraction. Many gave a definition of abstraction but failed to apply this to the LinkedList class and so did not achieve a mark. Good responses made clear that the LinkedList class was an example of 6 of 8
7 abstraction because it allowed a programmer to manipulate items in a linked list without having to be concerned about how the linked list was implemented. For part (b) candidates had to explain why the functions and procedures in the class were public whilst the data items were not. Many candidates were able to obtain a mark for the former, but few did so for the latter. Good responses made clear that the functions and procedures were public as they would need to be called from outside of the class to implement the game, and the data items were private so that their values could only be modified in a controlled way from outside of the class, by calling the procedures of the class. It was not sufficient to state that the data items were private because they were only used by the class or because they should not be changed. Candidates had to write an algorithm for deleting an item from a linked list for part (c). A question was asked in a previous year about inserting an item into a linked list and the standard of responses to this question was notably better than was the case in the previous year. The majority of candidates had at least a good attempt at writing the part of the algorithm that would find the correct item to delete and many were then able to change the pointers to delete the item. Common mistakes and omissions were to fail to keep track of the pointer to the previous item when searching, to release the item to delete back to the heap before changing the pointer around it or to increase the current pointer by the fixed value of 1 on each iteration of a search loop. Few candidates scored all eight marks. If a candidate achieved seven but not eight marks this was usually because the algorithm did not take account of the fact that the item to delete might be the first item in the list, in which case the start pointer would need to be changed. Question 11 This question was about the use of hashing. In part (a) candidates had to compare the efficiency of searching a hash table with searching an unordered list. There were many good responses to this which explained that a slow linear search would be required for an unordered list but a fast calculation of a hash value is all that would be needed for the hash table implementation, and using this the location of the translation could be directly found. For part (b) candidates had to explain what a collision was and how it could be dealt with. The majority of candidates appeared to understand both of these but some failed to achieve marks by not stating points explicitly. For example, too many candidates failed to explain the basic point that if two items hashed to the same value then they would be stored at the same location, and the second value would overwrite the first. Various sensible methods of dealing with a collision were well described. Part (c) required candidates to explain why the English word had to be stored in addition to the French word. Some correctly identified that when performing English to French translation, if two English words had hashed to the same value, it would not be possible to tell which the correct translation was unless the English word was stored. A small number of candidates incorrectly believed that the translation was being done in reverse (French to English) and explained that the hash function would be one-way, which whilst true was not a correct answer to the question that had been asked. 7 of 8
8 Question 12 This question was about different formal methods of defining a language. For part (a) some candidates correctly identified that a syntax diagram had been used, but many incorrectly identified the notation as Bakus-Naur Form (BNF). Three quarters of candidates identified that language definition 3 was different to the other two for part (b) and a pleasing number were able to explain that for definition 3 the sign before the binary number was optional in response to part (c). Some candidates gave an almost correct answer to part (c), recognising that the difference related to the sign, despite having identified the wrong language definition in part (b). For part (d) candidates had to write a regular expression to recognise the same language as the finite statue automaton on the question paper. This question part was quite difficult and was poorly tackled. The most common mistake was to assume that any repetitions of ba always had to be made before any repetitions of c and to give an answer like a(ba)*c*. Mark Ranges and Award of Grades Grade boundaries and cumulative percentage grades are available on the Results Statistics page of the AQA Website. Converting Marks into UMS marks Convert raw marks into Uniform Mark Scale (UMS) marks by using the link below. UMS conversion calculator 8 of 8
UNIVERSITY OF MALTA THE MATRICULATION EXAMINATION ADVANCED LEVEL. COMPUTING May 2016 EXAMINERS REPORT
 UNIVERSITY OF MALTA THE MATRICULATION EXAMINATION ADVANCED LEVEL COMPUTING May 2016 EXAMINERS REPORT MATRICULATION AND SECONDARY EDUCATION CERTIFICATE EXAMINATIONS BOARD Computing Advanced Level May 2016
UNIVERSITY OF MALTA THE MATRICULATION EXAMINATION ADVANCED LEVEL COMPUTING May 2016 EXAMINERS REPORT MATRICULATION AND SECONDARY EDUCATION CERTIFICATE EXAMINATIONS BOARD Computing Advanced Level May 2016
Example Candidate Responses. Cambridge International AS & A Level Computer Science. Paper 3
 Example Candidate Responses Cambridge International AS & A Level Computer Science 9608 Paper 3 Cambridge International Examinations retains the copyright on all its publications. Registered Centres are
Example Candidate Responses Cambridge International AS & A Level Computer Science 9608 Paper 3 Cambridge International Examinations retains the copyright on all its publications. Registered Centres are
GCSE Computer Science
 GCSE Computer Science 4512/2 Computing Fundamentals Report on the Examination 4512 Summer 2015 Version: 1.0 Further copies of this Report are available from aqa.org.uk Copyright 2015 AQA and its licensors.
GCSE Computer Science 4512/2 Computing Fundamentals Report on the Examination 4512 Summer 2015 Version: 1.0 Further copies of this Report are available from aqa.org.uk Copyright 2015 AQA and its licensors.
COMP3 (JUN13COMP301) General Certificate of Education Advanced Level Examination June 2013
 Centre Number Surname Candidate Number For Examiner s Use Other Names Candidate Signature Examiner s Initials Computing General Certificate of Education Advanced Level Examination June 2013 COMP3 Question
Centre Number Surname Candidate Number For Examiner s Use Other Names Candidate Signature Examiner s Initials Computing General Certificate of Education Advanced Level Examination June 2013 COMP3 Question
COMP3 (JUN10COMP301) General Certificate of Education Advanced Level Examination June 2010
 Centre Number Surname Candidate Number For Examiner s Use Other Names Candidate Signature Examiner s Initials Computing General Certificate of Education Advanced Level Examination June 2010 COMP3 Question
Centre Number Surname Candidate Number For Examiner s Use Other Names Candidate Signature Examiner s Initials Computing General Certificate of Education Advanced Level Examination June 2010 COMP3 Question
Cambridge International General Certificate of Secondary Education 0478 Computer Science June 2016 Principal Examiner Report for Teachers
 COMPUTER SCIENCE Paper 0478/11 Paper 1 Key messages This syllabus has now been running for a few sessions and candidate s work continues to improve. There is a continued move to provide questions where
COMPUTER SCIENCE Paper 0478/11 Paper 1 Key messages This syllabus has now been running for a few sessions and candidate s work continues to improve. There is a continued move to provide questions where
Cambridge International General Certificate of Secondary Education 0478 Computer Science June 2015 Principal Examiner Report for Teachers
 COMPUTER SCIENCE Paper 0478/11 Paper 1 Key Messages This is a new syllabus and the standard of candidates work was mostly very good. There is a continued move to provide questions where candidates have
COMPUTER SCIENCE Paper 0478/11 Paper 1 Key Messages This is a new syllabus and the standard of candidates work was mostly very good. There is a continued move to provide questions where candidates have
Cambridge Ordinary Level 2210 Computer Science June 2016 Principal Examiner Report for Teachers
 COMPUTER SCIENCE Paper 2210/11 Paper 1 Key messages This syllabus has now been running for a few sessions and candidate s work continues to improve. There is a continued move to provide questions where
COMPUTER SCIENCE Paper 2210/11 Paper 1 Key messages This syllabus has now been running for a few sessions and candidate s work continues to improve. There is a continued move to provide questions where
Hardware Revision. AQA Computing AS-Level COMP2. 63 minutes. 60 marks. Page 1 of 24
 Hardware Revision AQA Computing AS-Level COMP2 204 63 minutes 60 marks Page of 24 Q. The diagram below shows some of the components of a computer system. (a) Suggest names for the components numbered to
Hardware Revision AQA Computing AS-Level COMP2 204 63 minutes 60 marks Page of 24 Q. The diagram below shows some of the components of a computer system. (a) Suggest names for the components numbered to
Cambridge Ordinary Level 2210 Computer Science November 2016 Principal Examiner Report for Teachers
 COMPUTER SCIENCE Paper 2210/12 Paper 1 Key messages If a candidate writes the answer to a question on an additional page they must indicate very clearly to the Examiner where the revised answer can be
COMPUTER SCIENCE Paper 2210/12 Paper 1 Key messages If a candidate writes the answer to a question on an additional page they must indicate very clearly to the Examiner where the revised answer can be
Stating the obvious, people and computers do not speak the same language.
 3.4 SYSTEM SOFTWARE 3.4.3 TRANSLATION SOFTWARE INTRODUCTION Stating the obvious, people and computers do not speak the same language. People have to write programs in order to instruct a computer what
3.4 SYSTEM SOFTWARE 3.4.3 TRANSLATION SOFTWARE INTRODUCTION Stating the obvious, people and computers do not speak the same language. People have to write programs in order to instruct a computer what
COMP12111 Fundamentals of Computer Engineering Paul Nutter Vasilis Pavlidis Comments
 Fundamentals of Computer Engineering Paul Nutter Vasilis Pavlidis Comments Please see the attached report. 12 February 2016 Page 2 of 7 Exam Feedback 2015/16 Q1 set by Paul Nutter Q2 set by Vasilis Pavlidis
Fundamentals of Computer Engineering Paul Nutter Vasilis Pavlidis Comments Please see the attached report. 12 February 2016 Page 2 of 7 Exam Feedback 2015/16 Q1 set by Paul Nutter Q2 set by Vasilis Pavlidis
Midterm 2 Solutions. CS70 Discrete Mathematics and Probability Theory, Spring 2009
 CS70 Discrete Mathematics and Probability Theory, Spring 2009 Midterm 2 Solutions Note: These solutions are not necessarily model answers. Rather, they are designed to be tutorial in nature, and sometimes
CS70 Discrete Mathematics and Probability Theory, Spring 2009 Midterm 2 Solutions Note: These solutions are not necessarily model answers. Rather, they are designed to be tutorial in nature, and sometimes
Time: 1 hour 30 minutes
 Paper Reference(s) 666/0 Edecel GCE Core Mathematics C Bronze Level B Time: hour 0 minutes Materials required for eamination Mathematical Formulae (Green) Items included with question papers Nil Candidates
Paper Reference(s) 666/0 Edecel GCE Core Mathematics C Bronze Level B Time: hour 0 minutes Materials required for eamination Mathematical Formulae (Green) Items included with question papers Nil Candidates
CARIBBEAN EXAMINATIONS COUNCIL
 CARIBBEAN EXAMINATIONS COUNCIL REPORT ON CANDIDATES WORK IN THE CARIBBEAN ADVANCED PROFICIENCY EXAMINATION MAY/JUNE 2012 COMPUTER SCIENCE Copyright 2012 Caribbean Examinations Council St Michael Barbados
CARIBBEAN EXAMINATIONS COUNCIL REPORT ON CANDIDATES WORK IN THE CARIBBEAN ADVANCED PROFICIENCY EXAMINATION MAY/JUNE 2012 COMPUTER SCIENCE Copyright 2012 Caribbean Examinations Council St Michael Barbados
GCSE Computer Science
 GCSE Computer Science 4512/1 Practical Programming Report on the Examination 4512 Summer 2015 Version: 1.0 Further copies of this Report are available from aqa.org.uk Copyright 2015 AQA and its licensors.
GCSE Computer Science 4512/1 Practical Programming Report on the Examination 4512 Summer 2015 Version: 1.0 Further copies of this Report are available from aqa.org.uk Copyright 2015 AQA and its licensors.
How & Why We Subnet Lab Workbook
 i How & Why We Subnet Lab Workbook ii CertificationKits.com How & Why We Subnet Workbook Copyright 2013 CertificationKits LLC All rights reserved. No part of this book maybe be reproduced or transmitted
i How & Why We Subnet Lab Workbook ii CertificationKits.com How & Why We Subnet Workbook Copyright 2013 CertificationKits LLC All rights reserved. No part of this book maybe be reproduced or transmitted
CSE 12 Abstract Syntax Trees
 CSE 12 Abstract Syntax Trees Compilers and Interpreters Parse Trees and Abstract Syntax Trees (AST's) Creating and Evaluating AST's The Table ADT and Symbol Tables 16 Using Algorithms and Data Structures
CSE 12 Abstract Syntax Trees Compilers and Interpreters Parse Trees and Abstract Syntax Trees (AST's) Creating and Evaluating AST's The Table ADT and Symbol Tables 16 Using Algorithms and Data Structures
Chapter 2 Basic Elements of C++
 C++ Programming: From Problem Analysis to Program Design, Fifth Edition 2-1 Chapter 2 Basic Elements of C++ At a Glance Instructor s Manual Table of Contents Overview Objectives s Quick Quizzes Class Discussion
C++ Programming: From Problem Analysis to Program Design, Fifth Edition 2-1 Chapter 2 Basic Elements of C++ At a Glance Instructor s Manual Table of Contents Overview Objectives s Quick Quizzes Class Discussion
CMPSCI 145 MIDTERM #1 Solution Key. SPRING 2017 March 3, 2017 Professor William T. Verts
 CMPSCI 145 MIDTERM #1 Solution Key NAME SPRING 2017 March 3, 2017 PROBLEM SCORE POINTS 1 10 2 10 3 15 4 15 5 20 6 12 7 8 8 10 TOTAL 100 10 Points Examine the following diagram of two systems, one involving
CMPSCI 145 MIDTERM #1 Solution Key NAME SPRING 2017 March 3, 2017 PROBLEM SCORE POINTS 1 10 2 10 3 15 4 15 5 20 6 12 7 8 8 10 TOTAL 100 10 Points Examine the following diagram of two systems, one involving
F453. COMPUTING Advanced Computing Theory ADVANCED GCE. Thursday 23 June 2011 Morning
 ADVANCED GCE COMPUTING Advanced Computing Theory F453 *F430360611* Candidates answer on the question paper. OCR supplied materials: None Other materials required: None Thursday 23 June 2011 Morning Duration:
ADVANCED GCE COMPUTING Advanced Computing Theory F453 *F430360611* Candidates answer on the question paper. OCR supplied materials: None Other materials required: None Thursday 23 June 2011 Morning Duration:
A-level COMPUTER SCIENCE (7517/2) Paper 2. Mark scheme
 A-level COMPUTER SCIENCE (757/) Paper Mark scheme Mark schemes are prepared by the Lead Assessment Writer and considered, together with the relevant questions, by a panel of subject teachers. This mark
A-level COMPUTER SCIENCE (757/) Paper Mark scheme Mark schemes are prepared by the Lead Assessment Writer and considered, together with the relevant questions, by a panel of subject teachers. This mark
UNIVERSITY OF CAMBRIDGE INTERNATIONAL EXAMINATIONS General Certificate of Education Advanced Level. Paper 3 October/November hours
 *2685241834* UNIVERSITY OF CAMBRIDGE INTERNATIONAL EXAMINATIONS General Certificate of Education Advanced Level COMPUTING 9691/32 Paper 3 October/November 2013 2 hours Candidates answer on the Question
*2685241834* UNIVERSITY OF CAMBRIDGE INTERNATIONAL EXAMINATIONS General Certificate of Education Advanced Level COMPUTING 9691/32 Paper 3 October/November 2013 2 hours Candidates answer on the Question
Applied Information and Communication Technology
 Applied Information and Communication Technology Unit 7: Using Database Software Summer 2010 Example Solution and Principal Examiner Advice and Guidance Activity 1...3 Activity 2...6 Activity 3...12 Activity
Applied Information and Communication Technology Unit 7: Using Database Software Summer 2010 Example Solution and Principal Examiner Advice and Guidance Activity 1...3 Activity 2...6 Activity 3...12 Activity
EC121 Mathematical Techniques A Revision Notes
 EC Mathematical Techniques A Revision Notes EC Mathematical Techniques A Revision Notes Mathematical Techniques A begins with two weeks of intensive revision of basic arithmetic and algebra, to the level
EC Mathematical Techniques A Revision Notes EC Mathematical Techniques A Revision Notes Mathematical Techniques A begins with two weeks of intensive revision of basic arithmetic and algebra, to the level
Digital Fundamentals
 Digital Fundamentals Tenth Edition Floyd Chapter 2 2009 Pearson Education, Upper 2008 Pearson Saddle River, Education NJ 07458. All Rights Reserved Decimal Numbers The position of each digit in a weighted
Digital Fundamentals Tenth Edition Floyd Chapter 2 2009 Pearson Education, Upper 2008 Pearson Saddle River, Education NJ 07458. All Rights Reserved Decimal Numbers The position of each digit in a weighted
GCSE Computer Science
 GCSE Computer Science Unit 2 Computing Fundamentals Mark scheme 452/2 June 206 Version:. Final Mark schemes are prepared by the Lead Assessment Writer and considered, together with the relevant questions,
GCSE Computer Science Unit 2 Computing Fundamentals Mark scheme 452/2 June 206 Version:. Final Mark schemes are prepared by the Lead Assessment Writer and considered, together with the relevant questions,
Introduction to Scientific Computing Lecture 1
 Introduction to Scientific Computing Lecture 1 Professor Hanno Rein Last updated: September 10, 2017 1 Number Representations In this lecture, we will cover two concept that are important to understand
Introduction to Scientific Computing Lecture 1 Professor Hanno Rein Last updated: September 10, 2017 1 Number Representations In this lecture, we will cover two concept that are important to understand
F453 Module 7: Programming Techniques. 7.2: Methods for defining syntax
 7.2: Methods for defining syntax 2 What this module is about In this module we discuss: explain how functions, procedures and their related variables may be used to develop a program in a structured way,
7.2: Methods for defining syntax 2 What this module is about In this module we discuss: explain how functions, procedures and their related variables may be used to develop a program in a structured way,
MARKING KEY The University of British Columbia MARKING KEY Computer Science 260 Midterm #2 Examination 12:30 noon, Thursday, March 15, 2012
 MARKING KEY The University of British Columbia MARKING KEY Computer Science 260 Midterm #2 Examination 12:30 noon, Thursday, March 15, 2012 Instructor: K. S. Booth Time: 70 minutes (one hour ten minutes)
MARKING KEY The University of British Columbia MARKING KEY Computer Science 260 Midterm #2 Examination 12:30 noon, Thursday, March 15, 2012 Instructor: K. S. Booth Time: 70 minutes (one hour ten minutes)
3.1 DATA REPRESENTATION (PART C)
 3.1 DATA REPRESENTATION (PART C) 3.1.3 REAL NUMBERS AND NORMALISED FLOATING-POINT REPRESENTATION In decimal notation, the number 23.456 can be written as 0.23456 x 10 2. This means that in decimal notation,
3.1 DATA REPRESENTATION (PART C) 3.1.3 REAL NUMBERS AND NORMALISED FLOATING-POINT REPRESENTATION In decimal notation, the number 23.456 can be written as 0.23456 x 10 2. This means that in decimal notation,
unused unused unused unused unused unused
 BCD numbers. In some applications, such as in the financial industry, the errors that can creep in due to converting numbers back and forth between decimal and binary is unacceptable. For these applications
BCD numbers. In some applications, such as in the financial industry, the errors that can creep in due to converting numbers back and forth between decimal and binary is unacceptable. For these applications
1. INTRODUCTION TO DATA STRUCTURE
 1. INTRODUCTION TO DATA STRUCTURE 1.1 What is Data Structure? Data Structure: Data structure is a way to storing and organizing data in a computer so that it can be used efficiently. Data structure is
1. INTRODUCTION TO DATA STRUCTURE 1.1 What is Data Structure? Data Structure: Data structure is a way to storing and organizing data in a computer so that it can be used efficiently. Data structure is
Cambridge International Examinations Cambridge International Advanced Subsidiary and Advanced Level
 Cambridge International Examinations Cambridge International Advanced Subsidiary and Advanced Level *0586807379* COMPUTER SCIENCE 9608/32 Paper 3 Advanced Theory October/November 2017 1 hour 30 minutes
Cambridge International Examinations Cambridge International Advanced Subsidiary and Advanced Level *0586807379* COMPUTER SCIENCE 9608/32 Paper 3 Advanced Theory October/November 2017 1 hour 30 minutes
Signed umbers. Sign/Magnitude otation
 Signed umbers So far we have discussed unsigned number representations. In particular, we have looked at the binary number system and shorthand methods in representing binary codes. With m binary digits,
Signed umbers So far we have discussed unsigned number representations. In particular, we have looked at the binary number system and shorthand methods in representing binary codes. With m binary digits,
VARIABLES. Aim Understanding how computer programs store values, and how they are accessed and used in computer programs.
 Lesson 2 VARIABLES Aim Understanding how computer programs store values, and how they are accessed and used in computer programs. WHAT ARE VARIABLES? When you input data (i.e. information) into a computer
Lesson 2 VARIABLES Aim Understanding how computer programs store values, and how they are accessed and used in computer programs. WHAT ARE VARIABLES? When you input data (i.e. information) into a computer
Cambridge International Examinations Cambridge International Advanced Subsidiary and Advanced Level
 Cambridge International Examinations Cambridge International Advanced Subsidiary and Advanced Level *7825200973* COMPUTER SCIENCE 9608/32 Paper 3 Advanced Theory October/November 2018 1 hour 30 minutes
Cambridge International Examinations Cambridge International Advanced Subsidiary and Advanced Level *7825200973* COMPUTER SCIENCE 9608/32 Paper 3 Advanced Theory October/November 2018 1 hour 30 minutes
Project 3: RPN Calculator
 ECE267 @ UIC, Spring 2012, Wenjing Rao Project 3: RPN Calculator What to do: Ask the user to input a string of expression in RPN form (+ - * / ), use a stack to evaluate the result and display the result
ECE267 @ UIC, Spring 2012, Wenjing Rao Project 3: RPN Calculator What to do: Ask the user to input a string of expression in RPN form (+ - * / ), use a stack to evaluate the result and display the result
Group B Assignment 9. Code generation using DAG. Title of Assignment: Problem Definition: Code generation using DAG / labeled tree.
 Group B Assignment 9 Att (2) Perm(3) Oral(5) Total(10) Sign Title of Assignment: Code generation using DAG. 9.1.1 Problem Definition: Code generation using DAG / labeled tree. 9.1.2 Perquisite: Lex, Yacc,
Group B Assignment 9 Att (2) Perm(3) Oral(5) Total(10) Sign Title of Assignment: Code generation using DAG. 9.1.1 Problem Definition: Code generation using DAG / labeled tree. 9.1.2 Perquisite: Lex, Yacc,
Draw a diagram of an empty circular queue and describe it to the reader.
 1020_1030_testquestions.text Wed Sep 10 10:40:46 2014 1 1983/84 COSC1020/30 Tests >>> The following was given to students. >>> Students can have a good idea of test questions by examining and trying the
1020_1030_testquestions.text Wed Sep 10 10:40:46 2014 1 1983/84 COSC1020/30 Tests >>> The following was given to students. >>> Students can have a good idea of test questions by examining and trying the
19 Much that I bound, I could not free; Much that I freed returned to me. Lee Wilson Dodd
 19 Much that I bound, I could not free; Much that I freed returned to me. Lee Wilson Dodd Will you walk a little faster? said a whiting to a snail, There s a porpoise close behind us, and he s treading
19 Much that I bound, I could not free; Much that I freed returned to me. Lee Wilson Dodd Will you walk a little faster? said a whiting to a snail, There s a porpoise close behind us, and he s treading
Data Analysis and Solver Plugins for KSpread USER S MANUAL. Tomasz Maliszewski
 Data Analysis and Solver Plugins for KSpread USER S MANUAL Tomasz Maliszewski tmaliszewski@wp.pl Table of Content CHAPTER 1: INTRODUCTION... 3 1.1. ABOUT DATA ANALYSIS PLUGIN... 3 1.3. ABOUT SOLVER PLUGIN...
Data Analysis and Solver Plugins for KSpread USER S MANUAL Tomasz Maliszewski tmaliszewski@wp.pl Table of Content CHAPTER 1: INTRODUCTION... 3 1.1. ABOUT DATA ANALYSIS PLUGIN... 3 1.3. ABOUT SOLVER PLUGIN...
UNIT 7A Data Representation: Numbers and Text. Digital Data
 UNIT 7A Data Representation: Numbers and Text 1 Digital Data 10010101011110101010110101001110 What does this binary sequence represent? It could be: an integer a floating point number text encoded with
UNIT 7A Data Representation: Numbers and Text 1 Digital Data 10010101011110101010110101001110 What does this binary sequence represent? It could be: an integer a floating point number text encoded with
BCS THE CHARTERED INSTITUTE FOR IT BCS HIGHER EDUCATION QUALIFICATIONS BCS Level 5 Diploma in IT COMPUTER NETWORKS APRIL 2015 EXAMINERS REPORT
 BCS THE CHARTERED INSTITUTE FOR IT BCS HIGHER EDUCATION QUALIFICATIONS BCS Level 5 Diploma in IT COMPUTER NETWORKS APRIL 2015 EXAMINERS REPORT General Comments The performance in this session is arguably
BCS THE CHARTERED INSTITUTE FOR IT BCS HIGHER EDUCATION QUALIFICATIONS BCS Level 5 Diploma in IT COMPUTER NETWORKS APRIL 2015 EXAMINERS REPORT General Comments The performance in this session is arguably
Monitoring and Improving Quality of Data Handling
 Monitoring and Improving Quality of Data Handling The purpose of this document is to: (a) (b) (c) Maximise the quality of the research process once the question has been formulated and the study designed.
Monitoring and Improving Quality of Data Handling The purpose of this document is to: (a) (b) (c) Maximise the quality of the research process once the question has been formulated and the study designed.
Friday 16 June 2017 Morning
 Oxford Cambridge and RSA Friday 16 June 2017 Morning A2 GCE COMPUTING F453/01 Advanced Computing Theory *6880015394* Candidates answer on the Question Paper. OCR supplied materials: None Other materials
Oxford Cambridge and RSA Friday 16 June 2017 Morning A2 GCE COMPUTING F453/01 Advanced Computing Theory *6880015394* Candidates answer on the Question Paper. OCR supplied materials: None Other materials
Memory Addressing, Binary, and Hexadecimal Review
 C++ By A EXAMPLE Memory Addressing, Binary, and Hexadecimal Review You do not have to understand the concepts in this appendix to become well-versed in C++. You can master C++, however, only if you spend
C++ By A EXAMPLE Memory Addressing, Binary, and Hexadecimal Review You do not have to understand the concepts in this appendix to become well-versed in C++. You can master C++, however, only if you spend
Computer Science Foundation Exam
 Computer Science Foundation Exam August 6, 017 Section I A DATA STRUCTURES SOLUTIONS NO books, notes, or calculators may be used, and you must work entirely on your own. Question # Max Pts Category Passing
Computer Science Foundation Exam August 6, 017 Section I A DATA STRUCTURES SOLUTIONS NO books, notes, or calculators may be used, and you must work entirely on your own. Question # Max Pts Category Passing
CHW 261: Logic Design
 CHW 261: Logic Design Instructors: Prof. Hala Zayed Dr. Ahmed Shalaby http://www.bu.edu.eg/staff/halazayed14 http://bu.edu.eg/staff/ahmedshalaby14# Slide 1 Slide 2 Slide 3 Digital Fundamentals CHAPTER
CHW 261: Logic Design Instructors: Prof. Hala Zayed Dr. Ahmed Shalaby http://www.bu.edu.eg/staff/halazayed14 http://bu.edu.eg/staff/ahmedshalaby14# Slide 1 Slide 2 Slide 3 Digital Fundamentals CHAPTER
CS 0478 Topic 1.2. only. From sender to receiver. directions simultaneously. data can be sent from A to B and from B to A along the same line
 Communication and Internet Technologies:- When data is sent from one device to another, it is important to consider how that data is transmitted. It is also important to ensure that the data hasn t been
Communication and Internet Technologies:- When data is sent from one device to another, it is important to consider how that data is transmitted. It is also important to ensure that the data hasn t been
Principal Moderator Feedback. June Applied GCE ICT Web Development
 Principal Moderator Feedback June 2011 Applied GCE ICT 6955 01 - Web Development Edexcel is one of the leading examining and awarding bodies in the UK and throughout the world. We provide a wide range
Principal Moderator Feedback June 2011 Applied GCE ICT 6955 01 - Web Development Edexcel is one of the leading examining and awarding bodies in the UK and throughout the world. We provide a wide range
Examples of Code Roaches. First Draft List Cem Kaner September 11, 2005
 Examples of Code Roaches First Draft List Cem Kaner September 11, 2005 Why a Potential-Bug List? Given a potential error, you can develop a method to test for it Foundation for Code inspections Glass box
Examples of Code Roaches First Draft List Cem Kaner September 11, 2005 Why a Potential-Bug List? Given a potential error, you can develop a method to test for it Foundation for Code inspections Glass box
Course Report Computing Science Advanced Higher
 Course Report 2018 Subject Level Computing Science Advanced Higher This report provides information on the performance of candidates. Teachers, lecturers and assessors may find it useful when preparing
Course Report 2018 Subject Level Computing Science Advanced Higher This report provides information on the performance of candidates. Teachers, lecturers and assessors may find it useful when preparing
AAL 217: DATA STRUCTURES
 Chapter # 4: Hashing AAL 217: DATA STRUCTURES The implementation of hash tables is frequently called hashing. Hashing is a technique used for performing insertions, deletions, and finds in constant average
Chapter # 4: Hashing AAL 217: DATA STRUCTURES The implementation of hash tables is frequently called hashing. Hashing is a technique used for performing insertions, deletions, and finds in constant average
Student Performance Q&A:
 Student Performance Q&A: 2004 AP Computer Science A Free-Response Questions The following comments on the 2004 free-response questions for AP Computer Science A were written by the Chief Reader, Chris
Student Performance Q&A: 2004 AP Computer Science A Free-Response Questions The following comments on the 2004 free-response questions for AP Computer Science A were written by the Chief Reader, Chris
WACC Report. Zeshan Amjad, Rohan Padmanabhan, Rohan Pritchard, & Edward Stow
 WACC Report Zeshan Amjad, Rohan Padmanabhan, Rohan Pritchard, & Edward Stow 1 The Product Our compiler passes all of the supplied test cases, and over 60 additional test cases we wrote to cover areas (mostly
WACC Report Zeshan Amjad, Rohan Padmanabhan, Rohan Pritchard, & Edward Stow 1 The Product Our compiler passes all of the supplied test cases, and over 60 additional test cases we wrote to cover areas (mostly
Version 1.0: klm. General Certificate of Education. Media Studies. Creating Media. Report on the Examination examination - January series
 Version 1.0: 0310 klm General Certificate of Education Media Studies MEST2 Creating Media Report on the Examination 2010 examination - January series Further copies of this Report are available to download
Version 1.0: 0310 klm General Certificate of Education Media Studies MEST2 Creating Media Report on the Examination 2010 examination - January series Further copies of this Report are available to download
Part 5. Verification and Validation
 Software Engineering Part 5. Verification and Validation - Verification and Validation - Software Testing Ver. 1.7 This lecture note is based on materials from Ian Sommerville 2006. Anyone can use this
Software Engineering Part 5. Verification and Validation - Verification and Validation - Software Testing Ver. 1.7 This lecture note is based on materials from Ian Sommerville 2006. Anyone can use this
DS ata Structures Aptitude
 DS ata Structures Aptitude 1. What is data structure? A data structure is a way of organizing data that considers not only the items stored, but also their relationship to each other. Advance knowledge
DS ata Structures Aptitude 1. What is data structure? A data structure is a way of organizing data that considers not only the items stored, but also their relationship to each other. Advance knowledge
4.1 COMPUTATIONAL THINKING AND PROBLEM-SOLVING
 4.1 COMPUTATIONAL THINKING AND PROBLEM-SOLVING 4.1.2 ALGORITHMS ALGORITHM An Algorithm is a procedure or formula for solving a problem. It is a step-by-step set of operations to be performed. It is almost
4.1 COMPUTATIONAL THINKING AND PROBLEM-SOLVING 4.1.2 ALGORITHMS ALGORITHM An Algorithm is a procedure or formula for solving a problem. It is a step-by-step set of operations to be performed. It is almost
BCS HIGHER EDUCATION QUALIFICATIONS Level 4 Certificate in IT. April 2013 EXAMINERS REPORT. Software Development
 BCS HIGHER EDUCATION QUALIFICATIONS Level 4 Certificate in IT April 2013 EXAMINERS REPORT Software Development General comments on candidates' performance The standard for this examination was higher than
BCS HIGHER EDUCATION QUALIFICATIONS Level 4 Certificate in IT April 2013 EXAMINERS REPORT Software Development General comments on candidates' performance The standard for this examination was higher than
2015 Paper E2.1: Digital Electronics II
 s 2015 Paper E2.1: Digital Electronics II Answer ALL questions. There are THREE questions on the paper. Question ONE counts for 40% of the marks, other questions 30% Time allowed: 2 hours (Not to be removed
s 2015 Paper E2.1: Digital Electronics II Answer ALL questions. There are THREE questions on the paper. Question ONE counts for 40% of the marks, other questions 30% Time allowed: 2 hours (Not to be removed
Intro. Scheme Basics. scm> 5 5. scm>
 Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
SOFTWARE ENGINEERING Prof.N.L.Sarda Computer Science & Engineering IIT Bombay. Lecture #10 Process Modelling DFD, Function Decomp (Part 2)
 SOFTWARE ENGINEERING Prof.N.L.Sarda Computer Science & Engineering IIT Bombay Lecture #10 Process Modelling DFD, Function Decomp (Part 2) Let us continue with the data modeling topic. So far we have seen
SOFTWARE ENGINEERING Prof.N.L.Sarda Computer Science & Engineering IIT Bombay Lecture #10 Process Modelling DFD, Function Decomp (Part 2) Let us continue with the data modeling topic. So far we have seen
Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 14
 Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 14 Scan Converting Lines, Circles and Ellipses Hello everybody, welcome again
Computer Graphics Prof. Sukhendu Das Dept. of Computer Science and Engineering Indian Institute of Technology, Madras Lecture - 14 Scan Converting Lines, Circles and Ellipses Hello everybody, welcome again
M11/5/COMSC/HP2/ENG/TZ0/XX/M MARKSCHEME. May 2011 COMPUTER SCIENCE. Higher Level. Paper pages
 M11/5/COMSC/HP2/ENG/TZ0/XX/M MARKSCHEME May 2011 COMPUTER SCIENCE Higher Level Paper 2 13 pages 2 M11/5/COMSC/HP2/ENG/TZ0/XX/M This markscheme is confidential and for the exclusive use of examiners in
M11/5/COMSC/HP2/ENG/TZ0/XX/M MARKSCHEME May 2011 COMPUTER SCIENCE Higher Level Paper 2 13 pages 2 M11/5/COMSC/HP2/ENG/TZ0/XX/M This markscheme is confidential and for the exclusive use of examiners in
Example Candidate Responses. Cambridge International AS & A Level Computer Science. Paper 2
 Example Candidate Responses Cambridge International AS & A Level Computer Science 9608 Paper 2 Cambridge International Examinations retains the copyright on all its publications. Registered Centres are
Example Candidate Responses Cambridge International AS & A Level Computer Science 9608 Paper 2 Cambridge International Examinations retains the copyright on all its publications. Registered Centres are
Lecture 05 I/O statements Printf, Scanf Simple statements, Compound statements
 Programming, Data Structures and Algorithms Prof. Shankar Balachandran Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 05 I/O statements Printf, Scanf Simple
Programming, Data Structures and Algorithms Prof. Shankar Balachandran Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 05 I/O statements Printf, Scanf Simple
Detecting and correcting mistakes
 Chapter 6 Detecting and correcting mistakes 6.1 Errors and the law! In chapter 4 we saw that random noise will tend to reduce the amount of information transmitted or collected by making us uncertain that
Chapter 6 Detecting and correcting mistakes 6.1 Errors and the law! In chapter 4 we saw that random noise will tend to reduce the amount of information transmitted or collected by making us uncertain that
Physics 306 Computing Lab 5: A Little Bit of This, A Little Bit of That
 Physics 306 Computing Lab 5: A Little Bit of This, A Little Bit of That 1. Introduction You have seen situations in which the way numbers are stored in a computer affects a program. For example, in the
Physics 306 Computing Lab 5: A Little Bit of This, A Little Bit of That 1. Introduction You have seen situations in which the way numbers are stored in a computer affects a program. For example, in the
Number Systems MA1S1. Tristan McLoughlin. November 27, 2013
 Number Systems MA1S1 Tristan McLoughlin November 27, 2013 http://en.wikipedia.org/wiki/binary numeral system http://accu.org/index.php/articles/1558 http://www.binaryconvert.com http://en.wikipedia.org/wiki/ascii
Number Systems MA1S1 Tristan McLoughlin November 27, 2013 http://en.wikipedia.org/wiki/binary numeral system http://accu.org/index.php/articles/1558 http://www.binaryconvert.com http://en.wikipedia.org/wiki/ascii
Final Labs and Tutors
 ICT106 Fundamentals of Computer Systems - Topic 2 REPRESENTATION AND STORAGE OF INFORMATION Reading: Linux Assembly Programming Language, Ch 2.4-2.9 and 3.6-3.8 Final Labs and Tutors Venue and time South
ICT106 Fundamentals of Computer Systems - Topic 2 REPRESENTATION AND STORAGE OF INFORMATION Reading: Linux Assembly Programming Language, Ch 2.4-2.9 and 3.6-3.8 Final Labs and Tutors Venue and time South
Cambridge International Examinations Cambridge International General Certificate of Secondary Education. Published
 Cambridge International Examinations Cambridge International General Certificate of Secondary Education COMPUTER SCIENCE 0478/13 Paper 1 October/November 2016 MARK SCHEME Maximum Mark: 75 Published This
Cambridge International Examinations Cambridge International General Certificate of Secondary Education COMPUTER SCIENCE 0478/13 Paper 1 October/November 2016 MARK SCHEME Maximum Mark: 75 Published This
Cambridge International Examinations Cambridge International General Certificate of Secondary Education
 Cambridge International Examinations Cambridge International General Certificate of Secondary Education *4170308148* COMPUTER SCIENCE 0478/11 Paper 1 Theory October/November 2016 1 hour 45 minutes Candidates
Cambridge International Examinations Cambridge International General Certificate of Secondary Education *4170308148* COMPUTER SCIENCE 0478/11 Paper 1 Theory October/November 2016 1 hour 45 minutes Candidates
Digital Fundamentals
 Digital Fundamentals Tenth Edition Floyd Chapter 2 2009 Pearson Education, Upper 2008 Pearson Saddle River, Education NJ 07458. All Rights Reserved Quiz 2 Agenda Lecture: Chapter 2 (2-7 through 2-11):
Digital Fundamentals Tenth Edition Floyd Chapter 2 2009 Pearson Education, Upper 2008 Pearson Saddle River, Education NJ 07458. All Rights Reserved Quiz 2 Agenda Lecture: Chapter 2 (2-7 through 2-11):
CSE Theory of Computing Fall 2017 Project 1-SAT Solving
 CSE 30151 Theory of Computing Fall 2017 Project 1-SAT Solving Version 3: Sept. 21, 2017 The purpose of this project is to gain an understanding of one of the most central problems of computing: Boolean
CSE 30151 Theory of Computing Fall 2017 Project 1-SAT Solving Version 3: Sept. 21, 2017 The purpose of this project is to gain an understanding of one of the most central problems of computing: Boolean
THE BCS PROFESSIONAL EXAMINATION. Level 4 Certificate in IT. March 2015 EXAMINERS' REPORT SOFTWARE DEVELOPMENT
 THE BCS PROFESSIONAL EXAMINATION Level 4 Certificate in IT March 2015 EXAMINERS' REPORT SOFTWARE DEVELOPMENT General comments on candidates' performance The standard of answers was generally higher than
THE BCS PROFESSIONAL EXAMINATION Level 4 Certificate in IT March 2015 EXAMINERS' REPORT SOFTWARE DEVELOPMENT General comments on candidates' performance The standard of answers was generally higher than
We've tried to include the common errors and grading standard for every question.
 Fall 2003 CS61B Midterm (50/300 points) ;;;; Meta ;;;; GS = Grading Standard We've tried to include the common errors and grading standard for every question. QUESTION 1 GS: The T/F questions were worth
Fall 2003 CS61B Midterm (50/300 points) ;;;; Meta ;;;; GS = Grading Standard We've tried to include the common errors and grading standard for every question. QUESTION 1 GS: The T/F questions were worth
COURSE: COMPUTER FUNDAMENTALS AND PC SOFTWARE (MCA -01)
 COURSE: COMPUTER FUNDAMENTALS AND PC SOFTWARE (MCA -01) [Assignments are required to be written in your own language. Copying in toto from the learning materials will carry less score] A. Answer the following
COURSE: COMPUTER FUNDAMENTALS AND PC SOFTWARE (MCA -01) [Assignments are required to be written in your own language. Copying in toto from the learning materials will carry less score] A. Answer the following
Module Contact: Dr Tony Bagnall, CMP Copyright of the University of East Anglia Version 1
 UNIVERSITY OF EAST ANGLIA School of Computing Sciences Main Series UG Examination 2016-17 DATA STRUCTURES AND ALGORITHMS CMP-5014Y Time allowed: 2 hours Section A (Attempt all questions: 75 marks) Section
UNIVERSITY OF EAST ANGLIA School of Computing Sciences Main Series UG Examination 2016-17 DATA STRUCTURES AND ALGORITHMS CMP-5014Y Time allowed: 2 hours Section A (Attempt all questions: 75 marks) Section
MCT611 Computer Architecture & Operating Systems Module Handbook. Master of Science in Software Engineering & Database Technologies (MScSED)
 MCT611 Computer Architecture & Operating Systems Module Handbook Master of Science in Software Engineering & Database Technologies (MScSED) Table of Contents 1 Module Details... 2 1.1 Module Description...2
MCT611 Computer Architecture & Operating Systems Module Handbook Master of Science in Software Engineering & Database Technologies (MScSED) Table of Contents 1 Module Details... 2 1.1 Module Description...2
Problem A - EPIC. Line Width of Letters (# characters) EEEEEEEEEE EEEEEEEEEE EE EE EEEEEEEEEE EEEEEEEEEE EE EE EEEEEEEEEE EEEEEEEEEE
 Problem A - EPIC Professor Plum likes the idea of visiting EPIC for MICS 4. He wants you to write a program to generate ASC art printing EPIC vertically for a sign to tape to the back of the van on the
Problem A - EPIC Professor Plum likes the idea of visiting EPIC for MICS 4. He wants you to write a program to generate ASC art printing EPIC vertically for a sign to tape to the back of the van on the
UNIT III BALANCED SEARCH TREES AND INDEXING
 UNIT III BALANCED SEARCH TREES AND INDEXING OBJECTIVE The implementation of hash tables is frequently called hashing. Hashing is a technique used for performing insertions, deletions and finds in constant
UNIT III BALANCED SEARCH TREES AND INDEXING OBJECTIVE The implementation of hash tables is frequently called hashing. Hashing is a technique used for performing insertions, deletions and finds in constant
Countdown to your final Maths exam part 8 (2017) Examiners Report & Markscheme
 Countdown to your final Maths exam part 8 (2017) Examiners Report & Markscheme Examiner's Report Q1. Most candidates made good attempts at this final question. A small number of candidates scored one mark
Countdown to your final Maths exam part 8 (2017) Examiners Report & Markscheme Examiner's Report Q1. Most candidates made good attempts at this final question. A small number of candidates scored one mark
COMP171. Hashing.
 COMP171 Hashing Hashing 2 Hashing Again, a (dynamic) set of elements in which we do search, insert, and delete Linear ones: lists, stacks, queues, Nonlinear ones: trees, graphs (relations between elements
COMP171 Hashing Hashing 2 Hashing Again, a (dynamic) set of elements in which we do search, insert, and delete Linear ones: lists, stacks, queues, Nonlinear ones: trees, graphs (relations between elements
A-level Computer Science
 A-level Computer Science Paper (757/) Mark scheme 757 June 07 Version:.0 Final Mark schemes are prepared by the Lead Assessment Writer and considered, together with the relevant questions, by a panel of
A-level Computer Science Paper (757/) Mark scheme 757 June 07 Version:.0 Final Mark schemes are prepared by the Lead Assessment Writer and considered, together with the relevant questions, by a panel of
MARK SCHEME for the October/November 2013 series 9691 COMPUTING. 9691/32 Paper 3 (Written Paper), maximum raw mark 90
 CAMBRIDGE INTERNATIONAL EXAMINATIONS GCE Advanced Level MARK SCHEME for the October/November 2013 series 9691 COMPUTING 9691/32 Paper 3 (Written Paper), maximum raw mark 90 This mark scheme is published
CAMBRIDGE INTERNATIONAL EXAMINATIONS GCE Advanced Level MARK SCHEME for the October/November 2013 series 9691 COMPUTING 9691/32 Paper 3 (Written Paper), maximum raw mark 90 This mark scheme is published
TABLES AND HASHING. Chapter 13
 Data Structures Dr Ahmed Rafat Abas Computer Science Dept, Faculty of Computer and Information, Zagazig University arabas@zu.edu.eg http://www.arsaliem.faculty.zu.edu.eg/ TABLES AND HASHING Chapter 13
Data Structures Dr Ahmed Rafat Abas Computer Science Dept, Faculty of Computer and Information, Zagazig University arabas@zu.edu.eg http://www.arsaliem.faculty.zu.edu.eg/ TABLES AND HASHING Chapter 13
Cambridge International Examinations Cambridge International Advanced Level
 Cambridge International Examinations Cambridge International Advanced Level *6550085963* COMPUTER SCIENCE 9608/32 Paper 3 Advanced Theory October/November 2015 1 hour 30 minutes Candidates answer on the
Cambridge International Examinations Cambridge International Advanced Level *6550085963* COMPUTER SCIENCE 9608/32 Paper 3 Advanced Theory October/November 2015 1 hour 30 minutes Candidates answer on the
CS 125 Section #4 RAMs and TMs 9/27/16
 CS 125 Section #4 RAMs and TMs 9/27/16 1 RAM A word-ram consists of: A fixed set of instructions P 1,..., P q. Allowed instructions are: Modular arithmetic and integer division on registers; the standard
CS 125 Section #4 RAMs and TMs 9/27/16 1 RAM A word-ram consists of: A fixed set of instructions P 1,..., P q. Allowed instructions are: Modular arithmetic and integer division on registers; the standard
General comments on candidates' performance
 BCS THE CHARTERED INSTITUTE FOR IT BCS Higher Education Qualifications BCS Level 5 Diploma in IT September 2016 Sitting EXAMINERS' REPORT Computer Networks General comments on candidates' performance The
BCS THE CHARTERED INSTITUTE FOR IT BCS Higher Education Qualifications BCS Level 5 Diploma in IT September 2016 Sitting EXAMINERS' REPORT Computer Networks General comments on candidates' performance The
Query Processing: A Systems View. Announcements (March 1) Physical (execution) plan. CPS 216 Advanced Database Systems
 Query Processing: A Systems View CPS 216 Advanced Database Systems Announcements (March 1) 2 Reading assignment due Wednesday Buffer management Homework #2 due this Thursday Course project proposal due
Query Processing: A Systems View CPS 216 Advanced Database Systems Announcements (March 1) 2 Reading assignment due Wednesday Buffer management Homework #2 due this Thursday Course project proposal due
This book is licensed under a Creative Commons Attribution 3.0 License
 6. Syntax Learning objectives: syntax and semantics syntax diagrams and EBNF describe context-free grammars terminal and nonterminal symbols productions definition of EBNF by itself parse tree grammars
6. Syntax Learning objectives: syntax and semantics syntax diagrams and EBNF describe context-free grammars terminal and nonterminal symbols productions definition of EBNF by itself parse tree grammars
Number Systems. Decimal numbers. Binary numbers. Chapter 1 <1> 8's column. 1000's column. 2's column. 4's column
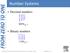 1's column 10's column 100's column 1000's column 1's column 2's column 4's column 8's column Number Systems Decimal numbers 5374 10 = Binary numbers 1101 2 = Chapter 1 1's column 10's column 100's
1's column 10's column 100's column 1000's column 1's column 2's column 4's column 8's column Number Systems Decimal numbers 5374 10 = Binary numbers 1101 2 = Chapter 1 1's column 10's column 100's
Heap Management. Heap Allocation
 Heap Management Heap Allocation A very flexible storage allocation mechanism is heap allocation. Any number of data objects can be allocated and freed in a memory pool, called a heap. Heap allocation is
Heap Management Heap Allocation A very flexible storage allocation mechanism is heap allocation. Any number of data objects can be allocated and freed in a memory pool, called a heap. Heap allocation is
Summer Final Exam Review Session August 5, 2009
 15-111 Summer 2 2009 Final Exam Review Session August 5, 2009 Exam Notes The exam is from 10:30 to 1:30 PM in Wean Hall 5419A. The exam will be primarily conceptual. The major emphasis is on understanding
15-111 Summer 2 2009 Final Exam Review Session August 5, 2009 Exam Notes The exam is from 10:30 to 1:30 PM in Wean Hall 5419A. The exam will be primarily conceptual. The major emphasis is on understanding
Malware, , Database Security
 Malware, E-mail, Database Security Malware A general term for all kinds of software with a malign purpose Viruses, Trojan horses, worms etc. Created on purpose Can Prevent correct use of resources (DoS)
Malware, E-mail, Database Security Malware A general term for all kinds of software with a malign purpose Viruses, Trojan horses, worms etc. Created on purpose Can Prevent correct use of resources (DoS)
Examiners Report. January Pearson Edexcel Functional Skills ICT Level 1 (FST01)
 Examiners Report January 2017 Pearson Edexcel Functional Skills ICT Level 1 (FST01) Edexcel and BTEC Qualifications Edexcel and BTEC qualifications are awarded by Pearson, the UK s largest awarding body.
Examiners Report January 2017 Pearson Edexcel Functional Skills ICT Level 1 (FST01) Edexcel and BTEC Qualifications Edexcel and BTEC qualifications are awarded by Pearson, the UK s largest awarding body.
Number Systems (2.1.1)
 Number Systems (2.1.1) Concept of a register. Operations of register, Complementation, Ranges, Left and right shifts, Addition of two binary number, Numerical overflow, 2 s complement representation, Binary
Number Systems (2.1.1) Concept of a register. Operations of register, Complementation, Ranges, Left and right shifts, Addition of two binary number, Numerical overflow, 2 s complement representation, Binary
Chapter 2. Data Representation in Computer Systems
 Chapter 2 Data Representation in Computer Systems Chapter 2 Objectives Understand the fundamentals of numerical data representation and manipulation in digital computers. Master the skill of converting
Chapter 2 Data Representation in Computer Systems Chapter 2 Objectives Understand the fundamentals of numerical data representation and manipulation in digital computers. Master the skill of converting
